Expanding bipartite Bell inequalities for maximum multi-partite randomness
Abstract
Nonlocal tests on multi-partite quantum correlations form the basis of protocols that certify randomness in a device-independent (DI) way. Such correlations admit a rich structure, making the task of choosing an appropriate test difficult. For example, extremal Bell inequalities are tight witnesses of nonlocality, but achieving their maximum violation places constraints on the underlying quantum system, which can reduce the rate of randomness generation. As a result there is often a trade-off between maximum randomness and the amount of violation of a given Bell inequality. Here, we explore this trade-off for more than two parties. More precisely, we study the maximum amount of randomness that can be certified by correlations exhibiting a violation of the Mermin-Ardehali-Belinskii-Klyshko (MABK) inequality. We find that maximum quantum violation and maximum randomness are incompatible for any even number of parties, with incompatibility diminishing as the number of parties grows, and conjecture the precise trade-off. We also show that maximum MABK violation is not necessary for maximum randomness for odd numbers of parties. To obtain our results, we derive new families of Bell inequalities certifying maximum randomness from a technique for randomness certification, which we call “expanding Bell inequalities”. Our technique allows a bipartite Bell expression to be used as a seed, and transformed into a multi-partite Bell inequality tailored for randomness certification, showing how intuition learned in the bipartite case can find use in more complex scenarios.
1 Introduction
Distant measurements on a shared quantum system can display correlations inaccessible to any locally realistic model [1, 2]. Such correlations are termed nonlocal and provide a device-independent (DI) witness of useful quantum characteristics, opening up a new paradigm of information processing [3]. Tasks such as randomness expansion [4, 5, 6, 7, 8], amplification [9] and key distribution [10, 11, 12, 13, 14, 15] can all be achieved in the DI regime, where security is proven based on the observed correlations and without trusting the inner workings of the devices. Moreover, nonlocal correlations can be used to prove the presence of a particular state or sets of measurements, known as self-testing [16, 17, 18, 19, 20, 21].
Certification of DI randomness typically uses a Bell inequality, and different Bell inequalities give different amounts of certified randomness. It is natural to consider extremal Bell inequalities, which form the minimal set separating local and non-local correlations. The set of correlations compatible with high violation is tightly constrained and can negatively affect the certification of randomness. For example, in the simplest bipartite scenario, correlations with higher violation of the only extremal Bell inequality, the Clauser-Horne-Shimony-Holt (CHSH) inequality, cannot certify maximal DI randomness, while those with a lower violation can [22, 23]. Further complications arise when scenarios with more inputs, outputs or parties are considered because the number of different classes of extremal Bell inequalities grows and it becomes more difficult to navigate the trade-offs between extremal Bell violation and maximum certifiable randomness. Alongside foundational interest, this question is also motivated practically, in finding more robust device-independent randomness expansion (DIRE) protocols [23].
In this work we study the family of multi-partite Bell inequalities due to Mermin, Ardehali, Belinskii, and Klyshko (MABK) [24, 25, 26] and their application to DIRE. These all have two inputs and two outputs per party. The one and two sided randomness given a tripartite MABK violation was bounded in [27, 28], and compared to other tripartite inequalities in [29]. Considering global randomness, reference [30] gave a bipartite construction for certification of bits of randomness using copies of almost unentangled states.
Reference [31] showed how, for an odd number of parties , maximum MABK violation can certify bits of DI randomness, whilst reference [32] provided an alternative family of Bell inequalities certifying bits in the even case. This leaves the open the following questions: is MABK suitable for maximum randomness generation when is even, and, if not, what is the compatibility trade-off between MABK violation and maximum randomness for arbitrary ? Are there correlations with lower MABK that achieve maximal randomness when is odd?
To analyse multi-partite nonlocality, we require tools to construct multi-partite Bell tests. To do so, one approach is to generalize intuition from the well understood CHSH scenario; this has been done to extend the number of measurements per party [33, 34], or the number of parties [35], where it was shown how to construct multi-partite Bell inequalities from a bipartite seed. Self-testing results using projections onto bipartite subsystems [36, 37, 38] suggest stronger capabilities of the technique presented in reference [35], prompting the question: can it be leveraged for multi-partite randomness certification?
Our work seeks to answer these questions. We first show maximum MABK violation certifies bits of global randomness when is even, contrasting the bits certified when is odd [31]. We then investigate the limits on certifiable randomness from quantum behaviours that violate an MABK inequality. To do so, we construct new families of -partite Bell inequalities whose maximum violation certifies bits for arbitrary . When is even, we show for any MABK violation up to a non-maximal value , there exists a quantum behaviour achieving which maximally violates an inequality from our family, and hence certifies maximum global randomness. For violations above , we find (using a second family of inequalities) that randomness monotonically decreases with MABK violation. Our results lower bound this trade-off, and we provide numerical evidence of tightness, indicating an extension of the known tight bound when [23] to arbitrary . Additionally, we show that this trade-off diminishes (in the sense that the gap between and maximal MABK violation decreases) as the number of parties grows. Finally, for odd , we use our family of Bell inequalities to show that bits of randomness can be certified for a range of MABK violations.
Our constructions are formed from a type of concatenation of bipartite Bell inequalities, allowing us to lift our intuition derived from the bipartite case [23] to the multipartite setting. Specifically, we extend the technique presented in reference [35], originally introduced to witness genuinely multi-partite nonlocality. Our extension exploits self-testing properties of the seed to certify randomness. Specifically, our main technical contribution is a decoupling lemma (see Eq.˜13), which shows that under certain conditions the maximum violation of an expanded Bell expression implies a decoupling between the honest parties and Eve. Such decoupling occurs for extremal quantum correlations, and guarantees security [39]. We envisage that this technique will be a useful tool in multi-partite DI cryptography and of independent interest.
The paper is structured as followed. In Section˜2 we provide the necessary background and notation. In Section˜3 we detail our enhancement of the technique from [35], along with the decoupling lemma. In Section˜4 we describe our constructions, and show that they certify bits of randomness for a broad range of MABK violations, which we conjecture to be optimal; this result is summarized in Lemmas˜6 and 7. We additionally show how the conjectured highest value of MABK at which maximum randomness remains possible tends to the maximum quantum value as the number of parties increases (see Proposition˜6). In Section˜5 we consider MABK values beyond the conjectured threshold for maximum randomness, up to the maximum quantum value. Here we give a candidate form for the exact trade-off, which is summarized in Lemma˜10. We conclude with a discussion in Section˜6. All technical proofs can be found in the appendices.
2 Background
2.1 Multiparty DI-scenario
We consider an party, 2-input 2-output DI scenario, where isolated devices are given a random input, labeled , and produce an output stored in a classical register , where indexes the party. We use bold to denote tuples; for example, denotes an bit string of device outputs. The behaviour of the devices is then described by the joint conditional probability distribution , which must be no-signalling following the isolation of the devices.
A behaviour is quantum if there exists (following Naimark’s dilation theorem [40]) a pure state and sets of orthonormal projectors that can reproduce the distribution via the Born rule. Specifically, we consider an adversary Eve, who wishes to guess the device outputs, and let denote the global state in the Hilbert space , where is held by Eve, and is held by device . Throughout the text, tildes will denote elements pertaining to physical Hilbert spaces (whose dimension is unknown), whilst no tilde will describe qubit Hilbert spaces . We let be binary-outcome projective measurements on , and we denote the corresponding observables of each party by ; here bracketed superscripts will typically keep track of the party to which the object belongs (i.e., the Hilbert space on which it acts). Following measurements by the honest parties, we obtain the classical quantum state , where and . The behaviour (as seen by the honest parties) is recovered by .
2.2 Multiparty Nonlocality
Given an observed distribution , it will be useful to quantify its distance from the local boundary. When , the CHSH inequality, as the only non-trivial facet, is a natural choice. The multiparty scenario is more complex however, and the number of classes of Bell inequality increases rapidly with [41]. Instead, a general way to quantify this distance for an arbitrary scenario can be used, which is related to how much the local polytope needs to be diluted to encompass a given non-local correlation. Computing this can be done using linear programming (see Section˜B.6).
In this work, we choose to study one such CHSH generalization and its relationship to DI randomness; the MABK family [24, 25, 26],
| (1) |
where when the behaviour is quantum. [In effect the prefactor corresponds to relabelling the outcomes and to match the usual formulation of observables with eigenvalues .] The local bound is given by , and the maximum quantum value is . Note that the MABK functional is characterized by the fact that the coefficients are equal for all strings with the same Hamming weight (that is, the number of s in the string ). When is even, , and when is odd . This is illustrated by writing out the first few cases. To ease notation, we let and .
| (2) | ||||
Above, is the CHSH functional, whereas is the Mermin functional, associated with the GHZ paradox [42]. The property that all input strings of the same Hamming weight have the same coefficient makes the MABK expressions invariant under party relabelings. Additionally, note that for even, every correlator for is included in the expression, whereas for odd, exactly half of the correlators are included.
2.3 Self-testing
It is known that maximum quantum violation of the MABK family is uniquely achieved, up to local isometries, by the GHZ state and pairs of maximally anticommuting observables [43, 44]. This form of uniqueness arising from a Bell expression is known as self-testing. In this work, we take the choice , , and , where .
Whilst self-testing statements can be formally defined between parties (see, e.g., [36, 20]), in our formulation it will only be necessary to use a bipartite definition.
Definition 1 (Bipartite self-test).
Let index two distinct parties. Define the sets of target qubit projectors , , and a target two qubit state . Let be a Bell operator between parties and , with maximum quantum value . The inequality self-tests the target state and measurements if, for all physical quantum strategies that satisfy , there exists a local isometery and ancillary state , such that
| (3) |
for all , , , , where is a purification of .
We define the shifted Bell operator as , and we say admits a sum-of-squares (SOS) decomposition if there exists a set of polynomials, , of the operators , satisfying
| (4) |
SOS decompositions can be used to enforce algebraic constraints on any quantum state , and measurements , satisfying . For example, when is pure, it must satisfy
| (5) |
(or more generally). Typically, we find that constraints of the form in Eq.˜5 are only satisfied by a unique state (up to local isometeries), and when that is the case we call Eq.˜5 the self-testing criteria.
2.4 DI randomness certification
We use the conditional von Neumann entropy, to measure the DI randomness generation rate. This is the correct quantity for spot-checking DI random number generation, where is a specified measurement choice used to generate randomness (see [45] for a discussion of this and other possibilities). The asymptotic rate of DI randomness generation is given by
| (6) |
and we require lower bounds on this quantity over states and measurements compatible with the observed statistics, , or linear functions of them, such as the value of some Bell expression. We will typically only consider one functional, , which will be a Bell inequality with observed value ; then we denote the infimum in Eq.˜6 as the function . The asymptotic rate can be used as a basis for rates with finite statistics using tools such as the entropy accumulation theorem [46, 47, 48].
Because we study fundamental limits on certifiable DI randomness we work in the noiseless scenario, using self-testing statements to certify DI randomness. Here, is a Bell expression, and we show all states and measurements that achieve its maximum violation correspond to a post-measurement state in tensor product with Eve, . This allows us to directly evaluate the conditional entropy , and the infimum becomes trivial since all compatible strategies give rise to the same classical distribution (see Appendix A.3 for details).
3 Expanding Bell inequalities
In this section we discuss and enhance the technique presented in [35], which allows us to derive the main results of this work. Ref. [35] introduced a method for building multi-partite Bell inequalities by expanding a bipartite inequality, called the “seed”, which can be used to witness genuinely multi-partite nonlocality. A new Bell expression is constructed by summing the seed over different subsets of parties, whilst the remaining parties perform some fixed measurement. The more multi-partite nonlocal the correlations, the more bipartite terms are violated. This resembles other recent results that enable multi-partite self-testing by projections onto bipartite subsystems [38, 36, 37].
In this work we extend this technique to make it suitable for DI cryptographic purposes. More precisely, we consider cases where the seed is a bipartite self-test, and use the maximum quantum violation of the expanded Bell expression, constructed in an equivalent manner to [35], to draw conclusions about the post-measurement state held between the honest parties and Eve. These conclusions allow us to derive rates for randomness certification.
3.1 Definition
We begin by introducing a generic formulation for expanding Bell expressions, shortly followed by an example.
Definition 2 (Expanded Bell expressions).
Let be an nonzero matrix with entries satisfying if , and otherwise. For each pair for which , let denote a set of bipartite Bell expressions between parties and , where indexes over the measurement outcomes of all parties excluding , and each Bell inequality is equivalent up to output relabellings, with a local bound strictly less than the maximum quantum value . Then the expanded Bell operator from the seed is defined as
| (7) |
where is the projector for all parties excluding and , corresponding to the joint setting and joint outcome 111We have written the Bell operator in Eq. 7 in terms of projectors, which is convenient since we consider quantum strategies. We can however rewrite it in a theory independent way, by taking the expectation value and making the substitution . .
Consider the following tripartite example. To ease notation we label the observables of the three parties and similarly for and . From reference [23], observing saturation of the following Bell expression certifies 2 bits of global randomness,
| (8) |
where . The bound is uniquely achieved, up to local isometeries, by the bipartite strategy
| (9) |
Now consider a tripartite extension of the above strategy,
| (10) |
One can verify that when all three parties measure , their outcomes are uniformly distributed, resulting in 3 bits of raw randomness; how can we certify this device-independently? Notice has the following property: when a single party, say , measures , the leftover state held by is where the sign depends on the parity of ’s measurement outcome . Parties and can now saturate one of the bounds conditioned on ’s measurement. By using as the seed, and choosing the matrix with party indices ,
| (11) |
we can construct the expanded Bell expression according to Footnote˜1:
| (12) |
Due to the properties of discussed above, we find is the maximum quantum value of , and achieved by the strategy in Eq.˜10. Moreover, it can be shown that this is strictly greater than the maximum local value of , implying is a nontrivial Bell functional. In later sections, we will prove that is a sufficient condition for certifying maximum randomness.
Returning to the general form of from Eq.˜7, we call an expanded Bell expression, since it is built by combining a bipartite seed, , conditioned on fixed measurement settings and outcomes for the remaining parties. We then sum over all possible outcomes of this party measurement, changing the Bell expression accordingly, and over different combinations of parties chosen according to . There needs to be a gap between the local and quantum bounds of for to define a nontrivial Bell inequality; typically, we find the following upper bound is achievable, which is strictly greater than the local bound:
Lemma 1.
Let be an expanded Bell expression according to Footnote˜1. The maximum quantum value of is upper bounded by .
A proof of Lemma˜1 is given in Section˜A.1. If achievable, the only strategy that can give is the one satisfying for all pairing combinations with , i.e., the reduced state held between parties and , following the projection on the global state, must achieve the maximum quantum value of . This explains why we must include a dependence on for the Bell expression, since it should be tailored to the bipartite state following the outcome . For simplicity we assume each bipartite state is equivalent up to local unitaries, meaning we effectively use a single seed . In principle however, one could use different seeds depending on the value of , which tailors the construction to non-symmetric states [35]. For our work we only consider the symmetric case. Additionally, one could further generalize by choosing specific measurement choices dependent on the choice of non-projecting parties , instead of fixing as we have done here.
3.2 Expanding Bell expressions and entropy evaluation
Next we present the characteristic of expanded Bell expressions that allows us to certify DI randomness from witnessing its maximum quantum value, forming the main technical contribution of our work.
Lemma 2 (Decoupling lemma).
Let be an expanded -party Bell expression defined in Footnote˜1 with binary inputs and outputs, and if and zero otherwise. Suppose for every , there exists an SOS decomposition that self-tests the same pure bipartite entangled state between parties and , along with some ideal measurements , according to Eq.˜3, satisfying for all . Then for any strategy that achieves , the post-measurement state , for measurement settings , admits the tensor product decomposition,
| (13) |
Having established that Eve is decoupled it is then straightforward to evaluate the rate in Eq.˜6 conditioned on observing the maximum quantum value of .
Lemma 3.
The proof can be found in Section˜A.3. Eq.˜13 allows one to relate observing the maximum quantum value of the expanded Bell expression , to a condition on the post-measurement state held by the parties and Eve, namely that it must be in tensor product with the purifying system . This allows one to directly evaluate the conditional entropy according to Lemma˜3.
4 Certifying bits of DI randomness
We now consider constructions for generating bits of DI randomness. As previously mentioned, when is odd the MABK family can be used [31]. For an arbitrary number of parties, we apply the previously outlined techniques to derive a suitable Bell expression for this task. This will involve generalizing a one parameter family of quantum strategies, symmetric under permutation of the parties.
4.1 odd
Using symmetry arguments, the authors of Ref. [31] showed that maximum violation of the MABK inequality, for odd, implies maximum randomness.
Proposition 1 (Maximum randomness for odd [31]).
When is odd, maximum quantum violation of the MABK family of Bell inequalities, given by Eq.˜1, certifies bits of global DI randomness, i.e.
| (15) |
From a self-testing point of view, maximum violation of the MABK family can only be achieved with a GHZ state and maximally anticommuting observables [43, 44]. For the form given in Eq.˜1, recall the following strategy achieves maximum violation:
| (16) |
with , and satisfies for each . Following this self-testing property, the infimum in Eq.˜15 reduces to a single point up to symmetries, and the fact that the parties hold a pure state implies Eve must be uncorrelated, i.e., . By direct calculation, one can verify for , , , hence . Similarly for , , , implying .
As an example, taking in the above construction we have , and the strategy in Eq.˜16 reaches the algebraic bound of . We therefore have that implies bits of randomness when all three parties use measurement . On the other hand, the correlators in the inequality must take the values to reach the algebraic bound, so no string of inputs which appears as a correlator in the inequality can generate more than 2 bits of global randomness (in fact they give exactly 2 bits when ).
4.2 even
When is even, all combinations appear in , and all must have non-zero weight to achieve the largest possible quantum value. This is incompatible with maximum randomness from one input combination. Hence, achieving the quantum bound does not certify maximum randomness; by direct calculation, maximum MABK violation certifies bits of global DI randomness when all parties use measurement 0.
We now proceed to construct new Bell expressions which certify bits of randomness in the even case. Specifically, we use the techniques introduced in Section˜3 to generalize the case, which was addressed in [23].
4.2.1 Bipartite self-tests
To begin with, we summarize the results obtained for the case.
Lemma 4 ( family of self-tests).
Define the set 222Note that .. Let , and define the family of Bell expressions parameterized by , for parties ,
| (17) |
Then we have the following:
-
(i)
The local bounds are given by , where
(18) -
(ii)
The quantum bounds are given by , where .
-
(iii)
Up to local isometries, there exists a unique strategy that achieves :
(19)
The above lemma is a rewriting of Proposition 1 in [23], and can be recovered as a special case of Lemma˜8 to follow. Importantly, the self-testing property implies that when their inputs are 0, both parties measure on , which results in 2 bits of randomness, . We also remark that the state with the same measurements achieves . This is a symmetry of the case above, since relabeling the measurement outcomes of party yields the new Bell expression . Therefore implies , which self-tests and the negated measurements, or equivalently and the original measurements.
4.2.2 Target strategy
For the partite case, we generalize the above bipartite strategy:
| (20) |
where is a free parameter. As before, we find , hence this is a target strategy for certifying bits of global randomness. Our objective now will be to design a tailored Bell inequality that can certify bits by witnessing its maximum value, attained by the strategy in Eq.˜20.
4.2.3 Constructing an -partite Bell inequality
We use the techniques introduced in Section˜3 to construct the desired Bell expression by expanding the seed . Studying the strategy in Eq.˜20, we notice that when parties perform their first measurement, , depending on the outcome parity the post-measurement state for the remaining parties is . Now, performing the measurements in Eq.˜20 on that post-measurement state achieves , which, according to the self-testing properties of , will certify 2 bits of randomness. Since the strategy is symmetric under party permutations, we can repeat this argument over different subsets of parties, and conclude that, when every bipartite self-test is satisfied, the output setting must generate uniform DI randomness. The corresponding Bell inequality is constructed according to the following lemma.
Lemma 5 (Bell inequality for maximum randomness).
Let be a tuple of measurement outcomes for all parties excluding , and be the parity of . Let and be a set of bipartite Bell expressions between parties , where
| (21) |
Then the expanded Bell expression given by
| (22) |
has quantum bounds where . Moreover, is achieved up to relabelings by the strategy in Eq.˜20, and cannot be achieved classically.
The proof can be found in Section˜B.1.
We can now state our first main result:
Proposition 2 (Maximum randomness certification).
Achieving the maximum quantum value of the Bell inequality in Lemma˜5 certifies bits of global randomness, i.e.,
| (23) |
4.3 MABK value and maximum randomness
Above we gave a new one parameter construction for certifying bits of device-independent randomness in any -party 2-input 2-output scenario. Now we will study some properties of the correlations used to certify maximum randomness. In particular we’re interested in how maximal randomness and nonlocality tradeoff against each other. For instance, how nonlocal can correlations be whilst certifying maximal randomness?
4.3.1 Achievable MABK values with maximum randomness
When is odd, we have discussed that one can always certify bits of DI randomness from maximum MABK violation; for the even case, it is unclear how large the MABK value can be whilst certifying maximum randomness. Using the fact that, for the strategy in Eq.˜20, , where , its MABK value is given by333This can be established using the identities and .
| (24) |
We begin with the following proposition:
Proposition 3.
For even , let
| (25) |
where is the element of the sequence given by
| (26) |
Then .
Proof can be found in Section˜B.2. Using this result, we are able to prove the following. It will be convenient to define
| (27) |
Proposition 4.
Let be an even integer. For every MABK value in the range , there exists a that satisfies .
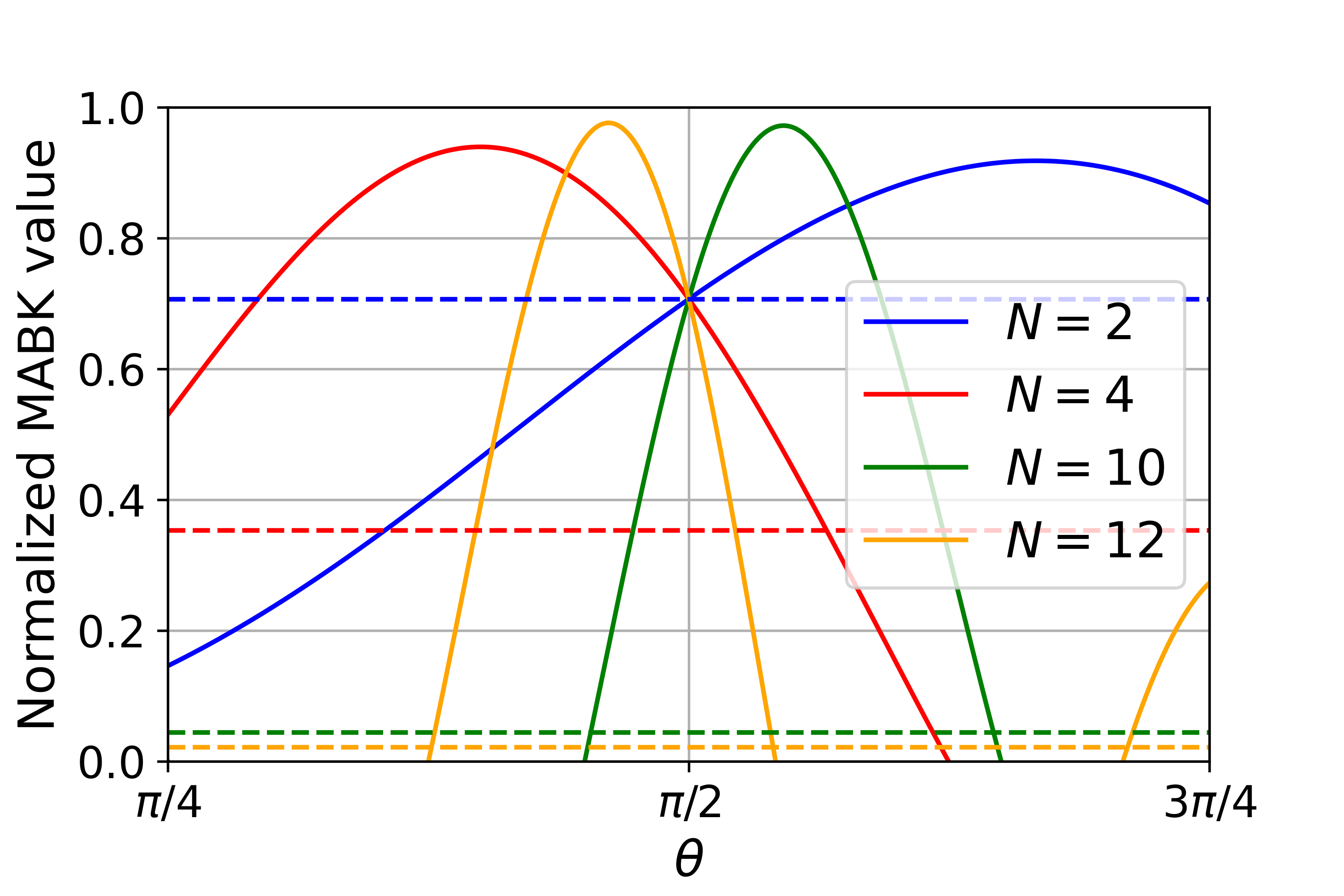
The proof of Proposition 4 can be found in Section˜B.3. In Fig.˜1, we plot the MABK value for a given as a function of , showing the full range of violations is accessible. Specifically, the dashed lines in Fig.˜1 indicate an MABK value of 1, while the peak of each graph is . As varies, the graph shows a continuous curve between these values. We next state the following technical conjecture, which holds in the case and we provide evidence for general in Appendix B.10.
Conjecture 1.
The maximum MABK value achievable by quantum strategies with uniformly random outputs on input , i.e., , is .
Fig.˜1 illustrates that is the largest MABK value that can be achieved by the family of strategies in Eq.˜20, all of which generate maximum randomness. However, we have not ruled out the existence of a strategy outside this family, also generating maximum randomness, achieving an MABK value greater than . ˜1 is that this is not the case, and is indeed the true maximum. Based on this, we can now state the range of MABK violations for which maximum DI randomness can be certified when is even.
Lemma 6 (MABK violations achievable with maximum DI randomness, even case).
For even , we have:
-
(i)
The maximum amount of device-independent randomness that can be certified for the range of MABK values is bits.
Suppose ˜1 holds. Then we additionally have:
-
(ii)
is the largest MABK value compatible with strategies generating bits of device-independent randomness.
Part can be established by the following reasoning: by varying , the family of strategies in Eq.˜20 achieves every MABK value in the interval by Proposition˜4. Since for all these values, the corresponding bipartite strategy is self-testable according to Lemma˜4; we can hence apply Lemma˜5 to expand the Bell expression to parties, and it follows from Lemma˜3 that this Bell expression certifies bits of DI randomness.
An implication of Proposition˜3 is that the MABK value becomes an achievable lower bound on the maximum MABK value for quantum correlations certifying maximum randomness. This follows from the same reasoning outlined in the previous paragraph, since implies maximum DI randomness can be certified from the correlations generated by the associated strategy in Eq.˜20. Part (ii) of Lemma 6 is that this is optimal (if ˜1 holds), in the sense that one cannot achieve a larger MABK value whilst simultaneously certifying maximum randomness. As evidence we derive a numerical technique that can generate upper bounds on this MABK value, and show these upper bounds match the lower bounds for some values . See Section˜B.4 for the details. We also remark that ˜1 is known to hold for the case [23].
We now consider the case of odd MABK expressions.
Proposition 5.
Let be an odd integer. For every MABK value in the range , there exists a that satisfies .
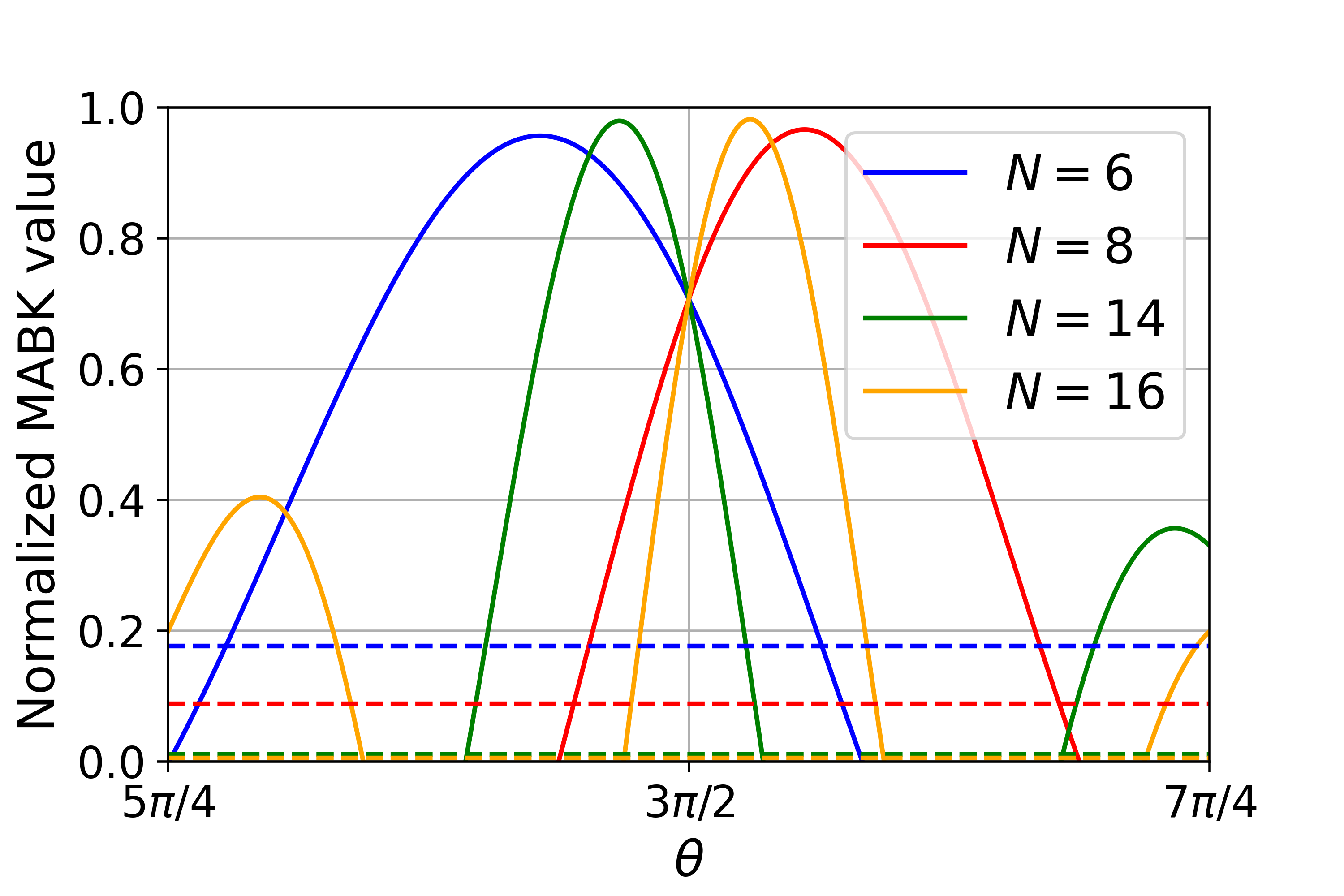
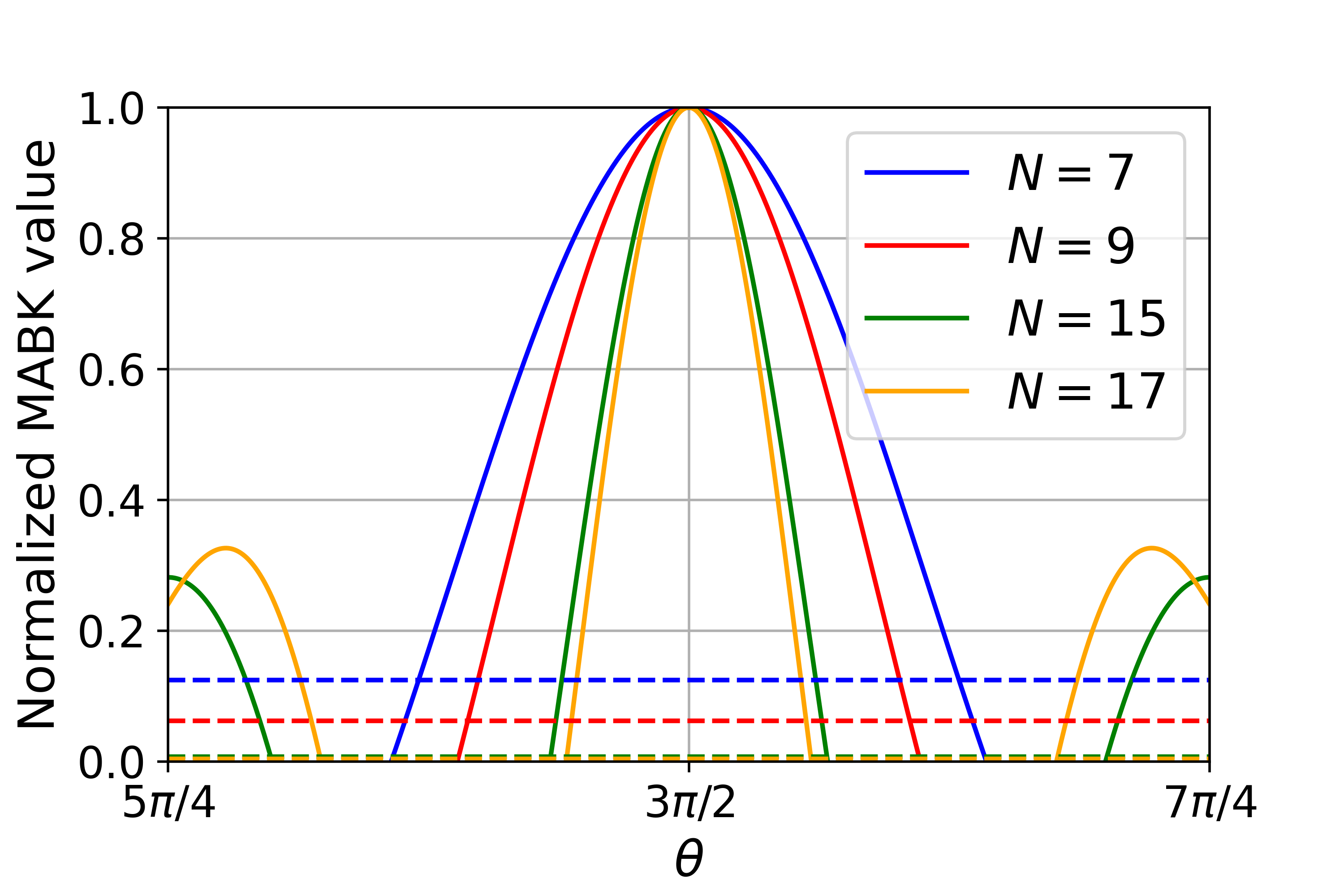
Poof can be found in Section˜B.3. Similar to the even case, in Fig.˜2 we plot the MABK value as a function of for different , and see that all quantum achievable values can be obtained by Eq.˜20 for some . We then have the following consequence:
Lemma 7 (MABK violations achievable with maximum DI randomness, odd case).
For odd the maximum amount of device-independent randomness that can be certified for the range of MABK values is bits.
The above lemma asserts that when is odd, for all quantum-achievable MABK values maximum randomness can be realized simultaneously. For the case of , i.e., the maximum quantum value, randomness can be certified according to Eq.˜15. For all other MABK values, Proposition˜5 implies maximum randomness can be certified by for some .
We remark on the nontrivial maximal MABK violation compatible with maximum randomness when is even, contrasting the odd case; as discussed in Section˜4.1, this can be seen as a consequence MABK expressions for even containing every party correlator. When maximum randomness is being certified, one of these correlators must be zero, which restricts the maximum MABK violation to be strictly less than the optimal quantum value.
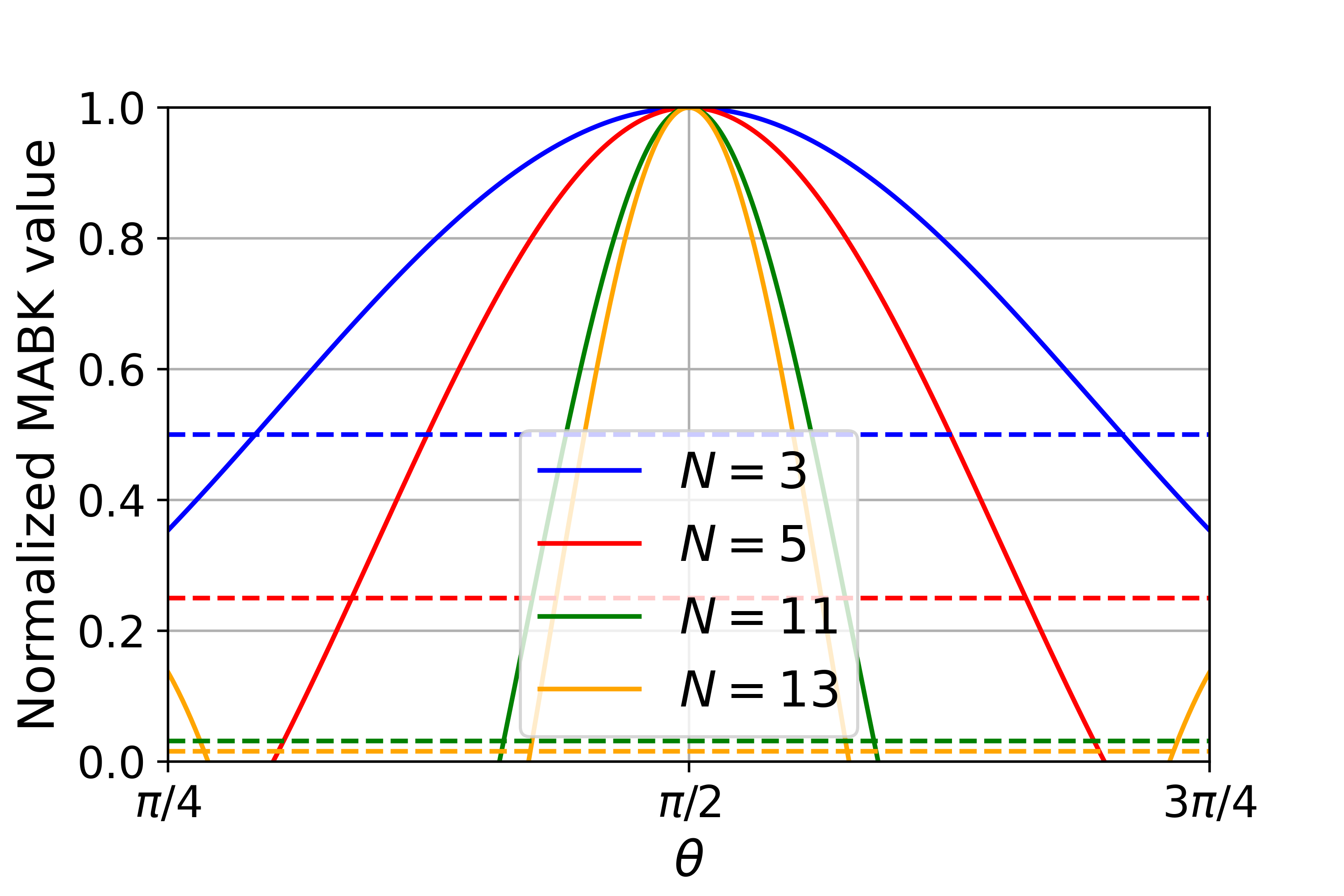
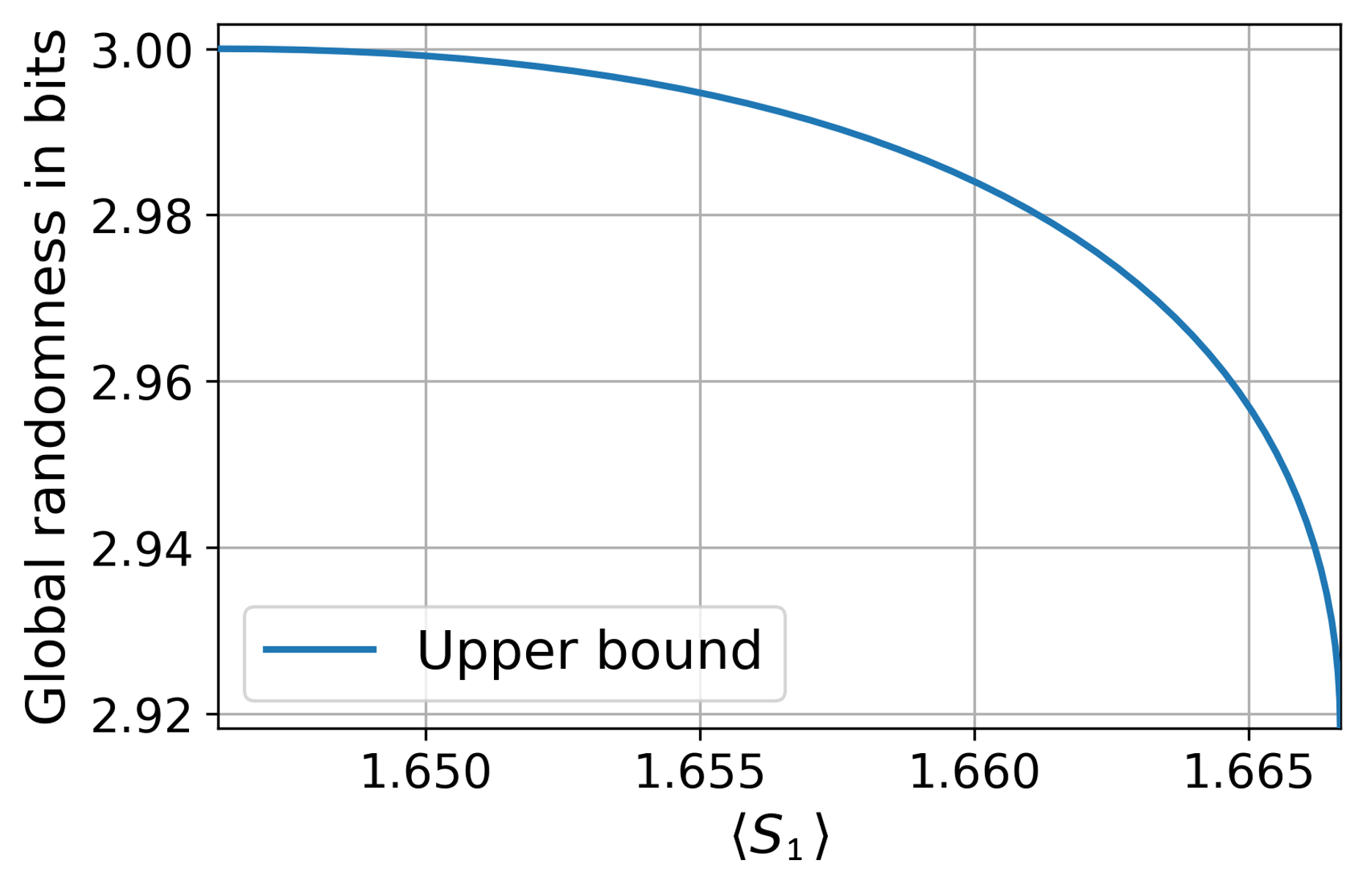
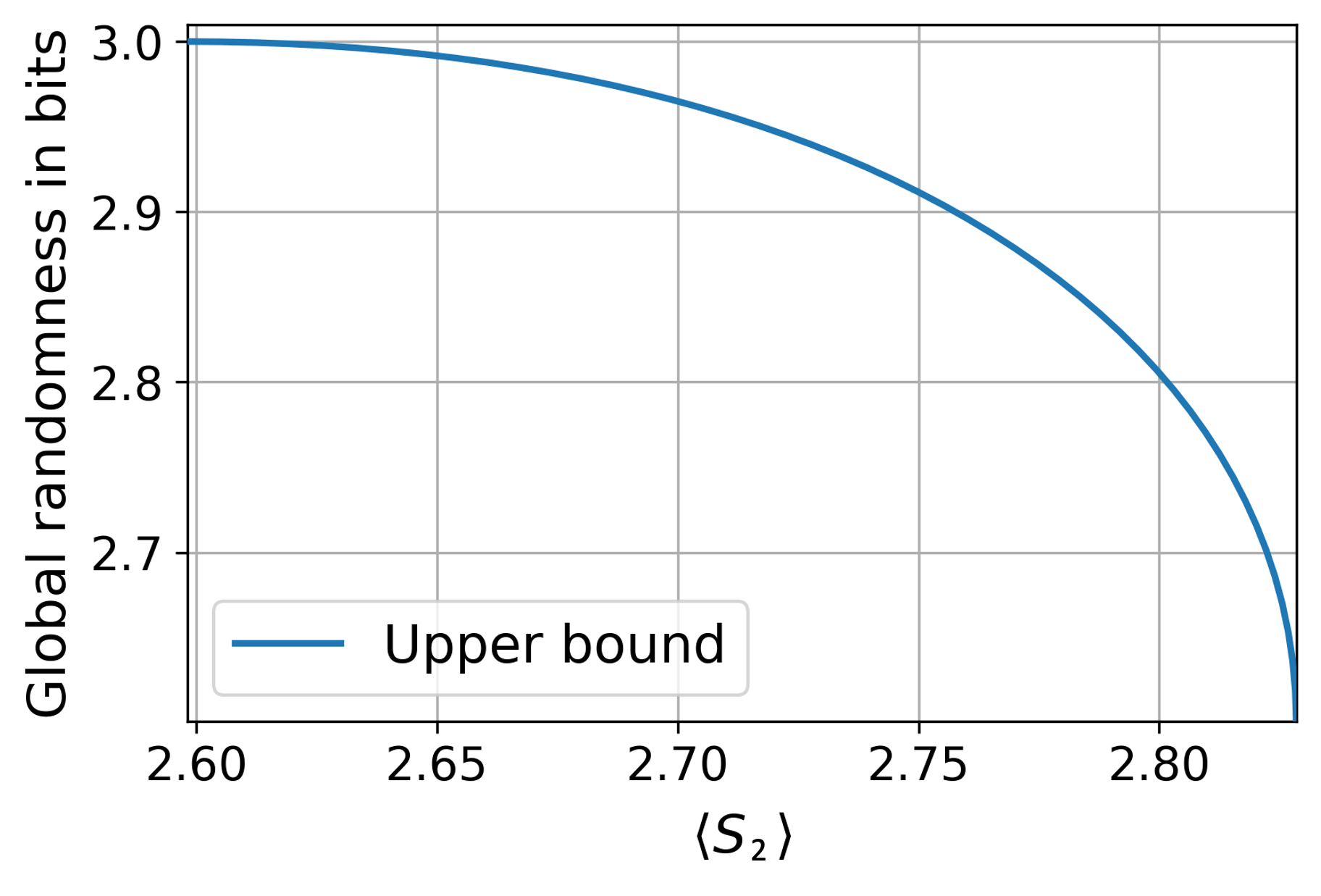
4.3.2 Asymptotic behaviour
We now consider the behaviour of the conjectured maximal MABK value achievable with maximum randomness, , for increasingly large even . We show that converges to the largest possible quantum value in this limit. Note this is not based on a conjecture; is an achievable lower bound, and in the following proposition we show this lower bound tends towards the global upper bound, namely the maximal quantum MABK value.
Proposition 6 (Maximum randomness in the asymptotic limit).
In the limit of large even , one can achieve arbitrarily close to the maximum quantum violation of the party MABK inequality, , whilst certifying maximum device-independent randomness.
This is proven in Section˜B.5.
4.3.3 Nonlocality and maximum randomness
Whilst we have studied the MABK values achieved by the strategies in Eq.˜20, we also consider how nonlocal they are, quantified by how much the local set needs to be “diluted” to contain them. We refer to this measure as the local dilution, which can be computed via a linear program for small , and we give details in Section˜B.6. Our findings are presented in Fig.˜3.
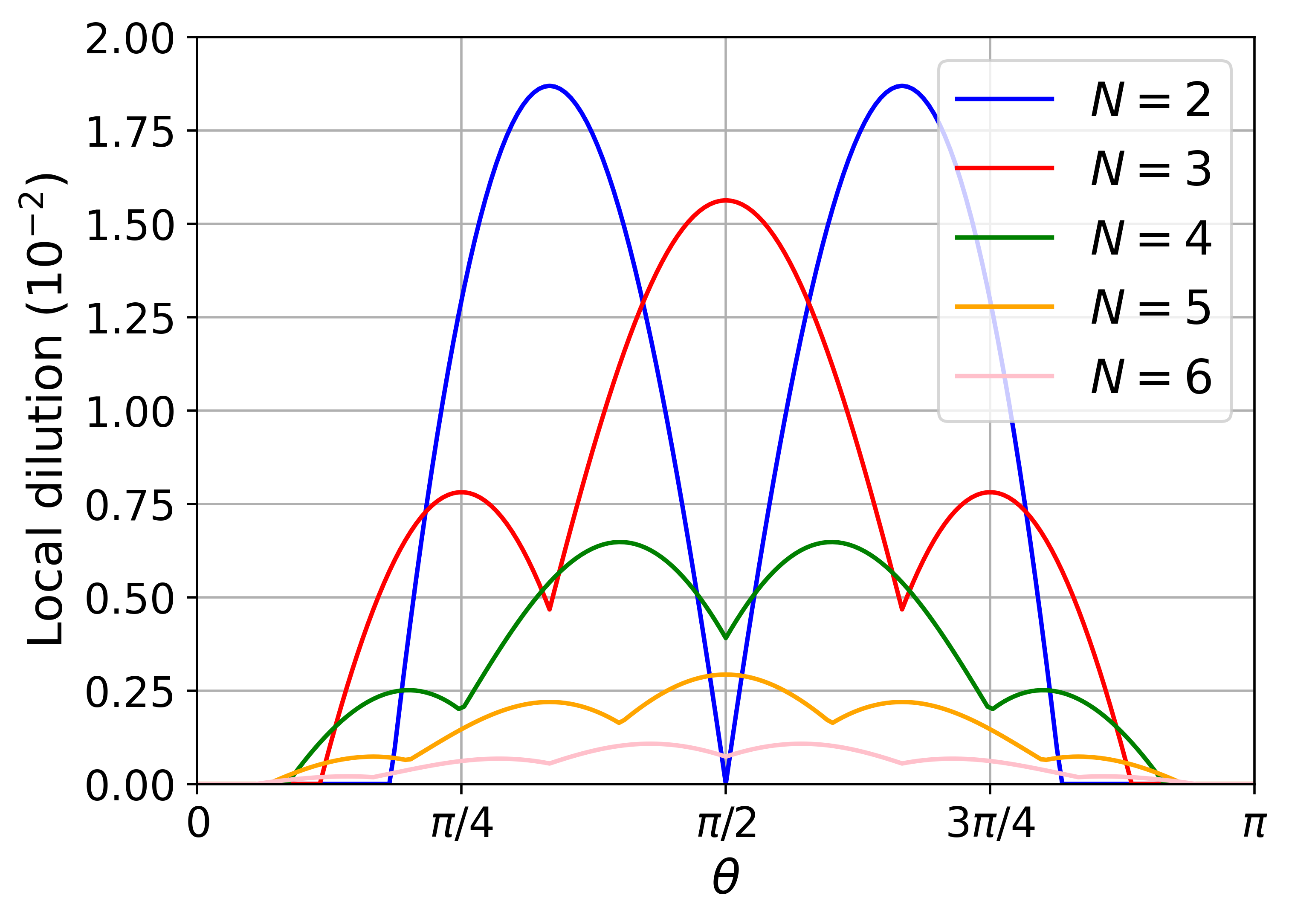
Interestingly, for the correlations of the strategy in Eq.˜20 are bounded away from the local boundary for any , even for small MABK violation; whilst the violation of a given MABK inequality can be made arbitrarily small, the correlations are still distant from the local boundary. In fact, by comparing Fig.˜3 with Fig.˜1 and Fig.˜2, one can see how correlations achieving at or below the maximum local MABK value, , can still be nonlocal and certify maximum randomness. To illustrate this point, consider the (blue) curve in Fig.˜2. Provided , bits of DI randomness can be certified following previous arguments. However, the blue dashed line in Fig.˜2, indicating the local bound (), intersects the solid curve inside the region , implying the corresponding strategy in Eq.˜20 achieves while simultaneously certifying maximum randomness. This is explained by the (red) curve in Fig.˜3, where it can be seen that in the closed region the correlations are nonlocal and hence must violate some other Bell inequality. This illustrates the complexity of the tradeoff between randomness versus nonlocality in the multi-partite scenario.
5 Trade-off between DI randomness and MABK violation
In this section, we present an achievable lower bound on the maximum device-independent randomness that can be generated by correlations achieving any given MABK violation. Moreover, we conjecture this lower bound to be tight based on numerical evidence. This is achieved by introducing a new family of two parameter quantum strategies along with their self-testing Bell expressions. Using this as the seed, we construct a multi-partite Bell expression which certifies their randomness.
5.1 Constructing the Bell expression
5.1.1 Bipartite self-tests
We begin by introducing a versatile family of bipartite self-tests which generalize the results in [23].
Lemma 8 ( family of self-tests).
Let such that and 444The reason for this condition is explained in Section B.7.. Define the family of Bell expressions parameterized by and ,
| (28) |
Then we have the following:
-
(i)
The local bounds are given by , where
(29) -
(ii)
The quantum bounds are given by , where .
-
(iii)
.
-
(iv)
Up to local isometries, there exists a unique strategy that achieves :
(30)
Note that when Lemma˜8 reduces to Lemma˜4. Moreover, this Bell expression retains the same symmetry properties of the family, namely that for the state and the same measurements, and is hence a self-test. Lemma˜8 can be obtained as a corollary of the self-testing results from Refs [49, 50, 51] (see Section˜B.7 for details).
For future convenience, we define the set . One can verify that points satisfy and , and therefore define a valid self-test according to Lemma˜8.
5.1.2 Target strategy
For the -partite case, we will consider the following strategy:
| (31) |
Using the fact that , where , the MABK value, defined in Eq.˜1, of the above strategy is given by
| (32) |
5.1.3 Constructing an -partite Bell inequality
Using the previous two building blocks, we construct the following Bell inequality using the expressions as the seed.
Lemma 9.
Let be a tuple of measurement outcomes for all parties excluding , and be the parity of . Let ,
| (33) |
and
| (34) |
Define the following Bell polynomial
| (35) |
If , is an expanded Bell expression, and has quantum bounds where , which can be achieved up to relabelings by the strategy
| (36) |
In addition, this quantum bound cannot be achieved classically.
The proof is given in Section˜B.8. Note that the Bell expressions (35) are written in terms of the shifted parameters , instead of the measurement angles . This is because the parties performing the projection no longer use , but use . This accumulates a phase factor on the state of the remaining parties, , which is equivalent to the action of some local unitary on . To correct for this, we use the Bell expression as the seed. See Section˜B.8 for the full details.
5.2 Randomness versus MABK value
Using the previously derived Bell inequality, we consider the trade-off between maximum device-independent randomness and MABK violation. Let us define
| (37) |
where is defined in Eq.˜25 and let
| (38) |
For the strategy in Eq.˜31, direct calculation yields
| (39) |
and . Hence by varying 555To ease notation, we write when and , interpreting the latter case as . and choosing one can obtain the desired range of MABK values , from the conjectured maximum MABK value with maximum randomness to the maximum quantum value. Choosing this parameterization, the raw randomness, , of the strategy in Eq.˜31 (with ), as a function of , is given by
| (40) |
where is the binary entropy function and is a smooth, monotonically decreasing function of in the range .
As shown in Section˜4 (by combining Lemma˜5 with Proposition˜3), when we can certify maximum DI randomness. It also follows from the self-testing properties of the MABK family that when we obtain bits of global DI randomness when all parties use measurement 0. What remains then, is to apply the new Bell expression constructed in Lemma˜9 to certify bits of DI randomness for . To do so, the following proposition shows that for every , there exists a valid Bell expression given by Lemma˜9.
This is proven in Section˜B.9. Proposition˜7 implies that, for every in the range we are interested in, the bipartite expression is a valid self-test of the strategy
| (41) | ||||
After applying the local unitary , where , this is equivalent to
| (42) | ||||
which is exactly the bipartite strategy we wanted to self-test, since it is the one held by parties and after the projector is applied to the global state . As a result, the correlations generated by the strategy in Eq.˜31, by choosing and varying , maximally violate the Bell inequality with and given in Eq.˜33. We can therefore employ the decoupling lemma to make the rate unconditioned on Eve, , device-independent.
Proposition 8.
Achieving the maximum quantum value of the Bell inequality in Lemma˜9 certifies bits of randomness, i.e.,
| (43) |
We have established that, for every MABK value , there exists a which defines a quantum strategy achieving , for which its generated randomness is device-independent. We have therefore related every MABK value with a DI rate. We now conjecture the curve is optimal in terms of raw randomness, which can then be made device-independent following the above discussion — see Lemma˜10.
Conjecture 2.
For even, the maximum randomness unconditioned on Eve, , that can be generated by quantum strategies achieving an MABK value, , is given by
| (44) |
where is defined in Eq.˜40, and
| (45) |
For the range , and , the rate and MABK value is achieved by the family of quantum strategies in Eq.˜20 and Eq.˜31, and certified device-independently by the Bell expressions in Lemma˜5 and Lemma˜9, respectively. Similarly to ˜1, Eq.˜45 is known to hold for the case [23].
The minimization in the definition of is included since we have not shown the set is unique. Intuitively, the closer is to zero the closer we are to maximum randomness; hence we expect to be monotonically decreasing with for , and minimization guarantees the best rate at a given . For the examples we have computed, the minimization turns out to be trivial, i.e., is the unique solution to .
Lemma 10.
The above lemma tells us that if the rate in Eq.˜44 is optimal without conditioning on Eve, it will also be optimal conditioned on Eve, i.e., the rate can be made device-independent. This is because Propositions˜3 and 7 ensure that, for every MABK value, the corresponding quantum strategy achieving it, given in Eq.˜20 or Eq.˜31, can generate certifiable randomness using the corresponding Bell expression or . A rewriting of Lemma˜10 without Conjecture 45, would say that (44) corresponds to a guaranteed lower bound on the maximum DI randomness as a function of MABK value. Our results are summarized in Fig.˜4.
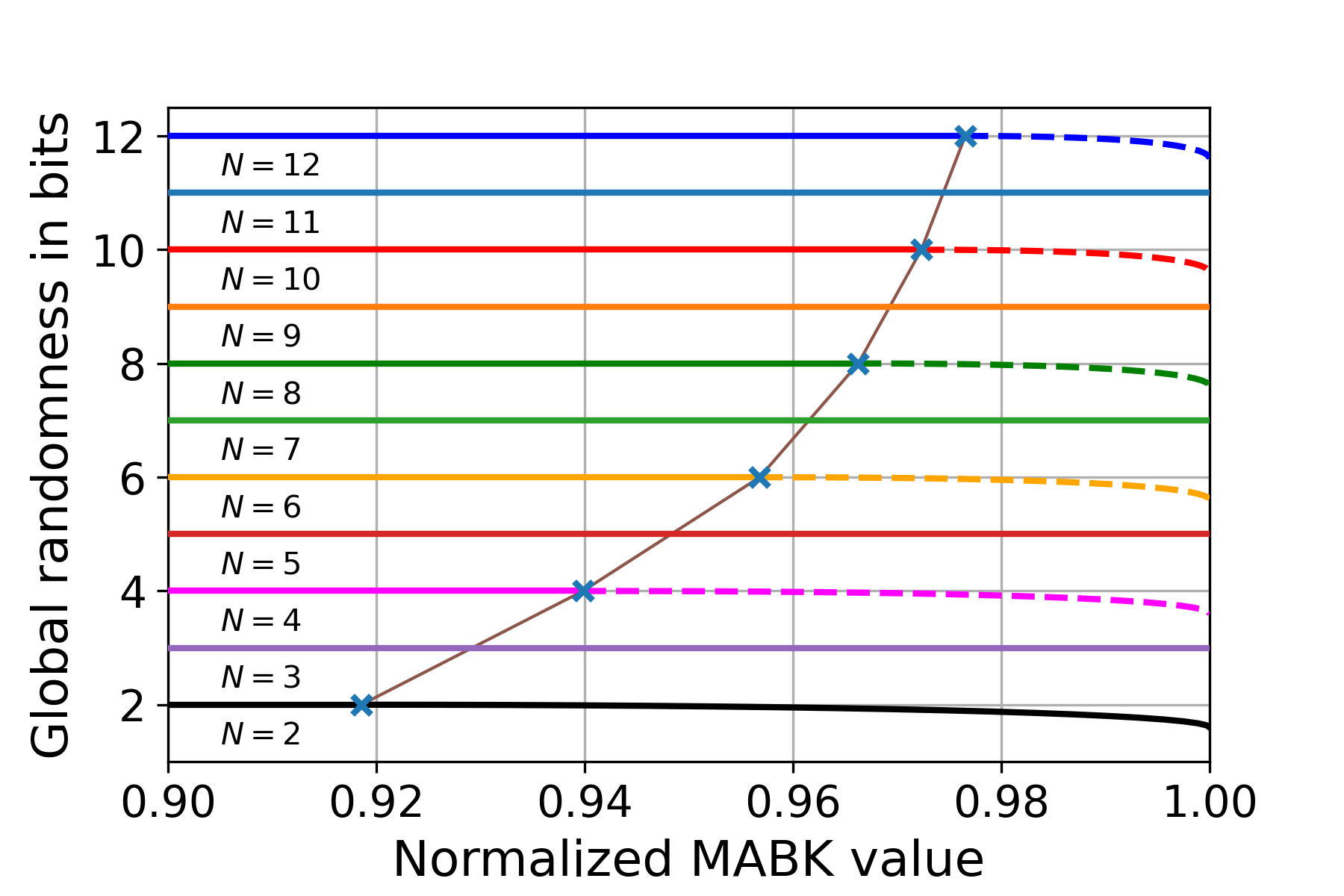
We provide evidence for Conjectures 1 and 45 in Section˜B.10, where we derive a numerical technique for upper bounding the maximum randomness that can be generated by quantum strategies achieving a given MABK value . By studying the numerical results, we find our analytical lower bound closely agrees with the numerical upper bound.
5.3 Other extremal Bell inequalities
In the -partite 2-input 2-output scenario, the MABK family is just one class of extremal Bell inequalities, and the techniques developed in this section can be readily applied to others. For example, when and restricting to Bell inequalities containing only three party correlators, there are a total of 3 non-trivial, new classes, one being the MABK inequality , and two being of the form [41]
| (46) | ||||
| (47) |
where we used for , for etc. for legibility. and have local bounds of and , and maximum quantum values and , respectively. We applied our numerical technique (see Section˜B.10) to find upper bounds on the maximum amount of randomness certifiable whilst achieving a given violation of and . A comparison can be found in Fig.˜5, and we provide additional figures and details in Section˜B.11.
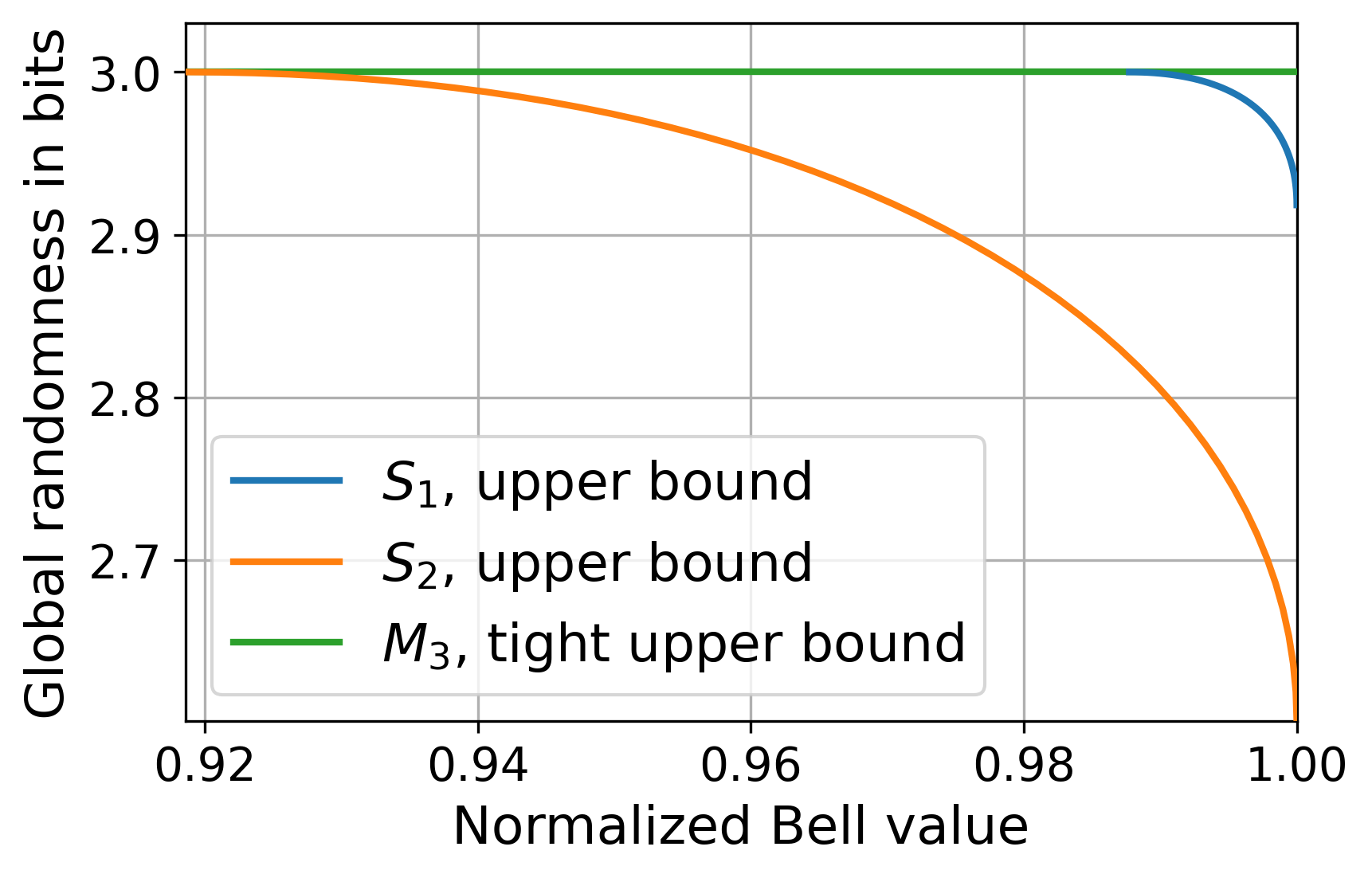
We find both and exhibit a trade-off for violations close to the quantum maximum. Due to its structure, exhibits identical trade-off characteristics to the CHSH inequality found in [23], with the maximum CHSH value achievable with maximum randomness being numerically close to . On the other hand, we find more randomness can be generated from maximum violation of , which is still strictly less than the maximum certified by MABK. Exact values are given in Section˜B.11.
6 Discussion
In this work, we studied how MABK violation constrains the generation of global DI randomness for an arbitrary number of parties. Whilst there is no trade-off in the odd case, we conjectured the precise trade-off for the even case. This conjecture is supported by an analytical lower bound and a numerical upper bound that agree up to several decimal places and have been checked for up to . We additionally showed that, in the asymptotic limit, this trade-off vanishes. Our main technical contribution was the extension of a recent tool, originally introduced to witness genuinely multi-partite nonlocality, to randomness certification.
The difference between the odd and even cases is explained by the odd MABK expressions containing half the full party correlators, allowing for input combinations not included in the Bell expression to be uniform. For even , all correlators are included and must be non-zero to obtain maximum violation, resulting in a trade-off between randomness and MABK value. The number of correlators is , whereas the quantum bound is . Maximum violation is achieved when the product of all correlators and their MABK coefficients have the same value, which in this case will be . Hence we find the penalty for fixing one correlator to zero (which is necessary for maximum randomness) diminishes as grows, and vanishes in the asymptotic limit.
We also quantified the nonlocality (measured using the dilution) of our constructions for low values of , calculated via a linear program. Interestingly we found our correlations are always separated from the local boundary (except for the case ). It would be interesting to find correlations that lie arbitrarily close to the local boundary whilst still certifying maximum randomness, as was found in the case [22, 23]. This could entail breaking the symmetry between the second measurements of each party, and the techniques presented here can be applied. Moreover, one could hope to go further and bound the trade-off between randomness and nonlocality in this setting; however, the challenge becomes finding a suitable measure of nonlocality that is efficient to work with. Specifically, for the case , constraining the amount of nonlocality of a quantum correlation is equivalent to constraining its CHSH value, which is linear in the correlators. When used as a constraint for maximizing randomness, this can then be handled using the techniques presented in Section˜B.10.1, which rely on the Navascués-Pironio-Acín hierarchy [52, 53]. For , the dilution measure is calculated via a linear program, therefore requiring a different approach.
We hope that the results found here will inform future experiments in DIRE; initial works have already made progress in this direction [54]. In such experiments, one should consider the optimal protocol for DIRE. In this work, we have proposed protocols that rely on spot-checking [7, 8, 45], where randomness is generated by a single input combination. An alternative approach has been explored in reference [45], where it was found that generating randomness from all inputs and averaging the result boosts the rate when the CHSH inequality is used. In the case of maximally violating a self-testing Bell inequality, spot-checking will always be optimal when a specific input combination leads to maximum randomness; having one maximally random setting necessarily implies that at least one other setting combination will not be maximally random for the correlations to be nonlocal, hence averaging will only decrease the overall rate. The noisy case remains an open question however, and the trade-off between using spot-checking and weighted averaging for our constructions deserves future investigation, with the aim of further improving practical rates.
Another interesting direction for future research is to connect expanded Bell inequalities to multi-partite self-testing. Our decoupling result allows the structure of the post-measurement state to be certified following the maximum violation of an expanded Bell expression; the open question we pose is whether an expanded Bell inequality can constitute a self-test of the -party state, opening up a new range of useful applications beyond randomness certification. Intuitively, if each pair of parties can self-test all of their measurements along with a projected state, the marginal information could be sufficient to make a statement about the global state. Such a strategy has already been adopted for self-testing certain multi-partite strategies [36]. However, there are subtleties to consider. For example, expanded Bell expressions tailored to some quantum strategies can result in trivial inequalities (i.e., ones that exhibit no classical-quantum gap), despite the underlying strategy being nonlocal, and furthermore self-testable. We therefore believe an additional ingredient is needed to self-test generic multi-partite states using the techniques in this work.
Finally, whilst we studied the MABK family of inequalities, one could consider a similar analysis for other families of extremal multi-partite Bell expressions [41]. For example, we explored upper bounds on the trade-offs for all extremal inequalities when , and found the MABK inequality to be optimal for global randomness; it would be interesting to find out if the upper bounds presented for the other inequalities are achievable. One might try to find explicit constructions that match these bounds, and use our techniques to make them device-independent. Analysing other extremal inequalities will build a more complete picture of how DI randomness can be generated in the multi-partite scenario, better informing the way forward for future multi-partite experiments.
Acknowledgements
This work was supported by the UK’s Engineering and Physical Sciences Research Council (EPSRC) via the Quantum Communications Hub (Grant No. EP/T001011/1) and Grant No. EP/SO23607/1.
References
- [1] J. S. Bell. “Speakable and unspeakable in quantum mechanics”. Cambridge University Press. (1987).
- [2] Nicolas Brunner, Daniel Cavalcanti, Stefano Pironio, Valerio Scarani, and Stephanie Wehner. “Bell nonlocality”. Reviews of Modern Physics 86, 419–478 (2014).
- [3] Jonathan Barrett, Noah Linden, Serge Massar, Stefano Pironio, Sandu Popescu, and David Roberts. “Nonlocal correlations as an information-theoretic resource”. Physical Review A 71, 022101 (2005).
- [4] Roger Colbeck. “Quantum and relativistic protocols for secure multi-party computation”. PhD thesis. University of Cambridge. (2007). arXiv:0911.3814.
- [5] S. Pironio, A. Acin, S. Massar, A. Boyer de la Giroday, D. N. Matsukevich, P. Maunz, S. Olmschenk, D. Hayes, L. Luo, T. A. Manning, and C. Monroe. “Random numbers certified by Bell’s theorem”. Nature 464, 1021–1024 (2010).
- [6] Roger Colbeck and Adrian Kent. “Private randomness expansion with untrusted devices”. Journal of Physics A 44, 095305 (2011).
- [7] Carl A. Miller and Yaoyun Shi. “Robust protocols for securely expanding randomness and distributing keys using untrusted quantum devices”. Proceedings of the 46th Annual ACM Symposium on Theory of Computing (STOC ’14) (New York, USA) pages 417–426 (2014).
- [8] Carl A. Miller and Yaoyun Shi. “Universal security for randomness expansion from the spot-checking protocol”. SIAM Journal of Computing 46, 1304–1335 (2017).
- [9] Roger Colbeck and Renato Renner. “Free randomness can be amplified”. Nature Physics 8, 450–454 (2012).
- [10] Artur K. Ekert. “Quantum cryptography based on Bell’s theorem”. Physical Review Letters 67, 661–663 (1991).
- [11] John Barrett, Lucien Hardy, and Adrian Kent. “No signalling and quantum key distribution”. Physical Review Letters 95, 010503 (2005).
- [12] Antonio Acin, Nicolas Brunner, Nicolas Gisin, Serge Massar, Stefano Pironio, and Valerio Scarani. “Device-independent security of quantum cryptography against collective attacks”. Physical Review Letters 98, 230501 (2007).
- [13] Stefano Pironio, Antonio Acin, Nicolas Brunner, Nicolas Gisin, Serge Massar, and Valerio Scarani. “Device-independent quantum key distribution secure against collective attacks”. New Journal of Physics 11, 045021 (2009).
- [14] Umesh Vazirani and Thomas Vidick. “Fully device-independent quantum key distribution”. Physical Review Letters 113, 140501 (2014).
- [15] Rotem Arnon-Friedman, Frédéric Dupuis, Omar Fawzi, Renato Renner, and Thomas Vidick. “Practical device-independent quantum cryptography via entropy accumulation”. Nature Communications 9, 459 (2018).
- [16] Dominic Mayers and Andrew Yao. “Self testing quantum apparatus” (2004). arXiv:quant-ph/0307205.
- [17] M. McKague, T. H. Yang, and V. Scarani. “Robust self-testing of the singlet”. Journal of Physics A: Mathematical and Theoretical 45, 455304 (2012).
- [18] Tzyh Haur Yang and Miguel Navascués. “Robust self-testing of unknown quantum systems into any entangled two-qubit states”. Physical Review A 87, 050102 (2013).
- [19] Andrea Coladangelo, Koon Tong Goh, and Valerio Scarani. “All pure bipartite entangled states can be self-tested”. Nature Communications 8, 15485 (2017).
- [20] Ivan Šupić, Joseph Bowles, Marc-Olivier Renou, Antonio Acín, and Matty J. Hoban. “Quantum networks self-test all entangled states”. Nature Physics 19, 670–675 (2023).
- [21] Ivan Šupić and Joseph Bowles. “Self-testing of quantum systems: a review”. Quantum 4, 337 (2020).
- [22] Antonio Acín, Serge Massar, and Stefano Pironio. “Randomness versus nonlocality and entanglement”. Physical Review Letters 108, 100402 (2012).
- [23] Lewis Wooltorton, Peter Brown, and Roger Colbeck. “Tight analytic bound on the trade-off between device-independent randomness and nonlocality”. Physical Review Letters 129, 150403 (2022).
- [24] N. David Mermin. “Extreme quantum entanglement in a superposition of macroscopically distinct states”. Physical Review Letters 65, 1838–1840 (1990).
- [25] M. Ardehali. “Bell inequalities with a magnitude of violation that grows exponentially with the number of particles”. Physical Review A 46, 5375–5378 (1992).
- [26] A. V. Belinskiĭ and D. N. Klyshko. “Interference of light and Bell’s theorem”. Physics-Uspekhi 36, 653 (1993).
- [27] Erik Woodhead, Boris Bourdoncle, and Antonio Acín. “Randomness versus nonlocality in the Mermin-Bell experiment with three parties”. Quantum 2, 82 (2018).
- [28] Federico Grasselli, Gláucia Murta, Hermann Kampermann, and Dagmar Bruß. “Entropy bounds for multiparty device-independent cryptography”. PRX Quantum 2, 010308 (2021).
- [29] Federico Grasselli, Gláucia Murta, Hermann Kampermann, and Dagmar Bruß. “Boosting device-independent cryptography with tripartite nonlocality”. Quantum 7, 980 (2023).
- [30] Cédric Bamps, Serge Massar, and Stefano Pironio. “Device-independent randomness generation with sublinear shared quantum resources”. Quantum 2, 86 (2018).
- [31] Chirag Dhara, Giuseppe Prettico, and Antonio Acín. “Maximal quantum randomness in Bell tests”. Physical Review A 88, 052116 (2013).
- [32] Gonzalo de la Torre, Matty J. Hoban, Chirag Dhara, Giuseppe Prettico, and Antonio Acín. “Maximally nonlocal theories cannot be maximally random”. Physical Review Letters 114, 160502 (2015).
- [33] Samuel L. Braunstein and Carlton M. Caves. “Wringing out better Bell inequalities”. Annals of Physics 202, 22–56 (1990).
- [34] I. Šupić, R. Augusiak, A. Salavrakos, and A. Acín. “Self-testing protocols based on the chained Bell inequalities”. New Journal of Physics 18, 035013 (2016).
- [35] Florian J. Curchod, Mafalda L. Almeida, and Antonio Acín. “A versatile construction of Bell inequalities for the multipartite scenario”. New Journal of Physics 21, 023016 (2019).
- [36] Ivan Šupić, A Coladangelo, R Augusiak, and A Acín. “Self-testing multipartite entangled states through projections onto two systems”. New Journal of Physics 20, 083041 (2018).
- [37] M. Zwerger, W. Dür, J.-D. Bancal, and P. Sekatski. “Device-independent detection of genuine multipartite entanglement for all pure states”. Physical Review Letters 122, 060502 (2019).
- [38] Xinhui Li, Yu Cai, Yunguang Han, Qiaoyan Wen, and Valerio Scarani. “Self-testing using only marginal information”. Physical Review A 98, 052331 (2018).
- [39] T. Franz, F. Furrer, and R. F. Werner. “Extremal quantum correlations and cryptographic security”. Physical Review Letters 106, 250502 (2011).
- [40] Vern Paulsen. “Completely bounded maps and operator algebras”. Cambridge Studies in Advanced Mathematics. Cambridge University Press. (2003).
- [41] R. F. Werner and M. M. Wolf. “All-multipartite Bell-correlation inequalities for two dichotomic observables per site”. Physical Review A 64, 032112 (2001).
- [42] D. M. Greenberger, M. Horne, and A. Zeilinger. “Going beyond Bell’s theorem”. In M. Kafatos, editor, Bell’s Theorem, Quantum Mechanics and Conceptions of the Universe. Pages 69–72. Kluwer Academic, Dordrecht, The Netherlands (1989).
- [43] Jȩdrzej Kaniewski. “Analytic and nearly optimal self-testing bounds for the Clauser-Horne-Shimony-Holt and Mermin inequalities”. Physical Review Letters 117, 070402 (2016).
- [44] Jȩdrzej Kaniewski. “Self-testing of binary observables based on commutation”. Physical Review A 95, 062323 (2017).
- [45] Rutvij Bhavsar, Sammy Ragy, and Roger Colbeck. “Improved device-independent randomness expansion rates using two sided randomness”. New Journal of Physics 25, 093035 (2023).
- [46] Frédéric Dupuis, Omar Fawzi, and Renato Renner. “Entropy accumulation”. Communications in Mathematical Physics 379, 867–913 (2020).
- [47] Frederic Dupuis and Omar Fawzi. “Entropy accumulation with improved second-order term”. IEEE Transactions on Information Theory 65, 7596–7612 (2019).
- [48] Tony Metger, Omar Fawzi, David Sutter, and Renato Renner. “Generalised entropy accumulation”. Communications in Mathematical Physics 405, 261 (2024).
- [49] Thinh P. Le, Chiara Meroni, Bernd Sturmfels, Reinhard F. Werner, and Timo Ziegler. “Quantum Correlations in the Minimal Scenario”. Quantum 7, 947 (2023).
- [50] Victor Barizien, Pavel Sekatski, and Jean-Daniel Bancal. “Custom Bell inequalities from formal sums of squares”. Quantum 8, 1333 (2024).
- [51] Lewis Wooltorton, Peter Brown, and Roger Colbeck. “Device-independent quantum key distribution with arbitrarily small nonlocality”. Physical Review Letters 132, 210802 (2024).
- [52] Miguel Navascués, Stefano Pironio, and Antonio Acín. “Bounding the set of quantum correlations”. Physical Review Letters 98, 010401 (2007).
- [53] Miguel Navascués, Stefano Pironio, and Antonio Acín. “A convergent hierarchy of semidefinite programs characterizing the set of quantum correlations”. New Journal of Physics 10, 073013 (2008).
- [54] Alban Jean-Marie Seguinard, Amélie Piveteau, Piotr Mironowicz, and Mohamed Bourennane. “Experimental certification of more than one bit of quantum randomness in the two inputs and two outputs scenario”. New Journal of Physics 25, 113022 (2023).
- [55] Marco Tomamichel. “Quantum information processing with finite resources”. Springer International Publishing. (2016).
- [56] C. Jordan. “Essai sur la géométrie à n dimensions”. Bulletin de la S. M. F. 3, 103–174 (1875).
- [57] Armin Tavakoli, Alejandro Pozas-Kerstjens, Peter Brown, and Mateus Araújo. “Semidefinite programming relaxations for quantum correlations”. Reviews of Modern Physics 96, 045006 (2024).
- [58] Koon Tong Goh, Jędrzej Kaniewski, Elie Wolfe, Tamás Vértesi, Xingyao Wu, Yu Cai, Yeong-Cherng Liang, and Valerio Scarani. “Geometry of the set of quantum correlations”. Physical Review A 97, 022104 (2018).
- [59] Cédric Bamps and Stefano Pironio. “Sum-of-squares decompositions for a family of Clauser-Horne-Shimony-Holt-like inequalities and their application to self-testing”. Physical Review A 91, 052111 (2015).
- [60] Cezary Śliwa. “Symmetries of the Bell correlation inequalities”. Physics Letters A 317, 165–168 (2003).
- [61] Peter Brown, Hamza Fawzi, and Omar Fawzi. “Computing conditional entropies for quantum correlations”. Nature Communications 12, 575 (2021).
Appendix A Proofs for expanded Bell expressions
A.1 Proof of Lemma˜1
Lemma 1. Let be an expanded Bell expression according to Footnote˜1. The maximum quantum value of is upper bounded by .
Proof.
To prove the above, we show that the operator expression is non-negative. Since each bipartite expression satisfies for all , we have positive expressions
| (48) |
We then have
| (49) |
Finally it follows from the above that , which proves the upper bound on the maximum quantum value. We can also upper bound the maximum local value by since . ∎
A.2 Uniqueness of binary distributions with fixed marginals
Before proving Eq.˜13, we establish the following fact about classical distributions of bit strings when their conditional distributions are fixed. We will later use this result to justify that the distribution used for randomness achieving the quantum bound of an expanded Bell inequality is unique when the seed is a self-test.
Lemma 11.
Let , , be a random bit string which takes values according to the distribution . Let be an bit partition of the string , excluding bits and , taking values . Then the distribution is entirely determined by the set of conditional distributions , provided for all .
Proof.
Proof can be established using a recursive argument to solve for a set of marginal terms , for a fixed , from which the full distribution can be recovered. Let us choose another partition with . Then we have
| (50) | ||||
By choosing different values of , this implies the two sets of equations
| (51) | ||||
Since , we can rearrange both for and equate:
| (52) |
where we have explicitly written in the variable, and denotes a tuple excluding parties and . The above equation tells us, for every choice of , the unknowns and are linearly dependent. Hence we consider the unknowns , since the terms can be computed via this linear dependence.
Consider choosing . We can find a new set of equations by repeating the above process with instead of , to find:
| (53) | ||||
where we have only included the case, and written to denote a tuple excluding parties . Notice we have now identified linear dependence between and . Neither of these equations contain a marginal with , so they relate pairs of unknowns distinctly to the parings from the previous equations, and are hence linearly independent. As before, we can proceed with the unknowns and recover the others by linear dependence.
We can apply the above procedure iteratively a total of times (for every ), halving the number of unknowns on every iteration by establishing linear dependence. Starting with marginals , this leaves us with 1 unknown, which can be solved via normalization, completing the proof. ∎
Now we can present a corollary which will be needed for the proof of Eq.˜13, showing the conditional distribution used for randomness, , achieving the quantum bound of an expanded Bell expression is unique.
Corollary 1.
Let be an expanded Bell inequality according to Footnote˜1 with if and zero otherwise, and be as defined in Lemma˜1. Let be constructed using a seed with the self-testing properties described in Eq.˜13, and denote a quantum behaviour that achieves . Then provided for all , the conditional the distribution is unique.
Proof.
If the quantum value is achieved, we must have
| (54) |
which implies from Eq.˜49. Next, we observe
| (55) |
where the second inequality follows from the fact for any operator (see e.g. [55, Lemma 3.3]). Above, , where is the quantum state that realizes the correlations, and identities on are implicit. Next we combine Eq.˜55 with Hölder’s inequality to obtain
| (56) |
Since
| (57) |
we conclude . Now we can write
| (58) |
where we define the normalized state . The self-testing properties of (see definition in Eq.˜13) then determine the unique correlations . Using the definition of , we find
| (59) |
We can now directly apply Lemma˜11. Explicitly we have , and the fixed conditional distributions , where we have identified .
∎
A.3 Proof of Eq.˜13
We can now proceed to prove Eq.˜13 in the main text, which is restated below:
Lemma 2. Let be an expanded -party Bell expression defined in Footnote˜1 with binary inputs and outputs, and if and zero otherwise. Suppose for every , there exists an SOS decomposition which self-tests the same pure bipartite entangled state between parties , along with some ideal measurements , according to Eq.˜3, which satisfy for all . Then for any strategy that achieves , the post-measurement state , for measurement settings , admits the tensor product decomposition,
| (60) |
Proof.
We will break this proof up into four steps. First, we will provide an SOS decomposition for the Bell operator , and derive the algebraic constraints satisfied by any state and measurements that achieves its maximum value. These turn out to be those implied by the bipartite Bell expressions that build up . Next, we will employ Jordan’s lemma, reducing the problem to qubits, and show how these constraints self-test the bipartite states. Finally we write down the global post-measurement state, and show how these self-tests imply a tensor product with .
A.3.1 SOS decomposition
By assumption, there exist SOS decompositions for the bipartite Bell operators , i.e., we can write
| (61) |
where is a polynomial of the operators , . We now use this to build an SOS decomposition for ,
| (62) |
Now, for some physical state and observables, observation of the maximum quantum value, , immediately implies the algebraic constraints
| (63) |
Since and commute, we define the post-measurement states
| (64) |
and arrive at the set of algebraic constraints, for a fixed ,
| (65) |
A.3.2 Applying Jordan’s lemma
Next, we employ Jordan’s lemma [56], which allows us to reduce our analysis to a convex combination of -qubit systems. Specifically, we will use the version presented in [45, Lemma 4], and apply [45, Lemma 6] to consider (without loss of generality) the set of post-measurement states arising from block diagonal measurement operators with block size , and a state which has support only on each block. We write to denote the qubit Hilbert space of party , and introduce a flag system which indicates the block. Then for every party , and the purified state takes the form
| (66) |
where is an -qubit state corresponding to block , where indexes the block for party and form a probability distribution. Tracing out , the total state received by the parties is then a classical quantum state, where the classical register indexes which -qubit state is in the quantum system. Eve then holds a purification of the state in register along with a label in register telling her which block it pertains to. Similarly, the projectors decompose
| (67) |
where is a rank one single qubit projector on corresponding to block [56, 13, 45]. The projector performed on all systems except and for inputs is
| (68) |
where the notation is understood to denote a tuple excluding entries , e.g., is a tuple of indices for . is then a rank one projector on the qubit Hilbert space shared by all parties excluding and , corresponding to the block .
We can now apply Jordan’s lemma to the projected states , by computing
| (69) |
where is the set of blocks for which the projection is non-zero. Here is understood to be the concatenation of , and we used the fact that the qubit projectors are rank one to write the state as a tensor product,
| (70) |
where , and . is then the state held by parties and Eve following the projection. By writing , and , we can re-write the constraints in Eq.˜65 as (suppressing the identity operator on Eve’s systems)
| (71) |
implying, for a fixed ,
| (72) |
This subsequently implies
| (73) |
where we wrote
| (74) |
using the decomposition in Eq.˜67.
A.3.3 Applying the bipartite self-tests
For the next part of the proof, we use the self-testing properties of the bipartite Bell expression , which are in turn derived from the SOS polynomials, and the constraints they impose on any state which achieves the maximum quantum value. Explicitly, for any state which satisfies the polynomial constraints, there exists a local isometry which transforms that state into an ideal state in tensor product with some junk. Due to Jordan’s lemma, the constraints in Eq.˜73 certify the the existence of a pair of local unitaries on the qubit registers of parties and , such that, for every measurement outcome and block combination , 666Note that the notation suppresses the tensor product of local unitaries to ease notation, that is, where is a unitary on system and is a unitary on system ., there exists a fixed two qubit state and projectors , satisfying
| (75) |
where is the junk system left over in the Eve register, which a priori may depend on and . Since we required that all bipartite expressions self-test the same state up to local unitaries, the above equation holds for all .
A.3.4 Global post-measurement state
Finally, we use the existence of the local unitaries to analyze the global post-measurement state held by all parties following their zero measurement, and storing their outcomes in the register , which takes the form
| (76) |
We can rewrite the term inside the partial trace
| (77) |
Now, tracing out equates to tracing out systems , which yields
| (78) |
By employing Corollary˜1, we know that, following observation of , the marginals are unique; hence the following equality holds:
| (79) |
where are those unique correlations needed to achieve . We then find
| (80) |
For a fixed , Eve can still establish correlations with the parties excluding and , by choosing the sets to be disjoint. She could then distinguish the different outcomes by a projective measurement on . She can also establish correlations by making the set distinguishable and measuring . To show Eve is in fact uncorrelated with all parties, we use the fact that there are choices of , i.e., one can choose different combinations of parties to maximally violate the bipartite self-tests.
We now include extra notation , , which denotes a tuple of outcomes for all parties excluding and , and define the following state, which is just a rewriting of Eq.˜80 making the choice explicit:
| (81) |
Now, we could equally define a second state where in the exact same way, except we chose instead of as the self-testing party. Since both states are a rewriting of the same post measurement state given by Eq.˜80, they must be equal, and we establish the equalities
| (82) |
These equalities will allow us to place constraints on the sets , and ultimately show they are all equal. Specifically, Eq.˜82 implies777Note that we have implicitly equated the rewriting of the same outcome string , and only considered cases which appear in the summation, i.e., strings with nonzero probability, .
| (83) |
By tracing out system , and using the fact that , Eq.˜83 can only hold if
| (84) |
Consider the case and . Then we have for a fixed ,
| (85) |
Since the RHS is independent of , we must have that , i.e., the LHS is also independent of . We can apply the same argument for , deducing that
| (86) |
which is independent of the outcome string . There is nothing unique about choosing , allowing us to write
| (87) |
Hence Eve can learn nothing about any of the outcomes by measuring her register . What remains is to deal with the vectors . We will show that the set contains one linearly independent vector, hence Eve can learn nothing about the outcome from measuring her register .
Using the same approach as before, Eq.˜82 now implies, for every ,
| (88) |
Now equating for a given value of , we obtain
| (89) |
We can hence conclude the two vectors are linearly dependent,
| (90) |
where denotes equality up to a constant888Note it is sufficient to just consider the cases for which the probabilities are nonzero. If they are zero, then the vector will not appear in the summation, and Eve will never observe it.. Notice on the left hand side of the above equation, one has the freedom to choose any value of without changing the right hand side up to a constant. Therefore
| (91) |
There are such equations written above, corresponding to the different choices of once is fixed. We have unknowns that we want to fix, hence this is sufficient to show linear dependence for the case. If , we can select another party not equal to and add another equations,
| (92) |
allowing us to write
| (93) |
The combination of the two will solve the case. We can see that for the first choice of , we get equations which is half the unknowns, reducing the number of unknowns to . Each new choice of , of which there are in total, halves the number of unknowns, until we are left with one, which shows that every vector can be written as a linear combination of a fixed vector, i.e.
| (94) |
for some constants , which due to normalization must be equal to 1. Putting the above into Eq.˜88 we also notice , hence we can drop the label.
Now we finally conclude
| (95) |
which is of the desired tensor product form, and completes the proof. ∎
A.4 Proof of Lemma˜3
Proof.
Lemma˜3 directly follows from Eq.˜13 since the state for which then entropy is evaluated on has Eve’s part in tensor product. This implies, for all compatible post measurement states, . Since , derived explicitly in the proof of Eq.˜13, is the same for all compatible states and measurements, we obtain the claim:
| (97) |
∎
Appendix B Proofs and details for DI randomness certification
Recall the bipartite Bell-inequalities which are defined as
| (98) |
for where
| (99) |
We now prove a few results about these Bell-inequalities that were stated in the main text.
B.1 Proof of Lemma˜5
Lemma 5. Let be a tuple of measurement outcomes for all parties excluding , and be the parity of . Let and be a set of bipartite Bell expressions between parties , where
| (100) |
Then the expanded Bell expression given by
| (101) |
has quantum bounds where . Moreover, is achieved up to relabelings by the strategy in Eq.˜20, and cannot be achieved classically.
Proof.
The above is an example of Footnote˜1, where we used the bipartite expression in Lemma˜4 as a seed, and chose if and , and 0 otherwise. First we notice that if the bound is achievable, then must define a nontrivial Bell inequality. This is because the maximum local value is upper bounded by , since . A similar argument holds for the minimum local value.
We now proceed to show is achieved by the strategy in Eq.˜20. Notice that, for the ideal operators () if (),
| (102) |
where spans the support of , and . We then have
| (103) |
where the final equality comes from the fact that when , we recover the state and measurements in Eq.˜19 which yields the maximum quantum value of , and when , we obtain a strategy equivalent to Eq.˜19 up to a relabeling, which yields the maximum quantum value of .
Since the maximum quantum bound is achievable, a nontrivial Bell inequality follows. The minimum quantum value is simply achieved by relabeling the outcomes. ∎
B.2 Proof of Proposition˜3
Proposition 3. For even , let
| (104) |
where is the element of the sequence given by
| (105) |
Then .
Proof.
The sequence splits naturally into four subsequences for
| (106) | |||||
First notice that the first terms in each of these subsequences are contained in one of the subintervals of
| (107) | |||||
Looking at the ratio of subsequent terms in each subsequence
we see that the subsequences and are strictly monotonically decreasing sequences whereas and are strictly monotonically increasing sequences. Furthermore their limits are
| (108) | ||||
The limits correspond to the boundaries of the respective subinterval of that the first terms of the subsequences are contained in. As they converge strictly monotonically to these limits this implies that every term in the subsequences in contained within their respective subintervals and hence for all even . ∎
B.3 Proof of Propositions˜4 and 5
Proposition 4. Let be an even integer. For every MABK value in the range , there exists a that satisfies .
Proof.
We examine each subsequence independently.
Case 1. For , recall that . When , the claim can be seen from Fig.˜1, which indicates MABK values below for , and the fact that is continuous. We hence consider in the following. First note
| (109) |
Consider the point . We have
| (110) |
Therefore, by continuity of the function in , the range of achievable MABK values corresponding to contains the sub-interval . By a similar argument, the sub-interval must also be achievable for . For the value , notice
| (111) |
and . Hence there must exist a such that .
Case 2. For , recall . As before, we only need to consider by analyzing Fig.˜1. Let . Then
| (112) |
We also note
| (113) |
and
| (114) |
We can therefore apply the same arguments as the previous case.
Case 3. For , recall . We observe the claim holds for by examining Fig.˜1, and consider . Let , and note
| (115) |
By checking
| (116) |
and
| (117) |
we can apply the same arguments as case 1.
Case 4. Finally, for , we have . The case can be seen by examining Fig.˜1, and for we define . Then
| (118) |
We also have
| (119) |
and
| (120) |
By the arguments in case 1, this completes the proof. ∎
Proposition 5. Let be an odd integer. For every MABK value in the range , there exists a that satisfies .
Proof.
As was done for the even case, we consider four subsequences.
Case 1. For , we note . When , the claim can be verified from Fig.˜2, hence we consider . Consider the point . Then
| (121) |
where . Notice that
| (122) |
Similarly
| (123) |
Hence
| (124) |
Therefore, the achievable MABK values from the interval include the sub-interval by continuity of the function in .
Case 2. For , note . The claim for can be verified using Fig.˜2, so we consider . Let , and note
| (125) |
where . Following the same steps as before, we have
| (126) |
and
| (127) |
implying
| (128) |
The same arguments used in case 1 prove the claim.
Case 3. For , we consider the MABK expression obtained by relabelling the inputs of every party, followed by the output of every party’s first measurement, i.e., and . The resulting MABK value of the strategy in Eq.˜20 is given by999Rather than relabelling the MABK expression, we could equivalently consider the strategy in Eq. 31, which achieves the MABK value in Eq. 32 of the original expression (Eq. 1), with the substitution . This also results in Eq. 129.
| (129) |
We then have . We can verify the claim for from Fig.˜2, hence we consider . Let , and note
| (130) |
where . We have
| (131) |
and
| (132) |
which implies
| (133) |
The claim then follows from the same arguments as the previous cases.
Case 4. For , we also consider the relabelled MABK expression in Eq.˜129, and note . Let , and consider
| (134) |
where . We have
| (135) |
and
| (136) |
implying
| (137) |
By following the same steps as before this proves the claim. ∎
B.4 Evidence for ˜1
Conjecture 1. The maximum MABK value achievable by quantum strategies that generate maximum randomness, i.e., strategies with , is .
The goal of ˜1 is to claim the analytical lower bound, , on the maximum MABK value achievable whilst generating maximum randomness, is optimal, in the sense there exists no other set of quantum correlations with a higher MABK value achieving maximum randomness. To justify this claim, we developed a numerical technique to upper bound the maximum MABK value of quantum correlations achieving maximum randomness, and checked this against the achievable lower bounds . We found close agreement between our numerical calculations and the analytic lower bounds, modulo a small discrepancy which pushed the numerical values slightly below the analytical ones. Since the SDP being solved is a minimization, we judge this to be caused by numerical precision, and the accumulations of errors pushing the global optimum below its true value. A comparison between our analytical lower bound and the numerics can be found in Table˜1, and details of the numerical method can be found in Section˜B.10.1. We also remark that this conjecture was proven analytically for the case in [23].
| Analytical lower bound, | Numerical upper bound | ||||
|---|---|---|---|---|---|
| 2 | 1.29903810 | ||||
| 4 | 2.65828370 | ||||
| 6 |
|
5.41251940 | |||
| 8 |
|
10.93208548 | |||
| 10 |
|
22.00125885 | |||
| 12 |
|
44.19316040 |
B.5 Proof of Proposition˜6
Proposition 6. In the limit of large even , one can achieve arbitrarily close to the maximum quantum violation of the party MABK inequality, , whilst certifying maximum device-independent randomness.
Proof.
We consider the asymptotic behaviour of , which gives an achievable lower bound on the maximum MABK value compatible with maximum randomness. Our aim is to show that as becomes very large, whilst remaining an even integer, the MABK violation tends to the maximum quantum violation , i.e.,
| (138) |
This can be established directly from the asymptotic behaviour of given in Eq.˜108, as follows.
We then consider two cases:
Case 1: or . For these values of , we know . One can then verify
| (140) | |||
Now we split into two sub-cases to evaluate in the limit (B.5).
1a: . Here we find
| (141) |
which has the oblique asymptote . We hence find
| (142) |
1b: . Here we find
| (143) |
which also has the oblique asymptote , implying Eq.˜142.
Case 2: or . For these values of , we know . One can then verify
| (144) | |||
Splitting into two sub-cases:
2a, : Here
| (145) |
which has the oblique asymptote . Inserting into the limit we find
| (146) |
2b, : For the final case
| (147) |
which has the oblique asymptote . Inserting into the limit we find
| (148) |
This shows that the MABK violation tends to the maximum quantum value in the regime of large . Note however, in the limit tends to or ; these values are not self-testable, since does not lie in a valid interval for there to be a gap between the local and quantum bound for the two party Bell inequality. However, the points either side of both angles are self-testable. We hence obtain the result that one can achieve arbitrarily close to maximum MABK violation whilst certifying maximum DI randomness, for an arbitrarily large finite . ∎
B.6 Local dilution measure of nonlocality
In this section we briefly outline the linear program used to generate Fig.˜3 in the main text (see also [57, Section I.B.1] for a description of this technique). Given a distribution , we can represent it as a vector in a high dimensional space, . We denote the set of local deterministic distributions as , and the local polytope can be constructed by taking its convex hull,
| (149) |
To check wether admits a local description, we can search for a set , where , , using a standard linear program.
To quantify the distance of a given from , we define the diluted sets, for ,
| (150) |
As , tends to the affine hull of the points , and we have the inclusion: , where . We then define the following measure, which we call the local dilution:
| (151) |
can be interpreted as the smallest dilution of the local polytope that contains . If , one has to enlarge the local set more to include than to include . We can hence understand to be more nonlocal than .
B.7 Proof of Lemma˜8
In the main text, we detailed a two parameter family of bipartite Bell expressions which are used to build our -partite expressions. These are generalizations of the two families introduced in [23], and can be recovered as sub-families of the self-tests studied in [50, 51, 49].
Lemma 8. Let such that and . Define the family of Bell expressions parameterized by and ,
| (152) |
Then we have the following:
-
(i)
The local bounds are given by , where
(153) -
(ii)
The quantum bounds are given by , where .
-
(iii)
.
-
(iv)
Up to local isometries, there exists a unique strategy that achieves :
(154)
Proof.
B.8 Proof of Lemma˜9
Lemma 9. Let be a tuple of measurement outcomes for all parties excluding , and be the parity of . Let ,
| (158) |
and
| (159) |
Define the following Bell polynomial
| (160) |
If , is an expanded Bell expression, and has quantum bounds where , which can be achieved up to relabelings by the strategy
| (161) |
In addition, this quantum bound cannot be achieved classically.
Proof.
Suppose , and consider the ideal projection operators derived from the observables in Eq.˜31, i.e., where
| (162) |
We then have
| (163) |
where spans the support of and
| (164) |
Notice where . We now calculate
| (165) |
We can now calculate how transforms under . Let for be an arbitrary observable. Then
| (166) |
Substituting and into the above, we find
| (167) |
and similarly for party , where we used the definitions of in Eq.˜154. We therefore find
| (168) |
The largest and smallest eigenvalues of are , and are associated with the eigenvectors . We therefore have
| (169) |
Putting everything together, we obtain
| (170) |
The quantum bound then follows by summing over , which shows achievability. The minimum quantum value is achieved by relabeling the outcomes. Moreover, the quantum bound cannot be achieved classically since corresponds to an expanded Bell inequality when (cf. the discussion below Eq.˜49). ∎
B.9 Proof of Proposition˜7
Proof.
For convenience, we restate the set below,
| (171) |
First we will consider the range of as we vary . By definition, , which takes values over the interval . Then
| (172) |
which implies .
Next we consider as a function of ,
| (173) |
When , , and when ,
| (174) |
We first consider , which satisfies and . By inserting the definition of from Proposition˜3,
| (175) |
We therefore see (since is a linear function of and lies in that range for the extremal values of ).
For , and . We have
| (176) |
implying . For , we have , and
| (177) |
implying . Finally, for , , and
| (178) |
implying . For every , we have shown and for , hence . ∎
B.10 Evidence for Eq.˜45
Conjecture 2. For even, the maximum randomness unconditioned on Eve, , that can be generated by quantum strategies achieving an MABK value, , is given by
| (179) |
where is defined in Eq.˜40, and
| (180) |
B.10.1 Numerical approach for upper bounding maximum randomness versus MABK value
The objective of this section is to generalize the technique introduced in [23], which found upper bounds on the maximum randomness versus CHSH value using an SOS technique. We begin by defining the problem in detail.
Let denote the set of quantum distributions, and denote the MABK value of a distribution . Moreover, let be the conditional von Neumann entropy of the outputs for inputs given the observed distribution , taking the infimum over all quantum strategies that could give rise to , i.e.,
| (181) |
Similarly let be the Shannon entropy of the distribution on for inputs . Then the curve we want to find is defined by the optimization
| s.t. | ||||
| (182) |
Our technique proceeds by defining a sequence of upper bounds on . [We speak of upper bounds on because we either upper bound or , and because the functions turn out to be monotonic either gives an upper bound.]
We begin by removing the dependence on Eve, which results in an upper bound on the previous problem via strong subadditivity of the von Neumann entropy. Explicitly,
| s.t. | ||||
| (183) |
Next we state the following two lemmas, adapted from Ref. [23].
Lemma 12.
[Monotonicity of ] Suppose is the largest MABK value compatible with (cf. Conjecture 1). Then the function is strictly decreasing on .
We will prove Lemma 12 as a corollary of the following.
Lemma 13.
Let be a convex set, be concave, be linear and subject to , . Then is convex.
Proof.
We directly calculate
| s.t. | ||||
| s.t. | ||||
| s.t. | ||||
| (184) |
where the first inequality follows due to the linearity of and convexity of , and the second inequality due to the concavity of . ∎
Proof of Lemma 12.
Note that is concave in , the quantum set, , is convex and the MABK value, , is linear. Lemma 13 hence implies that is concave in .
Then note that . This follows from the assumption that the largest MABK value achievable when is , and hence is initially decreasing, which implies the claim. ∎
In the case , it is known is the largest MABK value compatible with ; see [23, Corollary 1]. For , we have verified tightness numerically, as shown in Table˜1101010Monotonicity of is not needed to establish [23, Corollary 1] or the upper bounds presented in Table 1.
Lemma 14 (Inverse function of ).
Suppose . The function has the following inverse, denoted , that satisfies , given by
| (185) |
Proof.
We prove Lemma˜14 by showing , and , and using Lemma˜12. First consider ,
| s.t. | ||||
| (186) |
The constraint implies the achievable MABK values for the distribution must lie to the left of , i.e., , since the curve is strictly decreasing (cf. Lemma˜12). To see this, suppose . Then by Lemma˜12. But, , implying , which by assumption cannot hold, giving a contradiction. We therefore have that . Moreover, this bound is saturated by the behaviour which achieves the maximum defining 111111Note that the function is continuous, and the quantum set is compact (see the discussion in [58, Appendix B]), from which it follows that is also compact. This implies the objective function in (183) attains its maximum over its domain., i.e., satisfies and . This establishes .
For the other direction , the same reasoning holds. The constraint implies that since any distribution that achieves a CHSH value of can generate no more than bits of randomness. Hence . This bound is saturated by the behaviour achieving the maximum defining , completing the proof. ∎
From the above lemma, we can solve for upper bounds on the points using the inverse function, i.e., where . What remains is to upper bound , which will correspond to an upper bound on due to the monotonicity argument. Next we obtain a upper bound by applying a symmetrization step to the distribution :
Lemma 15.
Let be the local channel that maps all even (odd) parity outcome strings to a uniform mixture of all even (odd) parity outcome strings,
| (187) |
The entropy after applying is non-decreasing, and the MABK value is invariant under .
Proof.
The first claim follows from the data processing inequality, . The second claim comes from the fact that the correlators are invariant under . ∎
After the map is applied, the probabilities are symmeterized, i.e., if is even and if is odd, for . We can hence define the following upper bound on where
| s.t. | ||||
| s.t. | ||||
| (188) |
We can now apply Lemma˜14 (which still holds after applying , since it preserves the convexity of ), and define the function
| s.t. | ||||
| (189) |
We can further relax this by considering the correlator after symmetrization, . Then we have where
| s.t. | ||||
| (190) |
This follows from the fact that the feasible region of the former optimization is a subset of the latter.
Next, consider the expression for the entropy of a symmetrized distribution . By direct computation we find
| (191) |
Since for , there is a one to one correspondence between and . Hence if , there exists a unique that satisfies . We can therefore write
| s.t. | ||||
| (192) |
Next we introduce the function
| (193) | |||||
Here is an SOS decomposition for the operator expression
| (194) |
hence for any feasible point , all quantum correlations satisfying also satisfy . This implies . Now, by choosing a basis of monomials for , one can evaluate the function numerically using a standard SDP solver. We refer the reader to [59] for details of how to find such formulation, and provide a self-contained description below.
If the monomial basis is chosen to be , where each is a product of operators from the set , then one can construct polynomials of the form , . then admits an SOS decomposition if are chosen such that
| (195) |
where are matrix elements , the Gram matrix of the set of vectors , where . One now arrives at the following optimization problem
| (196) |
Now one can write , where is some complex matrix with elements , for , which denotes the canonical reduction of the set using the commutation and projective relations (see Ref. [59] for details). Similarly, one can express the operator expression in this basis, , and arrive at an SDP of the form
| (197) |
For our numerical calculations, we choose the monomial basis , consisting of elements.
B.10.2 Numerical results
B.11 Other Bell inequalities for
The above technique can be directly applied to find bounds on other Bell inequalities. We applied this to the tripartite expressions in Eqs.˜46 and 47, which, along with the MABK expression, trivial extensions of CHSH and positivity cover all inequivalent classes of facets for the local polytope with uniform marginals (see [60] for the general case). The exact trade-offs we found are detailed in Fig.˜7, and we summarize various bounds of each class in Table˜2. We restate the Bell expressions studied below [41]:
| (198) |
where we have made the substitution , etc. for readability. For and , we applied our numerical technique by substituting them in for the MABK expression. When , the SDP returns an upper bound on the maximum violation with maximum randomness, which we label (the facet class in question will be clear from context). For , we numerically identified that achieves the maximum quantum value of , for which the corresponding entropy is given by Eq.˜191, which evaluates to ; by varying we achieve the trade off in Fig.˜7, which corresponds to an upper bound. Similarly, for we found achieves the maximum quantum value , so by varying we find the curve in Fig.˜7. The corresponding entropy is which is exactly 1 plus the amount certified by maximum CHSH violation [45, 61, 23].
We checked the value of our constructions in Eq.˜20, with , for the expressions and . We find
| (199) |
By varying , we find one can achieve a wide range of values from the local bound, however the values of are inaccessible using this parameterization; one will need to consider a larger family of strategies to further investigate if is achievable with maximum randomness.
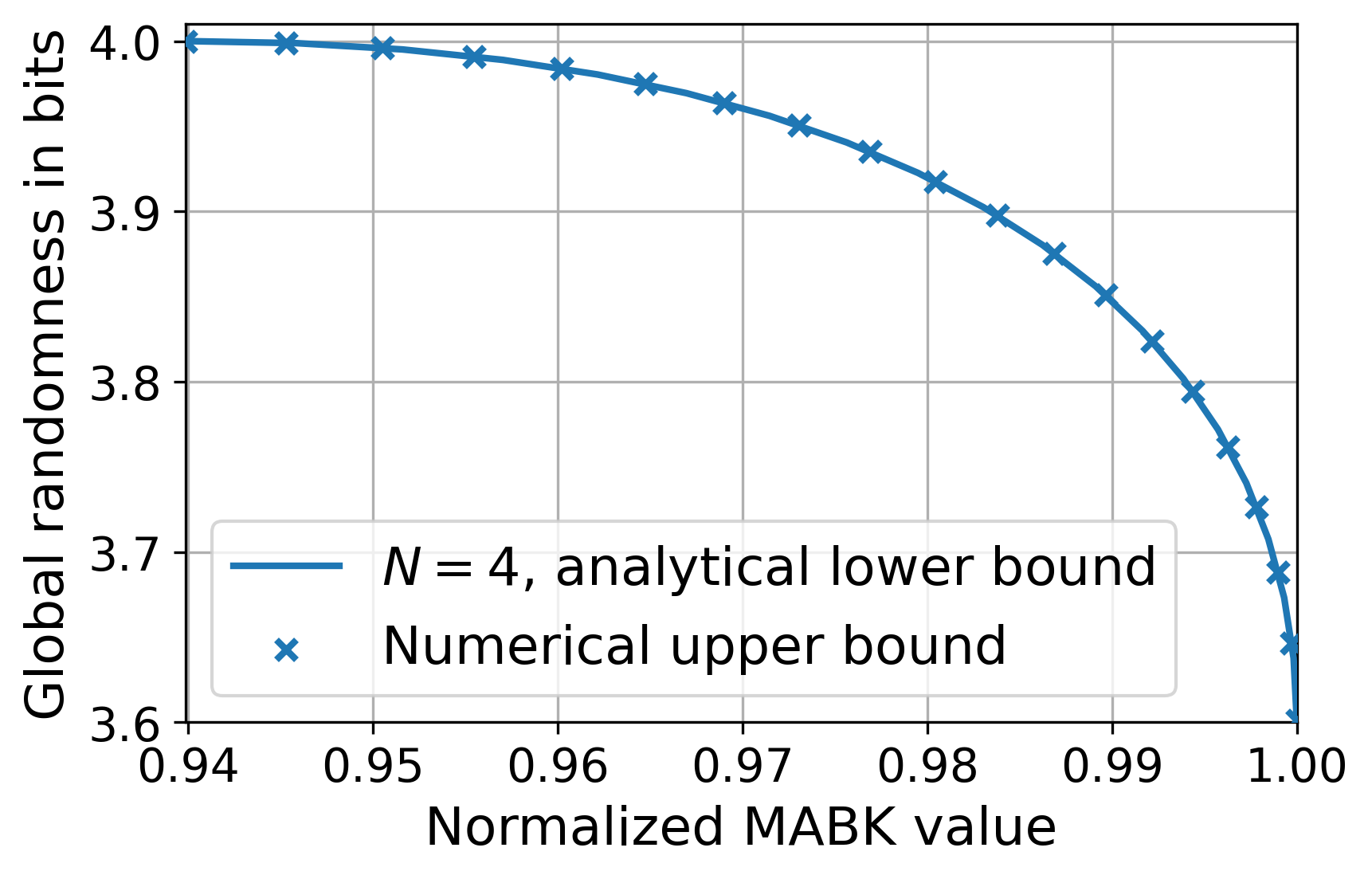
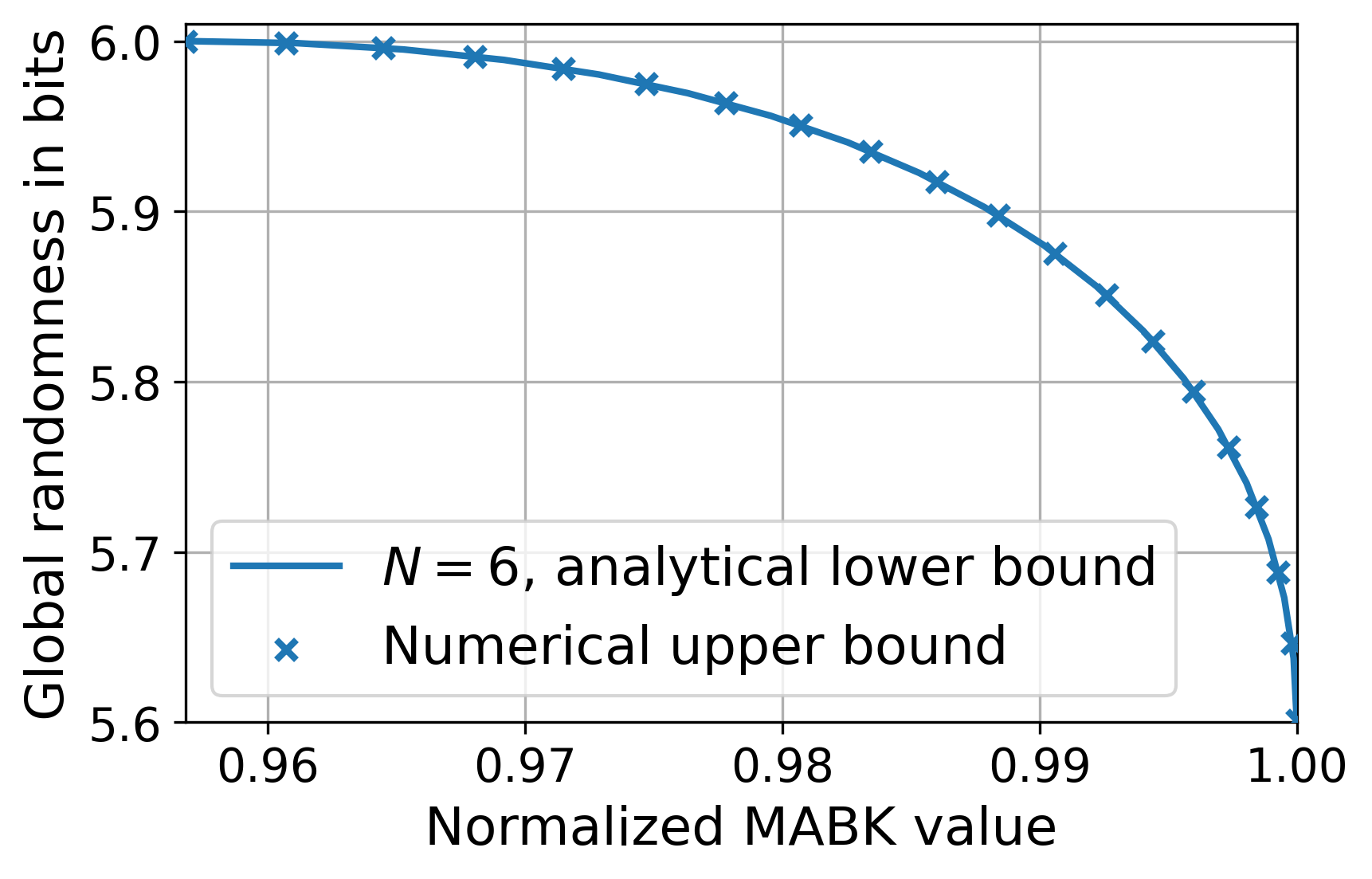
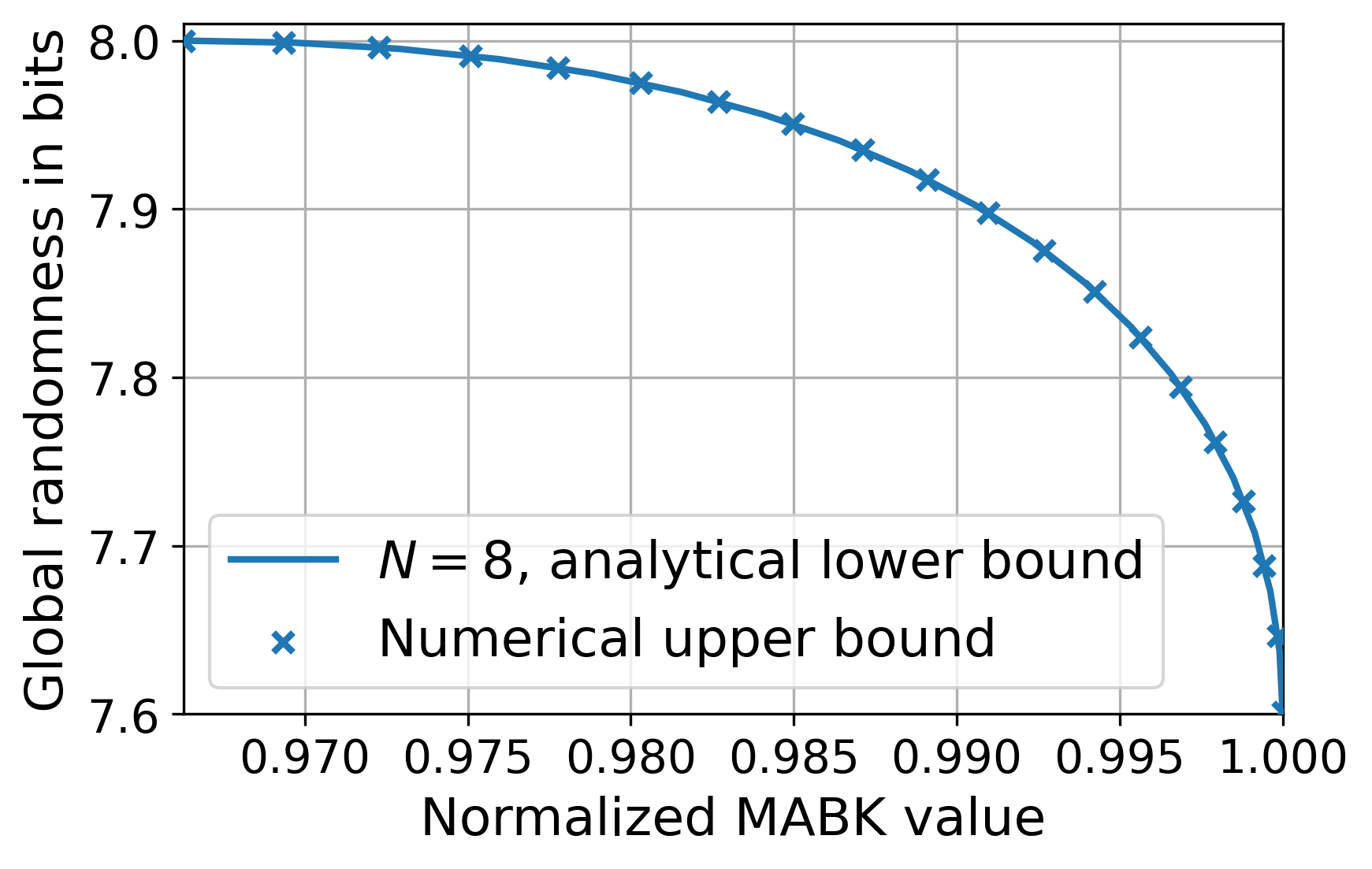
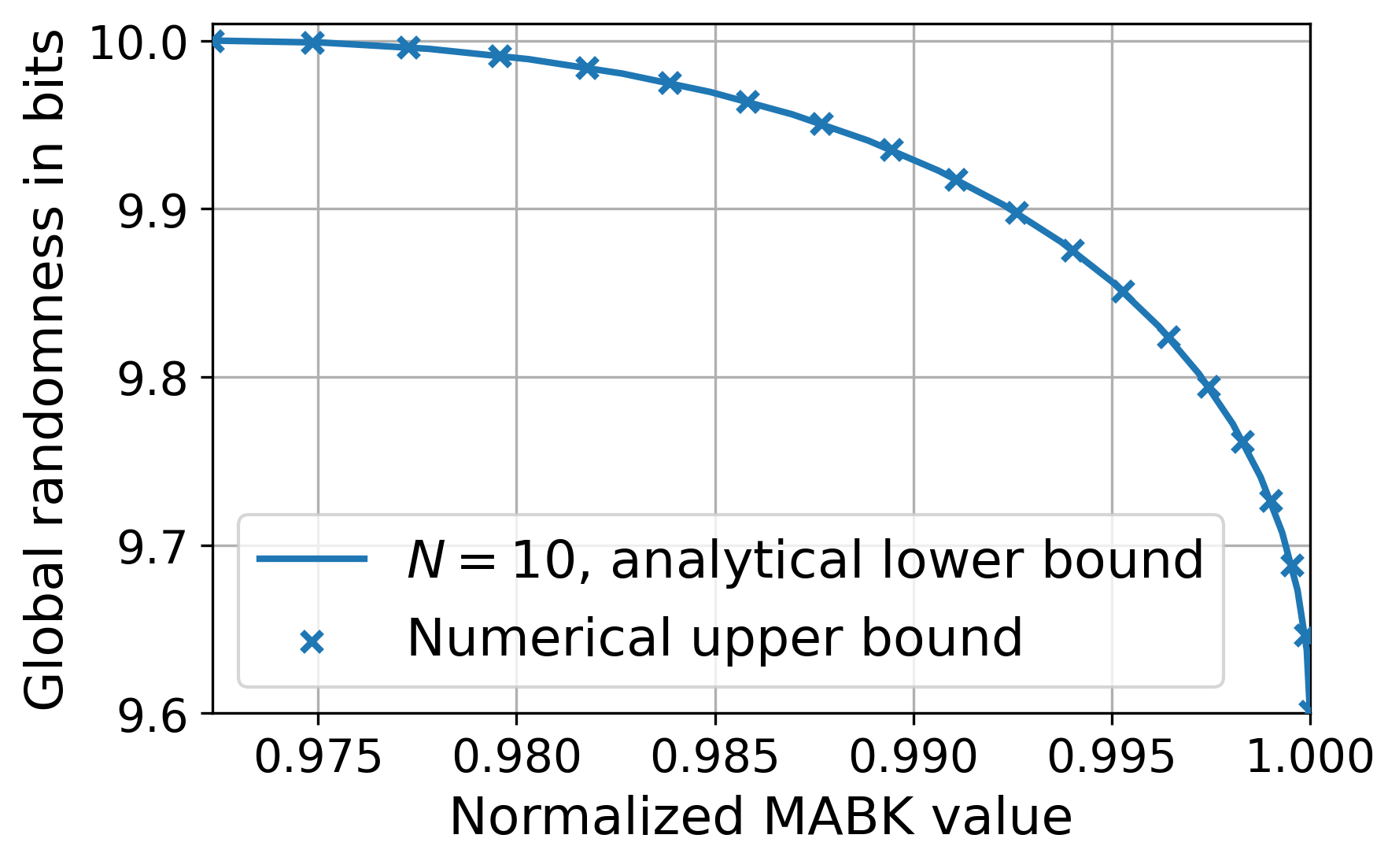
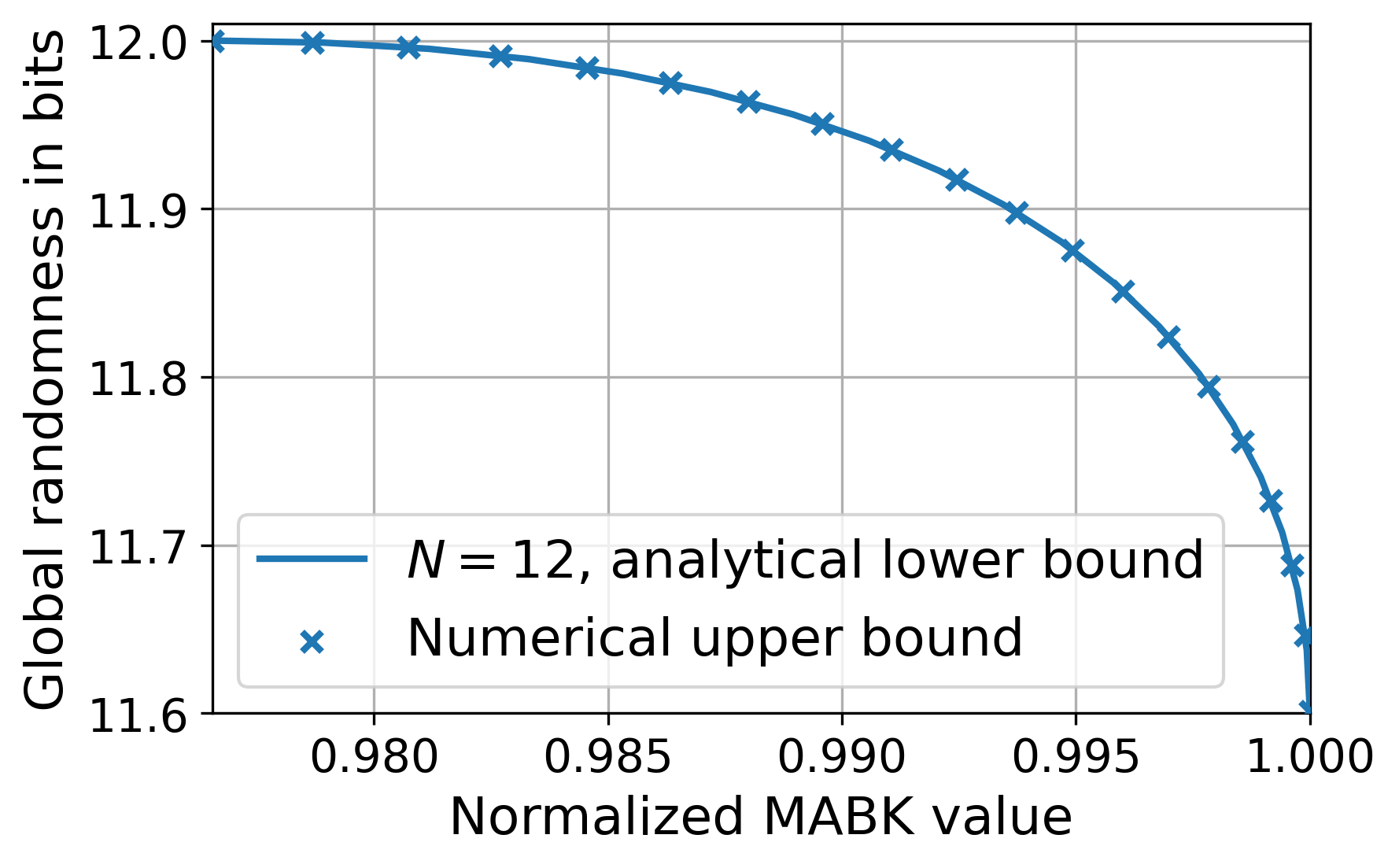
| Facet | ||||
|---|---|---|---|---|
| 1 | 2 | 2 | 3 | |
| 1 | 1.64621108 | |||
| 2 | 2.59807617 | |||
| 2 | ||||
| 1 | 0 | 1 | 0 |