Architectural Design Alternatives based on Cloud/Edge/Fog Computing for Connected Vehicles
Abstract
As vehicles playing an increasingly important role in people’s daily life, requirements on safer and more comfortable driving experience have arisen. Connected vehicles (CVs) can provide enabling technologies to realize these requirements and have attracted widespread attentions from both academia and industry. These requirements ask for a well-designed computing architecture to support the Quality-of-Service (QoS) of CV applications. Computation offloading techniques, such as cloud, edge, and fog computing, can help CVs process computation-intensive and large-scale computing tasks. Additionally, different cloud/edge/fog computing architectures are suitable for supporting different types of CV applications with highly different QoS requirements, which demonstrates the importance of the computing architecture design. However, most of the existing surveys on cloud/edge/fog computing for CVs overlook the computing architecture design, where they (i) only focus on one specific computing architecture and (ii) lack discussions on benefits, research challenges, and system requirements of different architectural alternatives. In this paper, we provide a comprehensive survey on different architectural design alternatives based on cloud/edge/fog computing for CVs. The contributions of this paper are: (i) providing a comprehensive literature survey on existing proposed architectural design alternatives based on cloud/edge/fog computing for CVs, (ii) proposing a new classification of computing architectures based on cloud/edge/fog computing for CVs: computation-aided and computation-enabled architectures, (iii) presenting a holistic comparison among different cloud/edge/fog computing architectures for CVs based on functional requirements of CV systems, including advantages, disadvantages, and research challenges, (iv) presenting a holistic overview on the design of CV systems from both academia and industry perspectives, including activities in industry, functional requirements, service requirements, and design considerations, and (v) proposing several open research issues of designing cloud/edge/fog computing architectures for CVs.
I Introduction
As vehicles playing an increasingly important role in people’s daily life, more requirements, such as higher efficient traffic, safer road, and more comfortable driving experience, have arisen. These requirements may consume a large amount of computation and communication resources. Connected vehicles (CVs), which provide enabling technologies to realize the aforementioned requirements in vehicular networks, have attracted widespread attentions from both academia and industry.
CVs are network attached vehicles that exchange data with the cloud and other network attached devices and servers [1]. CVs use different communication technologies to communicate with the driver, other cars on the road. Vehicle-to-everything (V2X) communications, as shown in Table I, include vehicle-to-vehicle (V2V), vehicle-to-infrastructure (V2I), vehicle-to-cloud (V2C), and vehicle-to-driver (V2D) communications. Traditionally, the automotive industry has been mainly driven by automotive original equipment manufacturers (OEMs) that were capable of producing and maintaining a massive amount of car hardware. However, the trend of CVs will accommodate other types of key players to make it realized, such as governments building roadside infrastructures, telecommunication companies maintaining nation-wide communication infrastructures, and information technology (IT) companies providing various software-based services using a large amount of data. Hence, it is necessary to develop key technologies required to drive the trend in a larger context with such new stakeholders.
| Characteristics | Research Topics | Example Messages | |||||
| V2X | V2V | 1. V2V channel is distinct from the typical cellular channel 2. Antenna heights of both transmitter and receiver are low 3. Both transmitter and receiver are mobile 4. Channel characteristics are influenced by different traffic environments [2, 3] |
|
Cooperative awareness message [10], Broadcast safety message [11, 12], Decentralized environment notification message [13] | |||
| Security and privacy [12, 14, 15, 16, 17, 18] | |||||||
| Testbed & simulation framework [19, 20, 21] | |||||||
| V2I | 1. Data transmission is influenced by Doppler effect [22] 2. Require a large uplink capacity [23] | Channel modelling [24, 25, 26, 27] | Cooperative traffic safety message [28], Edge-assisted service message [29, 30] | ||||
| Security and privacy [30, 31, 32] | |||||||
| Testbed & simulation framework [25] | |||||||
| V2C | 1. High latency 2. Require routing protocols | Scheduling [33, 34] | Cloud-assisted service message [35] | ||||
| Security and privacy [36] | |||||||
| Testbed & simulation framework [37] | |||||||
|
|
Testbed & simulation framework [39] |
|
||||
Therefore, the development of CVs is largely dependent on the information and communication technologies which have fueled a plethora of innovations in various areas, including computing, communication, and caching. Due to the limited on-board battery and computation capacity in vehicles, in order to execute a large number of computations in limited time, offloading power-intensive time-consuming computation tasks to other more powerful servers may significantly improve the performance of many applications of CVs, such as intelligent driving, cruise assist, and high-resolution map creation. Therefore, cloud computing, edge computing, and fog computing are proposed to realize such computation offloading.
| Features | MCC | Edge Computing | Fog Computing | ||||||||||
| MEC | Cloudlet | ||||||||||||
| Firstly Proposed By | Not specific | ETSI | Carnegie Mellon University | Cisco | |||||||||
| Architecture | CVs - cloud | CVs - edge servers | CVs - cloudlet nodes - cloud | CVs - fog nodes - cloud | |||||||||
|
|
|
|
|
|||||||||
| Operation Mode | Standalone | Standalone | Standalone/cooperate with cloud | Cooperate with cloud | |||||||||
| Distance to CVs | Far | Close | Very close | Very close | |||||||||
| Service Coverage | Global | Less global | Local | Local | |||||||||
| Communication Latency | High | Low | Low | Low | |||||||||
| Virtualization Technology | VM & others | VM & others | Only VM | VM & others | |||||||||
| Main Driver | Academia |
|
|
|
|||||||||
|
|
1. Poor mobility support 2. Limited computation & storage capabilities | |||||||||||
|
|
|
|||||||||||
Mobile cloud computing (MCC) which can perform large-scale and computation-intensive computing has been developed over the past decade. Cloud computing is defined as “a model for allowing ubiquitous, convenient, and on-demand network access to a number of configured computing resources (e.g., networks, server, storage, application, and services) that can be rapidly provisioned and released with minimal management effort or service provider interaction” [43]. MCC offers a lot of attractive features, such as parallel processing, virtualized resources, high scalability, and security. Therefore, MCC can not only provide the ability of processing computation-intensive tasks, but also offers low cost infrastructure maintenance [44]. However, nowadays it is predicted that CVs may produce a large amount of data in high speeds such as the camera captured videos for driving assistance, which will make the data dramatically increase to TB/PB levels in seconds [45]. Additionally, a large number of applications of CVs tend to be latency-sensitive and have fast big-data processing with quick response demands. In an intelligent driving scenario, for example, sensors and -D cameras attached to a CV can generate considerably massive data. Thus, the cloud server must complete computing these data and send back highly accurate operating instructions to the CV’s steering system in milliseconds level. However, since in terms of network topology, cloud servers are far away from the CVs, a long latency may be caused by the network congestion or queuing, which may, in the worst case, incurs car accidents.
Multi-access edge computing (MEC) is an efficient solution to address the aforementioned issues, where a lower response delay can be obtained due to the computation is performed close to CVs, instead of being sent to the remote cloud. The concept of MEC is firstly introduced by the European Telecommunications Standards Institute (ETSI) in under the name of Mobile Edge Computing (MEC), where an IT service environment and cloud-computing capabilities can be acquired at the mobile network edges (e.g., the edge of the cellular network) [46, 47]. In , ETSI officially renamed Mobile Edge Computing to Multi-Access Edge Computing “to embrace the challenges in the second phase of work and better reflect non-cellular operators’ requirements” [48]. Thus, the access approaches in MEC become more variant in CV scenarios. For example, a CV can directly offload its collected raw data to a powerful computing unit that is deployed in a nearby small cell base station (BS) or a roadside unit (RSU). In addition, Cloudlet is one of the most typical edge computing platforms, where a cluster of resource-rich computing nodes are placed only one wireless hop away from mobile users (MUs). The computing nodes run multiple virtual machines (VMs) to provide computing services for MUs. “Essentially, a cloudlet resembles a data center in a box: it is self-managing, requiring little more than power, Internet connectivity, and access control for setup. Internally, a cloudlet resembles a cluster of multicore computers, with gigabit internal connectivity and a high-bandwidth wireless local area network (WLAN)” [49]. Because of the network proximity, cloudlet can offer a wireless connection with low latency and high bandwidth between the server and the CV, making it an ideal place for providing location-awareness, latency-intensive, and fast mobility management services and applications.
Fog computing is another potential solution to address the presented issues in MCC. It is first proposed by Cisco in [50]. The definition of fog computing is “a system-level horizontal architecture that distributes resources and services of computing, storage, control, and networking anywhere along the continuum from cloud to Thing” [51]. Fog computing offers several compelling features [52] that are described below. (i) Heterogeneity, fog computing may contain a wide variety of computing nodes such as access points (APs), high-end servers, edge routers, RSUs, and even mobile nodes (e.g., smartphones and CVs). (ii) Geo-distribution and decentralized management, in contrast to cloud computing, fog computing is deployed widely geographical distributed at the edge of networks and manages its computation and storage resources in a decentralized way. (iii) Support for interplaying with the cloud, a cloud server is deployed at the top of the fog layer for deep analytics, where not only delay-intensive applications can be supported at the fog layer, but also computation-intensive and delay-tolerant applications (e.g., Big Data) can be performed at the cloud layer because of its large storage and powerful computing capability. Therefore, unlike MEC, fog computing often serves as a complement to a cloud rather than a substitute (i.e., fog computing “cannot operate in a standalone mode” [53]). In Table II, we present a comparison among different computing paradigms that we introduced above in terms of multiple key features, including architecture, location of computation resources, operation mode, etc.
Existing studies on CVs have proposed several cloud/edge/fog computing architectures based on the special requirements of different services/applications (will be discussed in Section IV). Different cloud/edge/fog computing architectures may be suitable for supporting different types of CV applications with highly different Quality-of-Service (QoS) requirements in terms of latency, computation resources, and storage capacity. Under different architectures, the computing and communication workload for CVs may also vary over time and locations, which poses challenges to capacity planning, resource management of computation nodes, and mobility management of CVs. Thus, a well-designed computing architecture is very important for CV systems.
I-A Existing Surveys and Tutorials
There are several related survey articles that focus on various aspects of cloud/edge/fog computing and CVs. We divide these existing survey papers into three categories: work on (i) MCC/edge/fog computing, (ii) vehicular networks, and (iii) MCC/edge/fog computing for CVs. In Table III, we summarize published surveys on MCC/edge/fog computing. These articles focus on a wide range of issues related to MCC/edge/fog computing, including applications, architectures, computation offloading, taxonomy, security, standardization, communication, caching, resource management, and energy efficiency. However, none of them investigate the MCC/edge/fog computing for CVs. In Table IV, we summarize published surveys on vehicular networks, e.g., vehicular ad-hoc networks (VANETs), which discuss CVs only from the perspective of the communication.
Articles listed in Table V are most related to our work, which discuss several research issues in the MCC/edge/fog computing for CVs. However, (i) the number of published surveys is quite few; (ii) these studies need to investigate more the system architecture design, where they only focus on one specific computing architecture in their whole paper, such as vehicular cloud computing (VCC) or vehicular fog computing (VFC); and (iii) to the best of our knowledge, there is no survey work that compares different architecture alternatives based on cloud/edge/fog computing for CVs or discusses their benefits, research challenges, and system requirements. Therefore, in view of prior survey work, there still lacks a systematic survey article offering comprehensive and concrete discussions on the architectural design alternatives based on cloud/edge/fog computing for CVs, which motivates this work.
| Category | Aspects | Reference | Main Contribution | ||
| MCC/Edge/Fog Computing | MCC | [54] |
|
||
| [55] |
|
||||
| [56, 57] |
|
||||
| [58] |
|
||||
| [59] |
|
||||
| [60] |
|
||||
| [61] |
|
||||
| [62] |
|
||||
| Edge Computing | [63] |
|
|||
| [64] |
|
||||
| [65, 66, 67, 68, 69, 70] |
|
||||
| [71] |
|
||||
| [72] |
|
||||
| [73] |
|
||||
| [74] |
|
||||
| [75] |
|
||||
| [76] |
|
||||
| [77] |
|
||||
| [78] |
|
||||
| [79] |
|
||||
| Fog Computing | [53] |
|
|||
| [80] |
|
||||
| [81] |
|
||||
| [82, 83, 84, 85, 86, 87, 88, 89] |
|
||||
| [90] |
|
||||
| [91, 92, 93] |
|
||||
| [88, 94] |
|
||||
| [95, 96] |
|
||||
| [97] |
|
| Category | Aspects | Reference | Main Contribution | |||
| Vehicular networks | Taxonomy | [98] |
|
|||
|
[99] |
|
||||
| Routing | [100, 101, 102, 103] |
|
||||
|
[104] |
|
||||
| Wireless technologies & protocols | [105, 106] |
|
||||
| [107, 106] |
|
|||||
| [108, 106, 109, 110] |
|
|||||
| Security | [111] |
|
||||
|
[112] |
|
| Category | Aspects | Reference | Main Contribution | ||||
| MCC/Edge/Fog computing for CV |
|
[113, 114, 115] |
|
||||
| Vehicular fog computing | [116] |
|
|||||
| [117] |
|
||||||
| Vehicular applications | [118] |
|
|||||
| [119] |
|
||||||
| [120] |
|
I-B Contribution
In contrast to the above-mentioned surveys, this paper provides a comprehensive survey on different architectural design alternatives based on cloud/edge/fog computing for CVs. The main contributions of this paper are presented as follows:
- •
-
•
Providing a comprehensive literature survey on existing proposed architectural design alternatives based on cloud/edge/fog computing for CVs (Section IV).
-
•
Proposing a new classification of computing architectures based on cloud/edge/fog computing for CVs: computation-aided and computation-enabled architectures (Section IV).
-
•
Presenting a holistic comparison among different cloud/edge/fog computing architectures for CVs based on functional requirements of CV systems, including advantages, disadvantages, and research challenges (Section IV).
-
•
Proposing several open research issues of designing cloud/edge/fog computing architectures for CVs, including other hybrid architectural alternatives, localizing data traffic, mobility support in heterogeneous architectures, and computing resource management (Section V).
I-C Paper Organization
The rest of the paper is organized as follows: In Section II, we first present an overview introduction on the design of CV systems with a brief summary on the activities of the U.S. Department of Transportation on CVs. The main functions of a CV eco-system are also described. In Section III, we summarize the service requirements and design considerations of using cloud/edge/fog computing for CV applications. Existing architectural design alternatives in the literature, i.e., computation-aided computing and computation-enabled computing, are holistically surveyed and compared in Sections IV. Open research issues are discussed in Section V. Finally, we conclude in Section VI. Table VI presents the list of acronyms used in this paper.
| Acronym | Description | ||
| 5G-PPP | 5G Public Private Partnership | ||
| AECC | Automotive Edge Computing Consortium | ||
| AP | Access Point | ||
| ARC-IT |
|
||
| BS | Base Station | ||
| BASN | Body Area Sensor Network | ||
| CV | Connected Vehicle | ||
| CTS | Clear-to-Send | ||
| CSMA/CA | Carrier Sense Multiple Access with Collision Avoidance | ||
| CPU | Central Processing Unit | ||
| C-ITS | Cooperative Intelligent Transport System | ||
| DoS | Denial of Service | ||
| D2D | Device-to-Device | ||
| DSRC | Dedicated Short-range Communication | ||
| ETSI | European Telecommunications Standards Institute | ||
| FCC | Federal Communications Commission | ||
| GPS | Global Positioning System | ||
| HOV | High Occupancy Vehicle | ||
| IT | Information Technology | ||
| IoT | Internet of Things | ||
| IaaS | Infrastructure-as-a-Service | ||
| ITS-G5 |
|
||
| LOS | Line-of-Sight | ||
| LTE | Long-Term Evolution | ||
| MAN | Metropolitan Area Network | ||
| MIMO | Multiple-Input Multiple-Output | ||
| MU | Mobile User | ||
| MCV | Maintenance and Construction Vehicle | ||
| MCC | Mobile Cloud Computing | ||
| MEC | Mobile Edge Computing/Multi-Access Edge Computing | ||
| MAC | Medium Access Control | ||
| OTA | Over-the-Air | ||
| OEM | Original Equipment Manufacturer | ||
| PKI | Public Key Infrastructure | ||
| PaaS | Platform-as-a-Service | ||
| QoS | Quality of Service | ||
| RAN | Radio Access Network | ||
| RSU | Roadside Unit | ||
| RSE | Roadside Equipment | ||
| RTS | Request-to-Send | ||
| RTT | Round-Trip Time | ||
| SCMS | Security Credential Management System | ||
| SDN | Software Defined Network | ||
| SaaS | Software-as-a-Service | ||
| TMC | Transportation Management Center | ||
| TDMA | Time Division Multiple Access | ||
| USDOT | United States Department of Transportation | ||
| V2X | Vehicle-to-everything | ||
| V2V | Vehicle-to-Vehicle | ||
| V2I | Vehicle-to-Infrastructure | ||
| V2C | Vehicle-to-Cloud | ||
| V2D | Vehicle-to-Driver | ||
| VANET | Vehicular ad-hoc Network | ||
| VC | Vehicular Cloud | ||
| VCC | Vehicular Cloud Computing | ||
| VC-MAC | Vehicular Cooperative Media Access Control | ||
| VFC | Vehicular Fog Computing | ||
| VM | Virtual Machine | ||
| WLAN | Wireless Local Area Network | ||
| WiMAX | Worldwide Interoperability for Microwave Access | ||
| WiBro | Wireless Broadband | ||
| WAN | Wide Area Network | ||
| WAVE | Wireless Access in Vehicular Environments |
II CV System Design
Before diving into the computing architectures for CVs, we first give an overview introduction on the design of CV systems. In particular, we first introduce some CV projects initiated by the U.S. government and European Commission. Then, we summarize the functional requirements of a CV eco-system.
The United States and Europe advances on the deployment of CVs are summarized in paper [121]. In particular, the United States Department of Transportation (USDOT) issued a new rule in December 2016 that requires that V2V technologies must be implemented in all the new manufactured light-duty vehicles. Thus, developing standardized messaging technology together with industry can efficiently improve the deployment of CV technologies in the U.S. In addition, the U.S. version of IEEE 802.11p and the dedicated short-range communications (DSRC) are the two alternatives for transmitting data (e.g., vehicle speed, direction, and location) among vehicles using V2V communications. Therefore, V2V-equipped vehicles can identify risks and provide warnings to drivers to avoid imminent crashes. Other activities initiated by USDOT are explained in the following sub-section.
Similarly, the European Commission submitted the European Strategy on Cooperative Intelligent Transport Systems (C-ITS) in November 2016. C-ITS messages will be transmitted for a wide range of services between different vehicles. To support all C-ITS services on the vehicle side, a full hybrid communication mix needs to be on board. Currently, the commission considers a combination of ETSI ITS-G5 (The European Telecommunications Standards Institute, Intelligent Transport Systems operating in the 5 GHz frequency band), the European version of IEEE 802.11p, and existing cellular networks as the promising hybrid communication mix that ensures the best possible support for deploying C-ITS services.
II-A USDOT Activities on CVs
The USDOT initiated many CV projects by interacting with a wide range of stakeholders. One of the projects is the CV pilot projects [122] launched in three different regions in U.S.A. — Wyoming, New York city, and Tampa. The main purpose of this project is to demonstrate how to improve driving safety and comfort by allowing vehicles to communicate with road-side units or centers; those applications may include, but not limited to, pedestrian collision avoidance, early warning of severe weather conditions, traffic flow improvement, and so on111USDOT listed more than one hundred potential connected applications in Architecture Reference for Cooperative and Intelligent Transportation (ARC-IT) website [123] and some of them are the target applications of these pilot projects..
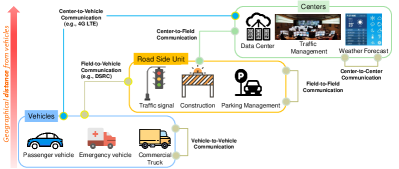
USDOT is developing various open reference system architectures [123] that are specific to implement specific use cases, but the common aspects of those architectures can be summarized as shown in Fig. 1. This high-level architecture illustrates the overview of the CV eco-system that consists of three levels: vehicles, RSUs, and centers. The corresponding communications in such an eco-system include intra-level communications (i.e., V2V communication, field-to-field communication (from one RSU to another), and center-to-center communication) and inter-level communications (i.e., field-to-vehicle communication, center-to-vehicle communication, and center-to-field communication).
Various types of vehicles are considered in this eco-system, such as passengers’ vehicles, emergency vehicles, or trucks that have wireless communication capability. Those vehicles may communicate with the RSUs installed in the close proximity of the vehicles. RSUs are typically equipped with computation units that can perform local computation and wireless communication that allow them to exchange messages with vehicles or other systems. The general role of RSUs is to make a local decision based on the data collected from vehicles or centers, but their specific roles may vary depending on the applications. In New York city pilot project [124], for example, the RSUs are installed in urban intersection areas so that it can monitor pedestrian crossing or approaching vehicles and send warning messages to them; in Wyoming city pilot project [125], the RSUs monitor the hazardous weather or road conditions on the rural highway via on-board sensors and inform any necessary warnings via wireless communications.
Centers are the largest system that can monitor the data gathered from vehicles or RSUs and perform global decisions that can make a broader impact on the overall eco-system. Such a decision may include to control a range of deployed RSUs or to provide generic traffic services to vehicles.
Regarding security, USDOT designs the Security Credential Management System (SCMS) [126] which is a proof-of-concept security solution for CVs. The SCMS is based on Public Key Infrastructure (PKI), and its goal is to ensure integrity, authenticity, and privacy for the communication between CVs, RSUs, and aftermarket safety devices.
II-B Functional Requirements of CV Systems
Now, we briefly explain the five main functions of such a CV eco-system described above.
Data Sharing: Data sharing is when vehicles share their collected data in CV systems. The process of data sharing can be generally divided into three levels: V2V (e.g., in a VANET), V2D (e.g., in a body area sensor network (BASN)), and V2I. Different services may require varying size of collected data. The bandwidth required for data sharing and the throughput of data sharing are different in the three different data sharing levels.
Data Processing: Data processing is when computing units (e.g., the centers, RSUs, and vehicles) process the collected data. For example, in the intelligent driving scenario, collected data from vehicles such as cruising, video, and control data need to be offloaded to a computing unit which then processes these data heavily. Thus, the computing power of computing units constrains what type of services they can support.
Monitoring: Monitoring is when upper-level entities in the system monitor the presence and experience of lower-level entities. For example, the data center monitors the presence and experience of RSUs, or a field element monitors the vehicle presence and experience.
Warning: Warning is when the center, field equipment, or vehicles offer advisories and warnings to drivers, such as current road conditions and predicted weather events.
Control: Control is when upper-level entities in the system send control instructions to lower-level entities. For example, an RSU checks a vehicle’s condition to see if it is suitable for operating on automated lanes based on certain vehicle control parameters (such as speed and headway) that will be used by the vehicle in those lanes, and once confirmed, sends the control parameters to the vehicle.
Note that every function is possibly associated with its required security levels. In USDOT ARC-IT, required security levels of confidentiality, integrity, and availability are provided for physical objects and information flows.
In Table VII, under different example applications of CVs, the requirements of these five functions at different levels of the eco-system as illustrated in Fig. 1 are listed.
| Category | Sub category | Example requirements | ||
| Data Sharing | Center-to-Center |
|
||
| Vehicle-to-Center |
|
|||
| Field-to-Center |
|
|||
| Field-to-Field |
|
|||
| V2V |
|
|||
| Vehicle-to-Field |
|
|||
| Data Processing | Center-level | SU04-10 (Map Management): A center shall use CV location information to refine roadway geometry. | ||
| Field-level |
|
|||
| Vehicle-level |
|
|||
| Personal-device |
|
|||
| Monitoring | Center-level |
|
||
| Vehicle-level |
|
|||
| Field-level |
|
|||
| Warning | Center-level |
|
||
| Field-level |
|
|||
| Vehicle-level |
|
|||
| Control | Center-level |
|
||
| Field-level |
|
III Service Requirements and Design Considerations of Cloud/Edge/Fog Computing for CVs
To realize such a CV eco-system with the five main functions as explained in Section II, different computing architectures can be considered. One alternative is to adopt a cloud-based computing architecture where the centers in Fig. 1 are located in a remote cloud. Another alternative is to consider an edge/fog-based computing architecture to bring the computing capabilities closer to vehicles or field equipment. In this way, the centers in Fig. 1 are distributed at multiple locations in the system. In this section, we first introduce the service requirements in Section III-A, and then the design considerations to realize a cloud/edge/fog computing system for CVs in Section III-B.
III-A Service Requirements
There are a wide range of IoT devices that provide many different types of services. Some may share commonality with CV services, while some are not. The purpose of this subsection is to highlight the unique characteristics of CV services via comparison with a representative IoT device. For this comparison, we chose a smartphone as a comparison peer, because (1) its user base is as wide as the one of vehicles, (2) continuous connectivity is required for most applications, (3) and it has a mobility aspect that a user is expected to receive services while moving. Even though the uniqueness claimed in this section may not be generalized across all other IoT devices beyond smartphones, we believe this gives a good insight as to the major challenges in realizing CV services.
III-A1 Data Generation in vehicular networks
In comparison to smartphones, the amount of data generated from a vehicle is huge in its volume. A high-end vehicle is typically equipped around a hundred sensors or more to monitor correct system operation, and enhance safety and driving comfort. Even though not all raw sensor data need to be transferred to the remote cloud, it is generally expected that each vehicle needs to send at least 20 GB of data per month to the cloud to achieve practical automotive applications according to Automotive Edge Computing Consortium (AECC) [128]; in contrast, in spite of varying statistics, a typical smartphone user consumes around 2 to 5 GB of cellular data these days222These statistics exclude Wi-Fi usages..
In addition, the dataflow pattern of vehicle data is quite different from smartphones. Most smartphones are dedicated for downloading services; that is, the remote cloud server is typically a data producer that creates contents, and sends it to the smartphone, which is a data consumer. Due to this characteristic, many Internet Service Providers assign higher network bandwidth to the downlink services than uplink services. On the other hand, a vehicle is more likely to become a data producer, which generates various raw data, and send it to the cloud for being used by additional services.
III-A2 Response Time
One typical type of the service response time is a duration from the moment a user requests a data or computation to the moment it has been completed or received by the user. Both smartphone and CV services need to meet diverse granularity of timing requirements; for example, real-time multi-user game (smartphone service) or road-side object recognition (CV service) typically need to meet the response time in the order of milliseconds; on the other hand, storage backup application (smartphone service) or HD map generation (CV service) need to meet the response time in the order of seconds or minutes.
However, the consequences of violating such expected response time is significantly different each other, so designing those systems also become different. Many CV services are safety-critical services where delayed response time has a safety impact on drivers or others. For example, a vehicle platooning service that needs to guarantee a constant distance among a group of vehicles may end up crashing each other unless a series of positions of other vehicles do not arrive on time. For this reason, many CV services are typically equipped with a fail-safe mode that is activated when such abnormal condition arises. Hence, the architecture should be designed more robustly to cope with such abnormal delays and to provide sufficient information to activate such a fail-safe mode. On the other hand, most smartphone applications do not have safety implication on the users when the response time is delayed, so the supporting architecture typically do not accompany with such a consideration in place.
III-A3 Availability-Cost Tradeoff
Both smartphone and vehicles may be equipped with various services that require different degrees of network availability depending on their service requirements. Some services require high network availability to provide proper functionalities such as video streaming (smartphone service) or vehicle platooning (CV service). On the other hand, other services may only require intermittent network availability as their local compute unit and storage can support the continuation of the services without continuous network connectivity, such as downloadable standalone games (smartphone service), downloadable navigation map (CV service).
Even though there is an ongoing debate as to the best way to provide connectivity for future vehicles [129, 130, 131], vehicles may be exposed more heterogeneous wireless networks that have different costs and latencies than smartphones while they are moving; a cellular network is typically the only option for a smartphone to maintain the connectivity while it is moving at a similar speed with a vehicle. In United States, some of ongoing V2I services [122] are provided by government via DSRC that allows DSRC-compatible vehicle to freely receive the public services. At the same time, a vehicle is also equipped with a cellular modem that can transfer other types of data via cellular network, which incur costs in most cases. This requires a moving vehicle to make a unique design decision, which does not arise in a moving smartphone, as to when multiple network options are available on the vehicle route, how to schedule the service execution by considering various aspects, such as latency, cost and so on.
III-A4 Data Security and Privacy
Unlike smartphones’ impact resulted from security or privacy attack, the CV service attack has safety implications as those services are linked to safety-critical control applications. For example, a roadway signal infrastructure may broadcast safety messages (e.g., pedestrian positions or speed limits) in intersections for a crash-mitigation service [122]; when the information is compromised by attackers, a vehicle that utilizes the fake information may trigger unexpected control operation resulting in safety issues such as unexpected hard braking due to fake pedestrian crossing information or unexpected speed increase due to fake speed limit.
However, it is also challenging to achieve the necessary degree of security and privacy as it typically negatively affects system performance and convenience. For example, adding strong encryption to all data from cloud or out from vehicles may add extra complexity to the vehicle system design such as latency, extra compute and storage power. Therefore, it is necessary to impose different types of security measure depending on their criticality levels accounting for their interaction with control-related systems. Note that a smartphone also provides multi-level security and privacy measures, but the burden to achieve the required level of security and privacy is mainly imposed to the users by asking more credential (e.g., multi-factor authentication). However, it is not possible for drivers to follow such complex procedure during driving, so it is desirable to perform such procedure more seamlessly.
III-A5 Data Locality and Data Sovereignty
Vehicle data has a higher locality than the one used for smartphone services. Many CV services utilize data that is only consumed in the areas where it is originating, such as positions of other vehicles, semantics of road signs, local HD map information and so on; that is, such data is meaningless in other remote areas irrelevant to the CV services. Therefore, it is not desirable to send all data to remote clouds as it consumes the network and compute resources unnecessarily such as network bandwidth or cloud storage. The system architecture should be able to support the unique characteristics of data locality for CV services so that the infrastructure-wide resources can be efficiently utilized for other non-CV services as well.
In addition, as data is increasingly an important asset to each country, it is necessary to follow the local rules and regulations imposed by each nation. For example, some countries may restrict some type of data to physically stay in their territories depending on how they are used. If a vehicle is used for a certain that falls in such a restrictive category, the data transmission should strictly follow the local regulation. These days, OEMs typically do not have that level of customization as it increases the manufacturing cost significantly. However, this situation will arise as more data is shared with remote cloud or vehicles, so it is necessary to consider a system architecture design to enable data to be transmitted conforming such local regulation via support from either in-vehicle system or infrastructure.
III-B Design Considerations
Given the service requirements described above, the challenges and considerations of cloud/edge/fog computing architectural design for CVs are discussed in this sub-section.
III-B1 Networking
Due to the reason that vehicular connections are usually uncertain and frequently changing in topology, and thus the reliability of vehicular networks is still challenging. At the same time, the bandwidth resources of cellular networks are limited and BSs’ signal cannot extend to all the urban and suburban areas. Therefore, we need to design a heterogeneous vehicular network that combines the best of cellular networks and V2V ad hoc networking. In such a heterogeneous vehicular network, resource sharing and co-scheduling among different networks is still an open issue. A lot of work, currently, has investigated in resource sharing in 5G-enabled vehicular networks [132]. However, so far co-scheduling mechanism design is still lacking for CVs with heterogeneous communication network support[133].
III-B2 Data Sharing in Vehicular Networks
Since co-located vehicles often require shared content, such as navigation or environment recognition, the broadcast nature of V2V communications can improve the performance of content sharing in vehicular networks. However, due to the fact that IEEE 802.11p utilizes the carrier sense multiple access with collision avoidance (CSMA/CA) mechanism, the request-to-send/clear-to-send (RTS/CTS) handshake is disabled in broadcast [29]. Thus, V2V communications are subject to a severe hidden terminal problem that will cause potential collisions at the receivers. Therefore, an efficient medium access control (MAC) mechanism should be designed to avoid such collisions. According to the space-constraint deadlines, the data demands have different urgent levels, even for the same content. Thus, in a certain area, sharing different data contents will have different gains. In order to increase the amount of data transmitted through vehicular networks as much as possible, three issues should be carefully planned: (i) which content to broadcast; (ii) when to broadcast; and (iii) which vehicle to broadcast. Edge servers that know the served vehicles’ content demands and positions, can coordinate transmissions among vehicles to improve the network gain and make sure no collisions among the served vehicles. However, a single edge server cannot realize collision avoidance among vehicles in different locations. Timely and frequent interactions among multiple edge servers should be introduced to avoid such collisions. Furthermore, the frequent control messages among multiple edge servers and served vehicles will incur extra overhead for vehicular networks. Thus, it is necessary for vehicular networks to share contents in a distributive and cooperative manner [29].
III-B3 Application Deployment
Vehicular applications can be deployed in cloud centers, edge/fog nodes, or vehicles. The application deployment depends on factors such as the vehicular network topology, users’ delay tolerance, and the vehicles’ and users’ mobility predictions. In paper [134], the authors focused on application deployment on the rented cloud nodes or the own fog nodes, and proposed a heuristic-based algorithm that tries to make a trade-off between the makespan and the expenditures of cloud nodes. In paper [135], taking the mobility of mobile devices into consideration, an adaptive content reservation scheme, which reserves the resources on the cloud centers and fog nodes for real-time video streaming to mobile devices, is proposed. In paper [136], the authors proposed to develop a new fog that treats the idle devices of game players or organizations as fog nodes, rendering game streaming to the nearby players. Still, it is challenging to consider the mobility of edge/fog nodes in application deployment. On the one hand, both the vehicles and the data sources may move at the same time. On the other hand, it is complex to coordinate the computation and communication systems simultaneously [133].
III-B4 Security and Privacy
Most existing researches focus on the potential attacks or threats in cloud/edge/fog-assisted vehicular applications. Attacks can be generally classified into two types, active attacks and passive attacks. The functionality of a vehicular cloud/edge/fog system cannot be destroyed by passive attacks which only want to eavesdrop the private information. However, the active attacks are more damaging than the passive ones, due to the reason that the active ones attempt to interrupt the operations of the cloud/edge/fog computing systems, or modify the sharing data. Active attacks are usually easy to be detected when it induces huge damages to the vehicular system. However, it is hard to be noticed if the attacks are performed in an inconspicuous manner within a very limited time [117]. Additionally, the attackers generally falls into two categories: insider and external attackers. An insider attacker comes from inside the vehicular system, and are usually equipped with key materials. An internal attacker may induce more potential risks than an external attacker, since the internal attacker knows the existing security control policy and can circumvent it.
Specifically, in paper [137], the authors show that in a connected car environment, a real vehicle and malicious smartphone application can be used to perform a long-range wireless attack. Then, a security protocol for controller area network is proposed as a countermeasure. In paper [138], the authors identify the security challenges that are specific to vehicular clouds (VCs), including authentication of high-mobility vehicles, scalability and single interface, the complexity of establishing trust relationships among multiple players caused by intermittent communications, and tangled identities and locations. A security scheme is proposed to address several of the aforementioned challenges. In paper [139], security issues in service-oriented vehicular networks are elaborated, i.e., minimizing V2I authentication latency and distributed public key revocation. These two security issues are considered as among the most challenging design targets in service-oriented vehicular networks. Accordingly, a fast V2I authentication based vehicle mobility prediction scheme and an infrastructure-based short-time certificated management scheme are proposed to address the aforementioned two challenges. In paper [117], the authors discuss several key security and forensic challenges and their potential solutions. A secure VFC implementation should provide multiple baseline security and forensic properties, including confidentiality, integrity, authentication, access control, non-repudiation, availability, reliability, and forensics. Most of the security requirements can be achieved by cryptographic techniques. Moreover, the authors investigate the compromise attack and selfish attacks, and their potential countermeasures. In paper [72], the authors holistically analyze the mechanisms, challenges, and security threats existing in all edge scenarios, while highlighting the collaboration and synergies among them. In paper [140], the authors consider the security and privacy aspects of CVs, including security of communication links, data validity, security of devices, identity and liability, access control and privacy issues.
IV Cloud/Edge/Fog Computing Architectures for CVs
| Sub-Category | Design Consideration | Reference | Proposed Solution | ||||
|---|---|---|---|---|---|---|---|
| Centralized | Data | [141] |
|
||||
| [142] |
|
||||||
| [143] |
|
||||||
| Application | [141] |
|
|||||
| [142] |
|
||||||
| [143] |
|
||||||
| Communication | [143] |
|
|||||
| [132] |
|
||||||
| [144] |
|
||||||
| [145] |
|
||||||
| [146] |
|
||||||
| Computation & Storage | [132] |
|
|||||
| [147] |
|
||||||
| Security | [141] |
|
|||||
| [142] |
|
||||||
| Hybrid | Data | [148, 149] |
|
||||
| [150] |
|
||||||
| [151] |
|
||||||
| Application | [148, 149] |
|
|||||
| [150] |
|
||||||
| [151] |
|
||||||
| Communication | [148, 149] |
|
|||||
| [152] |
|
||||||
| Computation & Storage | [153] |
|
|||||
| Interaction | [148] |
|
|||||
| Security | [154, 155, 156] |
|
|||||
| [157] |
|
||||||
| [158] |
|
||||||
| [159] |
|
||||||
| [160] |
|
| Sub-Category | Design Consideration | Reference | Proposed Solution | ||
|---|---|---|---|---|---|
| Distributed | Application | [161] |
|
||
| [162] |
|
||||
| [163] |
|
||||
| Formation | [163] |
|
|||
| [164] |
|
||||
| [165] |
|
||||
| [166, 162] |
|
||||
| Communication | [163] |
|
|||
| [165] |
|
||||
| [167] |
|
||||
| [168] |
|
||||
| Computation & Storage | [162] |
|
|||
| [169] |
|
||||
| Security | [113] |
|
|||
| Hybrid | Application | [170, 45] |
|
||
| [171] |
|
||||
| [115] |
|
||||
| [172] |
|
||||
| Communication | [173] |
|
|||
| Computation & Storage | [172] |
|
|||
| Interaction | [174] |
|
|||
| [175, 120] |
|
||||
| Security | [176] |
|
| Category | Sub | On-Board | External | Reference | Proposed Architecture | ||||
| Category | Computation | Computation | |||||||
| Computation-aided | Centralized | Disabled | Enabled | [141] |
|
||||
| [142] |
|
||||||||
| [143] |
|
||||||||
| Hybrid | Disabled | Enabled | [148] |
|
|||||
| [149] |
|
||||||||
| [150] |
|
||||||||
| [153, 177] |
|
||||||||
| Computation-enabled | Distributed | Enabled | Disabled | [163, 164, 165] |
|
||||
| [178, 166] |
|
||||||||
| Hybrid | Enabled | Enabled | [170, 171, 115, 172, 174] |
|
|||||
| [175, 120] |
|
||||||||
| [173] |
|
In this section, we survey the existing proposed computing architectural alternatives for CVs. They can be broadly classified into two categories: computation-aided computing architecture, where CVs only generate computing tasks and do not possess the computation ability, and computation-enabled computing architecture, where CVs not only generate computing tasks but obtain computation capabilities.
In computation-aided computing architectures, external infrastructures (e.g., the cloud server, edge servers, and fog servers) are the only computation resources for CVs that are sources of data. Several non-negligible design considerations for computation-aided computing architectures are briefly described as follows:
-
•
Data: What kind of data might be generated or collected from the CVs (e.g., driver status, road traffic, weather information, etc.)?
-
•
Application: What kind of services or applications are provided by the cloud, edge, and fog servers (e.g., customized CV services, intelligent transportation, surveillance, etc.), which is crucial because different services or applications may have completely different requirements (e.g., latency-sensitive, requiring a large amount of collected data, computation-intensive, etc.)?
-
•
Communication: How to enable efficient data transmissions between CVs and external infrastructures due to the limited network resources (e.g., deploying advanced communication technologies, enabling V2V or cooperative-relay transmission, deploying smart path selection or routing strategies, etc.)?
-
•
Computation & Storage: How to manage the computation and storage resources of the external infrastructures?
-
•
Interaction: How the cloud, edge, and fog servers interact and coordinate with each other?
-
•
Security: How can security and privacy be ensured in computation-aided computing architectures?
In computation-enabled computing architectures, CVs might be not only the sources of data but also the sources of computation. Besides external infrastructures, the idle computation resources on each CV can be shared with other CVs. Thus, VCC/VFC is a key component in computation-enabled computing architectures, where “a group of largely autonomous vehicles whose corporate computing, sensing, communication and physical resources can be coordinated and dynamically allocated to authorized users” [113, 138]. Several non-negligible design considerations for computation-enabled computing architectures are briefly described as follows:
-
•
Data: What kind of data might be generated or collected from the CVs?
-
•
Application: What kind of services or applications are provided by the VCC/VFC and external infrastructures?
-
•
Formation: What are the possible VCC/VFC formation scenarios?
-
•
Communication: How to enable efficient data transmissions between (i) CVs within the same VCC/VFC, (ii) CVs in different VCCs/VFCs, and (iii) VCC/VFC and external infrastructures?
-
•
Computation & Storage: How to manage the computation and storage resources of the VCC/VFC?
-
•
Interaction: How the VCC/VFC interacts and coordinates with the external infrastructures?
-
•
Security: How can security and privacy be ensured in computation-enabled computing architectures?
Note that not all of the aforementioned design considerations are taken into account in each existing work. Table VIII and IX present brief summaries of the state-of-the-art solutions of design considerations for both computation-aided and -enabled computing architectures.
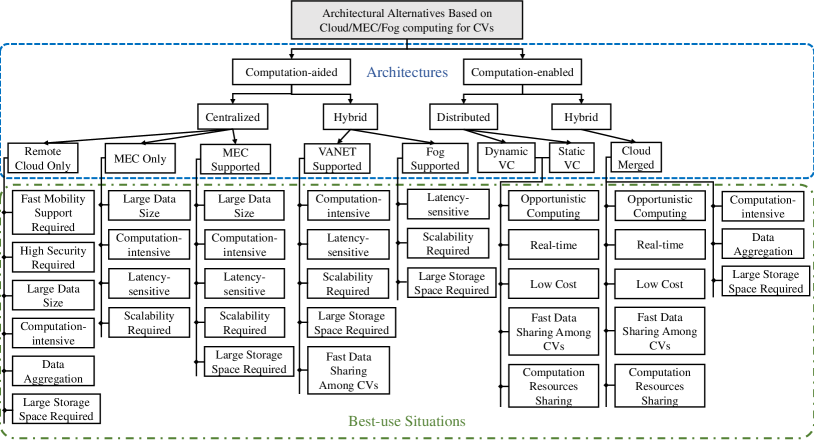
Under each category, computing architectures can be further divided into centralized, distributed, and hybrid architectures based on the distribution of the computation resources. In centralized computing architectures, computing and storage resources are organized in a remote centralized server. Centralized architectures may also have hierarchical computing where computing and storage resources are organized in a hierarchical structure from the edge of networks to the remote center. In distributed computing architectures, computing resources are distributed in a number of individual units without the support of a centralized controller. Hybrid computing architectures combine centralized and distributed computing architectures. Fig. 2 and Table X present a taxonomy and a comparison of computing architectural design alternatives for CVs, respectively, which will be discussed in detail in the following sections.
IV-A Computation-aided Computing Architectures
The computing architectures considered in papers [141, 142, 143, 179, 180, 181, 144, 182, 132, 183, 145, 147, 146, 184, 149, 148, 150, 185, 153, 151, 186, 187, 188, 189, 152, 190, 177, 23, 154, 155, 159, 157, 158, 156, 191, 192, 193] for supporting CVs are computation-aided architectures, where CVs only generate computing tasks (i.e., CVs are considered as computation sources only), leaving task computation to external units, such as nearby edge nodes (e.g., WiFi routers, small-cell BSs, and macro-cell BSs) or cloud servers, which depends on the service requirements on the computation load. Since CVs in computation-aided computing architectures do not possess the computation ability, their generated tasks must be offloaded to external computing infrastructures. Therefore, distributed architectures, under which CVs usually compute their generated tasks utilizing their own on-board or other nearby vehicle clusters’ computation resources, will not be discussed in this subsection.
IV-A1 Centralized Architecture [141, 142, 143, 179, 180, 181, 144, 182, 132, 183, 145, 147, 146, 184]
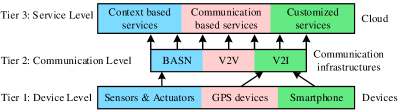
Paper [141] proposed a three-layer VC architecture from the perspective of communication support. This architecture is composed of the device level, communication level, and service level, as shown in Fig. 3. At the device level, various devices ranging from sensors, actuators, Global Positioning System (GPS) devices, and smartphones are used for collecting data such as temperature, pressure, image, and driver’s bio-medical information. Then, these collected raw data are stored in a repository and wait for further processing at the upper level. Based on the pre-processing techniques, those stored raw data can be classified into high-level context (such as human activity and gesture) and low-level context (such as pressure and temperature). The communication level is divided into in-car communication modules (e.g., BASNs), V2V communication modules, and V2I communication modules (e.g., satellite and cellular networks). The service level includes various services such as context-based services (e.g., driver status monitoring), communication-based services (e.g., road traffic monitoring, weather information, and Internet access), and customized services (e.g., parking, health-care, and dining booking). Context-based services are given charge of tasks that include drivers’ health and safety improvements, while tasks like drivers’ convenience and comfort degree improvements are allocated to communication-based services. As stated above, this proposed three-tier architecture collects a wide variety of data on the device level. Thus, customized CV services that require various data and high accuracy are suitable for being executed in this architecture.
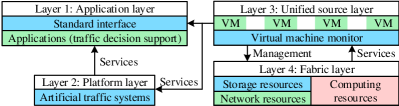
In paper [142], a four-layer agent-based intelligent traffic cloud architecture from the perspective of computation support is proposed. This proposed architecture mainly focuses on the scenario of intelligent transportation systems and aims to handle a large amount of computing and storage resources that are required to use traffic strategy agents and massive transport data. It includes the application layer, platform layer, unified source layer, and fabric layer. The application layer shown in Fig. 4, contains all the applications that run in the clouds, including agent management, generation, optimization, testing, traffic decision support, and agent-oriented task decomposition. Customers can obtain the services that they need through a pre-defined standard interface. The platform layer is made of artificial transportation systems, providing platform as a service. Components such as weather simulator, population synthesizer, D game engine, and path planner are contained in this layer and provide services to the traffic applications in the upper application layer. The unified source layer maintains the hardware resources in the lower fabric layer and provides infrastructure as a service. In the unified source layer, VMs are utilized to protect users’ data and equipment safety. In addition, a unified access interface is established for the upper distribute computing resources. These features described above can help the intelligent transportation system efficiently mine useful knowledge from the massive urban traffic data. Furthermore, hardware-level resources (e.g., storage, network, and computing resources) are contained in the fabric layer, which will help the intelligent traffic cloud supply the peak demand of urban-traffic management systems. CV services with requirements such as large data size, high security, multiple users, latency-insensitive, and high computing power are recommended for using this four-layer architecture.
As stated above, one of the advantages of centralized cloud architectures is data aggregation. By using the cloud storage techniques, the cloud can provide a variety of stored data for the private and government agencies (e.g., department of transportation, the meteorology department) to perform various studies. Therefore, several papers described various studies in vehicular systems based on centralized cloud computing architectures. For example, paper [143] proposed a metropolitan air quality monitoring service. In this service, vehicles act as the air quality data gathering sensors under a similar architecture described above. Vehicles offload their gathered data to a remote centralized cloud for performing an air quality estimation. The main contribution of this paper is the investigation of the trade-off between monitoring accuracy and data offloading overhead, where dynamic grid partition and probabilistic reporting approaches are proposed to adjust data sampling rate and avoid redundant data.
However, with the development of the latency-critical and computation-intensive applications in CVs, centralized architectures with a remote cloud server described above are not efficient. Therefore, architectures of CV networks with MEC are proposed, where besides a centralized cloud server, additional computing infrastructures (e.g., RSUs, BSs, and/or edge/fog servers) are also given the role of computing units, forming a hierarchical computing architecture. The main objective of MEC is to extend the cloud computing functionality to the edge of networks, which saves network bandwidth and reduces the communication latency. For example, several papers [181, 132, 184] proposed to utilize 5G and MEC together to help CVs improve task transmission efficiency. Among these papers, paper [132] proposed a paradigm of G-enabled vehicular networks to improve the network capacity. The cloud server is extended by integrating geographically distributed cloudlets that are responsible for local services. In addition, the matrix game theoretical approach is exploited to operate the resource sharing and allocation among cloudlets.
In addition, other variations of hierarchical computing architectures for CVs were also proposed. Paper [144] proposed a cloud-based MEC offloading framework in vehicular networks. Considering the time consumption of the computation task execution and the mobility of the vehicles, data are adaptively offloaded to the MEC servers through a direct uploading mode, i.e., V2I, or a predictive relay mode, i.e., V2V. Furthermore, the proposed framework does not have a remote core cloud server and all computing tasks are offloaded to different MEC servers, which reduces the transmission cost and the latency of the computation offloading. However, since MEC servers are deployed at the edge of networks, e.g., RSUs, their computation capacities, storage, and service ranges are limited. Thus, applications require high computation resource, a large amount of feed data, and constant offloading environment with fast mobility may be seriously restricted by this proposed framework. In papers [145, 147], fog servers are proposed to co-locate with BSs, forming a BS-fog node. However, all of these proposed architectures face a common challenge – mobility management issue. In order to mitigate the impact of mobility, paper [146] proposed a mobility prediction mechanism where RSUs exploit mobility predictions to decide which data they should fetch from the Internet and to schedule the further transmission to vehicles.
IV-A2 Hybrid Architecture [149, 148, 150, 185, 153, 151, 186, 187, 188, 189, 152, 190, 177, 23, 154, 155, 159, 157, 158, 156]
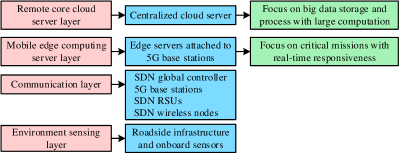
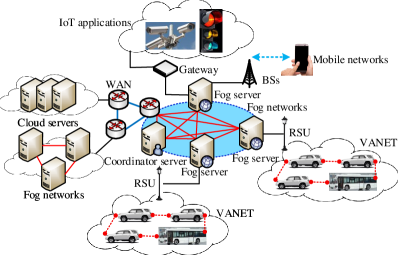
Papers [149, 148] proposed a four-layer architecture for urban traffic management with the convergence of G networks, VANETs, MEC, and SDNs technologies, as shown in Fig. 5. It contains the environment sensing layer (e.g., traffic data are derived from the roadside infrastructure and on-board sensors), communication layer, including SDN global controller, 5G BSs, SDN RSUs, and SDN wireless nodes (e.g., vehicles), MEC server layer (MEC servers are deployed in 5G BSs), and remote core cloud server layer. The communication layer with two emerging network paradigms, 5G and SDN, provides several advantages. First, since the data and control planes are separated, forwarding policies can be exploited to balance the traffic flows, and provide a more flexible path selection strategy with the network’s programmability. Second, in order to support different approaches of communication, several wireless modules are deployed on vehicles. Thus, the SDN-based communication layer can provide a path selection strategy based on the cognitive radio and channel allocation policy, which may reduce the communication latency and increase the communication bandwidth in CV networks. Thus, the channel and frequency selection in CV networks can be more flexible. Third, the 5G cellular network with multiple-input multiple-output (MIMO), wide spectrum, and ultra-dense network technologies can achieve Gb/s data rate in a mobile environment, where a vehicle is at the speed of km/h, based on 28 GHz spectrum [149]. Fourth, because the current cellular network is designed for mobile broadband traffic, it lacks support for V2V communications. Although IEEE 802.11p is proposed for V2V communications, its limited bandwidth and peak data rate (i.e., up to 27 Mbps [108, 107]) might not satisfy the diverse requirements of vehicular applications [194]. The 5G Public Private Partnership (5G-PPP) proposed device-to-device (D2D) communications that data can be directly exchanged among mobile users by bypassing infrastructure within 1 ms delay [195], which demonstrates that 5G is a promising approach for V2V communications. In addition, paper [194] presents three salient features of 5G-enabled communications in vehicular scenarios, including proximity service, integration of MEC, and network slicing. For example, (i) proximity service provides a solid foundation for vehicular safety communications and identifies the source of autonomous vehicle attacks; (ii) MEC plays a fundamental role in 5G [63], which can improve the user experience of vehicular applications such as the traffic information system that have flexible latency requirements; and (iii) variant network slices can be designated based on the diverse requirements of vehicular applications, which simplifies the design of vehicular systems. Compared with the centralized cloud computing architecture, mobile edge servers are deployed closer to end users in this architecture. Thus, it reduces the delay of data offloading and is suitable for implementing latency-sensitive applications. A rapid road accident rescue system, for instance, can be built under this architecture with the support of the low-latency and high-bandwidth SDN-based heterogeneous network and the fast-response MEC server.
Paper [150] proposed a three-layer hybrid computing architecture, including the micro layer (vehicles and users), meso layer (transmission), and macro layer (cloud services). However, the vehicular cluster under this architecture only performs the function of sharing data, e.g., entertainment resources and traffic accident information among vehicles in this cluster, instead of providing computing services. Papers [153, 177] introduced a new concept, fog computing, into the cloud computing architecture for CVs, where a cooperative fog architecture, shown in Fig. 6, is proposed. The cooperative fog architecture mainly contains two layers: edge layer and fog layer. The edge layer may include the components such as VANETs (i.e., a VANET can be applied for V2V communications and traffic information broadcasting), IoT (i.e., lots of IoT application are widely used in city transportation systems such as video traffic surveillance systems, range finders, and wireless sensors), and mobile cellular networks. The fog layer is a federation of geographically distributed local fog servers and may include entities such as fog servers (i.e., the long data transmission latency between CVs and the cloud server can be reduced via offloading the computation and data in the edge layer to local fog servers), access control routers (i.e., they are responsible for controlling or migrating the input data flow), cloud server (i.e., it is deployed out of the fog layer and has strong computation and storage capacity), and coordinator server (i.e., it is responsible for the federation and autonomy of fog networks). Four potential functions might be achieved in this architecture: mobility control, multi-source data acquisition, distributed computation and storage, and multi-path data transmission. Additionally, a flexible hierarchical resource management methodology that includes Intra-fog and Inter-fog resource management is designed for reducing the system maintenance cost and improving the QoS in areas with high population density. Paper [152] proposed a hybrid architecture that offloads the vehicular communication traffic in cellular networks to V2V paths based on the SDN. A centralized V2V path selection approach, a lifetime-based network state routing algorithm, is developed based on the SDN inside the MEC architecture, where each CV reports its location, speed, direction, and IDs of the neighboring vehicles to a context database implemented in the MEC server. The proposed approach can not only find the V2V routing path that has the longest life time but also recover a broken V2V.
Several papers proposed multiple CV services in hybrid architectures. For instance, paper [151] described a photo surveillance service, named Pics-on-Wheels, that a group of vehicles in a certain area are selected to take camera images of a required urban landscape based on the requirements of a customer. CVs that participate in this service should periodically offload their GPS location to the cloud manager. The customer who requests the service has to send a message containing the time and location to the centralized cloud manager first. Then, the cloud manager will search for available vehicles in the requested time and location by using the best vehicle selection algorithm proposed in this paper. This service can assist with forensic purpose where an accident occurred.
The security and privacy issues in computation-aided hybrid architectures can be divided into two categories, VANET and V2I. As we presented, the VANET is one of key components of computation-aided hybrid architectures. Thus, it is crucial to meet the critical security requirements of VANETs for designing computation-aided hybrid architectures. Firstly, one of the most prevalent security issues is how to maintain the availability of each V2V connection in VANETs, where Denial of Service (DoS) is considered as one of the potential attacks that may affect VANETs [196]. Several possible solutions for the DoS attack is discussed in paper [157]. Secondly, in order to secure the integrity and ensure the reliability of applications trust must be developed among vehicles in VANETs. In paper [158], a fuzzy trust model is proposed to secure vehicles to receive correct and credible information from surrounding vehicles. A series of security checks is conduct by the proposed trust model to ensure the correctness of the received information. Lastly, papers [154, 155, 156, 197] jointly investigates the reputation management and privacy protection in VANETs, where reputation management is responsible for rewarding the complying vehicles and punishing the misbehaving ones. A joint privacy and reputation assurance scheme is proposed to reconcile the requirement conflicts of the privacy protection and the reputation management in VANETs. In paper [154], edge servers are adopted to perform local reputation management tasks for vehicles, while, in papers [155, 156], vehicles’ reputation values are updated by themselves. Thus, the solution proposed in paper [154] is said to provide more reliable reputation manifestation and more accurate reputation update than the other two solutions.
Furthermore, V2I is also considered as an important component of computation-aided hybrid architectures, where V2I communication enables vehicles to access services from the cloud/edge/fog computing infrastructures. Preservation of the confidentiality in the V2I communication is one of the most important security requirements. Paper [31] proposes a secure and efficient mutual authentication and key agreement scheme for V2I communications to defend against the RSU replication attack and to prevent all entities from eavesdropping. Paper [159] investigates security challenges in wireless communications between CVs and RSUs and proposed a protocol which enables CVs to download data securely from RSU with privacy preservation in VANETs. In addition to that, a smart security framework for VANETs equipped with edge computing nodes is proposed in paper [160] to provide secure V2V and V2I communications by using the Quotient filter which is a probabilistic data structure.
IV-B Computation-enabled Computing Architectures
The architectures considered in papers [163, 168, 198, 165, 178, 199, 166, 200, 201, 202, 203, 204, 164, 205, 113, 206, 207, 171, 115, 208, 172, 117, 133, 174, 29, 209, 210, 175, 120, 176, 162, 161, 169] for supporting CVs are computation-enabled architectures, where CVs not only generate computing tasks, but have computation capabilities. In other words, tasks generated by CVs will be computed by themselves, other nearby vehicle clusters, or with the cooperation of remote clouds. Thus, centralized architectures, under which CVs offload their tasks directly to the remote cloud, will not be discussed in this subsection.
IV-B1 Distributed Architecture [163, 168, 198, 165, 178, 199, 166, 200, 201, 202, 203, 204, 164, 205, 113, 206, 207, 162, 161, 169]
VC is new technological shifting, where a cluster of vehicles are in the role of corporate computing, sensing, communication, and data sharing units. In other words, “a group of CVs whose physical resources can be coordinated and dynamically allocated to authorized users” [161]. Since every CV can be a computing unit, we consider VC as distributed computing. There are three major objectives of VC: (i) it provides low-cost computational services to the authorized users (e.g., vehicle drivers); (ii) it helps minimize road traffic congestion, travel time and accidents; (iii) it offers real-time and low energy consumption services of software, platform, and infrastructure with QoS to drivers. Architectures of VC can be classified into two categories, dynamic VC and static VC.
Regarding dynamic VC, papers [163, 165, 202, 203, 164] proposed a distributed computing architecture that provides computation services in dynamic vehicular environments via managing the idle computational resources on each vehicle and utilizing them efficiently. This proposed architecture contains three types of vehicles named requesters, processors, and forwarders. Vehicles that generate jobs are requesters, while others that are responsible for processing these jobs are processors. Forwarders are responsible for relaying the generated jobs to nearby available processors. In addition, a vehicle may be a processor for one job and also be a requester for another job that it does not have sufficient capacity to process. Paper [168] investigated a VC service, content-based routing, that allows VC applications to store, share, and search data within the cloud. Regarding static VC, papers [178, 166, 162, 169] proposed a static architecture of VC to augment the computation and storage power of fog computing. Under this static VC architecture, a pool of smart vehicles parked at a shopping mall, or parked vehicles on the roadside are composed of a computing cloud. In addition, paper [198] investigated the service migration issue among different VCs.
However, the network capacity is considerably limited in a vehicular environment, which may significantly constraint the data sharing and cooperations among vehicles in VC scenarios. In paper [163], a VC framework that focuses on processor discovery and job scheduling is proposed to decrease the job transmission and processing latency and improve the total utility. The proposed framework consists of three submodules: a job queue module, a resource management module, and a scheduling module. The job queue module is responsible for caching jobs in a CV, which avoids channel contention caused by multiple simultaneous job transmissions. The resource management module controls the available on-board computation resources of a CV, while the scheduling module is responsible for communicating with other CVs, determining the job assignment, offloading jobs and receiving feedbacks. In addition to that, a MAC layer protocol named Vehicular Cooperative Media Access Control is proposed in paper [167] to improve the network throughput and decrease the channel collision.
Compared to security systems in traditional clouds that are not associated with vehicles, security systems in VCs face more complicated challenges. In the VC scenario, it is difficult to locate an attacker because it is physically moving with a high speed, which may cause several security issues, such as secure location and localization, authentication, data security, and VC access control [113]. In addition to that, attackers in VCs can pretend to be both computation providers and requesters, which increases the complexity of designing a secure scheme to identify the attackers in VCs. Furthermore, security schemes for VCs must be capable of overcoming a dynamically changing number of vehicles [138], where the number of vehicles in a CV may dynamically change due to the traffic volume, time, terrain, etc. Lastly, security issues in VCs includes security of both networks (e.g., VANET, V2V, V2I, etc.) and cloud computing. Although some security approaches for vehicular networks are applicable in VCs, few specific solutions are developed for VCs. Therefore, in order to make the VC become reality, the challenges of assuring trust and security in VCs need to be addressed [161]. However, to the best of our knowledge, few of existing work investigate the security challenges presented above.
IV-B2 Hybrid Architecture [170, 171, 115, 208, 172, 117, 133, 174, 29, 209, 210, 175, 173, 120, 45, 176]
Papers [170, 171, 115, 208, 172, 174, 173, 209, 176] propose to merge VCs with cloud computing to form a hybrid computing architecture, as shown in Fig. 7, where RSUs act as gateways for VCs to access the centralized cloud. High-speed wired communications can be used for connecting RSUs with the centralized cloud. VCs are further divided into two cases, moving VCs (i.e., a cluster of vehicles on the road) and static VCs (i.e., a cluster of vehicles in a parking lot). For example, some vehicles may need specific applications that require a large number of computing resources or storage space. Therefore, vehicles that have unused storage space can share their computing resources or storage space as a cloud-based service. In addition, in a VC, vehicles can be either the service providers to enrich existing cloud services by providing various on-road information or be the service consumers to enjoy existing centralized cloud services. Therefore, a user can acquire cloud services from either the centralized cloud or the distributed VCs. In papers [175, 120], the proposed architecture consists of two hierarchies, permanent cloud, e.g., a powerful and stationary server, and temporary clouds, e.g., vehicles and drivers’ devices. In the permanent cloud, three different types of services (i.e., infrastructure-as-a-service (IaaS), platform-as-a-service (PaaS), and software-as-a-service (SaaS)) are provided for CVs. The permanent cloud has powerful and stationary computing and storage capacities and can provide computing, storage, and network resources to the CV system entities. While in temporary clouds, CVs, vehicles’ on-board modules, and the drivers’ devices are temporarily integrated together to expand the computing capacity. However, this architecture does not meet some requirements such as scalable, reliable, and secure in a large-scale deployment, especially considering vehicle mobility and dynamic participation of mobile computing resources.
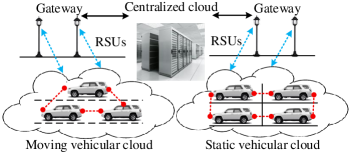
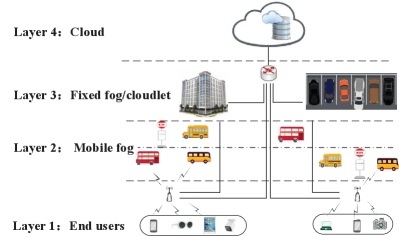
In addition, paper [173] proposed a four-layer hybrid architecture which consists of end users, mobile buses, public infrastructures, and remote cloud, as shown in Fig. 8. Each layer differentiates each other from communication capacity, computation capability, and their inherent properties (e.g., buses have mobility). There is an AP near each bus station, and it serves as the gateway from the users to different kinds of computing resources via the corresponding network interfaces. When a task arrives, users will transmit the task directly to the nearby AP via the wireless network. Then, the collected tasks by the AP can be further offloaded to the mobile fog (i.e., buses in the figure), the fixed fog/cloudlet, or the cloud. The user layer includes people who wear intelligent devices such as smartphones or intelligent glasses, as well as sensor devices such as roadside cameras. They will generate tasks and may not have enough computation resources to execute these tasks. End users may connect to the APs near the bus stations using different network access technologies. The mobile fog layer is formed by a large number of mobile buses that are routinely driving in the city. When buses stop at a station or pass through a station, they will connect to the APs using the millimeter wave technology, offloading tasks from APs. Since these mobile fog nodes are usually located close to end users, they can achieve low latency for uploading and downloading tasks. Once a bus completes the computation tasks, it will return the results directly, if the AP is still in the effective transmission range; otherwise, it will transmit the results to the next AP. The fixed fog layer refers to the infrastructures, such as smart buildings, parking lots, or BSs which usually have fixed locations. Compared with the mobile fog layer, the fixed fog layer may have higher computation capability but longer communication latency. The fixed fog nodes can connect with the mobile fog through the WLAN created by the APs. The cloud layer refers to the cloud data center. It can be physically located in remote areas far from the users. It is usually equipped with powerful computation units but with a high cost of access delay. In traditional cloud applications, users can offload computation tasks to the cloud data center via the wide-area network (WAN). The characteristics of different layers are summarized in Table XI.
| Layers & Property | Communication Capacity | Computation Capability | Availability to Users | |||||||
|---|---|---|---|---|---|---|---|---|---|---|
| Buses |
|
|
|
|||||||
| Vehicles |
|
|
|
|||||||
| Fixed fog |
|
Medium | Medium distance | |||||||
| Cloud |
|
Unlimited resource | Remote, large number of hops |
As shown in Fig. 8, the concerned task scheduling period starts when there are buses approaching a bus stop. In case there is no bus or vehicles approaching the stop, the tasks will be processed by the fixed fog or the cloud. According to IEEE 802.11ad standard, time division multiple access (TDMA) can be adopted for mmwave transmission among devices [214]. When two transmitters (i.e., buses) are close at the bus stop, the corresponding MAC protocol of the adopted wireless access network can manage the interference by coordinating the transmission among different devices towards two transmitters [215]. In addition, highly directional antennas can greatly decrease the interference of concurrent transmissions among mmwave transmitters. Therefore, the interference caused by two buses transmitting simultaneously can be managed. Note that the number of the allocated slots for a task determines the transmission rate of the task. When a bus is approaching a bus station, the achievable data rate increases rapidly.
Security issues in hybrid computation-enabled architectures include security challenges in both computation-aided and distributed computation-enabled architectures, such as trustworthiness between the VC members, misbehaving vehicles, vehicular privacy, etc. Although some of these security challenges are investigated in VANETs and VCs, there are still no solutions that treat all these challenges. For example, in a hybrid computation-enabled architecture, a vehicle can interact with a lot of entities, such as neighboring vehicles, RSUs, conventional cloud/edge server, etc. The vehicle therefore face more danger from the data stealing, hostile attack, and virus infection. Thus, it is crucial to develop a suite of elaborate and comprehensive security solutions for hybrid computation-enabled architectures.
IV-C Comparison among Computing Architectural Alternatives
In this section, we compare the pros and cons of centralized, distributed, and hybrid computing architectures in terms of supporting CV applications, which are summarized in Tables XII and XIII, based on the five functional requirements of CV systems explained in Section II-B.
| Sub | Category | Advantages | ||||||||||
| Category | Data Sharing | Data Processing | Monitoring | Warning | Control | |||||||
| Centralized | Computation- aided |
|
|
|
||||||||
| Stable network connections |
|
|
||||||||||
| Secure |
|
|
||||||||||
| Distributed | Computation- enabled | High bandwidth | Greenness |
|
||||||||
| Improved network efficiency |
|
|||||||||||
| Hybrid | Computation- aided | Comprehensive data transmission approaches (i.e., V2I, V2V, V2D, V2C) | Resilience |
|
||||||||
| Low response latency | Robust | |||||||||||
| Improved service agility | ||||||||||||
| Computation- enabled |
|
Resilience |
|
|||||||||
| Information filtration | Greenness |
|
||||||||||
| Low response latency | Flexible | |||||||||||
| Improved service agility | ||||||||||||
| Sub | Category | Disadvantages & Challenges | ||||||||
| Category | Data Sharing | Data Processing | Monitoring | Warning | Control | |||||
| Centralized | Computation- aided | Traffic congestion | Long response latency | Long response latency | ||||||
| Constrained bandwidth | ||||||||||
| Distributed | Computation- enabled |
|
Variable computation resource density |
|
||||||
| Instability | Unreliability & Heterogeneity |
|
||||||||
|
|
Insecure | ||||||||
| Hybrid | Computation- aided | Lack of mobility management |
|
|||||||
|
Interoperability and standardization required | |||||||||
|
||||||||||
| Computation- enabled | Lack of mobility management |
|
||||||||
|
|
|||||||||
|
|
|||||||||
IV-C1 Data Sharing
-
*
Centralized: Advantages: (i) Under centralized computing architectures, V2I, V2V, V2D, and V2C data sharing are all available for CVs. For example, in paper [143], a metropolitan air quality monitoring service is proposed, where CVs act as the air quality data gathering sensors. Vehicles offload their gathered data to a centralized cloud for performing an air quality estimation. (ii) In addition, centralized architectures provide relatively stable network connections, where CVs can obtain cloud services from anywhere in the world at any time. (iii) Furthermore, centralized computing architectures usually offer greater security over decentralized systems because all of the user data is stored in a central location.
Disadvantages & Challenges: In centralized computing architectures, all of the shared data is directly transmitted to the remote cloud server or MEC servers without any pre-processing or filtering at local. In spite of potential advances in wireless communication technologies (e.g., 5G), “the bandwidth required for efficient transmission of such a big volume of data is not guaranteed due to a wide range of logistical, political, and geographical factors” [117]. For example, “assuming 20 GB per month per vehicle and three million vehicles ( market share and regional ratio of 100 million vehicles), 60 petabytes of vehicle data will come to the cloud every month. Assuming the data transaction rate at the cloud is 10 GB per second, it will take 70 days just for the transactions” [128]. Therefore, the constrained bandwidth will be a bottleneck for most vehicular services/applications that transmit a large amount of data or require frequent data sharing.
-
*
Distributed: Advantages: Under distributed computing architectures, direct wireless communications from vehicle to vehicle allow to data to be exchanged fast even where there is no communication infrastructures such as BSs of cellular networks or APs of WLANs. Defined specifically to VANETs, the DSRC that operates in the GHz band is intended to provide high-speed and secure wireless communication for V2V and V2I communications. The U.S. Federal Communications Commission (FCC) allocated MHz bandwidth at - GHz spectrum band for DSRC, while ETSI allocated MHz in the - GHz band. The DSRC can support a CV with a speed up to km/h, covering a range of m and reaching up to m, and the default data rate is up to Mbps [108, 107]. IEEE 802.11p wireless access in vehicular environments (WAVE) is the specification of DSRC [216]. In addition, there have been extensive research work to explore communication properties of DSRC [217, 218, 219, 220].
Disadvantages & Challenges: (i) Under distributed computing architectures, CVs only possess very limited data transmission approaches, such as V2V and V2D. Furthermore, the small effective network diameter of VANET leads to a weak connectivity in the communication between CVs. These significantly constrain the data sharing efficiency in many situations. For example, if a CV, named “red”, in vehicle cluster A intends to share its information with another CV, named “yellow”, in vehicle cluster B, its data can only be successfully transmitted to “yellow” through multi-hop V2V connections. Furthermore, in urban areas, the line-of-sight (LOS) path of V2V may often be blocked by buildings at intersections. (ii) One of the major challenges of distributed computing architectures for CVs is the instability of communication connections among CVs. Because of the high mobility, there is no guarantee on the behaviors of the vehicle and the highly dynamic topology results in frequent changes in its connectivity. Therefore, the connection between two CVs can be quickly interrupted when they are transmitting data. Additionally, high vehicle mobility also leads to Doppler effects, which may cause severe wireless loss. (iii) In addition, there are several challenges that threaten CVs’ security under distributed computing architectures. Providing secure network connections in distributed architectures is more difficult than in centralized architectures because of the high mobility of CVs [110]. For example, in VANET-based distributed architectures, the security issues can be classified into five categories [113]: authentication [221, 222, 223], non-repudiation [224, 225], confidentiality [226], verification of data [227], and localization [228, 229].
-
*
Hybrid (Computation-aided): Advantages: Hybrid architectures also offer comprehensive data sharing approaches including V2I, V2V, V2D, and V2C.
Disadvantages & Challenges: (i) One of the major characteristics of VCs is the high mobility, which may cause several challenges in different fields including routing protocol designing, security, and data transmission reliability, especially in hybrid architectures. (ii) Due to the large diversity of networks in the hybrid computing architecture (e.g., mobile ad hoc networks, wireless sensor networks, VANETs, etc.), comprehensive policy and operational management should be established. For instance, we are expecting that several types of networks will emerge and they will interact with each other seamlessly. (iii) Security issues in hybrid CV systems are more complicated than in other networks (e.g., wireless sensor networks) due to the high mobility of CVs and the large diversity of networks. For example, it is difficult to verify the integrity of messages and authentication of users when vehicles move fast [113]. Therefore, security issues in both network (e.g., VANET) and transmission (e.g., wireless communication channel) layers in hybrid computing architectures need more consideration.
-
*
Hybrid (Computation-enabled): Advantages: Localized computation resources such as fog nodes and on-board computing units can pre-process the collected data of CVs. Thus, the collected data can be aggregated/processed/filtered before uploading to the cloud, which reduces the offloaded data volume and meanwhile improves the efficiency of the network.
Disadvantages & Challenges: (i), (ii), and (iii) presented in Hybrid (Computation-aided).
IV-C2 Data Processing
-
*
Centralized: Advantages: (i) The remote cloud server and MEC servers under centralized computing architectures possess large storage space and huge computation power. Therefore, centralized computing architectures can provide CVs the facility of unlimited computing power accessible on demand, which is suitable for vehicle applications that need large storage capacity and computation power. (ii) Under centralized architectures, CVs are capable of accessing servers’ computation resources from anywhere at any time. Because of the high mobility characteristic of vehicles, this benefit is significantly important for CVs to obtain stable and uninterrupted services. (iii) Furthermore, centralized architectures do not require early planning of computation resource provisioning.
Disadvantages & Challenges: As we mentioned previously, the current trend of concentrating data processing at centralized cloud servers will cause huge data transmission traffic. This will directly incur unnecessarily long response delay and in turn, will increase the computation latency [128]. Therefore, CV applications, such as intelligent driving and high resolution map creation and distribution [128], which are latency-sensitive cannot be handled effectively under centralized computing architectures.
-
*
Distributed: Advantages: In centralized architectures, the cloud data server consumes a huge amount of energy each year [230]. In contrast, distributed architectures enable green computing by efficiently using the spare on-board computation resources on CVs. Since vehicles are self-powered, efficiently using on-board computation resources on CVs will help minimize the energy consumption of cloud/edge servers.
Disadvantages & Challenges: (i) The computation resource density in distributed architectures varies depending on the traffic density, which can be very high in the case of a traffic jam, or very low, as driving on the highway. However, when a vehicle stops or moves slowly, it does not require more computation power (e.g., a CV does not need to rapidly process or refresh its high-definition map for supporting intelligent driving). In contrast, when the vehicle is moving fast, it requires much computation power to accurately, frequently, and rapidly process its sensors captured data (e.g., accurately localize its surrounding dynamic objects). (ii) A VC has the issue that its computation resource availability is not reliable. Since the computation resource availability in a VC and the behavior of each CV are not guaranteed. For instance, vehicles might unexpectedly leave or join a VC. In fact, this is also one of the major differences between the distributed architecture and the centralized architecture. In addition, different CVs in a VC usually have different characteristics or capabilities (e.g., processor speed and memory volume) upon their manufacturers, models, and applications. For example, CVs can be classified into private vehicles and buses. Private vehicles have unpredictable routes, whereas buses have fixed routes. (iii) Because of the variable computation resource density and the unreliability of the computation resources in distributed architectures, it is critical for every CV to frequently monitor its cooperated CVs and to periodically search for potential candidates.
-
*
Hybrid (Computation-aided): Advantages: (i) Compared to the centralized and distributed architectures, the hybrid architecture provides CVs with more potential computation sources, which improves the resilience of CV systems. (ii) The hybrid architecture also can provide low response latency for CVs that require running latency-sensitive applications. Instead of offloading collected data to a remote cloud, CVs can choose to process their data at neighboring fog nodes or RSUs.
Disadvantages & Challenges: (i) High deployment cost of heterogeneous computing infrastructures. (ii) Interoperability and standardization required. Since the hybrid architecture is based on diverse stationary and mobile computing resources, many steps should be taken to address the interoperability challenge to allow these different entities to work together. In addition, standardization is a potential solution to address the interoperability issue so that a consensus can be reached among developers, vehicle manufacturers, etc.
-
*
Hybrid (Computation-enabled): Advantages: (i), (ii), and (iii) presented in Hybrid (Computation-aided) and greenness presented in Distributed.
Disadvantages & Challenges: (i) and (ii) presented in Hybrid (Computation-aided). (iii) A comprehensive task scheduler is required in hybrid computing architectures. As we presented above, a variety of computing units/sources coexist in a hybrid CV system, which reflects the situation in which a task generated by a CV can be processed by different approaches. Such a situation will lead to an issue that what is the best computing approach for each task or what are the criteria of the processing decision making. From the perspective of the CV application, for instance, it may depend on the complexity of the application, requirement of the response latency, transmitted data volume, required computation capacity, energy consumption, monetary cost, etc. While, from the perspective of the system, it may depend on the position and role of the CV in the hierarchical system deployment, load of each computing sources, accessibility of each computing units, etc. Therefore, designing a comprehensive task scheduler that can cover multiple criteria from different perspectives is essential and challenging in hybrid architectures.
IV-C3 Monitoring, Warning, and Control
-
*
Centralized: Advantages: (i) Since all vehicles under centralized computing architectures are covered by a cloud server or several MEC servers, it is efficient to monitor the presence and experience of CVs under this architecture. For example, global warning services, such as warnings of traffic jam, accident, road condition, and predicted weather event, can be provided by the remote cloud server. (ii) In addition, by using the centralized cloud storage that can gather a huge amount of user historic information, various governmental and private agencies can use the gathered data to provide various monitoring and warning services or perform diverse studies. Furthermore, control services that need historical information of CVs can be implemented under this architecture. For example, the centralized server can make the control decision on whether a vehicle should enter the automated driving mode or not, based on not only the current collected data about the vehicle, such as the speed, but also the historical data, such as road conditions.
Disadvantages & Challenges: since the centralized servers are located relatively far away from the CVs, the delay of receiving control messages is relatively long, which means that centralized computing architectures may not be suitable for delay-sensitive services, such as autonomous driving.
-
*
Distributed: Advantages: (i) Comparing to the centralized architecture, the distributed architecture, such as VC, has great advantage in emergency warning scenarios. Disaster management, for instance, is an emergent warning application, where CVs send or broadcast the warning messages to all resources such as nearby vehicles and authorized authorities in case of any disaster. (ii) Distributed architectures provide flexibility for CVs to design user-self-defined monitoring/warning/control services. For example, it is easier for a user to set up a driver’s health monitoring service with its own concerns, such as driver’s medical records and habits. In addition, this monitoring service can still work even without an Internet connection.
Disadvantages & Challenges: (i) Unlike the previously described global warning services under centralized computing architectures, distributed computing architectures can only provide one type of local warning services, driver health warning, because of the constraint of VC coverage. (ii) The limited storage space constrains the ability of storing and analyzing a large amount of user historic data.
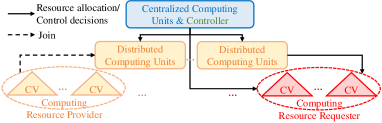
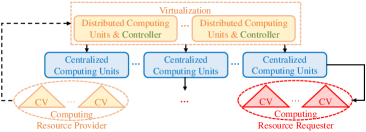
V Summary and Open Research Issues
V-A Summary
-
•
The effective design of computing architectures for CVs should integrate advanced techniques from both areas of wireless communications (e.g., 5G, V2V, and V2I) and mobile computing (e.g., cloud/edge/fog computing).
-
•
It is critical to choose suitable computing architectures for different CV applications or services. For example, the centralized computation-aided computing architecture can be applied for intelligent transportation systems which require complicated traffic management strategies and massive transport data but is not suitable for autonomous driving services due to the stringent computation latency requirements.
-
•
Comparing to computation-aided architectures, computation-enabled architectures have the potential to provide more flexible and lower energy/monetary cost computation services for CVs due to the variant computation resource providers and short distances between the computation resource requesters and providers. However, they are still facing a lot of challenges, such as fast mobility support, stability (i.e., dynamic participation of mobile computing resources), and security.
V-B Open Research Issues
Designing an appropriate computing architecture for CVs is one key research to successfully provide a wide range of CV services by meeting their QoS requirements. Hence, we believe that existing architectural alternatives introduced in this paper can be a good starting point to build a future CV eco-system that utilizes a large amount of data generated by vehicles. However, designing a good computing architecture cannot entirely solve all the issues that we will encounter in the future. We conclude this paper by listing several open challenges and research directions.
V-B1 Data sharing
Localizing data traffic: In order for OEMs to provide diverse and personalized connected services, it is essential to collect various types of sensor data from each vehicle such as camera images, acceleration/deceleration or hard braking. Those services may include personalized insurance service, predictive vehicle maintenance, high-definition (HD) map generation, intelligent driving and so on. Some forecasts that each vehicle will generate data in the order of gigabytes every day. If those data are directly sent to cloud servers, it will add a huge amount of network traffic in the existing infrastructure. Even though a vehicle can produce the raw data at a high frequency and volume, it may not be necessary to forward every single data. For example, some data are only meaningful in a particular geographic region (e.g., a hard braking signal to avoid frontal collision in the highway); it may be also fine to send data less frequently to the server (e.g., analyzing drivers’ behavior for a personalized insurance service). One research direction is to precisely characterize various types of connected services to determine the sufficient amount of frequency and volume of data enough to achieve service-specific QoS. Such knowledge can then be distributed across the multiple layers of the system architecture to appropriately localize data to avoid excessive and unnecessary traffic in the overall network.
Highly heterogeneous vehicular networks: Due to the diverse QoS requirements of vehicular services and unique characteristics of vehicular network connections, such as high mobility, frequent topology changes, and unreliable connectivity, homogeneous radio access technology (e.g., either DSRC or LTE) cannot satisfy the performance requirements of vehicular services. For example, DSRC is capable of providing low round-trip time (RTT) (i.e., below 10 milliseconds [130]), which satisfies the latency requirement of safety-related vehicular services. However, its limited peak data rate and signal coverage decline the efficiency and reliability of data sharing among CVs and infrastructures. Furthermore, although cellular networks such as LTE offers a much wider signal coverage and a higher peak data rate for CVs compared to DSRC, stringent latency requirement cannot be guaranteed due to its long RTT (i.e., over 300 milliseconds [130]). Therefore, in order to meet different QoS requirements of vehicular services, future vehicular networks tend to be highly heterogeneous. However, several open issues are imposed by the network heterogeneity. (i) Developing radio access method selection, link adaptation, and radio resource management schemes in heterogeneous vehicular networks are crucial and complicated. Thus, the main challenge is how to balance performance and complexity. (ii) Maintaining a seamless connectivity across diverse radio access technologies is complex, which includes inter- and intra-radio handoffs. Most traditional handoff approaches for cellular networks are centralized and provide a single trigger mechanism, which is not sufficient to support distributed and hybrid vehicular environments.
Support mobility in heterogeneous architectures: Mobility is one key feature of the automotive system; a vehicle continuously moves around different regions expecting to receive services seamlessly. However, it is practically difficult to expect the vehicle to communicate with a uniform infrastructure or architecture everywhere for several practical reasons. For example, different organizations (e.g., government, network providers, OEMs) may want to own their infrastructures exclusively due to security concerns; an infrastructure may be installed in a limited area only due to a budget issue or lack of profitability. Such situations will cause a vehicle to communicate with very different infrastructure as it moves. Another research direction is to develop a way to provide seamless CV services across heterogeneous infrastructure or architectures. This requires each infrastructure to provide the open interface that specifies which types of services can be supported or prohibited more explicitly, instead of hiding such information. Then, each CV service provider may have a better understanding as to where the infrastructure support for the service is available, and if it is not available, what are the alternative way to provide the service, such as service hand-over and migration. Making such interfaces available across different organizations will also boost the adoption of CVs.
V-B2 Data processing
Computing resource management: Each individual subsystem (e.g., cloud servers, fog/edge servers, RSUs, and vehicles) in the surveyed architectures has a different limitation of the computing resources such as memory or computation power. On the other hand, each connected service may require different types and sizes of computing resources. For example, the over-the-air (OTA) update service may require fog servers to reserve a portion of memory storage that can be used to distribute the latest version of the software patch to the vehicles in a particular area; the HD map generation requires relatively a higher computation power to synthesize local maps at real-time. Guaranteeing QoS of various services should take into account such computing resource constraints imposed on each subsystem. The relevant research direction is to manage computing resources in a more rigorous way, and the example research may include the following. If a particular area experiences a relatively higher request on a certain service, one can allocate more resources on the infrastructure in the area (resource allocation); depending on the current workload on the infrastructure, one can decide to (or not to) offload a certain computation (data/computation offloading); one can predict the future usage of the resources by reading the past trend of the requested connected services (resource provisioning). If this type of research is combined with the surveyed architectures, we expect a better quality of CV services can be provided.
V-B3 Monitoring, warning, and control
Other hybrid architectural alternatives: As we discussed in Section IV, architectural design is significantly important for acquiring diverse system features and satisfying different service requirements. Although a large number of architectural alternatives for CV systems have been proposed in existing work, there should be more possibilities, especially for the hybrid architectural design. For example, as shown in Fig. 9, most of existing hybrid architectures choose to put the centralized computing in the highest layer, which acts as a remote cloud. However, besides this stereotypical architectural design, we may have another alternative, as shown in Fig. 9, where distributed computing is in the highest layer in the CV system. The centralized computing units are located closer to CVs (e.g., RSUs) rather than located in remote cloud servers. Such design will (i) make the CV system fully utilize the computation and storage capacities of centralized computing units; (ii) reduce both communication and computation latency. Furthermore, distributed computing units, such as spare computing resources in neighbouring CVs and fog nodes, can be combined as a virtual localized controller which is responsible for allocating the computing resources in its governed centralized computing units to CVs. Therefore, based on the above discussion, there might be a set of interesting research opportunities in CV system computing architectural design, which are not yet tackled in the reviewed literature.
VI Conclusion
CV has a great potential to provide safer and more comfortable driving experience with the expected service scenarios, such as intelligent driving, V2C cruising, high-definition map generation, etc. In contrast to existing related surveys which only focus on one specific computing architecture in the whole paper and lack discussions on benefits, research challenges, and system requirements of different architectural alternatives, this paper has presented a thorough study on architectural design based on cloud/edge/fog computing for CVs. We have comprehensively surveyed and compared the state-of-the-art architectural alternatives with the goal of understanding the benefits and challenges of each architectural design within different CV applications. However, given the relative infancy of the field, there are still a number of outstanding problems that require further investigation from the perspective of advanced solutions including other hybrid architectural alternatives, localizing data traffic, mobility support in heterogeneous architectures, and computing resource management.
References
- [1] AECC. Driving data to the edge: The challenge of traffic distribution. [Online]. Available: https://aecc.org/wp-content/uploads/2019/09/AECC_WG2_TR_v1.0.2.pdf
- [2] R. Sun, D. W. Matolak, and P. Liu, “Parking garage channel characteristics at 5 GHz for V2V applications,” in 2013 IEEE 78th Vehicular Technology Conference (VTC Fall), Las Vegas, NV, USA, 2013, pp. 1–5.
- [3] D. W. Matolak, “Channel modeling for vehicle-to-vehicle communications,” IEEE Communications Magazine, vol. 46, no. 5, pp. 76–83, May 2008.
- [4] G. Acosta-Marum and M. A. Ingram, “Six time-and frequency-selective empirical channel models for vehicular wireless LANs,” IEEE Vehicular Technology Magazine, vol. 2, no. 4, pp. 4–11, Dec. 2007.
- [5] I. Sen and D. W. Matolak, “Vehicle–vehicle channel models for the 5-GHz band,” IEEE Transactions on Intelligent Transportation Systems, vol. 9, no. 2, pp. 235–245, Jun. 2008.
- [6] J. Karedal, F. Tufvesson, N. Czink, A. Paier, C. Dumard, T. Zemen, C. F. Mecklenbrauker, and A. F. Molisch, “A geometry-based stochastic MIMO model for vehicle-to-vehicle communications,” IEEE Transactions on Wireless Communications, vol. 8, no. 7, pp. 3646–3657, Jul. 2009.
- [7] A. F. Molisch, F. Tufvesson, J. Karedal, and C. F. Mecklenbrauker, “A survey on vehicle-to-vehicle propagation channels,” IEEE Wireless Communications, vol. 16, no. 6, pp. 12–22, Dec. 2009.
- [8] C. F. Mecklenbrauker, A. F. Molisch, J. Karedal, F. Tufvesson, A. Paier, L. Bernadó, T. Zemen, O. Klemp, and N. Czink, “Vehicular channel characterization and its implications for wireless system design and performance,” Proceedings of the IEEE, vol. 99, no. 7, pp. 1189–1212, Feb. 2011.
- [9] J. Karedal, N. Czink, A. Paier, F. Tufvesson, and A. F. Molisch, “Path loss modeling for vehicle-to-vehicle communications,” IEEE Transactions on Vehicular Technology, vol. 60, no. 1, pp. 323–328, Nov. 2011.
- [10] ETSI EN 302 637-2. Intelligent transport systems (ITS); Vehicular communications; Basic set of applications; Part 2: Specification of cooperative awareness basic service. Accessed on Apr. 2019. [Online]. Available: https://standards.globalspec.com/std/13271189/EN%20302%20637-2
- [11] M. Chevreuil, “IVHW: An inter-vehicle hazard warning system concept within the DEUFRAKO program,” in Proc. e-safety Congress and Exhibition, Lyon, France, 2002.
- [12] H. S. Basheer and C. Bassil, “A review of broadcasting safety data in V2V: Weaknesses and requirements,” Ad Hoc Networks, vol. 65, pp. 13–25, Oct. 2017.
- [13] ETSI EN 302 637-3. Intelligent transport systems (ITS); Vehicular communications; Basic set of applications; Part 3: Specifications of decentralized environmental notification basic service. Accessed on Apr. 2019. [Online]. Available: https://standards.globalspec.com/std/13271201/EN%20302%20637-3
- [14] W. Whyte, A. Weimerskirch, V. Kumar, and T. Hehn, “A security credential management system for V2V communications,” in Proc. 2013 IEEE Vehicular Networking Conference, Boston, MA, USA, 2013, pp. 1–8.
- [15] A. Rao, A. Sangwan, A. A. Kherani, A. Varghese, B. Bellur, and R. Shorey, “Secure V2V communication with certificate revocations,” in Proc. IEEE 2007 Mobile Networking for Vehicular Environments, Anchorage, AK, USA, 2007, pp. 127–132.
- [16] J. Harding, G. Powell, R. Yoon, J. Fikentscher, C. Doyle, D. Sade, M. Lukuc, J. Simons, J. Wang et al., “Vehicle-to-vehicle communications: Readiness of V2V technology for application.” United States. National Highway Traffic Safety Administration, Washington, DC, USA, Tech. Rep. DOT HS 812 014, Aug. 2014.
- [17] H. Hasrouny, C. Bassil, A. E. Samhat, and A. Laouiti, “Group-based authentication in V2V communications,” in Proc. IEEE Fifth International Conference on Digital Information and Communication Technology and its Applications (DICTAP), Beirut, Lebanon, 2015, pp. 173–177.
- [18] A. Iyer, A. Kherani, A. Rao, and A. Karnik, “Secure V2V communications: Performance impact of computational overheads,” in Proc. IEEE INFOCOM Workshops, Phoenix, AZ, USA, 2008, pp. 1–6.
- [19] Z. H. Mir and F. Filali, “Large-scale simulations and performance evaluation of connected cars - A V2V communication perspective,” Simulation Modelling Practice and Theory, vol. 73, pp. 55–71, Apr. 2017.
- [20] X. Wang, E. Anderson, P. Steenkiste, and F. Bai, “Improving the accuracy of environment-specific vehicular channel modeling,” in Proc. the seventh ACM international workshop on Wireless network testbeds, experimental evaluation and characterization, Istanbul, Turkey, 2012, pp. 43–50.
- [21] O.-Y. Kwon, R. Song, Y.-Z. Ma, and B.-S. Kim, “Integrated MIMO antennas for LTE and V2V applications,” in Proc. IEEE 2016 URSI Asia-Pacific Radio Science Conference (URSI AP-RASC), Seoul, South Korea, 2016, pp. 1057–1060.
- [22] J. Lorca, M. Hunukumbure, and Y. Wang, “On overcoming the impact of Doppler spectrum in millimeter-wave V2I communications,” in Proc. 2017 IEEE Globecom Workshops (GC Wkshps), Singapore, 2017, pp. 1–6.
- [23] H. Wang, B. Kim, J. Xie, and Z. Han, “E-auto: A communication scheme for connected vehicles with edge-assisted autonomous driving,” in Proc. IEEE International Conference on Communications (ICC), Shanghai, China, May 2019, pp. 1–6.
- [24] R. Zhang, Z. Zhong, J. Zhao, B. Li, and K. Wang, “Channel measurement and packet-level modeling for V2I spatial multiplexing uplinks using massive MIMO,” IEEE Transactions on Vehicular Technology, vol. 65, no. 10, pp. 7831–7843, Mar. 2016.
- [25] S. Lee, J. Kwon, S. Jung, and Y. Kwon, “Simulation modeling of visible light communication channel for automotive applications,” in Proc. IEEE 15th International Conference on Intelligent Transportation Systems, Anchorage, AK, USA, 2012, pp. 463–468.
- [26] W. Viriyasitavat, M. Boban, H.-M. Tsai, and A. Vasilakos, “Vehicular communications: Survey and challenges of channel and propagation models,” IEEE Vehicular Technology Magazine, vol. 10, no. 2, pp. 55–66, May 2015.
- [27] M. Khabbaz, M. Hasna, C. M. Assi, and A. Ghrayeb, “Modeling and analysis of an infrastructure service request queue in multichannel V2I communications,” IEEE Transactions on Intelligent Transportation Systems, vol. 15, no. 3, pp. 1155–1167, Jan. 2014.
- [28] G. Toulminet, J. Boussuge, and C. Laurgeau, “Comparative synthesis of the 3 main european projects dealing with cooperative systems (CVIS, SAFESPOT and COOPERS) and description of coopers demonstration site 4,” in Proc. 2008 11th IEEE International Conference on Intelligent Transportation Systems, Beijing, China, 2008, pp. 809–814.
- [29] Q. Yuan, H. Zhou, J. Li, Z. Liu, F. Yang, and X. S. Shen, “Toward efficient content delivery for automated driving services: An edge computing solution,” IEEE Network, vol. 32, no. 1, pp. 80–86, Jan. 2018.
- [30] H. Qiu, M. Qiu, and R. Lu, “Secure V2X communication network based on intelligent PKI and edge computing,” IEEE Network, vol. 34, no. 2, pp. 172–178, Sep. 2019.
- [31] J.-Y. Kim, H.-K. Choi, and J. A. Copeland, “An efficient authentication scheme for security and privacy preservation in V2I communications,” in Proc. IEEE 72nd Vehicular Technology Conference-Fall, Sep. 2010, pp. 1–6.
- [32] T. Ayoub and T. Mazri, “Security challenges in V2I architectures and proposed solutions,” in Proc. IEEE 5th International Congress on Information Science and Technology (CiSt), Marrakech, Morocco, 2018, pp. 594–599.
- [33] W. Quan, F. Song, C. Yu, and M. Zhang, “ICN based vehicle-to-cloud delivery for multimedia streaming in urban vehicular networks,” IEEE China Communications, vol. 13, no. 9, pp. 103–112, Oct. 2016.
- [34] J. Ibarz, M. Lauer, M. Roy, J.-C. Fabre, and O. Flébus, “Optimizing vehicle-to-cloud data transfers using soft real-time scheduling concepts,” in Proc. ACM the 28th International Conference on Real-Time Networks and Systems, 2020, pp. 161–171.
- [35] Z. Wang, X. Liao, X. Zhao, K. Han, P. Tiwari, M. J. Barth, and G. Wu, “A digital twin paradigm: Vehicle-to-cloud based advanced driver assistance systems,” in Proc. 2020 IEEE 91st Vehicular Technology Conference (VTC2020-Spring), Antwerp, Belgium, 2020, pp. 1–6.
- [36] S. Rangarajan, M. Verma, A. Kannan, A. Sharma, and I. Schoen, “V2C: A secure vehicle to cloud framework for virtualized and on-demand service provisioning,” in Proc. ACM International Conference on Advances in Computing, Communications and Informatics, 2012, pp. 148–154.
- [37] H. Kim, J. Han, S.-H. Kim, J. Choi, D. Yoon, M. Jeon, E. Yang, N. Pham, S. Woo, J. Park et al., “IsV2C: An integrated road traffic-network-cloud simulator for V2C connected car services,” in Proc. 2017 IEEE International Conference on Services Computing (SCC), Honolulu, HI, USA, 2017, pp. 434–441.
- [38] M. A. Hanson, H. C. Powell Jr, A. T. Barth, K. Ringgenberg, B. H. Calhoun, J. H. Aylor, and J. Lach, “Body area sensor networks: Challenges and opportunities,” IEEE Computer, vol. 42, no. 1, pp. 58–65, Jan. 2009.
- [39] C. Spelta, V. Manzoni, A. Corti, A. Goggi, and S. M. Savaresi, “Smartphone-based vehicle-to-driver/environment interaction system for motorcycles,” IEEE Embedded Systems Letters, vol. 2, no. 2, pp. 39–42, Jun. 2010.
- [40] (2019) Multi-access Edge Computing - Standards for MEC - ETSI. [Online]. Available: https://www.etsi.org/technologies/multi-access-edge-computing
- [41] (2019) Open Edge Computing Initiative. [Online]. Available: https://www.openedgecomputing.org/
- [42] (2019) OpenFog Consortium. [Online]. Available: https://www.openfogconsortium.org
- [43] P. Mell, T. Grance et al., “The NIST definition of cloud computing,” National Institute of Standards and Technology, vol. 53, no. 6, p. 50, Sep. 2009.
- [44] C.-W. Lu, C.-M. Hsieh, C.-H. Chang, and C.-T. Yang, “An improvement to data service in cloud computing with content sensitive transaction analysis and adaptation,” in Proc. IEEE Annual Computer Software and Applications Conference Workshops (COMPSACW), Japan, Jul. 2013, pp. 463–468.
- [45] T. S. J. Darwish and K. A. Bakar, “Fog based intelligent transportation big data analytics in the Internet of vehicles environment: Motivations, architecture, challenges, and critical issues,” IEEE Access, vol. 6, pp. 15 679–15 701, Mar. 2018.
- [46] ESTI. Mobile-edge computing—introductory technical white paper. [Online]. Available: https://portal.etsi.org/portals/0/tbpages/mec/docs/mobile-edge_computing_-_introductory_technical_white_paper_v1%2018-09-14.pdf
- [47] Y. C. Hu, M. Patel, D. Sabella, N. Sprecher, and V. Young, “Mobile edge computing—a key technology towards 5G,” ETSI White Paper, vol. 11, no. 11, pp. 1–16, Sep. 2015.
- [48] ESTI. Etsi multi-access edge computing starts second phase and renews leadership team. [Online]. Available: https://www.etsi.org/technologies/radio/short-range-devices/9-news-events/news/1180-2017-03-news-etsi-multi-access-edge-computing-starts-second-phase-and-renews-leadership-team
- [49] M. Satyanarayanan, P. Bahl, R. Caceres, and N. Davies, “The case for VM-based cloudlets in mobile computing,” IEEE Pervasive Computing, vol. 8, no. 4, pp. 14–23, Oct. 2009.
- [50] F. Bonomi, R. Milito, J. Zhu, and S. Addepalli, “Fog computing and its role in the internet of things,” in Proc. the First Edition of the MCC Workshop on Mobile Cloud Computing, Aug. 2012, pp. 13–16.
- [51] Openfog consortium architecture working group, Openfog architecture overview, white paper opfwp001.0216, 2016.
- [52] F. Bonomi, R. Milito, P. Natarajan, and J. Zhu, “Fog computing: A platform for Internet of Things and analytics,” in Springer Big data and Internet of Things: A Roadmap for Smart Environments, May 2014, pp. 169–186.
- [53] C. Mouradian, D. Naboulsi, S. Yangui, R. H. Glitho, M. J. Morrow, and P. A. Polakos, “A comprehensive survey on fog computing: State-of-the-art and research challenges,” IEEE Communications Surveys & Tutorials, vol. 20, no. 1, pp. 416–464, Nov. 2017.
- [54] M. Othman, S. A. Madani, S. U. Khan et al., “A survey of mobile cloud computing application models,” IEEE Communications Surveys & Tutorials, vol. 16, no. 1, pp. 393–413, Jul. 2013.
- [55] L. Guan, X. Ke, M. Song, and J. Song, “A survey of research on mobile cloud computing,” in Proc. 10th IEEE/ACIS International Conference on Computer and Information Science, Nov. 2011, pp. 387–392.
- [56] H. T. Dinh, C. Lee, D. Niyato, and P. Wang, “A survey of mobile cloud computing: architecture, applications, and approaches,” Wireless Communications and Mobile Computing, vol. 13, no. 18, pp. 1587–1611, Oct. 2013.
- [57] S. Patidar, D. Rane, and P. Jain, “A survey paper on cloud computing,” in Proc. IEEE 2012 Second International Conference on Advanced Computing & Communication Technologies, Mar. 2012, pp. 394–398.
- [58] X. Fan, J. Cao, and H. Mao, “A survey of mobile cloud computing,” ZTE Communications, no. 1, pp. 4–8, 2011.
- [59] N. Fernando, S. W. Loke, and W. Rahayu, “Mobile cloud computing: A survey,” Future Generation Computer Systems, vol. 29, no. 1, pp. 84–106, Jan. 2013.
- [60] M. Alizadeh, S. Abolfazli, M. Zamani, S. Baharun, and K. Sakurai, “Authentication in mobile cloud computing: A survey,” Journal of Network and Computer Applications, vol. 61, pp. 59–80, Feb. 2016.
- [61] G. Ramachandra, M. Iftikhar, and F. A. Khan, “A comprehensive survey on security in cloud computing,” Procedia Computer Science, vol. 110, pp. 465–472, Jul. 2017.
- [62] B. Varghese and R. Buyya, “Next generation cloud computing: New trends and research directions,” Future Generation Computer Systems, vol. 79, pp. 849–861, Feb. 2018.
- [63] Y. Mao, C. You, J. Zhang, K. Huang, and K. B. Letaief, “A survey on mobile edge computing: The communication perspective,” IEEE Communications Surveys & Tutorials, vol. 19, no. 4, pp. 2322–2358, Aug. 2017.
- [64] P. Mach and Z. Becvar, “Mobile edge computing: A survey on architecture and computation offloading,” IEEE Communications Surveys & Tutorials, vol. 19, no. 3, pp. 1628–1656, Mar. 2017.
- [65] Y. Ai, M. Peng, and K. Zhang, “Edge computing technologies for internet of things: a primer,” Digital Communications and Networks, vol. 4, no. 2, pp. 77–86, Apr. 2018.
- [66] N. Abbas, Y. Zhang, A. Taherkordi, and T. Skeie, “Mobile edge computing: A survey,” IEEE Internet of Things Journal, vol. 5, no. 1, pp. 450–465, Sep. 2017.
- [67] E. Ahmed and M. H. Rehmani, “Mobile edge computing: opportunities, solutions, and challenges,” Future Generation Computer Systems, vol. 70, pp. 59–63, Mar. 2017.
- [68] K. Bilal, O. Khalid, A. Erbad, and S. U. Khan, “Potentials, trends, and prospects in edge technologies: Fog, cloudlet, mobile edge, and micro data centers,” Computer Networks, vol. 130, pp. 94–120, Jan. 2018.
- [69] T. Taleb, K. Samdanis, B. Mada, H. Flinck, S. Dutta, and D. Sabella, “On multi-access edge computing: A survey of the emerging 5G network edge cloud architecture and orchestration,” IEEE Communications Surveys & Tutorials, vol. 19, no. 3, pp. 1657–1681, May 2017.
- [70] W. Shi, J. Cao, Q. Zhang, Y. Li, and L. Xu, “Edge computing: Vision and challenges,” IEEE Internet of Things Journal, vol. 3, no. 5, pp. 637–646, Oct. 2016.
- [71] M. T. Beck, M. Werner, S. Feld, and S. Schimper, “Mobile edge computing: A taxonomy,” in Proc. of the Sixth International Conference on Advances in Future Internet. Citeseer, Nov. 2014, pp. 48–55.
- [72] R. Roman, J. Lopez, and M. Mambo, “Mobile edge computing, fog et al.: A survey and analysis of security threats and challenges,” Future Generation Computer Systems, vol. 78, pp. 680–698, Jan. 2018.
- [73] F. Liu, G. Tang, Y. Li, Z. Cai, X. Zhang, and T. Zhou, “A survey on edge computing systems and tools,” Proceedings of the IEEE, vol. 107, no. 8, pp. 1537–1562, Jun. 2019.
- [74] S. Wang, X. Zhang, Y. Zhang, L. Wang, J. Yang, and W. Wang, “A survey on mobile edge networks: Convergence of computing, caching and communications,” IEEE Access, vol. 5, pp. 6757–6779, Mar. 2017.
- [75] K. Toczé and S. Nadjm-Tehrani, “A taxonomy for management and optimization of multiple resources in edge computing,” Wireless Communications and Mobile Computing, vol. 2018, Jun. 2018.
- [76] W. Z. Khan, E. Ahmed, S. Hakak, I. Yaqoob, and A. Ahmed, “Edge computing: A survey,” Future Generation Computer Systems, vol. 97, pp. 219–235, Aug. 2019.
- [77] C. Li, Y. Xue, J. Wang, W. Zhang, and T. Li, “Edge-oriented computing paradigms: A survey on architecture design and system management,” ACM Computing Surveys (CSUR), vol. 51, no. 2, p. 39, Apr. 2018.
- [78] R. Olaniyan, O. Fadahunsi, M. Maheswaran, and M. F. Zhani, “Opportunistic edge computing: concepts, opportunities and research challenges,” Future Generation Computer Systems, vol. 89, pp. 633–645, Dec. 2018.
- [79] P. Porambage, J. Okwuibe, M. Liyanage, M. Ylianttila, and T. Taleb, “Survey on multi-access edge computing for internet of things realization,” IEEE Communications Surveys & Tutorials, vol. 20, no. 4, pp. 2961–2991, Jun. 2018.
- [80] L. M. Vaquero and L. Rodero-Merino, “Finding your way in the fog: Towards a comprehensive definition of fog computing,” ACM SIGCOMM Computer Communication Review, vol. 44, no. 5, pp. 27–32, Oct. 2014.
- [81] S. Yi, C. Li, and Q. Li, “A survey of fog computing: concepts, applications and issues,” in Proc. ACM 2015 Workshop on Mobile Big Data, Jun. 2015, pp. 37–42.
- [82] M. Yannuzzi, R. Milito, R. Serral-Gracià, D. Montero, and M. Nemirovsky, “Key ingredients in an IoT recipe: Fog computing, cloud computing, and more fog computing,” in Proc. 2014 IEEE 19th International Workshop on Computer Aided Modeling and Design of Communication Links and Networks (CAMAD), Dec. 2014, pp. 325–329.
- [83] A. V. Dastjerdi and R. Buyya, “Fog computing: Helping the internet of things realize its potential,” IEEE Computer, vol. 49, no. 8, pp. 112–116, Aug. 2016.
- [84] P. Bellavista, J. Berrocal, A. Corradi, S. K. Das, L. Foschini, and A. Zanni, “A survey on fog computing for the internet of things,” Pervasive and Mobile Computing, Jan. 2018.
- [85] J. Lin, W. Yu, N. Zhang, X. Yang, H. Zhang, and W. Zhao, “A survey on internet of things: Architecture, enabling technologies, security and privacy, and applications,” IEEE Internet of Things Journal, vol. 4, no. 5, pp. 1125–1142, Mar. 2017.
- [86] H. F. Atlam, R. J. Walters, and G. B. Wills, “Fog computing and the internet of things: a review,” Big Data and Cognitive Computing, vol. 2, no. 2, p. 10, Apr. 2018.
- [87] A. Sciarrone, C. Fiandrino, I. Bisio, F. Lavagetto, D. Kliazovich, and P. Bouvry, “Smart probabilistic fingerprinting for indoor localization over fog computing platforms,” in Proc. 5th IEEE International Conference on Cloud Networking (CloudNet), Oct. 2016, pp. 39–44.
- [88] H. Elazhary, “Internet of things (IoT), mobile cloud, cloudlet, mobile IoT, IoT cloud, fog, mobile edge, and edge emerging computing paradigms: Disambiguation and research directions,” Journal of Network and Computer Applications, vol. 128, pp. 105–140, Feb. 2018.
- [89] L. Bittencourt, R. Immich, R. Sakellariou, N. Fonseca, E. Madeira, M. Curado, L. Villas, L. DaSilva, C. Lee, and O. Rana, “The internet of things, fog and cloud continuum: Integration and challenges,” Internet of Things, vol. 3, pp. 134–155, Oct. 2018.
- [90] P. Zhang, J. K. Liu, F. R. Yu, M. Sookhak, M. H. Au, and X. Luo, “A survey on access control in fog computing,” IEEE Communications Magazine, vol. 56, no. 2, pp. 144–149, Feb. 2018.
- [91] A. Yousefpour, C. Fung, T. Nguyen, K. Kadiyala, F. Jalali, A. Niakanlahiji, J. Kong, and J. P. Jue, “All one needs to know about fog computing and related edge computing paradigms: A complete survey,” Journal of Systems Architecture, vol. 98, pp. 289–330, Sep. 2019.
- [92] P. Hu, S. Dhelim, H. Ning, and T. Qiu, “Survey on fog computing: architecture, key technologies, applications and open issues,” Journal of Network and Computer Applications, vol. 98, pp. 27–42, Nov. 2017.
- [93] T. H. Luan, L. Gao, Z. Li, Y. Xiang, G. Wei, and L. Sun, “Fog computing: Focusing on mobile users at the edge,” arXiv preprint arXiv:1502.01815, Mar. 2015.
- [94] K. Dolui and S. K. Datta, “Comparison of edge computing implementations: Fog computing, cloudlet and mobile edge computing,” in Proc. IEEE Global Internet of Things Summit (GIoTS), Geneva, Switzerland, Jun. 2017.
- [95] S. Yi, Z. Qin, and Q. Li, “Security and privacy issues of fog computing: A survey,” in International Conference on Wireless Algorithms, Systems, and Applications. Springer, Aug. 2015, pp. 685–695.
- [96] P. Zhang, M. Zhou, and G. Fortino, “Security and trust issues in fog computing: A survey,” Future Generation Computer Systems, vol. 88, pp. 16–27, Nov. 2018.
- [97] M. Mukherjee, L. Shu, and D. Wang, “Survey of fog computing: Fundamental, network applications, and research challenges,” IEEE Communications Surveys & Tutorials, vol. 20, no. 3, pp. 1826–1857, Mar. 2018.
- [98] C. Cooper, D. Franklin, M. Ros, F. Safaei, and M. Abolhasan, “A comparative survey of vanet clustering techniques,” IEEE Communications Surveys & Tutorials, vol. 19, no. 1, pp. 657–681, Sep. 2016.
- [99] J. Rios-Torres and A. A. Malikopoulos, “A survey on the coordination of connected and automated vehicles at intersections and merging at highway on-ramps,” IEEE Transactions on Intelligent Transportation Systems, vol. 18, no. 5, pp. 1066–1077, Sep. 2016.
- [100] F. Li and Y. Wang, “Routing in vehicular ad hoc networks: A survey,” IEEE Vehicular Technology Magazine, vol. 2, no. 2, pp. 12–22, Jun. 2007.
- [101] M. Altayeb and I. Mahgoub, “A survey of vehicular ad hoc networks routing protocols,” International Journal of Innovation and Applied Studies, vol. 3, no. 3, pp. 829–846, Jul. 2013.
- [102] S. M. Bilal, C. J. Bernardos, and C. Guerrero, “Position-based routing in vehicular networks: A survey,” Journal of Network and Computer Applications, vol. 36, no. 2, pp. 685–697, Mar. 2013.
- [103] A. Awang, K. Husain, N. Kamel, and S. Aïssa, “Routing in vehicular ad-hoc networks: A survey on single-and cross-layer design techniques, and perspectives,” IEEE Access, vol. 5, pp. 9497–9517, Apr. 2017.
- [104] K. Zhu, D. Niyato, P. Wang, E. Hossain, and D. In Kim, “Mobility and handoff management in vehicular networks: a survey,” Wireless Communications and Mobile Computing, vol. 11, no. 4, pp. 459–476, Apr. 2011.
- [105] S. Al-Sultan, M. M. Al-Doori, A. H. Al-Bayatti, and H. Zedan, “A comprehensive survey on vehicular ad hoc network,” Journal of Network and Computer Applications, vol. 37, pp. 380–392, Jan. 2014.
- [106] K. Zheng, Q. Zheng, P. Chatzimisios, W. Xiang, and Y. Zhou, “Heterogeneous vehicular networking: A survey on architecture, challenges, and solutions,” IEEE Communications Surveys & Tutorials, vol. 17, no. 4, pp. 2377–2396, Jun. 2015.
- [107] N. Lu, N. Cheng, N. Zhang, X. Shen, and J. W. Mark, “Connected vehicles: Solutions and challenges,” IEEE Internet of Things Journal, vol. 1, no. 4, pp. 289–299, May 2014.
- [108] F. Cunha, L. Villas, A. Boukerche, G. Maia, A. Viana, R. A. Mini, and A. A. Loureiro, “Data communication in VANETs: Protocols, applications and challenges,” Ad Hoc Networks, vol. 44, pp. 90–103, Jul. 2016.
- [109] H. Hartenstein and L. Laberteaux, “A tutorial survey on vehicular ad hoc networks,” IEEE Communications Magazine, vol. 46, no. 6, pp. 164–171, Jun. 2008.
- [110] G. Karagiannis, O. Altintas, E. Ekici, G. Heijenk, B. Jarupan, K. Lin, and T. Weil, “Vehicular networking: A survey and tutorial on requirements, architectures, challenges, standards and solutions,” IEEE Communications Surveys & Tutorials, vol. 13, no. 4, pp. 584–616, Jul. 2011.
- [111] L. B. Othmane, H. Weffers, M. M. Mohamad, and M. Wolf, “A survey of security and privacy in connected vehicles,” in Wireless Sensor and Mobile Ad-Hoc Networks. Springer, 2015, pp. 217–247.
- [112] M. Alsabaan, W. Alasmary, A. Albasir, and K. Naik, “Vehicular networks for a greener environment: A survey,” IEEE Communications Surveys & Tutorials, vol. 15, no. 3, pp. 1372–1388, Nov. 2012.
- [113] M. Whaiduzzaman, M. Sookhak, A. Gani, and R. Buyya, “A survey on vehicular cloud computing,” Journal of Network and Computer Applications, vol. 40, pp. 325–344, Apr. 2014.
- [114] A. Boukerche and E. Robson, “Vehicular cloud computing: Architectures, applications, and mobility,” Computer Networks, vol. 135, pp. 171–189, Apr. 2018.
- [115] L. Gu, D. Zeng, and S. Guo, “Vehicular cloud computing: A survey,” in Proc. IEEE Globecom Workshops, Atlanta, GA, USA, Dec. 2013, pp. 403–407.
- [116] V. G. Menon and P. J. Prathap, “Moving from vehicular cloud computing to vehicular fog computing: Issues and challenges,” International Journal on Computer Science and Engineering, vol. 9, no. 2, pp. 14–18, 2017.
- [117] C. Huang, R. Lu, and K.-K. R. Choo, “Vehicular fog computing: architecture, use case, and security and forensic challenges,” IEEE Communications Magazine, vol. 55, no. 11, pp. 105–111, Nov. 2017.
- [118] N. K. Giang, V. Leung, and R. Lea, “On developing smart transportation applications in fog computing paradigm,” in Proc. the 6th ACM Symposium on Development and Analysis of Intelligent Vehicular Networks and Applications, Nov. 2016, pp. 91–98.
- [119] J. Grover, A. Jain, S. Singhal, and A. Yadav, “Real-time VANET applications using fog computing,” in Proc. First International Conference on Smart System, Innovations and Computing. Springer, Jan. 2018, pp. 683–691.
- [120] S. Bitam, A. Mellouk, and S. Zeadally, “VANET-cloud: a generic cloud computing model for vehicular ad hoc networks,” IEEE Wireless Communications, vol. 22, no. 1, pp. 96–102, Feb. 2015.
- [121] E. Uhlemann, “The US and Europe advances V2V deployment [connected vehicles],” IEEE Vehicular Technology Magazine, vol. 12, no. 2, pp. 18–22, Jun. 2017.
- [122] USDOT. Connected vehicle pilot deployment program. [Online]. Available: https://www.its.dot.gov/pilots/
- [123] ——. Architecture reference for cooperative and intelligent transportation. [Online]. Available: https://local.iteris.com/arc-it/
- [124] NYDOT. NYC connected vehicle project. [Online]. Available: https://cvp.nyc/
- [125] ——. Wyoming DOT connected vehicle project. [Online]. Available: https://wydotcvp.wyoroad.info/
- [126] USDOT. Security credential management system (SCMS). [Online]. Available: https://www.its.dot.gov/resources/scms.htm
- [127] ——. Service packages. [Online]. Available: https://local.iteris.com/arc-it/html/servicepackages/servicepackages-areaspsort.html
- [128] AECC. General principle and vision, white paper version 2.1.0. [Online]. Available: https://aecc.org/wp-content/uploads/2019/04/AECC_White_Paper_v2.1_003.pdf
- [129] A. Mahmood, W. E. Zhang, and Q. Z. Sheng, “Software-defined heterogeneous vehicular networking: The architectural design and open challenges,” Future Internet, vol. 11, no. 3, p. 70, Mar. 2019.
- [130] Z. Xu, X. Li, X. Zhao, M. H. Zhang, and Z. Wang, “DSRC versus 4G-LTE for connected vehicle applications: A study on field experiments of vehicular communication performance,” Journal of Advanced Transportation, vol. 2017, Aug. 2017.
- [131] K. Abboud, H. A. Omar, and W. Zhuang, “Interworking of DSRC and cellular network technologies for V2X communications: A survey,” IEEE Transactions on Vehicular Technology, vol. 65, no. 12, pp. 9457–9470, Dec. 2016.
- [132] R. Yu, J. Ding, X. Huang, M. T. Zhou, S. Gjessing, and Y. Zhang, “Optimal resource sharing in 5G-enabled vehicular networks: A matrix game approach,” IEEE Transactions on Vehicular Technology, vol. 65, no. 10, pp. 7844–7856, Oct. 2016.
- [133] Y. Xiao and C. Zhu, “Vehicular fog computing: Vision and challenges,” in Proc. IEEE International Conference on Pervasive Computing and Communications Workshops (PerCom Workshops), Kona, HI, USA, Mar. 2017, pp. 6–9.
- [134] X.-Q. Pham and E.-N. Huh, “Towards task scheduling in a cloud-fog computing system,” in Proc. IEEE Asia-Pacific Network Operations and Management Symposium (APNOMS), Japan, Oct. 2016.
- [135] C. Huang and K. Xu, “Reliable realtime streaming in vehicular cloud-fog computing networks,” in 2016 IEEE/CIC International Conference on Communications in China (ICCC), Chengdu, China, Jul. 2016.
- [136] Y. Lin and H. Shen, “Cloud fog: Towards high quality of experience in cloud gaming,” in Proc. IEEE International Conference on Parallel Processing, Beijing, China, Sep. 2015, pp. 500–509.
- [137] S. Woo, H. J. Jo, and D. H. Lee, “A practical wireless attack on the connected car and security protocol for in-vehicle CAN,” IEEE Transactions on Intelligent Transportation Systems, vol. 16, no. 2, pp. 993–1006, Sep. 2014.
- [138] G. Yan, D. Wen, S. Olariu, and M. C. Weigle, “Security challenges in vehicular cloud computing,” IEEE Transactions on Intelligent Transportation Systems, vol. 14, no. 1, pp. 284–294, Sep. 2012.
- [139] H. Zhu, R. Lu, X. Shen, and X. Lin, “Security in service-oriented vehicular networks,” IEEE Wireless Communications, vol. 16, no. 4, pp. 16–22, Oct. 2009.
- [140] H. Othmane, Lotfi Benand Weffers, M. M. Mohamad, and M. Wolf, A Survey of Security and Privacy in Connected Vehicles. New York, NY: Springer, Jan. 2015, pp. 217–247.
- [141] J. Wang, J. Cho, S. Lee, and T. Ma, “Real time services for future cloud computing enabled vehicle networks,” in Proc. IEEE International Conference on Wireless Communications and Signal Processing (WCSP), Nanjing, China, Nov. 2011.
- [142] Z. Li, C. Chen, and K. Wang, “Cloud computing for agent-based urban transportation systems,” IEEE Intelligent Systems, vol. 26, no. 1, pp. 73–79, Jan. 2011.
- [143] Y. C. Wang and G. W. Chen, “Efficient data gathering and estimation for metropolitan air quality monitoring by using vehicular sensor networks,” IEEE Transactions on Vehicular Technology, vol. 66, no. 8, pp. 7234–7248, Aug. 2017.
- [144] K. Zhang, Y. Mao, S. Leng, Y. He, and Y. Zhang, “Mobile-edge computing for vehicular networks: A promising network paradigm with predictive off-loading,” IEEE Vehicular Technology Magazine, vol. 12, no. 2, pp. 36–44, Jun. 2017.
- [145] S.-C. Hung, H. Hsu, S.-Y. Lien, and K.-C. Chen, “Architecture harmonization between cloud radio access networks and fog networks,” IEEE Access, vol. 3, pp. 3019–3034, Dec. 2015.
- [146] F. Malandrino, C. Casetti, C.-F. Chiasserini, and M. Fiore, “Content download in vehicular networks in presence of noisy mobility prediction,” IEEE Transactions on Mobile Computing, vol. 13, no. 5, pp. 1007–1021, May 2014.
- [147] J. Li, C. Natalino, D. P. Van, L. Wosinska, and J. Chen, “Resource management in fog-enhanced radio access network to support real-time vehicular services,” in Proc. IEEE 1st International Conference on Fog and Edge Computing (ICFEC), Madrid, Spain, May 2017, pp. 68–74.
- [148] J. Liu, J. Wan, B. Zeng, Q. Wang, H. Song, and M. Qiu, “A scalable and quick-response software defined vehicular network assisted by mobile edge computing,” IEEE Communications Magazine, vol. 55, no. 7, pp. 94–100, Jul. 2017.
- [149] J. Liu, J. Wan, D. Jia, B. Zeng, D. Li, C. H. Hsu, and H. Chen, “High-efficiency urban traffic management in context-aware computing and 5G communication,” IEEE Communications Magazine, vol. 55, no. 1, pp. 34–40, Jan. 2017.
- [150] J. Wan, D. Zhang, Y. Sun, K. Lin, C. Zou, and H. Cai, “VCMIA: a novel architecture for integrating vehicular cyber-physical systems and mobile cloud computing,” Springer Mobile Networks and Applications, vol. 19, no. 2, pp. 153–160, Apr. 2014.
- [151] M. Gerla, J. T. Weng, and G. Pau, “Pics-on-wheels: Photo surveillance in the vehicular cloud,” in Proc. IEEE International Conference on Computing, Networking and Communications (ICNC), San Diego, CA, USA, Jan. 2013, pp. 1123–1127.
- [152] C. M. Huang, M. S. Chiang, D. T. Dao, W. L. Su, S. Xu, and H. Zhou, “V2V data offloading for cellular network based on the software defined network (SDN) inside mobile edge computing (MEC) architecture,” IEEE Access, vol. 6, pp. 17 741–17 755, Mar. 2018.
- [153] W. Zhang, Z. Zhang, and H.-C. Chao, “Cooperative fog computing for dealing with big data in the Internet of vehicles architecture and hierarchical resource management,” IEEE Communications Magazine, vol. 55, no. 12, Dec. 2017.
- [154] X. Huang, R. Yu, J. Kang, and Y. Zhang, “Distributed reputation management for secure and efficient vehicular edge computing and networks,” IEEE Access, vol. 5, pp. 25 408–25 420, Nov. 2017.
- [155] Z. Li and C. T. Chigan, “On joint privacy and reputation assurance for vehicular ad hoc networks,” IEEE Transactions on Mobile Computing, vol. 13, no. 10, pp. 2334–2344, Jan. 2014.
- [156] W. Li and H. Song, “ART: An attack-resistant trust management scheme for securing vehicular ad hoc networks,” IEEE Transactions on Intelligent Transportation Systems, vol. 17, no. 4, pp. 960–969, Apr. 2015.
- [157] H. Hasbullah, I. A. Soomro et al., “Denial of service (dos) attack and its possible solutions in VANET,” International Journal of Electronics and Communication Engineering, vol. 4, no. 5, pp. 813–817, Jan. 2010.
- [158] S. A. Soleymani, A. H. Abdullah, M. Zareei, M. H. Anisi, C. Vargas-Rosales, M. K. Khan, and S. Goudarzi, “A secure trust model based on fuzzy logic in vehicular ad hoc networks with fog computing,” IEEE Access, vol. 5, pp. 15 619–15 629, Jul. 2017.
- [159] Y. Hao, J. Tang, Y. Cheng, and C. Zhou, “Secure data downloading with privacy preservation in vehicular ad hoc networks,” in Proc. 2010 IEEE International Conference on Communications (ICC), May 2010, pp. 1–5.
- [160] S. Garg, A. Singh, K. Kaur, G. S. Aujla, S. Batra, N. Kumar, and M. S. Obaidat, “Edge computing-based security framework for big data analytics in VANETs,” IEEE Network, vol. 33, no. 2, pp. 72–81, Mar. 2019.
- [161] M. Eltoweissy, S. Olariu, and M. Younis, “Towards autonomous vehicular clouds,” in Proc. International Conference on Ad Hoc Networks. Springer, Aug. 2010, pp. 1–16.
- [162] S. Arif, S. Olariu, J. Wang, G. Yan, W. Yang, and I. Khalil, “Datacenter at the airport: Reasoning about time-dependent parking lot occupancy,” IEEE Transactions on Parallel and Distributed Systems, vol. 23, no. 11, pp. 2067–2080, Jan. 2012.
- [163] J. Feng, Z. Liu, C. Wu, and Y. Ji, “AVE: Autonomous vehicular edge computing framework with ACO-based scheduling,” IEEE Transactions on Vehicular Technology, vol. 66, no. 12, pp. 10 660–10 675, Dec. 2017.
- [164] S. Olariu, I. Khalil, and M. Abuelela, “Taking VANET to the clouds,” International Journal of Pervasive Computing and Communications, vol. 7, no. 1, pp. 7–21, Apr. 2011.
- [165] J. Wang, K. Liu, K. Xiao, C. Chen, W. Wu, V. C. S. Lee, and S. H. Son, “Dynamic clustering and cooperative scheduling for vehicle-to-vehicle communication in bidirectional road scenarios,” IEEE Transactions on Intelligent Transportation Systems, vol. 19, no. 6, pp. 1913–1924, Jun. 2018.
- [166] H. Gong, L. Yu, N. Liu, and X. Zhang, “Mobile content distribution with vehicular cloud in urban VANETs,” China Communications, vol. 13, no. 8, pp. 84–96, Aug. 2016.
- [167] J. Zhang, Q. Zhang, and W. Jia, “VC-MAC: A cooperative mac protocol in vehicular networks,” IEEE Transactions on Vehicular Technology, vol. 58, no. 3, pp. 1561–1571, Aug. 2008.
- [168] Y.-T. Yu, T. Punihaole, M. Gerla, and M. Sanadidi, “Content routing in the vehicle cloud,” in Proc. IEEE Military Communications Conference, Orlando, FL, USA, Oct. 2012.
- [169] T. Kim, H. Min, and J. Jung, “Vehicular datacenter modeling for cloud computing: Considering capacity and leave rate of vehicles,” Future Generation Computer Systems, vol. 88, pp. 363–372, May 2018.
- [170] J. A. Guerrero-ibanez, S. Zeadally, and J. Contreras-Castillo, “Integration challenges of intelligent transportation systems with connected vehicle, cloud computing, and internet of things technologies,” IEEE Wireless Communications, vol. 22, no. 6, pp. 122–128, Dec. 2015.
- [171] W. He, G. Yan, and L. D. Xu, “Developing vehicular data cloud services in the IoT environment,” IEEE Transactions on Industrial Informatics, vol. 10, no. 2, pp. 1587–1595, May 2014.
- [172] R. Yu, Y. Zhang, S. Gjessing, W. Xia, and K. Yang, “Toward cloud-based vehicular networks with efficient resource management,” IEEE Network, vol. 27, no. 5, pp. 48–55, Sep. 2013.
- [173] J. Wang, T. Liu, K. Liu, B. Kim, J. Xie, and Z. Han, “Computation offloading over fog and cloud using multi-dimensional multiple knapsack problem,” in Proc. IEEE Global Communications Conference (GLOBECOM), Dec. 2018, pp. 1–7.
- [174] H. Zhang, Q. Zhang, and X. Du, “Toward vehicle-assisted cloud computing for smartphones,” IEEE Transactions on Vehicular Technology, vol. 64, no. 12, pp. 5610–5618, Dec. 2015.
- [175] M. Tao, K. Ota, and M. Dong, “Foud: Integrating fog and cloud for 5G-enabled V2G networks,” IEEE Network, vol. 31, no. 2, pp. 8–13, Mar. 2017.
- [176] J. Zhou, X. Dong, Z. Cao, and A. V. Vasilakos, “Secure and privacy preserving protocol for cloud-based vehicular DTNs,” IEEE Transactions on Information Forensics and Security, vol. 10, no. 6, pp. 1299–1314, Feb. 2015.
- [177] X. Ge, Z. Li, and S. Li, “5G software defined vehicular networks,” IEEE Communications Magazine, vol. 55, no. 7, pp. 87–93, Feb. 2017.
- [178] M. Sookhak, F. R. Yu, Y. He, H. Talebian, N. S. Safa, N. Zhao, M. K. Khan, and N. Kumar, “Fog vehicular computing: Augmentation of fog computing using vehicular cloud computing,” IEEE Vehicular Technology Magazine, vol. 12, no. 3, pp. 55–64, Sep. 2017.
- [179] H. Khayyam, J. Abawajy, B. Javadi, A. Goscinski, A. Stojcevski, and A. Bab-Hadiashar, “Intelligent battery energy management and control for vehicle-to-grid via cloud computing network,” Applied Energy, vol. 111, pp. 971–981, Nov. 2013.
- [180] W. Zhang, S. Zhou, A. Srinivasan, J. Wu, and Y. Lin, “Detecting attacks smartly in vehicle cloud computing,” in Proc. IEEE Conferences on Ubiquitous Intelligence and Computing, Advanced and Trusted Computing, Scalable Computing and Communications, Cloud and Big Data Computing, Internet of People, and Smart World Congress (UIC/ATC/ScalCom/CBDCom/IoP/SmartWorld), Toulouse, France, Jul. 2016, pp. 245–252.
- [181] S. Nunna, A. Kousaridas, M. Ibrahim, M. Dillinger, C. Thuemmler, H. Feussner, and A. Schneider, “Enabling real-time context-aware collaboration through 5G and mobile edge computing,” in Proc. IEEE 12th International Conference on Information Technology - New Generations, Las Vegas, NV, USA, Apr. 2015, pp. 601–605.
- [182] N. Kumar, S. Zeadally, and J. J. P. C. Rodrigues, “Vehicular delay-tolerant networks for smart grid data management using mobile edge computing,” IEEE Communications Magazine, vol. 54, no. 10, pp. 60–66, Oct. 2016.
- [183] T. Y. He, N. Zhao, and H. Yin, “Integrated networking, caching and computing for connected vehicles: A deep reinforcement learning approach,” IEEE Transactions on Vehicular Technology, no. 99, Jan. 2017.
- [184] I. Stojmenovic, “Fog computing: A cloud to the ground support for smart things and machine-to-machine networks,” in Proc. IEEE Australasian Telecommunication Networks and Applications Conference (ATNAC), Southbank, VIC, Australia, Nov. 2014, pp. 117–122.
- [185] P. Jaworski, T. Edwards, J. Moore, and K. Burnham, “Cloud computing concept for intelligent transportation systems,” in Proc. IEEE International Conference on Intelligent Transportation Systems (ITSC), Washington, DC, USA, Oct. 2011, pp. 391–936.
- [186] N. B. Truong, G. M. Lee, and Y. Ghamri-Doudane, “Software defined networking-based vehicular adhoc network with fog computing,” in Proc. IEEE International Symposium on Integrated Network Management (IM), Ottawa, ON, Canada, May 2015, pp. 1202–1207.
- [187] D. J. Deng, S. Y. Lien, C. C. Lin, S. C. Hung, and W. B. Chen, “Latency control in software-defined mobile-edge vehicular networking,” IEEE Communications Magazine, vol. 55, no. 8, pp. 87–93, Aug. 2017.
- [188] S. Chaba, R. Kumar, R. Pant, and M. Dave, “Secure and efficient key delivery in VANET using cloud and fog computing,” in Proc. International Conference on Computer, Communications and Electronics (Comptelix), Jaipur, India, Jul. 2017, pp. 27–31.
- [189] J. Ni, A. Zhang, X. Lin, and X. S. Shen, “Security, privacy, and fairness in fog-based vehicular crowdsensing,” IEEE Communications Magazine, vol. 55, no. 6, pp. 146–152, Jun. 2017.
- [190] Z. Zhao, L. Guardalben, M. Karimzadeh, J. Silva, T. Braun, and S. Sargento, “Mobility prediction-assisted over-the-top edge prefetching for hierarchical VANETs,” IEEE Journal on Selected Areas in Communications, vol. 36, no. 8, pp. 1786 – 1801, Jun. 2018.
- [191] H. Wang and J. Xie, “User preference based energy-aware mobile ar system with edge computing,” in Proc. IEEE Conference on Computer Communications (INFOCOM), Toronto, ON, Canada, Jul. 2020, pp. 1379–1388.
- [192] H. Wang, J. Xie, and T. Han, “A smart service rebuilding scheme across cloudlets via mobile AR frame feature mapping,” in Proc. IEEE ICC, Kansas City, MO, USA, 2018, pp. 1–6.
- [193] H. Wang, B. Kim, J. Xie, and Z. Han, “How is energy consumed in smartphone deep learning apps? Executing locally vs. remotely,” in Proc. IEEE Globecom, Waikoloa, HI, USA, 2019, pp. 1–6.
- [194] S. A. A. Shah, E. Ahmed, M. Imran, and S. Zeadally, “5G for vehicular communications,” IEEE Communications Magazine, vol. 56, no. 1, pp. 111–117, Jan. 2018.
- [195] J. Lee, Y. Kim, Y. Kwak, J. Zhang, A. Papasakellariou, T. Novlan, C. Sun, and Y. Li, “Lte-advanced in 3GPP Rel-13/14: an evolution toward 5G,” IEEE Communications Magazine, vol. 54, no. 3, pp. 36–42, Mar. 2016.
- [196] M. A. Elsadig and Y. A. Fadlalla, “VANETs security issues and challenges: A survey,” Indian Journal of Science and Technology, vol. 9, no. 28, pp. 1–8, Jul. 2016.
- [197] X. Lin, X. Sun, P.-H. Ho, and X. Shen, “GSIS: A secure and privacy-preserving protocol for vehicular communications,” IEEE Transactions on Vehicular Technology, vol. 56, no. 6, pp. 3442–3456, Nov. 2007.
- [198] R. I. Meneguette, A. Boukerche, A. H. M. Pimenta, and M. Meneguette, “A resource allocation scheme based on semi-markov decision process for dynamic vehicular clouds,” in Proc. IEEE International Conference on Communications (ICC), Paris, France, May 2017.
- [199] M. Gerla, E. K. Lee, G. Pau, and U. Lee, “Internet of vehicles: From intelligent grid to autonomous cars and vehicular clouds,” in Proc. IEEE World Forum on Internet of Things (WF-IoT), Seoul, South Korea, Mar. 2014, pp. 241–246.
- [200] T. Li, M. Zhao, A. Liu, and C. Huang, “On selecting vehicles as recommenders for vehicular social networks,” IEEE Access, vol. 5, pp. 5539–5555, Mar. 2017.
- [201] C. Wang, Y. Li, D. Jin, and S. Chen, “On the serviceability of mobile vehicular cloudlets in a large-scale urban environment,” IEEE Transactions on Intelligent Transportation Systems, vol. 17, no. 10, pp. 2960–2970, Oct. 2016.
- [202] S. K. Datta, J. Haerri, C. Bonnet, and R. F. D. Costa, “Vehicles as connected resources: Opportunities and challenges for the future,” IEEE Vehicular Technology Magazine, vol. 12, no. 2, pp. 26–35, Jun. 2017.
- [203] E. Lee, E. K. Lee, M. Gerla, and S. Y. Oh, “Vehicular cloud networking: architecture and design principles,” IEEE Communications Magazine, vol. 52, no. 2, pp. 148–155, Feb. 2014.
- [204] X. Hou, Y. Li, M. Chen, D. Wu, D. Jin, and S. Chen, “Vehicular fog computing: A viewpoint of vehicles as the infrastructures,” IEEE Transactions on Vehicular Technology, vol. 65, no. 6, pp. 3860–3873, Jun. 2016.
- [205] I. Stojmenovic and S. Wen, “The fog computing paradigm: Scenarios and security issues,” in Proc. IEEE Computer Science and Information Systems, Warsaw, Poland, Sep. 2014.
- [206] M. Gerla, “Vehicular cloud computing,” in Proc. IEEE The 11th Annual Mediterranean Ad Hoc Networking Workshop (Med-Hoc-Net), Ayia Napa, Cyprus, Jun. 2012, pp. 152–155.
- [207] J. Cui, L. Wei, J. Zhang, Y. Xu, and H. Zhong, “An efficient message-authentication scheme based on edge computing for vehicular ad hoc networks,” IEEE Transactions on Intelligent Transportation Systems, vol. 20, no. 5, pp. 1621 – 1632, May 2018.
- [208] R. Hussain, J. Son, H. Eun, S. Kim, and H. Oh, “Rethinking vehicular communications: Merging VANET with cloud computing,” in Proc. IEEE CloudCom, Taipei, Taiwan, Dec. 2012, pp. 606–609.
- [209] A. Soua and S. Tohme, “Multi-level SDN with vehicles as fog computing infrastructures: A new integrated architecture for 5G-VANETs,” in Proc. 21st Conference on Innovation in Clouds, Internet and Networks and Workshops (ICIN), Paris, France, Feb. 2018.
- [210] A. A. Khan, M. Abolhasan, and W. Ni, “5G next generation VANETs using SDN and fog computing framework,” in Proc. IEEE Annual Consumer Communications Networking Conference (CCNC), Las Vegas, NV, USA, Jan. 2018.
- [211] T. Baykas, C. S. Sum, Z. Lan, J. Wang, M. A. Rahman, H. Harada, and S. Kato, “IEEE 802.15.3c: the first IEEE wireless standard for data rates over 1 Gb/s,” IEEE Communications Magazine, vol. 49, no. 7, pp. 114–121, Jul. 2011.
- [212] Z. Liu, Y. Yan, X. Qu, and Y. Zhang, “Bus stop-skipping scheme with random travel time,” Transportation Research Part C: Emerging Technologies, vol. 35, pp. 46–56, Oct. 2013.
- [213] J. Wu, B. Cheng, C. Yuen, N. M. Cheung, and J. Chen, “Trading delay for distortion in one-way video communication over the Internet,” IEEE Transactions on Circuits and Systems for Video Technology, vol. 26, no. 4, pp. 711–723, Apr. 2016.
- [214] Y. Niu, Y. Li, D. Jin, L. Su, and V. Vasilakos, “A survey of millimeter wave communications (mmwave) for 5G: opportunities and challenges,” Springer Wireless Networks, vol. 21, no. 8, pp. 2657–2676, Feb. 2015.
- [215] J. Qiao, X. S. Shen, J. W. Mark, Q. Shen, Y. He, and L. Lei, “Enabling device-to-device communications in millimeter-wave 5g cellular networks,” IEEE Communications Magazine, vol. 53, no. 1, pp. 209–215, Jan. 2015.
- [216] D. Jiang and L. Delgrossi, “IEEE 802.11 p: Towards an international standard for wireless access in vehicular environments,” in Proc. 2008 IEEE Vehicular Technology Conference (VTC), May 2008, pp. 2036–2040.
- [217] J. Yin, T. ElBatt, G. Yeung, B. Ryu, S. Habermas, H. Krishnan, and T. Talty, “Performance evaluation of safety applications over DSRC vehicular Ad Hoc networks,” in Proc. the 1st ACM international Workshop on Vehicular Ad Hoc Networks, Oct. 2004, pp. 1–9.
- [218] V. Taliwal, D. Jiang, H. Mangold, C. Chen, and R. Sengupta, “Empirical determination of channel characteristics for DSRC vehicle-to-vehicle communication,” in Proc. the 1st ACM International Workshop on Vehicular Ad Hoc Networks, Oct. 2004, pp. 88–88.
- [219] F. Bai, D. D. Stancil, and H. Krishnan, “Toward understanding characteristics of dedicated short range communications (DSRC) from a perspective of vehicular network engineers,” in Proc. the 6th ACM Annual International Conference on Mobile Computing and Networking, Sep. 2010, pp. 329–340.
- [220] X. Wu, S. Subramanian, R. Guha, R. G. White, J. Li, K. W. Lu, A. Bucceri, and T. Zhang, “Vehicular communications using DSRC: challenges, enhancements, and evolution,” IEEE Journal on Selected Areas in Communications, vol. 31, no. 9, pp. 399–408, Sep. 2013.
- [221] P. Kamat, A. Baliga, and W. Trappe, “An identity-based security framework for VANETs,” in Proc. the 3rd ACM International Workshop on Vehicular Ad Hoc Networks, Sep. 2006, pp. 94–95.
- [222] G. Calandriello, P. Papadimitratos, J.-P. Hubaux, and A. Lioy, “Efficient and robust pseudonymous authentication in VANET,” in Proc. the fourth ACM International Workshop on Vehicular Ad Hoc Networks, Sep. 2007, pp. 19–28.
- [223] M. Verma and D. Huang, “SeGCom: secure group communication in VANETs,” in Proc. 6th IEEE Consumer Communications and Networking Conference, Jan. 2009, pp. 1–5.
- [224] I. T. S. Committee et al., “IEEE trial-use standard for wireless access in vehicular environments-security services for applications and management messages,” IEEE Vehicular Technology Society Standard, vol. 1609, Jul. 2006.
- [225] M. Raya, A. Aziz, and J.-P. Hubaux, “Efficient secure aggregation in VANETs,” in Proc. the 3rd ACM International Workshop on Vehicular Ad Hoc Networks, Sep. 2006, pp. 67–75.
- [226] D. Huang, X. Hong, and M. Gerla, “Situation-aware trust architecture for vehicular networks,” IEEE Communications Magazine, vol. 48, no. 11, pp. 128–135, Nov. 2010.
- [227] P. Golle, D. Greene, and J. Staddon, “Detecting and correcting malicious data in VANETs,” in Proc. the 1st ACM International Workshop on Vehicular Ad Hoc Networks, Oct. 2004, pp. 29–37.
- [228] C. Harsch, A. Festag, and P. Papadimitratos, “Secure position-based routing for VANETs,” in Proc. 66th IEEE Vehicular Technology Conference, Oct. 2007, pp. 26–30.
- [229] A. Vora and M. Nesterenko, “Secure location verification using radio broadcast,” IEEE Transactions on Dependable and Secure Computing, vol. 3, no. 4, pp. 377–385, Oct. 2006.
- [230] Q. Zhang, L. Cheng, and R. Boutaba, “Cloud computing: state-of-the-art and research challenges,” Journal of Internet Services and Applications, vol. 1, no. 1, pp. 7–18, May 2010.