11email: {gustun,cluna,adrians}@fing.edu.uy 22institutetext: CIFASIS, Universidad Nacional de Rosario, Argentina.
22email: cristia@cifasis-conicet.gov.ar
A Formal Analysis of the MimbleWimble Cryptocurrency Protocol
Abstract
MimbleWimble (MW) is a privacy-oriented cryptocurrency technology which provides security and scalability properties that distinguish it from other protocols of its kind.
We present and discuss those properties and outline the basis of a model-driven verification approach to address the certification of the correctness of the protocol implementations.
In particular, we propose an idealized model that is key in the described verification process, and identify and precisely state sufficient conditions for our model to ensure the verification of relevant security properties of MW. Since MW is built on top of a consensus protocol, we develop a Z specification of one such protocol and present an excerpt of the prototype generated from the Z specification. This prototype can be used as an executable model where simulations can be run. This allows us to analyze the behavior of the protocol without having to implement it in a low level programming language.
Finally, we analyze the Grin and Beam implementations of MW in their current state of development.
Keywords: Cryptocurrency, MimbleWimble, Idealized model, Formal verification, Security.
1 Introduction
Cryptocurrency protocols deal with virtual money so they are a valuable target for highly skilled attackers. Several attacks have already been mounted against cryptocurrency systems, causing irreparable losses of money and credibility (e.g. [18]). For this reason the cryptocurrency community is seeking approaches, methods, techniques and development practices that can reduce the chances of successful attacks. One such approach is the application of formal methods to software implementation. In particular, the cryptocurrency community is showing interest in formal proofs and formally certified implementations [54, 31] .
MimbleWimble (MW) is a privacy-oriented cryptocurrency technology encompassing security and scalability properties that distinguish it from other technologies of its kind. MW was first proposed in 2016 [44]. The idea was then further developed by Poelstra [52]. In MW, unlike Bitcoin [50], there exists no concept of address and all the transactions are confidential. In this paper we outline an approach based on formal software verification aimed at formally verifying the basic mechanisms of MW and its implementations [43, 27].
We put forward a model-driven verification approach where security issues that pertain to the realm of critical mechanisms of the MW protocol are explored on an idealized model of this system. Such model abstracts away the specifics of any particular implementation, and yet provides a realistic setting. Verification is then performed on more concrete models, where low level mechanisms are specified. Finally the low level model is proved to be a correct implementation of the idealized model.
Security (idealized) models have played an important role in the design and evaluation of high assurance security systems. Their importance was already pointed out in the Anderson report [1]. The paradigmatic Bell-LaPadula model [9], conceived in 1973, constituted the first big effort on providing a formal setting in which to study and reason on confidentiality properties of data in time-sharing mainframe systems. State machines can be employed as the building block of a security model. The basic features of a state machine model are the concepts of state and state change. A state is a representation of the system under study at a given time, which should capture those aspects of the system that are relevant to the analyzed problem. State changes are modeled by a state transition function that defines the next state based on the current state and input. If one wants to analyze a specific safety property of a system using a state machine model, one must first specify what it means for a state to satisfy the property, and then check if all state transitions preserve it. Thus, state machines can be used to model the enforcement of a security policy.
Related work
Developers of cryptocurrency software have already shown interest in using mathematics as a tool to describe software. In fact, Nakamoto uses maths in his seminal paper on Bitcoin [50] and Wood uses it to describe the EVM [60]. However, these descriptions can not be understood as Formal Methods (FM) because they are not based on standardized notations nor on clear mathematical theories.
On the other hand the FM community has started to pay attention to cryptocurrency software. Idelberger et al. [42] proposed to use defeasible logic frameworks such as Formal Contract Logic for the description of smart contracts. Bhargavan et al. [14] compile Solidity programs into a verification-oriented functional language where they can verify source code. Luu et al. [47] use the Oyente tool to find and detect vulnerabilities in smart contracts. Hirai [40] uses Lem to formally specify the EVM; Grishchenko, Maffei and Schneidewind [38] also formalize the EVM but in F*; and Hildenbrandt et al. do the same but with the reachability logic system known as . Pîrlea and Sergey [51] present a Coq [57, 10] formalization of a blockchain consensus protocol where some properties are formally verified.
More recently, Rosu [54] presented academic and commercial results in developing blockchain languages and virtual machines that come directly equipped with formal analysis and verification tools. Hajdu et al. [39] developed a source-level approach for the formal specification and verification of Solidity contracts with the primary focus on events. Santos Reis et al. [53] introduced Tezla, an intermediate representation of Michelson smart contracts that eases the design of static smart contract analysers. In [17], Boyd et al. presented a blockchain model in Tamarin, that is useful for analyzing certain blockchain based protocols. On the other hand, Garfatta et al. [31] described a general overview of the different axes investigated actually by researchers towards the (formal) verification of Solidity smart contracts.
Additionally, Metere and Dong [49] present a mechanised formal verification of the Pedersen commitment protocol using EasyCrypt [2] and Fuchsbaue et al. [28] introduce an abstraction for the analysis of some security properties of MW. Our work assumes some of these results to formalize and analyze the MW protocol, to then propose a methodology to verify their implementations.
Finally, in Betarte et al. [11] we outline some formal methods related techniques that we consider particularly useful for cryptocurrency software. We present some guidelines for the adoption of formal methods in cryptocurrency software projects. We argue that set-based formal modeling (or specification), simulation, prototyping and automated proof can be applied before considering more powerful approaches such as code formal verification. In particular, we show excerpts of a set-based formal specification of a consensus protocol and of the Ethereum Virtual Machine. We also exhibit that prototypes can be generated from these formal models and simulations can be run on them. By last, we show that test cases can be generated from the same models and how automated proofs can be used to evaluate the correctness of these models. The work we present here closely follows the approach of [11].
Contribution
This article builds upon and extends a previously published paper in AIBlock 2020 [13]111A preliminary version of that work is also available on arXiv [12].. In that paper, we present elements that comprise the essential steps towards the development of an exhaustive formalization of the MW cryptocurrency protocol and the analysis of some of its properties. The proposed idealized model constitutes the main contribution together with the analysis of the essential properties it is shown to verify. We have also introduced and discussed the basis of a model-driven verification approach to address the certification of the correctness of a protocol’s implementation.
In the present paper we extend both the definition of the MimbleWimble protocol and the idealized model. In particular, the formal definition and discussion of the notion of commitment scheme in Section 2.3 is completely new. We have also extended the section where we study the security properties of MW, incorporating the discussion on the security properties of Pedersen commitments in Section 4.3. We study the strength of the scheme regarding the main security properties a cryptocurrency protocol must have. The sections Model-driven verification and Mimblewimble implementations are also new. In the first one, since MW is built on top of a consensus protocol, we develop a Z specification of one such protocol and present an excerpt of the prototype generated from the Z specification. This prototype can be used as an executable model where simulations can be run. This allows us to analyze the behavior of the protocol without having to implement it in a low level programming language. Finally, we compare two MW implementations, Grin [43] and Beam [27], with our model and we discuss some features that set them apart.
Organization of the paper
The rest of the paper is organized as follows. Section 2 provides a brief description of MW. Section 3 describes the building blocks of a formal idealized model (abstract state machine) of the computational behaviour of MimbleWimble. Sections 4 and 5 provide a account of the verification activities we are putting in place in order to verify the protocol and its implementation. Then, Section 6 analyzes the Grin and Beam implementations of MW in their current state of development. Final remarks and directions for future work are presented in Section 7.
2 The MimbleWimble protocol
Confidential transactions [48, 32] are at the core of the MW protocol. A transaction allows a sender to encrypt the amount of bitcoins by using blinding factors. In a confidential transaction only the two parties involved know the amount of bitcoins being exchanged. However, for anyone observing that transaction it is possible to verify its validity by comparing the number of inputs and outputs; if both are the same, then the transaction will be considered valid. Such procedure ensures that no bitcoins have been created from nothing and is key in preserving the integrity of the system. In MW transactions, the recipient randomly selects a range of blinding factors provided by the sender, which are then used as proof of ownership by the receiver.
The MW protocol aims at providing the following properties [44, 43]:
-
•
Verification of zero sums without revealing the actual amounts involved in a transaction, which implies confidentiality.
-
•
Authentication of transaction outputs without signing the transaction.
-
•
Good scalability, while preserving security, by generating smaller blocks—or better, reducing the size of old blocks, producing a blockchain whose size does not grow in time as much as, for instance, Bitcoin’s.
The first two properties are achieved by relying on Elliptic Curves Cryptography (ECC) operations and properties. The third one is a consequence of the first two.
2.1 Verification of transactions
If is the value of a transaction (either input or output) and is a point over an elliptic curve, then encrypts because it is assumed to be computationally hard to get from if we only know . However, if and are other values such that , then if we only have the result of encrypting each of them with we are still able to verify that equation. Indeed:
due to simple properties of scalar multiplication over groups. Therefore, with this simple operations, we can check sums of transactions amounts without knowing the actual amounts.
Nevertheless, say some time ago we have encrypted with and now we see , then we know that it is the result of encrypting . In the context of blockchain transactions this is a problem because once a block holding is saved in the chain it will reveal all the transactions of coins. For such problems, MW encrypts as where is a scalar and is another point in ’s elliptic curve, is called blinding factor and is called Pedersen commitment. By using Pedersen commitments, MW allows the verification of expressions such as providing more privacy than the standard scheme. In effect, if then we choose , and such that and so the expression is recorded as:
making it possible for everyone to verify the transaction without knowing the true values.
2.2 Authentication of transactions
Consider that Alice has received coins and this was recorded in the blockchain as , where was chosen by her to keep it private. Now she wants to transfer these coins to Bob. As a consequence, Alice looses coins and Bob receives the very same amount, which means that the transaction adds to zero: . However, Alice now knows Bob’s blinding factor because it must be the same chosen by her (so the transaction is balanced). In order to protect Bob from being stolen by Alice, MW allows Bob to add his blinding factor, , in such a way that the transaction is recorded as:
although now it does not sum zero. However, this excess value is used as part of an authentication scheme. Indeed, Bob uses as a private key to sign the empty string (). This signed document is attached to the transaction so in the blockchain we have:
-
•
Input: .
-
•
Output: .
-
•
Bob’s signed document: .
This way, the transaction is valid if the result of decrypting with (in the group generated by ) yields . If does not yield something in the form of , then will not be recovered and so we know there is an attempt to create money from thin air or there is an attempt to steal Bob’s money.
2.3 Commitment Scheme
A commitment scheme [20] is a two-phase cryptographic protocol between two parties: a sender and a receiver. At the end of the commit phase the sender is committed to a specific value that he cannot change later and the receiver should have no information about the committed value.
A non-interactive commitment scheme [19] can be defined as follows:
Definition 1 (Non-interactive Commitment Scheme)
A non-interactive commitment scheme consists of two probabilistic polynomial time algorithms, and , such that:
-
•
generates public parameters for the scheme depending on the security parameter .
-
•
is the commitment algorithm: , where is the message space, the randomness space and the commitment space. For a message , the algorithm draws uniformly at random and computes the commitment .
We have simplified the notation, but it is important to keep in mind that all the sets depend on the public parameters, in particular, the commitment algorithm.
It is said that the commitment scheme is homomorphic if:
In other words, is additive in both parameters.
Transactions in MW are derived from confidential transactions [48], which are enabled by Pedersen commitments with homomorphic properties over elliptic curves. We define the non-interactive Pedersen commitment scheme we will use in our model, based on Definition 1, as follows:
Definition 2 (Pedersen Commitment Scheme with Elliptic Curves)
As in Definition 1, let and be the finite field and let be the set of points determined by an elliptic curve of prime order .
The probabilistic polynomial time algorithms are defined as:
-
•
generates the order (dependent on the security parameter ) and two generator points and on the elliptic curve of prime order whose discrete logarithms relative to each other are unknown.
-
•
, with the transactional value and the blinding factor choosen randomly in .
Security properties of this commitment scheme (for MW) will be analyzed in Section 4.3.
3 Idealized model of MimbleWimble-based blockchain
The basic elements of our model are transactions, blocks and chains. Each node in the blockchain maintains a local state. The main components are the local copy of the chain and the set of transactions waiting to be validated and added to a new block. Moreover, each node keeps track of unspent transaction outputs (UTXOs). Properties such as zero-sum and the absence of double spending in blocks and chains must be proved for local states. The blockchain global state can be represented as a mapping from nodes to local states. For global states, we can state and prove properties for the entire system like, for instance, correctness of the consensus protocol.
3.1 Transactions
Given two fixed generator points and on the elliptic curve of prime order (whose discrete logarithms relative to each other are unknown), we define a single transaction between two parties as follows:
Definition 3 (Transaction)
A single transaction is a tuple of type:
with representing the lists of elements of type and where:
-
•
and are the lists of inputs and outputs. Each input and output are points over the curve and they are the result of computing the Pedersen commitment with the blinding factor and the transactional value in the finit field .
-
•
is the transaction kernel where:
-
–
is a list of range proofs of the outputs.
-
–
is the transaction excess represented by .
-
–
is the kernel signature222For simplicity, fees are left aside..
-
–
-
•
is the transaction kernel offset.
The transaction kernel offset will be used in the construction of a block to satisfy security properties.
Definition 4 (Ownership)
Given a transaction , we say owns the output if knows the opening for the Pedersen commitment .
The strength of this security definition is directly related to the difficulty of solving the logarithm problem. If the elliptic curve discrete logarithm problem in is hard then given a multiple of , it is computationally infeasible to find an integer such that .
Definition 5 (Balanced Transaction)
A transaction , with transaction kernel , is balanced if the following holds:
A balanced transaction guarantees no money is created from thin air and the transaction was honestly constructed.
Property 1 (Valid Transaction)
A transaction is valid () if satisfies:
-
i.
The range proofs of all the outputs are valid.
-
ii.
The transaction is balanced.
-
iii.
The kernel signature is valid for the excess.
These three properties have a straightforward interpretation in our model. Due to limitations of space, we formalize and analyze in this paper only some of the properties mentioned throughout the document.
3.2 Aggregate Transactions
Transactions can be aggregated into bigger transactions. A single transaction can be seen as the sending of money between two parties. The following definition represents multiple parties:
Definition 6 (Aggregate Transaction)
An aggregate transaction is a tuple of type:
with representing the lists of elements detailed in definition 3.
Transactions can be merged non-interactively to contruct an agreggate transaction.
Definition 7 (Transaction Join)
Given a valid transaction and an aggregate transaction :
a new aggregate transaction can be constructed as:
Where is the list concatenation operator and is the scalar sum.
This process, called CoinJoin, can be applied recursively to add more transactions into one aggregate transaction. A single transaction (Definition 3) can be seen as a particular case where the transaction kernel list cointains a single element. Besides, the ownership of the coins is between two parties.
The validity of an aggregate transaction is guaranteed by the validity of the transactional parties during the construction process.
Lemma 1 (Invariant: CoinJoin Validity)
Given a valid transaction and a valid aggregate transaction as in Definition 6. Let be the result of aggregating into . Then, is valid.
In our model, aggregate transactions and blocks (Definition 9) are the same (without considering headers). We are interested in distinguishing them because the unconfirmed transaction pool will contain aggregate transactions.
Notice that, in an aggregate transaction, an adversary could find out which input cancel which output. They could try all possible permutations and verify if they summed to the transaction excess. The property of transaction unlinkability will be proved over blocks, as we will see in Property 3.
3.3 Unconfirmed Transaction Pool
The unconfirmed transaction pool (mempool) contains the transactions which have not been confirmed in a block yet.
Definition 8 (Mempool)
A mempool is a list of type:
3.4 Blocks and chains
Genesis block is a special block since it is the first ever block recorded in the chain. Transactions can be merged into a block. We can see a block as a big transaction with aggregated inputs, outputs and transaction kernels.
Definition 9 (Block)
A Block is either the genesis block , or a tuple of type:
where:
-
•
and are the lists of inputs and outputs of the transactions.
-
•
is the list of transaction kernels.
-
•
is the block kernel offset which covers all the transactions of the block.
We can say a block is balanced if each aggregated transaction is balanced.
Definition 10 (Balanced Block)
Let be a block of the form with the list of transaction kernels and where the j-th item in is of the form . We say the block is balanced if the following holds:
We assume the genesis block is valid. We define the notion of block validity as follows:
Property 2 (Valid Block)
A block is valid () if is the genesis block or it satisfies:
-
i.
The block is balanced.
-
ii.
For every transaction kernel, the range proofs of all the outputs are valid and the kernel signature is valid for the transaction excess.
Blocks can be constructed by aggregating transactions as follows:
Definition 11 (Block Aggregation)
Given a valid transaction and a valid block as follows:
a new block can be constructed as:
where is the list concatenation operator and is the scalar sum.
Block agreggation preserves the validity of blocks; i.e. block validity is invariant w.r.t. block agreggation.
Lemma 2 (Invariant: Block Validity)
Given a valid transaction and a valid block as in Definition 11. Let be the result of aggregating into . Then, is valid.
Proof.
Let be the transaction with . Let be the block , with , the list of transaction kernels.
Applying Definition 11, we have that the resulting is of the form:
According to Definition 10, we need to prove the following equality holds for the block :
Each term can be written as follows:
Rearranging the equality and using algebraic properties on elliptic curves, we have:
Now, we apply the hypothesis concerning the validity of and . In particular, applying Definition 5 for and Definition 10 for , we have the following equalities are true:
and
That is exactly what we wanted to prove. ∎
Notice that proof above is analogous to the proof of CoinJoin Validity (Lemma 1).
Definition 12 (Chain)
A chain is a non-empty list of blocks:
For a chain and a valid block , we can define a predicate representing the fact that is correct to add to . This relation must verify, for example, that all the inputs in are present as outputs in , in other words, they are unspent transaction outputs (UTXOs).
3.5 Validating a chain
The model formalizes a notion of valid state that captures several well-formedness conditions. In particular, every block in the blockchain must be valid. A predicate can be defined for a chain by checking that:
-
•
is a valid genesis block
-
•
For every ,
The axiomatic semantics of the system are modeled by defining a set of transactions, and providing their semantics as state transformers. The behaviour of transactions is specified by a precondition and by a postcondition :
This approach is valid when considering local (nodes) or global (blockchain) states (of type ) and transactions (of type ). Different sets of transactions, pre and postcondition are defined to cover local or global state transformations. At a general level, is .
3.6 Executions
There can be attempts to execute a transaction on a state that does not verify the precondition of that transaction. In the presence of such situation the system answers with a corresponding error code (of type ). Executing a transaction over a valid state ()333When dealing with global states, is . produces a new state and a corresponding answer (denoted ), where the relation between the former state and the new one is given by the postcondition relation .
Whenever a transaction occurs for which the precondition holds, the valid state may change in such a way that the transaction postcondition is established. The notation may be read as the execution of the transaction in a valid state results in a new state . However, if the precondition is not satisfied, then the valid state remains unchanged and the system answer is the error message determined by a relation 444Given a state , a transaction and an error code , holds iff is an acceptable response when the execution of is requested on state .. Formally, the possible answers of the system are defined by the type:
where is the answer resulting from a successful execution of a transaction.
One-step execution with error management preserves valid states.
Lemma 3 (Validity is invariant)
The proof follows by case analysis on . When does not hold, . From this equality and
then . Otherwise, must hold and we proceed by case analysis on , considering that is a valid transaction and is a valid state.
System state invariants, such as state validity, are useful to analyze other relevant properties of the model. In particular, the properties in this work are obtained from valid states of the system.
4 Verification of MimbleWimble
We now detail some relevant properties that can be verified in our model. In addition to some of the properties mentioned in previous sections, we include in our research other properties such as those formulated in [51], and various security properties considered in [30, 45, 28].
4.1 Protocol Properties
The property of no coin inflation or zero-sum guarantees that no new funds are produced from thin air in a valid transaction. The property can be stated as follows.
Lemma 4 (No Coin Inflation)
Given a valid transaction with transaction kernel , then the transaction excess only contains the blinding factor and the kernel offset.
Proof.
We know the transaction is valid, in particular, the transaction is balanced. Applying Definition 5, we know that:
Using Definition 3, we start to unfold the terms in the equality:
Applying algebraic properties on elliptic curves, we have:
Therefore,
It means that all the inputs and outputs add to zero. In other words, they summed to the commitment to the kernel offset plus the commitment to the excess blinding factor. ∎
Thus, we have proved no money is created from thin air and the only ones who knew the blinding factors were the transacting parties when they created the transaction. This means the new outputs will be spendable only by them.
An important feature of MW is the cut-through process. The purpose of this process is to erase redundant outputs that are used as inputs within the same block. Let be some coins that appear as an output in the block . If the same coins appear as an input within the block, then can be removed from the list of inputs and outputs after applying the cut-through process. In this way, the only remaining data are the block headers, transaction kernels and unspent transaction outputs (UTXOs). After applying cut-through to a valid block it is important to ensure that the resulting block is still valid. We can say that the validity of a block should be invariant with respect to the cut-through process.
Lemma 5 (Invariant: Cut-through Block Validity)
Let be a block of the form with and the list of inputs and outputs, the list of transaction kernels and the block kernel offset. Let be the resulting block after applying the cut-through process to where:
-
•
-
•
Hence, if is a valid block, then is valid too.
Proof.
Let be the block , with the list of transaction kernels, where the j-th item in is of the form .
Let be where we assume because otherwise the lemma holds trivially as .
Let be the block , with , the list of transaction kernels, and .
We want to prove that is valid. In particular, that is balanced. According to Definition 10, we need to prove:
By hypothesis, we know that is a valid block. Applying Property 2, we know that is balanced. According to Definition 10, the following equality holds for block :
Applying the definition of , we can rewrite the above equality as follows:
Rearranging the equality, we have:
Now, we can observe that we are substracting the sum of all the elements belonging to the same set . Thus, the term is equal to zero.
Then, if we remove the term we have:
By hypothesis, we know that and ; therefore we can rewrite the above equality as:
That is exactly what we wanted to prove. ∎
4.2 Privacy and Security Properties
In blockchain systems the notion of privacy is crucial: sensitive data should not be revealed over the network. In particular, it is desirable to ensure properties such as confidentiality, anonymity and unlinkability of transactions. Confidentiality refers to the property of preventing other participants from knowing certain information about the transaction, such as the amounts and addresses of the owners. Anonymity refers to the property of hiding the real identity from the one who is transacting, while unlinkability refers to the inability of linking different transactions of the same user within the blockchain.
In the case of MW no addresses or public keys are used; there are only encrypted inputs and outputs. Privacy concerns rely on confidential transactions, cut-through and CoinJoin. CoinJoin combines inputs and outputs from different transactions into a single unified transaction. It is important to ensure that the resulting transaction satisfies the validity defined in the model.
The security problem of double spending refers to spending a coin more than once. All the nodes keep track of the UTXO set, so before confirming a block to the chain, the node checks that the inputs come from it. If we refer to our model, that validation is performed in the predicate validate mentioned in Section 3.4.
4.3 Security properties of Pedersen commitments
In MW transactions, input and output amounts are hidden in Pedersen commitments. In Section 2.3 we have introduced the definition of a commitment schema (Definition 1).
A commitment scheme is expected to satisfy the following two security properties:
-
•
Hiding: the receiver, who received the commitment, does not learn anything about the original value.
-
•
Binding: after the commit stage, there is at most one value that the sender can successfully open.
In the cryptocurrencies world, these two properties should be understood this way:
-
•
Hiding: a commitment scheme is used to keep the transactions secure. The sender commits to an amount of coins and this should remain private for the rest of the network over time.
-
•
Binding: senders cannot change their commitments to a different transaction amount. If that were possible, it would mean that an adversary could spend coins which have already been committed to an UTXO, what would amount to create coins out of thin air.
There are two possible specifications for these properties. Computational hiding or binding is when for all polynomial time adversaries, they can break the security property with negligible probability. This asymptotic security is parameterized by a security parameter and adversaries run in polynomial time in and their other inputs. On the other hand, we talk about perfectly hiding or binding, when even with infinite computing power it would be not possible to break the security property.
Notice that a commitment scheme cannot be perfectly hiding and binding at the same time:
-
i.
If the scheme is perfectly hiding, there must exist several inputs committing to the same value. Otherwise, an adversary with infinite computing power attempting to find out which input committed to a certain output, could try all possible inputs finding out the corresponding output. This shows that this scheme cannot be perfectly binding.
-
ii.
If the scheme is perfectly binding, it means that there is at most one input that committed to an output. Imagine an adversary with infinite computing power attempting to find out which input committed to a target output. It would be possible to try all inputs and find which one verifies the commitment. Thus, this scheme cannot be perfectly hiding.
So, for cryptocurrencies systems is better to provide stronger security in order to guarantee the hiding property. In other words, we prefer a commitment scheme with computational binding and perfectly hiding. We can understand this by first assuming adversaries break the binding property. It means that they could create money from thin air from a certain point in time but this would not affect the blockchain history. On the other hand, if the adversary breaks the hiding property, history could be inspected and all the transactions revealed. That breaks one of the main principles of a privacy-oriented cryptocurrency.
4.3.1 Pedersen commitments are computational binding
This property relies on the discrete logarithm assumption. In provable security, security is proved to hold against any probabilistic time adversary by showing an efficient way to break the cryptography protocol implies a way to break the underlying mathematical problem which is supposed to be hard (security reduction). The adversary is modeled as a procedure.
Definition 13 (Computational Binding Commitment)
Let be a Pedersen commitment scheme as in Definition 2. Let be a polynomial probabilistic time adversary against the binding property running in the context of the game as in Figure 1. We say that the Pedersen commitment scheme is computational binding if the success probability of winning game is negligible.
In game , firstly the scheme is set up by choosing two generator points, and , over the elliptic curve of prime order . All these parameters are public. Secondly, the adversary performs the attack attempting to find out two different transactional values and that commit to the same commitment. Once the adversary finishes the attack, two pair of different opening values are returned. The adversary succeeds if both pairs commit to the same value and .
As we mentioned before, the computational binding property is based on a security reduction. In terms of Pedersen commitment, it means that if the adversary could perform the attack in the context of game and could win with non-negligible probability, an adversary attacking a game against the discrete logarithm problem on the group could use to win the game with non-negligible probability.
Recall that MW uses Pedersen commitment with elliptic curves (Definition 2). The discrete logarithm problem on this context means: given a point over the elliptic curve with generator , it is hard to find such that .
The following lemma captures the semantics of that security reduction.
Lemma 6 (Computational Binding)
Let be a Pedersen commitment scheme as in Definition 2. Let be an adversary against the computational binding commitment (Definition 13) in the commitment scheme .
Let us assume that succeeds in finding two distinct pair of opening values that commit to the same commitment with probability. Therefore, there exists an inversor which can find out the discrete logarithm to the base of a randomly chosen element on the elliptic curve with probability using the adversary .
Hence, if is negligible then is negligible too.
In these cases, the contraposition is proved: if is non-negligible, then is non-neglible too. The goal of the proof is to show how to transform the efficient adversary that is able to break the computational binding commitment into an algorithm that efficiently solves the discrete logarithm assumption. The inversor will provide a simulation context in which the adversary will perform its attack. The attack of the inversor will be successful if is successful and the simulation does not fail.
According to game , when the adversay succeeds we have two identical commitments and such that (Definition 2):
So we can compute:
Which means that we have computed the discrete logarithm of with respect to .
Figure 2 shows the game which captures the semantic of the reduction. The failure event captures when the adversary fails and therefore, the adversary fails too.
The probability of success of is equal to the probability of success of .
4.3.2 Pedersen commitments are perfectly hiding
Basically, it is because, given a commitment , there are many combinations of that satisfies . Despite the adversary have infinite computing power and could attempt all possible values, there would be no way to know which opening values were the original ones. Furthermore, is a random value of the finite field so is a random element of .
Definition 14 (Perfectly Hiding Commitment)
In the game described in Figure 3, first the game is set up and then the adversary chooses two distinct transactional values and . Then, one of these values is randomly choosen as , as well as with the blinding factor . The commitment of is computed and the adversary performs the attack attempting to find out which one of the values was committed.
4.3.3 Switch commitments
As already mentioned, if an attacker succeeds in breaking the computational binding property of a commitment then money can be created from thin air. Switch commitments [55] were introduced to enable the transition from computational bindingness to statistical bindingness, specially to the commitments stored in the blockchain. The notion of statistical security implies that a computationally unbounded adversary cannot violate the property except with negligible probability.
If in a certain moment we believe that the bindingness of the commitment scheme gets broken, we could make a soft fork on the chain and switch existing commitments to this new validation scheme which is backwards compatible.
Below, we show the changes that are needed for our model to also encompass Switch commitments. In Pedersen commitment definition (Definition 2) we add a third point generator of the elliptic curve whose discrete logarithm relative to and is unknown. We define the new commitment algorithm as follows:
where is the blinding factor randomly chosen in the finite field and is the third point generator.
Note that is still randomly distributed and the hash value of ElGamal commitment is computed which is the combination of ElGamal encryption [29] and a commitment scheme.
4.4 Zero-knowledge Proof
The goal is to prove that a statement is true without revealing any information beyond the verification of the statement. In MW we need to ensure that in every transaction the amount is positive so that users cannot create coins. Here, the hard part is to prove that without revealing the amount. In our model, the output amounts are hidden in the form of a Pedersen commitment, and the transaction contains a list of range proofs of the outputs to prove that the amount is positive. MW uses Bulletproofs to achieve this goal. In our model, this verification is performed as the first step of the validation of the transaction.
4.5 Unlinkability and Untraceability
MW does not use addresses; the protocol relies on confidential transactions to hide the identity of the sender and the recipient. It means that users have to communicate off-chain to create the transactions.
As we specified in our model, each node has a pool of unconfirmed transactions in the mempool. This transactions are waiting for the miners in order to be included in a block. We can distinguish two security properties of the transactions. Untraceability refers to the transactions in the mempool and unlinkability to the transactions in the block. In our model, this two notions are formalized as follows.
Property 3 (Transaction Unlinkability)
Given a valid block , it is computationally infeasible to know which input cancels which output.
The following lemma captures the semantics of this property in MW. Moreover, the operations cut-through and CoinJoin, which were described above, also contribute to this property.
Lemma 7 (Transaction Unlinkability)
For any valid block and for any polynomial probabilistic time adversary , the probability of in finding a balanced transaction within is negligible.
Proof.
Let be a valid block with the list of transaction kernels. The -th item in is of the form .
The goal of the adversary is to find a tuple of the form where the list of inputs is a subset of and the list of outputs is a subset of , satisfying Definition 5 of a balanced transaction. It means that, the following equality must be true for the tuple:
where is the transaction excess and the transaction kernel offset.
If we refer to the construction process in Definition 11, the transaction kernel offsets were added to generate a single aggregate offset to cover all transactions in the block. It means that we do not store the individual kernel offset of the transaction in once the transaction is aggregated to the block.
The challenge is trying to solve the adversary could be seen as the subset sum problem (NP-complete) but, in this case, is unrecoverable. So, although many transactions have few inputs and outputs, it is computationally infeasible, without knowing that value, to find the tuple. ∎
We can define:
Definition 15 (Transaction Unlinkable)
We say block is transaction-unlinkable, if the probability of any polynomial probabilistic time adversary in finding a balanced transaction within is negligible.
Then, due to Lemma 7 we conclude that in MW all blocks are transaction-unlinkeable.
Property 4 (Transaction Untraceability)
For every transaction in the mempool, it is not possible to relate the transaction to the IP address of the node which originated it.
Regarding this property, we should refer mainly, to the broadcast of the transactions. Once the transactions are created, they are broadcasted to the network and they are included in the mempool. Each node could track the IP address from the node which received the transaction. At that point nodes could record the transactions, allowing them to build a transaction graph.
We define that the broadcast of a transaction can be performed with or without confusion. Without confusion means that, once the transactions are created, they are broadcasted immediately to all the network. However, if someone controls enough nodes on the network and discovers how the transaction moves, he could find out the IP address node from which the transaction comes from.
On the other hand, we define the broadcast with confusion as a way to obscure the IP address node.
Definition 16 (Broadcast with confusion)
Let’s say node sends a transaction to node . We say receives the transaction with confusion if given the IP address of node , the node does not know if the transaction was originated by the node or not.
In other words, it can be said that if some malicious nodes, working together, construct a graph of the pairs , the IP address node will not convey information about what node originated the transaction. Therefore, in our model, we require Property 16 to hold before the broadcast takes place. In order to achieve this, we can establish that the node broadcasting the transaction should be far enough from the one which originated it. Moreover, CoinJoin could be performed before the broadcast.
Dandelion, proposed by Fanti et al [58], is a protocol for transaction broadcasting intended to resist that deanonymization attack. Dandelion is not part of the MW protocol, however this kind of protocols should be implemented by each node to lower the risk of creating the transaction graph. In Dandelion, broadcasting is performed in two phases: the “steam” phase and the “fluff” phase. In the “steam” phase the transaction is broadcasted randomly to one node, which then randomly sends it to another, and so on. This process finishes when the “fluff” phase is reached, and the transaction is broadcasted to the network. The following routines capture the semantic of the phases:
Each node, besides having the local state, should implement these two routines. Once the transaction is created and is ready to be included in the mempool, its broadcasting start in the “steam” phase. When it reaches the “fluff” phase, it is broadcasted to the network and added in the mempool.
Dandelion relies on the following three rules: all nodes obey the protocol, each node generates exactly one transaction, and all nodes on the network run Dandelion. The problem is that an adversary can violate them. For that reason, Grin implements a more advanced protocol called Dandelion++ [26] which intends to prevent that [37]. However, it is believed that Dandelion++ is not good enough to guarantee the privacy of a virtual coin [36]. For instance, the flashlight attack [41] is an open problem still under investigation [35]. The scenario here is when an ‘activist’ want to accept donations but he cannot reveal his identity. At some point, he will deposit those payments to an exchange and his identity would be compromised. The adversary injects ‘tainted coins’ and could build a ‘taint tree’ looking through all deposits to the exchange. This way, he could link those deposits to the ‘activist’.
The combined use of the MW protocol with a Zerocash-style commitment-nullifier schema has been put forward in [59] as a countermeasure to the above attack. In the case of Zcash, every shielded transaction has a large anonymity set, namely, a set of transactions form which it is indistinguishable from. In the case of Spectrecoin [25] the main idea is the use, only once, of public addresses (XSPEC) to receive the payments combined with an anonymous staking protocol.
5 Model-driven verification
MW is built on top of a consensus protocol. In that direction, we have developed a Z specification of one such protocol, part of which is included in what follows. Z specifications in turn can be easily translated into the language [22], which can be used both as a (prototyping) programming language and a satisfiability solver for an expressive fragment of set theory and set relation algebra. We present an excerpt of the prototype after its Z specification. This prototype can be used as an executable model where simulations can be run. This allows us to analyze the behavior of the protocol without having to implement it in a low level programming language.
We also plan to use to prove some of the basic properties mentioned above, such as the invariance of . However, for complex properties or for properties not expressible in the set theories supported by we plan to develop a complete and uniform formulation of several security properties of the protocol using the Coq proof assistant [57]. The Coq environment supports advanced logical and computational notations, proof search and automation, and modular development of theories and code. It also provides program extraction towards languages like Ocaml and Haskell for execution of (certified) algorithms [46]. Additionally, Coq has an important set of libraries; for example [3] contains a formalization of elliptic curves theory, which allows the verification of elliptic curve cryptographic algorithms.
The fact of first having a prototype over which some verification activities can be carried out without much effort helps in simplifying the process of writing a detailed Coq specification. This is in accordance with proposals such as QuickChick whose goal is to decrease the number of failed proof attempts in Coq by generating counterexamples before a proof is attempted [24].
By applying the program extraction mechanism provided by Coq we would be able to derive a certified Haskell prototype of the protocol. This prototype can be used as a testing oracle and also to conduct further verification activities on correct-by-construction implementations of the protocol. In particular, both the and Coq approaches can be used as forms of model-based testing. That is, we can use either specification to automatically generate test cases with which protocol implementations can be tested [23, 24].
5.1 Excerpt of a Z model of a consensus protocol
The following is part of a Z model of a consensus protocol based on the model developed by Pîrlea and Sergey [51]. For readers unfamiliar with the Z notation we have included some background in Appendix 0.A.
The time stamps used in the protocol are modeled as natural numbers. Then we have the type of addresses (), the type of hashes (), the type of proofs objects () and the type of transactions (). Differently from Pîrlea and Sergey’s model555From now on we will refer to Pîrlea and Sergey model simply as PS. we model addresses as a given type instead as natural numbers. In PS the only condition required for these types is that they come equipped with equality, which is the case in Z.
The block data structure is a record with three fields: , (usually) points to the parent block; , stores the sequence of transactions stored in the block; and is a proof object required to validate the block.
Next we define the following parameters of the model: , a function computing the hash of a block; , a function computing the hash of a transaction; , a function computing a proof object of a node; , a relation used to validate proof objects; , a relation used to validate transactions; and , a relation used to modify a set of pending transactions stored in a node. is constrained to triplets where the block whose proof is being considered is not one of the blocks of the chain being considered.
Another parameter of our model is the genesis block, called , which should be provided by the client of the model. Clearly, is a block enjoining two particular properties: it has no parent and it contains no transactions.
The local state space of a participating network node is given by four state variables: , representing the address of the node; , are the addresses of the peers this node is aware of; , is a block forest which records the minted and received blocks; and , is a set of received transactions which eventually will be included in minted blocks.
As nodes can send messages we define their type. is used when, actually, the node does not send any message (think of it as the null statement in programming languages, i.e. ). Also note that some messages contain some data, e.g. which communicates a set of peers by transmitting their addresses.
Packets are used to build so-called packet soups which are used later to define the system configuration (see schema ). A packet is a triple where the first component is the message sender, the second is the destination’s address and the third is the message content.
The model has twelve state transitions divided into two groups: local and global. Local transitions are those executed by network nodes, while global transitions promote local transitions to the network level. In turn, the local transitions are grouped into receiving and internal transitions. Receiving transitions model the nodes receiving messages from other nodes and, possibly, sending out new messages; internal transitions model the execution of instructions run by each node when some local condition is met.
With the model elements defined so far we can give the specification of the local transitions. We start with which models a rather trivial operation of the protocol when actually the state of the node does not change because the has been received.
specifies the transition where the node receives a message making it to add the sender’s address as a new peer. In this transition we see that a node can output a set of packets (which in this particular case is a singleton set) as a side effect of receiving a message. In this case the packet says that node is sending the packet addressed to the node that just sent a packet to . In turn the payload of the packet is an message which informs the destination the transactions and blocks stored by .
The next transition is . As can be seen, it sends out a set of packets which can potentially have many elements. The node checks whether or not the packet’s destination address coincides with its own address. In that case, the node adds the received addresses to its local state and sends out a set of packets that are either of the form or . The former are packets generated from the received addresses and sent to the new peers the node now knows, while the latter are messages telling its already known peers that it has learned of new peers.
specifies the reception of a new transaction by a node. In this case the node adds the transaction to its local state and sends out an to its peers telling them that is now possessing the received transaction.
The next transition is which specifies a node receiving a block instead of a transaction. However, in order to specify we first need to introduce several elements in the form of parameters to the model. We start by introducing as an order relation on the set of block chains. Note that the axioms imply that is total, transitive and irreflexive. The fourth axiom states that extensions of a chain are “heavier” than the chain itself.
The function returns the maximum chain of a set of chains according to the order.
Function is one of the building blocks necessary to compute the ledger of a block forest. Block forests are represented as partial functions from hashes to blocks (formally ). Then, takes as inputs a block forest and a block an returns a block chain. We will use to “iterate” over all the blocks of a given block forest.
Now we define the ledger of a block forest as the longest block chain returned by for each block in the forest.
Finally, we can give the specification of .
As can be seen, adds the received block to the block forest without checking its validity. This is so because the node might not have received the preceding blocks which determine the validity of the received block.
specifies the behavior of the node when it receives an message. Such a message is used to inform nodes of the transactions and blocks stored by a given node. Then, when receives an message it asks the system the transactions and block it does not know yet by means of a message.
The last receiving local transition is . This operation is divided into three cases: the node receiving a block (); the node receiving a transaction (); and the node receiving data it has not requested ().
5.2 Excerpt of the prototype generated from the Z specification
In this section we show part of the code corresponding to the Z model presented above. code can be seen as both a formula and a program [22]. Thus, in this case we use the code as a prototype or executable model of the Z model. The intention is twofold: to show that passing from a Z specification to a program is rather easy, and to show how a program can be used as a prototype. The first point is achieved mainly because provides the usual Boolean conectives and most of the set and relational operators available in Z. Hence, it is quite natural to encode a Z specification as a program.
Given that is based on Prolog its programs resemble Prolog programs. The encoding of is the following:
rcvAddr(LocState,P,Ps,LocState_) :-
LocState = {[as,As], [this,This] / Rest} &
P = [_,This, addrMsg(Asm)] & un(As,Asm,As_) &
diff(Asm,As,D) &
Ps1 = ris(A in D,[],true,[This,A,connectMsg]) &
Ps2 = ris(A in As,[],true,[This,A,addrMsg(As_)]) &
un(Ps1,Ps2,Ps) &
LocState_ = {[as,As_], [this,This] / Rest}.
As can be seen, rcvAddr is clause receiving the before state (LocState), the input variable (P), the output variable (Ps) and the after state (LocState_). As in Prolog, programs are based on unification with the addition of set unification. In this sense, a statement such as LocState = {[as,As], [this,This] / Rest} (set) unifies the parameter received with a set term singling out the state variables needed in this case (As and This) and the rest of the variables (Rest). The same is done with packet P where _ means any value as first component and addrMsg(Asm) gets the set of addresses received in the packet without explicitly introducing an existential quantifier.
The set comprehensions used in the Z specification are implemented with ’s so-called Restricted Intentional Sets (RIS) [21]. A RIS is interpreted as a set comprehension where the control variable ranges over a finite set (D and As).
Given rcvAddr we can perform simulations on such as:
S = {[as,{}], [this,This] / R} &
rcvAddr(S,[_,This,addrMsg({a1,a2})],P1,S1) &
rcvAddr(S1,[_,This,addrMsg({a1,a3})],P2,S2).
in which case returns:
P1 = ris(A in {a1,a2/_N2},[],true,[This,A,connectMsg],true),
S1 = {[as,{a1,a2}], [this,This] / R},
P2 = {[This,a3,connectMsg],[This,a1,addrMsg({a2,a1,a3})],
[This,a2,addrMsg({a2,a1,a3})] /
ris(A in _N1,[],true,[This,A,connectMsg],true)},
S2 = {[as,{a2,a1,a3}], [this,This] / R}
Constraint: subset(_N2,{a1,a2}), subset(_N1,{a1,a3}),
a1 nin _N1, a2 nin _N1
That is, binds values for all the free variables in a way that the formula is satisfied (if it is satisfiable at all). In this way we can trace the execution of the protocol w.r.t. states and outputs by starting from a given state (e.g. S) and input values (e.g. [_,This,addrMsg({a1,a2})]), and chaining states throughout the execution of the state transitions included in the simulation (e.g. S1 and S2).
6 Mimblewimble implementations
In August 2016, someone called "Tom Elvis Jedusor” (french name for Voldemort in Harry Potter) posted a link to a text file on the IRC Channel describing a cryptocurrency protocol with a different approach from BitCoin. This article titled ‘Mimblewimble’ [44] addressed some privacy concerns and the ability of compressing the transaction history of the chain without loss of validity verification. Since this document left some questions open, in October 2016 Andrew Poelstra published a paper [52] where he describes, in more detail, the design of a blockchain based on Mimblewible. In 2019, the first two practical implementations were launched: Grin and Beam. In what follows, we shall first describe the main features of their design and will compare them with our model. Then, we shall discuss features that set apart Grin from Beam.
6.1 Grin
Grin [43] is an open source software project with a simple approach to MW. As we will see below, its design is a straightforward interpretation of our model.
6.1.1 Blocks and Transactions
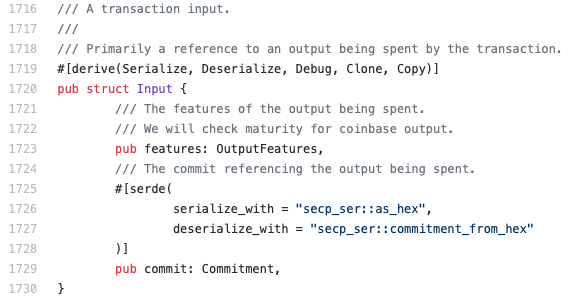
In order to provide privacy and confidentiality guarantees, Grin transactions are based on confidential transactions. In Figure 4, we can observe that each transaction contains a list of inputs and outputs. Each input and output is in the form of a Pedersen commitment, i.e, a linear combination of the value of the transaction and a blinding factor. For instance, in the input structure (Figure 5, line 1729), there is a field that stores the commitment pointing to the output being spent.
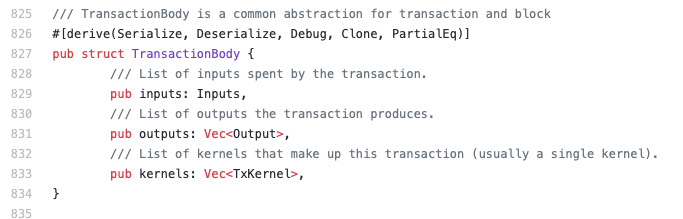
In addition, the transaction structure has a list of transaction kernels (of type TxKernel) with the transaction excess and the kernel signature. All this data has a straightforward relation to our definition of transaction (Definition 3).
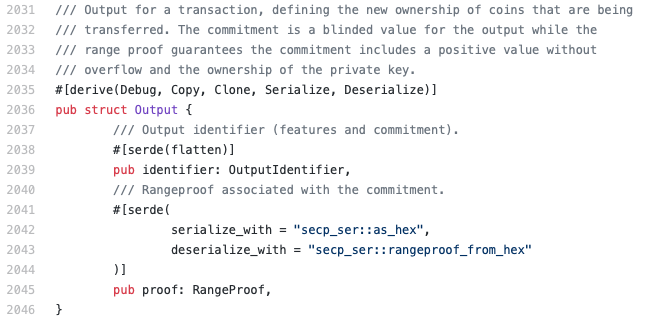
However, it is important to notice that the transaction kernel structure differs from our model since it does not contain the list of range proofs of the outputs. In Grin, it is part of the output structure (Figure 6, line 2045).
Moreover, a Grin transaction also includes the block number at which the transaction becomes valid. We did not add this data to the transaction structure yet. We also should include it in the signature process. In Grin, not only the transaction fee is signed, the signing process also takes into account the absolute position of the blocks in the chain. In this way, if a kernel block points to a height greater than the current one, it is rejected. If the relative position points to a specific kernel commitment, Grin has the same behavior.
Grin Blocks also stores a kernel offset which is the sum of all the transaction kernel offsets added to the block. In our model, the kernel offset is defined within a block (Definition 9) and the notion of adding a transaction into a block is formalized on the block aggregation (Definition 11). Besides, the single aggregate offset allows to prove Lemma 7 as part of the Transaction Unlinkability property (Property 3).
6.1.2 Privacy and Security Properties
The cut-through process, as explained in Section 4.1, provides scalability and further anonimity. Grin performs this process in the transaction pool, which we formalized as mempool (Definition 8). Outputs which have already been spent as new inputs are removed from the mempool, using the fact that every transaction in a block should sum to zero.
CoinJoin, as we mentioned in Section 4.2, combines inputs and outputs from multiple transactions into a single transaction in order to obfuscate them. In Grin, every block is a CoinJoin of all other transactions in the block.
In addition, Grin supports a pruning process. This process could be applied to past blocks. Outputs that have been spent in a previous block are removed from the block. Block validity (Property 2) should be invariant w.r.t. the pruning process. Each node maintains a local state with a local copy of the chain. The pruning process can be applied recursively to the chain and keep it as compact as possible. Pruning is useful to free space. As a consequence, when a new node wants to join the network, it can receive just a pruned (i.e. partial) chain and the node needs to validate it, which makes the synchronization process faster. In Section 3.5, should be modified to guarantee the validity of a partial chain.
As we have mentioned in Section 4.2, Switch commitments provides perfect hiddenness and statistical bindingness. Grin implements a switch commitment [33] as part of a transaction output in order to provide more security than computational bindingness (Definition 13), which is crucial for the age of quantum adversaries.
6.2 Beam
Beam [5] was the other Mimblewimble project launched on January 2019. This open source system has a founding model and a dedicated development team.
6.2.1 Blocks and Transactions
Beam transactions are confidential transactions implemented by the Pedersen commitment scheme. This follows the same approach as our model.
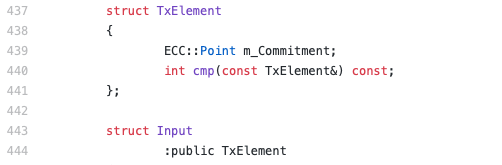
Figure 7 shows (line 439) how Beam’s input stores the commitment, i.e, a point over the elliptic curve (class of ECC::Point).
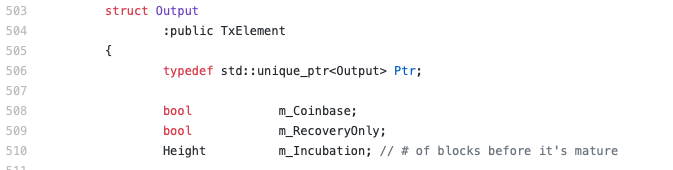
In Section 3 we described how each node maintains a local state. The state keeps track of the unspent transaction output set (UTXOs). Beam extends the behaviour of that set, supporting the incubation period on a UTXO. This means that Beam sets the minimum number of blocks created after the UTXO entered the blockchain, before it can be spent in a transaction. This number is included in the transaction signature. Figure 8 shows (line 510) how Beam’s output stores the number of blocks corresponding to the incubation period.
In our model (Section 3.5), the predicate should check that every output with certain incubation period on a block was ‘lawfully’ spent for the entire blockchain (global state). In other words, if we have an output transaction with an incubation period on a confirmed block over the chain and a later confirmed block containing as an input, then should be, at least, blocks away from on the blockchain.
6.2.2 Privacy and Security Properties
6.3 Discussion
Both Grin and Beam implementations address the main features of the MW protocol, namely the properties of confidentiality, anonymity and unlinkability comprised in our work.
6.3.1 Broadcasting Protocol
Both Grin and Beam use the Dandelion scheme as broadcasting protocol [58]. We have formalized that a broadcasting protocol should hold Property 4 of Transaction Untraceability. It should not be possible to link transactions and their originating IP addresses, in other words, to deanonymize users. Broadcast with confusion, as we describe in Property 16, should be carried out to satisfy Transaction Untraceability. We have also described the steam and fluff phases of the Dandelion scheme.
Grin’s implementation, in the steam phase, allows for transaction aggregation (CoinJoin) and cut-through, which provides greater anonymity to the transactions before they are broadcasted to the entire network.
In addition, in order to improve privacy, Beam’s implementation adds dummy transaction outputs at the steam phase. Each output has a value of zero and it is indistinguishable from regular outputs. Later, after a random number of blocks, the UTXOs are added as inputs to new transactions, i.e., they are spent and removed from the blockchanin.
In Section 4.5 we have specified the steam routine. Following, we extend the routine to capture Beam’s behaviour:
To capture that semantic, we have combined two Beam’s features: incubation period on UTXO and aggregation of zero value transaction outputs. Firstly, we randomly choose as an incubation period. Then, we create a zero value transaction output () with incubation period . The incubation period will ensure not to spend the dummy output before blocks are confirmed on the chain. After that, is added to the UTXO set (which is maintained in the local state of the node) and to the transaction that is being broadcasted. Finally, the routine follows as we specified in Section 4.5.
6.3.2 Range proofs
Grin and Beam implement range proofs using Bulletproofs [19]. Bulletproofs are a non-interactive zero-knowledge proof protocol. They are short proofs (logarithmic in the witness size) with the aim of proving that the committed value is in a certain (positive) range without reveling it. Proof generation and verification times are linear in the length of the range. Regarding our model, it is the first property a transaction should satisfy to be valid (Property 1). Furthermore, for every transaction in a bock, the range proofs of all the outputs should be valid too (Property 2).
6.3.3 Some Design Decisions
Emission Scheme
It is known that BitCoin has a limited and finite supply of coins. Nowadays, new coins come from the process called “mining” where miners are paid because of their work of aggregating new blocks to the chain besides of the transaction fees. However, once the maximum amount of coins in circulation is reached, there will not be new coins and the miners will be paid only with the transaction fees.
Grin has a different approach. It has a static emission rate, where a fixed number of coins is released as a reward for agreggating a new block to the chain. This algorithm has no upper bound for new coins. However, Beam has a capped total supply standing at 262M. The reward algorithm is decreasing over the years [6].
Parties Negotiation
Mimblewimble establishes that communication between the parties to construct a new transaction is made off-chain. Parties should collaborate in order to choose blinding factors and construct a valid transaction, in particular, a balanced transaction as in Definition 5. Grin offers this process synchronously. Both parties are connected directly to one another and they should be online simultaneously.
On the other hand, in order to construct a new transaction, Beam offers a non-interactive negotiation between the parties. The Secure Bulletin Board System (SBBS) [8] runs on the nodes and it allows the parties to communicate off-line. Moreover, Beam also presents a one-side payment scheme. This scheme allows senders to pay a specified value to a particular receiver, without any interaction from the receiver side. The key here is not revealing blinding factors. It is addressed with a process called kernel fusion. Basically, both parties construct a half kernel and both kernels should be present in the transaction.
Chain Syncronization
Grin allows partial history syncronization. When a new node wants to enter the network, it is not necesary to download the full history of the chain but it will query the block header at a horizon. The node can increase this limit as necessary. Then, it will download the full UTXO set of the horizon block.
Beam improves node synchronization using macroblocks. A macroblock is a compressed version of blockchain history after applying the cut-through process. Each node stores macroblocks locally. When a new node connects to the network, it will download the latest macroblock and will start working from that point.
7 Final remarks
MW constitutes an important step forward in the protection of anonymity and privacy in the domain of cryptocurrencies. Since it facilitates traceability and the validation process, both Grin and Beam adopted the MW protocol for their implementations.
We have highlighted elements that constitute essential steps towards the development of an exhaustive formalization of the MW cryptocurrency protocol, the analysis of its properties and the verification of its implementations. The proposed idealized model is key in the described verification process. We have also identified and precisely stated sufficient conditions for our model to ensure the verification of relevant security properties of MW. With respect to our previous paper [13], we have extended the definition of the MW protocol and the idealized model, incorporating in particular the discussion on the security properties of Pedersen commitments. Furthermore, we have studied the strength of the commitment scheme introduced regarding the main security properties a cryptocurrency protocol must have.
Since MW is built on top of a consensus protocol, we have developed a Z specification of a consensus protocol and presented an excerpt of the prototype after its Z specification. This prototype can be used as an executable model where simulations can be run. This allows us to analyze the behavior of the protocol without having to implement it in a low level programming language.
Finally, we analyze and compare the Grin and Beam implementations in their current state of development, considering our model and its properties as a reference base.
We plan to continue working on the lines presented in Section 4, namely, considering tools oriented towards the verification of cryptographic protocols and implementations, such as EasyCrypt [2], ProVerif [16], CryptoVerif [15] and Tamarin [56]. In particular, we are especially interested in using EasyCrypt666See http://www.easycrypt.info., an interactive framework for verifying the security of cryptographic constructions in the computational model.
References
- [1] J. Anderson. Computer Security technology planning study. Technical report, Deputy for Command and Management System, USA, 1972.
- [2] G. Barthe, F. Dupressoir, B. Grégoire, C. Kunz, B. Schmidt, and P. Strub. Easycrypt: A tutorial. In Alessandro Aldini, Javier López, and Fabio Martinelli, editors, Foundations of Security Analysis and Design VII - FOSAD 2012/2013 Tutorial Lectures, volume 8604 of Lecture Notes in Computer Science, pages 146–166. Springer, 2013.
- [3] E. Bartzia and P. Strub. A formal library for elliptic curves in the coq proof assistant. In ITP, volume 8558 of LNCS, pages 77–92. Springer, 2014.
- [4] Beam. Beam description. Comparison with classical MW. https://docs.beam.mw/BEAM_Comparison_with_classical_MW.pdf, July 2018.
- [5] Beam. Beam. https://tlu.tarilabs.com/protocols/grin-beam-comparison/MainReport.html#grin-vs-beam-a-comparison, March 2021.
- [6] Beam. Beam emission schedule. https://docs.beam.mw/BEAM_Position_Paper_v0.2.2.pdf, March 2021.
- [7] Beam. Beam project github. https://github.com/BeamMW/beam, March 2021.
- [8] BeamMW. Secure bulletin board system (sbbs). https://github.com/BeamMW/beam/wiki/Secure-bulletin-board-system-(SBBS), December 2018.
- [9] D. E. Bell and L. J. LaPadula. Secure computer systems: Mathematical foundations. Technical Report MTR-2547, Vol. 1, MITRE Corp., Bedford, MA, 1973.
- [10] Y. Bertot, P. Castéran, G. (informaticien) Huet, and C. Paulin-Mohring. Interactive theorem proving and program development: Coq’Art : the calculus of inductive constructions. Texts in theoretical computer science. Springer, Berlin, New York, 2004. Données complémentaires http://coq.inria.fr.
- [11] G. Betarte, M. Cristiá, C. Luna, A. Silveira, and D. Zanarini. Set-based models for cryptocurrency software. CoRR, abs/1908.00591, 2019.
- [12] G. Betarte, M. Cristiá, C. Luna, A. Silveira, and D. Zanarini. Towards a formally verified implementation of the mimblewimble cryptocurrency protocol. CoRR, abs/1907.01688, 2019.
- [13] G. Betarte, M. Cristiá, C. Luna, A. Silveira, and D. Zanarini. Towards a formally verified implementation of the mimblewimble cryptocurrency protocol. In J. Zhou, M. Conti, C. M. Ahmed, M. H. Au, L. Batina, Z. Li, J. Lin, E. Losiouk, B. Luo, S. Majumdar, W. Meng, M. Ochoa, S. Picek, G. Portokalidis, C. Wang, and K. Zhang, editors, Applied Cryptography and Network Security Workshops, pages 3–23, Cham, 2020. Springer International Publishing.
- [14] K. Bhargavan, A. Delignat-Lavaud, C. Fournet, A. Gollamudi, G. Gonthier, N. Kobeissi, N. Kulatova, A. Rastogi, T. Sibut-Pinote, N. Swamy, and S. Zanella-Béguelin. Formal verification of smart contracts: Short paper. In Proceedings of the 2016 ACM Workshop on Programming Languages and Analysis for Security, PLAS ’16, pages 91–96, New York, NY, USA, 2016. ACM.
- [15] B. Blanchet. CryptoVerif: A computationally sound mechanized prover for cryptographic protocols. In Dagstuhl seminar "Formal Protocol Verification Applied", October 2007.
- [16] Bruno Blanchet. An efficient cryptographic protocol verifier based on prolog rules. In 14th IEEE Computer Security Foundations Workshop (CSFW-14 2001), 11-13 June 2001, Cape Breton, Nova Scotia, Canada, pages 82–96. IEEE Computer Society, 2001.
- [17] C. Boyd, K. Gjøsteen, and S. Wu. A Blockchain Model in Tamarin and Formal Analysis of Hash Time Lock Contract. In Bruno Bernardo and Diego Marmsoler, editors, 2nd Workshop on Formal Methods for Blockchains (FMBC 2020), volume 84 of OpenAccess Series in Informatics (OASIcs), pages 5:1–5:13, Dagstuhl, Germany, 2020. Schloss Dagstuhl–Leibniz-Zentrum für Informatik.
- [18] Vitalik Buterin. Critical update re: Dao vulnerability, June 2016.
- [19] B. Bünz, J. Bootle, D. Boneh, A. Poelstra, P. Wuille, and G. Maxwell. Bulletproofs: Short proofs for confidential transactions and more. In 2018 IEEE Symposium on Security and Privacy (SP), pages 315–334, May 2018.
- [20] Claude Crépeau. Commitment. In Henk C. A. van Tilborg, editor, Encyclopedia of Cryptography and Security. Springer, 2005.
- [21] M. Cristiá and G. Rossi. A decision procedure for restricted intensional sets. In CADE, volume 10395 of LNCS, pages 185–201. Springer, 2017.
- [22] M. Cristiá and G. Rossi. Solving quantifier-free first-order constraints over finite sets and binary relations. J. Autom. Reasoning, 64(2):295–330, 2020.
- [23] M. Cristiá, G. Rossi, and C. Frydman. {log} as a test case generator for the test template framework. In Robert M. Hierons, Mercedes G. Merayo, and Mario Bravetti, editors, Software Engineering and Formal Methods - 11th International Conference, SEFM 2013, Madrid, Spain, September 25-27, 2013. Proceedings, volume 8137 of LNCS, pages 229–243. Springer, 2013.
- [24] M. Dénès, C. Hritcu, L. Lampropoulos, Z. Paraskevopoulou, and B. Pierce. Quickchick: Property-based testing for coq. In The Coq Workshop, 2014.
- [25] Eirik Korsell and Philip Mueller and Yves Schumann. Spectrecoin. https://spectreproject.io/Spectrecoin_White-Paper.pdf, June 2019.
- [26] G. C. Fanti, S. B. Venkatakrishnan, S. Bakshi, B. Denby, S. Bhargava, A. Miller, and P. Viswanath. Dandelion++: Lightweight cryptocurrency networking with formal anonymity guarantees. CoRR, abs/1805.11060, 2018.
- [27] Beam Foundation. Beam confidential cryptocurrency. https://beam.mw/, 2020.
- [28] G. Fuchsbauer, M. Orrù, and Y. Seurin. Aggregate cash systems: A cryptographic investigation of mimblewimble. In Y. Ishai and V. Rijmen, editors, Advances in Cryptology - EUROCRYPT 2019 - 38th Annual International Conference on the Theory and Applications of Cryptographic Techniques, Darmstadt, Germany, May 19-23, 2019, Proceedings, Part I, volume 11476 of Lecture Notes in Computer Science, pages 657–689. Springer, 2019.
- [29] Taher El Gamal. A public key cryptosystem and a signature scheme based on discrete logarithms. In Advances in Cryptology, Proceedings of CRYPTO ’84, Santa Barbara, California, USA, August 19-22, 1984, Proceedings, volume 196 of Lecture Notes in Computer Science, pages 10–18. Springer, 1984.
- [30] J. Garay, A. Kiayias, and N. Leonardos. The bitcoin backbone protocol: Analysis and applications. In Proc. of EUROCRYPT 2015 - LNCS 9057. Springer, 2015.
- [31] I. Garfatta, K. Klai, W. Gaaloul, and M. Graiet. A survey on formal verification for solidity smart contracts. In 2021 Australasian Computer Science Week Multiconference, ACSW ’21, New York, NY, USA, 2021. Association for Computing Machinery.
- [32] A. Gibson. An investigation into confidential transactions. https://github.com/AdamISZ/ConfidentialTransactionsDoc/blob/master/essayonCT.pdf, 2018.
- [33] Github. Grin source code switch commitments. https://github.com/mimblewimble/secp256k1-zkp/blob/73617d0fcc4f51896cce4f9a1a6977a6958297f8/src/modules/commitment/main_impl.h#L267, March 2021.
- [34] Grin. Grin project github. https://github.com/mimblewimble/grin, March 2021.
- [35] Grin Community. Grin:Open Research Problems. https://grin.mw/open-research-problems, 2020.
- [36] Grin Team. Privacy Primer. https://github.com/mimblewimble/docs/wiki/Grin-Privacy-Primer, November 2018.
- [37] Grin Team. Dandelion++ in Grin: Privacy-Preserving Transaction Aggregation and Propagation. https://github.com/mimblewimble/grin/blob/master/doc/dandelion/dandelion.md, July 2019.
- [38] I. Grishchenko, M. Maffei, and C. Schneidewind. A semantic framework for the security analysis of ethereum smart contracts. In Lujo Bauer and Ralf Küsters, editors, Principles of Security and Trust, pages 243–269, Cham, 2018. Springer International Publishing.
- [39] A. Hajdu, D. Jovanovic, and G. Ciocarlie. Formal specification and verification of solidity contracts with events, 2020.
- [40] Yoichi Hirai. Defining the ethereum virtual machine for interactive theorem provers. In Michael Brenner, K. Rohloff, J. Bonneau, A. Miller, P. Ryan, V. Teague, A. Bracciali, M. Sala, F. Pintore, and M. Jakobsson, editors, Financial Cryptography and Data Security - FC 2017 International Workshops, WAHC, BITCOIN, VOTING, WTSC, and TA, Sliema, Malta, April 7, 2017, Revised Selected Papers, volume 10323 of LNCS, pages 520–535. Springer, 2017.
- [41] Ian Miers. Blockchain Privacy: Equal Parts Theory and Practice. https://www.zfnd.org/blog/blockchain-privacy/#flashlight, February 2019.
- [42] F. Idelberger, G. Governatori, R. Riveret, and G. Sartor. Evaluation of logic-based smart contracts for blockchain systems. In J. Alferes, L. Bertossi, G. Governatori, P. Fodor, and D. Roman, editors, Rule Technologies. Research, Tools, and Applications - 10th International Symposium, RuleML 2016, Stony Brook, NY, USA, July 6-9, 2016. Proceedings, volume 9718 of LNCS, pages 167–183. Springer, 2016.
- [43] T. Jedusor. Introduction to MimbleWimble and Grin. https://github.com/mimblewimble/grin/blob/master/doc/intro.md, 2016.
- [44] T. Jedusor. Mimblewimble. //scalingbitcoin.org/papers/mimblewimble.txt, 2016.
- [45] A. Kiayias, A. Russell, B. David, and R. Oliynykov. Ouroboros: A provably secure proof-of-stake blockchain protocol. In CRYPTO - LNCS 10401. Springer, 2017.
- [46] P. Letouzey. A new extraction for coq. In Herman Geuvers and Freek Wiedijk, editors, Types for Proofs and Programs, Second International Workshop, TYPES 2002, Berg en Dal, The Netherlands, April 24-28, 2002, Selected Papers, volume 2646 of LNCS, pages 200–219. Springer, 2002.
- [47] L. Luu, D. Chu, H. Olickel, P. Saxena, and A. Hobor. Making smart contracts smarter. In E. Weippl, S. Katzenbeisser, C. Kruegel, A. Myers, and S. Halevi, editors, Proceedings of the 2016 ACM SIGSAC Conference on Computer and Communications Security, Vienna, Austria, October 24-28, 2016, pages 254–269. ACM, 2016.
- [48] G. Maxwell. Confidential transactions write up. https://people.xiph.org/˜greg/confidential_values.txt, 2020.
- [49] R. Metere and C. Dong. Automated cryptographic analysis of the pedersen commitment scheme. In J. Rak, J. Bay, I. Kotenko, L. Popyack, V. Skormin, and K. Szczypiorski, editors, Computer Network Security, pages 275–287, Cham, 2017. Springer International Publishing.
- [50] S. Nakamoto. Bitcoin: A peer-to-peer electronic cash system. Cryptography Mailing list at https://metzdowd.com, 03 2009.
- [51] G. Pîrlea and I. Sergey. Mechanising blockchain consensus. In Proc. of CPP 2018, pages 78–90, New York, USA, 2018. ACM.
- [52] A. Poelstra. Mimblewimble. https://download.wpsoftware.net/bitcoin/wizardry/mimblewimble.pdf, October 2016.
- [53] J. Santos Reis, P. Crocker, and S. Melo de Sousa. Tezla, an Intermediate Representation for Static Analysis of Michelson Smart Contracts. In Bruno Bernardo and Diego Marmsoler, editors, 2nd Workshop on Formal Methods for Blockchains (FMBC 2020), volume 84 of OpenAccess Series in Informatics (OASIcs), pages 4:1–4:12, Dagstuhl, Germany, 2020. Schloss Dagstuhl–Leibniz-Zentrum für Informatik.
- [54] Grigore Rosu. Formal Design, Implementation and Verification of Blockchain Languages Using K (Invited Talk). In Bruno Bernardo and Diego Marmsoler, editors, 2nd Workshop on Formal Methods for Blockchains (FMBC 2020), volume 84 of OpenAccess Series in Informatics (OASIcs), pages 1:1–1:1, Dagstuhl, Germany, 2020. Schloss Dagstuhl–Leibniz-Zentrum für Informatik.
- [55] T. Ruffing and G. Malavolta. Switch commitments: A safety switch for confidential transactions. Cryptology ePrint Archive, Report 2017/237, 2017. https://eprint.iacr.org/2017/237.
- [56] Tamarin Team. Tamarin prover. https://tamarin-prover.github.io, March 2021.
- [57] The Coq Dev. Team. The Coq Proof Assistant Reference Manual – V. 8.9.0, 2019.
- [58] S. B. Venkatakrishnan, G. C. Fanti, and P. Viswanath. Dandelion: Redesigning the bitcoin network for anonymity. CoRR, abs/1701.04439, 2017.
- [59] Wanseob-Lim. Ethereum 9 3/4: Send ERC20 privately using Mimblewimble and zk-SNARKs. https://ethresear.ch/t/ethereum-9-send-erc20-privately-using-mimblewimble-and-zk-snarks/6217, September 2019.
- [60] G. Wood. Ethereum: A secure decentralised generalised transaction ledger eip-150 revision (759dccd - 2017-08-07), 2017. Accessed: 2018-01-03.
Appendix 0.A Background on the Z Notation
The Z notation is a formal method based on first-order logic and Zermelo-Fraenkel set theory. Any Z specification takes the form of a state machine—not necessarily a finite one. This machine is defined by giving its state space and the transitions between those states. The state space is given by declaring a tuple of typed state variables. A transition, called operation in Z, is defined by specifying its signature, its preconditions and its postconditions. The signature of an operation includes input, state and output variables. Each operation can change the state of the machine. State change is described by giving the relation between before-state and after-state variables.
In order to introduce the Z notation we will use a simple example. Think in the savings accounts of a bank. Each account is identified by a so-called account number. The bank requires to keep record of just the balance of each account. Since account numbers are used just as identifiers we can abstract them away, not caring about their internal structure. Z provides so-called basic or given types for these cases. The Z syntax for introducing a basic type is:
In this way, it is possible to declare variables of type and it is possible to build more complex types involving it—for instance the type of all sets of account numbers is .
We represent the money that clients can deposit and withdraw and the balance of savings accounts as natural numbers. The type for the integer numbers, , is built-in in Z. The notation also includes the set of natural numbers, . Then, we define:
In other words, we introduce two synonymous for the set of natural numbers so the specification is more readable.
The state space is defined as follows:
This construction is called schema; each schema has a name that can be used in other schemas. In particular this is a state schema because it only declares state variables. In effect, it declares one state variable by giving its name and type. Each state of the system corresponds to a particular valuation of this variable. The type constructor defines partial functions777It must be noted that the Z type system is not as strong as the type systems of other formalisms, such as Coq. So we will be as formal as is usual in the Z community regarding its type system.. Then, is a partial function from onto . It makes sense to define such a function because each account has a unique ; and it makes sense to make partial because not every account number is used all the time at the bank (i.e. when an account is opened the bank assigns it an unused account number; and when an account is closed its account number is no longer used).
Now, we can define the initial state of the system as follows:
is another schema. The upper part is the declaration part and the lower part is the predicate part—this one is optional and is absent from . In the declaration part we can declare variables or use schema inclusion. The latter means that we can write the name of another schema instead of declaring their variables. This allows us to reuse schemas. In this case the predicate part says that the state variable is equal to the empty set. It is important to remark that the symbol is logical equality and not an imperative assignment—Z has no notion of control flow. In Z, functions are sets of ordered pairs. Being sets they can be compared with the empty set. The symbol is polymorphic in Z: it is the same for all types.
Now we can define an operation of the system (i.e. a state transition) specifying how an account is opened.
As can be seen, operations are defined by means of schemas. The expression in the declaration part is a shorthand for including the schemas and . We already know what it means including . is equal to but all of its variables are decorated with a prime. Therefore, declares of the same types than that in . When a state variable is decorated with the prime it is assumed to be an after-state variable. The net effect of including is, then, the declaration of one before-state variable and one after-state variable. A expression is included in every operation schema that produces a state change.
Variables decorated with a question mark, like , are assumed to be input variables. Then, represents the account number to be assigned to the new savings account. To simplify the specification a little bit we assume that a bank’s clerk provides the account number when the operation is called—instead of the system generating it.
Note that the predicate part consists of two atomic predicates. When two or more predicates are in different rows they are assumed to be a conjunction. In other words:
is equivalent to:
Z uses the standard symbols of discrete mathematics and set theory so we think it will not be difficult for the reader to understand each predicate. Remember that functions and relations are sets of ordered pairs so they can participate in set expressions. For instance, adds an ordered pair to . Again, the expression is actually a predicate saying that is equal to , and not that the latter is assigned to the former. In other words, this predicate says that the value of in the after-state is equal to the value of in the before-state plus the ordered pair .
Note that operations are defined by giving their preconditions and postconditions. In the precondition is:
while its postcondition is:
Therefore, does not say what the system shall do when does not hold. The bank says that nothing has to be done when the account number chosen by the clerk is already in use. Then, we define a new schema for this case:
This is another way of writing schemas, called horizontal form. It has the same meaning than:
The expression is a shorthand for:
If a expression is included in an operation schema, it means that the operation will not produce a state change because all the primed state variables are equal to their unprimed counterparts. When a schema whose predicate part is not empty is included in another schema, the net effect is twofold: (a) the declaration part of the former is included in the declaration part of the latter; and (b) the predicate of the former is conjoined to the predicate of the latter. Hence, could have been written as follows:
Usually, schemas like are said to specify the successful cases or situations, while schemas like specify the erroneous cases. Finally, we assemble the two schemas to define the total operation—i.e. an operation whose precondition is equivalent to —for opening a savings account in the bank:
is defined by a so-called schema expression. Schema expressions are expressions involving schema names and logical connectives. Let be the schema defined as where is the declaration part and is its predicate. Similarly, let the schema defined by . Then, the schema defined by , where is any of , and , is the schema . In other words, the declaration parts of the schemas involved in a schema expression are joined together and the predicates are connected with the same connectors used in the expression—if there is some clash in the declaration parts it must be resolved by the user. In symbols: