Auxiliary Network-Enabled Attack Detection and Resilient Control of Islanded AC Microgrid
Abstract
This paper proposes a cyber-resilient distributed control strategy equipped with attack detection capabilities for islanded AC microgrids in the presence of bounded stealthy cyber attacks affecting both frequency and power information exchanged among neighboring distributed generators (DGs). The proposed control methodology relies on the construction of an auxiliary layer and the establishment of effective inter-layer cooperation between the actual DGs in the control layer and the virtual DGs in the auxiliary layer. This cooperation aims to achieve robust frequency restoration and proportional active power-sharing. It is shown that the in situ presence of a concealed auxiliary layer not only guarantees resilience against stealthy bounded attacks on both frequency and power-sharing but also facilitates a network-enabled attack identification mechanism. The paper provides rigorous proof of the stability of the closed-loop system and derives bounds for frequency and power deviations under attack conditions, offering insights into the impact of the attack signal, control and pinning gains, and network connectivity on the system’s convergence properties. The performance of the proposed controllers is illustrated by simulating a networked islanded AC microgrid in a Simulink environment showcasing both attributes of attack resilience and attack detection.
Index Terms:
AC microgrids, cyber-security, network-enabled attack detection, resilient control, stealthy attacks.I Introduction
Distributed control has been the most widely adopted strategy over the past decade to exercise frequency and voltage control of islanded AC microgrids [1]. The cooperation among the DGs in a microgrid relies on local information exchange over a sparse communication network, which is vulnerable to cyber attacks [2]. Such attacks, commonly known as false data injection (FDI) attacks, jeopardize the integrity of information transmitted across communication channels and have garnered significant attention in resilient microgrid control [3]. A trust factor-based control regime was proposed in [4] to synchronize the frequencies of DGs under attack, by real-time monitoring of a confidence factor associated with all the neighboring DGs. Wang et al.[5] proposed cyber-resilient adaptive controllers for frequency and voltage restoration with active/reactive power-sharing in networked AC/DC microgrids. These controllers utilize time-varying adaptive gains based on frequency, voltage, and power errors. An auxiliary state was introduced in [6] to make conventional distributed frequency consensus protocol cyber resilient and maintain frequency synchronization and proportional active power-sharing. Recently, [7] proposed attack magnitude-dependent time-variant communication weights, to implement an adaptive frequency regulation strategy using the most optimal communication channels in the presence of multiple link attacks.
Apart from incorporating cyber resilience in the control framework, topology switching induced by different types of attack detection techniques has been the other counterpart of attack mitigation strategies in microgrid control. These techniques can be further classified into (a) system-based [8, 9, 10] and (b) data-based approaches [11, 12], where the states of system under consideration are continuously estimated using an observer in (a), while historical training data is used for attack detection for redundancy in (b). To the best of the authors’ knowledge, the concepts of attack resilience and attack detection have often been addressed separately in the microgrid control literature. Therefore, designing a suitable distributed control framework together with resilience and detection capabilities is a crucial research direction for ensuring the safety and security of microgrid control.
In recent times, cyber adversaries have evolved to employ increasingly sophisticated and deceptive stealthy attacks [13] that might be challenging to ascertain using novel detection strategies like [8, 9, 10, 11, 12]. Equipped with the complete knowledge of dynamics and control architecture of the system, the attacks are now specifically designed as bounded intermittent disturbances with state-dependent linear/nonlinear dynamics [13, 14] which can easily deceive state observers and showcase zero neighborhood error, even when the neighboring DGs are out of synchronization [15]. In view of such bounded stealthy attacks, a virtual hidden layer-based cyber resilient framework was proposed in [16] for distributed control of networked systems. Motivated by [16], in this paper, we propose auxiliary virtual network-enabled distributed resilient control for frequency synchronization and proportional active power-sharing among a group of inverter-based DGs.
Distributed controllers adopting the aforementioned idea of the virtual layer have been previously developed in [17, 18, 19, 20], addressing the problem of frequency synchronization in microgrids. However, these works do not emphasize the need for a dedicated power controller that can provide resilience against any possible attack on power-sharing between neighboring DGs. The distributed secondary controllers in [17, 18, 19, 20] are devised to provide a frequency set point to the droop-based primary control which depends on the inherent linear relationship between frequency and active power [21]. However, any FDI attack affecting the sharing of active power can significantly hamper system frequency and lead to deviations in power demand beyond the rated values of the respective DGs. Therefore, a resilient power controller is obligatory for preserving the resilience of the frequency controller against cyber attacks. Motivated by this fact, in this paper, we design resilient frequency and power controllers capable of functioning in the presence of simultaneous attacks on both frequency and active power within a microgrid.
It is also evident to mention that the stability under proposed controllers in [16, 17, 19, 20] is leveraged by assumptions on the magnitude of resilient control gain and inclusion of attack vector in the Lyapunov candidate function. However, considering that a cyber attack is an external breach that is completely unknown to both the system and the control engineer, establishing the closed-loop stability of a cyber-resilient control system relying solely on the state dynamics of the system appears to be a more practical and mathematically viable approach. Further, the control architecture inclusive of an auxiliary layer hidden from the attacker provides an alternate safeguarded path for communication among neighboring DGs, thereby giving a provision to compare and detect any discrepancy in information being shared through the actual cyber layer. Leveraging this, we propose a straightforward test for detecting an attack, as compared to the works [17, 18, 19, 20]. In the light of above discussion, the major contributions of this paper can be summarized as follows:
-
i)
Relying on an auxiliary layer, we propose frequency and power-distributed controllers as leader-follower and leaderless resilient cooperative systems, respectively, for frequency regulation and proportional active power-sharing in an islanded AC microgrid, under the presence of FDI attacks affecting both frequency and power-sharing between the neighboring DGs. The FDI attacks are uniformly bounded and governed by the dynamics having finite gain.
-
ii)
Due to the difference in the nature of cooperation and distributed consensus protocols, we provide separate stability analyses under frequency and power attacks and obtain analytical bounds characterizing the deviations of frequency and power from their steady-state value under no-attack conditions. It is shown that these bounds depend on the underlying network topology, the magnitude of the attack signals, pinning gain and a gain term decided by the control designer.
-
iii)
As a byproduct of auxiliary layer-based control design, we propose a network-enabled attack detection mechanism showcasing secured propagation of control variables between the cyber and auxiliary layer, thereby devising a detection test for surveillance of any possible attack in the cyber layer.
Additionally, an extensive simulation study is presented under the simultaneous presence of both cyber attacks and load perturbations. The remnant of this paper is arranged as follows: Section I commences with an introduction, summarizing mathematical preliminaries and a brief review of secondary droop control. Section II describes system architecture and attack model and formulates the problem. Section III proposes a resilient frequency controller and obtains various bounds characterizing the effect of attack and network connectivity on the steady-sate frequency error. The philosophy behind resilient power controllers is discussed under Section IV. Section V explains the auxiliary network-enabled attack identification scheme and proposes a generalized test for detecting the attacks. Lastly, Section VI presents simulation case studies, before concluding the paper in Section VII.
I-A Notations, Graph Theory, and Mathematical Preliminaries
Throughout the paper, denotes the set of real numbers, and . For , represents its Euclidean norm. The complex number is represented by . The symbol denotes the Kronecker product of two matrices. represents an eigenvalue of any square matrix , is its transpose and denotes its operator (or induced) 2-norm such that , where is the maximum eigenvalue of the symmetric matrix . Consider a network of DGs, described as an undirected graph , with node set and edge set . The information flow between and nodes can be represented by an undirected edge . The set of neighbors of the node is denoted by = . The adjacency matrix of is denoted by = with , else . The Laplacian matrix of is denoted by , where and for . For an undirected and connected graph , the eigenvalues of the Laplacian can be arranged in the ascending order as . The following lemmas will be useful in the subsequent analysis of this paper:
Lemma 1 ([22], [23]).
Let be an undirected and connected graph with Laplacian , and be a diagonal matrix with diagonal entries . Then, the matrix is positive-definite.
Lemma 2 ([24]).
Consider a uniformly bounded signal , where is a positive constant. Then, for a Hurwitz matrix , there exists a constant vector and some finite-time such that following holds true for all :
I-B Distributed Secondary Droop Control
Droop control exploits the linear dependence of frequency on active power, causing the frequency of an inverter-based DG to droop with its output active power [25], according to the relation
| (1) |
where is angular frequency, is the nominal angular frequency, is measured output active power and is the droop coefficient associated with the DG. Due to primary droop control, since the inverter’s frequency undergoes a deviation from its nominal value, a suitable secondary control needs to be designed to restore the frequency of all the inverters to nominal microgrid frequency [21]. This is realized by cooperation among all the DGs at the secondary control level and designing distributed controllers and for frequency and active power for each . Using these, the nominal frequency is obtained from (1) as:
| (2) |
In the subsequent analysis, we use the vectors , and to represent the frequency, power, and droop-coefficient associated active power for the network of DGs.
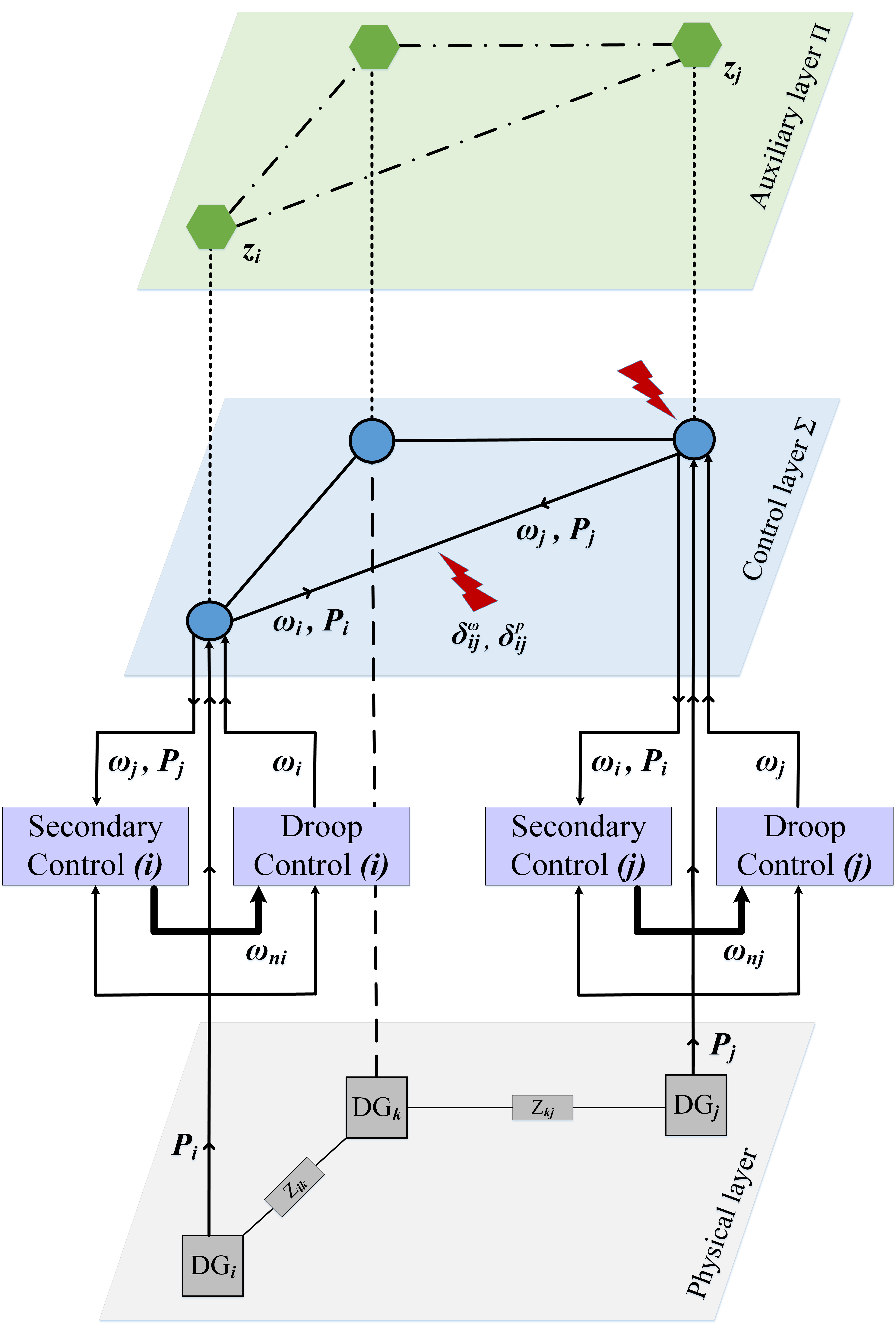
II System Description and Problem Statement
II-A System Description
Consider a microgrid network comprising DGs in the physical layer, along with the associated control layer and the auxiliary layer , as shown in Fig. 1. Each DG is equipped with individual primary and secondary controllers where frequency and active power are the physical state variables to be controlled for each . According to (2), the secondary control generates nominal frequency to the primary droop controller for computing the actual frequency of the DG. Consequently, both frequency and the average active power signals of the DGs are shared among them according to the communication network at the control layer for designing frequency and power controllers.
However, owing to the attacker’s knowledge about the control layer, the communication network over is vulnerable to FDI attacks on both frequency and power signals, deviating the system from the desired cooperative control objectives. To account for these attacks, our approach relies on the construction of an auxiliary layer and its integration with to assure resiliency toward frequency regulation and proportional active power-sharing. The auxiliary nodes in are considered to have their own state dynamics but the same inter-agent interaction network as in . Further, there exists a hidden network connecting the corresponding nodes in and (see Fig. 1).
Under an FDI attack, the frequency and power signals received at a particular node in may be different from the one transmitted by the neighboring nodes and can be expressed as:
| (3) |
where is the frequency signal received at node from node , is the actual frequency of the DG, and is the FDI attack affecting the link connecting nodes and . Similar notations can be defined for . The total external injection at the node can be written as (resp., for power as ), leading to the attack vector (resp., ) for the nodes in . In general, an attacker might employ an FDI attack varying as per the real-time states of the system, which dies out as the system states become stable. Such kinds of attacks deviate the system from achieving the desired convergence properties and even make it unstable while being stealthy [16]. In this paper, we model the frequency attack (resp., power attack) as a function of states (resp., ) and time such that (resp., ) satisfies the following assumption:
Assumption 1.
The injections and are uniformly bounded for bounded and , that is, there exist positive constants such that and for all and . In particular, if these attacks are generated by the dynamics,
| (4) |
these must have a finite -gain.
The relevance of this assumption lies in the fact that an intelligent attacker always aims at inserting a bounded attack signal, as the injections with large magnitude are easy to detect and will be rejected before they spread across the network. Further, dynamics (4) having finite -gain implies that and settle down to some value, as and reach the steady-state, respectively.
II-B Problem Statement
Consider DGs, connected via an undirected and connected graph , as shown in Fig. 1. Assume that the DGs be governed by the droop-based frequency dynamics (2) and subject to frequency and power attacks and in control layer , according to Assumption 1. Let be the state vector associated with the auxiliary nodes and be the desired value of the microgrid frequency. Based on the integration between and layers, design the vector functions such that the following auxiliary-state coupled dynamics, under the frequency and power attacks and , disseminated over using Laplacian , respectively,
| (5) |
assures that the following hold true for some small constants and :
-
(P1)
Frequency is maintained at the desired nominal value for all the DGs, that is, .
-
(P2)
Power is shared among the DGs in proportion to their droop coefficients, that is, , where is a constant.
Additionally,
-
(P3)
Based on the integration of and , propose an attack detection mechanism such that non-zero FDI attacks and , as defined in (3), are detected for all .
III Distributed Attack Resilient Frequency control
For resiliency towards frequency attacks , we propose the system in (5) as follows:
| (6a) | ||||
| (6b) | ||||
where is the reference frequency fed to the leader DGs in the group. The matrix is given by
| (7) |
where is a diagonal matrix with its entries represents the pinning gain, such that if the DG is a leader and otherwise. Further, is a gain factor and the vectors and are defined as and . In (6), matrices and are such that the frequency controller of the DG contains relative frequency term (because of the Laplacian ) responsible for frequency consensus, and the term associated with the pinning gain , shapes the solution trajectories such that consensus occurs at the desired frequency . The interconnection between the two layers and is realized by the matrix , associated with (i) the auxiliary state vector in the in dynamics (6a), and (ii) the actual frequency vector in the dynamics (6b). Note that the auxiliary state vector has no physical significance and may assume any steady-sate value. We have the following lemma relating matrices and :
Lemma 3.
Proof.
Multiplying by on both sides of (III), we have that , since for an undirected and connected graph. Further, since by definition, it follows that . ∎
For further analysis, let us introduce the frequency error vector
| (8) |
using which, (6) can be expressed as:
Following Lemma 3, the above equations are simplified as:
| (9a) | ||||
| (9b) | ||||
Let be the joint state vector, using which, (9) can be written in the compact form as:
| (10) |
where and the block matrix is given by
| (11) |
Lemma 4.
The block matrix in (11) is Hurwitz.
Proof.
Using Kronecker product, (11) can be written as , where
| (12) |
is a matrix with eigenvalues . Further, since graph is undirected and connected, is positive semi-definite [22]. Also, matrix contains at least one non-zero diagonal entry (as there is at least one leader in the group). Using Lemma 1 from Subsection I-A, it can be stated that is symmetric and positive-definite. Alternatively, , as defined in (III), is symmetric and negative-definite, and hence, has all real and strictly negative eigenvalues . Now, using the multiplicative property of Kronecker product [26, Theorem 4.2.12], it can be inferred that . Alternatively, all eigenvalues of are complex conjugate having strictly negative real part, implying that is Hurwitz. ∎
For better motivation and simplicity, we first discuss that the proposed framework (10) assures the frequency consensus in the absence of an attack, followed by the result in the attacked scenario.
Lemma 5 (Frequency control in absence of attack).
If , the dynamics (10) assures that as .
Proof.
If , we have the following convergence theorem for microgrid frequency, addressing the problem (P1).
Theorem 1 (Frequency control in presence of attack).
Before proceeding to the proof, we first discuss the below important result:
Lemma 6.
Let be a block matrix of dimension , where is given by (III). The operator norm of is given by
Proof.
Using Kronecker product, the matrix can be rewritten as . Taking operator norm on both sides, we have
using the property of the operator norms for Kronecker products of two matrices and [27, Theorem 8, p. 412]. Note that and . From (III), it is straightforward to check that . The last relation can also be rewritten as , where matrix is positive-definite. Using this, one can write . Consequently, it can be concluded using (III) that , and hence, proving the result. ∎
We are now ready to prove Theorem 1.
Proof of Theorem 1.
If , the solution of linear system (10) is obtained as . Now, taking norm on both sides and applying the Cauchy–Schwarz inequality results in . Since , as is Hurwitz (see Lemma 4), it can be written that . Note that is uniformly bounded, as it is , according to Assumption 1. Now, it immediately follows from Lemma 2 (from Subsection I-A) that there exists a time-independent vector with (where is defined in Assumption 1) such that for some constant vector for all . This implies that , which on further simplification results in . Note that is invertible as it has all non-zero eigenvalues (Lemma 4) and its inverse is given by [28, Theorem 0.7.3]:
| (13) |
using which, it holds that
| (14) |
where and [28, Theorem 0.7.3], with and , from (11). Substituting these, we get and , and hence,
where we have replaced the first term by , using Lemma 6. Since (since for an undirected and connected graph ) and (see Assumption 1), it holds that
| (15) |
exploiting Lemma 6. From (15), one can conclude that as , with . Further, since is small for sufficiently large values of gain (which is a design parameter), converges to a small neighborhood around as , using (8). ∎
Remark 1.
It can be inferred from inequality (15) that the steady-state bound is:
-
•
proportional to the maximum eigenvalue of Laplacian and the attack bound . If the graph has minimal connectivity (i.e., small ), the attacker will have fewer links to target, and hence, will have relatively less impact.
-
•
inversely proportional to the minimum eigenvalue of matrix and the design parameter . Beside selecting large , it is possible to make large by choosing the large value of pinning gain , since , using Weyl’s theorem [28, Chapter 4, p. 239] and the fact that . Therefore, primarily influenced by the pinning gain .
In summary, it is evident that the effect of varying is more dominant on the value of , as compared to , and can be decided appropriately by the user.
IV Distributed Attack Resilient Power Control
Unlike frequency control, the implementation of the distributed power controller is done in a leaderless configuration to assure the proportional power-sharing among the DGs, leading to the system in (5) as follows:
| (16a) | ||||
| (16b) | ||||
where Laplacian is associated with the state vector , instead of matrix as in (6). Here, the interconnection between and is realized by the matrix . Defining power-sharing error as (where is defined in Problem (P2))
| (17) |
(16) can be expressed in terms of as:
| (18a) | ||||
| (18b) | ||||
We have the following lemma in absence of power attacks:
Lemma 7 (Power-sharing control in absence of attack).
If , the dynamics (18) assures that as .
Proof.
Consider the candidate Lyapunov function , whose time-derivative along (18) with is obtained as , where we used the fact that for an undirected and connected graph . On further simplification, one can get that , which is negative semi-definite. Now, using LaSalle’s invariance theorem [29, Corollary 4.2, p. 129], it can be concluded that is the desired equilibrium point, implying that, as , using (17). ∎
In case , the analysis is different from the earlier Theorem 1, as the system matrix in (18) has one zero eigenvalue and rest positive eigenvalues for an undirected and connected graph . To proceed further, we filter out the dynamics associated with the simple zero eigenvalue by using the transformation:
| (19) |
where and and the transformation with being the left eigenvector associated with , . Using transformation , can be diagonalized as:
| (20) |
where is a diagonal matrix comprising non-zero eigenvalues of . Using (19), (18) can be rewritten as:
| (21a) | ||||
| (21b) | ||||
Now, using (20), since , (21) further reduces to
| (22a) | ||||
| (22b) | ||||
| which can be expressed in the compact form as: | ||||
| (23) |
where , and
| (24) |
Since and is a positive definite matrix by construction, is Hurwitz and has strictly negative eigenvalues in accordance with Lemma 4. We are now ready to state the following convergence result, solving Problem (P2):
Theorem 2 (Power-sharing control in presence of attack).
Proof.
The solution of (23) is given by . Upon taking norm on both sides and following similar steps as in the proof of Theorem 1, one can obtain , where for some time-independent vector satisfying (see Assumption 1 for ) such that , according to Lemma 2 from Subsection I-A. Now, similar to (15), it can be concluded that
| (25) |
Now, exploiting Lemma 6 by replacing by , it can be obtained that
| (26) |
since and by construction, where is the Fielder eigenvalue of the Laplacian . From (26), it can be concluded that (and hence, ) as , where . Furthermore, for sufficiently large values of gain , assumes small value, and hence, converges to a small neighborhood around as , using (17). ∎
V Attack Detection: Exploring Interaction Between Control and Auxiliary Layers
Addressing Problem (P3), this section proposes an attack detection method relying on the interaction between the control layer and auxiliary layer in Fig. 1. For brevity and clarity, we provide a discussion for the frequency attacks affecting dynamics in (5). However, it is equally applicable to the power attacks appearing in the dynamics .
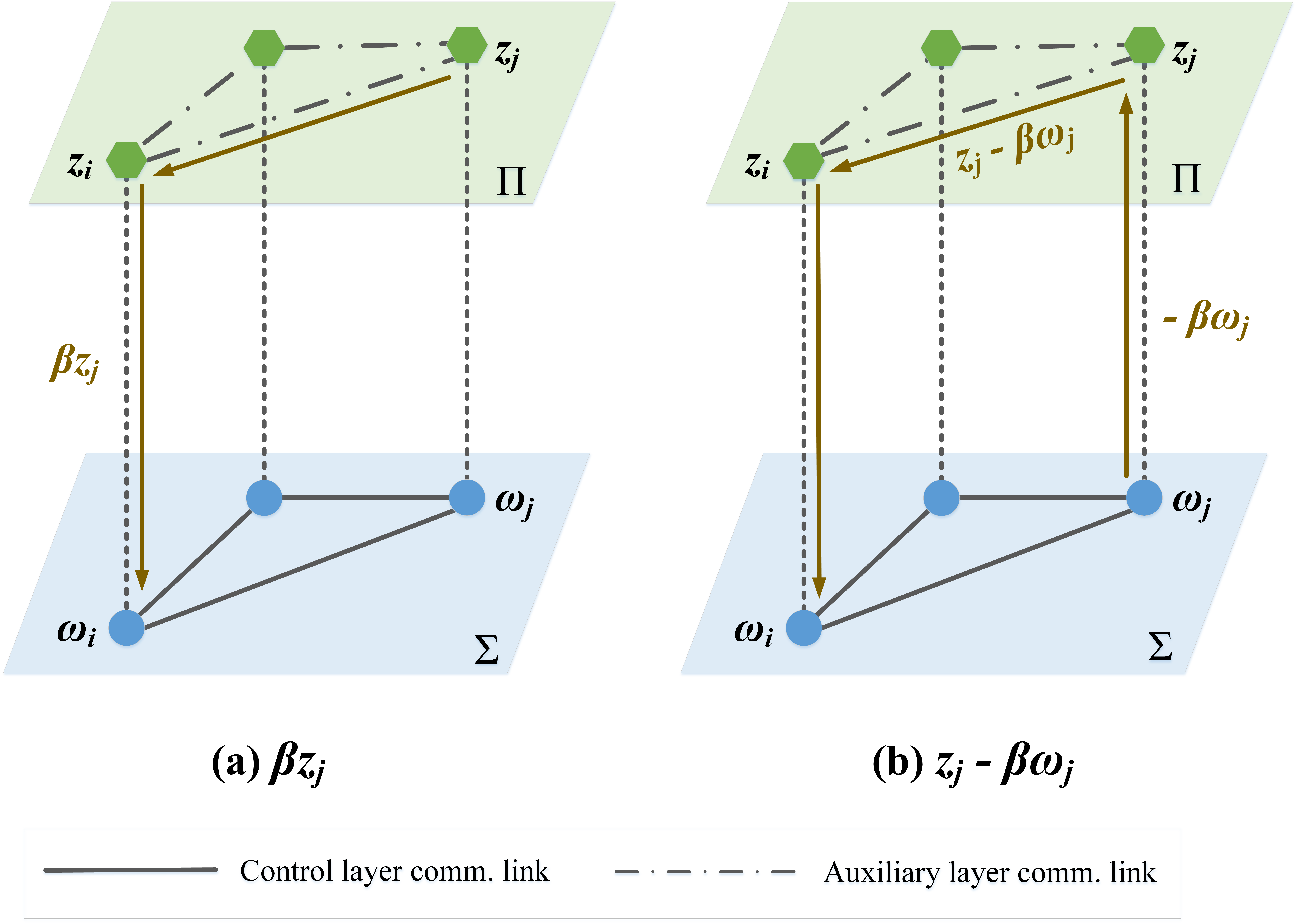
Since the layer is vulnerable to attacks injected by the attacker as compared to the secured and hidden layer , one can exploit the layer to check the authenticity of the information shared between two nodes in the layer . As shown in Fig. 1, the layer contains a set of (virtual) nodes, directly associated with individual (actual) nodes in the layer . Consequently, the node in has state information of the associated node in and similarly the node in has information of the associated node in . Further, both the layers are connected to each other via interconnection matrices . With respect to the node, (6) can be rewritten, by segregating terms on the basis of the contributions by the node itself and the neighboring nodes in both and layers, as follows [30]:
| (27a) | ||||
| (27b) | ||||
where denote the row of matrices and , respectively. Further, if the node is the leader, else . The following observations are straightforward toward practical implementation of (27):
- •
- •
From the above discussion, it is clear that the node in has access to the following two pieces of additional information due to the interaction between and :
| (28) |
where notations and are used to emphasize that these signals contain information about the neighboring nodes in . According to (28), the node estimates the frequency received from the node in as:
| (29) |
which can be compared with the actual frequency signal in (3) received at the node to testify whether the communication link in is under attack or not. Consequently, if , the corresponding link is declared to be under attack. Once the corrupted communication link is identified, it can be isolated (provided the remaining network contains a spanning tree) from the rest of the control layer till the time attack remains prevalent in the network.
Remark 2.
It is essential to emphasize that the attack detection approach described above is a byproduct of the interaction between and . It can be employed if there is a specific need to isolate any corrupted link, thereby enhancing the accuracy of the steady-state behavior. However, it’s crucial to note that the isolation of any link is not mandatory for the proper functioning of the proposed resilient controllers (6) and (16) for some finite and . Moreover, the isolation between the layers and can be ensured using contemporary communication network slicing approaches, such as cloud computing management and software-defined networking [31, 32]. These advanced techniques provide effective mechanisms for segregating communication channels and ensuring the secure operation of the system.
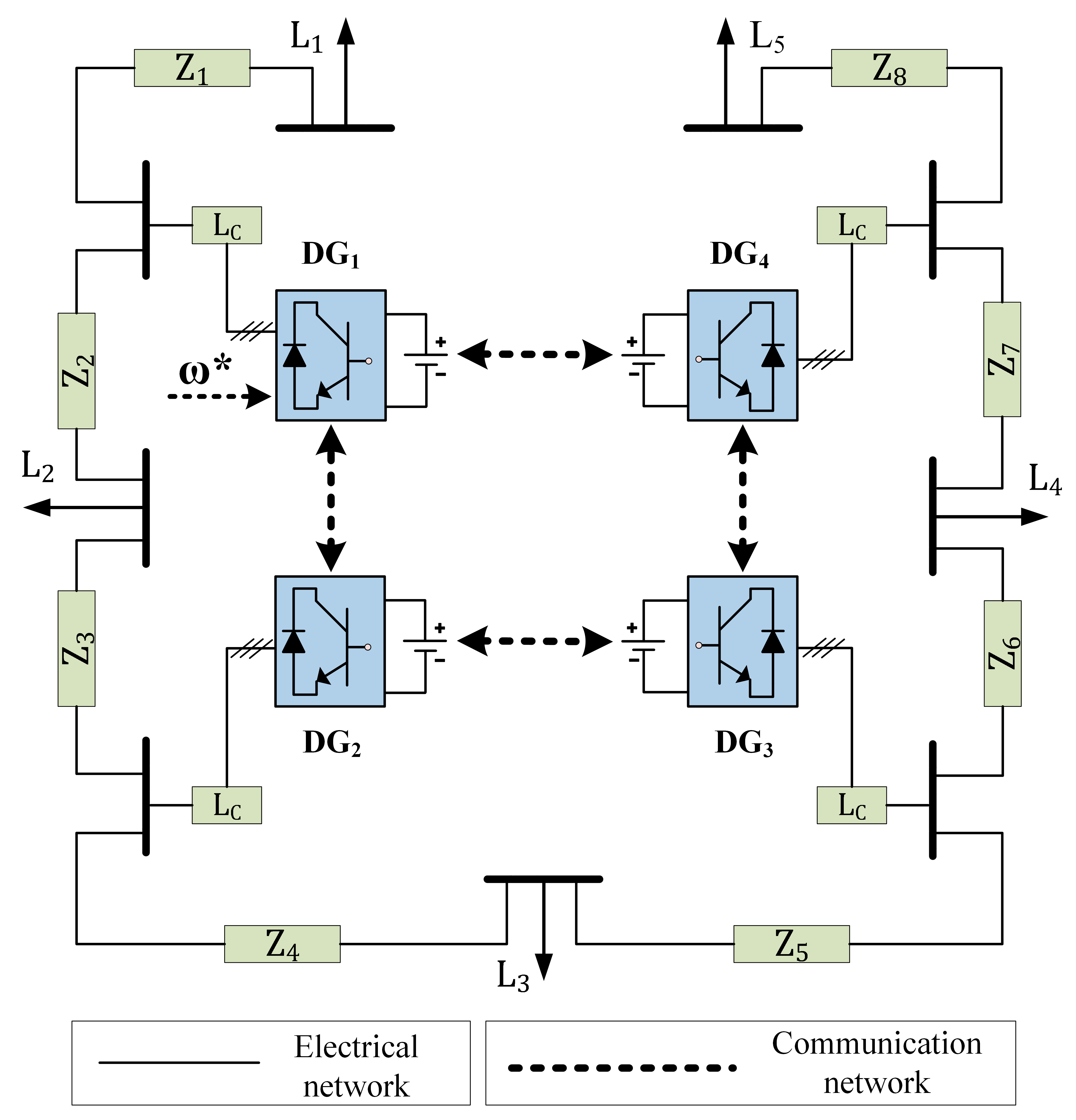
| Parameter | Value |
|---|---|
| Droop gain () | |
| Droop gain () | |
| Filter inductance () | mH |
| Filter capacitance () | F |
| Coupling inductance () | mH |
| Line impedance () | , 12mH |
| Line impedance () | , 10mH |
| Line impedance () | , 8mH |
| Line impedance () | , 5mH |
| Loads () | kW, kVar |
| Loads () | kW, kVar |
VI Simulation Case Studies
Consider a 3-phase, 415 V islanded AC microgrid as shown in Fig. 3, which comprises DGs, connected through transmission lines and loads, whose values are as listed in Table I. The DGs are connected as per the undirected and connected communication topology, as shown in Fig. 3, which has the following Laplacian:
Assume that DG acts as the leader and has access to reference frequency rad/s ( Hz), with all the remaining DGs acting as fully connected followers. Therefore, the pinning gain and for . Associated with each DG, there exist control and auxiliary nodes in the layers and , respectively. Consequently, the matrices in (6) can be obtained as
According to Lemma 5 and Lemma 7, one can easily verify that, in the absence of any attack, the frequencies of all the DGs converge to rad/s, while DGs 1, 2 and DGs 3, 4 share equal active power as per their equal droop coefficients. We now analyze protocols (6) and (16) in case of an attack as discussed below.
VI-A Controller performance under attacked condition
According to Assumption 1, we consider that the frequency and power attacks are governed by the dynamics:
| (30) |
where
and
| (31) |
where
Please note that these frequency and power attacks (30) and (31) are completely unknown to the controller and are initialized in the system as injections by the attacker at a given time. To emphasize the importance of introducing an auxiliary layer in the distributed control framework, we now discuss the performance of proposed controllers in the absence and presence of , followed by the effect of load perturbations.
VI-A1 Absence of auxiliary layer
We first illustrate the test system in the presence of cyber-attacks and the absence of an auxiliary layer (and hence, the auxiliary nodes) from the frequency and power controllers (6) and (16), respectively.
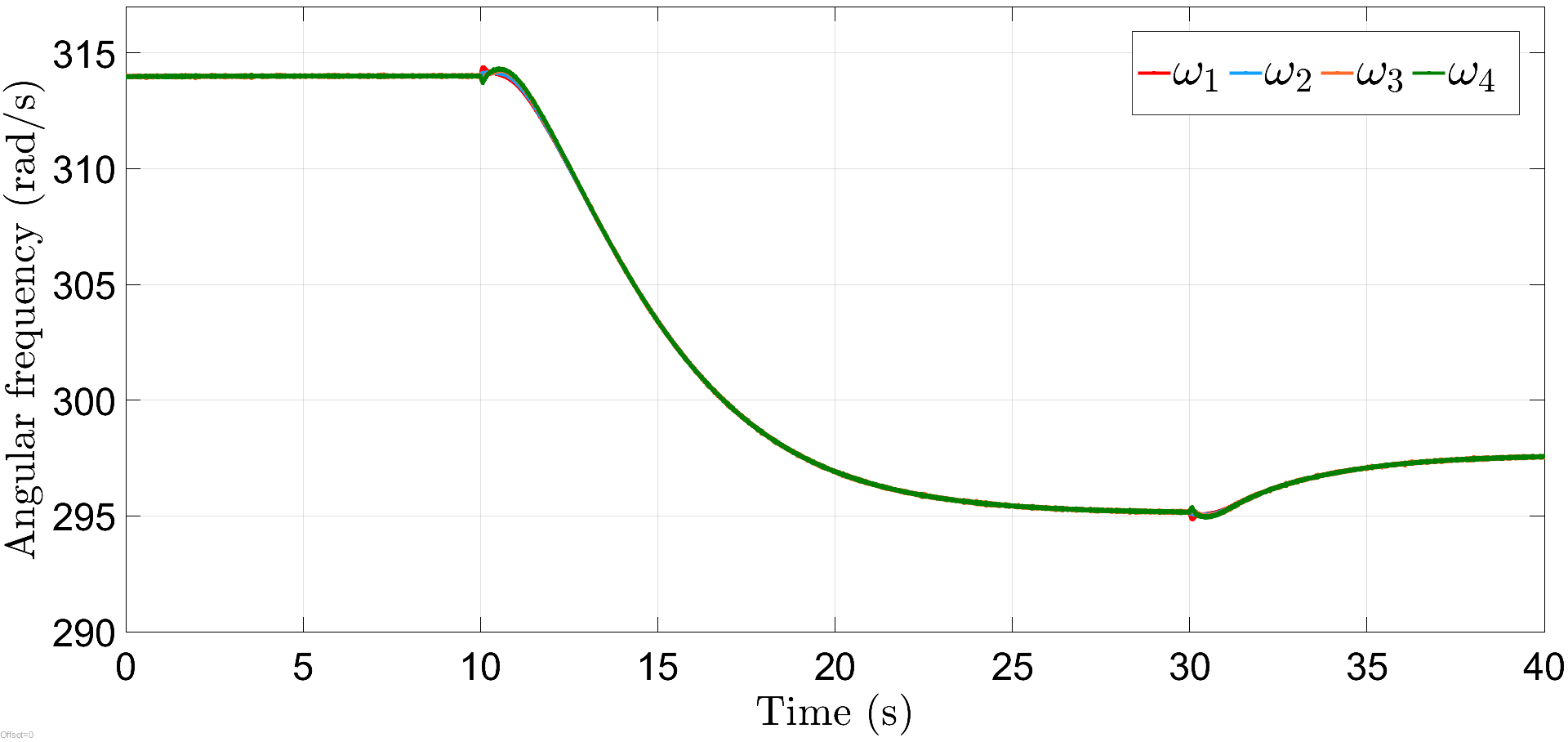
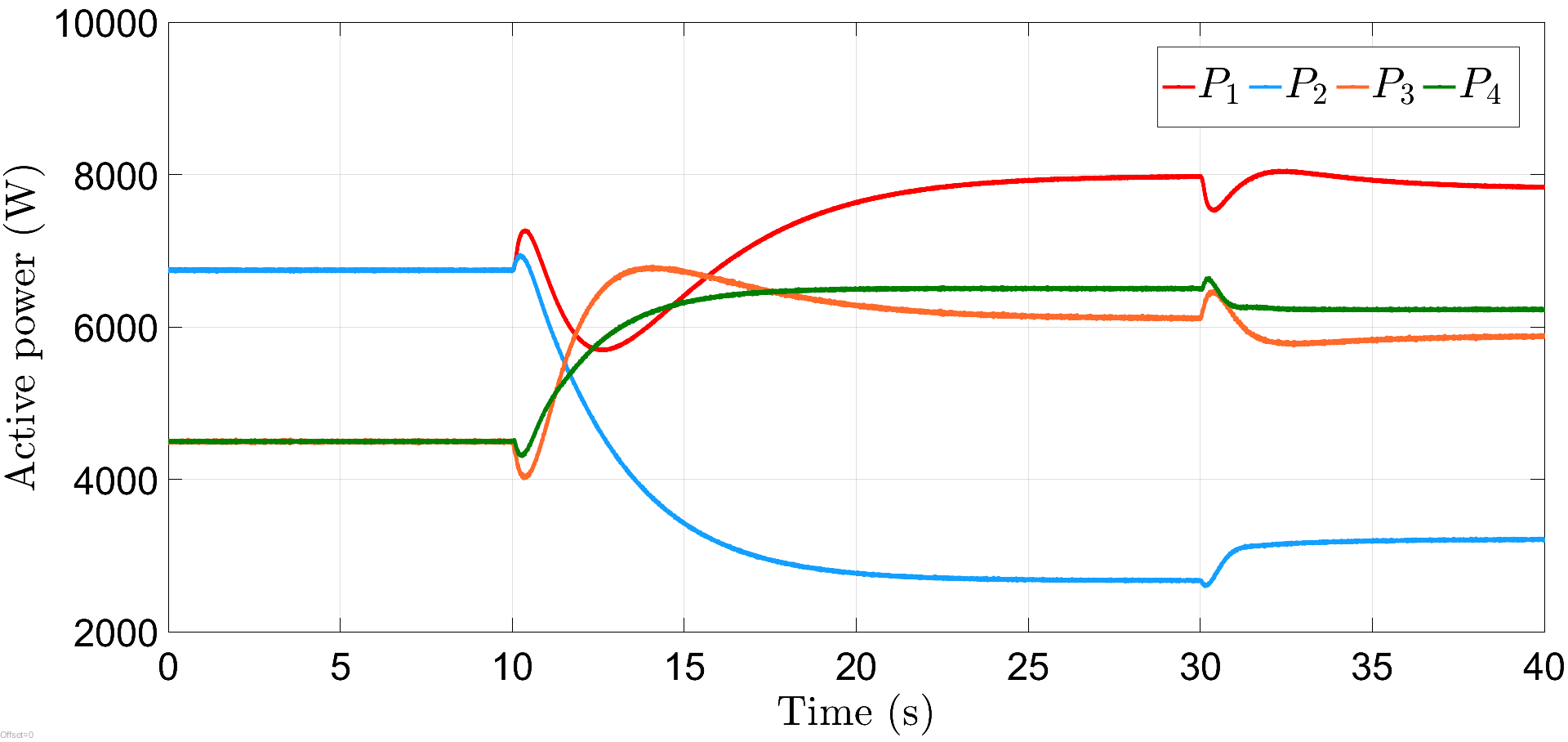
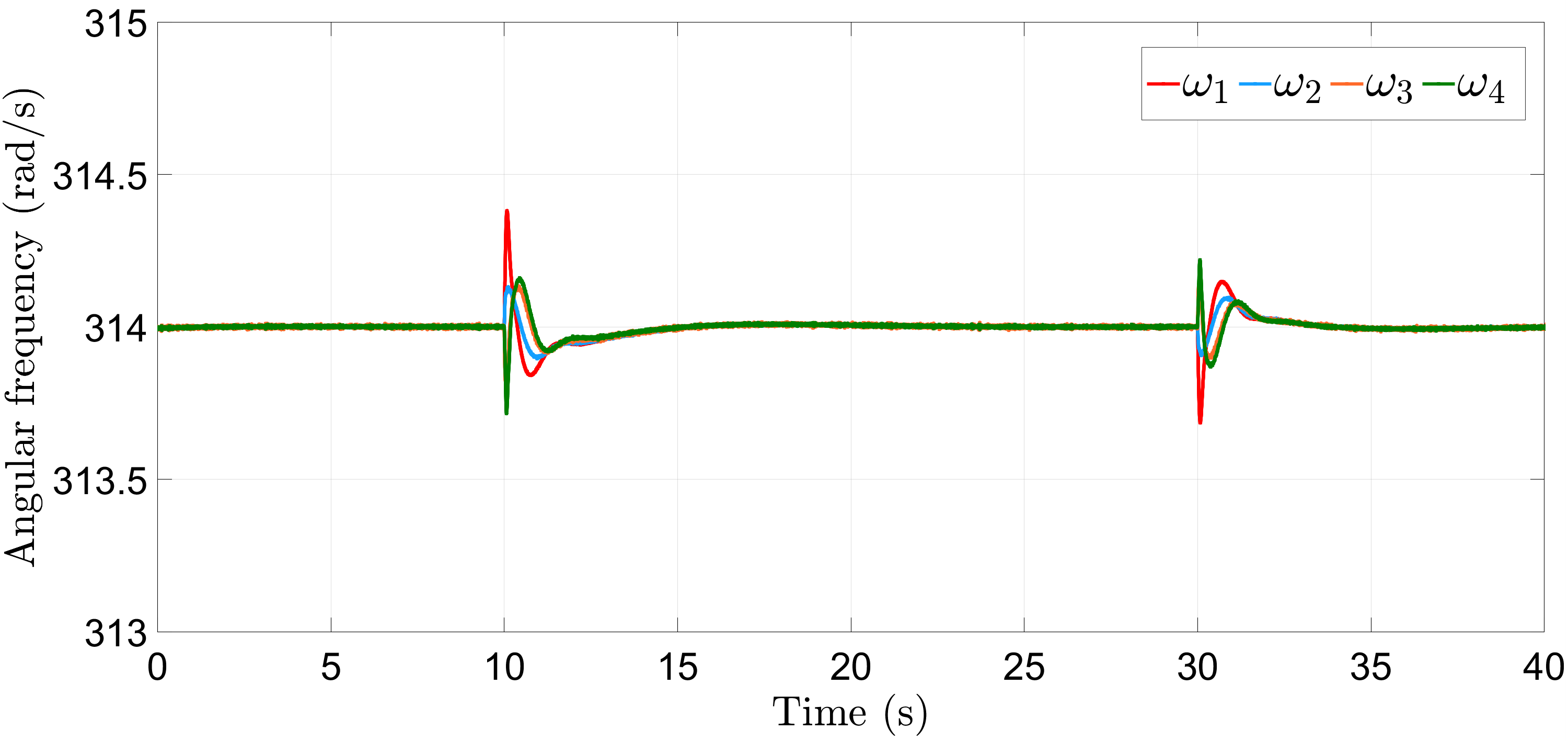
Initially, in the absence of an attack, the microgrid is operating normally under controllers (6a) and (16a), at rad/s with DGs 1, 2 and 3, 4 delivering equal power at kW and kW, respectively, as shown in Figs. 4 and 5 for the initial 10 s. The frequency and power attacks in (30) and (31) are initialized at s and s, causing the frequency of all the DGs to deviate by about rad/s from the nominal value at 10 s and settle down to a common steady-state value of rad/s due to the distributed action of nodes in the control layer, which is further shifted to rad/s post introduction of power attack at s. Similarly, the active power-sharing is also adversely affected, as depicted by Fig. 5.
VI-A2 Presence of auxiliary layer
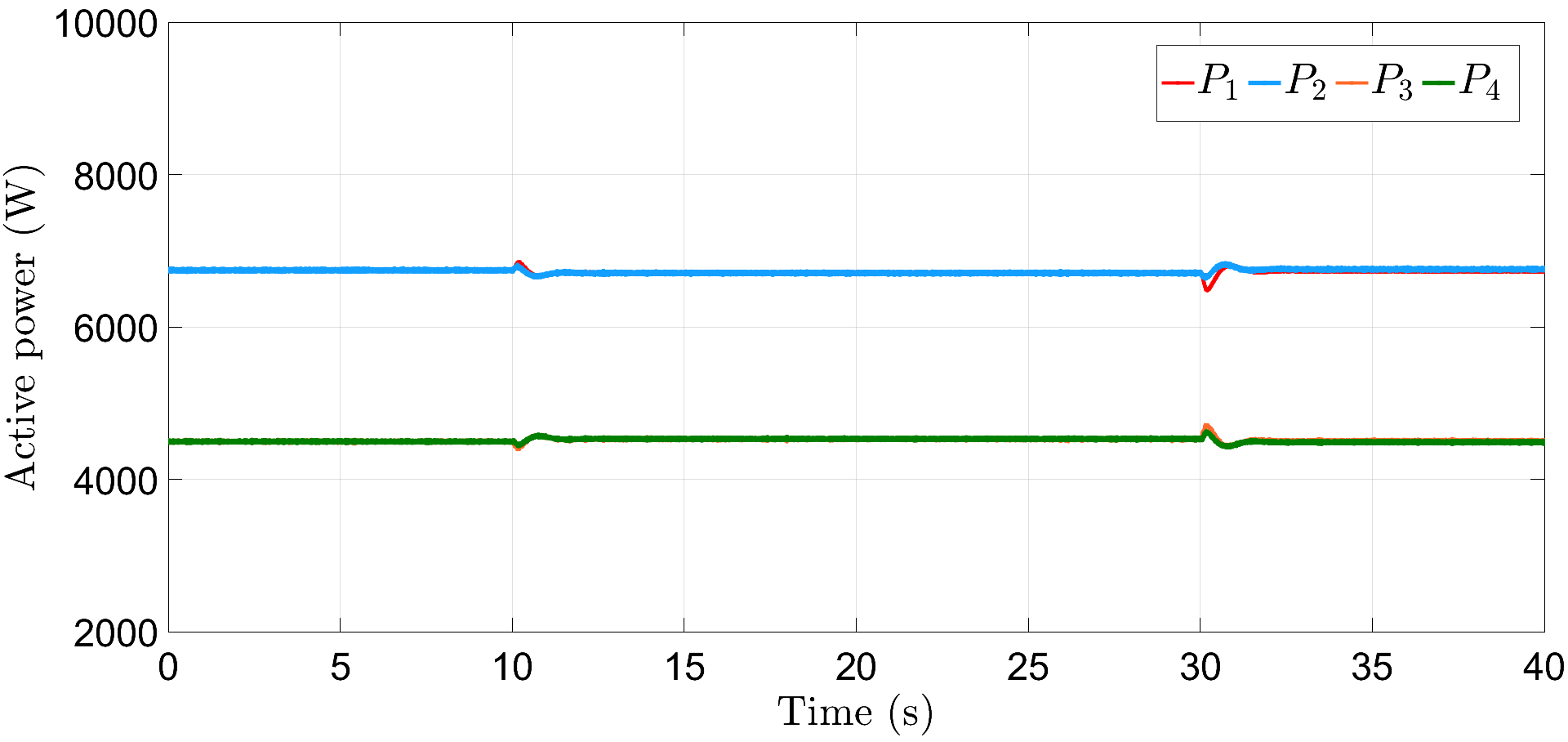
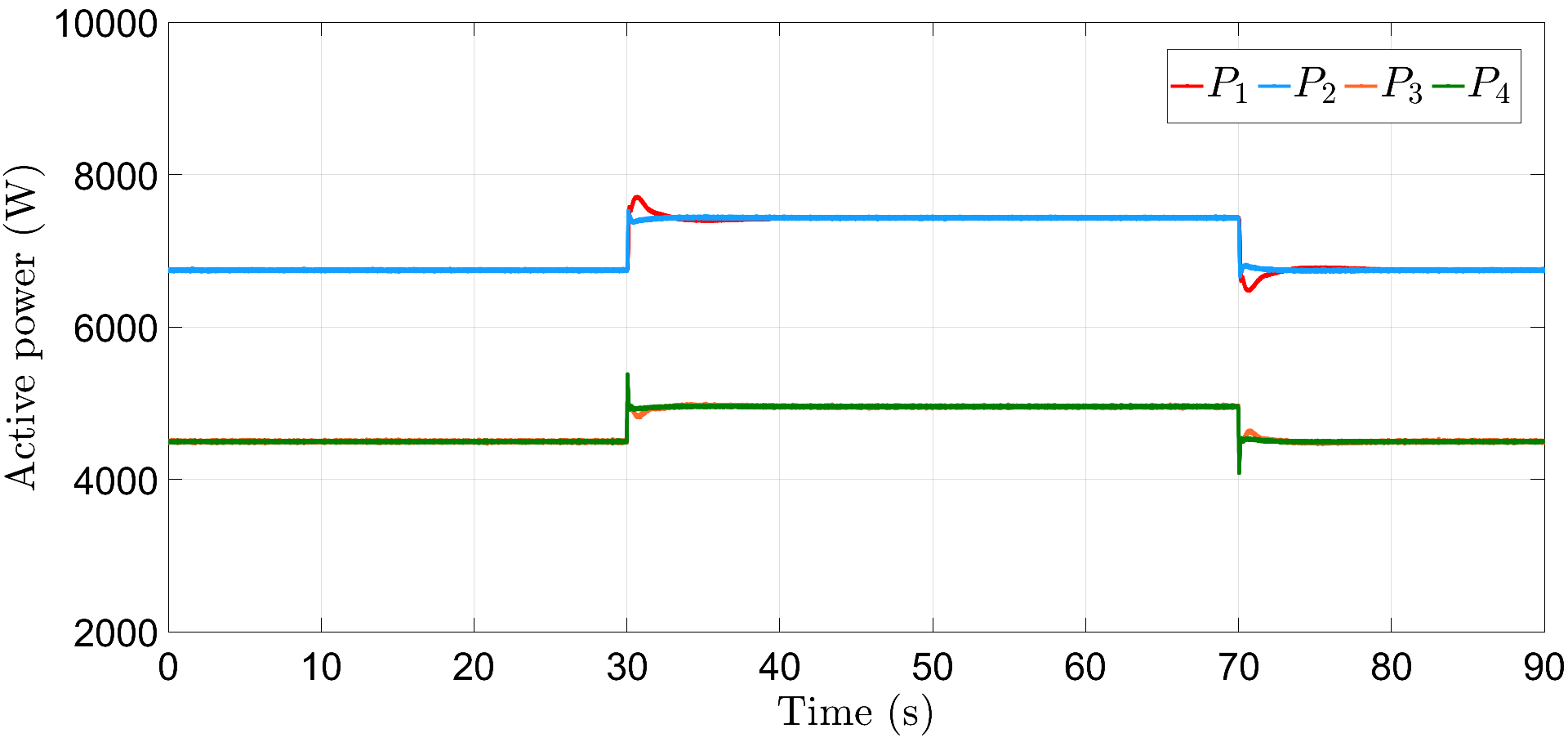
We now simulate the test microgrid in the presence of auxiliary layer in (6) and (16), where the initial states of the auxiliary nodes are randomly chosen and gain . As shown in Fig. 6, frequencies are restored in the neighborhood of rad/s in about s, post attacks (30) and (31), introduced at s and s, respectively. Similarly, Fig. 7 shows that power-sharing is also maintained for DGs 1, 2 and 3, 4 in the neighborhood of their nominal values, after a slight deviation at s and s, which lasts approximately about s.
VI-A3 Effect of load perturbations
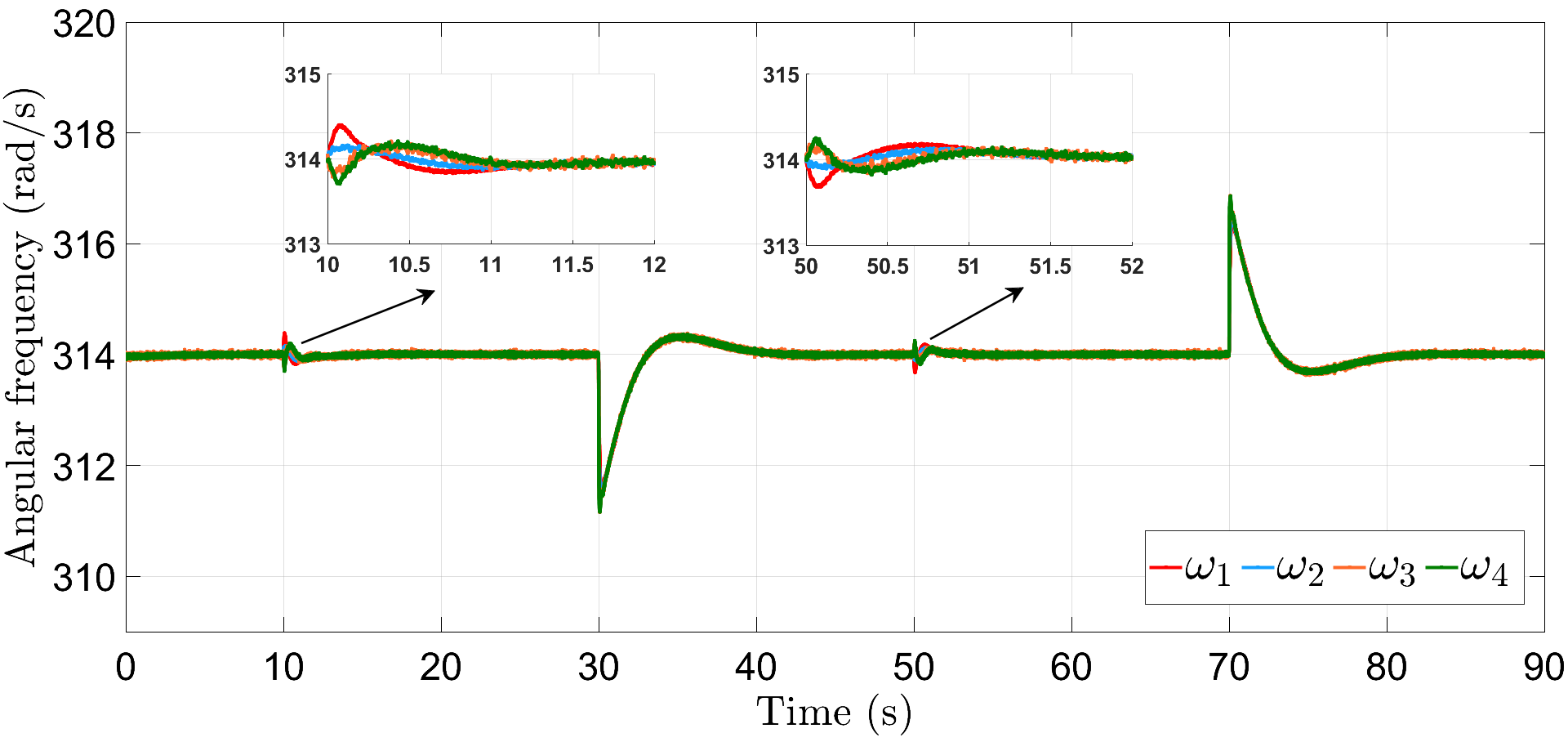
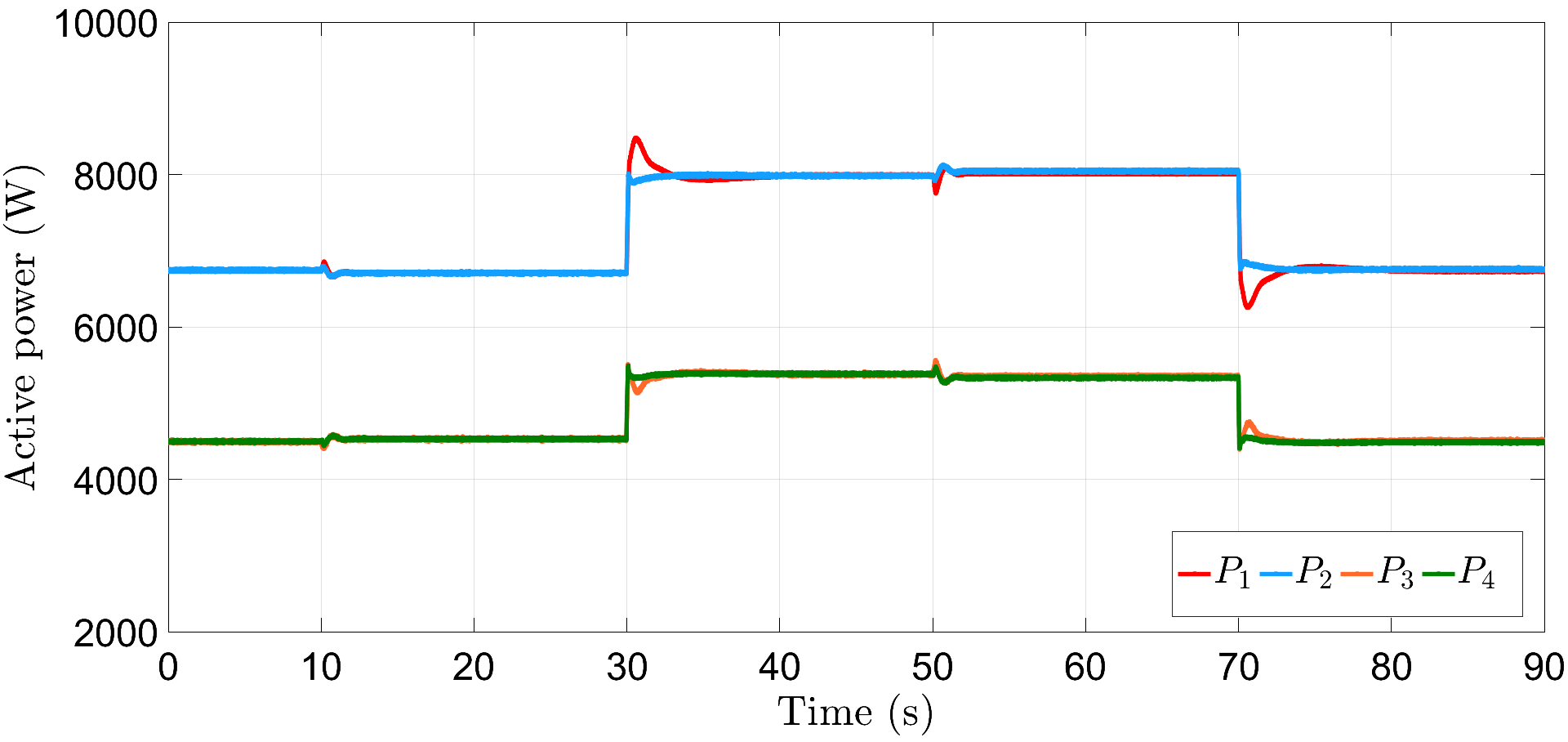
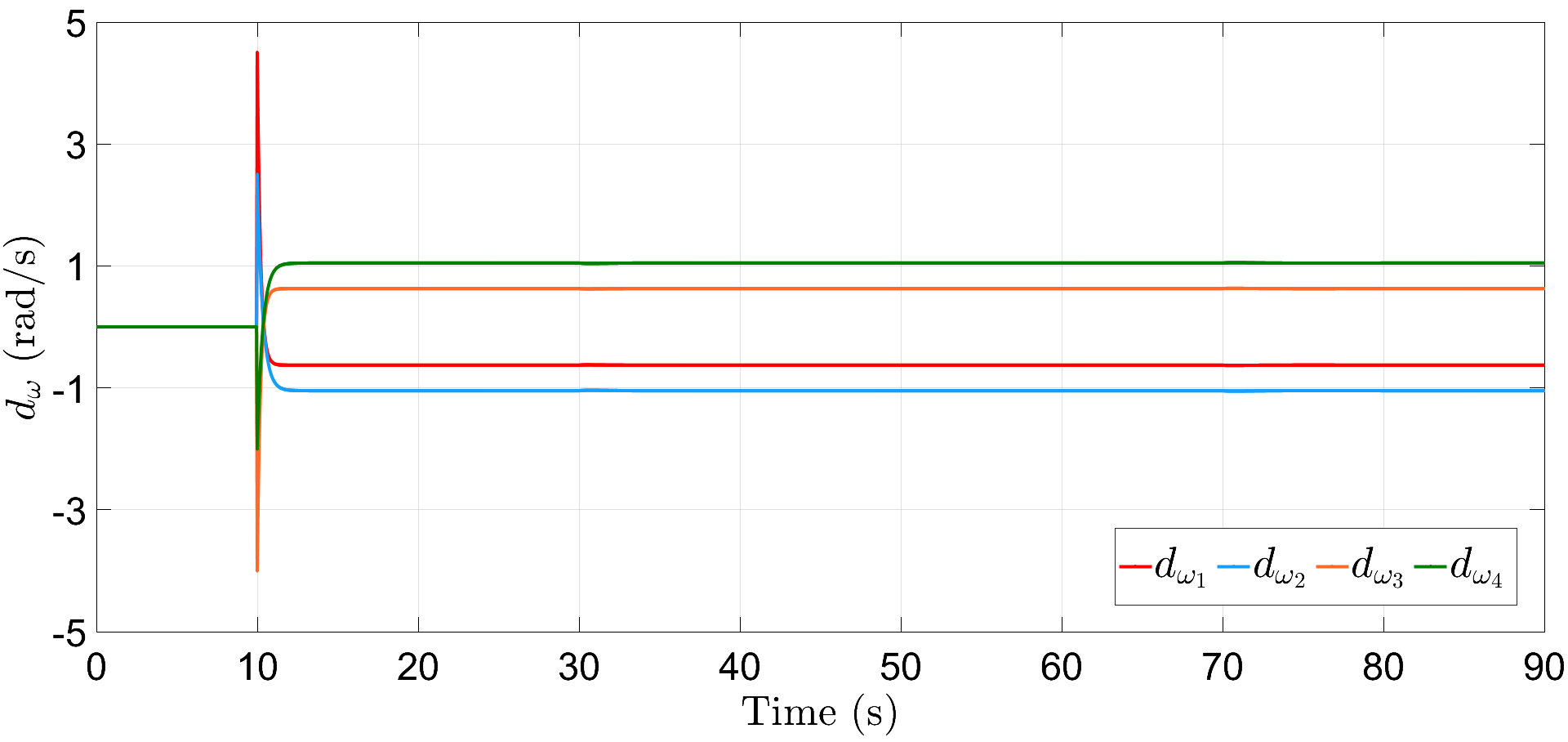
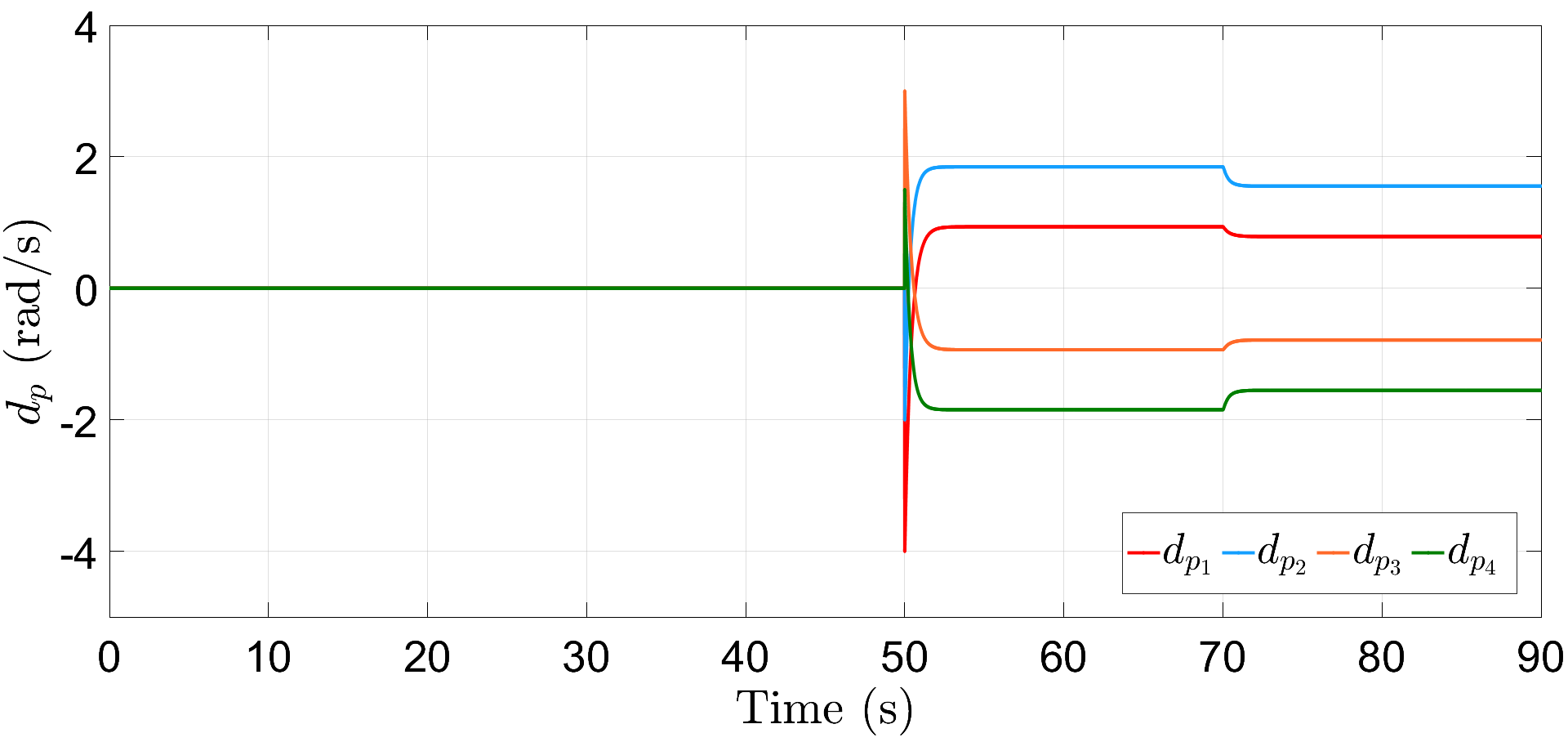
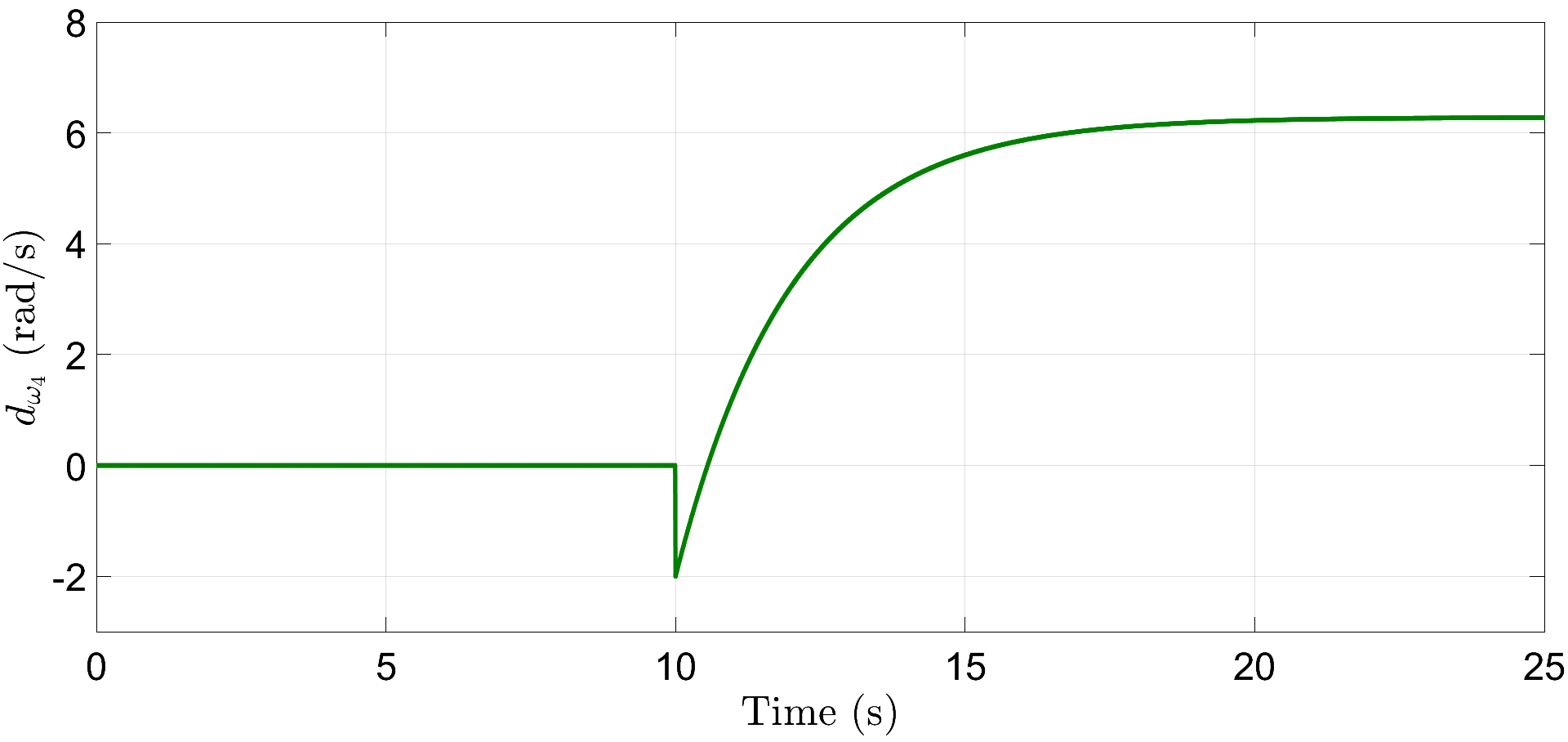
In addition to the resiliency against frequency and power attacks, we also verify the robustness of proposed controllers (6) and (16) against abrupt load deviations. For illustration, we consider here that the frequency and power attacks are initiated at s and s with different (initial) values for each communication link, given by, and , respectively. Further, the loads are increased by times their initial magnitude at s and then decreased by the same amount at s, respectively. Fig. 8 depicts that the proposed resilient control scheme restores the DG frequencies to their nominal value within a span of s. Similarly, Fig. 9 illustrates accurate power-sharing post load perturbation, with DGs 1, 2 now sharing kW and DGs 3, 4 sharing kW, respectively. The plots for and are shown in Figs. 10 and 11, respectively, where the attacks converge to different steady-state values. Note that the term in (30) is of the order of and is dominated by the first term , the plot for does not show noticeable fluctuations with load perturbations, as compared to .
VI-B Attack Detection
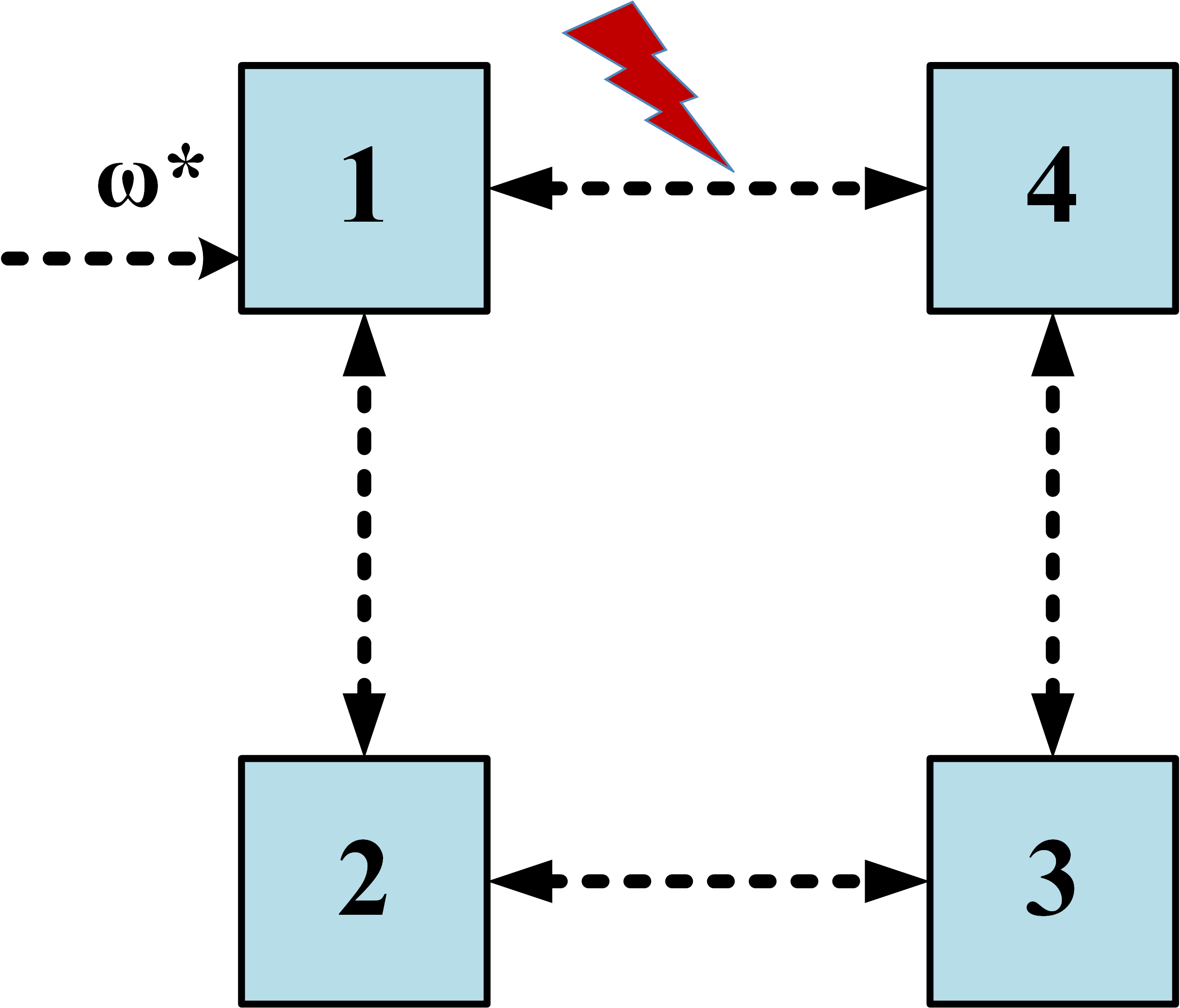
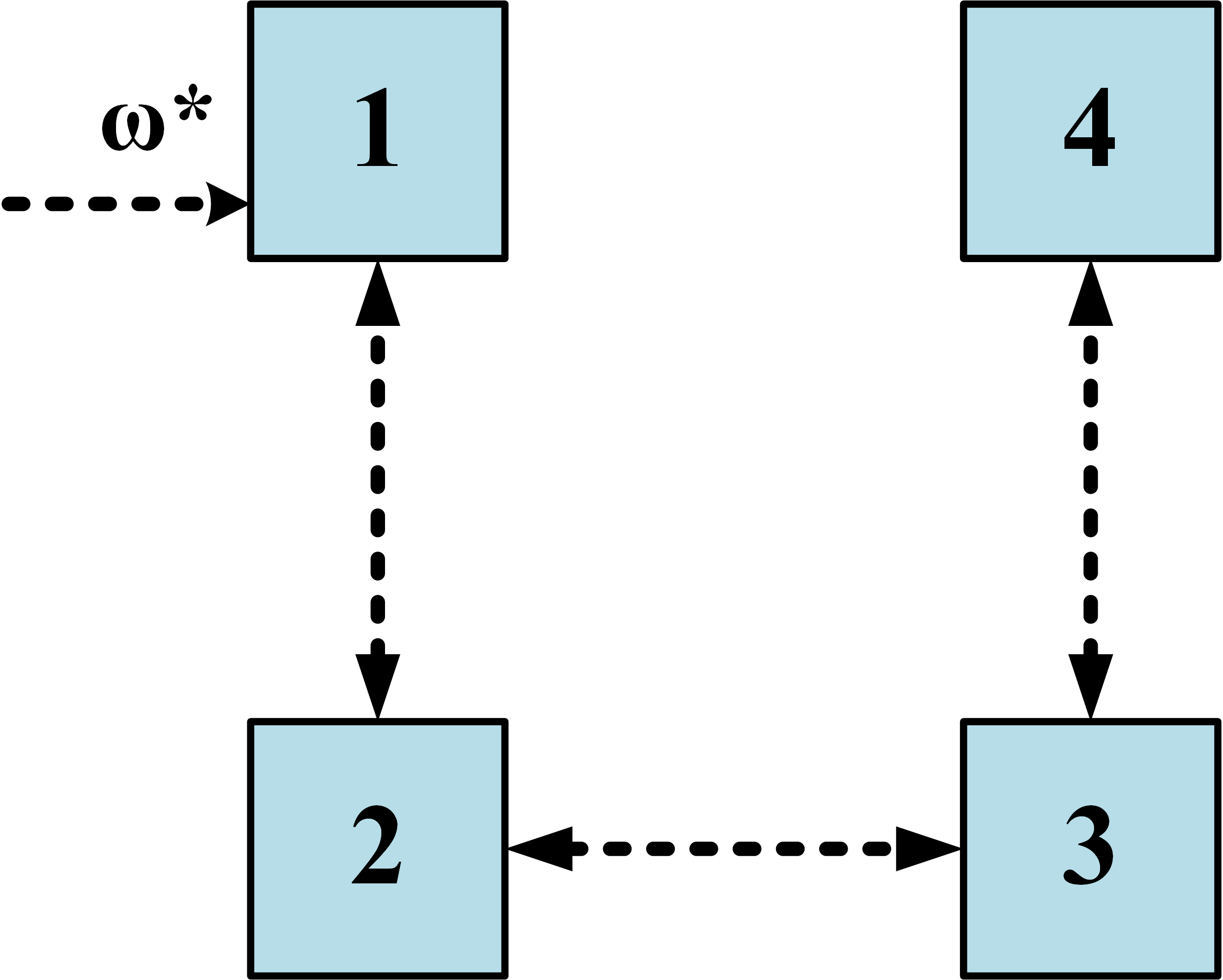
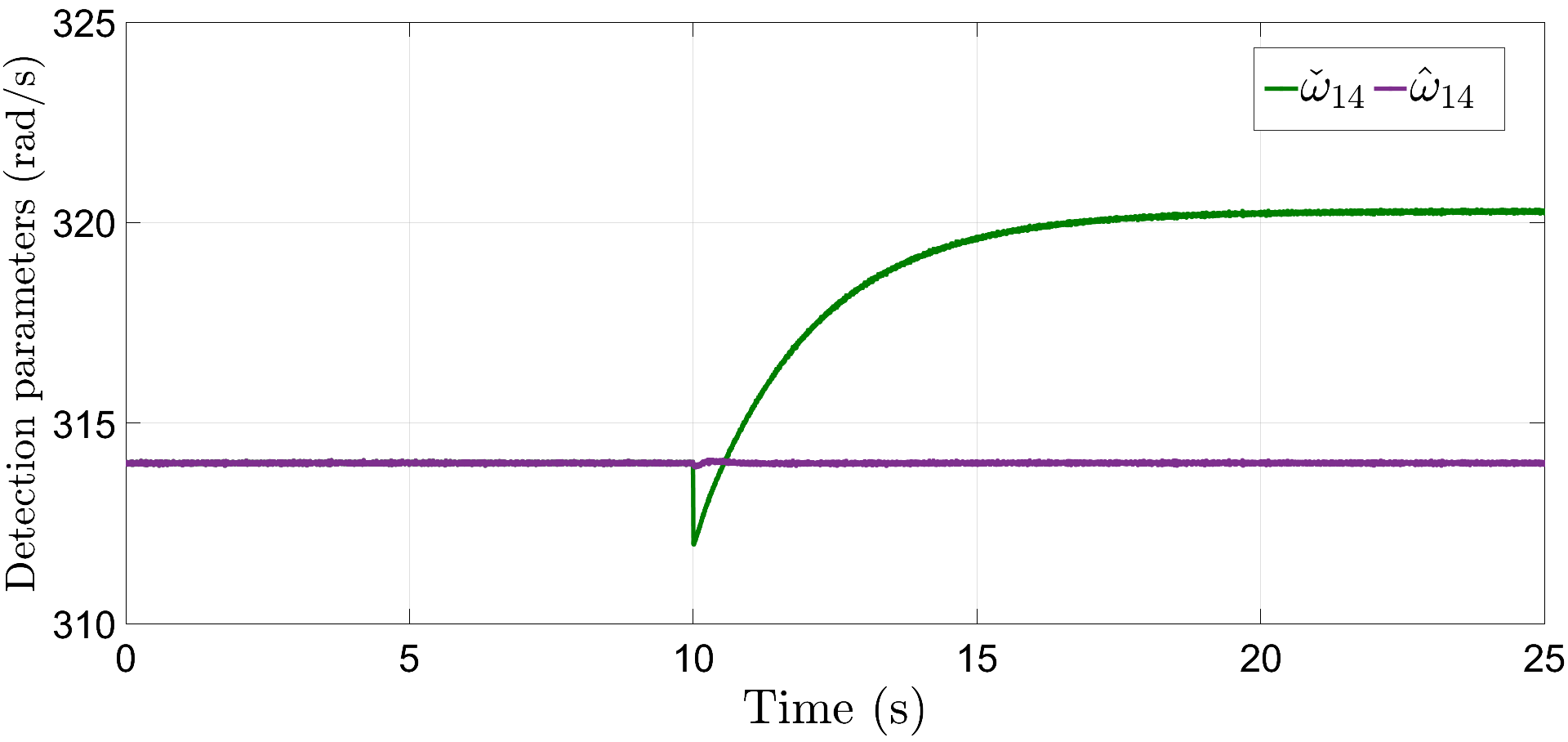
To illustrate this, we consider the following scenario wherein the communication link between DG 1 and DG 4 is under attack as shown in Fig. 12(a), which is initialized at s with an initial magnitude of rad/s as shown in Fig. 13, with all the other attack components being 0. Due to this, a corrupted frequency signal (please refer to (3)) is sent from node to node in the control layer . However, DGs and share an additional information through the auxiliary layer according to (28), and is given by , using which, the estimated frequency signal at node 1, due to an attack on node 4, can be calculated using (29) as .
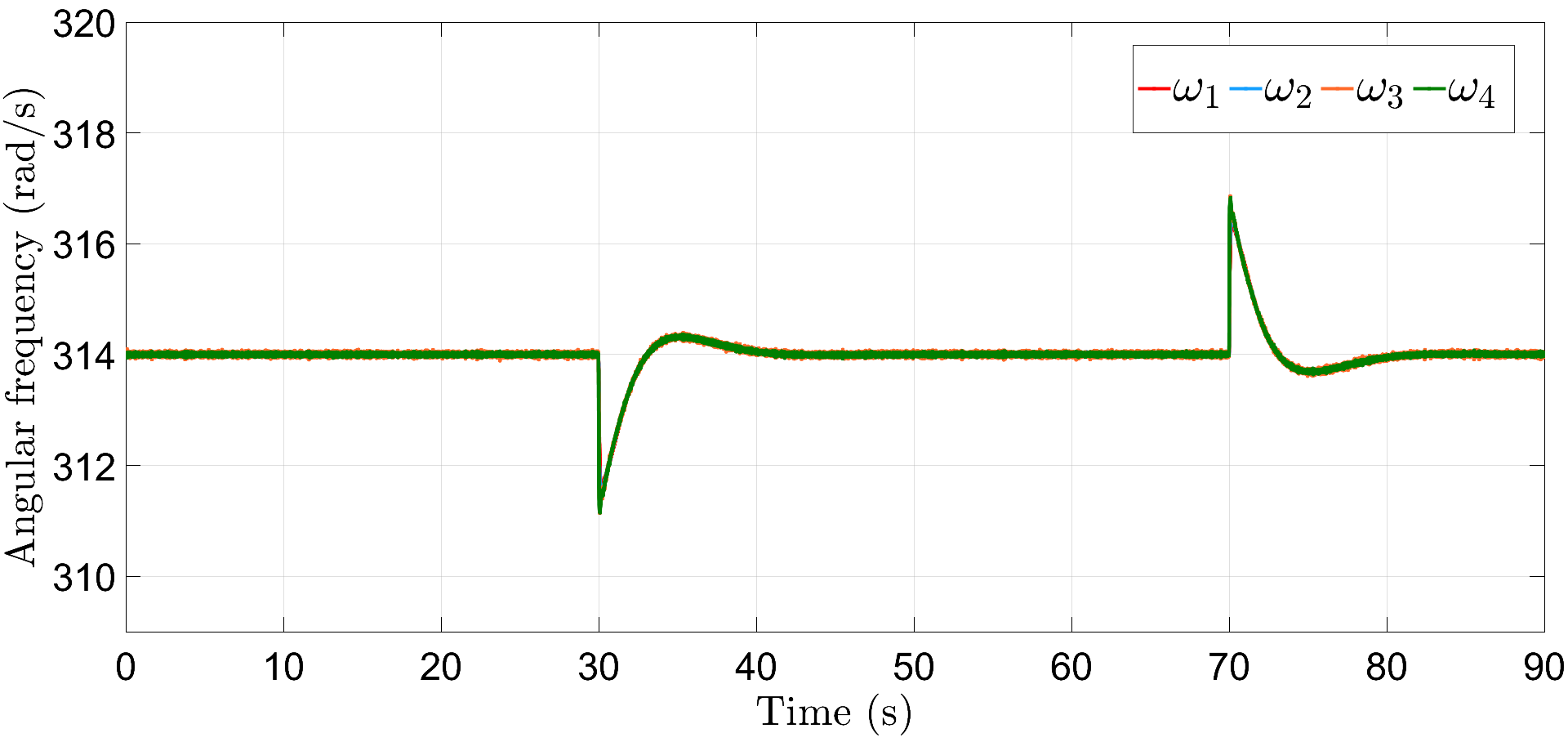
Fig. 14 shows the plot of actual and estimated frequency signal with time. Clearly, after s, and hence, an attack is detected on the communication link connecting nodes 1 and 4. This attack can be isolated by removing the edge provided the remaining network is connected, that is, the isolated network contains at least one spanning tree. As shown in Fig. 12(b), since the microgrid system remains connected even after isolation of the corrupted communication link, it operates normally likewise in subsection VI-A; please refer to Figs. 15 and 16 for frequency restoration and power-sharing in this situation. Here, the load perturbations are introduced with the same magnitude and at similar time instants as in the previous subsection.
VII Conclusion
Relying on an auxiliary layer-based design, we investigated an attack-resilient distributed control mechanism for achieving frequency regulation and active power-sharing in an islanded AC microgrid network. One of the main features of our approach is that it not only guarantees the resiliency against simultaneous frequency and power attacks but also, devises an attack detection mechanism as a byproduct, leveraging the interaction between the control and auxiliary layers. The frequency and power controllers were formulated as leader-follower and leaderless multi-agent systems, respectively, accompanied by suitable auxiliary-state dynamics. Under (standard) assumptions on frequency and power attacks, it was shown that the proposed approach assures the frequency restoration and active power-sharing in the small neighborhood of their steady-state values in the presence of any attack. It was proved that these bounds depend on the underlying network topology, the magnitude of the attack signal, and the pinning and control gains decided by the designer. Extensive simulation results were provided to illustrate and verify the theoretical developments in the paper, followed by a simulation demonstrating attack detection and isolation provided the resulting network is connected.
It would be interesting in future work to extend the analysis to a resilient finite-time distributed framework as the power systems are expected to respond in a certain time to avoid any serious damage.
References
- [1] Q. Zhou, M. Shahidehpour, A. Paaso, S. Bahramirad, A. Alabdulwahab, and A. Abusorrah, “Distributed control and communication strategies in networked microgrids,” IEEE Communications Surveys & Tutorials, vol. 22, no. 4, pp. 2586–2633, 2020.
- [2] C. Peng, H. Sun, M. Yang, and Y.-L. Wang, “A survey on security communication and control for smart grids under malicious cyber attacks,” IEEE Transactions on Systems, Man, and Cybernetics: Systems, vol. 49, no. 8, pp. 1554–1569, 2019.
- [3] H. T. Reda, A. Anwar, and A. Mahmood, “Comprehensive survey and taxonomies of false data injection attacks in smart grids: attack models, targets, and impacts,” Renewable and Sustainable Energy Reviews, vol. 163, p. 112423, 2022.
- [4] R. Lu, J. Wang, and Z. Wang, “Distributed observer-based finite-time control of ac microgrid under attack,” IEEE Transactions on Smart Grid, vol. 12, no. 1, pp. 157–168, 2020.
- [5] Y. Wang, S. Mondal, C. Deng, K. Satpathi, Y. Xu, and S. Dasgupta, “Cyber-resilient cooperative control of bidirectional interlinking converters in networked ac/dc microgrids,” IEEE Transactions on Industrial Electronics, vol. 68, no. 10, pp. 9707–9718, 2020.
- [6] M. S. Sadabadi, S. Sahoo, and F. Blaabjerg, “A fully resilient cyber-secure synchronization strategy for ac microgrids,” IEEE Transactions on Power Electronics, vol. 36, no. 12, pp. 13 372–13 378, 2021.
- [7] J. Xiao, L. Wang, Z. Qin, and P. Bauer, “A resilience enhanced secondary control for ac micro-grids,” IEEE Transactions on Smart Grid, 2023.
- [8] A. Intriago, F. Liberati, N. D. Hatziargyriou, and C. Konstantinou, “Residual-based detection of attacks in cyber-physical inverter-based microgrids,” IEEE Transactions on Power Systems, 2023.
- [9] S. Madichetty and S. Mishra, “Cyber attack detection and correction mechanisms in a distributed dc microgrid,” IEEE Transactions on Power Electronics, vol. 37, no. 2, pp. 1476–1485, 2021.
- [10] M. Liu, C. Zhao, J. Xia, R. Deng, P. Cheng, and J. Chen, “Pddl: Proactive distributed detection and localization against stealthy deception attacks in dc microgrids,” IEEE Transactions on Smart Grid, vol. 14, no. 1, pp. 714–731, 2022.
- [11] Y. Wan and T. Dragičević, “Data-driven cyber-attack detection of intelligent attacks in islanded dc microgrids,” IEEE Transactions on Industrial Electronics, vol. 70, no. 4, pp. 4293–4299, 2022.
- [12] A. Takiddin, S. Rath, M. Ismail, and S. Sahoo, “Data-driven detection of stealth cyber-attacks in dc microgrids,” IEEE Systems Journal, vol. 16, no. 4, pp. 6097–6106, 2022.
- [13] K. Zhang, C. Keliris, T. Parisini, and M. M. Polycarpou, “Stealthy integrity attacks for a class of nonlinear cyber-physical systems,” IEEE Transactions on Automatic Control, vol. 67, no. 12, pp. 6723–6730, 2021.
- [14] L.-Y. Lu, J.-H. Liu, S.-W. Lin, and C.-C. Chu, “Concurrent cyber deception attack detection of consensus control in isolated ac microgrids,” IEEE Transactions on Industry Applications, 2023.
- [15] A. Mustafa and H. Modares, “Attack analysis and resilient control design for discrete-time distributed multi-agent systems,” IEEE Robotics and Automation Letters, vol. 5, no. 2, pp. 369–376, 2019.
- [16] A. Gusrialdi, Z. Qu, and M. A. Simaan, “Competitive interaction design of cooperative systems against attacks,” IEEE Transactions on Automatic Control, vol. 63, no. 9, pp. 3159–3166, 2018.
- [17] Y. Chen, D. Qi, H. Dong, C. Li, Z. Li, and J. Zhang, “A fdi attack-resilient distributed secondary control strategy for islanded microgrids,” IEEE Transactions on Smart Grid, vol. 12, no. 3, pp. 1929–1938, 2020.
- [18] Q. Zhou, M. Shahidehpour, A. Alabdulwahab, A. Abusorrah, L. Che, and X. Liu, “Cross-layer distributed control strategy for cyber resilient microgrids,” IEEE Transactions on Smart Grid, vol. 12, no. 5, pp. 3705–3717, 2021.
- [19] Y. Liu, Y. Li, Y. Wang, X. Zhang, H. B. Gooi, and H. Xin, “Robust and resilient distributed optimal frequency control for microgrids against cyber attacks,” IEEE Transactions on Industrial Informatics, vol. 18, no. 1, pp. 375–386, 2021.
- [20] M. Jamali, M. S. Sadabadi, M. Davari, S. Sahoo, and F. Blaabjerg, “Resilient cooperative secondary control of islanded ac microgrids utilizing inverter-based resources against state-dependent false data injection attacks,” IEEE Transactions on Industrial Electronics, 2023.
- [21] J. M. Guerrero, J. C. Vasquez, J. Matas, L. G. De Vicuña, and M. Castilla, “Hierarchical control of droop-controlled AC and DC microgrids—a general approach toward standardization,” IEEE Transactions on industrial electronics, vol. 58, no. 1, pp. 158–172, 2010.
- [22] L. Wang and F. Xiao, “Finite-time consensus problems for networks of dynamic agents,” IEEE Transactions on Automatic Control, vol. 55, no. 4, pp. 950–955, 2010.
- [23] V. Vaishnav, D. Sharma, and A. Jain, “Quadratic-droop-based distributed secondary control of microgrid with detail-balanced communication topology,” IEEE Systems Journal, 2023.
- [24] H. Dong, C. Li, and Y. Zhang, “Resilient consensus of multi-agent systems against malicious data injections,” Journal of the Franklin Institute, vol. 357, no. 4, pp. 2217–2231, 2020.
- [25] J. Guerrero, L. G. de Vicuna, J. Matas, M. Castilla, and J. Miret, “Output impedance design of parallel-connected ups inverters with wireless load-sharing control,” IEEE Transactions on Industrial Electronics, vol. 52, no. 4, pp. 1126–1135, 2005.
- [26] R. A. Horn and C. R. Johnson, Topics in matrix analysis. Cambridge university press, 1991.
- [27] P. Lancaster and H. K. C. R. Farahat, “Norms on direct sums and tensor products,” mathematics of computation, vol. 26, no. 118, pp. 401–414, 1972.
- [28] R. A. Horn and C. R. Johnson, Matrix analysis. Cambridge university press, 2012.
- [29] H. K. Khalil, “Nonlinear systems third edition,” Patience Hall, vol. 115, 2002.
- [30] A. Gusrialdi and Z. Qu, “Cooperative systems in presence of cyber-attacks: a unified framework for resilient control and attack identification,” in 2022 American Control Conference (ACC). IEEE, 2022, pp. 330–335.
- [31] P. Danzi, M. Angjelichinoski, C. Stefanovic, T. Dragicevic, and P. Popovski, “Software-defined microgrid control for resilience against denial-of-service attacks,” IEEE Transactions on Smart Grid, vol. 10, no. 5, pp. 5258–5268, 2019.
- [32] S. Zhang, “An overview of network slicing for 5g,” IEEE Wireless Communications, vol. 26, no. 3, pp. 111–117, 2019.