Adaptation for Validation of a Consolidated Control Barrier Function based Control Synthesis
Abstract
We develop a novel adaptation-based technique for safe control design in the presence of multiple control barrier function (CBF) constraints. Specifically, we introduce an approach for synthesizing any number of candidate CBFs into one consolidated CBF candidate, and propose a parameter adaptation law for the weights of its constituents such that the controllable dynamics of the consolidated CBF are non-vanishing. We then prove that the use of our adaptation law serves to certify the consolidated CBF candidate as valid for a class of nonlinear, control-affine, multi-agent systems, which permits its use in a quadratic program based control law. We highlight the success of our approach in simulation on a multi-robot goal-reaching problem in a crowded warehouse environment, and further demonstrate its efficacy experimentally in the laboratory via AION ground rovers operating amongst other vehicles behaving both aggressively and conservatively.
I Introduction
Since the arrival of control barrier functions (CBFs) to the field of safety-critical systems [1], much attention has been devoted to the development of their viability for safe control design [2, 3, 4]. As a set-theoretic approach founded on the notion of forward invariance, CBFs encode safety in that they ensure that any state beginning in a safe set remains so for all future time. In the context of control design, CBF conditions are often used as constraints in quadratic program (QP) based control laws, either as safety filters [5] or in conjunction with stability constraints (e.g. control Lyapunov functions) [6]. Their utility has been successfully demonstrated for a variety of safety-critical applications, including mobile robots [7, 8], unmanned aerial vehicles (UAVs) [9, 10], and autonomous driving [11, 12]. But while it is now well-established that CBFs for controlled dynamical systems serve as certificates of safety, the verification of candidate CBFs as valid is in general a challenging problem.
Though for a single CBF there exist guarantees of validity under certain conditions for systems with either unbounded [2] or bounded control authority [13, 14], these results do not generally extend to control systems seeking to satisfy multiple candidate CBF constraints. Recent approaches to control design in the presence of multiple CBF constraints have mainly circumvented this challenge by considering only one such constraint at a given time instance, either by assumption [15] or construction in a non-smooth manner [16, 17]. In contrast, the authors of [18] and [19] each propose smoothly synthesizing one candidate CBF for the joint satisfaction of multiple constraints, but make no attempt to validate their candidate function. The problem of safe control design under a multitude of constraints is especially relevant in practical applications involving autonomous mobile robots, where the main challenge is in the robot completing its nominal objective while satisfying constraints related to collision avoidance with respect to obstacles both static and dynamic.
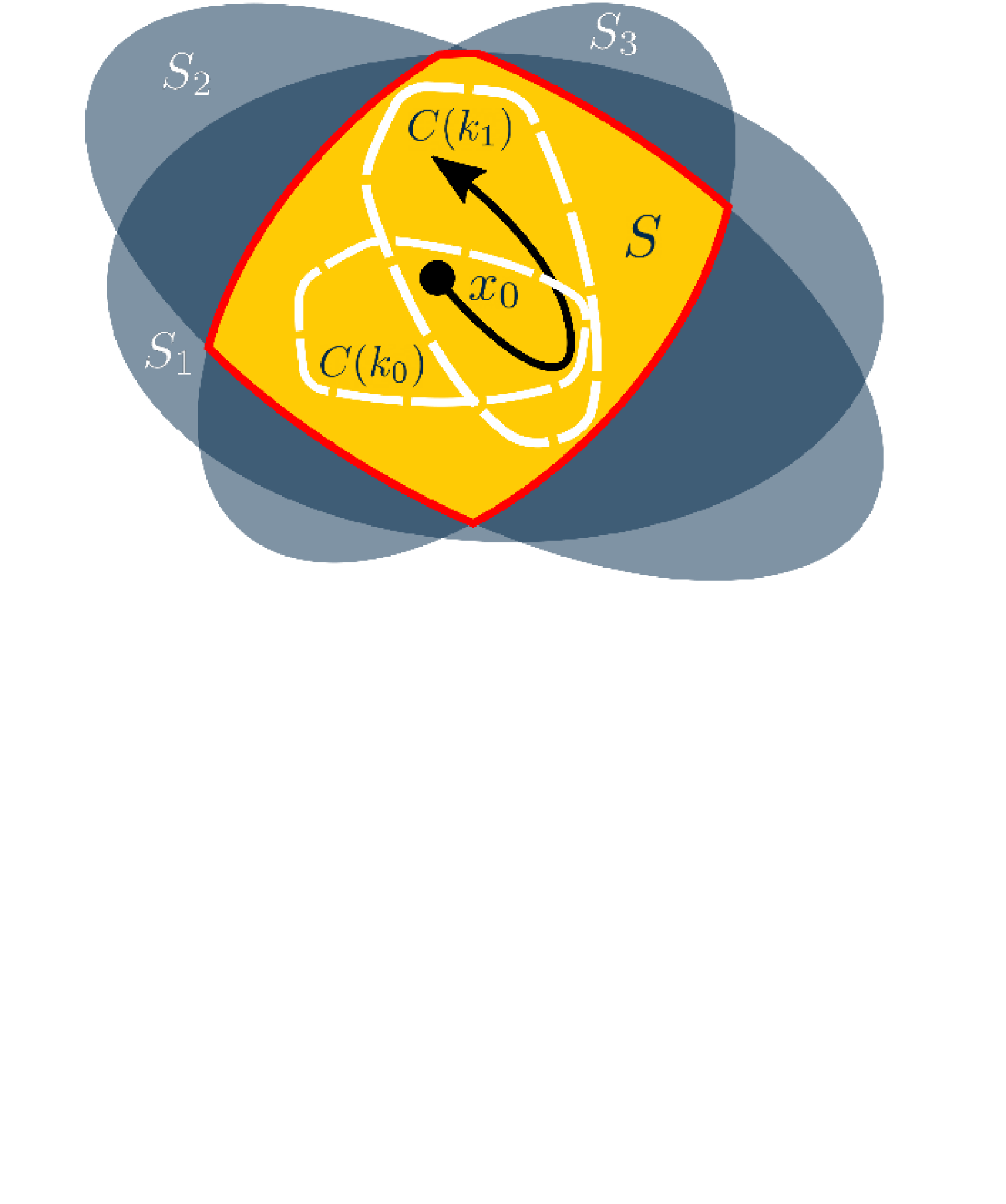
It is with this problem in mind that we propose a consolidated CBF (C-CBF) based approach to control design for multi-agent systems in the presence of both non-communicative and non-responsive (though non-adversarial) agents. Constructed by smoothly synthesizing any arbitrary number of candidate CBFs into one, our C-CBF defines a new super-level set that can under-approximate the intersection of its constituent sets arbitrarily closely (see Figure 1). We further propose a parameter adaptation law for the weighting of the constituent functions, and prove that its use renders our C-CBF valid and the super-level set controlled invariant for the class of nonlinear, control-affine, multi-agent systems under consideration. And while various works have utilized parameter adaptation in the context of control for safety-critical systems, usually in an attempt to either learn [20, 21] or compensate for [22] unknown parameters in the system dynamics, our proposed adaptation law is the first to our knowledge to be used for the simultaneous verified satisfaction of multiple CBF constraints. To show the effectiveness of our proposed control formulation, we study a decentralized multi-robot goal-reaching problem in a crowded warehouse environment amongst non-responsive agents. As a practical demonstration, we tested our controller experimentally on a collection of ground rovers in the laboratory setting and found that it succeeded in safely driving the rovers to their goal locations amongst non-responsive agents behaving both aggressively and conservatively.
The paper is organized as follows. Section II introduces some preliminaries, including set invariance, optimization based control, and our first problem statement. In Section III, we introduce the form of our C-CBF and propose a parameter adaptation law for rendering it valid. Sections IV and V contain the results of our simulated and experimental case studies respectively, and in Section VI we conclude with final remarks and directions for future work.
II Mathematical Preliminaries
We use the following notation throughout the paper. denotes the set of real numbers. The set of integers between and (inclusive) is . represents the Euclidean norm. A function is said to belong to class if and is increasing on the interval , A function is said to belong to class if for each fixed (resp. ), the function is decreasing with respect to (resp. ) and is such that for (resp. ). The Lie derivative of a function along a vector field at a point is denoted .
In this paper we consider a multi-agent system, each of whose constituent agents may be modelled by the following class of nonlinear, control-affine dynamical systems:
| (1) |
where and are the state and control input vectors for the ith agent, with the input constraint set, and where and are known, locally Lipschitz, and not necessarily homogeneous . We denote the concatenated state vector as , the concatenated control input vector as , and as such express the full system dynamics as
| (2) |
where and . We assume that a (possibly empty) subset of the agents are communicative, denoted , in the sense that they share information (e.g. states, control objectives, etc.) with one another, and that the remaining agents are non-communicative, denoted , in that they do not share information, where and are the number of communicative and non-communicative agents respectively. We further assume that all agents are non-adversarial in that they do not seek to damage or otherwise deceive others, though there may be non-communicative agents which are non-responsive () in that they do not actively avoid unsafe situations.
II-A Safety and Forward Invariance
Consider a set of safe states defined implicitly by a continuously differentiable function , as follows:
| (3) |
where the boundary and interior of are denoted as and respectively. In many works (e.g. [23, 24]), the set defined by (3) is referred to as safe if it is forward-invariant, i.e. if , . Nagumo’s Theorem provides a necessary and sufficient condition for rendering the set forward-invariant for the system (2).
Lemma 1 (Nagumo’s Theorem[25]).
One way to render a set forward-invariant is to use CBFs in the control design.
Definition 1.
In this paper, we assume that is Lipschitz continuous so that and are likewise. In other works (e.g. [26]), the function responsible for defining is a CBF if there exists a class function satisfying
| (6) |
We note, however, that with unbounded control authority (i.e. ) a sufficient condition for the existence of some satisfying (5), and thus for to be a CBF, is , , though this does not generally hold for a system with multiple CBF constraints.
II-B Control Design using CBFs
Decentralized controllers, in which agents compute inputs based on local information, have found empirical success as a control strategy for multi-agent systems of the form (2) [27, 28]. The following is an example of one such controller for an agent with safety constraints encoded via candidate CBFs:
| (7a) | ||||
| s.t. | ||||
| (7b) | ||||
where (7a) seeks to produce a control solution that deviates minimally from some nominal input , and (7b) encodes safety constraints of the form (5) via candidate CBFs , where and . Notably, for many classes of systems (7) is neither guaranteed to be feasible nor to preserve safety between agents [8]. When some subset of agents are able to communicate with one another, i.e. agents share information, their control inputs may be computed in a centralized fashion as follows:
| (8a) | ||||
| (8b) | ||||
| (8c) | ||||
where is the nominal input vector shared amongst communicative agents, is the Minkowski sum of their input constraint sets, (8b) denotes the individual CBF constraints for agent (e.g. speed), and (8c) represents combinations of safety constraints between agents (e.g. collision avoidance), where , , and . When all agents are communicative, (8) is guaranteed to be safe provided that it is feasible.
A challenge when it comes to both (7) and (8) is in satisfying all of the safety constraints simultaneously, especially when it comes to the design of . In some recent works, authors have proposed setting and including the parameters as decision variables in the QP [29] (and thus an additional term for in the objective function), but the performance of these approaches are still heavily dependent on the gains . Other techniques have avoided the issue of multiple candidate CBFs by assuming that only one constraint is in need of satisfaction at once [15] or by synthesizing a single non-smooth candidate CBF [16, 17], both of which may lead to undesirable chattering behavior or the loss of existence and uniqueness of solutions. We seek to address this open problem, and require the following assumption to do so.
Assumption 1.
The intersection of the safe sets for all is non-empty, i.e. .
Problem 1.
Given that Assumption 1 holds for a collection of candidate control barrier functions corresponding to safe sets , design a consolidated control barrier function candidate with constituent gains for the zero super-level set such that for all satisfying , .
III Consolidated CBF based Control
In this section, we first introduce our proposed solution to Problem 1, a consolidated control barrier function (C-CBF) candidate that smoothly synthesizes multiple candidate CBFs into one, and then design a parameter adaptation law which renders the candidate C-CBF valid for safe control design.
III-A Consolidated CBFs
Let the vector of candidate CBFs evaluated at a given state be denoted , and define a gain vector as , where for all . Our C-CBF candidate is the following:
| (9) |
where belongs to class , is continuously differentiable, and satisfies . For example, the decaying exponential function, i.e. , satisfies these requirements over the domain . With possessing these properties, it follows then that the new zero super level-set is a subset of (i.e. ), where the level of closeness of to depends on the choices of gains . This may be confirmed by observing that if any then , and thus for it must hold that , for all .
As such, defined by (9) is a solution to Problem 1, i.e. is a C-CBF candidate. This implies via Lemma 1 that if is valid over the set , then is controlled invariant and thus the trajectories of (2) remain safe with respect to each constituent safe set , . By Definition 1, for a static gain vector (i.e. ) the function is a CBF on the set if there exists such that the following condition holds for all :
| (10) |
where from (9) it follows that
| (11) | ||||
| (12) |
Again taking as an example, we obtain that , in which case it is evident that the role of the gain vector is to weight the constituent candidate CBFs and their derivative terms and in the CBF condition (10). Thus, a higher value indicates a weaker weight in the CBF dynamics, as the exponential decay overpowers the linear growth. Due to the combinatorial nature of these gains, for an arbitrary there may exist some such that , which may violate (6) and lead to the state exiting (and potentially as a result). Using online adaptation of , however, it may be possible to achieve for all , which motivates the following problem.
Problem 2.
Given a C-CBF candidate defined by (9) and associated with the set , design an adaptation law such that for all .
III-B Adaptation for Control Synthesis
Before proceeding with our main result, we require the following assumption.
Assumption 2.
The matrix of controlled candidate CBF dynamics is not all zero, i.e.
| (13) |
We now present our main result, an adaptation law that solves Problem 2 and thus renders a valid CBF for the set , for all .
Theorem 1.
Suppose that there exist candidate CBFs defining sets , , and that it is known that . If is such that at , then, under the ensuing adaptation law,
| (14a) | ||||
| (14b) | ||||
| (14c) | ||||
the controlled CBF dynamics for all , and thus the function defined by (9) is a valid CBF for the set , for all , where is a positive-definite gain matrix, , is the nominal , is the vector of minimum allowable values , and
| (15) | ||||
| (16) |
with , , and
| (17) |
such that constitutes a basis for the null space of , i.e. , where is given by (13).
Proof.
First, given (9), we have that
where is given by (15), by (13), , and . As such, and . With , it follows that as long as it is possible to choose such that . We will now show that with given by (14) it holds that and thus is a CBF for , for all .
Since , the problem of showing that is equivalent to proving that . Since the vector can be expressed as a sum of vectors perpendicular to and parallel to (respectively and ), it follows that as long as , where by vector projection, and is given by (17). Thus, a sufficient condition for is that
| (18) |
for some , where is given by (16). Then, by defining a function , it follows from (5) that when (18) is true at , it is true as long as (14c) holds.
Therefore, gains adapted according to the law (14) are guaranteed to result in . Thus, is a CBF for the set , for all . This completes the proof. ∎
Remark 1.
With depending on basis vectors spanning , it is not immediately obvious under what conditions is continuous (or even well-defined). Prior results show that if the rank of is constant then varies continuously [30], but analytical derivations of are not available to the best of our knowledge. In practice, we observe that the rank of is indeed constant, and we approximate numerically using finite-difference methods.
With consolidating the many constituent constraints into one CBF condition, we can then replace the centralized CBF-QP controller (8) with the following:
| (19a) | ||||
| s.t. | ||||
| (19b) | ||||
where and . If all agents are communicative, i.e. , then since is a CBF for the set , for all , the system trajectories are guaranteed to stay within and thus remain safe. In the presence of non-communicative agents, we replace the decentralized CBF-QP controller (7) with
| (20a) | ||||
| s.t. | ||||
| (20b) | ||||
where , i.e. the portion of the dynamics of that agent controls, and , where . While for the case of unbounded control authority is similarly unbounded, in practice it is reasonable to assume that agents have limited control authority and thus to use (20) assuming some bounded .
IV Multi-Robot Numerical Study
In this section, we demonstrate our C-CBF controller on a decentralized multi-robot goal-reaching problem.
Consider a collection of 3 non-communicative, but responsive robots () in a warehouse environment seeking to traverse a narrow corridor intersected by a passageway occupied with 6 non-responsive agents (). The non-responsive agents may be e.g. humans walking or some other dynamic obstacles. Let be an inertial frame with a point denoting its origin, and assume that each robot may be modeled according to a dynamic extension of the kinematic bicycle model described by [31, Ch. 2], provided here for completeness:
| (21a) | ||||
| (21b) | ||||
| (21c) | ||||
| (21d) | ||||
| (21e) | ||||
where and denote the position (in m) of the center of gravity (c.g.) of the ith robot with respect to , is the orientation (in rad) of its body-fixed frame, , with respect to , is the slip angle111 is related to the steering angle via , where is the wheelbase with (resp. ) the distance from the c.g. to the center of the front (resp. rear) wheel. (in rad) of the c.g. of the vehicle relative to (assume ), and is the velocity of the rear wheel with respect to . The state of robot is denoted , and its control input is , where is the acceleration of the rear wheel (in m/s2), and is the angular velocity (in rad/s) of .
The challenges of this scenario relate to preserving safety despite multiple non-communicative and non-responsive agents present in a constrained environment. A robot is safe if it 1) obeys the speed restriction, 2) remains inside the corridor area, and 3) avoids collisions with all other robots. Speed is addressed with the following candidate CBF:
| (22) |
where , while for corridor safety and collision avoidance we used forms of the relaxed future-focused CBF introduced in [11] for roadway intersections, namely
| (23) | ||||
| (24) | ||||
where (23) prevents collisions with the corridor walls (defined as lines in the -plane via ), and (24) prevents inter-robot collisions and is defined , , where , is the Euclidean distance between agents and at arbitrary time , and denotes the time in the interval at which the minimum inter-agent distance will occur under constant velocity future trajectories. For a more detailed discussion on future-focused CBFs, see [11]. As such, (22), (23), and (24) define the sets
the intersection of which constitutes the safe set for agents , i.e. .
We control robots using a C-CBF based decentralized controller of the form (20) with constituent functions , , , an LQR based nominal control input (see [11, Appendix 1]), and initial gains . The non-responsive agents used a similar LQR controller to move through the passageway in pairs of two, with the first two pairs passing through the intersection without stopping and the last pair stopping at the intersection before proceeding.
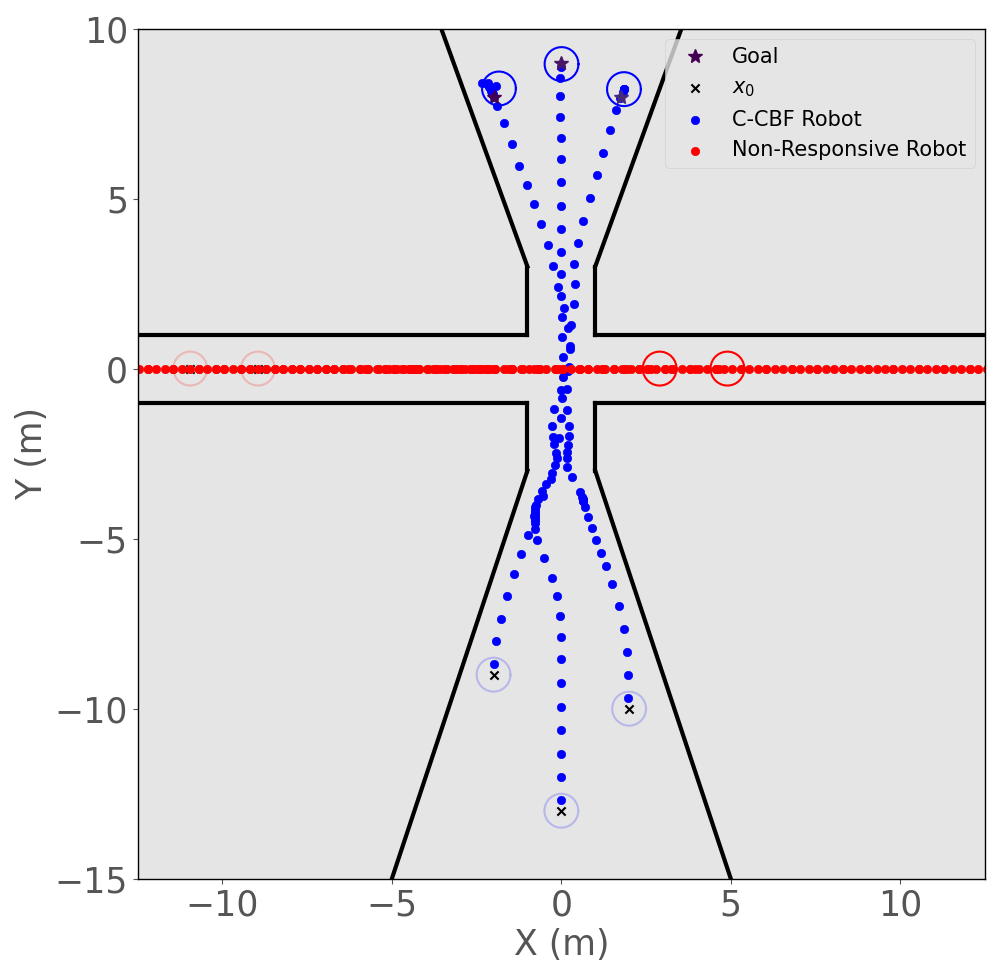
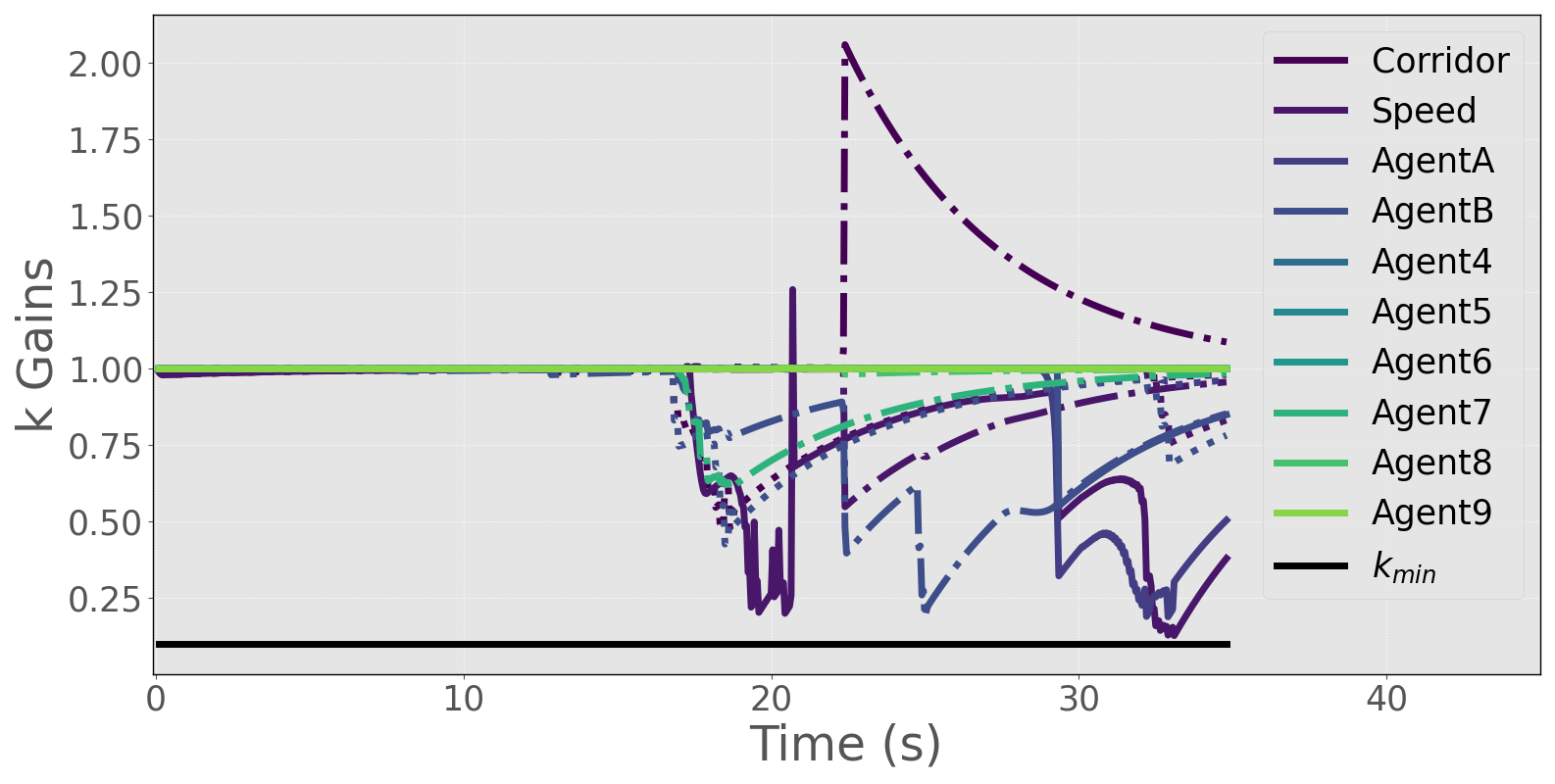
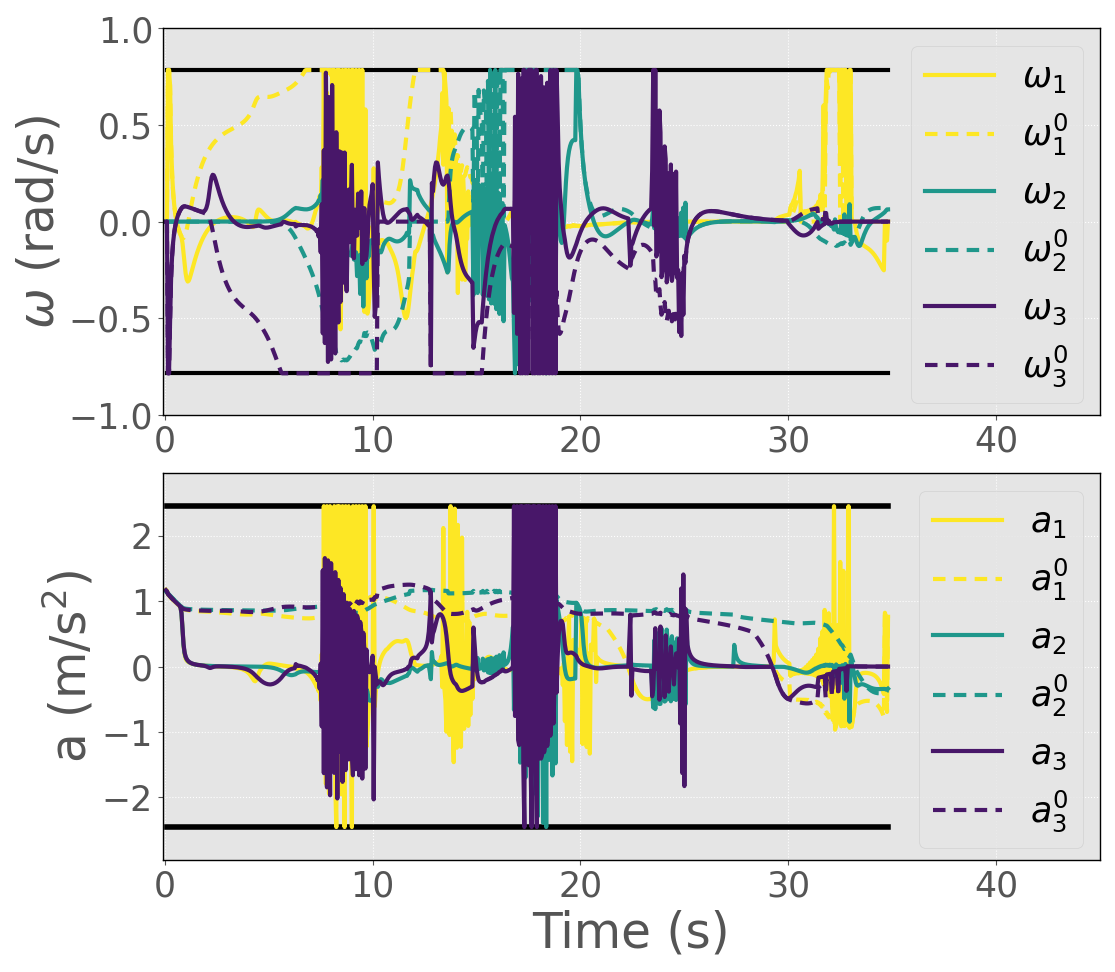
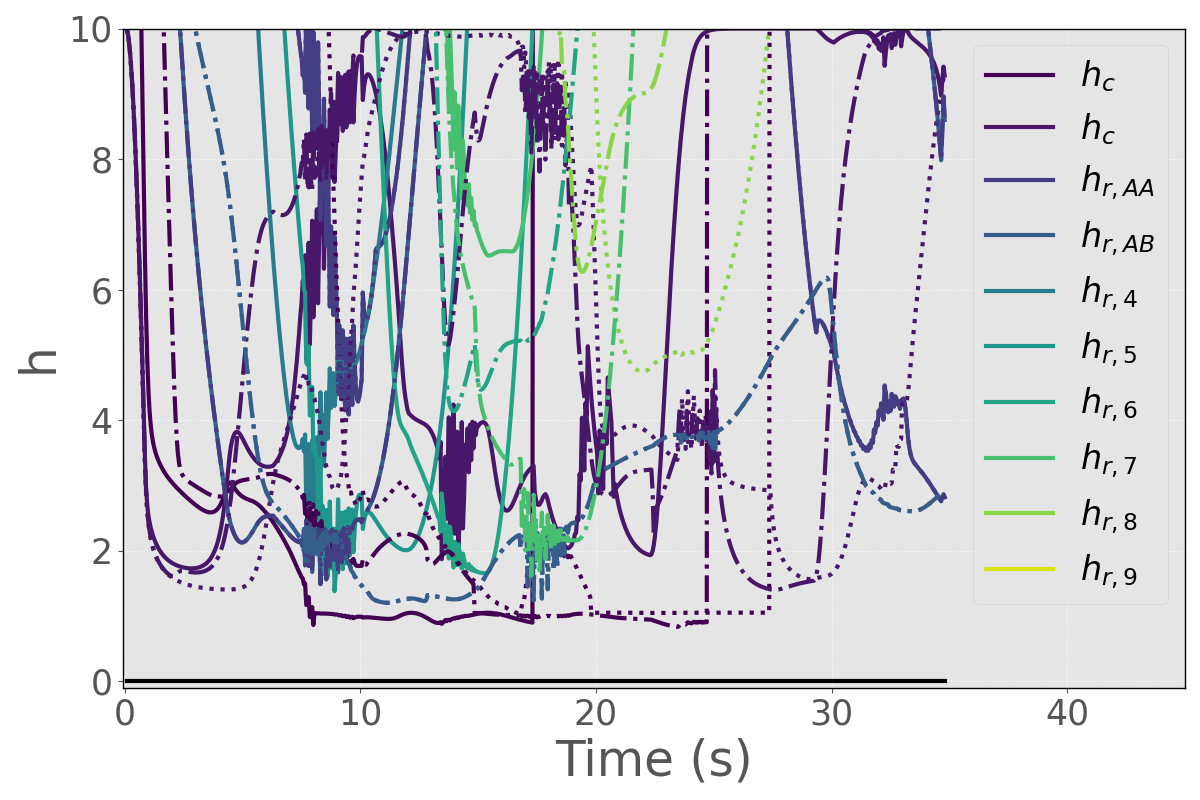
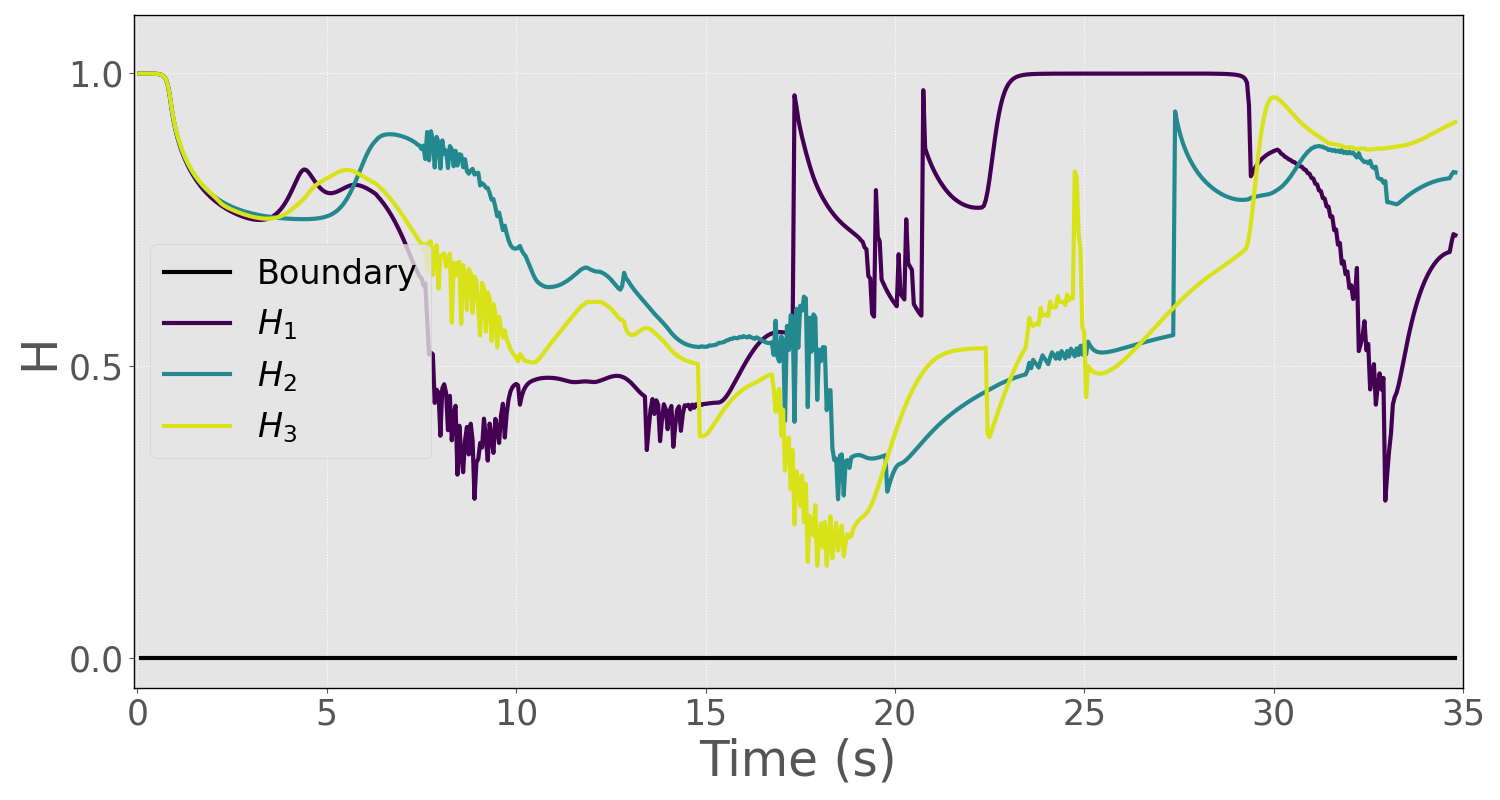
As shown in Figure 2, the non-communicative robots traverse both the narrow corridor and the busy intersection to reach their goal locations safely. The trajectories of the gains for each warehouse robot are shown in Figure 3, while their control inputs are depicted in Figure 4. The CBF time histories for the constituent and consolidated functions are highlighted in Figures 5 and 6 respectively, and show that the C-CBF controllers maintained safety at all times.
V Experimental Case Study
For experimental validation of our approach, we used an AION R1 UGV ground rover as an ego vehicle in the laboratory setting and required it to reach a goal location in the presence of two non-responsive rovers: one static and one dynamic. We modeled the rovers as bicycles using (21), and sent angular rate and velocity (numerically integrated based on the controller’s acceleration output) commands to the rovers’ on-board PID controllers. The ego rover used our proposed C-CBF (20) with constituent candidate CBFs (22) (with m/s) and the rff-CBF defined in (24) for collision avoidance. The nominal input to the C-CBF controller was the LQR law from the warehouse robot example, as was the controller used by the dynamic non-responsive rover. A Vicon motion capture system was used for position feedback, and the state estimation was performed by extended Kalman filter via the on-board PX4.
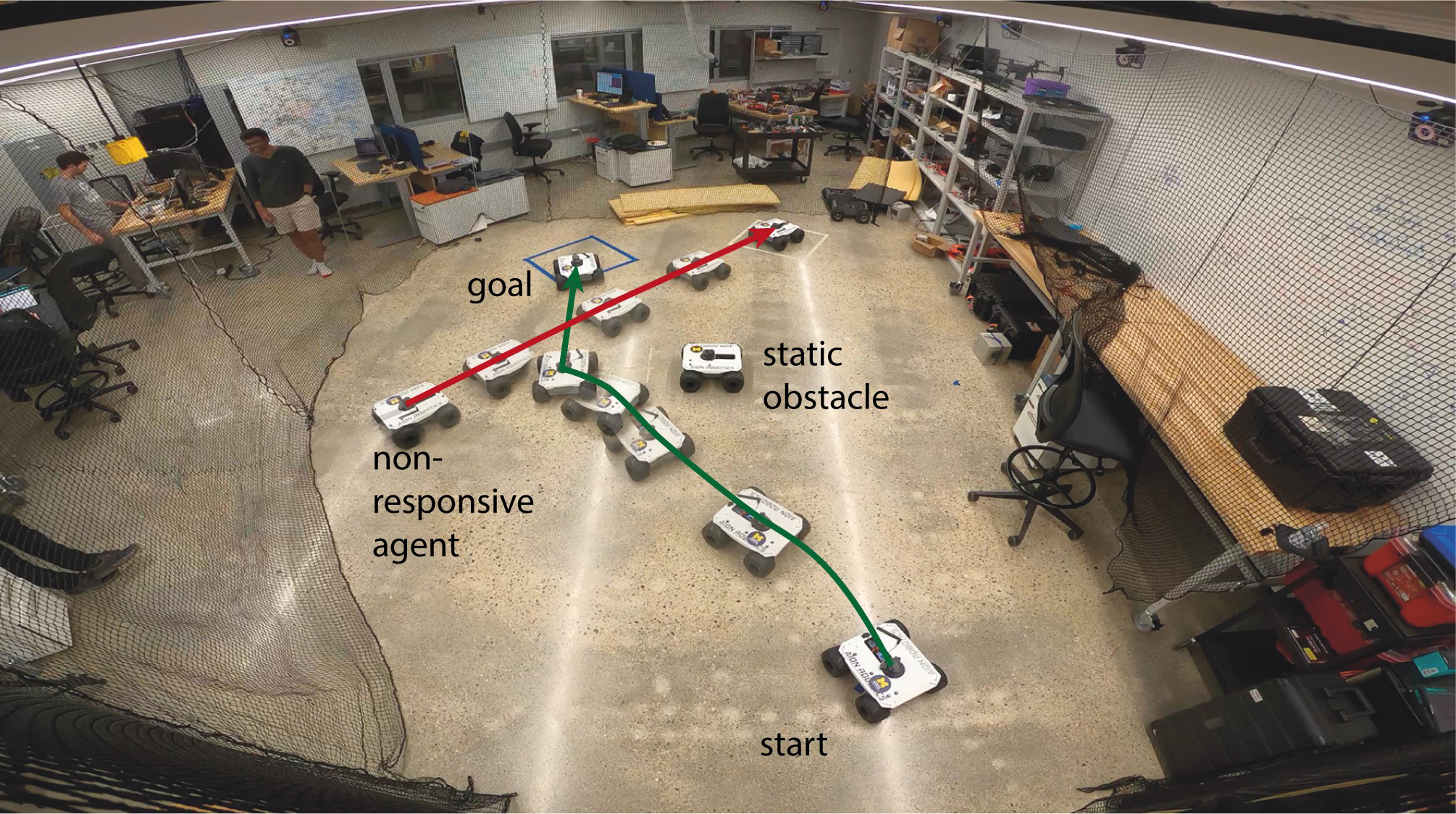
For the setup, the static rover was placed directly between the ego rover and its goal, while the dynamic rover was stationary until suddenly moving across the ego’s path as it approached its target. As highlighted in Figure 7, the ego rover first headed away from the static rover and then decelerated and swerved to avoid a collision with the second rover before correcting course and reaching its goal. Videos and code for both this experiment and the simulation in Section IV is available on Github222Link to Github repo: github.com/6lackmitchell/CCBF-Control.
VI Conclusion
In this paper, we addressed the problem of safe control under multiple state constraints via a C-CBF based control design. To ensure that the synthesized C-CBF is valid, we introduced a parameter adaptation law on the weights of the C-CBF constituent functions and proved that the resulting controller is safe. We then demonstrated the success of our approach on a multi-robot control problem in a crowded warehouse environment, and further validated our work on a ground rover experiment in the lab.
In the future, we plan to explore conditions under which the C-CBF approach may preserve guarantees in the presence of input constraints, including whether alternative adaptation laws for the weights assist in guarantees of liveness in addition to safety.
References
- [1] P. Wieland and F. Allgöwer, “Constructive safety using control barrier functions,” IFAC Proceedings Vols., vol. 40, no. 12, pp. 462–467, 2007.
- [2] A. D. Ames, X. Xu, J. W. Grizzle, and P. Tabuada, “Control barrier function based quadratic programs for safety critical systems,” IEEE Trans. on Automatic Control, vol. 62, no. 8, pp. 3861–3876, 2017.
- [3] W. Xiao and C. Belta, “Control barrier functions for systems with high relative degree,” in IEEE 58th Conference on Decision and Control (CDC), 2019, pp. 474–479.
- [4] W. S. Cortez, D. Oetomo, C. Manzie, and P. Choong, “Control barrier functions for mechanical systems: Theory and application to robotic grasping,” in IEEE Trans. on Control Systems Tech., 2019, pp. 1–16.
- [5] Y. Chen, H. Peng, and J. Grizzle, “Obstacle avoidance for low-speed autonomous vehicles with barrier function,” IEEE Transactions on Control Systems Technology, vol. 26, no. 1, pp. 194–206, 2018.
- [6] K. Garg and D. Panagou, “Robust control barrier and control lyapunov functions with fixed-time convergence guarantees,” in 2021 American Control Conference (ACC), 2021, pp. 2292–2297.
- [7] Y. Chen, A. Singletary, and A. D. Ames, “Guaranteed obstacle avoidance for multi-robot operations with limited actuation: A control barrier function approach,” IEEE Control Systems Letters, vol. 5, no. 1, pp. 127–132, 2021.
- [8] M. Jankovic and M. Santillo, “Collision avoidance and liveness of multi-agent systems with cbf-based controllers,” in 2021 60th IEEE Conference on Decision and Control (CDC), 2021, pp. 6822–6828.
- [9] B. Xu and K. Sreenath, “Safe teleoperation of dynamic uavs through control barrier functions,” in 2018 IEEE International Conference on Robotics and Automation (ICRA), 2018, pp. 7848–7855.
- [10] M. Khan, M. Zafar, and A. Chatterjee, “Barrier functions in cascaded controller: Safe quadrotor control,” in 2020 American Control Conference (ACC), 2020, pp. 1737–1742.
- [11] M. Black, M. Jankovic, A. Sharma, and D. Panagou, “Intersection crossing with future-focused control barrier functions,” arXiv preprint arXiv:2204.00127, 2022.
- [12] S. Yaghoubi, G. Fainekos, T. Yamaguchi, D. Prokhorov, and B. Hoxha, “Risk-bounded control with kalman filtering and stochastic barrier functions,” in 2021 60th IEEE Conference on Decision and Control (CDC), 2021, pp. 5213–5219.
- [13] J. Breeden and D. Panagou, “High relative degree control barrier functions under input constraints,” in 2021 60th IEEE Conference on Decision and Control (CDC), 2021, pp. 6119–6124.
- [14] W. Xiao, C. Belta, and C. G. Cassandras, “Adaptive control barrier functions,” IEEE Transactions on Automatic Control, vol. 67, no. 5, pp. 2267–2281, 2022.
- [15] W. S. Cortez, X. Tan, and D. V. Dimarogonas, “A robust, multiple control barrier function framework for input constrained systems,” IEEE Control Systems Letters, vol. 6, pp. 1742–1747, 2022.
- [16] P. Glotfelter, J. Cortes, and M. Egerstedt, “Nonsmooth barrier functions with applications to multi-robot systems,” IEEE Control Systems Letters, vol. 1, pp. 310–315, 10 2017.
- [17] Y. Huang and Y. Chen, “Switched Control Barrier Function With Applications to Vehicle Safety Control,” ser. Dynamic Systems and Control Conference, vol. 1, 10 2020.
- [18] L. Lindemann and D. V. Dimarogonas, “Control barrier functions for signal temporal logic tasks,” IEEE Control Systems Letters, vol. 3, no. 1, pp. 96–101, 2019.
- [19] M. Machida and M. Ichien, “Consensus-based control barrier function for swarm,” in 2021 IEEE International Conference on Robotics and Automation (ICRA), 2021, pp. 8623–8628.
- [20] M. Black, E. Arabi, and D. Panagou, “Fixed-time parameter adaptation for safe control synthesis,” arXiv preprint arXiv:2204.10453, 2022.
- [21] B. T. Lopez, J.-J. E. Slotine, and J. P. How, “Robust adaptive control barrier functions: An adaptive and data-driven approach to safety,” IEEE Control Systems Letters, vol. 5, no. 3, pp. 1031–1036, 2021.
- [22] A. J. Taylor and A. D. Ames, “Adaptive safety with control barrier functions,” in 2020 American Control Conference (ACC), 2020, pp. 1399–1405.
- [23] T. Gurriet, A. Singletary, J. Reher, L. Ciarletta, E. Feron, and A. Ames, “Towards a framework for realizable safety critical control through active set invariance,” in 9th ACM/IEEE International Conference on Cyber-Physical Systems (ICCPS), 2018, pp. 98–106.
- [24] S. Kolathaya and A. D. Ames, “Input-to-state safety with control barrier functions,” IEEE Control Systems Letters, vol. 3, no. 1, pp. 108–113, 2019.
- [25] F. Blanchini, “Set invariance in control,” Automatica, vol. 35, no. 11, pp. 1747–1767, 1999.
- [26] M. Jankovic, M. Santillo, and Y. Wang, “Multi-agent systems with cbf-based controllers – collision avoidance and liveness from instability,” arXiv preprint arXiv:2207.04915, 2022.
- [27] U. Borrmann, L. Wang, A. D. Ames, and M. Egerstedt, “Control barrier certificates for safe swarm behavior,” IFAC-PapersOnLine, vol. 48, no. 27, pp. 68–73, 2015.
- [28] L. Wang, A. D. Ames, and M. Egerstedt, “Safety barrier certificates for collisions-free multirobot systems,” vol. 33, no. 3. IEEE, 2017, pp. 661–674.
- [29] H. Parwana and D. Panagou, “Trust-based rate-tunable control barrier functions for non-cooperative multi-agent systems,” arXiv preprint arXiv:2204.04555, 2022.
- [30] T. F. Coleman and D. C. Sorensen, “A note on the computation of an orthonormal basis for the null space of a matrix,” Mathematical Programming, vol. 29, pp. 234–242, 6 1984.
- [31] R. Rajamani, Vehicle Dynamics and Control. Springer US, 2012.