LFSR based RNG on low cost FPGA for QKD applications
Abstract
Linear-feedback shift register (LFSR) based pseudo-random number generator (PRNG) has applications in a plethora of fields. The issue of being linear is generally circumvented by introducing non-linearities as per the required applications, with some being adhoc but fulfilling the purpose while others with a theoretical proof. The goal of this study is to develop a sufficiently “random” resource for Quantum Key Distribution (QKD) applications with a low computational cost. However, as a byproduct, we have also studied the effect of introducing minimum non-linearity with experimental verification. Starting from the numerical implementation to generate a random sequence, we have implemented a XOR of two LFSR sequences on a low-cost FPGA evaluation board with one of the direct use cases in QKD protocols. Such rigorously tested random numbers could also be used like artificial neural networks or testing of circuits for integrated chips and directly for encryption for wireless technologies.
I Introduction
In any digital encryption scheme, random numbers are an indispensable resource, as proposed by Claude Shannon [1]. The applications of random numbers are stratified from cryptography to simulations and the gambling industry. For cryptographic applications, in an ideal world, one would like to use quantum random number generators (QRNGs), which are innately random. However, pertaining to the resource intensiveness, the real-time use case for QRNGs is a little far. The next best alternatives available are pseudo random number generators (PRNGs) and chaotic random number generators. Chaotic ones cannot be used for security applications primarily because Eve can exploit the fact that there is no good way of characterising noise. Amongst PRNGs, one of the earliest, extremely fast and easy to generate known techniques for generating random numbers is using linear feedback shift registers (LFSRs). Being hardware friendly, they are used in testing for power consumption in integrated circuits. In particular, it is typically used to create test patterns for built-in self-test [2]. On the low power front, LFSR based Random Number generators (LRNGs) are widely used in providing encryption to wireless technology such as Bluetooth, where they are used to encrypt frequency hopping spread spectrum systems to protect against signal jamming kind of attacks [3].
Such random number generators are easily implementable on hardware like Field Programmable Gate Array (FPGA) [4] and, thus, could provide an easy access to “randomness” resources for ongoing applications like Quantum Key Distribution (QKD). Succinctly, QKD is the study of securely distributing keys between two communicating parties (say, Alice and Bob) using properties of photons (quanta of light). The field is proposed to takeover the current encryption technique (particularly, ubiquitously used Rivest-Shamir-Adleman (RSA) algorithm) for the latter being inefficient against upcoming quantum computers. The premise being that laws of quantum physics are more fundamental compared to increasingly accessible computational resources (built on fundamentals of physics) against an eavesdropper [5]. The major application for LRNG in QKD applications comes into the picture for prepare-and-measure (P&M) protocols. Pertaining to the particular property of photons being used, there are different P&M based QKD protocols such as those proposed by Bennet and Brassard in 1984 (BB84) and coherent one-way protocol. In the context of BB84 protocol, Alice selects the polarization degree of freedom as her encoding mechanism. To achieve an unbiased distribution of signals across the four polarization states, Alice requires a random bit stream based on LFSR. It generates random numbers that Alice utilizes for preparing the four polarization states in a randomized manner, ensuring equal probability and impartiality among the different polarization states. This requirement is a pre-requisite for unconditional security of any P&M based QKD protocol. In addition to being used at Alice’s end, Bob could also use LRNG sequence to choose the measurement basis by feeding this random bit stream into a liquid crystal polarisation rotator. This requirement at Bob’s end is true for every QKD protocol (not restraining to P&M protocols). This, however, is not a strict requirement as there are other alternatives with certain trade-offs. Hence, we focus on a stronger requirement of “randomness” resource at Alice’s end.
In this work, we aim to obtain a LRNG bit stream, which is implementable on low cost, low powered FPGA boards suitable for BB84 protocol. It is varied for different parameters, say input seed value and post-processed so that it is sufficiently random for QKD applications. The paper is divided into four further sections. Section II discusses preliminaries such as why such random numbers are a good candidate for QKD applications, how it works, and what classifies as a sufficiently random bit stream. In section III, we first discuss our numerical approach followed by hardware implementation of LFSR based random numbers, where we elaborate on how the randomness gets affected by introducing non-linearities. Towards the end, we show one practical application where we have used this in practical BB84 setup for preparing polarisation states randomly. In Section IV, we list possible improvements that are hardware and application dependent. In section V, we conclude the article by summarizing this study.
II Methodology
Here, we focus on generating pseudo random numbers that are sufficiently random and easily implementable on FPGA. LFSR fits this overlap naturally compared to any other pseudo random number algorithm.
II.1 Working of LFSR
LFSR, a type of sequential digital circuit, utilizes clock-driven flip-flops in its operation. It is composed of a collection of D flip-flops, and the quantity of these flip-flops determines the number of bits in the LFSR’s seed. Specifically, a -bit LFSR requires number of D flip-flops. If appropriate taps (XORing position of bits in the initial seed) are chosen, LFSR produces a sequence of bits that are random with a repeatability cycle of () [6]. The operational concept of the LRNG is illustrated in the FIG. 1.
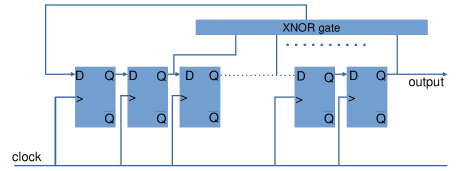
Inspired by hardware implementation, one can also simulate these LFSR on a computer using primitive polynomials. There are two types of LFSR based on the type of XORing operation: Galois field-based and Fibonacci numbers-based [7]. Galois field based have an easier software implementation, while Fibonacci based has an easier hardware implementation. This is primarily because Fibonacci based LFSRs don’t require additional ‘AND’ operations and, thus, more easily weave into the fabric of FPGA.
One of the major disadvantages of the LRNG is that they are linear. Hence, algorithms to catch such correlations exist in the literature. One such algorithm is Berlekamp-Massey Algorithm (BMA) which is the basis of the Linear Complexity Test (LCT) in NIST test suites. Since BMA targets to decipher the generation process of LFSR rather than the output periodicity (), it can decipher a -bit LFSR after measuring just bits with a very high probability. Hence, we add non-linearity via XOR operation to explore the nuances between LCT and the quality of the LFSR bit stream.
II.2 Testing random numbers using NIST statistical test suite
To check the quality of LRNG, we treat the NIST test suite as a gold standard for checking randomness. It is a sufficient criterion, as suggested in the literature. The test suite is a hypothesis testing suite where is null hypothesis that sequence is random while is alternate hypothesis that sequence is not random. In this suite, we majorly focus on Type-I and Type-II errors as depicted below in the TABLE 1 and highlighted in [8].
| True situation | Accept | Accept |
|---|---|---|
| is true | No error | Type-I |
| is true | Type-II | No error |
One can assign a threshold and for Type-I and Type-II errors, respectively. The test static value defines the value, and and are connected. Thus, keeping a check on one is enough, and for NIST, it is . Lower values means higher values.
The test suite checks for certain statistical correlations. A couple of tests in the suite check for disparity between zeroes and ones in a binary sequence for short range and long range. A few of the tests are a variant of auto-correlation tests. Others check for patterns using some pre-decided templates or based on Fourier transforms. The most stringest amongst these tests is LCT as it targets the process of LFSR rather than the output. Other than LCT, LFSRs pass all other 14 statistical tests pretty easily. Also, to avoid misrepresenting these tests using different input parameters, NIST recommends specifying these parameters upfront. In our case, we have used default input parameters, and the test-statistic is set to the default 0.01.
II.3 Numerical approach
Before implementing on hardware, we generated a variety of Fibonacci number based LRNG on software using primitive polynomials. The first variation is on different length strings, whether a 4-bit or 8-bit LFSR. The code used to generate the LRNG is obtained from the GitHub repository [9]. To generate a random bit stream in our case, we have augmented the Matlab code, which generates the desired number of bits () for some defined random input seeds (). For ease of understanding of further variations tested, we use the convention where is width of seed and is initial seed value. In the numerical test bench, we have generated 55M bit stream to check against NIST (pre-requisite of 551 M, as recommended in the manual).
For the second variation, we utilize two randomly generated bit sequences derived from and . The non linearity to the bit stream is introduced via XORing the two outputs. In the third case, we generalise it with inputs XOR(, ). The premise of choosing values is that the numbers should be co-prime. We have discussed two sub-cases in this category. The first variant involves using consecutive values, and the second variant involves using consecutive prime values.
II.4 Previous attempts
Previous attempts in the realm of hardware implementation of random numbers [10] have explored different ideas to overcome the limitations of algorithm-based randomness. Two veins branch out in this direction. One generating random numbers using noise (chaos based random bits). This noise could be because of clock jitter [11], [12] circuit noise [13], [14] etc. The other generating LFSR based random numbers by introducing sufficient non-linearities[15]. This work follows the second vein and introduces a minimum non linearity such that it provides a low computational cost on the FPGA for QKD applications. This minimum non-linearity can be theoretically backed easily with similar approaches to [16].
III Results and Discussion
The following subsections show results for all four variants in tabular form. Broadly speaking, the NIST test suite has 15 statistical tests, and LCT has the stringiest requirement against the LFSR generated bit streams and hence is explicitly mentioned in another column. We have generated the bit stream first on software, and later, hardware implementation is performed only for cases where it passes the NIST test suite for all 15 statistical tests. We have mentioned all the less-sensitive tests (14 of 15) under the column name NIST-tests, while LCT is explicitly mentioned in another column in the tabular representation.
III.1 Numerically generated RNG test results
The numerical simulation was performed using primitive polynomials. The results of the simulation are shown in TABLE 2, 3, 4, and 5.
Variant 1:
This is the simplest case. Here, initialized shift register with the seed and taps which generate the maximum length bit-sequence () and tested for quality of randomness. We observed that only in case of , 14 out of 15 NIST tests are passed. However, the LCT tests still fails. For smaller values, all the 15 tests failed. The results are shown in TABLE 2.
| -bit | NIST-tests | LCT |
|---|---|---|
| 8 | Failed | Failed |
| 16 | Failed | Failed |
| 24 | Failed | Failed |
| 32 | Failed | Failed |
| 64 | Failed | Failed |
| 128 | Passed | Failed |
Results for the case of bolsters our faith in the quality of the randomness test suite. The failure for is evident as the bit stream is generated via the linear operations. This holds true for any or value. Hence, we employ a single XOR operator as a non-linear function to enhance the quality of randomness required for LCT.
Variant 2: XOR(, )
In the second variation, we generate two random-bit sequences using two different seeds ( value) but the same -bit LFSR. This also doesn’t improve the quality of randomness, as verified by the test suite. A few reasons contribute to this failure. Starting with XOR being a linear operation between two same LFSRs. Further, BMA (disguised as LCT in NIST tests) targets the process rather than the bit stream. Finally, LFSR is generated with primitive polynomials implying both BMA and LFSR are seed-agnostic. Hence, the results are similar to what has been discussed in the previous case. The results for same values are shown in TABLE 3.
| NIST-tests | LCT | |
|---|---|---|
| 8 | Failed | Failed |
| 16 | Failed | Failed |
| 24 | Failed | Failed |
| 32 | Failed | Failed |
| 64 | Failed | Failed |
| 128 | Passed | Failed |
Variant 3.1: XOR(, )
In the third category, we generalise the above XOR operation to consecutive , ( and being consecutive are co-prime). The sequence passes all the quality checks, except LCT for the XOR of and . However, the results for and are different. It is based on the fact that the XOR operation introduces enough non-linearity such that LCT isn’t able to catch it. Even the other NIST tests pass for as low as and as shown in TABLE 4.
| NIST-tests | LCT | ||
|---|---|---|---|
| 8 | 9 | Failed | Failed |
| 16 | 17 | Failed | Failed |
| 24 | 25 | Passed | Failed |
| 32 | 33 | Passed | Failed |
| 64 | 65 | Passed | Failed |
| 128 | 129 | Passed | Passed |
Variant 3.2: XOR(, )
In an attempt to find lower values for hardware implementation, we looked at another variant of XOR(, ), with and to be consecutive prime numbers. However, this didn’t provide any significant advantage compared to Variant 1 with results in TABLE 4 for our QKD application. Also, the results did improve compared to the previous variant. Specifically, for values of and , the generated bit sequences pass all NIST tests except for the LCT, which initially showed failures. For XOR(, ) passed all the tests and thus, can be used for suitable application. The results are shown in TABLE 5.
| -bit | -bit | NIST-tests | LCT |
|---|---|---|---|
| 3 | 5 | Failed | Failed |
| 5 | 7 | Failed | Failed |
| 7 | 11 | Passed | Failed |
| 11 | 13 | Passed | Failed |
| … | … | … | … |
| 113 | 127 | Passed | Failed |
| 127 | 131 | Passed | Passed |
As evident from the preceding four variations of LRNGs, it is clear that XOR(, ) and XOR(, ) passes all the 15 tests (14 NIST-tests + LCT). To further investigate, we took 100 sets of random sequences for these two cases. We found that XOR(, ) fails 1.53% of the individual tests, while XOR(, ) fails 1.40% of any individual tests. Passing these tests is a proof that our test statistics value set to 0.01 is correct. Moreover, for both the variants, the interval of acceptance proportions given the significance level and number of tested sequences [17] lies within
For the above case, and =100 and lies within the range [0.990.0099499]. With all the consistency checks and good results, we implement both XOR(, ) and XOR(, ) on FPGA/hardware for our QKD source generation.
III.2 Hardware implementation and test results
Utilizing hardware like FPGA is a necessity for QKD experiments, primarily because of the generation of voltage pulses to control/trigger the operation of any circuit/hardware. For this purpose, we prefer Arty 7 FPGA Evaluation Kit, Artix 7 35T FPGA [18] from AMD to implement the proposed LRNG method. The design of this board is specifically focused on providing a remarkably flexible Micro Blaze Soft Processing System. The board incorporates an on-chip analog-to-digital converter and provides an ample number of I/O options for generating and acquiring voltage signals. Consequently, there is no need for an additional daughter board to facilitate interfacing with real-time signals. In addition to its specifications, this board boasts a compact form factor, affordability, and suitability for our operations. Additionally, the board is a low cost ($159) and provides 100 MHz clock rate.
We have chosen Very high speed integrated circuit hardware Description Language (VHDL) codes for our implementation. One can use Verilog or another high level language like C or Python for programming FPGA. The generated random voltage pulses are time tagged and subsequently generated bits are tested against NIST test suite. The resulting outcomes are presented in the TABLE 6 and 7. The VHDL code implemented on FPGA for the current article can be obtained from the Ref. [19].
III.2.1 Test setup
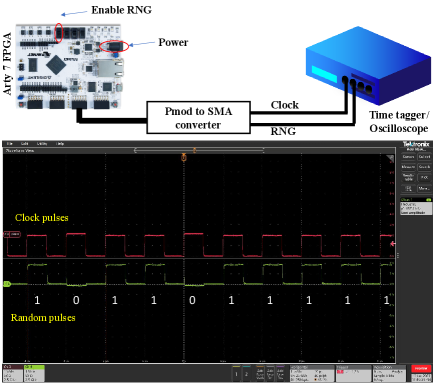
The VHDL code for generating random numbers via shift register is fed to Arty 7 FPGA board. The setup for generating time stamps and corresponding voltage pulses is shown in FIG. 2. Along with random voltage pulses, we also generate clock pulses for referencing to assign random pulses as bit 0 and 1. In this setup, the FPGA board’s output is derived from its I/O ports, featuring Pmod connectors. Typically to generate random bits, the clock and random voltage signal produced by the FPGA board must be fed into the time tagger module. However, since the time tagger module is equipped with an SMA connector, the use of a Pmod to SMA converter shown in FIG. 2 becomes imperative to establish the necessary connection. Furthermore, in QKD setup, the laser diode driver circuit also incorporates an SMA connector. Consequently, the utilization of a Pmod to SMA converter is also crucial to seamlessly integrate the FPGA board’s signals with the laser diode driver circuit.
The timing waveform in FIG. 2 illustrates the waveform of the random voltage pulses and reference clock pulses. We utilize a time tagger (IDQuantique ID900) to accurately track the timestamps of the clock and random pulses. This enables precise recording and synchronization of their timing information.
III.2.2 NIST results for FPGA implemented random bit stream
To test the random pulses generated from the FPGA board for XOR(, ) and XOR(, ), we connect both the ports (clock and random signals) to the IDQuantique ID900 time-tagger. It records the time of the arrival of these pulses. The time stamps recorded by the time-tagger are post-processed in Matlab to obtain a raw binary bit stream.
In the first step, we record time stamps of random pulses and clock pulses for XOR(), ). The clock rate for random voltage generation is set to 1 MHz for hardware implementation. The overall data consists of (55 sets 1 M) random bits, where each set is recorded for 1 second and is concatenated. The results obtained are in good agreement with the numerically obtained data. We have used the “randperm()” function, which is built on the Ziggurat algorithm variant incorporating MT-19937 as a generator. The TABLE 6 showcases the results from different shuffling referred as Random-1/2/3/4/5 while other concatenations are obvious. The last row entry under the column “None” means that we generated a random bit stream of 55 M length in one go. In all of these cases, all 15 NIST tests successfully passed. Similarly for XOR(, ), the corresponding results are depicted in the TABLE 7.
| Exposure time | Concatenation | NIST-tests | LCT |
|---|---|---|---|
| 1 s | Serial | Passed | Passed |
| 1 s | Reverse | Passed | Passed |
| 1 s | Random-1 | Passed | Passed |
| 1 s | Random-2 | Passed | Passed |
| 1 s | Random-3 | Passed | Passed |
| 1 s | Random-4 | Passed | Passed |
| 1 s | Random-5 | Passed | Passed |
| 55 s | None | Passed | Passed |
| Exposure time | Concatenation | NIST-tests | LCT |
|---|---|---|---|
| 1 s | Serial | Passed | Passed |
| 1 s | Reverse | Passed | Passed |
| 1 s | Random-1 | Passed | Passed |
| 1 s | Random-2 | Passed | Passed |
| 1 s | Random-3 | Passed | Passed |
| 1 s | Random-4 | Passed | Passed |
| 1 s | Random-5 | Passed | Passed |
| 55 s | None | Passed | Passed |
Throughout the hardware implementation, the selection of an optimal clock rate proved to be a crucial parameter due to the limitations in synthesizing certain code configurations on the FPGA board. We systematically generated random numbers for 1 MHz clock rate using FPGA. The device consumes 64 mW of power for XOR (, ) and 63 mW for XOR(, ).
III.3 Application of FPGA based RNG in QKD
The major application for LFSR in QKD applications comes into the picture for P&M protocols. Our application is mainly dedicated to the BB84 protocol implementation which is one of the well-studied P&M and popular QKD protocols. The operational functioning behind P&M based QKD protocols is to use a particular property of photons (say, polarisation/phase) and use it to generate quantum states in mutually unbiased bases, send them to another party who measures them, and form a key. Say, Alice chooses a polarisation degree of freedom to encode and share the key with Bob for communication. Alice needs to prepare her states which are indistinguishable (arbitrary) in four different polarisation quantum states, namely horizontal , vertical , diagonal , anti-diagonal. To prepare this signal, Alice uses four different laser diodes (one for each quantum state) and combines them. However, while combining, we need to make sure that laser circuits for all four laser diodes should fire randomly so that the signal is unbiased to all four quantum states. This requirement is a pre-requisite for unconditional security of any P&M-based QKD protocol.
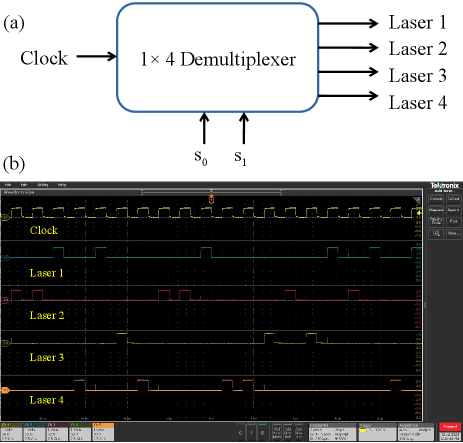
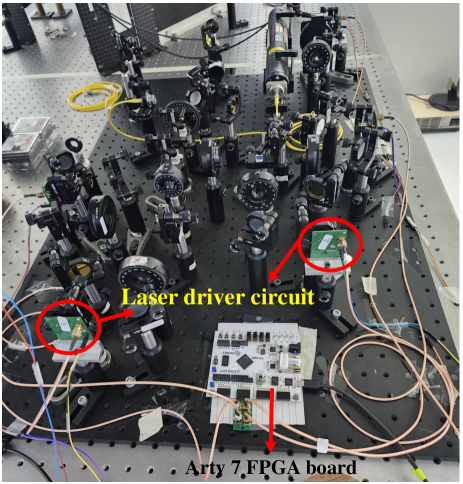
To meet the specified requirements, we have developed a laser driver circuit that utilizes random voltage pulses generated from an FPGA. Additionally, we have incorporated a 14 demultiplexer in the FPGA, which is controlled by randomly generated select lines derived from LFSR generated random bits. This demultiplexer ensures that only one output port of the FPGA is enabled at any given time, thereby allowing for the activation of a single laser diode at a time. By implementing this demultiplexing scheme, we can achieve the generation of four random polarization states in FIG. 3. The schematic diagram illustrating the demultiplexing scheme is presented in FIG. 3 (top). The random voltage pulses generated from Arty 7 for driving the laser diode driver circuit is shown in FIG. 3 (bottom). The optical setup of the QKD transmitter is shown in FIG. 4. Here, we have used laser diode driver circuit (marked in red circle), integrated with other optical components of BB84 setup [20]. Information bits are encoded in polarisation and then sent to Bob via quantum channel.
IV Outlook
In this work, we have studied the application of LFSR based RNG implemented on FPGAs to be used in QKD applications. Within the QKD framework, these RNG can also be used to provide robustness against electromagnetic interference while transferring data to a trusted node via Serial Advanced Technology Attachment (SATA) protocol [21]. Outside of QKD, it could be used for carrying out vulnerability analysis of FPGA based computer vision applications [22]. On the premise that there are no specific guidelines on generating a robust non-linear Boolean function, a natural extension of this work could be to look in this direction. LFSRs on FPGAs are being tested for Internet of Things (IoT) applications using Artificial Neural Networks [23]. In this work, we improved the quality of LRNG by modifying the generation process of RNG. The proposed method and proposed for LFSRs are, one can say, are sufficient to pass the NIST statistical test suite; however, they are not the limit. Depending upon the application requirement and availability of the FPGA board, there are several possible improvements in this technique. Some improvements that are foreseen are listed below:
-
1.
One can generate a new seed everytime the device boots such that the linear correlations cannot be deciphered if one models the data for too long.
-
2.
Another open direction is to use higher values, not restricting up to 131. This could be used for other applications. Say, for example, one can choose XOR(, ) which passes not only the default block length parameter (m=500) in LCT but passes LCT upto m=3100. This direction of inquiry is strictly application and resource dependent.
-
3.
In the current work we have synthesised VHDL code of LRNG in FPGA for different clock rate(1 MHz, 5MHz, 10 MHz, 15 MHz, 20 MHz, and 25 MHz) for 2 cases XOR(, ) and XOR(, ). However, hardware implementation and verification on FPGA was done only for 1 MHz as per our current requirement for QKD application. As the code is synthesizable for higher bit-rates, this technique promises compatibility for setups with higher key rate. Depending on hardware constraints and use case, and one can generate the bit stream in GHz range which is suitable for video-conferencing using QKD applications.
-
4.
Increasing complexity in a controlled manner is another way to circumvent going to higher d values to pass LCT test for higher m values. The amount of controlled complexity that can be introduced is dependent on both hardware and theoretically proof of non-linearity. For example operations like XOR(XOR(, ), XOR(, )) using four different ’s and ’s.
-
5.
On the quality of randomness testing front, one can check for chi-square hypothesis testing against other statistical test suites, say, Dieharder, TestU01, ENT. One could also use other alternatives for hypothesis testing, like the Kolmogorov-Smirnoff test or Borel normality, depending on how stringent the randomness is for specific applications.
V Conclusion
In this article, we proposed a method to generate LRNG for QKD applications which passes all th NIST statistical test suites and can be easily theoretically backed. The number of tests failed also cross-verifies the meaning of test specific -value. We verified various cases of single XOR operation, which can introduce enough non-linearity to pass the LCT test. We have shown that amongst the variants XOR(, ) and XOR(, ) passed the test for 100 sets with better accuracy and hence, is a better random number generator. Compared to the consensus on the quality of the bit stream, our random bit stream passes stringent conditions (15/15 tests). Further, the proposed method was implemented on a low-cost FPGA board and verified that those random pulses, too, passed the test. On the application side, we use our method for the weak-coherent pulses-based source to study the BB84 protocols.
Acknowledgement
The authors like to acknowledge the funding support from the Department of Science and Technology (DST), India through QuEST program. The authors also acknowledge initial discussions with Dr. Ayan Biswas, York Centre for Quantum Technologies, School of Physics Engineering and Technology, University of York.
Data Availability
The data that support the findings of this study are available from the corresponding author upon reasonable request.
Disclosures
The authors declare no conflicts of interest related to this article.
References
- Shannon [1949] C. E. Shannon, Communication theory of secrecy systems, The Bell system technical journal 28, 656 (1949).
- Devika and Bhakthavatchalu [2017] K. Devika and R. Bhakthavatchalu, Design of reconfigurable LFSR for VLSI IC testing in ASIC and FPGA, in 2017 international conference on communication and signal processing (ICCSP) (IEEE, 2017) pp. 0928–0932.
- Ebrahimzadeh et al. [2013] A. Ebrahimzadeh, A. Falahati, et al., Frequency hopping spread spectrum security improvement with encrypted spreading codes in a partial band noise jamming environment, Journal of Information Security 4, 1 (2013).
- Madhupavani and Suneetha [2017] G. Madhupavani and K. Suneetha, Design of random number generation using 256 Bit LFSR in FPGA, International Journal of Advanced Technology and Innovative Research 9 (2017).
- Krishna et al. [2001] C. Krishna, A. Jas, and N. A. Touba, Test vector encoding using partial LFSR reseeding, in Proceedings International Test Conference 2001 (Cat. No. 01CH37260) (IEEE, 2001) pp. 885–893.
- Alfke [1996] P. Alfke, Efficient shift registers, LFSR counters, and long pseudo random sequence generators (1996).
- wikipedia [2023] wikipedia, Linear-feedback shift register (2023).
- Moore [2023] T. Moore, The NIST Statistical Test Suite (2023), accessed: 2023-06-11.
- Bajaj and Best [2023] N. Bajaj and F. Best, Nikeshbajaj/linear_feedback_shift_register: 1.0.7 (2023).
- Wang and Lu [2020] C.-C. Wang and S.-W. Lu, 100 mhz random number generator design using interleaved metastable NAND/NOR latches, in 2020 IEEE Asia Pacific Conference on Circuits and Systems (APCCAS) (IEEE, 2020) pp. 98–101.
- Demir and Ergün [2020] K. Demir and S. Ergün, A comparative study on fibonacci-galois ring oscillators for random number generation, in 2020 IEEE 63rd International Midwest Symposium on Circuits and Systems (MWSCAS) (IEEE, 2020) pp. 631–634.
- Majzoobi et al. [2011] M. Majzoobi, F. Koushanfar, and S. Devadas, Fpga-based true random number generation using circuit metastability with adaptive feedback control, in Cryptographic Hardware and Embedded Systems–CHES 2011: 13th International Workshop, Nara, Japan, September 28–October 1, 2011. Proceedings 13 (Springer, 2011) pp. 17–32.
- Santoro et al. [2009] R. Santoro, O. Sentieys, and S. Roy, On-the-fly evaluation of FPGA-based true random number generator, in 2009 IEEE Computer Society Annual Symposium on VLSI (IEEE, 2009) pp. 55–60.
- Xu and Wang [2016] X. Xu and Y. Wang, High speed true random number generator based on FPGA, in 2016 International Conference on Information Systems Engineering (ICISE) (IEEE, 2016) pp. 18–21.
- Zode et al. [2019] P. Zode, P. Zode, and R. Deshmukh, Fpga based novel true random number generator using LFSR with dynamic seed, in 2019 IEEE 16th India Council International Conference (INDICON) (IEEE, 2019) pp. 1–3.
- Fúster-Sabater and Caballero-Gil [2014] A. Fúster-Sabater and P. Caballero-Gil, Weak equivalents for nonlinear filtering functions, in Computational Science and Its Applications–ICCSA 2014: 14th International Conference, Guimarães, Portugal, Vol. Proceedings, Part VI 14 (Springer, 2014) pp. 592–602.
- Marton and Suciu [2015] K. Marton and A. Suciu, On the interpretation of results from the nist statistical test suite, Science and Technology 18, 18 (2015).
- AMD [2015] AMD, Artix 7 35T Arty FPGA Evaluation Kit (2015).
- Meka and Chandravanshi [2023] J. Meka and P. Chandravanshi, LFSR based RNG for QKD application (2023).
- Biswas et al. [2021] A. Biswas, A. Banerji, P. Chandravanshi, R. Kumar, and R. P. Singh, Experimental side channel analysis of bb84 qkd source, IEEE Journal of Quantum Electronics 57, 1 (2021).
- Guha et al. [2016] S. Guha, W. Wang, S. Ibraheem, M. Balakrishnan, and J. Szefer, Design and implementation of open-source SATA III core for Stratix V FPGAs, in 2016 International Conference on Field-Programmable Technology (FPT) (IEEE, 2016) pp. 237–240.
- Chadjiminas et al. [2015] I. Chadjiminas, C. Kyrkou, T. Theocharides, M. K. Michael, and C. Ttofis, In-field vulnerability analysis of hardware-accelerated computer vision applications, in 2015 25th International Conference on Field Programmable Logic and Applications (FPL) (IEEE, 2015) pp. 1–4.
- Teodoro et al. [2021] A. A. Teodoro, O. S. Gomes, M. Saadi, B. A. Silva, R. L. Rosa, and D. Z. Rodríguez, An FPGA-based performance evaluation of artificial neural network architecture algorithm for IoT, Wireless Personal Communications , 1 (2021).