Folding One Polyhedral Metric Graph into Another
Abstract
We analyze the problem of folding one polyhedron, viewed as a metric graph of its edges, into the shape of another, similar to 1D origami. We find such foldings between all pairs of Platonic solids and prove corresponding lower bounds, establishing the optimal scale factor when restricted to integers. Further, we establish that our folding problem is also NP-hard, even if the source graph is a tree. It turns out that the problem is hard to approximate, as we obtain NP-hardness even for determining the existence of a scale factor . Finally, we prove that, in general, the optimal scale factor has to be rational. This insight then immediately results in NP membership. In turn, verifying whether a given scale factor is indeed the smallest possible, requires two independent calls to an NP oracle, rendering the problem DP-complete.
1 Introduction
Viewing a polyhedron as a metric graph (graph with specified edge lengths), when can we fold it into another polyhedron, in the sense of 1D origami [4] where lengths must be preserved and we view multiple overlapping layers as one? More formally:
Problem 1 (IsoCovering).
Given two metric spaces and , find an isometric covering of by , that is, a surjective map such that, for every path in , the arc length of in equals the arc length of in .
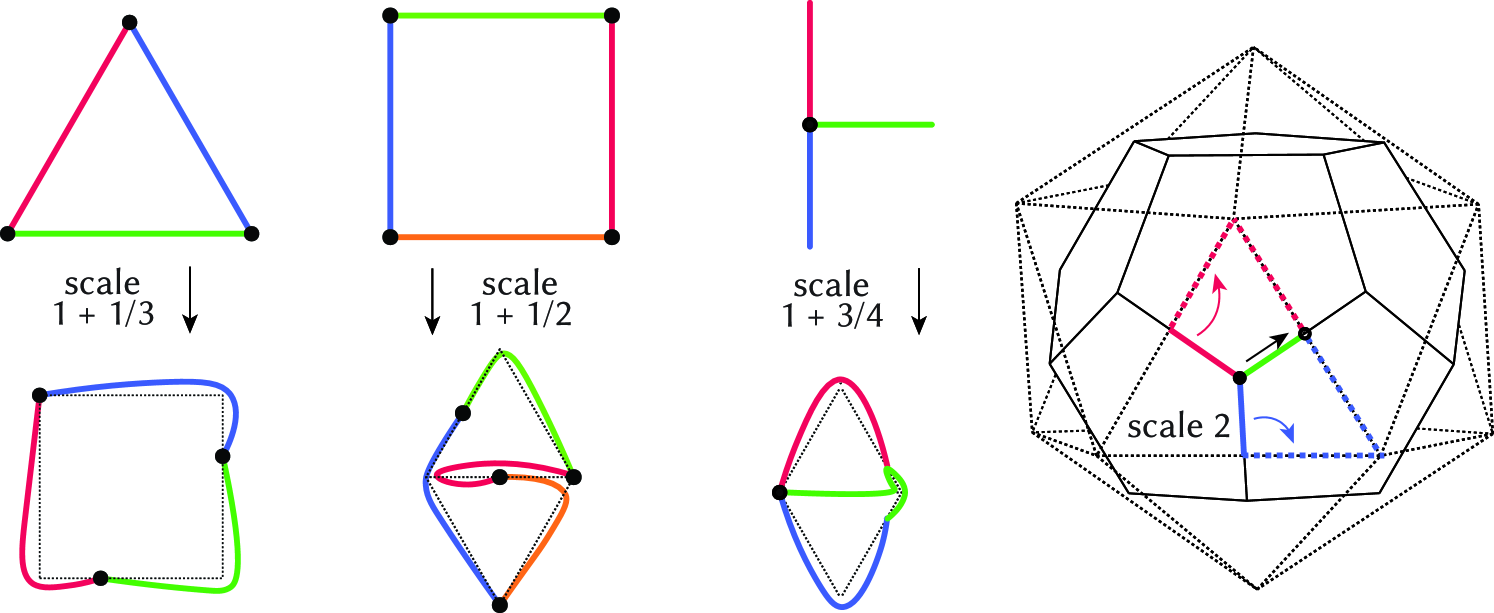
Figure 1 shows simple examples. To ensure that this is always possible, we can scale the lengths in by a constant scale factor (in Figure 1, scale factors are given for unit edge lengths). The required scale factor between source and target shape is also the primary concern in computational origami design [4].
We aim to compute the minimum possible scale factor. This leads to the decision problem of verifying whether a given scale factor is possible as well as the following optimization problem.
Problem 2 (Optimization).
Given graphs and , minimize such that scaled by has an isometric covering from .
Some well-known problems can be cast into this framework. When the source graph is a path or a cycle, this problem is exactly the Chinese postman tour problem: what is the shortest cycle that visits every edge at least once? This problem, and thus optimal scale factors in this case, can be computed in polynomial time [5]. Notably, folding cycles like this are commonly studied in the context of 1D origami [3, Chapters 12].
1.1 Our Results
First, we consider foldings of every Platonic solid into every other, proving many upper bounds (Section 2) and lower bounds (Section 3) on the optimal scale factor . Table 1 summarizes these results, which are tight if we artificially restrict to integral scale factor.
Next, we analyze the complexity of the general problem. We prove that IsoCovering is NP-hard and that the optimization problem is hard to approximate within some constant factor (Section 4). We prove that the optimal scale factor is always rational (Section 5), which immediately gives rise to NP membership. We also show DP-completeness of verifying that a given scale factor is the optimal (Section 5.1). We conclude with open problems in Section 6.
| Tetrahedron | Cube | Octahedron | Dodecahedron | Icosahedron | |
|---|---|---|---|---|---|
| Tetrahedron | [1, 1] | [2+1/3, 2+5/6] | (2, 2+1/2] | [6+1/3, 6+5/6] | (5+2/3, 5+7/8] |
| Cube | (1/2, 5/6] | [1, 1] | (1, 1+1/2] | [3, 3] | (2+2/3, 3] |
| Octahedron | (1/2, 1] | (1+1/12, 1+1/2] | [1, 1] | (3+1/12, 4] | (2+1/2, 3] |
| Dodecahedron | (1/5, 3/5] | (2/5, 4/5] | (2/5, 3/4] | [1, 1] | (1, 1+1/3] |
| Icosahedron | (1/5, 1] | (1*, 1+1/3] | (2/5, 1] | (1+2/15, 2] | [1, 1] |
2 Platonic Upper Bounds (Foldings)
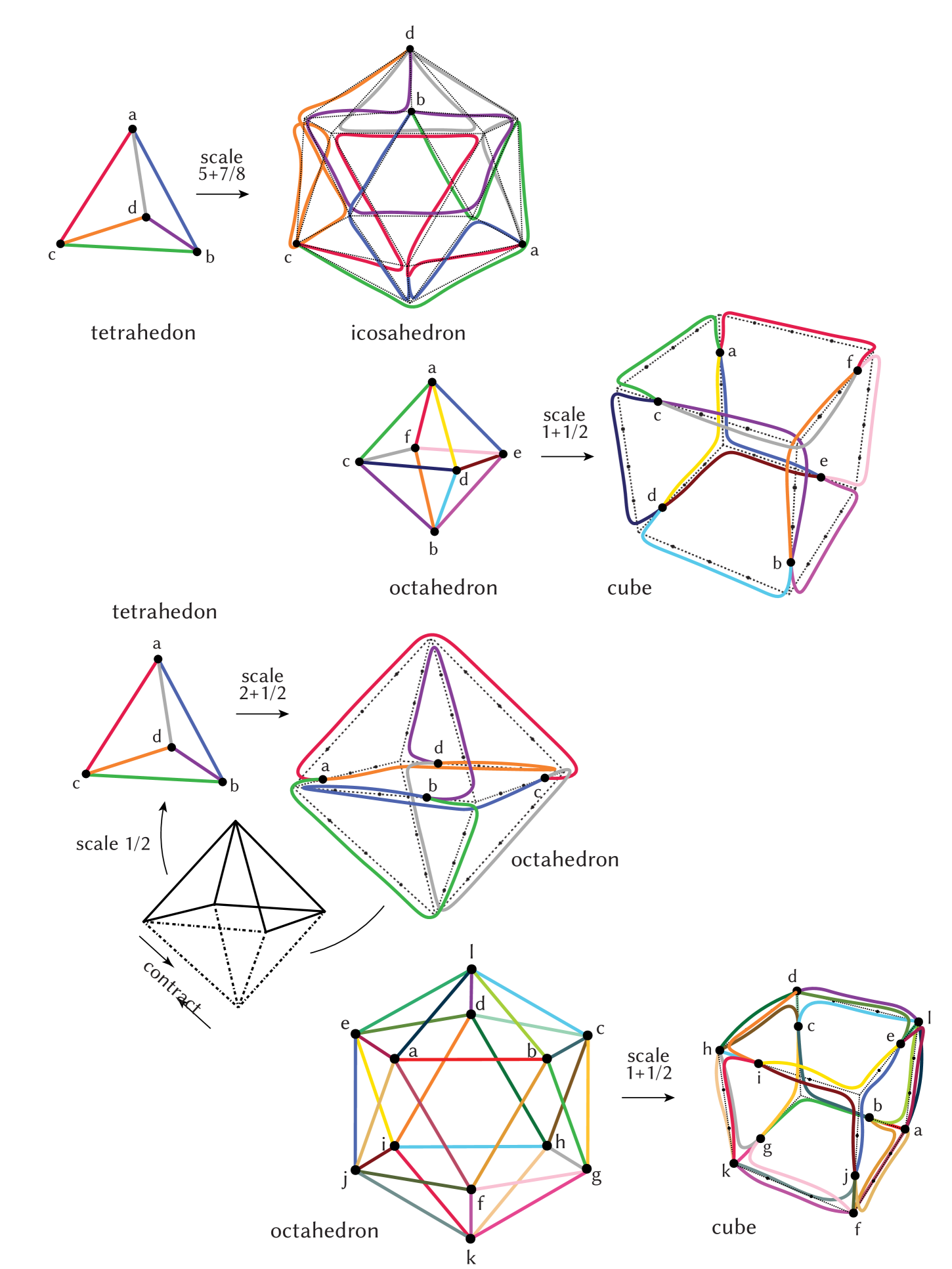
To achieve the upper bounds reported in Table 1, we developed initial solutions by observing inscriptions of one polyhedron in another (Figure 1 (right)), and then further optimized these solutions through manual rerouting and automated search. For the latter, we combined two brute-force paradigms—logic programming and integer linear programming—along with local improvement techniques.
2.1 Automated Upper Bounds
For obtaining upper bounds, we use two different computing techniques. First, we will discuss an approach based on logic programming, which inherits concepts from propositional satisfiability (SAT) with direct language supports for transitive closure (reachability). Then, we briefly present an integer linear program. At the end of this section, we describe our approach of combining both technologies in the form of a local improvement.
2.1.1 Integer Scales
Modern SAT-based search engines [6] provide an efficient tool for searching for solutions to combinatorial problems. The advantage of these solvers is that they are based on non-chronological backtracking, thereby using sophisticated heuristics to efficiently traverse and cut the search space. With the help of sophisticated conflict analysis, the idea is to learn from unsuccessful branches of the search tree, with the goal of avoiding (short-cutting) similar conflicts in the future.
We design an encoding to utilize a SAT-based logic programming solver, called clingo [7], which is particularly focused on efficiently evaluating transitive closure properties by lazily adding constraints during solving. While we do not expect to fully solve optimization problems in general, in practice we can use our encoding to efficiently compute solutions of decent quality.
However, as this method is SAT-based it translates to Boolean variables. Consequently, we cannot expect arbitrarily large precision, but we can aim for integer or limited rational scale factors. These approaches still work well for quickly obtaining decent solutions that then serve as a basis for further optimization. Let be the source graph and be the target graph. While we do not care about the direction of edges, we assume both graphs to be directed (any fixed edge orientation), simplifying the encoding.
Note that we extend this encoding to capture limited rational scale factors. However, it works similarly and was skipped for the sake of presentation. There, we subdivide target edges (which then still allows us to map source vertices only to target vertices) and consider these subdivisions when computing the scale factor.
2.1.2 Rational Scales via ILP
In the following we discuss an integer linear program (ILP). To this end let be the source graph and be the target graph. Further, we assume to be a modification of target , where each edge in is subdivided using up to intermediate auxiliary vertices. These auxiliary vertices allow us to position source vertices on edge positions and are positioned between 0 () and 1 (). For every target edge , we assume a predecessor relation among the vertices in on obtained after subdividing. Without loss of generality, we assume that edges in are directed, based on this ordering, i.e. edges go from -lower to -higher vertices. Let be a chosen scale factor upper bound constant.
In the encoding, we use the following variables:
| directed flow | ||||
| directed edge decision | ||||
| src mapping | ||||
| aux position | ||||
| src reachability | ||||
| directed edge length | ||||
| objective | ||||
For every , we then generate the following ILP:
| edge/flow rel. | ||||
| edge/reach rel. | ||||
| edge/length rel. | ||||
| degree constr. | ||||
| edges covered | ||||
2.1.3 Local Improvement of Limited Rational Scales
For computing and improving upper bounds among platonic solids (as presented in Table 1 works as follows. First, using the approach discussed in Section 2.1.1, we obtain initial mappings with integer or limited rational scale factors. These mappings are then relaxed, where we allow a shift of source vertices mapped onto target vertices or edges. The goal is then to use the approach of Section 2.1.2 to optimize those shifts such that the resulting solution is better or at least only slightly worse. We then iteratively try to keep parts of a solution that is then optimized and completed with the presented encoding. Whenever we obtain a new solution we keep parts of it for the next iteration, assuming the quality improved or only slightly worsened.
3 Lower Bounds
For any pair of polyhedra, a naïve lower bound on the optimal scale factor is immediate: every target edge needs to be covered by a source edge, thus . We significantly improve this lower bound with the following observations:
-
•
Each source vertex is mapped to either a vertex or a point along an edge of the target;
-
•
Each source edge is routed to a path in the target;
-
•
The scale factor is the maximum length of the routed target paths.
Let be the number of vertices in the source graph, and let be the number of vertices of odd degree in the target. The following result forms the basis of our lower bounds:
Lemma 1.
Every target edge not containing a source vertex is either covered (1) by one or more paths going straight along the complete edge, or (2) by two doubling-back paths that meet at a point (doubling the entire target edge).
Proof.
If there is at least one path going straight along the complete edge, then it is never helpful to have a doubling-back path: such a doubling-back can be shortcut to just never enter the edge. ∎
We obtain the following based on doubly covering edges.
Lemma 2.
In any solution, at least target edges must be fully doubly covered. If at least one source vertex is placed in the middle of a target edge, this bound is strict.
Proof.
Locally at an odd-degree vertex of the target graph, if does not have a vertex of the source graph at it, then is visited by a sequence of paths that enter and leave. Because has odd degree, there must be a local doubling along an edge incident to . If this doubling continues fully along the edge then we get one doubled edge for two (potentially) odd-degree vertices, matching the bound of .
Now suppose the doubling does not continue fully along the edge . If there are no source vertices along edge then by Lemma 1, the edge has two meeting doubling paths, which doubles the entire edge, and again we are done. So suppose there is a source vertex along edge . If there are at least two outgoing paths in each direction from , then again, the edge is fully doubled, so provided no benefit. Otherwise, there is at most one outgoing path in some direction, say . Then locally acts the same as if were not there, so it must have an incident doubling not on the edge (i.e., not toward so the argument above applies. The other vertex no longer necessarily has an incident wholly doubled edge, but this matches the “” in the bound. Note: if there are two source vertices along the same edge then both endpoints potentially have no incident wholly doubled edge. But this again matches the “” in the bound (there are two source vertices to charge to).
If at least one source vertex is in the middle of a target edge, then the above bound becomes strict. In this case, we get a doubled partial edge beyond the bound (on the side so we have strictly more doubling and get a strictly large bound. ∎
This yields the following adapted lower bound.
Theorem 1 (Improved Lower Bound).
|
Tetrahedron
(, perim) |
Cube
(, perim) |
Octahedron
(, perim) |
Dodecahedron
(, perim) |
Icosahedron
(, perim) |
||
|---|---|---|---|---|---|---|
|
Tetrahedron
|
(, perim) | 1 | ||||
| Cube | (, perim) | 1 | ||||
| Octahedron | (, perim) | 1 | ||||
| Dodecahedron | (, perim) | 1 | ||||
| Icosahedron | (, perim) | 1 |
Table 2 details computation steps to obtain the lower bounds given in Table 1. Bounds are strict according to Lemma 2 and by the observation that mapping between vertices of different degrees (or from larger to smaller degree vertices) causes doubly covered edge parts. If mapping from icosahedron to cube, we obtain the following stronger lower bound.
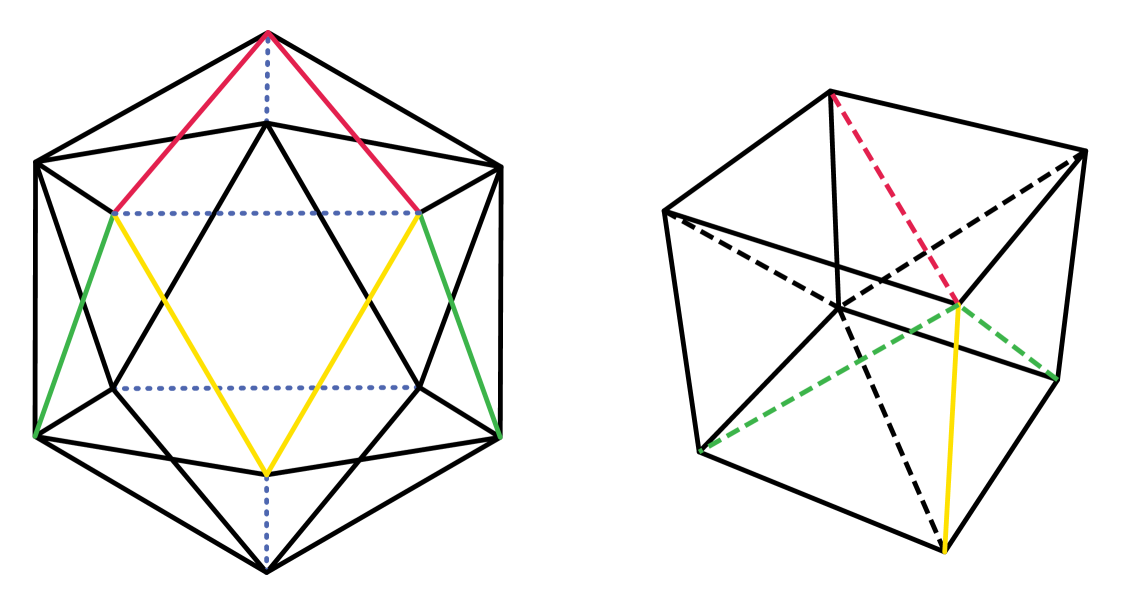
Theorem 2.
There cannot exist an isometric covering from icosahedron to cube.
Proof.
By contracting four edges (highlighted in color in Figure 3 (left)), we obtain a cube (right) with additional diagonals. By contracting edges, we simplified the source linkage by assigning certain source vertices to the same position. Therefore, lower bounds are preserved using the simplified source. Note that a cube without diagonals can never provide the same connectivity as a cube. Therefore, we need additional scaling, as certain edges of the source linkage can never be represented in the target linkage via an isometric covering. ∎
4 Hardness and Inapproximability
We show that deciding if one embedded (planar) graph can be mapped onto another via folding is NP-complete. Further deciding the scale factor needed to allow one planar graph to be mapped onto another cannot be approximated within a factor of for any constant .
Theorem 3 (Inapproximability).
Given two metric planar graphs , and scale factor , deciding whether can be folded onto via an isometric covering (scale factor ) is NP-complete. Further, the optimal scale factor OPT of mapping onto is NP-hard to approximate within a factor of .
Proof.
Membership immediately follows from utilizing an ILP that is presented in Section 2.1.2.
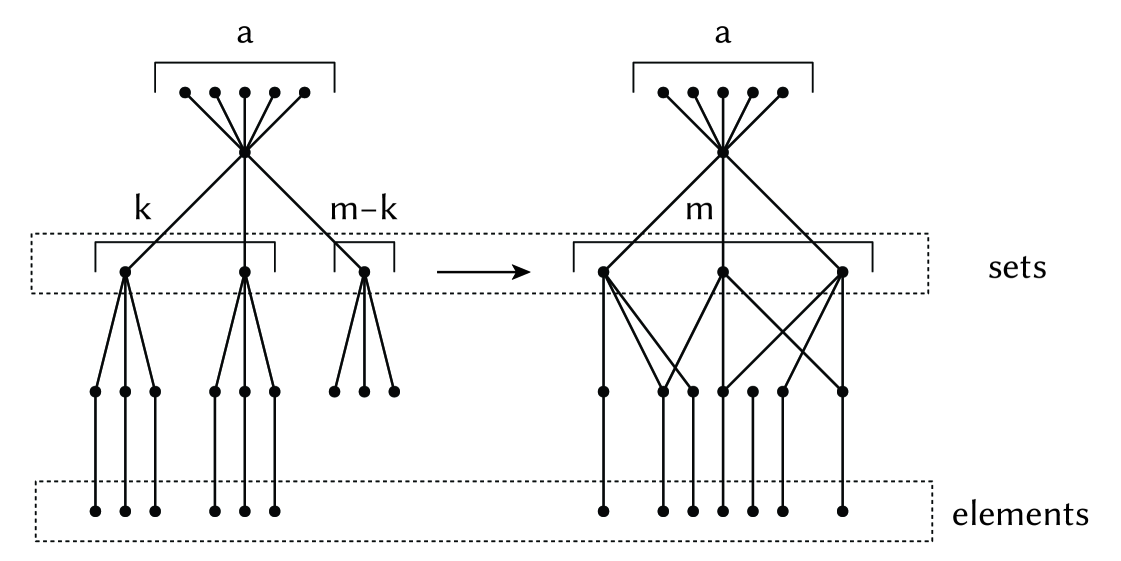
For hardness, we reduce from Planar Set Cover with sets of size exactly 3 [8]. Here we are given a set of elements and a collection of sets of three elements of . Further, if one constructs the bipartite graph with notes for elements of and and edges when , then that graph is planar. The question is whether there is a subset of size such that each element of is contained in .
In this construction, which is sketched in Figure 4, all edges are of length 1. For the target graph first construct a top node and one node for each set and connect them to the root. Also connect nodes to the root, which will help anchor the root node in the construction. Then, we construct a node for each element and connect it to the nodes representing sets containing that element. Finally, off of each , add an additional degree-1 node connected to it. This has a total of nodes and edges.
The initial graph is a tree. The root node has children. Of these children will be leaf nodes. Then children will each be connected to three length 2 paths which will be the intended to be used to solve the set cover of size . The other children will be connected to leaves and be used to cover the edges in the unused sets. This graph has nodes and edges.
In this construction, due to the leave nodes, a valid solution must map the root node to the top node.
If there is a valid solution to the set cover, take the subtrees of depth 3 and map them to the sets in the set cover solution. This will allow the paths of length 2 to cover the element nodes and their leaves. Next, use the remaining subtrees to cover all the unchosen set nodes and the edges of their elements.
If a solution to the set cover does not exist we will show there is no solution to the graph folding problem. First, note that all of the element leaves in the target are distance three from the top node and that these leaves are distance 4 from each other. Thus we know the leaves of the subtrees of depth 3 must be used to cover the leaves of the element nodes. These subtrees are distance 1 from the root and thus must either be mapped to the nodes (which then prevents them from covering element leaves) or to set nodes. The element leaves in a set are of distance 2 from the node containing them and thus can be covered by the leaves of a subtree mapped to that set node. However, all leaves of the elements not contained in that set are of distance at least 4 and thus cannot be covered. Thus, if there is no set cover of size , some of the element leaves will be impossible to cover in the graph folding. ∎
For establishing also membership in NP, we rely on the insights from the next section.
5 The Optimum is Rational
It turns out that the best scale factor is guaranteed to be rational, which we prove as follows.
Theorem 4.
Given graphs and , the optimal scale such that can be folded onto via isometric covering is rational.
Proof.
We will prove the result by designing an ILP, where we can compute all (exponential) possibilities for binary variable assignments. After assigning these integer variables, we invoke the remaining LP. This LP only has rational coefficients, so the optimal solution will be rational [1, 9, 2]. Consequently, optimal scale factors are rational.
Recall the ILP encoding from Section 2.1.2, as well as scale factor upper bound , source graph , target graph and that is obtained from after subdividing. After fixing integer variables, the following variables remain:
| directed flow | ||||
| aux position | ||||
| directed edge length | ||||
| objective | ||||
Then, if some of the constraints containing integer variables are not satisfied, we can stop. For the remainder, we are left with the following non-integer constraints, constructed for every , as the remaining integer variables are fixed constants:
5.1 Complexity Consequences
This insight results in NP membership for verifying a given scale factor.
Corollary 1.
Given two graphs , , and a scale factor , deciding whether scaled by can be folded onto via an isometric covering is in NP.
Proof.
The NP algorithm is given in the proof of Theorem 4. ∎
Therefore we can use binary search with logarithmic many calls to an NP oracle to compute the optimum. Verifying the optimality of a given scale factor is complete for complexity class .
Theorem 5.
Given graphs , , and a scale factor , it is DP-complete to decide whether is the smallest scale factor to enable isometric covering of folding onto .
Proof.
Verifying that is a valid scale factor is in NP by Corollary 1. Deciding whether there is a strictly smaller scale factor is in NP, so verifying the nonexistence of such a scale factor is in coNP. Because both can be verified independently, the problem is in DP.
Hardness follows by applying the construction of Theorem 3 two times. We reduce from a tuple comprising the NP-hard problem Planar Set Cover and the coNP-hard coproblem Planar Set Uncover . For , we use the same approach as in Figure 4, where we have a scale factor in case is a no-instance. For , we still use this approach, but with a different large-degree (to distinguish from ) and where we replace every edge of the source tree by a path comprising edges and every edge of the target tree by a path of edges.
Consequently, the ideal scale factor for (if it is a yes instance) would be instead of . Otherwise (in case of a no-instance), the scale would be , which is, however, larger than . As a result, if we manage a combined scale factor of , we know that is a yes-instance (as the factor is smaller than ). Further, if we do not manage combined scale factor , is a no-instance (as desired). ∎
6 Open Problems
The next steps include tightening the bounds in Table 1 and developing heuristics for folding general polyhedra. We would also like to strengthen the hardness proof to apply to polyhedral graphs, which requires more connectivity than our current construction. Finally, it would be interesting to develop solutions that permit continuous folding motions, which are required in the case of rigid polyhedral linkages.
References
- [1] B. Aspvall and R. E. Stone. Khachiyan’s Linear Programming Algorithm. J. Algorithms, 1(1):1–13, 1980.
- [2] Dandelion. Linear programming restricted to rational coefficients. https://cs.stackexchange.com/questions/82086/linear-programming-restricted-to-rational-coefficients, 2019 (accessed Nov 03, 2024).
- [3] E. D. Demaine and J. O’Rourke. Geometric folding algorithms - linkages, origami, polyhedra. Cambridge University Press, 2007.
- [4] E. D. Demaine and J. O’Rourke. Geometric Folding Algorithms: Linkages, Origami, Polyhedra. Cambridge University Press, 2007.
- [5] J. Edmonds and E. L. Johnson. Matching, Euler tours and the Chinese postman. Math. Program., 5(1):88–124, 1973.
- [6] J. K. Fichte, D. L. Berre, M. Hecher, and S. Szeider. The Silent (R)evolution of SAT. Commun. ACM, 66(6):64–72, 2023.
- [7] M. Gebser, R. Kaminski, B. Kaufmann, and T. Schaub. Multi-shot ASP solving with clingo. Theory Pract. Log. Program., 19(1):27–82, 2019.
- [8] D. Lichtenstein. Planar formulae and their uses. SIAM journal on computing, 11(2):329–343, 1982.
- [9] N. Megiddo. Towards a Genuinely Polynomial Algorithm for Linear Programming. SIAM J. Comput., 12(2):347–353, 1983.