Distributed Grid restoration based on graph theory
Abstract
With the emergence of smart grids as the primary means of distribution across wide areas, the importance of improving its resilience to faults and mishaps is increasing. The reliability of a distribution system depends upon its tolerance to attacks and the efficiency of restoration after an attack occurs. This paper proposes a unique approach to the restoration of smart grids under attack by impostors or due to natural calamities via optimal islanding of the grid with primary generators and distributed generators(DGs) into sub-grids minimizing the amount of load shed which needs to be incurred and at the same time minimizing the number of switching operations via graph theory. The minimum load which needs to be shed is computed in the first stage followed by selecting the nodes whose load needs to be shed to achieve such a configuration and then finally deriving the sequence of switching operations required to achieve the configuration. The proposed method is tested against standard IEEE 37-bus and a 1069-bus grid system and the minimum load shed along with the sequencing steps to optimal configuration and time to achieve such a configuration are presented which demonstrates the effectiveness of the method when compared to the existing methods in the field. Moreover, the proposed algorithm can be easily modified to incorporate any other constraints which might arise due to any operational configuration of the grid.
Index Terms:
Smart grids, Grid islanding, Grid restorationI Introduction
Smart grids have been emerging readily since their inception due to their capability of imbibing powers of communication and computation in electrical grids which leads to better control and management of the grids. Smart grids being fully configurable with respect to their transmission and distribution have enabled the application of various methodologies to develop better resilience to attacks or natural disasters [5]. Moreover, the problem of automatic restoration of smart grids after an anomalous event has gained importance since maximum load restoration needs to be done at the earliest to minimize losses to the economy.
Typically, the reliability of a grid is assured via N-1 or N-k security criterion but for resilience, various operational measures need to be employed. Hardening of smart grids is another step that could be taken to reduce the impact of attacks on the grid [1]. Grid restoration post-attack is mainly done by islanding the grid into microgrids which are self-sufficient through Distributed Generators(DGs) if not connected to the main grid itself. The reconfiguration is mainly done through switches that enable connecting tie lines and opening a normally closed bus to redistribute the load. Redistribution enables restoration of maximum possible load by using DGs in combination with the primary generator or even with other DGs.
This paper primarily involves a new approach to power restoration in smart grids post attacks. The objectives are two-fold. First, the minimum amount of load which needs to be shed is calculated. Then, the sequence of switching operations required for achieving such a configuration with minimum load shed is deduced. For solving the above problems, a graph-based approach is used where the complete grid is mapped to a graph with graph nodes as the grid nodes and the edges as the lines in the grid. In the case of an attack, the graph is decomposed into several connected components. For the first stage, to find the minimum load shed which could be achieved, all the available tie lines are connected supplying as much load as possible to the areas blacked out. Once this configuration is obtained, the second stage is carried out by identifying the unnecessary tie lines which are connected. This is identified by removing the tie lines sequentially and re-computing the load shed at each of the configurations which satisfy the grid criterion. This method is quite efficient since the order in which the tie lines are disconnected does not matter which results in a very competitive complexity once combined with memoization. Once the best configuration is obtained, a multi-source search is carried out with the leaf nodes of an island as the sources. The one with the lowest impact is selected to be shed and the corresponding sectionalization switches are opened. Moreover, any such line which causes the radial topology to be disrupted such as forming a cycle is disconnected.
Finally, the approach is tested with standard IEEE 37-node and a 1069 node grid against various attacks and with various hardening plans. The minimum load shed, the optimum reconfiguration, and the time to achieve such a result is noted. Finally, it is compared to the modern state of the art techniques.
II Related Work
Smart grid resilience can primarily be enforced by either hardening the transmission buses through physical measures [2] or through various operational measures such as reconfiguration and DG islanding [3]. Reconfiguration in power systems has been particularly helpful since it enables using various energy sources in harmony and the process reduces load shed [4]. Moreover, specific importance can be given to nodes that are pivotal to the system [6]. Islanding on the other hand helps mitigate the effects of disasters by clustering the original network into smaller networks [7]. Several approaches have been researched to enable restoration of power distribution during disasters using microgrids and DG islanding such as in [8, 9].
For resilience against attacks or disasters, hardening serves as the first layer of protection for smart grids. [11] proposed a greedy algorithm that considers the bus with a maximum load at each step to develop a corresponding hardening plan. The Defender Attacker Defender(DAD) model [12] is a widely used infrastructure for the analysis of smart grids and devising hardening plans. The DAD model iteratively finds the optimal hardening plan for a grid considering reinforced attacks at each stage. Problems formulated by the DAD model have often been solved by the Column Constraint Generation(CCG) method of solving optimization problems [13]. The DAD model was further modified to use line switching as restoration measures [14]. Moreover, the model was further developed to include certain operational constraints which would account for real-life limitations [15]. Accounting for DGs, microgrids, etc. in the DAD model to create a more resilient solution was first experimented with by [16]. [6] proposed a three-stage hardening and restoration plan based on the DAD model. It provides an optimal DG islanding strategy and a hardening plan by iteratively using the results of the previous iteration.
Restoration of power in smart grids is often formulated as a Distributed System Restoration(DSR) problem which is primarily characterized by optimization problems with complex objective functions and several topological and operational constraints. The various techniques employed to solve these problems include expert systems [17], artificial intelligence such as genetic algorithms [18] and fuzzy logic [19], dynamic programming [20], various mathematical optimization techniques [21] and several graph-based heuristic search algorithms [22]. Most of these algorithms do not account for the inclusion of DGs or microgrids in the computation of the optimum solution. These factors include various uncertainties such as bi-directional power flows, islanded configurations, etc. These factors have been tackled by [23] which account for DGs and develop a restoration plan in a two-stage process specialized for Cold Load Pick Up(CLPU) conditions and in [24] which used spanning-tree search to develop a restoration plan considering microgrids inside the primary grid. Resilient system restoration procedures have also been proposed by [25] which extends it to the case of natural disasters where several buses are to be affected at once. For time-critical computations, an approach based on sequential optimization is proposed in [28] which provides an approximately accurate solution in a much shorter time.
Smart grids can be easily modeled in the form of graphs with the feeders as graph edges between two nodes. [26] proposed a method of restoration based on minimum spanning forests. The complete grid is divided into several smaller Self-Sustained Islanded Grids(SSIGs) which operate in harmony with each other either through the main turbine or through DGs. [24] on the other hand represented the grid a spanning tree and then used selective cyclic interchange policies to generate a new spanning tree iteratively and selecting the most optimal one. [27] again used a minimum spanning tree search to propose a new algorithm for finding the optimal configuration accounting for priority information of nodes. [10] proposes a time-efficient self-healing strategy to connect the blacked-out sections of the grid to a microgrid with a DG with a rolling-horizon optimization technique. [29] devises a power restoration strategy in a radial network with the help of sectionalization switches based on Edmond’s Maximal Spanning Tree Algorithm. [31] proposed a restoration algorithm based on Dijkstra’s algorithm for computation of shortest paths and used the results of a stage to reinforce the results of the next stage. [32] gives another algorithm using Kruskal’s algorithm. [33] gives an analysis of the various restoration techniques and compares them on several bases. [35] provides an algorithm which could find all possible solutions to connect energized healthy zones with blacked-out zones using graph theory. It then rejects the solutions which do not satisfy all the constraints. But the algorithm doesn’t account for cases where a single node from the inactive sub-graph is connected to multiple nodes from the healthy active sub-graph. Moreover, it doesn’t account for DGs during load restoration.
III Proposed methodology
Our proposed methodology for power restoration in smart grids can be primarily divided into certain sections. The problem is defining or choosing a mathematical formulation based on which we base our further architecture. Then, we need to devise an algorithm for restoration based on the constraints of the mathematical formulation. Devising an algorithm involves finding the minimum load shed possible along with the optimum switching sequence for reaching a grid configuration which provides the minimum load shed.
Nomenclature
-
Sample bus indexes.
-
Set of branches in the grid.
-
Set of buses in the grid.
-
Resistance of the feeders.
-
Reactance of the feeders.
-
Load weight.
-
Large number.
-
Active Load demand.
-
Reactive Load demand.
-
Set of parent buses of j.
-
Set of child buses of j.
-
Binary variable to determine whether feeder is operational or not.
-
Active load to be shed.
-
Reactive Load to be shed.
-
Impact of load shed.
-
Active Load supply.
-
Reactive Load supply.
-
Active power flow.
-
Reactive power flow.
-
Bus voltage.
III-A Mathematical formulation of constraints
An efficient restoration strategy should account for most of the topological and operational constraints which might occur in real-life implementations of the system. In a modern smart grid, it is assumed that the DGs can operate in harmony with each other and also with the primary generator. Moreover, each DG should possess the capability to operate independently in islanded situations. One of the most widely used models for the formulation of constraints for solving hardening and restorations problems is the linearized DistFlow model [30]. It has proved to be quite efficient in the representation of these kinds of problems as suggested by [13] and [6]. The constraints according to the linearized DistFlow model can be formulated as eqs. 1, 2, 3, 4 and 5. Each constraint corresponds to a limitation of the power grid. More specifically, the first constraint refers to the power flow balance in the grid. The second equation corresponds to the actual DistFlow equation which states that in a closed branch the flow should be limited whereas in an open branch it should be zero. The bounds for the amount of load that can be shed at each bus is given by eq. 3. The generators are constrained by eq. 4. The voltage constraints at each bus are represented by eq. 5.
| (1) |
| (2) |
| (3) |
| (4) |
| (5) |
For accountability of partitioning of the grid into several smaller microgrids, several topological constraints such as clustering constraints, connectivity constraints, etc. are to be considered as mentioned in [6]. The above constraints are simplified into a sufficient and necessary condition of radiality according to which a radial graph obeys all the above constraints [34]. A radial graph is characterized by two major properties. Each sub-graph of a graph should be connected and the number of edges should be equal to the number of sub-graphs subtracted from the number of nodes. It has been assumed that each controllable DG could form its own separated island and operate independently to the main grid or in harmony with it.
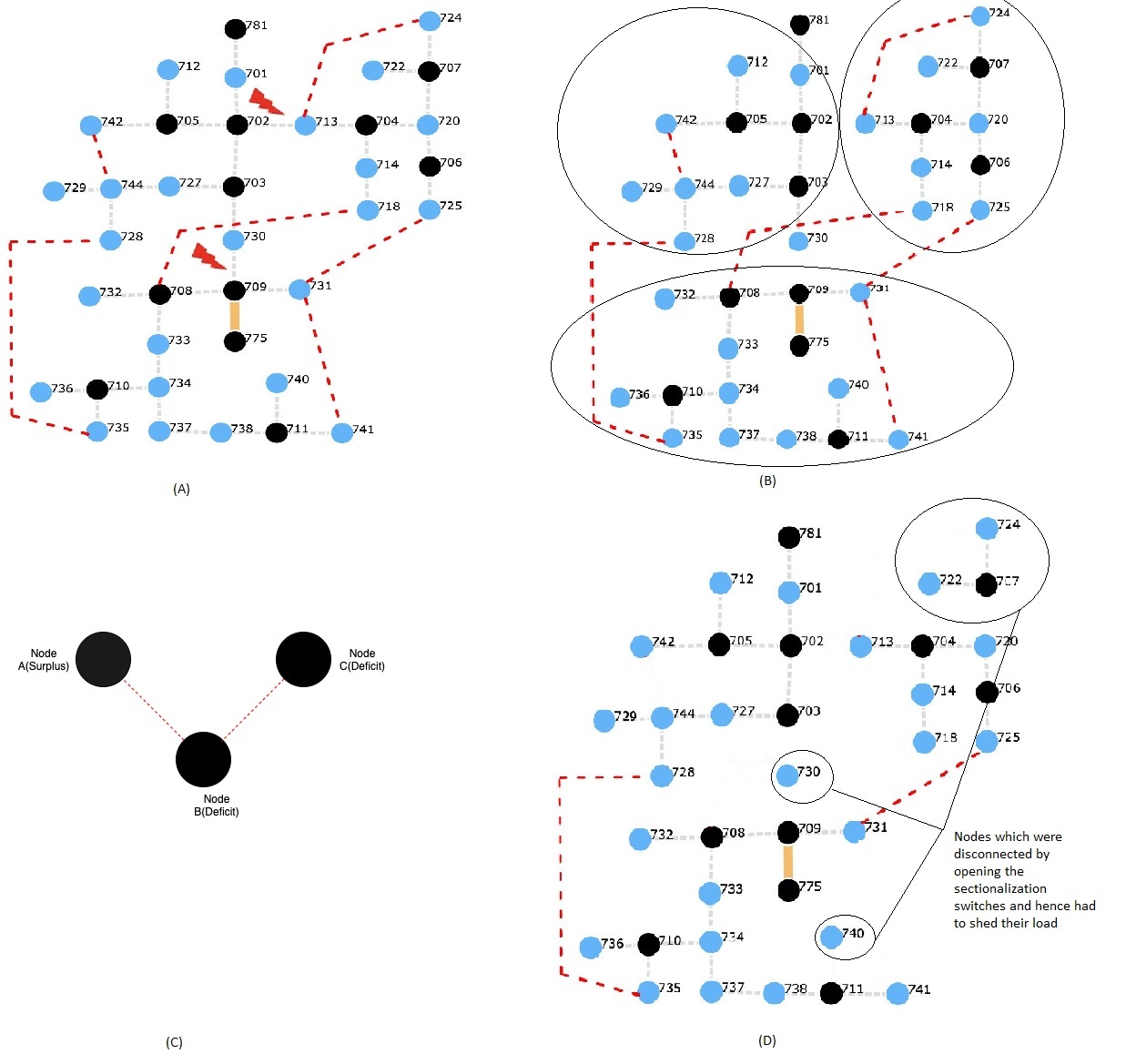
III-B Graphical Formulation
We have modeled the grid as a connected graph consisting of the grid feeders represented as graph edges and the buses as vertices . In the normal operational mode, the tie lines in the grid represented as edges are not connected, all the sectionalization switches are closed and the DGs operate together with the main grid if connected. In the case of a mishap, the tie lines to be closed are identified along with the sectionalization switches to be closed. The DGs in the network could form separate independent islands and operate autonomously. The radial structure of the graph needs to be maintained across all situations to satisfy the topological constraints. The operational constraints are taken into account while construction of the new graph . In the final representation, each unsupplied island needs to shed its load, whereas a supplied island can continue its operation through a DG or the main generator. The computation required to find this newly computed graph is essentially a combinatorial problem, but we aim to solve this in polynomial time through several optimizations in the later sections.
The graph can be simplified for processing post-attack by modeling a connected component of the graph as a node in a new auxiliary graph . The nodes in would either have a surplus or a deficit of power supply. The nodes in which are initially disconnected could be connected by closing the tie lines . The tie lines need to be remodeled for the auxiliary graph by using the mapping for nodes in the original graph to the nodes in . The auxiliary graph can be remodeled back to the graph for computation of by reverse mapping the nodes.
III-C Estimation of the minimum load shed
The auxiliary graph is used for computing approximately the minimum amount of load to be shed. The nodes in the auxiliary graph are initially isolated but can be connected by the tie lines in the smart grid. To estimate the minimum amount of load shed, we propose to connect all the tie lines across all the nodes, since this would ensure that the maximum number of nodes in , hence the maximum nodes in , is interconnected. Hence, the graph can be represented in terms of as:
| (6) |
This ensures that the surplus load in certain nodes to be distributed to the nodes in deficit. In case two nodes in deficit are connected, it just adds an extra redundant feeder to the grid with zero power flow. On connecting the tie lines, when two nodes are connected their combined deficit or surplus power will be determined by the addition of the two individual power flow values. This is essentially true since it is consistent with the power flow eq. 1 of the linearized DistFlow model used for the mathematical formulation. It is also powered by the assumption made above that two DGs or even a DG and the main generator can work in harmony with each other. This obtained value for the minimum load shed is used as a reference for the next stages to obtain an optimal configuration for achieving this minimum.
III-D Obtaining the optimal islanding configuration
The optimal islanding configuration can be obtained using auxiliary graph constructed in the previous step and iteratively disconnecting the tie lines which are redundant. For identification of the maximum number of tie lines to be disconnected, keeping the minimum load shed constant, we first order the tie lines in . Now, we remove each tie line from the auxiliary graph to form graphs . Mathematically, the edges of any such graph can be represented as:
| (7) |
We compute the load shed with the above configurations. If any of them achieve the minimum, we save them as a potential solution. Now further we compute graphs by removing the tie line and from and respectively. More generally, we compute the graph with edges:
| (8) |
The process continues until all the tie lines are considered for a particular branch. Hence, the change in edges could be generalized as:
| (9) |
Note that, we do not consider the configuration where , i.e. removing after removing , since the final configuration would be the same as that of the removal of before . It can be said that the removal of tie lines is independent of order of removal. This particularly saves a lot of computations and brings the complexity to polynomial time.
The complexity of the above algorithm can be easily computed by noting the number of trees formed by the above process. It can be observed that the number of trees formed by removal of at least from could be given by
| (10) |
This relation can be used to form a recursive relation on the total number of trees formed:
| (11) |
This term is of order where is the number of tie lines in the grid. Moreover, we need to check for the validity of the constraints for each tree. This would require an additional where is the number of buses. Hence, the overall complexity of the process is .
Finally, the potential configuration with the maximum number of removals is selected as the optimal configuration . If there is more than one such combination, then all are considered as potential solutions. This configuration is further adjusted to recognize the nodes whose load needs to be shed.
III-E Identifying the load shed buses
The configuration obtained in the previous needs to be modified in order to obey all the operational constraints. The topological constraints established aren’t violated in the previous steps. The islands with a power deficit need to shed some load in order to satisfy the power balance constraints in eq. 1. Now if the grid has manual control over the individual buses, it can easily unauthenticated any of the buses it deems fit to shed load, but this is not often the case. Buses for load shed are selected from the terminals of each component with a deficit. Now, each bus might have a weight associated with it. The impact of load shed on it being represented as :
| (12) |
We consider a connected component with a power deficit of the configuration and start a multi-source breadth-first search with the terminal nodes as the sources. We identify the nodes which would lead to minimal overall impact according to the eq. 12 but could shed enough load so as to satisfy the power balance eq. 1. The node might belong to any of the branches but nodes selected in a branch should be continuous and should originate from the terminals. Once these nodes are identified, the sectionalization switches which need to be opened which can disconnect the selected nodes from the connected component . For a without a DG or the main turbine, all the buses in it need to shed their load in order to satisfy the operational constraints. Moreover, any such line which causes the radial topology to be disrupted such as forming a cycle is disconnected. This step introduces an extra computational complexity of order but its negligible in comparison to the previous term which was of order
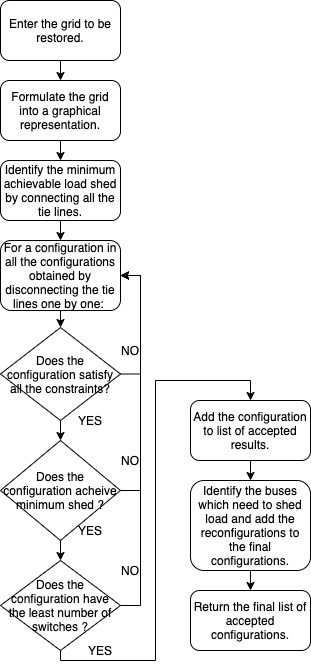
Once we perform this for all such connected components, we have our tie lines to be connected along with the sectionalization switches to be opened. Hence, we have all the switching operations which lead to a configuration with a minimum load shed and a minimum number of switching operations, and one which satisfies all the constraints. A brief summary of the complete process is given in fig. 1.
IV Experimentation and Results
| Scenario | Fault location | Proposed Methodology | Spanning Tree Search | ||
| Time(in s) | Switching Sequence | Time(in s) | Switching Sequence | ||
| 1 | 713-704 | 0.081 | Close: 713-724 | 1.335 | Close: 713-724 |
| 2 | 730-709 | 0.103 | Close: 708-718 | 0.825 | Close: 708-718 |
| 3 | 730-709, | 1.523 | Close: 708-718, 735-728; | – | – |
| 702-713 | Open: 720-707, 703-730, 711-740 | ||||
| Scenario | Fault location | Proposed Methodology | MILP based 2-stage restoration | ||
| Time(in s) | Switching Sequence | Time(in s) | Switching Sequence | ||
| 1 | 241-159() | 1.676 | Close: 252()-266(), 254()-248() | – | Close: 254()-248(), 252()-266() |
| 75()-252(), 236()-256() | |||||
| Open: 256-254(), 256-261() | Open: 220-254(), 136-245() | ||||
| 195-256() | |||||
| 2 | 181-182() | 8.76 | Close: 252()-266(), 254()-248() | – | Close: 254()-248(), 252()-266() |
| 236()-256(),244()-257() | 261()-263(), 244()-257() | ||||
| 236()-256(), 252()-75() | |||||
| Open: 256-77(), 256-261() | Open: 77-220(), 177-240() | ||||
| 256-261() | 195-256(), 208-251() | ||||
| 220-254() | |||||
| 3 | 193-195() | 1.577 | Close: 75()-252(), 254()-248() | – | Close: 254()-248(), 75()-252() |
| 105-191() | 252()-266() | ||||
| Open: 195-256() | |||||
| Number of Faults | IEEE-37 node | R3-12.47-2 1069 node |
|---|---|---|
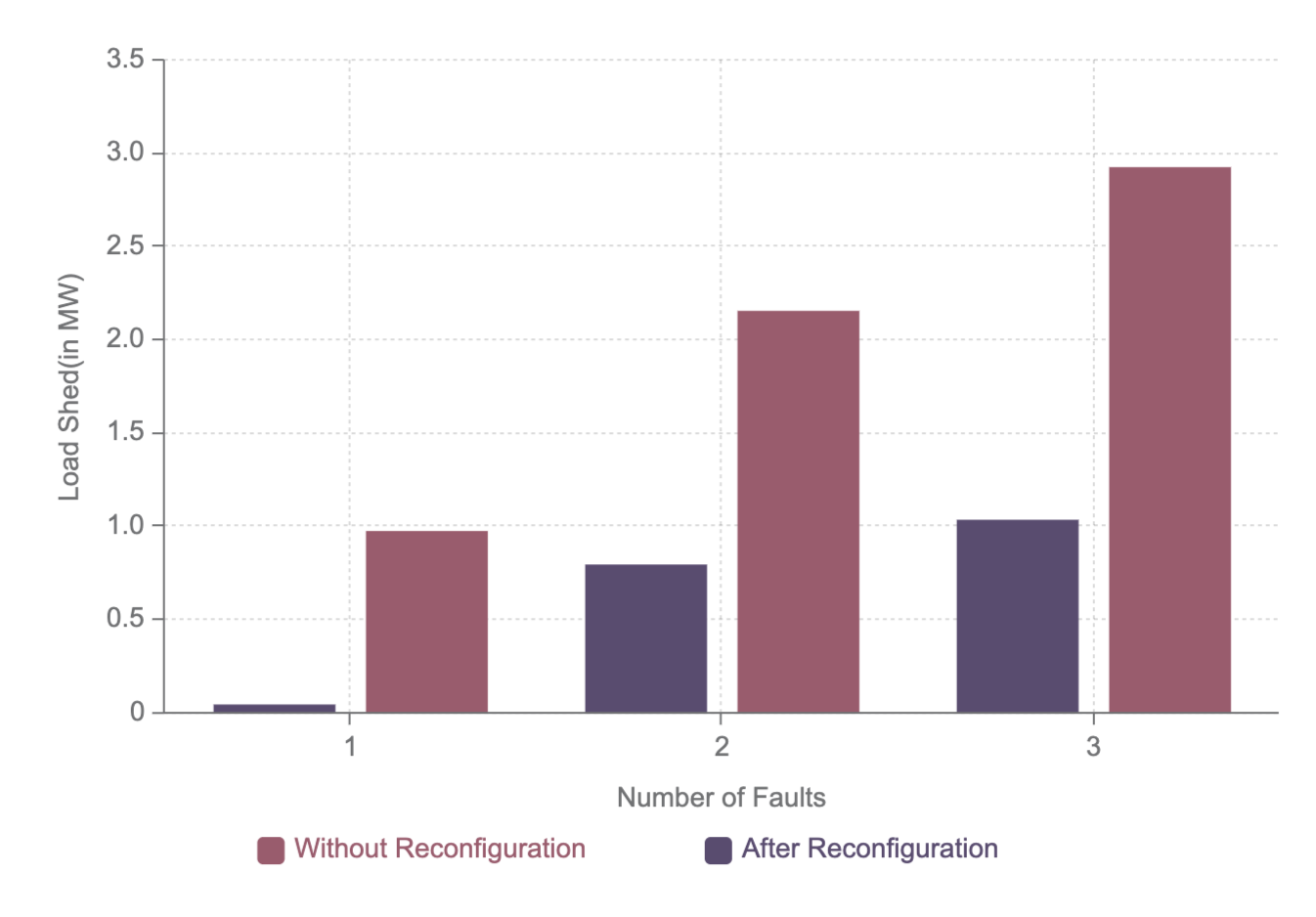
| 1 | 99.45% | 97.32% |
| 2 | 63.02% | 54.48% |
| 3 | 46.73% | 35.50% |
The proposed methodology was tested against modified versions of the standard IEEE-37 and IEEE-1069 bus test systems. The reduction in load shed on reconfiguration and the reconfiguration strategy for sample attacks are recorded and compared with results from currently established systems. Each system was imported from a GridLAB-D model with load models of constant power, current and impedance. The algorithm was implemented and tested on MATLAB and GridLAB-D on a system with Intel Core i7 8th generation processor and 16GB RAM.
Each system was imported from a GridLAB-D model with load models of constant power, current and impedence. The algorithm was implemented and tested on MATLAB and GridLAB-D on a system with Intel Core i7 8th gen processor with 16GB ram.
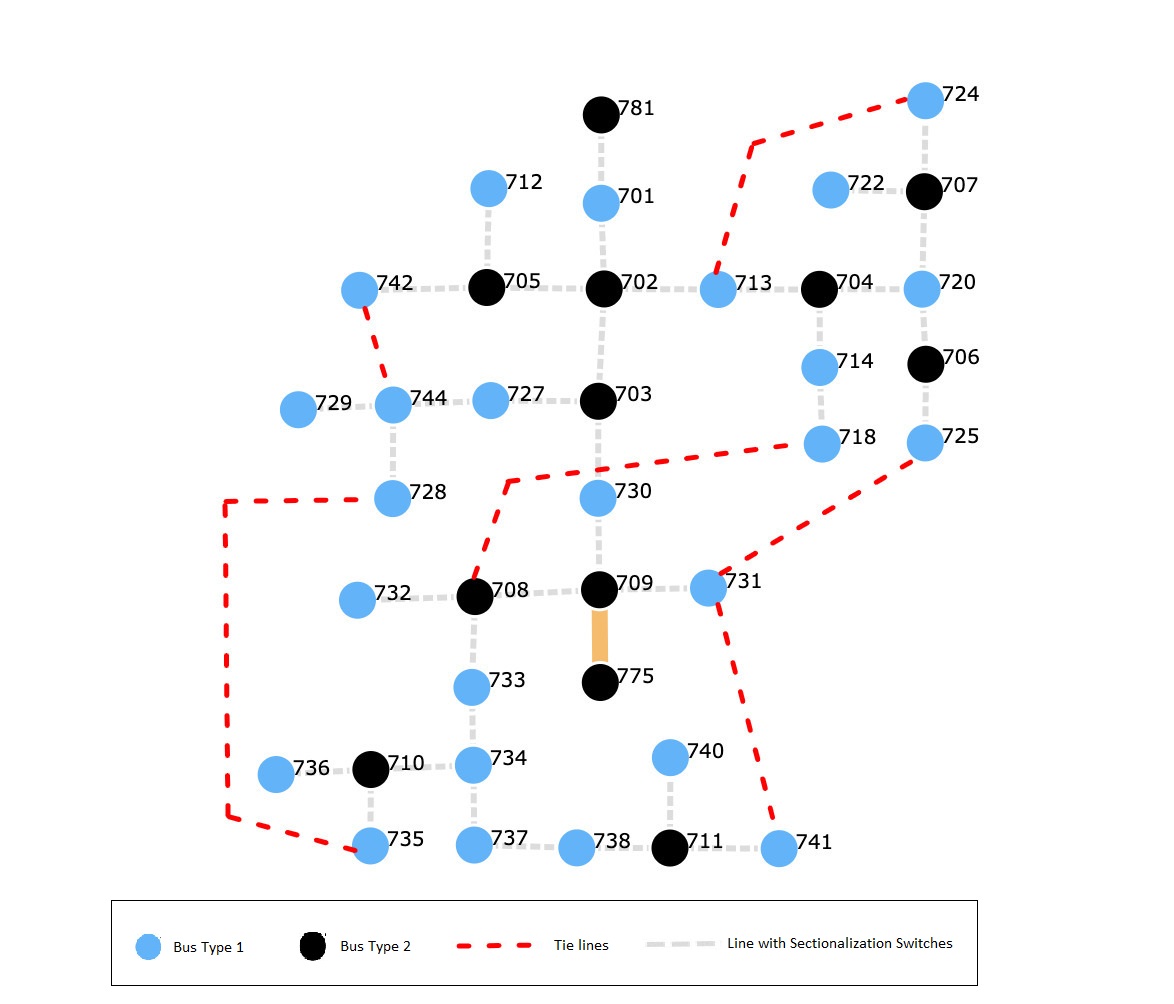
The modified IEEE-37 bus system fig. 4 is implemented as shown in [24] and [25]. Additionally, the system is augmented with 6 normally open tie lines and 4 DGs at random positions. All the branches are supported by sectionalization switches. The performance of the system is compared with the methods in [24]. The faults were simulated as given in [24] so as to be able to easily compare our methods. One advantage of our proposed algorithm is that it works in case of multiple attacks whereas the one in [24] doesn’t. The simulation results are presented in table I.
In Scenario 1, the attack is on the line connecting buses 713 and 704. As a result of this, the buses to the right of 714 in fig. 4 are disconnected from the main grid. These could be connected by joining the tie lines 713-724, 731-725, or 708-718. Some sectionalization switches might need to be opened in case excess load needs to be shed. The best solution to this would be closing the tie line 713-724. This way no-load needs to be shed and the normal working of the grid would be restored in minimum operations.
In Scenario 2, the attack is on the line connecting buses 730 and 709. As a result of this, the buses to the bottom of 709 in fig. 4 are disconnected from the main grid. These could be connected by joining the tie lines 735-728, 731-725, or 708-718. The best solution to this would be closing the tie line 708-718. On connecting the line 735-728, we find that an over-current flow through the bus 744 and hence it violates the power constraints. No load would be shed in this scenario.
In Scenario 3, there are multiple attacks on the lines 730-709 and 702-713. As a result, the complete grid is divided into three islands two of which are not connected to any generator. For load restoration, the tie lines 708-718 and 735-728 are connected. This leads to overload in the grid and some load needs to be shed. On computation according to the proposed methodology, nodes 730, 740, 722, 707, and 724 need to shed their load. Hence, the switches in lines 720-707, 703-730, and 711-740 need to be opened. The net load shed was approximately 2.10 MW.
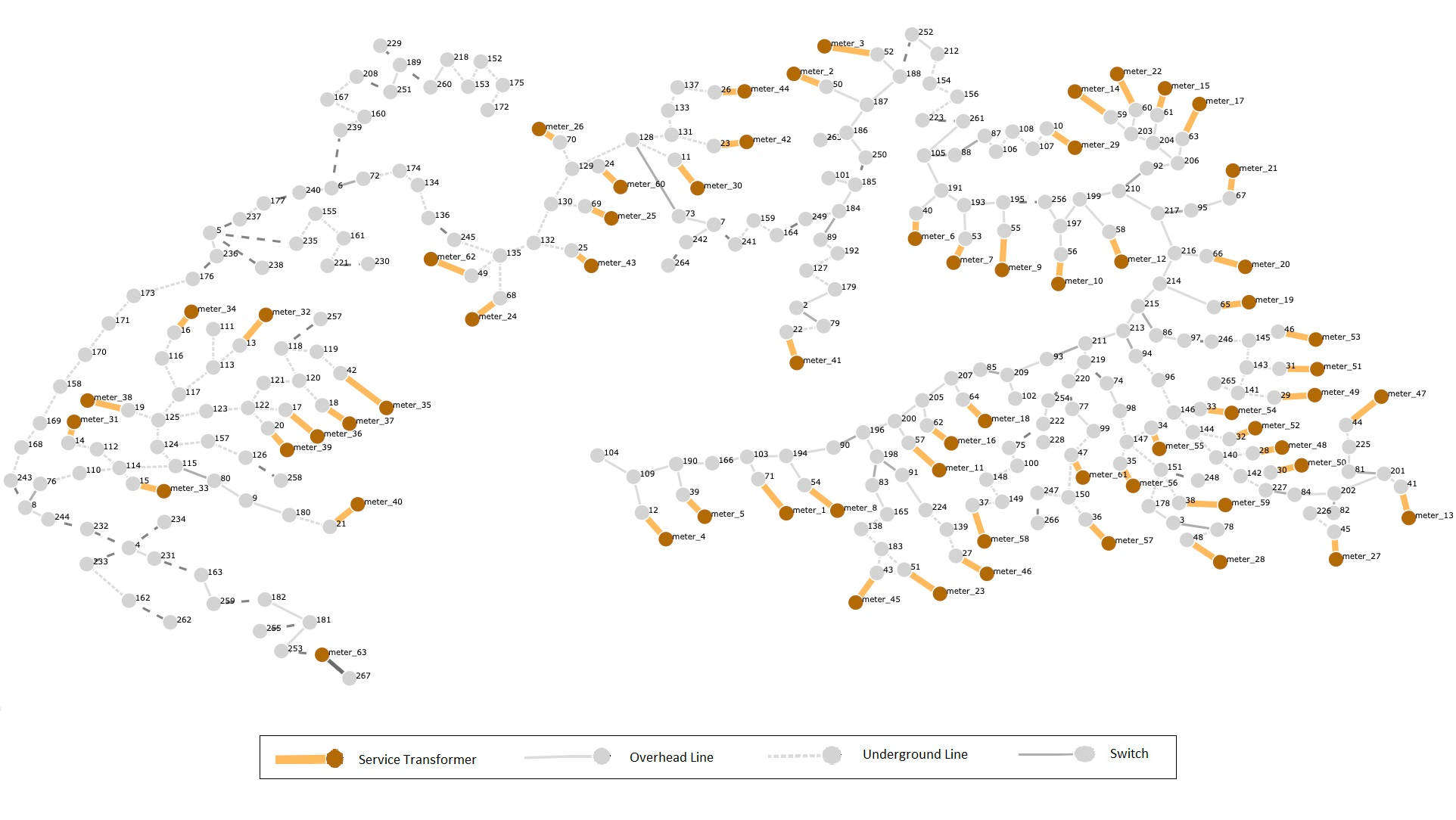
The R3-12.47-2 1069 bus test system fig. 3 consists of four taxonomy feeders and numerous tie lines as used by [23] and [24]. The model provides a good representation of a real-world populated area. Replicas of a single feeder is made to construct the four feeder system () where the feeders are interconnected with tie switches. Hence, with net 1069 buses, 152 branches with sectionalization switches, and 122,586 possible number of radial topologies, the grid is a typical representation of an urban grid. Moreover, the grid is augmented with several DGs to support the primary generators in case of outrages. The system is similarly simulated against attacks and reconfigured by the algorithm suggested in this paper and by [23]. The data about the time taken for each solution is not available in [23] but since it uses MILP which is NP-Hard it would be much more time-intensive as compared to our methodology. The simulation results are presented in table II.
In Scenario 1, the attack was simulated on line 241-159 of supply feeder . As the result, the part of the grid supplied by after node 159 was blacked out. For restoration, the tie line between 252() to 266() and 254() to 248() was connected. This leads to overload in certain buses in and hence switches between nodes 256-254 of and 256-261 of were opened. This restores the load in the minimum number of operations. The net load shed before islanding was approximately 3.5MW but it was restored completely.
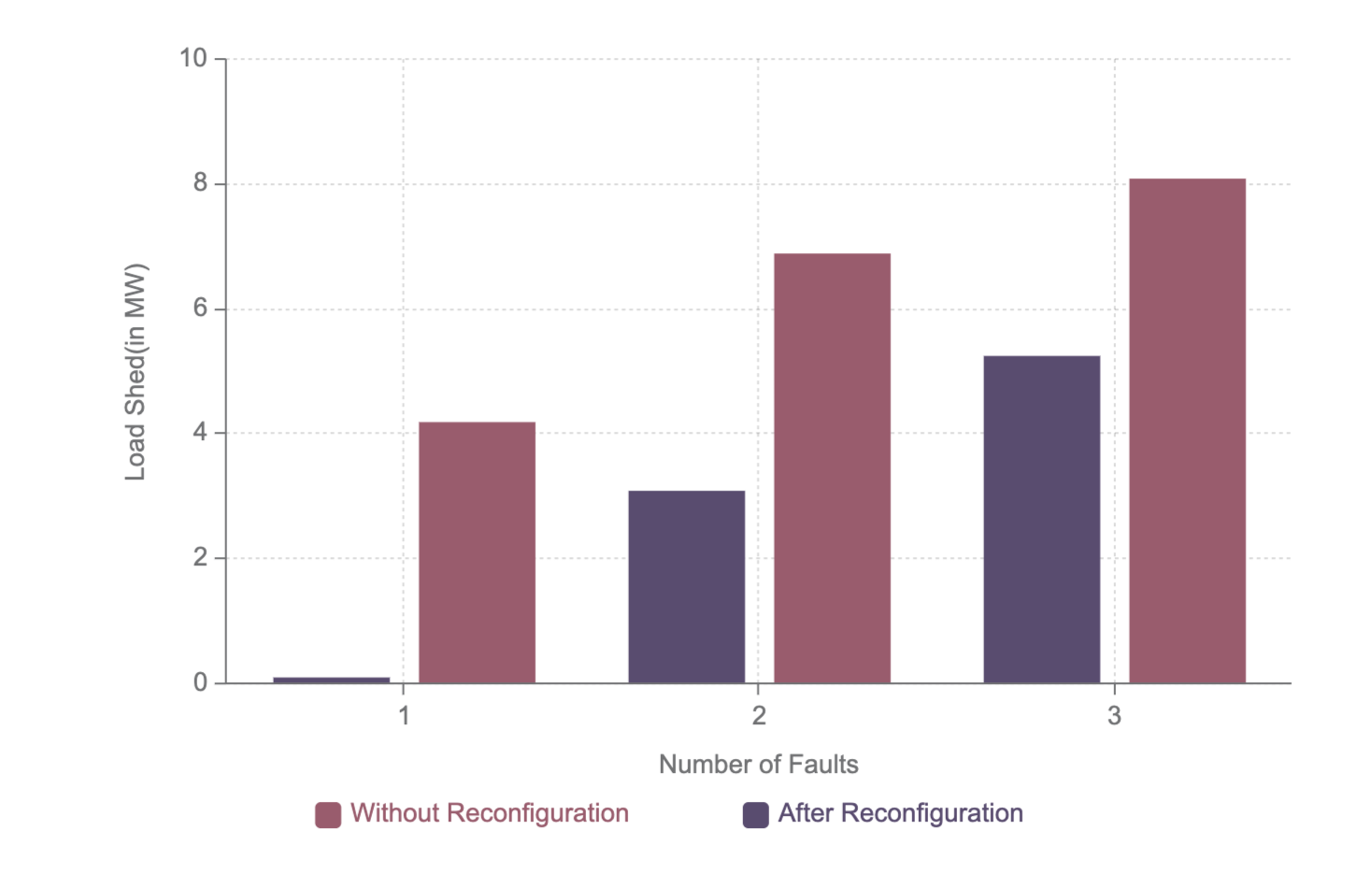
In Scenario 2, attack was simulated on line 181-182 of supply feeder . As a result the part of the grid supplied by after node 181 was blacked out. For restoration, the tie line between 257() to 244(), 252() to 266() and 236() to 256() and 254() to 248() were connected. This leads to overload in certain buses in and violation of radial topology and hence switches between nodes 256-261 of , 256-77 of and 256-261 of were opened. This restores the load in a minimum number of operations.
In Scenario 3, multiple attacks were simulated on line 193-195 of supply feeder and 105-191 of supply feeder . As a result the part of the grid supplied by after node 195 and the grid supplied by after node 191 was blacked out. For restoration, the tie line between 75() to 252() and 254() to 248() were connected. This restores the load in a minimum number of operations. The net load shed was 6.5 MW but was completely restored.
V Conclusion
In this paper, we present a novel graph-based approach to the restoration of a distributed smart grid with DGs post-attack. The method considers all the operational and topological constraints and provides the minimum load shed along with the sequence of switching operations to achieve such a configuration. The method was tested against standard IEEE grids and other taxonomy grids which prove that it compares well to the existing methods and provides a result with much lesser switching operations in much lesser time.
Further improvements may revolve around providing a resilient hardening strategy based on similar principles which would enable the system to incur even lower losses in cases of attacks. Moreover, the algorithm could be modified to account for dynamic changes in grids, isolation of the attack nodes from the rest of the grid in case it has the potential to compromise other nodes, etc. Thoughts could be given on predicting the cost for reconfiguration before attacks.
References
- [1] Farzin, H., Fotuhi-Firuzabad, M. and Moeini-Aghtaie, M., 2016. Enhancing power system resilience through hierarchical outage management in multi-microgrids. IEEE Transactions on Smart Grid, 7(6), pp.2869-2879.
- [2] Salman, A.M., Li, Y. and Stewart, M.G., 2015. Evaluating system reliability and targeted hardening strategies of power distribution systems subjected to hurricanes. Reliability Engineering & System Safety, 144, pp.319-333.
- [3] Panteli, M. and Mancarella, P., 2015. The grid: Stronger, bigger, smarter?: Presenting a conceptual framework of power system resilience. IEEE Power and Energy Magazine, 13(3), pp.58-66.
- [4] Nagata, T., Hatakeyama, S., Yasouka, M. and Sasaki, H., 2000, December. An efficient method for power distribution system restoration based on mathematical programming and operation strategy. In PowerCon 2000. 2000 International Conference on Power System Technology. Proceedings (Cat. No. 00EX409) (Vol. 3, pp. 1545-1550). IEEE.
- [5] Bie, Z., Lin, Y., Li, G. and Li, F., 2017. Battling the extreme: A study on the power system resilience. Proceedings of the IEEE, 105(7), pp.1253-1266.
- [6] Lin, Y. and Bie, Z., 2018. Tri-level optimal hardening plan for a resilient distribution system considering reconfiguration and DG islanding. Applied Energy, 210, pp.1266-1279.
- [7] Haddadian, H. and Noroozian, R., 2017. Multi-microgrids approach for design and operation of future distribution networks based on novel technical indices. Applied energy, 185, pp.650-663.
- [8] Ding, T., Lin, Y., Bie, Z. and Chen, C., 2017. A resilient microgrid formation strategy for load restoration considering master-slave distributed generators and topology reconfiguration. Applied energy, 199, pp.205-216.
- [9] Cao, W., Wu, J., Jenkins, N., Wang, C. and Green, T., 2016. Benefits analysis of Soft Open Points for electrical distribution network operation. Applied Energy, 165, pp.36-47.
- [10] Wang, Z. and Wang, J., 2015. Self-healing resilient distribution systems based on sectionalization into microgrids. IEEE Transactions on Power Systems, 30(6), pp.3139-3149.
- [11] Bier, V.M., Gratz, E.R., Haphuriwat, N.J., Magua, W. and Wierzbicki, K.R., 2007. Methodology for identifying near-optimal interdiction strategies for a power transmission system. Reliability Engineering & System Safety, 92(9), pp.1155-1161.
- [12] Brown, G., Carlyle, M., Salmerón, J. and Wood, K., 2006. Defending critical infrastructure. Interfaces, 36(6), pp.530-544.
- [13] Yuan, W., Zhao, L. and Zeng, B., 2014. Optimal power grid protection through a defender–attacker–defender model. Reliability Engineering & System Safety, 121, pp.83-89.
- [14] Yuan, W. and Zeng, B., 2014. Achieving cost-effective power grid hardening through transmission network topology control. Dept. Ind. Manag. Syst. Eng., Univ. South Florida, Tampa, FL, USA, Tech. Rep.
- [15] Yuan, W., Wang, J., Qiu, F., Chen, C., Kang, C. and Zeng, B., 2016. Robust optimization-based resilient distribution network planning against natural disasters. IEEE Transactions on Smart Grid, 7(6), pp.2817-2826.
- [16] Abbey, C., Cornforth, D., Hatziargyriou, N., Hirose, K., Kwasinski, A., Kyriakides, E., Platt, G., Reyes, L. and Suryanarayanan, S., 2014. Powering through the storm: Microgrids operation for more efficient disaster recovery. IEEE power and energy magazine, 12(3), pp.67-76.
- [17] Chen, C.S., Lin, C.H. and Tsai, H.Y., 2002. A rule-based expert system with colored Petri net models for distribution system service restoration. IEEE Transactions on Power Systems, 17(4), pp.1073-1080.
- [18] Vadivoo, N.S. and Slochanal, S.M.R., 2009. Distribution system restoration using genetic algorithm with distributed generation. Modern Applied Science, 3(4), p.98.
- [19] Lim, S.I., Lee, S.J., Choi, M.S., Lim, D.J. and Ha, B.N., 2006. Service restoration methodology for multiple fault case in distribution systems. IEEE Transactions on Power Systems, 21(4), pp.1638-1644.
- [20] R. Perez-Guerrero, G. T. Heydt, N. J. Jack, B. K. Keel and A. R. Castelhano, ”Optimal Restoration of Distribution Systems Using Dynamic Programming,” in IEEE Transactions on Power Delivery, vol. 23, no. 3, pp. 1589-1596, July 2008, doi: 10.1109/TPWRD.2007.916112.
- [21] S. Khushalani, J. M. Solanki and N. N. Schulz, ”Optimized Restoration of Unbalanced Distribution Systems,” in IEEE Transactions on Power Systems, vol. 22, no. 2, pp. 624-630, May 2007, doi: 10.1109/TPWRS.2007.894866.
- [22] Kumar, A. and Grijalva, S., 2018, September. Graph Theory and Critical Load-Based Distribution System Restoration using Optimal Microgrids Formation. In 2018 Clemson University Power Systems Conference (PSC) (pp. 1-6). IEEE.
- [23] Poudel, S. and Dubey, A., 2020. A Two-Stage Service Restoration Method for Electric Power Distribution Systems. arXiv preprint arXiv:2004.07921.
- [24] Li, J., Ma, X.Y., Liu, C.C. and Schneider, K.P., 2014. Distribution system restoration with microgrids using spanning tree search. IEEE Transactions on Power Systems, 29(6), pp.3021-3029.
- [25] Chen, C., Wang, J., Qiu, F. and Zhao, D., 2015. Resilient distribution system by microgrids formation after natural disasters. IEEE Transactions on smart grid, 7(2), pp.958-966.
- [26] Poudel, S., Sun, H., Nikovski, D. and Zhang, J., 2019, August. Resilient Restoration of Power Distribution System Based on Minimum Spanning Forest. In 2019 IEEE Power & Energy Society General Meeting (PESGM) (pp. 1-5). IEEE.
- [27] Kumar, A. and Grijalva, S., 2018, September. Graph Theory and Critical Load-Based Distribution System Restoration using Optimal Microgrids Formation. In 2018 Clemson University Power Systems Conference (PSC) (pp. 1-6). IEEE.
- [28] Chen, B., Chen, C., Wang, J. and Butler-Purry, K.L., 2017. Sequential service restoration for unbalanced distribution systems and microgrids. IEEE Transactions on Power Systems, 33(2), pp.1507-1520.
- [29] Sarkar, D., Konwar, P., De, A. and Goswami, S., 2020. A graph theory application for fast and efficient search of optimal radialized distribution network topology. Journal of King Saud University-Engineering Sciences, 32(4), pp.255-264.
- [30] Ding, T., Lin, Y., Li, G. and Bie, Z., 2017. A new model for resilient distribution systems by microgrids formation. IEEE Transactions on Power Systems, 32(5), pp.4145-4147.
- [31] Sudhakar, T.D., Vadivoo, N.S. and Slochanal, S.M.R., 2004. Power Restoration Problem Analysis In Various Distribution Systems. In National Power Systems Conference.
- [32] Pavana, D. and Triveni, M.T., 2015. Power System Restoration in Distribution Network Through Reconfiguration Using MST-Kruskal’s Algorithm. IJRET: International Journal of Research in Engineering and Technology, pp.295-299.
- [33] Bie, Z., Lin, Y., Li, G. and Li, F., 2017. Battling the extreme: A study on the power system resilience. Proceedings of the IEEE, 105(7), pp.1253-1266.
- [34] Balakrishnan, R. and Ranganathan, K., 2012. A textbook of graph theory. Springer Science & Business Media.
- [35] D. T. Vedullapalli, R. Hadidi and L. S. Bozeman, ”Distribution system restoration using graph theory after multiple faults,” in IET Energy Systems Integration, vol. 2, no. 3, pp. 235-242, 9 2020, doi: 10.1049/iet-esi.2019.0118.