Lawvere-Tierney topologies for computability theorists
Abstract.
In this article, we introduce certain kinds of computable reduction games with imperfect information. One can view such a game as an extension of the notion of Turing reduction, and generalized Weihrauch reduction as well. Based on the work by Lee and van Oosten, we utilize these games for providing a concrete description of the lattice of the Lawvere-Tierney topologies on the effective topos (equivalently, the subtoposes of the effective topos preordered by geometric inclusion). As an application, for instance, we show that there exists no minimal Lawvere-Tierney topology which is strictly above the identity topology on the effective topos.
1. Introduction
1.1. Summary
Our goal in this article is to accomplish a detailed analysis of the entire structure of “intermediate worlds” between “the world of computable mathematics” and “the world of set-theoretic mathematics.” In [20], Hyland discovered the effective topos , and proposed it as the world of computable mathematics. In topos theory, there is a notion called a Lawvere-Tierney topology (also known as a local operator or a geometric modality), and any topology on a topos yields a new subtopos . The least topology is the identity topology that does not cause any change to the base topos. The largest topology is the indiscrete topology that contracts all truth-values to a single value, and the resulting degenerated topos may be thought of as the world of inconsistent mathematics. The next largest topology is the double negation . In the effective topos, the new topos created from is exactly the world of set-theoretic mathematics; that is, . What this suggests is that analyzing the intermediate topologies between and on the effective topos may correspond to exploring the intermediate worlds between computable mathematics and set-theoretic mathematics.
Under this perspective, a topology on the effective topos is a kind of data that indicate how much non-computability to add to the world. In other words, a topology plays the same role as an oracle. Indeed, Hyland [20] noticed that each Turing degree has a corresponding topology on the effective topos, which yields the world of -relatively computable mathematics. However, this does not mean that we have exhausted all the topologies, and of course, there may be other topologies besides them. For instance, instead of a subset of or a total function on , one can use a partial function as an oracle. Not only that, but even a partial multi-valued function can be used as an oracle, and has a corresponding topology on the effective topos as we observe in this article. As another example, Pitts [33] found an intermediate topology that is not bounded by any Turing degree topology. This topology has properties that are far from any of the other topologies mentioned above. Remarkably, Lee-van Oosten [24] gave a concrete presentation of all topologies on the effective topos.
The first step of our work in this article is to capture the presentation of Lee-van Oosten [24] within the framework of generalized Weihrauch reducibility [19]. However, generalized Weihrauch reducibility (which involves a perfect information game) itself is insufficient to deal with all topologies, so we introduce an imperfect information game that incorporates some sort of nonuniform computation with advices. Coincidentally, it turns out that our notion is heavily related to another notion called extended Weihrauch reducibility, which is introduced in Bauer [2]. By viewing topologies in this way, it is possible, for example, to position the study of the structure of Lawvere-Tierney topologies as an extension of the Weihrauch-style analogue [6] of reverse mathematics (note, however, that this is by no means an extension of the standard reverse mathematics [38, 11] at all; reverse mathematics has more to do with the internal logic, and more finitary aspects). By bringing the arguments on topologies into pure computability theory in this way, we solve some problems proposed in [23, 24].
While the notion of Lawvere-Tierney topology is originally studied in an abstract context, we develop our theory in the most intuitive and elementary way possible. We believe that it is important for the development of a theory to present it in a way that reduces prior knowledge of the theory as much as possible. For this purpose, we maintain appropriate notations and keep the discussion moving forward with concrete ideas. In Section 2, we introduce certain kinds of computable reduction games with imperfect information. By using these games, we also define a notion of computability-theoretic reduction for certain extended functions. In Section 3, we see that this reducibility notion characterizes the notion of Lawvere-Tierney topology on the effective topos, based on the idea in Lee-van Oosten [24]. In Section 4, by using the characterization, we solve some problems on topologies proposed in [23, 24]. For instance, we see that there is no world of non-computable mathematics which is closest to computable mathematics. In Section 5, we discuss a few other topologies, which has not been studied in the past. One corresponds to the world of computable mathematics with error probability , and the other to computable mathematics with error density .
1.2. Notations
In this article, we assume that the reader is familiar with elementary facts about computability theory. For the basics of computability theory, we refer the reader to [10, 30, 35, 39]. We use the following notations on strings: Let be the set of all finite strings. For finite strings , we write if is an initial segment of , and write if is a proper initial segment of . We also use the same notation even if is an infinite string, i.e., . For and , define as the initial segment of of length . For finite strings , let be the concatenation of and . If is a string of length , i.e., is of the form for some , then is abbreviated to . Similarly, is abbreviated as .
A tree is a set which is downward closed under . An element of a tree is often called a node. The -least node (i.e., the empty string) of is called the root, and a -maximal node of is called a leaf. We always assume that is equipped with the standard Baire topology, that is, the countable product of the discrete topology on . For , let be the clopen set generated by , i.e., . For , let be the th partial computable function on , and be the th partial computable function relative to an oracle . For a partial function , we write if is defined, and if is undefined.
As usual, for , we often use to denote . We denote a partial function from to as . We use the symbol to denote the power set of a set . In this article, a partial function is often called a partial multi-valued function (abbreviated as a multifunction), and written as . In computable mathematics, we often view a -formula as a partial multifunction. Informally speaking, a (possibly false) statement is transformed into a partial multifunction such that and . Here, we consider formulas as partial multifunctions rather than relations in order to distinguish a hardest instance (corresponding to a false sentence) and an easiest instance (corresponding to a vacuous truth). In this sense, a relation does not correspond to a partial multifunction, but to a total multifunction which may take empty value.
2. Generalized Turing reducibility
2.1. Perfect information game
The notion of relative computation (or Turing reducibility) has been first introduced by Turing in 1939. From that time to the present, its structure has been investigated to an extremely deep level. As a result, a vast amount of research results are known (see e.g. [12, 18, 39] for the tip of the iceberg). Traditionally, Turing reducibility is usually considered for sets or total functions . However, a slight extension of this, the notion of Turing reducibility for partial functions , has also been considered, and the induced structure is known to be isomorphic to the enumeration degrees; see [10, Section 11.3]. The concept of relative computability can be extended to even larger classes of functions. As one such class, we first deal with partial multi-valued functions (abbreviated as multifunctions) on . In recent years, the notion of partial multifunction has received a great deal of attention in computability theory and related fields; see e.g. [6].
Relative Computation Model: Let us introduce the notion of computation relative to a partial multifunction on . Our computation model is the same as that of an ordinary programming language, except that a program can contain a special instruction of the form . The computation model accepts a number and a partial multifunction as inputs. The instruction assigns one of the values of to the variable . So far, it is exactly the same as an oracle Turing machine. However, if is undefined, the computation will never terminate. Moreover, if is multi-valued, i.e., if there are more than one possible values for the output of , this generally produces a nondeterministic computation.
We write for the partial multifunction defined by the above relative computation. To be precise, for an input , if the program terminates along any path of nondeterministic computation, we declare that is contained in the domain of , i.e., . Furthermore, if the program along some path of nondeterministic computation returns , then we declare .
Definition 2.1.
We say that is Turing reducible to (written ) if there exists a program such that refines . Here, for partial multifunctions and , we say that refines if, for any , implies and .
This notion coincides with ordinary Turing reducibility when restricted to total single-valued functions. One may think that this programming definition is too vague, so we give a mathematically rigorous description of this. Formally, the process of Turing reduction for partial multifunctions can also be described as a perfect information two-player game. However, since the players’ abilities are asymmetric, we will describe it as a game between Merlin and Arthur.
Definition 2.2 (Perfect information game).
For partial multifunctions , let us consider the following perfect information two-player game :
Game rules: Each player chooses a natural number at each round. Here, Merlin and Arthur need to obey the following rules.
-
•
First, Merlin chooses .
-
•
At the th round, Arthur reacts with .
-
–
The choice indicates that Arthur makes a new query to . In this case, we require .
-
–
The choice indicates that Arthur declares termination of the game with .
-
–
-
•
At the th round, Merlin responds to the query made by Arthur at the previous stage. This means that .
Then, Arthur wins the game if either Merlin violates the rule before Arthur violates the rule or Arthur obeys the rule and declares termination with .
Strategies: Hereafter, we require that Arthur’s moves are chosen in a computable manner. In other words, Arthur’s strategy is a code of a partial computable function . On the other hand, Merlin’s strategy is any partial function (which is not necessarily computable). Arthur’s strategy is winning if, as long as Arthur follows the strategy , Arthur wins the game, no matter what Merlin’s strategy is.
Observation 2.3.
Let and be partial multifunctions. Then, is Turing reducible to if and only if Arthur has a computable winning strategy for .
Remark.
Arthur’s winning strategy is a one-query strategy if, for any play following , either Merlin violates the rule or Arthur’s second move is of the form , i.e., declares termination at the second round.
Definition 2.4.
Let and be partial multifunctions. We say that is one-query Turing reducible to (written ) if there exists Arthur’s one-query winning strategy for .
Equivalently, is a one-query Turing reducible to if and only if there exist computable functions and such that for any and ,
Such an is called an inner reduction, and is called an outer reduction.
Remark.
A similar notion for partial multifunctions on has been extensively studied under the name Weihrauch reducibility; see e.g. Brattka-Gherardi-Pauly [6]. Indeed, one-query Turing reducibility is exactly the restriction of Weihrauch reducibility to functions on . This reducibility is also called many-one reducibility in [31].
Remark.
As is well known, it is very difficult to find a natural computably enumerable (c.e.) set whose Turing degree lies strictly between computable ones and the halting problem; see e.g. [27]. As one way to solve this problem of the lack of natural intermediate c.e. degrees, Simpson [37] proposed to study the Muchnik degrees of subsets of Cantor space. Here, however, we present an alternative solution, which is to consider the Turing degrees of multifunctions on . Observe that the Turing degree of a c.e. set is determined by its enumeration time function , where is the stage when is enumerated into if such a stage exists; otherwise . One can easily see that the graph of is always co-c.e., i.e., . In this light, one can consider that the counterpart of the Turing degrees of c.e. sets in the multi-valued context is the Turing degrees of multifunctions with graphs. In Example 2.5, we give a natural intermediate degree between computable problems and the halting problem.
To point out the relevance of the multifunctions on to the subsets of , note that if is a multifunction, then the product forms a subset of . However, be careful about that Turing reducibility for multifunctions is entirely different from Muchnik reducibility for their product sets.
Example 2.5 (Intermediate Turing degree).
The following is the -version of a well-studied principle, called the lesser limited principle of omniscience.
There are a huge number of mathematical principles which are equivalent to ; see Diener [11] and also Brattka-Gherardi-Pauly [6]. The principle may also be called de Morgan’s law for formulas. In the realizability context, this is closely related to Lifschitz realizability [25, 40]. It is not hard to see that the Turing degree of strictly lies between the computable problems and the halting problem. This also follows from our results in later sections (see Propositions 4.2 and 4.4).
Note that is one-query Turing equivalent to a multifunction with a graph. Given , define as follows:
where is the stage approximation of . Note that it is not possible for both and to terminate; that is, we always have . Then we define . Obviously, the graph of the multifunction is , and .
2.2. Imperfect information game
There are various forms of computation, one of which is the notion of probabilistic computation. As a simple example, let us consider the situation where a program is given an oracle at random, and for an input , the oracle computation halts with probability at least . In other words, this is the situation where
for some set . Here, is the uniform probability measure on (i.e., the probability measure by infinite fair coin flips). This probabilistic computation yields a multifunction such that the value for each is a possible output. This computation has two parameters, and . Of course, is an input given by us, while is a witness that the computation halts except for probability at most . It is only guaranteed that such an exists mathematically, but the computer does not know what exactly is.
Let us write for the procedure of giving an oracle randomly to the program and having it perform a computation with error probability at most . If one wants to make explicit a parameter which witnesses that the computation succeeds with error probability at most for an input , we use the following notation:
A pair of parameters is properly accepted only if witness that halts except for probability at most :
Then, the value for each is a possible output:
Although the roles of and are entirely different, if we just treat them formally, the above process can be regarded as a partial multifunction
In this sense, both and can be thought of as inputs for the above multifunction, but is an input that is disclosed during the computation, while is an unknown input that cannot be accessed during the computation. Hence, we call a public input, and a secret input.
Definition 2.6.
A partial multifunction , where is a set, is called a bilayer function in this article (any suggestions for a better name for this notion would be welcome). In this context, a pair is always written as . For , we call a public input and a secret input. Then, the public domain of is defined as the set of all such that for some .
Example 2.7.
Any partial multifunction can be identified with the following bilayer function :
Remark.
If one wants to avoid dealing with an arbitrary set , one can just consider , which yields . Conversely, if a partial function of the form is given, one can always assume that the elements of are indexed as . Then, we consider to mean , which yields a partial multifunction .
Indeed, previous studies, such as Lee-van Oosten [24], rather deal only with -valued functions. In the terms of Bauer [2], a -valued function is called an extended Weihrauch degree, and a partial multifunction as seen as an extended Weihrauch degree is called a modest extended Weihrauch degree. However, from the point of view of advised computation, there are advantages to the way of looking at it as in Definition 2.6.
Let us consider relative computation with a bilayer function oracle. In our computation model, a secret input for an oracle acts like an advice string in computational complexity theory. For the role of advice in computability theory, we refer the reader to Brattka-Pauly [7] and Ziegler [43]. One-query computation with advice in the context of -computation has also been discussed there.
Example 2.8.
In the context of -computation, the bilayer function defined by can be used to deal with nonuniform computability [7, 43]. However, in the context of -computation, is too strong and produce the -topology on the effective topos [24]. Several variants of random advice in the context of -computation have also been studied in [7, 5].
Relative Computation Model: Our computation model deals not only with one-query relative computation, but also with many-query relative computation. During a computation with a bilayer function oracle , when the program makes a query to , the advisor chooses a parameter . However, the information of chosen by the advisor is not given to the machine, but only the information of one of the possible values of is given. If this process computes a partial multifunction when the advisor secretly makes the best choice, then we declare that is Turing reducible to in the bilayered context, and write .
Again, one may think that this programming definition is too vague, so we give a mathematically rigorous description of this. Formally, this procedure can be understood by describing it as an imperfect information game between three players, Merlin, Arthur, and Nimue. The player Merlin makes a public input and a secret input on his first move. Here, among the moves of Merlin, only the secret input is invisible to Arthur. All of Nimue’s moves are visible to Merlin, but not to Arthur, a mere human being. The players Merlin and Nimue, who are not mere humans, can see all the previous moves at each round.
Definition 2.9 (Imperfect information game).
For bilayer functions and , let us consider the following imperfect information three-player game :
Game rules: Here, the players need to obey the following rules.
-
•
First, Merlin chooses a pair .
-
•
At the th round, Arthur reacts with .
-
–
The choice indicates that Arthur makes a new query to . In this case, we require .
-
–
The choice indicates that Arthur declares termination of the game with .
-
–
-
•
At the th round, Nimue makes an advice parameter such that .
-
•
At the th round, Merlin responds to the query made by Arthur and Nimue at the previous stage. This means that .
Then, Arthur and Nimue win the game if either Merlin violates the rule before Arthur or Nimue violates the rule, or both Arthur and Nimue obey the rule and Arthur declares termination with .
Strategies: As noted above, Arthur can only read the moves , and the other players can see all the moves. Moreover, we require that Arthur’s moves are chosen in a computable manner. In other words, Arthur’s strategy is a code of a partial computable function , which reads Merlin’s moves and then returns . On the other hand, Merlin and Nimue’s strategies are any partial functions (which are not necessarily computable).
A pair of Arthur’s computable strategy and Nimue’s strategy is called an Arthur-Nimue strategy. An Arthur-Nimue strategy is winning if, as long as Arthur and Nimue follow the strategy , Arthur and Nimue win the game, no matter what Merlin’s strategy is.
We now introduce a generalization of Turing reducibility for bilayer functions.
Definition 2.10.
Let and be bilayer functions. We say that is bilayered Turing reducible (or LT-reducible) to (written ) if there exists a winning Arthur-Nimue strategy for .
Obviously, bilayered Turing reducibility for partial multifunctions (which can be viewed as bilayer functions as in Example 2.7) is the same as Turing reducibility.
Remark.
The notion of an Arthur-Nimue strategy is strongly related to the notion of a dedicated sight in Lee-van Oosten [24, Definition 4.3]. The statement that is a -dedicated sight roughly corresponds to that is a winning Arthur-Nimue strategy witnessing , where for .
Before examining bilayered Turing reducibility, we again consider one-query reductions. A winning Arthur-Nimue strategy is a one-query strategy if, for any play following , either Merlin violates the rule or Arthur’s second move is of the form , i.e., declares termination at the second round.
Definition 2.11.
Let and be bilayer functions. We say that is one-query bilayered Turing reducible to (written ) if there exists a one-query winning Arthur-Nimue strategy for .
Equivalently, is a one-query bilayered Turing reducible to if and only if there exist computable functions and and a function such that for any and ,
Such an is called an inner reduction, and is called an outer reduction. We also call a secret inner reduction.
Remark.
One-query bilayered Turing reducibility for bilayer functions (extended Weihrauch degrees) is simply called Weihrauch reducibility in Bauer [2]. The algebraic structure of the one-query bilayered Turing degrees (the extended Weihrauch degrees) has been studied there.
Proposition 2.12.
is a preorder.
Proof.
Reflexivity is trivial. For transitivity, let witness and witness . Then implies , which implies . Hence, is an inner reduction, is an outer reduction, and is a secret inner reduction witnessing . ∎
Proposition 2.13.
is a preorder.
Proof.
Reflexivity is trivial. For transitivity, we only need to combine the argument in Proposition 2.12 and the proof of transitivity of generalized Weihrauch reducibility [19, Proposition 4.4]. We assume that and . To avoid confusion, we name , , and for the players in the game , and , , and for the players in the game . Let be a winning - strategy for the corresponding game for each . In the following, we assume that and always follow their winning strategies. We construct a winning Arthur-Nimue strategy for .
Let be Merlin’s first move in the game . Then, consider as ’s first move in the game as well, and simulate a play following the - strategy . Along such a play, if declares termination with some at some round, then also declares termination with the same value . If and make a query to at some round, then think of as ’s first move in the game , and simulate a play following the - strategy . During this subplay, Arthur and Nimue simply copy the moves made by and , respectively, and play them as their own moves. Here, Merlin copies ’s moves, except for the first move, and uses them directly in his own moves. Since and follow their winning strategies, declares termination with some at some round, and moreover . Hence, one can think of such as ’s response to the previous move by and . This allows the game to move on to the next round (and this can be simulated by Arthur and Nimue, since they know the value of ). Repeating this process, since and follow their winning strategies, declares termination with some at some round, and moreover . Therefore, also declares termination with some at some round. Hence, the Arthur-Nimue strategy described above is winning for , which concludes . ∎
Note that the rule of the game does not mention except for Player I’s first move. Hence, if we skip Player I’s first move, we can judge if a given play follows the rule without specifying . Such a restricted game is denoted by . Arthur and Nimue win the game if either Merlin violates the rule before Arthur or Nimue violates the rule, or both Arthur and Nimue obey the rule and Arthur declares termination.
Definition 2.14.
Given a bilayer function , let us define the new bilayer function as follows: An input for is an Arthur-Nimue strategy , where Arthur’s strategy is a public input, and Nimue’s strategy is a secret input.
-
•
is defined only if, along any play following the strategy , Arthur and Nimue win the game whatever Merlin’s strategy is.
-
•
if and only if there is a play in that follows the strategy such that Arthur declares termination with at some round, where all players obey the rule.
The first condition says that if and only if is a winning Arthur-Nimue strategy for in a certain sense, and in particular, Arthur declares termination at some round unless Merlin violates the rule. Alternatively, can be thought of as a universal machine for -relative computation.
Proposition 2.15.
For bilayer functions and , if and only if .
Proof.
Let be a winning Arthur-Nimue strategy witnessing . Given an input for , define and . Any corresponds to a play in following the strategy , where Merlin’s first move is , and declares termination with . Since is winning in , we must have . Thus, is an inner reduction, is a secret inner reduction, and is an outer reduction witnessing .
Let witness . As is an inner reduction, note that is (a code of) Arthur’s strategy, and think of as Arthur’s move after reading Merlin’s moves . Then, define if does not declare termination, i.e., is of the form . If declares termination with , then define ; that is, declares termination with . Clearly, is computable. We also define .
Assume that Arthur and Nimue follow the strategy in the game . If Merlin’s first move is , then, by the definitions of and , Arthur and Nimue follow the strategy in the subgame until Arthur declares termination. Since , either Merlin violates the rule before Arthur or Nimue violates the rule, or all players obey the rule and Arthur declares termination. Assume that Merlin follows a strategy obeying the rule. Then, in the subgame , Arthur declares termination with at some round, i.e., . Hence, by the definition of , in the game , Arthur declares termination with . As are reductions witnessing , implies . This verifies that is a winning Arthur-Nimue strategy witnessing . ∎
Proposition 2.16.
.
Proof.
Remark.
Remark.
Several variants of Weihrauch reducibility can be explained by using bilayer functions in the context of -computation. For instance, is computable reducible to in the sense of [14, 19] if and only if is one-query bilayered Turing reducible to (see Definition 4.5) if we properly extend the above notions to the context of -computability. The notion of omniscient computable/Weihrauch reducibility [26, 15, 13] can also be explained in the bilayer context.
3. Lawvere-Tierney topology
3.1. Realizability
For sets we define if there exists a partial computable function such that implies . Then forms a Heyting algebra, where the Heyting operations are given as follows:
Now we put , and consider as the set of truth values in the world of computable mathematics. Indeed, the morphism tracked by , where , is a subobject classifier in the effective topos. For more information on the effective topos, see [20, 23, 40].
Let be a propositional formula, where all propositional variables belong to . Then can be thought of as an element of by using Heyting operations on . We say that realizes if belongs to under the above interpretation. We also say that realizes if for any . Then, is realizable if some realizes .
3.2. Lawvere-Tierney topologies
In this section, we reveal the hidden relationship between bilayered Turing degrees and Lawvere-Tierney topologies (Definition 3.2) on the effective topos. As mentioned in Section 1.1, we regard an Lawvere-Tierney topology on the effective topos as a kind of data that indicate how much non-computability to add to the world, and thus, a topology plays the same role as an oracle. In this regard, Hyland [20] found an embedding of the Turing degrees (of total single-valued functions on ) into the lattice of Lawvere-Tierney topologies on the effective topos. Hyland’s embedding can be extended to partial functions or even partial multifunctions on . By extending this further, we show that there exists an isomorphism between the bilayered Turing degrees and the lattice of Lawvere-Tierney topologies on the effective topos (Corollary 3.5). This guarantees that, in the strict sense, any topology on the effective topos can be identified with a (bilayer) oracle. Note that most of the results in Section 3.2 have almost been proven by Lee and van Oosten [24], although their language is completely different from ours, and in particular they do not give any computational interpretation of their notions.
A function is said to be computably monotone if the following is realizable:
In other words, there exists such that for any if realizes then realizes . We define a preorder on computably monotone functions on as follows:
that is, there exists such that, for any , realizes . For a preorder, its quotient by the induced equivalence relation is called the poset reflection.
Theorem 3.1.
The poset reflections of the following preorders are isomorphic:
-
•
The one-query bilayered Turing preorder on bilayer functions.
-
•
The preorder on computably monotone functions on .
Proof.
Given a bilayer function , we define a function as follows:
Roughly speaking, is a problem that asks us to solve a problem with the help of . Of the solutions and to , we sometimes call an inner reduction and an outer reduction. Indeed, if we put , then if and only if witnesses . Note that, if is a bilayer function, is essentially the same as under the notation in Lee-van Oosten [24, page 873]. One can easily see that is computably monotone (see also [24]). We first show the following:
For the forward direction, assume that witnesses , and witnesses with some . Then, the composition of inner reductions and the composition of outer reductions witness with . This is because for any solution we have as is a reduction triple, and for any we have ; hence . Put and let be an index of the computable function . Then we have . Clearly is computable and independent of . Hence we get .
For the backward direction, let be a realizer for for any . Given , let us consider . It is obvious that witnesses . Thus, witnesses . In other words, implies for some . One can find an index such that . Then, is an inner reduction, is a secret inner reduction, and is an outer reduction for .
Now, given a computably monotone function , define a bilayer function as follows:
Remark.
Recall that, in [2], one-query bilayered Turing reducibility is called extended Weihrauch reducibility. Together with the result in Bauer [2] that extended Weihrauch degrees and instance degrees (over a relative partial combinatory algebra) are equivalent preorders, one can deduce that the orders in Theorem 3.1 are also isomorphic to instance degrees over Kleene’s first algebra.
By the proof of Theorem 3.1, note that we also have and
We next consider the notion of Lawvere-Tierney topology (also known as local operator or geometric modality), which is, in general, defined as a certain operator on the truth-value object in a given topos. In the effective topos, it is essentially the same as the following notion (see also [23, 24]):
Definition 3.2.
A function is a Lawvere-Tierney topology if all of the following are realizable
-
(1)
.
-
(2)
.
-
(3)
Recall from the proof of Theorem 3.1 that is the set of reduction pairs for (where a secret reduction is not included). Therefore, by Proposition 2.15, is essentially the set of Arthur’s winning strategies for . We next see that the function is always a Lawvere-Tierney topology.
Observation 3.3.
Let be a bilayer function. Then, is a Lawvere-Tierney topology.
Proof.
(1) If one can solve a problem without any help, it is clear that one can also solve the problem with the help of . (2) For the backward direction, if one can solve problems and with the help of , then by running these strategies in parallel, one can also solve the problem with the help of . The forward direction is obvious.
(3) By definition, if and only if realizes for some . Thus, if and then realizes for some . As in the proof of Proposition 2.13, we combine two games, but this time in series. On the first game , Arthur and Nimue follow their strategies with one exception: Even if the strategy declares termination , then Arthur do not declare termination, but move on to the next game which is also . Then Arthur and Nimue next follow their strategies with one exception: If the strategy declares termination , then Arthur declares termination with . Note that if Merlin obeys the rule, then we always have . This can be viewed as a single game which is also , and we write for the Arthur-Nimue strategy described above. It is easy to check that , and if then . Therefore, the identity map realizes . Hence, . Clearly, is computable, and thus an index of the computable function realizes for all . ∎
For any monotone function , consider . By the above observation, is always a topology.
Theorem 3.4 (see also [24, Proposition 1.2]).
Let be a computably monotone function. Then, is the -least topology such that .
Proof.
First, since , we have by Theorem 3.1; that is, always holds. Thus, it remains to show that implies for any topology . To prove this, as in [24, Proposition 1.2], consider the following:
As shown in [24, Proposition 1.2], implies . Hence, it remains to show . Here, recall that a realizer for is a pair of an inner reduction and an outer reduction for , i.e., realizes for some . In this case, we must have , which means that is a winning Arthur-Nimue strategy for the game .
To compute a realizer of , assume that we are given a realizer of and a realizer of in the premise of , which are independent of . On some play of the game , if is Arthur and Nimue’s queries to in their moves (without declaring termination) at some round, then we have , which means that and . Since realizes , we have . Hence, yields Merlin’s strategy which obeys the rule. Therefore, one can simulate one of the plays of the game from the information in d, c, and b. Since is a winning Arthur-Nimue strategy, and Merlin’s strategy b obeys the rule, Arthur declares termination at some round along this play. In particular, one can compute Arthur’s final move in this play, which yields some . By applying e to this result, we can get a realizer for . Furthermore, by applying a to this result, we get a realizer for . This procedure yields a realizer for independent of , and thus, is realizable. ∎
As in [24], we define
In summary, for bilayer functions and , we obtain
Here, the first equivalence follows from Proposition 2.15, and the second one follows from Theorem 3.1. As any computably monotone function is -equivalent to a function of the form , this concludes the following:
Corollary 3.5.
The poset reflections of the following preorders are isomorphic:
-
•
The bilayered Turing preorder on bilayer functions.
-
•
The preorder on computably monotone functions on .
-
•
The preorder on Lawvere-Tierney topologies.
In summary, for any bilayer function , the map which, given a problem , returns a problem asking us to giving an Arthur’s winning strategy for is always a Lawvere-Tierney topology, and conversely, every Lawvere-Tierney topology on the effective topos can be described in this way.
4. On the structures of Lawvere-Tierney topologies
4.1. Turing degrees of choices from co--tons
If the domain (for public inputs) of a bilayer function is a singleton (i.e., an input is always of the form ), then we call a basic bilayer function. In this section, we deal with the basic bilayer function for defined by
This is a problem such that of the choices are wrong. In particular, one-query -relative computation is the one in which computations are run in parallel, of which may be wrong. Note that the basic bilayer function is denoted as in [24]. Lee-van Oosten [24] proposed to study the structure of . By Theorem 3.1 and Corollary 3.5, this is the same as the examining the structure of .
Of course, the basic bilayer function is closely related to the well-known notion, the lessor limited principle of omniscience (recall Example 2.5). Here, we consider its generalization:
Clearly, is equivalent to . The principle is first introduced in Richman [34], and extensively studied in constructive mathematics and related areas. For the computability-theoretic study, see Brattka-Gherardi-Pauly [6]. Note that one can deduce several results on the structure of from the work by Cenzer-Hinman [8].
One may relativize by replacing with for a given oracle , and then the resulting function is denoted by . Recall from Example 2.7 that a partial multifunction can be thought of as a bilayer function. The following is obvious:
Observation 4.1.
For any oracle , .
If , we can do a little better.
Proposition 4.2.
.
Proof.
We define a secret inner reduction as follows: For any ,
One can easily check that belongs to the domain of . For an outer reduction , define for any . To compute , wait for finding many such that . If it is found at some stage, then is defined as the least such that for any such , so implies . Otherwise, the computation never terminates, i.e., .
We claim that witnesses . Assume . If then we have ; hence . If then by our definition of , we must have . The computation for eventually recognizes this fact at some stage, and this implies that ; hence . ∎
In particular, we get . One can easily see that the above proof indeed shows that . However, it cannot be improved any further. To prove this, we need a little preparation. We say that a tree is -fat if any node which is not a leaf has at least many immediate successors. We use the following easy combinatorial fact, which is a slight modification of Cenzer-Hinman [8, Proposition 2.9] (see also Lemma 5.7 below).
Fact 4.3.
For , let be an -fat finite tree, and be the set of all leaves of . Assume that every leaf of has the same length. Then, for any function there exists an -fat tree such that is constant on the leaves of .
Proposition 4.4.
.
Proof.
The proof is by a typical recursion trick; see [21]. Suppose for the sake of contradiction that there exists a winning Arthur-Nimue strategy witnessing . Except for the first move , Merlin’s move is always a number , which yields the tree of all possible moves by Merlin. Fix , and then Arthur’s strategy yields a partial computable function , where if and only if, after reading Merlin’s moves , Arthur’s strategy declares termination with . Moreover, as Nimue makes a secret input for at each round, Nimue’s strategy restricts Merlin’s possible moves to an -fat finite subtree of , where after Arthur declares termination, Nimue makes no further moves; hence if and then has to be a leaf of . On the other hand, if Arthur does not declare termination, then Nimue makes the next move, so restricted to the leaves of yields a total function from to . One can assume that every leaf of has the same length: Otherwise, let be the length of a longest node of , and for each leaf of of length , place a full -branching tree of height on the leaf . Then, for a leaf of the resulting tree , define as the value for the unique initial segment of such that . Then replace with if necessary.
Since is -valued, and is -fat, by Fact 4.3, there exists a -fat subtree of of the same height such that is constant on the leaves of . Recall that depends on , so there exists a computable function such that . Now, we construct an algorithm as follows: By brute-force, Merlin searches for a -fat finite subtree of such that is total and constant on the leaves of . Let be the unique value of on the leaves of . Then, we declare that halts, and never halts for .
Since Nimue’s move reduces the number of possible moves for Merlin by at most one at each round, and is -fat, contains Merlin’s correct moves in a play following as a path . Since is winning, since is Merlin’s first move. This means that . However, by the Kleene recursion theorem (see e.g. [10, Theorem 4.1.1] or [30, Theorem II.2.10]), there exists such that , and by our definition, we have . This is a contradiction. ∎
This also shows that .
Definition 4.5.
For a partial multifunction and a basic bilayer function , we define a bilayer function as follows:
A similar argument as above also shows the following:
Proposition 4.6.
for any partial multifunction .
Proof.
Note that any partial multifunction is one-query Turing reducible to a single-valued function. This is because any choice function for refines . Thus, without loss of generality, one can assume that is a single-valued function.
Suppose for the sake of contradiction that there exists there exists a winning Arthur-Nimue strategy . Except for the first move , the second coordinate of Merlin’s move is always a number , which yields the tree of all possible moves. Given Arthur’s moves, the first coordinates of the corresponding moves by Merlin are computable in . Therefore, Arthur’s strategy and the corresponding responses by Merlin yield a partial -computable function , where if and only if, after reading Merlin’s moves whose second coordinates are , Arthur’s strategy declares termination with . Moreover, Nimue’s strategy restricts second coordinates of Merlin’s possible moves to an finite subtree of . As in the proof of Proposition 4.4, one can assume that every leaf of has the same length . Then, restricted to yields a total function from to . By considering , one can assume that is a partial -valued function even if we consider an input . By Fact 4.3 applied to any totalization of , one can see that there exists a -fat subtree of of the same height such that takes at most one value (or undefined) on the leaves of (where can be partial).
Let be the only possible value of on the leaves of . Note that this value only depends on Arthur’s strategy ; hence it is independent of Merlin’s first move . Since Nimue’s move reduces the number of possible moves for Merlin by at most one at each round, and is -fat, contains the second coordinates of Merlin’s correct moves in a play following as a path . Since is winning, is defined, and is the only possible value. Hence since is Merlin’s first move. However, this value is independent of , which is a contradiction. ∎
One can apply combinatorial techniques developed in [8] to prove the following:
Theorem 4.7.
, where .
This solves all problems asked in Lee-van Oosten [24, Open problems in pages 876–877].
Proof of Theorem 4.7.
As in Cenzer-Hinman [8, Proposition 2.4], one can easily see that implies . Now, let us think of as a problem of choosing a surviving block, where there are blocks and one may secretly destroy at most of them. As a variant of this problem, consider , where there are blocks as above, but of them are hard blocks. One can secretly hit blocks times, and while a normal block will break in one hit, a hard block will only break if we hit it all times. The information about which blocks are hard is given as a public input , and the information on which blocks to hit is given as a secret input , where for any and . Formally,
This notion is an analogue of a sequence of type in [8, Theorem 2.6]. Now assume that there are blocks, of which are hard blocks. Consider an operation of consolidating of the normal blocks into a single hard block. Then we now have blocks, since we have consolidated blocks into one. The number of normal blocks remaining is , and the number of hard blocks is . One can secretly hit a block times, but assuming that a hard block will always break if one hits it all the times does not change the difficulty of the problem, so one can assume that the number of times we hit it is . This consolidating operation transforms an instance of into an instance of .
The join of bilayer functions and is defined as follows:
The next claim corresponds to the formula (6) in Cenzer-Hinman [8, Theorem 2.6].
Claim.
.
Proof.
Assume that an input for is given. There are only a finite number of patterns of consolidating normal blocks, and the location information of the hard blocks is given as a public input. Therefore, by brute-force, Arthur can try all patterns of consolidating normal blocks. If the number of patterns is , at the first rounds, Arthur and Nimue make queries to . For such a round, Arthur chooses normal blocks , i.e., , and consolidate them into a single hard block . Then Nimue hits the new blocks according to the original secret input ; that is, if then , and if then . Then, Nimue’s next move is given by .
If Merlin’s response is not at some round, then is a solution to the original problem, so Arthur declares termination with . If Merlin’s response is the new consolidated hard block at each round, then the original secret input does not hit normal blocks. This is because if hits normal blocks then consolidates these blocks into a single hard block at some round, and so Nimue hits the new hard block times. This means that Nimue breaks , so is not acceptable as Merlin’s response. Hence, the original secret input hits at most normal blocks, so can also be thought of as an input of . Thus, at round , Arthur use and Nimue use as a query to , and then Merlin’s response must be a solution to . Then, Arthur declares termination with . This is a winning Arthur-Nimue strategy witnessing . ∎
The next claim corresponds to the formula (11) in Cenzer-Hinman [8, Theorem 2.6].
Claim.
If then .
Proof.
If then and there is no difference between normal blocks and hard blocks; hence . We prove the claim by induction on and . By the induction hypothesis, if we put and , then
We clearly have , and moreover
Thus, and this implies that . Hence, by the previous claim,
This verifies the claim. ∎
In particular, if we put , then we have as . This concludes the proof of Theorem 4.7. ∎
4.2. Non-existence of a minimal topology
We next consider the basic bilayer function for defined by
In Lee-van Oosten [24, Propositions 5.1 and 5.2], it is shown that , but . Interestingly, as shown in [24, Proposition 5.5], is the -least basic bilayer function which is strictly -above . However, we include bilayer functions, is not the -least one. For instance, the basic bilayer function is closely related to the notion called all-or-counique choice [6]:
One may relativize by replacing with for a given oracle , and then the resulting function is denoted by . Again, we think of a partial multifunction as a bilayer function as in Example 2.7. The following is obvious:
Observation 4.8.
for any oracle .
Lee [23, Open Problem 3.5.18] asked if there is the least topology strictly above . By Corollary 3.5, it is the same as asking if there is the -least bilayer function which is strictly -above . If such a function exists, then it must be a non-basic bilayer function. To solve this problem, given a partial function , we consider the following multifunction :
We first show that there exists no -least partial multifunction which is strictly -above .
Lemma 4.9.
Let be a partial multifunction such that . Then, there exists a total function such that
Proof.
Let be an oracle coding the full information of . For instance,
Let be an -generic real (that is, is contained in any dense -computable open set in Cantor space , and such a exists by the Baire category theorem). By genericity, for any computable function , there are infinitely many such that ; hence . Suppose for the sake of contradiction that Arthur has a winning strategy for . Then we show the following claim:
Claim.
For any , there exist and such that
where recall that by we mean that, after reading Merlin’s moves , Arthur declares termination with .
Proof.
Otherwise, there is a number refuting the claim. Let denote the second coordinate of . Let us consider a sequence such that for any , i.e., is Merlin’s moves obeying the rule. It is clear that there always exists such an since only reduces the number of possible values by one. Since is winning, after reading a finite initial segment of the sequence , Arthur declares termination; that is, for some and .
In particular, there exists with such that for some . Given , without knowing the information about , one can effectively find such a by brute-force. Then define as . Clearly, is a computable function. However, since the claim is supposed to fail, we have either or . Hence, the computable function refines , which means . However this contradicts our assumption on . ∎
Given , one can find an and a in the above claim in an -computable manner since contains the full information of . For a given , put , and for this , we write and for and in the claim. By the above claim, after reading Merlin’s play , Arthur’s strategy declares termination, but fails to compute a solution of . However, since is a winning strategy for , Merlin must have violated the rule at some round. In other words, there exists such that . Put , and we now have for some . Note that, since for any , if then by our choice of . Now consider the finite set defined by
Given , one can find the canonical code of is an -computable manner. Note that there exists such that . However, note that
yields a dense -computable open set in Cantor space . This is because, given a binary string , choose , and extend to so that for any . This is doable since obviously implies . In this way, any extends to and thus is dense. Since is -generic, we have ; that is, there exists such that for any . However, by the property of , for any , we must have a pair such that , a contradiction. ∎
Theorem 4.10.
There exists no -minimal bilayer function which is strictly -above ; that is, for any bilayer function there exists a bilayer function such that . Hence, there exists no minimal Lawvere-Tierney topology which is strictly above .
Proof.
Let be a bilayer function such that . Put , and then is a basic bilayer function. If , then by minimality of ([24, Proposition 5.5]), we have . By Observation 4.8, cannot be minimal. Thus, one can assume that for any . This implies that, since is a basic bilayer function, if , then is nonempty. This is because, at some round in the reduction game for , Arthur’s winning strategy declares termination with some , which is independent of , as is invisible to Arthur. Then, since is a partial multifunction, by Lemma 4.9, there exists a total function such that and .
We claim that also holds. Otherwise, there exists Arthur’s winning strategy witnessing , where note that, since is a partial multifunction, Nimue does not intervene in the game. Let be Merlin’s first move. Since is winning, Arthur declares termination with some . However, since is invisible to Arthur, the last value only depends on . This implies that . Namely, the strategy also witnesses . However, this contradicts our choice of .
Moreover, since the Lawvere-Tierney topologies form a lattice, the Turing degrees of bilayer functions also form a lattice by Corollary 3.5. For an explicit description of the infimum operation, we define the meet of bilayer functions and as follows:
Note that this is a bilayer analogue of the meet in the Weihrauch lattice [6]. We claim that the meet of and strictly lies between and . As , we have . If , then , so is computable. This means that there exists a computable function such that for . First consider the case that for any there exists such that is of the form . For such an , since is total, we also have , and thus , so for any . In this case, given , by brute-force, we effectively search for such that the first coordinate of is , then return its second coordinate, which must be a solution to as seen above. Hence, this procedure witnesses that is computable, which contradicts the assumption . Thus, there must exist such that is of the form , for any . As in the above argument, we have , so . Then, the algorithm which, given , returns the second coordinate of witnesses that is computable. However, this contradicts the property . Consequently, . This verifies the first assertion. Then, the second assertion follows from Corollary 3.5. ∎
This solves Lee’s problem [23, Open Problem 3.5.18].
5. Other topologies
5.1. Probabilistic computation
As in Section 2.2, we consider bilayer functions expressing certain kinds of probabilistic computation. However, unlike Section 2.2, for the sake of brevity in discussion, we require that a parameter be compact. By inner regularity, every -measurable set in is approximated from the inside by a compact set, so adding this assumption does not make much difference. Here, recall that is the uniform probability measure on . Then we consider the following bilayer function:
One would say that the subtopos obtained from the Lawvere-Tierney topology corresponding to is the “world of probabilistically computable mathematics with error probability .” Surprisingly, we show that induces exactly the same topology as Lee-van Oosten’s function .
Proposition 5.1.
For any with , .
Proof.
Obviously, we have . We show the other direction. Let be an input for and assume that . This means that for any . Since is compact, there exists such that the stage approximation halts for any . Note that is not necessarily computable, and thus Arthur does not have access to this information, but Nimue does have access to it.
The public input can be thought of as a partial function . This induces the push-forward measure on defined by . We consider its finitary approximation; that is, put , and define . For each stage , the value is rational, and moreover happens for at most finitely many . Let be a list of all such ’s. Clearly, is computable. Since we have only finitely many rationals , we can assume that all values have the same denominator and are of the form . Note that we clearly have . Fix a pairwise disjoint sequence such that and .
Since by Theorem 4.7, there is Arthur’s winning strategy witnessing this fact. As is computable, one can easily see that the proof of Theorem 4.7 ensures that is also computable. Hence, instead of taking Nimue’s moves as secret inputs to , we can take them directly as secret inputs to through the above reduction implicitly. Here, note that such a conversion takes multiple rounds through Arthur and Nimue’s moves, but we do not count this number of rounds, and without mentioning it, all conversions are assumed to be done automatically.
Thus, at the -st round, after seeing Nimue’s previous move, we assume that Merlin plays a move less than . Then Arthur reacts to this. If Merlin’s move is contained in for some , then Arthur declares termination with . Otherwise, Arthur declares that the game proceeds to the next round, and urges Nimue to make the next move. Now we describe Nimue’s move at the -th round. Nimue reads the secret input and then define as follows: For any , we define
For , we define
where . One can see that if then is included in , where is a number mentioned in the first paragraph of this proof. Note that, in order to enumerate many elements in into , the measure of needs to be removed by . Similarly, in order to enumerate elements in into , the measure of needs to be removed by
Since the measure of is greater than or equal to , the measure removed from should be at most . Therefore, only at most many elements can be enumerated into , so belongs to the domain of . Hence, Nimue’s move obeys the rule.
We claim that Arthur and Nimue win this game along the play described above. Note that Arthur declares termination by the -th round. This is because the complement of is included in , and thus Merlin must play a move from at the -th round. In response to this move, Arthur’s strategy described above declares termination. We now assume that Arthur declares termination with at the -st round. In order for this to happen, Merlin’s previous move must belong to . In such a case, Nimue’s previous move must satisfy . This means that . In particular, there exists such that . Hence, . ∎
One can also consider a counterpart of in the context of partial multifunctions, which is known as weak weak König’s lemma [5]. Let be the -th subset of (or the set of all infinite paths though the -th primitive recursive subtree of ).
As in Proposition 5.1, one can show that . However, of course, weak weak König’s lemma is known to be much stronger than the lessor limited principle of omniscience. Indeed, if we consider analogues of and in the Kleene-Vesley algebra (i.e., in the context of -computation), then one can easily see that is strictly above with respect to Turing reducibility for -computability (i.e., generalized Weihrauch reducibility). Therefore, Proposition 5.1 is a phenomenon specific to the effective topos. If we consider another (relative) realizability topos, such as the Kleene-Vesley topos, the situation would be completely different.

5.2. Cofinite choice
The basic bilayer functions we have dealt with so far was of no help at all for computing a single-valued function when treated as an oracle. However, indeed, there is a known basic bilayer function which is rather powerful when considered as an oracle. Pitts [33, Example 5.8] introduced the following basic bilayer function :
Note that one-query -relative computation is the one in which countably many computations are run in parallel, a finite number of which may be wrong. Pitts [33] observed that the above function yields a Lawvere-Tierney topology on the effective topos such that . Here, note that in our terminology. Interestingly, van Oosten [41, Theorem 2.2] showed that, for a total function , the topology forces to be decidable if and only if is hyperarithmetic. In other words, for a total function , if and only if is hyperarithmetic. For the basics of hyperarithmetic sets, we refer the reader to Sacks [36] and Chong-Yu [9]. It is also known that for any (see [24, Proposition 5.11]).
Pitts’ function also has a partial multi-valued counterpart, which has been studied as cofinite choice [4, 1] or bound [17] in the context of -computation. We introduce cofinite choice relative to an oracle as follows:
It is obvious that for any oracle . Moreover, we also have , where is the Turing jump of . To estimate the strength of cofinite choice, we consider the following equivalent definition of the hyperarithmetical hierarchy based on the effective Baire hierarchy.
Definition 5.2 (Effective Baire hierarchy).
For each computable ordinal , we define a set of total functions on as follows: First, is the set of all total computable functions on , and a -code of is a program code computing . For , is the set of functions such that for some sequence , where there exists an algorithm which, given , returns a -code of for some . A -code of is a pair of a code of and a code of such .
By the Shoenfield limit lemma (see e.g. [39, Lemma III.3.3] or [30, Proposition IV.1.19]), corresponds to -computability for , and corresponds to -computability for an infinite ordinal , where is the -th Turing jump of a computable function. Obviously, Definition 5.2 of produces a computable well-founded tree whose leaves are labeled by computable functions. Here, such a is full-splitting, that is, if is not a leaf, then for any .
Conversely, let be a computable full-splitting well-founded tree. We inductively define , the rank of , as follows: The rank of a leaf of is , and if is not a leaf, then the rank of is . Then, , the rank of , is defined as the rank of its root.
Let be the set of leaves of . A computable assignment is a computable function . We inductively label each node of with a function or an undefined symbol as follows: If is a leaf of , then put . If is labeled by for some , then is also labeled by . If exists for all , then is labeled by the pointwise limit . Otherwise, is labeled by . Then define as the label of the root of if it is defined. Observe that if is defined, then . Indeed, one can compute a -code of .
Definition 5.3.
We call a pair of a computable full-splitting well-founded tree and a computable assignment a blueprint.
One can easily see that if and only if there exists a blueprint such that and . We are now ready to prove the following:
Proposition 5.4.
For any computable ordinal , we have .
Proof.
It suffices to show that . As mentioned above, corresponds to . Therefore, it suffices to show that for any . Let be a blueprint defining as above. Since is defined, is also defined for any by definition.
We describe Arthur’s strategy for . Assume that Merlin’s first move is , and the second and subsequent moves are . If is a leaf of , then Arthur declares termination with . Here, Arthur can use the information of since is computable. Assume that is not a leaf of . Since the rank of is , the rank of is at most and thus the rank of any immediate successor of is less than . By the property of a blueprint, given , one can compute a -code of for some . In particular, is -computable.
Then consider the following program : Given an input , the computation searches for such that . If such a is found, the computation halts. Otherwise, never halts. Since is defined, exists; that is, there exists such that for any . Hence, there are at most finitely many such that halts. This means that . Then, Arthur declares that the game is to continue, and uses as the next query, that is, is Arthur’s next move.
We claim that this is Arthur’s winning strategy. To see this, if Merlin’s second and subsequent moves are , then we inductively show that . We inductively assume that . As the next move, if Arthur declares that the game is to continue, and uses as the next query, Merlin responds to this with some . This means that . Hence, by the induction hypothesis, we have .
If the history of Merlin’s moves reaches a leaf of , then Arthur declares termination with , and by the above property, we obtain . Hence, the procedure described above is shown to be Arthur’s winning strategy. Consequently, we get . ∎
As for any oracle , this explains the reason why is so powerful as an oracle. Interestingly, by the result in van Oosten [41, Theorem 2.2] mentioned above, one can observe that even if relativized by a tremendously powerful oracle , never be able to compute a non-hyperarithmetic function; that is, for any non-hyperarithmetic , we have no matter what an oracle is. Roughly speaking, this is because a computational process beyond hyperarithmetic is not a finite approximation process, but an approximation process along an ordinal, which prevents us from using “time trick”; see e.g. [3].
5.3. Asymptotic density
As a candidate for another basic bilayer function, one that uses asymptotic density may come to mind. For a set , the lower asymptotic density of is defined by
Then, for any real , we define the basic bilayer function as follows:
Obviously, we have for any real since the asymptotic density of a cofinite set is . The major difference between and is the following property.
Observation 5.5.
for any .
Proof.
We define an outer reduction as follows: For and , put . Then, for an input for , a secret inner reduction is defined by . Note that the asymptotic density of is . Clearly, implies ; hence . ∎
We say that a partial multifunction is hyperarithmetic if there exists a partial function such that for any .
Proposition 5.6.
Let be a partial multifunction whose codomain is with . For any , if , then is hyperarithmetic.
To prove this, we need to show an auxiliary lemma. For a tree , let be the set of all immediate successors of in . For a function , a tree is -fat if, for any which is not a leaf, has at least immediate successors, i.e., . For a function and , consider the function . The following is an analogue of Cenzer-Hinman [8, Proposition 2.9].
Lemma 5.7.
Let be a function, be an -fat finite tree, and be the set of all leaves of . Then, for any function there exists a -fat tree such that is constant on the leaves of .
Proof.
Since is finite, one can assume that any has the same length. We prove the assertion by induction on the height of . Let be given. If , then has leaves, where is the empty strings. As is -valued, there are at least leaves on which is constant.
Next, assume that . Then, for any of length , define as the least such that . Since is -fat, we have , so such a exists. Note that is a function from to . By the induction hypotheis, there exists a -fat tree such that is constant on the leaves of . Let be the unique value of on the leaves of . Note that . Then, define
By definition, clearly is constant on the leaves of . Moreover, for any , by our definition of and , we have
Therefore, is -fat. This concludes the proof. ∎
Proof of Proposition 5.6.
Let be a winning Arthur-Nimue strategy witnessing . Except for the first move , Merlin’s move is always a number , which yields the tree of all possible moves by Merlin. Fix , and then Arthur’s strategy yields a partial computable function , where if and only if, after reading Merlin’s moves , Arthur’s strategy declares termination with . Nimue’s strategy restricts Merlin’s possible moves to a well-founded subtree of such that, for each , if is a leaf then is defined, and the lower asymptotic density of the set is at least since Nimue obeys the rule as long as Merlin obeys the rule, and this value is greater than since . By the definition of lower asymptotic density, there exists such that, for any , we have . In particular, we have
Fix such , where if is either a leaf of or , then is arbitrary. Then, consider the tree of -bounded strings:
Since is finite branching and is well-founded, is finite by König’s lemma. Moreover, is total on the leaves of . Note that if is not a leaf of then . Hence, is -fat. Since is -valued, by Lemma 5.7, there exists a -fat subtree of of the same height such that is constant on the leaves of . Hereafter, we write as since such a satisfying the above density condition is depend on Merlin’s first move .
For a function , our algorithm searches for a -fat finite tree such that is constant on the leaves of , and returns the unique value of on the leaves of if such an exists. Note that if is a correct witness for the above density condition for , then such an always exists. Now, we define as follows
where by we mean that for any . Note that is defined only if succeeds in finding , which means that the algorithm only reads up to the height of . Thus, the above predicate is .
We claim that implies . To see this, put . If then we have by our choice of . If then the algorithm succeeds in finding a -fat finite tree such that for any leaf of . Note that by the definition of , and since is -fat. This implies that is nonempty. Hence, has a common leaf . Since is winning, and is a leaf of , we must have . By our choice of , is constant on the leaves of , and thus must be equal to . This concludes .
We next claim that for any there exists such that . Otherwise, for any there exists such that either is undefined or for any . Then, put . As , clearly, is a correct witness for the above density condition for . Then, by the argument using Lemma 5.7 described above, the algorithm succeeds in finding , so that for some . However, as , this contradicts our assumption on . Therefore, determines a total relation. Since is , by -selection (see Moschovakis [28, 4B.5] or Sacks [36, Theorem II.2.3]), there exists a hyperarithmetic function such that holds. By the first claim, this implies that . ∎
In particular, and have partly the same properties in the following sense.
Corollary 5.8.
Assume . Then, for a function , if and only if is hyperarithmetic.
Proposition 5.6 also shows that for a sufficiently powerful oracle . By Observation 4.1, this implies that . Now it is natural to ask whether or not. One can answer this question by introducing the concept of hyperarithmetical reducibility for bilayer functions. First consider the one-query version.
Definition 5.9.
Let and be bilayer functions. We say that is a one-query hyperarithmetically LT-reducible to (written ) if there exist partial functions and and a partial function such that for any and ,
Let be the th patrial function (given by the canonical enumeration of all sets). Then, consider the following partial multifunction:
It is well-known that is higher analogue of computable enumerability, i.e., a set is if and only if there exists a hyperarithmetical enumeration procedure along a computable ordinal; see e.g. [36, 28]. The following is a hyperarithmetical analogue of Proposition 4.2:
Proposition 5.10.
-.
Proof.
We define a secret inner reduction as follows: For any ,
One can easily check that belongs to the domain of . For an outer reduction , define for any . To compute along computable ordinal steps, wait for finding many such that . If it is found at some ordinal stage, then is defined as the least such that for any such . Otherwise, the computation never terminates, i.e., . One can easily see that is .
For readers who are not familiar with ordinal computability, we describe the details. Let be Kleene’s system of ordinal notations; see e.g. [36, 9]. As Kleene’s is -complete, and the graph of is , there exists a many-one reduction witnessing , where denotes many-one reducibility. Then, for , one can consider the stage approximation of ; that is, if and only if . Note that is c.e. (see e.g. Sacks [36, Theorem I.3.5]); hence is also a c.e. property. Then define as follows:
Now we introduce the notion of hyperarithmetical reducibility for bilayer functions. Arthur’s hyperarithmetic strategy is a code for a partial function .
Definition 5.11.
Let and be bilayer functions. We say that is hyperarithmetically LT-reducible to (written ) if there exists a hyperarithmetical winning Arthur-Nimue strategy for .
The following is an analogue of Proposition 5.6:
Proposition 5.12.
Let be a partial multifunction whose codomain is with . For any , if , then is hyperarithmetic.
Proof.
The argument is the same as Proposition 5.6. Only the complexity of needs to be considered. If we consider a hyperarithmetical strategy, is no longer a computable function, but a function. For this reason, is also . To see this, note that is defined to be if and only if there exists a -fat finite tree such that is defined and constant on the leaves of and its unique value is . This condition is since is finite and is . Moreover, as mentioned in the proof of Proposition 5.6, if is defined then the algorithm only reads up to the height of . Thus, holds if and only if for any , there exists a finite string such that majorizes up to and . This condition is . The rest follows the same argument as in Proposition 5.6. ∎
Corollary 5.13.
For any , if and only if .
Proof.
Note that the above proof also shows that if and only if .
The above results say nothing about . Note that since the asymptotic density of a cofinite set is , we have . We show that computability with density error is strictly stronger than computability with finitely many error in the following sense:
Theorem 5.14.
.
Proof.
Suppose not. Then, there exists a winning Arthur-Nimue strategy witnessing . Except for the first move , Merlin’s move is always a number , which yields the tree of all possible moves by Merlin. Here is a secret input, which is invisible to Arthur. Hence, Arthur’s strategy yields a partial computable function , where if and only if, after reading Merlin’s moves , Arthur’s strategy declares termination with . For , consider the tree . Nimue’s strategy restricts Merlin’s possible moves to the tree , where , and moreover, as is winning, the computation determines covers the tree ; that is, for any infinite path through there exists an initial segment of such that is defined.
This ensures the existence of a function such that the computation covers the tree . Consider the set of all minimal strings such that is defined. Note that any infinite path through has an initial segment in . Then, yields a well-founded subtree of so that is the set of all leaves of . One can see that if is not a leaf then the set of its immediate successors is cofinite. This is because, for any , any infinite path extends has an initial segment . Then is a leaf of , and since is not a leaf, must extend . Hence we have since a tree is -downward closed.
We label each node of this well-founded tree as follows: First, a leaf is labeled by the value of . If is not a leaf, then turn to its immediate successors. If has infinitely many immediate successors which have the same label , then is also labeled by . If there is no such label , then is labeled by .
Now, suppose that the label of the root of is . Then, Merlin plays as his first move, which has clearly asymptotic density . In the following, we assume that Arthur and Nimue follows their winning strategies and , respectively. If Nimue reacts to the above move with , search for such that and the label of is . Such an exists, since for the former condition , recall that the set of immediate successors of a node in is cofinite, and for the latter condition, the label of the root is , so there are infinitely many immediate successors labeled by . Then Merlin plays as his next move. Continuing this argument, Merlin can keep returning nodes of with the same label , and Merlin’s moves eventually reach a leaf of . Reaching a leaf means that Arthur declares termination of the game with some value , but since the label of this leaf is , the value must be . Since and Merlin’s first move is , this means that Merlin wins the game, which contradicts our assumption that is a winning Arthur-Nimue strategy.
Thus, the root of must be labeled by . We say that a node is a big sibling of a node if and take the same value except for the last entry, and is larger than for the last entry; that is, for any and . We also say that a node is decisive if all proper initial segments of are labeled by , but and all big siblings of are labeled by some values in . Note that the root of is not decisive as it is labeled by , so any decisive node has a proper initial segment. Let be a list of all decisive nodes of . First put . At stage , assume that has already been defined. The immediate predecessor of is labeled by since is decisive. The label of means that, for any , there are only finitely many siblings of labeled by . Therefore, by the pigeonhole principle, has a big sibling labeled by some . As is decisive, must be a finite value. Then, put .
Now Merlin plays as his first move, which has asymptotic density since for any by our construction. At the round , assume that the history of Merlin’s previous moves is , and Nimue’s previous move is . First consider the case that the label of is . If has infinitely many immediate successors labeled by , then as his next move Merlin plays so that is labeled by . Otherwise, there are only finitely many immediate successors of labeled by , and thus, there exists a decisive immediate successor of of the form for some . Then we must have for some . As seen above, has a big sibling labeled by . As his next move, Merlin plays the last entry of . Note that the history of moves is now labeled by . Next consider the case that the label of has already become a finite value . In this case, has infinitely many immediate successors labeled by , and then as his next move Merlin can play so that is labeled by .
As this play follows a winning Arthur-Nimue strategy, Arthur declares termination at some round. Then, the history of Merlin’s moves eventually reaches a leaf of which is labeled by a finite value. Hence, the history of Merlin’s moves is labeled by a finite value at some round, and once the label becomes a finite value, our construction of Merlin’s strategy ensures that the value of the label does not change after that. Indeed, Merlin’s strategy described above stabilizes the labels of the histories of Merlin’s moves to for some . Therefore, the history of Merlin’s moves eventually reaches a leaf of which is labeled by , which turns out to be (the second coordinate of) Arthur’s last move since the leaf of is labeled by the value of on it. However, and Merlin’s first move is . This means that Merlin wins the game, which contradicts our assumption that is a winning Arthur-Nimue strategy. Consequently, there exists no winning Arthur-Nimue strategy; hence . ∎
Hence, we get the strict hierarchy of computability with error density :
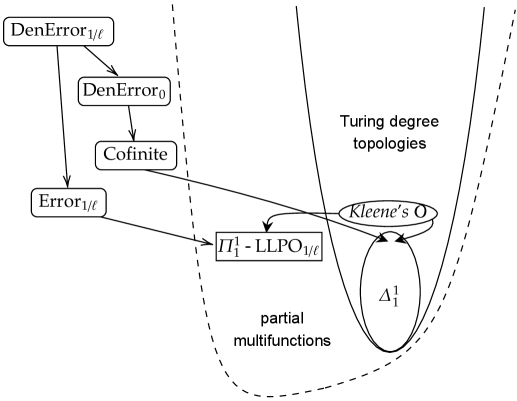
Figure 2 summarizes some of basic implications about the -ordering on the Lawvere-Tierney topologies (around hyperarithmetic Turing topologies) on the effective topos, where means (or ).
6. Future work
One may come up with other basic bilayer functions not mentioned in this article, but we do not know which ones are non-trivial and interesting. It is a vague question, but finding interesting basic bilayer functions is a big problem in itself.
Question 1.
Is there any other interesting basic bilayer function?
In Section 5.1, we have seen that the -version of weak weak König’s lemma, , is Turing equivalent to . Due to this kind of phenomenon, unlike -computation, it is difficult to find a nontrivial partial multifunction in the context of -computation. There are partial multifunctions on not mentioned so far, such as all-or-unique choice on (see e.g. [22]). However, the -version of turns out to be Turing equivalent to by the same argument as above, and is Turing equivalent to the halting problem by considering enumeration time functions as in Section 2.1.
Question 2.
Is there any other natural partial multifunction on whose Turing degree strictly lie between the computable ones and the halting problem?
In this article, we have focused on topologies on the effective topos; however “the world of computable mathematics” for modern computability theorists seems to be the Kleene-Vesley topos rather than the effective topos. As indicated in Section 2.2, the structure of Lawvere-Tierney topologies on the Kleene-Vesley topos seems isomorphic to the bilayer version of generalized Weihrauch reducibility. This structure should also be explored in depth in the future.
As another topos, the realizability topos induced by Kleene’s second algebra corresponds to “the world of continuous mathematics,” and a Lawvere-Tierney topology on the topos is a kind of data that indicates how much discontinuity to add to the world. One can see that the structure of Lawvere-Tierney topologies on the topos is isomorphic to the bilayer version of generalized continuous Weihrauch reducibility.
In general, there are many other toposes that are related to computability theory and (effective) descriptive set theory. As mentioned in Kihara [21], any -pointclass (see [28]) yields a (relative) partial combinatory algebra, which induces a topos. If the pointclass is used as a seed, a topos corresponding to “the world of Borel measurable mathematics” will be created, and if the pair is used, a topos corresponding to “the world of effective Borel measurable mathematics” will be created. These lead us to the study of “Lawvere-Tierney topologies for (effective) descriptive set theorists.” The topologies in this case are some sort of data that indicate how much non-Borel objects to add to the world.
It may also be reasonable to study these structures in the context of synthetic descriptive set theory [32]. We leave the exploration of these structures as a future task.
Acknowledgements.
The author would like to thank Satoshi Nakata for valuable discussions. Kihara’s research was partially supported by JSPS KAKENHI Grant 19K03602 and 21H03392, and the JSPS-RFBR Bilateral Joint Research Project JPJSBP120204809.
References
- [1] Paul-Elliot Anglès d’Auriac and Takayuki Kihara. A comparison of various analytic choice principles. to appear in Journal of Symbolic Logic, arXiv:1907.02769, 2019.
- [2] Andrej Bauer. Instance reducibility and Weihrauch degrees. arXiv:2106.01734, 2021.
- [3] Laurent Bienvenu, Noam Greenberg, and Benoit Monin. Bad oracles in higher computability and randomness. Israel J. Math., 241(1):229–276, 2021.
- [4] Vasco Brattka and Guido Gherardi. Effective choice and boundedness principles in computable analysis. Bull. Symbolic Logic, 17(1):73–117, 2011.
- [5] Vasco Brattka, Guido Gherardi, and Rupert Hölzl. Probabilistic computability and choice. Inform. and Comput., 242:249–286, 2015.
- [6] Vasco Brattka, Guido Gherardi, and Arno Pauly. Weihrauch complexity in computable analysis. arXiv: 1707.03202, 2017.
- [7] Vasco Brattka and Arno Pauly. Computation with advice. In Xizhong Zheng and Ning Zhong, editors, Proceedings Seventh International Conference on Computability and Complexity in Analysis, Zhenjiang, China, 21-25th June 2010, volume 24 of Electronic Proceedings in Theoretical Computer Science, pages 41–55. Open Publishing Association, 2010.
- [8] Douglas Cenzer and Peter G. Hinman. Degrees of difficulty of generalized r.e. separating classes. Arch. Math. Logic, 46(7-8):629–647, 2008.
- [9] Chi Tat Chong and Liang Yu. Recursion theory, volume 8 of De Gruyter Series in Logic and its Applications. De Gruyter, Berlin, 2015. Computational aspects of definability, With an interview with Gerald E. Sacks.
- [10] S. Barry Cooper. Computability Theory. Chapman & Hall/CRC, Boca Raton, FL, 2004.
- [11] Hannes Diener. Constructive reverse mathematics, 2018. Habilitationsschrift, University of Siegen.
- [12] Rodney G. Downey and Denis R. Hirschfeldt. Algorithmic Randomness and Complexity. Theory and Applications of Computability. Springer, New York, 2010.
- [13] Damir Dzhafarov and Ludovic Patey. , , and multiple functionals. arXiv: 1905.00321, 2019.
- [14] Damir D. Dzhafarov. Strong reductions between combinatorial principles. J. Symb. Log., 81(4):1405–1431, 2016.
- [15] Damir D. Dzhafarov, Denis R. Hirschfeldt, and Sarah C. Reitzes. Reduction games, provability, and compactness. arXiv:2008.00907, 2020.
- [16] Jun Le Goh. Compositions of multivalued functions. Computability, 9(3-4):231–247, 2020.
- [17] Jun Le Goh, Arno Pauly, and Manlio Valenti. Finding descending sequences through ill-founded linear orders. to appear in Journal of Symbolic Logic, arXiv:2010.03840, 2021.
- [18] Edward R. Griffor, editor. Handbook of Computability Theory, volume 140 of Studies in Logic and the Foundations of Mathematics. North-Holland Publishing Co., Amsterdam, 1999.
- [19] Denis R. Hirschfeldt and Carl G. Jockusch, Jr. On notions of computability-theoretic reduction between principles. J. Math. Log., 16(1):1650002, 59, 2016.
- [20] J. M. E. Hyland. The effective topos. In The L.E.J. Brouwer Centenary Symposium (Noordwijkerhout, 1981), volume 110 of Stud. Logic Foundations Math., pages 165–216. North-Holland, Amsterdam-New York, 1982.
- [21] Takayuki Kihara. Degrees of incomputability, realizability and constructive reverse mathematics. arXiv:2002.10712, 2020.
- [22] Takayuki Kihara and Arno Pauly. Dividing by zero—how bad is it, really? In 41st International Symposium on Mathematical Foundations of Computer Science, volume 58 of LIPIcs. Leibniz Int. Proc. Inform., pages Art. No. 58, 14. Schloss Dagstuhl. Leibniz-Zent. Inform., Wadern, 2016.
- [23] Sori Lee. Subtoposes of the effective topos. arXiv:1112.5325, 2011.
- [24] Sori Lee and Jaap van Oosten. Basic subtoposes of the effective topos. Ann. Pure Appl. Logic, 164(9):866–883, 2013.
- [25] Vladimir Lifschitz. is stronger than . Proc. Amer. Math. Soc., 73(1):101–106, 1979.
- [26] Benoit Monin and Ludovic Patey. -encodability and omniscient reductions. Notre Dame J. Form. Log., 60(1):1–12, 2019.
- [27] Antonio Montalbán. Martin’s conjecture: a classification of the naturally occurring Turing degrees. Notices Amer. Math. Soc., 66(8):1209–1215, 2019.
- [28] Yiannis N. Moschovakis. Descriptive Set Theory, volume 155 of Mathematical Surveys and Monographs. American Mathematical Society, Providence, RI, second edition, 2009.
- [29] Eike Neumann and Arno Pauly. A topological view on algebraic computation models. J. Complexity, 44:1–22, 2018.
- [30] Piergiorgio Odifreddi. Classical Recursion Theory, volume 125 of Studies in Logic and the Foundations of Mathematics. North-Holland Publishing Co., Amsterdam, 1989. The theory of functions and sets of natural numbers, With a foreword by G. E. Sacks.
- [31] Arno Pauly. Many-one reductions and the category of multivalued functions. Math. Structures Comput. Sci., 27(3):376–404, 2017.
- [32] Arno Pauly and Matthew de Brecht. Descriptive set theory in the category of represented spaces. In 2015 30th Annual ACM/IEEE Symposium on Logic in Computer Science (LICS 2015), pages 438–449. IEEE Computer Soc., Los Alamitos, CA, 2015.
- [33] Andrew M. Pitts. The Theory of Triposes. PhD thesis, The University of Cambridge, 1981.
- [34] Fred Richman. Polynomials and linear transformations. Linear Algebra Appl., 131:131–137, 1990.
- [35] Hartley Rogers, Jr. Theory of Recursive Functions and Effective Computability. MIT Press, Cambridge, MA, second edition, 1987.
- [36] Gerald E. Sacks. Higher Recursion Theory, volume Volume 2 of Perspectives in Mathematical Logic. Springer-Verlag, Berlin, 1990.
- [37] Stephen G. Simpson. An extension of the recursively enumerable Turing degrees. J. Lond. Math. Soc. (2), 75(2):287–297, 2007.
- [38] Stephen G. Simpson. Subsystems of Second Order Arithmetic. Perspectives in Logic. Cambridge University Press, 2009.
- [39] Robert I. Soare. Recursively Enumerable Sets and Degrees. Perspectives in Mathematical Logic. Springer-Verlag, Berlin, 1987. A study of computable functions and computably generated sets.
- [40] Jaap van Oosten. Realizability: an introduction to its categorical side, volume 152 of Studies in Logic and the Foundations of Mathematics. Elsevier B. V., Amsterdam, 2008.
- [41] Jaap van Oosten. Realizability with a local operator of A. M. Pitts. Theoret. Comput. Sci., 546:237–243, 2014.
- [42] Linda Westrick. A note on the diamond operator. Computability, 10(2):107–110, 2021.
- [43] Martin Ziegler. Real computation with least discrete advice: a complexity theory of nonuniform computability with applications to effective linear algebra. Ann. Pure Appl. Logic, 163(8):1108–1139, 2012.