Double Link Failure Protection
using a Single P-cycle
Abstract
In this letter, we investigate survivability in optical networks for protection from two simultaneous link failures. Failure probability of two links with overlapping protection can be high if these links are geographically close. In a network with deterministic single link protection, simultaneous failure of two links may lead to partial or full loss of traffic on the failed links. Two link failure protection will make the network more resilient by protecting double failures having overlapping protection. A method for achieving double fault tolerance is double cycle method (DB); it uses two pre-configured cycles (p-cycles) to protect a link. Single p-cycle (SG) method, which uses one p-cycle to protect a link from two simultaneous link failure is introduced in this letter. Integer linear programs (ILP) are formulated for the SG method as well as DB method. It has been observed that the SG method provides solution to bigger networks with lesser computational resources as compared to the DB method.
Index Terms:
optical network, p-cycle, straddling link, two link failure.I Introduction
Optical networks carry enormous amount of information. Failure of any element in an optical network even for a small duration can lead to a large amount of information loss, and consequently, the revenue loss. Thus it is important to build mechanisms of survivability to take care of failures. Survivability of a network is the ability of the network to either maintain uninterrupted flow of information or to minimize the outage period. In an optical network, it is of great importance and has been studied extensively by the researchers [1] [2].
Among various protection schemes, p-cycles are quite promising due to their mesh like efficiency and ring like speed. P-cycles were first introduced by Grover [3] and has been extensively studied for optical network survivability [4]. A p-cycle can protect working capacity of the on-cycle as well as the straddling links. A straddling link is a chord of a cycle with its end nodes being part of the cycle. When a straddling link fails, a p-cycle has two paths to reroute the traffic and hence, the capacity requirement in the p-cycle is reduced to half of the protected working capacity in the straddling link. A single copy of a p-cycle can provide unit capacity protection to an on-cycle link and, two unit capacity protection to straddling links on it.
Feng et-al [5], described a method which provides deterministic protection from two link failures using p-cycles. In [5], each link is protected using two p-cycles having link-disjoint protection segments. In this letter, we have described a method which use one p-cycle to protect working capacity on each link against two simultaneous link failures. This protection method is applicable to graphs which has at least three link disjoint paths between each set of nodes like for all other protection methods. Since, our method requires only one p-cycle for each link to protect against two simultaneous link failures, the number of variables involved and the computational time is significantly less. We have also observed that the required spare capacity is more efficient. The efficiency is even better for optical network with higher average nodal degree.
II SG method
Normally a copy of a p-cycle can protect unit capacity on an on-cycle link and two unit capacity on a straddling link. A straddling link has two alternative paths on the p-cycle for restoration, and this attribute of p-cycle is employed in the SG method to protect the optical network from two simultaneous link failures. In the SG protection method, p-cycles are used to provide protection only to straddling links and no on-cycle protection is used. In case, a p-cycle is shared among multiple straddling links, the number of copies of that p-cycle is taken to be equal to the highest capacity straddling link. Number of copies of p-cycles to protect a straddling link is equal to its capacity. If the capacity of the straddling link to be protected is an odd number, then the number of copies of p-cycle is kept one unit capacity higher than the capacity of the straddling link. Even number of copies of p-cycle are required to ensure protection where the capacity of straddling links sharing the p-cycle are equal and an odd number. For example, if the capacity of every straddling link to be protected is three, then the number of copies of the p-cycle should be four. Restoration takes place in two different ways depending on which two links have failed two straddling links, or a straddling and an on-cycle link. When two straddling links fail simultaneously, the highest capacity straddling link uses half of the capacity of p-cycle, and the other failed link uses the remaining capacity of the p-cycle. When a straddling link and an on-cycle link fail, then the straddling link uses the intact alternative path on p-cycle for restoration. The working paths through the on-cycle links must have been restored as a straddling link by some other p-cycle.
Theorem 1.
A p-cycle can protect all the straddling links on it from any two simultaneous link failure, if the number of copies of the p-cycle
Here, is the working capacity of the straddling link with maximum capacity, on p-cycle .
Proof.
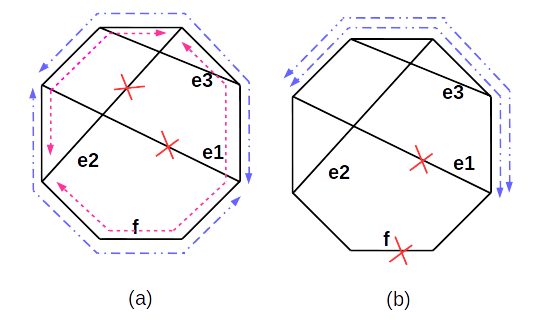
Consider a p-cycle protecting three straddling links , and as shown in Fig. 1. Assume that is the highest capacity straddling link with capacity protected by the p-cycle. The number of copy of p-cycle required as per our algorithm to protect network from two link failure will be when is even, and when is odd. In case of failure of the two straddling links and as shown in Fig. 1 (a), half of the (or when is odd) copies of p-cycle will be used to restore . The link is restored using remaining half copies of the p-cycle.
In case of the failure of a straddling link and an on-cycle link as shown in Fig. 1(b), capacity of the intact alternative path on the p-cycle will restore the straddling link . Link is restored by some other p-cycle of the network as it must have also been given double fault protection as a straddling link.
∎
II-A ILP for the SG method
The objective of this ILP is to find the minimum spare capacity required to protect the optical network from two simultaneous link failure using the proposed protection method. We find the minimum spare capacity needed for single fault protection when only straddling link protection is used. Thereafter, number of p-cycles needed are simply doubled to provide double fault tolerance.
Notations
S=set of links.
P=set of cycles.
We use to denote the amount of demand capacity of link protected by unit capacity of p-cycle for single fault tolerance with only straddling link protection.
We also define,
Variables
=spare capacity on link .
=working capacity on link .
=cost of unit capacity of link .
= number of copies of p-cycle .
=number of copies of p-cycle required to protect working capacity of link in single fault tolerance scenario.
ILP for the SG method is as follows.
Minimize:
| (1) |
Subject to :
| (2) | |||
| (3) | |||
| (4) | |||
| (5) |
In equation (1), the objective function that minimizes the total spare capacity is defined. Constraint (2) ensures that the protection capacity on p-cycle is sufficient to protect the working capacity on link as a straddling link under single fault tolerance scenario. Constraint (3) selects the minimum number of copies of the p-cycles , required to provide protection to any two straddling links that fail simultaneously. Constraint (4) ensures that the spare capacity on each link is sufficient to form the p-cycles.

III DB method
The most intuitive method for deterministic dual link failure protection is to protect each link of the network with two p-cycles as described in [5]. The pair of p-cycles chosen to protect a link must have link disjoint backup paths as shown in Fig. 2. We consider the bidirectional graph G(N,L) and formulate an alternative ILP. This ILP uses a pair of p-cycles to protect each link. Here N is the number of nodes and L is the number of links. The set of cycles, and the set of pair of p-cycles for each link are precomputed and given as inputs to the optimization model.
Definition 1 (Protection-Pair).
A protection-pair of link , is defined as a pair of p-cycles which are link disjoint or have only one link as common on-cycle link.
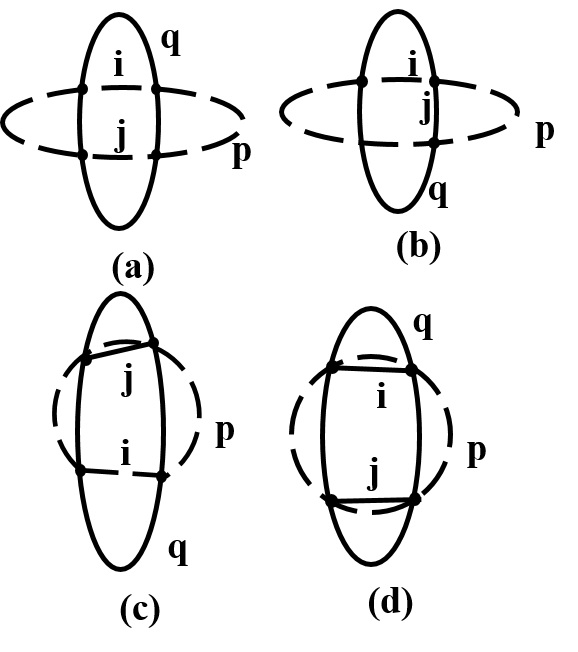
The protection-pair for each link is chosen independently. The p-cycles are shared for protecting more than one link. Thus a p-cycle can pair with many other p-cycles simultaneously. In some cases the same pair of protecting p-cycles can protect more than one links. The simultaneous failure of two links having same protection-pair may lead to a situation when, the failed links have only one p-cycle for protection. The spare capacity required in such cases is higher. Possible scenarios when a pair of p-cycles can protect more than one link are shown in Fig. 3.
Fig. 3 (a) shows the case in which two links and are ‘on-cycle’ on p-cycle and ‘straddling’ on p-cycle . If link fails, the protection is provided by one of the p-cycles from the pair. If second failure occur on the p-cycle which is used to restore the first failure, then the traffic is diverted on to the unused p-cycle of the pair. Link is also protected by the pair of p-cycle and in the same way. In case of simultaneous failure of link and , the p-cycle fails to protect the links, and traffic for both the links is restored by the p-cycle . The required number of copies of p-cycles and should be sufficient to incorporate all the two failure scenarios mentioned above. The number of copies of p-cycle required will be the maximum of the working capacities of and . The number of copies of p-cycle will be the sum of half the capacities of and approximated to the lowest integer greater than or equal to the sum.
| (6) |
To ensure protection for the three cases shown in Fig. 3 (b), 3(c) and 3(d), number of copies of p-cycle and required will be the same as needed to protect the maximum of the capacities on link and . In the case of simultaneous failure of links and , the p-cycles and protect links and respectively.
III-A ILP for DB method
This linear program finds the minimum spare capacity required to form p-cycles, ensuring the protection of each link from two simultaneous link failure using the DB method.
Notations
S=set of links.
P=set of cycles.
=set of protection-pair p-cycles of link , indexed as .
For a link having in the set , we define the indicator variable as follows,
We also define the indicator variable ,
Variables
=spare capacity on link .
=working capacity on link .
=cost of unit capacity of link .
= number of copies of p-cycle .
=number of copies of p-cycle required to protect link in pair with p-cycle to protect link from two simultaneous failure.
=number of copies of p-cycle required to protect working capacity of link .
Minimize:
| (7) |
Subject to :
| (8) |
If link is an on-cycle or a straddling link on both and , then
| (9) |
If link is a straddling link on and on-cycle on , then,
| (10) |
| (11) |
| (12) |
.
| (13) |
| (14) |
The objective function (7) minimizes the total spare capacity. Constraint (8), (9) and (10) ensure full protection of the working capacity on each link from two simultaneous link failures. Constraint (11) calculates the number of copies of p-cycle required to protect a link as the sum of the number of copies of the p-cycle in pair with other p-cycles , required to protect the link . Constraint (12) ensures that the number of copies of p-cycle is sufficient to protect the link with highest working capacity. Constraint (12) also takes care of the case when two links share the same pair of p-cycles, as described in this section earlier and illustrated by Fig. (3). Constraint (13) ensures that spare capacity on each link is sufficient to form the p-cycles.
IV Results and discussion
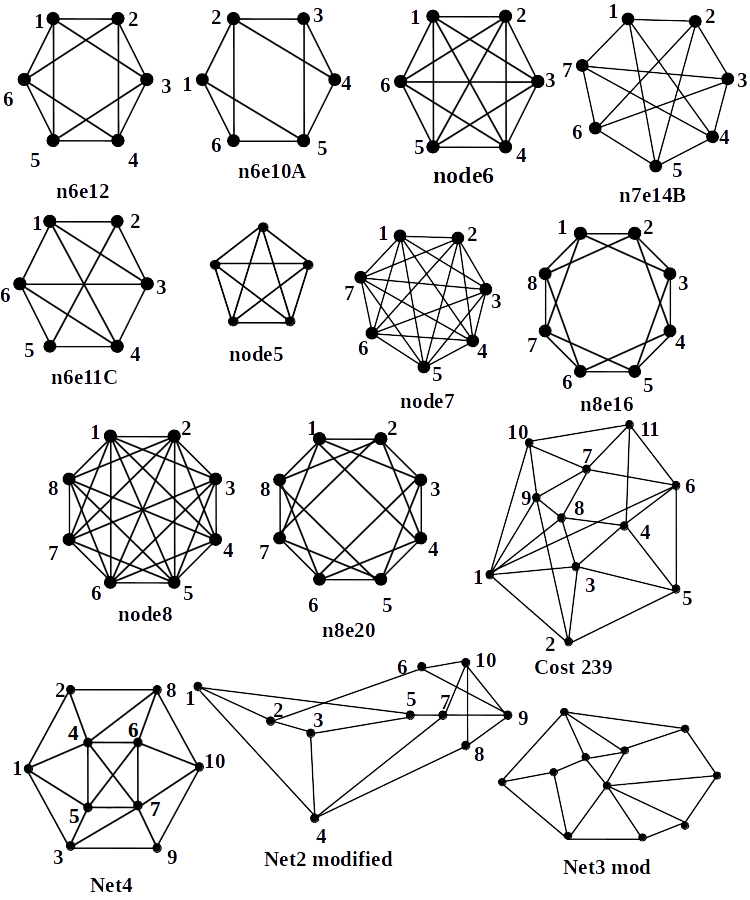
ILP formulation is carried out on scilab 5.5, and ILOG CPLEX 9 is used to solve the ILP on AMD Opteron (tm) 1.8 GHz CPU. The number of variables required in the SG method is where is the number of links, and is the number of cycles. In the SG method number of variables and constraints involved in the ILP formulation is . Variables and constraints involved in ILP formulation of DB method is . Therefore, the complexity of SG method is lower than the DB method. One can also note that the complexity of the SG method is same as that of the best known single fault protection method. As evident from the simulation results in Table 1, time to solve the ILP is significantly less for the SG method. Spare capacity efficiency (SE) is the ratio of spare capacity required for protection and the working capacity of network, and it is given by Eqn. (15).
| (15) |
The SE should be as low as possible. Simulation results shows the smaller value of SE for most of the networks (see table 1) with the SG method as compared to DB method. While for average nodal degree higher than 3.6, SG method always gives better SE.
Further, it is observed that the SG method has better restoration speed than DB method. When the first failure occurs, the failed link is restored as a straddling link. In this way, at least half of the copies of p-cycle remain in spare. Restoration path of the first failed link does not require rearrangement if second failure is also on a straddling link. If the second failure occur on the on-cycle link of p-cycle, only half of the traffic requires restoration second time. In case of the DB method restoration of the second failure requires the switching of the traffic from the first p-cycle to a different p-cycle. This restoration will be slower as switching action takes place at nodes which may not be the end nodes of the failed link.
| DB method | Proposed method | |||||
| Network | Avg | Working | SE | ILP time | SE | ILP time |
| degree | capacity | (in sec) | (in sec) | |||
| n6e10A | 3.3 | 40 | 2.80 | 0 | 2.45 | 0 |
| net2m | 3.4 | 164 | 3.03 | 0.07 | 3.10 | 0.01 |
| net3mod | 3.4 | 198 | 2.57 | 22.54 | 2.65 | 0.03 |
| n6e11C | 3.6 | 38 | 2.63 | 0.01 | 2.63 | 0 |
| n8e16 | 4 | 80 | 1.70 | 115906 | 1.28 | 14.53 |
| n7e14B | 4 | 56 | 1.89 | 18487 | 1.50 | 0.01 |
| n6e12 | 4 | 36 | 1.78 | 32.23 | 1.50 | 0.11 |
| node5 | 4 | 20 | 1.50 | 4.12 | 1.00 | 0 |
| net4 | 4.4 | 142 | _ | *inf | 1.65 | 0.48 |
| cost239 | 4.7 | 172 | _ | *inf | 1.06 | 1745.93 |
| node6 | 5 | 30 | 1.00 | 52594 | 0.80 | 2.72 |
| n8e20 | 5 | 72 | _ | *inf | 1.11 | 0.93 |
| node7 | 6 | 42 | _ | *inf | 0.67 | 1498.58 |
| node8 | 7 | 56 | _ | *inf | 0.57 | 195681.18 |
*inf means solution cold not be achieved by the machine used by us.
V Conclusion
From this study, we can conclude that the spare capacity requirement for deterministic two-link failure protection is less for the SG method as compared to the DB method. SG method is also able to compute the spare capacity of large networks for which DB method fails, because number of variables required for the SG method is while DB method requires variables. Also, ILP of the SG method is simpler than any other two-link failure protection method. Consequently, the time required in the ILP formulation and ILP solution is also significantly less.
References
- [1] D. Zhou and S. Subramaniam, “Survivability in optical networks,” IEEE Network, vol. 14, no. 6, pp. 16–23, Nov 2000.
- [2] M. F. Habib, M. Tornatore, F. Dikbiyik, and B. Mukherjee, “Disaster survivability in optical communication networks,” Computer Communications, vol. 36, no. 6, pp. 630 – 644, 2013.
- [3] W. D. Grover, “Cycle-oriented distributed preconfiguration: Ring-like speed with mesh-like capacity for self-planning network restoration,” Proceedings of IEEE ICC ‘98, Altanta, vol. 54, no. 17, pp. 537 – 543, 1998.
- [4] R. Asthana, Y. N. Singh, and W. D. Grover, “p-cycles: An overview,” IEEE Communications Surveys Tutorials, vol. 12, no. 1, pp. 97–111, First 2010.
- [5] T. Feng, L. Long, A. E. Kamal, and L. Ruan, “Two-link failure protection in wdm mesh networks with p-cycles,” Comput. Netw., vol. 54, no. 17, pp. 3068–3080, Dec. 2010.