A Practical Runtime Security Policy Transformation Framework for Software Defined Networks
Abstract
Software-defined networking (SDN) has been widely utilized to enforce the security of traditional networks, thereby promoting the process of transforming traditional networks into SDN networks. However, SDN-based security enforcement mechanisms rely heavily on the security policies containing the underlying information of data plane, such as MAC address, IP address or switch ports. These security policies need to be specifically developed by the network operators, and loaded into the control plane by manual inputting. With increasing the scale of underlying network, the current security policy management mechanism will confront more and more challenges. The security policy transformation for SDN networks is to research how to transform the high-level security policy without containing the underlying information of data plane into the practical flow entries used by the OpenFlow switches automatically, thereby implementing the automation of security policy management. Based on this insight, a practical runtime security policy transformation framework is proposed in this paper. First of all, we specify the security policies used by SDN networks as a system model of security policy (SPM). From the theoretical level, we establish the system model for SDN network and propose a formal method to transform SPM into the system model of flow entries automatically. From the practical level, we propose a runtime security policy transformation framework to solve the problem of how to find a connected path for each relationship of SPM in the data plane, as well as how to generate the practical flow entries according to the system model of flow entries. In order to validate the feasibility and effectiveness of the framework, we set up an experimental system and implement the framework with POX controller and Mininet emulator. The experimental results illustrate the framework can synchronously perceive the changes caused by cutting down one edge or changing SPM, and keep the data plane holding the security properties defined by SPM continuously at runtime.
keywords:
SDN , security policy , model transformation , data plane.1 Introduction
Software-defined networking (SDN) is a novel networking technique or architecture that changes the limitation of traditional network infrastructures by breaking the vertical integration, decoupling the control logics from the underlying forwarding devices, promoting the centralization of control and introducing the abilities to program the network directly[1]. In SDN networks, the control logics of network, such as routing, traffic engineering or security policy developed in the application plane, are loaded into the control plane via the northbound interfaces (NBI) and transformed into a set of forward entries used by the OpenFlow switches. After that, the control plane distributes the generated flow entries to the associated switches in the data plane via the southbound interfaces (SBI). Because of its programmable, centralized intelligent control as well as global traffic view, SDN has been widely utilized to enhance the security of tradition networks, thereby promoting the process of transforming traditional networks into SDN networks. For instances, Garay et al.[2] proposed a SDN-based network access control mechanism, flownac, which is a centralized EAP (extensible authentication protocol) for IEEE 802.1x wireless local area network (WLAN). Yakasai et al.[3] proposed a network access control mechanism, flowidentity. This mechanism integrates EAP security authentication mechanism into the SDN controller. Hu et al.[4] proposed a dynamic firewall mechanism, flowguard, based on SDN. Koerner et al.[5] proposed a device security authentication mechanism based on MAC address and SDN.
However, SDN-based security enforcement mechanisms rely heavily on the security policies containing the underlying information of the data plane, such as MAC address, IP address or switch ports. These security policies need to be specifically developed by the network operators, and loaded into the control plane by means of the manual inputting. With increasing the scale of underlying network, the current security policy management mechanism will confront more and more challenges. First of all, it is nearly impossible for any operator to completely understand all the information of underlying network. In addition, with the emergence of multi-controller SDN[6], network operators need to manage a variety of heterogeneous controllers at the same time. In this case, the same security policy often needs to be developed and deployed for the different types of controller, which inevitably increases the complexity and difficulty for network management. Therefore, a novel security policy management mechanism which can be completely transparent to the underlying information of data plane is urgently needed for SDN networks. That is, it can permit the operators only to define the high-level security policy without containing any underlying information, then by means of the security policy transformation, the high-level security policy can be automatically transformed into its corresponding flow entries used by the OpenFlow switches in the data plane, thereby implementing the automation of security policy management for SDN networks.
Based on these insights, we have proposed a security policy model transformation and verification approach for SDN networks and published the approach in our previous paper[7]. In that paper, we proposed a security policy transformation method to transform the high-level security policy model (SPM) without containing the underlying information into its corresponding low-level security policy model (LSPM) containing the underlying information. To verify the soundness of proposed security policy model transformation method, we further proposed a security policy verification method and proved that the problem of whether the data plane can satisfy the security properties defined by SPM is equivalent to the problem of searching the connected paths related with SPM in the data plane, that is, as long as each access control relationship SPM can be transformed into a corresponding connected path in the data plane, next transforms into a set of flow entries used by the OpenFlow switches, then the data plane must can hold the security properties defined by SPM. However, that paper only proposed the method from the theoretical level, and did not specifically implement this method. Moreover, it did not solve the problem of how to find a connected path for each relationship of SPM in the data plane, and how to transform LSPM into the practical flow entries used by the switches.
And based on the theoretical foundation of that paper, we propose a runtime security policy transformation framework for SDN networks in this paper. First of all, this paper further improves the system model of SDN networks and solves the problem of how to transform SPM into the flow entries used by the OpenFlow switches from the theoretical level. Moreover, this paper proposes a runtime security policy transformation framework from the practical level, thereby solving the problem of how to find a connected path for each relationship SPM in the data plane, as well as how to transform the system model of flow entries into the practical flow entries used by the switches at runtime. In addition, this paper further implements the proposed framework with an experimental system. The experimental result illustrate the framework is completely effective at runtime.
Hence, the contributions of this paper can be summarized as follows:
We specify the security policies used by SDN networks, such as access control policies or firewall policies, as a system model of security policy (SPM). SPM is of a high-level system model without containing any underlying information of data plane.
From the theoretical level, we establish the system model for SDN network, and propose a formal method to transform SPM into the system model of flow entries automatically. The system model of flow entry is of a low-level system model containing the underlying information of data plane.
From the practical level, we propose a runtime security policy transformation framework which consists of the security policy module, topology discovery module, runtime monitoring module, path generation module and flow entry generation module. Leveraging these functional modules, the framework can solve the problem of how to find a connected path for each relationship of SPM in the data plane, how to transform the path into the system model of flow entries, as well we how to generate the practical flow entries by using the system model of flow entries.
In order to validate the feasibility and effectiveness of the framework, we set up an experimental system and implement the framework by using POX controller and Mininet emulator. The experimental result illustrate the framework is completely effective at runtime.
The remainder of this paper is structured as follows. Section 2 discusses some related works. Section 3 proposes the system model and elaborates on how to transform SPM into the flow entries from the theoretical level. Section 4 proposes the runtime security policy transformation framework from the practical level and introduces its functional modules. Section 5 implements the framework with an experimental system and elaborates on how to evaluate the effectiveness and performance of the framework. Finally, Section 6 concludes this paper and presents some future directions.
2 Related Work
In this section, we discuss some research works related with the policy model transformation and the security policy verification.
2.1 Policy Model Transformation
According to the definitions of model-driven architecture (MDA), the model transformation refers to the process of transforming the platform independent model (PIM) to its corresponding platform specific model (PSM)[8]. As far as the literatures we have read, the researches towards the policy model transformation can be roughly divided into three categories, they are the template-based transformation, RBAC-oriented transformation as well as the transformation based on the system model and mapping rules[9]. Due to the limitation of template, the template-based model transformation has very limited transformation capability. Generally, RBAC-oriented model transformation[10] is only suitable for transforming RBAC (role-based access control) policies, and does not have enough capability to describe the complex system, so that these two methods are not suitable for SDN networks.
At present, the model transformation based on the system model and mapping rules has been widely used for transforming the policy models. The main idea of this method can be summarized as follows: (1) System Model: it defines the objects of system and the relationship between the system objects; (2) Policy Model: it defines the policy object and the relationship between the policy objects; (3) Mapping Rules: it establishes the mapping rules between the upper-level policy objects and the lower-level system objects[11][12]. The transformation based on the system model and mapping rules first establishes the policy model and the system model which can describe the underlying system, then establishes the mapping rules between the policy objects and the system objects, then transforms the upper-level policy model into its corresponding lower-level policy model by means of the established mapping rules. In particular, Davy et al.[13] proposed a policy model transformation method based on mapping rules, in which the policy model is defined as a tuple ( event, condition, behavior, subject, object ) and used the ontology to establish the mapping rules between the different system layers. Luck et al.[14] proposed a method to transform RBAC model defined in service layer into the policy model used in the system layer. In this method, the system model is divided into three layers: roles and object (RO), subject and resources (SR) and processes and hosts (PH), and the mapping rules between the three layers have been established. Based on the Luck’s research, Porto et al.[15] further decomposes the PH layer into two sub layers, namely DAS (diagram abstract subsystem) layer and PH layer. DAS layer is mainly used to describe the network topology in the original PH layer, while PH layer is used to describe the specific network information in DAS layer. In addition, the authors also proposed a policy verification framework, which can be used to verify the consistency problems in the process of policy transformation. In addition, Lampson et al.[16] proposed a network policy model transformation method for the distributed computing environment. Maullo et al.[17] proposed a policy transformation system based on the first-order predicate logics, which transforms the high-level policy model into the low-level network configuration policy through the network topology and other information. Nanxi et al.[18] proposed a SDN-oriented access control policy transformation framework. In this paper, In this paper, we also propose a security policy transformation framework based on the system model and mapping rules. We first establish the system model of security policy (SPM) and data plane, then establish the transformation rules between the policy objects of SPM and the objects of the data plane, thereby transforming SPM into the system model of flow entries automatically.
2.2 Security Policy Verification
To assure the information systems running securely, security mechanisms of information system need to be validated whether it can satisfy the security properties defined by the security policy. The traditional validation methods based on the testing and simulation can only confirm the system can work properly under the different testing scenarios, but it is difficult to find some hidden scenarios that occur with little probability. Formal verification methods have been applied to overcome the shortcomings existed in the traditional validation methods. At present, the formal verification methods for validating the security policy mainly include theorem proving and model checking[19]. Theorem proving is unsuitable to validate the properties of complex systems due to its lower efficiency. Model checking[20] can be used to validate whether the system model can satisfy the expected dynamic behaviors and specific static properties. Model checking technique has been widely used for the security policy verification. For instances, Al-Shaer et al.[21] proposed a static policy inconsistency detection method for the firewall policies of network. Bandara et al.[22] proposed a security policy verification framework based on event calculus (EC) and used the reasoning techniques for the policy conflict identification. May et al.[23] verified the privacy policies by means of an asynchronous model checker. Rubio-Loyola et al.[24] proposed a goal-oriented policy refinement and conflict detection method by means of the model checking technique and linear temporal Logic (LTL). Graham et al.[25] proposed a policy conflict detection method with the model checking and an extended decision table. Baliosan and Serrat[26] proposed a specific finite automata based method for the policy conflict detection.
3 Problem Formalization
The security policy transformation for SDN networks is to research how to transform the high-level security policy without containing the underlying information into the set of practical flow entries used by the OpenFlow switches in the data plane automatically, thereby implementing the automation of security policy management in SDN network. In the following of this section, we first establish the system model for SDN network, then propose a formal method to transform the security policy (SPM) into the system model of flow entries from the theoretical level.
3.1 System Model
Definition 1
(Security Policy): The high-level security policy is defined as a finite set of access control relationships: SPM = , ,…, = , , , where represents the subject of the relationship, represents the object of the relationship, represents the access authorization, i.e., the subject can access the object.
Definition 2
(Host): The host existed in the data plane is defined as a tuple: = , , , where represents the host’s IP address in the data plane, represents the OpenFlow switch connected with the host, represents the port connected with the host in .
Definition 3
(OpenFlow Switch): The OpenFlow switch existed the data plane is defined as a finite set of flow entries: = , , …, .
Definition 4
(Flow Entry): The flow entry existed in the OpenFlow switch is defined as a tuple: = , , , where represents the traffic’s source IP address, represents the traffic’s destination IP address, represents the traffic input from will be outputted from in the switch .
Definition 5
(Edge): The edge existed in the data plane is defined as: = , where represents the port connected with the edge in the start switch , represents the port connected with the edge in the end switch , so that the direction of the edge is from to .
Definition 6
(Topology): The topology of the data plane is defined as an graph: = , , where represents a finite set of OpenFlow switches, represents a finite set of edges.
Definition 7
(Connected Path): The connected path between the host and the host in the topology is defined as: = = , , ,…, , , where the direction of the path is from to .
3.2 Transforming SPM into the Flow Entries
Based on the established system model, we propose a formal method to transform SPM into the system model of flow entries from the theoretical level. The method can be described as Figure 1 and summarized as follows: First of all, for SPM, the subject is transformed into a host in the data plane, the object is transformed into a host in the data plane; Next, the access authorization is transformed into a connected path between and ; After that, the connected path is transformed into a set of flow entries used by the switches which are passed by ; Finally, SPM is transformed into the set of flow entries when all relationships of SPM have been transformed. As shown in Figure 1, the relationship SPM is transformed into the connected path between and , thus is transformed into the flow entries deployed in , so as to implement the security policy transformation from the system model level. The soundness of the formal method has been proven in our previous paper[7]. That is, if the security properties defined by SPM is denoted as , the system model of data plane is denoted as , the flow entries generated by the method is denoted as , then the method can ensure the data plane loaded with can synchronously and continuously hold the security properties at runtime, i.e., .
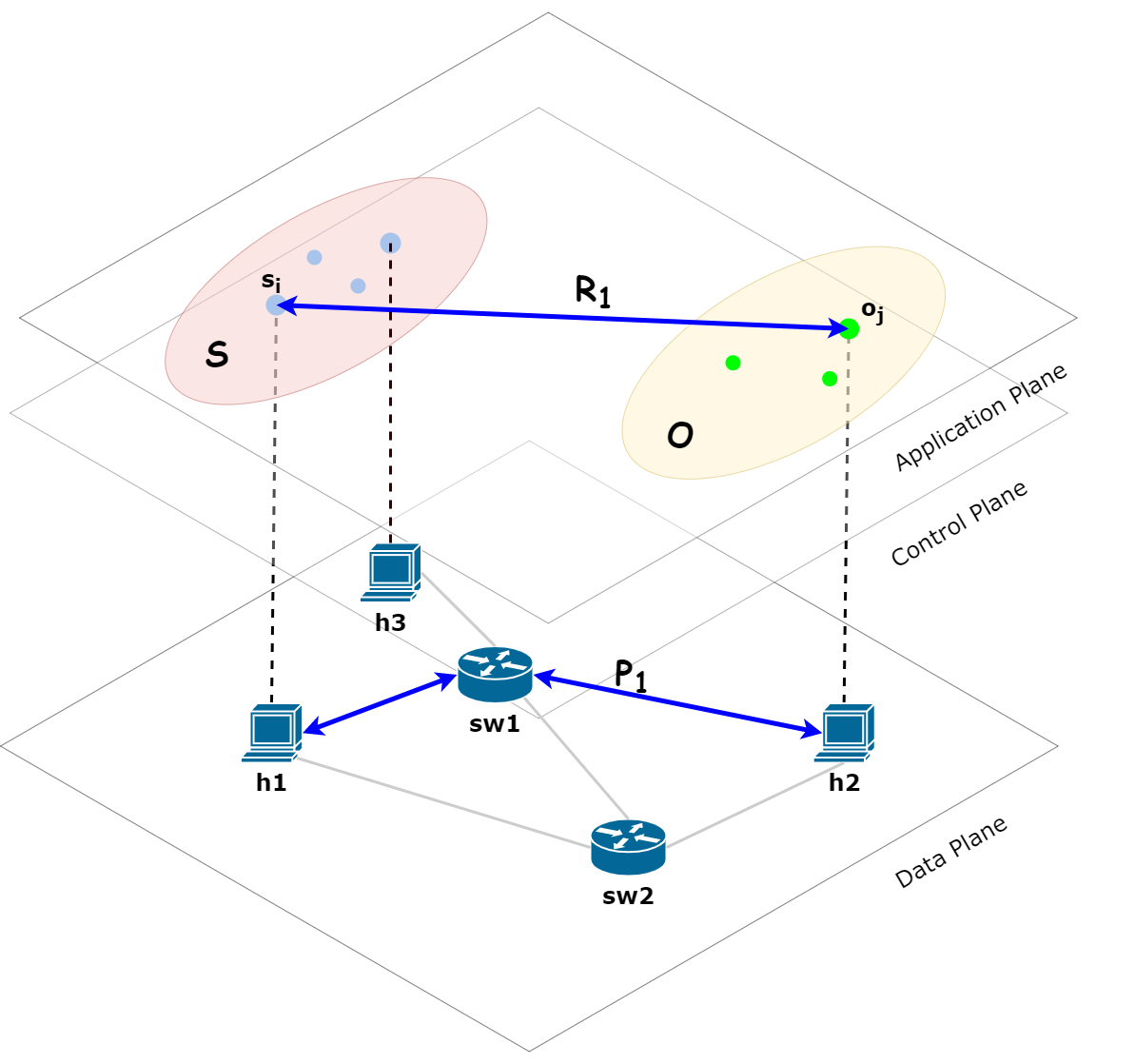
Specifically, the formal method to transform SPM into the system model of flow entries is defined as follows.
Transforming the Subject Given an access control relationship SPM and the subject , then is transformed into a corresponding host existed in the data plane. The rule of transforming the subject of SPM is formally defined as follows:
| (1) |
where represents the host mapped with in the data plane, represents the IP address of in the data plane, represents the OpenFlow switch connected with in the data plane, represents the port connected with in .
Transforming the Object Given an access control relationship SPM and the object , then is transformed into a corresponding host existed in the data plane. The rule of transforming the object of SPM is formally defined as follows:
| (2) |
where represents the host mapped with in the data plane, represents the IP address of in the data plane, represents the OpenFlow switch connected with , represents the port connected with in .
Transforming the Authorization Given an access control relationship SPM and the access authorization , if there existing a connected path between and in the topology, then is transformed into the connected . The rule of transforming the authorization is formally defined as follows:
| (3) |
where represents a directional connected path from to in the topology.
Transforming the Path The connected path is transformed into a set of flow entries deployed in the OpenFlow switches which are passed by the path. The rule of transforming the connected path is formally defined as follows:
| (4) |
where = , , represents a flow entry deployed in the switch which is passed by . Leveraging the definitions of the system model, we can proof that the rule of transforming the connected path is sound.
Therefore, SPM, the subject , the object and the autherization , if = in the topology, then can be transformed into a corresponding set of flow entries by using the system model step by step, it can be formally defined as follows:
| (5) |
Transforming SPM SPM is transformed into a corresponding set of flow entries by using the equation (5). If SPM = , then the rule of transforming SPM is formally defined as follows:
| (6) |
4 The Security Policy Transformation Framework
The problem of how to transform SPM into the corresponding flow entries used by the OpenFlow switches has been solved from the theoretical level in Section 3. However, we cannot solve the problem of how to find a connected path in the data plane for each relationship SPM. In addition, by means of the security policy transformation method, SPM can be transformed into the corresponding flow entries, but the flow entry transformed from SPM is of the system model, i.e. it is only the formal description of the real flow entry and cannot be used by the real OpenFlow switch directly, so that we need to further solve the problem of how to generate the practical flow entries by using the system model of flow entries. Based on this insight, a runtime security policy transformation framework for SDN networks is proposed from the practical level in this section. By means of the framework, we can solve the problem of how to find the connected path for each relationship defined by SPM, as well as the problem of how to generate the practical flow entries based on the system model at runtime. As shown in Figure 2, this framework consists of 5 functional modules, i.e., the security policy module, the topology discovery module, the runtime monitoring module, the path generation module and the flow entry generation module.
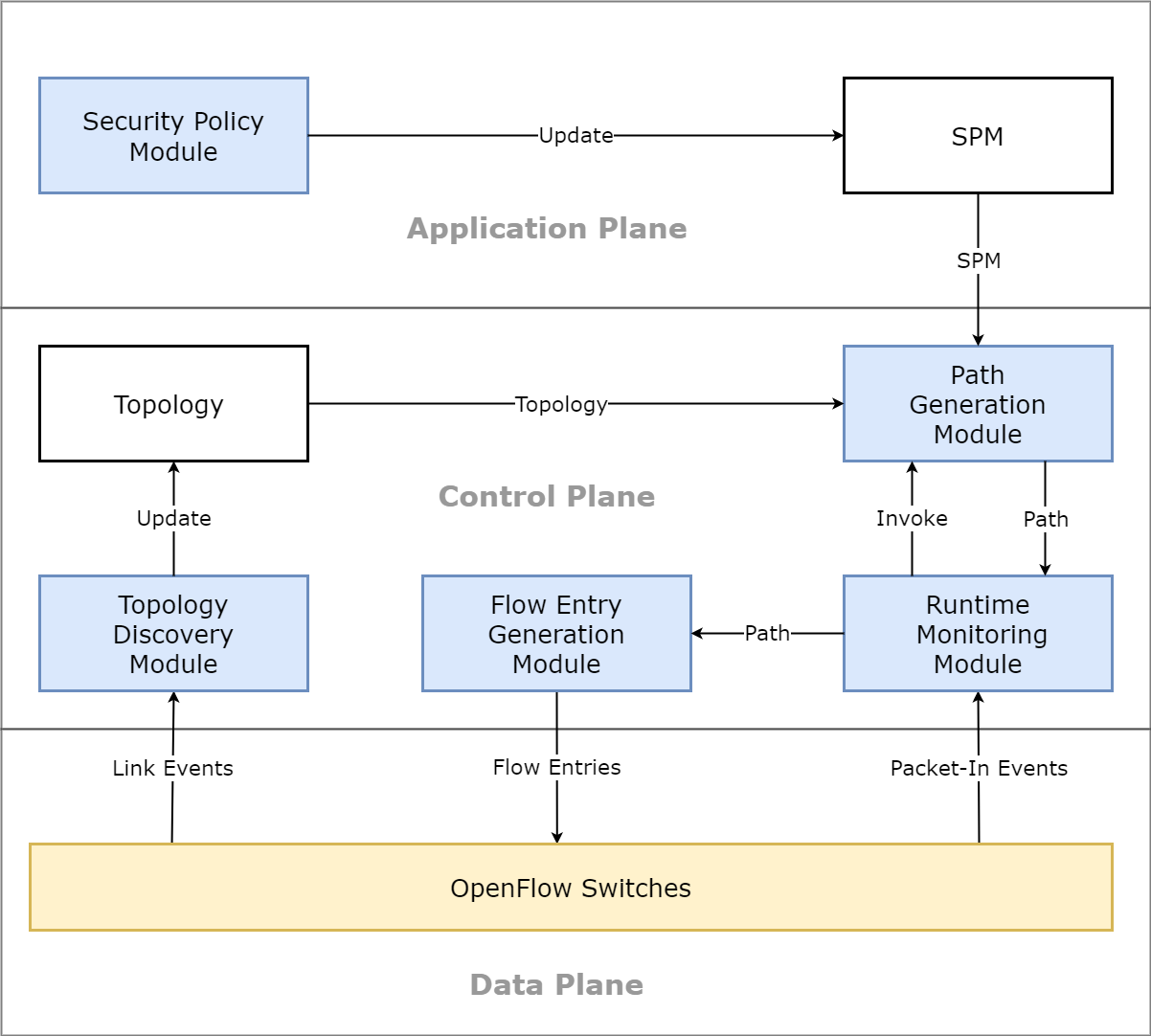
4.1 Overview of the Framework
Security policy module is deployed in the application plane and responsible for maintaining the security policy (SPM). Each access control relationship SPM is designed as a 3-tuple: , , based on the system model, where is the subject; is the object; = 0, 1 is a tag bit, =1 represents the relationship has been updated by user, =0 represents it is unchanged. SPM is stored as a text document and can be updated by the user at runtime.
Topology discovery module is deployed in the control plane and responsible for creating a dynamic real-time topology of the entire data plane by capturing the link events transmitted from the OpenFlow switches. Based on the system model, each edge in the topology is designed as a tuple: = , , , , , , where = , is a tag bit and can be changed by the real-time link events at runtime, = represents the edge can be used now, = represents the edge is interrupted now. For the convenient of researching, the cost of each edge is set to 1, i.e., =1. The generated topology is stored as a text document and can also be updated by the real-time link events at runtime.
Runtime monitoring module is deployed in the control plane and responsible for monitoring all the traffics in the data plane by capturing the real-time packet-in events transmitted from the OpenFlow switches. When a new packet-in event arrives in the controller, the module first invokes the path generation module to transform the latest security policy (SPM) into a set of connected paths in the data plane, then invokes the flow entry generation module to transform all the connected paths into their corresponding flow entries deployed in the OpenFlow switches which are passed by these paths. As SPM and the topology of data plane will be evolved with the runtime environment, this module is designed to be triggered by the real-time packet-in events continuously, so that, when SPM is changed (i.e., occurring =1) or the topology is changed (i.e., occurring =) at runtime, the module will first delete all the current flow entries deployed in the OpenFlow switches, then update all the flow tables by using the latest generated flow entries, so as to ensure the security properties defined by SPM can be synchronously and continuously hold in the data plane at runtime.
Path generation module is deployed in the control plane and invoked by the runtime monitoring module at runtime. The module is responsible for transforming each SPM input from the runtime monitoring module into a corresponding path in the data plane by using the latest topology file and the path searching algorithm. Specifically, it first transforms the subject and the object into the hosts and in the data plane respectively, then finds a shortest connected path between and by using the path searching algorithm, finally all the connected paths transformed from SPM are returned to the runtime monitoring module.
Flow entry generation module is also deployed in the control plane and invoked by the runtime monitoring module at runtime. The module is responsible for transforming the connected path into a set of flow entries deployed in the OpenFlow switches which are passed by the path, then utilizing the instructions provided by the controller to generate the practical flow entries and distributing these flow entries to the corresponding OpenFlow switches at runtime.
4.2 Runtime Monitoring Algorithm
The runtime monitoring algorithm deployed in the runtime monitoring module plays the role of coordinator in the framework, and can be described as Algorithm 1 in pseudo code. First of all, the algorithm creates two dynamic lists and by reading the latest SPM and Topo file respectively. If there existing an access control relationship has been changed by user (.=1) or a edge has been shut down in the topology (.=) at runtime, it will clear all the current flow entries deployed in the OpenFlow switches for ready of the updating. In the following, for each access control relationship , it maps the subject and the object with the switches and in the data plane, then transforms into a corresponding connected path by invoking the path searching algorithm djk-route(, , ). Based on the transformation rules, can be further transformed into a set of flow entries. When all the relationships in the List having been transformed, SPM has been transformed into a corresponding set of flow entries , the algorithm invokes the flow entry generation module to update the data plane by using . Since the algorithm is designed to be triggered by the packet-in events at runtime, so that it ensures the framework can perceive any changes in time when the security policy or the topology of data plane has been evolved with the environment, and then update the data plane synchronously at runtime.
4.3 Path Searching Algorithm
Another important algorithm in the framework is the path searching algorithm deployed in the path generation module. The algorithm is improved from the classic Dijkstra algorithm and can be described as the Algorithm 2 in pseudo code. First of all, the algorithm creates a dynamic matrix [][] by using the sum of Openflow switches and the topology file. In the following, it calculates a shortest connected path between and in the data plane by using [][] and the created stacks. After multi-round calculating, the shortest path between and is found and returned to the runtime monitoring module. As the cost of each edge has been set to 1 and not considering of the quality of services (QoS) of edges, so that the shortest path found by the algorithm is generated by calculating the minimum number of hops in the topology. Moreover, since the matrix [][] is dynamically created by the topology file, so that the searched shortest path will be evolved with the changing of the topology at runtime.
5 Implementation and Evaluations
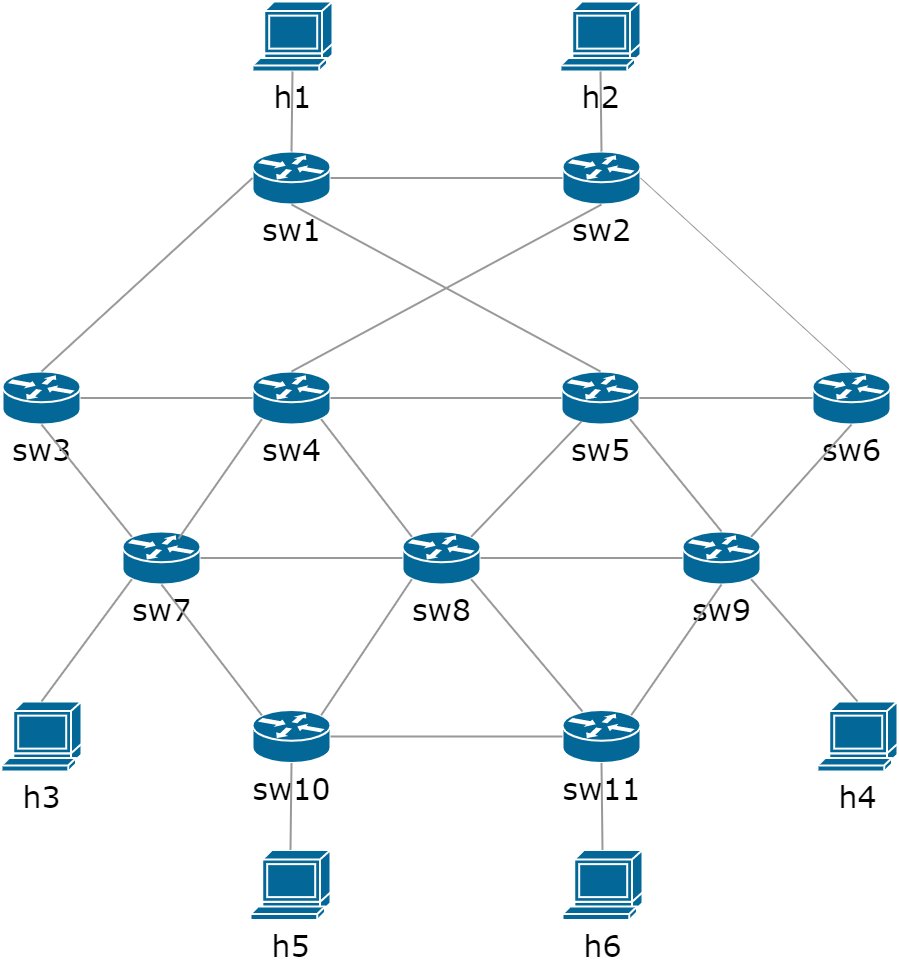
In order to validate the feasibility and effectiveness of the framework proposed in Section 4, we set up an experimental system and implement the framework with POX controller[27] and Mininet emulator[28]. First of all, we implement a virtual SDN network by using the Mininet emulator. As shown in Figure 3, the topology of the network consists of 6 hosts () and 11 OpenFlow switches (). We further implement the security policy module, topology discovery module, runtime monitoring module, path generation module and flow entry generation module with Python 3.6.1 and integrate these modules with the core of POX controller. The experimental system consists of a Lenovo workstation with Windows OS, Intel-i7 32Cores 2.60GHz CPU, 32GB RAM and a Raspberry platform with Linux OS, ARM-v7 CPU and 945MB RAM. The POX controller and the functional modules are deployed in Lenovo workstation, Mininet emulator is deployed in Raspberry platform, and Lenovo workstation is connected with Raspberry platform using coaxial cable directly.
| , , | |
|---|---|
| , , | |
| , , | |
| , , |
5.1 Effectiveness Evaluation
The security policy used for validating the effectiveness of the framework is shown in Table I. Since any effective interaction is bidirectional in SDN networks, i.e., the subject’s host and the object’s host must be ensured they can access each other in the data plane, so that we design the security policy as 4 access control relationships () to ensure (1) and (5) can access each other, (2) and (4) can access each other, and all the relationships of SPM are set as =1, i.e., having been updated by user. In the following, the effectiveness evaluations towards the framework will be carried out under 4 different scenarios at runtime, they are the effectiveness after loading the flow entries, the effectiveness after cutting down the path and the effectiveness after changing SPM.
5.1.1 Effectiveness after Loading the Flow Entries
The purpose of this experiment is to validate whether the data plane after loading the generated flow entries can hold the security properties defined by SPM. First of all, the subjects and objects of SPM shown in Table I, i,e., the , , and , are transformed into their corresponding hosts in the data plane by using security policy transformation. Specifically, the is transformed into = 10.0.0.1, , 1 , the is transformed into = 10.0.0.2, , 1 , the is transformed into = 10.0.0.4, , 1 and the is transformed into = 10.0.0.5, , 1 respectively. In the following, the path searching algorithm, i.e., Algorithm 2, searches the shortest path between the subject’s host and the object’s host for each SPM based on the latest topology generated from the topology file.
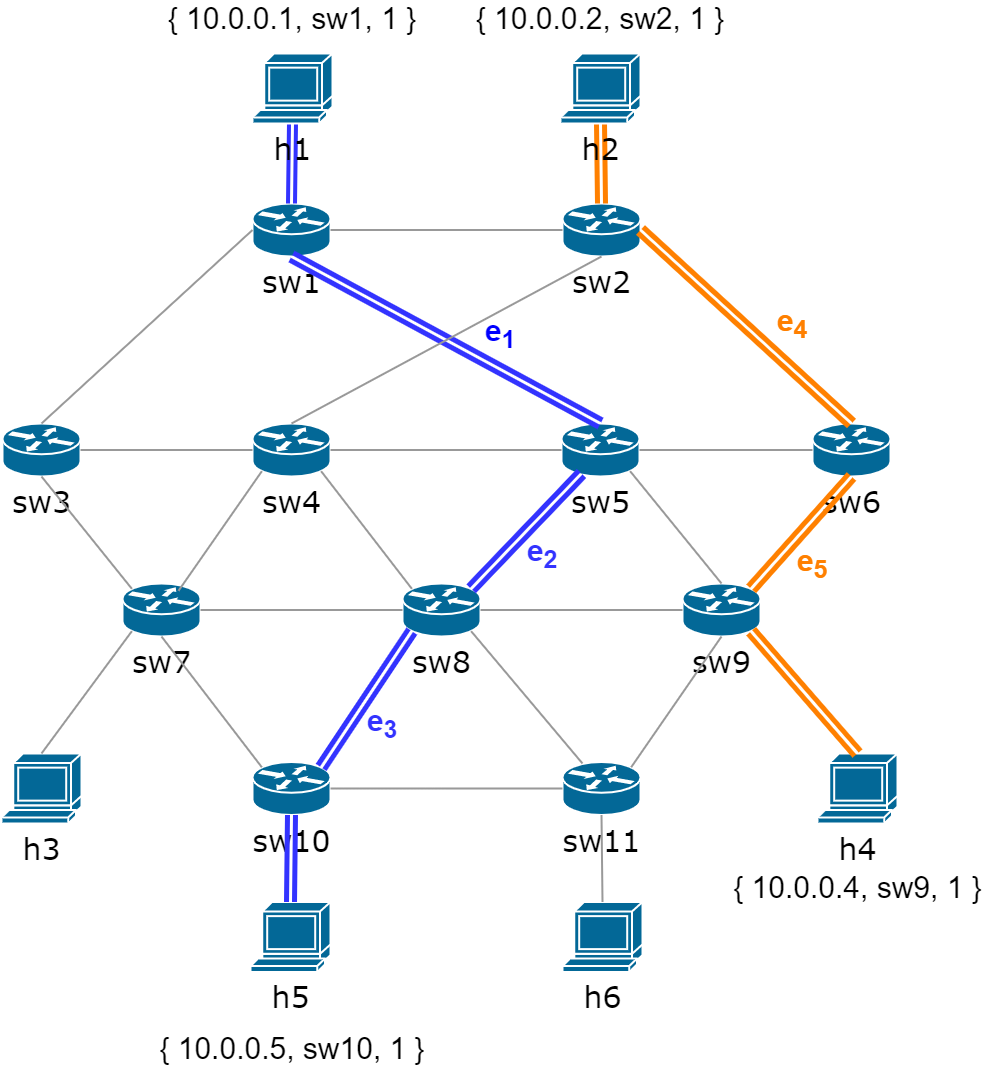
After that, the relationships shown in Table I have been transformed into 4 corresponding shortest connected paths () in the data plane. As shown in Figure 4, the is transformed into = , , , , , the is transformed into = , , , , , the is transformed into = , , , and the is transformed into = , , , , where the and are depicted with the blue lines, the and are depicted with the orange lines. In the following, the flow entry generation module transforms each path into a set of flow entries deployed in the switches passed by the path. Specifically, and are transformed into the flow entries deployed in the switches , , , , while and are transformed into the flow entries deployed in the switches , , .
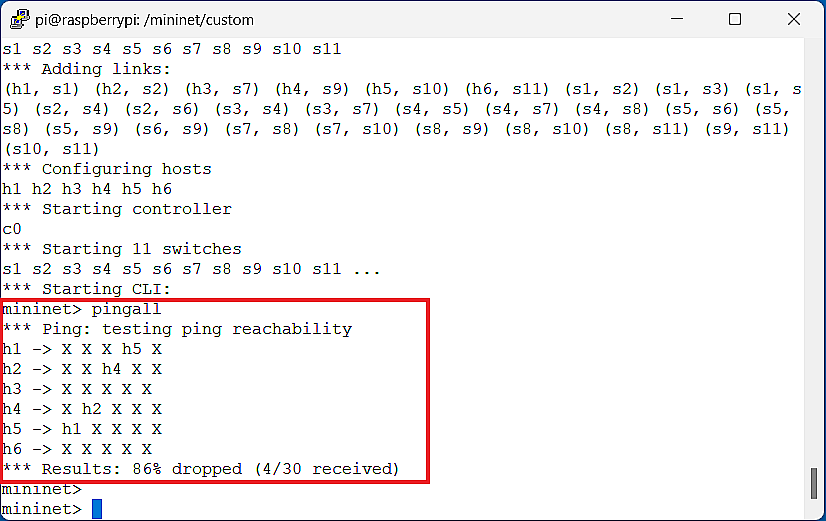
After that, we execute the instruction in the Mininet CLI and observe the reachability of the entire data plane. As shown in Figure 5, and can access each other, and can access each other either, so that the data plane after loading the generated flow entries has been proven that it can hold all the security properties defined by SPM.
5.1.2 Effectiveness after Cutting down the Path
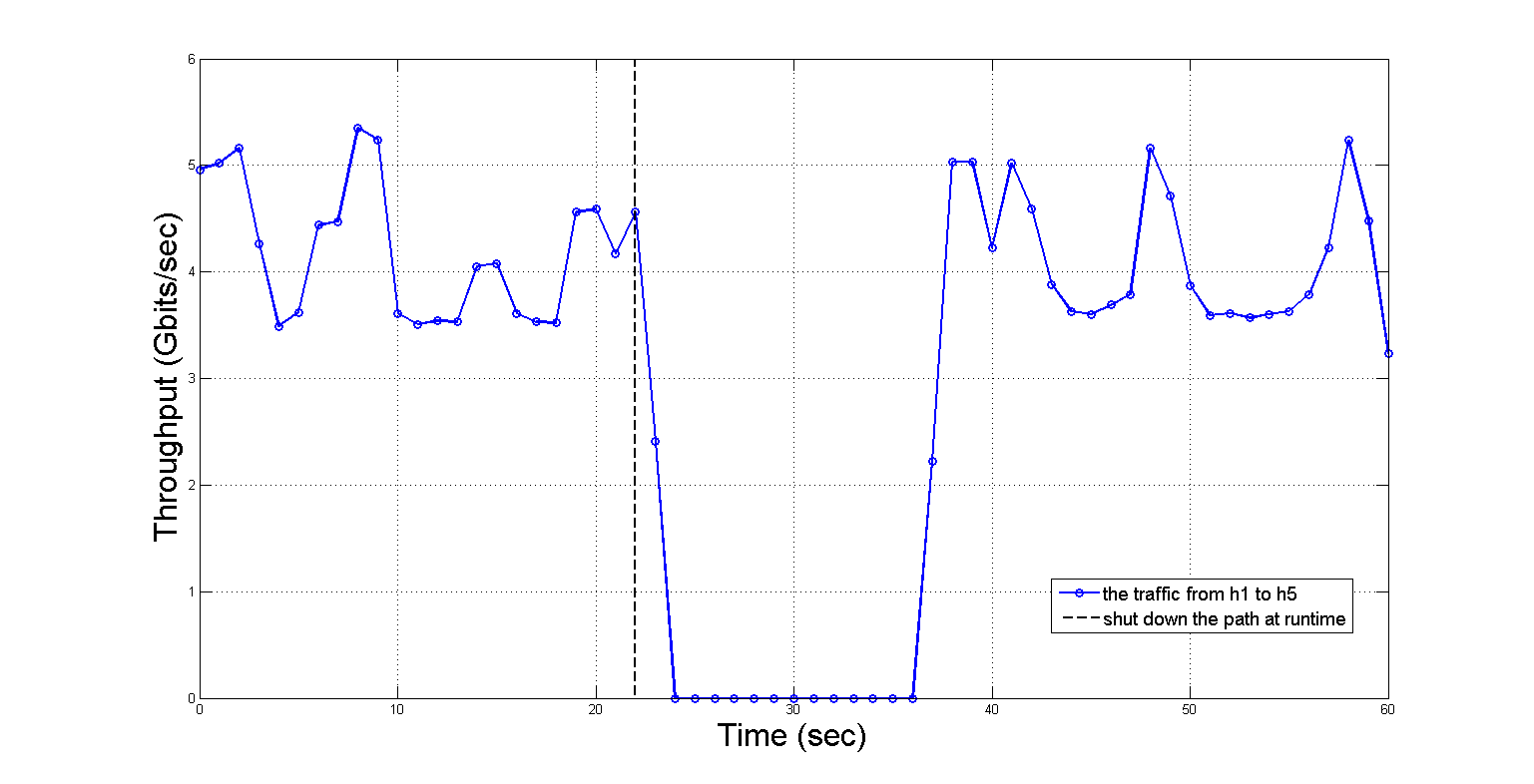
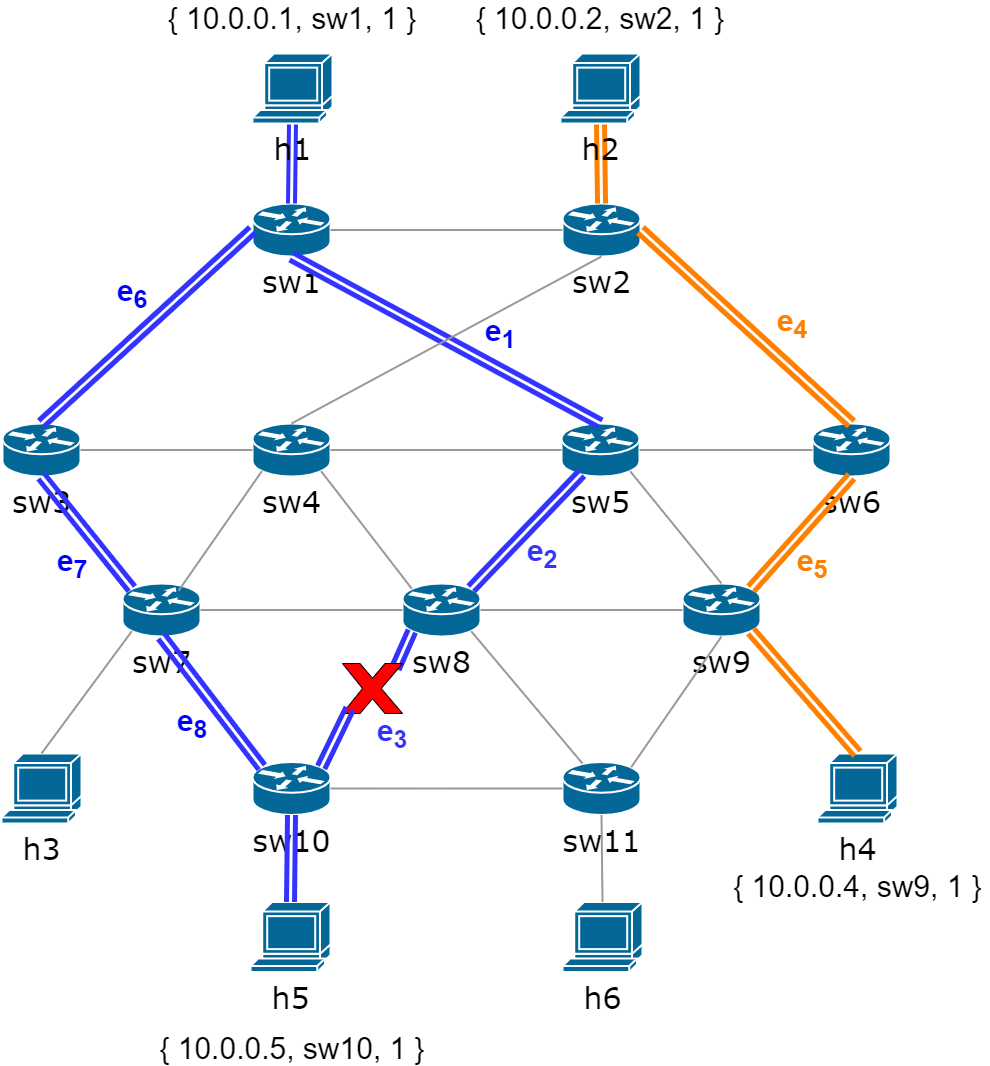
The purpose of this experiment is to validate whether the security properties defined by SPM can be continuously hold in the data plane after the connected path between the subject’s host and the object’s host is shut down at runtime. If the framework can synchronously perceive this change from the topology and automatically find another new connected path to keep the data plane holding the security properties at runtime, then the framework will be proven to be effective under this scenario. First of all, we let and can access each other by loading the corresponding flow entries into the data plane, and the shortest path between and is initialed with , , , , . In the following, we make a continuous TCP traffic sent from to by using the instruction in the Mininet CLI, we set the duration time of the experiment equals 60 seconds and record the throughput of the traffics in . When the time reaches 23 seconds, we shut down the edge between and existed in the path by using the instruction in the Mininet CLI and let the experiment going on. When the experiment is finished, we read the data recorded in and plot them in Figure 6. As shown in Figure 6, the throughput of the traffic sent from to is sharply declined after the edge is shut down at 23 seconds, and completely becomes zero from 25 seconds to 37 seconds. After 38 seconds, the traffic quickly returns to normal until the end of the experiment. The experimental result has illustrated that the framework can synchronously perceive the change caused by cutting down one edge between and , and automatically find another new shortest connected path between and , i.e., , , , , , so as to make the traffic returning to normal quickly and keep the data plane holding the security properties defined by SPM at runtime. The new shortest connected path searched by Algorithm 2 after cutting down the using path is shown in Figure 7.
5.1.3 Effectiveness after Changing SPM
The purpose of this experiment is to validate whether the security properties defined by SPM can be continuously hold in the data plane after SPM is changed by the user at runtime. If the framework can synchronously perceive this change from SPM and automatically update the flow entries deployed in the switches to keep the data plane holding the evolved security properties at runtime, then the framework will be proven to be effective under this scenario. First of all, we let and can access each other by loading a corresponding flow entries into the data plane, then make a continuous TCP traffic sent from to by using the instruction in the Mininet CLI, we set the duration time of the experiment equals 60 seconds and record all the throughput data of the traffic in .
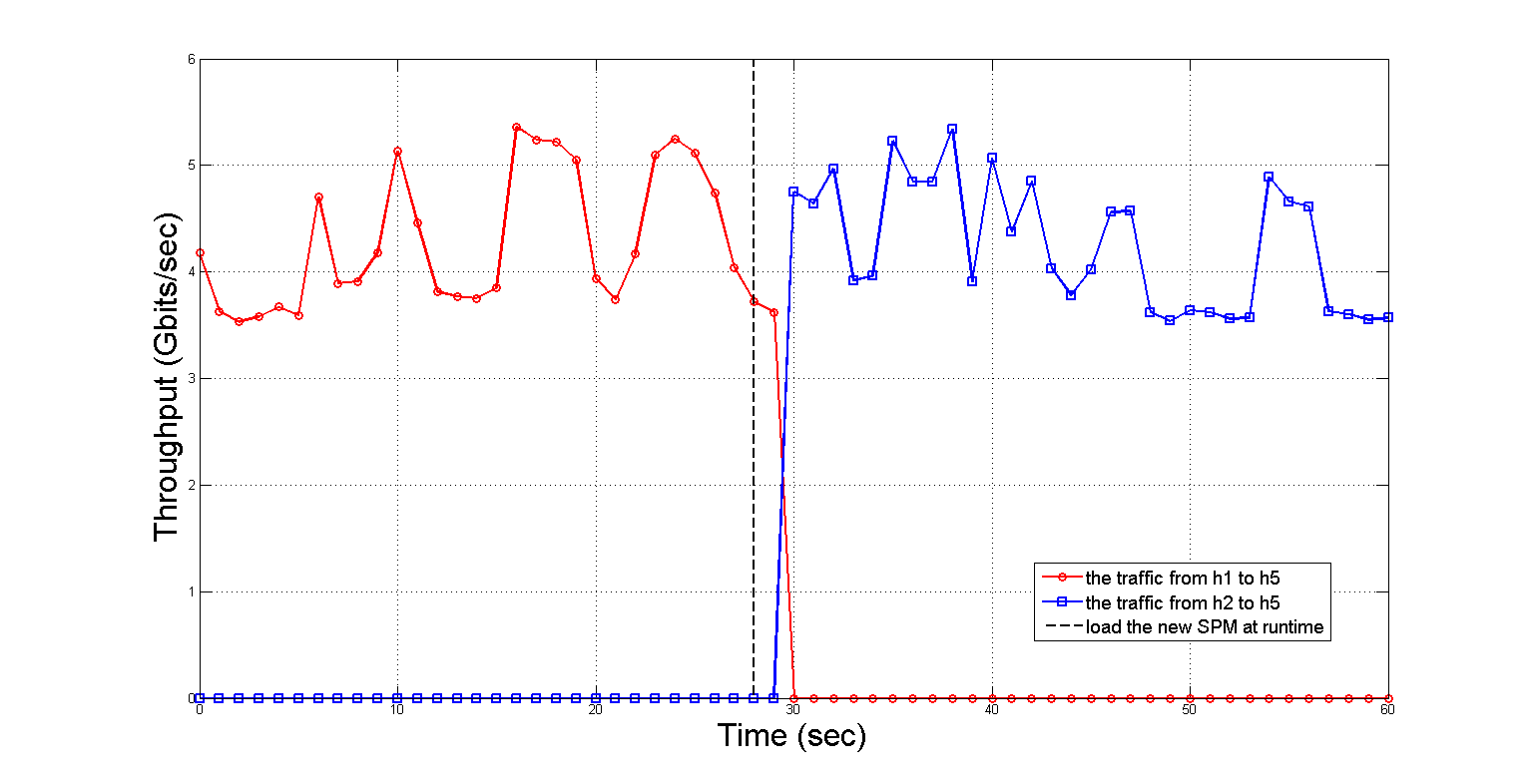
In the following, we first validate the effectiveness of the framework under the scenario of changing SPM from and can access each other to and can access each other at runtime, and the experimental result under this scenario is plotted in Figure 8. As shown in Figure 8, the throughput of the traffic sent from to , which is depicted with the red line, is quickly declined when we load the new SPM into the controller at 29 seconds, and completely becomes zero after 31 seconds. From 31 seconds until to the end of the experiment, can only receive the traffic sent from which is depicted with the blue line. The experimental result illustrates the framework can synchronously perceive this change and keep the data plane holding the evolved security properties after changing SPM from and can access each other to and can access each other at runtime.
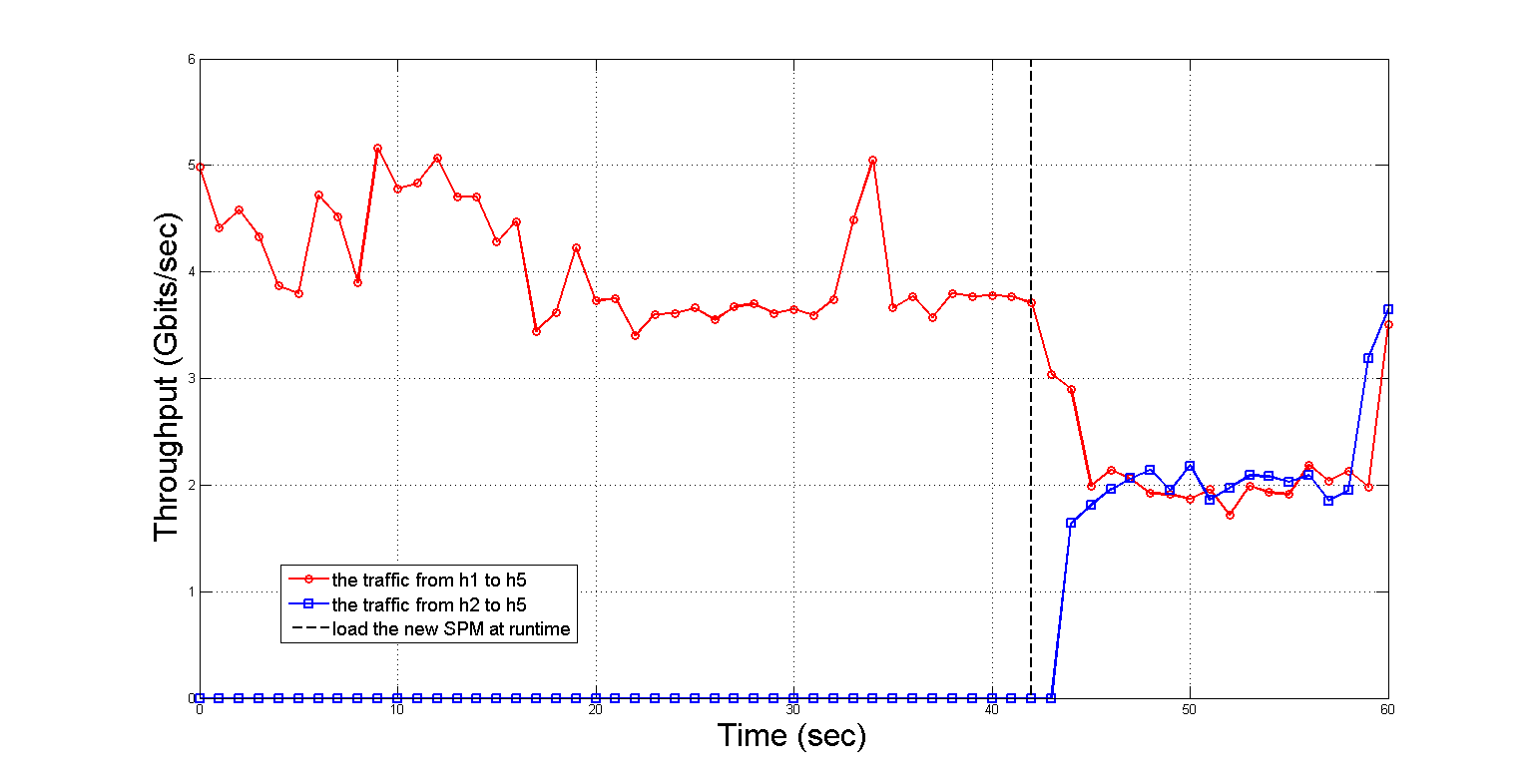
After that, we further validate the effectiveness of the framework under the scenario of adding a new relationship into SPM, i.e., adding and can access each other, at runtime. The experimental result under this scenario is plotted in Figure 9. As shown in Figure 9, the throughput of the traffic sent from to , which is depicted with the red line, still keeps normal before we load the new SPM into the controller at 43 seconds. From 44 seconds until to the end of the experiment, can receive the continuous traffic sent from which is depicted with the blue line, and can also receive the traffic sent from at the same time. Due to the crowding of the traffic sent from , the throughput of the traffic from is declined from 3.71GB/s to 1.99 GB/s. The throughput of the traffic sent from is still kept between 1.6GB/s and 2.2GB/s after 44 seconds. The experimental result illustrates the framework can synchronously perceive this change and keep the data plane holding the evolved security properties after adding a new relationship into SPM at runtime.
5.2 Performance Evaluation
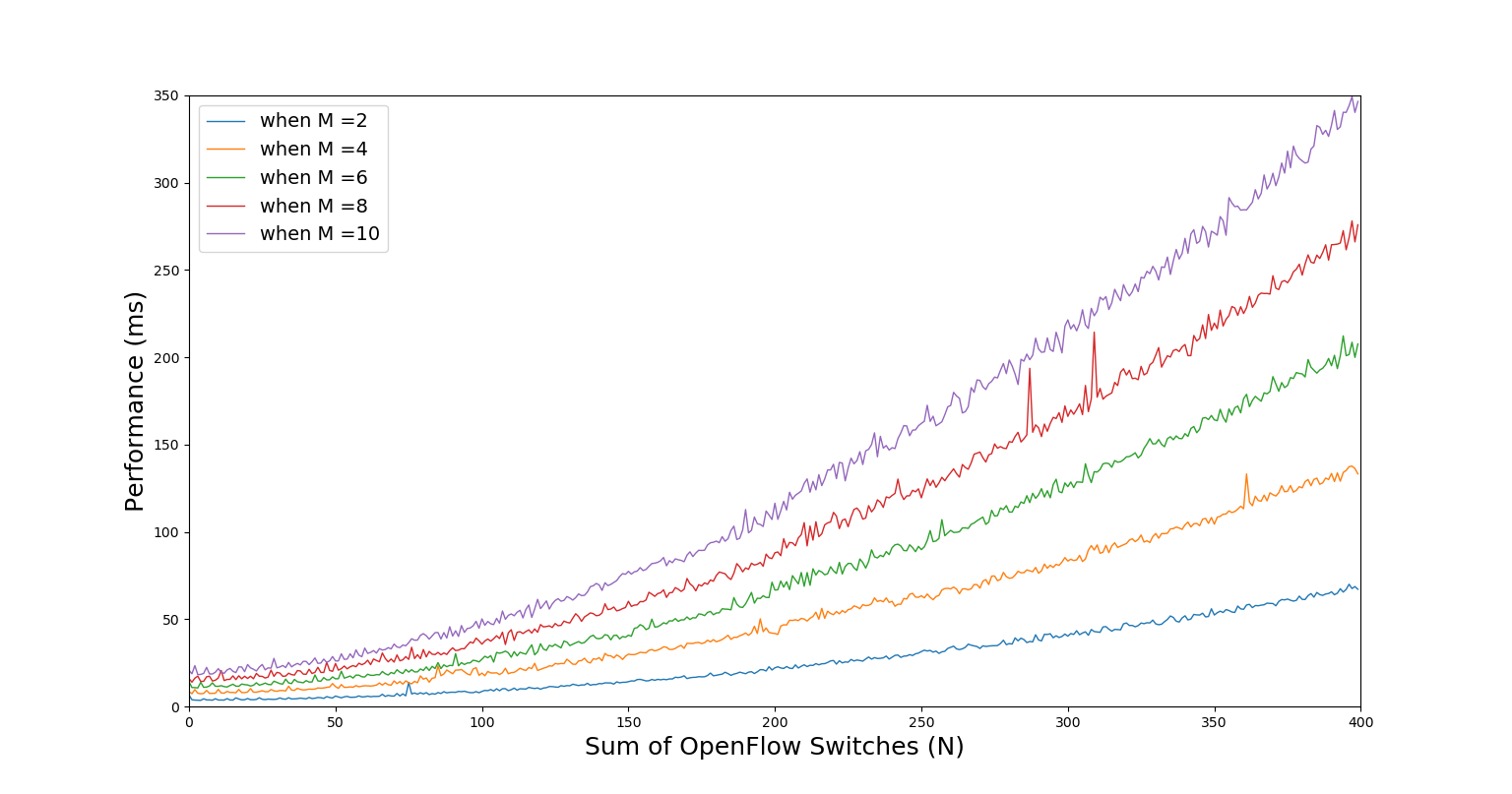
As the critical algorithm used for implementing the security policy transformation, the performance of the path searching algorithm, i.e., Algorithm 2, needs to be further evaluated. First of all, the sum of access control relationships of the security policy (SPM) is denoted as , and the sum of OpenFlow switches in the topology is denoted as in this performance evaluation. Then by leveraging the Python programming, the execution time of Algorithm 2 have been recorded in milliseconds (ms) for calculating the shortest paths under setting the different value of and . The experimental result is plotted in Figure 10. As shown in Figure 10, with gradually amplifying the value of from 2 to 10, and the value of from 11 to 400 respectively, the execution time of Algorithm 2 shows an obvious exponential upward trend. Moreover, according to the description of Algorithm 2, the time complexity for calculating only one shortest path will reach (), because the Algorithm 2 needs to create a dynamic matrix and further calculates the while loop, so that the time complexity for transforming all the access control relationships defined by SPM into their corresponding shortest paths will reach ().
6 Conclusion
In this paper, we propose a practical runtime security policy transformation framework for SDN networks. First of all, we specify the security policies used by SDN networks, such as access control policies or firewall policies, as a system model of security policy (SPM). SPM is of a high-level system model without containing any underlying information of data plane. From the theoretical level, we establish the system model for SDN network and propose a formal method to transform SPM into the corresponding flow entries automatically. The flow entry transformed from SPM is of a low-level system model containing the underlying information of data plane. From the practical level, we propose a runtime security policy transformation framework which consists of the security policy module, topology discovery module, runtime monitoring module, path generation module, as well as flow entry generation module. Leveraging these functional modules, the framework can solve the problem of how to find a connected path for each relationship defined by SPM in the data plane, how to transform the path into the system model of flow entries, as well as how to generate the practical flow entries by using the system model of flow entries. In order to validate the feasibility and effectiveness of the framework, we set up an experimental system and implement the framework by using POX controller and Mininet emulator. The experimental result illustrate the framework is completely effective at runtime.
However, there still exists some problems needed to be further researched in the future. The current path searching algorithm, i.e., Algorithm 2, used by the framework is improved from the classic Dijkstra algorithm and finds the shortest path by calculating the minimum number of hops in the topology. However, in the real SDN networks, the problem of searching a connected path between the two hosts need to consider the matters of quality of service (QoS), load balance, as well as some specific requirements about the traffic engineering at runtime, so that the framework needs to be further improved by employing some novel path searching algorithms based on multi-object optimization[29] or reinforcement learning[30] methods.
Acknowledgment
This paper has been sponsored and supported by National Key Research and Development Program of China (Grant No.2018YFB0803400), Doctoral Foundation of Qingdao Binhai University (Grant No. BS2022A10), partially supported by Key Program of National Natural Science Foundation of China (Grant No.61932013).
References
References
- [1] D. Kreutz, F. M. V. Ramos, P. E. Verissimo, C. E. Rothenberg, S. Azodolmolky, S. Uhlig, Software-defined networking: A comprehensive survey, Proceedings of the IEEE 103 (1) (2014) 10–13.
- [2] J. M. J. Garay, A. Mendiola, N. Toledo, E. Jacob, Flownac: Flow-based network access control, in: Third European Workshop on Software-defined Networks, 2014.
- [3] S. T. Yakasai, C. G. Guy, Flowidentity: Software-defined network access control, in: IEEE Conference on Network Function Virtualization and Software-defined Networks, 2015.
- [4] H. Hu, W. Han, G. J. Ahn, Z. Zhao, Flowguard: Building robust firewalls for software-defined networks, in: Acm Sigcomm Workshop on Hot Topics in Software Defined Networking, 2014.
- [5] M. Koerner, O. Kao, Mac based dynamic vlan tagging with openflow for wlan access networks, Procedia Computer Science 94 (2016) 497–501.
- [6] K. Phemius, M. Bouet, J. Leguay, Disco: Distributed sdn controllers in a multi-domain environment, in: Noms IEEE/IFIP Network Operations and Management Symposium, 2014.
- [7] Y. Meng, Z. Huang, G. Shen, C. Ke, A security policy model transformation and verification approach for software defined networking, Computers & Security 100 (102089).
- [8] A. Kleppe, J. Warmer, W. Bast, MDA Explained, Addison-Wesley Professional, 2004.
- [9] J. P. D. Albuquerque, H. Krumm, P. L. D. Geus, Formal validation of automated policy refinement in the management of network security systems, International Journal of Information Security 9 (2) (2010) 99–125.
- [10] K. Jayaraman, M. C. Rinard, M. Tripunitara, V. Ganesh, S. Chapin, Automatic error finding in access control policies, in: CCS, 2011.
- [11] C. Wang, G. Wang, A. Chen, H. Wang, S. Uczekaj, A policy-based approach for qos specification and enforcement in distributed service-oriented architecture, in: IEEE International Conference on Services Computing, 2005.
- [12] C. A. Kamienski, R. Dantas, E. Azevedo, C. Dias, B. Ohlman, Unleashing the power of policies for service-oriented computing, in: International Conference on Network and Service Management, 2011.
- [13] S. Davy, B. Jennings, Harnessing models for policy conflict analysis, in: AIMS2007, 2007.
- [14] I. Luck, C. Schfer, H. Krumm, Model-based tool-assistance for packet-filter design, in: Policies for Distributed Systems and Networks, International Workshop, POLICY 2001 Bristol, UK, January 29-31, 2001, Proceedings, 2001.
- [15] J. P. D. Albuquerque, H. Krumm, P. L. D. Geus, Policy modeling and refinement for network security systems., in: IEEE International Workshop on Policies for Distributed Systems and Networks, 2005.
- [16] B. Lampson, M. Abadi, M. Burrows, Authentication in distributed systems: theory and practice, in: ACM SIGOPS Operating Systems Review, 1991.
- [17] M. Abadi, M. Burrows, B. Lampson, G. Plotkin, A calculus for access control in distributed systems, in: International Cryptology Conference, 1991.
- [18] N. Kang, J. Reich, J. Rexford, D. Walker, Policy transformation in software defined networks, Acm Sigcomm Computer Communication Review 42 (4) (2012) 309.
- [19] J. Ma, D. Zhang, G. Xu, Y. Yang, Model checking based security policy verification and validation, in: International Workshop on Intelligent Systems and Applications, 2010.
- [20] E. M. Clarke, O. Grumberg, D. Peled, Model checking, Springer Berlin Heidelberg, 1997.
- [21] E. S. Alshaer, H. H. Hamed, Firewall policy advisor for anomaly discovery and rule editing, in: IFIP/IEEE Eighth International Symposium on Integrated Network Management, 2003.
- [22] A. Bandara, E. Lupu, A. Russo, Using event calculus to formalise ppolicy specification and analysis, in: International workshop on policies for distributed systems and networks, 2003, pp. 26–39.
- [23] M. J. May, C. A. Gunter, I. Lee, Privacy apis: Access control techniques to analyze and verify legal privacy policies, in: IEEE Computer Security Foundations Workshop, 2006, pp. 85–97.
- [24] J. Rubio-Loyola, J. Serrat, M. Charalambides, P. Flegkas, A. Lluch-Lafuente, Using linear temporal model checking for goal-oriented policy refinement frameworks, in: 6th IEEE International Workshop on Policies for Distributed Systems and Networks (POLICY 2005), 6-8 June 2005, Stockholm, Sweden, 2005.
- [25] A. Graham, T. Radhakrishnan, C. Grossner, Incremental Validation of Policy-Based Systems, 2004.
- [26] J. Baliosian, J. Serrat, Finite state transducers for policy evaluation and conflict resolution, in: IEEE International Workshop on Policies for Distributed Systems and Networks, 2004, pp. 250–259.
-
[27]
POX (2017).
[link].
URL https://github.com/noxrepo/pox -
[28]
Mininet (2012).
[link].
URL http://www.mininet.org - [29] R. T. Marler, J. S. Arora, Survey of multi-objective optimization methods for engineering, Structural and multidisciplinary optimization 26 (6) (2004) 369–395.
- [30] L. P. Kaelbling, M. L. Littman, A. W. Moore, Reinforcement learning: A survey, Journal of artificial intelligence research 4 (1996) 237–285.