2021
[1]\fnmXiangke \surWang
[1]\orgdivCollege of Intelligence Science and Technology, \orgnameNational University of Defense Technology, \orgaddress \stateChangsha, \countryP. R. China
Integrated Design of Cooperative Area Coverage and Target Tracking with Multi-UAV System
Abstract
This paper systematically studies the cooperative area coverage and target tracking problem of multiple-unmanned aerial vehicles (multi-UAVs). The problem is solved by decomposing into three sub-problems: information fusion, task assignment, and multi-UAV behavior decision-making. Specifically, in the information fusion process, we use the maximum consistency protocol to update the joint estimation states of multi-targets (JESMT) and the area detection information. The area detection information is represented by the equivalent visiting time map (EVTM), which is built based on the detection probability and the actual visiting time of the area. Then, we model the task assignment problem of multi-UAV searching and tracking multi-targets as a network flow model with upper and lower flow bounds. An algorithm named task assignment minimum-cost maximum-flow (TAMM) is proposed. Cooperative behavior decision-making uses Fisher information as the mission reward to obtain the optimal tracking action of the UAV. Furthermore, a coverage behavior decision-making algorithm based on the anti-flocking method is designed for those UAVs assigned the coverage task. Finally, a distributed multi-UAV cooperative area coverage and target tracking algorithm is designed, which integrates information fusion, task assignment, and behavioral decision-making. Numerical and hardware-in-the-loop simulation results show that the proposed method can achieve persistent area coverage and cooperative target tracking.
keywords:
Multi-UAV, Task assignment, Area coverage, Target tracking1 Introduction
The multi-UAV cooperative area coverage and target tracking problem is a typical problem in area surveillance tasks, which is an essential means of information acquisition. Typical application scenarios of area coverage and target tracking include forest fire monitoring, search and rescue, and pursuit-evasion. These applications not only require continuous search and coverage of the mission area. They also need the multi-UAV system to promptly detect the intruding non-cooperative targets and cooperatively track the allocated targets. However, various factors, such as the dynamic environment, the target appearance probability, and the sensor performance, make the problem very complex.
Many existing works consider the area coverage or target tracking problem sololy bib1 ; bib2 .The integrated design of area coverage and target tracking has not gotten enough attention bib1 . Previous studies of area coverage and target tracking problem usually include two categories: coupling or decouping. The coupling study of area coverage and target tracking problem simultaneously considers the coverage and tracking tasks, usually called simultaneous coverage and tracking (SCAT). SCAT focuses on the multi-objective optimization of coverage and tracking tasks, and the typical method of SCAT is the voronoi-based coverage method bib2 ; bib3 . The target tracking part in bib2 is treated as a parameter-based procedure. Then, the area coverage and target tracking problem is translated to the problem of covering environments with time-varying density functions. Although SCAT has been verified in actual scenarios, it ignores the single performance of area coverage or target tracking task to a certain extent. For the decoupling design of coverage and tracking, it is necessary to make the UAV switch between different modes according to specific environments and mission requirements bib5 and reasonably allocate different UAVs to track multiple targets. Control logic design based on a finite state automaton model, integrating four modes of operations, is presented in bib8 . The semi-flocking algorithm in bib5 ; bib6 ; bib7 assigns a small flock of sensors to each target while at the same time leaving some sensors free to explore the environment. It enables mobile nodes to self-organize themselves switch between searching and tracking modes. Although the above decoupling algorithms have been well applied, they lack the coordinated management of UAVs, making it difficult to achieve optimal cooperation between UAVs.
Considering that the coupled algorithms ignores the performance of a single task, this paper solves the area coverage and target tracking problem under the decoupled framework. A hierarchical modular architecture is designed to enhance the collaboration of UAVs in the distributed manner. The hierarchical modular method integrates three sub-modules of information fusion, task allocation, and behavior decision-making.
The information fusion module includes data preprocessing and information fusion methods. Most of the current work is based on Bayesian methods bib24 ; bib25 for data pre-processing, while the sensors are modeled as sources of uncertainty. While for the data fusion in a distributed system, nodes need to be guided through an interactive protocol to generate a consistent estimate. The information consensus algorithm bib28 has been widely used in distributed estimation bib29 , task assignment bib32 ; bib33 , and other scenarios. However, the consensus process is highly dependent on the communication links, and the algorithm convergence time increases rapidly as the task complexity increases. bib34 gives the termination condition of the maximum consensus algorithm in the distributed information fusion process. In this paper, we improve the maximum consensus information fusion algorithm in bib34 so that it can be applied to the area coverage and target tracking task.
The task allocation module is the key to enhancing the collaboration of UAVs. It can be solved by centralized or distributed methods. Centralized assignment methods bib36 can globally coordinate the complex relationships between tasks, but they rely too much on the control center and lack robustness. Commonly used distributed allocation methods are based on the market mechanism bib44 ; bib45 . Distributed task assignment methods are computationally flexible and suitable for solving large-scale assignment problems. However, there are challenges to obtaining global optimal assignments. In this paper, based on consensus algorithms and network flow theory bib49 , we design an algorithm that can get the global optimal allocation in a distributed manner. Applications of network flow theory to the task assignment are not typical. We find that the multi-UAV task assignment problem in area coverage and target tracking task can essentially be modeled as a minimum-cost maximum-flow problem bib50 , which then can be solved using various MCMF algorithms. The MCMF algorithms are centralized methods. Combining the MCMF algorithms with the consensus algorithms enables the allocation algorithm to adapt to the overall distributed architecture.
The collaborative behavioral decision-making module utilizes Fisher information as the task reward, and UAVs make decisions according to the assigned coverage or tracking tasks. As for coverage decision, researchers have focused on geometric, probabilistic or biological intelligence approaches bib10 . Geometric-based methods bib13 ; bib14 can achieve complete coverage of the area.However, the centralized and offline nature makes the geometry-based approach unsuitable for dynamic environments. The probabilistic-based approach bib10 builds probabilistic models to characterize the environmental uncertainty and uses search algorithms for distributed online decisions to reduce environmental uncertainty. Compared with other decision-making algorithms, the methods based on biological intelligence can generate coverage behavior through simple rules with low computational cost bib19 . Therefore, we choose a rule-based anti-flocking algorithm bib22 ; bib23 for the coverage decision. In the tracking behavior decision-making part, most target tracking methods are based on the principles of placing the target in the center of the field of view bib54 . In this paper, we use the rolling horizon method for tracking decision-making. And the optimal action sequence that maximizes the cumulative Fisher information volume is found.
According to the hierarchical modular design and the ideas of the three sub-modules, our main contributions are as follows:
-
•
First, a distributed hierarchical modular architecture is provided for the area coverage and target tracking problem. We modularize information fusion, task assignment, and behavioral decision-making and integrate the three modules through a distributed architecture design. Compared with the coupling SCAT architecture, the distributed hierarchical modular design can fully exploit the capabilities of each sub-module, thereby improving the area coverage and target tracking performance of the system.
-
•
Second, a distributed information fusion strategy that combines the compression, extraction, and fusion of the coverage time maps in the coverage task with the fusion of the target states is designed. The compression and extraction of the coverage information map allow our information fusion strategy to be adapted in arbitrarily large mission areas.
-
•
Third, model the allocation problem of multi-UAV coverage and target tracking task as a network flow model. Then, a minimum-cost maximum-flow algorithm for task assignment is designed. The allocation algorithm adapts to the change in the quantitative relationship between UAVs and targets and can achieve fast allocation for large-scale tasks.
The rest of the paper is organized as follows. Section 2 analyzes the area coverage and target tracking problem and decomposes it into three subproblems: distributed information fusion, multi-UAV task assignment, and behavioral decision-making. And then, each subproblem is studied accordingly in Sections 3,4 and 5. Section 6 systematically designs a distributed multi-UAV cooperative area coverage and target tracking algorithm. Finally, Section 7 gives the numerical and hardware-in-loop simulations and corresponding discussions. Numerical and hardware-in-the-loop simulations demonstrate that our proposed hierarchical modular architecture can effectively solve the area coverage and target tracking problem.
2 Problem formulation
In this paper, several ground targets are moving in the mission area and the number and states of the targets are unknown. The multi-UAV system consisting of homogeneous UAVs needs to cover the area continuously and automatically assigns UAVs to track the searched targets, while the remaining UAVs perform the coverage task. According to the mission requirements, each UAV has two task modes, i.e., the area coverage mode and the target tracking mode. Fig. 1 shows a typical scenario of the area coverage and target tracking task.
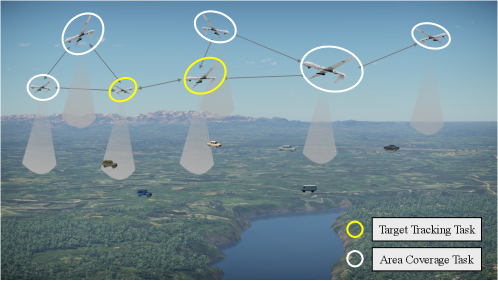
Assuming that there are targets searched at the current moment. Let denote the number list of all UAVs and denote the number list of all targets. Beaides, and denote the th UAV and th target, respectively. The detection sensor is modeled by a disk with limited sensing capability and a fixed field of view (FOV). While the th UAV can observe any targets within its measurement range , which is determined by its altitude and FOV. UAVs communicate through the wireless communication module with the communication range of . Let denote the position of . Then we use to represent the undirected communication subgraph containing and its neighbors, where and . Here depends on the communication range and the relative location between UAVs.
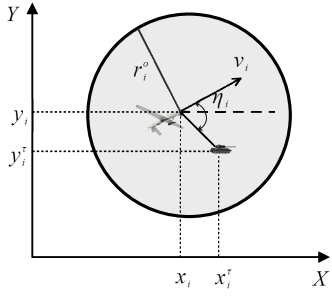
Let represent the state of target . We use the linear kinematic model for the ground moving targets. Meanwhile, we assume that the UAVs all fly at a constant altitude. The state of is defined by , where is the flight speed and is the heading angle. The geometric relationship of UAV and target in the two-dimensional plane is shown in Fig. 2. The discrete kinematics model of the fixed-wing UAV is as follows:
| (1) |
where denotes the length of each time step, and the action command of the th UAV is , indicating the ground acceleration and heading angular velocity.
In our work, we only consider the target tracking task in the task allocation stage, since moving targets are more valuable. We calculate the tracking action and the corresponding reward of each UAV to each target through the tracking decision algorithm and then assign tasks to UAVs according to the reward matrix . is the corresponding task reward when tracks target . denotes the task decision matrix. indicates that task is assigned to and 0 otherwise. denotes the action command of all UAVs. And is the action command of . Our goal is to find the optimal mapping from the tasks to UAVs and plan the action of each UAV to maximize the overall mission reward while meeting the task constraints. Then, the optimization function of the multi-UAV system is:
| (2) | ||||
The first constraint indicates that the number of UAVs tracking one target cannot exceed . While the second constraint shows that each UAV can select at most one target to track. Note that if a UAV is assigned no target to track, it then performs the area coverage tasks.
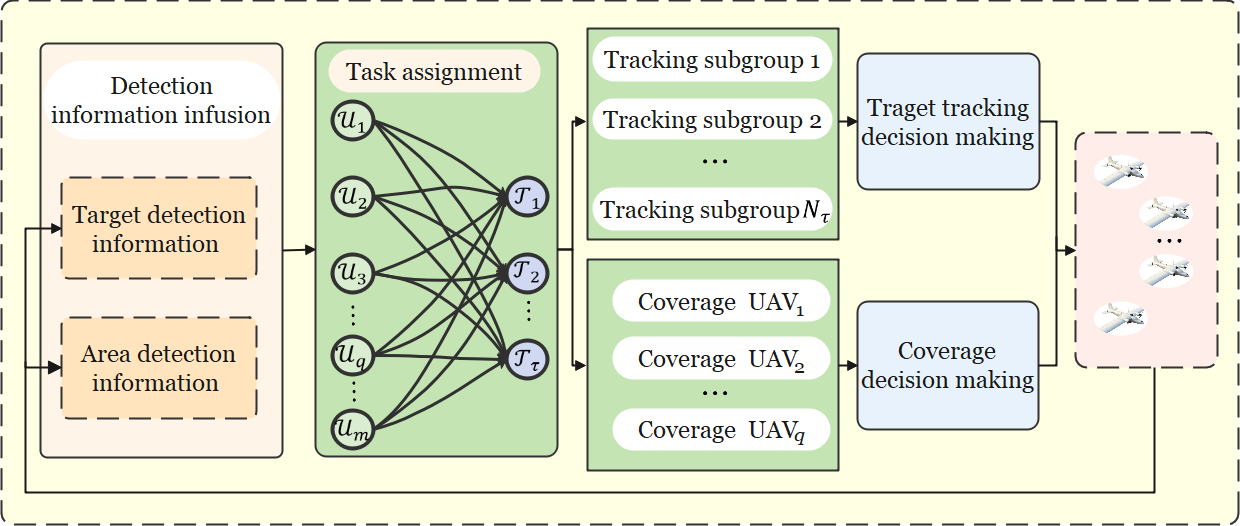
In the decoupling architecture, we divide the area coverage and target tracking task into three sub-problems: information fusion, task assignment, and multi-UAV behavior decision-making. Fig. 3 is the framework of our multi-UAV area coverage and target tracking system. Then we analyze each sub-problem in detail in the following sections.
3 Multi-UAV information fusion
The information interaction is essential for realizing the cooperation among UAVs. It can improve the area coverage efficiency and the tracking accuracy of targets. In this section, a distributed approach is proposed where the joint estimation state of multi-targets and the coverage information of each UAV are propagated through the whole network so that the consistency of the detection information is guaranteed. The information fusion algorithm in this section improves the information fusion strategy in bib34 which is designed only for the target tracking task.
3.1 Definition of detection information
In the information fusion process, UAVs need to exchange their detection information (the local area coverage information and the local estimation state of multi-targets) with neighbors. Therefore, we design the area information map and a target information table to save the detection information of each UAV.
3.1.1 Equivalent visiting time map
In order to record the coverage information of each UAV and cooperate with other UAVs, we discretize the task area into a grid map with grids. Suppose we set the detection radius of the airborne sensor simply as a disk. The target will be covered as long as within the sensor’s detection range, which does not consider the probability of successful detection. Therefore, we build an equivalent visiting time map (EVTM) considering the sensor’s performance.
Let denote the EVTM of the th UAV. The equivalent visiting time map (See Fig. 5) records the equivalent time when the grids were last visited. represents the equivalent visiting time of grid at the end of time step . is the actual time at time step .
Initialize the equivalent visiting time map with , and the update rule of the EVTM is as follows:
| (3) |
is relevant to the probability of successful detection and will be calculated subsequently. is updated only by the detection information of . After information fusion phase, we can get with the dection information of the UAVs in the same connected network.
Let denote the successful detection probability of grid by at time step . is related to the sensor performance and the distance between and the detection grid , that is:
| (4) |
where , , and are adjustable parameters.
Considering the successful detection probability , the visiting requirement of grid is:
| (5) |
We can also use an S-curve function to represent the visiting requirement of grid from its corresponding equivalent visiting time:
| (6) |
where and are curve parameters, is the revisit time threshold.
3.1.2 Target information table
In our previous work bib34 , each UAV maintains an information table to store its current estimation states of the targets. We define the information for a single target at time step as the following tuple:
| (8) |
and are the local estimated state and the error covariance matrix of target and can be obtained through the local Kalman filtering of . Perceptual confidence quantifies the accuracy of the UAV’s target state estimation and is set as the trace of the covariance matrix, which is:
| (9) |
Besides, and are the corresponding estimated state and error covariance matrix after information fusion. Therefore, we can use to denote the local detection information of to all targets.
3.2 Distributed information fusion
In the distributed information fusion process, each UAV exchanges information with its neighbors to update the local information. The coverage time map, the perceptual confidence value, and the corresponding estimated state and error covariance matrix are propagated over the network in a finite time. Through limited updates with max-consensus protocol, the perceptual information of all UAVs in the connected network achieves consistency.
3.2.1 Communication topology
When performing the area coverage and target tracking task, UAVs are constantly moving. Thus the communication topology of the multi-UAV system is time-varying. Depending on the spatial distribution and communication radius of UAVs, several communication topologies may emerge as shown in Fig. 4.
-
(a)
The connected communication topology;
-
(b)
The communication topology which is divided into several isolated connected communication topologies;
-
(c)
The communication topology that all nodes can not communicate with each other.

To simplify the analysis, the communication topology is assumed to remain constant during each time step. Only the UAVs within the same connected communication topology need to exchange and fuse information to make the detection information achieve consistency.
3.2.2 The compression and extraction of EVTM
To reduce the interactive information, we compress and extract the visiting time map to get a compressed time map and a local time map, representing the global coverage information and local coverage information, respectively.
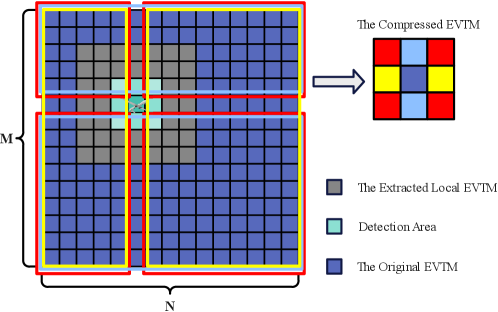
Fig. 5 shows the schematic of the compression and extraction of the EVTM. Assuming that is located at grid , the compressed time map can be obtained by averaging the equivalent visiting time of the grids around in EVTM , which is:
| (10) |
where is the compression function of the equivalent visiting time map.
The local equivalent time map is obtained by extracting the grids around the UAV’s location from the EVTM . The extraction function is as follows:
| (11) | ||||
is a positive odd number.
Table 1 shows the message passed from neighboring UAV to , of which is the local equivalent time map of . Such information interaction allows our coverage algorithm to extend to surveillance tasks with arbitrarily large mission areas.
| Information type | Information content |
|---|---|
| Status information | |
| Area detection information | |
| Target detection information | |
| \botrule |
Remark 1.
Regardless of the size of the area, the interaction information between UAVs is always a map with grids. Then, for an arbitrarily large detection area with an area information map of grids, the information content is only of the original global map.
3.2.3 The distributed information fusion based on maximum consistency
In order to get consistent information before the subsequent decision-making process, we define a new sampling time denoted by index with a higher frequency in the information fusion phase. Moreover, to express the fusion process more clearly, a group of temporary variables initialized with the information at time step (See Table 2) is defined.
| Temporary variable | Initialization |
|---|---|
| \botrule |
The detection information from neighbors can then be fused based on the max-consensus protocol. Specifically, the equivalent visiting time map is updated with the received EVTM as follows:
| (12) |
The update rule of the perceptual confidence is:
| (13) |
According to the general definition of maximum consistency in bib52 , we give the concept of maximum consistency of the detection information in our area coverage and target tracking system.
Definition 1 (Maximum consistency of the detection information).
Consider the undirected communication subgraph where is located, the initial value of the equivalent visiting time map, and the initial value of perceptual confidence of each UAV in the subgraph, the update rules of EVTM and the perceptual confidence are (12) and (13), respectively. Then the system achieves maximum consistency, if , so that:
| (14) | ||||
| (15) |
where is the lower bound of the iteration number to achieve maximum consistency in the whole connected graph .
According to the termination condition of the maximum consistency algorithm given in Theorem 1 of bib34 , we directly set the number of iterations of the th UAV as , which is the diameter of the shortest path tree (SPT) of rooted at node . Algorithm 1 gives the information fusion process of the th UAV. After the information fusion phase, we get the joint estimation states of multi-targets (JESMT) and the joint EVTM of the mission area.
4 Task assignment based on minimum-cost maximum-flow method
According to the task allocation problem of multi-UAV search and tracking multi-target formulated in (2), it is assumed that target should be tracked by at least one UAV and at most UAVs. Meanwhile, each UAV can choose one target to track at most. Combined with the network flow theory, this task allocation problem can be modeled as a network flow model with upper and lower flow bounds.
4.1 Related concepts of network flow
-
1)
Capacity Network: Given a directed graph and the capacity of each arc , is called the capacity network.
-
2)
Source, Sink, and Intermediate Vertices: In a capacity network, the source node is denoted as with in-degree zero, the sink node has out-degree zero, and the other nodes are called intermediate vertices.
-
3)
Network Flow: A function defined from the arc set to the nonnegative number set is called the network flow on , while is the flow on arc .
- 4)
-
5)
Upper and Lower Bounds of Flow: For each arc of the directed graph , the capacity constraints (16) can be further extended with the upper bound flow and the lower bound flow .
-
6)
Minimum-cost maximum-flow: Given a capacity network , the cost of the unit flow for arc is denoted as . The minimum-cost maximum-flow problem is to find a feasible flow , so that
(19)
4.2 Network flow model for multi-UAV task assignment
According to the concepts of network flow introduced in the previous section, the task assignment problem of multi-UAV searching and tracking multi-target can be modeled as a network flow model with upper and lower flow bounds.
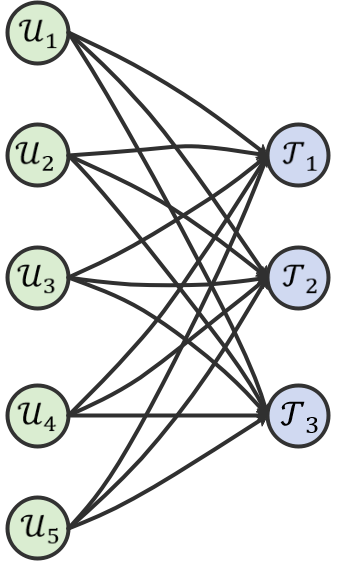
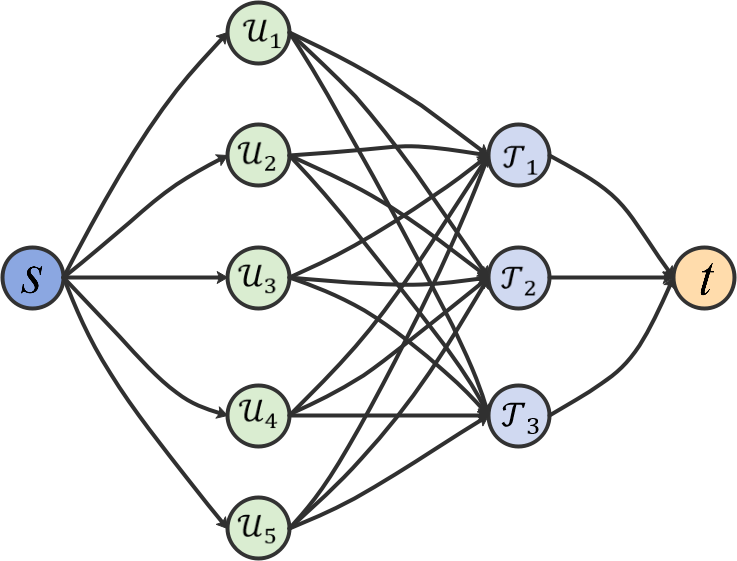
We first build a graph (See Fig. 6) with the UAV vertices , the target vertices , and the edges connecting each UAV vertex and each target vertex. Then, graph (See Fig. 6) can be obtained by adding a source vertex , a sink vertex , and new edges and .
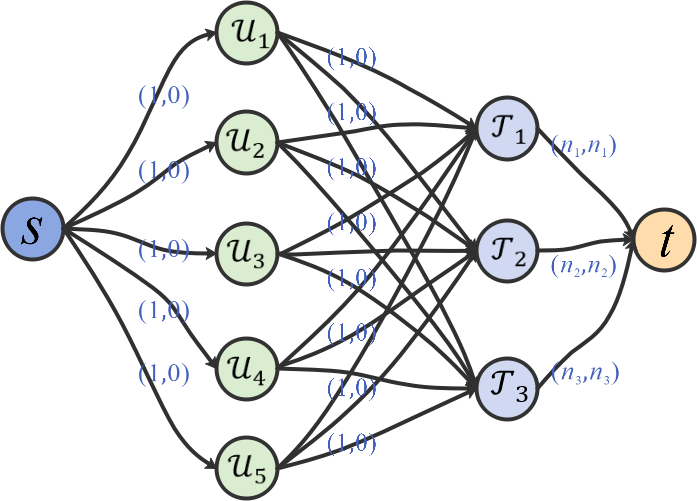
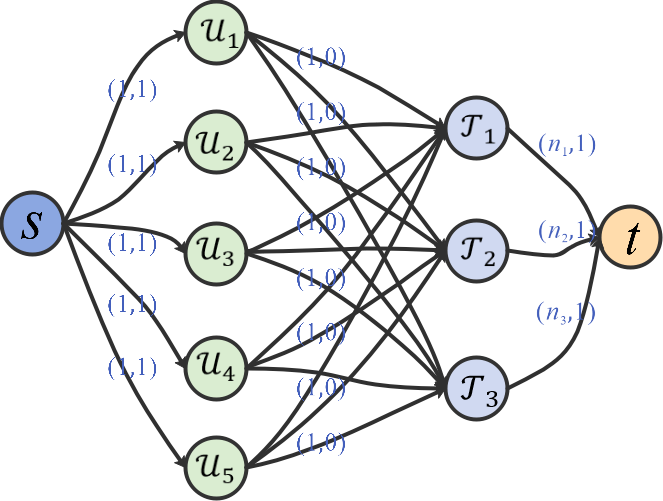
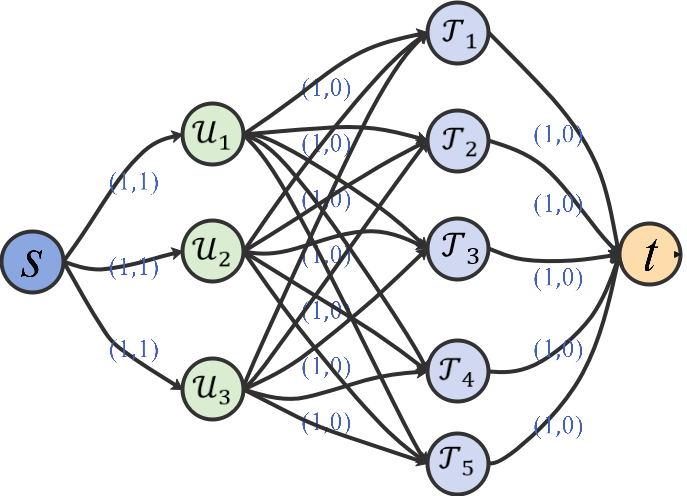
Considering the relationship between the number of UAVs , the number of targets , and the maximum number of UAVs required for all targets , graph can be further transformed into a capacity network by adding some flow bounds (See Fig. 7).According to the optimization objective function (2), our goal is to maximize the task rewards of the multi-UAV system. Then we set the cost of arc as and the cost of all other arcs as 0. The flow bounds and cost for each arc in the transformed network is shown in Table 3.
| Numerical relationship | Flow bounds/ | Cost | |||
|---|---|---|---|---|---|
| (1,0) | (1,0) | () | 0 | ||
| (1,0) | (1,1) | () | 0 | ||
| (1,0) | (1,1) | (1,0) | 0 | ||
Definition 2 (Network flow model for multi-UAV task assignment).
Given a graph constructed by all UAV vertices and target vertices, set the upper flow bound of arc as 1 and the lower as 0. According to the numerical relationship between , , and , add the flow bounds and the cost to arc and arc with Table 3. The resulting capacity network is a network flow model with upper and lower flow bounds for multi-UAV task assignment.
For the transformed network, the feasible flow that satisfies the flow constraints must be the maximum flow. Moreover, when the network cost is minimized, the reward of the corresponding multi-UAV system is maximized. So far, the multi-UAV task assignment problem has been transformed into an MCMF problem.
4.3 Task assignment minimum-cost maximum-flow algorithm
The traditional MCMF algorithm is aimed at the case where there is no lower flow bound. Therefore, we further convert the network obtained in Section 4.2 and design an algorithm named task assignment minimum-cost maximum-flow (TAMM) for our multi-UAV task assignment problem. The detailed TAMM algorithm is given in Algorithm 2. In order to describe the algorithm more clearly, we first define the sum of the lower flow bounds of all arcs flowing into vertex and that flowing out of as and .
The basic idea of TAMM is to convert the network with lower flow bounds into the network without lower flow bounds by adding new source vertex, sink vertex, and related edges. The detailed conversion process is shown in Fig. 8. Then the minimum-cost maximum-flow method can be used to find the MCMF of the converted network. The task assignment results can be obtained by mapping the obtained flow to the matching relationship between UAVs and targets.
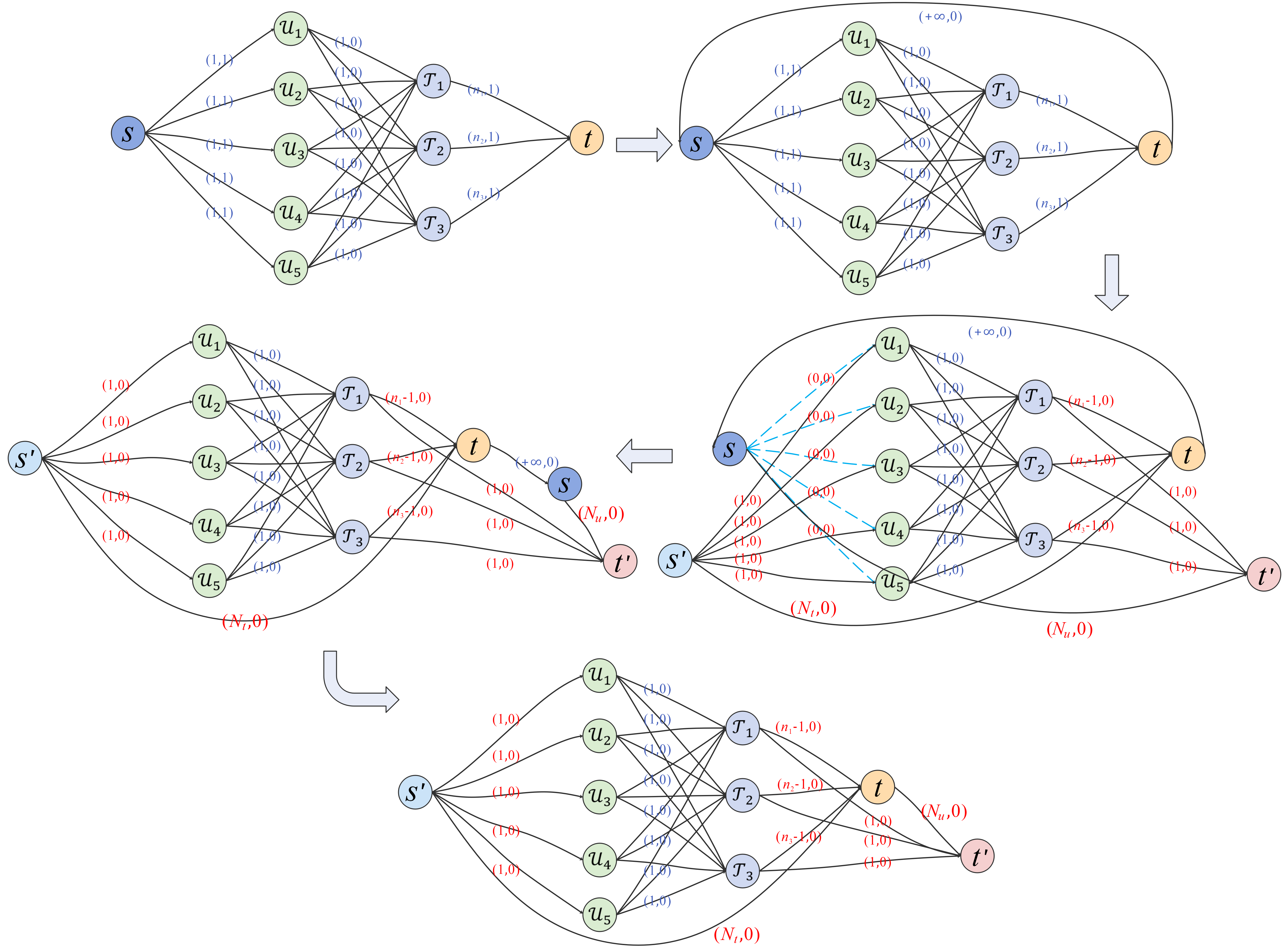
Remark 3.
Our task assignment algorithm entails a complexity . Since and in network , the complexity of task assignment is . Therefore, our TAMM algorithm has the polynomial time complexity and can quickly solve the multi-UAV task assignment problem.
Since the MCMF of corresponds to the allocation plan that maximizes the task reward. To illustrate the MCMF of the converted network also corresponds to the allocation plan with the maximum task reward, we introduce the following theorem.
Theorem 1.
Given the network with the upper and lower bounds, construct the network following the steps in Algorithm 2, then the minimum-cost maximum-flow of the original network is also that of the converted network .
Proof: In the transformation process, the original network is first converted into the no-source and no-sink network by introducing an arc with the capacity constraint . The minimum-cost maximum-flow of the original network is also that of . After that, each step of the transformation from network to network follows the conservation constraints (17).
Then, if a feasible flow makes any arcs or in reach maximum capacity, this flow must be a feasible flow of network . On the contrary, any feasible flow in network corresponds to the flow whose arc or achieves maximum capacity in network .
The flow reaching maximum capacity from the source to the sink of network must be the maximum flow of the network. Therefore, finding a feasible flow of network is equivalent to finding the maximum flow from to of network .
According to the flow constraints of and in network , the feasible flow of must be its maximum flow. Then the maximum flow of the network is also the maximum flow of . Since the cost of the newly added arc is 0, the minimum-cost maximum-flow of the converted network is that of . Furthermore, is also the minimum cost maximum-flow of the original network .
5 Multi-UAV behavior decision-making
In our modular framework, the cooperative behavior decision-making process includes tracking behavior decision-making module and coverage behavior decision-making module. The main idea of cooperative behavior decision-making is to first get the tracking action and the corresponding rewards through the tracking decision-making for each UAV and then assign tasks to UAVs according to the reward matrix. If a UAV is assigned one target to track, its action is the optimal tracking action calcaulated by tracking decision-making module. While if a UAV is assigned no target to track, it then plans its action through coverage decision-making.
5.1 Tracking behavior decision-making
The objective of tracking decision-making is to plan the actions of UAVs according to the predicted target states to obtain more accurate measurements of targets.
We use the determinant of the Fisher information matrix (FIM) as the reward value. bib34 explained the reasons for using FIM as the reward function: FIM processes the original measurement data from the sensor and is derived from the measurement model in the natural sensor polar coordinate system directly, reflecting the volume of information of the measurement data.
The FIM of UAV about target at time is defined as , and denotes the determinant of the FIM. When considering the information accumulated over time step, the reward at time step can be approximated by the sum of the determinants of the FIM as follows:
| (20) |
The tracking decision-making algorithm based on the rolling horizon method finds the optimal action sequence that maximizes the cumulative Fisher information volume.
| (21) |
At time step , each UAV predicts the target positions of the future steps according to the state updated in the distributed fusion phase. Then the optimal planning method is used to find the optimal action sequence that maximizes the objective function. The planned action of is the first item of the optimal action sequence, which is:
| (22) |
We also call the planned action the optimal tracking action. The optimal tracking action of UAVs at each step can be obtained by repeating the above process.
5.2 Coverage behavior decision-making
The purpose of the area coverage task is to continuously search the targets and reduce the uncertainty of the dynamic environment. Inspired by solitary organisms, the distributed anti-flocking algorithm bib20 is well suited for area coverage tasks and is summarized as follows: 1) Collision avoidance: avoid surrounding obstacles and neighbors. 2) Decentralization: move away from neighboring centers. 3) Selfishness: maximize own gains.
Our previous work bib18 designed a distributed multi-UAV persistent coverage algorithm based on the anti-flocking method, of which several area coverage information maps are designed. The algorithm uses the collision avoidance and decentering rules in the anti-flocking method to design a heading matching map (HMM), making the UAVs disperse from each other to increase the instantaneous coverage area and avoid collisions. The EVTM, the compressed EVTM, and the HMM are integrated to calculate the detection rewards of UAVs and guide the UAV to the area where the rewards are maximized. We briefly describe the algorithm below.
First, calculate the desired separation heading of each UAV through the rules of collision avoidance and decentering.
| (23) |
is a non-negative repulsive potential function. represents the safety distance of , is the distance threshold that the decentering term works, and is the total number of neighboring obstacles and UAVs of . Besides, denotes the position of the centroid of the neighbor UAVs.
Let denote the heading of to the grid , that is:
| (24) |
where represents the position of grid .
The heading matching value between and the desired heading is:
| (25) |
where is the deviation value between and .
Then the coverage reward is calculated from EVTM . We define the coverage reward that obtains from grid by the visiting requirement as follows:
| (26) |
Suppose is located at at the next step and denotes the detection area of , then the predicted coverage reward is:
| (27) |
The global searching reward map of is , which calculated from the compressed EVTM as follows:
| (28) |
Furthermore, we need to extract the heading matching value and the coverage reward of the grids around the location of the UAV to get the local heading matching map and local coverage reward map . The overall coverage reward map (OCRM) consists of the weighted sum of , , and , which is:
| (29) |
where , and are the weights of the corresponding term.
Based on the selfishness rule of the anti-flocking method, we directly select the grid with maximum reward in the OCRM as the target grid . denotes the grid with the maximum reward in map . When is located at , then and .
Finally, let be the desired gird of . The control input of is:
| (30) |
is the position of grid . And is the desired heading when flies to from its current position, which is:
| (31) |
6 System design of distributed multi-UAV cooperative area coverage and target tracking
Integrating the information fusion strategy, the task assignment method, and the behavior decision algorithm designed in Sections 3-5, this section designs the distributed multi-UAV cooperative area coverage and target tracking algorithm. The framework is shown in Fig. 9.
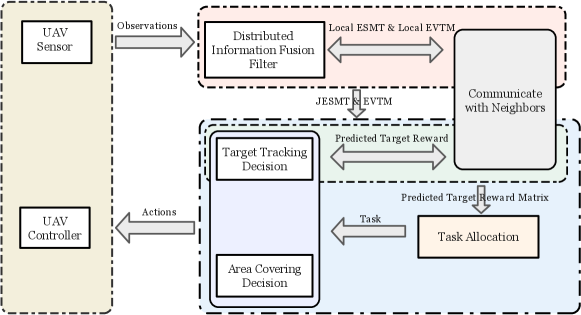
As shown in the information fusion process, we use the maximum consensus protocol to update the joint estimation state of multi-targets and the equivalent visiting time map, which reach the consensus in the connected communication network after limited iterations. Then each UAV uses the Fisher information reward value to get the optimal tracking action sequence and exchanges the Fisher information reward with its neighbors to get the reward matrix. The task assignment method based on minimum-cost maximum-flow assigns the task to each UAV that maximizes the task reward. If is assigned a target to track, the optimal tracking action of is the first item of the optimal tracking action sequence. While for those UAVs assigned the coverage task, we use the coverage behavior decision-making algorithm based on the anti-flocking method to plan its action.
In particular, the task assignment algorithm in Section 4 needs to know the global reward matrix. While each UAV only has its reward about targets initially. Therefore, each UAV exchanges the Fisher information reward with its neighbors. Through limited updates with max-consensus protocol, the reward matrix of all UAVs in the connected network achieves consistency. As with the information fusion algorithm in Section 3, we set the iteration number for the th UAV as according to the termination condition of the maximum consistency algorithm given in bib34 . Therefore, the distributed information interaction enables the proposed task allocation algorithm to be adapted to the overall distributed framework.
Algorithm 3 below summarizes the distributed approach for local detection, fusion, assignment, and decision-making of .
In the tracking behavior decision phase, each UAV calculates its rewards for all tasks. The complexity of a single step of computing is , where is the cardinality of the action set. Compared with the computational complexity of the centralized decision-making, our approach has lower computational complexity. Apart from the decision-making phase, the task assignment phase entails a complexity . The information fusion phase also has low computational complexity. Therefore, our distributed hierarchical modular algorithm can be well applied to the area coverage and target tracking tasks of a large area with multiple UAVs.
7 Simulation results
The proposed Algorithm 3 for area coverage and target tracking has been analyzed in the simulated environment. The area surveillance mission aims to maintain continuous coverage of the area and keep track of the detected targets. We evaluate the performance of our method through performance indicators such as area uncovered time and target observation coverage rate in a series of simulations. The setup for the different simulations and their corresponding results are detailed in the following subsections.
7.1 Simulation setup
Suppose the UAV flies at a fixed altitude of , and the communication radius between the UAV is set through specific experiments. We set the task area to be which is rasterized into grids with both length and width of . ground moving targets are initially randomly distributed in this area, and their speed and heading can change with time. The sensor parameters are the same as those in bib34 .
The numerical simulation is implemented on MATLAB R2020b, and Fig. 10 is one example of the simulation scenarios. And we also perform the hardware-in-the-loop simulations, which are described in Section 7.3. Assuming that each target can be tracked by a maximum of 2 UAVs simultaneously, set the parameters related to grid visiting requirements as and the related parameters of sensor detection performance as . Considering the randomness of the experiment, including the initial positions of the target and the UAV, and the random movement of the target, we performed 50 repetitions of each set of experiments with 1500 simulation steps to get average results.
7.2 Simulation analysis
7.2.1 The effect of different parameters
In this subsection, we take the simulations with different communication ranges and UAV numbers to study the effect of these parameters on the performance of our distributed area surveillance method.
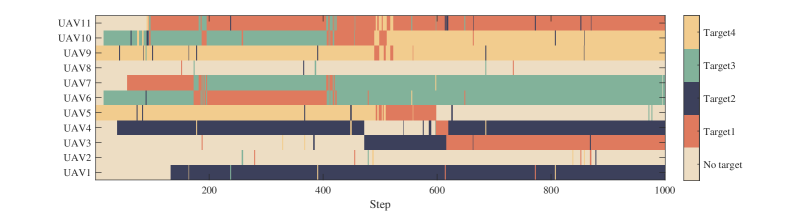
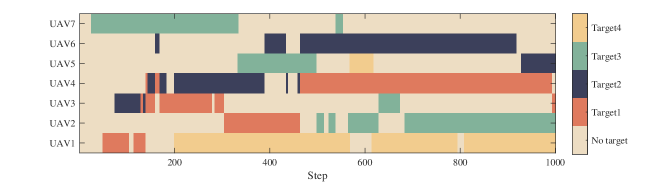
First, we set the UAV numbers as with a fixed communication radius of . Since the target is tracked by at most two UAVs, ideally, when , there have some targets that are not assigned to the UAV. When , each target can be assigned to at least one UAV to track. When , each target can be assigned to two UAVs to track. Fig. 11 is an example of the allocation result when the number of UAVs is 11. Due to the random movement of the target, the detected targets can be lost and require the multi-UAV system to search the targets again.
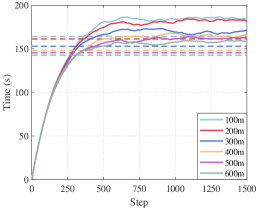
We use the instantaneous average uncovered time to present the coverage performance of our algorithm, as shown in Fig. 13. indicates the average uncovered time of all grids at time step . We find that the higher the number of UAVs, the shorter the average uncovered time, indicating a shorter visit interval.
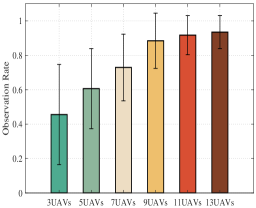
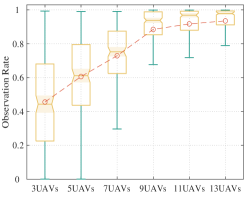
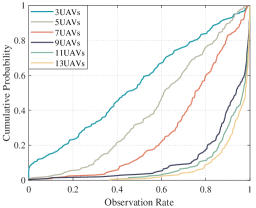
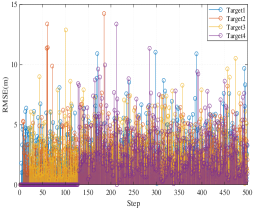
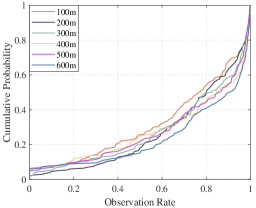
For the target tracking effect, we use the observation coverage rate to represent the ratio of the time duration that the target is observed to the total simulation time. The average observation coverage rate of all targets is shown in Fig. 13. Since the initial positions of the UAVs and the targets are random and the target moves randomly, the tracking performance can be measured directly using the overall average observation rate. Fig. 13 shows that with the increase of the UAV numbers, the average observation rate of the targets is also gradually increasing. The distribution of the observation coverage rate for our repeated simulations is shown in Fig. 14. It indicates that the observation coverage rate of most of the targets is maintained at a high level when the number of UAVs is more than that of targets. Moreover, Fig. 16 shows the RMSE of targets in one simulation.
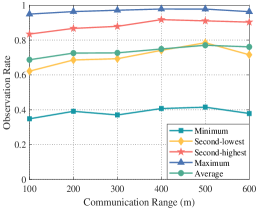
Then, we evaluate the performance under different communication ranges, which vary from to (See Fig. 16 and 17). To explore the influence of the communication range on the coverage performance, we consider that UAVs only perform the coverage task. Fig. 16 indicates that the uncovered time decreases gradually with the increased communication ranges. When simultaneously considering the search and tracking tasks, since the target tracking algorithm can ensure the targets are tracked most time, the communication range has little effect on the observation coverage rate, as shown in Fig. 17. Simulation results show that the area coverage and target tracking performance can be enhanced by improving communication capability.
7.2.2 Comparison with other algorithms
Here, we compare our method with the simultaneous coverage and tracking (SCAT) algorithm in bib2 and the multi-target tracking (MT) algorithm in bib34 . The SCAT method in bib2 translates the area coverage and target tracking problem to the problem of covering environments with time-varying density functions. However, the target tracking task is not explicitly considered in SCAT. The MT method in bib34 uses the distributed partially observable Markov decision algorithm to make tracking decisions. It assumes that the targets are initially located in the field of view of the UAVs. In order to make the comparison reasonable, we combine our coverage algorithm with the MT algorithm for the subsequent comparison, called CMT. In addition, the task assignment of the MT algorithm adopts multiple rounds of 1-to-1 assignment to solve the many-to-many assignment problem. There are no restrictions on the number of UAVs tracking the same target, resulting in UAVs selecting to perform the tracking task. We limit the number of 1-to-1 assignments in the task allocation part of CMT and call this algorithm as L-CMT.
We compare these algorithms from the target observation coverage rate and the area uncovered time. We set the number of UAVs as 7 and the number of targets as 4 in subsequent comparisons.
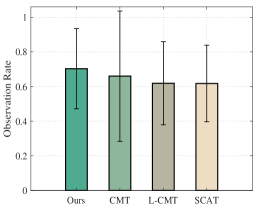
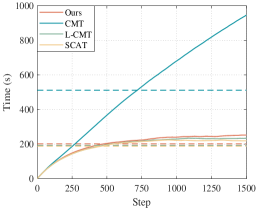
Fig. 19 shows the average observation coverage rate of all targets. The average observation coverage rate is for our method, for the CMT method, for the L-CMT method, and for the SCAT method. Fig. 19 shows the average uncovered time of the mission area. The average uncovered time of the SCAT method is the smallest, indicating the coverage performance of SCAT is the best. Since the SCAT algorithm ignores the explicit tracking of the target, its coverage performance is good, while the tracking performance is poor. The CMT algorithm does not limit the number of UAVs tracking the same target, making UAVs tend to choose the tracking task and sometimes focus on tracking the same targets. Thus, the CMT algorithm has the worst area coverage performance. Besides, the target observation coverage variance of CMT is the largest. The L-CMT method improves the coverage performance of CMT by limiting the number of allocations. Due to the design of the task assignment minimum-cost maximum-flow algorithm, our method has the best tracking effect, and the area coverage effect is slightly lower than that of L-CMT and SCAT methods. These simulation results indicate that our method is more suitable for the area coverage and target-tracking task.
7.2.3 Other performance
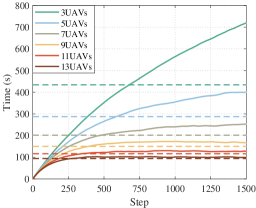
Here, we also list the time taken by the allocation algorithm in Table 4, which shows that our allocation algorithm can be applied to the fast real-time allocation of large-scale tasks.
| Time use (s) | 0.00218 | 0.00948 | 0.02526 |
| Time use (s) | 0.00925 | 0.01168 | 0.01469 |
| Time use (s) | 0.00491 | 0.00768 | 0.01083 |
| \botrule |
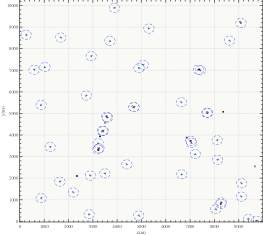
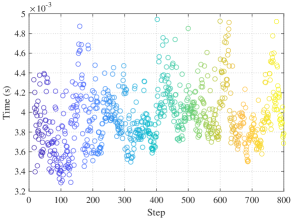
In addition, to reflect the scalability of the distributed algorithm, we set the task area as 10km*10km with 50 UAVs and 15 targets in Fig. 21. Fig. 21 shows the single-step decision-making time of the simulation, which can meet the needs of real-time decision-making.
7.3 Hardware-in-the-loop simulation
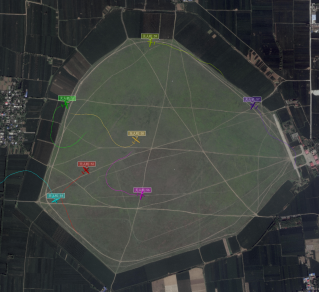
The hardware-in-the-loop (HIL) verification of our distributed area coverage and target tracking algorithm is carried out through the the HIL simulator bib55 constructed by our team. We set the task area as 2.5km*2.5km with 7 UAVs and 4 moving targets. As shown in Fig. 22, all UAVs take the area coverage task when there are no targets. Fig. 22 shows that the UAV automatically decides the task mode when detecting the targets, and each target is assigned to one UAV for tracking. While the remaining UAVs carry out the area coverage tasks.

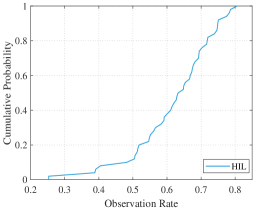
We count the target observation coverage rate and the area uncovered time of multiple HIL simulations (See Fig. 24 and 24). Here, the coverage and tracking performance difference between HIL simulations and numerical simulations mainly comes from the uncertainty of the underlying modeling in hardware-in-the-loop simulations. The average observation coverage rate is in HIL simulatons. Moreover, the assignment results in one of the HIL simulations are given in Fig. 25. The hardware-in-the-loop simulations demonstrate the feasibility of the real-time onboard implementations of our area coverage and target tracking algorithm.
8 Conclusion
This paper proposes a distributed algorithm for area coverage and multi-target tracking. We use a distributed information fusion strategy based on maximum consensus protocol to estimate the joint state of multi-targets and get the joint detection information of the mission area. We also design a task allocation algorithm based on minimum cost and maximum flow. Optimal tracking and area coverage action are obtained based on optimal planning and distributed anti-flocking algorithm. In the distributed information fusion phase, we introduce the area compression map to extend the coverage algorithm to any large task area, and the scalability is verified in the simulation. In addition, combined with the consensus strategy, the designed network flow allocation algorithm is implemented in a distributed way. And we use the Fisher information as the task reward of target tracking.
We apply the integrated algorithm to area coverage and target tracking tasks and study the effects of the number of UAVs and communication range on the coverage and tracking performance. The results show that the coverage performance of UAVs can be significantly enhanced by increasing their scale and improving their communication capability. However, the communication range has little effect on the tracking performance. In addition, we apply our algorithm in the hardware-in-the-loop simulation of area coverage and target tracking tasks.
In future work, we will consider these problems and focus on reducing the communication load and dealing with the communication delay problem to promote the practical application of the algorithm.
References
- \bibcommenthead
- (1) Meng, W., He, Z., Teo, R., Su, R., Xie, L.: Integrated multi-agent system framework: Decentralised search, tasking and tracking. IET Control Theory and Applications 9, 493–502 (2015)
- (2) Pimenta, L.C.A., Schwager, M., Lindsey, Q., Kumar, V., Rus, D., Mesquita, R.C., Pereira, G.A.S.: Simultaneous Coverage and Tracking (SCAT) of Moving Targets with Robot Networks, vol. 57, pp. 85–99. Springer, Berlin, Heidelberg (2010)
- (3) Moon, S., Frew, E.W.: Distributed cooperative control for joint optimization of sensor coverage and target tracking. In: 2017 International Conference on Unmanned Aircraft Systems (ICUAS), pp. 759–766 (2017)
- (4) Semnani, S.H., Basir, O.A.: Semi-flocking algorithm for motion control of mobile sensors in large-scale surveillance systems. IEEE Transactions on Cybernetics 45(1), 129–137 (2015)
- (5) Meng, W., He, Z., Su, R., Yadav, P.K., Teo, R., Xie, L.: Decentralized multi-UAV flight autonomy for moving convoys search and track. IEEE Transactions on Control Systems Technology 25(4), 1480–1487 (2017)
- (6) Yuan, W., Ganganath, N., Cheng, C.-T., Qing, G., Lau, F.C.M.: Semi-flocking-controlled mobile sensor networks for dynamic area coverage and multiple target tracking. IEEE Sensors Journal 18(21), 8883–8892 (2018)
- (7) Yuan, W., Ganganath, N., Cheng, C.-T., Valaee, S., Qing, G., Lau, F.C.M., Iu, H.H.C.: Semi-flocking-controlled mobile sensor networks for tracking targets with different priorities. In: 2019 IEEE International Symposium on Circuits and Systems (ISCAS), pp. 1–5 (2019)
- (8) Achanta, S.: Passive target tracking using unscented kalman filter based on monte carlo simulation. Indian Journal of Science and Technology, 8, 1–5 (2015)
- (9) Lee, D.-y., Shim, S.-W., Hwang, M.-c., Tahk, M.-J.: Target tracking using adaptive coarse-to-fine particle filter. In: AIAA Guidance, Navigation, and Control Conference (2017)
- (10) Ren, W., Beard, R.W., Atkins, E.M.: Information consensus in multivehicle cooperative control. IEEE Control Systems Magazine 27(2), 71–82 (2007)
- (11) Yu, D., Xia, Y., Li, L., Zhu, C.: Distributed consensus-based estimation with unknown inputs and random link failures. Automatica 122, 109259 (2020)
- (12) Fanti, M.P., Mangini, A.M., Ukovich, W.: A quantized consensus algorithm for distributed task assignment. In: 2012 IEEE Conference on Decision and Control (CDC), pp. 2040–2045 (2012)
- (13) Luo, L., Chakraborty, N., Sycara, K.: Distributed algorithms for multirobot task assignment with task deadline constraints. IEEE Transactions on Automation Science and Engineering 12(3), 876–888 (2015)
- (14) Zhao, Y., Wang, X., Wang, C., Cong, Y., Shen, L.: Systemic design of distributed multi-uav cooperative decision-making for multi-target tracking. Autonomous Agents and Multi-Agent Systems 33, 132–158 (2019)
- (15) Bänziger, T., Kunz, A., Wegener, K.: Optimizing human-robot task distribution using a simulation tool based on standardized work descriptions. Journal of Intelligent Manufacturing 31, 1635–1648 (2020)
- (16) Wu, W., Nai-gang, C.: Distributed task allocation for multiple heterogeneous uavs based on consensus algorithm and online cooperative strategy. Aircraft Engineering and Aerospace Technology 90(9), 1464–1473 (2018)
- (17) Chen, X., Zhang, P., Du, G., Li, F.: A distributed method for dynamic multi-robot task allocation problems with critical time constraints. Robotics and Autonomous Systems 118, 31–46 (2019)
- (18) Dantzig, G., Thapa, M.: Network Flow Theory, pp. 253–313. Springer, New York, NY (1997)
- (19) Li, B., Springer, J., Bebis, G., Gunes, M.: A survey of network flow applications. Journal of Network and Computer Applications 36(2), 567–581 (2013)
- (20) Zhu, K., Han, B., Zhang, T.: Multi-UAV distributed collaborative coverage for target search using heuristic strategy. Guidance, Navigation and Control 01(1), 2150002 (2021)
- (21) Ni, J., Tang, G., Mo, Z., Cao, W., Yang, S.X.: An improved potential game theory based method for multi-uav cooperative search. IEEE Access 8, 47787–47796 (2020)
- (22) Chen, J., Du, C., Zhang, Y., Han, P., Wei, W.: A clustering-based coverage path planning method for autonomous heterogeneous uavs. IEEE Transactions on Intelligent Transportation Systems, 1–11 (2021)
- (23) Liu, Z., Gao, X., Fu, X.: A cooperative search and coverage algorithm with controllable revisit and connectivity maintenance for multiple unmanned aerial vehicles. Sensors 18(5), 1472 (2018)
- (24) Ganganath, N., Cheng, C.-T., Tse, C.K.: Distributed antiflocking algorithms for dynamic coverage of mobile sensor networks. IEEE Transactions on Industrial Informatics 12(5), 1795–1805 (2016)
- (25) Ganganath, N., Yuan, W., Fernando, T., Iu, H.H.C., Cheng, C.-T.: Energy-efficient anti-flocking control for mobile sensor networks on uneven terrains. IEEE Transactions on Circuits and Systems II: Express Briefs 65(12), 2022–2026 (2018)
- (26) Zhang, M., Liu, H.: Cooperative tracking a moving target using multiple fixed-wing uavs. Journal of Intelligent and Robotic Systems 81, 505–529 (2016)
- (27) Monajemi Nejad, B., Attia, S., Raisch, J.: Max-consensus in a max-plus algebraic setting: The case of fixed communication topologies, pp. 1–7 (2009)
- (28) Miao, Y.-Q., Khamis, A., Kamel, M.S.: Applying anti-flocking model in mobile surveillance systems. In: 2010 International Conference on Autonomous and Intelligent Systems, AIS 2010, pp. 1–6 (2010)
- (29) Zhang, M., Li, H., Li, J., Wang, X.: A distributed persistent coverage algorithm of multiple unmanned aerial vehicles in complex mission areas. In: 2021 IEEE International Conference on Robotics and Biomimetics (ROBIO), pp. 1835–1840 (2021)
- (30) Chen, H., Cong, Y., Wang, X., Xu, X., Shen, L.: Coordinated path-following control of fixed-wing unmanned aerial vehicles. IEEE Transactions on Systems, Man, and Cybernetics: Systems 52(4), 2540–2554 (2022)