Asymmetric Traveling Salesman Path and
Directed Latency Problems111A preliminary
version of this paper appeared in the Proceedings of 21st Annual ACM-SIAM Symposium on
Discrete Algorithms
Abstract
We study integrality gaps and approximability of two closely related problems on directed graphs. Given a set of nodes in an underlying asymmetric metric and two specified nodes and , both problems ask to find an - path visiting all other nodes. In the asymmetric traveling salesman path problem (ATSPP), the objective is to minimize the total cost of this path. In the directed latency problem, the objective is to minimize the sum of distances on this path from to each node. Both of these problems are NP-hard. The best known approximation algorithms for ATSPP had ratio [7, 9] until the very recent result that improves it to [3, 9]. However, only a bound of for the integrality gap of its linear programming relaxation has been known. For directed latency, the best previously known approximation algorithm has a guarantee of , for any constant [25].
We present a new algorithm for the ATSPP problem that has an approximation ratio of , but whose analysis also bounds the integrality gap of the standard LP relaxation of ATSPP by the same factor. This solves an open problem posed in [7]. We then pursue a deeper study of this linear program and its variations, which leads to an algorithm for the -person ATSPP (where - paths of minimum total length are sought) and an -approximation for the directed latency problem.
1 Introduction
Let be a complete directed graph on a set of nodes and let be a cost function satisfying the directed triangle inequality for all . However, is not necessarily symmetric: it may be that for some nodes . In the metric Asymmetric Traveling Salesman Path Problem (ATSPP), we are also given two distinct nodes . The goal is to find a path that visits all the nodes in while minimizing the sum . ATSPP can be used to model scenarios such as minimizing the total cost of travel for a person trying to visit a set of cities on the way from a starting point to a destination. This is a variant of the classical Asymmetric Traveling Salesman Problem (ATSP), where the goal is to find a minimum-cost cycle visiting all nodes. In the -person ATSPP, given an integer , the goal is to find paths from to such that every node is contained in at least one path and the sum of path lengths is minimized.
Related to ATSPP is the directed latency problem. On the same input, the goal is to find a path that minimizes the sum of latencies of the nodes. Here, the latency of node in the path is defined as . The objective can be thought of as minimizing the total waiting time of clients or the average response time. There are possible variations in the problem definition, such as asking for a cycle instead of a path, or specifying only but not , but they easily reduce to the version that we consider. Other names used in the literature for this problem are the deliveryman problem [23] and the traveling repairman problem [1].
1.1 Related work
Both ATSPP and the directed latency problem are closely related to the classical Traveling Salesman Problem (TSP), which asks to find the cheapest Hamiltonian cycle in a complete undirected graph with edge costs [21, 15]. In general weighted graphs, TSP is not approximable. However, in most practical settings it can be assumed that edge costs satisfy the triangle inequality (i.e. ). Though metric TSP is still NP-hard, the well-known algorithm of Christofides [8] has an approximation ratio of . Later the analysis in [27, 29] showed that this approximation algorithm actually bounds the integrality gap of a linear programming relaxation for TSP known as the Held-Karp LP. This integrality gap is also known to be at least . Furthermore, for all , approximating TSP within a factor of is NP-hard [26]. Christofides’ heuristic was adapted to the problem of finding the cheapest Hamiltonian path in a metric graph with an approximation guarantee of if at most one endpoint is specified or if both endpoints are given [16].
In contrast to TSP, no constant-factor approximation for its asymmetric version is known. The current best approximation for ATSP is the very recent result of Asadpour et al. [3], which gives an -approximation algorithm. It also upper-bounds the integrality gap of the asymmetric Held-Karp LP relaxation by the same factor. Previous algorithms guarantee a solution of cost within factor of optimum [11, 19, 18, 9]. The algorithm of Frieze et al. [11] is shown to upper-bound the Held-Karp integrality gap by in [28], and a different proof that bounds the integrality gap of a slightly weaker LP is obtained in [24]. The best known lower bound on the Held-Karp integrality gap is essentially 2 [5], and tightening these bounds remains an important open problem. ATSP is NP-hard to approximate within [26].
The path version of the problem, ATSPP, has been studied much less than ATSP, but there are some recent results concerning its approximability. An approximation algorithm for it was given by Lam and Newman [20], which was subsequently improved to by Chekuri and Pal [7]. Feige and Singh [9] improved upon this guarantee by a constant factor and also showed that the approximability of ATSP and ATSPP are within a constant factor of each other, i.e. an -approximation for one implies an -approximation for the other. Combined with the result of [3], this implies an approximation for ATSPP. However, none of these algorithms bound the integrality gap of the LP relaxation for ATSPP. This integrality gap was considered by Nagarajan and Ravi [25], who showed that it is at most . To the best of our knowledge, the asymmetric path version of the -person problem has not been studied previously. However, some work has been done on its symmetric version, where the goal is to find rooted cycles of minimum total cost (e.g., [12]).
The metric minimum latency problem is NP-hard for both the undirected and directed versions since an exact algorithm for either of these could be used to efficiently solve the Hamiltonian Path problem. The first constant-factor approximation for minimum latency on undirected graphs was developed by Blum et al. [4]. This was subsequently improved in a series of papers from 144 to 21.55 [13], then to 7.18 [2] and ultimately to 3.59 [6]. Blum et al. [4] also observed that there is some constant such that there is no -approximation for minimum latency unless P = NP. For directed graphs, Nagarajan and Ravi [25] gave an approximation algorithm that runs in time , where is the integrality gap of an LP relaxation for ATSPP. Using their upper bound on , they obtained a guarantee of , which is the best approximation ratio known for this problem before our present results.
1.2 Our results
In this paper we study both the ATSPP and the directed latency problem.
| min | (1) | |||
| s.t. | (2) | |||
| (3) | ||||
| (4) | ||||
| (5) | ||||
The natural LP relaxation for ATSPP is (1) with , where denotes the set of outgoing edges from a vertex or a set of vertices, and denotes the set of incoming edges. A variable indicates that edge is included in a solution. Let us refer to this linear program as LP(), as we study it for different values of in constraints (5). We begin in Section 2 by proving that the integrality gap of LP() is .
Theorem 1.1
If is the cost of a feasible solution to LP (1) with , then one can find, in polynomial time, a Hamiltonian path from to with cost at most .222All logarithms in this paper are base 2.
We note that, despite bounding the integrality gap, our algorithm is actually combinatorial and does not require solving the LP. We strengthen the result of Theorem 1.1 by extending it to any with . This captures the LP of [25], which has , and is also used in our algorithm for the directed latency problem. We prove the following theorem in Section 3.
Theorem 1.2
If is the cost of a feasible solution to LP (1) with , then one can find, in polynomial time, a Hamiltonian path from to with cost at most .
It is worth observing that this theorem, together with the results of [25], imply a polylogarithmic approximation algorithm for the directed latency problem which runs in quasi-polynomial time, as well as a polynomial-time -approximation. However, that approach relies on guessing a large number of intermediate vertices of the path, and thus does not yield an algorithm that has both a polynomial running time and a polylogarithmic approximation guarantee. So, to obtain a polynomial-time approximation, we use a different approach. For that we consider LP() for values of that include . If we allow then LP(), as a relaxation of ATSPP, can be shown to have an unbounded integrality gap. However, we prove the following theorem in Section 4.
Theorem 1.3
If is the cost of a feasible solution to LP (1) with , for integer , then one can find, in polynomial time, a collection of at most paths from to , such that each vertex of appears on at least one path, and the total cost of all these paths is at most .
Next, we study another generalization of the ATSPP, namely the -person asymmetric traveling salesman path problem. In Section 5 we prove the following theorem:
Theorem 1.4
There is an approximation algorithm for the -person ATSPP. Moreover, the integrality gap of its LP relaxation is bounded by the same factor.
Given these results concerning LP(), we study a particular LP relaxation for the directed latency problem in Section 6. We improve upon the -approximation of [25] substantially by proving the following:
Theorem 1.5
A solution to the directed latency problem can be found in polynomial time that has cost no more than , where is the value of LP relaxation (8), which is also a lower bound on the integer optimum.
We note that this seems to be the first time that a bound is placed on the integrality gap of any LP relaxation for the minimum latency problem, even in the undirected case.
2 Integrality gap of ATSPP
We show that LP relaxation (1) of ATSPP with has integrality gap of . Let be its optimal fractional solution, and let be its cost. We define a path-cycle cover on a subset of vertices containing and to be the union of one - path and zero or more cycles, such that each occurs in exactly one of these subgraphs. The cost of a path-cycle cover is the sum of costs of its edges.
Our approach is an extension of the algorithm by Frieze et al. [11], analyzed by Williamson [28] to bound the integrality gap for ATSP. That algorithm finds a minimum-cost cycle cover on the current set of vertices, chooses an arbitrary representative vertex for each cycle, deletes other vertices of the cycles, and repeats, at the end combining all the cycle covers into a Hamiltonian cycle. As this is repeated at most times, and the cost of each cycle cover is at most the cost of the LP solution, the upper bound of on the integrality gap is obtained. In our algorithm for ATSPP, the analogue of a cycle cover is a path-cycle cover (also used in [20]), whose cost is at most the cost of the LP solution (Lemma 2.2). At the end we combine the edges of path-cycle covers to produce a Hamiltonian path. However, the whole procedure is more involved than in the case of ATSP cycle. For example, we don’t choose arbitrary representative vertices, but use an amortized analysis to ensure that each vertex only serves as a representative a bounded number of times.
We note that a path-cycle cover of minimum cost can be found by a combinatorial algorithm, using a reduction to minimum-cost perfect matching, as explained in [20]. In the proof of Lemma 2.2 below, we make use of the following splitting-off theorem, as also done in [24], where splitting off edges and refers to replacing these edges with the edge (unless , in which case the two edges are just deleted).
Theorem 2.1 (Frank [10] and Jackson [17])
Let be a Eulerian directed graph and . There exists an edge such that splitting off and does not reduce the directed connectivity from to for any .
This theorem also applies to weighted Eulerian graphs, i.e. ones in which the weighted out-degree of every vertex is equal to its weighted in-degree, since weighted edges can be replaced by multiple parallel edges, producing an unweighted Eulerian multigraph.
Lemma 2.2
For any subset that includes and , there is a path-cycle cover of of cost at most .
Proof. Consider the graph obtained from by assigning capacities to edges and adding a dummy edge from to with unit capacity. From constraints (2)-(4) of LP() it follows that this is a weighted Eulerian graph. Constraints (5) and the max-flow min-cut theorem imply that for any , the directed connectivity from to in is at least .
We apply the splitting-off operation on , as guaranteed by Theorem 2.1, to vertices in until all of them are disconnected from the rest of the graph. Let be the resulting graph on and let be its edge capacities except for the dummy edge (which was unaffected by the splitting-off process). By Theorem 2.1, the directed connectivity from to any does not decrease from the splitting-off operations, which means that in it is still at least . This ensures that satisfies constraints (5) for all sets with and , and is a feasible solution to LP() on the subset of vertices. Furthermore, the triangle inequality implies that the cost of is no more than that of , namely .
Now we make the observation that if we remove from LP() constraints (5) for all but singleton sets, the resulting LP is equivalent to a circulation problem, and thus has an integer optimal solution. Since there is a feasible solution to LP() on the set of cost at most (namely ), and removing a constraint can only decrease the optimal objective value, it means that there is an integer solution to the following program that costs no more than :
| min | (6) | ||||
| s.t. | |||||
| (7) | |||||
In principle, this integer solution can have for some nodes . In this case, we find a Euler tour of each component of the resulting graph (with dummy edge added in) and shortcut it over any repeated vertices. This ensures that for all without increasing the cost. But such a solution is precisely a path-cycle cover of .
is an acyclic flow on the nodes
We consider Algorithm 1. Roughly speaking, the idea is to find a path-cycle cover, select a representative node for each cycle, delete the other cycle nodes, and repeat. Actually, a representative is selected for a component more general than a simple cycle, namely a union of one or more cycles. We ensure that each vertex is selected as a representative at most times, which means that after iterations, each surviving vertex has participated in the acyclic part of the path-cycle covers at least times. This allows us at the end to find an - path which spans all the surviving vertices, , and consists entirely of edges in the acyclic part, , of the union of all the path-cycle covers, using a technique of [25]. Then we insert into it the subpaths obtained from the cyclic part, , of the union of path-cycle covers, connected through their representative vertices. We occasionally treat subgraphs satisfying appropriate degree constraints as flows or circulations.
Lemma 2.3
During the course of the algorithm, no label exceeds the value .
The idea of the proof is, as the algorithm proceeds, to maintain a forest on the set of nodes , such that the number of leaves in a subtree rooted at any node is at least . The lemma then follows because the total number of leaves is at most . We first prove an auxiliary claim.
Claim 2.4
Proof. Let be the value of at the start of the current iteration of the outside loop, i.e. before is added to it on line 4. is acyclic, because during the course of the loop, all cycles of are subtracted from it. So is a union of cycles, formed from the sum of an acyclic flow and a path-cycle cover , which sends exactly one unit of flow through each vertex.
Consider a topological ordering of nodes based on the flow , and let and be the first and last nodes of , respectively, in this ordering. As always contains at least two nodes, and are distinct. Since and participate in some cycle(s) in , their in-degrees are at least 1. We now claim that the in-degree of in is at most 1. Indeed, since all other nodes of are later than in the topological ordering, it cannot have any flow coming from them in . So the only incoming flow to can be in . But since sends a flow of exactly one unit through each vertex, the in-degree of in is at most one. A symmetrical argument can be made for , showing that its out-degree in is at most one. But since is a union of cycles, every node’s in-degree is equal to its out-degree, and the in-degree of is also at most 1.
Proof of Lemma 2.3. As the algorithm proceeds, let us construct a forest on the set of nodes . Initially, each node is the root of its own tree. We maintain the invariant that is the set of tree roots in this forest. For each component that the algorithm considers, and the node found on line 8, we attach the nodes of , except , as children of . Note that the invariant is maintained, as these nodes are removed from on line 12. The set of nodes of each component found on line 6 is always a subset of , and thus our construction indeed produces a forest.
We show by induction on the steps of the algorithm that if a node has label , then its subtree contains at least leaves. Thus, since there are nodes total, no label can exceed . At the beginning of the algorithm, all labels are 0, and all trees have one leaf each, so the base case holds. Now consider some iteration in which the label of vertex is increased from to . By Claim 2.4, there are nodes (possibly one of them equal to ) with . Since minimizes among all vertices , we have that and , and thus and . Thus, by the induction hypothesis, the trees rooted at and each have at least leaves. Because we update the forest in such a way that ’s new tree contains all the leaves of trees previously rooted at and , this tree now has at least leaves.
Lemma 2.5
At the end of the algorithm’s main loop, the flow in passing through any node is equal to , and thus (by Lemma 2.3) is at least .
Proof. There are iterations, each of which adds one unit of flow through each vertex . We now claim that for a vertex , the amount of flow removed from it is equal to its label, . Flow is removed from only if becomes part of some component . Now, if it is ever part of , but not chosen as a representative on line 8, then it is removed from . Thus, we are only concerned about vertices that are chosen as representatives every time that they are part of . Such a vertex has flow going through it in , which is the amount subtracted from . But since this is also the amount by which its label increases, the lemma follows.
We now show that Algorithm 1 returns a Hamiltonian - path of cost at most .
Proof of Theorem 1.1. At the end of the main loop, all nodes of are part of either or or both. So when all components of are incorporated into the path , all nodes of become part of the path. We bound the cost of all the edges used in the final path by the total cost of all the path-cycle covers found on line 3 of the algorithm. We note that at the end of the algorithm, the cost of the flow is no more than this total.
We claim that when the - path is found on line 17, contains flow on every edge between consecutive nodes of . This is similar to an argument used in [25]. First, since is acyclic, it has a topological ordering. Suppose we find a flow decomposition of into paths. There are at most such paths, and, by Lemma 2.5, each vertex of participates in at least , or more than half, of them. This means that any two vertices must share a path, say , in this decomposition. In particular, suppose that immediately follows in the path . This means that appears later than in the topological order, so on comes after . Moreover, we claim that on , will be the immediate successor of . If not, suppose that there is a node that appears between and in . But this means that in the topological ordering (and thus in ), will appear after and before , which contradicts the fact that they are consecutive in . So we conclude that there is an edge with flow in between any two consecutive nodes of , and thus the path costs no more than the flow .
Regarding , we note that it is a sum of cycles, and thus Eulerian. So it is possible to find a Euler tour of each of its components, using only edges with flow in . The subsequent shortcutting can only decrease the cost. Thus, the total cost of cycles found on line 19 is no more than the cost of the flow . To describe how these cycles are incorporated into the path , we show that each of them (or, equivalently, each connected component of ) shares exactly one node with (and thus with ). Note that every component added to contains only nodes that are in at that time. Moreover, when this is done, all but one nodes of are expelled from . So when several components of are connected by the addition of , the invariant is maintained that there is one node per component that is shared with . Now, suppose that is the vertex shared by the cycle obtained from component and the path . On line 20, we incorporate the cycle into the path by following the path up to , then following the cycle up to the predecessor of , then connecting it to the successor of on the path. By triangle inequality, the resulting longer path costs no more than the sum of costs of the old path and the cycle.
3 Integrality gap for relaxed ATSPP LP
Consider LP() with , and say that it has cost . We bound its integrality gap for ATSPP. As in the proof of Lemma 2.2, we can apply splitting-off to obtain a feasible solution to LP(), of cost at most , on a graph induced by a subset of vertices . Let be such a solution. Lemma 3.1 below shows how to use to find a feasible fractional solution to LP (6) on , of cost within a constant factor of , namely . Since LP (6) has integer optimum, there is an integer solution to LP (6) on , and thus a path-cycle cover, of cost at most . Then we can proceed as in Section 2, applying Algorithm 1 to bound the cost of the resulting ATSPP solution by times the path-cycle cover cost. This shows that LP() has integrality gap at most , proving Theorem 1.2.
Lemma 3.1
Given a solution to LP(), with , on a subset , with cost at most , a feasible solution to LP (6) on of cost at most can be found.
Proof. Multiply by . Now it constitutes a flow of units from to . Constraints (5), restricted to sets of size 1, imply that each node now has at least one unit of flow going through it. Find a flow decomposition of into paths and cycles, so that the union of the paths is acyclic. Let , where is the sum of flows on the paths in our decomposition, and is the sum of flows on the cycles.
Choose some such that . For any node such that the amount of flow going through is less than , shortcut any flow decomposition paths that contain , so that there is no more flow going through . Let be the set of vertices still participating in the flow. Then each vertex in has at least units of flow going through it, and each vertex in has at least units of flow going through it.
We find a topological ordering of vertices in according to (which is acyclic), and let be an - path that visits the nodes of in this topological order. We claim that the cost of is within a constant factor of the cost of . The argument for this is similar to one in the proof of Theorem 1.1. Out of units of flow going from to in , each vertex carries units, which is more than half of the total amount (as ). So for any two such vertices and , there must be shared flow paths that carry flow of at least units. In particular, for every two consecutive nodes , must contain such shared paths in which immediately follows . So the cost of is at most times the cost of .
We now define as a flow equal to one unit of - flow on the path plus times the flow . We claim that is a feasible solution to LP (6): there is exactly one unit of flow from to (as consists of cycles not containing or ); there is flow conservation at all nodes except and ; each vertex in (and thus in ) has at least one unit of flow going through it; and each vertex in has at least one unit of flow going through it (as it had at least units of flow). The cost of this solution is at most
If we set , which satisfies , we see that the cost of is at most .
4 Relaxed ATSPP LP with
Consider LP (1) with for some integer . It can be shown that, as a relaxation for the ATSPP problem, this LP has unbounded integrality gap. For example, let be an arbitrarily large value and consider the shortest path metric obtained from the graph in Figure 1. One can verify that the following assignment of -values to the arcs is feasible for LP (1) with . Assign a value of to arcs , , , , , and and a value of 1 to arcs and . Every other arc is assigned a value of 0. This assignment is feasible for the linear program and has objective function value 5. On the other hand, any Hamiltonian path from 1 to 6 has cost at least .
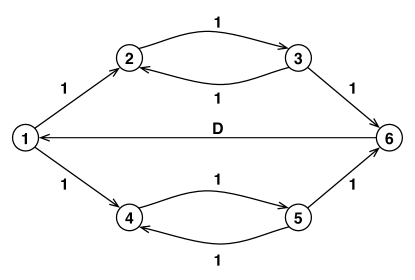
Let be the cost of the optimal solution to LP(). We show how to find paths from to , such that each node of appears on at least one path, and the total cost of all these paths is at most . Let us define a -path-cycle cover to be a set of disjoint paths from to and zero or more cycles, which together cover all nodes. Like a path-cycle cover, the minimum-cost -path-cycle cover can be found by a combinatorial algorithm by creating copies of both and and using the matching algorithm described in [20].
Lemma 4.1
For any subset that includes and , there is a -path-cycle cover of with total cost at most .
Proof. As in the proof of Lemma 2.2, we apply splitting-off to a solution of LP() to get a solution to LP() on a subset of vertices, of no greater cost. Now, if we multiply this solution by , we get a feasible solution to LP (6) with constraints (7) replaced with
The cost of this solution is no more than . But this LP has an integer optimum, which, possibly after shortcutting, is exactly a -path-cycle cover.
Proof of Theorem 1.3. We start with and repeat the following until :
-
1.
Find a -path-cycle cover of of cost at most , as guaranteed by Lemma 4.1.
-
2.
Remove from all nodes (except and ) that participate in paths of .
-
3.
For each cycle of , choose a representative node , and remove from all nodes of except .
Let us say that the procedure terminates after iterations. As the size of halves in each iteration, is at most . In the last iteration, all elements of must have participated in the paths, as otherwise there would be a node that remains in after this iteration. This implies that the graph is connected. It also has total cost at most , and, if we add edges from to , becomes Eulerian. This means that we can construct paths from to , covering all nodes of , out of edges of .
5 Algorithm for -person ATSPP
In this section we consider the -person asymmetric traveling salesman path problem. The LP relaxation for this problem is similar to LP (1), but with for constraint (3) and for constraint (5). Arguments similar to those in Section 2 show that a -path-cycle cover on any subset is a lower bound on the value of the LP relaxation for the -person ATSPP. Our algorithm constructs a solution that uses each edge of -path-cycle covers at most times, proving a bound of on the approximation ratio and the integrality gap.
Our algorithm starts by running lines 1-16 of Algorithm 1, except with iterations of the loop and finding minimum-cost -path-cycle covers instead of the path-cycle covers on line 3. Then it finds - paths in the resulting acyclic graph , satisfying conditions of Lemma 5.1 below. The algorithm concludes by incorporating each component of the circulation into one of the obtained paths, similarly to lines 18-21 of Algorithm 1.
Lemma 5.1
After lines 1-16 of Algorithm 1 are executed with iterations of the loop on line 2 and finding minimum-cost -path-cycle covers on line 3, there exist - paths in the resulting acyclic graph , such that each edge of is used at most times, and every node of is contained in at least one path. Moreover, these paths can be found in polynomial time.
Proof. We prove the existence result first. We note that the graph can support units of flow from to . This is because in each of the iterations, - paths were added to the graph, whereas the removal of cycles does not decrease the amount of flow supported. So can be decomposed into edge-disjoint paths from to . Moreover, each node of participates in at least of these paths by Lemma 2.5.
Let be the comparability graph obtained from . Namely, has the same set of nodes as , and there is an undirected edge between nodes and in if contains a directed path either from to or from to . We claim that the nodes of can be partitioned into at most cliques. As comparability graphs are perfect graphs [14], the minimum number of cliques that can be partitioned into is equal to the size of the maximum independent set in . So suppose, for the sake of contradiction, that contains an independent set of size . Then no nodes in must share any of the paths in our decomposition of . Since each appears on at least paths, there must be at least paths total in the decomposition. However, this is a contradiction, since .
Given the set of cliques in , we can convert each of them into an - path in . For each such clique , order the nodes of in a way consistent with a topological ordering of . Then contains a path from each node of to the next node : the existence of a edge in shows that there is a path between these nodes in , and the topological ordering guarantees that this path goes in the correct direction. There must also be paths from to the first node of as well as from the last node of to , since is the only source and is the only sink of . Furthermore, the acyclicity of shows that each edge of is used at most once for connecting nodes in . As there are cliques, each edge is used at most times in total. If the number of cliques is smaller than , then we can add arbitrary paths from to our collection to obtain exactly paths.
To find the required paths algorithmically, we construct the following bipartite graph from with bipartitions and . For each , add nodes to and to (note that ). Now, for each ordered pair of nodes such that there is a directed path from to in , add an edge from to . Let be the directed graph obtained from by orienting each edge according to flow . It is easy to see that any collection of disjoint cliques covering corresponds to a covering of by vertex-disjoint paths and vice-versa. We claim that there is a covering of by disjoint paths if and only if there is a matching in that leaves only nodes in and nodes in unmatched.
Consider a covering of by vertex-disjoint paths . Form a matching . Since is a collection of vertex-disjoint paths, each node has indegree and outdegree at most one in , so is a valid matching. Furthermore, since covers the nodes of with paths, then exactly nodes have indegree 0 and exactly nodes have outdegree 0. Thus, in exactly nodes of and nodes of are unmatched. Conversely, let be a matching of that leaves exactly nodes of unmatched. For each unmatched node , form a directed path in starting at by the following process. If is matched to, say, , then add arc to the path. Continue this process from until the corresponding node in is not matched. This will form vertex-disjoint paths in that cover all nodes.
As noted earlier, we know that can be covered by at most disjoint cliques. Therefore, there is a matching in that leaves at most nodes in and nodes in unmatched. Compute such a matching and map it to the corresponding paths in . Finally, extend these at most paths to paths by adding an arc from to the start of each path and an arc from the end of each path to . Again, since the only source in is and the only sink in is , these arcs correspond to edges in .
Proof of Theorem 1.4. Let be the cost of a linear programming relaxation for the problem. The edges of as well as the edges used to connect the eulerian components of to the paths come from the union of -path-cycle covers on subsets of , and thus cost at most . However, the algorithm may use each edge of up to times in the paths of Lemma 5.1, which makes the total cost of the produced solution at most .
6 Approximation algorithm for Directed Latency
We introduce LP relaxation (8) for the directed latency problem. The use of and variables in an integer programming formulation for directed latency was proposed by Mendez-Diaz et al. [22], who do a computational evaluation of the strength of its LP relaxation. However, our LP formulation uses a different set of constraints than the one in [22].
In LP (8), a variable indicates that node appears before node on the path. Similarly, for three distinct nodes , , indicates that they appear in this order on the path. For every node , we send one unit of flow from to , and we call it the -flow. Then is the amount of -flow going through edge , and is the latency of node . To show that this LP is a relaxation of the directed latency problem, given a solution path , we can set whenever the edge is in and occurs later than in , and otherwise. So is one unit of flow from to along the path . Also setting the ordering variables and to 0 or 1 appropriately and setting to the latency of in , we get a feasible solution to LP (8) of the same cost as the total latency of .
| min | (8) | |||
| s.t. | ||||
| (9) | ||||
| (10) | ||||
| (11) | ||||
| (12) | ||||
| (13) | ||||
| (14) | ||||
| (15) | ||||
| (16) | ||||
Constraints (12) are the flow conservation constraints for -flow at node . Constraints (13) ensure that no -flow enters or leaves . Constraints (14) say that -flow passes through if and only if occurs before . Since the -flow goes through every vertex, when all the variables are in , it defines an - path. We can think of the -flow as the universal flow and Constraints (15) ensure that every -flow follows an edge which has a universal flow on it. Constraints (16), in an integer solution, ensure that if a set contains some node that comes before (i.e. ), then at least one unit of -flow enters .
We note that a min-cut subroutine can be used to detect violated constraints of type (16), allowing us to solve LP (8) using the ellipsoid method. Our analysis does not actually use Constraints (15), so we can drop them from the LP. Although without these constraints the corresponding integer program may not be an exact formulation for the directed latency problem, we can still find a solution whose cost is within factor of this relaxed LP.
Lemma 6.1
Given a feasible solution to LP (8) with objective value , we can find another solution of value at most in which the ratio of the largest to smallest latency is at most .
Proof. Let be a feasible solution with value , with the largest latency value in this solution. Note that . Define a new feasible solution by . The total increase in the objective function is at most as there are nodes in total. Thus, the objective value of this new solution is at most .
Using Lemma 6.1 and scaling the edge lengths (if needed), we can assume that we have a solution satisfying the following:
Corollary 6.2
There is a feasible solution in which the smallest latency is 1 and the largest latency is at most and whose cost is at most times the optimum LP solution.
Let be the value (i.e. total latency) of this solution.
The idea of our algorithm is to construct - paths for several nodes , such that together they cover all vertices of , and then to “stitch” these paths together to obtain one Hamiltonian path. We use our results for ATSPP to construct these paths. For this, we observe that parts of a solution to the latency LP (8) can be transformed to obtain feasible solutions to different instances of LP(). For example, we can construct a Hamiltonian - path of total length as follows. From a solution to LP (8), take the -flow defined by the variables , and notice that it constitutes a feasible solution to LP(). In particular, since for all , constraints (16) of LP (8) for imply that the set constraints (5) of LP (1) are satisfied. The objective function value for LP (1) of this solution is at most . Thus, by Theorem 1.1, we can find the desired path. Of course, this path is not yet a good solution for the latency problem, as even nodes with can have latency in this path close to . Our algorithm constructs several paths of different lengths, incorporating most nodes into paths of length , and then combines these paths to obtain the final solution.
6.1 Constructing the paths
Algorithm 2 finds an approximate solution to the directed latency problem, and we now explain how some of its steps are performed. The algorithm maintains a path , initially containing only the source, and gradually adds new parts to it. This is done through operation append on lines 9, 10, and 16. To append a path to means to extend by connecting its last node to the first node of that does not already appear in , and then following until the end of . For example, if and , the result is . Step 10 appends a set of paths to . This just means sequentially appending all paths in the set, in arbitrary order, to .
Next we describe how to build paths and in Steps 9 and 10. We described above how to use Theorem 1.1 to build a Hamiltonian - path of length , which is used on line 16 of the algorithm. The idea behind building paths and with their corresponding length guarantees is similar.
To construct , we do the following. Since each node has , the amount of -flow that goes through is at least . We apply splitting-off on this flow to nodes outside of , and obtain a total of one unit of - flow over the nodes in , of cost no larger than . This flow satisfies all the constraints of LP(), including the set constraints (5), which are implied by the set constraints (16) of the latency LP (8), as for . Thus, using Theorem 1.2, we can find a path from to , spanning all the nodes of , whose cost is at most for some constant .
To obtain the set of paths , we look at the -flow going through each node of , whose amount is at least . After splitting-off all nodes outside of , we get a feasible solution of cost at most to LP(). By Theorem 1.3, we can find paths, each going from to , which together cover all the nodes of , and whose total cost is at most .
6.2 Connecting the paths
We now bound the lengths of edges introduced by the append operation in the different cases. For a path , let be the length of the edge used for appending to the path in the algorithm.
Lemma 6.3
For any , , and path , . Also, .
Proof. Let be the last node of the path before the append operation, be the last node of , and be the first node of that does not appear in . We need to bound , the distance from to .
We observe that . If , this is trivial. Otherwise, is the endpoint of some path constructed in an earlier iteration. Note that and by our assumption that , which means that . So, if we had , then would be included in the set and in the path , and thus be already contained in , which is a contradiction.
Consequently, . This means that the amount of -flow that goes through is at least . Since this flow has to reach after visiting , it has to cover a distance of at least , thus adding at least to , the latency of . Thus, , and . Now, if , it must be in , which, by definition, means that , and therefore . So . If , then .
To bound the cost of appending a path to , we need an auxiliary lemma.
Lemma 6.4
For any , if , then .
Proof. Using Constraint (10) we have:
On the other hand, , using again Constraint (10), then Constraint (11), and the assumption of the lemma. Therefore, , i.e. . Then the claim follows using Constraint (9).
Lemma 6.5
For any and , .
Proof. Let , , and be as in the proof of Lemma 6.3. To bound , we consider two cases.
Case 1: If , we apply the same proof as for Lemma 6.3 and conclude that .
Case 2: If , let be an earlier iteration of the algorithm in which node was added to . Since , it must be that , and thus . On the other hand, since , it must be that . Because , we have
Using Lemma 6.4, we get that .
Lemma 6.6
Suppose that a node is first added to path in iteration of the outer loop of the algorithm. Then the latency of in is at most , for some constant .
Proof. Let denote the length of a path . The latency of node on is at most:
Suppose that is the number of nodes that are originally placed into the set . Since a node is originally placed in if , the value of the LP solution can be bounded by:
| (17) |
Let denote the size of at the beginning of iteration of the outer loop. Note that may be larger than since some nodes may have been moved to in Step 14 of the previous iteration.
Claim 6.7
For any , the size of the set at the end of iteration is at most .
Proof. Consider the iteration . Note that the vertex is chosen precisely to maximize the number of nodes in with , which is the size of the set . If we imagine a directed graph on the set of vertices , in which an edge exists whenever , then is the vertex with highest in-degree in this graph. Now, from Constraint (11), it’s not hard to see that some vertex in will have in-degree at least . So the number of nodes removed from in step 11 of the algorithm is at least , and size of decreases at least by a factor of two. Similarly, at least half of the remaining nodes of are removed in the iteration , so overall the size of decreases at least by a factor of four.
We now show that the total latency of the final solution is at most .
Proof of Theorem 1.5. From Claim 6.7, it follows that at most a fraction of the nodes that are in at the beginning of iteration are moved to the set at the end of this iteration. Thus, for any , . This implies that .
Now we claim that the total latency of the solution is at most . This is because at most nodes are added to in iteration , and each such node has latency at most (using Lemma 6.6). Therefore, the total latency of the solution is at most:
using the bound on , re-ordering the summation, and using inequality (17). Combined with Corollary 6.2, this proves the theorem.
6.3 Extensions
The above algorithm can be easily extended to the more general setting in which every node of the graph comes with a weight and the goal is to find a Hamiltonian - path to minimize the total weighted latency, where the weighted latency of a node is equal to . This requires changing the objective function of LP (8) to and changing the definition of on line 6 of Algorithm 2 to maximize the total weight, instead of the number, of vertices in .
We also note that our approximation guarantee for directed latency is of the form , where is the integrality gap of ATSPP. So an improvement of the bound on would not immediately lead to an improvement for directed latency.
Acknowledgements
This work was partly done while the second author was visiting Microsoft Research New England; he thanks MSR for hosting him. We also thank the anonymous referees for helpful comments.
References
- [1] F. N. Afrati, S. S. Cosmadakis, C. H. Papadimitriou, G. Papageorgiou, and N. Papakostantinou. The complexity of the travelling repairman problem. Informatique Theorique et Applications, 20(1):79–87, 1986.
- [2] A. Archer, A. Levin, and D. P. Williamson. A faster, better approximation algorithm for the minimum latency problem. SIAM J. Comput., 37(5):1472–1498, 2008.
- [3] A. Asadpour, M. X. Goemans, A. Madry, S. Oveis Gharan, and A. Saberi. An -approximation algorithm for the asymmetric traveling salesman problem. In Proc. 21st ACM Symp. on Discrete Algorithms, 2010.
- [4] A. Blum, P. Chalasani, D. Coppersmith, B. Pulleyblank, P. Raghavan, and M. Sudan. The minimum latency problem. In Proc. 26th ACM Symp. on Theory of Computing, 1994.
- [5] M. Charikar, M. X. Goemans, and H. Karloff. On the integrality ratio for asymmetric TSP. In Proc. 45th IEEE Symp. on Foundations of Computer Science, 2004.
- [6] K. Chaudhuri, B. Godfrey, S. Rao, and K. Talwar. Paths, trees, and minimum latency tours. In Proc. 44th IEEE Symp. on Foundations of Computer Science, 2003.
- [7] C. Chekuri and M. Pal. An approximation ratio for the asymmetric traveling salesman path problem. Theory of Computing, 3(1):197–209, 2007.
- [8] N. Christofides. Worst-case analysis of a new heuristic for the traveling salesman problem. Technical report, Graduate School of Industrial Administration, Carnegie-Mellon University, Pittsburgh, PA, 1976.
- [9] U. Feige and M. Singh. Improved approximation ratios for traveling salesperson tours and paths in directed graphs. In Proc. 10th APPROX, 2007.
- [10] A. Frank. On connectivity properties of Eulerian digraphs. Ann. Discrete Math., 41:179–194, 1989.
- [11] A. Frieze, G. Galbiati, and F. Maffioli. On the worst-case performance of some algorithms for the asymmetric traveling salesman problem. Networks, 12:23–39, 1982.
- [12] A. M. Frieze. An extension of Christofides heuristic to the k-person travelling salesman problem. Discrete Applied Mathematics, 6(1):79–83, 1983.
- [13] M. Goemans and J. Kleinberg. An improved approximation ratio for the minimum latency problem. Math. Program., 82:111–124, 1998.
- [14] M. C. Golumbic. Algorithmic Graph Theory and Perfect Graphs (Annals of Discrete Mathematics, Vol 57). North-Holland Publishing Co., Amsterdam, The Netherlands, second edition, 2004.
- [15] G. Gutin and A. P. Punnen, editors. Traveling Salesman Problem and Its Variations. Springer, Berlin, 2002.
- [16] J. A. Hoogeveen. Some paths are more difficult than cycles. Oper. Res. Lett., 10:291–295, 1991.
- [17] B. Jackson. Some remarks on arc-connectivity, vertex splitting, and orientation in digraphs. Journal of Graph Theory, 12(3):429–436, 1988.
- [18] H. Kaplan, M. Lewenstein, N. Shafrir, and M. Sviridenko. Approximation algorithms for asymmetric TSP by decomposing directed regular multigraphs. J. ACM, 52(4):602–626, 2005.
- [19] J. Kleinberg and D. P. Williamson. Unpublished note, 1998.
- [20] F. Lam and A. Newman. Traveling salesman path problems. Math. Program., 113(1):39–59, 2008.
- [21] E. Lawler, J. K. Lenstra, A. H. G. Rinnooy Kan, and D. Shmoys, editors. The Traveling Salesman Problem: A guided tour of combinatorial optimization. John Wiley & Sons Ltd., 1985.
- [22] I. Mendez-Diaz, P. Zabala, and A. Lucena. A new formulation for the traveling deliveryman problem. Discrete Applied Mathematics, 156(17):3223–3237, 2008.
- [23] E. Minieka. The deliveryman problem on a tree network. Ann. Oper. Res., 18:261–266, 1989.
- [24] V. Nagarajan and R. Ravi. Poly-logarithmic approximation algorithms for directed vehicle routing problems. In Proc. 10th APPROX, pages 257–270, 2007.
- [25] V. Nagarajan and R. Ravi. The directed minimum latency problem. In Proc. 11th APPROX, pages 193–206, 2008.
- [26] C. H. Papadimitriou and S. Vempala. On the approximability of the traveling salesman problem. Combinatorica, 26(1):101–120, 2006.
- [27] D. Shmoys and D. P. Williamson. Analyzing the Held-Karp TSP bound: a monotonicity property with application. Inf. Process. Lett., 35(6):281–285, 1990.
- [28] D. P. Williamson. Analysis of the Held-Karp heuristic for the traveling salesman problem. M.S. Thesis, MIT, 1990.
- [29] L. A. Wolsey. Heuristic analysis, linear programming and branch and bound. Mathematical Programming Study, 13:121–134, 1980.