Hybrid Resource Scheduling for Aggregation in Massive Machine-type Communication Networks
Abstract
Data aggregation is a promising approach to enable massive machine-type communication (mMTC). Here, we first characterize the aggregation phase where a massive number of machine-type devices transmits to their respective aggregator. By using non-orthogonal multiple access (NOMA), we present a hybrid access scheme where several machine-type devices (MTDs) share the same orthogonal channel. Then, we assess the relaying phase where the aggregatted data is forwarded to the base station. The system performance is investigated in terms of average number of MTDs that are simultaneously served under imperfect successive interference cancellation (SIC) at the aggregator for two scheduling schemes, namely random resource scheduling (RRS) and channel-dependent resource scheduling (CRS), which is then used to assess the performance of data forwarding phase.
Index Terms:
data aggregation, mMTC, resource scheduling, NOMAI Introduction
Machine-type Communication (MTC) is an inherent part of the fifth generation (5G) cellular networks [1, 2], covering automatic data generation, exchange, processing and actuation that are the basis of intelligent machine networks. Such MTC networks are growing at an impressive rate and some predictions are pointing to 20 billion machine-type devices (MTDs) connected to wireless networks in 2023 and beyond [3]. Massive Machine-type Communication (mMTC) are envisaged to cope with that large number of, often low-complexity low-power, MTDs that are becoming part of wireless networks [4]. A survey on the requirements, technical challenges, and existing work on medium access control (MAC) layer protocols for supporting these new use cases, is presented in [5], while authors describe also the issues related to efficient, scalable, and fair channel access. In fact, different strategies have been proposed to provide more efficient access, e.g., access class barring [6], prioritized random access [7], backoff adjustment scheme [8], delay-estimation based random access [9], distributed queuing [10], data aggregation [2, 11]. Data aggregation consists in MTDs that organize themselves locally to MTC area networks, then, the area networks connect to the core network through MTC gateways or data aggregators. This alleviates the problem of massive signaling overhead on the architectural side and it is a key solution strategy to collect, process, and communicate data in MTC use cases with static devices, especially if the locations of the devices are known, such as smart utility meters or video surveillance cameras [12, 4, 13].
In [14], authors survey data aggregation strategies in large-scale wireless sensor networks (WSNs), while focusing on the processing challenges behind the large volume of data. In [15], an experimental study using state-of-the-art drive testing equipment is conducted in order to capture and analyze the impact of MTC data aggregation on signaling overhead in cellular networks with focus on static MTDs such as smart meters and monitoring sensors. Authors of [16] present a scheme designed to provide data aggregation for heterogeneous and concurrent sets of Constrained Application Protocol [17] (CoAP) data-requests. The problem of energy-optimal routing and multiple-sink aggregation is investigated in [18], as well as joint aggregation and dissemination of sensor measurement data in MTC edge networks. An aggregation scheme is proposed in [11] for capillary networks connected to the LTE network to improve their communication efficiency. Authors analyze the trade-offs between random access interaction, resource allocation, and communication latency, and reveal that accepting the extra latency for accumulating packets can significantly reduce the random access requests and the required resources for the data transmissions.
Notice that when aggregating a massive number of MTDs, the density of the aggregators, although it is considerably smaller compared to the density of the MTDs, will still be large. Hence, the interference generated by the devices sharing the same resource is not negligible. There is, though, limited literature considering the interference in mMTC with data aggregation and resource scheduling. Authors in [19] partially address those issues by considering a multi-cell network scenario, whose key metrics (namely MTD success probability, average number of successful MTDs and probability of successful channel utilization) are investigated for the random resource scheduling (RRS) and channel-dependent resource scheduling (CRS) schemes.
Another technique called non-orthogonal multiple access (NOMA) is seen as a promising technology for the 5G networks to improve the system spectral efficiency while meeting the demand of massive connectivity demanded by certain MTC applications (e.g [20]). The key idea behind NOMA is to exploit the power domain for multiple access so that multiple users can be multiplexed at different power levels, but at the same time/frequency/code employing SIC to separate superimposed messages [21]. The performance of NOMA is evaluated in [22, 23] by using the stochastic geometry tools. However, the inter-cell interference, which is a pervasive problem in most of the existing wireless networks, is not explicitly considered in [22], as many other works on NOMA. In contrast, authors in [23] do consider the inter-cell interference when evaluating the performance of NOMA on coverage probability and average achievable rate, but on a downlink setup. In [24], we propose and analyze a hybrid OMA-NOMA scheme for mMTC uplink scenarios by extending the scheduling schemes RRS and CRS initially proposed in [19]. Therein we deal with the limited resources and allow up to two MTDs to share the same orthogonal channel while we consider imperfect SIC. We show that even when the hybrid scheme would lead to a less reliable system with greater chances of outages per MTD, due to the additional intra-cluster interference, it can significantly improve the number of simultaneous active MTDs for high access demand scenarios.
Differently from [24], in this work we allow the RRS scheme to control the power coefficients of the MTDs sharing the same channel, thus both, RRS and CRS, have the same impact in terms of interference generated on the outside network (network outside of the aggregation zone of interest). Additionally, here we are agnostic of the outside network topology, nonetheless our proposed model captures the interference coming from outside. We also include the evaluation of the relaying phase of the aggregated data to the base stations, while we focus on the average number of simultaneous active MTDs. That allow us to highlight the advantages of our scheme which aims to provide massive connectivity in scenarios with high access demand, which is not covered by usual OMA setups. Although CRS achieves better performance by providing access to the MTDs with best channels, RRS could be more practical since the random pairing could model scenarios where some MTDs have urgency to be served. Results show that failing to efficiently eliminate the intra-cluster interference could reduce significantly the benefits from NOMA while challenging its practical implementation, thus, power control plays a main role in these systems. Finally, we attain approximated, yet accurate, expressions when analyzing the CRS scheme. In contrast to the time-consuming Monte-Carlo simulations, our analytical derivations allow for fast computation.
Next, Section II introduces the system model. Section III discusses the RRS and CRS scheduling schemes for the aggregation phase, while Section IV analyses the relaying phase and the overall system performance. Section V presents the numerical results and Section VI concludes the paper.

Notation: denotes expectation, is the probability of event , is the conditioned on . is an indicator function which is equal to if its argument is true and otherwise; while . is the gamma function, is the digamma function, is the regularized incomplete gamma function, and is the Kummer confluent hypergeometric function. and is the imaginary part of . and are the Probability Density Function (PDF) and Cumulative Distribution Function (CDF) of random variable (RV) , respectively. is an exponential distributed RV with unit mean, e.g., and ; while is a Poisson distributed RV with mean , e.g., and .
II System Model and Assumptions
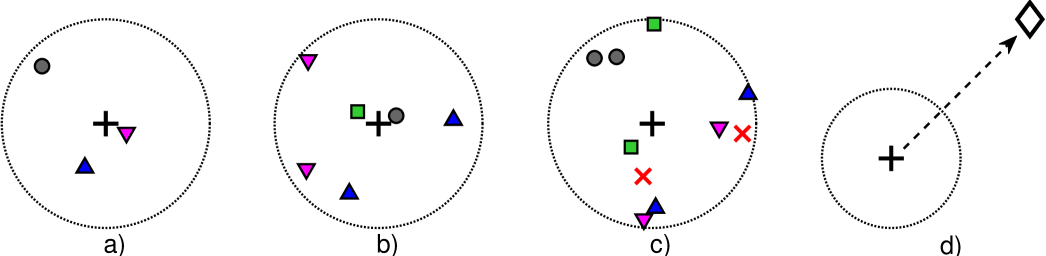
Consider interference-limited111The interference from other MTDs is much larger than the white noise in the receivers and, therefore, can be ignored. However, notice that the impact of the noise can be easily incorporated into our analysis. uplink of MTC network is divided into two phases. In the first phase (aggregation phase), the MTD tries to transmit its data with fixed payload size (bits) to its serving aggregator. The MTDs are served through orthogonal channels as in [19]; however, here the same orthogonal channel could be used for more than one MTD. When the access demand is not so high, the aggregator will be allocating one MTD per channel. But, when the access demand exceeds the availability of orthogonal channels, some MTDs are allowed to share the same orthogonal channel. This scheme is our proposed hybrid OMA-NOMA multiple access scenario [24]. The number of MTDs requiring service is modeled as . The maximum number of users per orthogonal channel is , where reduces to an OMA scenario, and for simplicity we focus on the setup. Furthermore, the scenario with seems more practical than when we take into consideration the processing complexity for SIC receivers, especially when SIC error propagation is considered as discussed in [25]. Figs.1a-c show snapshots of the considered aggregation phase for three different realizations. The silent MTDs are those out of the available resources being used by the active MTDs. The aggregator implements the resource scheduling according to one of the schemes presented in Section III, and the MTDs considered are those with granted access since the random access in the network is assumed to be performed222The resource scheduling schemes require that synchronization procedures, as well as the random access stage, are performed in advance. In fact, the work in [26] proposes a NOMA scheme allowing the combination of random access and data transmissions phases, where our resource scheduling schemes can be easily incorporated to improve the overall system performance. The details of such implementation are out of the scope of this work. as in [19, 27, 24].
After aggregating the MTDs’ data, the aggregator acts as an ordinary cellular user and relays the entire information to its associated BS in the second phase (relaying phase) as shown in Fig. 1d. For the aggregation phase with , there is both: outside interference (i.e. interference from MTDs operating on the same channels but being served by other aggregators), and inside interference (i.e. interference from MTDs within the serving area of the aggregator), which are both RVs. For the relaying phase, let be the interference at the BS from aggregators in other cells operating with the same channel resources. Notice that relies on the outside network topology, which is assumed unknown, but with a Laplace transform of in the form of
| (1) |
which is a established result from the stochastic geometry for wireless networks generated as PPP with Rayleigh fading, where is the path-loss exponent, while accounts for network density, characteristics of the aggregation/relaying areas, and others [28, 19]. Also, (1) holds under the assumption of using statistical full inversion power control [29] with parameter , as we assume here to guarantee a uniform user experience while saving valuable energy. The latter implies that devices control their transmit power such that the average signal power received at the serving aggregator/BS is equal to the predefined value . Thus, the instantaneous received power at the receiver side is , where is the channel power gain under quasi-static Rayleigh fading, and does not impact the performance since we assume the network as interference-limited.
Notice that the process could also be dependent of , as discussed in [30, 31]. In that case, the Laplace transform of the interference for different point processes appear to be merely horizontally shifted versions of each other (in dB) as long as their diversity gain is the same. Thus, scaling the threshold by this SIR gain factor ,333 will also depend on , but finding for a fixed already gives a good approximation [31]. we get , where would be included in . By properly selecting , the outside interference for any given topology could be then characterized. Finally, full channel state information (CSI) is assumed at receiver side as in [19, 22, 23].
III Aggregation Phase
In this section we discuss the RRS and CRS scheduling schemes for our hybrid access protocol.
III-A RRS for the Hybrid Access
Under the RRS scheme, out of the instantaneous MTDs requiring transmissions are independently and randomly chosen and then matched, one-to-one, with the orthogonal channels. If , all MTDs get channel resources, and even channels will be unused. Otherwise, if , the channel allocation is executed again by allowing the remaining MTDs to share channels with the already served MTDs. This process is executed repeatedly until all the MTDs are allocated or the maximum number of MTDs per channel, , is reached for all the channels. The inside interference, coming from the MTDs within the same aggregation zone and sharing the same channel, is faced with SIC. The SIR, , of the th MTD being decoded on a typical channel, given the number of MTDs on the same channel and the RRS scheme, is , while
| (2) | ||||
| (3) |
where is used to model the impact caused by imperfect SIC [32], while and are the channel power coefficients of both MTDs sharing the channel when .
We can weight the power of coexistent nodes on the same channel through and coefficients. Of course, some kind of feedback from the aggregators would be required after pairing the MTDs444Since up to 2 MTDs can be scheduled to transmit over the same channel, acquiring and using CSI at the MTD side is not appropriate. Instead, the aggregator should acquire the CSI and use it for the scheduling and for determining the power control coefficients; while finally forwarding such information back to the MTDs.. By letting be a fixed value we impose some kind of total transmission power constraint. This is crucial for NOMA scenarios, and here it is particular important in order to control the interference generated on close aggregators in the outside area555Notice that power constraints are usually linked to each device individually since they are mostly related to hardware limitations. In fact , therefore, we are implicitly considering also individual power constraints. However, since one channel may be occupied by 2 MTDs, by setting we are able of controlling the interference generated on the given channel on close aggregators in the outside area, and even if we are making it comparable to the interference that would generate a single MTD if operating alone in that channel.. Also, is unbounded, but since , thus the performance of the second MTDs being decoded on the channel is strongly limited by the SIC imperfection parameter, but by properly selecting that situation can be relaxed. Consider fixed rate coding scheme where the receiver decodes successfully if the SIR exceeds a threshold , achieving the information rate of [bits/symbol], we state the following theorem.
Theorem 1.
The RRS success probability, , of the th MTD sharing a typical channel conditioned on MTDs, is given by
| (4) | ||||
| (7) | ||||
| (10) |
Proof.
See Appendix A.
Remark 1.
As long as , it is advisable choosing such that , and both MTDs operating on the same channel get the success probability shown in the first line of (7) and (10). Notice that by going closer to we favor the first MTD being decoded, while if we choose a smaller , the second MTDs benefits. However, finding the values of and for which the MTDs could perform with similar reliability for any setup, seems intractable.
Theorem 2.
The Probability Mass Function (PMF) of the number of active MTDs, , is given in (III-A) at the top of the next page, where , and .
Proof.
See Appendix B.
| (11) |
III-B CRS for the Hybrid Access
The CRS scheme seeks to make better use of channel resources by strongly relying on all the CSI available for scheduling. The MTD with better fading (equivalently, better SIR) will be preferentially assigned with the available channel resources. An aggregator with instantaneous MTDs requiring transmission has the knowledge of their fading gains. Let denote the decreasing ordered channel gains, where . If all the MTDs will be chosen, but if the aggregator will pick the MTDs with better channel gains, i.e., , and then will assign randomly the orthogonal channels to them [19]. As a continuation, the remaining MTDs can be still allocated sharing those same resources, i.e., users ,…, go to the second round for allocation. This process is executed repeatedly until all the MTDs are allocated or the maximum number of MTDs per channel, , is reached [24].666Notice that imperfect CSI would not only affect the information decoding procedure under this scheme, but also the resource scheduling stage since the channel coefficients’ ordering may be affected. A detailed performance analysis under imperfect CSI is regarded as our future work.
Under the CRS scheme and using SIC to face the inside interference, the SIR, , of the th MTD being decoded on a typical channel, given the first MTD allocated there has the th larger channel coefficient, , and there are MTDs sharing that same channel, is given by and
| (12) |
| (13) |
Notice that the bound performance is the same as previously discussed for the RRS scheme. Meanwhile, the feedback/signaling overhead is also the same as for the RRS scheme since the CSI acquisition would take place at the aggregator side, which in turn will only forward back the channel allocation for each MTD and the power control coefficients if necessary. We have assumed that such metadata information is sufficiently small such that the low-rate feedback is error-free. However, practical performances would be upper bounded by our results.
Now, assuming that the receiver can decode successfully (SIR exceeds a threshold ), we state the following theorem.
Theorem 3.
Given the first MTD allocated has the th largest channel coefficient, , and that MTDs share that same channel, the CRS success probability, , of the th MTD being decoded on a typical channel is approximated as
| (14) |
where , and
| (15) | ||||
| (16) | ||||
| (17) |
Proof.
| (19) |
Theorem 4.
Proof.
The fact that the success probabilities for the CRS scheme, , depend on and complicates heavily the problem. Finding their average with regard the index allows us to use the same procedure when deriving Theorem 2 while attaining an accurate approximation. Now when in (56), we substitute each probability value, and , respectively by (20) and (21) since the success probability depends on the number of MTDs requiring transmission. When we do similar by replacing by (22) in (56). ∎
III-C Optimum Scheduling: Is it Feasible?
Notice that previous scheduling schemes do not guarantee an optimum performance. This is obvious for the case of RRS since such scheme relies entirely on random pairing, while CRS, even when it exploits CSI for making the pairing decisions, is also sub-optimal. As an example, notice that for a better scheduling when and will probably be the one pairing the MTDs with better fading conditions with the ones having the worst fading. This is because such pairing benefits always the MTD to be decoded first, while the MTD to be decoded second is not going to be affected by significant outside interference neither by residual interference from SIC. Consequently, it is expected that as and/or take meaningful values, the CRS’s performance approaches (but not necessary reaches) the optimum.
The optimum scheduling requires an exhaustive search over all the feasible scheduling outcomes in order to adopt the one offering maximum performance. Notice that the dimension of the search space, , depends on and since
-
•
If there is only one feasible allocation, which is granting individual channel resources to all MTDs;
-
•
if , there are MTDs that will be scheduled alone in their channels. Thus, there is a total of for making such selection, while the remaining MTDs need to be paired between each others to share channels; which can be performed in different ways;
-
•
if , it is necessary selecting the MTDs that will get the channel resources for which there are possibilities; and also making the pairing by testing all the different alternatives.
Therefore,
| (26) |
while on average the dimension of the search space is , which can be stated as in (27) at the top of the next page. Notice that came from using (26), while followed from using the CDF of , evaluating the sums and using the definition of the Kummer confluent hypergeometric function, and performing some algebraic transformations and simplifications.
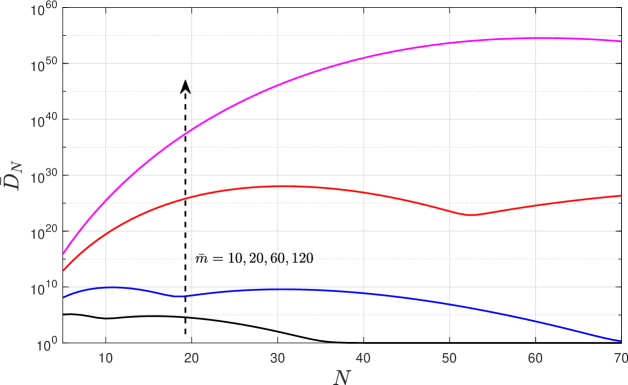
| (27) |
Fig. 2 shows as a function of for different values of . Notice that unless , the dimension of the search space becomes extremely large on average, which makes the exhaustive search unfeasible. Since the scheduling problem appears exactly when the contrary occur, e.g., when is comparable or greater than since otherwise MTD per channel is frequently viable, we can conclude that indeed the optimum scheduling through brute force is unfeasible.
In the following section we discuss the overall system performance after analyzing the relaying phase, in which all collected data is forwarded to the BS.
IV Relaying Phase & Overall Performance
In the relaying phase, the aggregator transmits its aggregated data to the BS777For simplicity, we assume that each aggregator has no buffer and transmits all its aggregated data in one go as in [24, 19].888Notice that this transmission occurs over only one BS serving channel, therefore, the aggregation topology is reducing the number of BS channel allocations to the MTC devices in a cluster, from in the case of no aggregation, down to . The importance of such approach is highlighted in [2, 11].. The aggregated data can be successfully decoded by the BS if SIR meets the following condition , where in bits per channel use per MTD (bpcu/MTD) with being the relaying transmission time and is the available bandwidth for that transmission. is the SIR of the signal received at the BS. Then, we write the relaying success probability conditioned on active aggregated MTDs as
| (28) |
where comes from using assuming that denotes the channel power gain of the link between the aggregator and the BS, comes from using , follows after using the definition of the Laplace transform, and finally comes from using (1).
We now are able to evaluate the average number of successful MTDs, which is an overall performance metric embracing both, the aggregation and relaying phases. That metric evaluates the average number of MTDs being served by the aggregator, whose data can be successfully received by the BS. We can formally write this metric as
| (29) |
where is given in (III-A) and (III-B) for the RRS and CRS schemes, respectively.
V Numerical Results
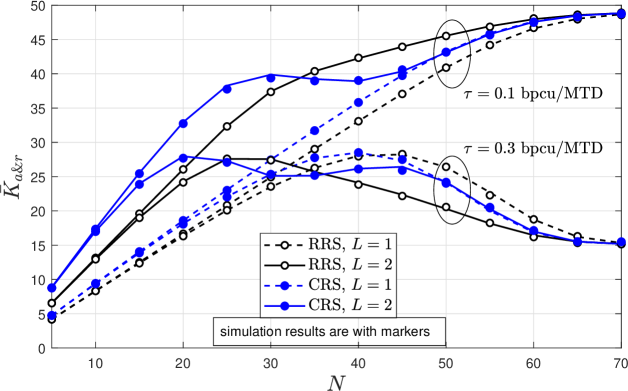
Both, simulation and analytical results, are presented in this section to investigate the performance of our hybrid scheme as a function of the system parameters while comparing it with an OMA setup. Unless stated otherwise, results are obtained by setting , , , , bpcu/MTD and . We set dB, which matches the scenario where all the outside aggregators, serving areas of radius m, are operating with one MTD per channel, while forming a PPP with density . Also, such that the average consumed power per orthogonal channel keeps the same for either the or setup, while the interference generated over MTDs sharing the same channel but outside the serving zone keeps similar as in the OMA setup. For the relaying phase we set dB, which matches the scenario where BSs are serving circular areas of approximately m, while forming a PPP with density . Simulation results are generated using 20000 Monte Carlo runs999Note that simulations, proposed analytical expressions and approximations fit well in all the cases depicted Fig. 3-7, which validates our findings..
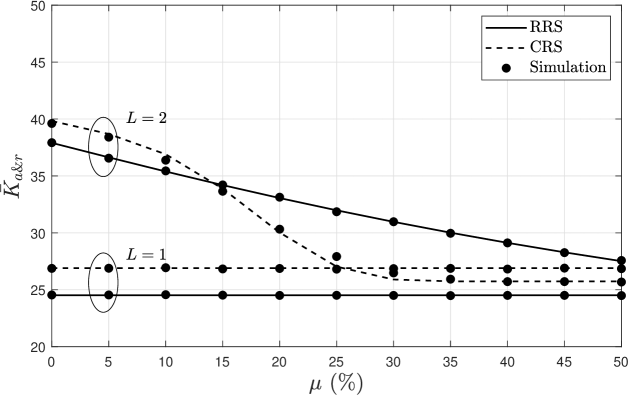
Fig. 3 shows that the hybrid scheme for the aggregation phase can improve the spectral efficiency by providing service to a greater number of MTDs when the access demand increases, e.g., . This claim comes from [24], where only the aggregation phase was analyzed. We now extend it by considering the relaying phase, where spite the fact that multiplexing a greater number of MTDs with the same rate degrades the system reliability, the advantage of the hybrid scheme over the purely OMA setup holds. Notice that spectral efficiency for both setups, e.g., and , degrades by decreasing , as can be observed in Fig. 4, and/or by increasing . In fact, when increases the degradation of the relaying phase performance due to more data that it is being transmitted could be faster than the increase in the number of active MTDs in the aggregation phase when increases, thus, the overall performance may worsen as it is shown in Fig. 3 for the case of bpcu/MTD when . On the other hand all the curves tend to overlap when increases since the probability of having two MTDs sharing the same orthogonal channel decreases so that performance is similar to OMA setup. The fluctuations observed in the CRS scheme for different values of is consequence of higher dependence/sensitivity on power control coefficients compared to RRS scheme. Thus, a careful selection of those parameters is required for each system setup.
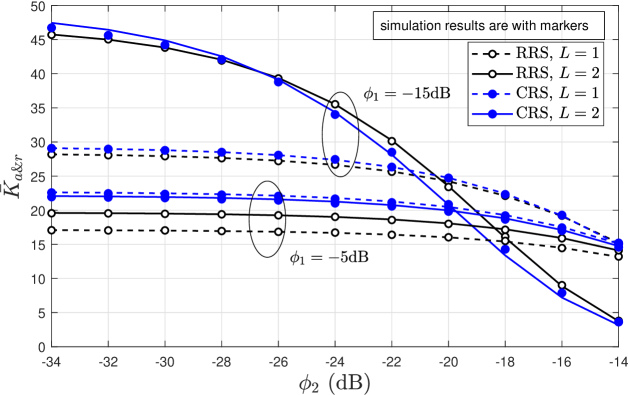
For the CRS scheme we were able to reach closed-form expressions in [24, Eqs. (33), (34)] for the power control coefficients while attaining similar reliability for both MTDs sharing the same channel. Notice that when using the RRS scheme, all MTDs have chance to transmit independently of the channel conditions, which could model more realistic scenarios where some MTDs require be served urgently. Also, RRS has a slight decreased performance compared to CRS scheme in the aggregation phase [24].
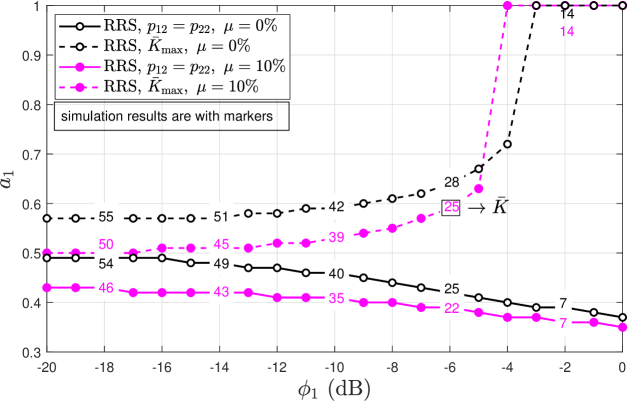
Fig. 5 investigates the required for RRS to attain either similar reliability for both MTDs sharing the same channel or a maximum average number of simultaneously active MTDs in the aggregation phase [24, Eq. (17)], as a function of . As outside interference increases, the required power control coefficient for the first MTD, , decreases when similar reliability is the goal, since the performance of the second MTD deteriorates faster and the power control coefficient should increase. Otherwise, when the goal is to maximize the number of simultaneously active MTDs, the performance of the second MTD needs to be sacrificed, even more so when the outside interference increases until the hybrid scheme performs as the OMA setup, e.g., . Notice that almost all the time, a greater SIC imperfection leads to a reduction in the required , decreasing its impact on the performance of the second decoded MTD. Only when reaching is the goal and the outside interference is sufficiently large, a greater SIC imperfection accelerates the transition to OMA by increasing . Also, increasing deteriorates (see numbered labels in Fig. 5).
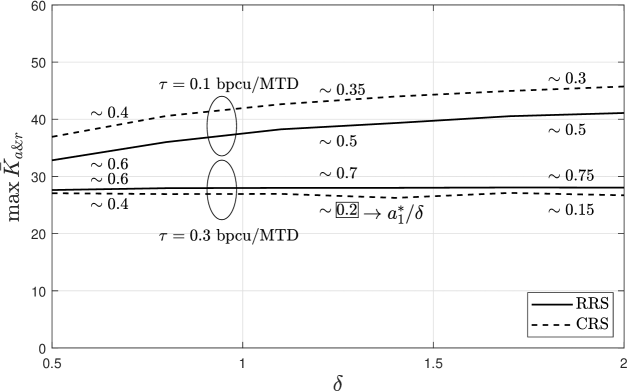
The reachable maximum average of simultaneously served MTDs as a function total power constraint coefficient, , is shown in Fig. 6. Therein, we find the coefficients and that maximize such that . Notice that increasing has a positive impact on the system performance as long as the appropriate values of and are selected, which can be deduced from numbered labels in the figure. For the case of bpcu/MTD this effect is not evident since the relaying phase is limiting the system performance much more than the aggregation phase. On the other hand, increasing is not always feasible, e.g., due to transmit hardware limitations, or even advisable, e.g., due to the extra interference that might be generated over other OMA networks or because of a low energy efficiency performance. Therefore, the appropriate selection of is of paramount importance.
Fig. 7 shows the average number of simultaneously served MTDs as a function of the SIC imperfection coefficient. We set such that each channel is operating with two MTDs almost all the time, which are more sensitive to the interference and imperfection of the SIC. Since SIC is only related with the setup, the OMA setup curves are shown with straight lines. Of course, when increases, the performance of the setup deteriorates, specifically if the power coefficients are not tuned accordingly. This is because those coefficients work well for certain system parameters but others will be required if they change, e.g. different in this case. It is expected that a smaller , hence larger , work better as increases as shown previously in Fig. 5. It is clear that failing to efficiently eliminate the inside interference could reduce significantly the benefits from NOMA, and can be a challenging issue for implementing NOMA in practice.
VI Conclusion
We analyzed the data aggregation and relaying in interference-limited mMTC network. We evaluate a hybrid access scheme, OMA-NOMA, while investigating its performance in terms of average number of simultaneously served MTDs. Power control coefficients are incorporated to the practical-interest RRS scheme, while we investigate them numerically. The numerical results also show that our hybrid access scheme aims at providing massive connectivity in scenarios with high access demand. However, inter-cluster interference could reduce significantly the benefits from NOMA, and challenging its implementation in practice.
Appendix A Proof of Theorem 1
As in [24, Th. 1], let us write the success probabilities as
| (30) | ||||
| (33) |
| (36) |
where , and , while and come from using their CDF expressions, which are obtained next.
| (37) |
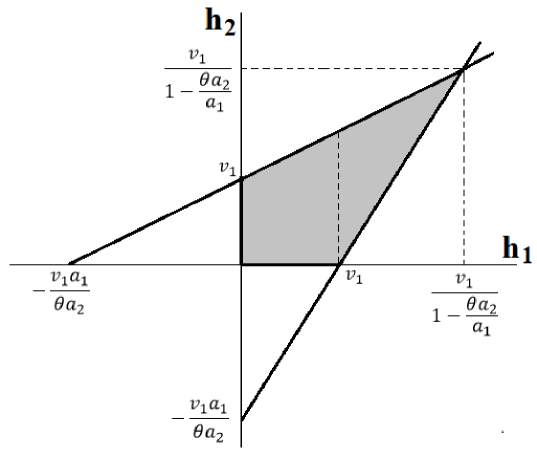
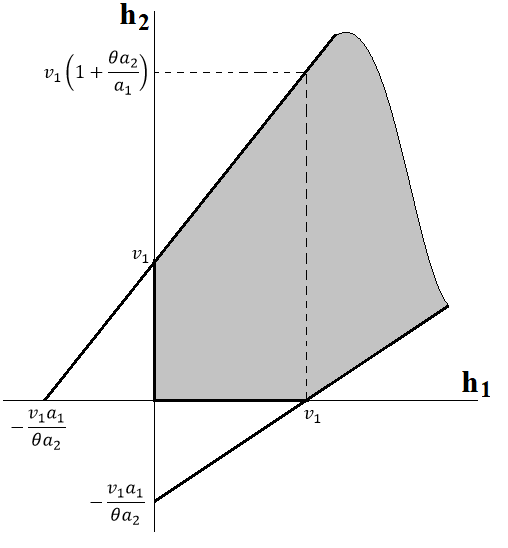
Lets consider the following cases:
-
•
, then we can continue from equation (37) as follows.
(38) and the intersection region is shown in Fig. 8a and notice that are also restrictions. Therefore we can transform (38) to attain the result in (39) at the top of the next page.
(39) -
•
, then we can continue from equation (37) as follows.
(40) Notice that regions and do not say nothing new because we already know that . Therefore we can write (40) as
(41) and the intersection region is shown in Fig. 8b. Thus, by working on (41) we reach (42) at the top of next page (below (39)).
(42)
By combining (39) and (42) we attain the general expression for , which is
| (46) |
while
| (50) |
can be attained by following a similar procedure.
Finally, by taking the expectation in (30), (33) and (36) we attain (4), (7) and (10), respectively. ∎
| (56) |
Appendix B Proof of Theorem 2
For the system model in Section II the outside interference on each channel is independent. Let be the number of MTDs requiring data transmission, the conditional distribution of is given in (56) (on the top of the next page) where , and . Notice that when all the MTDs are operating alone in their channels, while when , MTDs will be operating alone and will be sharing their channels. Additionally, when , the MTDs with channel resources are sharing their channels. Thus, (56) comes from combinatorial and probability theories. The indicator function guarantees operation in the appropriate regions, e.g., and , according to the particular case. After using along with some algebraic manipulations we attain the result in (III-A). ∎
References
- [1] L. Atzori, A. Iera, and G. Morabito, “Understanding the Internet of Things: definition, potentials, and societal role of a fast evolving paradigm,” Ad Hoc Networks, vol. 56, pp. 122–140, 2017.
- [2] K.-C. Chen and S.-Y. Lien, “Machine-to-machine communications: Technologies and challenges,” Ad Hoc Networks, vol. 18, pp. 3–23, 2014.
- [3] Ericsson. (2017, nov) Ericsson mobility report. [Online]. Available: https://www.ericsson.com/en/mobility-report/reports/november-2017/internet-of-things-outlook
- [4] Z. Dawy, W. Saad, A. Ghosh, J. G. Andrews, and E. Yaacoub, “Toward massive machine type cellular communications,” IEEE Wireless Commun., vol. 24, no. 1, pp. 120–128, February 2017.
- [5] A. Rajandekar and B. Sikdar, “A survey of MAC layer issues and protocols for machine-to-machine communications,” IEEE Internet of Things Journal, vol. 2, no. 2, pp. 175–186, April 2015.
- [6] 3GPP TS 36.331 V10.50.0, “Evolved universal terrestrial radio access (E-UTRA); radio resource control (RRC),” Mar 2012.
- [7] T. M. Lin, C. H. Lee, J. P. Cheng, and W. T. Chen, “PRADA: Prioritized random access with dynamic access barring for MTC in 3GPP LTE-A networks,” IEEE Trans. on Vehic. Tech., vol. 63, no. 5, pp. 2467–2472, Jun 2014.
- [8] X. Yang, A. Fapojuwo, and E. Egbogah, “Performance analysis and parameter optimization of random access backoff algorithm in LTE,” in IEEE VTC-Fall, Sept 2012, pp. 1–5.
- [9] M. I. Hossain, A. Azari, and J. Zander, “DERA: Augmented random access for cellular networks with dense H2H-MTC mixed traffic,” in 2016 IEEE Globecom Workshops (GC Wkshps), Dec 2016, pp. 1–7.
- [10] A. Laya, C. Kalalas, F. Vazquez-Gallego, L. Alonso, and J. Alonso-Zarate, “Goodbye, ALOHA!” IEEE Access, vol. 4, pp. 2029–2044, 2016.
- [11] H. Shariatmadari, P. Osti, S. Iraji, and R. Jäntti, “Data aggregation in capillary networks for machine-to-machine communications,” in 2015 IEEE 26th Annual International Symposium on Personal, Indoor, and Mobile Radio Communications (PIMRC), Aug 2015, pp. 2277–2282.
- [12] P. H. Nardelli, M. de Castro Tomé, H. Alves, C. H. de Lima, and M. Latva-aho, “Maximizing the link throughput between smart meters and aggregators as secondary users under power and outage constraints,” Ad Hoc Networks, vol. 41, pp. 57–68, 2016.
- [13] I. Ramezanipour, P. Nouri, H. Alves, P. H. J. Nardelli, R. D. Souza, and A. Pouttu, “Finite blocklength communications in smart grids for dynamic spectrum access and locally licensed scenarios,” IEEE Sensors Journal, vol. 18, no. 13, pp. 5610–5621, July 2018.
- [14] S. Boubiche, D. E. Boubiche, A. Bilami, and H. Toral-Cruz, “Big data challenges and data aggregation strategies in wireless sensor networks,” IEEE Access, vol. 6, pp. 20 558–20 571, 2018.
- [15] N. Kouzayha, M. Jaber, and Z. Dawy, “M2M data aggregation over cellular networks: Signaling-delay trade-offs,” in 2014 IEEE Globecom Workshops (GC Wkshps), Dec 2014, pp. 1155–1160.
- [16] A. Riker, E. Cerqueira, M. Curado, and E. Monteiro, “Data aggregation for group communication in machine-to-machine environments,” in 2014 IFIP Wireless Days (WD), Nov 2014, pp. 1–7.
- [17] C. Bormann, A. P. Castellani, and Z. Shelby, “CoAP: An application protocol for billions of tiny Internet nodes,” IEEE Internet Computing, vol. 16, no. 2, pp. 62–67, March 2012.
- [18] E. Fitzgerald, M. Pióro, and A. Tomaszewski, “Energy-optimal data aggregation and dissemination for the Internet of Things,” IEEE Internet of Things Journal, vol. 5, no. 2, pp. 955–969, April 2018.
- [19] J. Guo, S. Durrani, X. Zhou, and H. Yanikomeroglu, “Massive machine type communication with data aggregation and resource scheduling,” IEEE Transactions on Communications, vol. 65, no. 9, pp. 4012–4026, Sept 2017.
- [20] M. Shirvanimoghaddam, M. Dohler, and S. J. Johnson, “Massive non-orthogonal multiple access for cellular IoT: Potentials and limitations,” IEEE Communications Magazine, vol. 55, no. 9, pp. 55–61, 2017.
- [21] Y. Saito, A. Benjebbour, Y. Kishiyama, and T. Nakamura, “System-level performance evaluation of downlink non-orthogonal multiple access (NOMA),” in IEEE PIMRC, Sept 2013, pp. 611–615.
- [22] Z. Ding, Z. Yang, P. Fan, and H. V. Poor, “On the performance of non-orthogonal multiple access in 5G systems with randomly deployed users,” IEEE Sig. Proces. Lett., vol. 21, no. 12, Dec 2014.
- [23] Z. Zhang, H. Sun, R. Q. Hu, and Y. Qian, “Stochastic geometry based performance study on 5G non-orthogonal multiple access scheme,” in IEEE GLOBECOM, Dec 2016, pp. 1–6.
- [24] O. L. A. López, H. Alves, P. H. J. Nardelli, and M. Latva-aho, “Aggregation and resource scheduling in machine-type communication networks: A stochastic geometry approach,” IEEE Transactions on Wireless Communications, vol. 17, no. 7, pp. 4750–4765, July 2018.
- [25] F. Liu, P. Mähönen, and M. Petrova, “Proportional fairness-based power allocation and user set selection for downlink NOMA systems,” in 2016 IEEE International Conference on Communications (ICC), May 2016, pp. 1–6.
- [26] M. Shirvanimoghaddam, M. Dohler, and S. J. Johnson, “Massive multiple access based on superposition raptor codes for cellular M2M communications,” IEEE Trans. on Wireless Commun., vol. 16, no. 1, pp. 307–319, Jan 2017.
- [27] D. Malak, H. S. Dhillon, and J. G. Andrews, “Optimizing data aggregation for uplink machine-to-machine communication networks,” IEEE Trans. on Commun., vol. 64, no. 3, pp. 1274–1290, March 2016.
- [28] M. Haenggi, Stochastic geometry for wireless networks. Cambridge University Press, 2012.
- [29] M. Gharbieh, H. ElSawy, A. Bader, and M. S. Alouini, “Spatiotemporal stochastic modeling of IoT enabled cellular networks: Scalability and stability analysis,” IEEE Transactions on Communications, vol. 65, no. 8, pp. 3585–3600, Aug 2017.
- [30] M. Haenggi, “The mean interference-to-signal ratio and its key role in cellular and amorphous networks,” IEEE Wireless Commun. Letters, vol. 3, no. 6, pp. 597–600, Dec 2014.
- [31] R. K. Ganti and M. Haenggi, “Asymptotics and approximation of the SIR distribution in general cellular networks,” IEEE Trans. on Wireless Commun., vol. 15, no. 3, pp. 2130–2143, March 2016.
- [32] H. Sun, B. Xie, R. Q. Hu, and G. Wu, “Non-orthogonal multiple access with SIC error propagation in downlink wireless MIMO networks,” in IEEE Vehicular Technology Conference (VTC-Fall), Sept 2016, pp. 1–5.