Composing Control Barrier Functions for Complex Safety Specifications
Abstract
The increasing complexity of control systems necessitates control laws that guarantee safety w.r.t. complex combinations of constraints. In this letter, we propose a framework to describe compositional safety specifications with control barrier functions (CBFs). The specifications are formulated as Boolean compositions of state constraints, and we propose an algorithmic way to create a single continuously differentiable CBF that captures these constraints and enables safety-critical control. We describe the properties of the proposed CBF, and we demonstrate its efficacy by numerical simulations.
I INTRODUCTION
Control designs with formal safety guarantees have long been of interest in engineering. Safety is often captured as constraints on the system’s states that must be enforced for all time by the controller. To enable the satisfaction of state constraints with formal guarantees of safety, control barrier functions (CBFs) [1] have become a popular tool in nonlinear control design. As the complexity of safety-critical control systems increases, complex combinations of multiple safety constraints tend to arise, which creates a need for controllers incorporating multiple CBFs.
The literature contains an abundance of studies on multiple safety constraints. Some approaches directly used multiple CBFs in control design. For example, [2, 3] directly imposed multiple CBF constraints on the control input in optimization-based controllers; [4] synthesized controllers by switching between multiple CBFs whose superlevel set boundaries do not intersect; [5] investigated the compatibility of CBFs; [6] ensured feasible controllers with multiple CBFs; and [7, 8] addressed multi-objective constraints via barrier Lyapunov functions. These works usually linked safety constraints with AND logic: they maintained safety w.r.t. constraint 1 AND constraint 2, etc. Other approaches combined multiple constraints into a single CBF. These include versatile combinations, such as Boolean logic with both AND, OR and negation operations, which was established in [9, 10] by nonsmooth barrier functions. Similarly, [11] used Boolean logic to create a smooth CBF restricted to a safe set in the state space; [12] combined CBFs with AND logic via parameter adaptation; while [13, 14] used signal temporal logic to combine CBFs in a smooth manner.
In this letter, we propose a framework to capture complex safety specifications by CBFs. We combine multiple safety constraints via Boolean logic, and propose an algorithmic way to establish a single CBF for nontrivial safety specifications. Our method leverages both the Boolean logic from [9] and the smooth combination idea from [13], while merging the benefits of these approaches. We address multiple levels of logical compositions of safety constraints, i.e., arbitrary combinations of AND and OR logic, which was not established in [13], while we create a continuously differentiable CBF to avoid discontinuous systems like in [9]. Meanwhile, as opposed to [11], the stability of the safe set is guaranteed.
In Section II, we introduce CBFs and motivate multiple safety constraints. In Section III, we propose a single CBF candidate to address the compositions of multiple constraints. We also characterize its properties, and we use simulations to demonstrate its ability to address safety-critical control with nontrivial constraints. Section IV closes with conclusions.
II CONTROL BARRIER FUNCTIONS
We consider affine control systems with state , control input , and dynamics:
| (1) |
where and are locally Lipschitz. Our goal is to design a controller , such that the closed-loop system:
| (2) |
satisfies certain safety specifications.
If is locally Lipschitz, then for any initial condition system (2) has a unique solution , which we assume to exist for all . We say that the system is safe if the solution evolves inside a safe set . Specifically, we call (2) safe w.r.t. if . We define the safe set as the 0-superlevel set of a continuously differentiable function :
| (3) |
assuming it is non-empty and has no isolated points. Later we extend this definition to more complex safety specifications.
The input affects safety through the derivative of :
| (4) |
where and are the Lie derivatives of along and . By leveraging this relationship, control barrier functions (CBFs) [1] provide controllers with formal safety guarantees.
Definition 1 ([1]).
Function is a control barrier function for (1) on if there exists 111Function , is of extended class- () if it is continuous, strictly increasing and . Function is of extended class- () if and . such that for all :
| (5) |
Note that the left-hand side of (5) is if and it is otherwise. Thus, (5) is equivalent to222In (5)-(6), strict inequality () can also be required rather than non-strict inequality () to ensure the continuity of the underlying controllers [15].:
| (6) |
Given a CBF, [1] established safety-critical control.
Accordingly, if the controller is synthesized such that (7) holds for all , then the closed-loop system evolves in the safe set: . Moreover, even if the initial condition is outside , i.e., , the system converges towards if (7) is enforced for all [16].
Condition (7) is often used as constraint in optimization to synthesize safe controllers. For example, a desired but not necessarily safe controller can be modified to a safe controller via the quadratic program (QP):
| (8) | ||||
also known as safety filter, which has explicit solution [17]:
| (9) |
II-A Motivation: Multiple CBFs
Controller (9) guarantees safety w.r.t. a single safe set . However, there exist more complex safety specifications in practice that involve compositions of multiple sets. Such general specifications are discussed in the next section. As motivation, we first consider the case of enforcing multiple safety constraints simultaneously, given by the sets:
| (10) |
and CBF candidates , with . Our goal is to maintain and , that corresponds to rendering the intersection of sets safe.
One may achieve this goal by enforcing multiple constraints on the input simultaneously, for example, by the QP:
| (11) | ||||
However, (11) may not be feasible (its solution may not exist) for arbitrary number of constraints. Even if each is CBF and consequently each individual constraint in (11) could be satisfied by a control input, the same input may not satisfy all constraints. For the feasibility of (11) we rather require:
| (12) |
cf. (5), that can also be stated in a form like (6) as follows.
Theorem 2.
The proof is given in the Appendix.
This highlights that multiple CBFs are more challenging to use than a single one. With this as motivation, next we propose to encode all safety specifications into a single CBF.
III COMPLEX SAFETY SPECIFICATIONS
We propose a framework to construct a single CBF candidate that captures complex safety specifications, wherein safety is given by Boolean logical operations between multiple constraints. For example, the motivation above involves logical AND operation: AND … AND must hold. Next, we discuss arbitrary logical compositions (with AND, OR and negation) of safety constraints.
III-A Operations Between Sets
Consider multiple safety constraints, each given by a set in (10). These may be combined via the following Boolean logical operations to capture complex safety specifications.
III-A1 Identity / class- function
The 0-superlevel set of is the same as that of for any :
| (14) |
III-A2 Complement set / negation
The complement333More precisely, is the closure of the complement of , i.e., it includes the boundary (where ). of the 0-superlevel set of is the 0-superlevel set of :
| (15) |
III-A3 Union of sets / maximum / OR operation
The union of multiple 0-superlevel sets:
| (16) |
can be given by a single inequality with the function [9]:
| (17) |
The union describes logical OR relation between constraints:
| (18) |
III-A4 Intersection of sets / minimum / AND operation
The intersection of multiple 0-superlevel sets:
| (19) |
can be compactly expressed using the function [9]:
| (20) |
As in the motivation above, the intersection of sets captures logical AND relation between multiple safety constraints:
| (21) |
Further operations between sets can be decomposed into applications of identity, complement, union and intersection, which are represented equivalently by class- functions, negation, and operations, respectively.
Remark 1.
Note that may have various physical meanings and orders of magnitude for different . Thus, for numerical conditioning (especially when we use exponentials later on), one may scale to with continuously differentiable . For example, scales to the interval that may help numerics. Next, we assume that the definitions of already include any necessary scaling and we omit . Likewise, we do not discuss negation further by assuming that are defined with proper sign.
III-B Smooth Approximations to Construct a Single CBF
While the union and intersection of sets are described by a single function in (17) and (20), the resulting expressions, and , may not be continuously differentiable in [9], and they are not CBFs. As main result, we propose a CBF candidate by smooth approximations of and , and describe its properties. This enables us to enforce complex safety specifications as a single constraint.
III-B1 Union of Sets
To capture the union of sets in (17), we propose a CBF candidate via a smooth over-approximation of the function using a log-sum-exp expression [13]:
| (22) |
with smoothing parameter . The Lie derivatives are:
| (23) |
with the coefficients:
| (24) |
that satisfy . The proposed CBF candidate in (22) has the properties below; see proof in the Appendix.
Theorem 3.
Consider sets in (10) given by functions , and the union in (17). Function in (22) over-approximates the expression in (17) with bounds:
| (25) |
such that . The corresponding set in (3) encapsulates the union, , such that . Moreover, if (13) holds for all with in (24), then is a CBF for (1) on with any that satisfies and .
Remark 2.
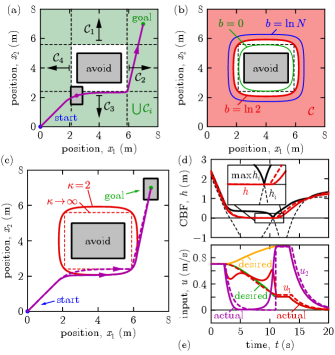
Example 1.
Consider Fig. 1, where a rectangular agent with planar position , velocity , and dynamics:
| (27) |
is controlled to reach a desired position while avoiding a rectangular obstacle444Matlab codes for each example are available at: https://github.com/molnartamasg/CBFs-for-complex-safety-specs.. To reach the goal, we use a proportional controller with gain and saturation:
| (28) |
where with some . We modify this desired controller to a safe controller using the safety filter (9) and the proposed CBF construction.
To avoid the obstacle, the agent’s center must be outside a rectangle that has the combined size of the obstacle and the agent; see Fig. 1(a). This means constraints linked with OR logic: keep the center left to OR above OR right to OR below the rectangle. Accordingly, the safe set is given by the union of four individual sets described by four barriers at location with normal vector :
| (29) |
. We combine the four barriers with (26). The resulting safe set is plotted in Fig. 1(b) for and various buffers . Set encapsulates for , whereas set lies inside for ; cf. Remark 2. For the problem-specific buffer (where is replaced by since two barriers meet at each corner), the approximation gets very close to the corners of .
We executed controller (9) with , , , and ; see solid lines in Fig. 1(c). The reach-avoid task is successfully accomplished by keeping the agent within set . Fig. 1(d) highlights that safety is maintained w.r.t. a smooth under-approximation (red) of the maximum (black) of the individual barriers (dashed). Fig. 1(e) indicates the underlying control input. We also demonstrate by dashed lines in Fig. 1(c)-(e) the case of increasing the smoothing parameter to . The sharp corner is recovered and the input becomes discontinuous ( jumps). While discontinuous inputs can be addressed by nontrivial nonsmooth CBF theory [9], they may be difficult to realize accurately by actuators in engineering systems.
III-B2 Intersection of Sets
To capture the intersection of sets in (20), we propose to use a smooth under-approximation of the function as CBF candidate [13], analogously to (22):
| (30) |
The Lie derivatives of are expressed by (23) with:
| (31) |
that satisfy . The proposed CBF candidate in (30) has the properties below, as proven in the Appendix.
III-C Single CBF for Arbitrary Safe Set Compositions
Having discussed the union and intersection of sets, we extend our framework to arbitrary combinations of unions and intersections. These include e.g. two-level or three-level compositions, like or , etc. We propose an algorithmic way to capture these by a single CBF candidate.
Specifically, consider levels of safety specifications that establish a single safe set by composing individual sets. The individual sets are in (10), . The specification levels are indexed by . At each level, the union or intersection of sets is taken, resulting in new sets, denoted by , . This is repeated until a single safe set, called , is obtained:
| (33) | ||||
where is the indices of sets that combine into , while and are the indices of levels with union and intersection (). Unions and intersections imply the maximum and minimum of the individual barriers , respectively, resulting in the combined CBF candidate [9]:
| (34) | ||||
This describes the safe set (that is assumed to be non-empty):
| (35) |
While the combined function is nonsmooth [9], we propose a continuously differentiable function , by extending the smooth approximations (22) and (30) of min and max:
| (36) | ||||
Note that we included a buffer , according to Remark 2, to be able to adjust whether the resulting set encapsulates or lies inside it. The derivative of the CBF candidate is:
| (37) |
The proposed function approximates with the following properties that are proven in the Appendix.
Theorem 5.
Consider sets in (10) given by functions , and the composition in (33) given by in (34)-(35). Function in (36) approximates with the error bound:
| (38) |
where , , , and is the number of elements in . If , the corresponding set in (3) lies inside , i.e., , whereas if , set encapsulates , i.e., . Furthermore, we have and .
The proposed approach in (36) captures complex safety specifications algorithmically by a single CBF candidate , via the recursive use of (22) and (30) such that exponentials and logarithms are computed only once. Safety is then interpreted w.r.t. set , which can be tuned to approximate the specified set as desired. Based on the error bound (38), increasing makes the approximation tighter, while affects whether or . Note that is a valid CBF only if it satisfies (5). This is not guaranteed by Theorem 5, and it would require additional conditions like (13) in Theorem 3. If is a CBF, formal safety guarantees can be maintained, for example, by QP (8) that has a single constraint and the explicit solution (9). If the constraint is enforced outside set , then is asymptotically stable; cf. Theorem 1. We remark that, potentially, the log-sum-exp formulas could be replaced by other smooth approximations of and . Furthermore, note that computing exponentials may cause numerical issues if is too large. These may be alleviated by scaling CBF candidates by class- functions; see Remark 1.
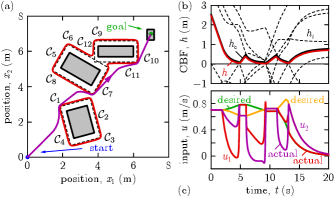
Example 2.
Consider the reach-avoid task of Example 1, with dynamics (27), desired controller (28), safety filter (9), and multiple obstacles shown in Fig. 2. Like in Example 1, each of the three obstacles yields four safety constraints, leading to sets and functions , given by (29). The four constraints of each obstacle are linked with OR logic, like in Example 1, while the constraints of different obstacles are linked with AND: safety is maintained w.r.t. obstacle 1 AND obstacle 2 AND obstacle 3. Thus, the safe set:
| (39) |
is given by a level specification, combining sets to sets ( from sets given by , from and from ), and then to a single set (via sets given by ).
The behavior of controller (9) with the proposed CBF candidate (36) is shown in Fig. 2 for , , , and . The reach-avoid task is successfully accomplished with formal guarantees of safety. Remarkably, the controller is continuous and explicit, since the control law (9) and CBF formulas (36)-(37) are in closed form. Such explicit controllers are easy to implement and fast to execute. Note that controller (11) could also handle multiple obstacles if each obstacle was given by a single CBF candidate. Yet, (11) cannot address multi-level safety specifications like (39), while the proposed method can.
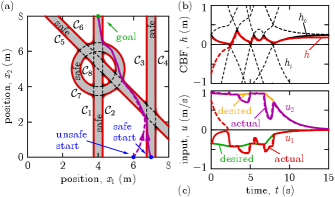
Example 3.
Consider the setup of Fig. 3 where a point agent is driven to a desired location while staying on a road network, with dynamics (27), desired controller (28) and safety-critical controller (9). Safety is determined by the road geometry. Each road boundary is related to a set, which is given for straight roads by (29) and for ring roads by:
| (40) |
Here plus and minus signs stand for the inner and outer circles, respectively, is their radius, and is their center. Safety must be ensured w.r.t. boundary 1 AND boundary 2 of each road, while the agent must stay on road 1 OR road 2 OR road 3 OR road 4. Thus, the combined safe set becomes:
| (41) |
That is, we have a level specification with sets combined first to sets (as intersections of sets given by , , , ), and then to a single set (as union via ).
The execution of the reach-avoid task with the proposed CBF candidate (36) and controller (9) is shown in Fig. 3 for , , , and . The end result is guaranteed safety (see solid lines). Moreover, the safe set is attractive: in case of an unsafe, off-road initial condition the agent returns to to the safe set on the road and continues to be safe (see thick dashed lines). Remarkably, this property was not provided by earlier works like [11].
IV CONCLUSION
We established a framework to capture complex safety specifications by control barrier functions (CBFs). The specifications are combinations of state constraints by Boolean logic. We proposed an algorithmic way to create a single CBF candidate that encodes these constraints and enables efficient safety-critical controllers. We described the properties of this CBF candidate, and we used simulations to show its ability to tackle nontrivial safety-critical control problems.
APPENDIX
Proof of Theorem 2.
Proof of Theorem 3.
Since the exponential function is monotonous and gives positive value, we have:
| (43) |
that yields (25) via (22) and the monotonicity of . The limit on both sides of (25) yields , and consequently holds. Due to (25), , therefore , and follows.
We prove that is a CBF by showing that (6) holds. We achieve this by relating and to and . The Lie derivatives are related by (23), while the following bound holds for all :
| (44) |
where we used (25) and . Consequently, since and hold via (24), we have:
| (45) |
If , we get based on (23), and since (13) is assumed to hold, (45) finally yields . Thus, (6) holds and is a CBF. ∎
Proof of Theorem 4.
Proof of Theorem 5.
By leveraging that the exponential function is monotonous, we write (34) equivalently as:
| (47) | ||||
We compare this with the definition (36) of . First, by using the middle row of (36), we establish that for all :
| (48) | ||||
and . Then, we relate to by induction. For we assume that there exist such that:
| (49) |
and . This is true for with since . By substituting (49) into (48), using the middle row of (47) and , we get:
| (50) |
with and:
| (51) | ||||
By induction, (50) holds for with and . Taking the logarithm of (50) with and using the last rows of (36) and (47) result in (38). ∎
References
- [1] A. D. Ames, X. Xu, J. W. Grizzle, and P. Tabuada, “Control barrier function based quadratic programs for safety critical systems,” IEEE Transactions on Automatic Control, vol. 62, no. 8, pp. 3861–3876, 2017.
- [2] M. Rauscher, M. Kimmel, and S. Hirche, “Constrained robot control using control barrier functions,” in IEEE/RSJ International Conference on Intelligent Robots and Systems, 2016, pp. 279–285.
- [3] X. Xu, “Constrained control of input–output linearizable systems using control sharing barrier functions,” Automatica, vol. 87, pp. 195–201, 2018.
- [4] W. Shaw Cortez, X. Tan, and D. V. Dimarogonas, “A robust, multiple control barrier function framework for input constrained systems,” IEEE Control Systems Letters, vol. 6, pp. 1742–1747, 2022.
- [5] X. Tan and D. V. Dimarogonas, “Compatibility checking of multiple control barrier functions for input constrained systems,” in 61st IEEE Conference on Decision and Control, 2022, pp. 939–944.
- [6] J. Breeden and D. Panagou, “Compositions of multiple control barrier functions under input constraints,” in American Control Conference, 2023, pp. 3688–3695.
- [7] L. Liu, Y.-J. Liu, D. Li, S. Tong, and Z. Wang, “Barrier Lyapunov function-based adaptive fuzzy FTC for switched systems and its applications to resistance–inductance–capacitance circuit system,” IEEE Transactions on Cybernetics, vol. 50, no. 8, pp. 3491–3502, 2020.
- [8] L. Liu, W. Zhao, Y.-J. Liu, S. Tong, and Y.-Y. Wang, “Adaptive finite-time neural network control of nonlinear systems with multiple objective constraints and application to electromechanical system,” IEEE Transactions on Neural Networks and Learning Systems, vol. 32, no. 12, pp. 5416–5426, 2021.
- [9] P. Glotfelter, J. Cortés, and M. Egerstedt, “Nonsmooth barrier functions with applications to multi-robot systems,” IEEE Control Systems Letters, vol. 1, no. 2, pp. 310–315, 2017.
- [10] ——, “A nonsmooth approach to controller synthesis for Boolean specifications,” IEEE Transactions on Automatic Control, vol. 66, no. 11, pp. 5160–5174, 2021.
- [11] L. Wang, A. D. Ames, and M. Egerstedt, “Multi-objective compositions for collision-free connectivity maintenance in teams of mobile robots,” in 55th IEEE Conference on Decision and Control, 2016, pp. 2659–2664.
- [12] M. Black and D. Panagou, “Adaptation for validation of a consolidated control barrier function based control synthesis,” arXiv preprint, no. arXiv:2209.08170, 2022.
- [13] L. Lindemann and D. V. Dimarogonas, “Control barrier functions for signal temporal logic tasks,” IEEE Control Systems Letters, vol. 3, no. 1, pp. 96–101, 2019.
- [14] ——, “Control barrier functions for multi-agent systems under conflicting local signal temporal logic tasks,” IEEE Control Systems Letters, vol. 3, no. 3, pp. 757–762, 2019.
- [15] M. Jankovic, “Robust control barrier functions for constrained stabilization of nonlinear systems,” Automatica, vol. 96, pp. 359–367, 2018.
- [16] X. Xu, P. Tabuada, J. W. Grizzle, and A. D. Ames, “Robustness of control barrier functions for safety critical control,” in IFAC Conference on Analysis and Design of Hybrid Systems, vol. 48, no. 27, 2015, pp. 54–61.
- [17] A. Alan, A. J. Taylor, C. R. He, A. D. Ames, and G. Orosz, “Control barrier functions and input-to-state safety with application to automated vehicles,” IEEE Transactions on Control Systems Technology, vol. 31, no. 6, pp. 2744–2759, 2023.
- [18] S. Boyd and L. Vandenberghe, Convex optimization. Cambridge University Press, 2004.