Boson condensation and instability in the tensor network representation of string-net states
Abstract
The tensor network representation of many-body quantum states, given by local tensors, provides a promising numerical tool for the study of strongly correlated topological phases in two dimension. However, the representation may be vulnerable to instabilities caused by small variations in the local tensors. For example, the topological order in the tensor network representations of the toric code ground state has been shown in Ref.Chen et al., 2010 to be unstable if the variations break certain symmetry of the tensor. In this work, we ask whether other types of topological orders suffer from similar kinds of instability and if so, what is the underlying physical mechanism and whether we can protect the order by enforcing certain symmetries on the tensor. We answer these questions by showing that the tensor network representation of all string-net models are indeed unstable, but the matrix product operator (MPO) symmetries of the tensors identified in Ref.Şahinoğlu et al., 2014 can help to protect the order. In particular we show that a subset of variations that break the MPO symmetries lead to instability by inducing the condensation of bosonic quasi-particles which destroys the topological order in the system. Therefore, such variations must be forbidden for the encoded topological order to be reliably extracted from the local tensors. On the other hand, if a tensor network based variational algorithm is used to simulate the phase transition due to boson condensation, such variation directions may prove important to access the continuous transition correctly.
pacs:
I Introduction
The tensor network representation of quantum states (including the matrix product states in D)Fannes et al. (1992); White (1993); Verstraete et al. (2008); Vidal (2009) provides a generic tool for the numerical study of strongly interacting systems. As variational wave functions, the tensor network states can be used to find the ground state wave function of local Hamiltonians and identify the phase at zero temperature. In particular, it has become a powerful approach in the study of topological phases, whose long range entanglement is hard to capture with conventional methods. It has been shown that a large class of topological states, the string-net condensed states Levin and Wen (2005), can be represented exactly with simple tensors Gu et al. (2009); Buerschaper et al. (2009). Moreover, numerical studies applied to realistic models have identified nontrivial topological features in the ground state wave function (see e.g. Ref.Yan et al., 2011; Jiang et al., 2012; Depenbrock et al., 2012).
In the numerical program, the parameters in the tensors are varied so as to find the representation of the lowest energy state. After that, topological properties are extracted from these tensors in order to determine the topological phase diagram at zero temperature. However, this problem might not be numerically ‘well-posed’. That is, arbitrarily small variations in the local tensor may lead to completely different result as to what topological order it represents. In particular, Ref. Chen et al., 2010 demonstrates that this happens in the case of toric code topological order. While this presents a serious problem for the tensor network approach to study topological phases, Ref. Chen et al., 2010 also showed that such instabilities can be avoided if certain symmetry is preserved in the local tensor. It has been shown that the topological order in the toric code model is stable against arbitrary local perturbation to the Hamiltonian of the system Bravyi et al. (2010). The fact that a certain variation direction of the tensor network representation may induce an immediate change in the topological order indicates that such a variation corresponds to highly nonlocal changes in the ground state wave function.
Does similar problem occur for general string-net states as well? This is the question we address in this paper. In particular, we ask:
-
1.
Does the tensor network representation of other string-net states also have such unstable directions of variation?
-
2.
If so, can they be avoided by preserving certain symmetries in the local tensor?
-
3.
What is the physical reason behind such instabilities and their prevention?
While the symmetry requirement for toric code is naturally related to the gauge symmetry of the theory, for more general string-nets which are not related to gauge theory, it is not clear whether similar symmetry requirement is necessary and if so what they are.
In this paper, we answer the above questions as follows:
-
1.
All string-net tensors have unstable directions of variation.
- 2.
-
3.
The physical reason for the instability is that ‘stand-alone’ variations which violate these symmetries induce condensation of bosonic quasi-particles and hence destroys (totally or partially) the topological order.
To support the above claims, we calculate the topological entanglement entropy Kitaev and Preskill (2006); Levin and Wen (2006) from the representing tensor and (partially) characterize the encoded topological order. In particular, consider a tensor network state represented by a local tensor . We are interested in varying the local tensor everywhere on the lattice, in such a way that, , where . In order to study whether topological order is lost or still present after a variation in the direction , we calculate topological entanglement entropy of the original and the modified state as a function of , . We say the variation is unstable in direction if
| (1) |
If is smaller than , we say that topological order is (partially) lost. If we call that direction stable meaning that topological order is still present and remains the same. This understanding of tensor instability is important not only for the identification of topological order for a particular model, but also for the numerical study of phase transitions between topological phases. In particular, if one is to use the tensor network approach to study phase transition due to boson condensation, then the corresponding variation direction must be allowed in order for the simulation to give correct results. For example, in Ref. Gu et al., 2008, it was shown that if such variation directions are not included as variational parameters, then we see a first order transition even though in fact it is second order. We are going to elaborate more on this point later in the paper.
The paper is organized as follows. In section II, we start from the simplest string-net model – the toric code modelKitaev (2003), and study two types of tensor network representation of its ground state. The single line representation was studied in Ref. Chen et al., 2010 and here we recover the result on the instability of the tensor with respect to certain symmetry breaking variations. While reproducing the result, we introduce a new algorithm which allows us to investigate more complicated string-net models in later parts of this paper. The second representation we study for the toric code is the double line representation, as discussed in Ref.Gu et al., 2008. While the single line representation has only one virtual symmetry, the double line representation has multiple of them. Do they all protect the encoded topological order in the same way? To find out, we calculate, with the new algorithm, the topological entanglement entropy for the double line representation with different variations. It reveals that there are actually two kinds of symmetries, and their relation to the topological order is actually opposite to one another. That is, the only variations that change the topological order are the ones that respect the first kind of symmetry (which we call ‘stand-alone’) but actually break the second kind (MPO symmetry Şahinoğlu et al. (2014)). One of the key results of this paper is contained in the next section, III, where we first identify the source of these two symmetries and define them precisely, and make the general conjecture of TNR-instability. This conjecture says that all TNR have these two kinds of symmetries it is always the variations that respect the stand-alone but break the MPO symmetry that are unstable.
Then in section IV we put forward the physical understanding of TNR instability by systematically understanding the physical significance of the two symmetries and their interplay. This understanding concludes that the instability occurs due to condensation of topological bosons of the string-net model under consideration. In the next section we note that tensor instability actually has implications for phase transition simulations using tensor network ansatz. And hence, our result should guide the choice of tensor network anstaz in phase transition simulations. To generalize our study to generic string-net models, we study next the double semion model in section VI. We first predict instabilities using our conjecture, and then find them to be true in our numerical calculation.
We then directly apply our study to the general string-net model and its triple-line TNR in section VII. We calculate the required symmetries and conclude that our conjecture predicts that triple-line TNR of all string-net have unstable directions of variations. An analytical proof of this prediction can be found in Appendix F. Finally in section VIII we test our understanding of the general string-model on the double-Fibonacci model, which has a non-abelian topological order as opposed to toric code and double-semion. We again find our conjectures to be precisely accurate. Our results also reveal the physical meaning of the virtual tensor network symmetries for topologically ordered ground states that have been found for Kitaev quantum double models (G-injectivitySchuch et al. (2010)) and later generalized to twisted quantum doubles (twisted G-injectivityBuerschaper (2014) and MPO-injectivityŞahinoğlu et al. (2014)) and general string-net models (MPO-injectivityŞahinoğlu et al. (2014)).
Finally, a summary of the results is given in section IX and open questions are discussed. Some details of our analysis are explained in the appendices, including relations of MPO symmetries to the Wilson-loop operators, a brief review of string-net models, their tensor network representation and their transformation under the application of string-operators, proof of the existence of unstable directions in triple-line representations of general string-net ground states, and finally the dependence of topological entanglement entropy on the choice of boundary condition in our calculation.
II Instabilities in TNRs of the toric code
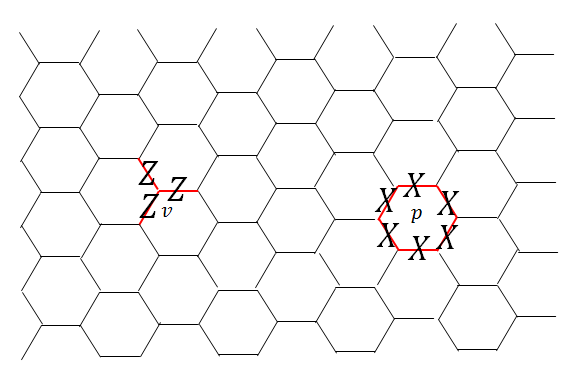
We start from the simplest illustrative example of nonchiral intrinsic topological order: the toric code (Kitaev, 2003). We work on a hexagonal lattice and assign local degrees of freedom, i.e. -spin down- or -spin up, on the edges of the lattice. It is convenient to consider spin up as a presence of a string and as the absence of the string. So the total Hilbert space can be thought of as the space of all string configurations on a hexagonal lattice. The toric code Hamiltonian is a sum of local commuting projectors, given as
| (2) | |||||
where denotes the vertices, and denotes the plaquettes. denotes the edges attached to and denotes the edges on the boundary of plaquette (see Fig. 1). Vertex terms restrict the ground states to closed strings of s and plaquette terms make all possible loop configurations of equal weight. Hence, the toric code ground state (up to normalization) can be written as
| (3) |
where denotes the string configurations on the lattice. So, the ground state of toric code Hamiltonian is an equal weight superposition of all closed string configurations. It has topological order and has topological entanglement entropy . The toric code model has 4 anyons (superselection sectors), . is the vacuum, -particle is the -gauge charge (violates the vertex term) and -particle is the -gauge flux (violates the plaquette term). Both and have a trivial topological spin, so we call them topological bosons, or simply bosons. Braiding with produces a phase factor of .
Now we look at tensor network representations (TNR) of the toric code ground state. Specifically, we will first explain the Single-line tensor representation, and then the Double-line tensor representation. We will see that different TNRs of the same state can have different kinds of instabilities.
II.1 Single-line TNR of the toric code and its instability
This is the simplest TNR of the toric code state. We first copy each computational basis into two, as shown in the Fig. 2. That is, the labels and on every edge become and on the same edge. Now the local Hilbert space neighbouring each vertex is made out of three qubits. We associate a tensor with three physical indices/legs (throughout the paper we will use “indices” and “legs” interchangeably), and three virtual indices/legs to each vertex, represented algebraically as where are the three physical indices and are the three virtual indices, as shown in Fig. 2. The components of the tensor are
| (4) |
where is the kronecker delta function. So, physical and virtual legs are identified and an even number of indices carry label out of every three edges neighbouring a vertex, i.e., we satisfy the vertex condition. The plaquette condition is also satisfied since every configuration is of equal weight. Therefore, the tensor network state constructed using the above local tensor leads to the toric code ground state given in Eq. (3).
It was shown by Chen et al. (2010) that single-line TNR of the toric code state is not stable in certain directions of variation. Before we explain what these unstable directions of variation are, we first note that the single-line TNR explained above has a virtual symmetry. If an operation on the virtual indices leaves the tensor invariant, we will call it a virtual symmetry of the tensor. Because the single-line tensor is non-zero only when virtual legs have even number of 1s, it has a natural virtual symmetry (see Schuch et al. (2010) for TNR virtual symmetries of the quantum double models). That is, the tensor in (4) satisfies the relation,
| (5) |
where we have omitted the physical legs for visual clarity. (We would often omit physical legs from tensor diagrams throughout the paper when we are mostly concerned with the virtual space/indices.) It is a symmetry with group elements and acting on the virtual legs of the local tensor. Chen et al. (2010) showed that topological order is stable with any respecting variations and unstable with any violating variation. To illustrate this, we can consider two different directions of variation in single-line TNR. We can add an or variation on one of the virtual indices of the tensor,
| (6) |
More explicitly, these tensor components are given by,
| (7) | |||
| (8) |
variation violates the symmetry while does not. That is,
| (9) |
and it was shown that type variations cause an instability and while type variations do not. Note that, though we chose variations only on the virtual indices for simple illustration, the same conclusion applies for any random variation including those on the physical indices. However, if a variation acts only on the physical indices, it cannot break the virtual symmetry, and hence would always be stable.
We reproduce this known result with a new algorithm for calculating . This algorithm allows us to calculate in more complicated examples to be dealt with later. Before we move on to other TNRs, we would like to explain the algorithm used here. Readers can skip this section if they are not interested in the details of the algorithm.
II.2 Algorithm for calculating topological entanglement entropy
Here we explain the algorithm we use to calculate the topological entanglement entropy of any translation invariant tensor network state. We use the idea presented by Cirac et al. (2011) to calculate reduced density matrix on a region and hence its entanglement entropy. We consider honeycomb lattice, though it can easily be extended to other lattices. By translation invariant we mean that all vertices on the sublattice A and sublattice B are attached with the same tensors, and , respectively. First we define certain notations for convenience of later discussion. The starting objects are given tensors , where and denote the set of physical and virtual indices, respectively: . The state represented by these tensors can be written as
| (10) |
We denote the tensor resulting from contracting the virtual indices of tensors on a region as . denotes the ‘double tensor’ resulting from contracting the physical indices of with those of , that is, . Similar to , we denote the double tensor contracted on a region as .
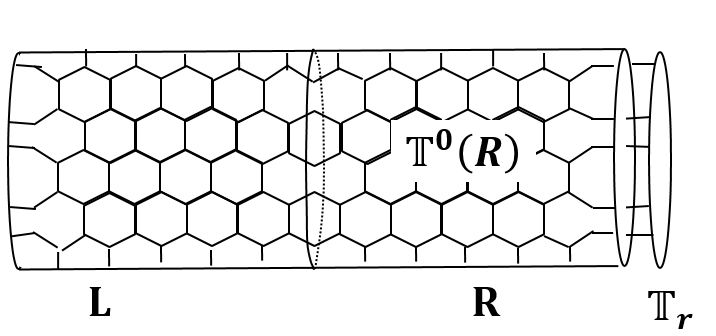
Now let us consider putting this tensor network state on a cylinder. We denote the left half of the cylinder as and the right half as . The honeycomb lattice is placed in a way so that and divide it into exact halves. So the line between the two halves goes through the middle of the plaqeuttes as shown in the Fig. 3. We denote the tensors on the left and right boundaries as and .
When we contract bulk double tensors with the boundary double tensors, we get a density matrix operator on the virtual indices,
| (11) |
Cirac et al. (2011) showed that the physical reduced density matrix on one of these halves, let’s say the left one, is related to the density operator on the virtual indices as,
| (12) |
where is an isometry. Hence and have the same spectrum. In addition, under right symmetry conditions, . When this is true, up to change of basis, we find that . The normalized reduced density matrix is
| (13) |
It is known that the Rényi entropy with any Rényi index gives the same topological entanglement entropyFlammia et al. (2009). So we calculate Rényi entropy with Rényi index ,
| (14) | |||||
In the limit of large cylinder, it should behave like
| (15) |
where is the circumference of the cylinder. This is how we calculate starting with a tensor network state.
Before we move on to the next step, we would like to mention an important subtlety regarding computation of on a cylinder. In Ref.Dong et al., 2008; Zhang et al., 2012 it has been shown that calculated this way on a cylinder, in general, might depend on the boundary conditions. We choose a particular boundary condition for all our calculations and examine the dependence of on boundary condition in the appendix G. Our findings are consistent with the conclusion in Ref.Zhang et al., 2012.
We first have to calculate for the above setup. The problem is, the computational complexity of exact tensor contraction grows exponentially with the size of , so we need to use some approximate renormalization algorithm. We use an algorithm which is a slight modification of known tensor renormalization algorithms (Gu et al., 2008; Vidal, 2003, 2009). Consider double tensors contracted along a thin strip on the cylinder giving us a transfer matrix operator, . If includes of such strips, we have . Since the tensor network state under consideration are short range correlated along the cylinder, the spectrum of is gapped. Consequently, for large , only the highest eigenvalue and the corresponding eigenvector of dominates. That is, in thermodynamic limit, only depends on the highest eigenvalue/eigenvector of the transfer matrix operator, . Moreover, we expect to approximate the eigenvector of highest eigenvalue with a Matrix Product State (MPS) with finite bond dimensions, since the tensor network state is short range correlated along the circumference of the cylinder. So we can start with a boundary MPS, apply the transfer matrix operator, and approximate the resulting state as an MPS with a fixed, finite bond dimensions. With each step, approximation to the eigenvector with highest eigenvalue improves and we do this recursively until we reach the fixed point giving us the desired eigenvector. Note that we require transfer matrix operators to be reflection symmetric for the condition to hold true.
The recursive algorithm is as following:
-
1.
Initiate the boundary double tensor and . The tensor network to be contracted looks as
![[Uncaptioned image]](https://cdn.awesomepapers.org/papers/690c64a3-bcf4-458a-9cef-b735cb8527dd/initialize.png)
(16) -
2.
Contract the bulk double tensors, and with the boundary tensors and in the following way to make the 4 leg tensor ,
(17) -
3.
Reshape the tensor into a matrix where Vidal (2003). Now we perform an SVD decomposition of , and the approximation step: we keep only the highest singular values, and define the new tensors and as and where takes values . and form an approximate decomposition of ,
(18) (19) -
4.
Check convergence of . is the precison tolerance. Let denote the th recursion step. If exit algorithm.
-
5.
Put and and go to step 2.
II.3 Numerical result for single-line TNR with random variations
.
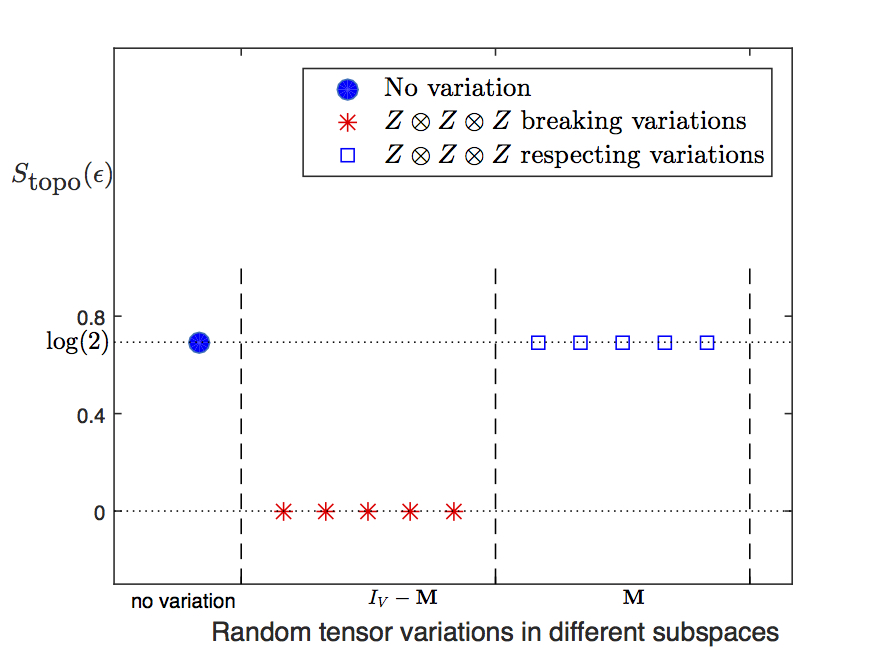
We use the algorithm described in the previous section to calculate of the tensor network state constructed by a local tensor with random variations added to the fixed point tensor given in Eq. (4). is projector onto the full virtual space. is a projector on to the space of variations that respect the symmetries. So, is a projector on to the space of variations that break symmetries. We first calculate in the state constructed by the fixed point tensor, . Then we generate a random tensor on the full space, project it on to the subspace , add it to the fixed point value, and calculate . Similarly, we generate a random tensor on the full space, project it on to respecting subspace , add it to the fixed point value, and calculate . We keep the value of variation strength (low enough) to make sure it is not near any phase transition point. The results are shown in Fig. 4.
We see that respecting variations lead to the same topological entanglement entropy as the fixed point state, while violating variations lead to zero topological entanglement entropy. This reproduces the result by Chen et al. (2010).
II.4 Double-line TNR of the toric code state and its instablities
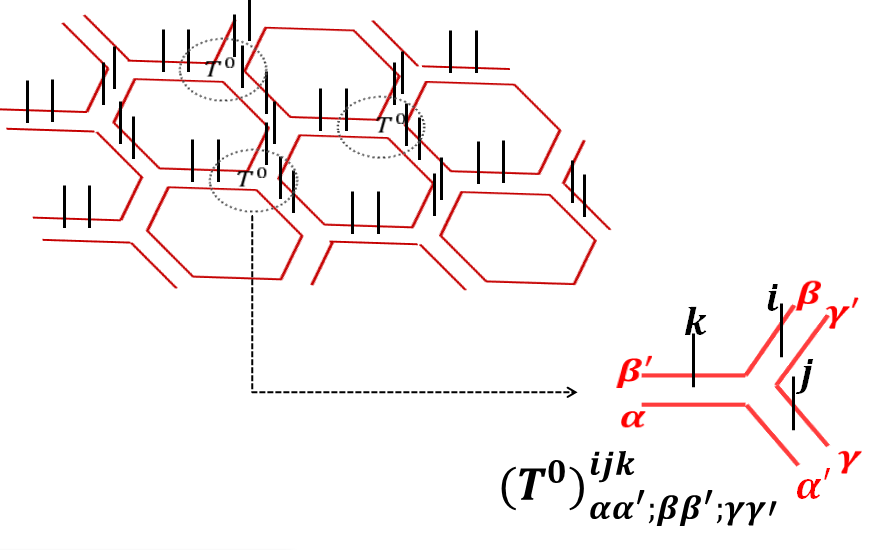
In the double-line TNR of the toric code state, we associate with each vertex a tensor with 3 physical legs and 6 virtual legs, , (see Fig. 5). We will refer to these virtual indices as ‘plaquette indices’ or ‘plaquette legs’ sometimes, because they carry the plaquette degree of freedom that comes from the local Hamiltonian term. All indices take values 0 and 1. We denote the TNR corresponding to the RG fixed point state as . (We use the same notation for different fixed point tensors, but it should be clear from the context which fixed point tensor we are discussing.) First property of is that , that is, indices on the same plaquette assume the same values. The second property is that the physical indices can be considered as labeling the domain wall between the virtual indices. If the two virtual indices in the same direction have the same values (both either or ) then the physical index in the middle has value , otherwise it is . That is, (all additions are modulo 2). So we can write as
We can write all non-zero components explicitly,
Is double-line TNR unstable too? We find that it is unstable as well in certain directions of variations. Similar to the single-line case, a variation is stable or unstable depending on whether or not it violates certain virtual symmetries. So let’s first look at the symmetries of the double-line TNR. It has 6 virtual indices, so the virtual space dimension is , while the physical space dimension is again 4. So we need a symmetry group with . Indeed the tensor has a virtual symmetries. First it has a symmetry. That is, if we flip all the six virtual indices, the tensor remains the same. Second, it has three symmetries, where are applied to the two virtual indices on the same plaquette. So the double-line tensor in (LABEL:DLTNReq) satisfies these symmetry equations:
| (21) |
Single-line TNR had only one such symmetry and it turned out that breaking it results in phase transition. For double-line we have four symmetries. So the question is, are all of them important? That is, is it the case that breaking any of them with a variation leads to instability? Indeed many different possible kinds of variations are possible:
| (22) |
A variation can violate but not (for example, 22(a) ), or it can violate but not (for example, 22(b) ), or it can violate both (for example, 22(c) ), or it can violate neither(for example, 22(d) ), etc. So to find out, we need to look at the unstable directions of variations of the fixed point tensor.
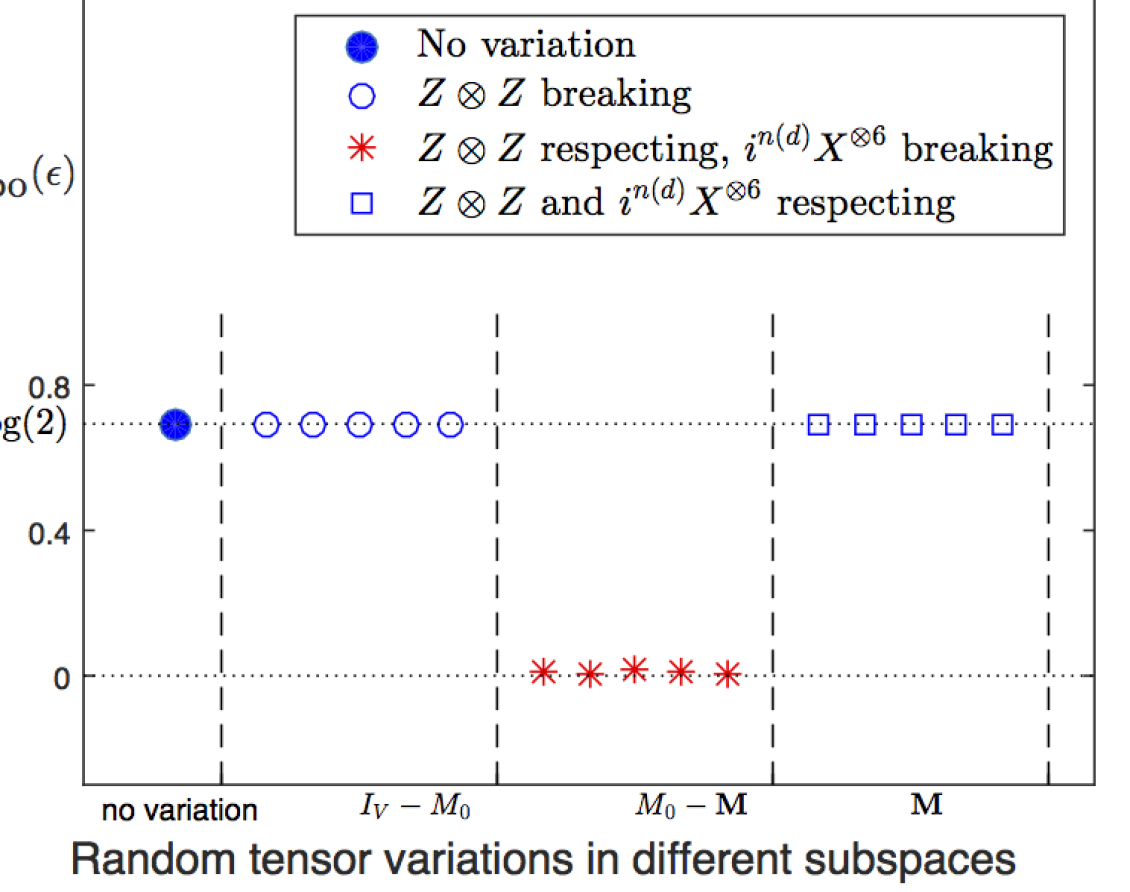
Our numerical calculation reveals an interesting result. We find that (see Fig. 6 )
-
1.
If a variation violates any of the symmetries then it is stable.
-
2.
If a variation respects all symmetres then there are two subcases
-
(a)
If it respects symmetry then it is stable.
-
(b)
If it breaks symmetries then it is unstable.
-
(a)
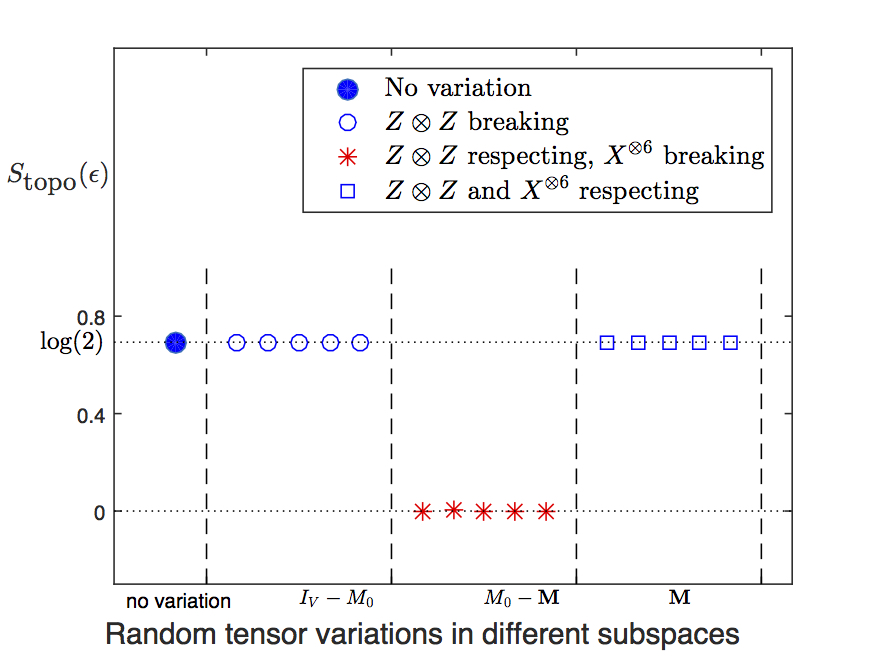
So we see that the relation between unstable variations and virtual symmetries of the double-line TNR is more complicated than that for single-line TNR. The symmetry looks like the symmetry of the single-line TNR, as they both operate as a loop operators, and unstable variations in both TNR violates these loop symmetries. However, the crucial difference in double-line is that then there are extra symmetries (the 3 symmetries) which have an exact opposite relation with the unstable variations: a variation is actually stable when it violates these symmetries (irrespective of whether or not it violated the loop symmetry). It indicates that the sources of these two kinds of symmetries must be different.
How can we understand this phenomena? We will now show that the sources of these symmetries are indeed different, and it is the interplay between these two symmetries that determines the tensor instability phenomena. The symmetries whose violation causes instability comes from the so-called MPO-injective subspaceŞahinoğlu et al. (2014) of the virtual space, while the symmetries whose violation causes stability comes from what we define to be stand-alone subspace. We now define these subspaces precisely and put forward the conjecture regarding their relationship to TNR instability.
III Virtual symmetries/subspaces of a TNR and Tensor-Instability Conjecture
We first give a constructive definition of stand-alone subspace of a TNR.
III.1 Stand-alone subspace
A generic tensor can be thought of as a linear map from virtual vector space to the physical vector space. Consider a generic tensor, where is the collection of all physical indices and is the collection of all virtual indices. Double tensor of a tensor is defined as . For example, for single-line TNR the double tensor can be represented diagrammatically as follows
| (23) |
In general we would think of double tensor as having two layers of virtual indices, lower and upper. Double tensor can be interpreted as a density matrix on the virtual space. Now consider the double tensor of a RG fixed point TNR, , contracted over some large region . Let’s say we remove from one site and replace it with some other double tensor, as follows:
| (24) |
What do we get? In particular, are there tensors such that this replacement collapses the whole tensor network? By ‘collapse’, we mean that we simply get zero upon contraction. The answer turns out to be yes for tensors that represent topological order. In fact, as we will see later, most tensors will collapse the fixed point tensor network upon replacement. It turns out that only the tensors supported on a particular subspace of the full virtual space can replace the fix point tensor without collapsing the whole tensor network. We will call this space the stand-alone subspace of the TNR. Now we will give a systematic way of calculating this subspace for a given fixed-point TNR.
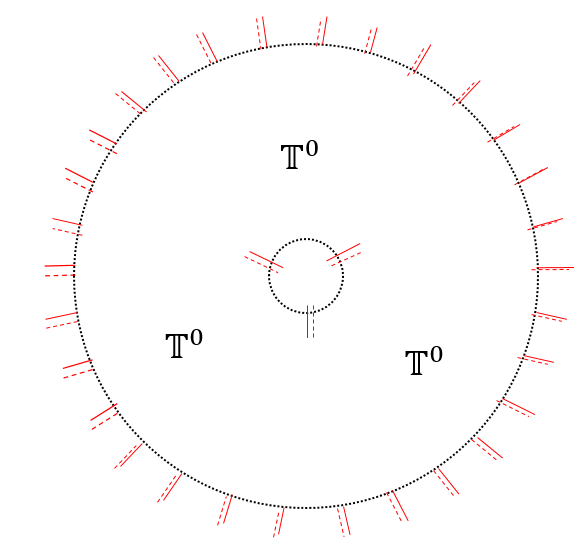
Consider contracting the fixed-point double tensors on a large disc with an open boundary. Now we remove the tensor at the origin. We get a tensor network with dangling virtual indices at the origin and at the boundary of the disc. We want to find out the space of tensors that can be put on the origin without collapsing the tensor network. We do not care what tensor at the boundary we get. So we trace out the indices at the outer boundary (i.e. contract upper and lower virtual indices with each other). This leaves us with a tensor at the origin. The support space of this tensor will be precisely the stand-alone space. Any tensor supported on this subspace can stand alone with the surrounding tensor being the fixed-point tensors.
Note that definition of stand-alone space implies that it is a vector space. If and doesn’t collapse the tensor network then will also not collapse the network.
Stand-alone subspace of double-line TNR: Now let’s first calculate the stand-alone subspace of double-line TNR of toric code as it is more interesting than that of single-line TNR. The double tensor of in (LABEL:DLTNReq) can be written as (ignoring an overall normalization factor)
| (25) | |||||
where the double tensor is written as an operator between the lower virtual indices and upper virtual indices. The and act in the way it is shown in Fig. 21. We need to contract this tensor on a disc with a hole at the origin. To contract two tensors given in an operator form, we need to multiply them and take a trace on the shared indices. A cumbersome but straight-forward calculation shows that double tensor contracted on a region give (ignoring an overall normalization factor)
| (26) | |||||
where denote the boundary of , and is the length of the boundary. means the operator is applied on the virtual legs along the boundary . We will omit this when it is clear from the context which leg the operator is being applied on. The region we want is a disc with a vertex removed, . denotes the disc with virtual legs at the boundary. It has two disconnected boundaries, one the boundary of and other the boundary of (with opposite orientation).
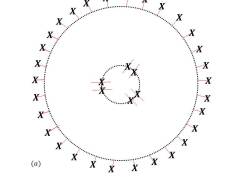
| (27) | |||||
As explained in Fig. 8, operators act on the two boundaries simultaneously, but operators act independently. Now to get the stand-alone space at the origin, we need to trace out the virtual legs at the boundary of . If we expand the expression for above and apply trace on the operators on the outer boundary, only the terms with identity on the outer boundary survive. operator does not have such a term, but does. So finally, tracing out the outer boundary leaves only on the inner boundary. That is, we get the following tensor on the 6 virtual indices incident on a singe vertex
| (28) |
, so
| (29) |
is a projector on to the support space of . defines the stand-alone space of double-line TNR of toric code. Any tensor that satisfies can ‘stand alone’. will be used to denote the projector on to stand-alone space throughout the paper. So we see that only the tensors that respect the symmetry can stand alone. The symmetry, however, is not required to define the stand-alone space.
Stand-alone subspace of single-line TNR: We can also calculate the stand-alone subspace of single-line TNR of toric code. One can calculate the double tensor of single-line TNR in Fig. 4 to be
| (30) |
This double tensor upon contraction on the disc with a hole at the origin () gives (up to an overall normalization)
| (31) |
Now contracting the outer circle gives us
| (32) |
So we see that, for single-line TNR, the stand-alone subspace is actually all of the virtual space. That is, there are no tensors that cannot stand alone.
III.2 MPO-injective subspace
Here we repeat the definition of MPO-injective subspace given in Ref. Şahinoğlu et al., 2014 for convenience.
As explained above, stand-alone subspace is the maximal virtual subspace such that any tensor supported on this subspace can be inserted into the tensor network without collapsing it. Therefore, the virtual space of the RG fixed point tensor, itself must be inside the stand-alone subspace. This virtual space of , which is by definition a subspace of the stand-alone space, is what we would call the MPO-injective subspace. The reason for calling it an MPO-injective space is that, as it turns out, this space is protected by symmetry operators which are Matrix Product Operators (MPO). Let’s make the notion of virtual space of precise. We can think of it as a matrix with indices and and perform an SVD decomposition,
| (33) |
where and are unitary matrices in virtual and physical space, and is the diagonal matrix containing the singular values.
Definition 1.
The MPO-injective space, defined as the virtual support space of ,is the virtual subspace spanned by columns of for which corresponding singular value is non-zero.
Another way to think about this is to again consider the double tensor which is a matrix in the virtual space. An equivalent but more useful definition is,
Definition 2.
The MPO-injective space is the space spanned by eigenvectors of with nonzero eigenvalues.
Using Eq. (33) we can write
| (34) | |||||
| (35) |
where are the singular values and and are the corresponding vectors in virtual and physical space. MPO-injective space is the space spanned by , so the projector on this space is
| (36) |
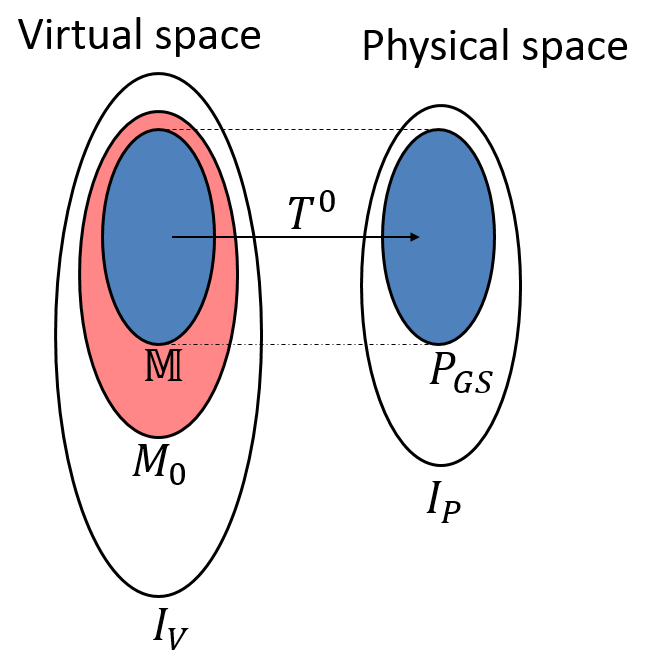
The mathematical understanding of the MPO-injective space is that it is the virtual subspace which is isomorphic to the ground state physical subspace and is the isomorphism. MPO-injective subspace by definition nested inside the stand-alone subspace, which by definition is nested inside the full virtual space. Similarly, the ground-state physical space is by definition a subspace of the full physical space. These spaces are represented visually in Fig. 9 for clarity.
MPO-injective subspace of single-line TNR: We can write the single-line tensor in Eq. (4) in the Eq. (33) form,
Of course, this happened to be already written in SVD decomposed form. So the MPO-injective space is spanned by vectors . So the MPO projector is
| (38) | |||||
We see that this projector can be written as a translation invariant superposition of tensor product of matrices. That’s why we call it the MPO-injective subspace. Remember that stand-alone space of single-line TNR was determined to be all of virtual space, . So as expected, .
MPO-injective subspace of double-line TNR: For calculation of the MPO-injective subspace of double-line tensor in Eq. (LABEL:DLTNReq) we use the second definition in 2 above to avoid a cumbersome but straight forward calculation. We already calculated the double tensor of double-line TNR in Eq. (25). We ignored the normalization factor there. If we use a normalization factor of and write
| (39) | |||||
Then is a projector, that is, it satisfies , and has the same support as hence this is the desired MPO projector. Remember that stand-alone projector was calculated to be , and hence , as expected.
III.3 TNR instability conjecture
Now that we have defined the stand-alone and MPO-injective subspaces precisely, we are ready to state the central conjecture of this work.
Conjecture 1.
If, for a given RG fixed point TNR, , of a topological state, and are the projectors onto the stand-alone and MPO-injective subspaces as defined above, then an infinitesimal tensor variation changes the topological phase of the state if and only if .
It implies that the projector onto the stable space is .
Corollary 1.
An infinitesimal variation does not change the topological phase if and only if .
Corollary 2.
For any tensors , the variation , with does not change the topological phase.
Or in simple words, a variation is unstable if and only if it has a component in the stand-alone space that is outside the MPO-injective subspace. A pictorial representation of the decomposition of the virtual space through these projectors is shown in Fig. 9. We will denote as for convenience. Note that shouldn’t be thought of as ‘the projector onto unstable subspace’ because unstable variations do not form a vector space, as opposed to stable variations that do form a vector space. It is because and does not imply .
Let’s first see how this conjecture is true for the single-line and double-line TNR of the toric code. For single-line we have already calculated the stand-alone and MPO-injective subspaces and found and . So,
| (40) |
So for a tensor if and only if it violates the symmetry. Indeed, this is exactly what we saw numerically in Fig 2. All variations can be summarized visually using Fig. 9 as follows:
| (41) |
Variations supported on the red region are unstable, while those on blue and white are stable. The dimension of each space is indicated. So we see that the space is 4 dimensional space spanned by basis
| (42) |
It is wrong to think that these basis set span the space of unstable variations, because unstable variations do not form a vector space. All we can say is if a variations has overlap with any of these basis, it would cause instabilty.
For double-line TNR we found,
| (43) |
So,
So if and only if satisfies the three symmetries but violates the symmetry. Indeed this is precisely what we found numerically as shown in Fig. 5. All variations can be summarized visually as follows
| (44) |
Variations supported on the red region are unstable, while those on blue and white are stable. The dimension of each space is indicated. So we see that the space is 4 dimensional space spanned by basis
| (45) |
IV Physical understanding of TNR instability
TNR-instablity conjecture would predict mathematicall exactly which variations would be unstable. But what is the physical reason behind such instabilities? To answer, we put forward the following physical conjecture, which we would justify and explain in detail in the rest of this section.
Conjecture 2.
Variations in stand-alone subspace correspond to ‘bosonic excitations’ that can proliferate/condense in the given TNR. Variations in the MPO-injective subspace are the subset of these condensable ‘bosons’ that are trivial (belong to trivial superselection sector). Hence the variations in are the non-trivial condensable bosons. So such a variation results in topological boson condensation and causes a topological phase transition of the state.
By ‘excitation’ we mean any point-like variation to the ground state, or its TNR. It should be carefully noted that the word ‘boson’ here refers to any point like excitation (not necessary an irreducible excitation) that has trivial topological spin. For example, if is an anyon of the given model, then composite particle where and are sitting next to each other is included in this definition of boson. Of course it is a topologically trivial boson. Similarly, if we apply any local operation on the topological state, we would say that the resulting state contains a boson. Though, of course, it is again a topologically trivial boson.
Now we turn to the first part of the claim, which is basically the physical significance of stand-alone space
IV.1 Physical understanding of stand-alone space
As claimed, the physical significance of stand-alone space is that it contains proliferatable bosonic excitations.
IV.1.1 Proliferatable variations of a TNR
First we explain what we mean by ‘Proliferatable variations/excitations’. (We use the term ’variation’ for any mathematical variation to the ground state tensors. ‘Excitation’ should be used for a quasi-particle excitation. But in slight abuse of the nomenclature we would often use them interchangeably. It is justified as we are only working with the wave functions and not Hamiltonians.) Let’s say is the RG fixed point tensor of some topological ground state wave function . Let’s say we add a variation, and the resulting wave function is .
| (46) | |||||
where denotes the tensor network state similar to except has been replaced with at site . Similarly, denotes the tensor network state similar to except is replaced with at site and . Higher order terms can be understood in a similar manner. Physically, can be interpreted as ‘excitation’ (which may be trivial) sitting at site with probability . Similarly, can be interpreted as excitation sitting at sites and with probability . Higher order terms can be interpreted in a similar fashion. Though looks small compared to the weight of , one has to bear in mind there are such terms in the expansion, where is the number of sites. So after normalization they can have comparable weights.
When is in the stand-alone space then it can appear anywhere in the tensor network state, independent of each other, even at large scales. However when is outside of the stand-alone space, then it can at most appear next to other s. But then the distance between excitations is exponentially suppressed since each appears with an weight. So such excitations do not appear at large scale and would vanish under RG process. Tensors within the stand-alone space, on the other hand, can appear at any scale and would not vanish under RG process. So we can call the new wave function as a ‘proliferation/condensate of ’, since the variation/excitation proliferates and each site is in superposition of appearing and not appearing at all length scales. (We caution that we use the term ‘proliferation’ to denote the mathematical fact that the wave function is a superposition of a variation appearing everywhere. While the term ‘condensate’ in physics means something more specific. But, again, we would use these terms interchangeably. It is justified as we are not dealing with the Hamiltonians, rather looking at the changes in the wave functions as we vary the tensors. So the ‘condensation of variations’ doesn’t necessarily mean a phase transition. It just means a particular mathematical variations, which can be interpreted as an excitation, proliferates and the resulting wave function is a superposition of this variation appearing everywhere.)
A key point here is that and can be at arbitrary distance from each other but the contribution of this term in the superposition remains . Let’s compare this with how the ground state changes with respect to a perturbation on the Hamiltonian level. Let’s perturb the toric code Hamiltonian in (2) with perturbations on every link,
| (47) |
The ground state of this perturbed Hamiltonian is also a superposition of and terms like . But the weight that appears with is of the order of , that is, the separation between two particles is exponentially suppressed. So, in thermodynamic limit, these excitations disappear. But this is not the case with state in Eq. (46). That is why the state in Eq. (46) cannot be produced by infinitesimal small local perturbation of the parent Hamiltonian.
So we have argued that stand-alone space, by definition, is the space of variations that can condense. But how do we know they are ‘bosonic excitations’, that is, they have a trivial topological spin? We will show it now.
IV.1.2 Condensable excitations are ‘bosons’
Consider the tensor network state which has the fixed point tensor everywhere except at sites and , where has been replaced by stand-alone tensors . We denote this wave function as , as above. Topological spins of quasi-particles in topological models are calculated using the string-operators that create them. So we need to first define a string-operators that create these variations. The anyonic string operators in topological models have the property that they commute with the Hamiltonian everywhere except possibly at its ends. But we are working directly with the quantum wave function and are not really concerned with the underlying Hamiltonian, whose form can change going away from the RG fixed point. We see that we can define an appropriate string-operator for tensor network states without referring to a Hamiltonian. To do that, first notice that every tensor network state has underlying gauge symmetries at the virtual level. That is, if we apply operators and on the two contracting virtual legs, such that , the tensor network state doesn’t change (though the individual tensors may change). That is,
| (48) |
It means that if we apply a string of , on virtual levels along a path, the tensor network state would not change along the path but only at the ends. For example, on the double-line TNR we can create a stand-alone excitation in the following way,
| (49) |
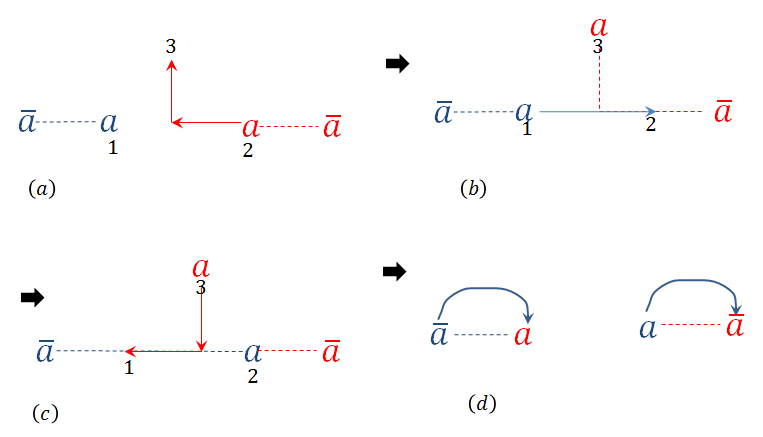
The and cancel each other on each plaquette as all the 6 virtual legs are contracted. We chose double-line tensor network for illustration but of course it can be done for any tensor network. So wave functions like can be created by such string operators. Note that since the tensor network didn’t change along the path, is still in the ground state along the path. So this string operator can only possibly create excitations at the ends, which is what we wanted. We will call such string operators gauge-string-operators to distinguish them from the usual string operators on the physical level. Note that gauge-string-operators can only create stand-alone variations/excitations, and they are deformabale on the ground state subspace, like the physical string operators. We know that physical string-operators might not be deformed through a site that has an anyonic excitation present. Gauge-string operators also may not be be deformed through excitations. For example, there may be another operator present at the virtual legs such that . But the interesting thing to note is that they can always be deformed through a stand-alone excitation. The reason for this is simple. A stand-alone tensor is surrounded by fixed point tensor . So if we consider a Wilson-loop of gauge-string operator around it, is still true, so and will simply cancel each other. So the Wilson-loop will simply disappear irrespective of what stand-alone excitation was there. So not only gauge-string operators create stand-alone excitations, they also always commute with the other stand-alone excitations. This suggests that all excitations in the stand-alone space have trivial mutual and self stastics. But to prove they are bosons, we need to do the topological spin calculation. Though again, using the same reasoning, it can readily be seen that the topological spin of stand-alone excitation is 1, as explained in Fig. 10.
We have determined that the variations in the stand-alone space are condensable bosons. So any such variation results in a wave function which is a condensate of the boson the variation corresponds to. But this alone does not necessarily cause a phase transition, because if the boson was topologically trivial, there should be not topological phase transition. Or, mathematically speaking, the stand-alone projector projects out variations that cannot proliferate, but it doesn’t project out those stable variations that can proliferate. For example, the double-line stand-alone projector does not project out variation though it is not unstable. So to find the unstable variations, we need an additional projector to project out condensable but stable variations. We will argue now MPO-injective subspace is precisely this projector.
To find out whether a virtual variation would cause the phase transition we need to first determine what this virtual variation corresponds to on the physical level. That is, we need to ‘lift’ the variation from the virtual level to the physical level. When we do that we discover that there are two kinds of variations: The first kind is where a local virtual variation is lifted to a local physical variation, and the second kind is where the local virtual variation is lifted to a non-local physical variation. We know that a local physical variation can only correspond to a topologically trivial boson since it can be removed by a local operation. This distinction between variations further decomposes the stand-alone into two subspaces: the MPO-injective space , which corresponds to the first kind of variation, and the unstable subspace , which corresponds to the second kind of variation. Let’s first focus on the first kind of variations.
IV.2 Physical understanding of MPO-injective subspace
As claimed above, the physical significance of MPO-injective subspace is that the variations in this subspace are lifted to local physical variations, which have to be topologically trivial bosons since they can be removed by a local operation. Hence the physical significance of MPO-injective subspace is that it contains all the topologically trivial excitations.
To understand it better, let us look at concrete examples of variations that are lifted to local physical variation. Consider a variation on the virtual leg of the fixed point single-line TNR. If we lift it to the physical level, what do we get? Since the virtual legs are just copies of the physical legs, we get
| (50) |
So virtual variation is lifted to a physical variation, which is local. According to our claim, it should be in the MPO-injective subspace. And indeed it is, since it respects the MPO symmetry of the single-line TNR, . Also note that a physical variation corresponds to a pair of particles sitting next to each other, not a single particle. It is a trivial excitation and can be removed by applying one operation on the state, so it matches our claim. Contrast this with the variation on the virtual level. Can we find any local physical operator such that
| (51) |
One can try and see that there is no such local operator for which this equation holds. (We will later show that can be lifted to the physical level, but it results in a non-local operator. )
A similar phenomena occurs in double-line TNR. The variation can be lifted to a local physical operator,
| (52) |
but a variation cannot be. (We will later show that can be lifted to the physical level, but it results in a non-local operator.) It is again consistent with the claim as variation respects the double-line MPO symmetry but variation breaks it. Note that variation on the physical level corresponds to a pair of particles sitting across a plaquette. It is a topologically trivial excitation and can be removed by an operation on the state. So again, this matches our claim.
Now we prove that these examples are no coincidence, and in fact any variation in the MPO-injective subspace is a local physical variation.
Let us repeat the definition of the MPO-injective subspace here for convenience. We SVD decomps the fixed point RG tensor as a matrix between virtual and physical legs
| (53) |
where are the singular values, and and are orthonormal vectors in the virtual and ground-state physical spaces respectively. Then the MPO-injective subspace is the virtual subspace spanned by vectors such that corresponding singular values . So the MPO projector is
| (54) |
A mathematically inclined reader would note that MPO-injective subspace is nothing but the virtual subspace which is isomorphic to the image of the tensor as a map from virtual to ground state physical space. That is, if we restrict the domain of the tensor to this subspace, then tensor is an injective map from the virtual to the physical space, and a bijective map from MPO-injective subspace to ground-state physical subspace. Since these spaces are isomorphic, any operator in MPO-injective subspace can be mapped to an operator in the ground-state physical space and vice-versa, and this mapping would be bijective (one-to-one) as well. Let us make it precise,
Lemma 1.
If is any operator on the virtual space completely supported on () then there exists an operator on the ground state physical space such that and vice-versa. That is, any variation in the subspace is equivalently a variation on the ground state physical space and vice-versa.
Proof.
Let us say an virtual operator is given which is completely supported on subspace . Define pseudo-inverse of as
| (55) |
It is a pseudo-inverse since
| (56) | |||||
| (57) |
where denotes projector on the ground-state physical subspace of the full physical space. is the projector onto the full physical space. Now define a physical operator as
| (58) |
then
| (59) |
The last equality follows from the assumption that is completely supported on MPO-injective subspace. Similarly, given physical operator on the ground-state physical space, define . So we have . And of course these maps are injective. So and have a one-to-one correspondence. ∎
With this lemma, we see why in general variations in the MPO-injective subspace are trivial excitations. They are nothing but a local variation on the physical level, which is a local physical operator and can be removed by another local operator. In fact notice that if is unitary (within the space ) then so is and vice-versa. Since all trivial excitations are obtained by local unitaries, or their linear combinations, we conclude that MPO-injective subspace should contain all trivial virtual excitations as well.
This completes the study of first kind of variations (those that are lifted to local physical variations) mentioned above. Now we study the second kind of variations.
IV.3 Physical understanding of subspace
The physical significance of subspace is that it contains the second kind of variations: the virtual variations that are lifted to a non-local physical operator. So these variations cannot be removed by a local physical operation on the state, and hence represent a topologically non-trivial excitation. And this excitation has to be a boson, as all excitations in stand-alone space are. So it means that the physical significance of space is that it contains condensable excitations that are topologically non-trivial bosons, and that’s why these variations cause a topological phase transition.
Let us first look at some concrete examples to understand this phenomena. We saw how a virtual variation on the single-line TNR couldn’t be lifted to a local physical variation. But, the question is, can it be lifted to a non-local physical variation? The answer is, yes. To see it, first note that although a single variation cannot be lifted locally, two variations can be. That is, the fixed point single-line tensor satisfies
| (60) |
And also, we have the usual guage symmetry
| (61) |
Using these two relations, we see that a single virtual variation on can be moved to another tensor on the same sublattice, and this transfer produces an operation on the physical level,
| (62) |
In the first equality, Eq. (61) is used while in the second equality Eq. (60) is used. We see that the variation moved from site 1 to site 3 while leaving operator along the path (on site 2). We can repeat this process and move to the next tensor and so on. After is moved from site 1 to there will be an -string operator applied on the physical level along the path. Finally, if there is already an variation present at site , the two will cancel and we will be left with an -string operator only,
| (63) |
Of course the particular path between site 1 and chosen is completely arbitrary. We can choose any path between them as we like. So we have successfully shown that though a single variation cannot be completely lifted to the physical level, two such variations sitting far apart can be, and they are lifted to a non-local physical operator between them. It implies that a variation on the single-line TNR cannot be removed locally on a physical level. Only two of them can be removed by applying a non-local operator between them. In fact, it is easy to recognize what this excitation is. Since -string operators correspond to creation or annihilation of -particles in the toric code, it is clear that the virtual variation actually is an particle excitation. It is topologically non-trivial, which is in line with our claim. Condensation of variations is actually the condensation of particles, and that is why it leads to topologically phase transition.
A similar analysis can be carried out for the variation in the double-line tensor. We noted that it cannot be lifted to a local physical operator. But two operators can be lifted to a non-local physical operator,
| (64) |
where in the first equality, the following relation (similar to Eq. (61)) has been used,
| (65) |
And in the second equality, the following property of the fixed point double-line tensor is used.
| (66) |
So we see that two variations on the virtual level, sitting far apart cannot be removed by local operations on the physical level. They can only be removed by a non-local operator, the -string operator. This suggests that the variation is a topologically non-trivial excitation. Indeed, it is easy to see that it is nothing but the particle excitation, since -string operator creates and annihilates -particles. This is in line with all our claims: variation is in the space; it cannot be removed locally, and that it is a topological boson.
IV.4 Non-trivial gauge string-operators: Zero-string operators
It may look a little puzzling that a local virtual operator in can create a non-trivial physical excitation. We analyzed what these variations correspond to by lifting them up to the physical level. To understand the phenomena better we can ask the opposite question: what happens when we ’bring down’ a non-trivial quasi-particle excitation on the physical level to the virtual level? Since such an excitation is created by a physical string-operator, the equivalent question is, what happens to string-operators of the model when we bring them down to the virtual level? We can look at the specific examples considered above. For example, if we look at Eq. (63) in the opposite way, we see that the physical -string operator, which creates -particles, becomes a gauge-string operator on the virtual level, which subsequently creates a variation in the space. Contrast this with -string operator, that creates -particles. This operator does not map to gauge-string operator,
| (67) |
Similarly, Eq. (64) shows that that the physical -string operator, which creates -particles, becomes a gauge-string operator on the virtual level. So we see that if a physical anyonic string operator maps to a gauge-string operator on the virtual level, it creates an excitation in the space. This property of the tensor network state in general is the reason why a local virtual variation can actually correspond to non-local variation on the physical level. In other words, certain gauge-string operators are non-trivial because they come from a non-trivial string operator on the physical level. We would call such physical string operators that map to gauge-string operator on the virtual level a zero-string operator. The reason behind this terminology will become clearer in the next chapter. So we conclude that the -particle operator is the zero-string operator of the double-line TNR, while the -particle string operator is the zero-string operator of the single-line TNR.
Since variations in the unstable space are created by zero-string operators, it implies that, if, in a given TNR, none of the physical string operators map to a gauge-string operator then it will have no variation in . In that case, we would simply have . Such a TNR will have no instabilities.
Before going to the physical explanation of instabilities, we would like to mention that there is one more way of decomposing the stand-alone space in trivial and non-trivial excitations: using Wilson-loops of anyonic string-operators. We can use these operators to detect whether a nontrivial excitation is sitting at a site, hence can potentially differentiate between and . This has been explored in appendix A for readers who are interested in this perspective.
IV.5 Physical reason of instability: topological boson condensation
Now we put together the physical understanding of all the relevant subspaces ( and ) to make the coherent picture of why variations in the subspace are unstable, and, in particular, explain the numerical results shown in Fig. 4 and Fig. 6. The general explanation has already been stated in form of conjecture 2 but we repeat it again informally going through all possible variations one by one.
-
•
The variations on the physical indices are of course not stable because they are topologically trivial and can be removed with local operations.
-
•
Variations outside the stand-alone space, are not unstable because they cannot proliferate.
-
•
Every variation inside is ‘bosonic’ and does proliferate and the varied wave function is a condensate of that ‘boson’. But when the variations is inside , it was a topologically trivial boson and hence does not cause a topological phase transition. Or, equivalently, every variation inside MPO-injective subspace was nothing but a variation on the physical level hence stable.
-
•
Finally, when the variation was inside stand-alone, but outside MPO-injective subspace then it can condense and is a topologically non-trivial boson. Hence it causes a topological phase transition, resulting in a TNR instability.
Now we explain this boson condensation specifically for the single-line and double-line TNR considering specific variation.
IV.5.1 -particle condensation in single-line TNR
To guide the discussion, consider two illustrative variations to single-line TNR as before
| (68) |
-
•
The variation exemplifies variations that can condense but correspond to a local physical variation, hence are trivial/elementary excitations. Such variations result in a proliferation of elementary excitation which does not cause a topological phase transition.
-
•
The variation exemplifies variations that can condense but do not correspond to local physical variations. In fact, such variations correspond to -particle excitation. Hence such variation results in an -particle condensation and destroys the topological order of the tensor network state.
IV.5.2 -particle condensation in double-line TNR
Let’s consider the different variations in double-line TNR as before
| (69) |
-
1.
Variations in (a) and (c) exemplify variations that break the stand-alone symmetry , hence they cannot proliferate and, therefore, are stable.
-
2.
Variation in (b) exemplifies variations that can stand alone, so can proliferate. But they break the MPO symmetry, so correspond to a non-trivial boson. In fact it corresponds to an -particle excitation. So this variations causes particle condensation and results in the loss of topological order.
-
3.
Finally, variation in (d) exemplifies variations that can proliferate. But they also are inside the MPO-injective subspace, so correspond to trivial/elementary excitations. So their proliferation does not cause a topological phase transition.
V Implications for the simulation of phase transitions
Projected Entangled Pair States (PEPS), one type of Tensor Network States (TNS), are often used as ansatz for different numerical simulations of gapped lattice topological models. In particular, TNS can be used to simulate phase transitions between different topological phasesGu et al. (2008). The fixed point Hamiltonian is perturbed with a local Hamiltonian and the perturbation strength, is increased slowly. At some finite value of the gap closes and the system goes through a phase transition. For many perturbations, this phase transition consists of boson condensation. For example, for the toric code Hamiltonian Eq. (2), two kinds of perturbations can be added
| (70) | |||
| (71) |
Let’s first discuss the first kind of perturbation. In the first Hamiltonian, we keep and study the ground state as the relative values of and change. At the ground state is simply the fixed point toric code state given in Eq. (3). That is, it is an equal weight superposition of all closed string configuration. At , the state is the vacuum state, that is, all spins are 0. These two states are topologically different, hence there must be a phase transition as we change from 0 to . This phase transition can be understood as a condensation of particles. Recall that corresponds to no particle and corresponds to an particle excitation at a plaquette , where is the plaquette term of the toric code Hamiltonian. For ground state we have , while for ground state we have . It indicates that as is increased, particles proliferate and at phase transition point, the system goes through a boson ( particle) condensation and the ground state becomes a trivial state. Boson condensation phase transitions are known to be second order phase transitions. That is, ground state energy and its first order derivative as a function of are smooth functions, but its second order derivative is discontinuous at the phase transition point.
It was shown by Gu et al. (2008) that an attempt to numerically simulate this phase transition point with single-line tensor network state ansatz gives a transition that is wrong both quantitatively and qualitatively. It gives a wrong critical point value of , and it gives a first order phase transition, not a second order one. But with double-line tensor network state ansatz, it gives the correct second order phase transition with correct critical point.
This difference can be easily understood in light of our discussion on single-line and double-line TNR of toric code state. As we showed, double-line TNR is capable of condensing particles while single-line TNR is not. That is why double-line TNR is suitable for simulating a phase transition that involves particle condensation.
A similar analysis can be done for the second type of perturbation. We set and change relative value of and . For the ground state is the toric code ground state in Eq. (3), and for the state is trivial state with all qubits aligned in +x direction. Here the phase transition involves particle condensation which is again a second order phase transition. Hence, to simulate this phase transition, one should use single-line TNS ansatz and not the double-line TNS ansatz.
This is one of the important point of understanding the unstable direction of variations that a particular TNR possesses. To simulate a boson condensation phase transition, one should choose the TNR that is capable of condensing that particular boson of the model.
Of course, there is also a flip side to this. If one is interested in determining the topological order of a particular TNR by calculating the topological entanglement entropy, one should make sure to keep out of the unstable space, , for numerical stability. A small numerical variation in this space will change the state globally and result in wrong results. For example, in calculations involving Tensor Entanglement Renormalization Group (TERG) Gu et al. (2008) and Tensor Network Renormalization (TNR 111not to be confused with TNR that we use for referring to tensor network representation.) Evenbly and Vidal (2015) steps, we should project the resulting tensor after every RG step back to the stable space, (), or naturally occurring numerical errors might gain a component in space and change the topological order of the state radically.
Now we will apply what we learned from the toric code example to analyze the TNR of another closely related model, the double semion model.
VI Double-semion
Double-semion model can be understood as a ‘twisted’ quantum double modelFreedman et al. (2004); Levin and Wen (2006). Its Hamiltonian is almost the same as that of toric code, except for the phase factor associated to the plaquette term
| (72) |
where ‘legs of ’ refers to the six legs attached to a plaquette. Its ground state is
| (73) |
where again refers to string configurations on the hexagonal lattice. denotes the number of loops in a given string configuration. The ground state, like that of toric code, is again a superposition of all closed string configurations. But it has a phase factor of which is for even number of loops and for odd number of loops. It has 3 quasi-particle excitations: a semion, an anti-semion, and a self-boson. So, unlike the toric code, it has only one boson. There is a known double-line TNR of this state Gu et al. (2009); Buerschaper et al. (2009), , with the same structure as that of toric code. So,
| (74) |
But now the values are
| (75) |
Clearly, it has the same symmetry, as the toric code double-line TNR. That is, satisfies
| (76) |
But it does not have the exact symmetry as that of toric code double-line TNR. By looking at the tensor values, it can be seen that it has the with an additional phase factor between virtual legs,
| (77) |
where if the virtual legs on the two sides of it take different values (that is, there is a domain wall) and otherwise. So has symmetry of the form where is the number of domain walls between and . That is,
| (78) |
To apply our conjecture we first need to calculate the stand-alone and MPO-injective subspaces of . The double tensor is,
| (79) |
Comparing it with the toric code double tensor in Eq. (25), we can immediately guess that the stand-alone projector is given by
| (80) |
which is the same as that of toric code. And the MPO projector is,
| (81) |
So we see that the symmetries identified in Eq. (76) are actually the stand-alone symmetries, and the symmetry identified in Eq. (77) is actually the MPO symmetry. With this information, our mathematical conjecture predicts:
-
1.
If the variations breaks the symmetries, then it is stable.
-
2.
If the variations respects all symmetries then there are two subscases
-
(a)
If it also respects the symmetry then it is stable.
-
(b)
If it breaks the symmetry then it is stable.
-
(a)
We test these predictions numerically. The results are shown in Fig. 11. We conclude that the conjecture predicts the numerical observation correctly.
What about the physical conjecture? Is it compatible with the numerical observation? The answer is, yes. the double-semion model has one boson whose string operator is the -string operator, the same as that of the -particle in toric code. Since both also have the same stand-alone space, it means bringing down this string operator to the virtual level would again give us a gauge-string operator. Hence the string-operator corresponding to the boson in the double-semion model is a zero-strong operator, which implies that the variations in the stand-alone space corresponds to this boson. So the instability we see is due to the condensation of this topological boson. Another way to see it is to notice that the MPO symmetry in Eq. (77) actually comes from the Wilson loop operator corresponding to semion (or anti-semion). So variations that break it actually signify the presence of the boson.
Comparing double-line TNR of toric code and double-semion
So we see that the space for double-semion is 4-dimensional space spanned by basis
| (82) |
This looks exactly similar to the basis in double-line toric code in Eq. (45), which might lead one to believe that they both are unstable for similar variations. But one has to carefully note that the tensor for both models are different, so the basis shown in Eq. (45) and in Eq. (82) are actually different. To illustrate this consider the following variation:
| (83) |
This variation is in stand-alone space of both toric code and double-semion, but it respects MPO symmetry of the toric code but violates the MPO symmetry of the double-semion. Indeed this variation causes phase transition in double-semion but not toric code. This variation cannot be lifted to the physical level on the double-semion tensor like it did for toric code (Eq. (52)). But one can readily see that this variation is not spanned by the basis in Eq. (82). And the reason for this is that this variation has components both in the MPO-injective subspace and the unstable subspace, which can be seen by applying the projector of the two spaces. We find that and . This examples reminds us that for a variation to be unstable, all it needs is to have a non-zero component in the unstable space. So it should not be thought that only variations spanned by the unstable basis are unstable.
VII General String-net Models
The models discussed so far, the toric code model and the double semion model, are particular examples of a general class of 2D topological models known as string-net models Levin and Wen (2006). Also, the TNR discussed so far (single-line and double-line) are reduced versions of the a general triple-line TNR of the string-net statesGu et al. (2009); Buerschaper et al. (2009).
A string-net construction defines a topological model on a honeycomb lattice for any arbitrary unitary tensor fusion category Kitaev (2003); Levin and Wen (2006). The local Hilbert space has spins sitting on the edges. These spins can take values called string-types. corresponds to the vacuum state. In general strings have orientation and for each string-type we have a unique strng-type with opposite orientation. If then the string is called ‘unoriented’. In this paper we would assume all strings are unoriented for simplicity but we believe our results are easily generalizable to oriented links. A branching rule defines what string-types are allowed to meet at a vertex. An -symbol guides how the strings fuse with each other. The -symbol comes from the unitary tensor category data and satisfies the so called pentagon equations. A local commuting Hamiltonian is defined, , where and denote the vertices and plaquettes of the honeycomb lattice. The vertex term projects onto the space allowed by the branching rule. The plaquette term acts by creating loops of -type strings which subsequently fuse with the existing string. As for any local commuting Hamiltonian, the ground state can be obtained by applying the projector on the vacuum state. A brief review of the string-net models has been given in the Appendix B. Readers can refer to the original papers for more details on the subject Levin and Wen (2006); Gu et al. (2009); Buerschaper et al. (2009); Şahinoğlu et al. (2014).
VII.1 Triple-line TNR of RG fixed point string-net state
As shown by Gu et al. (2009); Buerschaper et al. (2009), RG fixed point string-net states described above are known to have a triple-line TNR. We will only briefly discuss the relevant details here. A short derivation of the triple-line TNR is given in the Appendix C. An interested reader may refer to the original papers Levin and Wen (2005); Gu et al. (2009); Buerschaper et al. (2009) for more details.
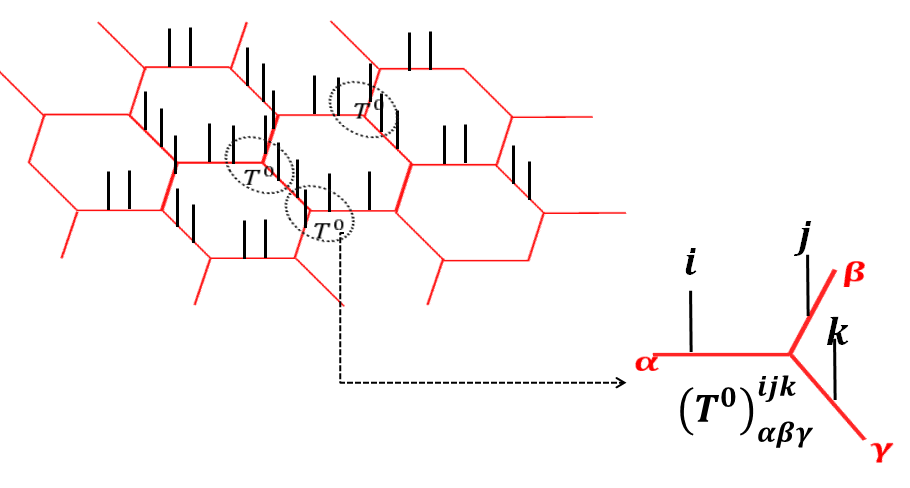
A general triple-line Tensor is represented diagrammatically as:
| (84) |
A string-net fixed point state has a triple line TNR with components given by
| (85) |
So it would be represented diagrammatically as:
| (86) |
Before we discuss the properties of the triple-line TNR of the general string-net models, we would like to mention that double-line TNR and single-line TNR are actually reduced versions of the triple-line TNR, and as such, many results about the triple-line TNR apply to double-line and single-line as well. We can discard some of the legs of the triple-line tensor if fewer legs are required to encode the necessary information. For example, for abelian models, the middle leg of the triple-line tensor is redundant; it always assumes value which is a product (fusion) of the two legs on either side of it. That’s why for abelian models, double-line tensors suffice and the middle-leg can be discarded. Non-abelian models, such as the double-Fibonacci model we will study in section VIII, the middle-leg does carry essential information and cannot discarded. So one cannot have a double-line TNR of non-abelian models. Furthermore, if the ground state of a model can be written as an equal superposition of states allowed by branching rules then the ground state admits a single-line TNR. For example, toric code ground state is an equal superposition of all closes string configurations, and hence admits a single-line TNR. In fact, any quantum double model with an abelian gauge group can have a single-line TNR. The double-semion model, on the other hand, is not an equal superposition of states allowed by the branching rules (it has a phase factor ), and hence it cannot admit a single-line TNR.
To apply the conjecture to the triple-line TNR of general string-net model, we now first calculate its MPO-injective and stand-alone subspaces. We will do so in the next two sections.
VII.2 Stand-alone space of triple-line TNR string-net
We find that the stand-alone space of the triple-line TNR is given by the following theorem:
Theorem 1.
The stand alone space, , of the triple-line string net TNR is spanned by the orthonormal vectors
| (87) |
where is the branching rule of the string-net model. label the middle legs, and label the plaquette legs.
The proof of this result is rather involved and is given in Appendix D. These basis vectors can be represented as string-configurations,
| (88) |
So we get,
| (89) |
VII.3 MPO-injective subspace of String-net triple-line TNR
we will use definition 2 to find the MPO-injective subspace of triple-line TNR. Using the triple-line TNR of string-net states given in Eq. (VII.1), the virtual density matrix is found to be
| (90) | |||||
Clearly, this density matrix can simply be written as
| (91) | |||||
| (92) | |||||
So has a diagonal form in terms of vectors . To get the projector on to its support space,we simply need to use the unit vectos , where is the norm of vector . So the string-net MPO projector is
| (93) |
Note that if . It means that projects on to the physical states allowed by the branching rules, and
| (94) |
Comparing Eq. (89) with Eq. (94), we can see that . So according to our conjecture, there must always be unstable directions of variations in the triple-line TNR of any string-net model! Indeed, we give examples of such unstable directions and will prove in section F that triple-line TNR of string-net always have instabilities.
VII.4 Tensors in the unstable space
We have determined both the stand-alone space, and the MPO-injective space . space is spanned by vectors,
| (95) |
And the MPO-injective space space is spanned by , where
| (96) |
The tensors supported on are precisely the tensors that cause instability. To determine the orthogonal basis of this space we simply need to find vectors orthogonal to which are within the stand-alone space. First note that space decomposes in orthogonal subspaces where the subspace is spanned by , that is, for which is non-zero. space can be decomposed into two subspaces,
-
1.
: This consists of all the string-configurations in Fig. 88 for which . They are obviously orthogonal to all since if . Since these vectors violate the vertex term of the Hamiltonian we will refer to them as ‘vertex variations’.
-
2.
: This is the subspace spanned by string configurations for which . We need to find other vectors in that are orthogonal to . where if and otherwise. Note that since are orthogonal for different values of , we just need to find vectors in individual subspaces. To find these we will use the orthogonality of (135)
(97) And the fact that matrices defined by can be simultaneously diagonalized . Let’s say is its qth such simultaneous eigenvector. As discussed in Appendix B.1, , that is, the vector formed by quantum dimensions is an eigenvector to . These vectors are orthogonal, , which also implies that . Now we are ready to write down the vectors spanning .
Consider vectors
| (98) |
where superscript indicates that the th eigenvector is used on leg . Using the orthogonality relation, we get
| (99) | |||||
| (100) | |||||
| (101) | |||||
| (102) |
So we see that the vector is orthogonal to if . Since takes non-zero values and it can be put on leg or we seem to have such vectors. However not all of them will be independent, but they span the full vector space . Since these kinds of variations change the plaquette leg factors, hence violating the plaquette term, we will refer to these variations as ‘plaquette variations’.
VII.5 Instability of triple-line TNR
Theorem 2.
Let be the fixed point triple-line TNR of a string net ground state. There exist tensors in the space (that is,) that for the variation , .
The proof of this theorem is rather involved and has been included in the appendx F.
With this we have concluded the analysis of general string-net mdodels and their triple-line TNR. Now we turn to some concrete examples to understand how the conjecture in III.3 explains the instabilities in string-nets.
VII.6 Examples: Triple-line TNR of the toric code and double semion states
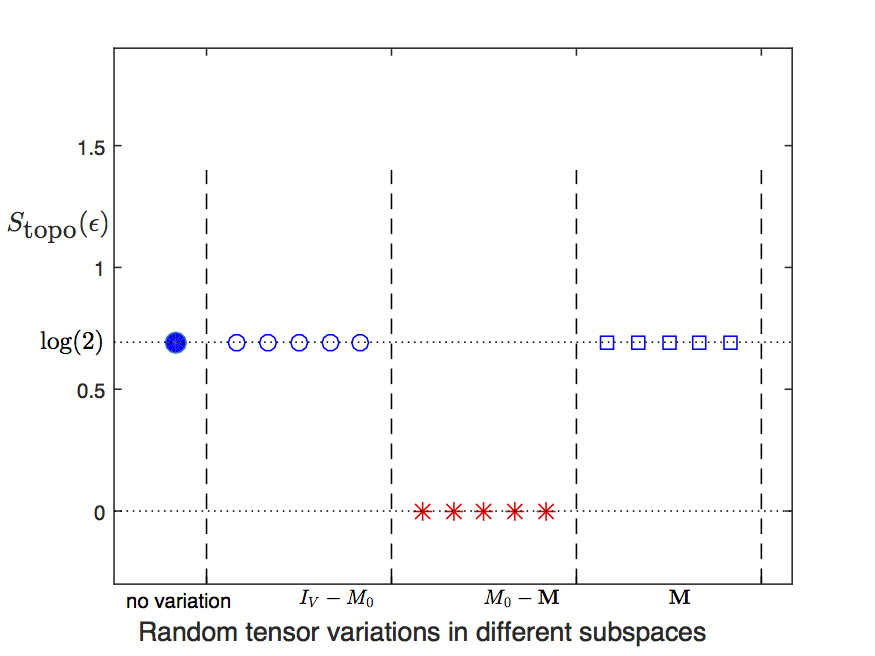
let’s first examine how models covered in the previous chapter, toric code and double semion, fit into triple-line TNR. One can get the triple-line TNR for them by plugging in the relevant string-net data into Eq. (VII.1). We will apply the results about general-string net models developed in previous sections to the two cases.
Toric code string-net data is,
The triple-line TNR of toric code can be built by plugging in this data into the general expression in Eq. (VII.1). This tensor has 9 virtual indices, each of which takes 2 values. So the full virtual space is dimensional. The dimension of the stand-alone space is
| (104) |
and the dimension of the MPO-injective subspace is
| (105) |
These imply that and . So we reach the conclusion that out of 512 possible variations, 504 are stable since they are outside the stand-alone space. In the remaining 8 dimensional subspace, perturbations in a 4 dimensional subspace are in stable whereas the ones in the other 4 dimensional subspace are unstable. Using Fig. 9, the classification of all variations can be represented as follows
| (106) |
The numerical calculation supporting this conclusion is shown in Fig. 12. Also note that all unstable variations are flux variations, that is, it happens through the condensation of -particle. It is not possible for the -particle to condense in this way.
For the double semion model, the string-net data is
The triple-line TNR of the double semion model can be built by plugging in this data into the general expression in Eq. (VII.1). This tensor has 9 virtual indices, each of which takes 2 values. So the full virtual space is dimensional. Dimension of the stand-alone space is
| (108) |
and the dimension of the MPO-injective subspace is
| (109) |
These imply that and . So we reach the conclusion that out of 512 possible variations, 504 are stable since they are outside the stand-alone space. In the remaining 8, 4 are in stable and 4 are unstable. The numerical calculation supporting this conclusion is shown in Fig. 13.
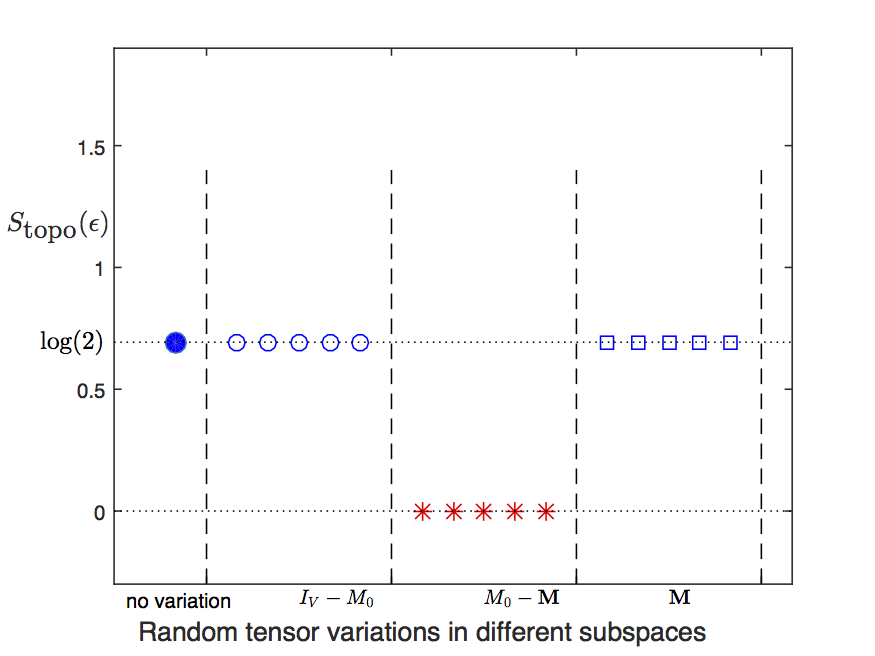
Also note that all unstable variations are plaquette variations, that is, it happens through condensation of the boson of the double-semion model. The classification of all variations is the same as that for toric code shown in (106) above.
Now we are ready to discuss a concrete example of the string-net triple line TNR and its instabilities. We choose double-Fibonacci model for two main reasons: 1- Unlike the toric code and the double-semion model, it is a non-abelian model, so the general triple-line TNR, as far as we know, cannot be reduced to a double-line or single-line TNR. So it serves as a good example to test our conjecture for the general string-net TNR. 2- Unlike toric code and double-semion, its bosonic string operator is not a zero string operator, so it does not disappear along the path.
VIII A non-abelian example: Double-Fibonacci Model
Toric code and the double-semion models are abelian models. Now we will discuss a non-abelian model: the double-Fibonacci model. The Ground state of non-abelian string net models cannot be described by a single-line or the double-line TNR; it only accepts a triple line TNR (tensor in Eq. (VII.1)). Let’s first describe the model briefly. The data for this can be found in section IV.B of Levin and Wen (2005). There is one type of string (). Its quantum dimension is, . Its branching rules are,
| (110) | ||||
| (111) |
The branching rules tells us that one string is allowed to branch into two, unlike the abelian models we have studied until now. First, let’s apply our conjecture to find out how many unstable directions we should expect. The triple-line TNR of the Fibonacci model can be built by plugging in this data into the general expression in Eq. (VII.1). This tensor has 9 virtual indices, each of which takes 2 values. So the full virtual space is dimensional. The dimension of the stand-alone space is
| (112) |
which is bigger than that of the toric code and the double-semion models. The dimension of the MPO-injective subspace is
| (113) |
which implies that and . So we reach the conclusion that out of 512 possible (virtual) variations, 494 are stable since they are outside the stand-alone space. In the remaining 18, 5 are in stable as they are in the MPO-injective subspace and remaining 13 are unstable. The classification of all variations can be represented pictorially as follows:
| (114) |
The numerical calculation supporting this conclusion is shown in Fig. 14.
Comparing it to the toric code and the double-semion models we see that the Fibonacci triple-line TNR is significantly more unstable. Another difference is that the stand-alone space does have vertex unstable variations in addition to plaquette ones. Out of 13 unstable variations in the following 3 are vertex variations and the rest 10 are plaquette variations:
| (115) | |||||
That is, the following 3 tensor components are allowed in the stand-alone space but not in the physical space:
| (116) |
Since these 3 vectors are not in the MPO-injective subspace .
To understand the physics behind this, we need to look at the quasi-particles of the Fibonacci model. There are 3 quasi-particles excitations: , and . The and matrices of the particles are as follows:
| (117) |
It is best seen as two layers of Fibonacci model with opposite chiralities. and are particles in the two respective layers. They have non-trivial self statistics. But, because they are in different layers, they have a trivial statistics with one another. And the boson, is the composition of the Fibonacci particles in the two layers. The string operator for these quasi-particles are given in equation (51) of Levin and Wen (2006). We are most interested in the boson of the model, so let us write its string operator ( matrices) explicitly:
| (118) |
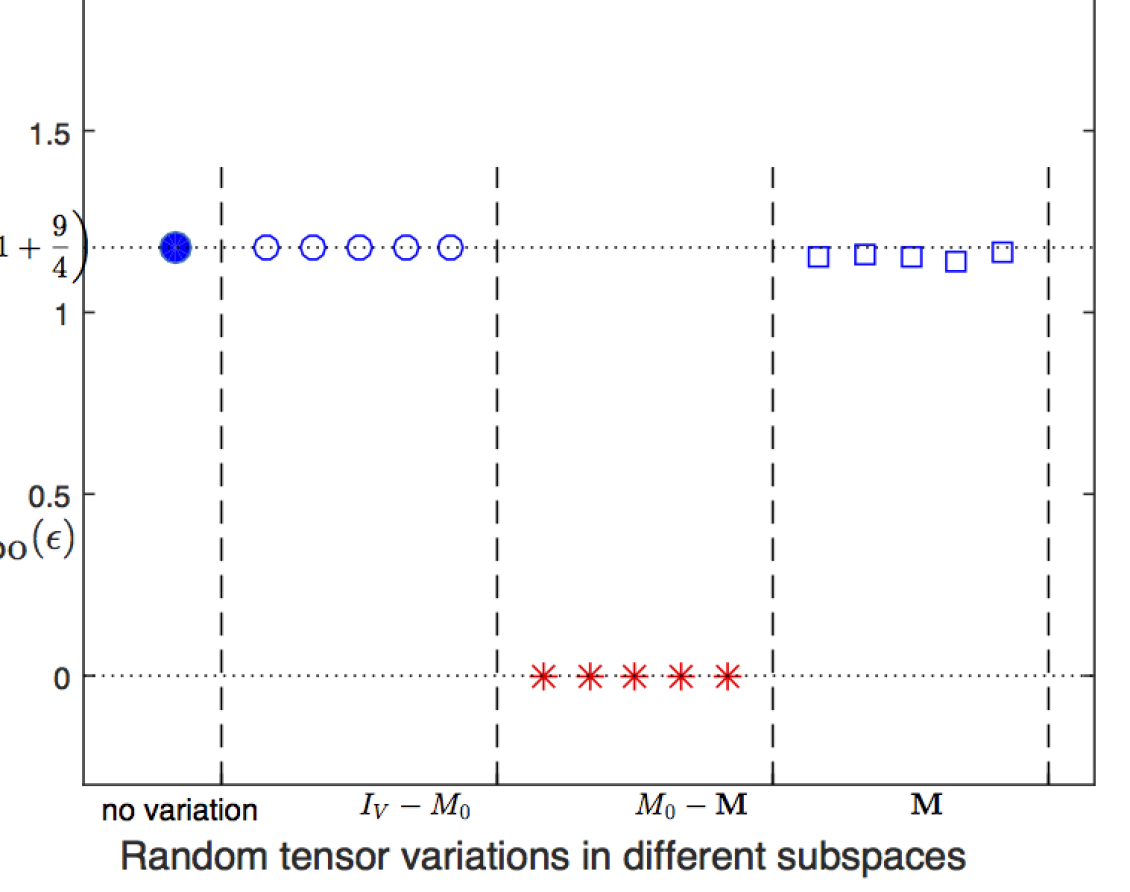
One can see that it is not a simple-string operator: when applied on the vacuum, it creates both 0-type and 1-type strings. So we see that the double-Fibonacci model is different from the above two examples in one crucial aspect: the boson string operators in the toric code and the double-semion models were zero-string operators for the given TNRs. That is, the string operator ‘disappeared’ along the path (Figs. 63, 64), not changing tensors along the path. This is why a single variations standing alone could be thought of as an operator sitting at the ends of an invisible string operator. But the same is not true for the double-Fibonacci model. The string operator corresponding to the boson does not disappear in the middle.
Because the bosons don’t have a zero string operator, one might conclude that there would be no unstable directions as bosons cannot condense. However, numerical calculations find that there actually are unstable directions. How can we understand that?
We look at how the boson string-operator changes the tensors along the path. In Fig. 15, one can see that a wave function corresponding to the boson sitting at two places, and , is actually a superposition of many wave functions:
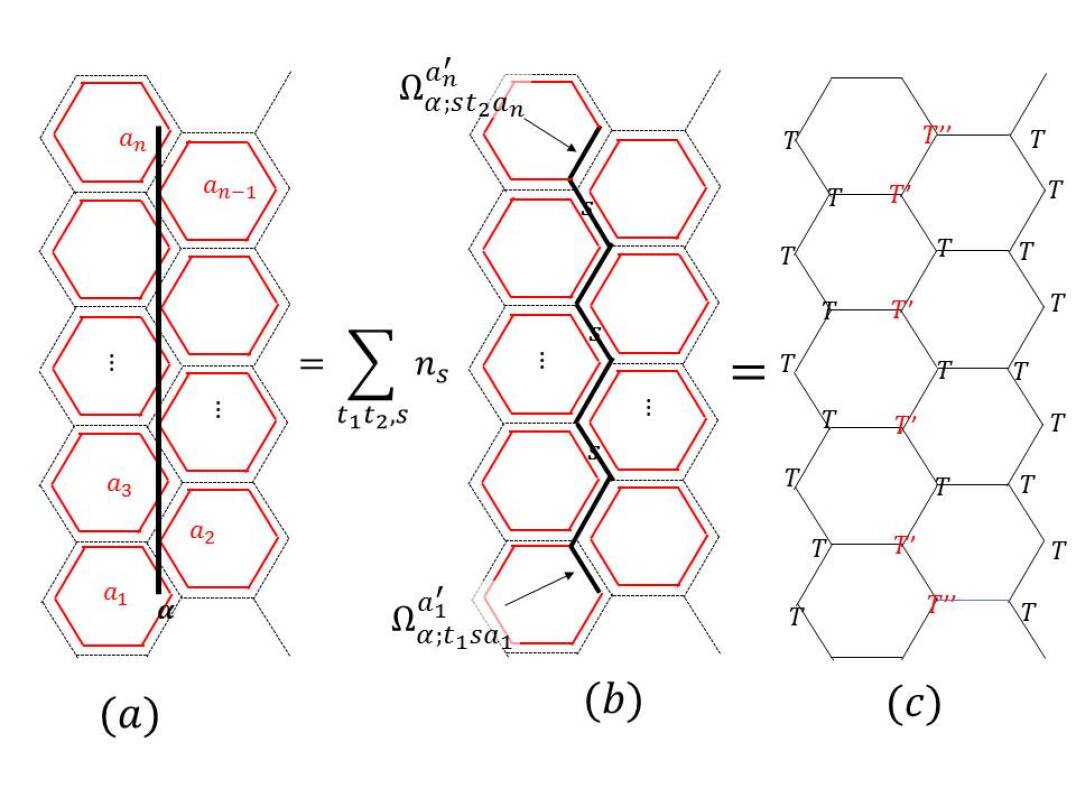
where the operator is explained in Fig. 15. is equivalent to applying and on the loops at the ends of the string operator, and creating a type string along the path. Fusing the loops with each other and with the string along path gives the final state. The important thing to note is that, though a TNR of the full state involves changing tensors along the path, the TNR of , have tensors changed only on the ends. Simply putting, the zero-string component of the string operator does not change the tensors in the middle, as expected. So the boson state has a finite overlap with the state where tensors are changed only at the ends. So when the variations corresponding to the ends of this zero-string component of the boson operator proliferate, it effectively condenses the bosons, as they have finite overlap with the resulting state.
So in conclusion, we see that although the boson string operator is not a zero-string operator, that is, it does not disappear in the middle for the triple-line TNR, its zero-string component still causes an instability because the resulting state has a finite overlap with the boson-condensed state.
Now we have looked through important examples of string-net TNR and their instabilities. Finally, we will give a proof of instability in the generic case.
IX Conclusions and Discussion
In this paper, we try to answer the following question: are the tensor network representation of string-net states stable? That is, if we start from the tensor network representation of a string-net state and add arbitrarily small variations to the local tensor, does the topological order of the represented state always remain the same? This is an important question because if the answer is no, then the task of determining topological order of a tensor network state may be numerically ‘ill-posed’. That is, arbitrarily small numerical error in the process may change our conclusion in a qualitative way. Previous workChen et al. (2010) has shown that this is indeed the case for the single line representation of the toric code state. While this may seem to seriously limit the applicability of tensor network methods to the study of the toric code type topological order, Ref.Chen et al., 2010 also identified an inner symmetry by preserving which the numerical task becomes ‘well-posed’ again.
We want to know if similar problems happen for general string-net states. In particular, we asked
-
1.
Does the tensor network representation of other string-net states also have unstable directions of variation?
-
2.
If so, can they be avoided by preserving certain symmetries in the tensor?
-
3.
What is the physical reason behind such instabilities and their prevention?
We found that
-
1.
All string-net tensors have unstable directions of variation.
- 2.
-
3.
The physical reason for the instability is that ‘stand-alone’ variations which violate these symmetries induce condensation of bosonic quasi-particles and hence destroys (totally or partially) the topological order.
We demonstrated the case explicitly for the tensor network representation of the toric code (single, double, triple line), the double semion, and the double Fibonacci model, by calculating the topological entanglement entropy of tensors with random variations. We observe that MPO symmetry preserving variations keep invariant and MPO symmetry breaking variations lower (to zero). While for general string-net models, we cannot prove the above claim analytically, we are able to show that 1. the fixed point tensor of any string-net has unstable directions (which break the MPO symmetry) 2. MPO breaking variations induce the condensation of bosons in the state, and therefore destroy (at least partially) the topological order. Moreover, we point out that to correctly simulate the local properties of a phase transition induced by such boson condensation, these MPO breaking variations must be allowed in the variational calculation; otherwise, one may reach the wrong conclusion about the phase transition (e.g. regarding the order of the transition). This has been observed in the case of toric code in Ref.Gu et al., 2008.
Given this result, we can ask, how to properly design the tensor network algorithm so that it can correctly simulate topological phases and phase transitions? In particular, if we want to determine whether the ground state of some Hamiltonian has topological order by calculating topological entanglement entropy in the thermodynamic limit, we need to use a variational ansatz with the proper MPO symmetry. How to do that in an efficient and unbiased way is an interesting open question.
On the other hand, if we want to properly simulate a topological phase transition induced by boson condensation, we need to put in the proper variational parameter. However, as we have seen in the case of the toric code, different representations (single line, double line, triple line) contain parameters corresponding to the condensation of different bosons ( or ). In fact, none of the representations contain parameters which correspond to the condensation of both bosons. Therefore, it is not possible to use any of them to correctly obtain the full phase diagram. It implies that, if we want to study a topological phase transition whose nature is unknown, we need to try different ansätze. How to do that in an efficient and unbiased way is again an interesting open problem. We leave these problems to future study.
Acknowledgements.
Sujeet Shukla would like to thank Pinaky Bhattacharyya for help with the numerical calculations. X.C. is supported by the Caltech Institute for Quantum Information and Matter and the Walter Burke Institute for Theoretical Physics.Appendix A Decomposing stand-alone space using Wilson-loops: MPO symmetries
In sections IV.2 and IV.3, we argued how the stand alone space decomposes further into two subspaces, and on the basis whether a stand-alone variation can be lifted to the physical level locally or non-locally. In doing so we used the fact about topological models: anyonic excitation cannot be removed by a local operation but an elementary excitation can be.
There is another way to distinguish between trivial and non-trivial excitations. Consider the tensor network state made out of , except at site , has been replaces by some stand-alone tensor . Now we want to find out whether this variation/excitation is a topologically non-trivial excitation. In topological models the way to detect the presence of anyon is by measuring Wilson-loop operators around it. We will do the same here, but on the virtual level. Doing so will reveal another interpretation of the MPO subspace/symmetries: these symmetries come from Wilson-loops of anyons of the model.
Consider the following physical process. We generate an anyon , anti-anyon pair, move around the site where is sitting and finally fuse it with . Mathematically, this is equivalent to applying a Wilson loop operator corresponding to particle . represents the closed curve/loop around the site. If there was another anyonic excitation present at and if and have a non-trivial braiding statistics with each other, then this process produces a phase factor. Hence application of , where is a loop around a site can be used to detect if there is a topologically non-trivial excitation present at the site. Of course are symmetries of the ground state for all anyons . But more than that, it would be a symmetry of any state with a trivial local excitation sitting at .
is an operator on the physical degrees of freedom, which induces an operator, , on the virtual degrees of freedom. is guaranteed to have a representation on the virtual level because is an operator supported on the ground-state physical space of local tensors, and as we noted in Lemma 1, such an operator can be mapped to an operator on the virtual level. Hence, just as is a symmetry on the physical level, should be a symmetry of the ground state tensor on the virtual level. But, in fact, any stand-alone variation that is topologically trivial excitation would be symmetric under for all . A tensor variation that breaks this symmetry for some would imply the presence of a non-trivial excitation. So the space of stand-alone tensors that satisfy symmetries for all has to the space of topologically trivial excitations. This precisely is the source of MPO symmetries, and is nothing but the projector onto the symmetric subspace for all . In fact this is why the MPO projector for both double-line (Eq. (39) and single-line (Eq. (38)) could be written in terms of loop operators on the virtual level. These loop operators are nothing but the Wilson loop operators on the virtual level.
Let’s illustrate the above discussion with the single-line TNR of toric code state. Let’s say the stand-alone tensor is surrounded by . We apply an -particle Wilson-loop around this stand-alone tensor. This Wilson-loop applies operators on the physical legs of the surrounding tensors. We have already seen that this operation can be brought down to the virtual level (Eq. (50) in the opposite direction),
| (120) |
Keeping in mind that also satisfies the symmetry of Eq. (5), we see that the -particle Wilson-loop finally reduces to a operator on the stand-alone tensor . That is,
| (121) |
In first equality, we have used relation (120) and in second equality we have used the symmetry of the single-line Tensor. So we find that the representation of -particle Wilson loop, on the stand-alone space is, . So we have shown that the presence of symmetry constraint inside the stand-alone space actually comes from the -particle Wilson loop.
Now a natural question arises: why isn’t there an analogous symmetry constraint on the tensor corresponding to an -string operator Wilson loop? Let’s apply the -particle Wilson-loop, which is a loop of operators on the single-line TNR, and then bring it down to the virual level. We find,
| (122) |
where we have used the fact that operators on the nearby virtual legs simply cancel each other. This was already noted in the discussion of zero-string operators and in Eq. (63). So we see that the -particle Wilson-loop poses no extra symmetry constraint on the stand-alone tensors.
Now let’s see if the MPO symmetry of double-line TNR also comes from a Wilson-loop. Double-line case is more interesting than the single-line case because, as we have already discussed, the double-line has a stand-alone space smaller than the full virtual space. We first look at the -particle Wilson-loop, which is a loop of operators on the physical level. We have already seen that this operation can be brought down to the virtual level (Eq. (52) in the opposite direction)
| (123) |
So we find
| (124) |
where in first equality we used Eq. 123 and in the second equality we simply used the relation
| (125) |
So we have shown that the MPO symmetry, , of double-line TNR is actually a representation of the -particle Wilson-loop on the stand-alone space. At this point, it is important to note that relation (125) holds only when is in the stand-alone space, so it has the symmetry. If was outside the stand-alone space, this would not be true. This is why we say that MPO symmetries, in this particular case, are representations of the Wilson-loops on the stand-alone space, not on the full virtual space.
Now we analyze the -particle Wilson-loop, which is a loop of operators. Eq. (66) tells us how to bring down the operators on double-line fixed point tensor, . Using this and other obvious properties of and , we find
| (126) |
The first equality follows from Eq. (66) and the fact that operators can be slid along contracted virtual legs. The last equality follows from the fact that is a stand-alone tensor, so it satisfies the symmetries by definition. Or, in other words, the representation of the Wilson-loop operator on the stand-alone space is . That is, it is represented trivially. So we see that all stand-alone tensors satisfy the -particle Wilson-loop symmetry. Hence this symmetry poses no extra constraint within stand-alone space, and that is why the MPO-injective subspace had only one symmetry. In fact, this analysis has shown what we already knew from Eq. (64): -string operator is a zero-string operator of the double-line TNR.
At this point, we can notice the similarity between double-line -particle relation and single-line -particle relation. But there is a crucial difference. has trivial representation on all of the virtual space of single-line TNR, but has trivial representation only in a subspace of the virtual space of double-line TNR.
This analysis points toward a representation theoretic way of understanding tensor instabilities. is a linear map from virtual vector space to the physical vector space. This map induces a representation of operators on the physical space in the virtual space. In particular, it induces the representation of Wilson-loop operators, . Such a representation is always possibly as is guaranteed by the MPO-injectivity (lemma 1 ). In fact, this representation would be faithful on individual tensors. But there is no guarantee that it would be faithful on the whole tensor network, because can be a gauge-string operator, as we have already discussed for in single-line and in double-line. So the string-operator algebra is not faithfully represented on the virtual level. It is this unfaithful representation of anyonic algebra that causes tensor instability.
Appendix B A brief review of string-net models
String-net models, which are Hamiltonian realizations of Turaev-Viro TQFTs, are introduced by Levin and Wen (2005) as RG fixed point models that describe topological order in spacetime dimensions. Following are the defining data of the string-net states:
1- Local Hilbert space: String-nets are lattice spin models. Spins sit on the links of hexagonal lattice. Each spin can be in state, . at a link can be understood as a string of ‘type ’ present on the link. Strings are oriented and denotes string type with the opposite orientation. If the strings are called ‘unoriented’. We have assumed the strings to be unoriented in the present paper for the sake of simplicity, though our results can easily be generalized to the oriented case.
2- Branching rules: There are branching rules denoted by . if string type are allowed to meet at a point, and otherwise.
3- Quantum dimensions: For every string type , there is a value associated to it, called its quantum dimensions. is called the
‘total quantum dimension’.
4- String-net condensed state: If we assign a particular string to each link, it forms a string-net configuration on the lattice. A string-net condensed quantum state is a superposition of these different string-net configurations on the lattice. Let’s denote the string-net configurations with . So a string-net condensed state is,
| (127) |
where is the amplitude with which a configuration appears in the description of the state. In general, can be complicated and states belonging to the same topological phase might have different wave functions. However, if we perform an RG process, then all states in the same phase would end at the same fixed point state, which is to say that they should look the same at large distances. can be described for this fixed point state. Though their absolute values are again complicated, we can give their relative values by describing local constraints on how amplitude changes as we deform a configuration locally. These deformations involve rebranching, removing bubbles, fusing two strings together, etc. These constraint equations are given in equation (4)-(7) of Levin and Wen (2005). The most significant of these local constraint is the so called ’’-move.
5- -symbols: A local constraint involving rebranching of 5 strings is the following:
| (128) |
-symbol is a six indexed object and it satisfies the following properties:
| (129) | |||||
| (130) |
Properties of the -symbol under index permutations can be best captured by defining a new object called -symbol by . -symbol can be considered as a value associated to a tetrahedron and the six indices sit on the six edges of tetrahedron. Then it is invariant under all tetrahedron symmetries. It satisfies an important equation, the so-called ‘Pentagon Identity’:
| (131) |
Finally we describe the exactly solvable Hamiltonian such that the RG fixed point state defined as above is one of the ground states,
| (132) |
where and denote the vertices and plaquette of the lattice. The vertex term is
| (133) |
So, the vertex term simply projects configurations to only the ones that contain the allowed branchings. The plaquette term is more involved:
| (134) |
where is an operator that creates an -type string that fuses with the strings on the plaquette. Two strings can be fused together by assuming a 0-string between them and then using -moves.
Finally putting all of it together, we see that the data describes a string-net model.
B.1 Algebraic Identities
Here we enlist multiple algebraic relations regarding string-net data that are used throughout the paper. For rotational convenience, cyclic products will be simply denoted by with a cyclic . One of the most important identities is the ‘Pentagon Identity’,
| (I.1) |
symbols also satisfy an ‘orthogonality identity’,
| (135) |
-symbols are normalized as
| (136) |
Cyclic products of symbols satisfy the following equation:
| (137) |
Plaquette operators correspondingly satisfy
| (138) |
We know that if we contract an -type loop we get a factor of . Combining this with the last two equation, we find that quantum dimensions satisfy the same identity:
| (139) |
where are nothing but the eigenvalues of the plaquette operators operators where the eigenstate is the string-net ground state.
Define matrix as . Since matrices are real symmetric matrices, and commute with each other for different values of , they share a complete set of orthogonal eigenvectors.We write the th such simultaneous eigenvector of as
| (140) |
Since quantum dimensions form one such eigenvector, we fix . The following equations follow
| (141) | |||||
| (142) |
The branching tensor is part of a fusion category data. Under the additional assumptions of braiding defined on the fusion category and braiding being sufficiently non-trivial (modularity), the above are just the columns of matrix. But we don’t really need this for our results.
Appendix C Triple-line TNR of string-net states
We now briefly describe the derivation of triple-line TNR along the lines described in the original paper by Gu et al. (2009). It is important to understand this derivation as it gives us a way to apply string-operators on triple-line TNR.
String net RG fixed point ground state can be constructed by applying plaquette operator to the vacuum state . creates an -type string loop on the plaquette .
| (143) | |||||
where
| (144) |
is a string configuration on the ‘fattened lattice’. We will refer to as the ‘loop state’. See Fig. 16.
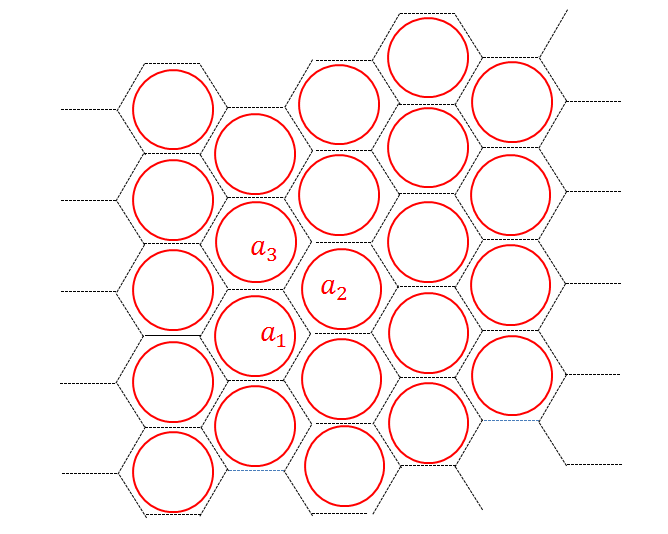
We need to fuse these loops together to get the physical state. We then fuse these strings together to get the final physical state,
| (145) |
There are essentially 3 steps leading up to the expression of the triple-line TNR. We mention them here explicitly as we will need to refer back to them for other calculations.
Step 1: We start with the ‘loop state’ on the fattened lattice. th plaquette has a loop in state . The ground state is
| (146) |
So every plaquette contributes a factor of . We distribute it uniformly among the 6 vertices, so each vertex gets a factor of from each vertex.
Step 2: We fuse all loops with nearby loops producing a string on the links:
| (147) |
We assume a 0-string between them and perform an -move. It produces a factor of on each link between plaquette and . A link is shared between two vertices, so each vertex gets a factor of .
Step 3: After the previous step, we are left with a ‘bubble’ on the vertex. Now we remove it,
| (148) |
Removing it produces a factor of .
Putting the 3 steps together, we get
| (149) |
A general triple-line Tensor is represented diagrammatically as:
| (150) |
For the specific RG fixed point tensor we have . So it would be represented diagrammatically as:
| (151) |
Appendix D Proof of theorem 1
To calculate the stand-alone space, we need to know how to contract double-tensors on a large region. First we need to define the concept of boundary operators that show up in double-tensor contraction.
D.1 Boundary operators
It is more convenient to work with the dual lattice of honeycomb lattice. The dual lattice of honeycomb lattice is the triangular lattice. We label the vertices with an integer . The edges are labeled by the two vertices on its ends, . The triple line tensor is represented as a triangle,
| (152) |
The inner indices sit on the vertices of the triangles, and the physical legs and the middle legs on the edges. We denote the inner index sitting on vertex as , and the physical and middle legs sitting on the edge are denoted as . With this construction, the tensor component can be written as
| (153) |
A double tensor of a tensor is defined as and is denoted by . denotes the set of physical indices. So we get the double tensor of a tensor by contracting the physical indices between and its complex conjugate, . Since the tensor is represented by a triangle, the double tensor can be represented by a double layer triangle.
The edge labels are the same bottom to top, only the labels of the vertices change. We label the upper vertices as . With this a double tensor can be written as
| (154) |
Using the pentagon equation we get
| (155) | |||||
| (156) |
can be represented as the boundary of double-layer triangle,
| (157) |
It is useful to decompose into terms that sit on the edge of the triangle and terms that sit on the vertices,
| (158) |
The first cyclic product on the RHS sits on the edges while the second term sits on the vertices. So we see that the double tensor on a triangle is (we will denote triangle as )
| (159) |
The tensor resulting from contracting tensors on a region will be denoted as . We call , the -type boundary operator. It lives on the boundary of a region ,
| (160) |
See Fig. 160. Let’s say the vertices on the boundary of a region on the triangluar lattice are labeled as . We associate with each vertex a factor of . denotes the number of the triangles inside meeting at vertex . It can simply be written as , where is the angle the loop makes on vertex . Finally, on every edge we associate an operator . With this construction, can be written as,
| (161) |
Now we are ready to contract tensors on individual triangles with each other in order to find the double tensor on a region .
D.2 Double-tensor/Virtual density matrix on a general region
We present the result in a lemma.
Lemma 2.
We find that the double tensor satisfies the general version of Eq. (159):
| (162) |
where is the Euler characteristic of region . ,, and are the number of vertices, edges, and faces that are completely inside the region (that is, they are inside the region where tensors have been contracted).
Proof.
There is a simple proof of this result. We have to contract on each triangle with each other on the common edges and vertices to get ,
| (163) | |||||
where, as defined before, tTr denotes the operation of contracting a set of tensors along shared indices. So we basically have to see how contracts with . They can be contracted in two steps. First we contract all the edges, and then we contract all the vertices, and we will be left with terms sitting only on the boundary of the region. Using the orthogonality identity, Eq. (135), edge contraction on the edge between and gives
| (164) | |||||
The factor implies that only contracts with . So the expression in Eq. (163) is only non-zero for . So we have
| (165) |
where is the number of faces in region . Then there are factors of in Eq. (164) that will be used in the second step of vertex contraction. Finally note a factor of that comes out of every edge contraction. So when we are done with all the edges, we will have an overall factor of , where is the number of edges.
Now we do tensor contraction on each vertex. Note that each of the six triangles around a vertex contribute a factor of , so we have a total factor on each vertex. We multiply this with the factor that came out of edge contraction. So, finally we have the vertex contraction using identity (139),
| (166) |
So we see that contraction of 6 tensors on each vertex simply produces a factor of for every -type boundary operator. When we are done with all the vertex contractions, we will have an overall factor. Putting all the factors together, we get
| (167) | |||||
This completes the proof.
To calculate the stand-alone space, we need to know how these boundary operators behave on a large region. We present the result of this calculation in the following important lemma: ∎
Lemma 3.
| (168) |
Proof.
To prove this, we would calculate on a sphere using the virtual-density method laid out in II.2 in the previous chapter, and compare it to the known result, . We divide the sphere in symmetric two halves, let’s say and , and calculate . We assume the state has the appropriate symmetry such that . Using the result by Cirac et al. (2011), we know that the physical density matrix has the same spectrum as , that is, . Let’s say , where is the normalization factor. We first calculate . To do that, we first need to calculate the algebra and the trace of .
Let’s put the string-net tensor network state on a sphere. Consider the left hemisphere, denoted as , and right hemisphere, denoted as . Let’s denote the indices of the vertices on the boundary as . Then on this boundary is given by,
| (169) |
Since divides the region in to exact two halves, we assume that the boundary divides the boundary plaquette in to exact two halves, setting . So we get,
| (170) |
Note that, using relation (136)
| (171) | |||||
| (172) |
Now, using identity (137) the algebra of operators is,
| (173) | |||||
| (174) |
We also know how to contract with each other through the calculations done previously in the privious subsection. We learned that only contracts with itself, and it gives a factor of for every edge and a factor of for every vertex. On a loop the number of vertices is equal to number of edges. So we get,
| (175) |
If calculate , we find
| (176) | |||||
where is a matrix whose components are . If has a non-degenerate highest eigen-value , for large , . Note that Perron-Frobenius theorem makes sure that , highest eigen-value of , will be non-degenerate. So we have
| (177) |
For abelian models, since . For the double-Fibonacci model to be discussed in VIII, a simple calculation shows and , where is the quantum dimension of the string. Because , for large .
On a hemisphere, , so from lemma 2 we have and where is a normalization factor. First we calculate the normalization factor ,
| (178) | |||||
Now, calculating Renyi entropy with renyi index , we get
| (179) | |||||
We know that for a string-net model topological entanglement entropy is , which implies . This completes the proof. ∎
D.3 String-net stand-alone subspace
Now we combine lemma 2 and lemma 3 to prove theorem 1. That is, to prove that the stand alone space is given by The stand alone space of the triple-line string net TNR is given by
| (180) |
Proof.
Now we are ready to calculate the stand-alone space. Consider the same tensor network but on a very large disc with one triangle removed from the origin. We will denote this space as . This has two disconnected boundaries, one on the outer edge, one on the inner one. for this region, so using lemma 2
| (181) | |||||
| (182) |
To get the stand-alone space, we simply trace out the inner indices on the outer edge. But according to lemma 3, only contribute in the large disc limit. So we simply get (up to an overall normalization factor which we ignore) on the triangle,
| (183) | |||||
| (184) |
But using (171) we get
| (185) |
Stand-alone projector, , is simply the projector onto the support space of , which is clearly . So we have proved that for triple-line TNR of general string-net is,
| (186) |
This completes the proof. ∎
This is the projector on to the stand-alone space of triple-line TNR of general string-net models. For notational convenience we will denote these basis vectors as , that is,
| (187) | |||||
| (188) |
So we get,
D.4 String-net MPO symmetries from Wilson-loop operators
In last chapter, we showed how MPO symmetries or the MPO-injective subspace come from representation of anyonic Wilson-loops of the model on the stand-alone space. It is instructive to do the same with general string-net models.
When an -type simple string operator passes through the tensor on the physical level, it induces an operation on the virtual level in the way shown in Fig. 190.
That is, it simply becomes a -type string which is then fused with the plaquette legs. We consider the Wilson loop that encircles the 3 plaquettes of the tensor. This Wilson loop creates an -type string that then fuses with the 3 plaquette loops. Remember that we need to calculate the representation of this operator on the stand-alone space. That is, we need to calculate the matrix elements . So we imagine a tensor network in which the tensor in the stand-alone basis is surrounded by . We now apply the Wilson loop encircling 3 plaquettes and calculate induced operator on the stand-alone basis. It can be done in a convenient way using string-net diagrams in Eq. (188).
There are essentially 3 steps:
Step 1: Since the surrounding tensors are the fixed point tensor , the Wilson loop on the physical level simply becomes an -type string that fuses with the plaquette legs,
| (190) |
Since these plaquette legs are contracted with the plaquette legs of the stand-alone tensor, it is equivalent to fusing -string loop with the 3 plaquette legs of the stand-alone tensor,
| (191) |
Step 2: We fuse these strings with the three nearby strings ,
| (192) |
Let’s say they fuse to make strings . We gain factors for each fusion.
Step 3: In the last step we remove the three bubbles created in the previous step,
| (193) |
Each bubble removal produces a factor of .
Collecting the factors from step 2 and step 3, we get
| (194) |
This is the expression for . Now considering the projector , we get
| (195) | |||||
It should be understood as an operator written in its components in the basis . We used pentagon identity in the second step. We can see that it projects on to the space with , that is .
There is a small technical issue though. The factor does not exactly match the factors in the support space given in Eq. (92)). It is simply because we did not keep track of exactly how to distribute factors that share a plaquette while applying the Wilson loop. In fact, the Wilson loop around a single vertex is somewhat ill-defined. But we are only trying to get a symmetry condition on the individual tensors which makes sure that Wilson loop on a larger region is a symmetry of the state. We can show that this factor has to be exactly if the Wilson loop is to be a symmetry of the state. The reason is simply, as concluded in the original string-net paper, a Wilson loop commutes with the plaquette term only when . In tensor network language, it translates to the fact that every tensor must contribute a factor of for the Wilson loop to be a symmetry. Also we know that an -type Wilson loop applied to the ground state produces a factor of . Combining all these we can write the exact Wilson loop operator on a single tensor as:
| (196) | |||||
| (197) |
The fixed point triple-line tensor satisfies
| (198) | |||||
| (199) |
One can check that is indeed a projector and it projects onto the support space of .
Finally, just like boundary operators , -type MPO can be extended to an arbitrary large region as
| (200) |
and it represents the operation induced on the virtual level by a Wilson loop applied on the boundary of the region .
Appendix E 0-type string operator is a zero-string operator of triple-line TNR
In last chapter we argued how the reason for instability is that some of the non-trivial anyon operators might have a trivial representation on the virtual level. That is, they disappear identically on the ground state tensor network, even in the presence of a topological hole. We saw that, for the single-line and double-line TNR of toric code, -string and -string operators were the zero-string operators respectively. Indeed, the general string-net also has such an operator. These are the operators that only has string-type 0 in it. Remember that string-operators on the string net model act by adding a string-type (possibly more than one) to the string-net and then fusing it with the string-net by some fusion rules. The expression of Wilson-loop operators can be used to see how a string operator with open ends would act on the tensors along the path. It would look the same as in Eq. (200) along the path with some changes at the end. But we don’t worry too much about the details of how this operator looks at its ends, since those details can always be changed using local unitary operators at its ends. Looking at the Wilson-loop operators in Eq. (200), it is immediately clear what the invisible string operators are for the triple-line TNR of general string-nets. For , (using identity (136))
| (201) | |||||
But the final expression is the very definition of stand-alone space itself. It means this operator will act trivially on the stand-alone space. So, a -type simple string operator is a non-trivial invisible string operator, that is, it is a zero-string operator. From this it should be clear why we denoted the stand-alone space and why we called non-trivial invisible string-operators zero-string operators. These names come from the general string-net formalism.
It is also clear that for , acts necessarily non-trivially on the tensors along the path. One should carefully note that, though non-zero-string operators change tensors along the path, it does not mean that this path is a physical observable. These paths can always be deformed as passes through without any phase accumulation. It is called the ‘pulling-through condition’ Şahinoğlu et al. (2014). When there is an MPO violating variation present at a tensor, cannot be pulled through it. Hence our conjecture can be alternatively worded as ‘the stand-alone variations which prohibit the pulling-through property of fixed point tensors cause instability.’
Appendix F Proof of theorem 2
We will give an analytical proof of why all string-net triple-line TNR have at least one unstable direction which comes from the subspace. We will do so by directly calculating .
F.1 Topological entanglement entropy on a cylinder with non-RG fixed point tensor
Lemma 4.
Proof.
The proof is quite simple. We follow the same steps as used in the proof of lemma 3, replacing with . We first calculate the normalization of the density matrix.
| (204) | |||||
By calculating Renyi entropy with renyi index , we get
When we let and using Eq. (3)
| (205) | |||||
| (206) |
This completes the the proof.
∎
Finally we are ready to show the unstable tensor perturbations in the triple line TNR of the string-net models.
F.2 Instability in string-net
Now we give proof of theorem 2.
Proof.
Combination of the lemma 2, theorem D.3 and lemma 4 gives a clue to why , are unstable variations. We will choose particular variations in for analytical simplicity, but it should be understood that any arbitrary variation that has a component in those directions will result in instability. We discussed in section VII.4 that there are two kinds of variations in ; vertex variations (that violate the vertex term) and plaquette variations (that violate the plaquette term). We will treat them one by one.
Before we do any analytical calculation, let us describe in simple words what the reason for instability is. We saw in the proof of lemma 2 that as fixed point tensors contract, every face, every edge, and every vertex contribute a factor of , , and respectively. It can be visualized like this,
![[Uncaptioned image]](https://cdn.awesomepapers.org/papers/690c64a3-bcf4-458a-9cef-b735cb8527dd/dfeverywhere.png) |
(207) |
It combines to give which is a topological invariant of the lattice. If a tensor variation changes the double tensor in such a way that one of these factors (face, edge or vertices) are changed, even infinitesimally, then the we get is not a topological invariant, and due to lemma 4 changes. We will now show that this is precisely what variations in do. In particular, the vertex variations change the vertex factors, and the plaquette variations change the face factors.
Let’s choose a particular tensor variation
| (208) |
such that
| (209) |
This tensor is supported on the full space and clearly has components outside the MPO-injective subspace because as we showed . So . Now, the double tensor for the varied tensor is
| (210) | |||
| (211) |
We have ignored the linear terms in as they are contained within the MPO-injective subspace, and we don’t need to worry about them. This double tensor will contract with itself in exactly the same way as did, but the only difference is, now every face will contribute a factor of , where, , and . The vertex factors and edge factors will remain to be and , respectively. After contracting it on a large region we will get a double tensor , where . So and . So we see that is exponentially larger than even for an infinitesimal , hence, using Eq. (206), .
Now we look an example of plaquette variations. Consider tensors that are exactly the same as the fixed point tensors, except the plaquette factors are replaced by a factor of , where is the th component of the th eigenvector of , as explained in Eq. (140).
| (212) |
This tensor is clearly supported on the stand-alone space, and is outside the MPO-injective subspace as to be inside the MPO-injective subspace it has to have factors. The double tensor will again produce a factor of on the faces, and on the edges upon contraction. But now the factors on the vertices would be
where is normalized to give and is the th eigenvalue of the matrix . A conclusion similar to that for vertex variation case follows. is not a topological invariant, as it extensively depends on the number of vertices . As a result, the weight of one of the boundary operator in becomes exponentially larger than the others even for an infinitesimal variation , and hence the topological order is lost.
Result I-IV together complete the proof that triple-line TNR of general string-net states have at least one unstable direction.
∎
Appendix G Dependence of on boundary conditions in cylindrical geometry
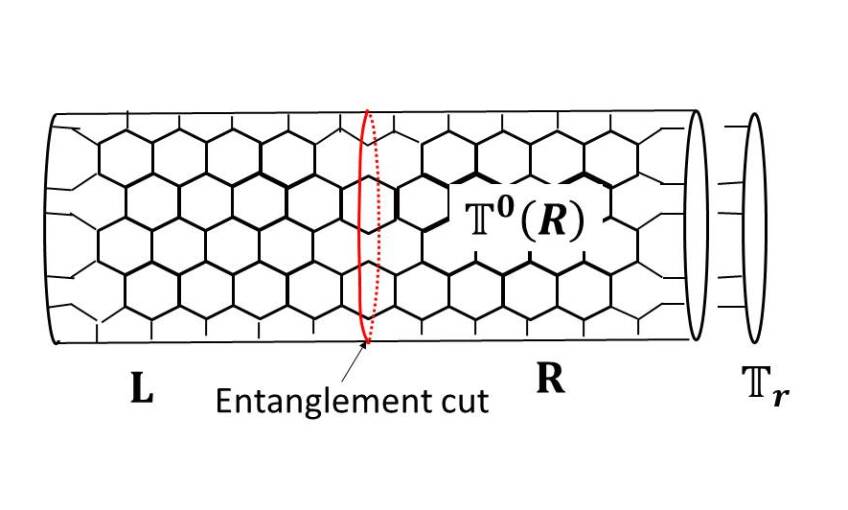
Topological entanglement entropy calculation is done by calculating the entanglement entropy of a subsystem . When the boundary of consists of topologically trivial loops, for example when has a disc geometry, is known to depend only on the total quantum dimension , . However when the boundary of consists of non-contractible topologically non-trivial loops, for example when a torus or cylinder is divided into two cylinders, it has been shown by Zhang et al. (2012) that also depends on the linear combination of ground states. For a ground state wave function on a torus
| (214) |
where the sum is over the degenerate ground states labeled by quasi-particles of the model, the th Rényi entropy is given by
| (215) | |||||
where is the quantum dimension of th quasi-particle and . are special basis for which is maximal, or entanglement entropy is minimal. These states are called the Minimum Entropic States (MES) . It was shown that MES correspond to eigenstates of Wilson-loop operators along the entanglement cut.
This dependence of on the ground state is of crucial importance to us since we have used cylinder with a boundary for calculations. So, numerically obtained contain information about the boundary as well. For example, consider the toric code.
when we get although the the topological order is not lost. So one has to be careful using as an indicator of topological order.
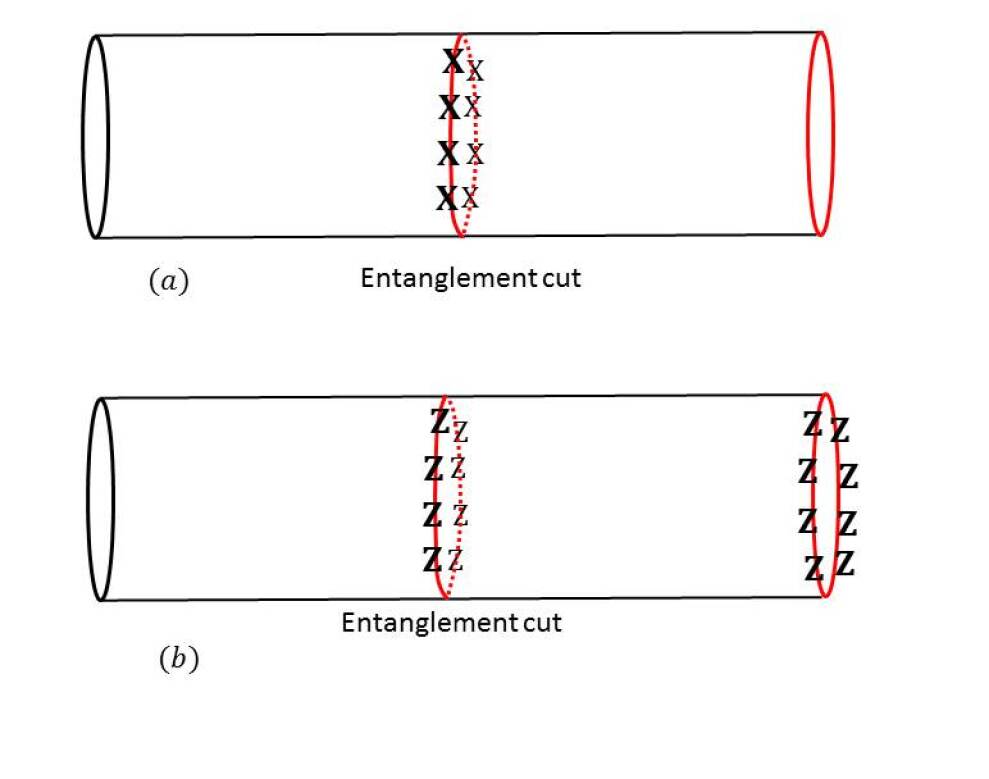
Let’s first take the example of the single-line TNR of the toric code. See Fig. 18. We put our system on a cylinder with some boundary conditions to be determined later. The entanglement cut is in the middle of the cylinder, and the right half cylinder, denoted as , is the subsystem whose entanglement entropy we are calculating (see Fig. 17). The four MES correspond to four eigen states of and Wilson-loops on the entanglement cut. But, since -Wilson loop is a zero-string operator, the state is always in its eigenstate (Fig. 18(a)). So we have access to only two MES corresponding to eigenstates of -Wilson loop. We also know that the state is in eigenstate of the , where subscript stands for loop at entanglement cut, and stands for the loop at the right boundary of . Since the state is in +1 eigenstate of (see Fig. 18)(b), the state can be either in eigen-state of both and or in eigenstate of the both. The boundary tensor determines which eigenstate of the wave function is in, and consequently also which eigenstate of . This is how the boundary tensors and MES are connected. Since we have access to only two MES
| (217) |
A similar analysis follows in the double-line TNR, with the role of and Wilson loop operators reversed: now the state is always in the eigen state of -Wilson loop and the two MES correspond to the two eigenstates of Wilson loop at the entanglement cut, which in turn depends on the boundary tensors.
We saw in the Appendix 4 where
| (218) |
where denotes the double tensor on the boundary. We know that, up to an irrelevant normalization constant,
| (219) | |||||
where and for the single-line TNR and for the double-line TNR. Let’s say the boundary double tensor contracts with to produce the constants (see Fig. 19)
| (220) | |||||
where and and . Note that satisfy the following,
| (221) |
With this, we get the normalized density matrix as,
| (222) | |||||
| (223) |
The th Renyi entropy is,
Comparing it with the MES formula in Eq. (217), we see that and . So the state is an MES if for which we get maximal topological entanglement entropy, . This illustrates the direct dependence of on .
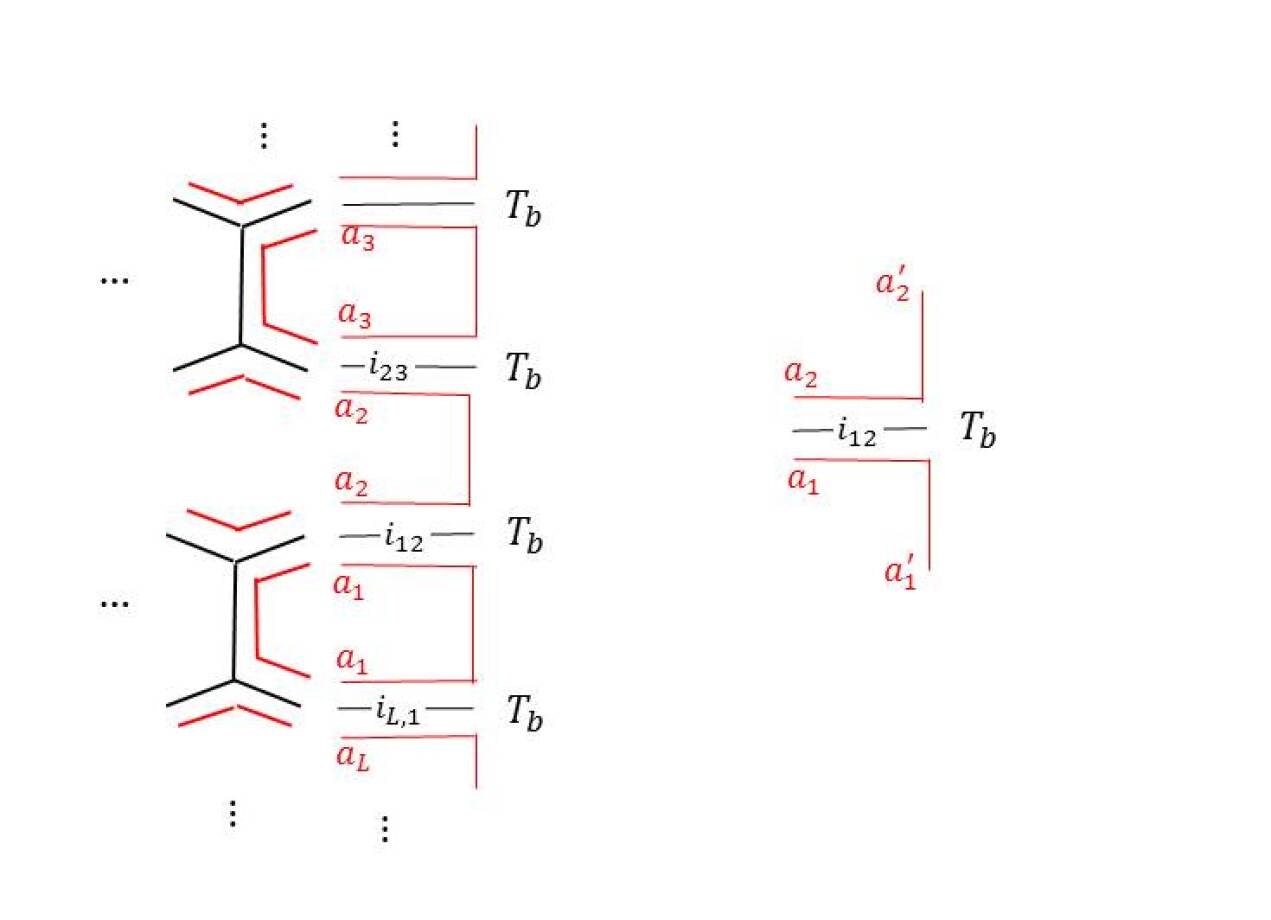
Of course the above analysis is done for the RG fixed point tensors only. We have to choose a boundary double tensor such that is truly indicative for topological order, or lack of it, for both RG fixed point and varied tensors. We choose the following boundary tensor for our numerical calculations: For any tensor network, fixed point or varied, We use a ‘smooth boundary condition’. It is explained in the Fig. 20. First we will explain it for the triple-line tensors. For double-line and single-line an appropriately reduced version of will be used. Note that we haven’t drawn the physical index explicitly and it should be understood the same as the middle index (the index in black color). So the boundary tensor has four virtual indices, and we fix its components to be,
| (225) |
that is, we put the physical/middle index to zero (vacuum) and allow the plaquette legs to vary with this restriction. For double-line we don’t have a middle leg, but we can simply put the physical leg to 0. For single-line we only have the middle legs and we put them to zero.
Before we discuss why we choose this particular boundary, let us calculate what we are supposed to get with this particular choice of boundary tensor. For that, we need to calculate . Note that implies . So the double tensor is
| (226) |
So
| (227) | |||||
Then using Eq. (206), is simply . For the toric code, and double semion models , so we get . For the double Fibonacci model, however, we get
| (228) | |||
| (229) |
So we get , which is consistent with our numerical result.
There are mainly two reasons why we choose this particular boundary condition
1- This is a very simple boundary condition which gives us a precise analytical value of the topological entanglement entropy (namely, , with given in Eq. (227)) against which numerical calculations can be checked.
2- Though situation for non-abelian cases is more complicated, this boundary is definitely MPO symmetric for abelian models. That is, we expect the tensor network state to be an MES with maximal (=).
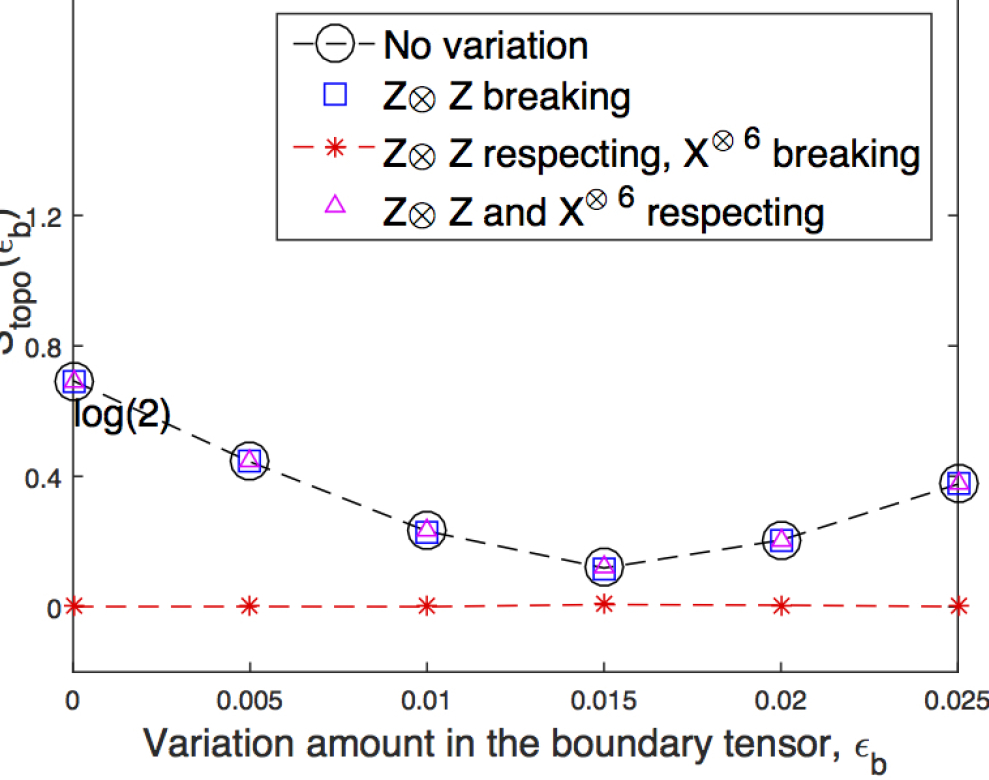
Numerical calculations of will be checked against the analytical result in Eq. (227). Now the remaining question is about the trustworthiness of the same calculation for varied tensor. That is, how can we deduce the conclusion about the topological order of the varied tensor by ? First point is, if , then we can definitely say that the state is in the same topological phase. But needs to be further verified as it might be because of the particular boundary conditions imposed. To verify, we will test for dependence on infinitesimal variation on the boundary tensors. The reason for this is clear by looking at the dependence of on etc. So, if the state indeed has a topological order, should sensitively depend on the . If the state has lost its topological order, will remain zero under any changes of the boundary tensor. This way, we can avoid getting any ‘accidental ’ cases, for example when .
One such verification is shown in Fig. 21. We first fix the boundary tensor to be given in Eq. (20) and calculate the for variations in and subspaces added to the fixed point bulk tensor. Now we add an infinitesimal random variation to the boundary tensor, . (different from , which the bulk variation strength) is the strength of the boundary variation. We increase slowly and for each value of the we calculate for random bulk variations in different subspaces. Fig. 21 shows as a function of for bulk variations in different subspaces. (the bulk variation strength is kept fixed throughout). We observe that
1- The variations which are unstable (i.e. ) for , continue to be unstable for for all values of . It implies that we get for these variation because the bulk topological order is indeed destroyed and not because of a specific boundary tensor chosen which gave an accidental zero.
2-The variations which are stable (i.e. ) for , have the same value of as the fixed point tensor for all boundary tensors. It implies that tensor network state with these variations indeed have the same topological order as the fixed point tensor network state.
Though this verification is shown for double-line toric code only, we find the same behavior for all numerical calculations presented in this paper.
It should be noted that any strictly positive value of (assuming sufficiently large cylinder was considered) is a sufficient condition for topological order but it is not a necessary condition. So all we need to do is to avoid getting accidental zeros.
Appendix H Details of numerical calculations
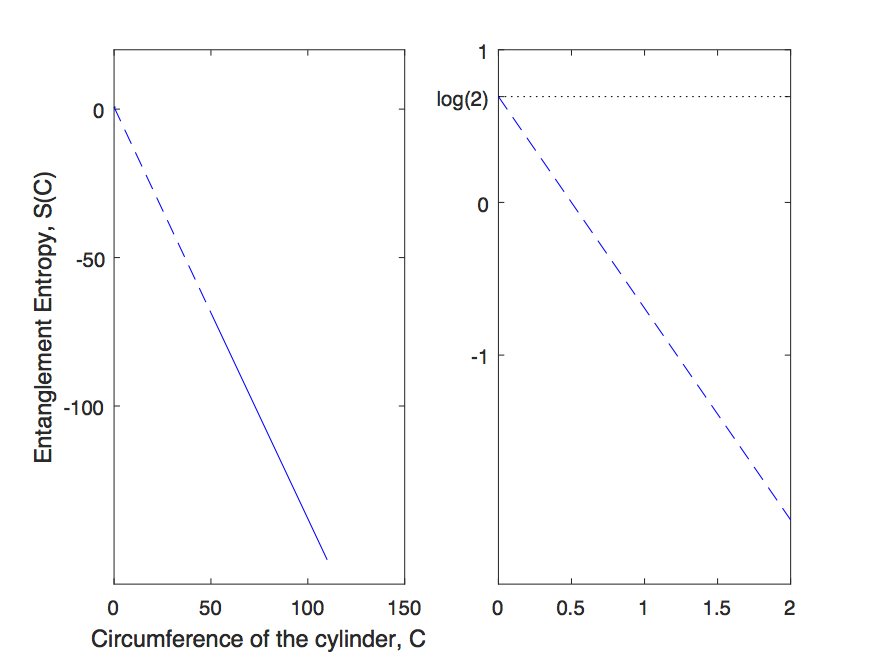
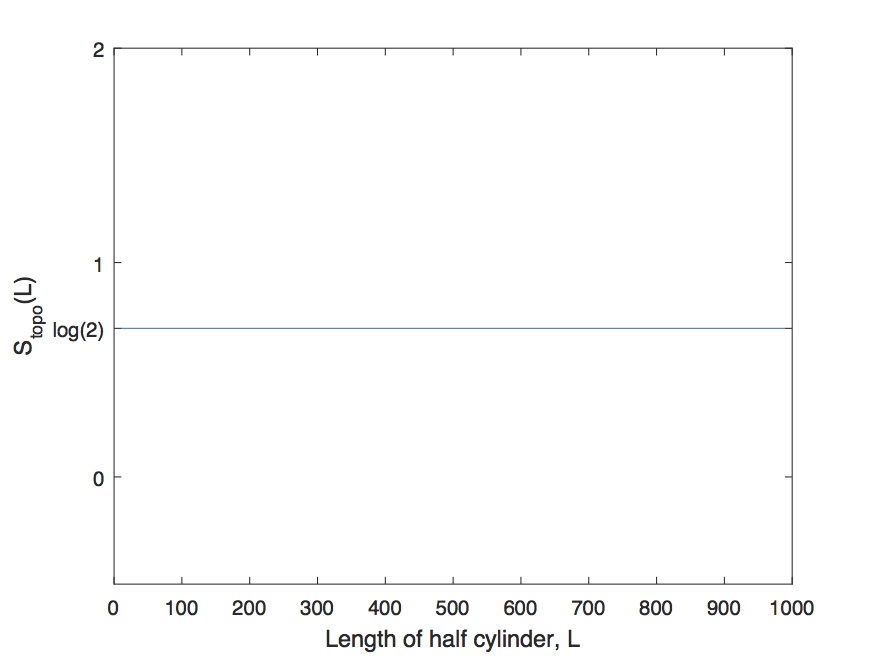
Here we will provide the various numerical details and data regarding the numerical calculations whose results were presented in the main text.
First, we will show convergence of numerical calculation of . We choose the simplest case, the single-line TNR of toric code. We first repeat the algorithm described in section II.2 in simple words here for convenience. In the first step, the transfer matrix is calculated using the tensor given (fixed point or varied). Then we choose a specific boundary double tensor as explained in the Appendix G. We apply the transfer matrix on this boundary double tensor and approximate the resulting tensor as an MPS of bond dimensions . We apply transfer matrix again and approximate the resulting tensor as an MPS of bond dimension 8. We repeat this process and each repetition physically corresponds to increasing the longitudinal length of the our cylindrical subsystem by one unit. Let’s say we repeat this process until the length of the half cylinder subsystem is equal to . This process gives us the virtual density matrix , and assuming the mirror symmetry of transfer matrix, the physical reduced density matrix of the half cylinder is . With this reduced density matrix we calculate the entanglement entropy of the half cylinder subsystem for different circumferences . We plot vs and extrapolate it to which gives us the topological entanglement entropy . In principle, one needs to take infinitely large cylinder to achieve the precise value of . Practically, we need to keep increasing until we get a fixed point MPS and keep increasing until the value converges to a fixed point.
Let’s first look at the calculation for the single-line toric code fixed point tensor in Eq. (4). Half cylinder length is fixed at . is varied from 50 to 110. Fig. 22 shows the entanglement entropy vs the circumference . We get a straight line which is extrapolated to . The right figure is a zoomed in version of the left figure to see clearly where the extrapolated line crosses the y-axis. We get as expected. Fig. 23 shows the dependence of on the half cylinder length . We see that there is no dependence, that is, fixed point MPS is achieved immediately. It is expected as it is an RG fixed point tensor network state.
Now we look at the calculation for single-line toric code fixed point tensor varied with an MPO symmetry breaking tensor. Remember that it is claimed in the main text that this is a trivial state. The variation strength is fixed at . Half cylinder length is fixed at . is varied from 50 to 110. Fig. 24 shows entanglement entropy vs the circumference . We get a straight line which is extrapolated to . The right figure is a zoomed in version of the left figure to show clearly where the extrapolated line crosses the y-axis. We see . To see the effect of cylinder length we calculate again but with different cylinder lengths. The results are shown in Fig. 25. We see that is for small cylinders but converges to zero as the length is increased. Comparing it to Fig. 23 we see that, unlike the fixed point case, we need to consider large enough cylinder ( in this case) to calculate the correct value for the non-fixed point tensor network state.
Finally we show the effect of variation strength, , on the convergence. In above calculation we fixed . Now we vary from 0.01 to 0.02 (making sure it is well below any critical points) and calculate corresponding convergence plots similar to Fig. 25. The results are shown in Fig. 26. We see that the strength of the variation has a huge effect on convergence. Bigger variations lead to faster convergence.
Though we have presented details of calculation only for one case (single-line toric code TNR), it should be understood that similar patterns are followed in all other cases. For completeness, we present the numerical data plotted in the main text and the relevant parameters used in each case.
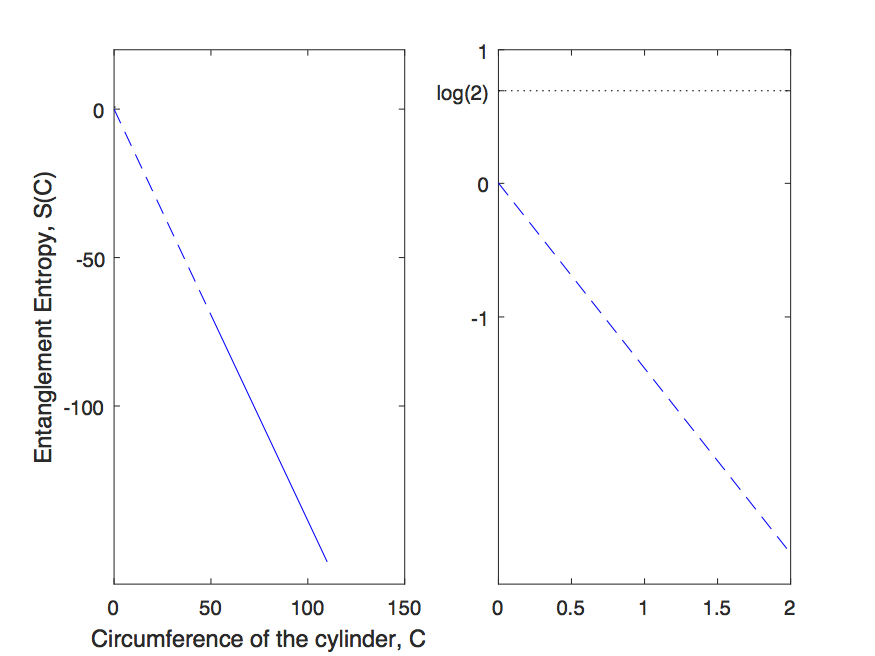
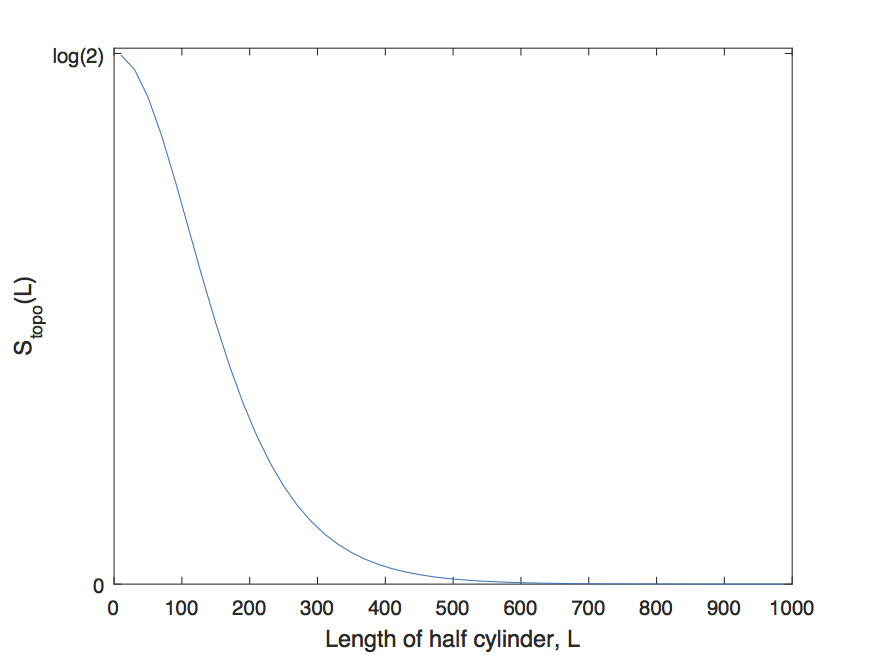
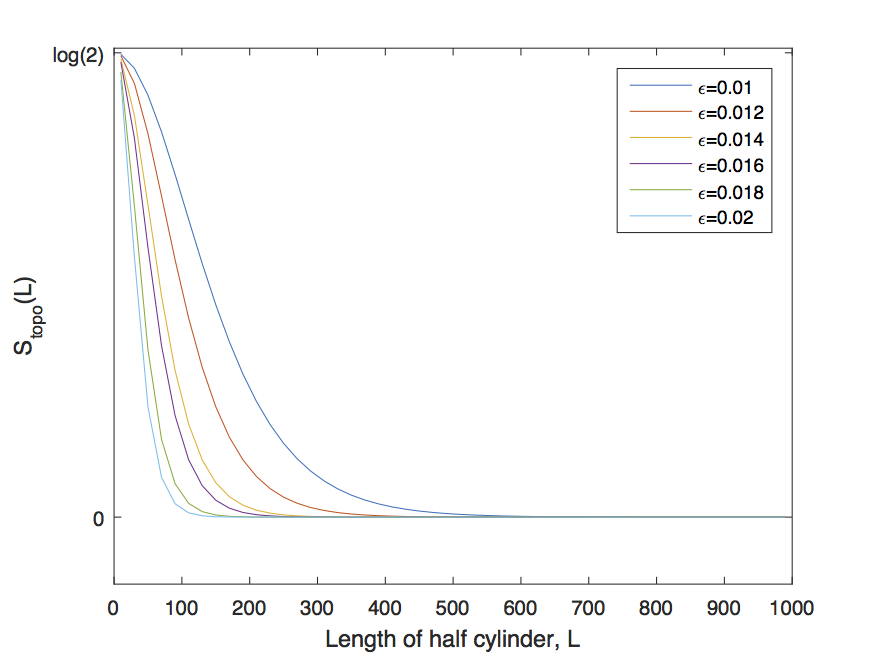
H.1 Single-line TNR toric code
The bond dimension of the MPS is kept fixed at at each step of the iteration. The starting MPS is as explained in the Appendix G. The strength of the variations is fixed at . Half cylinder length is either the length at which convergence of is reached (convergence is reached when value in two successive steps differ by less than ) or , whichever is smaller. The circumference is varied from 50 to 110.
Following table contains the exact values of the plotted in Fig. 4.
| No Variation | 0.6931 |
|---|---|
| respecting variations | 0.6931 0.6931 0.6931 0.6931 0.6931 0.6931 0.6931 0.6931 0.6931 |
| violating variations | 0.9095 0 -0.4547 -0.4547 0 0 0.9095 0.4547 -0.4547 |
H.2 Double-line TNR toric code
The bond dimension of the MPS is kept fixed at at each step of the iteration. The starting MPS is as explained in the Appendix G. The strength of the variations is fixed at . Half cylinder length is either the length at which convergence of is reached (convergence is reached when value in two successive steps differ by less than ) or , whichever is smaller. The circumference is varied from 50 to 110. Following table contains the exact values of the plotted in Fig. 6.
| No Variation | 0.6931 |
|---|---|
| breaking variations | 0.6931 0.6931 0.6931 0.6931 0.6931 |
| respecting, breaking variations | 0.0000 0.0015 0.0000 0.0000 0.0002 |
| and respecting variations | 0.6931 0.6931 0.6931 0.6931 0.6931 |
H.3 Double-line TNR double semion code
The bond dimension of the MPS is kept fixed at at each step of the iteration. The starting MPS is as explained in the Appendix G. The strength of the variations is fixed at . Half cylinder length is either the length at which convergence of is reached (convergence is reached when value in two successive steps differ by less than ) or , whichever is smaller. The circumference is varied from 50 to 110. Following table contains the exact values of the plotted in Fig. 11.
| No Variation | 0.6931 |
|---|---|
| breaking variations | 0.6931 0.6931 0.6931 0.6931 0.6931 |
| respecting, breaking variations | 0.0133 0.0047 0.0191 0.0086 0.0063 |
| and respecting variations | 0.6931 0.6931 0.6931 0.6931 0.6931 |
H.4 Triple-line toric code
The bond dimension of the MPS is kept fixed at at each step of the iteration. The starting MPS is as explained in the Appendix G. The strength of the variations is fixed at . Half cylinder length is either the length at which convergence of is reached (convergence is reached when value in two successive steps differ by less than ) or , whichever is smaller. The circumference is varied from 50 to 110. Following table contains the exact values of the plotted in Fig. 12.
| No Variation | 0.6931 |
|---|---|
| Variations in | 0.6931 0.6931 0.6931 0.6931 0.6931 |
| Variations in | 0.2467 0.0986 0.2658 0.0257 0.0005 |
| Variations in | 0.6931 0.6931 0.6931 0.6931 0.6931 |
H.5 Triple-line double-semion
The bond dimension of the MPS is kept fixed at at each step of the iteration. The starting MPS is as explained in the Appendix G. The strength of the variations is fixed at . Half cylinder length is either the length at which convergence of is reached (convergence is reached when value in two successive steps differ by less than ) or , whichever is smaller. The circumference is varied from 50 to 110. Following table contains the exact values of the plotted in Fig. 13.
| No Variation | 0.6931 |
|---|---|
| Variations in | 0.6932 0.6931 0.6932 0.6931 0.6932 |
| Variations in | 0.7877 0.0849 0.0003 0.0006 0.0000 |
| Variations in | 0.6931 0.6931 0.6931 0.6931 0.6931 |
H.6 Triple-line Fibonacci model
The bond dimension of the MPS is kept fixed at at each step of the iteration. The starting MPS is as explained in the Appendix G. The strength of the variations is fixed at . Half cylinder length is either the length at which convergence of is reached (convergence is reached when value in two successive steps differ by less than ) or , whichever is smaller. The circumference is varied from 50 to 110. Following table contains the exact values of the plotted in Fig. 14.
| No Variation | 1.1787 |
|---|---|
| Variations in | 1.1779 1.1776 1.1774 1.1778 1.1779 |
| Variations in | -0.2330 0.2841 0.0517 0.0335 0.0299 |
| Variations in | 1.1535 1.1623 1.1556 1.1386 1.1667 |
References
- Chen et al. (2010) X. Chen, B. Zeng, Z.-C. Gu, I. L. Chuang, and X.-G. Wen, Phys. Rev. B 82, 165119 (2010).
- Şahinoğlu et al. (2014) M. B. Şahinoğlu, D. Williamson, N. Bultinck, M. Mariën, J. Haegeman, N. Schuch, and F. Verstraete, arXiv preprint arXiv:1409.2150 (2014).
- Fannes et al. (1992) M. Fannes, B. Nachtergaele, and R. Werner, Communications in Mathematical Physics 144, 443 (1992), 10.1007/BF02099178.
- White (1993) S. R. White, Phys. Rev. B 48, 10345 (1993).
- Verstraete et al. (2008) F. Verstraete, V. Murg, and J. Cirac, Advances in Physics 57, 143 (2008).
- Vidal (2009) G. Vidal, ArXiv e-prints 0912.1651 (2009), arXiv:0912.1651 [cond-mat.str-el] .
- Levin and Wen (2005) M. A. Levin and X.-G. Wen, Phys. Rev. B 71, 045110 (2005), cond-mat/0404617 .
- Gu et al. (2009) Z.-C. Gu, M. Levin, B. Swingle, and X.-G. Wen, Phys. Rev. B 79, 085118 (2009), arXiv:0809.2821 [cond-mat.str-el] .
- Buerschaper et al. (2009) O. Buerschaper, M. Aguado, and G. Vidal, Phys. Rev. B 79, 085119 (2009).
- Yan et al. (2011) S. Yan, D. A. Huse, and S. R. White, Science 332, 1173 (2011).
- Jiang et al. (2012) H.-C. Jiang, Z. Wang, and L. Balents, Nat Phys 8, 902 (2012).
- Depenbrock et al. (2012) S. Depenbrock, I. P. McCulloch, and U. Schollwöck, Phys. Rev. Lett. 109, 067201 (2012).
- Bravyi et al. (2010) S. Bravyi, M. B. Hastings, and S. Michalakis, Journal of Mathematical Physics 51, 093512 (2010).
- Buerschaper (2014) O. Buerschaper, Annals of Physics 351, 447 (2014), arXiv:1307.7763 [cond-mat.str-el] .
- Kitaev and Preskill (2006) A. Kitaev and J. Preskill, Phys. Rev. Lett. 96, 110404 (2006).
- Levin and Wen (2006) M. Levin and X.-G. Wen, Phys. Rev. Lett. 96, 110405 (2006).
- Gu et al. (2008) Z.-C. Gu, M. Levin, and X.-G. Wen, Phys. Rev. B 78, 205116 (2008), arXiv:0806.3509 [cond-mat.str-el] .
- Kitaev (2003) A. Kitaev, Annals of Physics 303, 2 (2003).
- Schuch et al. (2010) N. Schuch, I. Cirac, and D. Pérez-García, Annals of Physics 325, 2153 (2010), arXiv:1001.3807 [quant-ph] .
- Cirac et al. (2011) J. I. Cirac, D. Poilblanc, N. Schuch, and F. Verstraete, Phys. Rev. B 83, 245134 (2011).
- Flammia et al. (2009) S. T. Flammia, A. Hamma, T. L. Hughes, and X.-G. Wen, Phys. Rev. Lett. 103, 261601 (2009).
- Dong et al. (2008) S. Dong, E. Fradkin, R. G. Leigh, and S. Nowling, Journal of High Energy Physics 5, 016 (2008), arXiv:0802.3231 [hep-th] .
- Zhang et al. (2012) Y. Zhang, T. Grover, A. Turner, M. Oshikawa, and A. Vishwanath, Phys. Rev. B85, 235151 (2012), arXiv:1111.2342 [cond-mat.str-el] .
- Vidal (2003) G. Vidal, Phys. Rev. Lett. 91, 147902 (2003).
- Note (1) Not to be confused with TNR that we use for referring to tensor network representation.
- Evenbly and Vidal (2015) G. Evenbly and G. Vidal, Phys. Rev. Lett. 115, 180405 (2015).
- Freedman et al. (2004) M. Freedman, C. Nayak, K. Shtengel, K. Walker, and Z. Wang, Annals of Physics 310, 428 (2004).