Environment Sensing Considering the Occlusion Effect: A Multi-View Approach
Abstract
In this paper, we consider the problem of sensing the environment within a wireless cellular framework. Specifically, multiple user equipments (UEs) send sounding signals to one or multiple base stations (BSs) and then a centralized processor retrieves the environmental information from all the channel information obtained at the BS(s). Taking into account the occlusion effect that is common in the wireless context, we make full use of the different views of the environment from different users and/or BS(s), and propose an effective sensing algorithm called GAMP-MVSVR (generalized-approximate-message-passing-based multi-view sparse vector reconstruction). In the proposed algorithm, a multi-layer factor graph is constructed to iteratively estimate the scattering coefficients of the cloud points and their occlusion relationship. In each iteration, the occlusion relationship between the cloud points of the sparse environment is recalculated according to a simple occlusion detection rule, and in turn, used to estimate the scattering coefficients of the cloud points. Our proposed algorithm can achieve improved sensing performance with multi-BS collaboration in addition to the multi-views from the UEs. The simulation results verify its convergence and effectiveness.
Index Terms:
Integrated sensing and communication (ISAC), environment sensing, occlusion effect, multi-view sensing.I Introduction
I-A Motivation
The emergence of innovative wireless communication technologies, such as ultra-massive multiple input multiple output (MIMO) technology, intelligent reflective surface (IRS), and wireless artificial intelligence (AI) [1, 2, 3], etc., provides more possibilities for the development of future wireless communication systems design. In the foreseeable future wireless communication application scenarios, autonomous driving [4], intelligent robot localization [5], and unmanned aerial vehicle (UAV) control [6] require not only wireless broadband connections, but also accurate environmental information, including the location, shape, and electromagnetic (EM) characteristics, etc. of objects in the environment. Therefore, integrated sensing and communication (ISAC), as a research hotspot for the next generation wireless communication system, aims to use the wireless communication equipment and infrastructure to achieve environment sensing.
Such kind of environment sensing has long been accomplished by traditional radar technology and its later evolution of joint radar and communication [7]. The latter usually aims to achieve the sharing of software and hardware equipment and time-frequency resources between radar equipment and communication equipment. Compared with traditional radar or early joint radar and communication systems, efficient use of communication signals in the existing communication systems for environment sensing, and efficient exploitation of the environment sensing results to enhance communication, are two major design goals of the ISAC systems. For the former goal, one straightforward realization is to fully exploit the environmental information embedded in the received communication data, due to the simple fact that the distribution of environmental scatterers dramatically affects the wireless multipath channels. For the latter, direct channel prediction (reconstruction) can be conducted based on the sensed distribution and characteristics of scatterers within the environment thus to enhance the performance of communication [8, 9, 10]. In this paper, we mainly focus on the first part and study how to perform efficient and accurate environment sensing based on the uplink data received from multiple users, in a way compatible with existing communication systems thus to achieve a smooth integration of communication and sensing.
One major challenge to do this is the large number of unknown variables embedded in the generally complicated environment, including the unknown location and EM characteristics of the environmental scatterers themselves, and the very common occlusion effect within and between scatterers, which blocks the propagation of EM waves and makes portions of some scatterers or even all of them invisible to the receivers. In such a case, it is hard for a single user or base station (BS) to fully sense the entire environment and the different views of the environment from different users and/or BS(s) should be exploited. However, a challenge still remains since in each separate sensing (transmitting and receiving), we generally cannot know which scatterers or which part of them participates in the final generation of the received signal in an environment yet to know, and it differs from user to user and BS to BS. This motivates us to develop a practical and efficient multi-view sensing algorithm to deal with the above problem.
I-B Related Works
So far, the design of ISAC system has raised extensive research effort. In [11], the author comprehensively discussed the novel applications, key performance requirements, challenges, and future research directions of ISAC system designs. In [12], the author compared the difference between the radar sensing scheme and the ISAC scheme. The author showcased that a common signal wave should be jointly designed to realize the integration of sensing and communication, and the advantages and disadvantages of various design methodologies are also discussed.
Rapid progresses have been witnessed in the practical ISAC system and algorithm design recently. [13] designed an ISAC system based on the wireless cellular networks. The author jointly designed signal waveforms suitable for sensing and communication based on 5G NR (New Radio) and its frame structure. Also under the 5G framework, [14] proposed a multi-beam based sensing and communication scheme. In addition to the beams used for communication, some other ones are used to sense the environment around the BS. Based on the 4G and 5G frameworks, [15] studied the processing principles, implementation challenges, and performance of orthogonal frequency division multiplexing (OFDM)-based radars, and achieved excellent sensing performance by using high channel bandwidth and configurable sub-carriers. In a Wi-Fi communication context, based on the Doppler frequency shift embedded in the channel state information (CSI), [16] achieved the sensing of human body posture. In the regime of internet of vehicles, [17] designed a fast beam alignment and tracking algorithm based on a hardware test platform to achieve vehicle tracking while performing millimeter wave communication with low latency and high data rate. As the research interest on ISAC keeps on increasing, more and more potential technologies are also introduced into this field, such as channel modeling [18], joint beam optimization [19] and machine learning [20], etc.
As for the environment sensing system design, some works have made full use of the sparsity of environmental information and achieved better and lower-complexity solutions based on the compressed sensing (CS) [21, 22] framework. In the field of microwave computational imaging, the utilization of the intrinsic sparsity of scatterers within the environment is key to their effective detection. This type of algorithm usually treats the scatterer as a sparsely distributed point cloud, thereby convert the imaging problem into a CS reconstruction problem, which is solved by orthogonal matching pursuit (OMP) [23], approximate message passing (AMP) [24], generalized approximate message passing (GAMP) [25] and other widely used methods.
Recently, in [26] and [27], the authors innovatively used BS to sense actively, and based on the block sparse Bayesian learning (BSBL) algorithm, proposed an IRS-assisted microwave computing imaging method. Although the above-mentioned methods effectively exploit the sparsity of the environment but ignore the occlusion effect caused by the scatterers. They ideally believe that EM signals can be freely transmitted to any location in the environment, and there still lacks sufficient consideration of the occlusion effect in the ISAC system design.
I-C Main Ideas and Contributions
In this paper, based on the existing wireless communication framework, we design a multi-view environment sensing scheme taking into full consideration the occlusion effect in an outdoor scenario.
Different from the above-mentioned application scenarios, we have achieved ISAC by noninvasively making use of the multi-user uplink communication data. At the same time, we have designed an effective sensing algorithm called GAMP-MVSVR which refers to the generalized-approximate-message-passing-based multi-view sparse vector reconstruction. In the uplink communication scenario, we consider an environment sensing scenario with single or multiple BSs, where users and BSs perform multi-view and collaborative sensing, and a centralized processor retrieving the environmental information from all the channel information obtained at the BSs. As a special case of the multi-BS scheme, a single BS itself can also complete all the sensing tasks, and we compare the performance differences between the two schemes.
Our design is depicted as follows. In one or more time slots, the BS estimates the multi-user uplink channel after detecting user pilot symbols (sounding signals). We propose an occlusion detection model based on the geometric location of the cloud points and convert the environment sensing problem into a CS reconstruction problem with the occlusion effect. Then we propose a probabilistic reasoning model based on the factor graph by analyzing the relationship among multipath channels, environmental information, and occlusion effects. Based on the well-known AMP method, the proposed GAMP-MVSVR algorithm achieves environment sensing by iteratively estimating the scattering coefficients of the cloud points and their occlusion relationship. In each iteration, the occlusion relationship between the cloud points of the sparse environment is recalculated according to the proposed occlusion detection rule, and in turn, used to estimate the scattering coefficients of the cloud points. Our proposed algorithm achieves improved sensing performance with multi-BS collaboration in addition to the multi-views from the users. To the best of our knowledge, there has been little work on the design of such an ISAC system in the literature.
The main contributions of this paper are summarized as follows:
-
•
We propose an ISAC scheme, which makes full use of the different views of the environment from different users and/or BS(s) to achieve improved sensing performance with multi-BS collaboration in addition to the multi-views from the UEs.
-
•
We propose an effective environment sensing algorithm called GAMP-MVSVR that considers the occlusion effect, where a multi-layer factor graph is constructed to iteratively estimate the scattering coefficients of the cloud points and derive their occlusion relationship based on a simple occlusion detection rule.
-
•
We analyze the impact of the multi-view schemes on environment sensing range and system performance. Extensive simulation results verify the convergence and effectiveness of the proposed algorithm.
The rest of this paper is organized as follows. Section II presents the environment setting and system model in the uplink communication scenario. Section III proposes the environment sensing problem formulation. Section IV proposes the GAMP-MVSVR algorithm under the occlusion effect. In section V, we analyze the impact of the multi-view schemes on environment sensing range and system performance. Finally, section VII presents the numerical results, and section VIII concludes the paper.
Notations: Fonts , and represent scalars, vectors and matrices, respectively. Notations and denote transpose and Frobenius norm of , respectively. and represent the -th row and -th column of matrix , respectively. represents the Hadamard product between two matrices. Finally, notation represents a diagonal matrix with the entries of on its main diagonal, and is the Dirac delta function.
II Environment Setting and System Model
II-A Environment Setting
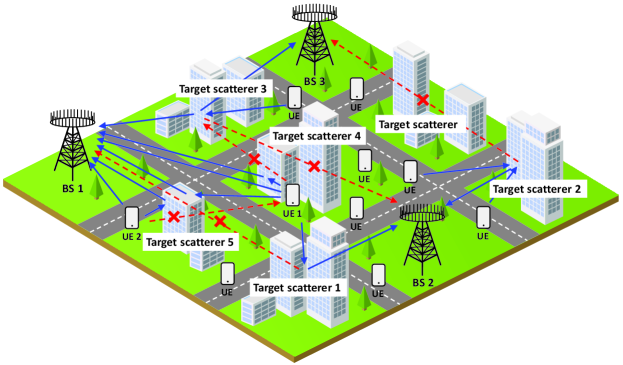
As shown in Fig. 1, we consider that in the outdoor wireless communication scenario, multiple BSs are deployed and there are multiple active user equipments (UEs). There are some buildings (target objects, serve as scatterers) in the outdoor environment that affect the wireless communication channel. We assume w.l.o.g. that the channel is a quasi-static channel where one block of transmission time is much shorter than the channel coherence time , , and the UE is stationary within the coherence time of the multipath channel estimation by UE pilots. In the uplink communication scenario, multiple single-antenna UEs send uplink communication data to multi-antenna BSs. The transmitted signal is scattered by the scatterer, and received by BSs through multipath channel. Therefore, the received signal of the BS contains environmental information.
We consider two schemes: a single-BS scheme and a multi-BS joint scheme to achieve multi-view environment sensing. The specific analysis is as follows.
-
•
As shown in Fig. 1, the single-BS environment sensing scheme is treated as a special case of the multi-BS joint scheme. When multiple UEs send uplink data to BS 1, the uplink communication channel is affected by the target scatterer. In the scenario, due to the occlusion effect, the multipath channel of UE 1 is only affected by the scattering of target scatterers 4 and 5, and the multipath channel of UE 2 is only affected by the scattering of target scatterers 5. Therefore, not all scatterers in the environment will affect the multipath channel of the same user, and the occlusion effect makes it hard for a single user to fully sensed the entire environment. The different views of the environment from different users should be exploited to deal with the occlusion effect.
-
•
Fig. 1 shows the scenario where multiple BSs are used for joint environment sensing, where the multi-BS scheme is performed. Sensing by multiple BSs will effectively expand the sensing range. In addition to the same user multi-view method as in the single-BS scheme, the different views of the environment from different BSs should be exploited. For example, in Fig. 1, BS 2 cannot receive the scattered signal from the target scatterer 3, and BS 1 and 3 also have scatterers that cannot be observed. Therefore, a multi-BS joint scheme should be designed to achieve the sensing of the entire environment.
II-B System Model
For the receiving antennas deployed on the BS, the single-BS scheme and the multi-BS joint scheme have the same system model. Let the number of users in the environment be , and the total number of receiving antennas of all BSs is . In the uplink communication scenario, the channel from the user to the BS is mainly composed of two parts: the line-of-sight channel from the user to the BS, and the multipath channel caused by the scatterer.
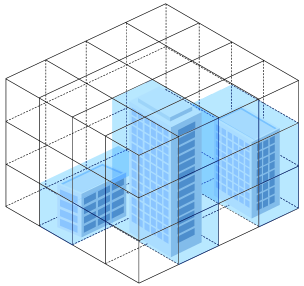
We discretize environmental information and treat the environmental information in the entire environment as point clouds. Each point in the point cloud represents the environmental information of the small cube with length , width , and height around it, and these small cubes are called pixels. The inside of each pixel may be empty, or there may be scatterers. The length, width and height of the environment to be sensed are , and respectively, then the number of point clouds is . Fig. 2 shows the method of discretizing environmental information into point clouds. We use the scattering coefficient to represent the scattering coefficient of the small cube where the -th cloud point is located. If the small cube is empty, then . Otherwise, . Therefore, the environmental information to be sensed is expressed as
Multiple users in the space share time-frequency resources. On a single subcarrier, the antennas of all BSs are analyzed independently. The signal received at the -th receiving antenna can be expressed as
| (1) |
where represents codewords with the length of sent by users, represents the received signal of the -th BS antenna, and represents noise. The term represents the channel coefficient of the line-of-sight path from the user to the receiving antenna, where the free space channel is decomposed into amplitude attenuation and phase shift, , is the line-of-sight channel amplitude attenuation, and is the line-of-sight channel phase shift. The line-of-sight channel occlusion can be detected through beam scanning, received power, etc. The term represents the channel coefficient of the multipath channel from the user to the receiving antenna.
As mentioned in Section I-B, we consider that in ISAC system design, the utilization of the intrinsic sparsity of objects or scatterers within an environment is key to the effective detection. We separate the free space channel (microwave background field) and scatterers in the multipath channel model to obtain sparse environmental information. In this way, the occlusion relationship between the scatterer and the antenna can be modeled by the existence of the free space channel between them. The multipath channel from the user to the receiving antenna is expressed as
| (2a) | ||||
| (2b) | ||||
| (2c) | ||||
where the free space channel coefficient with occlusion is expressed as the Hadamard product of the free space channel coefficient and the occlusion matrix . The element 0 in the occlusion matrix indicates that the path from -th user to -th receiving antenna is blocked, and the element 1 indicates that the path from -th user to -th receiving antenna is not blocked. represents the channel coefficient from the user to the point cloud position, where , represents the channel amplitude attenuation from the user to the point cloud position, represents the channel phase shift from the user to the point cloud position. represents the channel coefficient from the point cloud position to the BS receiving antenna, where , represents the channel amplitude attenuation from the point cloud position to the BS receiving antenna, represents the channel phase shift from the point cloud position to the BS receiving antenna, . represents the occlusion matrix from the user to the point cloud position, and its distribution reflects the different views from different users. When contains an all-zero column, it means that all users cannot sense the corresponding pixel, and the corresponding pixel is out of the sensing range. represents the occlusion matrix from the point cloud position to the receiving antenna, and its distribution reflects the different views from different BSs. When contains a zero element, it means that the receiving antenna cannot sense the corresponding pixel, and the corresponding pixel is also out of the sensing range, .
In (2), the model is derived as follows. First, in (2a), we decompose the multipath channel in (1) into free space channel with occlusion and environmental information . Then, in (2b), we decompose free space channel with occlusion into free space channel and occlusion matrix . Finally, in (2c), we further decompose the free space channel with occlusion into the channels from the user, the base station to the point cloud position , and their corresponding occlusion matrices , .
III Problem Formulation
In this section, we analyze the detection method of the occlusion effect in environment sensing, and based on this, we convert the environment sensing problem into a CS reconstruction problem with occlusion effect.
III-A Occlusion Detection Model
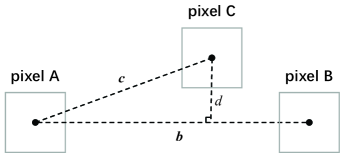
We detect the occlusion effect between scatterers based on the geometric positions between pixels. As shown in Fig. 3, there is a pixel C with a scattering coefficient greater than the threshold between pixels A and B. We believe that pixel C will cause an occlusion effect. Let the position of pixel A be the origin of coordinates, then the position vectors of pixel B and C are expressed as and respectively. According to the following conditions, it is considered that pixel C blocks the line-of-sight path between pixels A and B.
-
•
The distance between pixel C and the line-of-sight path between pixels A and B is less than the threshold ,
(3) where the detection threshold should be selected according to the side length or diagonal length of the small cube, that is, .
-
•
The angle between vector and vector is an acute angle, which means that pixel C is located in the same direction of the line-of-sight path from pixel A to pixel B, but not pixel A is located between the pixel B and the pixel C. It is expressed as
(4) -
•
Pixel C is located between pixel A and pixel B, which is expressed as
(5)
According to the above occlusion detection method, we design the environment sensing algorithm. However, the proposed occlusion detection method is not the only method, and the proposed environment sensing algorithm does not depend on the uniqueness of the occlusion detection method.
III-B Environment Compressed Sensing Model
As mentioned in Section I, since the distribution of scatterers in the environment is sparse, according to the CS theory, the optimization problem of solving environmental information is expressed as
| (6) |
where is a slack variable. In the system model of Section II-B, We can calculate the free space channel coefficients and through the basic free space path propagation model. In addition, some empirical models, simplified models, or interpolation methods are also suitable, and the appropriate model needs to be selected according to the practical environment. The BS estimates the multipath channel by detecting the UE pilot and calculating the relationship with the received signal . Therefore, in general, in order to achieve accurate channel estimation (e.g. least-squares channel estimation), the pilot length should be greater than the number of users, that is, . The proposed algorithm does not rely much on the method of channel estimation. Note that the channel estimation is only the first step of the overall integrated sensing and communication process. The subsequent environment sensing problem studied here is always an underdetermined CS problem with given channel matrix. Due to the large propagation range of wireless signals, according to different precision requirements, the number of pixels will be greater than . At the same time, based on the sparsity of the environmental information , the optimization problem (6) is expressed as the CS reconstruction problem equation
| (17) | ||||
| (18) |
where is formed by splicing the multipath channel matrix between receiving antennas and users. In the multi-BS joint environment sensing scheme, receiving antennas include the number of all antennas on multiple BSs.
IV Environment Sensing Algorithm under The Occlusion Effect
In this section, we propose an environment sensing algorithm called GAMP-MVSVR under the occlusion effect to solve the environment information in the (18). According to (2), (18) is expressed as
| (19) |
where channel matrix is formed by splicing channel matrix of receiving antennas, and occlusion matrix is formed by splicing occlusion matrix of receiving antennas.
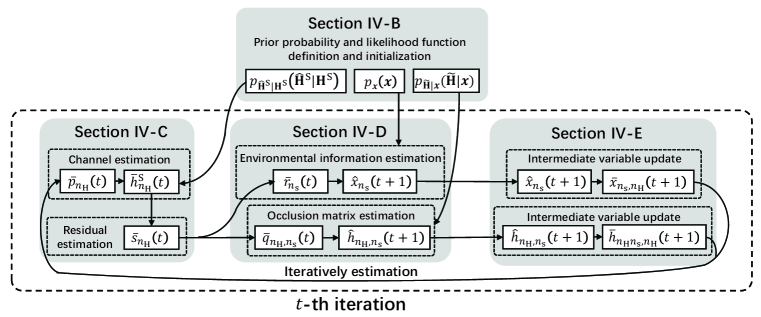
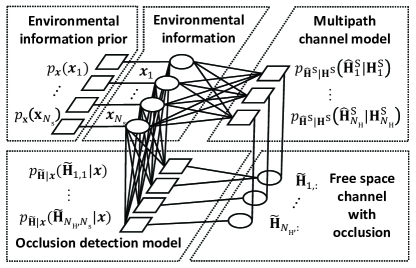
IV-A Overview of the Proposed GAMP-MVSVR Algorithm
Different from the traditional CS reconstruction problem, solving the environment sensing problem with occlusion effect requires not only solving the environment information but also needs to consider the unknown occlusion matrix . Traditional CS reconstruction algorithms, such as GAMP algorithm [25], can solve environmental information in an ideal (ignoring occlusion, ) situation. In this way, since the accurate measurement matrix cannot be obtained, the environmental information cannot be accurately solved. Compared with the GAMP algorithm, the Bilinear GAMP algorithm [28] can solve the bilinear problem, that is, simultaneously solve the occlusion matrix and the environmental information . However, it does not consider the relationship between the occlusion effect and the environmental information, the Bilinear GAMP algorithm cannot constrain the uniqueness and accuracy of the occlusion matrix and the environmental information .
Fig. 4 shows a sketch of the proposed GAMP-MVSVR algorithm. In Section IV-B, we propose a factor graph based on the decomposition result of the joint posterior probability. Based on the sum-product algorithm (SPA) algorithm, we calculate the message passed in the factor graph, and define the prior probability and likelihood function. In Section IV-C, we approximate the message from factor node to variable node. Through the approximate process, we use the result in the previous iteration to calculate its corresponding multipath channel. We compare it with the channel estimated by the pilot and calculate the residual to guide this iteration. In Section IV-D, we approximate the message from variable node to factor node. Through the approximate process, according to the occlusion effect, we estimate and based on the residual. In Section IV-E, We update the intermediate variables in Section IV-C and IV-D, and achieve the iterative execution of the estimation methods in Section IV-C and IV-D.
IV-B Factor Graph and Passed Messages
As mentioned in Section III-B, let be the multipath channel estimated by the pilot, then , where represents the estimation error. The estimation error is caused by two main reasons, including the multipath channel estimation error caused by pilot estimation and the free space channel estimation error caused by modeling estimation. In order to simplify the analysis, we assume that the noise obeys a Gaussian distribution. The joint posterior distribution of the occluded multipath channel and the environmental information is expressed as
| (20) |
where is a constant. To simplify the expression, let denote the length of the multipath channel vector . As shown in Fig. 5, according to the (20), the posterior distribution is expressed in the form of a factor graph.
As shown in Fig. 5, the circles represent the variable nodes and , the squares represent the factor node , and . The lines between the nodes represent that the variables are included in the function of the factor nodes. Specifically, the environmental information prior probability function contains the environmental information variable . The relationship between the environmental information variable and the channel with occlusion conforms to the occlusion detection model function . The multipath channel observation function contains the environmental information variable and the free space channel . The specific function is expressed as follows: can be considered as the observation of under the interference of additive white Gaussian noise, i.e.,
| (21) |
where is the variance of Gaussian white noise. Due to the sparseness of environmental information , we assume that the obeys a Bernoulli-Gaussian distribution,
| (22) |
where is the sparsity of the environment, and represent the mean and variance of the scattering coefficient of the environmental scatterer. represents the occlusion effect of environmental information on the channel, i.e.,
| (23) |
where represents the occlusion detection function, the specific method is as described in the Section III-A, and the occlusion detection threshold is set to .
Based on the sparse prior information and occlusion relationship of environmental information, we aim to obtain the minimum mean square error (MMSE) estimate of environmental information
| (24) |
According to the loopy belief propagation (LBP) theory [29], based on the factor graph model, we calculate the MMSE estimated value of the environment information through the SPA [30]. As explained in Appendix A, the method of SPA message passing is as follows. As shown in Fig. 5, the output message of the variable node along the edge (solid line) is obtained by calculating the product of all its input messages. The output message of the factor node is calculated by multiplying and integrating the function of the factor node and its input message. The marginal distribution of the variable is calculated from the product of all messages input to the node. Since it is difficult to accurately calculate the passed message , we approximate the message in the following sections.
IV-C Approximated Factor-to-Variable Messages
In this section, we approximate the message from the factor node to the variable node according to the central limit theorem (CLT) and Gaussian approximation based on the idea of approximate message passing [24, 25, 28]. Based on CLT, when , remains constant, we drop some high-order infinitesimal terms. In the iteration, the sparsity in the prior distribution of environmental information remains constant. As mentioned in Section III-A and Section V, the number of zero elements in the occlusion matrix in the variable remains fixed, and the position of the zero elements is determined by . Therefore, we consider that variable is independent of variable in the -th iteration. As explained in Appendix B, the passed message in (77) is approximated as
| (25) |
where
| (26) |
Adding the -th term to the summation in in (86), then and are considered as an estimate of , i.e.,
| (27) |
| (28) |
We define a residual variable whose mean value is,
| (29) |
due to the Gaussian property of , the variance of the residual is expressed as,
| (30) |
where and represent the first and second derivatives of the first argument of , and represents the first derivative of the second argument of .
As explained in Appendix C, we get the final approximation result of the passed message in (77)
| (31) |
According to (27), is considered to be an estimate of , we can express the posterior probability of as the product of the prior probability and the likelihood as follows
| (32) |
where is a normalization constant. Then the mean and variance of (32) are the mean and variance of calculated as follows
| (33) |
| (34) |
where represents the mean of and represents the variance of .
Pluging (32), (33) and (34) into (29) and (30). Based on the likelihood in (21), according to the derivation in [25, 28], the mean and variance of the residual are expressed as
| (35) |
| (36) |
As mentioned in this section, in the -th iteration, we consider that variable is independent of variable , so the same as the derivation of (31), we approximate the message in (79) as
| (37) |
In summary, in this section we approximate the message from factor node to variable node as follows. We calculate (as shown in (27)) to obtain the calculated channel (as shown in (33)). Then we calculate the residual according to and the channel estimation value using the pilot (as shown in (35)). Finally, we use the residual and the approximate mean and variance of the passed message to represent the message from the factor node to the variable node (as shown in (31) and (37)).
IV-D Approximated Variable-to-Factor Messages
In this section, we approximate the message from the factor node to the variable node. We plug (31) in (78), the message from variable node to factor node is approximated as
| (38) |
where
| (39) |
| (40) |
Then the mean and variance of the passed message in (38) are expressed as,
| (41) |
| (42) |
where is a normalization constant, and represents the first derivative of the first argument of the . The specific derivation of the relationship between (41) and (42) was shown in [25].
Adding the -th term to the summation in , then and are expressed as
| (43) |
| (44) |
Based on AMP [24, 25, 28], and are considered as an estimate of as follows
| (45) |
| (46) |
where represent the first derivative of the first argument of . Finally, we calculate the relationship between the mean of the passed message and the mean of the marginal distribution as follows
| (47) |
in which we drop infinitesimal terms such as in the second step of approximation, and we perform Taylor series expansion on the first argument of the function at point and drop the infinitesimal term in the second step of approximation.
In the -th iteration, we consider that variable is independent of variable and recalculate the relationship between variables and after each iteration. Therefore, we approximate the passed message from variable node to factor node the same way as (38), and calculate the mean and the variance of the marginal distribution of variable the same way as (45) and (46), i.e.,
| (48) |
| (49) |
| (50) |
where is a normalization constant, represent the first derivative of the first argument of , and are considered as an estimate of as follows
| (51) |
| (52) |
Similar to the approximation process of (47), we calculate the relationship between the mean of the passed message and the mean of the marginal distribution as follows
| (53) |
Since the environmental information is an unknown variable, in the -th iteration, we use instead of for occlusion detection, (50) is expressed as
| (54) |
In summary, in this section we approximate the message from variable node to factor node as follows. Firstly, we calculate and based on the residual (as shown in (43) and (51)), and calculate the new estimated values and (as shown in (45) and (48)). Secondly, since the message from the variable node to the factor node is similar to the posterior probability, we approximate the relationship between the estimated value , and the passed message , (as shown in (47) and (53)).
IV-E Algorithm Iterative Execution
In Section IV-C and Section IV-D, we have obtained the estimation methods for variables and , but the intermediate variables , , and contain the passed messages and . We need to replace the passed message with the current estimated variable and to calculate these intermediate variables again to achieve the iteration of the algorithm.
Pluging (47) and (53) into (27), we can get
| (55) |
where we replace with , replace with , and drop the infinitesimal term under the CLT condition. In most AMP algorithms [25, 28], (55) can be interpreted as the Onsager correction to , and (28) is expressed as
| (56) |
Similar to the approximate method in the (55), pluging (47) and (53) into (43) and (44), it yields
| (57) |
| (58) |
And similar to the approximate method in the (55), pluging (47) and (53) into (51) and (52), it yields
| (59) |
| (60) |
We summarize the proposed GAMP-MVSVR algorithm in Algorithm 1. During the execution process of the GAMP-MVSVR algorithm, the approximate message passing and the occlusion detection method execute repeatedly and converge to the estimated value of environmental information. The computational complexity of the GAMP-MVSVR algorithm consists of two parts: approximate message passing and occlusion detection method. The computational complexity is expressed as , where is the number of the environmental scatterers, the number of pixels has a major influence on the computational complexity. The setting of is to stop the iteration in time when the system performance is poor. Due to the small order of magnitude of iterations, the number of algorithm iterations will hardly reach , and we omit the term when calculating the computational complexity.
V System Performance Analysis
In this section, we compare the performance of the single-BS environment sensing scheme and the multi-BS joint environment sensing scheme from two aspects: environment sensing range and environment sensing accuracy.
V-A Environment Sensing Range
In this section, we analyze the impact of the CS measurement matrix on the system performance. According to the CS reconstruction model in Section III-B, the environment sensing range is determined by the CS measurement matrix . Specifically, the number of 0 elements in the occlusion matrix , , and is calculated to obtain the environment sensing range.
As mentioned in Section II-B, the number of pixels is , and the position of -th pixel is . The number of users in the environment is , and the position of -th user is . In the multi-BS joint environment sensing scheme, the number of BSs in the environment is , and the position of -th BS is . Under these definitions, the analysis of the occlusion matrix and is summarized in the following theorem.
Theorem 1
The probability that the element in the occlusion matrix is 0 can be expressed as
| (61) |
where is the distribution function of -th user in the environment. For the receiving antenna deployed on the -th BS, the probability that the element in the occlusion matrix is 0 can be expressed as
| (62) |
where is the distribution function of -th BS in the environment.
Proof:
According to the occlusion detection model in Section III-A, when there is a scatterer in the space of size between the -th user and the -th pixel, the EM propagation path is blocked. The location distribution function of each user is independent, and the division of pixels is uniform. Therefore, in the space of size , the probability of a scatterer between the -th user and the -th pixel is denoted as (61). In the occlusion detection model, the analysis methods of the BS and the user are the same. Therefore, according to (61), replacing with and replacing with , we obtain (62). ∎
The occlusion matrix reflects the different views from different users. In the single-BS environment sensing scheme and the multi-BS joint environment sensing scheme, the multi-views from users are the same. As mentioned in Section II-B, when contains an all-zero column, it means that all users cannot sense the corresponding pixel, and the pixel is out of the user sensing range. According to Theorem 1, when the number of users is , the probability that the pixels in the environment are outside the user sensing range is
| (63) |
Let and the occlusion matrix reflects the different views from different BSs. In the single-BS environment sensing scheme, since the receiving antennas are deployed close to each other, they have almost the same views to the scatterers in the environment. Therefore, the probability that a pixel is outside the sensing range of a single BS is . In the multi-BS joint environment sensing scheme, when contains an all-zero row, it means that all BSs cannot sense the corresponding pixel, and the pixel is out of the BS sensing range. According to Theorem 1, since the location distribution probability of each BS is independent, the probability that a pixel in the environment is outside the sensing range of the BS is
| (64) |
According to (61), (62), (63), and (64), we calculate the mean value of the number of pixels that cannot be sensed in the single-BS environment sensing scheme and the mean value of the number of pixels that cannot be sensed in the multi-BS joint environment sensing scheme as
| (65) |
| (66) |
The multi-BS joint environment sensing has a larger sensing range than single-BS environment sensing. In practical applications, a multi-BS scheme should be implemented according to the BS location. When the multi-BS scheme is difficult to implement, e.g., when the BSs are far away and users cannot communicate with each BS, a single-BS scheme should be used. In addition, if there is a failure of environment sensing for some pixels, a larger number of base stations and users or users after moving locations should be used for joint sensing.
V-B Environment Sensing Accuracy
In this section, we analyze the impact of environmental information on system performance. The mean square error (MSE) between the estimated environmental information and the real environmental information is used to describe the accuracy of environment sensing, i.e.,
| (67) |
According to the CS reconstruction model in Section III-B (6), the reconstruction problem in (18) is expressed as
| (68) |
where is a slack variable. We consider that the performance of environment sensing methods for solving the occlusion problem should be as close as possible to the upper limit in Theorem 2.

Theorem 2
The upper bound of the environment sensing error when the CS measurement matrix under the ideal (no occlusion, the occlusion detection is completely correct) situation is
| (69) |
where is a normalized constant, and
| (74) |
Proof:
Remark 1
When the number of BS antennas or the number of users increases, the upper bound of environment sensing error MSE decreases. When the environment sparsity and other system parameters remain constant, the number of pixels increases (this means a wider sensing range or higher sensing resolution), the upper bound of environment sensing error MSE increases. Therefore, wider and more accurate sensing results require more resource costs.
According to (65) and (66), under the condition that the number of users is the same and the total number of antennas of all BSs is the same, the number of environmental scatterers sensed by multiple BSs is more than that of a single BS, . Therefore, according to (69), for the scatterers in the sensing range, the upper bound of MSE of multi-BS joint environment sensing is higher than that of the single-BS scheme. However, in practical applications, the total number of antennas deployed by multiple BSs is usually more than that of a single BS. The increase in the number of antennas will significantly improve system performance.
We analyze the probability distribution of the occlusion matrix caused by the environmental scatterers as shown in Corollary 1.
Corollary 1
The elements in the occlusion matrix conform to the Bernoulli distribution. The probability that the element in the occlusion matrix is 0 can be expressed as
| (76) |
Proof:
According to , as shown in Theorem 1, the probability that the element in the occlusion matrix is 0 can be calculated by and . ∎
Therefore, the unknown occlusion matrix is equivalent to causing a multiplicative Bernoulli perturbation to the known free space channel matrix as shown in (19). At present, some works [31, 32] have analyzed the compressed sensing reconstruction performance under the condition that there is a specific perturbation in the compressed sensing measurement matrix. In this paper, the proposed algorithm iteratively eliminates the perturbation to the measurement matrix caused by the occlusion effect according to the results of each iteration and obtains accurate imaging results. The system performance analysis of this iterative detection process will be future work, and extensive simulation results have verified the effectiveness and convergence of the proposed algorithm.
VI Numerical Results
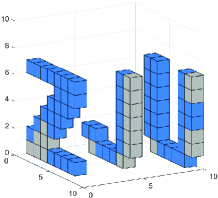
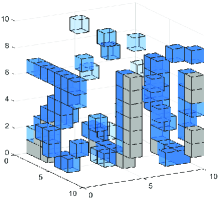
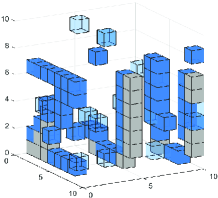
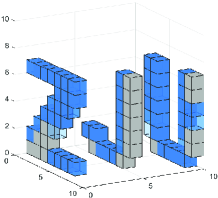
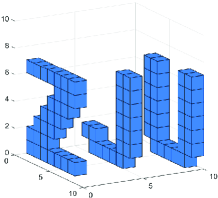
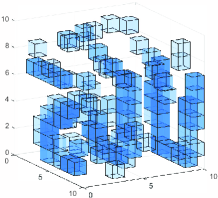
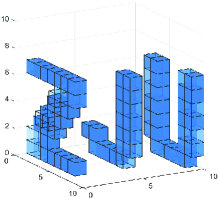
In this section, we simulate the performance of the algorithm. In order to reduce the computational cost and reflect the environment sensing accuracy, we set up a small-scale simulation sensing region, the environmental scatterers are distributed in the sensing region of , and the sensing region is evenly divided into pixels. Multiple BSs and users are randomly distributed in or around the sensing region. The carrier frequency of the uplink signal is set to . The positions of scatterers distributed in sensing region are random, and the scattering coefficient is set to . As shown in the Fig. 7 and Fig. 7, small cubes are used to represent the position and scattering coefficient of pixels. The lower the transparency of the small cubes, the higher the scattering coefficient of the pixel.
In this section, as mentioned in Section IV-A, we choose GAMP and Bilinear GAMP algorithm as the baseline algorithms to solve the environment sensing problem under the occlusion effect. Compared with the two baseline algorithms, in this paper, the proposed GAMP-MVSVR algorithm based on the occlusion effect significantly improves the accuracy of environment sensing.
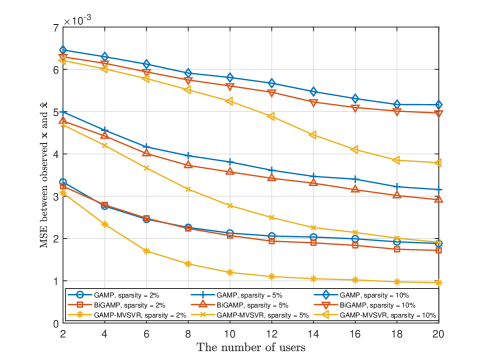
Fig. 7 shows the results of the single-BS environment sensing, where the gray cubes represent scatterers that are out of the sensing range due to the occlusion effect. The system parameters are set to the number of users , a single BS is deployed with a array antenna, and the signal-to-noise ratio (SNR) . Compared with the baseline algorithms, it can be seen that the proposed algorithm clearly and accurately obtains the shape of the original target.
Fig. 7 shows the results of the multi-BS joint environment sensing. In order to make the total number of antennas deployed in the environment the same, we reduce the number of antennas on each BS. The system parameters are set to the number of users , 5 BSs are deployed with array antennas, and the SNR . Compared with the single-BS scheme, as analyzed in (65) and (66), multi-BS joint environment sensing scheme effectively increases the environment sensing range. In Fig. 7, there is no scatterer that cannot be sensed even though the occlusion effect is exist. It can be seen that the sensing results of baseline algorithms are more blurred than the results of the single-BS scheme. This is because, as analyzed in Section V-B, when the total number of receiving antennas is the same, multi-BS joint environment sensing has a larger environment sensing range, which causes a small decrease in the accuracy of environment sensing within the sensing range.
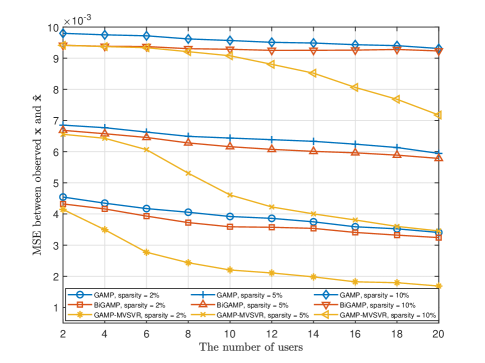
Fig. 8 and Fig. 9 show the relationship between the single-BS environment sensing performance, the multi-BS joint environment sensing performance and the number of users , respectively. The MSE between the environmental information within the sensing range and the environmental information estimated by the algorithm reflects the accuracy of environment sensing within the sensing range. The system parameters are set as follows: the single BS in the scenario in Fig. 8 is deployed with a array antenna, and 5 BSs in the scenario in Fig. 9 are deployed with array antennas, and the SNR .
Remark 2
As analyzed in (69), as the number of users increases or the number of environmental scatterers decreases, the accuracy of environment sensing increases. Both the proposed algorithm and the baseline algorithm perform poorly when the number of users is small. But as the number of users increases, the performance of the proposed algorithm improves significantly.
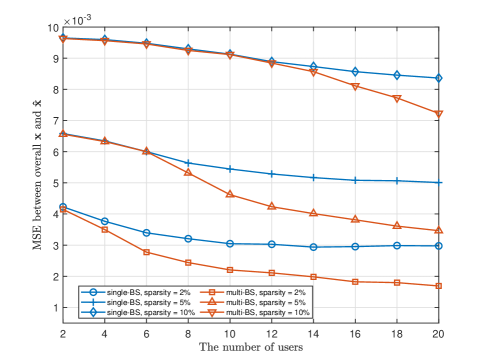
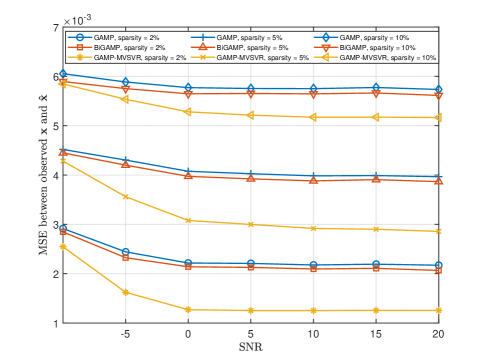
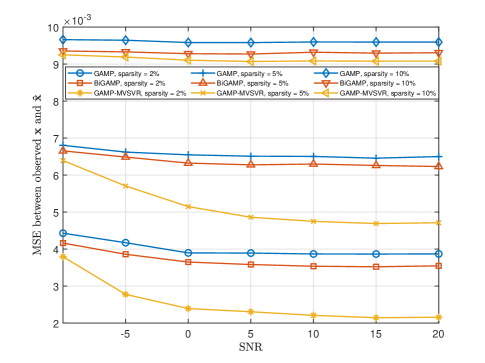
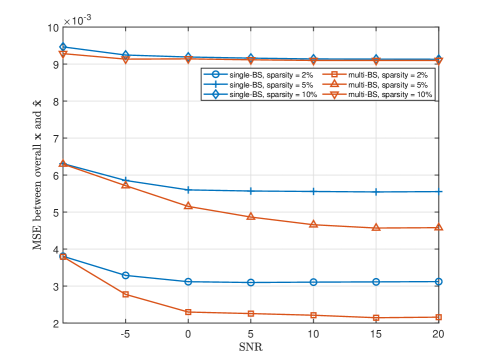
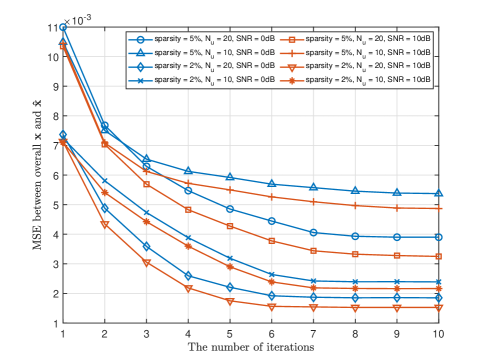
Fig. 10 shows the relationship between the number of users and the MSE within the full range of two sensing schemes. The MSE between the environmental information within the full range and the environmental information estimated by the algorithm reflects the size of the environment sensing range. The system parameter settings of the two environment sensing schemes are the same as those in Fig. 8 and Fig. 9, respectively.
Remark 3
As analyzed in (69), as the number of users increases or the number of environmental scatterers decreases, the accuracy of environment sensing increases. At the same time, as analyzed in (65) and (66), for the full range of the environment, the multi-BS scheme has a lower sensing error, so it effectively increases the environment sensing range.
Fig. 11 and Fig. 12 show the relationship between the single-BS environment sensing performance, the multi-BS joint environment sensing performance and the SNR , respectively. The system parameters are set as follows: the single BS in the scenario in Fig. 11 is deployed with a array antenna, and 5 BSs in the scenario in Fig. 12 are deployed with array antennas, and the number of users .
Remark 4
As the SNR increases, the estimated value of the multipath channel is more accurate, and the accuracy of environment sensing increases. At the same time, the less sparse the environmental scatterer distribution, the closer the performance of the proposed algorithm and the baseline algorithm are. This is because the more environmental scatterers cause more occlusion, which reduces the performance of all algorithms at the same time.
Fig. 13 shows the relationship between the SNR and the MSE within the full range of two sensing schemes. The system parameter settings of the two environment sensing schemes are the same as those in Fig. 11 and Fig. 12, respectively.
Remark 5
As shown in Fig. 14, we provide performance curves under various parameter settings to verify the convergence of the proposed algorithm. The antenna settings of the multi-base station scheme are the same as above.
Remark 6
As the number of iterations increases, the sensing error MSE gradually decreases and converges. The sparser the environmental information, the faster the algorithm converges and the better the system performs. Meanwhile, the increase in the number of users and the signal-to-noise ratio accelerates algorithm convergence and improves system performance.
VII Conclusion
In this paper, we have designed a multi-view environment sensing scheme taking into full consideration the occlusion effect in an outdoor scenario. Based on the occlusion effect, we have proposed a probabilistic reasoning model based on the factor graph. According to the AMP theory, the GAMP-MVSVR algorithm is proposed to achieve multi-view environment sensing. The proposed GAMP-MVSVR algorithm achieves environment sensing by iteratively estimating the scattering coefficients of the cloud points and their occlusion relationship. In each iteration, the occlusion relationship between the cloud points of the sparse environment is recalculated according to the proposed occlusion detection rule, and in turn, used to estimate the scattering coefficients of the cloud points. Our proposed algorithm achieves improved sensing performance with multi-BS collaboration in addition to the multi-views from the users, which will provide ideas for future ISAC system design.
Appendix A
According to the factor graph shown in Fig. 5, the logarithmic form of the passed message is calculated as follows. In the -th iteration, the message passed from the factor node to the variable node is
| (77) |
where the passed message is expressed in logarithmic form. is a normalization constant, so that the integral of the exponential passed message is 1. In the subsequent passed message and marginal distribution in this section, the constant has the same meaning. In the -th iteration, the message passed from the variable node to the factor node is
| (78) |
Let the mean and variance of the exponential form of the message passed in (78) be and , respectively. In the -th iteration, the message passed from the factor node to the variable node is expressed as
| (79) |
In the -th iteration, similar to (78), the message passed from the variable node to the factor node is expressed as
| (80) |
Let the mean and variance of the exponential form of the message passed in (80) be and , respectively.
According to the factor graph in Fig. 5, the logarithmic marginal distribution of the variable and are calculated as follows. With the iteration of the algorithm, the marginal distributions of variables gradually converge to their MMSE estimates. The marginal distribution of the variable is
| (81) |
Let the mean and variance of the exponential form of the marginal distribution in (81) be and , respectively. The marginal distribution of the variable is
| (82) |
Let the mean and variance of the exponential form of the marginal distribution in (82) be and , respectively.
Appendix B
Here we derive the approximate result (25). The Roman font is used to represent the elements , , and in the matrix , , and in the case of CLT. Let and , then the mean is , and the variance is and .
In the iteration, the sparsity in the prior distribution of environmental information remains constant. As mentioned in Section IV-C, we consider that variable is independent of variable in the -th iteration. Therefore, the mean and the variance of variable are independent of variable . is expressed as
| (83) |
Based on the CLT condition, , the mean and variance of in (83) is written as
| (84) |
| (85) |
where
| (86) |
| (87) |
Appendix C
Here we derive the approximate result (31). Pluging (27) and (28) into (25) we obtain
| (88) |
where, since , we drop infinitesimal terms such as and so on.
As with most AMP algorithms [24, 25, 28], we make the same derivation. We perform Taylor series expansion of variable in (88) at point , the passed message in (25) is approximated as
| (89) |
where and represent the first and second derivatives of the first argument of , and represents the first derivative of the second argument of . We drop infinitesimal terms such as the second derivative term of the second argument of .
According to the derivation in Appendix D that
| (90) |
Appendix D
According to (26), we obtain
| (93) |
References
- [1] F. Liu, Y. Cui, C. Masouros, et al., “Integrated sensing and communications: Towards dual-functional wireless networks for 6G and beyond,” 2021, [online] https://arxiv.org/abs/2108.07165.
- [2] W. Saad, M. Bennis, and M. Chen, “A vision of 6G wireless systems: Applications, trends, technologies, and open research problems,” IEEE Network, vol. 34, no. 3, pp. 134–142, 2020.
- [3] T. S. Rappaport, Y. Xing, O. Kanhere, et al., “Wireless communications and applications above 100 GHz: Opportunities and challenges for 6G and beyond,” IEEE Access, vol. 7, pp. 78729–78757, 2019.
- [4] L. Kong, M. K. Khan, F. Wu, et al., “Millimeter-wave wireless communications for IoT-cloud supported autonomous vehicles: Overview, design, and challenges,” IEEE Communications Magazine, vol. 55, no. 1, pp. 62–68, 2017.
- [5] G. Han, J. Jiang, C. Zhang, et al., “A survey on mobile anchor node assisted localization in wireless sensor networks,” IEEE Communications Surveys Tutorials, vol. 18, no. 3, pp. 2220–2243, 2016.
- [6] H. Menouar, I. Guvenc, K. Akkaya, et al., “UAV-enabled intelligent transportation systems for the smart city: Applications and challenges,” IEEE Communications Magazine, vol. 55, no. 3, pp. 22–28, 2017.
- [7] F. Liu, C. Masouros, A. P. Petropulu, et al., “Joint radar and communication design: Applications, state-of-the-art, and the road ahead,” IEEE Transactions on Communications, vol. 68, no. 6, pp. 3834–3862, 2020.
- [8] C. Jiao, Z. Zhang, C. Zhong, et al., “An indoor mmwave joint radar and communication system with active channel perception,” in 2018 IEEE International Conference on Communications (ICC), 2018, pp. 1–6.
- [9] C. Jiao, Z. Zhang, C. Zhong, et al., “Millimeter wave communication with active ambient perception,” IEEE Transactions on Wireless Communications, vol. 18, no. 5, pp. 2751–2764, 2019.
- [10] X. Tong, Z. Zhang, J. Wang, et al., “Joint multi-user communication and sensing exploiting both signal and environment sparsity,” IEEE Journal of Selected Topics in Signal Processing, vol. 15, no. 6, pp. 1409–1422, 2021.
- [11] D. K. P. Tan, J. He, Y. Li, et al., “Integrated sensing and communication in 6G: Motivations, use cases, requirements, challenges and future directions,” in 2021 1st IEEE International Online Symposium on Joint Communications Sensing (JC S), 2021, pp. 1–6.
- [12] J. A. Zhang, M. L. Rahman, K. Wu, et al., “Enabling joint communication and radar sensing in mobile networks – a survey,” 2020, [online] https://arxiv.org/abs/2006.07559v3.
- [13] T. Wild, V. Braun, and H. Viswanathan, “Joint design of communication and sensing for beyond 5G and 6G systems,” IEEE Access, pp. 1–1, 2021.
- [14] C. B. Barneto, S. D. Liyanaarachchi, T. Riihonen, et al., “Multibeam design for joint communication and sensing in 5G new radio networks,” in ICC 2020 - 2020 IEEE International Conference on Communications (ICC), 2020, pp. 1–6.
- [15] C. B. Barneto, T. Riihonen, M. Turunen, et al., “Full-duplex OFDM radar with LTE and 5G NR waveforms: Challenges, solutions, and measurements,” IEEE Transactions on Microwave Theory and Techniques, vol. 67, no. 10, pp. 4042–4054, 2019.
- [16] B. Tan, Q. Chen, K. Chetty, et al., “Exploiting WiFi channel state information for residential healthcare informatics,” IEEE Communications Magazine, vol. 56, no. 5, pp. 130–137, 2018.
- [17] Q. Zhang, H. Sun, Z. Wei, et al., “Sensing and communication integrated system for autonomous driving vehicles,” in IEEE INFOCOM 2020 - IEEE Conference on Computer Communications Workshops (INFOCOM WKSHPS), 2020, pp. 1278–1279.
- [18] P. Almers, E. Bonek, A. Burr, et al., “Survey of channel and radio propagation models for wireless MIMO systems,” EURASIP Journal on Wireless Communications and Networking, vol. 2007, 02 2007.
- [19] L. Chen, F. Liu, W. Wang, et al., “Joint radar-communication transmission: A generalized pareto optimization framework,” IEEE Transactions on Signal Processing, vol. 69, pp. 2752–2765, 2021.
- [20] G. K. Papageorgiou, M. Sellathurai, and Y. C. Eldar, “Deep networks for direction-of-arrival estimation in low SNR,” IEEE Transactions on Signal Processing, vol. 69, pp. 3714–3729, 2021.
- [21] D. L. Donoho, “Compressed sensing,” IEEE Transactions on Information Theory, vol. 52, no. 4, pp. 1289–1306, 2006.
- [22] E. J. Candes and T. Tao, “Near-optimal signal recovery from random projections: Universal encoding strategies?,” IEEE Transactions on Information Theory, vol. 52, no. 12, pp. 5406–5425, 2006.
- [23] T. T. Cai and L. Wang, “Orthogonal matching pursuit for sparse signal recovery with noise,” IEEE Transactions on Information Theory, vol. 57, no. 7, pp. 4680–4688, 2011.
- [24] D. L. Donoho, A. Maleki, and A. Montanari, “Message passing algorithms for compressed sensing: I. motivation and construction,” in 2010 IEEE Information Theory Workshop on Information Theory (ITW 2010, Cairo), 2010, pp. 1–5.
- [25] S. Rangan, “Generalized approximate message passing for estimation with random linear mixing,” in 2011 IEEE International Symposium on Information Theory Proceedings, 2011, pp. 2168–2172.
- [26] J. Yao, Z. Zhang, X. Shao, et al., “Concentrative intelligent reflecting surface aided computational imaging via fast block sparse bayesian learning,” in 2021 IEEE 93rd Vehicular Technology Conference (VTC2021-Spring), 2021, pp. 1–6.
- [27] Y. Tao and Z. Zhang, “Distributed computational imaging with reconfigurable intelligent surface,” in 2020 International Conference on Wireless Communications and Signal Processing (WCSP), 2020, pp. 448–454.
- [28] J. T. Parker, P. Schniter, and V. Cevher, “Bilinear generalized approximate message passing—part I: Derivation,” IEEE Transactions on Signal Processing, vol. 62, no. 22, pp. 5839–5853, 2014.
- [29] B. J. Frey and D. J. C. MacKay, “A revolution: Belief propagation in graphs with cycles,” Advances in neural information processing systems, pp. 479–485, 1998.
- [30] F. R. Kschischang, B. J. Frey, and H. A. Loeliger, “Factor graphs and the sum-product algorithm,” IEEE Transactions on Information Theory, vol. 47, no. 2, pp. 498–519, 2001.
- [31] A. Lavrenko, F. Römer, G. Del Galdo, et al., “Sensing matrix sensitivity to random Gaussian perturbations in compressed sensing,” in 2018 26th European Signal Processing Conference (EUSIPCO), 2018, pp. 583–587.
- [32] Z. Yang, C. Zhang, and L. Xie, “Stable signal recovery in compressed sensing with a structured matrix perturbation,” in 2012 IEEE International Conference on Acoustics, Speech and Signal Processing (ICASSP), 2012, pp. 2737–2740.