An Improved Square-root Algorithm for V-BLAST Based on Efficient Inverse Cholesky Factorization
Abstract
A fast algorithm for inverse Cholesky factorization is proposed, to compute a triangular square-root of the estimation error covariance matrix for Vertical Bell Laboratories Layered Space-Time architecture (V-BLAST). It is then applied to propose an improved square-root algorithm for V-BLAST, which speedups several steps in the previous one, and can offer further computational savings in MIMO Orthogonal Frequency Division Multiplexing (OFDM) systems. Compared to the conventional inverse Cholesky factorization, the proposed one avoids the back substitution (of the Cholesky factor), and then requires only half divisions. The proposed V-BLAST algorithm is faster than the existing efficient V-BLAST algorithms. The expected speedups of the proposed square-root V-BLAST algorithm over the previous one and the fastest known recursive V-BLAST algorithm are and , respectively.
Index Terms:
MIMO, V-BLAST, square-root, fast algorithm, inverse Cholesky factorization.I Introduction
Multiple-input multiple-output (MIMO) wireless communication systems can achieve huge channel capacities [1] in rich multi-path environments through exploiting the extra spatial dimension. Bell Labs Layered Space-Time architecture (BLAST) [2], including the relative simple vertical BLAST (V-BLAST) [3], is such a system that maximizes the data rate by transmitting independent data streams simultaneously from multiple antennas. V-BLAST often adopts the ordered successive interference cancellation (OSIC) detector [3], which detects the data streams iteratively with the optimal ordering. In each iteration, the data stream with the highest signal-to-noise ratio (SNR) among all undetected data streams is detected through a zero-forcing (ZF) or minimum mean-square error (MMSE) filter. Then the effect of the detected data stream is subtracted from the received signal vector.
Some fast algorithms have been proposed [4, 5, 6, 7, 10, 11, 8, 9] to reduce the computational complexity of the OSIC V-BLAST detector [3]. An efficient square-root algorithm was proposed in [4] and then improved in [5], which also partially inspired the modified decorrelating decision-feedback algorithm [6]. In additon, a fast recursive algorithm was proposed in [7] and then improved in [8, 9, 10, 11]. The improved recursive algorithm in [8] requires less multiplications and more additions than the original recursive algorithm [7]. In [9], the author gave the “fastest known algorithm” by incorporating improvements proposed in [10, 11] for different parts of the original recursive algorithm [7], and then proposed a further improvement for the “fastest known algorithm”.
On the other hand, most future cellular wireless standards are based on MIMO Orthogonal Frequency Division Multiplexing (OFDM) systems, where the OSIC V-BLAST detectors [3, 4, 5, 6, 7, 10, 11, 8, 9] require an excessive complexity to update the detection ordering and the nulling vectors for each subcarrier. Then simplified V-BLAST detectors with some performance degradation are proposed in [12, 13], which update the detection [12] or the detection ordering [13] per group of subcarriers to reduce the required complexity.
In this letter, a fast algorithm for inverse Cholesky factorization [14] is deduced to compute a triangular square-root of the estimation error covariance matrix for V-BLAST. Then it is employed to propose an improved square-root V-BLAST algorithm, which speedups several steps in the previous square-root V-BLAST algorithm [5], and can offer further computational savings in MIMO OFDM systems.
This letter is organized as follows. Section \@slowromancapii@ describes the V-BLAST system model. Section \@slowromancapiii@ introduces the previous square-root algorithm [5] for V-BLAST. In Section \@slowromancapiv@, we deduce a fast algorithm for inverse Cholesky factorization. Then in Section \@slowromancapv@, we employ it to propose an improved square-root algorithm for V-BLAST. Section \@slowromancapvi@ evaluates the complexities of the presented V-BLAST algorithms. Finally, we make conclusion in Section \@slowromancapvii@.
In the following sections, , and denote matrix transposition, matrix conjugate, and matrix conjugate transposition, respectively. is the zero column vector, while is the identity matrix of size .
II System Model
The considered V-BLAST system consists of transmit antennas and receive antennas in a rich-scattering and flat-fading wireless channel. The signal vector transmitted from antennas is with the covariance . Then the received signal vector
| (1) |
where is the complex Gaussian noise vector with the zero mean and the covariance , and
is the complex channel matrix. Vectors and represent the column and the row of , respectively.
Define . The linear MMSE estimate of is
| (2) |
As in [4, 5, 7, 10, 11, 8, 9], we focus on the MMSE OSIC detector, which usually outperforms the ZF OSIC detector [7]. Let
| (3) |
Then the estimation error covariance matrix [4]
| (4) |
The OSIC detection detects entries of the transmit vector iteratively with the optimal ordering. In each iteration, the entry with the highest SNR among all the undetected entries is detected by a linear filter, and then its interference is cancelled from the received signal vector [3]. Suppose that the entries of are permuted such that the detected entry is , the entry. Then its interference is cancelled by
| (5) |
where is treated as the correctly detected entry, and the initial . Then the reduced-order problem is
| (6) |
where the deflated channel matrix , and the reduced transmit vector . Correspondingly we can deduce the linear MMSE estimate of from (6). The detection will proceed iteratively until all entries are detected.
III The Square-Root V-BLAST Algorithms
The square-root V-BLAST algorithms [4],[5] calculate the MMSE nulling vectors from the matrix that satisfies
| (7) |
Correspondingly is a square-root matrix of . Let
| (8) |
denote the first columns of . From , we define the corresponding , and by (3), (4) and (7), respectively. Then the previous square-root V-BLAST algorithm in [5] can be summarized as follows.
The Previous Square-Root V-BLAST Algorithm
Initialization:
-
P1)
Let . Compute an initial : Set . Compute and iteratively for , where “” denotes irrelevant entries at this time, and is any unitary transformation that block lower-triangularizes the pre-array . Finally .
Iterative Detection:
-
P2)
Find the minimum length row of and permute it to the last row. Permute and accordingly.
-
P3)
Block upper-triangularize by
(9) where is a unitary transformation, is an column vector, and is a scalar.
-
P4)
Form the linear MMSE estimate of , i.e.,
(10) -
P5)
Obtain from via slicing.
- P6)
-
P7)
If , let and go back to step P2.
IV A Fast Algorithm for Inverse Cholesky Factorization
The previous square-root algorithm [5] requires extremely high computational load to compute the initial in step P1. So we propose a fast algorithm to compute an initial that is upper triangular.
If satisfies (7), any also satisfies (7). Then there must be a square-root of in the form of
| (11) |
as can be seen from (9). We apply (11) to compute from , while the similar equation (9) is only employed to compute from in [4] and [5].
From (11), we obtain
| (12) |
On the other hand, it can be seen that defined from by (3) is the leading principal submatrix of [7]. Then we have
| (13) |
Now let us substitute (13) and (12) into
| (14) |
which is deduced from (7) and (4). Then we obtain
| (15) |
where “” denotes irrelevant entries. From (15), we deduce
| (16a) | |||||
| (16b) |
From (16b), finally we can derive
| (17a) | |||||
| (17b) |
We derive (17b) from (16a). Then (17b) is substituted into (16b) to derive
| (18) |
We can use (17b) and (11) to compute from iteratively till we get . The iterations start from satisfying (14), which can be computed by
| (19) |
Correspondingly instead of step P1, we can propose step N1 to compute an initial upper-triangular , which includes the following sub-steps.
The Sub-steps of Step N1
-
N1-a)
Assume the successive detection order to be . Correspondingly permute to be , and permute to be .
- N1-b)
- N1-c)
The obtained upper triangular is equivalent to a Cholesky factor [14] of , since and can be permuted to the lower triangular and the corresponding , which still satisfy (7). Notice that the with columns exchanged still satisfies (7), while if two rows in are exchanged, the corresponding two rows and columns in need to be exchanged.
Now from (13), (7) and (4), it can be seen that (9) (proposed in [4]) and (11) actually reveal the relation between the and the order inverse Cholesky factor of the matrix . This relation is also utilized to implement adaptive filters in [15, 16], where the order inverse Cholesky factor is obtained from the order Cholesky factor [15, equation (12)], [16, equation (16)]. Thus the algorithms in [15, 16] are still similar to the conventional matrix inversion algorithm [17] using Cholesky factorization, where the inverse Cholesky factor is computed from the Cholesky factor by the back-substitution (for triangular matrix inversion), an inherent serial process unsuitable for the parallel implementation [18]. Contrarily, the proposed algorithm computes the inverse Cholesky factor of from directly, as shown in (17b) and (11). Then it can avoid the conventional back substitution of the Cholesky factor.
In a word, although the relation between the and the order inverse Cholesky factor (i.e. (9) and (11)) has been mentioned [4, 15, 16], our contributions in this letter include substituting this relation into (14) to find (18) and (17b). Specifically, to compute the order inverse Cholesky factor, the conventional matrix inversion algorithm using Cholesky factorization [17] usually requires divisions (i.e. divisions for Cholesky factorization and the other divisions for the back-substitution), while the proposed algorithm only requires divisions to compute (19) and (17a).
V The Proposed Square-root V-BLAST Algorithm
Now has been computed in sub-step N1-b. Thus as the recursive V-BLAST algorithm in [11], we can also cancel the interference of the detected signal in
| (20) |
by
| (21) |
where is the permuted with the last entry removed, and is in the permuted [11, 9], as shown in (13). Then to avoid computing in (10), we form the estimate of by
| (22) |
It is required to compute the initial . So step N1 should include the following sub-step N1-d.
-
N1-d)
Compute .
The proposed square-root V-BLAST algorithm is summarized as follows.
The Proposed Square-root V-BLAST Algorithm
Initialization:
-
N1)
Set . Compute , and the initial upper triangular . This step includes the above-described sub-steps N1-a, N1-b, N1-c and N1-d.
Iterative Detection:
Since obtained in step N1 is upper triangular, step N3 requires less computational load than the corresponding step P3 (described in Section \@slowromancapiii@), which is analyzed as follows.
Suppose that the minimum length row of found in step N2 is the row, which must be
with the first entries to be zeros. Thus in step N3 the transformation can be performed by only Givens rotations [14], i.e.,
| (23) |
where the Givens rotation rotates the and entries in each row of , and zeroes the entry in the row.
In step N2, we can delete the row in firstly to get , and then add the deleted row to as the last row to obtain the permuted . Now it is easy to verify that the obtained from by (9) is still upper triangular. For the subsequent , we also obtain from by (9), where is defined by (23) with . Correspondingly we can deduce that is also triangular. Thus is always triangular, for .
To sum up, our contributions in this letter include steps N1, N3, N4 and N6 that improve steps P1, P3, P4 and P6 (of the previous square-root V-BLAST algorithm [5]), respectively. Steps N4 and N6 come from the extension of the improvement in [11] (for the recursive V-BLAST algorithm) to the square-root V-BLAST algorithm. However, it is infeasible to extend the improvement in [11] to the existing square-root V-BLAST algorithms in [4, 5], since they do not provide that is required to get for (21).
VI Complexity Evaluation
In this section, (, ) denotes the computational complexity of complex multiplications and complex additions, which is simplified to () if . Similarly, denotes that the speedups in the number of multiplications, additions and floating-point operations (flops) are , and , respectively, which is simplified to if . Table \@slowromancapi@ compares the expected complexity of the proposed square-root V-BLAST algorithm and that of the previous one in [5]. The detailed complexity derivation is as follows.
In sub-step N1-c, the dominant computations come from (17b). It needs a complexity of to compute firstly, where is triangular. Then to obtain the column of , we compute (17b) by
| (24a) | |||||
| (24b) |
In (24b), the complexity to compute is , and that to compute the other parts is . So sub-step N1-c totally requires a complexity of to compute (17b) for iterations, while sub-step N1-b requires a complexity of () [7] to compute the Hermitian . As a comparison, in each of the iterations, step P1 computes to form the pre-array , and then block lower-triangularizes by the Householder transformation [5]. Thus it can be seen that step P1 requires much more complexity than the proposed step N1.
In steps N3 and P3, we can apply the efficient complex Givens rotation [19] to rotate into , where and are real, and is complex. The efficient Givens rotation equivalently requires [7] complex multiplications and complex additions to rotate a row. Correspondingly the complexity of step P3 is . Moreover, step P3 can also adopt a Householder reflection, and then requires a complexity of [5]. On the other hand, the Givens rotation in (23) only rotates non-zero entries in the first rows of the upper-triangular . Then (23) requires a complexity of . When the detection order assumed in sub-step N1-a is statistically independent of the optimal detection order, the probabilities for are equal. Correspondingly the expected (or average) complexity of step N3 is . Moreover, when the probability for is 100%, step N3 needs the worst-case complexity, which is . Correspondingly we can deduce that the worst-case complexity of the proposed V-BLAST algorithm is . The ratio between the worst-case and expected flops of the proposed square-root algorithm is only , while recently there is a trend to study the expected, rather than worst-case, complexity of various algorithms [20]. Thus only the expected complexity is considered in Table \@slowromancapi@ and in what follows.
In MIMO OFDM systems, the complexity of step N3 can be further reduced, and can even be zero. In sub-step N1-a, we assume the detection order to be the optimal order of the adjacent subcarrier, which is quite similar or even identical to the actual optimal detection order [13]. Correspondingly the required Givens rotations are less or even zero. So the expected complexity of step N3 ranges from to zero, while the exact mean value depends on the statistical correlation between the assumed detection order and the actual optimal detection order.
The complexities of the ZF-OSIC V-BLAST algorithm in [6] and the MMSE-OSIC V-BLAST algorithms in [4, 7, 8, 9] are , [5], , and , respectively. Let . Also assume the transformation in [5] to be a sequence of efficient Givens rotations [19] that are hardware-friendly [4]. Then the expected speedups of the proposed square-root algorithm over the previous one [5] range from to , while the expected speedups of the proposed algorithm over the fastest known recursive algorithm [9] range from to .
For more fair comparison, we modify the fastest known recursive algorithm [9] to further reduce the complexity. We spend extra memories to store each intermediate () computed in the initialization phase, which may be equal to the required in the recursion phase [9]. Assume the successive detection order and permute accordingly, as in sub-step N1-a. When the assumed order is identical to the actual optimal detection order, each required in the recursion phase is equal to the stored . Thus we can achieve the maximum complexity savings, i.e. the complexity of [9, equations (23) and (24)] to deflate s. On the other hand, when the assumed order is statistically independent of the actual optimal detection order, there is an equal probability for the undetected antennas to be any of the possible antenna combinations. Correspondingly is the probability for the stored to be equal to the required in the recursion phase. Thus we can obtain the minimum expected complexity savings, i.e. [9, equations (23) and (24)],
| (25) |
The ratio of the minimum expected complexity savings to the maximum complexity savings is 22% when , and is only 1.2% when . It can be seen that the minimum expected complexity savings are negligible when is large. The minimum complexity of the recursive V-BLAST algorithm [9] with the above-described modification, which is , is still more than that of the proposed square-root V-BLAST algorithm. When , the ratio of the former to the latter is .
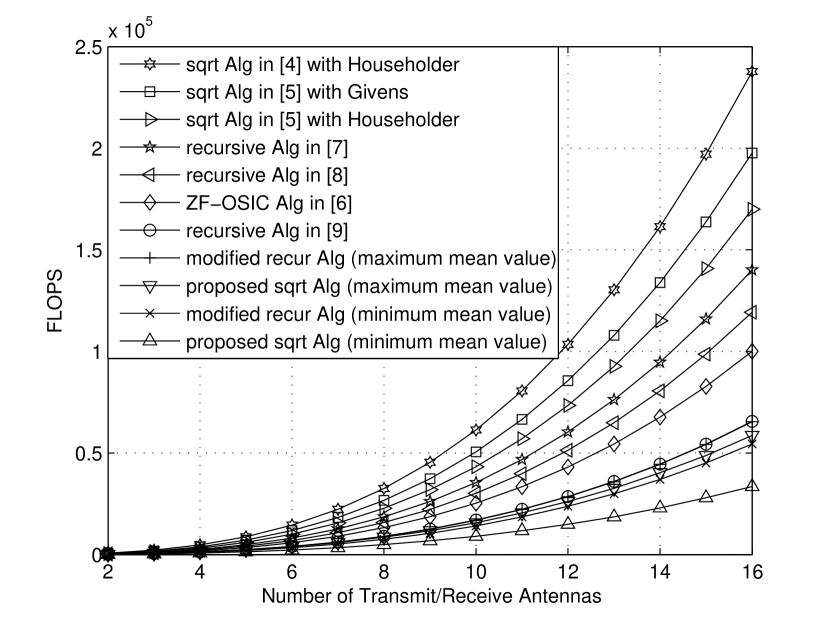
Assume . For different number of transmit/receive antennas, we carried out some numerical experiments to count the average flops of the OSIC V-BLAST algorithms in [4, 7, 8, 9, 6, 5], the proposed square-root V-BLAST algorithm, and the recursive V-BLAST algorithm [9] with the above-described modification. The results are shown in Fig. 1. It can be seen that they are consistent with the theoretical flops calculation.
VII Conclusion
We propose a fast algorithm for inverse Cholesky factorization, to compute a triangular square-root of the estimation error covariance matrix for V-BLAST. Then it is employed to propose an improved square-root algorithm for V-BLAST, which speedups several steps in the previous one [5], and can offer further computational savings in MIMO OFDM systems. Compared to the conventional inverse Cholesky factorization, the proposed one avoids the back substitution (of the Cholesky factor), an inherent serial process unsuitable for the parallel implementation [18], and then requires only half divisions. The proposed V-BLAST algorithm is faster than the existing efficient V-BLAST algorithms in [4, 5, 6, 7, 10, 11, 8, 9]. Assume transmitters and the equal number of receivers. In MIMO OFDM systems, the expected speedups (in the number of flops) of the proposed square-root V-BLAST algorithm over the previous one [5] and the fastest known recursive V-BLAST algorithm [9] are and , respectively. The recursive algorithm [9] can be modified to further reduce the complexity at the price of extra memory consumption, while the minimum expected complexity savings are negligible when is large. The speedups of the proposed square-root algorithm over the fastest known recursive algorithm [9] with the above-mentioned modification are , when both algorithms are assumed to achieve the maximum complexity savings. Furthermore, as shown in [21], the proposed square-root algorithm can also be applied in the extended V-BLAST with selective per-antenna rate control (S-PARC), to reduce the complexity even by a factor of .
References
- [1] G. J. Foschini and M. J. Gans, “On limits of wireless communications in a fading environment when using multiple antennas,” Wireless Personal Commun., pp. 311-335, Mar. 1998.
- [2] G. J. Foschini, “Layered space-time architecture for wireless communication in a fading environment using multi-element antennas,” Bell Labs. Tech. J.,, vol. 1, no. 2, pp. 41 C59, 1996.
- [3] P. W. Wolniansky, G. J. Foschini, G. D. Golden and R. A. Valenzuela, “V-BLAST: an architecture for realizing very high data rates over the rich-scattering wireless channel”, Proc. Int. Symp. Signals, Syst., Electron. (ISSSE 98), pp. 295-300, Sept. 1998.
- [4] B. Hassibi, “An efficient square-root algorithm for BLAST”, Proc. IEEE Int. Conf. Acoustics, Speech, and Signal Processing, (ICASSP ’00), pp. 737-740, June 2000.
- [5] H. Zhu, Z. Lei and F. P. S. Chin, “An improved square-root algorithm for BLAST”, IEEE Signal Processing Letters, vol. 11, no. 9, pp. 772-775, Sept. 2004.
- [6] W. Zha and S. D. Blostein, “Modified decorrelating decision-feedback detection of BLAST space-time system”, Proc. IEEE ICC, vol. 4, pp. 59-63, 2002.
- [7] J. Benesty, Y. Huang and J. Chen, “A fast recursive algorithm for optimum sequential signal detection in a BLAST system”, IEEE Trans. on Signal Processing, pp. 1722-1730, July 2003.
- [8] Z. Luo, S. Liu, M. Zhao and Y. Liu, “A Novel Fast Recursive MMSE-SIC Detection Algorithm for V-BLAST Systems”, IEEE Transactions on Wireless Communications, vol. 6, Issue 6, pp. 2022 - 2025, June 2007.
- [9] Y. Shang and X. G. Xia, “On Fast Recursive Algorithms For V-BLAST With Optimal Ordered SIC Detection”, IEEE Transactions on Wireless Communications, vol. 8, pp. 2860-2865, June 2009.
- [10] L. Szczeci nski, and D. Massicotte, “Low complexity adaptation of MIMO MMSE receivers, Implementation aspects”, Proc. IEEE Global Commun. Conf. (Globecom 05), St. Louis, MO, USA, Nov. 28 - Dec. 2, 2005.
- [11] H. Zhu, Z. Lei, and F. P. S. Chin, “An improved recursive algorithm for BLAST”, Signal Process., vol. 87, no. 6, pp. 1408-1411, Jun. 2007.
- [12] N. Boubaker, K.B. Letaief and R.D. Murch, “A low complexity multicarrier BLAST architecture for realizing high data rates over dispersive fading channels,” IEEE Vehicular Technology Conference (VTC), 2001 Spring, May 2001.
- [13] W. Yan, S. Sun and Z. Lei, “A low complexity VBLAST OFDM detection algorithm for wireless LAN systems”, IEEE Communications Letters, vol. 8, no. 6, pp. 374-376, June 2004.
- [14] G. H. Golub and C. F. Van Loan, Matrix Computations, Johns Hopkins University Press, Baltimore, MD, 3rd edition, 1996.
- [15] A. A. Rontogiannis and S. Theodoridis, “New fast QR decomposition least squares adaptive algorithms”, IEEE Trans. on Signal Processing, vol. 46, no. 8, pp. 2113-2121, Aug. 1998.
- [16] A. A. Rontogiannis, V. Kekatos and K. Berberidis, “A square-root adaptive V-BLAST algorithm for fast time-varying MIMO channels”, IEEE Signal Processing Letters, vol. 13, no. 5, pp. 265-268, May 2006.
- [17] A. Burian, J. Takala and M. Ylinen, “A fixed-point implementation of matrix inversion using Cholesky decomposition”, Micro-NanoMechatronics and Human Science, 2003 IEEE International Symposium on, 27-30 Dec. 2003, vol. 3, pp. 1431-1434.
- [18] E. J. Baranoski, “Triangular factorization of inverse data covariance matrices”, International Conference on Acoustics, Speech, and Signal Processing, 1991 (ICASSP-91), 14-17 Apr 1991, pp. 2245 - 2247, vol.3.
- [19] D. Bindel, J. Demmel, W. Kahan and O. Marques, “On Computing Givens rotations reliably and efficiently”, ACM Transactions on Mathematical Software (TOMS) archive, vol. 28 , Issue 2, June 2002. Available online at: www.netlib.org/lapack/lawns/downloads/.
- [20] B. Hassibi and H. Vikalo, “On the sphere decoding algorithm: Part I, the expected complexity”, IEEE Transactions on Signal Processing, vol 53, no 8, pages 2806-2818, Aug. 2005.
- [21] H. Zhu, W. Chen and B. Li, “Efficient Square-root Algorithms for the Extended V-BLAST with Selective Per-Antenna Rate Control”, IEEE Vehicular Technology Conference (VTC), 2010 Spring, May 2010.
| Step | The Algorithm in [5] | The Proposed Algorithm |
| 1-b | () [5] for step P1 | ()[7] |
| 1-c | () | |
| 3 | () or () [5] | From () to () |
| 4 | () [5] | |
| Sum | ( | From |
| ) | ||
| or () | to () |