Exponential speedup of quantum algorithms for the pathfinding problem
Abstract
Given on an unweighted undirected graph , the goal of the pathfinding problem is to find an - path. In this work, we first construct a graph based on welded trees and define a pathfinding problem in the adjacency list oracle . Then we provide an efficient quantum algorithm to find an - path in the graph . Finally, we prove that no classical algorithm can find an - path in subexponential time with high probability. The pathfinding problem is one of the fundamental graph-related problems. Our findings suggest that quantum algorithms could potentially offer advantages in more types of graphs to solve the pathfinding problem.
1 Introduction
Quantum algorithms can exploit the superposition and interference properties of quantum mechanics to solve certain problems significantly faster than classical algorithms, achieving super-polynomial speedup. However, the list of such problems is limited. The most well-known problems demonstrating this advantage include Simon’s problem, factoring, discrete logarithms, the Pell equation, and other related algebraic problems. Efficient quantum algorithms [1, 2, 3] exist for these problems, while no known classical algorithms can solve them. In addition, there are graph-related problems, such as the welded tree problem [4] and the graph property testing problem [5], where exponential separations can be achieved relative to the adjacency list oracle.
Identifying problems that can be leveraged by quantum algorithms to achieve superpolynomial speedup over classical algorithms remains one of the major challenges in the field of quantum computation. These challenges arise from two aspects. First, the problem needs to be believed to be classically hard. Second, the problem also needs to be quantumly easy. Several previous attempts to identify such problems have failed due to these constraints. For example, hopes of achieving exponential speedup with quantum algorithms in various machine learning problems, including recommendation systems, principal component analysis, supervised clustering, support vector machines, low-rank regression, and solving semidefinite programs, were later refuted by Tang’s breakthrough results [6] and subsequent work [7, 8]. Moreover, although quantum algorithms [9, 10] that utilize the HHL algorithm [11] as a subroutine show potential to achieve superpolynomial speed-up in solving certain multivariate polynomial systems, it remains unknown how to find such special polynomial systems to demonstrate this quantum speedup.
The welded tree pathfinding problem in the adjacency list oracle is one of the top open problems in the field of quantum query complexity [12]. A welded tree graph consists of two balanced binary trees of height with roots and and a random cycle that alternates between the leaves of the two binary trees. Given the name of the two roots and , the goal of the welded tree pathfinding problem is to output the names of vertices of an - path. While there is an efficient quantum algorithm to solve the welded tree problem, that is, finding the name of the root given the name of the root , it has been shown that a natural class of quantum algorithms cannot solve the welded tree pathfinding problem [13].
Moreover, the pathfinding problem in isogeny graphs plays an important role in the security of isogeny-based cryptosystems [14, 15, 16, 17]. An isogeny graph is constructed with vertices as isomorphism classes of elliptic curves and edges as isogenies (maps) between two elliptic curves. The size of the graph is exponentially large, making it difficult to find a path (map) between two vertices (elliptic curves) of polynomial length. Depending on the constraints on the isogenies, there will be different types of graph, such as volcano graphs, Cayley graphs, and supersingular graphs. So far, the best quantum algorithm takes exponential time to solve the pathfinding problem in supersingular isogeny graphs [18, 19]. Notably, given a vertex in an isogeny graph, one can efficiently compute its neighbors. This makes isogeny graphs a natural instantiation of the adjacency list oracle of an abstract graph. Recent advances have shown that efficient classical algorithms can be used to attack SIDH and SIKE in certain supersingular isogeny graphs, provided additional information is available alongside the starting vertex [20]. However, the general pathfinding problem underlying isogeny-based cryptosystems remains secure [21]. Consequently, other isogeny-based cryptosystems, such as CSIDH [22] continue to be secure against this attack [23].
In this paper, we show that the pathfinding problem in some graphs admits an exponential separation between the quantum algorithm and the classical algorithm under the adjacency list oracle. Instead of solving the welded tree pathfinding problem and the isogeny graph pathfinding problem directly, we construct a graph by associating distinct welded trees with a path of length as in Figure 1. Given the name of two vertices , in , the goal of the pathfinding problem is to output the names of vertices of an - path. Similarly to the welded tree pathfinding problem, there is an exponential number of - paths in the graph . On the other hand, the shortest - path is unique in the graph , while there is an exponential number of shortest paths in the welded tree graph. Using the distinctness of the welded trees in the graph , we show that there is an efficient quantum algorithm that solves this pathfinding problem. This quantum algorithm works by finding the edges of the - shortest path step-by-step. For each step, the polynomial time continuous quantum walk algorithm [4] for the welded tree problem is used to select one edge of the shortest - path. Repeat steps, the quantum algorithm outputs the shortest - path. In particular, our quantum algorithm uses the continuous quantum walk algorithm [4] as a subroutine, which is a new class of algorithm outside of the natural quantum algorithms considered in [13]. This suggests that there might be a new way to solve the welded tree pathfinding problem.
Finally, we show that no classical algorithm can solve the path-finding problem in subexponential time. Observe that any paths between the two vertices and have to go through a vertex of degree at least , or pass the vertex as indicated in Figure 1. To establish the classical lower bound, we show that it is classically hard to output the name of the vertex or vertices that have a degree of at least . The proof uses the result of the classical lower bound of the welded tree problem, which informally states that, given the name of one root, it is classically hard to traverse through the welded tree to find the other root.
To the best of our knowledge, this is the first example that exhibits the exponential speedup of quantum algorithms for the pathfinding problem. Previous quantum algorithms have achieved at most a polynomial speedup for solving the pathfinding problem in both general and specific graphs. For example, quantum algorithms based on amplitude amplification [24] can solve the pathfinding problem in a general graph using queries to the adjacency matrix oracle, where is the number of vertices in the graph. By restricting the class of graphs and under the same query model, a quantum algorithm [25] based on the span program to generate the quantum - electrical flow slightly improves the query complexity to solve the pathfinding problem. In the incidence list oracle model, [26] uses the HHL algorithm to generate the quantum - electrical flow and provide a sublinear time () quantum algorithm for the pathfinding problem in some graphs while the known classical and quantum algorithms take linear time . Furthermore, there exist quantum algorithms [27, 28, 29] that utilize quantum walks to solve the pathfinding problem in specific graph structures such as a chain of star graphs and a regular tree graph, providing a quadratic speedup compared to classical algorithms.
Organization.
In Section 2, we introduce the main results of the continuous quantum walk for the welded tree problem, which will be a key subroutine of our quantum pathfinding algorithm. In Section 3, we construct the graph from the welded trees and use it to define the pathfinding problem. Then we present the quantum algorithm that solves the pathfinding problem. In Section 4, we establish the classical lower bound of the pathfinding problem showing that no classical algorithm can solve this problem with a polynomial number of queries. Finally, we give a discussion and provide some open problems in Section 5.
2 Quantum algorithms for the welded tree problem
In this section, we introduce the main results of the continuous quantum walk approach for the welded tree problem, which will be a key subroutine of our quantum algorithm for the pathfinding problem.
It should be noted that several quantum algorithms have been developed to solve the welded tree problem, encompassing techniques such as continuous quantum walks [4], multidimensional quantum walks [30], discrete quantum walks [31] and the coupled classical oscillator approach [32]. However, in this paper, we specifically focus on the original continuous quantum walk approach for the welded tree problem.
A welded tree graph consists of two balanced binary trees of height with roots and and a random cycle that alternates between the leaves of the two binary trees. The number of vertices in is and the names of the vertices are randomly assigned from the set . To access the neighbors of a particular vertex, we use an adjacency list oracle denoted as for the graph . Given a -bit string , the adjacency list oracle provides the neighboring vertices of , or it returns if is not a valid vertex name in the graph.
Problem 2.1 (The welded tree problem).
Given an adjacency list oracle of the welded tree and the name of the starting vertex , the goal is to output the name of the other root .
Let be the adjacency matrix of a graph , be a real number, and as the initial input state, the continuous-time quantum walk is defined as
Lemma 2.2 (Theorem 3 in [4]).
Let be the adjacency matrix of the welded tree graph . With the adjacency list oracle of the welded tree , the name of the starting vertex and let , running the continuous quantum walk for a time chosen uniformly in and then measuring on the computational basis yields a probability of finding the name of the other root vertex that is greater than .
By querying the adjacency list oracle of a given vertex, one can determine whether it has a degree of or not. Since only two vertices, and , have a degree of in the welded tree , repeating the quantum algorithm multiple times can find the other root in poly() time. On the other hand, no classical algorithm can solve the welded tree problem in subexponential time by the following Lemma 2.3.
Lemma 2.3 (Theorem 9 in [4]).
For the welded tree problem, any classical algorithm that makes at most queries to the oracle finds the ending vertex or a cycle with probability at most .
Note that the exact statement of Theorem 9 in [4] does not mention finding a cycle while the proof in their classical lower bound result holds for this case.
3 The pathfinding problem and the quantum algorithm
In this section, we construct a graph based on welded trees and provide an efficient quantum algorithm that outputs an - path. The key idea is to construct the graph associating an - path of length with distinct welded trees. The quantum algorithm finds the - path step by step. For each step, we use the quantum algorithm for the welded tree problem [4] to detect and select the edge that is in the path . Then we remove the selected edge and update the starting vertex . Repeat until and output all selected edges as an - path.
Without loss of generality, assume that is an even positive integer. Given disjoint welded trees with roots and , the graph is constructed as follows:
-
1.
For each , adding new isolated edges , then adding new edges between and vertices such that the root vertex has degree .
-
2.
Given a path graph with vertices , for each , add an edge between and .
-
3.
Adding a random cycle between all vertices for each and . Denote the resulting graph as .
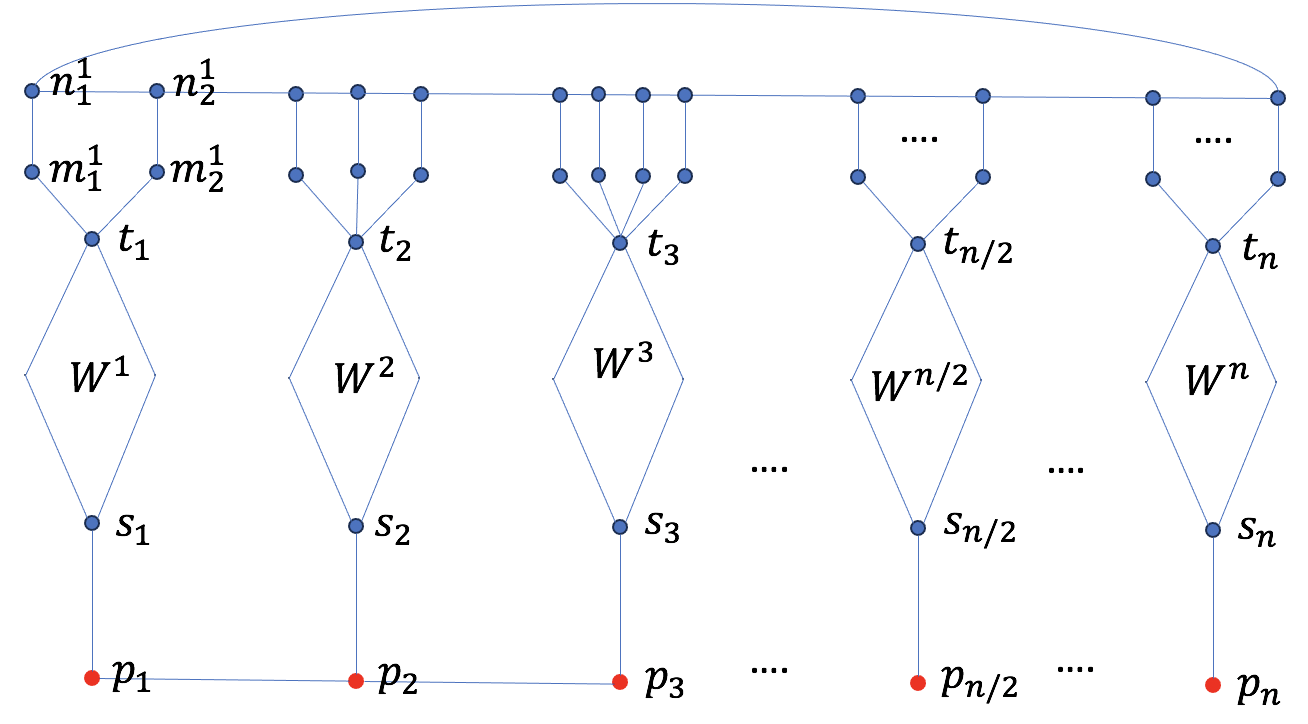
Let be the starting vertex, be the ending vertex, and given the names of and , the goal is to find an - path in the graph .
Problem 3.1 (Pathfinding problem).
Given the adjacency list oracle of the graph and the name of the starting, ending vertices , the goal is to output an - path in .
-
1.
Given the name of the vertex , the adjacency list oracle returns the names of the two neighbors of , that is . Without loss of generality, pick one of the two neighbors as the initial state .
-
2.
Let be the modified adjacency matrix of the adjacency matrix of by removing all the edges adjacent to a degree vertex. Let be except it returns no edge if one endpoint of the edge is a degree vertex. Run the continuous quantum walk for a uniform random time . Measure the resulting state in the computational basis and get the name of an outcome vertex . Compute the degree of the vertex by querying the adjacency list oracle of .
-
3.
Repeat Step 2 times or until the degree of the measured vertex equals .
-
4.
If the degree of the measured vertex equals , then collect the edge as an - path edge and let . Otherwise, collect the edge as an - path edge and let .
-
5.
Let i=i+1 and update the graph by deleting the selected edge. Repeat all the above steps until , then output all the selected edges as an - path.
Theorem 3.2.
With high probability, Algorithm 1 outputs an - path in poly() time.
Proof.
For the -th iteration, the key subroutine is to implement the continuous quantum walk for in Step 2. The adjacency list oracle can be performed by removing all edges adjacent to a degree vertex from the adjacency list oracle . Then use the adjacency list oracle to construct a block encoding of the modified adjacency matrix . With this block encoding, we can perform the Hamiltonian simulation in poly() time by implementing polynomials of [33, Theorem 58].
Recall that the only vertex that has degree is the root of the welded tree in the graph . If is the same as the root vertex of the welded tree , then by Lemma 2.2, the success probability of measuring a vertex of degree is . The probability of success is by repeating Step 2 times. Otherwise, the probability of measuring a vertex of degree is . This is true because the initial starting vertex is disconnected from the welded tree and connected to the welded trees in the modified graph associated with the adjacency list oracle . Therefore, for each iteration, Algorithm 1 outputs an edge of the - path with probability in poly() time.
Remark 3.3.
The random cycle at the top of the graph is not strictly necessary for showing the exponential quantum-classical separation for the pathfinding problem. Instead, it serves to illustrate the exponential separation persists when there are multiple - paths, highlighting the robustness of the quantum advantage in more complex graph structures.
4 Classical Lower bound
In this section, we prove that no classical randomized algorithm can solve the pathfinding problem 3.1 in the welded tree path graph within subexponential time. Our approach is inspired by the classical lower bound established for the welded (glued) tree graph in [4], which demonstrates an exponential quantum-classical separation for finding a marked vertex. We adapt their techniques to address the classical lower bound for the pathfinding problem.
Intuitively, the pathfinding problem can be seen as a generalization of the vertex-finding problem, as it requires identifying a sequence of vertices that form an - path. To establish a classical lower bound for the pathfinding problem, we demonstrate that no classical algorithm can efficiently identify certain critical vertices along - paths of the constructed welded tree path graph . By the construction of the graph , we define the set of critical vertices as and the vertices with degrees of at least , specifically .
First, by assigning a random -bits string to each vertex in the graph , any classical algorithm to solve the pathfinding problem with at most queries of must traverse connected subgraphs with starting vertices or . The reason is as follows: the total number of vertices in the graph is while the total number of potential vertex names is . If makes at most queries, the probability of querying the name of a vertex that has not been previously returned by the oracle is at most
Thus, it is unlikely that can guess a name of vertices of the graph that is not returned by the oracle when making at most queries. Without loss of generality, in the rest of the section, we restrict to traverse two connected subgraphs starting with vertices and , respectively.
Under these conditions, solving the pathfinding problem with at most queries of the adjacency list oracle is equivalent to playing the following game.
Game A The oracle assigns each vertex of a randomly chosen graph a distinct -bit string as its name. The starting vertex has the name and the ending vertex has the name . At each step, sends a -bit string to , and the oracle returns the names of the neighbors of that vertex if the given vertex name is valid. wins if it outputs the names of the vertices forming an - path.
To bound on the success probability of winning Game A, we consider a simpler Game B, which relaxes the winning conditions. In Game B, wins by outputting the name of any critical vertex, such as or the vertex or a cycle while winning Game A needs to output names of an - paths.
Game B Let Game B be the same as Game A, except that wins if it outputs the name of any vertex of degree at least , i.e., or the name of the vertex , or a cycle among the vertices visited by .
To prove the classical lower bound for the pathfinding problem, it suffices to show that cannot win this easier Game B in subexponential time. Following [4], the condition that allows to win by finding a cycle in Game B simplifies the analysis. One key concept in [4] is the random embedding of a rooted binary tree. To analyze the success probability of in Game B, we restate the defintion of a random embedding of a rooted binary tree as follows:
Definition 4.1 (Random embedding of a rooted binary tree).
Given the name of the starting vertex , the random embedding of a rooted binary tree into the graph is defined as a function from the vertices of to the vertices of such that
-
1.
.
-
2.
Let and be the two neighbors of in and let and be the neighbors of in . With probability set and , and with probability set and .
-
3.
For any non-leaf vertex in , let and denote the children of vertex , and let denote the parent of vertex . Let and be the two neighbors of in other than . With probability set and , and with probability set and .
We say that an embedding is proper if it is injective, that is for any , we have if . We say that exits under if, for any , the degree of in is at least or is or .
Theorem 4.2.
If uses queries to the oracle , then its probability of finding an - path is at most .
Proof.
To obtain an upper bound of the probability of for solving the pathfinding problem, it suffices to show that the probability of finding the certain set of vertices, that is and vertices that have degrees at least , is at most .
-
1.
Given the name of the starting vertex , the upper bound of the probability of winning Game can be expressed as the probability that the embedding is improper or exits under using the result of [4, Equation 72, Lemma 7]. This comes from the fact that there exists an algorithm to generate a random rooted binary tree by simulating any classical algorithm for Game B.
Let be a random rooted binary tree with at most vertices and be the image in the graph under the random embedding . We have the following result:
-
(a)
First, it is unlikely that contains a vertex with degree at least , i.e., or a cycle. For the vertices and the cycles in can only be located by entering a welded tree graph. This is true because, as indicated in Figure 1, the vertices that have a degree at least are the roots , and the path with the welded trees form a tree structure. Lemma 2.3 shows that any classical algorithm that makes at most queries to the oracle can find a root or a cycle in a single welded tree graph with probability at most . Since there are welded trees and vertices of degree at least in the welded tree path graph , the union bound 111The union bound states that the probability of at least one event occurring is at most the sum of the probability of each event: . implies that the
-
(b)
The probability of contains the vertex is exponentially small. Consider a path in from the root to a leaf. To reach the vertex , must follow the path times, which has probability . Since there are at most tries on each path of and there are at most paths. The probability of finding the name of the vertex is at most , that is,
Therefore, by the union bound, given the name of the starting vertex , the probability of finding the vertex , a cycle, or a vertex of degree at least is at most .
-
(a)
-
2.
By symmetry structure of the welded tree path graph,, the same bound also holds when the only given name is the vertex .
Hence, given the names of and and by union bound, the probability of uses queries to the oracle to find a cycle, the vertex , or a vertex with a degree at least is at most . That is, cannot win Game A in subexponential time. ∎
5 Discussion
In this paper, we show that the pathfinding problem in the graph admits an exponential separation between quantum and classical algorithms under the adjacency list oracle. The key idea is to encode the path information into distinct welded trees, in which quantum algorithms can extract the path information efficiently by distinguishing the distinct welded trees but no classical algorithm can do this in polynomial time. In fact, there are more types of graphs to show an exponential separation of the pathfinding problem as long as they satisfy this property, for example, replacing the random cycle at the top of the graph with an arbitrary graph. Also, using the continuous quantum walk approach, [34] exhibits a superpolynomial quantum-classical separation to find a vertex in random hierarchy graphs. Therefore, we can also replace the welded trees with random hierarchy graphs to achieve quantum-classical separation for the pathfinding problem.
Moving forward, we provide several open problems related to the quantum advantages of pathfinding problems in more types of graphs that do not have the properties used in this paper.
-
•
The welded tree path graph we constructed in our paper is not regular, which is the structure that our quantum algorithm exploits to run efficiently. However, isogeny graphs, such as the Cayley graph and supersingular graphs, are examples of regular graphs. It would be intriguing to explore whether there exist regular graphs that exhibit exponential separations between quantum and classical algorithms.
-
•
In addition to achieving exponential speedups, exploring and characterizing polynomial speedups of quantum algorithms for the pathfinding problem in various types of graphs is a promising and exciting future direction.
Acknowledgements
J.L. would like to thank Sean Hallgren, Andrew Childs, Yi-Kai Liu, Daochen Wang, Sebastian Zur and Guanzhong Li for their valuable feedback and conversations and Mingming Chen for assistance in drawing the figure. Part of this work was done while the author visited Quantum Information and Computer Science (QuICS) and the Simons Institute for the Theory of Computing. J.L. acknowledges funding from the National Science Foundation awards CCF-1618287, CNS-1617802, and CCF-1617710, and a Vannevar Bush Faculty Fellowship from the US Department of Defense.
References
- [1] Daniel R. Simon. On the power of quantum computation. SIAM Journal on Computing, 26(5):1474–1483, 1997. Earlier version in FOCS’94.
- [2] Peter W. Shor. Polynomial-time algorithms for prime factorization and discrete logarithms on a quantum computer. SIAM Journal on Computing, 26(5):1484–1509, 1997. Earlier version in FOCS’94. arXiv: quant-ph/9508027
- [3] Sean Hallgren. Polynomial-time quantum algorithms for pell’s equation and the principal ideal problem. Journal of the ACM (JACM), 54(1):1--19, 2007.
- [4] Andrew M. Childs, Richard Cleve, Enrico Deotto, Edward Farhi, Sam Gutmann, and Daniel A. Spielman. Exponential algorithmic speedup by a quantum walk. In Proceedings of the 35th ACM Symposium on the Theory of Computing (STOC), pages 59--68, 2003. arXiv: quant-ph/0209131
- [5] Shalev Ben-David, Andrew M. Childs, András Gilyén, William Kretschmer, Supartha Podder, and Daochen Wang. Symmetries, graph properties, and quantum speedups. In Proceedings of the 61st IEEE Symposium on Foundations of Computer Science (FOCS), pages 649--660, 2020. arXiv: 2006.12760
- [6] Ewin Tang. A quantum-inspired classical algorithm for recommendation systems. In Proceedings of the 51st ACM Symposium on the Theory of Computing (STOC), pages 217--228, 2019. arXiv: 1807.04271
- [7] Ewin Tang. Quantum principal component analysis only achieves an exponential speedup because of its state preparation assumptions. Physical Review Letters, 127(6):060503, 2021. arXiv: 1811.00414
- [8] Nai-Hui Chia, András Gilyén, Tongyang Li, Han-Hsuan Lin, Ewin Tang, and Chunhao Wang. Sampling-based sublinear low-rank matrix arithmetic framework for dequantizing quantum machine learning. In Proceedings of the 52nd ACM Symposium on the Theory of Computing (STOC), page 387–400, 2020. arXiv: 1910.06151
- [9] Yu-Ao Chen and Xiao-Shan Gao. Quantum algorithm for boolean equation solving and quantum algebraic attack on cryptosystems. Journal of Systems Science and Complexity, 35(1):373--412, 2022.
- [10] Jintai Ding, Vlad Gheorghiu, András Gilyén, Sean Hallgren, and Jianqiang Li. Limitations of the macaulay matrix approach for using the hhl algorithm to solve multivariate polynomial systems. Quantum, 7:1069, 2023.
- [11] Aram W. Harrow, Avinatan Hassidim, and Seth Lloyd. Quantum algorithm for linear systems of equations. Physical Review Letters, 103, 10 2009.
- [12] Scott Aaronson. Open problems related to quantum query complexity. ACM Transactions on Quantum Computing, 2(4):1--9, 2021.
- [13] Andrew M. Childs, Matthew Coudron, and Amin Shiraz Gilani. Quantum Algorithms and the Power of Forgetting. In 14th Innovations in Theoretical Computer Science Conference (ITCS 2023), volume 251, pages 37:1--37:22, 2023.
- [14] Kirsten Eisenträger, Sean Hallgren, Chris Leonardi, Travis Morrison, and Jennifer Park. Computing endomorphism rings of supersingular elliptic curves and connections to path-finding in isogeny graphs. Open Book Series, 4(1):215--232, 2020.
- [15] Denis X. Charles, Kristin E. Lauter, and Eyal Z. Goren. Cryptographic hash functions from expander graphs. Journal of Cryptology, 22:93--113, 1 2009.
- [16] Anamaria Costache, Brooke Feigon, Kristin Lauter, Maike Massierer, and Anna Puskás. Ramanujan graphs in cryptography, 2018.
- [17] Benjamin Wesolowski. The supersingular isogeny path and endomorphism ring problems are equivalent. In 2021 IEEE 62nd Annual Symposium on Foundations of Computer Science (FOCS), pages 1100--1111. IEEE, 2022.
- [18] Samuel Jaques and John M Schanck. Quantum cryptanalysis in the ram model: Claw-finding attacks on sike. In Annual International Cryptology Conference, pages 32--61. Springer, 2019.
- [19] Seiichiro Tani. Claw finding algorithms using quantum walk. Theoretical Computer Science, 410(50):5285--5297, 2009.
- [20] Wouter Castryck and Thomas Decru. An efficient key recovery attack on sidh. In Annual International Conference on the Theory and Applications of Cryptographic Techniques, pages 423--447. Springer, 2023.
- [21] Sarah Arpin, Mingjie Chen, Kristin E Lauter, Renate Scheidler, Katherine E Stange, and Ha TN Tran. Orientations and cycles in supersingular isogeny graphs. In Research Directions in Number Theory: Women in Numbers V, pages 25--86. Springer, 2024.
- [22] Wouter Castryck, Tanja Lange, Chloe Martindale, Lorenz Panny, and Joost Renes. Csidh: an efficient post-quantum commutative group action. In Advances in Cryptology--ASIACRYPT 2018: 24th International Conference on the Theory and Application of Cryptology and Information Security, Brisbane, QLD, Australia, December 2--6, 2018, Proceedings, Part III 24, pages 395--427. Springer, 2018.
- [23] Steven Galbraith. Breaking supersingular isogeny diffie-hellman (sidh), Aug 2022.
- [24] Christoph Dürr, Mark Heiligman, Peter HOyer, and Mehdi Mhalla. Quantum query complexity of some graph problems. SIAM Journal on Computing, 35(6):1310--1328, 2006.
- [25] Stacey Jeffery, Shelby Kimmel, and Alvaro Piedrafita. Quantum algorithm for path-edge sampling. arXiv preprint arXiv:2303.03319, 2023.
- [26] Sean Hallgren and Jianqiang Li. Quantum algorithms for the pathfinding problem via the quantum electrical flow. Under preparation, 2023.
- [27] Daniel Reitzner, Mark Hillery, and Daniel Koch. Finding paths with quantum walks or quantum walking through a maze. Physical Review A, 96(3):032323, 2017.
- [28] Mark Hillery. Finding more than one path through a simple maze with a quantum walk. Journal of Physics A: Mathematical and Theoretical, 54(9):095301, 2021.
- [29] Daniel Koch and Mark Hillery. Finding paths in tree graphs with a quantum walk. Physical Review A, 97(1):012308, 2018.
- [30] Stacey Jeffery and Sebastian Zur. Multidimensional quantum walks. In Proceedings of the 55th Annual ACM Symposium on Theory of Computing, pages 1125--1130, 2023.
- [31] Guanzhong Li, Jingquan Luo, and Lvzhou Li. Recover the original simplicity: concise and deterministic quantum algorithm for the welded tree problem. arXiv preprint arXiv:2304.08395, 2023.
- [32] Ryan Babbush, Dominic W Berry, Robin Kothari, Rolando D Somma, and Nathan Wiebe. Exponential quantum speedup in simulating coupled classical oscillators. arXiv preprint arXiv:2303.13012, 2023.
- [33] András Gilyén, Yuan Su, Guang Hao Low, and Nathan Wiebe. Quantum singular value transformation and beyond: exponential improvements for quantum matrix arithmetics. arXiv preprint arXiv:1806.01838, 2018.
- [34] Shankar Balasubramanian, Tongyang Li, and Aram Harrow. Exponential speedups for quantum walks in random hierarchical graphs. arXiv preprint arXiv:2307.15062, 2023.