IEEE Copyright Notice
Copyright 2024 IEEE. Personal use of this material is permitted. Permission from IEEE must be obtained for all other uses, in any current or future media, including reprinting/republishing this material for advertising or promotional purposes, creating new collective works, for resale or redistribution to servers or lists, or reuse of any copyrighted component of this work in other works.
Annealing-Assisted Column Generation
for Inequality-Constrained Combinatorial Optimization Problems
Hiroshi Kanai 1
Masashi Yamashita1
Kotaro Tanahashi2
Shu Tanaka13456
Annealing-Assisted Column Generation
for Inequality-Constrained Combinatorial Optimization Problems
Abstract
Ising machines are expected to solve combinatorial optimization problems faster than the existing integer programming solvers. These problems, particularly those encountered in practical situations, typically involve inequality constraints. However, owing to the hardware limitations of the current Ising machines, solving combinatorial optimization problems with inequality constraints remains challenging. The Capacitated Vehicle Routing Problem (CVRP) is a typical example of a problem with inequality constraints. The objective function of the CVRP is to minimize the total distance traveled by each vehicle while limiting the total demand of customers served by a single vehicle to the vehicle’s capacity. The CVRP is classified as -hard and, thus, is commonly solved using heuristic algorithms, such as column generation. Column generation attempts to iteratively generate only the promising routes, as the number of feasible routes increases exponentially. Within this framework, the CVRP is formulated as a set cover problem. The corresponding dual solutions are used to define the pricing subproblem, which is intended to create a new route. By applying Ising machines to this pricing subproblem, the overall computation time can be reduced. This study aims to solve combinatorial optimization problems with inequality constraints using a hybrid algorithm that combines column generation and Ising machines, thereby extending the applications of the latter. We parameterize the difficulty of the inequality constraints and demonstrate that our annealing-assisted column generation can converge to a better lower bound.
Index Terms:
Ising machines, column generation, simulated annealing, capacitated vehicle routing problem, inequality constraints, combinatorial optimization problem.I Introduction
Combinatorial optimization problems entail identifying the optimal solutions that, among numerous candidate solutions, satisfy the defined constraints. These problems find applications in various fields, including marketing, drug development, and routing. If represents a vector of the decision variables with combinatorial structure, a combinatorial optimization problems is one that seeks to obtain the solution that minimizes the objective function , i.e.:
| (1) |
where denotes the specific equality or inequality constraints of the problem. Ising machines are expected to provide polynomial improvements in both time complexity and scalability for the combinatorial optimization problems compared to conventional integer programming solvers [1]. Such enhancements are crucial, given that most combinatorial optimization problems belong to the -hard class, wherein even slight variations in the coefficient of the exponential function can substantially reduce computation time. Combinatorial optimization problems can be formulated using the Ising model, one of the most fundamental statistical mechanical models, so that the model’s ground states correspond to the optimal solutions of combinatorial optimization problems [2, 3, 4, 5]. However, solving combinatorial optimization problems with numerous inequality constraints poses challenges due to the current hardware limitations of Ising machines. These limitations are manifested in the scarcity of available parameters and topological issues to express the interactions in the corresponding Ising model [6, 7, 8, 9, 10, 11]. Furthermore, the performance of Ising machines heavily relies on the formulations of the problems [12]. In this study, we focus on the Capacitated Vehicle Routing Problem (CVRP) as a prototypical optimization problem with inequality constraints.
The Vehicle Routing Problem (VRP), introduced by Dantzig and Ramser [13], exemplifies a multiobjective transportation network design and routing problem [14]. Its goal is to determine the shortest set of routes where each customer is visited exactly once. The objective function is defined as the total distance covered by each vehicle, with each vehicle required to depart from and return to its depot. In addition to these rudimentary premises, several VRP variants incorporate other practical constraints such as multiple depots and time windows [15]. Of these variants, the CVRP is a particularly representative case whose properties and classical approaches have been extensively studied. The CVRP introduces an additional inequality constraint that the total demand of the customers visited by a single vehicle must not exceed the vehicle’s capacity. Being -hard, the CVRP is commonly handled through heuristic algorithms, such as construction methods [16, 17], column generation [18, 19, 20], and local search [21]. In particular, the column generation scheme aims to iteratively generate only the promising routes, given the exponential increase in feasible routes. Formulating the CVRP as a set cover problem, termed as a master problem, involves using its duals to define the pricing subproblem with capacity constraints. This pricing subproblem plays a critical role in creating new routes that could potentially reduce the current objective value but often becomes the bottleneck of the entire algorithm. Recently, Ising machines have been suggested as capable of solving this pricing subproblem more efficiently than the existing solvers. Relevant research in this area [22, 23, 24] has applied hybrid algorithm combining column generation and Ising machines to solve other optimization problems. While previous studies have been problem-oriented, our research focuses attention on the inequality constraints of certain optimization problems.
Extended versions of branch-and-price algorithms or active set methods are commonly employed to obtain exact solutions for the CVRP. Specifically, the branch-and-cut-and-price method [25] accurately solved the problem when the number of customers was . In addition, recent efforts have explored the use of Ising machines to tackle larger instances of the CVRP [26, 27, 12, 28]. Nevertheless, the aforementioned hardware limitations prevent Ising machines from directly finding the optimal solutions for the CVRP. The subsequent section elaborates on these hardware limitations. This study aims to extend the application of Ising machines to combinatorial optimization problems with inequality constraints.
The remainder of this paper is structured as follows. We commence by introducing Ising machines and their intricacies in Section II. In Section III, we present the conventional CVRP formulation. Section IV outlines the principles of the column generation algorithm. The proposed methods are detailed in Section V. We present the obtained results in Section VI. Lastly, we draw conclusions in section VII.
II Ising machine
As noted earlier, combinatorial optimization problems are ubiquitous in our society. The most well-known combinatorial optimization problems belong to the -hard class. However, solving these -hard problems is time-consuming. Whether -hard problems can be solved in polynomial time remains to be determined. Thus, approximation and heuristic algorithms are currently being developed for this task. Recent years have seen the brilliant performances of Ising machines that aim to obtain the ground state of the Ising model [1, 2, 3, 4, 5]. Here, the state is defined as the spin configuration of the Ising model, and the lowest-energy state is specifically called the ground state. This Ising problem is also -hard, and many of the combinatorial optimization problems can be mapped to Ising model as well as its equivalent expression, the Quadratic Unconstrained Binary Optimization (QUBO) model. Therefore, improvements over the classical algorithms for these Ising problems can also have a significant influence on other combinatorial optimization problems as well [29].
The Ising model is defined on an undirected weighted graph , where and denote the vertex and undirected-edge set, respectively. Here, and their elements are given by and . Let be an Ising variable that takes either or . The Ising Hamiltonian is then given by:
| (2) |
represents the real-valued interaction coefficient between and . The real-valued local bias can be added to , which is also called the local magnetic field. Both and can be set in advance as constants. If is a nonzero value for every pair of and in the graph , the graph is stated to be fully connected. Moreover, a subset of vertices such that each and every pair of and is adjacent is called a clique. Binary variables are sometimes appropriate for formulating combinatorial optimization problems. The binary variables are denoted by . Using the following transformation rule, the Ising model can be converted to the QUBO model and vice versa.
| (3) |
The corresponding objective function is expressed as follows:
| (4) |
where is the off-diagonal coefficient and is the diagonal coefficient. Each element is a real constant. Note that we used based on the basic property of binary variables; therefore, the equation above includes a linear term. The penalty function method is usually a good way forward for formulating optimization problems with constraints. In the penalty function method, the equality and inequality constraints are expressed as a penalty function such that the penalty terms take a positive value if their corresponding constraints are violated. The linear combination of the penalty function and the objective function is a new objective function that should be optimized. Because we consider the minimization problems, the violation increases the objective values and prevents us from obtaining the global optima.
To obtain the lowest-energy states of the Ising Hamiltonian or the energy function, the various underlying operating mechanisms for Ising machines have been devised and implemented: Quantum Annealing (QA) [30], Simulated Annealing (SA) [31, 32], Coherent Ising Machine (CIM) [33, 34, 35], and Simulated Quantum Annealing (SQA) [36, 37].
When we make use of Ising machines to solve optimization problems, mapping from the logical model to the actual interaction topology, which is called minor embedding, is required. We refer to the decision variables in the logical model as the logical spins, which are distinguished from the physical spins in the actual circuit. We will later show that logical spins in a logical model sometimes need to be expressed as multiple physical spins in real devices. In this study, we employed Fixstars Amplify Annealing Engine. Fixstars Amplify Annealing Engine is a Graphics Processing Unit (GPU)-based Ising machine operated using an SA-like algorithm. The maximum number of available logical spins for a fully connected graph is .
Although Ising machines are undergoing significant progress in terms of their ability to handle a wide range of problems, three fundamental hardware limitations must be considered. First, the number of available bits is limited in real devices. For instance, the D-Wave Advantage [38] can handle more than qubits as a sparse graph and logical spins as a clique. Therefore, it remains a challenge to solve problems larger than that can be defined on fully connected graphs. Second, some of the interactions in the logical model cannot be directly expressed on real devices because of interaction topology issue [6]. As shown in Figure 1, although the logical spin is connected to four neighboring bits in the logical model, it may be impossible to connect them directly if the possible number of neighboring bits is three. Thus, multiple physical spins are used to express a single logical spin by setting the sufficiently large interactions between those equivalent physical spins. This interaction topology issue hinders us from solving larger problems whose corresponding undirected graphs have dense connectivity. Finally, the bit widths of the interactions and the local magnetic fields in the physical model are limited. Therefore, when mapping the logical models onto the physical models, the ground states of the original model and converted models can be different. To avoid this, bit-width reduction methods that maintain the correspondence between the logical model and the physical models have been studied [8, 11].
Owing to these limitations, Ising machines have difficulty in solving problems whose corresponding graphs require numerous variables and dense connectivity. However, the actual optimization problems in our society often demand both of them. Insofar as we encounter such complex problems, reducing the number of variables and breaking down the problem into smaller ones are indispensable. A typical example of these optimization problems is CVRP, which is explained in the following section.

III CVRP
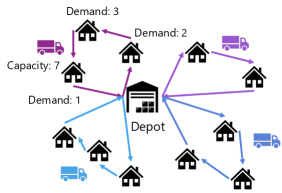
CVRP (Fig. 2) is defined on an undirected weighted complete graph . Each customer has a demand , and is the number of vehicles available. For simplicity, all the vehicles have the same capacity . The distances between and is denoted by . Note that we enforce the symmetry condition for the distance, which is as the graph is undirected. corresponds to the depot and its demand . Furthermore, is an undirected edge set whose elements are the edges between and for all . The number of movements between and is given by decision variable . We also define as the minimum number of vehicles required to visit all the customers in . The CVRP can then be formulated using the following equations [39]:
| min | (5) | |||
| s.t. | (6) | |||
| (7) | ||||
| (8) | ||||
| (9) | ||||
| (10) |
Constraint (9) forces to be if the vehicle moves from to and otherwise. Note that the constraint (9) excludes the case in which or . Then, constraint (10) complements the case where either or is . Note also that can be in constraint (10) because there might be a piston route, where a vehicle visits just one single customer and then returns to the depot. Constraint (6) ensures that the exact number of vehicles is operated to deliver to each customer. As every vehicle must depart from and return to the depot, the sum of should be twice the number of vehicles . Constraint (7) ensures that each and every customer is visited strictly once. Constraint (8) is called the rounded capacity inequality and imposes both the capacity and the subtour elimination constraints. By definition, Obtaining is realized by solving the corresponding bin packing problem. Nonetheless, the bin packing problem is -hard; thus, the following lower bound is commonly substituted for [39, 40]:
| (11) |
The symbol denotes the ceiling function. Obviously, this approximate version of represents the average number of vehicles required to visit each customer in .
CVRP can also be formulated in a different fashion, such that the decision variables are binary. In the natural course of events, a naive QUBO model for CVRP was unveiled, which is discussed in a subsequent section. However, as previously stated, the use of Ising machines to solve larger CVRP does not seem appropriate because of hardware limitations. Hence, the problem is decomposed into smaller problems to enable the use of Ising machines in larger CVRP. The subsequent section presents the underlying principles of column generation.
IV Column Generation
This section focuses on how the column generation scheme is applied to the CVRP. To begin with, we describe the set cover formulation for the CVRP. Thereafter, we introduce the corresponding dual problem. Finally, we discuss the fundamental principles of column generation.
IV-A Set Cover Problem
We define as the route set that includes all feasible routes in the specific CVRP instance. denotes the total distance of the th route . Let be a matrix whose element is if route contains the customer and if route does not contain the customer . The set cover problem for the CVRP can then be represented by the following equation:
| min | (12) | ||||
| s.t. | (13) | ||||
| (14) | |||||
| (15) | |||||
is the decision variable that takes if route is chosen and if is not selected for the solution. The optimization problem (12)–(15) is referred to as the master problem. Constraint (13) guarantees that every customer is visited at least once. Constraint (13) can be formulated as an equality constraint, but this typically slows down the convergence of the column generation. Consequently, an inequality form is typically used for this purpose, particularly during column generation. If the constraint (13) is expressed as an inequality, this problem is called the a set partition problem. The number of vehicles operated is determined by the constraint . Finally, the constraint (15) requires the decision variables to be integers. This is because the additional inequality constraint can be eliminated in a restricted master problem, that underwent linear programming relaxation, as discussed later. Because the optimal is or in this model, is not optimal.
The set cover problem is known to be -complete, and the greedy algorithm is a well-known approximation algorithm for this problem. The number of feasible routes in increases exponentially, and it is virtually impossible to consider all the feasible routes. Therefore, column generation focuses on a subset of , that comprises only promising routes. Let be such a restricted route set. Converting in the set cover problem (12)–(15) into yields the following restricted master problem:
| min | (16) | ||||
| s.t. | (17) | ||||
| (18) | |||||
| (19) | |||||
The restricted master problem (16)–(19) is differentiated from the original set cover problem (12)–(15) because the integer variable is relaxed to a real number. During this procedure, we aim to optimize the restricted master problem. This relaxation is effective because the restricted master problem provides a tight lower bound for the original set cover problem. More precisely, the optimal objective value of the restricted master problem asymptotically reaches the optimal objective value of the original set cover problem when the number of customers approaches to infinity [41, 42].
| (20) |
The following subsection introduces the dual problem of the restricted master problem, which is crucial to determine the existence of potential routes.
IV-B Dual Problem
The restricted master problem (12)–(15) can be rewritten in the following standard inequality form:
| min | (21) | ||||
| s.t. | (22) | ||||
| (23) | |||||
| (24) | |||||
Multiplying both sides of constraints (22)–(24) by the nonnegative dual variables , , , and then adding the resulting terms, we obtain:
| (25) |
Substituting with , the relationship above becomes equivalent to
| (26) |
Assuming the coefficients on the left side of (26) are smaller than ,
| (27) |
we obtain the following relationship:
| (28) |
According to the inequality (28), the lower bound of the objective value of the restricted master problem is given by the following term:
| (29) |
Therefore, the dual problem of the restricted master problem (16)–(19) is
| max | (30) | |||
| s.t. | (31) | |||
| (32) | ||||
| (33) |
The symbol denotes a nonnegative dual variable corresponding to each customer . Variable is a real dual variable corresponding to the depot.
IV-C The Principle of Column Generation
Prior to introducing the pricing subproblem, we describe the fundamental principles underlying the column generation scheme. The feasible region in the restricted master problem (16)–(19) expands proportionally with the number of generated columns. Conversely, the feasible region in the dual problem (30)–(33) contracts in proportion to the increase in the number of potential routes generated. This fact is of great importance because it implies that the dual solution , which is optimal in the feasible region , is a global optimum in if is feasible in [43]. Consequently, if the global optimum has not been determined from the current restricted master problem, there should be a concealed new route whose inequality constraints are violated by the current dual solution. This new route can be identified by solving the following pricing subproblem, which reflects the violation of the inequality constraints in the dual problem:
| min | (34) | |||
| s.t. | (35) |
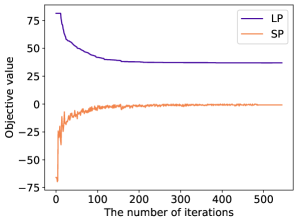
The objective function (34) is called the reduced cost . The prior discussion asserts that route with a negative reduced cost, i.e., has the potential to lower the current objective value. When , the iterative process of solving the restricted master problem, the dual problem, and the pricing subproblem continues. Figure 3 illustrates the evolution of the relevant objective values throughout the column generation process. Initially, a random set of routes is generated, the total distance of which is typically far from the optimal solution. It can be observed that the corresponding reduced cost is negative at the initial iteration. As the iteration progresses, the objective value of the restricted master problem improves, whereas the reduced cost approaches zero. If a new route is not acquired and the reduced cost is negative, the algorithm is terminated. After this iterative process, we solved the original set cover problem to obtain the optimal routes. However, these tentatively good routes may still be problematic owing to the set cover formulation; that is, some of the chosen routes visit the same customers. To resolve this undesirable situation, we finally solve the set partition problem, where the inequality constraint (13) is modified to an equality constraint. Note that the dual solutions in the pricing subproblem determine the order of priority for each customer. This is because customers whose dual-solution value is high can lower their reduced cost if the route contains such customers.
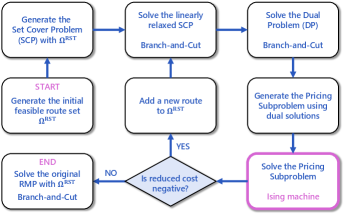
A new route is obtained as an output equivalent to the column of the matrix . Therefore, the sequence of optimization procedures described here is called column generation. Although the pricing subproblem is the shortest path problem with negative weight edges, it entails the capacity constraints (35) and is known to be -hard. One solution to this difficulty is to allow each customer to be visited more than once by modifying the matrix element alleviates this difficulty. Consequently, this modification enables the execution of the column generation in pseudopolynomial time using dynamic programming [42]. With respect to the restricted master problem and the dual problem, we used the COIN-OR branch and cut (CBC) solver offered by an open-source library PuLP to optimize them. An overall flowchart of the column generation method is shown in Figure 4.
In this study, we utilized a GPU-based Ising machine to solve this pricing subproblem, without modifying the matrix element . The next section is devoted to explaining how the pricing subproblem is solved using an Ising machine.
V Methods
In this section, we describe how our annealing-assisted column generation is implemented. As explained earlier, to solve the combinatorial optimization problem, the objective function must be written in either QUBO or the Ising model. The first subsection describes the formulation of the pricing subproblem as a QUBO model. In the second subsection, we explain the solution of the CVRP using only an Ising machine. The preprocessing and postprocessing techniques related to neighborhood searches are presented in the following subsections. Finally, we propose a method in which the generated columns have low similarity to each other, which is realized by fixing binary variables.
V-A Formulation of the Pricing Subproblem as a QUBO Model
The previous section introduced the pricing subproblem expressed in the Equations (34) and (35). Let be a binary variable that takes if the vehicle visits the customer at the th step, and otherwise. Using this binary variable , the QUBO model of the pricing subproblem is as follows:
| (36) | ||||
| (37) | ||||
| (38) | ||||
| (39) | ||||
| (40) | ||||
| (41) | ||||
| (42) |
where is a penalty coefficient and defined as to ensure that the reduced cost term is of the same order of magnitude as for the penalty term. is the maximum number of steps that each vehicle can take and is determined to satisfy . in Eq. (39) is a slack variable. Equations (37) and (38) correspond to the objective function of the pricing subproblem. The terms , , and are equivalent to the penalty terms. stipulates that each customer should be visited at most once. At each time step , the vehicle is assumed to visit only a single customer because of the term . Because only one variable with a value of exists in the same row, these types of constraints are referred to as the one-hot constraints. The capacity constraints of CVRP were converted into equality constraints to adapt the penalty function method in . Here, in (41) is a polynomial used to implement the conversion. Fixstars Amplify Annealing Engine selects with the least number of slack variables from the following three options:
| (43) | ||||
| (44) | ||||
| (45) |
where denotes a slack variable. All these polynomials are used to encode integers, that is, multiple discrete values, using binary variables. Hence, these encoding methods are known as binary-integer encoding [44, 45].
The first polynomial (43) is referred to as unary encoding, and can represent integers through the summation of slack variables that take . The number of slack variables required for this encoding method is equal to . Second, binary encoding, expressed as a polynomial (44), employs binary notation to encode integers. In contrast to unary encoding, binary encoding may include superfluous integers that have a detrimental effect on the inequality constraints. To circumvent this issue, the constant terms are subtracted from the polynomial (44). The number of slack variables required for binary encoding is estimated as . Finally, the polynomial (45) is called linear encoding. Linear encoding utilizes a linear combination of slack variables. The number of slack variables required for the linear encoding is reduced to . Figure 5 shows the number of slack variables required for the three binary-integer encoding techniques. As shown later, we prepared five different problem settings with capacities of , , , , and . Consequently, binary encoding is typically selected for the numerical simulations because it is likely to require the fewest number of slack variables.
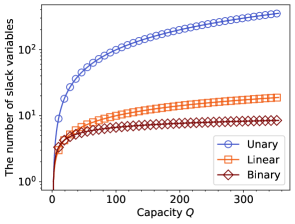
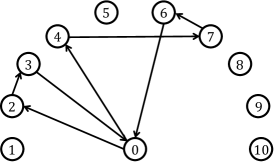
Table I illustrates an example solution when the pricing subproblem is solved. Each row represents the th vehicle movement, and each column corresponds to a depot or the customer. Note that this QUBO table satisfies the aforementioned one-hot constraints. In this case, the route is . This route is illustrated in Figure 6(a).
The present objective is to minimize the total distance traveled by each vehicle; thus, we require routes to comply with the following two rules:
-
1.
The distance matrix satisfies the triangle inequality:
(46) -
2.
Once the vehicle returns to the depot , it cannot depart again.
With regard to these two rules, we have incorporated two postprocessing algorithms into the column generation: the -opt neighborhood search and the triangular modification, which we will discuss in greater detail later. In this study, we refer to this annealing-assisted column generation as CG.
V-B Firsthand QUBO Modeling of CVRP
For comparison, we also applied Ising machines to CVRP naively. The general QUBO model for CVRP is relatively straightforward because we only need to extend the QUBO model (36)–(41) so that it can handle the multiple vehicles. To achieve this, the decision variable must be modified to . Appended index denotes the th vehicle. Using this newly created decision variable, we obtain:
| (47) | ||||
| (48) | ||||
| (49) | ||||
| (50) | ||||
| (51) | ||||
| (52) |
where is the penalty coefficient defined as . The forms of the objective function and constraints are nearly identical to those of the QUBO model written for the pricing subproblem. However, note that does not require slack variables because this QUBO model considers the routes of all the vehicles simultaneously. Hereafter in this paper, we refer to this method as AE.
V-C -Opt Neighborhood Search
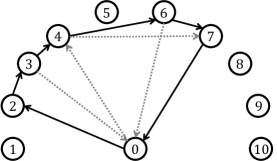
We adopted the -opt neighborhood search for the obtained route in order to take advantage of the rule . As the distance matrix satisfies the triangle inequality, reordering some crossing routes results in a shorter total distance for that route.
Algorithm 1 presents the pseudocode for the -opt neighborhood search. The procedure for the -opt neighborhood search is as follows: First, we select two edges, and from the obtained route. Subsequently, the selected edges are cut, the vertices are swapped, and new edges are created, namely and . If the lengths of the newly generated edges and are shorter than those of the former edge, and , we reconnect and to the route. This sequential process constitutes one iteration of the -opt neighborhood search. This process was repeated until no further improvement was observed. The time complexity of an iteration of this neighborhood search is .
The -opt neighborhood search was applied to CG when the initial set of feasible routes was generated and each time the pricing subproblems were solved. On the other hand, we applied this local search method to AE when the final solution was obtained.
V-D The Triangular Modification
The route obtained from the Table I infringes on the rule . Accordingly, we implemented a triangular modification of the solution as soon as it was generated. This postprocessing method is followed by a -opt neighborhood search. The example route in Figure 6(a) includes subtour where the vehicle returns to the depot and departs from it once again. Because the distance matrix satisfies the triangle inequality, we amended this subpath to which is certainly shorter than the previous one. The time complexity of the postprocessing method is estimated to be . Figure 6(b) shows the modified route. Note that a -opt neighborhood search was also executed.
Just as we apply the -opt neighborhood search to CG, this triangular modification is called when the initial routes are generated and every time the pricing subproblems are solved. In contrast, prior to the -opt neighborhood search, a triangular modification was employed in the event of the final solution acquisition regarding AE.
| / s | / s | ||||||||
|---|---|---|---|---|---|---|---|---|---|
V-E Limited Column Generation
Because the objective function of the pricing subproblem is given by the Equation (34), the customer , whose dual values are large, tends to be chosen to lower the objective value when using column generation. This potentially entraps the entire algorithm in a local optimum. Therefore, we propose fixing some variables in accordance with the following rule: customers in the th iteration of the obtained route must not be visited in the th iteration. More specifically speaking, let be the vertex set of the customers selected at the th iteration. We introduce the variable fixation shown below:
| (53) |
This fixation allows us to explore the solution space globally because the generated columns should have little similarity to each other while simultaneously reducing the number of logical spins. The time complexity of this fixation can be estimated as . Most importantly, the essence of this method is to remove the overlapping of the columns that are to be generated. Consequently, this fixation method can be applied to other optimization problems with inequality constraints if it can be formulated as a set cover problem. We call this method Limited Column Generation (Limited CG). Note that we performed the -opt neighborhood search and triangular modification in the same manner as for CG.
VI Numerical Results
We compared the three different methodologies explained in the last section. To achieve this, we parameterized the difficulty of the inequality constraints by designating the maximum value of demand . Demand for each customer is uniformly generated between closed intervals . Note that when , CVRP is equivalent to a pure VRP because each demand satisfies for all the customers . However, as the value of increases, the demand distribution becomes more complicated, leading to a challenging energy landscape. Furthermore, the location of each customer is generated uniformly within a closed interval .
Table II lists the parameters utilized to execute CG, Limited CG, and AE. in Table II refers to the standard deviation of the demand. The numbers of slack variables employed to express the inequality constraints are denoted by and . The value of corresponds to when CG and Limited CG are executed. The value of is the notation for AE.
We discovered that this number of slack variables results from the use of binary encoding was used to transform an inequality constraint into an equality constraint. Furthermore, note that and have the following relationship based on the difference in the formulation of the QUBO model:
| (54) |
In addition, denotes the timeout for the use of Fixstars Amplify AE in executing CG and Limited CG. is here again the notation for AE. To be sure, we solved the pricing subproblem once again with one second added to the current timeout if a route with a negative reduced cost could not be obtained. The number of this additional explorations was limited to ten times. To ensure fairness, the total computation time of CG and Limited CG was set to s, which was equal to the AE computation time.
VI-A Analysis Based on Difficulty of Inequality Constraints
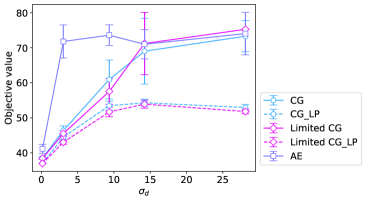
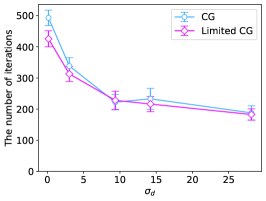
Ten instances of CVRP were solved for each problem setting, as shown in Table II. Figure 7 shows the dependence of the objective values and the number of iterations on . As shown in Figure 7(a), even AE could indeed efficiently solve the problem when is equal to , which is equivalent to a pure VRP in this case. However, CG and Limited CG were observed to be superior to AE when increased to and . When is and , instance problems become excessively challenging to the extent that CG and Limited CG are unable to obtain better solutions than AE. Although the objective values for integer variables between CG and Limited CG were not significantly different from each other, we confirmed that the relaxed objective value acquired by Limited CG was superior to that of CG. This is because Limited CG overcame the issue of CG in which a feasible set of routes was rarely obtained by eliminating the overlap of routes. Figure 7(b) shows the number of iterations that both CG and Limited CG took. There was no discernible enhancement in the speed at which each method reached convergence, whereas Figure 7(b) indicates that Limited CG can achieve better results without wasting further computational resources.
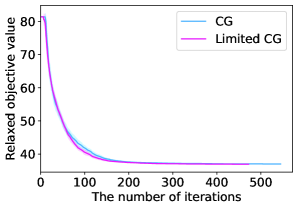
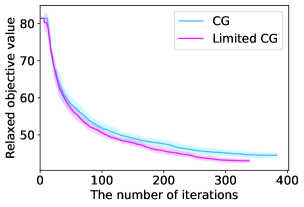
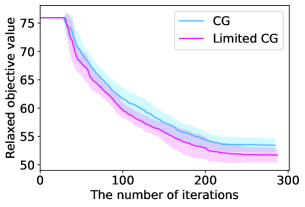
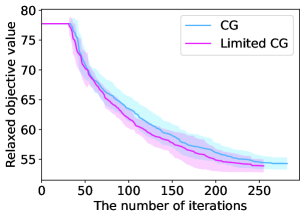
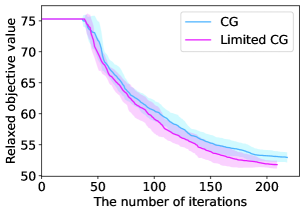
Figure 8 illustrates the time evolution of the objective value for a restricted master problem. When , the two lines almost overlap and we cannot observe the superiority of Limited CG to CG. Nevertheless, as increases, Limited CG can converge to a better lower bound at a faster rate than CG. As previously stated, obtaining a good lower bound is of paramount importance because the objective value gap between the original integer problem and its linear relaxation still exists when is finite.
VI-B The range of effectiveness for CG and Limited CG.
When was within , we confirmed the superiority of annealing-assisted column generation methods (CG and Limited CG) compared to the naive method (AE) in the last subsection. Further investigations were conducted to ascertain whether these annealing-assisted column generation methods were effective in resolving these problems. In this context, we introduce another evaluation factor , which is the average number of customers per vehicle. Table III presents the problem settings for the additional simulations. Owing to the difference in the model formulations, the performance of AE should be strongly affected by . As shown in Table III, the number of slack variables increases for a small whereas remains the same.
| / s | / s | ||||||||
|---|---|---|---|---|---|---|---|---|---|
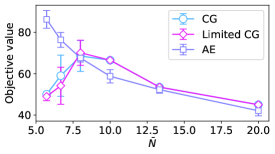
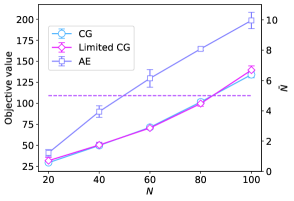
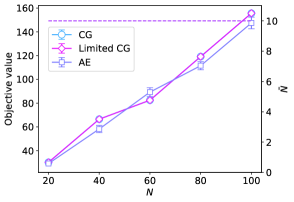
Figure 9 illustrates the dependence of the objective values on . We revealed that CG and Limited CG are effective in regions in which is small. This result does not contradict the finding that problems with many slack variables are difficult to resolve. Conversely, when increases, the superiority of CG and Limited CG will disappears.
We also found that this relationship also applies to when the problem size scales. Figure 10 shows the scalability of each method for two values of . Figure 10(a) shows the case where , while we can see the case where is increased to from Figure 10(b). When and , the three methods were not significantly different because they had similar objective values. This result is corroborated by Equation (20), which indicates that column generation is an effective approach for large . As increases, the difference in the number of slack variables becomes significant. Figure 10(b) shows the case in which is . In this case, the column generation scheme had almost no supremacy over AE because is relatively large, and the effects of the slack variables are diminished. This outcome is also attributable to the postprocessing algorithms’ capacity to function affirmatively for AE, which has led to a significant improvement in the final path length. However, whether the ultimate result is favorable for CG and Limited CG does not highly depend on the postprocessing algorithms, but rather on the number of feasible combinations acquired until the final iteration. As seen earlier, the objective values of Limited CG are not significantly different from those of CG. However, this result indicates that the column generation scheme is powerful enough to solve larger problems under specific conditions, offering a more effective alternative to the conventional naive approach.
VII Conclusion
In this study, we applied an annealing-assisted column generation method to the combinatorial optimization problems with inequality constraints. Such problems are typically challenging due to the hardware limitations of current Ising machines, with the abundance of decision and slack variables often leading to deteriorated final objective values.
Prior studies have addressed this challenge by introducing column generation and accelerating the solution process of the pricing subproblem using Ising machines [22, 23, 24]. Further extending this approach to obtain a better lower bound, we introduced Limited CG, wherein we fixed the decision variables to eliminate the overlap between the generated columns.
Numerical simulations confirm that Limited CG can achieve a more robust lower bound, even as the complexity of each customer’s demand increases. Because finite-size problems are prevalent under practical scenarios, obtaining such a good lower bound is of paramount importance. Additionally, we demonstrate that the average number of customers per vehicle influences the efficacy of the column generation scheme, with annealing-assisted column generation methods proving effective for problems with small , although this effectiveness diminishes as increases.
Because our proposed method overlooks priority determined by dual solutions, future investigations should explore the limitations of overlap elimination. In addition, the effectiveness of our method must be further assessed on benchmark problems. Finally, given the considerable objective value gap between the integer problem and its linear relaxation in finite-size problems, we should develop a method for converting real solutions into integer solutions, ensuring this gap is effectively minimized.
Acknowledgments
The authors wish to express their gratitude to the World Premier International Research Center Initiative (WPI), MEXT, Japan, for their support of the Human Biology-Microbiome-Quantum Research Center (Bio2Q).
References
- [1] N. Mohseni, P. L. McMahon, and T. Byrnes, “Ising Machines as Hardware Solvers of Combinatorial Optimization Problems,” Nature Reviews Physics, vol. 4, no. 6, pp. 363–379, 2022.
- [2] H. Nishimori, Statistical Physics of Spin Glasses and Information Processing: An Introduction. Clarendon Press, 2001, no. 111.
- [3] A. Lucas, “Ising Formulations of Many NP Problems,” Frontiers in physics, vol. 2, p. 74887, 2014.
- [4] S. Tanaka, R. Tamura, and B. K. Chakrabarti, Quantum Spin Glasses, Annealing and Computation. Cambridge University Press, 2017.
- [5] K. Tanahashi, S. Takayanagi, T. Motohashi, and S. Tanaka, “Application of Ising Machines and a Software Development for Ising Machines,” Journal of the Physical Society of Japan, vol. 88, no. 6, p. 061010, 2019.
- [6] W. Lechner, P. Hauke, and P. Zoller, “A Quantum Annealing Architecture with All-to-All Connectivity from Local Interactions,” Science advances, vol. 1, no. 9, p. e1500838, 2015.
- [7] T. Boothby, A. D. King, and A. Roy, “Fast Clique Minor Generation in Chimera Qubit Connectivity Graphs,” vol. 15, no. 1, p. 495–508, jan 2016.
- [8] D. Oku, M. Tawada, S. Tanaka, and N. Togawa, “How to Reduce the Bit-width of an Ising Model by Adding Auxiliary Spins,” IEEE Transactions on Computers, vol. 71, no. 1, pp. 223–234, 2020.
- [9] T. Shirai, S. Tanaka, and N. Togawa, “Guiding Principle for Minor-Embedding in Simulated-Annealing-Based Ising Machines,” IEEE Access, vol. 8, pp. 210 490–210 502, 2020.
- [10] S. Kikuchi, N. Togawa, and S. Tanaka, “Hybrid Optimization Method Using Simulated-Annealing-Based Ising Machine and Quantum Annealer,” Journal of the Physical Society of Japan, vol. 92, no. 12, p. 124002, 2023.
- [11] S. Kikuchi, N. Togawa, and S. Tanaka, “Dynamical Process of a Bit-Width Reduced Ising Model with Simulated Annealing,” IEEE Access, vol. 11, pp. 95 493–95 506, 2023.
- [12] S. Sinno, T. Groß, A. Mott, A. Sahoo, D. Honnalli, S. Thuravakkath, and B. Bhalgamiya, “Performance of Commercial Quantum Annealing Solvers for the Capacitated Vehicle Routing Problem,” 2023.
- [13] G. B. Dantzig and J. H. Ramser, “The Truck Dispatching Problem,” Management Science, vol. 6, no. 1, pp. 80–91, 1959.
- [14] J. Current and M. Marsh, “Multiobjective Transportation Network Design and Routing Problems: Taxonomy and Annotation,” European Journal of Operational Research, vol. 65, no. 1, pp. 4–19, 1993.
- [15] T. Weise, A. Podlich, and C. Gorldt, “Solving Real-World Vehicle Routing Problems with Evolutionary Algorithms,” pp. 29–53, 2009.
- [16] G. Clarke and J. W. Wright, “Scheduling of Vehicles from a Central Depot to a Number of Delivery Points,” Operations Research, vol. 12, no. 4, pp. 568–581, 1964.
- [17] M. L. Fisher and R. Jaikumar, “A Generalized Assignment Heuristic for Vehicle Routing,” Networks, vol. 11, no. 2, pp. 109–124, 1981.
- [18] G. B. Dantzig and P. Wolfe, “The Decomposition Algorithm for Linear Programs,” Econometrica, vol. 29, no. 4, pp. 767–778, 1961.
- [19] P. C. Gilmore and R. E. Gomory, “A Linear Programming Approach to the Cutting-Stock Problem,” Operations Research, vol. 9, no. 6, pp. 849–859, December 1961.
- [20] P. C. Gilmore and R. E. Gomory, “A Linear Programming Approach to the Cutting Stock Problem-Part II,” Operations Research, vol. 11, no. 6, pp. 863–888, 1963.
- [21] P. M. Thompson and H. N. Psaraftis, “Cyclic Transfer Algorithms for Multivehicle Routing and Scheduling Problems,” Operations Research, vol. 41, no. 5, pp. 935–946, 1993.
- [22] J. Ossorio-Castillo and F. Pena-Brage, “Optimization of a Refinery Scheduling Process with Column Generation and a Quantum Annealer,” Optimization and Engineering, vol. 23, no. 3, pp. 1471–1488, 2022.
- [23] W. da Silva Coelho, L. Henriet, and L.-P. Henry, “Quantum Pricing-Based Column-Generation Framework for Hard Combinatorial Problems,” Physical Review A, vol. 107, no. 3, p. 032426, 2023.
- [24] S. Hirama and M. Ohzeki, “Efficient Algorithm for Binary Quadratic Problem by Column Generation and Quantum Annealing,” Journal of the Physical Society of Japan, vol. 92, no. 11, p. 113002, 2023.
- [25] R. Fukasawa, H. Longo, J. Lysgaard, M. P. d. Aragão, M. Reis, E. Uchoa, and R. F. Werneck, “Robust Branch-and-Cut-and-Price for the Capacitated Vehicle Routing Problem,” Mathematical programming, vol. 106, pp. 491–511, 2006.
- [26] S. Feld, C. Roch, T. Gabor, C. Seidel, F. Neukart, I. Galter, W. Mauerer, and C. Linnhoff-Popien, “A Hybrid Solution Method for the Capacitated Vehicle Routing Problem Using a Quantum Annealer,” Frontiers in ICT, vol. 6, 2019.
- [27] H. Irie, G. Wongpaisarnsin, M. Terabe, A. Miki, and S. Taguchi, “Quantum Annealing of Vehicle Routing Problem with Time, State and Capacity,” in Quantum Technology and Optimization Problems: First International Workshop, QTOP 2019, Munich, Germany, March 18, 2019, Proceedings 1. Springer, 2019, pp. 145–156.
- [28] S. Bao, M. Tawada, S. Tanaka, and N. Togawa, “An ising-machine-based solver of vehicle routing problem with balanced pick-up,” IEEE Transactions on Consumer Electronics, vol. 70, no. 1, pp. 445–459, 2024.
- [29] S. Dutta, A. Khanna, A. S. Assoa, H. Paik, D. G. Schlom, Z. Toroczkai, A. Raychowdhury, and S. Datta, “An Ising Hamiltonian Solver Based on Coupled Stochastic Phase-Transition Nano-Oscillators,” Nature Electronics, vol. 4, no. 7, pp. 502–512, 2021.
- [30] T. Kadowaki and H. Nishimori, “Quantum Annealing in the Transverse Ising Model,” Physical Review E, vol. 58, no. 5, p. 5355, 1998.
- [31] S. Kirkpatrick, C. D. Gelatt Jr, and M. P. Vecchi, “Optimization by Simulated Annealing,” Science, vol. 220, no. 4598, pp. 671–680, 1983.
- [32] D. S. Johnson, C. R. Aragon, L. A. McGeoch, and C. Schevon, “Optimization by Simulated Annealing: An Experimental Evaluation; Part I, Graph Partitioning,” Operations research, vol. 37, no. 6, pp. 865–892, 1989.
- [33] Z. Wang, A. Marandi, K. Wen, R. L. Byer, and Y. Yamamoto, “Coherent Ising Machine Based on Degenerate Optical Parametric Oscillators,” Phys. Rev. A, vol. 88, p. 063853, Dec 2013.
- [34] Y. Yamamoto, K. Aihara, T. Leleu, K.-i. Kawarabayashi, S. Kako, M. Fejer, K. Inoue, and H. Takesue, “Coherent Ising Machines—Optical Neural Networks Operating at the Quantum Limit,” npj Quantum Information, vol. 3, no. 1, p. 49, 2017.
- [35] T. Honjo, T. Sonobe, K. Inaba, T. Inagaki, T. Ikuta, Y. Yamada, T. Kazama, K. Enbutsu, T. Umeki, R. Kasahara, K. ichi Kawarabayashi, and H. Takesue, “100,000-Spin Coherent Ising Machine,” Science Advances, vol. 7, no. 40, p. eabh0952, 2021.
- [36] E. Crosson and A. W. Harrow, “Simulated Quantum Annealing Can Be Exponentially Faster than Classical Simulated Annealing,” in 2016 IEEE 57th Annual Symposium on Foundations of Computer Science (FOCS), 2016, pp. 714–723.
- [37] T. Okuyama, M. Hayashi, and M. Yamaoka, “An Ising Computer Based on Simulated Quantum Annealing by Path Integral Monte Carlo Method,” in 2017 IEEE International Conference on Rebooting Computing (ICRC), 2017, pp. 1–6.
- [38] K. Boothby, P. Bunyk, J. Raymond, and A. Roy, “Next-Generation Topology of D-Wave Quantum Processors,” 2020.
- [39] T. K. Ralphs, L. Kopman, W. R. Pulleyblank, and L. E. Trotter, “On the Capacitated Vehicle Routing Problem,” Mathematical programming, vol. 94, pp. 343–359, 2003.
- [40] I. Diarrassouba, “The Separation Problem of Rounded Capacity Inequalities: Some Polynomial Cases,” Discrete Optimization, vol. 23, pp. 33–55, 2017.
- [41] M. Desrochers, J. Desrosiers, and M. Solomon, “A New Optimization Algorithm for the Vehicle Routing Problem with Time Windows,” Operations Research, vol. 40, no. 2, pp. 342–354, 1992.
- [42] J. B. David Simchi-Levi, Xin Chen, The Logic of Logistics Theory, Algorithms, and Applications for Logistics Management, ser. Springer Series in Operations Research. New York, NY: Springer New York, 2014.
- [43] D. Feillet, “A Tutorial on Column Generation and Branch-and-Price for Vehicle Routing Problems,” 4or, vol. 8, no. 4, pp. 407–424, 2010.
- [44] K. Tamura, T. Shirai, H. Katsura, S. Tanaka, and N. Togawa, “Performance Comparison of Typical Binary-Integer Encodings in an Ising Machine,” IEEE Access, vol. 9, pp. 81 032–81 039, 2021.
- [45] J. Chen, T. Stollenwerk, and N. Chancellor, “Performance of Domain-Wall Encoding for Quantum Annealing,” IEEE Transactions on Quantum Engineering, vol. 2, pp. 1–14, 2021.
![[Uncaptioned image]](https://cdn.awesomepapers.org/papers/447d7996-9f6e-4479-b94d-821b67f9b50b/x18.png) |
Hiroshi Kanai received his B. E. degree in Applied Physics and Physico-Informatics from Keio University, Kanagawa, Japan, in 2023. He is currently pursuing a M. Eng. degree in Fundamental Science and Technology at the same university. His research interests include mathematical optimization, quantum annealing, and Ising machines. |
![[Uncaptioned image]](https://cdn.awesomepapers.org/papers/447d7996-9f6e-4479-b94d-821b67f9b50b/yamashita.jpg) |
Masashi Yamashita received his B. E. and M. Eng degrees in Applied Physics and Physico-Informatics from Keio University, Kanagawa, Japan, in 2022 and 2024, respectively. He is currently engaged in product design at Recruit Co., Ltd., Tokyo, Japan. His research interests include mathematical optimization, quantum annealing, Ising machines, and machine learning. |
![[Uncaptioned image]](https://cdn.awesomepapers.org/papers/447d7996-9f6e-4479-b94d-821b67f9b50b/TanahashiKotaro_4x3cm.jpg) |
Kotaro Tanahashi received his M. Eng. degree from Kyoto University, Kyoto, Japan, in 2015. He has experience working as a machine learning engineer at Recruit Co., Ltd., and is working for Turing Inc., Tokyo, Japan. He also serves as a project manager for MITOU Target Program of the Information-Technology Promotion Agency (IPA). His research interests include mathematical optimization, quantum annealing, Ising machines, machine learning, and autonomous driving. |
![[Uncaptioned image]](https://cdn.awesomepapers.org/papers/447d7996-9f6e-4479-b94d-821b67f9b50b/x19.png) |
Shu Tanaka (Member, IEEE) received his B. Sci. degree from the Tokyo Institute of Technology, Tokyo, Japan, in 2003, and his M. Sci. and Ph. D degrees from the University of Tokyo, Tokyo, Japan, in 2005 and 2008, respectively. He is currently an Associate Professor in the Department of Applied Physics and Physico-Informatics, Keio University, a chair of the Keio University Sustainable Quantum Artificial Intelligence Center (KSQAIC), Keio University, and a Core Director at the Human Biology-Microbiome-Quantum Research Center (Bio2Q), Keio University. He is also a visiting associate professor at the Green Computing Systems Research Organization (GCS), Waseda University. His research interests include quantum annealing, Ising machines, quantum computing, statistical mechanics, and materials science. He is a member of the Physical Society of Japan (JPS), and the Information Processing Society of Japan (IPSJ). |