A Cycle-Accurate Soft Error Vulnerability Analysis Framework for FPGA-based Designs
Abstract
Many aerospace and automotive applications use FPGAs in their designs due to their low power and reconfigurability requirements. Meanwhile, such applications also pose a high standard on system reliability, which makes the early-stage reliability analysis for FPGA-based designs very critical.
In this paper, we present a framework that enables fast and accurate early-stage analysis of soft error vulnerability for small FPGA-based designs. Our framework first extracts the post-synthesis netlist from an FPGA design. Then it inserts the bit-flip configuration faults into the design netlist using our proposed interface software. After that, it seamlessly feeds the golden copy and fault copies of the netlist into the open source simulator Verilator for cycle-accurate simulation. Finally, it generates a histogram of vulnerability scores of the original design to guide the reliability analysis. Experimental results show that our framework runs up to 53x faster than the Xilinx Vivado fault simulation with cycle-level accuracy, when analyzing the injected bit-flip faults on the ITC’99 benchmarks.
Index Terms:
FPGA, Reliability, CAD Framework, Soft Error.I Introduction
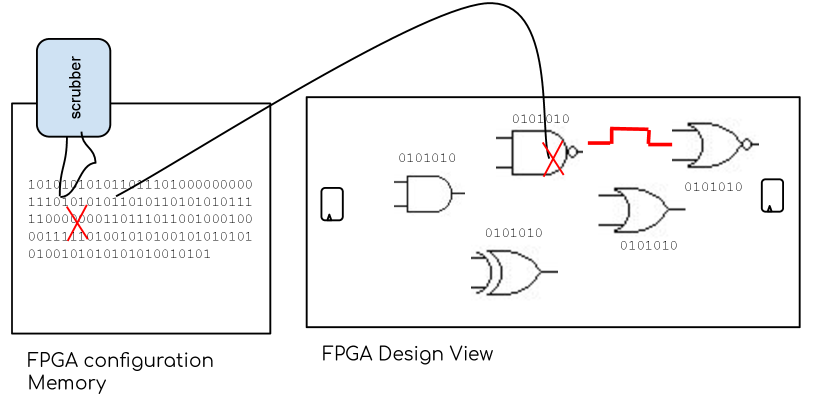
An FPGA usually contains a set of configurable logic blocks (CLBs) and programmable interconnect resources, making it possible to implement flexible digital systems in many areas such as aerospace, automotive, machine learning, and datacenters [1]. In order to have high density and fast configuration speed, the majority of FPGAs use SRAM (Static RAM) technology to store the configuration bitstream. However, SRAM-based FPGAs are vulnerable to radiation induced soft errors [2, 3]. Soft errors may occur with a particle strike to a sensitive region of a transistor in a SRAM cell resulting in an inversion of the logical value, which is called bit-flip. The bit-flips occurring in the FPGA configuration memory remain unchanged during the following cycles. Such bit-flips are permanent and can cause failure in an FPGA-based design. Therefore, it is very important to analyze such bit-flips in FPGA-based designs and provide corresponding protection and/or correction, especially for highly-reliable systems used in aerospace and automotive.
Modern FPGAs often use error correction methods, such as scrubbing, to correct configuration memory bit-flips [4, 1]. As shown in Fig. 1, memory bit-flips are usually corrected using coding mechanisms, or golden models, together with partial reconfiguration [5, 6]. As a result, single event upsets (SEUs) need not be permanent and their consequences can be classified as a transient fault that lasts until a scrubbing occurs. Moreover, if a bit-flip effect is further masked in the circuit design, this error will not be propagated to the circuit outputs. And thus the effect of that bit-flip will be completely transparent to the system. Therefore, to implement a highly-reliable design that still achieves high performance, it is essential to precisely analyze which parts of the FPGA-based design are most vulnerable to soft errors (bit-flips) and thus provide lightweight error protection and/or correction.
As presented in Section II, there are many methods developed to analyze the reliability of FPGA-based designs [9-48]. However, there is still the need for a fast and accurate toolflow, that is open source, to perform early-stage analysis of soft error vulnerability for FPGA-based applications in the design phase.
In this paper, we present a framework that enables fast and cycle-accurate soft error vulnerability analysis of an FPGA-based design using the post-synthesis netlist as input. First, given an initial FPGA design or partial design in the early design stage, our framework extracts the post-synthesis netlist. Based on the extracted netlist, it automatically inserts the bit-flip configuration faults. Then it seamlessly feeds the golden copy and fault copies of the netlist into the open source simulator Verilator [7] to perform cycle-accurate simulation. According to the simulation results, it generates a histogram of vulnerability scores for each component in the original design. To demonstrate the usefulness of our framework, we use it to analyze the reliability of the widely used ITC’99 benchmarks [8] with injected bit-flip faults and show which components are more vulnerable to bit-flip errors. Compared to the Xilinx Vivado fault simulation, our framework runs up to 53x faster while achieving cycle-level accuracy.
| Radiation Techniques | Run-time Reconfiguration | Fault Emulation | Analytical Modelling | Fault Simulation | |
|---|---|---|---|---|---|
| Controllability | low | fair | high | fair | high |
| Run-time | ultra fast | fast | fast | fair | slow |
| Accuracy | very high | high | high | fair | high |
| Flexibility | low | fair | fair | fair | high |
| Design flow stage | prototype | prototype | prototype | early | early |
| Cost | high | fair | fair | low | low |
II Review of Soft Error Analysis for FPGAs
To analyze the vulnerability of soft errors for an FPGA-based design, a common technique (called fault injection) is to intentionally inject faults to disturb some parts of the design and analyze the possibility of changes of its normal behavior [9]. There are many different means to insert artificial faults into an FPGA-based design, and we classify them as follows.
-
1.
Using radiation techniques to induce upsets in actual physical FPGA design [2, 10, 11]: These methods are fast and realistic. But they need a prototype version of the design and cannot be applied in early stages of the design flow. The lack of controllability of fault locations is another weakness. In addition, these methods destroy the equipment and are quite expensive.
-
2.
Modifying configuration memory to force upsets [12, 13, 14, 15, 16, 17]: Some studies try to modify an FPGA’s configuration bitstream file directly, where others modify an FPGA’s configuration memory at run-time using dynamic partial reconfiguration. According to the different configuration ports, these methods can be divided into two categories: external and internal fault injections. Note that they need the prototype version of the design.
-
3.
Emulating faults in FPGAs [18, 19, 20, 21, 22]: These studies add some extra hardware (saboteurs) to the original design and run the modified version on the board to emulate the behaviour of bit-flips. Existing techniques in this subject manipulate the design’s description in RTL (Register-Transfer Level) or post-implementation netlist. These methods need complex internal or external components for controlling the fault injection and inference processes. Therefore, they either need dedicated external hardware platforms or impose considerable area overhead. In addition, they need the prototype version of the design.
- 4.
-
5.
Fault simulation that uses a software simulator to simulate the behaviour of memory upsets for a given design descried in hardware description languages (HDLs) [28, 29, 30, 31, 19, 32, 33, 34, 35, 36, 37, 38]: These methods use either code modification to add mutants and saboteurs or simulator commands to change variable and signal values. Fault simulation offers important advantages over other techniques. They have both high observability and controllability of the faults, and can be applied soon at various level of design abstractions. Hence they are very useful for reliability aware CAD (computer-aided design) tool development. However, fault simulation methods suffer from long run-time.
We summarize the fault injection techniques in Table I and compare their controllability, run-time, accuracy, flexibility, design flow stage, and cost. Considering the pros and cons of fault injection methods, fault simulation is a good choice to analyze the reliability of an FPGA design accurately at early design stages. On one hand, high-level fault simulation suffers from high inaccuracy compared to low-level fault simulation [33]. On the other hand, low-level fault simulation tools [38, 39] use event-driven simulation, and thus, suffer from long execution time and large memory consumption.
In this paper, we explore a cycle-accurate fault simulation framework to enable accurate yet fast soft-error vulnerability analysis for FPGA-based designs. We decide to explore the fault simulation at the post-synthesis netlist level, which can be considered precise because it provides accurate fault injection locations in an already optimized netlist.
III Proposed Framework for Soft error Vulnerability Analysis
The overall structure of our proposed framework is presented in Figure 2. Given an input FPGA circuit described in VHDL or Verilog, it can automatically extract the post-synthesis netlist and insert bit-flips at the basic element (BEL) level, and seamlessly feed the golden and fault copies to the open source simulator Verilator [7] for fast and cycle-accurate simulation. Finally, it will generate a histogram of vulnerability scores for the input circuit. Next, we present more details of each component of our framework.
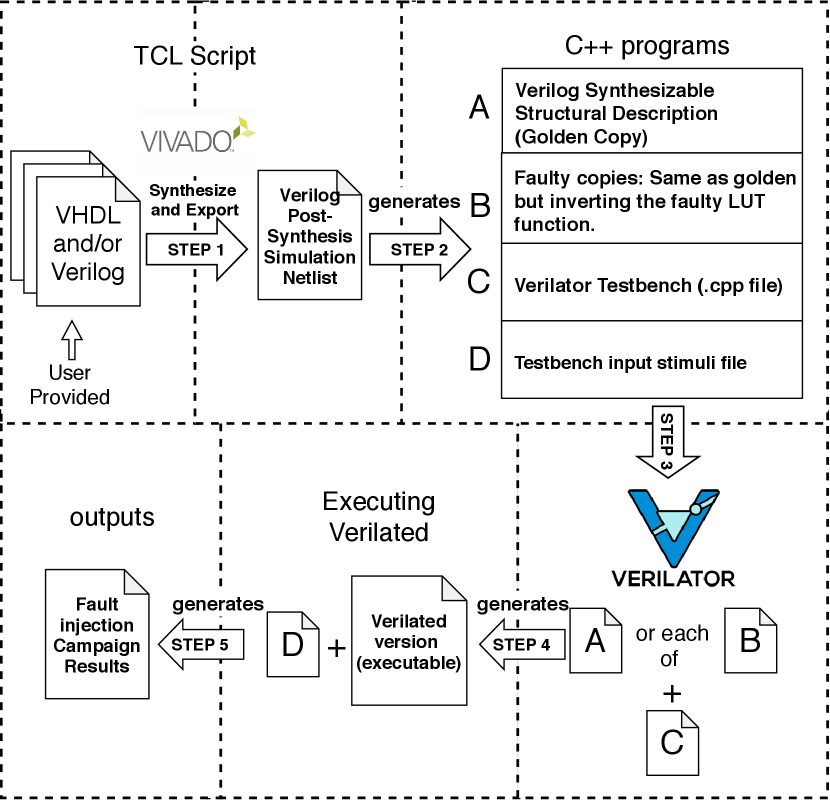
III-A Post-Synthesis Design Netlist Extraction
During the synthesis stage, a digital circuit expressed in synthesizable VHDL or Verilog code is synthesized to a lower level Verilog netlist, with the TCL (Tool Command Language) command ’write_verilog’ in a TCL script to automate the process. This exported Verilog netlist describes a digital circuit in terms of basic elements (BELs) that can be used in a post-synthesis simulation of the circuit. It is a structural description that interconnects the circuit primitive modules (BELs), which are generated by the Xilinx Vivado synthesis tool for the targeted FPGA. Each BEL has its behavioural description defined in a Xilinx proprietary library intended for behavioural simulation purpose only. For each BEL, its proprietary library is then replaced by a synthesizable behavioural Verilog description, so that it can be fed to the open source simulator Verilator for cycle-accurate simulation. Note, that in this work, we use the flatten hierarchy property of the synthesis step and we have no DSP in the synthesis option as the behaviour of faults in DSP elements is out of scope in this paper. Our current post-synthesis netlist extraction is developed for the Xilinx toolflow only; but it can be easily extended for the Intel Quartus toolflow as well.
III-B Interface Software
To seamlessly simulate the post-synthesis netlists in the open source simulator Verilator, we develop an interface software that connects them to facilitate the tool automation. The interface software is a C++ program that performs four major tasks.
-
1.
The first task is to open the exported netlist, add and/or remove some lines of Verilog code to obtain a synthesizable structural description that can be compiled by the Verilator tool. This task only includes the Verilog modules for the BELs in the structural description, generating the minimum necessary code to the Verilator compilation process. The generated Verilog file is going to be used in the fault injection campaign as the “golden copy”.
-
2.
The second task is to generate the input stimuli that will be used by the Verilator testbench during the fault injection campaign. The input stimuli can be generated in two different ways. First, for an extensive fault injection campaign, it generates all combinations of input stimuli. Second, when the extensive campaign is not feasible due to the long simulation time, it generates a pseudo-random fault injection input stimuli. In the pseudo-random case, the C++ software uses the boost C++ library to generate the pseudo-random integer numbers in a uniform distribution that is converted to its binary correspondent.
-
3.
The third task is to automatically generate the testbench that wraps the C++ model of the Verilog structural description. This testbench file, when executed, receives two parameters: the stimuli input file generated in the second task and the desired output file name to write the testbench results. The testbench algorithm can be summarized into three different stages. The first stage is the input stimuli read; the second is the input injection (including the clock event generation); and the last stage is reading the output from the Verilator simulator and writing the results to the output file. These three stages are repeated for the number of cycles intended for which the simulation runs.
-
4.
The fourth task is to generate all the faulty copies of the golden circuit by inverting only the logic function programmed at each lookup-table (LUT) for each file. Each copy has only one faulty component and in this case, the total number of faulty copies is equal to the total number of LUTs. In our current tool, only one LUT function is inverted in each file. But it can be easily extended to support fault injection at multiple LUTs and other types of BELs, which is left for future work.
III-C Cycle-Accurate Fault Simulation
Verilator is a cycle-accurate open source simulator [7]. Compared to an event-driven simulator—such as Xilinx Vivado logic simulator, which executes processes based on event triggering—Verilator executes the whole design in a topological order at every simulation cycle. Thus, the number of simulator-specific variables is significantly reduced and the simulation time is much faster. In our framework, Verilator takes the Verilog description and compiles the code into a much faster optimized and optionally thread-partitioned model. This model is then wrapped into a C++ module, all using parameters similar to GCC or Synopsys’s VCS that can be easily automated with Makefiles and the make command, available in any Unix and Unix-like operating systems.
III-D Vulnerability Score Histogram Generation
To better guide the soft error vulnerability analysis, we also calculate a normalized vulnerability score for each LUT and generate a histogram of vulnerability scores for all the LUTs in the design. The vulnerability score for each LUT is calculated as follows. First, for each output bit of a LUT, we multiply 1) the error possibility based on simulation results by 2) its weight, which can be configured by users (the default weight value is 1 for all output bits). Second, we divide the sum of all products calculated in the first step by the sum of all weights of output bits to get the vulnerability score for a LUT. The histogram of vulnerability scores for all the LUTs demonstrate which LUTs are more vulnerable to the bit-flip errors.
IV Fault Simulation Tool Comparison
To demonstrate the performance gain of cycle-accurate simulation using Verilator in our framework, we compare it to the Xilinx Vivado ISIM simulator. Both simulators are evaluated with the widely used ITC’99 benchmark subset circuits [8].
Both simulators are parallelized using the make command with the -j option and use 12 cores. Ideally, the each circuit should be simulated with all possible combinations of inputs. But as this number grows exponentially with the product of the number of input bits and the number of intended simulation cycles, we decided to use 1,024 pseudo-random input combinations due to the long time run. It already takes several hours to run the 1,024 input stimulus for the biggest circuit. Table II presents the simulation performance comparison for the Verilator and Vivado simulators. As shown in column 5, the cycle-accurate Verilator simulator is from 9.7 up to 53.8 times faster than the Vivado ISIM simulator. This is because the Verilator simulator compiles the Verilog code into a much faster optimized model and does not model intra-cycle events.
| Time (s) | Speedup of | |||
|---|---|---|---|---|
| Circuit | Num. of LUTs | Vivado | Verilator | Verilator |
| b01 | 5 | 17 | 0.45 | 37.8 |
| b02 | 4 | 16 | 0.56 | 28.6 |
| b03 | 23 | 50 | 1.49 | 33.6 |
| b04 | 85 | 200 | 7.59 | 26.4 |
| b05 | 109 | 276 | 13.75 | 20.1 |
| b06 | 8 | 22 | 0.73 | 30.1 |
| b07 | 63 | 152 | 5.13 | 29.6 |
| b08 | 18 | 46 | 3.51 | 13.1 |
| b09 | 34 | 72 | 1.47 | 49.0 |
| b10 | 34 | 85 | 1.58 | 53.8 |
| b11 | 82 | 194 | 7.13 | 27.2 |
| b12 | 213 | 609 | 37.7 | 16.2 |
| b13 | 45 | 102 | 3.16 | 32.3 |
| b14 | 1073 | 6219 | 642 | 9.7 |
V Use Cases of Our Framework
To demonstrate the usefulness of our framework, we conduct two case studies.
V-A Case Study #1: Cycle-Level Error Possibility
In this case study, we demonstrate how one can use our framework to analyze the possibility that each LUT output bit can be affected by an input bit-flip error, as the time goes cycle by cycle. We choose this granularity because sometimes a certain output bit may represent vital output information, for example, whether the circuit is ready or not (’1’ or ’0’). To calculate the error possibility for each output bit of a LUT, we simulate the circuit with each faulty input combination. If there is an error in the output bit (comparing to the golden copy), its corresponding error counter (per output bit per cycle) is incremented by one. The corresponding error possibility is computed by dividing the total number of counted errors by the total number of simulation runs (i.e. input combinations). This process is repeated for every cycle. At the end, we generate an error possibility distribution for each LUT output bit cycle by cycle.
As an example, let us consider the circuit b01 of the ITC’99 benchmark. Table III presents the detailed error possibility for each output bit of each LUT from cycle 1 to 4 by simulating the b01 circuit using our framework. Each row of the table presents the error possibility observed in each output bit of each LUT at each cycle. The ’Total’ column presents the error possibility considering at least one error in the total run. The total error metric is adjustable so that application designers can create and utilize different approaches to calculate the total error value that are appropriate according to their knowledge of the application.
| Cycle | ||||||
| LUT | Output bit | 1 | 2 | 3 | 4 | Total |
| FSM_st[0] | outp | 0 | 0.25 | 0.38 | 0.44 | 0.25 |
| FSM_st[0] | overflw | 0 | 0.25 | 0.25 | 0.22 | 0.25 |
| FSM_st[1] | outp | 0 | 0 | 0 | 0 | 0 |
| FSM_st[1] | overflw | 0 | 0 | 0 | 0 | 0 |
| FSM_st[2] | outp | 0 | 1 | 0.5 | 0 | 1 |
| FSM_st[2] | overflw | 0 | 0 | 0 | 0.62 | 0 |
| outp_i_1 | outp | 1 | 1 | 1 | 1 | 1 |
| outp_i_1 | overflw | 0 | 0 | 0 | 0 | 0 |
| overflw_i_1 | outp | 0 | 0 | 0 | 0 | 0 |
| overflw_i_1 | overflw | 1 | 1 | 1 | 1 | 1 |
As shown in Table III, there is one LUT (FSM_st[1]) that has no errors at the outputs. This is because the circuit topology has a reconvergence path. The fault propagates through two different paths and converges back to a specific component, where the bit flips twice resulting in an always masking condition. There are three LUTs that have a total error value of 100%. Two of them (overflw_i_1 and outp_i_1) are very close to the outputs and the third is the most significant bit of the circuit FSM (Finite State Machine) state register (the FSM_st[2]).
Such analysis gives designers some guidance into which LUTs they should pay most attention to for better system reliability. This works well for small circuits that do not have too many LUTs, or a partial circuit that designers want to dive into for more details. Note that one can also perform such analysis per LUT, instead of per output bit of each LUT.
V-B Case Study #2: Histogram of Vulnerability Scores
In this case study, we demonstrate how one can use our framework to analyze which LUTs are more vulnerable to bit-flip errors in a circuit at a higher level, by analyzing the histogram of vulnerability scores of all LUTs. For illustrative purpose, we consider that all LUT output bits have the same importance (i.e., same weight 1) for the overall circuit functionality. We run the fault simulation for the ITC’99 benchmark subset circuits for 10 cycles to calculate the total error possibility for each LUT output bit as explained in case study #1. Designers can configure the weights in our framework and decide how many cycles to simulate when they have better knowledge of the application.
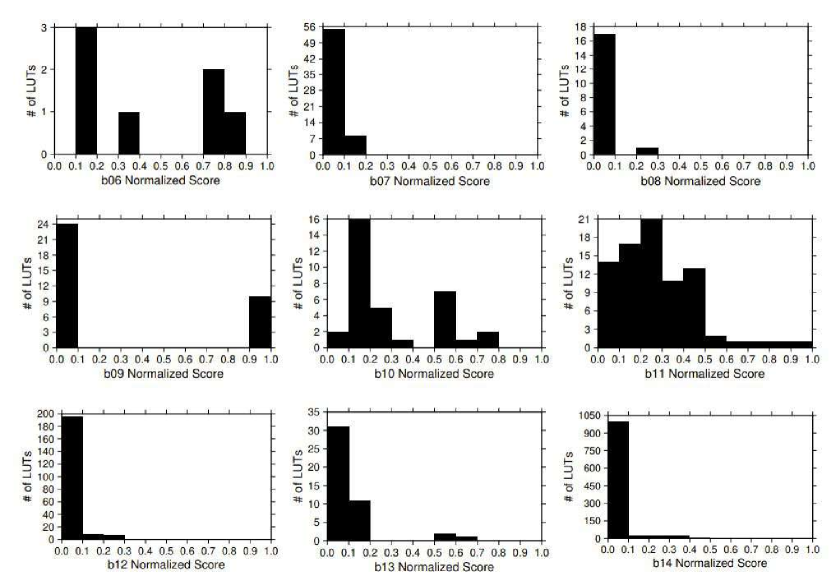
Figure 3 presents the histograms for some circuits in the ITC’99 benchmark subset. Each sub-figure shows the number of LUTs (y-axis) that fit within a 0.1 normalized vulnerability score range (x-axis) for a circuit. As shown in Figure 3, for some circuits, the majority of LUTs have normalized vulnerability scores below or equal to 0.5, e.g., circuits b07, b08, b11, b12, b13 and b14. Such circuits are less vulnerable to bit-flip errors. For the small portion of LUTs that have normalized vulnerability scores above 0.5, one can afford to protect them using an expensive yet effective method like TMR (Triple Modular Redundancy) technique [40]. On the other hand, some circuits, such as b06, b09 and b10, have a significant amount of LUTs with normalized vulnerability score above 0.5. Such circuits are more vulnerable to bit-flip errors and need more protection. In order to reduce the overhead of the error protection circuit, one may consider to apply the more lightweight DWC (Duplication With Comparison) technique [41] or even redesign the circuit to reduce the number of vulnerable LUTs.
VI Application for Large-scale Circuits
The proposed fault simulation is not limited to small circuits, but it can be challenging to perform the fault simulation on large designs due to the computational complexity involved. Large FPGA designs can have thousands or even millions of BLEs, making it impractical to simulate every possible fault (even random faults) in the circuit.
To address this issue, partitioning techniques can be used to divide the large design into smaller, more manageable parts that can be simulated individually via the proposed accurate method. The design can be partitioned based on various criteria, such as functional blocks, critical parts, or input/output interfaces. Each partition can then be simulated separately using the proposed cycle-accurate fault simulation techniques, and the results can be combined to obtain the overall reliability of the design. In addition, it can also help identify potential problems in specific parts (i.e. critical parts) of a large design, allowing for targeted optimization and testing.
VII Conclusion
In this paper, we have presented a framework that enables fast and cycle-accurate analysis of soft error vulnerability for FPGA-based circuits in the early design stage. The fault model is at the basic element (BEL) level in an already optimized post-synthesis netlist. In our framework, a post synthesis netlist is first extracted for a given FPGA design or partial design. Then, bit-flip errors are inserted at BEL level. Both the golden copy and faulty copies run through the cycle-accurate simulator Verilator to identify the effects of faulty LUTs. By applying user-defined weights to each output bit, a histogram of vulnerability scores will be generated to guide designers to identify and rank the more vulnerable LUTs in the design. Two case studies have been conducted on the widely used ITC’99 benchmark circuits to demonstrate the usefulness of our framework: one on cycle-level error possibility analysis for each LUT output, and the other on histogram of vulnerability scores of all LUTs. In general, our framework is up to 53x faster than the Xilinx Vivado simulation, while achieving cycle-level accuracy.
References
- [1] Wikipedia, “Field-programmable gate array,” 2020. [Online]. Available: https://en.wikipedia.org/wiki/Field-programmable_gate_array
- [2] A. M. Keller, T. A. Whiting, K. B. Sawyer, and M. J. Wirthlin, “Dynamic seu sensitivity of designs on two 28-nm sram-based fpga architectures,” IEEE Transactions on Nuclear Science, vol. 65, no. 1, pp. 280–287, Jan 2018.
- [3] D. S. Lee, G. R. Allen, G. Swift, M. Cannon, M. Wirthlin, J. S. George, R. Koga, and K. Huey, “Single-event characterization of the 20 nm xilinx kintex ultrascale field-programmable gate array under heavy ion irradiation,” in 2015 IEEE Radiation Effects Data Workshop (REDW), July 2015, pp. 1–6.
- [4] I. Herrera-Alzu and M. Lopez-Vallejo, “Design techniques for xilinx virtex fpga configuration memory scrubbers,” IEEE Transactions on Nuclear Science, vol. 60, no. 1, pp. 376–385, Feb 2013.
- [5] A. Sari and M. Psarakis, “Scrubbing-based seu mitigation approach for systems-on-programmable-chips,” in 2011 International Conference on Field-Programmable Technology, Dec 2011, pp. 1–8.
- [6] A. Stoddard, A. Gruwell, P. Zabriskie, and M. J. Wirthlin, “A hybrid approach to fpga configuration scrubbing,” IEEE Transactions on Nuclear Science, vol. 64, no. 1, pp. 497–503, Jan 2017.
- [7] W. Snyder, “Verilator: Open simulation-growing up,” 2013, https://www.veripool.org/wiki/verilator.
- [8] F. Corno, M. S. Reorda, and G. Squillero, “Rt-level itc’99 benchmarks and first atpg results,” IEEE Design Test of Computers, vol. 17, no. 3, pp. 44–53, July 2000.
- [9] J. Arlat, M. Aguera, L. Amat, Y. Crouzet, J. . Fabre, J. . Laprie, E. Martins, and D. Powell, “Fault injection for dependability validation: a methodology and some applications,” IEEE Transactions on Software Engineering, vol. 16, no. 2, pp. 166–182, Feb 1990.
- [10] M. Alderighi, F. Casini, S. D’Angelo, S. Pastore, G. R. Sechi, and R. Weigand, “Evaluation of single event upset mitigation schemes for sram based fpgas using the flipper fault injection platform,” in Proceedings of the 22nd IEEE International Symposium on Defect and Fault-Tolerance in VLSI Systems, ser. DFT ’07. USA: IEEE Computer Society, 2007, p. 105–113.
- [11] A. M. Keller and M. J. Wirthlin, “Single-event characterization of a stratix® 10 fpga using neutron irradiation,” in 2019 IEEE Radiation Effects Data Workshop, July 2019, pp. 1–6.
- [12] M. Violante, L. Sterpone, M. Ceschia, D. Bortolato, P. Bernardi, M. S. Reorda, and A. Paccagnella, “Simulation-based analysis of seu effects in sram-based fpgas,” IEEE Transactions on Nuclear Science, vol. 51, no. 6, pp. 3354–3359, Dec 2004.
- [13] U. Legat, A. Biasizzo, and F. Novak, “Automated seu fault emulation using partial fpga reconfiguration,” in 13th IEEE Symposium on Design and Diagnostics of Electronic Circuits and Systems, April 2010, pp. 24–27.
- [14] L. Sterpone and M. Violante, “A new partial reconfiguration-based fault-injection system to evaluate seu effects in sram-based fpgas,” IEEE Transactions on Nuclear Science, vol. 54, no. 4, pp. 965–970, Aug 2007.
- [15] L. Bozzoli, C. De Sio, L. Sterpone, and C. Bernardeschi, “Pyxel: An integrated environment for the analysis of fault effects in sram-based fpga routing,” in 2018 International Symposium on Rapid System Prototyping (RSP), Oct 2018, pp. 70–75.
- [16] A. Ullah, P. Reviriego, and J. A. Maestro, “An efficient methodology for on-chip seu injection in flip-flops for xilinx fpgas,” IEEE Transactions on Nuclear Science, vol. 65, no. 4, pp. 989–996, April 2018.
- [17] Xilinx, “Pg036 -soft error mitigation controller v4.1 product guide (v4.1),” 2018, https://www.xilinx.com/support/documentation.
- [18] M. Ebrahimi, A. Mohammadi, A. Ejlali, and S. G. Miremadi, “A fast, flexible, and easy-to-develop fpga-based fault injection technique,” Microelectronics Reliability, vol. 54, no. 5, pp. 1000 – 1008, 2014.
- [19] W. Mansour and R. Velazco, “An automated seu fault-injection method and tool for hdl-based designs,” IEEE Transactions on Nuclear Science, vol. 60, no. 4, pp. 2728–2733, Aug 2013.
- [20] J. Baraza, J. Gracia, S. Blanc, D. Gil, and P. Gil, “Enhancement of fault injection techniques based on the modification of vhdl code,” IEEE Transactions on Very Large Scale Integration (VLSI) Systems, vol. 16, no. 6, pp. 693–706, June 2008.
- [21] H. Guzman-Miranda, J. N. Tombs, and M. A. Aguirre, “Ft-unshades-up: A platform for the analysis and optimal hardening of embedded systems in radiation environments,” in 2008 IEEE International Symposium on Industrial Electronics, June 2008, pp. 2276–2281.
- [22] J. M. Mogollon, H. Guzmán-Miranda, J. Nápoles, J. Barrientos, and M. A. Aguirre, “Ftunshades2: A novel platform for early evaluation of robustness against see,” in 2011 12th European Conference on Radiation and Its Effects on Components and Systems, Sep. 2011, pp. 169–174.
- [23] A. Sari, D. Agiakatsikas, and M. Psarakis, “A soft error vulnerability analysis framework for xilinx fpgas,” in Proceedings of the 2014 ACM/SIGDA International Symposium on Field-Programmable Gate Arrays, ser. FPGA ’14. New York, NY, USA: Association for Computing Machinery, 2014, p. 237–240.
- [24] K. Huang, Y. Hu, and X. Li, “Reliability-oriented placement and routing algorithm for sram-based fpgas,” IEEE Transactions on Very Large Scale Integration (VLSI) Systems, vol. 22, no. 2, pp. 256–269, Feb 2014.
- [25] L. Sterpone and M. Violante, “A new analytical approach to estimate the effects of seus in tmr architectures implemented through sram-based fpgas,” IEEE Transactions on Nuclear Science, vol. 52, no. 6, pp. 2217–2223, Dec 2005.
- [26] L. Cassano, H. Guzman-Miranda, and M. A. Aguirre, “Early assessment of seu sensitivity through untestable fault identification,” in 2014 IEEE 20th International On-Line Testing Symposium (IOLTS), July 2014, pp. 186–189.
- [27] O. Heron, T. Arnaout, and H. . Wunderlich, “On the reliability evaluation of sram-based fpga designs,” in International Conference on Field Programmable Logic and Applications, 2005., Aug 2005, pp. 403–408.
- [28] C. Robach and M. Scholive, “Simulation-based fault injection and testing unsing the mutation technique,” in Fault injection techniques and tools for embedded systems reliability evaluation. Springer, 2003, pp. 195–215.
- [29] D. Gil, J. Gracia, J. C. Baraza, and P. J. Gil, “Study, comparison and application of different vhdl-based fault injection techniques for the experimental validation of a fault-tolerant system,” Microelectronics Journal, vol. 34, no. 1, pp. 41–51, 2003.
- [30] A. Bosio and G. D. Natale, “Lifting: A flexible open-source fault simulator,” in 2008 17th Asian Test Symposium, Nov 2008, pp. 35–40.
- [31] J. C. Baraza, J. Gracia, D. Gil, and P. J. Gil, “Improvement of fault injection techniques based on vhdl code modification,” in Tenth IEEE International High-Level Design Validation and Test Workshop, 2005., Nov 2005, pp. 19–26.
- [32] W. Mansour, R. Velazco, R. Ayoubi, H. Ziade, and W. El Falou, “A method and an automated tool to perform set fault-injection on hdl-based designs,” in 2013 25th International Conference on Microelectronics (ICM), Dec 2013, pp. 1–4.
- [33] E. Carlisle, N. Wulf, J. MacKinnon, and A. George, “Drseus: A dynamic robust single-event upset simulator,” in 2016 IEEE Aerospace Conference, March 2016, pp. 1–11.
- [34] V. Sieh, O. Tschache, and F. Balbach, “Verify: evaluation of reliability using vhdl-models with embedded fault descriptions,” in Proceedings of IEEE 27th International Symposium on Fault Tolerant Computing, June 1997, pp. 32–36.
- [35] W. Chao, F. Zhongchuan, C. Hongsong, and C. Gang, “Fsfi: A full system simulator-based fault injection tool,” in 2011 First International Conference on Instrumentation, Measurement, Computer, Communication and Control, Oct 2011, pp. 326–329.
- [36] M. Kooli and G. Di Natale, “A survey on simulation-based fault injection tools for complex systems,” in 2014 9th IEEE International Conference on Design Technology of Integrated Systems in Nanoscale Era (DTIS), May 2014, pp. 1–6.
- [37] D. Kammler, J. Guan, G. Ascheid, R. Leupers, and H. Meyr, “A fast and flexible platform for fault injection and evaluation in verilog-based simulations,” in 2009 Third IEEE International Conference on Secure Software Integration and Reliability Improvement, July 2009, pp. 309–314.
- [38] C. Bernardeschi, L. Cassano, A. Domenici, and L. Sterpone, “Assess: A simulator of soft errors in the configuration memory of sram-based fpgas,” IEEE Transactions on Computer-Aided Design of Integrated Circuits and Systems, vol. 33, no. 9, pp. 1342–1355, Sep. 2014.
- [39] ——, “Accurate simulation of seus in the configuration memory of sram-based fpgas,” in 2012 IEEE International Symposium on Defect and Fault Tolerance in VLSI and Nanotechnology Systems (DFT), Oct 2012, pp. 115–120.
- [40] F. L. Kastensmidt, L. Sterpone, L. Carro, and M. S. Reorda, “On the optimal design of triple modular redundancy logic for sram-based fpgas,” in Design, Automation and Test in Europe, March 2005, pp. 1290–1295 Vol. 2.
- [41] F. G. de Lima Kastensmidt, G. Neuberger, R. F. Hentschke, L. Carro, and R. Reis, “Designing fault-tolerant techniques for sram-based fpgas,” IEEE Design Test of Computers, vol. 21, no. 6, pp. 552–562, Nov 2004.