Analysis of Vehicular Safety Messaging in Cellular Networks
Abstract
This paper concerns the performance of vehicle-to-everything (V2X) communications. More precisely, we analyze the broadcast of safety-related V2X communications in cellular networks where base stations and vehicles are assumed to share the same spectrum and vehicles broadcast their safety messages to neighboring users. We model the locations of vehicles as a Poisson line Cox point process and the locations of users as a planar Poisson point process. We assume that users are associated with their closest base stations when there is no vehicle within a certain distance . On the other hand, users located within a distance from vehicles are associated with the vehicles to receive their safety messages. We quantify the properties of this vehicle-prioritized association using the stochastic geometry framework. We derive the fractions of users that receive safety messages from vehicles. Then, we obtain the expression for the signal-to-interference ratio of the typical user evaluated on each association type. To address the impact of vehicular broadcast on the cellular network, the paper also derives the effective rate offered to the typical user in this setting.
Index Terms:
Vehicle-to-Everything (V2X), Vehicular broadcast, Vehicular safety messaging, Network modeling, Poisson line process, Cox point process, Boolean model, Signal-to-interference ratio, effective data rate, Volume fractionI Introduction
I-A Motivation and Related Work
Device-to-device (D2D) technology has been used in various applications including file transfer [1], emergency service [2], and intelligent transportation systems (ITS)[3]. In the context of cellular 5G NR vehicle-to-all (V2X) applications [4], vehicle or pedestrian user equipment (UE) is enabled to transmit and receive data to/from nearby vehicular or roadside unit (RSU) UE using direct sidelink communications in the presence of existing cellular uplink or downlink [5, 6]. The messages transmitted through sidelink communications include basic safety information as well as traffic information [7]. In safety applications, it is essential for other vehicular or pedestrians UEs within a certain distance to be able to decode the data transmitted through sidelink even when this type of communications coexist with the existing cellular infrastructure [3, 5, 6, 8, 4]. This paper analyzes the performance of sidelinks and cellular communications when sidelinks are prioritized over cellular for users close to vehicles.
The representation of the locations of D2D transceivers based on planar Poisson point processes has been widely used in the literature (See [9, 10, 11, 12, 13] and references therein). The typical user performance was analytically derived in [14]. Moreover, various network protocols and techniques such as power control [15, 16], multi-input-multi-output [17, 18], and access control [19] were investigated in this context. The planar Poisson point process is tractable because its points are spatially independent [20, 21]. In networks with vehicles, on the other hand, vehicles exhibit a linear co-location and their motions are constrained by road layouts. The Poisson point process, however, is unable to capture such spatial constraints [21]. As an alternative, Poisson-line Cox point processes were used to model vehicles on roads [22, 23, 24, 25, 26, 27]. In Cox-based vehicle models, road networks are first modeled by a stationary Poisson line process and, conditionally on lines, vehicles are modeled by Poisson point processes on the lines. These models inherently capture the relationship between vehicles and their corresponding road structure.
In particular, the Cox-based model is useful to the analysis of V2X networks when vehicular networks coexist with cellular networks [8, 4]. In [23, 24, 28, 27], the V2X network was represented by two distinct spatial architectures; the cellular network is modeled by a planar Poisson point process and the vehicle network is modeled by an independent Poisson-line Cox point process . The distributions of signal-to-interference-plus-noise ratio (SINR) of typical links were analyzed in these papers. Particularly, [24] derived the SINR distributions of all existing typical pairs in such networks: links from vehicle base stations to vehicle users, from vehicle base stations to planar users, from planar base stations to planar users, and from planar base stations to vehicle users. In [24], users are assumed to be associated with their nearest transmitters to increase the data rate or coverage area [29, 11].
In safety applications, each vehicle broadcasts its basic safety information such as its location, speed, and acceleration to nearby pedestrians or vehicles. Specifically, if pedestrians or cellular user are within a certain distance from a vehicular UE, they are required to decode the messages from vehicles [3, 8, 4, 5, 6, 7, 30]. For instance, when ITS with vehicular safety messaging is deployed with a cellular architecture, the users are prioritized to be associated with vehicles over cellular base stations as long as they are close to vehicles. The aim of this paper is to evaluate the reliability of the communications from vehicles to users as well as the effective rate of downlink from cellular base stations to users. To the best of our knowledge, the interplay between sidelink broadcast and downlink unicast has not been investigated within the stochastic geometry framework.
I-B Contributions
Modeling of vehicular broadcast in cellular networks: We model the locations of base stations as a planar Poisson point process of intensity , and the location of cellular downlink users as an independent planar Poisson point process of intensity . To represent the linear patterns of vehicles on roads, we use an isotropic Poisson line process to model the road layout and then use Poisson point processes conditionally on the line process to model the locations of vehicles. We assume that control messages from vehicles have users decode vehicular safety messages when the users are within a distance from vehicles. Fig. 1 illustrates such vehicle-prioritized association region.
Derivation of network performance from a typical user perspective: The stationary framework of the proposed model allows us to derive the network performance of a typical user, which corresponds to the network performance spatially averaged over all users in the network. Specifically, we consider a V2X system where the typical user association is determined by the locations of vehicles and base stations with respect to the typical user. Using the mean area fraction of the Boolean model—which quantifies the relative size of the vehicular broadcast region in the Euclidean plane—we derive the probability that a typical user at the origin is prioritized to receive the vehicular broadcast message or is associated with a cellular base station for downlink communications, respectively. Conditional on the association of the typical user, we derive its signal-to-interference (SIR) distribution in terms of an integral formula. The impact of vehicular broadcasts on cellular unicasts is characterized as the effective data rate of cellular links, which accounts for the long-term average rate that the cellular users are offered through downlink unicast, assuming that each downlink base station is equally shared by all of its associated users. For this, we derive a formula for the mean number of users associated with each base station, by quantifying the area of the vehicle association region inside a Voronoi cell of the base station point process.
II System Model
This section discusses the spatial model, the vehicle-prioritized association principle, the propagation model, and the network performance metrics.
II-A Spatial Model
We model the random locations of cellular users, namely UEs in cellular networks, as a planar Poisson point process with intensity . The base stations of the cellular networks are modeled by an independent planar Poisson point process with intensity The locations of users and base stations are fixed (do not change overtime). In addition, we assume the density of users is high, i.e., and also assume that there is at least one active downlink user in each base station cell.
We model the locations of vehicles as a Cox point process [25] based on a Poisson line process. Roads are modeled by a stationary and isotropic Poisson line process . This line process is given by a Poisson point process on the cylinder with intensity [21]. Specifically, a point of the cylinder Poisson point process, say produces an undirected line on the Euclidean plane . Here, corresponds to the algebraic displacement from the origin to the line and corresponds to the angle between the line and the positive -axis in the counterclockwise direction. Conditionally on the line point process, vehicles are modeled by an independent one-dimensional Poisson point process, say with intensity on each line. Consequently, the proposed vehicle point process is stationary and the spatial density of vehicles per unit area is [25]. As shown in the literature including [25], the Cox-based vehicle point process captures the relationship between vehicles and corresponding road layouts.
This paper assumes that vehicles move at a constant speed along the lines on which they are located. For simplicity, we assume that the vehicles’ moving directions are independently chosen with probability half. Once vehicles’ moving directions are chosen at time , they are maintained forever. In the remainder of this paper, the vehicle point process at time is denoted by
II-B Channel Model
Let denote the distance between a transmitter and its designated receiver, or receivers (for broadcast). In this paper, we assume a rich scattering around cellular users such that the received signal power is characterized by the product of a distance-based path loss and a small-scale Rayleigh fading [31, 32].
Time is assumed to be slotted. For each time slot, the received signal power is given by where is the transmit power of the transmitter, is an exponential random variable with mean one, and is the path loss exponent assumed to be greater than two. The transmit powers of base stations and vehicles are denoted by and respectively.
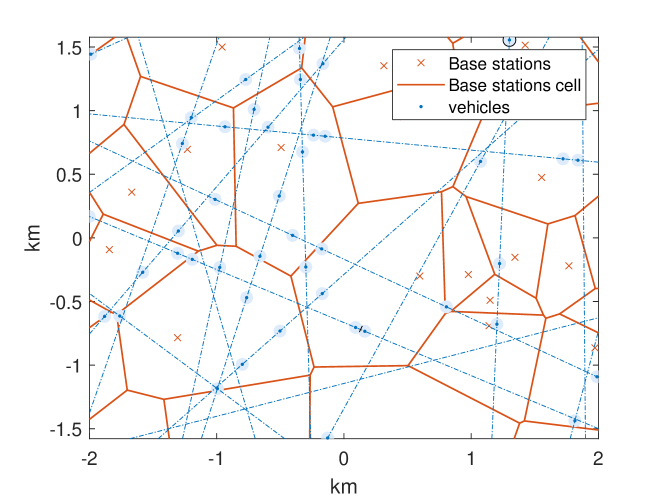
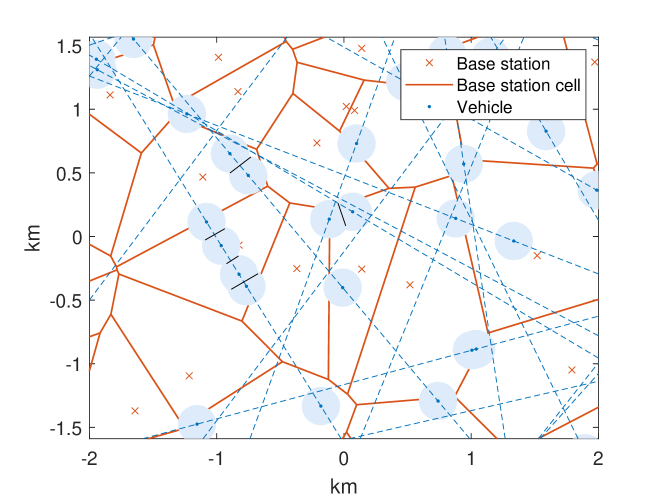
II-C Vehicle Priotizied Association Principle
Note that in ITS, it is essential for cellular users to be able to decode sidelink messages if there is a vehicle within some distance [7]. Thus, in this paper, we define the user association as follows: each user is associated with its nearest base station. However, if a cellular user is within some distance from a vehicle, that user is associated with the corresponding vehicle. If there are two such vehicles, the user is associated with the closest one.
Remark 1.
In practice, vehicle-prioritized association can be implemented using sidelink control messages. For instance, vehicles broadcast messages are preceded by vehicle control messages. Any user who receives a sidelink control message from a vehicle is required to try to decode the safety messages from the corresponding vehicle. In this context, the radius of the disk specifies the maximum distance to the users who try to decode the safety message.
Figs. 1 and 2 represent the association regions in the Euclidean plane. The vehicle association region is illustrated as the union of disks centered at vehicles. Users within this region are associated with their corresponding vehicles. The vehicle association region is given by
| (1) |
where denotes the disk of radius centered at . On the other hand, the cellular association region is given by
| (2) |
Remark 2.
In this paper, downlink and sidelink transmissions are assumed to differ in the way they deliver their messages. Specifically, downlink transmissions from base stations to cellular users are assumed to be unicasts; each base station selects one of its associated users at each time slot and serves it. On the other hand, sidelink transmissions from vehicles to users are assumed to be broadcasts; in other words, each vehicle broadcasts its message to nearby users and all of its users attempt to decode the message.
| Notation and distribution | Description |
|---|---|
| Poisson | User point process |
| Poisson | Cellular base stations |
| Vehicles | |
| Boolean on | Area assoc. w/ vehicles |
| Area assoc. w/ base stations | |
| Users assoc. w/ vehicles | |
| Users assoc. w/ base station | |
| Users served by vehicles at time t | |
| Unif. on at | Users served by base stations at time t |
II-D Preliminary: Typical Cell and Zero Cell
The Voronoi tessellation w.r.t. is the sequence of random sets as follows:
| (3) |
The points are the nuclei of the Voronoi cells. Based on the association principle in Section II-C, the cellular association region is the Voronoi tessellation w.r.t. the base station point process minus vehicle association region. This is described as non-shared areas in figs. 1 and 2.
Let us consider the Palm distribution of the base station point process [33], which has a typical point at the origin. Under this Palm distribution, the cell containing the typical point at the origin is referred to as a typical cell [34].
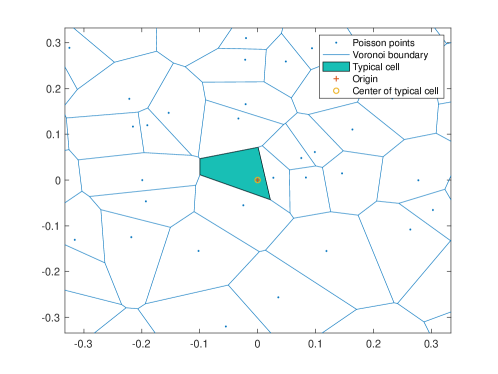
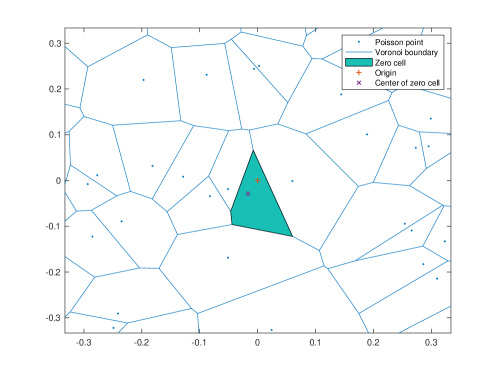
One may similarly consider the Voronoi tessellation of the base station point process under the stationary distribution of the user Poisson point process. Note that the origin is not an element of the base station point process. Instead, there exists a cell that contains the origin (i.e., the typical user) and this cell is referred to as the zero cell. Fig. 3 illustrates the typical cell (upper figure) and the zero cell (lower figure) w.r.t. the base station Poisson point processes of intensity , respectively. The zero cell will be used to derive the effective rate and then characterize the interplay between the cellular downlink unicast and vehicular sidelink broadcast.
II-E Network Performance Metrics
We first focus on the reliability of sidelink and downlink cellular communications, respectively. For each, reliability is captured by the coverage probability of the typical user. Then, we derive the effective data rate of the typical user, offered by downlink communications.
II-E1 Coverage Probability
We first use the Palm distribution of the user point process to feature a typical user at the origin. Note that the network performance seen by the typical user coincides with the network performance averaged over all users in the network [33].
The coverage probability of the typical cellular downlink user is defined by
| (4) |
where is the decoding threshold, is the location of the base station that is closest to the origin, and indicates that the metric is derived under the Palm distribution of , namely for the typical user at the origin. In the proposed network, we assume that interference dominates thermal noise. Thus, we investigate the SIR coverage probability.
Similarly, the coverage probability of the typical sidelink user is defined by
| (5) |
where is the location of the nearest vehicle.
II-E2 Effective Data Rate
The (load-balanced) effective downlink data rate is defined as the spatial average of the long-term achievable rate (bits/sec/Hz) of each cellular user, provided that the time resource of each base station is equally shared by all of its associated downlink users111A simple example: at each time slot, each base station chooses and serves one user out of its associated users..
Conditionally on the downlink association, the mean achievable rate of the typical user is denoted by . Here, we shall use the effective rate per user, which is defined as the mean achievable rate of the typical user, divided by the mean number of users that share the same base station. In addition, from the typical user’s perspective, this effective rate is multiplied by the probability that that the typical user has a downlink association. Therefore, the effective data rate is defined as follows:
| (7) |
where denotes the expected number of users that share the base station and denotes the Voronoi cell of base station minus the vehicle associaiton region .
| Notation | Description |
|---|---|
| Sidelink coverage probability | |
| Downlink coverage probability | |
| Sidelink association probability | |
| Downlink association probability | |
| Downlink effective rate per user |
III Result: Coverage Probability
This section analyzes the reliability of the sidelink and downlink communications. We derive the coverage probabilities of the typical user. Since the typical user at the origin is associated with either a vehicle or with a base station, the interference and SIR seen by the typical user varies w.r.t. the association type. For instance, when the typical user is associated with a vehicle, the origin is contained in a disk (sidelink association). In other words, there exists a vehicle within a distance that covers the origin. On the other hand, when the typical user is associated with a base station, the origin is not contained in any disk.
III-A User Association
Here, we focus on the derivation of the probability that the typical user is associated with a vehicle or with a base station. The vehicle association region depends on time as shown in Eq. (1). However, we will show below that the association probability is not a function of time.
Theorem 1.
The probability that the typical user is associated with a vehicle is
| (8) |
The probability that the typical user is associated with a base station is
| (9) |
Note that both Eqs are not functions of time.
Proof:
The probability that the typical user is associated with a vehicle is the same as the probability that there is at least one vehicle at a distance less than from the origin. Hence,
| (10) |
where we used the fact that and are independent. is the collection of point processes conditionally on Thus, the vehicle point process can be written as follows:
| (11) |
where denotes the Poisson point process on the line parameterized by at time For simplicity, we also denote the Poisson point process by . At time zero, is given by a one-dimensional Poisson point process with intensity . Based on the considered mobility model, every vehicle randomly chooses its moving direction on its line at time . At time the Poisson point process with intensity is translated by in one direction; similarly, the Poisson point process with intensity is translated by in the other direction. Based on the displacement theorem [9], the point process at any time is a Poisson point process with intensity . Finally, the underlying line process is time-invariant and we have that the vehicle point process at time and the vehicle point process at time are equal in distribution; As a result, we write the vehicle point process as
| (12) |
Due to the stationary and time-invariant properties of the expectation in Eq. (10) is
| (13) |
where we replace the Poisson point process with the Poisson point process using its displacement In the above, is the vector from the origin to the line with index . Then, we have
| (14) |
As a result, we have
| (15) |
where we use the probability generating functional of the cylinder Poisson point process with intensity [20]. We use to complete the proof. ∎
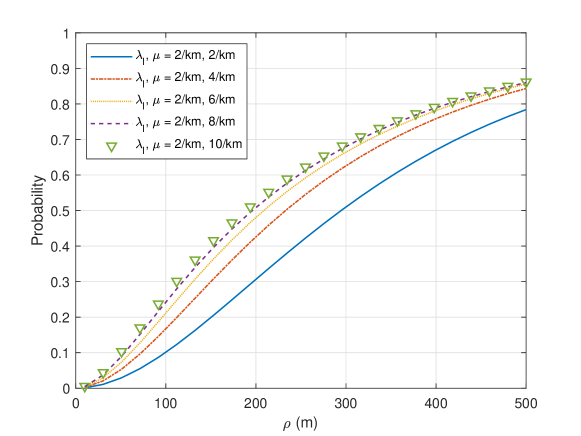
Fig. 4 plots the probability that the typical user at the origin is associated with a vehicle. The figure shows the way that the probability of vehicle association increases as the density increases. It also shows that the linear density yields a diminishing return of the association probability. In the asymptotic regime where the linear density is very high, we have Eq. (8) as . This formula corresponds to the probability that the disk of radius centered at the origin intersects with the Poisson line process of intensity
Remark 3.
We can interpret Theorem 1 in an ergodic sense [33]. For a given geometry of roads, base stations, and sidelink broadcast distance Eq. (8) gives the probability that the typical user is covered by the vehicle broadcast. In other words, it gives the instantaneous fraction of users that are receiving the sidelink broadcast. In addition, in an ergodic sense, the sidelink association probability Eq. (8) also corresponds to the fraction of the time that a typical user is associated with a sidelink vehicle. Similarly, the downlink association probability corresponds to the fraction of time that the user is associated with a downlink base station.
III-B SIR Coverage of the Typical Cellular Downlink
This section derives the SIR coverage probability of downlink.
Theorem 2.
The downlink coverage probability of the typical user is
| (16) |
where
We define the transmit power ratio
Proof:
The probability that the typical user is not in and its SIR is greater than is
| (17) |
where is the shot-noise process seen by the typical user and is the distance from the typical user to its nearest base station. In Eq. (17), is the density function of on the event conditional on , namely,
| (18) |
The integrand of Eq. (17) is the Laplace transform of the interference from vehicles outside of the disk and from base station outside of the disk conditional on and . Specifically, the integrand is
By using the independence of and and by applying the Laplace transform of the interference from cellular base stations outside of the disk of radius [9], we obtain
| (19) |
Using the independence and the power ratio , we have
| (20) |
In distribution, the points of the Poisson point process can be represented in terms of the points of the Poisson point process through Hence, we have
| (21) |
Similarly, we have
| (22) |
Then, from Eqs. (18)–(22), the coverage probability is given by
where the functions and are given in Eq. (21) and (22), respectively. Finally, we obtain the final result by using the Laplace transform of the Poisson line process. ∎
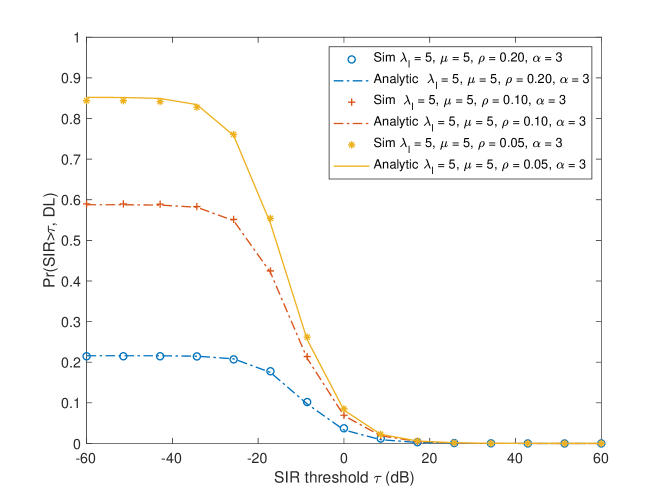
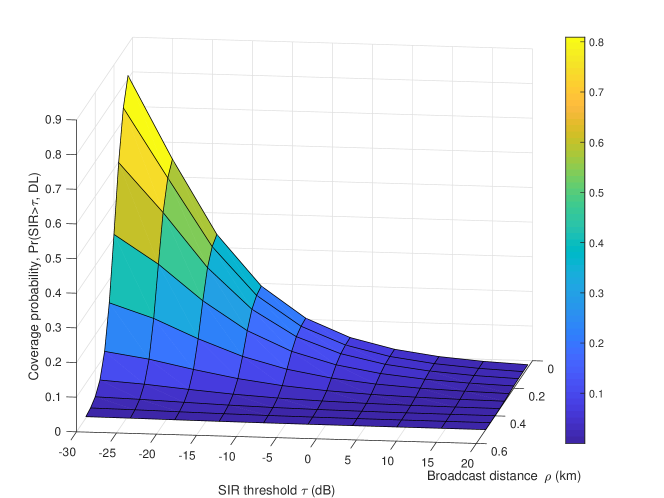
Fig. 5 illustrates the coverage probability of the typical user, obtained by Monte Carlo simulations and by Theorem 2. Fig. 6 illustrates the coverage probability of the typical user w.r.t. the safety message range and SIR coverage threshold . It shows how the SIR coverage decreases when or increase.
III-C SIR Coverage of the Typical Sidelink
This section derives the SIR coverage probability of sidelink.
Theorem 3.
The sidelink coverage probability of the typical user is
| (23) |
where
Proof:
The coverage probability is given by
| (24) |
where the conditional density function is given by
| (25) |
The first term is the probability that there is a point of at distance from the origin. The second term is the probability that there exists no point of , for any such that .
Conditional on and the Laplace transform of the interference is
| (26) |
On the right hand side of Eq. (26), the conditional expectation w.r.t. are ommitted.
By incorporating Eqs. (25) and (26) to Eq. (24), we can write the coverage probability as
| (27) |
where the integrand functions are given by
Applying Campbell’s formula in [9] on Eq. (27) w.r.t. the cylinder Poisson point process gives
| (28) |
where is the Palm expectation of the cylinder Poisson line process. We have
| (29) |
We obtain the first equation by using Slivnyak’s theorem and the second equation by using the probability generating functional of the cylinder Poisson point process. ∎
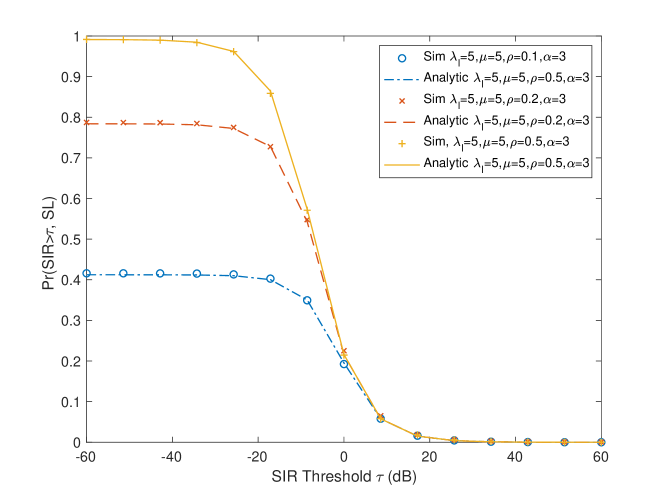
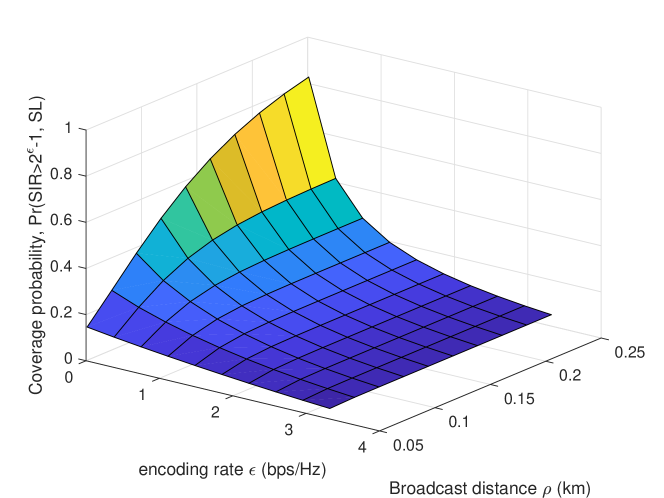
Fig. 7 illustrates the derived probability of the typical sidelink user, obtained by Monte Carlo simulations and by Theorem 3, respectively. In the proposed network model, vehicles broadcast their safety messages at a fixed encoding rate such as bps/Hz. The value of determines the corresponding SIR threshold at which safety messages are successfully decoded. In Fig. 8, we illustrate the sidelink coverage probability as a function of the encoding threshold (bps/Hz) and the broadcast distance (km). The -value is the probability that the message with the corresponding encoding rate is successfully decoded by the typical user: .
Remark 4.
The sidelink coverage probability conditional on the sidelink association is the ratio of the number of vehicle-associated users whose SIRs are greater than to the number vehicle-associated users, in a very large ball centered at the origin:
where denotes the SIR of user and denotes the vehicle association region. The sidelink coverage probability characterizes the reliability of the vehicular broadcast safety messaging.
IV Effective Data Rate
This section studies the effective data rate of the typical user through downlink communications. It captures the average amount of data that users will effectively receive through messages from base stations in the presense of sidelink interruptions.
Recall that the zero cell, denoted by is the Voronoi cell that contains the origin (or equivalently the typical user) under the Palm distribution of the user point process . The nucleus of the zero cell corresponds to the base station that serves the typical user.
IV-A Fraction of Vehicle Association Region in the Zero Cell
To derive the effective data rate, we first evaluate the expected number of downlink association users of the serving base station of the typical user: . We first derive the mean area of the set under the Palm distribution of Then, the mean number of downlink users is simply given by the product of the user density and the mean area of the zero cell, .
Lemma 1 (Inversion lemma).
Suppose a stationary point process of intensity For all non-negative functions the Palm inversion formula [9] is
| (30) |
In addition, for any non-negative function of the zero cell, we have
| (31) |
where is the area of the set and is the typical Voronoi cell (the typical cell under the Palm distribution ).
Proposition 1.
The mean areas of the sets and are given by
respectively. We use
Proof:
Let denote the area of the set in the zero cell Then, we have
Using the inversion lemma, the expected value is given by
| (32) |
where (a) is obtained by conditioning on the Cox point process . We have (b) from the fact that Then, we derive (c) by using the fact that the probability of the typical point is in is given by In Eq. (32), we denote by the typical Voronoi cell under the Palm distribution of the base station point process. Therefore we have
respectively. Then, in [35], the second moment is given by
where and
∎
IV-B Effective Data Rate of Typical User
Theorem 4.
Proof:
Note that the effective data rate can be interpreted as the long-term achievable rate on downlink.
IV-C Reliability of Sidelink in Cellular Networks
To improve the reliability of the vehicular safety messages, one should
-
1.
decrease the encoding rate of the vehicular safety messages,
-
2.
decrease the size of the vehicle association region,
-
3.
increase the transmit power of vehicular broadcast,
In practice, the encoding rate and the size of the vehicle association region might be given as the requirements for a V2X safety system. For instance, the encoding rate is determined by the size of safety messages that the ITS will adopt. Further, users are required to successfully decode such safety messages from vehicles especially from those within meters. In other words, the values of or might be given as system requirements. To improve the reliability of sidelink broadcasts, one could focus on the transmit power of the vehicular safety message
Increasing the transmit power of the vehicular broadcast will improve the reliability of safety messages. Nevertheless, it is important to note that the interference generated by other vehicles will also increase. In addition, varying the transmit power of vehicles affects other network performance metrics such as the downlink coverage probability or the effective rate of the typical user. As increases, the effective data rate of the typical downlink user decreases due to the increased sidelink interference from vehicles. Similarly, as decreases, the effective data rate will increase due to the decreased sidelink interference from vehicles. Table III summarizes the tradeoff relations between the coverage probability of the sidelink and the effective rate of the downlink w.r.t. the vehicular transmit power . We consider .
| Network parameter | Sidelink reliability | Effective rate |
|---|---|---|
| increase | increase (diminishing return) | decrease |
| decrease | decrease | increase |
| increase | unchanged | decrease |
| decrease | unchanged | increase |
One way of analyzing such a tradeoff is to formulate an objective function incorporating the tradeoff. Below, we introduce the overall network utility given by the sum of benefits that the typical user would be offered via sidelink and downlink. For weights the network utility is the following function of :
| (36) |
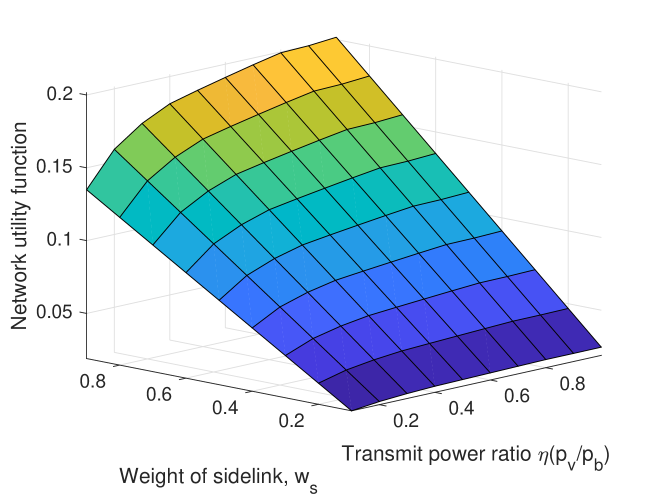
where the first term is the probability that the typical user successfully decodes the safety messages and the second term is the amount of effective data that it receives on the downlink channel. The interplay of network performances is captured by the weights, and Fig. 9 illustrates the proposed network utility function when To show the impact of power control in safety messaing, we consider where indicates that . For each power ratio, different sidelink weights are analyzed: . In the figure, as the transmit power ratio increases, the network utility increases. The increment of network utility w.r.t. is greater for a greater .
Example 1.
By leveraging the network utility expression, we can derive the total ergodic rate that the typical user obtains from both sidelink and downlink. For the downlink rate, the effective rate of Eq. (33) can be used. For the sidelink rate, we use transmission capacity given in [36]. To be specific, when the safety message is encoded with (bps/Hz), the probability of success is given by Therefore, we write the sidelink rate as . Using the law of total probability, the total rate from downlink and sidelink is
| (37) |
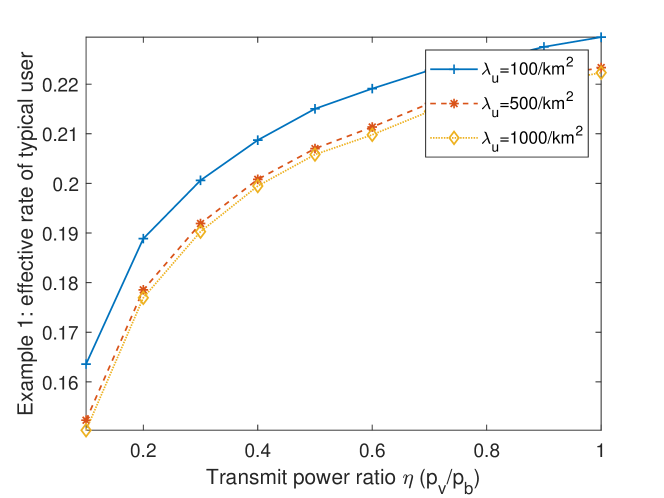
Fig. 10 illustrates the total data rate of the typical user. The figure considers different numbers of users to analyze the impact of network congestion where the density of users is high. In the simulation setup, the effective rate increases as the power ratio increases. Furthermore, a lightly loaded network (a smaller number of users) has a better total data rate because each base station is shared by fewer users.
V Conclusion
In this paper, we analyze the broadcast of safety messages from vehicles to users. These messages contain safety-critical information and they are assumed to be transmitted in the same spectrum as downlink communications. To capture the ‘compulsory’ reception of vehicular safety messages from vehicles to users, we assume that users within a distance are forced to decode the safety messages. To analyze the network performance, we use a Poisson line Cox point process to model vehicles and then a Boolean model on the vehicle process to represent the safety message prioritized regions. Under the proposed stationary framework, we quantify the association of users as the association probability of the typical user. We then derive the distribution of the SIR of the typical user to quantify the reliability of the vehicular safety messages and downlink messages, respectively. Finally, we derive the downlink effective rate of the typical user to quantify the impact of mandatory sidelink reception for users. To capture the tradeoff of network performances w.r.t. the transmit power of safety messages, we also analyze the network utility and the total data rate of the typical user.
Acknowledgement
This work is supported in part by the National Science Foundation under Grant No. NSF-CCF-1514275 and an award from the Simons Foundation (#197982), both to the University of Texas at Austin.
References
- [1] F. Rebecchi, M. Dias de Amorim, V. Conan, A. Passarella, R. Bruno, and M. Conti, “Data offloading techniques in cellular networks: A survey,” IEEE Commun. Surv&Tuts, vol. 17, no. 2, pp. 580–603, Secondquarter 2015.
- [2] L. Goratti, G. Steri, K. M. Gomez, and G. Baldini, “Connectivity and security in a D2D communication protocol for public safety applications,” in Proc. IEEE ISWCS, Aug 2014, pp. 548–552.
- [3] X. Cheng, L. Yang, and X. Shen, “D2D for intelligent transportation systems: A feasibility study,” IEEE Trans. Intell. Transp. Syst., vol. 16, no. 4, pp. 1784–1793, Aug 2015.
- [4] 3GPP TR 38.885, “Study on NR vehicle-to-all (V2X) services,” 3GPP TR 38885, July 2018.
- [5] G. Araniti, C. Campolo, M. Condoluci, A. Iera, and A. Molinaro, “LTE for vehicular networking: a survey,” IEEE Commun. Mag., vol. 51, no. 5, pp. 148–157, May 2013.
- [6] S. Chen, J. Hu, Y. Shi, Y. Peng, J. Fang, R. Zhao, and L. Zhao, “Vehicle-to-everything (V2X) services supported by LTE-based systems and 5G,” IEEE Commun. Standards Mag., vol. 1, no. 2, pp. 70–76, 2017.
- [7] J. B. Kenney, “Dedicated short-range communications (DSRC) standards in the united states,” Proceedings of the IEEE, vol. 99, no. 7, pp. 1162–1182, 2011.
- [8] 3GPP TR 36.885, “Study on LTE vehicle-to-all (v2x) services,” 3GPP TR 36885, July 2016.
- [9] F. Baccelli, B. Błaszczyszyn et al., “Stochastic geometry and wireless networks: Volume I theory,” Foundations and Trends® in Networking, vol. 3, no. 3–4, pp. 249–449, 2010.
- [10] J. G. Andrews, F. Baccelli, and R. K. Ganti, “A tractable approach to coverage and rate in cellular networks,” IEEE Trans. Commun., vol. 59, no. 11, pp. 3122–3134, Nov. 2011.
- [11] H. ElSawy, E. Hossain, and M. Haenggi, “Stochastic geometry for modeling, analysis, and design of multi-tier and cognitive cellular wireless networks: A survey,” IEEE Commun Surv&Tuts, vol. 15, no. 3, pp. 996–1019, Third 2013.
- [12] B. Błaszczyszyn, M. K. Karray, and H. P. Keeler, “Using Poisson processes to model lattice cellular networks,” in Proc. IEEE INFOCOM, Apr. 2013, pp. 773–781.
- [13] R. W. Heath, M. Kountouris, and T. Bai, “Modeling heterogeneous network interference using Poisson point processes,” IEEE Trans. Signal Process., vol. 61, no. 16, pp. 4114–4126, Aug 2013.
- [14] F. Baccelli, B. Błaszczyszyn et al., “Stochastic geometry and wireless networks: Volume II applications,” Foundations and Trends® in Networking, vol. 4, no. 1–2, pp. 1–312, 2010.
- [15] G. Fodor and N. Reider, “A distributed power control scheme for cellular network assisted D2D communications,” in Proc. IEEE GLOBECOM, Dec 2011, pp. 1–6.
- [16] H. ElSawy, E. Hossain, and M. Alouini, “Analytical modeling of mode selection and power control for underlay D2D communication in cellular networks,” IEEE Trans. Commun., vol. 62, no. 11, pp. 4147–4161, Nov 2014.
- [17] H. Min, J. Lee, S. Park, and D. Hong, “Capacity enhancement using an interference limited area for device-to-device uplink underlaying cellular networks,” IEEE Trans. Wireless Commun., vol. 10, no. 12, pp. 3995–4000, Dec 2011.
- [18] X. Lin, R. W. Heath, and J. G. Andrews, “The interplay between massive MIMO and underlaid D2D networking,” IEEE Trans. Wireless Commun., vol. 14, no. 6, pp. 3337–3351, June 2015.
- [19] A. H. Sakr and E. Hossain, “Cognitive and energy harvesting-based D2D communication in cellular networks: Stochastic geometry modeling and analysis,” IEEE Trans. Commun., vol. 63, no. 5, pp. 1867–1880, May 2015.
- [20] D. J. Daley and D. Vere-Jones, An introduction to the theory of point processes: volume II: general theory and structure. Springer Science & Business Media, New York, 2007.
- [21] S. N. Chiu, D. Stoyan, W. S. Kendall, and J. Mecke, Stochastic geometry and its applications. John Wiley & Sons, 2013.
- [22] F. Baccelli, M. Klein, M. Lebourges, and S. Zuyev, “Stochastic geometry and architecture of communication networks,” Telecommunication Systems, vol. 7, no. 1, pp. 209–227, Jun 1997.
- [23] F. Morlot, “A population model based on a Poisson line tessellation,” in Proc. IEEE WiOpt. IEEE, 2012, pp. 337–342.
- [24] C. Choi and F. Baccelli, “An analytical framework for coverage in cellular networks leveraging vehicles,” IEEE Trans. Commun., vol. 66, no. 10, pp. 4950–4964, Oct 2018.
- [25] ——, “Poisson Cox point processes for vehicular networks,” IEEE Trans. Veh. Technol., vol. 67, no. 10, pp. 10 160–10 165, Oct 2018.
- [26] V. V. Chetlur and H. S. Dhillon, “Coverage analysis of a vehicular network modeled as Cox process driven by Poisson line process,” IEEE Trans. Wireless Commun., vol. 17, no. 7, pp. 4401–4416, July 2018.
- [27] C. Choi and F. Baccelli, “Spatial and temporal analysis of direct communications from static devices to mobile vehicles,” IEEE Trans. Wireless Commun., vol. 18, no. 11, pp. 5128–5140, 2019.
- [28] V. V. Chetlur and H. S. Dhillon, “Coverage and rate analysis of downlink cellular vehicle-to-everything (C-V2X) communication,” arXiv preprint arXiv:1901.09236, 2019.
- [29] H. S. Dhillon, R. K. Ganti, F. Baccelli, and J. G. Andrews, “Modeling and analysis of K-tier downlink heterogeneous cellular networks,” IEEE J. Sel. Areas Commun., vol. 30, no. 3, pp. 550–560, April 2012.
- [30] B. Błaszczyszyn, P. Mühlethaler, and A. Nadjib, “Vehicular ad-hoc networks: Point-to-point, emergency and broadcast communications,” in Proc. of IFIP Wireless Days, Dublin, Ireland, 2012.
- [31] A. Goldsmith, Wireless communications. Cambridge university press, 2005.
- [32] D. Tse and P. Viswanath, Fundamentals of wireless communication. Cambridge university press, 2005.
- [33] F. Baccelli and P. Brémaud, Elements of queueing theory: Palm Martingale calculus and stochastic recurrences. Springer Science & Business Media, 2013, vol. 26.
- [34] J. Moller, Lectures on random Voronoi tessellations. Springer Science & Business Media, 2012, vol. 87.
- [35] A. Hayen and M. P. Quine, “Areas of components of a Voronoi polygon in a homogeneous Poisson process in the plane,” Advances in Applied Probability, vol. 34, no. 2, pp. 281–291, 2002.
- [36] S. P. Weber, X. Yang, J. G. Andrews, and G. de Veciana, “Transmission capacity of wireless ad hoc networks with outage constraints,” IEEE Trans. Inf. Theory, vol. 51, no. 12, pp. 4091–4102, Dec 2005.