Effect of payload size on goodput when message segmentations occur for wireless networks: Case of packet corruptions recovered by stop-and-wait protocol
Abstract
This paper investigates the effect of payload size on goodput for wireless networks where packets created from a message through a segmentation function are lost due to bit errors and they are recovered by a stop-and-wait protocol. To achieve this, we derive the exact analytical form of goodput using the analytical form of a packet-size distribution, given a message-size distribution and a payload size. In previous work, the packet sizes are assumed to be constant, which are payload size plus header size, although actual segmented packets are not constant in size. Hence, this constant packet-size assumption may be not justified for goodput analysis. From numerical results, we show that the constant packet-size assumption is not justified under low bit-error rates. Furthermore, we indicate that the curves of goodput are concave in payload size under high bit-error rates. In addition, we show that the larger mean bit-error burst length yields less concave curves of goodput.
Index Terms:
Message segmentation, wireless networks, payload size, goodput, burst bit error, stop-and-wait protocol.I Introduction
In the past decades, the evolution of wireless communication technologies, such as widespread introduction of wireless local area networks (WLANs) and emergence of cellular or Wi-Fi wide area networks, changed our life style dramatically. Wireless networks allow users to provide mobile communication service, which is a more beneficial characteristic compared with wired networks. However, the wireless networks have two main characteristics with negative impact on quality of service (QoS): high bit-error rate and low link capacity.
For wireless networks, which use open air as the transmission medium, high bit-error rates () are observed. Hence, wireless networks exhibit unacceptable corruption probabilities of packets, i.e., data units transferred over networks.
Wireless networks still provide lower link capacity, compared to the fiber optical wired links. The range of the link capacity for popular WLANs is Mbps. Because many terminals share the same transmission medium, the attainable capacity of each terminal becomes further smaller.
To provide an error-free transmission service of messages, i.e., data units generated by reliable applications such as transfer of Web pages and e-mail, over the wireless networks, solutions to overcome the high bit-error rate problem are required. The straightforward solution is implementation of an error-recovery function for each terminal (or host), which allows a sender to retransmit packets that are lost due to bit error and congestion. For example, IEEE 802.11 standard media access control protocol for WLANs [1] specifies a stop-and-wait protocol (SWP) to realize the error-recovery function in a simple manner.
Messages are frequently larger than the maximum permitted packet size, namely payload size. To convey such messages over the network, a sender implements a message-segmentation function. It enables the sender to divide a single message larger than the payload size into multiple packets.
The packet-size distribution has been significantly changed from the message-size distribution through message segmentations. For example, papers [2, 3] show this tendency using actual traffic measurements. On the other hand, paper [4] derives the analytical form of a packet-size distribution when a message-size distribution and a payload size are given. To achieve this, in paper [4] terms called body and edge packets are introduced. The body packet is defined as a segmented packet appearing between the head and penultimate packets in the original message. The edge packet is the final segmented packet if a message is segmented, or the message itself if it is not segmented. The sizes of body packets are equal to payload size plus header size, whereas those of edge packets are variable, not to exceed payload size plus header size. From numerical results based on traffic measurement, the findings include that the edge-packet occurrence probability is not negligible in some cases [4].
The packet size affects QoS measures such as mean response time and goodput because link-level transmission delay and packet-corruption probability depends on the packet size. For more details, link-level transmission delay is simply given by the packet size divided by the link capacity [5, pp. 64–65] and the packet-corruption probability is approximately proportional to the packet size [6, p. 132]. Especially, the packet size significantly affects these QoS measures for high bit-error prone and/or low bandwidth links such wireless links.
The packet sizes are restricted to the payload size. Furthermore, the payload size is one of the controllable (manageable) parameters. If payload size is enough small, the wireless networks are operating inefficiently because an overhead such as header per packet transmission is not negligible. On the other hand, if the packet size is larger, the packet is more likely to be corrupted, necessitating more retransmissions and resulting in reduction of goodput. To solve this tradeoff issue, many studies such as [7, 8, 9, 10, 11, 12, 13] proposed the adaptive payload sizing scheme.
In previous studies, however, segmented-packet-size sequence behavior through the message-segmentation function, has not been taken into consideration. Thus, the all packet sizes are assumed to be constant, which are payload size plus header one, although the edge-packet occurrence probability is assumed be negligible.
The purpose of this paper is to answer the following research questions:
-
Q1: What is approximation accuracy of constant packet-size assumption?, and
-
Q2: What is relationship between payload size and goodput in the case of the burst bit-error occurrence in addition to the independent one?
To achieve this, we develop the exact analytical form of goodput when segmented packets through the message-segmentation function are lost due to bit error and they are recovered by an SWP.
The rest of the paper is organized as follows. In the next section, we describe the communication network model underlying our study. In Section III, a model of a segmented packet size sequence is provided, given the message-size distribution and the payload size. Section IV derives the exact analytical form of goodput. Section V investigates the effect of payload size on good for a simple scenario where message sizes are constant. Finally, Section VI summarizes this paper and mentions future work.
II Communication network model
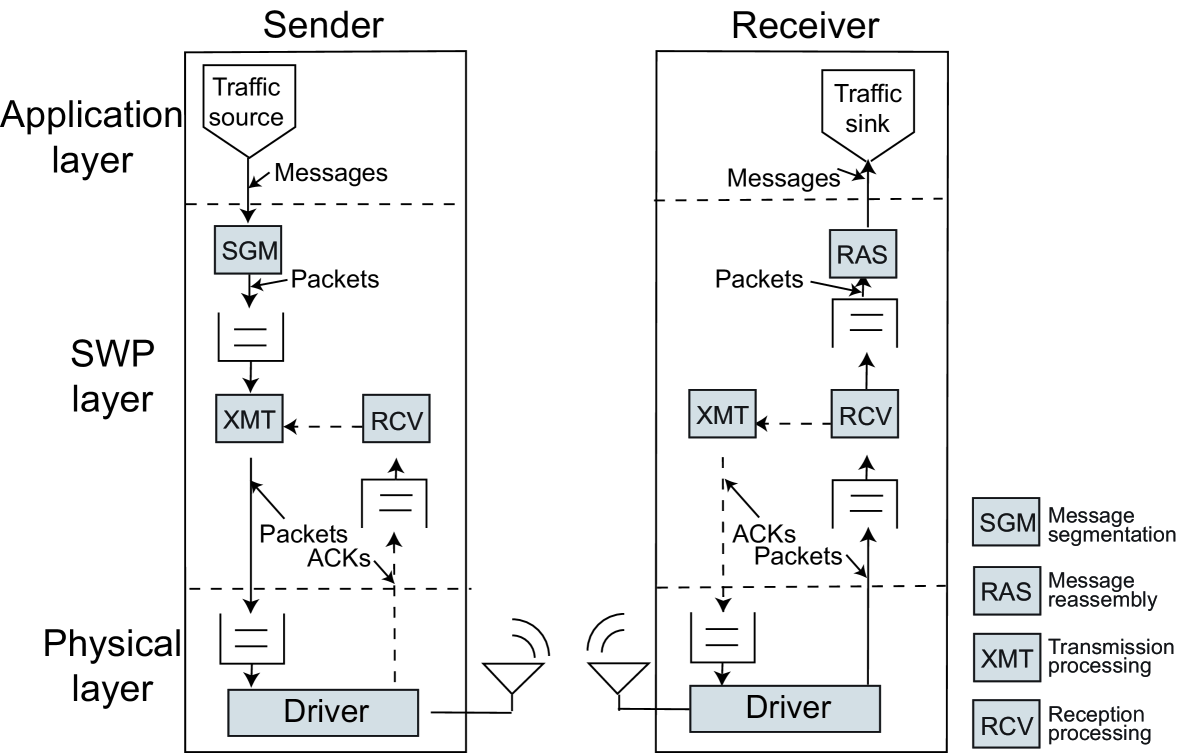
In this section, we first explain the two-layered communication network model under consideration. Next, the model of data units introduced in this paper at the respective layer is described.
II-A Layer model
We consider a communication network whose conceptual representation is shown in Fig. 1. Each station (a sender and a receiver) has three layers. The middle layer is referred to as an SWP layer. It implements message segmentation-reassembly and error-recovery functions. The error-recovery function is assumed to be implemented in a stop-and-wait scheme. The layer above the SWP layer, namely the application layer, contains a traffic source and sink. The traffic source generates the data units. On the other hand, the traffic sink terminates the corresponding data units. The layer below the SWP layer, namely the physical layer, contains an entity that can transfer data units over wireless links at a sender.
II-B Data unit model
We define data units exchanged between peer entities at the respective layer: messages and packets.
-
Message: a data unit generated at a traffic source of the application layer with a given size distribution.
-
Packet: a data unit created from a message through a segmentation-reassembly function, and transferred over wireless links. It consists of an information field and the appropriate protocol control information (PCI), such as a header and/or trailer. The information field contains a (divided) message.
The message-segmentation function implemented in the sender’s segmentation-reassembly layer enables a single message to be divided into multiple packets if the message size is larger than the payload size, denote by . The receiver’s segmentation-reassembly layer performs a message-reassembly function, thus reassembling the segmented packets before delivering them to the application layer.
II-C Burst bit error occurrence model
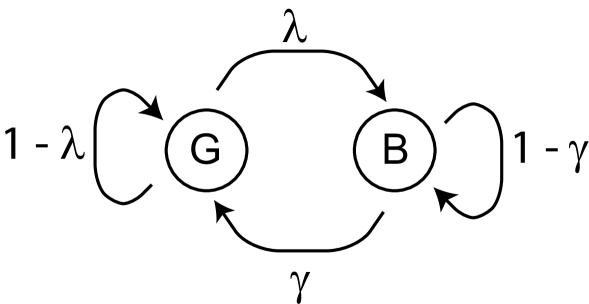
Bit errors for WLANs are reported to occur in bursts[14]. One of the simple but capable of capturing the bit-error burstiness is the Gilbert model [15]. The process of the Gilbert model is a two-state Markov chain with a transition diagram shown in Fig. 2. This Markov property enables us to obtain the form of goodput in a simple manner, as will be mentioned in Section IV.
State in this Markov chain represents the link in a “good” state, indicating that it is operating at very low bit-error rate denoted by . On the other hand, state B represents the link is operating in a fading or shadowing condition at high bit-error rate, i.e., in a “bad” state, denoted by . Within each state, bit errors occur independently at their own rates.
Let where be the link state at discrete time whose unit is bit. We denote a transition rate from state G to state B by where and that from state B to state G by where . Then, the stochastic process is represented as a discrete-time Markov chain with a transition matrix
| (1) |
We let be the stationary probability vector of process , i.e., the stationary probability vector of transition probability matrix . Then, its elements are given by
| (2) |
Here, is the stationary state probability that the link is in state G, and is that in state B (usually ).
We define the mean bit-error rate as
| (3) |
assuming that .
Remark 1
i.i.d. bit error model. Assume that bit errors occur independently with a fixed bit-error rate . This i.i.d. bit error model is identical to the burst bit-error model in the following cases: , , or . Thus, the burst bit-error model introduced above accommodates the i.i.d. model. Actually, the results from the correlated bit-error model in these cases agree with those from the i.i.d. model (see Proposition 3).
II-D Assumptions
For analytical tractability, we make the following assumptions.
- A1:
-
Message sizes are mutually independent and identically distributed according to a common message-size distribution function . The distribution has a finite mean value , which is referred to as the mean message size.
- A2:
-
When a sender cannot receive a reply from a receiver, i.e., acknowledgement, within in a specific constant interval timeout after transmission, it retransmits the lost packet.
We use notation to express the value of the interval timeout in sec, whereas which is expressed in bits, instead of , will be used for goodput analysis in Section IV. In this paper, the value of is given by where is the capacity of the wireless link.
- A3:
-
We denote size of the acknowledgement packet, that is ACK, by .
- A4:
-
The maximum number of retransmission attempts of the same packet is infinite.
- A5:
-
The sender operates under a heavy traffic assumption, which implies that the sender’s SWP layer always has a packet available to be sent.
- A6:
-
the size of PCI is constant and equal to .
- A7:
-
the packet of the first transmission arrives at the link in state G with probability and in state B with probability .
- A8:
-
the sum of processing delay and propagation delay, which is independent of a packet size, is constant and is denoted by .
III Packet size sequence model
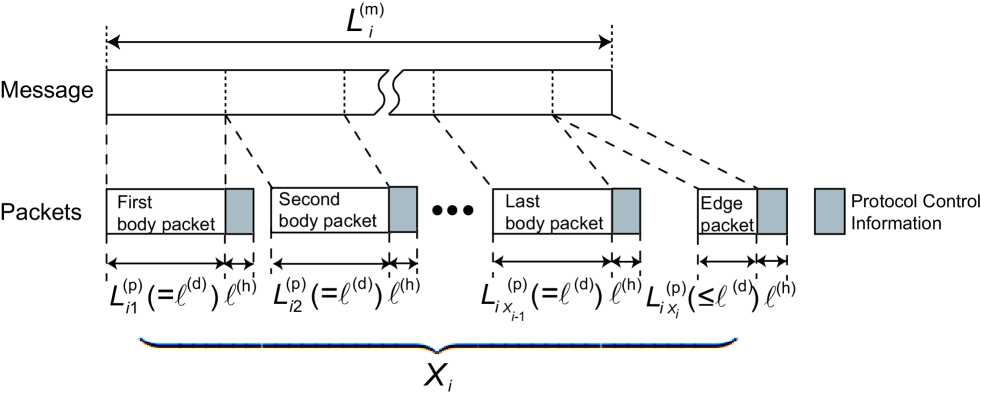
The creation of packets from a message through message segmentation is shown in Fig. 3. As shown in Fig. 3, if , then the th message is divided into multiple packets. Denoting the size of an information field of the th packet for the th message by , where and , we have
| (4) |
with . Here, the operator represents the smallest integer that is greater than or equal to .
We categorize a set of packets for the th message into two kinds: body and edge packets. we refer to a segmented packet appearing between the head and the penultimate packets i.e., packet from first to st as a body packet, and the final packet, i.e., th packet as an edge packet.
If , then the th message is not segmented, and a single packet, whose information field is identical to the original message, is generated. We also refer to this as edge packet because it satisfies (4). We note that the size of body packets are always equal to , whereas that of edge packets is variable but does not exceed .
Remark 2
The edge-packet size is less than or equal to . For example, edge-packet sizes equal when message sizes are a multiple of although message segmentations happen (see Section V-B).
We construct a stochastic process , replacing the pair of epoch labels with an in-sequence number for in (4).
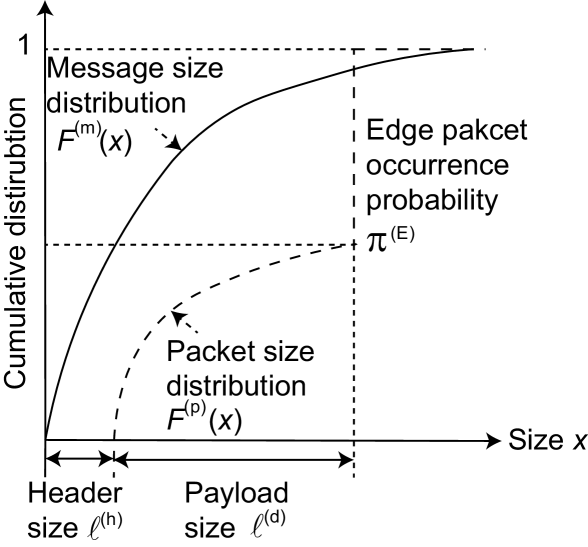
Denoting the stationary packet size distribution by , the assumptions of A1 and A2, using the argument [4], we have
| (5) |
where is an edge-packet occurrence probability, and is a stationary edge-packet size distribution (see Fig 4).
The forms of and are given by
| (6) |
and
| (7) |
From the definition of body packets, the stationary body-packet-size distribution is clearly given by . The occurrence probabilities of body packets and edge packets are given by and , respectively.
Letting be the mean of stationary distribution of , from we have
| (8) |
Example 1
Case of discrete message-size distribution[4, Example 4]. Consider the case where the message-size distribution function is given by
| (9) |
where , , for , and .
The form of is given by with . This can be intuitively shown from the fact that 1) packets are created from one message of size , and 2) they consist of packets of size , that is a body packet, and one edge packet. The packet-size distribution can be written as
| (10) |
The form of (10) can be rewritten as
| (11) |
where
| (12a) | ||||
| (12b) | ||||
IV Goodput analysis
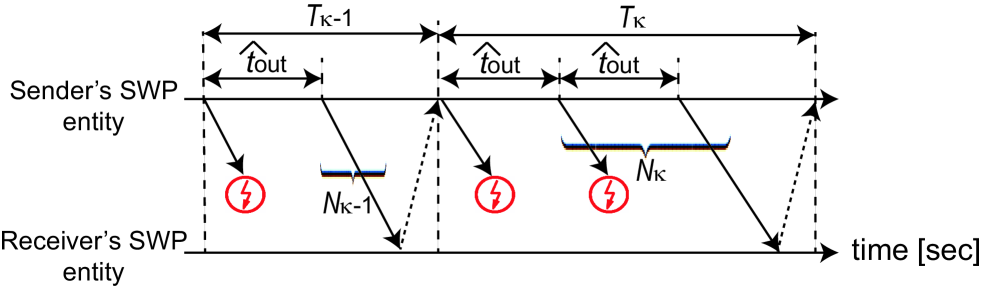
In this section, we derive the form of long-run goodput. Let be long-run goodput of a single SWP connection, which is defined as the mean number of bits by a receiver’s SWP entity per unit time [sec]. To derive the form of , we introduce the following random variables as shown in Fig. 5:
-
: time interval between two successful transmissions of the th packet, which is expressed in seconds,
-
: number of transmissions until when the th packet has been successfully transmitted, .
From the theory of renewal reward process [16, Sec. 3.9], we have the following proposition.
Proposition 1
The form of goodput is given by
| (13) |
Proof.
From the Markovian burst bit-error occurrence model mentioned in Section II-C the event point where a sender receives ACK is a renewal point. Then, the stochastic process becomes a renewal process.
The assumption A2 yields the form of given by
| (16) |
Remark 3
Equation (16) shows that overhead of per one packet transmission is at least necessary for one transmission of a packet with size equaled to .
To derive the form of , we introduce the following events:
-
: event that satisfying:
-
•
the transmission of a packet of bits was started at time [bit],
-
•
it has been finished successfully, i.e., with no bit errors, and
-
•
the link state is at the time just after the transmission, i.e., .
-
•
-
: the same event as , except that the transmission failed (i.e., the packet contains one or more erroneous bits).
Then, we have the following lemma.
Lemma 1
Let and be matrices whose th entries are conditional probabilities of events and , respectively, given that . Then, we have
| (17) | ||||
| and | ||||
| (18) | ||||
Here, is defined as the matrix of which th entry is the conditional probability that the link state changes to after a successful bit transmission, given that it was :
| (19) |
Proposition 2
The form of is given by
| (20) |
where is a unit vector and
| (21) |
Proof.
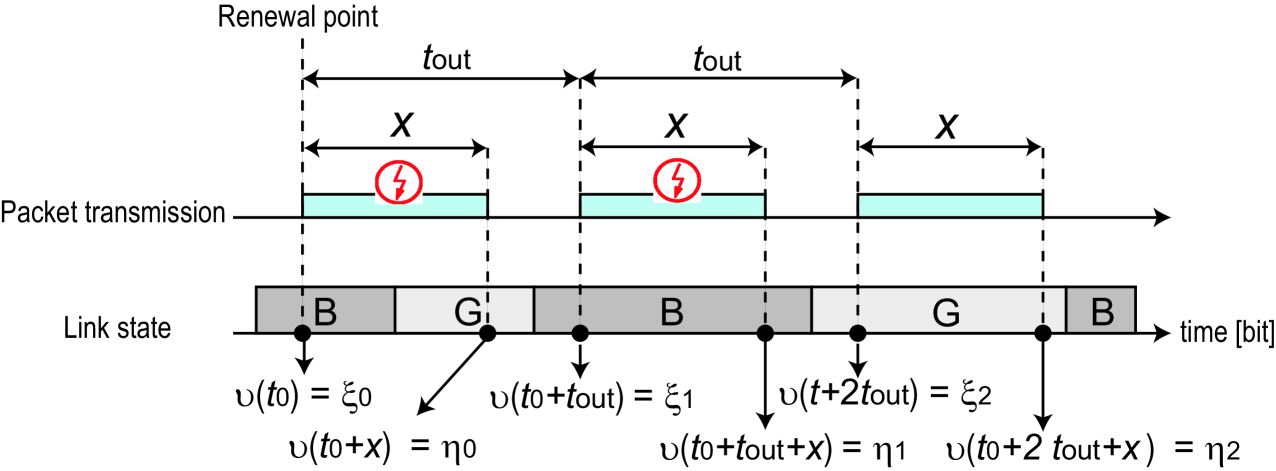
We consider the following scenario:
-
•
the th packet whose size is , i.e., , was transmitted first time at time [bit], and
-
•
it has been transmitted unsuccessfully times and transmitted successfully in the th transmission, i.e., in the th retransmission, resulting in .
An example of a packet transmission sequence, where and where when the packet of the second retransmission has been transmitted successfully is shown in Fig. 6.
Proposition 3
Let us consider the i.i.d. bit-error model with , which is a special case described in Remark 1. In this case, we have
| (23) |
where
| (24) |
Proof.
From , we have
| (25) |
From , for is given by
| (26) |
Furthermore, we have
| (27) |
Because of the definition of , that is the stationary probability vector of , we obtain
| (28) |
Because is the eigen-value corresponding to the eigen-vector of matrix , we have
| (29) |
Hence, we obtain
| (30) |
The form of is given by
| (from (21)) | |||||
| (from (28)) | |||||
| (from (30)) | |||||
| (from (29)) | |||||
| (from (24)) | |||||
| (from (28)) | (31) | ||||
Then, in a recursive manner, we obtain
| (32) |
On the other hand, we have
| (from (29)) | |||||
| (33) | |||||
∎
Proposition 4
The form of in (13) is given by
| (34) |
Proof.
Remark 4
The term of in (34) implies the mean retransmission times of the packet whose size is , i.e., .
V Numerical results and discussions
In this section, we answer the research questions mentioned in section I. First, we explain the assumptions made for numerical results. Next, we validate the constant packet-size assumption to answer research question Q1. In final, we discuss the relationship between payload size and goodput under several bit-error link conditions to answer research question Q2.
V-A Assumptions
In the following numerical results, we assume that 1) link capacity : Mbps, and 2) Bit-error rates of link state : , , 3) header size: (= ) = 38 bytes, 4) timeout value : msec, and 5) propagation delay : msec.
To answer research questions comprehensively, we consider the simple case, i.e., case of constant message size. Thus, message sizes are assumed to be distributed according to given by
| (41) |
The constant message size is assumed to be bytes, which is the approximate measured mean message size of Web object [17].
V-B Validation of constant packet-size assumption
From the case of , , and for example 1, the packet-size distribution is given by
| (42) |
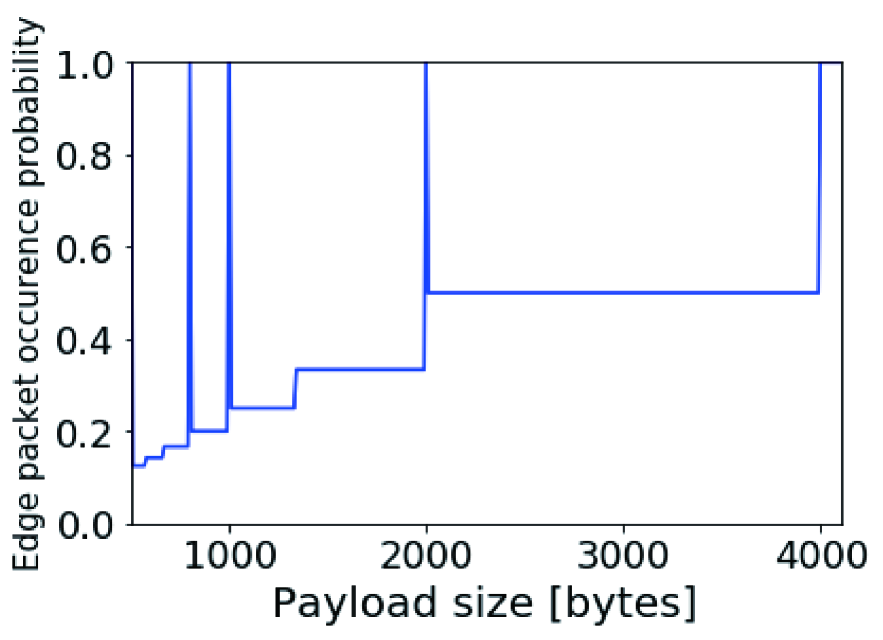
Figure 7 shows edge-packet occurrence probability versus payload size . From this figure, edge-packet occurrence probability has the stepwise tendency. We note that the value of is one but all packets are constant in size when message size is a multiple of payload size, such as 500, 1000, 2000, and 4000 bytes.
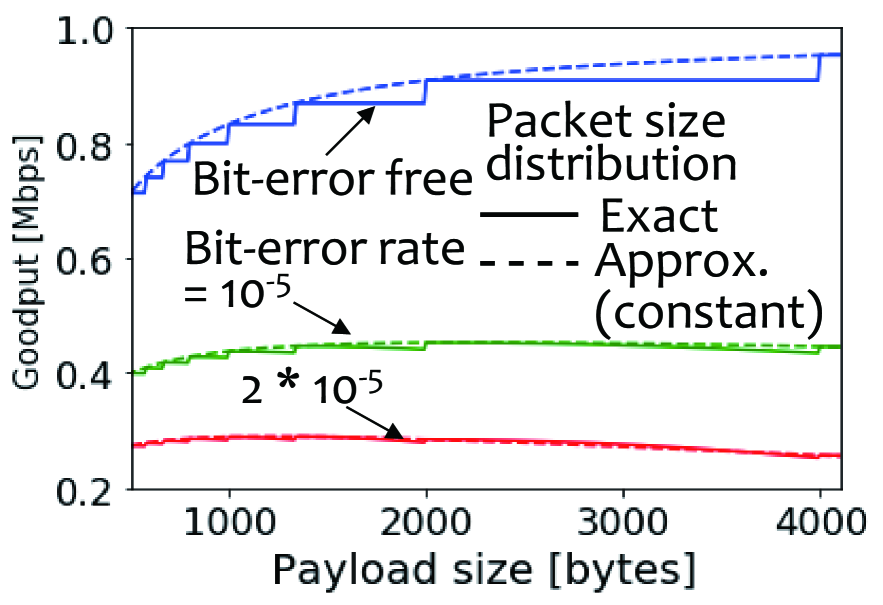
Figure 8 shows goodput versus payload size for different bit-error rates . In this figure, dashed line means goodput using constant packet-size approximation. From this figure this approximation error is not negligible under low bit-error rate. On the other hand, under high bit-error rate, this error is negligible. The reason for this is that the number of retransmissions of packet whose size is , which is the maximum packet size, are dominant in the total number of transmissions of packets because the packet is more likely to be corrupted (or retransmitted) if the packet size is larger [18].
V-C Impact of payload size to goodput in case of independent bit errors
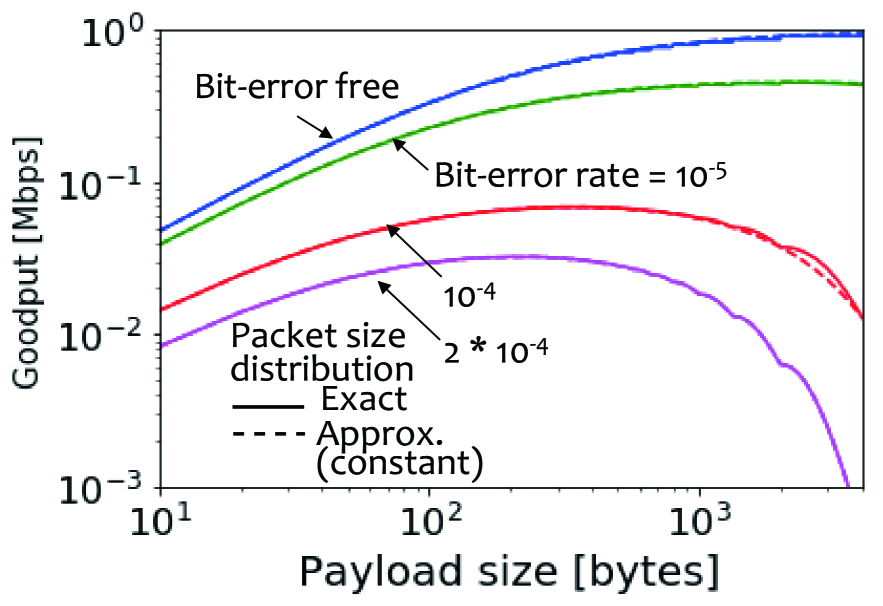
Figure 9 shows goodput versus payload size for different bit-error rates in case of i.i.d. bit errors. This figure shows that the curves of goodput are concave under high bit-error rates. The reason for this is as follows:
-
•
If payload size is enough small, the communication network is operating in efficiency because an overheating transmitting PCI and acknowledgements is not negligible.
-
•
On the other hand, as payload size increases, the packet is more likely to be corrupted. Hence, it causes more retransmissions, resulting in reduced goodput.
From the above argument, there exists an optimum payload size in the sense of maximizing goodput.
V-D Impact of payload size to goodput in case of burst bit errors
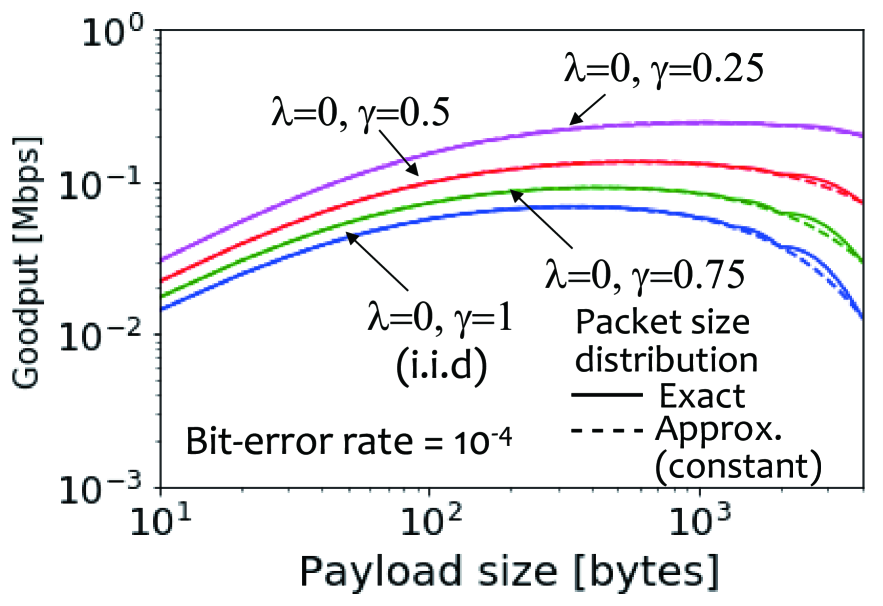
Final, we investigate the effect of mean bit-error burst length on goodput. Figure 10 shows goodput versus payload size for different mean bit-error burst lengths in the case of mean bit-error rate equaled to . This figure shows that the larger mean bit-error burst length yields less concave curves of goodput.
VI Conclusion
This paper investigated the effect of payload size on goodput for wireless networks where message segmentations occur and corrupted packets are recovered by a stop-and-wait protocol. To achieve this, we derived the analytical form of goodput for wireless networks using segmented packet-size distribution, given a message-size distribution and a payload size.
From numerical results, we show that the traditional constant packet-size assumption is not justified in the case of low bit error rates. Furthermore, we showed that the curves of goodput are concave in payload size under high bit error rates. In addition, we indicated that the larger mean bit-error burst length yields less concave curves of goodput.
The remaining issues include the investigation of the effect of payload size on goodput for various message size distributions, the extension of our model to realistic protocols rather than a simple stop-and wait protocol, and the development of simple and cost-effective payload adaptation algorithm in a wireless environment whose condition is dynamically changed.
Acknowledgment
This work was supported in part by JSPS KAKENHI Grant Number JP15K00139.
References
- [1] B. P. Crow, I. Widjaja, J. G. Kim, and P. T. Sakai, “IEEE 802.11 wireless local area networks,” IEEE Communications Magazine, vol. 35, no. 9, pp. 116–126, Sept. 1997.
- [2] C. Fraleigh, S. Moon, B. Lyles, C. Cotton, M. Khan, D. Moll, R. Rockell, T. Seely, and C. Diot, “Packet-level traffic measurements from the Sprint IP backbone,” IEEE Network, vol. 17, no. 6, pp. 6–16, Nov./Dec. 2003.
- [3] M. Allman, “A web server’s view of the transport layer,” ACM SIGCOMM Computer Communication Review, vol. 30, no. 5, pp. 10–20, Oct. 2000.
- [4] T. Ikegawa, Y. Kishi, and Y. Takahashi, “Data-unit-size distribution model when message segmentations occur,” Performance Evaluation, vol. 69, no. 1, pp. 1–16, Jan. 2012.
- [5] J. Kurose and . Ross, Computer Networking: A Top-Down Approach, 7th ed. Pearson Education Kimited, 2016.
- [6] M. Schwartz, Telecommunication Networks: Protocols, Modeling and Analysis. Addison-Wesley Publishing Company, 1987.
- [7] E. Modiano, “An adaptive algorithm for optimizing the packet size used in wireless ARQ protocols,” Journal Wireless Networks, vol. 5, no. 4, pp. 279–286, July 1999.
- [8] M. C. Vuran and I. F. Akyildiz, “Cross-layer packet size optimization for wireless terrestrial, underwater, and underground sensor networks,” in IEEE INFOCOM 2008 – The 27th Conference on Computer Communications, April 2008, pp. 780–788.
- [9] P. R. Jelenković and J. Tan, “Dynamic packet fragmentation for wireless channels with failures,” in Proc. ACM MobiHoc’08, 2008, pp. 73–82.
- [10] P. Lin and T. Lin, “Machine-learning-based adaptive approach for frame-size optimization in wireless LAN environments,” IEEE Transactions on Vehicular Technology, vol. 58, no. 9, pp. 5060–5073, Nov. 2009.
- [11] G. Ciccarese, M. D. Blasi, P. Marra, C. Palazzo, and L. Patrono, “An algorithm for controlling packet size in IEEE 802.16e networks,” Computer Networks, vol. 55, no. 13, pp. 2873 – 2885, 2011.
- [12] W. Dong, C. Chen, X. Liu, Y. He, Y. Liu, J. Bu, and X. Xu, “Dynamic packet length control in wireless sensor networks,” IEEE Transactions on Wireless Communications, vol. 13, no. 3, pp. 1172–1181, March 2014.
- [13] D. Kim, H. Nam, and D. Kim, “Adaptive code dissemination based on link quality in wireless sensor networks,” IEEE Internet of Things Journal, vol. 4, no. 3, pp. 685–695, June 2017.
- [14] A. Willig, M. Kubisch, C. Hoene, and A. Wolisz, “Measurements of a wireless link in an industrial environment using an IEEE 802.11-compliant physical layer,” IEEE Transactions on Industrial Electronics, vol. 49, no. 6, pp. 1265–1282, Dec. 2002.
- [15] E. N. Gilbert, “Capacity of a burst-noise channel,” The Bell System Technical Journal, vol. 39, no. 9, pp. 1253–1265, Sept. 1960.
- [16] S. M. Ross, Applied probability models with optimization applications, ser. Dover Books on Mathematics. Mineola, NY: Dover, 1992.
- [17] M. Molina, P. Castelli, and G. Foddis, “Web traffic modeling exploiting TCP connections’ temporal clustering through HTML-REDUCE,” IEEE Network, vol. 14, no. 3, pp. 46–55, May/June 2000.
- [18] T. Ikegawa and Y. Takahashi, “Effect of retransmitted packet size preservation property for wireless networks with a reliable communication protocol,” in Proc. ACM MSWiM’05: the 8th ACM International Symposium on Modeling, Analysis and Simulation of Wireless and Mobile Systems, Oct. 2005, pp. 313–317.