[1]\textbf\textitIndex terms— #1
Integrated Sensing and Communication for Edge Inference with End-to-End Multi-View Fusion
Abstract
Integrated sensing and communication (ISAC) is a promising solution to accelerate edge inference via the dual use of wireless signals. However, this paradigm needs to minimize the inference error and latency under ISAC co-functionality interference, for which the existing ISAC or edge resource allocation algorithms become inefficient, as they ignore the inter-dependency between low-level ISAC designs and high-level inference services. This letter proposes an inference-oriented ISAC (IO-ISAC) scheme, which minimizes upper bounds on end-to-end inference error and latency using multi-objective optimization. The key to our approach is to derive a multi-view inference model that accounts for both the number of observations and the angles of observations, by integrating a half-voting fusion rule and an angle-aware sensing model. Simulation results show that the proposed IO-ISAC outperforms other benchmarks in terms of both accuracy and latency.
Index Terms:
Edge inference, integrated sensing and communication, multi-view fusion.I Introduction
Realizing perception intelligence at distributed wireless sensors is a challenge due to the conflict between computationally demanding deep neural networks (DNNs) and computationally limited sensors [1]. Edge inference eases this conflict by providing DNN inference services to sensors with a proximal server [2], [3]. Existing edge inference consists of sensing, communication, and computation [2]. In this letter, the sensing and communication stages are merged via the ISAC technique, leading to a two-stage edge inference solution, i.e., , thus a one-stage reduction compared to the existing solution.
In contrast to existing ISAC systems [4], ISAC edge inference systems aim to minimize the inference error instead of maximizing the sensing resolution or the communication data-rate. Therefore, the associated resource allocation becomes very different from traditional ISAC resource allocation that considers only the wireless channels. For instance, the celebrated CRB-rate scheme allocates more resources to deterministic (random) channels for CRB (rate) maximization [5], and the multi-point ISAC scheme allocates more resources to closer-to-target devices to maintain the quality of sensing measurements [6]. While these schemes have proven to be very efficient in traditional ISAC systems, they could lead to poor performance in edge inference systems (as illustrated in Fig. 1), because they do not account for the inference requirements, e.g., the sensing data diversity that depends on the angle of observation. Note that existing edge inference schemes consider off-the-shelf sensing datasets, which ignore low-level sensing signal designs (e.g., physical-layer beamforming and power allocation) [7] and their impact on high-level inference services.
This paper proposes an end-to-end approach that integrates sensing, communication, and computation objectives and constraints into a unified optimization framework. First, to optimize the inference performance, we need an expression for the multi-view inference error with respect to the number of observations and the angles of observations. Hence, this paper derives an end-to-end inference error model by integrating a half-voting fusion rule and an angle-aware sensing model, and this newly derived model serves as an upper bound on the actual inference error. Second, while ISAC inference eliminates one stage, it does not necessarily reduce the end-to-end inference latency, as ISAC also introduces interference between sensing and communication functionalities [8]. Therefore, this paper further derives the upper bound of the end-to-end sensing, communication, and computation latency with respect to the co-functionality interference. Third, to optimize the two conflicting objectives. i.e., inference error and inference latency, we minimize their upper bounds according to majorization minimization (MM), and propose a joint power allocation and device scheduling (JPADS) algorithm, leading to an inference-oriented ISAC (IO-ISAC) scheme. Finally, various simulation results demonstrate the effectiveness of our proposed scheme, and show that the proposed IO-ISAC outperforms other benchmark schemes in terms of the inference accuracy and latency. To the best of our knowledge, this represents the first inference oriented paradigm guiding the design of ISAC systems.
II System Model
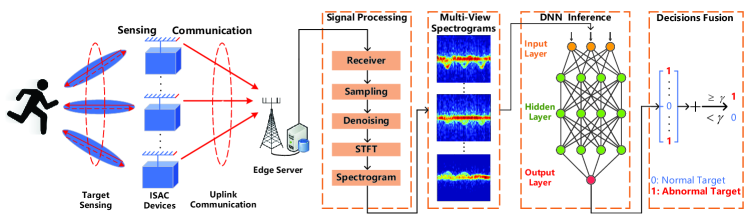
We consider an ISAC edge inference system shown in Fig. 1, which consists of ISAC devices each with antennas and one edge server with antennas. The task of our system is to detect the state of a target (i.e., normal or abnormal) using two consecutive stages. In the first ISAC stage, ISAC devices transmit radio signals to sense the target and upload the echo sensing data to the server simultaneously at the same frequency band. In the second computation stage, the server extracts features from the sensing data using DNNs and fuses the local inference results into a global decision. Below we present the model for the ISAC stage.
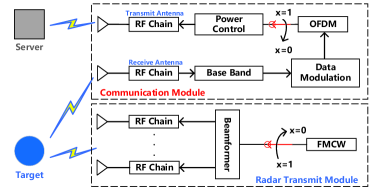
In particular, Fig. 1 demonstrates the architecture of an ISAC device, which consists of transmit antennas and receive antennas, where . The transmit antennas are divided into two groups [9], with antennas for sensing and the other antennas for communication. Without loss of generality, it is assumed that . To mitigate the interference leakage and energy cost, an activity controller with binary output is adopted to determine the working state of the -th ISAC device, where represents that the -th ISAC device is activated and otherwise. Let denote the states of all ISAC devices and denote the set of activated ISAC devices with cardinality .
II-1 Target Sensing Model
The -th ISAC device sends a sensing signal to probe the target and the echo signal received at the -th ISAC device is
| (1) |
where , with is the sensing signal, with is the communication signal, and is additive white Gaussian noise (AWGN) with power . Vector denotes the sensing echo channel from the -th device to the target and then back to the -th device. The vectors and denote the sensing interference channel from the -th device to the -th device and the sensing beamformer of the -th device, respectively. The scalars and represent the communication transmit power of the -th device and the communication interference channel from the -th device to the -th device, respectively. We adopt zero-forcing beamforming to mitigate sensing interference among different devices [10], where and denote the transmit sensing power and the steering vector for interference cancelation of the -th device. The vector is the normalized -st column of , where for and . The sensing signal-to-interference-plus-noise ratio (SINR) of the -th ISAC device is
| (2) |
Remark 1: The echo signal will be fed to the processor module for generating micro-doppler spectrograms shown in Fig. 1. As such, the target sensing problem is transformed into an image classification problem that can be solved by DNNs [11]. Note that if the sensing SINR is below a certain threshold, the spectrogram quality and the DNN accuracy would be significantly degraded as shown in Fig. 5 of [12]. Such degradation also emerges if the sensing angle exceeds a certain threshold [11], as shown in Fig. 1.
II-2 Uplink Communication Model
The -th ISAC device also transmits the communication signal for uploading the echo sensing data to the edge server, and the associated received signal at the server is [13]
| (3) |
where , the vector is the communication channel from the -th device to the server. The matrix represents the sensing interference channel from the -th device to the edge server. The vector is the AWGN. Since the transmitted sensing signal is deterministic, e.g., frequency modulated continuous wave (FMCW), and the channels are known at the server, the sensing interference term can be eliminated [14]. The server exploits a receiving filter to recover the transmit signal of the -th device. The uplink signal of the -th device recovered at the server is , i.e., . Here we adopt zero-forcing receive filters such that for , where , . The associated uplink communication SINR of the -th device is
| (4) |
III Inference Oriented ISAC
This section presents the end-to-end model and algorithms by integrating the and stages. First, each DNN at the server recognizes the micro-Doppler spectrograms generated by active devices as shown in Fig. 1. Then multiple DNN inference results are fused into a global inference output via voting. The inference error (i.e., denotes inference accuracy) and latency are functions of activation switch , sensing signal powers , and communication signal powers . The inference oriented problem is formulated as a multi-objective optimization problem of minimizing the error and the latency of inference, under individual and total transmit power constraints:
| (5a) | ||||
| (5b) | ||||
| (5c) | ||||
where and represent the maximum transmit power of the system and of each ISAC device, respectively. The challenge to solve is that the functions have no explicit expressions. To address this issue, Sections III-A and III-B will derive bounds for , and Section III-C optimizes the bounding functions according to MM.
III-A End-to-End Inference Error Model
We first derive the inference accuracy when . Without loss of generality, consider the -th ISAC device and its inference accuracy is modeled as
| (6) |
where represents the probability function, and are hypotheses that represent “normal target” and “abnormal target”, and are the prior probabilities of the two hypotheses, and represents the binary inference result of the -th device, with standing for “normal target” and standing for “abnormal target”. Now we consider two factors that affect as mentioned in Remark 1. First, depends on the . If , where denotes the sensing quality threshold, then a satisfactory can be achieved; otherwise, would be degraded by a certain factor. According to [12], we set . Second, depends on the observation angle , which is defined as the aspect angle between the line-of-sight direction and the target motion direction. If , where denotes the angle threshold, a satisfactory can be achieved; otherwise, would be degraded by a certain factor. According to [11], we set . Based on the above, the false alarm probability is modeled as
| (9) |
where is a constant value and is the degradation factor. Similarly, the missed detection probability is given by if the SINR and observation angle requirements are satisfied; and otherwise, where is also a constant. The values of can be estimated from the experimental data [12, 6].
With the single-device model, we can derive the multi-view inference accuracy model . Let denote the voting threshold111The most widely adopted threshold is , which corresponds to the half-voting rule for ensemble inference. such that our global inference after fusion is and . Following similar derivations in [6], the inference accuracy is given by , where is the actual number of ISAC devices satisfying the SINR and angle requirements, and
| (12) |
where , , and222Due to the different locations and observation views, the sensing data at different ISAC devices is assumed to be independent.
To compute using (12), we still need to compute . However, is random since depends on the unknown target motion. Fortunately, is a monotonically increasing function of due to the property of binomial functions. Therefore, we can bound from below to get a lower bound of . Specifically, let , and denote the intersection angle between the -th and -th devices with as (). Then we construct matrix , with the element being
| (13) | ||||
and the following proposition is established.
Proposition 1.
The global inference accuracy satisfies
| (14) |
Proof.
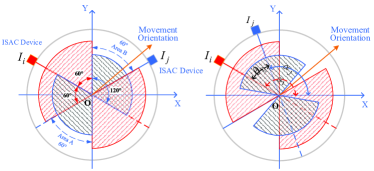
To prove the proposition, we only need to show that holds. We adopt the induction method to prove it, and first consider the two-devices case shown in Fig. 1.
-
•
If , then we have and . In such a case, the device always falls within the union of areas A and B as shown in the left hand side of Fig. 1. Hence we must have , and the target is guaranteed to be sensed by at least one ISAC device no matter in which direction the target moves. This implies that , and the holds.
-
•
If is not in the range of , then we have and . In such a case, there always exist sensing blind regions as shown in the right hand side of Fig. 1, and also holds.
Next, we prove the -devices case via graph theory. We use to represent an undirected graph, where is the set of nodes and is the set of edges between any two nodes in . Let , and connect nodes and to form edge if and ; otherwise, nodes and are not directly connected. For graph , we define as a matching of if and any two distinct edges in have no common endpoints. The size of , denoted as , is defined as the number of edges in . Then the maximum matching of , which is denoted by , represents the minimum number of ISAC devices with error probabilities no matter in which direction the target moves. This means that holds. On the other hand, according to the [15], we have . Therefore , and this completes the proof. ∎
III-B End-to-End Inference Latency Model
Mathematically, the end-to-end inference latency is equal to . Since sensing and communication are executed simultaneously in the ISAC stage, we have , where is the time for each ISAC device to sense the target and is the time for uploading sensing data to the server. Now we consider two cases: (i) , which happens if the target motion is slow and the communication speed is fast; (ii) , which happens if the target motion is fast and the communication speed is slow. In the considered system, due to co-channel interference brought by multiple working devices, the communicaion time is typically larger than the sensing time, so we have . Since the server needs to wait for the last data to be received for subsequent fusion, is upper bounded by the device with the worst channel, which is given by Where and represent the data volume per sample and the bandwidth for each device, and is the uplink spectral efficiency of the -th device in bps/Hz, which is written as
| (15) |
Moreover, the model computation time includes signal processing and DNN inference time, which is , where and represent the number of floating-point operations needed for processing each data sample and computing speed (FLOPs/s) at the server, respectively. The total latency for one inference round is bounded by
| (16) |
III-C MM Method and JPADS Algorithms
Based on the results in Sections III-A and III-B, we adopt the MM technique to replace functions with . Such a procedure would guarantee the worst-case performance of the ISAC edge inference system. Then problem is transformed into
| (17a) | ||||
| (17b) | ||||
This is a multi-objective mixed integer nonlinear programming (MO-MINLP) problem, and finding its Pareto optimal solutions is NP-hard in general. However, enjoys a special property that enables us to achieve Pareto optimality if the number of ISAC devices is small. In particular, given arbitrary device activation , problem with respect to is a convex problem
| (18) |
which can be solved by CVX with a computational complexity of . Note that to obtain from , we have removed the terms not related to , and leveraged the monotonicity of logarithm function. With the above property, the set of all Pareto optimal solutions can be found via a two-tier algorithm, with the outer layer explores all possible values of using exhaustive tree search, and the inner layer solving with a fixed controlled by the outer layer. This algorithm is named optimal-JPADS.
In practice, the number of ISAC devices may be large, and the optimal-JPADS algorithm would be time consuming. To this end, we further propose an iterative local search method, which is much faster and empirically achieves a solution set close to the Pareto optimality (as shown by experiments in Fig. 3b of Section IV).333The optimal solution to the weighted-sum problem of is not guaranteed to be a Pareto optimal solution [16]. First, we start from a feasible solution of , denoted as , and defines the neighborhood of as:
| (19) |
which is the variable size. Second, we randomly flip elements of to generate a new feasible solution . Third, with the choice of fixed to , we solves and obtains the associated optimal solution . Fourth, we compute the weighted-sum function , where denotes the weighting factor to balance the two objective functions, and consider the following two branches:444If the magnitudes of two conflicting objectives are close to each other, normalization is not needed [17].
-
•
If , we update . Then we construct the neighborhood of to execute the next iteration;
-
•
If , we execute the random flipping process repeatedly to generate another feasible solution within the until .
This process is executed iteratively until the maximum number of iterations is reached, generating a sequence . The entire algorithm is named fast-JPADS, and its complexity is .
IV Simulation Results
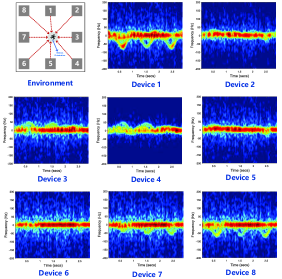
This section presents simulation results to verify the performance of the IO-ISAC scheme. We simulate the case of in a conference hall with size , and the associated sensing spectrograms are shown in Fig. 2. Unless otherwise specified, the maximum transmit power of each device is mW and the total transmit power budget is mW. The noise powers are set to dBm and dBm. All channels are modeled as distance-dependent rician fading, with dB pathloss at unit distance of m. The data volume per sample is MB.
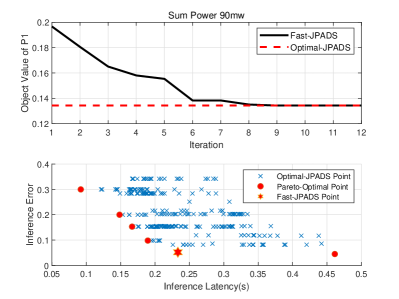
First, the sum of two objectives in versus the number of iterations under the fast-JPADS algorithm is shown in Fig. 2. It can be seen that the fast-JPADS converges to a value close to the lower bound obtained by optimal-JPADS. The number of iterations required for the fast-JPADS to converge is around . Consequently, we can early stop the iteration in practice, e.g., . On the other hand, the inference error-latency region of the fast-JPADS is shown in Fig. 2. It can be seen that the fast-JPADS achieves a region close to the Pareto front obtained by optimal-JPADS. In addition, the magnitudes of inference latency and error are close to each other. This corroborates our analysis in Section III-C. Due to its satisfactory performance, in the subsequent experiments, we adopt fast-JPADS for IO-ISAC scheme.
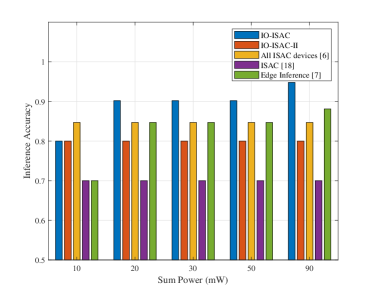
Next, to evaluate the performance gain brought by multi-view fusion, we compare the IO-ISAC scheme with that of ISAC [18], which selects a single ISAC device (e.g., device in Fig. 2). It can be seen from Fig. 2 that the inference accuracy of IO-ISAC is to higher than that of the ISAC scheme. This is because the fluctuation of spectrogram becomes weak as the target’s orientation is almost orthogonal to the sensing angle of device as shown in Fig. 2, resulting in subtle features for edge inference. In contrast, with the proposed IO-ISAC, the fluctuation of spectrograms is guaranteed to be strong, since there always exists a certain device outside the blind spot according to Proposition 1. For instance, at mW, the IO-ISAC activates devices in , and the two devices collaboratively eliminate the “sensing blind spots”. We define the accuracy gap between IO-ISAC and ISAC as multi-view fusion gain. This gain increases with the sum power, since a higher view diversity can be exploited under a looser power constraint. For instance, at mW and mW, the number of activated devices becomes (i.e., ) and (i.e., ), respectively. We also provide a variation of IO-ISAC, denoted as IO-ISAC-2, which increases weight on the inference latency. Therefore, compared with IO-ISAC, IO-ISAC-2 has a smaller inference latency.
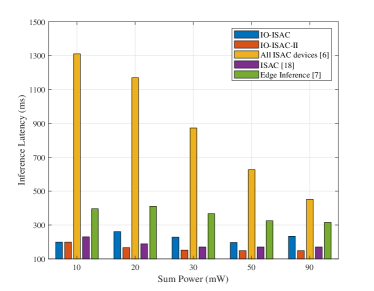
Then, to demonstrate the importance of device scheduling, we compare IO-ISAC with the all-devices scheme (i.e., with ), which follows the design criteria in [8]. It can be seen from Fig. 2 that the all-devices scheme leads to a lower inference accuracy than that of IO-ISAC although more devices are activated. This is because the co-device interference deteriorates the sensing SINRs at all devices. Moreover, as seen from Fig. 2, the inference latency of the all-devices scheme exceeds ms and is the highest among all the schemes. This is because different ISAC devices compete for the limited communication resources in the data uploading stage. In contrast, the proposed IO-ISAC selects a proper number of activated devices for collaborative inference, which results in a “win-win” situation that simultaneously reduces the error and latency. The gap between IO-ISAC and the all-devices scheme is device scheduling gain.
Finally, to evaluate the acceleration brought by ISAC, we compare the IO-ISAC scheme with the edge inference [7], which executes sensing and communication sequentially. It can be seen from Fig. 2 and Fig. 2 that the proposed IO-ISAC achieves an end-to-end latency significantly smaller than that of edge inference while guaranteeing similar inference accuracy. This demonstrates the benefits of one-stage reduction by merging the sensing and communication stages. We define this latency gap between IO-ISAC and edge inference as ISAC acceleration gain. Note that the ISAC co-functionality interference must be properly handled; otherwise, the gain may vanish.
V Conclusion
This paper has studied the end-to-end ISAC edge inference problem, and has derived two tractable models that bound the end-to-end edge inference error and the end-to-end edge inference latency from above. Leveraging these bounds, we have derived two JPADS algorithms and obtained the multi-view fusion gain, scheduling gain, and ISAC acceleration gain in an edge intelligence system. Simulation results have demonstrated the superiority of the IO-ISAC scheme.
References
- [1] Z. Zhou, X. Chen, E. Li, L. Zeng, K. Luo, and J. Zhang, “Edge intelligence: Paving the last mile of artificial intelligence with edge computing,” Proc. IEEE, vol. 107, no. 8, pp. 1738–1762, 2019.
- [2] D. Wen, P. Liu, G. Zhu, Y. Shi, J. Xu, Y. C. Eldar, and S. Cui, “Task-oriented sensing, computation, and communication integration for multi-device edge ai,” IEEE Trans. Wirel. Commun., vol. 23, no. 3, pp. 2486–2502, 2023.
- [3] J. Du, Z. Kong, A. Sun, J. Kang, D. Niyato, X. Chu, and F. R. Yu, “Maddpg-based joint service placement and task offloading in mec empowered air-ground integrated networks,” IEEE Internet Things J., vol. 11, no. 6, pp. 10 600–10 615, 2023.
- [4] T. Zhang, S. Wang, G. Li, F. Liu, G. Zhu, and R. Wang, “Accelerating edge intelligence via integrated sensing and communication,” in Proc. IEEE ICC, 2022, pp. 1586–1592.
- [5] Y. Xiong, F. Liu, Y. Cui, W. Yuan, T. X. Han, and G. Caire, “On the fundamental tradeoff of integrated sensing and communications under Gaussian channels,” IEEE Trans. Inf. Theory, vol. 69, no. 9, pp. 5723–5751, 2023.
- [6] G. Li, S. Wang, K. Ye, M. Wen, D. W. K. Ng, and M. Di Renzo, “Multi-point integrated sensing and communication: Fusion model and functionality selection,” IEEE Wirel. Commun. Lett., vol. 11, no. 12, pp. 2660–2664, 2022.
- [7] L. Zeng, C. Yang, P. Huang, Z. Zhou, S. Yu, and X. Chen, “GNN at the edge: Cost-efficient graph neural network processing over distributed edge servers,” IEEE J. Sel. Areas Commun., vol. 41, no. 3, pp. 720–739, 2022.
- [8] X. Li, F. Liu, Z. Zhou, G. Zhu, S. Wang, K. Huang, and Y. Gong, “Integrated sensing, communication, and computation over-the-air: MIMO beamforming design,” IEEE Trans. Wirel. Commun., vol. 22, no. 8, pp. 5383–5398, 2023.
- [9] F. Liu, C. Masouros, A. Li, H. Sun, and L. Hanzo, “MU-MIMO communications with MIMO radar: From co-existence to joint transmission,” IEEE Trans. Wirel. Commun., vol. 17, no. 4, pp. 2755–2770, 2018.
- [10] F. Liu, Y. Cui, C. Masouros, J. Xu, T. X. Han, Y. C. Eldar, and S. Buzzi, “Integrated sensing and communications: Toward dual-functional wireless networks for 6G and beyond,” IEEE J. Sel. Areas Commun., vol. 40, no. 6, pp. 1728–1767, 2022.
- [11] X. Qiao, G. Li, T. Shan, and R. Tao, “Human activity classification based on moving orientation determining using multistatic micro-doppler radar signals,” IEEE Trans. Geosci. Remote Sensing, vol. 60, pp. 1–15, 2021.
- [12] P. Liu, G. Zhu, S. Wang, W. Jiang, W. Luo, H. V. Poor, and S. Cui, “Toward ambient intelligence: Federated edge learning with task-oriented sensing, computation, and communication integration,” IEEE J. Sel. Top. Signal Process., vol. 17, no. 1, pp. 158–172, 2023.
- [13] X. Ju, S. Gong, N. Zhao, C. Xing, A. Nallanathan, and D. Niyato, “A framework on complex matrix derivatives with special structure constraints for wireless systems,” IEEE Trans. Commun., 2024.
- [14] B. Li and A. P. Petropulu, “Joint transmit designs for coexistence of MIMO wireless communications and sparse sensing radars in clutter,” IEEE Trans. Aerosp. Electron. Syst., vol. 53, no. 6, pp. 2846–2864, 2017.
- [15] M. O. Rabin and V. V. Vazirani, “Maximum matchings in general graphs through randomization,” J. Algorithms, vol. 10, no. 4, pp. 557–567, 1989.
- [16] E. Bedeer, O. A. Dobre, M. H. Ahmed, and K. E. Baddour, “A multiobjective optimization approach for optimal link adaptation of ofdm-based cognitive radio systems with imperfect spectrum sensing,” IEEE Trans. Wirel. Commun., vol. 13, no. 4, pp. 2339–2351, 2014.
- [17] O. Amin, E. Bedeer, M. H. Ahmed, and O. A. Dobre, “Energy efficiency–spectral efficiency tradeoff: A multiobjective optimization approach,” IEEE Trans. Veh. Technol., vol. 65, no. 4, pp. 1975–1981, 2015.
- [18] F. Liu, Y.-F. Liu, A. Li, C. Masouros, and Y. C. Eldar, “Cramér-Rao bound optimization for joint radar-communication beamforming,” IEEE Trans. Signal Process., vol. 70, no. 8, pp. 240–253, 2021.