Coded Event-triggered Control for Nonlinear Systems
Abstract
This paper studies a Coded Event-triggered Control (CEC) for a class of nonlinear systems under any initial condition. To reduce communication burden, the CEC is designed from the encoding-decoding viewpoint by which only -length string is transmitted for each communication between CEC and actuator. If a more general Entry Capture Problem is encountered, such control design will be rather complicated yet challenging where the performance constraints are satisfied some time after (rather than from the beginning of) system operation, rendering normally employed prescribed performance control invalid because they may be not defined in the initial interval. By introducing auxiliary functions, we develop a Self-adjustable Prescribed Performance (SPP) mechanism which can flexibly adjust the symmetric or asymmetric performance boundaries to accommodate different initial conditions, providing an effective solution for the underlying tracking problem. In this way, the resulted CEC can not only consume less communication resources but also regulate the tracking error under any initial condition into an allowable set before a given time in a bounded and customizable manner. Simulation results verify and clarify the theoretical findings.
keywords:
Coded event-triggered control; Self-adjustable prescribed performance; Nonlinear systems; Auxiliary functions., ,
1 Introduction
Practical systems often operate under limited computational loads but need to maintain certain performance constraints, arising from hardware capability and task requirements, for example, the target tracking problem of aerial robots or the manipulator grasping. Nowadays, event-based control has enticed sustained interest due to its resource efficiency (Wang & Krstic (2022); Åarzén (1999); Åström & Bernhardsson (1999); Heemels et al. (2012); Deng et al. (2022); Sun et al. (2022); Liu et al. (2023)). As systems grow in complexity, how to save communication resources and guarantee system performance at the same time deserve more in-depth studies.
The event-based control is pioneered in Åarzén (1999); Åström & Bernhardsson (1999), which emphasizes its advantages over periodic sampling and motivates its systematic design later (Tabuada (2007)). Since then, it has aroused widespread research interest, see, Dimarogonas et al. (2011); Fan et al. (2013); Girard (2014); Xing et al. (2016); Kumari et al. (2020); Zhang, Wen, Zhao & Song (2022) and references therein. However, most existing protocols primarily focus on reducing unnecessary signal transmission but neglect the encoding-decoding process and the associated security concerns for each communication between the control box and the actuator. In practice, when the event condition is met, the real control input is encoded into a lengthy codeword (i.e., 16 bits) before transmission. This could aggravate communication delays and congestion issues due to the limited bandwidth, particularly when communication bits are critical. Moreover, exposing sensitive system signals to public channels raises security concerns. This motivates us to further study event-triggered control from an encoding-decoding viewpoint, and the following two aspects need to be considered:
-
(i)
Resource saving. It might be redundant to transmit such a large number of digits for each communication between control box and actuator, especially when the magnitude of control signal is small. Moreover, in situations where the communication channel can only handle a limited number of bits at a time, lengthy strings for communication can lead to transmission delays and increase vulnerability to packet losses (Mazo Jr & Cao (2014); Ding et al. (2017)). Therefore, it is critical to further save communication resources from the encoding-decoding scheme viewpoint.
-
(ii)
Performance maintenance. Considering the error induced by the event-trigger scheme, it may degrade the tracking performance. By the prescribed performance control (Bechlioulis & Rovithakis (2008); Zhao et al. (2017); Ji, Li, Ma & Ge (2022); Bu et al. (2023), to name a few), the studies of event-triggered control with prescribed performance have been investigated in (Liu et al. (2020); Zhang & Yang (2020); Zhang, Che, Deng & Wu (2022)). These results are based on an implicit assumption that the prescribed performance should be satisfied from the beginning of system operation. However, in practice, the system’s initial conditions often violate the initial performance constraints, rendering these existing methods inapplicable since they are not defined outside the allowable set and the singularity problem is encountered. Therefore, how to develop an event-triggered control with prescribed performance applicable for any initial conditions is still an open problem.
To handle the first problem, one excellent work in Xing et al. (2018) proposes a 1-bit communication protocol for the relative threshold. Note that this protocol is unable to promptly respond to signal changes due to the high threshold when control inputs are extremely large. As stated in Xing et al. (2018), the original control signals need to be transmitted sometimes to re-calibrate the decoder due to the signal distortion problem. The other work in Zhang et al. (2020) studies a 2-bit strategy, switching between fixed and relative thresholds based on the magnitude of control inputs. Therefore, the transmissions of control inputs between control and actuator are necessary, which aggravates the communication burden, especially when the bandwidth is limited. Moreover, all these communication protocols are only applicable to binary systems, limiting their implementation in practice. How to design an effective coded event-triggered scheme for more general base- number systems to address the above problems is interesting yet challenging.
For the second problem, the funnel boundary (Ilchmann et al. (2002); Berger et al. (2022)), the global performance functions (Zhao et al. (2021); Chen & Hua (2020)), and tuning functions Zhang et al. (2021); Ji et al. (2023) can remove such initial limitations. However, several limitations are observed: (i) The global tracking abilities of funnel boundary and the global prescribed functions are achieved by sacrificing overshoot performance. As their initial performance tends to infinity, it leads to loose performance constraints. (ii) These two methods are only suitable for symmetric performance distribution and rely on specific performance functions, which limits their extensions to more general cases. (iii) Although tuning functions are studied to address a more practical yet challenging Entry Capture Problem, there are no performance constraints on tracking errors during the initial interval. This could lead to potential operational and safety issues. Therefore, how can we regulate any initial tracking error into the allowable set in a bounded and customized manner makes our control design more complicated.
In this paper, we propose a CEC and a SPP to reduce the communication resources between control and actuator while addressing the Entry Capture Problem for a class of nonlinear systems. The main contributions lie in:
-
(i)
We design a CEC, by which only -length string of base- number system is transmitted for each communication between control box and actuator. Compared with the existing event-triggered results, the CEC can further reduce the communication burden specifically from the encoding-decoding viewpoint.
-
(ii)
Different from Zhao et al. (2021); Zhang et al. (2021); Berger et al. (2022), the proposed SPP can flexibly adjust its performance boundaries in accordance with different initial conditions by introducing auxiliary functions. This feature offers an effective solution to make the control design applicable to any initial conditions, which can be easily extended to other methods.
-
(iii)
With the aid of SPP, for any initial condition (including initial-constraint violation), the resulted CEC can handle the Entry Capture Problem for either symmetric or asymmetric performance constraints, by which the tracking error is regulated into an allowable set before a given time in a bounded yet customizable manner rather than no constraints there. In this way, the initial-condition constraints are removed and better transient performance is achieved.
2 Problem Formulation and Preliminaries
2.1 Problem statement
Consider a class of strict-feedback nonlinear systems
| (4) |
where , , is the system state with , is an unknown but continuous function, denotes an unknown time-varying control coefficient, and are system input and output, respectively.
Define the tracking error with being the desired trajectory. The control objective is to design a CEC for the nonlinear systems (4) under any initial condition such that:
-
(i)
All signals in the closed-loop systems are bounded;
-
(ii)
Only a coded -length string is required for each communication between CEC and actuator when the event-trigger condition is satisfied; and
-
(iii)
For any initial condition, the tracking error can be regulated into the prescribed allowable set in a customizable manner before a given time and then be constrained within there.
Definition 1.
For any initial tracking condition (including initial constraint violation), if the tracking error is fully constrained by the prescribed performance boundaries right after a user-given settling time :
| (5) |
then, such error tracking performance is said to be Entry Capture Problem, where and denote lower and upper prescribed boundaries, respectively.
Remark 1.
The studied Entry Capture Problem represents a frequently encountered tracking situation that the prescribed performance is involved right after a given time , whereas, in most existing works, these performance constraints should be satisfied from the beginning of system operation. One typical example is a flight system which is often released from any condition (including initial-constraint violation), but is required to track and interact with a target in prescribed performance for successful task completion. Therefore, addressing such Entry Capture Problem is interesting yet more challenging since it needs the control design applicable for more general cases.
Assumption 1.
The desired trajectory and its time derivatives up to th-order are known, bounded, and piece-wise continuous.
Assumption 2.
The nonlinear function , , is unknown but certain crude information is available so that , , where is an unknown constant and is a known smooth function.
Assumption 3.
The control coefficient , ,is unknown and time-varying, but away from zero, that is, there exist positive constants and such that . Without loss of generality, we assume that the signs of are known and all positive.
Remark 2.
Assumption 1 is widely adopted in tracking control of nonlinear systems (Krstic et al. (1995)). Assumption 2 indicates that some core functions can be easily extracted only based on some crude system information, which is reasonable and in line with practice (Polycarpou & Ioannou (1993). Assumption 3 is necessary to guarantee the controllable condition of nonlinear system (4), which is made in most control design (Jin (2018)).
3 Main Results
3.1 Coded Event-triggered Scheme
With respect to the second objective of CEC, we introduce a Coded Event-triggered Scheme (CES) as follows:
| (6) | |||
| (7) |
where is the actual control to be developed, denotes the control signal error, represents the update time, is an even number leading to base- system (i.e., Binary, Octal number system), the selections of and adopt the following rules:
| (8) | |||
| (11) | |||
| (12) |
where , with being the length of encoded string to be transmitted, as such as there are variations, we specify to measure the level of control input, are positive constants chosen by designers, and denotes each digit value of base- number system at -th updated time. From the triggering condition in (7), it becomes essential to determine the sign of for accurate encoding-decoding procedures. As shown in the encoding procedure (11) and the later decoding procedure (16), it indicates that if , let , otherwise, . Therefore, supposing , , the encoded string , used for the communication between control and actuator, is constructed by
| (13) |
where is a -length string to be transmitted whenever the criteria in (7) is satisfied. Based on (7) and (11), can be seen as a sign-and-magnitude representation of the threshold for the control signal error . More specifically, denotes a sign digit, whose value determines the sign of (i.e., and ); and the magnitude of the threshold for is derived by the remaining digital numbers, i.e., .
If CES in (7) is satisfied at , is expected to be broadcasted to the actuator. When the actuator receives , it adopts the following decoder process to update with the aid of the last control input and parameters stored:
| (16) |
where , and the selections of and follow the same rules in (8)-(12), which are also stored in the actuator. Based on the triggering condition in (7) and the decoder rule in (16), it can be derived that . Throughout this paper, we only use to simplify the control design. In summary, the CES is illustratively described in Fig. 1.
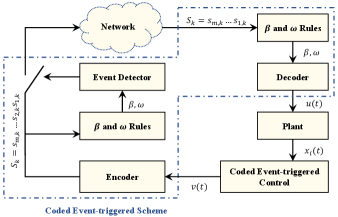
To clearly illustrate the CES, we give a simple case with and . This results in a Binary number system and -bit binary string is used for each communication between CEC and actuator, where each digit value of Binary number system has a value of either 1 or 0. The encoding and decoding processes in (13) and (16) are executed as shown in Table 1 whenever the condition in (7) is triggered.
| Encoder | Decoder |
|---|---|
| , , , | |
| , , , | |
| , , , | |
| , , , | |
| , , , | |
| , , , | |
| , , , | |
| , , , |
Some salient features of such CES can be observed from the following aspects.
-
(i)
Considering the relative threshold in Xing et al. (2018) with , it is unable to promptly respond to signal changes due to the high threshold when is extremely large. This signal distortion often degrades tracking performance. A switching threshold scheme is proposed in Xing et al. (2016) which switches between fixed and relative thresholds based on the magnitude of control input. However, it indicates that the transmission of raw control input between control and actuator is necessary, which aggravates the communication burden, especially when the bandwidth is limited. Therefore, our CES is designed from an encoding-decoding viewpoint by which only a concise m-length string is transmitted for each communication instead of the raw control input and can be chosen by designers. It not only reduces the bandwidth required but also provides a balanced strategy between system performance and network constraints. Please find the following critical point for more details.
-
(ii)
Different from the fixed threshold in Xing et al. (2016); Kumari et al. (2020); Zhang, Wen, Zhao & Song (2022) and the above relative threshold where thresholds are either constants or increase monotonically with , the proposed CES adopts a piecewise increasing threshold related to and tends to a constant threshold when is excessively large. This dynamic threshold facilitates more accurate tracking performance due to the lower threshold when is small, and ensures a rapid response to the signal’s change when is large with the aid of the constant threshold. Therefore, the signal distortion problem commonly observed in fixed and relative thresholds is effectively alleviated since our CES has a good balance between system performance and resource constraints. Comparative simulations are conducted in Section 6 to illustrate the effectiveness of our CES. Moreover, the fixed threshold can be seen as a special case of our CES if we set and in (7).
-
(iii)
The excellent work in Xing et al. (2018) also studies a 1-bit communication protocol for the relative threshold scheme. However, the original control input needs to be transmitted sometimes to re-calibrate the decoder due to the severe signal distortion as the aforementioned discussed. In this paper, our CES not only alleviates the signal distortion problem but also addresses the challenge of co-designing an event-trigger scheme with encoding-decoding rules. As a result, the CES provides a leaner communication protocol, which is friendly for practical systems with limited communication bit resources. On the other hand, by encrypting the control signal into an encoded string , we inherently improve communication security against potential cyber threats without the knowledge of encoding-decoding rules.
3.2 Auxiliary Functions
To deal with the third control objective of this article, we first introduce the definition of auxiliary functions.
Definition 2.
Auxiliary functions and are scalar functions which satisfies the following properties:
-
(i)
and , , are known, continuous, and bounded;
-
(ii)
and ;
-
(iii)
, , , as , where is the settling time in (5); and
-
(iv)
, and , .
Obviously, there exist many candidates satisfying these properties, for example,
| (19) | |||
| (22) |
where and are positive constants, and denote the initial values of performance constraints and which will be defined in the next section. Throughout this paper, we use the above functions as the auxiliary functions.
Remark 3.
More details about the motivation of such auxiliary functions are provided here. From the third objective in section 2.1, the control scheme should be adapted to any initial condition. However, in practice, the initial condition may violate the performance constraints initially, rendering most existing PPC methods inapplicable since they are not defined and suffer from singularity problem in such scenario. To handle this problem, a straightforward approach is to utilize these auxiliary functions to adjust the performance boundaries in accordance with the initial condition. By leveraging the second property in Definition 2, any given initial condition would remain within an updated and allowable set, thereby ensuring the applicability of the control method. Other properties are also crucial for system analysis under addressing the Entry Capture Problem (5). Moreover, there would be fruitful expressions of such additional auxiliary functions which facilitate their extension to other control approaches.
3.3 Self-adjustable Prescribed Performance
We design the following Self-adjustable Prescribed Performance (SPP) on the tracking error by introducing the above auxiliary functions into the performance boundaries:
| (23) |
with
| (24) | |||
| (25) |
where and represent the original upper and lower Tunnel Prescribed Performance (TPP) (Ji, Li & Ge (2022)), which are given by:
| (26) | |||
| (27) |
where , , with and .
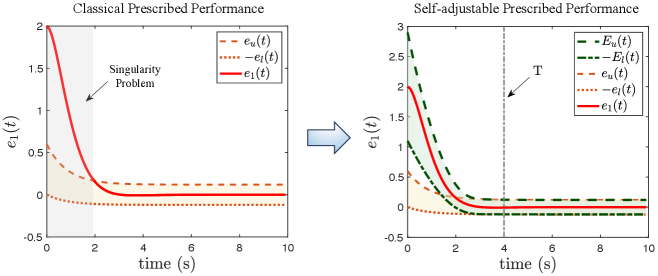
To better illustrate the mechanism behind such SPP, we take as an example. The parameters of SPP (24)-(25) are selected as: , , , , , , , and the initial tracking condition is . As shown in the left plot of Fig. 2, the initial tracking error violates the original allowable set established by and , which is colored in brown. It renders the previous methods inapplicable due to the singularity problem encountered. With the aid of the auxiliary functions, SPP is capable of re-adjusting the performance boundaries according to different initial conditions such that is always within the updated allowable set initially (i.e., ) as shown in the right plot of Fig. 2 in green color. During the initial time interval (), our SPP not only ensures the control method applicable for any initial conditions but also provides temporary performance constraints on the tracking error. When , SPP is equivalent to the original performance boundaries, that is, and since as depicted in the right figure. Therefore, SPP provides an effective solution for the underlying Entry Capture Problem (5) as stated in the following lemma.
Lemma 1.
If holds for all , then the Entry Capture Problem (5) is obtained.
Proof.
When , the boundedness of and is guaranteed according to Definition 2. By (26)-(27), the original TPP is also bounded there. It ensures that is bounded on . When , we have which can be rewritten as . If the above statement holds, the Entry Capture Problem is, therefore, addressed by invoking Definition 1. ∎
From the above discussion, the control objective is successfully transfered to guarantee evolving within the SPP envelope (23) to deal with the issue of Entry Capture Problem.
Remark 4.
In comparison with funnel boundary (Berger et al. (2022)), global prescribed performance (Zhao et al. (2021); Zhang et al. (2021)) and tuning functions (Zhang et al. (2021); Ji et al. (2023)), some salient features of the proposed SPP (23) are observed as follows:
-
(i)
(Improved transient performance) The funnel boundary and global prescribed performance often encounter an overshoot problem, as their initial performance constraints tend to infinity leading to a loose allowable set. Similarly, by tuning functions, there are no constraints on tracking errors during the initial interval, which is undesirable in practice due to safety concerns and task demands. Different from these methods, our SPP is capable of adjusting performance boundaries with the help of auxiliary functions such that the proposed control scheme can be applied to any initial condition even if the initial constraints are violated. It provides bounded yet customizable virtual performance boundaries during the initial interval as depicted in Fig. 2, effectively avoiding the aforementioned severe overshoot performance and unconstrained behaviors. The tracking error is regulated into the allowable set within finite time and Entry Capture Problem is therefore solved.
-
(ii)
(Flexibility and Extendibility) Our SPP allows for an easy extension to other control methods by integrating the introduced auxiliary functions into the performance boundaries as formulated in (23)-(25). However, the funnel boundary and global prescribed performance rely on specific performance functions, which limits their adaptability to other control methods. Moreover, the previous methods are limited to symmetric performance distributions but the proposed SPP is applicable to both symmetric and asymmetric cases, thereby enhancing its applicability to more general cases. In this paper, we employ asymmetric TPP as the baseline, which not only provides a tighter allowable set but also limits overshoot performance during the initial interval of the Entry Capture Problem.
4 Coded Event-triggered Control for Second-order System
To clearly illustrate our design methodology, we first consider the following second-order nonlinear system:
| (30) |
where and are system states, and , , are unknown yet smooth nonlinear functions satisfying Assumptions 2-3, and denotes the system control input.
Step 1: We first define the tracking errors:
| (31) | |||
| (32) |
where represents the virtual control input to be defined shortly. In order to guarantee satisfying SPP (23) for all , we introduce the following error transformation function
| (33) |
then, by invoking (24)-(25) and (32), its time derivative is
| (34) |
where and and . From (24)-(27) and the property (iv) in Definition 2, it can be derived that and are bounded functions for in the compact set . Therefore, we have and . Then, the time derivative of along (34) is:
| (35) |
where . Upon using Assumptions 1-3 and Young’s inequality, we have
| (36) | |||
| (37) | |||
| (38) | |||
| (39) |
Therefore, in (4) is bounded by
| (40) |
with
| (41) | |||
| (42) |
We develop the virtual control input as
| (43) | |||
| (44) |
where , , and are positive constants, and is the estimation of .
Consider the following Lyapunov function
where . Then, from (4), (40), (43) and (44), its time derivative can be derived as
Based on the definition of , it yields
We then have
| (45) |
where and is a bounded signal. Notice that the item will be tackled in the next step.
Step 2: From (30) and (32), the time derivative of is
| (46) |
with
| (47) |
where , which is computable. According to the definition of , we can obtain
| (48) |
where is a positive constant. We then consider the Lyapunov function :
| (49) |
where , is the estimation of in (53), and is a positive constant. The time derivative of , along (46)-(48), is derived
| (50) |
where . Using Young’s inequality, we can also expand as inequalities in (36)-(39). Note that the control input signal will be updated whenever the coded event-triggered scheme (7) is triggered, which indicates that holds. As , and are all bounded numbers, from (48), it can be derived that is a bounded constant, leading to:
| (51) |
It yields that
| (52) |
where
| (53) | |||
| (54) |
To move forward, the actual control is developed as
| (55) | |||
| (56) |
where and is the estimation of . By (52)-(56), the inequality (4) can be rewritten as
| (57) |
Based on the definition of , we obtain
| (58) |
By substituting (58) into (4) yields
| (59) |
where and .
To summarize, we establish the following theorem.
Theorem 1.
Consider the second-order nonlinear system (30) under Assumptions 1-3. The virtual control and the actual control input are developed in (43) and (55). The adaptive laws are given by (44) and (56). Following the Coded Event-triggered Scheme (6)-(7), the proposed control method guarantees the following.
-
(i)
The tracking error satisfies Entry Capture Problem property since it is strictly constrained by the prescribed performance: right after an user-given finite time as presented in Definition 1;
-
(ii)
All signals in the closed-loop system are guaranteed to be bounded regardless of initial conditions; and
-
(iii)
Zeno behavior is excluded.
Proof.
By revisiting (59), there is
where . Subsequently, we can have
It can be concluded that is bounded which guarantees the boundedness of , , , and . From the error transformation function in (33), it is certain that holds due to . According to Lemma 1, satisfies for , which indicates that follows the Entry Capture Problem in Definition 1.
Next, other tracking signals in the closed-loop system are proved to be bounded. Considering the adaptive laws (44) and (56), and remain bounded. The virtual control input defined in (43) belong to . Moreover, by (55), the boundedness of actual control signal is guaranteed. From (31) and (32), it can be derived that and also keep bounded. All the closed-loop signals are therefore bounded for the second-order nonlinear system under any initial condition.
To illustrate the exclusion of Zeno behavior, the time derivative of during the inter-execution interval is given
where By (55), it yields . In accordance with Assumptions 1-3, Definition 2, prescribed performance functions and defined in (26)-(27), and the fact that governed by (46) and other closed-loop signals remain bounded, the boundedness of is ensured. For convenience, the upper bound of can be specified by a positive constant . Therefore, we can obtain
where Given that and , it indicates that there exists a strictly positive constant such that
with denoting minimal inter-transmission interval. Thereby, the Zeno behavior is excluded and the proof is completed. ∎
5 Coded Event-triggered Control for high-order System
In this section, the proposed CEC will be extended to th-order systems (4). Instead of step-by-step procedure, its control design is omitted here for conciseness since its stability analysis is identical to the second-order system (30).
We first define the tracking error variables:
| (60) | |||
| (61) |
where represent virtual control inputs. In order to guarantee fulfilling the Self-adjustable Prescribed Performance (23), we introduce the following error transformation function:
| (62) |
Then, the virtual control inputs are designed as
| (63) | |||
| (64) |
and the adaptive laws are updated by
| (65) | |||
| (66) |
for , where , and , , are positive constants. is the estimation of , and is a computable function, where and are
| (67) | |||
| (68) | |||
| (69) | |||
| (70) |
where and and . We can also derived that and are bounded functions if belongs to a compact set . Therefore, we have and . Identically, the actual control input and the adaptive law are developed:
| (71) | |||
| (72) |
where , denotes the estimation of and is a computable function. Similar to (67)-(70), we have
| (73) | |||
| (74) |
In the following theorem, we summarize the result on the Coded Event-triggered Control for the th-order nonlinear systems.
Theorem 2.
Consider th-order nonlinear systems (4) under Assumptions 1-3. If the control inputs and the adaptive laws are designed as (67)-(72), by adopting the Coded Event-triggered Scheme (6)-(7), we can guarantee the following properties:
-
(i)
Given any initial condition, the tracking error is constrained by the prescribed performance: , for with being a preassigned finite time, that is, fulfills Entry Capture Problem properties in Definition 1;
-
(ii)
All signals in the closed-loop system are guaranteed to be bounded regardless of initial conditions;
-
(iii)
Zeno behavior is excluded.
Proof.
Consider the following Lyapunov candidates:
where . Similar to the stability analysis in Theorem 1, it can be also derived:
where , . In accordance with (6)-(7), we have , where is a bounded constant. Then, we obtain
It indicates that is bounded, leading to , , . According to the error transformation function (62), we can derive that is evolving within the SPP, namely, . Based on Lemma 1, the Entry Capture Problem is achieved, that is, for all .
Next, the boundedness of other signals in the closed-loop system is proved. From (65)-(67) and (72)-(73), and the definition of , it leads to and , for . By (63)-(64) and (71), the boundedness of control input signals is guaranteed. Considering (60)-(61), belong to . Therefore, all signals in the closed-loop system are bounded.
To verify the exclusion of Zeno phenomenon, the time derivative of before next triggering is given
where By invoking (71), there has . Since all the signals in the closed-loop system are bounded, from Assumptions 1-3, Definition 2, prescribed performance functions and defined in (26)-(26), is, therefore, bounded by
where Given that and , it indicates that there exists a strictly positive constant such that
with being the minimal inter-transmission interval. Thereby, the Zeno behavior is excluded and proof is completed. ∎
Remark 5.
We provide a guideline for the parameter selections. For the settling time in (5), its value should satisfy where is the minimum time necessary for signal processing. This assumption is widely used in existing results Zhao et al. (2021); Song & Zhou (2018). If is chosen too small, although faster convergence, it could lead to large control signals. Considering the control parameters and , their values will determine the convergence rate and tracking accuracy. Note that their extreme values may lead to large control inputs, making systems sensitive to external disturbances. Therefore, these parameters’ selections should consider the balance between tracking performance and system ability.
6 Simulation Results
To illustrate the effectiveness of our proposed CEC, some comparative simulations are conducted in this section. Consider the following second-order nonlinear system:
| (77) |
where , , , and . By Assumption 2, it can be derived that with and , and with and . The initial condition is set by and . The desired tracking trajectory is . The control parameters are selected as: (i.e., and ), , , , , , , , , , , and . Moreover, our CEC is compared with our control design with relative threshold Xing et al. (2018) and switching threshold Xing et al. (2016).
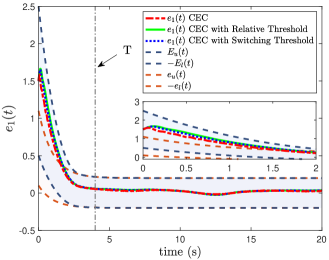
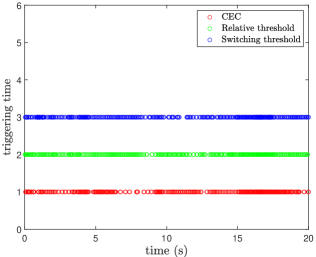
(Case I) The simulation results of our CEC under different threshold strategies are shown in Figs. 3-4. From Fig. 3, the initial tracking error violates the initial performance constraints colored in brown, leading to the classical prescribed control methods being inapplicable. By our CEC, we can regulate into the allowable set within the given time . With the aid of SPP, bounded yet customizable virtual performance boundaries are established during the initial interval as shown in blue color. Therefore, the severe overshoot or unconstrained behaviors over are effectively avoided. On the other hand, the triggering time of three threshold strategies is shown in Fig. 4, and the number of triggering events and bit assumptions are summarized in the second and third columns of Table 2, in which we exclude the initial signal transmission. Due to in the CES, it indicates that only a 3-bit string is transmitted for each communication when the event condition is satisfied. Compared with the relative threshold and the switching threshold where control inputs should be encoded by 8-bit strings before each transmission, our CES consumes fewer bits while maintaining the tracking performance, which is significant for the practical system with limited communication bandwidth.
| Case I | Case II | |||
| different strategies | trigger number | bit consumption | trigger number | bit consumption |
| CES | 332 | 996 | 460 | 1380 |
| Relative threshold | 339 | 2712 | X | X |
| Switching threshold | 373 | 2984 | 403 | 3224 |
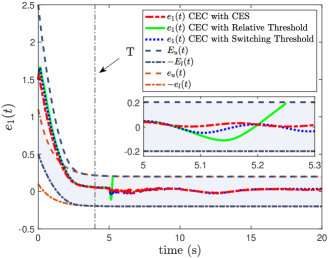
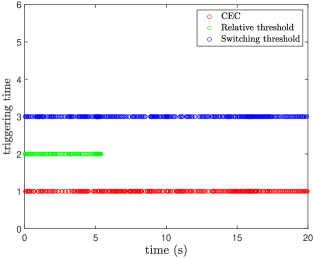
(Case II) To further illustrate the effectiveness of our CES, we consider the introduction of external disturbance during 5-10s in the second row of (77). The comparative results under different threshold strategies are shown in Figs. 5-6. Due to the signal distortion problem associated with the relative threshold strategy as discussed in Section 3.1, the tracking performance is severely degraded with depicted by the green line violating performance constraints at 5.24s, as illustrated in Fig. 5. It makes the control design suffer from the singularity problem. Note that our CES and switching threshold strategy accomplish a good balance between tracking performance and network constraints. Therefore, they can guarantee the tracking errors within the allowable set even the introduced external disturbances. However, from the fourth and fifth columns of Table 2 and the triggering time in Fig. 6, our CES strategy can consume fewer bit resources compared to the switching threshold one. On the other hand, for each communication case, we only transmit an encrypted -bit string through the public network rather than the sensitive real control input in the switching threshold strategy. Therefore, our control design reduces the communication burden and addresses the security concern at the same time.
7 Conclusion
A Coded Event-triggered Control has been designed for a class of nonlinear systems under any initial condition. We have shown that such control method can not only consume less communication bandwidth, but also enhance secure communication capability, since only -length string is encoded and transmitted for each communication. An effort has been also made on developing Self-adjustable Prescribed Performance such that the initial condition-dependence restriction is removed, allowing the Entry Capture Problem to be collectively addressed. Note that our communication protocol is based on the magnitude of control input. In the future, we would like to design the protocol from the changing rate of the control signal to further enhance the tracking performance.
References
- (1)
- Åarzén (1999) Åarzén, K.-E. (1999), ‘A simple event-based pid controller’, IFAC Proceedings Volumes 32(2), 8687–8692.
- Åström & Bernhardsson (1999) Åström, K. J. & Bernhardsson, B. (1999), ‘Comparison of periodic and event based sampling for first-order stochastic systems’, IFAC Proceedings Volumes 32(2), 5006–5011.
- Bechlioulis & Rovithakis (2008) Bechlioulis, C. P. & Rovithakis, G. A. (2008), ‘Robust adaptive control of feedback linearizable mimo nonlinear systems with prescribed performance’, IEEE Transactions on Automatic Control 53(9), 2090–2099.
- Berger et al. (2022) Berger, T., Puche, M. & Schwenninger, F. L. (2022), ‘Funnel control for a moving water tank’, Automatica 135, 109999.
- Bu et al. (2023) Bu, X., Lv, M., Lei, H. & Cao, J. (2023), ‘Fuzzy neural pseudo control with prescribed performance for waverider vehicles: A fragility-avoidance approach’, IEEE Transactions on Cybernetics .
- Chen & Hua (2020) Chen, J. & Hua, C. (2020), ‘Adaptive full-state-constrained control of nonlinear systems with deferred constraints based on nonbarrier lyapunov function method’, IEEE Transactions on Cybernetics 52(8), 7634–7642.
- Deng et al. (2022) Deng, C., Wen, C., Wang, W., Li, X. & Yue, D. (2022), ‘Distributed adaptive tracking control for high-order nonlinear multi-agent systems over event-triggered communication’, IEEE Transactions on Automatic Control .
- Dimarogonas et al. (2011) Dimarogonas, D. V., Frazzoli, E. & Johansson, K. H. (2011), ‘Distributed event-triggered control for multi-agent systems’, IEEE Transactions on Automatic Control 57(5), 1291–1297.
- Ding et al. (2017) Ding, L., Han, Q.-L., Ge, X. & Zhang, X.-M. (2017), ‘An overview of recent advances in event-triggered consensus of multiagent systems’, IEEE transactions on cybernetics 48(4), 1110–1123.
- Fan et al. (2013) Fan, Y., Feng, G., Wang, Y. & Song, C. (2013), ‘Distributed event-triggered control of multi-agent systems with combinational measurements’, Automatica 49(2), 671–675.
- Girard (2014) Girard, A. (2014), ‘Dynamic triggering mechanisms for event-triggered control’, IEEE Transactions on Automatic Control 60(7), 1992–1997.
- Heemels et al. (2012) Heemels, W. P., Johansson, K. H. & Tabuada, P. (2012), An introduction to event-triggered and self-triggered control, in ‘2012 ieee 51st ieee conference on decision and control (cdc)’, IEEE, pp. 3270–3285.
- Ilchmann et al. (2002) Ilchmann, A., Ryan, E. P. & Sangwin, C. J. (2002), ‘Tracking with prescribed transient behaviour’, ESAIM: Control, Optimisation and Calculus of Variations 7, 471–493.
- Ji, Li & Ge (2022) Ji, R., Li, D. & Ge, S. S. (2022), ‘Saturation-tolerant prescribed control for nonlinear time-delay systems’, IEEE Transactions on Fuzzy Systems .
- Ji et al. (2023) Ji, R., Li, D., Ge, S. S. & Li, H. (2023), ‘Tunnel prescribed control of nonlinear systems with unknown control directions’, IEEE Transactions on Neural Networks and Learning Systems .
- Ji, Li, Ma & Ge (2022) Ji, R., Li, D., Ma, J. & Ge, S. S. (2022), ‘Saturation-tolerant prescribed control of mimo systems with unknown control directions’, IEEE Transactions on Fuzzy Systems .
- Jin (2018) Jin, X. (2018), ‘Adaptive fixed-time control for mimo nonlinear systems with asymmetric output constraints using universal barrier functions’, IEEE Transactions on Automatic Control 64(7), 3046–3053.
- Krstic et al. (1995) Krstic, M., Kokotovic, P. V. & Kanellakopoulos, I. (1995), Nonlinear and adaptive control design, John Wiley & Sons, Inc.
- Kumari et al. (2020) Kumari, K., Bandyopadhyay, B., Reger, J. & Behera, A. K. (2020), ‘Event-triggered sliding mode control for a high-order system via reduced-order model based design’, Automatica 121, 109163.
- Liu et al. (2020) Liu, X., Su, X., Shi, P., Shen, C. & Peng, Y. (2020), ‘Event-triggered sliding mode control of nonlinear dynamic systems’, Automatica 112, 108738.
- Liu et al. (2023) Liu, Y.-J., Xu, F. & Tang, L. (2023), ‘Tangent barrier lyapunov function based adaptive event-triggered control for uncertain flexible beam systems’, Automatica 152, 110976.
- Mazo Jr & Cao (2014) Mazo Jr, M. & Cao, M. (2014), ‘Asynchronous decentralized event-triggered control’, Automatica 50(12), 3197–3203.
- Polycarpou & Ioannou (1993) Polycarpou, M. M. & Ioannou, P. A. (1993), A robust adaptive nonlinear control design, in ‘1993 American control conference’, IEEE, pp. 1365–1369.
- Song & Zhou (2018) Song, Y.-D. & Zhou, S. (2018), ‘Tracking control of uncertain nonlinear systems with deferred asymmetric time-varying full state constraints’, Automatica 98, 314–322.
- Sun et al. (2022) Sun, J., Yang, J. & Zeng, Z. (2022), ‘Predictor-based periodic event-triggered control for nonlinear uncertain systems with input delay’, Automatica 136, 110055.
- Tabuada (2007) Tabuada, P. (2007), ‘Event-triggered real-time scheduling of stabilizing control tasks’, IEEE Transactions on Automatic control 52(9), 1680–1685.
- Wang & Krstic (2022) Wang, J. & Krstic, M. (2022), ‘Event-triggered adaptive control of coupled hyperbolic pdes with piecewise-constant inputs and identification’, IEEE Transactions on Automatic Control .
- Xing et al. (2016) Xing, L., Wen, C., Liu, Z., Su, H. & Cai, J. (2016), ‘Event-triggered adaptive control for a class of uncertain nonlinear systems’, IEEE Transactions on Automatic Control 62(4), 2071–2076.
- Xing et al. (2018) Xing, L., Wen, C., Liu, Z., Su, H. & Cai, J. (2018), ‘Event-triggered output feedback control for a class of uncertain nonlinear systems’, IEEE Transactions on Automatic Control 64(1), 290–297.
- Zhang et al. (2020) Zhang, C., Chen, Z., Wang, J., Liu, Z. & Chen, C. P. (2020), ‘Fuzzy adaptive two-bit-triggered control for a class of uncertain nonlinear systems with actuator failures and dead-zone constraint’, IEEE Transactions on Cybernetics 51(1), 210–221.
- Zhang et al. (2021) Zhang, J.-X., Wang, Q.-G. & Ding, W. (2021), ‘Global output-feedback prescribed performance control of nonlinear systems with unknown virtual control coefficients’, IEEE Transactions on Automatic Control .
- Zhang & Yang (2020) Zhang, J.-X. & Yang, G.-H. (2020), ‘Event-triggered prescribed performance control for a class of unknown nonlinear systems’, IEEE Transactions on Systems, Man, and Cybernetics: Systems 51(10), 6576–6586.
- Zhang, Che, Deng & Wu (2022) Zhang, L., Che, W.-W., Deng, C. & Wu, Z.-G. (2022), ‘Prescribed performance control for multiagent systems via fuzzy adaptive event-triggered strategy’, IEEE Transactions on Fuzzy Systems 30(12), 5078–5090.
- Zhang, Wen, Zhao & Song (2022) Zhang, Z., Wen, C., Zhao, K. & Song, Y. (2022), ‘Decentralized adaptive control of uncertain interconnected systems with triggering state signals’, Automatica 141, 110283.
- Zhao et al. (2021) Zhao, K., Song, Y., Chen, C. P. & Chen, L. (2021), ‘Adaptive asymptotic tracking with global performance for nonlinear systems with unknown control directions’, IEEE Transactions on Automatic Control 67(3), 1566–1573.
- Zhao et al. (2017) Zhao, K., Song, Y., Ma, T. & He, L. (2017), ‘Prescribed performance control of uncertain euler–lagrange systems subject to full-state constraints’, IEEE transactions on neural networks and learning systems 29(8), 3478–3489.