Equivalence Checking and Simulation By Computing Range Reduction
Abstract
We introduce new methods of equivalence checking and simulation based on Computing Range Reduction (CRR). Given a combinational circuit , the CRR problem is to compute the set of outputs that disappear from the range of if a set of inputs of is excluded from consideration. Importantly, in many cases, range reduction can be efficiently found even if computing the entire range of is infeasible.
Solving equivalence checking by CRR facilitates generation of proofs of equivalence that mimic a “cut propagation” approach. A limited version of such an approach has been successfully used by commercial tools. Functional verification of a circuit by simulation can be viewed as a way to reduce the complexity of computing the range of . Instead of finding the entire range of and checking if it contains a bad output, such a range is computed only for one input. Simulation by CRR offers an alternative way of coping with the complexity of range computation. The idea is to exclude a subset of inputs of and compute the range reduction caused by such an exclusion. If the set of disappeared outputs contains a bad one, then is buggy.
I Introduction
The objective of this paper is to emphasize the importance of developing efficient algorithms for Computing Range Reduction (CRR). Earlier we showed that CRR can be used for model checking [5]. Adding equivalence checking and simulation to the list of problems that can be handled by CRR makes the need for developing efficient CRR algorithms more obvious.
I-A The CRR problem
Let be a combinational circuit where are the sets of input, intermediate and output variables of respectively (see Figure 1). We will refer to the set of all outputs produced by as the range of . By an “output” here we mean a complete assignment of values to the variables of . We will also use term “input” to denote a complete assignment to the variables of .
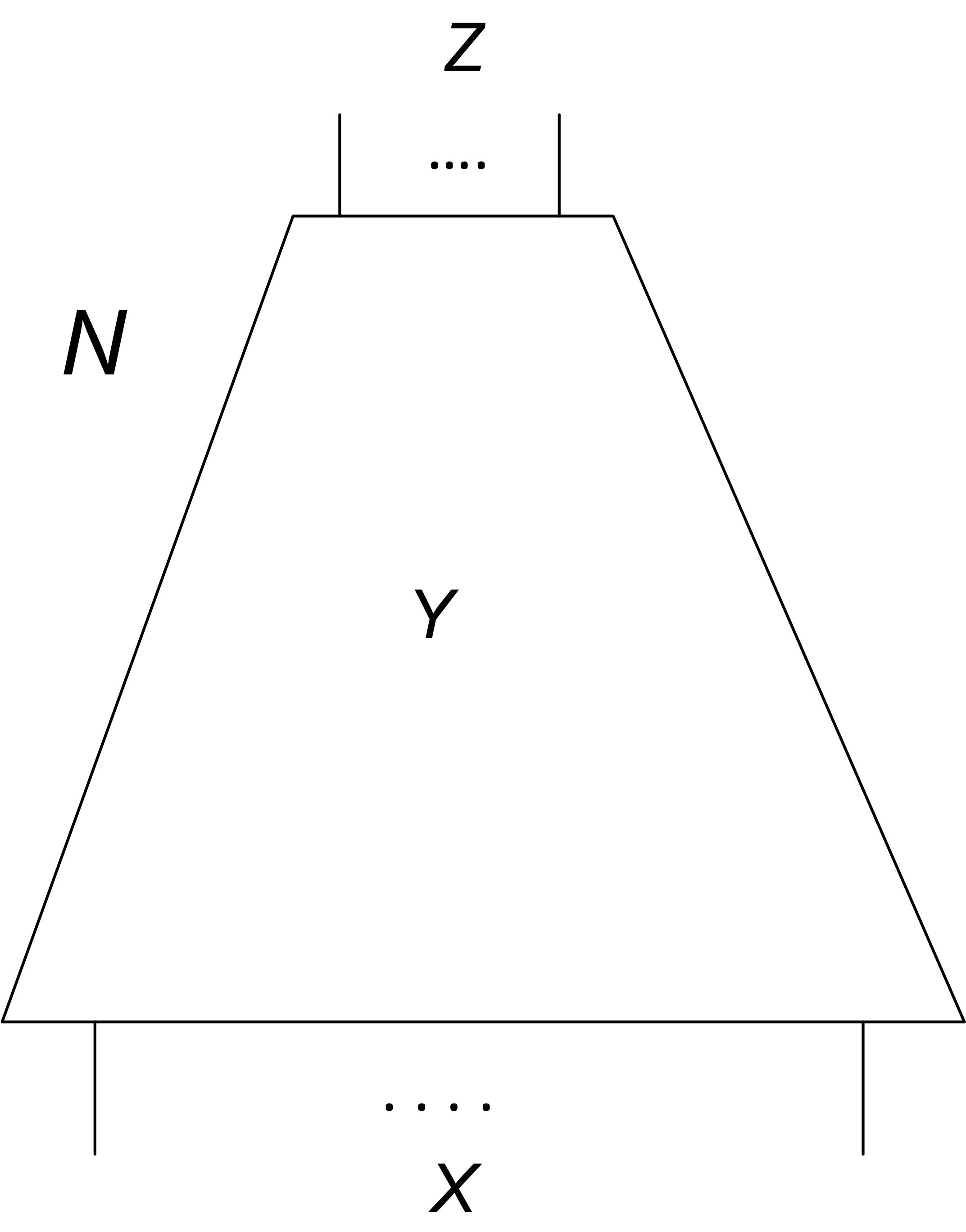
Suppose that one excludes a set of complete assignments to from the set of available inputs to . If an output is produced only by inputs that are in , excluding the inputs of from consideration leads to disappearance of from the range of . The CRR problem is to compute the outputs of that are excluded from the range of if the inputs of a set are excluded from consideration.
I-B Equivalence checking by CRR
Equivalence Checking can be a hard problem even for combinational circuits. This is especially true when the circuits to be compared have few functionally equivalent internal points. Our motivation here is that, as we argue in Section IV, equivalence checking by CRR facilitates construction of “natural” proofs. Such proofs are generated by industrial equivalence checkers when the circuits to be compared have a lot of internal points that are functionally equivalent.
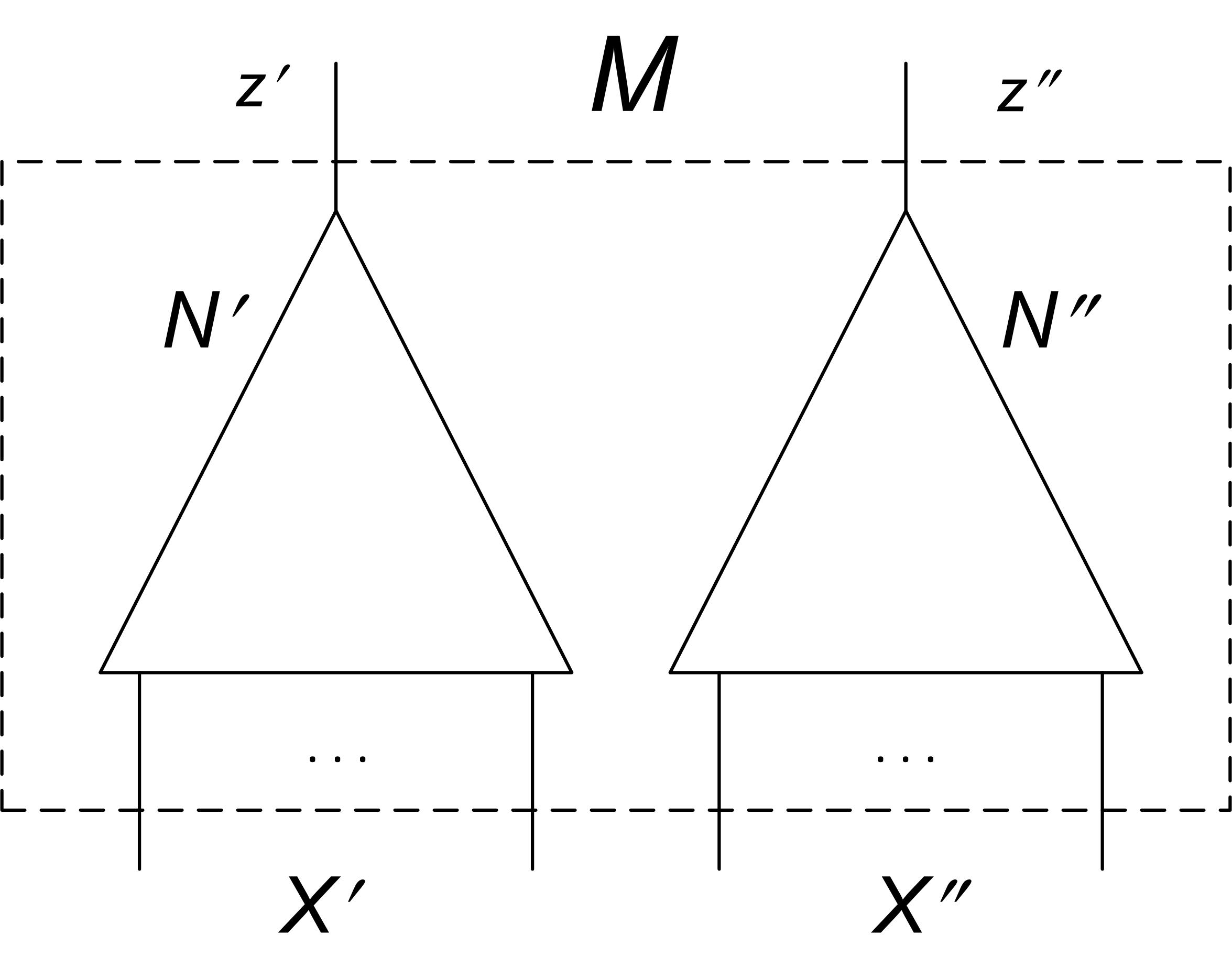
Application of CRR to equivalence checking is based on the following observation. Let and be single-output combinational circuits to be checked for equivalence. (The expression “a single-output circuit” means that this circuit has only one output variable. Whether we use term “output” to refer to an “output variable” or “output assignment” should be clear from the context.) Let be a two-output circuit composed of and as shown in Figure 2. Note that the sets and of input variables of and are independent of each other. Then, if and are not constants, the range of circuit consists of all four assignments to the output variables , of and .
Let (,) denote an assignment to variables . Suppose that one excludes from consideration all assignments (,) where . Then if and are functionally equivalent, such constraint on inputs of should lead to disappearing assignments and from the range of . If this is not the case, then there is an input (,) of where = for which and evaluate to different values i.e. and are inequivalent.
I-C Simulation by CRR
Functional verification of a combinational circuit comes down to checking if the range of contains an erroneous output. The straightforward approach of computing the range of is extremely inefficient. Simulation can be viewed as a way to simplify the range computation problem by reducing the set of inputs of to only one (regular simulation) or to a subset of inputs (symbolic simulation [2]). In this paper, we consider a different way to cope with complexity of range computation called simulation-by-exclusion. It is based on the idea of computing the reduction of range of caused by excluding some inputs from consideration rather than the entire range of .
Suppose that one needs to check if an erroneous output is produced by . Assume that a set of inputs is excluded from consideration. Let be the set of outputs that disappear from the range of due to exclusion of inputs from . One can have only the following two cases. The first case is . This means that either is not in the range of i.e. is correct or is buggy but there is an input producing . So exclusion of the inputs of does not make disappear from the range of . Then one can safely remove the inputs of from further consideration because if is buggy, the set of available inputs still contains a counterexample. The second case is . Then is buggy because is in its range.
In this paper, we describe the basic algorithm of simulation-by-exclusion and a few of its modifications.
I-D CRR by partial quantifier elimination
In [5], we showed that the CRR problem comes down to Partial Quantifier Elimination (PQE). The difference between partial and complete elimination is that, in PQE, only a part of the formula is taken out of the scope of quantifiers. Let us explain the relation between CRR and PQE in the context of equivalence checking. Let denote a propositional formula such that iff = . Equivalence checking by CRR comes down to taking out of the scope of quantifiers in formula . Here formulas and specify circuits and of Figure 2 and .
Taking out of the scope of quantifiers means finding a quantifier-free formula such that . If an output of circuit of Figure 2 disappears from its range after excluding inputs falsifying , this output falsifies . So if , circuits and are equivalent.
Let us explain the benefits of solving PQE. We assume here and henceforth that all formulas are represented in the Conjunctive Normal Form (CNF). The appeal of PQE is that it allows one to focus on deriving implications that matter. Namely, formula can be built solely from clauses that are implied by formula and are not implied by formula . This means that a PQE solver can ignore the resolvents obtained only from clauses of focusing on resolvents that are descendants of clauses of . Such zooming in on the “right” resolvents can make building formula much more efficient.
I-E Difference in CRR for equivalence checking and simulation
Our methods of using CRR for equivalence checking and simulation are different in one important aspect. In equivalence checking, one builds a circuit of Figure 2 and eliminates the spurious behaviors where . The presence of a bug corresponds to the situation when an erroneous output is not excluded from the range of under the input constraints. Conversely, simulation-by-exclusion is based on elimination of valid inputs. Then, the presence of a bug corresponds to the situation where an erroneous output is excluded from the range of the circuit under test.
The difference above is important for the following reason. When describing application of CRR to equivalence checking and simulation in Subsections I-B and I-C we assumed that range reduction is computed precisely. However, a PQE solver computes a superset of the set of excluded outputs [5] that may include outputs that are not in the range (see Subsection III-D.) We will refer to such outputs as noise. Adding noise to the set of excluded outputs in equivalence checking by CRR cannot trigger false alarms. (As we mentioned above the situation of concern here is when a bad output of is not excluded under input constraints. ) Conversely, in simulation-by-exclusion, adding noise can set off a false alarm. This happens when a bad output is in the set of excluded outputs computed by a PQE solver but, in reality, is not in the range of the circuit.
I-F Structure of the paper
This paper is structured as follows. Section II formally defines the CRR problem. Solving this problem by PQE is discussed in Section III. In Section IV, we introduce a method of equivalence checking by CRR. Simulation-by-exclusion is discussed in Sections V and VI. Some background and conclusions are given in Section VII and Section VIII respectively.
II Problem Of Computing Range Reduction
Let be a combinational circuit where are input, intermediate and output variables respectively. Let evaluate to output (i.e. a complete assignment to ) under an input (i.e. a complete assignment to ). We will say that is produced by .
Let be a set of inputs of . Denote by the range of under inputs of . That is an output is in iff is produced by for some input . If consists of all inputs of , then specifies the entire range of . From the definition of it follows that where is a set of inputs of .
Definition 1
Let and be sets of inputs of circuit such that . The CRR problem is to find the set . If an output is in , we will say that is excluded from due to excluding inputs of .
Below, we give definition of an approximate solution to the CRR problem. The reason is that, as we showed in [5], algorithms for partial quantifier elimination provide only approximate solutions to the CRR problem (see Subsection III-D).
Definition 2
Let denote from Definition 1. Let be a superset of . We will say that is an approximate solution of the CRR problem if for every it is true that . In other words, an approximate solution of the CRR problem is the precise solution modulo outputs that are not in . We will refer to such outputs as noise.
III Computing Range Reduction By Partial Quantifier Elimination
In this section, we relate range computation with quantifier elimination and range reduction computation with partial quantifier elimination. Besides, we recall our previous results on complete and partial quantifier elimination.
III-A Complete and partial quantifier elimination
Given a quantified CNF formula , the problem of Quantifier Elimination (QE) is to find a quantifier-free formula such that .
Given a quantified CNF formula , the problem of Partial Quantifier Elimination (PQE) is to find a quantifier-free CNF formula such that . We will say that formula is obtained by taking out of the scope of quantifiers in . The term “partial” emphasizes the fact that, in contrast to QE, only a part of the quantified formula is taken out of the scope of quantifiers.
III-B Computing range by QE and range reduction by PQE
Let be a CNF formula specifying circuit . That is every consistent assignment of Boolean values to variables of is a satisfying assignment for and vice versa. Let be a CNF formula such that . Then the outputs of satisfying specify the range of . So computing the range of comes down to solving the QE problem. Assume that only inputs satisfying formula are considered. Then a CNF formula equivalent to specifies the range of under inputs satisfying .
Suppose that we are interested only in finding how the range of reduces if the inputs falsifying are excluded i.e. only inputs satisfying are considered. As we showed in [5], this problem comes down to finding CNF formula such that where . Here specifies an approximate solution to the CRR problem (see Definition 2) i.e.
-
•
the outputs falsifying specify a superset of the set of outputs disappearing from the range of due to excluding inputs falsifying
-
•
every output falsifying either disappeared from the range of due to excluding inputs falsifying or is not in the range of
III-C Complexity of computing range and range reduction
As we mentioned above, computing the range of reduces to QE whereas finding range reduction comes down to PQE. So the complexity of computing range and range reduction is directly related to that of QE and PQE.
The difference between QE and PQE can be expressed in terms of computing clause redundancy [4, 6]. For the sake of simplicity, in descriptions of algorithms of [4] and [6] given below we omitted the fact that they use branching. (First the problem is solved in subspaces. Then the results of branches are merged to produce a solution that holds for the entire search space.)
As we showed in [3, 4], to eliminate quantifiers from where one needs to find a CNF formula implied by that makes all the clauses of with quantified variables redundant in . Then formula is logically equivalent to . We will refer to clauses containing variables of (i.e. quantified variables) as -clauses.
Clauses of are built from by adding resolvent clauses. If a resolvent is a -clause, its redundancy has to be proved along with the original -clauses of . Eventually, a sufficient number of clauses depending only on free variables (i.e. those of ) is added to make the new and old -clauses of redundant.
Now, let us consider the PQE problem of taking formula out of the scope of quantifiers in . As we showed in [6], this problem comes down to finding formula implied by that makes redundant the clauses of in . The clauses of are built by resolving clauses of . If a resolvent is a -clause and is a descendant of a clause of , its redundancy needs to be proved as well. On the other hand, -resolvents produced solely from clauses of do not need to be proved redundant. This can make PQE drastically simpler than QE if is much smaller than .
III-D Quality of PQE-solving
In this subsection, we clarify the relation between the quality of a PQE-algorithm and that of an approximate solution to the CRR problem. As in the previous subsection, we assume that formula is obtained by taking formula out of the scope of quantifiers in . Here and specifies circuit .
The definitions below are based on the following observation. If is a solution to the PQE problem above, a formula obtained by adding to a clause implied by is also a solution to the PQE problem. One can view as “noise”. Such a clause is falsified only by outputs that are not in the range of . In general, the set of outputs falsifying a clause of can contain outputs that are in the range of and those that are not.
Definition 3
Let be a clause of . We will say that is noise-free if every output falsifying is in the range of . Otherwise, clause is called noisy. Formula is called a noisy solution to the PQE problem if it contains a noisy clause. Otherwise, is called noise-free.
IV Equivalence Checking By Computing Range Reduction
In this section, we describe equivalence checking by CRR. In Subsection IV-A, we give the main proposition on which our method is based. Subsection IV-B compares equivalence checking by CRR and SAT-solving.
IV-A Main proposition
The intuition behind applying CRR to equivalence checking was described in the introduction. In this subsection, we substantiate this intuition in a formal proposition.
Let and be single-output combinational circuits to be checked for equivalence. Let be the circuit composed of and as shown in Figure 2. Let and be CNF formulas specifying and respectively. Assume that and . Denote by formula that is satisfied by inputs and to and iff = .
Proposition 1
Let be a CNF formula obtained by taking out of the scope of quantifiers from the formula where . Circuits and are functionally equivalent iff one of the two conditions below hold:
-
1.
-
2.
Circuits and are identical constants (i.e. or .).
Proof:
The if part. Assume that . Since is a solution to the PQE problem, it is implied by formula . This means that for any consistent assignments and to and such that = the values of and are equal to each other. Thus and are functionally equivalent. If the second condition holds i.e. and are identical constants, then are obviously equivalent.
The only if part. Assume that and are functionally equivalent. We need to prove that one of the conditions above holds. Assume the contrary i.e. that does not hold and , are not identical constants.
Let us assume, for the sake of clarity, that . (The case when can be considered in a similar manner.) This means that formula does not contain a clause falsified by an assignment . Let us consider the following two reasons for that.
First, is not implied by . This means that there is an assignment = to and for which evaluates to 0 and evaluates to 1. Hence and are inequivalent and we have a contradiction.
Second, is implied by both and and one does not need to add clause to make formula redundant. Since and do not share variables, the fact that implies means that the circuit does not produce output even when inputs of are not constrained by . This is possible only if at least one of the circuits , is a constant. Let us consider the following three cases.
-
•
and are identical constants. Contradiction.
-
•
is a constant 1 and is either a constant 0 or a non-constant circuit. Hence . Contradiction.
-
•
is a constant 0 and is either a constant 1 or a non-constant circuit. So . Contradiction.
∎
IV-B Equivalence checking by regular SAT-solving and CRR
In this subsection, we compare equivalence checking by a SAT-solver with Conflict Driven Clause Learning (CDCL) and by CRR.
The equivalence checking of circuits and can be performed by checking the satisfiability of formula equal to . Indeed, the existence of an assignment satisfying means that and produce different output values for the same input . We will refer to the method of equivalence checking by a SAT solver based on CDCL solver as EC_CDCL. Here EC stands for Equivalence Checking.
Proposition 1 justifies the following method of equivalence checking by CRR. We will refer to this method as EC_CRR. This method solves the PQE problem specified by formula equal to where . Namely, EC_CRR computes formula obtained by taking out of the scope of quantifiers in . If , then and are equivalent. Otherwise, one needs to check if and are identical constants. If so, then and are equivalent, otherwise they are not. Theoretically, proving and inequivalent does not require generation of a counterexample. The very fact that or and are not constants guarantees that and are not equivalent. However, in a practical implementation of EC_CRR, a counterexample may be generated before computation of formula is completed.
To distinguish the formulas solved by EC_CDCL and EC_CRR, we will refer to them as and respectively. The SAT problem can be viewed as a special case of QE where all variables of the formula are existentially quantified. Since EC_CRR is actually a PQE algorithm, one can compare EC_CRR and EC_CDCL in terms of computing clause redundancy as we did Subsection III-C. In those terms, the objective of deriving an empty clause by a SAT-solver is to make redundant all clauses with quantified variables (i.e. all clauses containing literals). So the difference between EC_CDCL and EC_CRR is that the former is aimed at making redundant all clauses of while the goal of the latter is to make redundant only a small subset of clauses of (namely those of ).
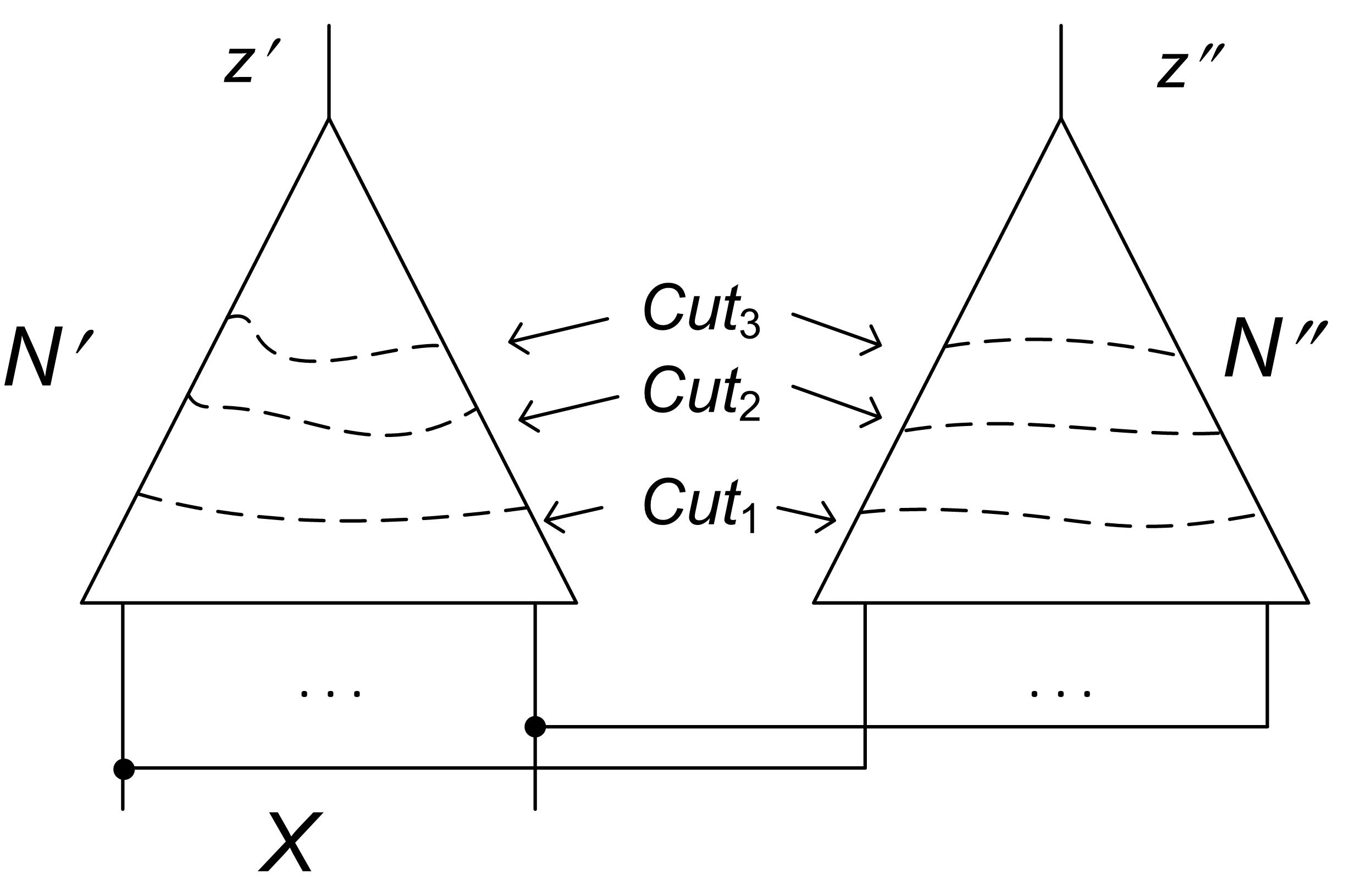
The fact that EC_CRR needs to prove redundancy of a smaller set of clauses than EC_CDCL does not necessarily imply greater efficiency of EC_CRR. What matters, though, is that solving the PQE problem specified by facilitates generation of proofs based on the cut advancement strategy shown in Figure 3. Such proofs are natural for structurally similar circuits. Here is a naive version of how this works. To make clauses of redundant one just needs to produce new clauses obtained by resolving with those of . Note that a PQE solver has to make redundant a new resolvent (depending on a quantified variable) only if it is a descendant of a clause from . In general, such a clause will contain variables of both and relating variables of and . The set of new resolvents that made the clauses of redundant specify a new “cut” that consists of the variables present in . After that a set of descendants of that make the clauses of redundant is built. This goes on until the cut consisting of variables and is reached.
A cut advancement strategy has been successfully used by industrial equivalence checkers. However, it is applied only when and are so structurally similar that one can build a cut consisting of internal points of and that are functionally equivalent. So this version of cut advancement is very limited. On the other hand, EC_CRR can arguably extend the cut advancement strategy to a much more general class of equivalence checking problems.
V Two Ways To Handle Complexity Of Range Computation
Function verification of a combinational circuit comes down to checking if there is an input for which produces an erroneous output. We assume that the erroneous outputs are specified by the user as a set . A straightforward way to verify is to find the range of and check if it overlaps with . As we mentioned in Subsection III-B, finding the range of comes down to solving the QE problem. Although, in general, the latter is very hard, in some cases, it can be efficiently solved for real-life circuits. For example, if is a single-output circuit, computing its range comes down to Circuit-SAT that, in many practical cases, can be solved by state-of-the-art SAT-solvers. In Sections V and VI, we assume that functional verification of is too hard for a SAT-solver.
In this section, we consider two methods for reducing the complexity of computing range of . One method is to compute range of for a subset of inputs. This method is used in traditional simulation. We introduce another method based on the following idea: compute range reduction caused by excluding some inputs of rather than the entire range.
V-A Simulation as range computation111 Traditionally, given a combinational circuit , simulation is a deterministic procedure for computing the output produced by when an input is applied. Unfortunately, this procedure does not have a trivial extension to the case when two or more inputs are applied at once. For that reason, we use a semantic notion of simulation as a computation of the range of for a subset of inputs, omitting a detailed description of this computation.
Let be a CNF formula specifying circuit . Computing the range of comes down to finding formula logically equivalent to where . Simulation can be viewed as a way to decrease the complexity of finding by shrinking the set of allowed inputs to only one. Let be a CNF formula satisfied by only one input . Then computing the output produced by comes down to solving the QE problem . Formula can be represented as a set of unit clauses satisfied only by . (A clause is called unit if it contains exactly one literal.) A solution for this QE problem can be represented as a set of unit clauses satisfied only by the output of for input .
An obvious flaw of traditional simulation is that it provides information about the value of only for one input out of . One can address this issue by using formulas with many satisfying assignments, Then solving the QE problem specified by finds the range of where all inputs satisfying are processed together. Unfortunately, the complexity of QE grows very fast as the number of inputs satisfying increases. One way to reduce the complexity of QE when allows many inputs is employed in symbolic simulation [2]. The idea is to pick formulas for which all inputs satisfying have the same execution trace.
V-B Simulation-by-exclusion
We described the main idea of simulation-by-exclusion in Subsection I-C. Given constraints excluding some inputs, compute only reduction of range of caused by this exclusion rather than the entire range of under allowed inputs. Here we continue explanation describing how simulation-by-exclusion is implemented by PQE. Let the complete assignments to falsifying CNF formula specify the inputs excluded from consideration. Let CNF formula be obtained by taking out of the scope of quantifiers in where . Then the outputs falsifying specify the range reduction of due to exclusion of inputs falsifying .
Suppose that no output falsifying is in the set of erroneous outputs of . This implies that either is correct or there is an input producing an output from (a counterexample) that is not excluded i.e. satisfies . This means that removing all inputs falsifying from consideration is safe because it cannot remove all counterexamples (if any).
As we mentioned earlier, a PQE solver provides only an approximate solution to the CRR problem. This means that even if an output falsifying is in , one still needs to check if is in the range of . A trivial way to do it is to check if formula is satisfiable where is the longest clause falsified by . If so, clause is not implied by and is in the range of .
Checking the satisfiability of may be expensive. However, in the algorithm of simulation-by-exclusion we introduce in Section VI, formula is constantly updated by adding clauses excluding inputs of . This may drastically simplify the SAT-check above. Besides, there are at least two techniques to make this SAT-check even simpler. The first technique is based on the fact that all inputs producing (if any) falsify . So checking if is in the range of reduces to testing the satisfiability .
The second technique is based on the following observation. Let be a resolution derivation of a clause of falsified by . Then if is in the range of , every cut of proof has to include at least one clause that is implied by but not . (We assume here that is a directed graph nodes of which correspond to original clauses of or resolvents.) If every clause of is implied by then the clause derived by is implied by too and so is not in the range of . So to find out if is in the range of it is sufficient to check if formula is satisfiable for every clause of . The longer clause is the simpler this SAT-check. If all such formulas are unsatisfiable for then is not in the range of . Otherwise, an input of producing can be extracted from an assignment satisfying formula .
V-C Simulation-by-exclusion versus regular simulation
In this subsection, term “regular simulation” refers to finding a solution to the QE problem specified by that we introduced in Subsection V-A (see also Footnote 1).
The main difference between regular simulation and simulation-by-exclusion is as follows. In regular simulation, to get a result one needs to perform a computation that goes all the way from inputs to outputs. If only one input is allowed by , this computation produces an execution trace consisting of values assigned to variables of when applying input . On the other hand, simulation-by-exclusion can get a valuable result even by a local computation that does not reach the outputs of .
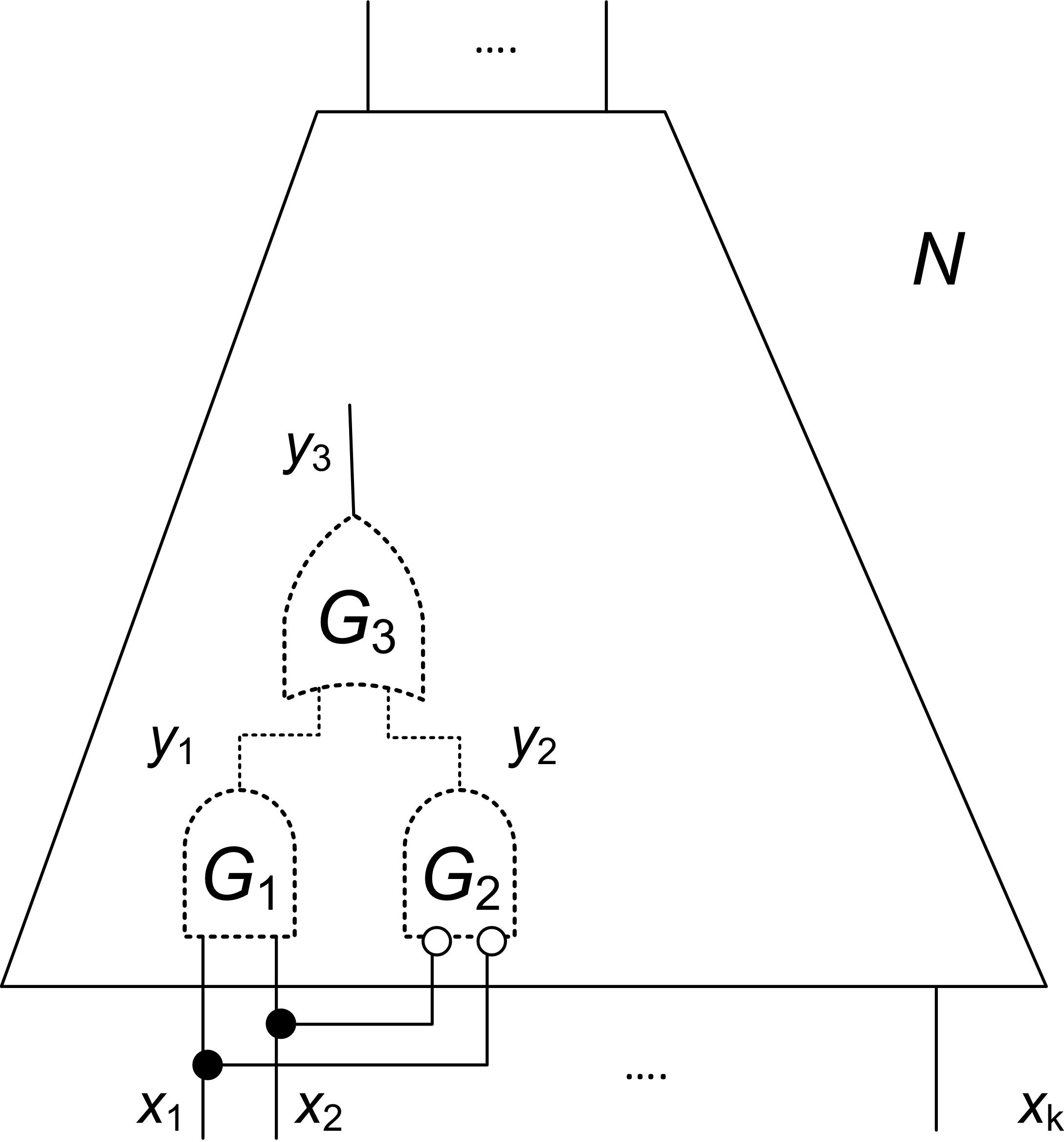
Let us consider the example of Figure 4 showing a circuit . Suppose that lines feed only gates and and lines feed only gate . Note that the output of specified by implements function i.e. iff values of and are equal. Let denote clause . It is not hard to show that is redundant in formula i.e. . The redundancy of means that one can exclude the inputs falsifying (i.e. all the inputs for which ) from consideration because such exclusion does not change the range of . Indeed, since feed only gates , circuit produces the same output for two inputs that are different only in the values of and/or if these inputs produce the same assignment to . Since, even after excluding assignment , both values of can still be produced, the set of outputs circuit can generate remains intact.
Importantly, the fact that clause can be safely used to exclude inputs of is derived locally without any knowledge of the rest of the circuit . Such a result cannot be reproduced efficiently by regular simulation. To exclude the inputs falsified by from consideration one would need to solve the QE problem specified by . The complexity of such QE can be very high if the size of circuit is large. Of course, if regular simulation succeeds in performing QE, it might find a bug. However, if no bug is found, the result is the same as for simulation-by-exclusion: the inputs falsifying can be excluded. However the price of this result in regular simulation can be dramatically higher than in simulation-by-exclusion.
VI A Few Algorithms Implementing Simulation-By-Exclusion
In this section, we describe a few algorithms implementing simulation-by-exclusion. The basic algorithm is shown in Figure 5 and described in Subsections VI-A and VI-B. Two modifications of this algorithm are given in Subsection VI-C. For the sake of clarity, we will assume that one needs to verify a single-output circuit . We will assume that if is correct it always evaluates to 0. An input for which evaluates to 1 is a counterexample showing that is buggy. The extension of algorithms of this section to multi-output circuits is straightforward.
VI-A Algorithm description
The algorithm of simulation-by-exclusion called SimByExl consists of three parts separated in Figure 5 by the dotted lines. In the first part (lines 1-6), an input is generated for which evaluates to 0 (lines 2-4). This input is never excluded and serves two purposes. First, it guarantees that is not a constant 1. Second, keeping allowed prevents SimByExcl from excluding all inputs for which evaluates to 0. SimByExcl also builds formula specifying (line 1) and generates , the longest clause falsified by (line 5). Finally, SimByExcl initializes formula that accumulates the clauses excluding inputs of (line 6).
The second part of SimByExcl (lines 7-14) consists of a while loop. In every iteration of this loop, a new clause is generated (line 10). Clause excludes at least one new input of constructed as an assignment satisfying formula (line 8). If SimByExcl fails to find such , all inputs of but have been excluded. Then is correct since, for the excluded inputs, it takes the same value as for i.e. 0.
| // is a single-output circuit | ||
| // is the set of input variables | ||
| // is the set of internal variables | ||
| // specifies the output variable | ||
| // returns a counterexample | ||
| // or nil if no counterexample exists | ||
| // | ||
| { | ||
| 1 | ; | |
| 2 | ; | |
| 3 | ||
| 4 | if () return(); | |
| 5 | ; | |
| 6 | ; | |
| 7 | while (true) { | |
| 8 | ; | |
| 9 | if () return(); | |
| 10 | ; | |
| 11 | ; // | |
| 12 | if () break; | |
| 13 | ; | |
| 14 | ; } | |
| 15 | if return(); | |
| 16 | ; | |
| 17 | return(); } |
After generating clause , SimByExcl computes CNF formula (line 11). It is obtained by taking out of the scope of quantifiers in where . Formula can only consist of clause or be empty (no clauses) in which case is always true. Note that formula cannot consist of unit clause because SimByExcl never excludes all inputs for which evaluates to 0. Hence clause is not implied by . If is empty, then the inputs falsifying can be safely excluded from consideration. So clause is added to (line 13) and to (line 14).
If is not empty and hence equal to , SimByExcl breaks the loop (line 12) and executes the third part of the algorithm (lines 15-17). In this part, SimByExcl checks whether the derived clause is pure noise or excludes a counterexample. If no counterexample is excluded by , then clause is just noise, i.e. and so is correct. Otherwise, SimByExcl extracts a counterexample from an assignment satisfying .
Note that one can just check whether is constant 0 by running the SAT-check on where is the original formula specifying . SAT-checking of can be much simpler for the following two reasons. First, is constantly updated by SimByExcl by adding clauses excluding inputs. As we explain in Subsection VI-C such clauses are obtained by non-resolution derivation and so are very valuable for a resolution-based SAT-solver. Second, the negation of clause consists of unit clauses that can additionally simplify the SAT-check. One more way to simplify this SAT-check that we described in Subsection V-B is to exploit the resolution derivation of clause . For the sake of simplicity this possibility is not mentioned in Figure 5.
VI-B Completeness and soundness of SimByExcl
SimByExcl produces an answer for every circuit and so it is complete. Indeed, in every iteration of the while loop, SimByExcl excludes at least one new input of that has not been excluded so far. So the set of allowed inputs monotonically decreases. Eventually, SimByExcl either excludes all inputs but or derives a clause . In either case, SimByExcl terminates returning a result.
SimByExcl is sound. It reports that is correct in two cases. First, when a clause is generated and SimByExcl proves that . Then is unsatisfiable and hence no counterexample exists. Second, SimByExcl reports that is correct when all inputs of but are excluded by added clauses. Since SimByExcl guarantees that a new clause cannot remove all counterexamples and evaluates to 0 at , this means that evaluates to 0 for all inputs. SimByExcl reports that is buggy when an assignment satisfying is found. This assignment specifies an input for which evaluates to 1.
VI-C Two modifications of the algorithm
In this subsection, we consider two modifications of SimByExcl that can be used to improve its efficiency. The first modification is given in Figure 6. The high-lighted part shows the lines added to the code of SimByExcl of Figure 5.
| { | |||
| 6 | ; | ||
| 6.1 | ; | ||
| 7 | while (true) { | ||
| 12 | if () break; | ||
| 13 | ; | ||
| 14 | ; | ||
| 14.1 | ; | ||
| 14.2 | if { | ||
| 14.3 | ; | ||
| 14.4 | ; | ||
| 14.5 | if () return();}} | ||
The main idea here is to occasionally run a light SAT-check on formula . We assume that the effort of the SAT-solver is limited by some parameter specifying e.g. the maximum number of backtracks. Such a SAT-check is invoked when the number of new clauses added to exceeds a threshold. Such a strategy makes sense because clauses added to by SimByExcl are not derived by resolution. Deriving such clauses by resolution may be dramatically more complex, which makes them quite valuable for a resolution based SAT-solver.
Consider for instance, derivation of clause for circuit shown in Figure 4 (see discussion of Subsection V-C). Assume that circuit has only one output specified by variable . Suppose that formula is satisfiable (i.e. is buggy) and excludes at least one counterexample. Then is not even implied by and thus cannot be derived by resolution. However, even if is implied by , its resolution derivation may be very hard and involve many clauses of . On the other hand, a PQE-solver is capable of concluding that can be safely added to just by examining the clauses specifying gates ,, and using the fact that variables do not feed any other gates.
| { | |||
| 6 | ; | ||
| 6.1 | ; | ||
| 7 | while (true) { | ||
| 12 | if () break; | ||
| 13 | ; | ||
| 14 | ; | ||
| 14.1 | ; | ||
| 14.2 | if { | ||
| 14.3 | ; | ||
| 14.4 | ; | ||
| 14.5 | if () return();}} | ||
The second modification is shown in Figure 7. In this modification one occasionally runs regular simulation. We assume that only tests that have not been excluded yet are generated. These are the tests satisfying formula . A simulation run is performed when the number of new clauses added to exceeds a threshold. We assume that the number of tests generated in a simulation run is limited by parameter #tries. Performing occasional simulation runs makes sense because adding new clauses reduces the search space and hence increases the probability of generating a counterexample.
VII Background
The existing methods for checking equivalence of combinational circuits and can be roughly partitioned into two groups. The first group consists of methods that do not try to exploit the structural similarity of and . An example of an equivalence checker of this group is an algorithm that builds separate BDDs [1] of and and then checks that these BDDs are identical. One more example, is an equivalence checker constructing a CNF formula that is satisfiable only if and ” are not equivalent. (In Subsection IV-B we explained how such a formula is generated.) This equivalence checker runs a SAT-solver [10, 11] to test the satisfiability of this formula. Unfortunately, the algorithms of this group do not scale well with the size of .
Methods of the other group try to take into account the similarity of [9, 7]. These methods work well even for quite large circuits if they are very similar structurally. A flaw of such methods is that they do not scale well as become more dissimilar. As we mentioned earlier, the method based on CRR that we introduced in this paper can be arguably used to design an equivalence checker that take the best of both worlds. That is it scales better than the methods of the first group in terms of circuit size and improves on the scalability of the methods of the second group in terms of circuit dissimilarity.
Simulation is still the main workhorse of verification. So a lot of research has been done to improve its efficiency and effectiveness. For example, symbolic simulation [2] is used to run many tests at once. Constrained random simulation generates tests aimed at achieving a particular goal e.g. better coverage with respect to a metric [8]. However, all these methods are based on the paradigm of decreasing the complexity of range computation by reducing the number of inputs to be considered at once. To the best of our knowledge none of existing methods exploits the idea of computing range reduction introduced in [5]. There we explored this idea in the context of model checking. In the current paper, we contrast simulation based on computing range reduction with traditional simulation.
VIII Conclusions
We described new methods of equivalence checking and simulation based on Computing Range Reduction (CRR). Our interest in these methods is twofold. First, they allow one to take into account subtle structural properties of the design. For instance, equivalence checking based on CRR allows can employ a “cut advancement” strategy. A limited version of this strategy has been very successful in equivalence checking of industrial designs. Second, one can argue that CRR can be efficiently performed using a technique called partial quantifier elimination that we are working on.
Acknowledgment
This research was supported in part by NSF grants CCF-1117184 and CCF-1319580.
References
- [1] R. Bryant. Graph-based algorithms for Boolean function manipulation. IEEE Transactions on Computers, C-35(8):677–691, August 1986.
- [2] R. Bryant. Symbolic simulation—techniques and applications. In DAC-90, pages 517–521, 1990.
- [3] E.Goldberg and P.Manolios. Quantifier elimination by dependency sequents. In FMCAD-12, pages 34–44, 2012.
- [4] E.Goldberg and P.Manolios. Quantifier elimination via clause redundancy. In FMCAD-13, pages 85–92, 2013.
- [5] E.Goldberg and P.Manolios. Bug hunting by computing range reduction. Technical Report arXiv:1408.7039 [cs.LO], 2014.
- [6] E. Goldberg and P. Manolios. Partial quantifier elimination. In Proc. of HVC-14, pages 148–164. Springer-Verlag, 2014.
- [7] E. Goldberg, M. Prasad, and R. Brayton. Using SAT for combinational equivalence checking. In DATE, pages 114–121, 2001.
- [8] O. Guzey and L.C. Wang. Coverage-directed test generation through automatic constraint extraction. In HLDVT.
- [9] A. Kuehlmann and F. Krohm. Equivalence Checking Using Cuts And Heaps. DAC, pages 263–268, 1997.
- [10] J. Marques-Silva and K. Sakallah. Grasp – a new search algorithm for satisfiability. In ICCAD-96, pages 220–227, 1996.
- [11] M. Moskewicz, C. Madigan, Y. Zhao, L. Zhang, and S. Malik. Chaff: engineering an efficient sat solver. In DAC-01, pages 530–535, New York, NY, USA, 2001.