MAC Wiretap Channels with Confidential and Open Messages: Improved Achievable Region and Low-complexity Precoder Design
Abstract
This paper investigates the achievable region and precoder design for multiple access wiretap (MAC-WT) channels, where each user transmits both secret and open (i.e., non-confidential) messages. All these messages are intended for the legitimate receiver (or Bob for brevity) and the eavesdropper (Eve) is interested only in the secret messages of all users. By allowing users with zero secret message rate to act as conventional MAC channel users with no wiretapping, we show that the achievable region of the discrete memoryless (DM) MAC-WT channel given in [1] can be enlarged. In [1], the achievability was proven by considering the two-user case, making it possible to prove a key auxiliary lemma by directly using the Fourier-Motzkin elimination procedure. However, this approach does not generalize to the case with any number of users. In this paper, we provide a new region that generally enlarges that in [1] and provide general achievability proof.
I Introduction
To meet the tremendous demand for wireless communications, the future mobile systems will incorporate many different network topologies and large numbers of devices that may access and leave at any time, making it difficult to generate and manage cryptographic keys. In addition, advances in quantum computing make systems based on classical computational cryptography intrinsically insecure. Hence, the conventional cryptographic encryption methods, which rely on secret keys and assumptions of limited computational ability at eavesdroppers (Eves), are no longer sufficient to guarantee secrecy in the future mobile networks. To address these issues, advanced signal processing techniques developed for embedding security directly in the physical layer have emerged and triggered considerable research interest in recent years [2, 3]. Different from the cryptographic encryption methods employed in the application layer, physical layer security techniques exploit the random propagation properties of radio channels and advanced signal processing techniques to prevent Eves from wiretapping. Furthermore, physical layer security guarantees privacy in an information theoretic sense, i.e., without relying on Eves’ limited computational limitations. Ever since the early seminal works [4, 5, 6, 7], the research of wiretap channels or physical layer security has evolved into various network topologies over the past decades, e.g., multiple access (MAC) wiretap channels [8, 9, 10, 11, 12, 13, 14, 15, 1], broadcast channels [16, 17, 18, 19, 20], interference channels [21, 22, 23, 24, 25, 26], relay-aided channels [27, 28, 29, 30, 31, 32, 33], etc. This paper mainly studies the physical layer security problem for MAC wiretap (MAC-WT) channels. Hence, we introduce MAC-WT related works in the following.
We begin the review from works that studied MAC-WT systems with two transmitters [8, 9, 10, 11, 12]. Reference [8] considered a discrete memoryless (DM) MAC-WT channel with a weaker Eve which has access to a degraded version of the main channel, and developed an outer bound for the secrecy capacity region. In [9], one user wishes to communicate confidential messages to a common receiver while the other one is permitted to eavesdrop. Upper (converse) and lower (achievable) bounds for this communication situation were investigated. A similar system was considered in [10] where, differently, each user attempts to transmit both common and confidential information to the destination, and sees the other user as an Eve. Reference [11] extended the work in [9] and [10] to a fading cognitive MAC channel. In [12], the MAC-WT system with a DM main channel and different wiretapping scenarios was studied.
In [1] and [13, 14, 15], the more general MAC-WT channel with any number of users was investigated. Specifically, [13] provided achievable rate regions for a Gaussian single-input single-output (SISO) MAC-WT channel with a weaker Eve under different secrecy constraints. The work was then extended by [14] to a non-degraded MAC-WT channel where, besides confidential information, each user has also an open (i.e., non-confidential) message intended for Bob. An achievable rate region for both secret and open message rates was provided in [14]. However, as we showed in [1] and [15], there is a problem with the coding scheme in [14], because of which rate tuples that are actually non-achievable are mistakenly claimed to be achievable. In this sense, [1] and [15] provide a general achievable rate region for the MAC-WT scenario with confidential and open messages while [14] does not. Note that in contrast to the works which considered only confidential information, by simultaneously transmitting secret and open messages, the spectral efficiency of the system can be greatly increased [1], [15].
Based on the information-theoretic results, many references have studied the resource allocation problems for MAC-WT channels [14, 34, 35, 36, 1]. The sum secrecy rate of a Gaussian SISO MAC-WT channel was maximized by power control in [14], and it was shown that in the optimal case, only a subset of the strong users will transmit using the maximum power while the other users will keep inactive. [34] and [35] maximized the sum secrecy rate of a single-input multi-output (SIMO) device-to-device (D2D) underlaid network. However, it was assumed in these two papers that both Bob and Eve adopted independent decoding, i.e., treating interference from the other users as independent additive noise. Notice that designing a system under the assumption that Eve uses a suboptimal detection scheme may be risky, since the system secrecy may break down if Eve actually applies an enhanced receiver. Reference [36] considered the sum secrecy rate maximization problem of a Gaussian multiple-input multiple-output (MIMO) MAC-WT system, where both Bob and Eve applied the optimal joint decoding scheme. However, a special power constraint was set to the signal vector covariance matrices, which limited the secrecy performance of the network. In [1], the general power constraint was considered and it was shown that the system secrecy performance could be greatly improved compared with [36].
In this paper, we continue the study of the information-theoretic secrecy problem for a general MAC-WT channel in [1]. To make full use of the channel resources, besides the confidential message, each user also has an open message for Bob. Eve aims to wiretap the confidential information of all users. The main contributions of this paper are summarized below.
In [1], we provided an achievable region for the DM MAC-WT channel in [1, Lemma ] and proved the achievability by considering a simple two-user case. Though the general proof can be developed by following similar steps, the key auxiliary result [1, Lemma ] does not appear to be directly extended to the case with arbitrary number of users . An extension of [1, Lemma ] (see Theorem 1 in this paper) is also of great importance for the general achievability proof in this paper. To prove Theorem 1, we first give the general form of [1, Lemma ] with any in Lemma 1. For a simple system with a few users, this lemma can be proven by directly using the Fourier-Motzkin procedure [37, Appendix D]. However, as grows, this direct proof becomes unmanageable due to the excessively large number of inequalities. We proved the case by direct elimination in note [38], which shows how the number of inequalities quickly explodes with . Besides the extremely high complexity, another disadvantage of the direct elimination strategy is that it works only if the number of users is given. Obviously, this makes the strategy inappropriate for the proof of Lemma 1 since it is a general result for any . In Appendix A, we circumvent this problem and provide a general proof of Lemma 1. Then, using Lemma 1, the general proof of Theorem 1 follows.
In [1], ‘garbage’ messages were introduced to all users to ensure perfect secrecy. This is important if a user’s secrecy rate is positive. However, when a user has zero secrecy rate, two options are possible: 1) still introducing ‘garbage’ messages such that Eve cannot decode all of its information; 2) acting as a conventional MAC channel user with no wiretapping and just transmitting its open message. We show in this paper that there is a trade-off between these two options, i.e., both of them have advantages and disadvantages. Using the first option, the user’s signal is noise and non-decodable for Eve and thus helps reduce Eve’s wiretapping capability. But as we will show, this option introduces many more constraints in determining the corresponding achievable region. With the second option, since it is possible for Eve to decode the user’s open message and then cancel it from the received signal, Eve may have a stronger wiretapping capability. However, this option causes fewer constraints to the user’s open message rate, which is of course good for determining the achievable region. In this paper, we consider all possible cases and provide in Theorem 2 an achievable region for the DM MAC-WT channel, which improves that given in [1, Lemma ]. Note that different from [1] which proved the achievability for a simple two-user case, we provide the general proof of Theorem 2 for arbitrary . Considering a special case where all users have only confidential information, we get directly from Theorem 2 an achievable region for the classical DM MAC-WT channel with no open messages. The achievable region for such a channel has already been studied in [8] and [13]. But we show in Lemma 4 that our result improves these provided by [8] and [13].
Notations: we use calligraphic capital letters to denote sets, to denote the cardinality of a set, “ ” to represent the set subtraction operation, and for the Cartesian product of the sets and . We use line over a calligraphic letter to indicate it is the complement of a set, e.g., if . We use calligraphic subscript to denote the set of elements whose indexes take values from the subscript set, e.g., , , , etc. is the set of natural numbers, and and are the real and complex spaces, respectively. Boldface upper (lower) case letters are used to denote matrices (vectors). A similar convention but with boldface upper-case letters is used for random vectors. stands for the dimensional identity matrix and denotes the all-zero vector or matrix. Superscript denotes the conjugated-transpose operation, denotes the expectation operation, and . The logarithm function is base .
II DM MAC-WT Channel
In this section, we introduce the general DM MAC-WT channel model and define metrics based on which coding schemes can be designed to guarantee perfect secrecy. Then, we provide an extension of [1, Lemma ], which plays quite an important role for the achievability proof.
II-A DM MAC-WT Channel Model
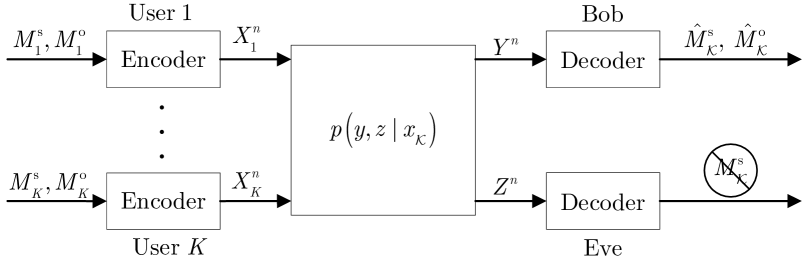
As shown in Fig. 1, we consider a DM MAC-WT channel with users, a legitimate receiver (or Bob for brevity), and an eavesdropper (Eve). Let denote the set of all users. The DM MAC-WT system can then be denoted by (in short ), where , , and are finite alphabets, is the channel inputs from user , and and are respectively channel outputs at Bob and Eve. For brevity, we use the short-hand notation to indicate . Analogous short-hand notations are clear from the context.
Each user transmits a secret message and an open message to Bob. Eve attempts to overhear all the secret messages but is not interested in the open messages. User encodes its information into a codeword , and then transmits it over the channel with transition probability . Upon receiving the sequence , Bob decodes the messages of all users. To avoid leakage of confidential information to Eve, the secret messages of all users, i.e., , should be protected. Let and denote the rate of user ’s secret and open messages. Then, a secrecy code for the considered DM MAC-WT channel consists of
-
•
Secret and open message sets: and . Messages and are uniformly distributed over the corresponding sets and .
-
•
randomized encoders: the encoder of user maps the message pair to a codeword .
-
•
A decoder at Bob which maps the received noisy sequence to the message estimate .
To ensure that all messages can be perfectly decoded at Bob and all confidential information can be perfectly protected from Eve, we define two metrics, i.e., the average probability of error
| (1) |
for Bob and the information leakage rate for Eve. For the MAC-WT channel, a widely used information leakage rate is and it is required that this rate vanishes as goes to infinity [1, 8, 13, 14]. In this paper, we use a different leakage rate, based on which perfect secrecy can be realized and the achievable rate region in existing literatures can be improved.
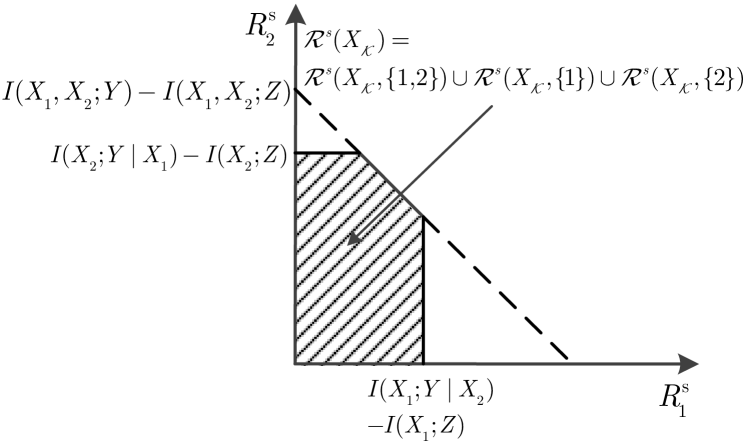
We divide the user set into two parts, i.e., with , and with . Here we do not require if such that users in can also be reclassified to . To protect the confidential information of users in , the coding scheme has to at least ensure that Eve cannot directly decode their messages using the normal MAC decoding scheme even if Eve has codebooks of all users. As for user , since , there is no such requirement and it is thus possible for Eve to get its open message . For a given , since and it is possible that Eve gets , we have
| (2) |
where the last step holds since the messages of all users are independent. If is used to evaluate the secrecy level, a hidden assumption is that Eve cannot decode the messages of all users, including , since otherwise due to (II-A), Eve may be able to extract the confidential information from even if . Hence, we argue that the secrecy requirement based solely on implicitly forces any achievable coding scheme to prevent Eve to decode the open messages of users in . This requirement may be too restrictive and thus may limit the achievable region. As an alternative, we propose to use
| (3) |
to evaluate the system’s secrecy level. For perfect secrecy, we require and take the union over all possible choices of . Obviously, by using (3), it is no longer necessary to design codes that prevent Eve from decoding .
Note that here we are not saying is always a bad metric in designing the codes and determining the achievable region. Actually, as we will show later, by preventing Eve from decoding , the signal of users in performs as noise to Eve, and may thus limit its wiretapping capability. What we want to emphasize is that more possibilities should be taken into account. In this paper, we use (3) to evaluate the secrecy level for all possible . As stated above, users in can be reclassified to . If , i.e., , it is obvious that (II-A) holds with equality, indicating that the case using metric is also considered.
II-B Extension of [1, Lemma ]
In wiretap channels, to protect or hide the confidential information, ‘garbage’ messages are usually introduced to the users [1, 15, 37]. We also do so in this paper. It is thus important to study the existence condition of the ‘garbage’ message rate (see a two-user example in [1, Lemma ]). With the condition satisfied, ‘garbage’ messages can be introduced at a feasible rate and perfect secrecy can be proven. We give the condition for the considered DM MAC-WT channel in the following theorem, which plays quite an important role for the achievability proof in this paper.
Theorem 1.
Let . For any , if , then, for any rate tuple satisfying
| (5) |
there exist such that
| (6) |
where , , , and is the rate of the ‘garbage’ message added by user to protect its confidential information
Proof: We give in the following Lemma 1, which is a special case of Theorem 1 for and directly extends [1, Lemma ] to the case with any . Lemma 1 is proven in Appendix A. Then, using this lemma, Theorem 1 is proven in Appendix B.
In contrast to [1, Lemma ], which considers only two users and can thus be easily proven, Theorem 1 not only extends the result to the general case with any , but also gives the existence conditions of for all possible subsets , which is quite important for the achievability proof in this paper. To apply the coding scheme provided in the next section, it is also necessary to know how to find the feasible . We show that this is easy. For a given and any rate tuple satisfying (5), the linear inequalities in (6) define a polytope as a feasible region of , which should be non-empty since otherwise the region defined by (5) is empty. Then, we may apply Dantzig’s simplex algorithm to obtain [39].
For the case , the basic result obtained from Theorem 1 is collected in the following lemma.
Lemma 1.
Let . If , for any rate tuple satisfying
| (7) |
there exist such that
| (8) |
where .
Proof: See Appendix A.
Remark 1.
As already remarked before, Lemma 1 is a direct extension of [1, Lemma ] from a two-user case to the general . For the simple system with a small , e.g., or , as stated in [1], Lemma 1 can be proven by eliminating in (8) using the Fourier-Motzkin procedure [37, Appendix D] and showing that (7) is the projection of (8) onto the hyperplane . However, when increases, the number of inequalities resulted in the elimination procedure grows very quickly (doubly exponentially), making it quite difficult or even impractical to prove this lemma by following this brute-force way. Besides the great complexity, another problem is that the strategy works only if is given. Obviously, this makes the strategy inappropriate for the proof of Lemma 1 since it is a general result for any .
In note [38], we consider a system with and prove Lemma 1 by eliminating , , and one by one. From (8) we first get upper bounds and lower bounds on . By pairing up these lower and upper bounds, we get inequalities, based on which upper bounds and lower bounds on are obtained. We then eliminate and get inequalities, in which most of them are redundant. Neglecting the redundant terms, we further get upper bounds and lower bounds on , and inequalities by pairing them up. Neglecting the redundant terms, we show that the inequalities left construct (7). This unpublished note is mentioned here and made public in [38] to illustrate how difficult the brute-force Fourier-Motzkin elimination is, even in the simple case of users.
III Improved Achievable Region of the DM MAC-WT Channel
As stated in the introduction part, the information-theoretic secrecy problem for a MAC-WT channel with both secret and open messages has been studied by [14] and [1]. However, it was shown in [1] that there is a problem with the coding scheme in [14], because of which rate tuples that are non-achievable are mistakenly claimed to be achievable. As a correction, [1] provided an achievable region in [1, Lemma ] and its proof for the two-user case. In this section, we show that the achievable region provided in [1, Lemma ] can be further improved and give the general proof for any . Using the result, we also show that a new achievable secrecy rate region can be obtained for the conventional MAC-WT channel with only secret messages, which improves the regions given in the existing literature.
III-A Motivations of Improving [1, Lemma ]
Here we explain why it is possible to improve [1, Lemma ]. For convenience, we rewrite [1, Lemma ] below.
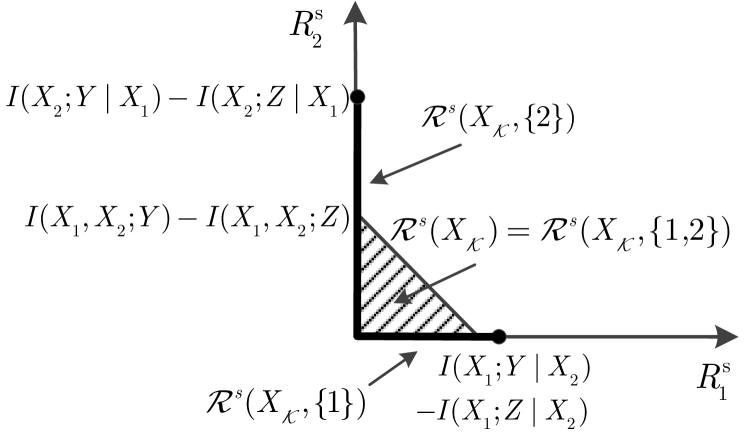
Lemma 2.
In Subsection III-B, we give Theorem 2, which improves the region in Lemma 2, and provide the general proof for any in Appendix C. Now we consider two special cases of Lemma 2 and provide some observations that evidence the fact that the region of Lemma 2 can be improved.
First, consider the case with . Then, (9) becomes
| (10) |
which can be further simplified as (11) since for any , it is obvious that . We give an achievable secrecy rate region in the following lemma.
Lemma 3.
Assume that and . Any rate tuple satisfying
| (11) |
is achievable. Let denote the set of rate tuples satisfying (11). Then, the convex hull of the union of over all is an achievable secrecy rate region of the DM MAC-WT channel with only secret messages.
Similar achievable secrecy rate regions for Gaussian MAC-WT channels can be found in [13, Theorem ] (with two users), [8, Theorem ] (with a weaker Eve which has access to a degraded version of the main channel), and also [14, Theorem ] (by letting all open message rates be ). Notice that we have shown in [1, Remark and Appendix G] that [14, Theorem ], which bounds the secret and open message rates is in general incorrect. We show in Lemma 4 in Subsection III-B that the region provided in Lemma 3 can be enlarged. The results in [13], [8], and [14] can thus also be improved.
Next we consider another special case with , i.e., each user has only an open message for Bob. Intuitively, we hope to get from Lemma 2 the capacity region of the standard MAC channel with users and no wiretapping. Unfortunately, we show that it is not the case. With , (9) becomes
| (12) |
which can be divided into two parts as follows
| (13a) | |||
| (13b) | |||
Obviously, (13a) over all constructs the capacity region of a conventional MAC channel with no wiretapping. However, due to (13b), the region becomes smaller, indicating that the achievability results given in Lemma 2 do not handle ‘well’ the case where all (or some) users do not have confidential information. This is because in [1], the coding scheme introduces ‘garbage’ messages to all users and ensures to hide the confidential information. This is important if . But if , i.e., user has no confidential information, this may be unnecessary or even have a negative effect in determining the achievable region. We will give the more detailed explanations in Subsection III-B.
III-B Improved Achievable Region
By allowing users with zero secret message rate to act as conventional MAC channel users with no wiretapping, we obtain a better achievable region in the following Theorem 2. We show later that this theorem not only improves Lemma 2, by considering the special cases with only secret or open messages as we have done in Subsection III-A, it also improves Lemma 3 and yields the standard MAC capacity region as a byproduct in a natural immediate way.
Theorem 2.
Proof: See Appendix C.
Remark 2.
Note that the partition of into and is very important since it considers a trade-off, which influences the size of the achievable region. To clarify this, we talk about a specific user in , and assume that all the other users are in for convenience. If , it is obvious from the achievability proof in Appendix C that should be included in such that its confidential information can be perfectly protected by the open and introduced ‘garbage’ messages. Differently, if , there are two cases for , i.e., and . We show that both these two cases have advantages and disadvantages in determining the corresponding achievable regions. For clarity, we only give some brief explanations in this remark. The more detailed analysis is provide in Appendix G.
In the first case with , and . We ensure
| (15) |
such that the information leakage rate vanishes, i.e.,
| (16) |
In the second case with , and . We ensure
| (17) |
such that
| (18) |
Note that (15) considers the combination of all users, while (17) does not take user into account. Hence, it is not possible for Eve to decode the open message in the first case, but is possible in the second case. This explains why we consider tighter lower bounds (with as a known condition) in (17) and a stronger condition on the leakage rate in (18). As shown in (145), the tighter lower bounds in (17) cause tighter upper bounds to the rate sums in . This shows the advantage of case one and disadvantage of case two.
On the other hand, since (15) considers one more user , it includes more inequalities than (17). Specifically, (15) sets lower bounds to while (17) does not. Then, it is known from the Fourier-Motzkin procedure given in Appendix A and also shown in (140) that we get many more inequalities, i.e., more constraints on the sum rates, in region (with ) compared with . In this sense, case two performs better than case one. Therefore, when , there is a trade-off between cases and . Since Theorem 2 considers all possible partitions of , it improves the results of Lemma 2.
As done for Lemma 2, we also consider two special cases with and for Theorem 2. First, if , (14) becomes
| (19) |
which can be simplified as (21) since for any ,
| (20) |
We provide another achievable region for the DM MAC-WT channel with only confidential information in the following lemma and show that it improves the region given in Lemma 3.
Lemma 4.
Assume that and . For each given , any secrecy rate tuple satisfying
| (21) |
is achievable. Let denote the set of rate tuples satisfying (21). Then, the convex hull of the union of over all and is an achievable secrecy rate region of the DM MAC-WT channel with only secret messages.
It can be easily found by setting that the achievable region given in Lemma 3 is contained in that provided by Lemma 4. In this sense, Lemma 4 not only improves the result in Lemma 3, but also those in [13, 8], and [14]. We further show this by giving a specific example with two users in Appendix H.
On the other hand, if , for a given , (14) can be rewritten as
| (22) |
If , we have and . (22) in this case becomes
| (23) |
which over all possible distributions constructs the capacity region of a conventional MAC channel with users and no wiretapping. If , (22) can be divided into two parts
| (24a) | ||||
| (24b) | ||||
It is obvious that (24a) is equivalent to (23). However, due to (24b), for any , the open message rate region jointly defined by (24a) and (24b) is included in that defined by (23). Hence, when , instead of taking into account (22) for all , the region union of over all can be easily characterized by (23). In this sense, the open message rate region defined by (12) is improved.
Since this paper considers MAC-WT channels, we are especially concerned about the maximum achievable sum secrecy rate of the system. In addition, since all users have open messages intended for Bob, then, an interesting question is if all users encode their confidential messages at the maximum sum secrecy rate, what is the maximum sum rate at which they could encode their open messages. We give the answer in the following Theorem.
Theorem 3.
For the considered DM MAC-WT channel, with a particular input distribution , the maximum achievable sum secrecy rate is
| (25) |
Let denote the subset in which achieves (25) and . If and all users transmit their confidential messages at sum rate 111Here we assume since otherwise we have , i.e., the system reduces to a conventional MAC channel with only open messages., the maximum achievable sum rate at which users in could send their open messages is given by
| (26) |
Proof: See Appendix I.
Theorem 3 shows that the channel can support a non-trivial additional open sum rate even if the coding scheme is designed to maximize the sum secrecy rate.
IV Conclusions
In this paper, we studied the information-theoretic secrecy of MAC-WT channels where each user had both secret and open messages for the intended receiver. We provided new achievable regions that enlarge previously known results and gave the general proof for any number of users.
Appendix A Proof of Lemma 1
As stated in Remark 1, it is impossible to prove Lemma 1 by directly using the Fourier-Motzkin procedure to eliminate all in (8), not only because of its huge complexity but also due to the fact that the elimination strategy works only if is given. Hence, we adopt mathematical induction in the following to prove Lemma 1.
We first consider the base case with . By eliminating in (8) using the Fourier-Motzkin procedure [37, Appendix D], it can be easily proven that (7) is the projection of (8) onto the hyperplane . Lemma 1 can thus be proven for this simple case.
Next, we consider the induction step. Assume that for any given positive integer , (7) is the projection of (8) onto the hyperplane . Then, by this assumption, it is possible to obtain (7) by eliminating the variables using the Fourier-Motzkin procedure. For convenience, in the following we refer to this assumption as the induction assumption. Under the induction assumption, we shall prove that the statement of Lemma 1 holds for users. With users, (7) and (8) become
| (27) |
and
| (28) |
We need to show that (27) is the projection of (28) onto the hyperplane , i.e., (27) can be obtained by eliminating as well as in (28). For this purpose, by separating user from users in set , we rewrite (27) equivalently as
| (29a) | |||
| (29b) | |||
| (29c) | |||
and (28) as
| (30a) | |||
| (30b) | |||
| (30c) | |||
| (30d) | |||
| (30e) | |||
| (30f) | |||
| (30g) | |||
| (30h) | |||
Note that in (30d) and (30e) we let since otherwise they will reduce to (30g) and (30h), which do not contain . In the following, we eliminate first and then in (30).
A-A Elimination of
To eliminate in (30), we focus on (30a) (30e) since only these inequalities contain while (30f) (30h) do not. Since there are different , as stated above, it is impractical to eliminate one by one. Hence, instead of eliminating directly from (30a) (30e), we divide these inequalities into categories, which together consider all possible upper and lower bound pairs on , and eliminate in each category using the induction assumption.
A-A1 Category
A-A2 Category
In this category we include inequalities (30a), (30d), and (30c), and rewrite them as
| (33) |
Note that though we let in (30d), (33) still has a similar expression as (8). It can be easily checked that if , the second inequality of (8) gives , which can be omitted. Hence, we may also let in (8) without changing its formulation. The induction assumption can thus be used to eliminate in (33) and obtain
| (34) |
which contains and thus has to be considered in the next step of eliminating .
A-A3 Category
A-A4 Category
A-B Elimination of
From (30g) and (A-A2), we get the following upper bounds on
| (39a) | ||||
| (39b) | ||||
Moreover, the following lower bounds on can be obtained from (30f), (30h), and (A-A4)
| (40a) | ||||
| (40b) | ||||
| (40c) | ||||
Comparing these upper and lower bounds, we can eliminate .
Firstly, we compare (39) with (40a), and get
| (41a) | |||
| (41b) | |||
Obviously, inequalities (41a) and (41b) can be integrated into one formula as follows
| (42) |
which is the same as (29b).
Secondly, we compare (39) with (40b), and get
| (43a) | |||
| (43b) | |||
By considering different , i.e., and , we may divide (43b) into two formulas as below
| (44a) | |||
| (44b) | |||
From (A-A3), (43a), and (44a), it can be found that these inequalities can be integrated into one formula as follows
| (45) |
which is the same as (29c). Combining (32), (42), and (45), it is known that (29) or (27) has already been obtained. All the other inequalities resulted from the elimination procedure should be redundant if Lemma 1 is true. Hence, we have to prove that (44b) is redundant. Since is independent of , (A-A3) can be rewritten and relaxed as follows
| (46) |
where the second inequality is the upper bound in (44b). Since (A-A3) has been included in (45), (44b) is thus redundant.
Finally, we compare (39) with (40c), which results in
| (47a) | |||
| (47b) | |||
Note that when comparing (39b) with (40c), which gives (47b), we replace notations and in (39b) with and , respectively, to avoid ambiguity. As stated after after (45), (47a) and (47b) should be redundant if Lemma 1 is true. We prove the redundancy in the following.
We first prove that (47a) is redundant. Since are independent of each other and , we have
| (48) |
By replacing the corresponding terms in (A-B) with (A-B), the redundancy of (47a) can be similarly proven as that of (44b). Since the redundancy proof of (47b) is not as easy as that of (44b) or (47a), for the sake of clarity, we give the proof in the following separate subsection.
A-C Redundancy Proof of (47b)
To prove that (47b) is redundant, we first rewrite its left-hand side term as follows
| (49) |
which is divided into two parts, i.e., Term and Term . In the following, we exchange the secret message rates and open message rates in Term and Term , and obtain Term as well as Term . When performing this operation, the following criteria have to be met.
-
•
Criterion . Term contains as many secret message rates as possible;
-
•
Criterion . Term contains as many open message rates as possible;
-
•
Criterion . Criterion has a higher priority than Criterion ;
-
•
Criterion . For any , there could be only one or in Term or Term ;
-
•
Criterion . For any , if is not in Term or Term , cannot be in this term.
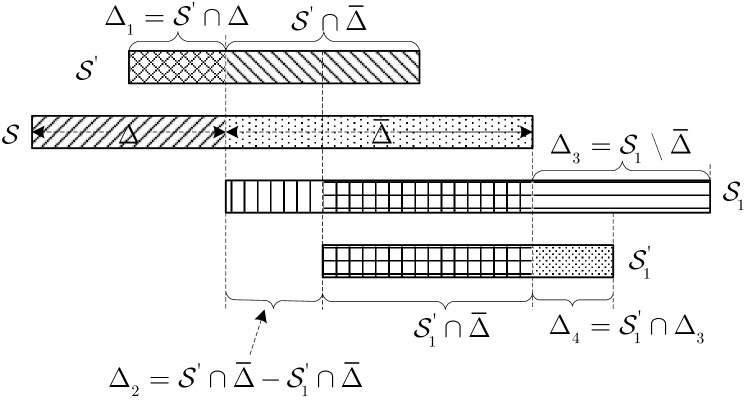
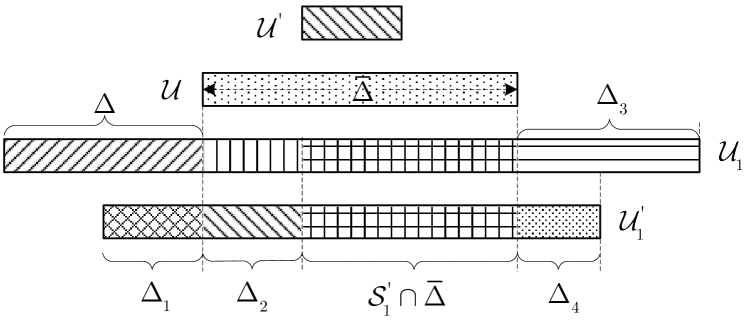
For ease of understanding, we give an example system with , , , , and . In this case, (49) takes on form
| (50) |
Since is not included in Term , according to Criterion and Criterion , should be moved into Term . Note that has also to be moved into Term since otherwise Criterion is violated. Since both Term and Term contain , while only Term contains , according to Criterion , should be moved into Term . Note that we may not move the in Term into Term since otherwise Criterion is violated, and may not move into Term since otherwise Criterion is violated. With these operations, (50) becomes
| (51) |
In the following, we describe these operations mathematically and prove the redundancy of (47b). For convenience, we give an example of sets , , , , and their divisions in Fig. 3. Let denote the set of user indexes which are in both and , and denote the set of indexes which are in but not in , i.e.,
| (52) |
Let denote the intersection of and , and denote the set of user indexes which are in but not in , i.e.,
| (53) |
With the operations described above, let , , , and , which respectively correspond to , , , and in (49), denote the user indexes in Term and Term . Then, according to Criterion ,
| (54) |
The complementary sets of and are
| (55) |
Moreover, according to Criterion , Criterion , and Criterion , we have
| (56) |
Fig. 3 depicts the sets , , , obtained from , , , in Fig. 3. We thus have
| (57) |
where the inequality results from (32) and (45). On the other hand, based on the definitions of , , and , and the chain rule of mutual information, (47b) can be rewritten as follows
| (58) |
In the following, we show that the upper bound in (A-C) is no larger and is thus tighter than that in (A-C). Then, (A-C) is redundant. Neglecting the common terms and in (A-C) and (A-C), we prove
| (59) |
and
| (60) |
From the definitions of and in (A-C), it is known that and . Hence,
| (61) |
Moreover, since ,
| (62) |
Based on (61) and (62), we have
| (63) |
Using the chain rule of mutual information, (63), and the fact that are independent of each other, we have
| (64) |
The inequation (59) is thus true. On the other hand, since , , and , as shown in Fig. 3, can be divided into two disjoint parts as follows
| (65) |
where we used the definition of in (A-C). Hence,
| (66) |
Let denote the set of user indexes which are in but not in , and denote the intersection of and , i.e.,
| (67) |
It can then be similarly proven as (66) that
| (68) |
which can also be found from Fig. 3. From (66), (68), and the definition of in (A-C), in (65) can be further divided into three disjoint parts as follows
| (69) |
where the last step holds since . Accordingly, we have
| (70) |
Then, using the chain rule of mutual information, (70), and the fact that are independent of each other, we have
| (71) |
i.e., (60) is true. Combining (A-C), (A-C), (A-C), and (A-C), it is known that (47b) is redundant.
Appendix B Proof of Theorem 1
Since has subsets, we may divide the inequality system (6) into subsystems with each one corresponding to a subset . For any , the inequality subsystem is
| (72) |
It is obvious that eliminating in (6) is equivalent to eliminating in (72) for all . Due to the assumption made in Theorem 1, for a given , we have
| (73) |
Then, by replacing in (8) with and with , we can eliminate in (72) based on Lemma 1 and get
| (74) |
Combining the inequalities (74) for all , (5) can be obtained, and Theorem 1 is thus proven.
Appendix C Proof of Theorem 2
We start the proof from a special case with , i.e., . In this case, (14) becomes
| (75) |
indicating that the region is included in the capacity region of a conventional MAC channel with no wiretapping, the achievability proof of which is well known.
Next, we show that for any , i.e., , there exists a code such that any rate tuple inside region is achievable. This, together with the standard time-sharing over coding strategies, suffices to prove the theorem. Without loss of generality (w.l.o.g.), we always assume
| (76) |
since otherwise users in cannot communicate with Bob. Moreover, for convenience, we assume
| (77) |
If (77) is not satisfied, we show later that Theorem 2 could be proven by simply modifying the following proof steps. Since are independent of each other, using the chain rule and non-negativity of mutual information, it is known that
| (78) |
Hence, (77) can be simplified as
| (79) |
With (79), Theorem 1 can be applied for the achievability proof in the following.
C-A Proof of Theorem 2 When Assumption (77) is True
If assumption (77) or (79) is true, the rate tuples inside region satisfy
| (80) |
where is an arbitrarily small positive number. Using Theorem 1, it is known that for any rate tuple satisfying (80), there exist such that
| (81) |
and can be found by applying Dantzig’s simplex algorithm [39].
In (81), we introduce a ‘garbage’ message to each user in to interfere with the decoding of Eve, i.e., besides the secret and open messages, each user also has to transmit a ‘garbage’ message at rate though it is not necessary for Bob. The rate of ‘garbage’ messages satisfies (81), which is the key point for proving Theorem 2. In particular, the second inequation of (81) ensures that the messages (even after adding ‘garbage’ messages) of all users can be perfectly decoded at Bob. With the third inequation in (81), on one hand, Eve obviously cannot decode the messages (including all secret, open, and garbage messages) of users in using the normal MAC decoding scheme. On the other hand, we show that Eve cannot extract any confidential information.
In the following, we prove Theorem 2 by first providing a random coding scheme, and then showing that (II-A) can be satisfied, i.e., all users can communicate with Bob with arbitrarily small probability of error, while the confidential information leaked to Eve tends to zero.
C-A1 Coding Scheme
For a given rate tuple inside region , choose satisfying (81). Assume w.l.o.g. that , , , and , are integers. Denote
| (82) |
Then, a coding scheme is provided below.
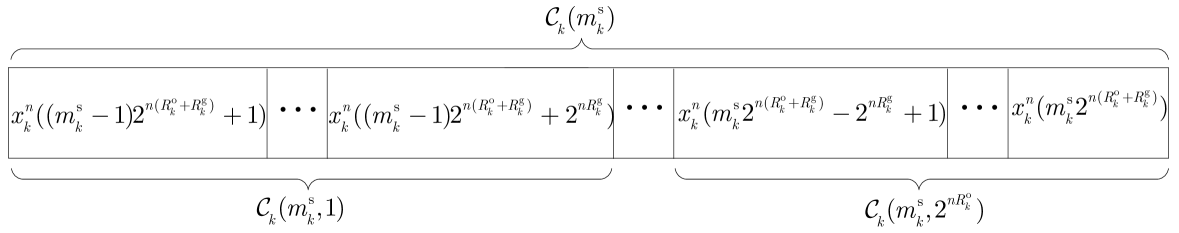
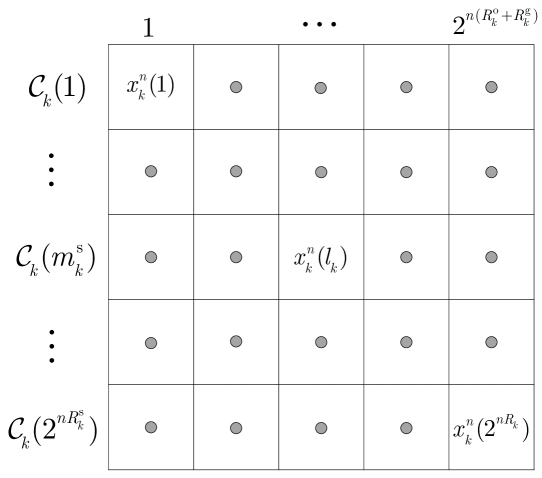
Codebook generation. For each message pair of user , generate a sub-subcodebook by randomly and independently generating sequences , each according to . For a given secret message , the sub-subcodebooks for all open messages constitute subcodebook , i.e., . Fig. 4 gives an example of subcodebook . Then, as shown in Fig. 5, these subcodebooks constitute the codebook of user , i.e., . For each user in , we apply the random coding scheme used in the conventional MAC channel with no wiretapping. In particular, generate its codebook by randomly and independently generating sequences , each according to . The codebooks of all users are then revealed to all transmitters and receivers, including Eve.
Encoding. To send message pair , encoder uniformly chooses a codeword (with index ) from and then transmits . To send message , encoder transmits .
Decoding. The decoder at Bob uses joint typicality decoding to find an estimate of the messages and declares that is sent if it is the unique message tuple such that , for some such that .
C-A2 Analysis of the Probability of Error
Since
| (83) |
it can be proven by using the law of large numbers (LLN) and the packing lemma that the probability of error averaged over the random codebook and encoding tends to zero as . The proof follows exactly the same steps used in [37, Subsection 4.5.1]. Hence, .
C-A3 Analysis of the Information Leakage Rate
Based on the coding scheme provided above, it is known that for a given codebook of user , the secret message is a function of the codeword index . As for user , its open message is the index of its codeword . Note that the messages of all users are independent. Hence, we have
| (84) |
To measure the information leakage rate, we separately evaluate entropies and . First, can be transformed to
| (85) |
where holds since the messages and encoding of different users are independent and for any , is the index of the codeword , holds since forms a Markov chain, and follows since . Then, we provide an upper bound to in the following theorem.
Lemma 5.
Using the coding scheme provided above, we have the following inequation
| (86) |
Proof: See Appendix D.
C-B Proof of Theorem 2 When Assumption (77) is not True
If (77) is not true, i.e., there exist , , , , and such that
| (88) |
From (C), it is known that (88) ensures
| (89) |
With (89), there exist two possible cases, i.e.,
| (90) |
and
| (91) |
In the following, we prove that Theorem 2 is true when either (90) or (91) holds.
In the first case, i.e., when (90) holds, we have . (14) thus becomes
| (92) |
By always letting in (92), we get
| (93) |
Since (93) considers only partial inequalities in (92), the region defined by (92) is included in that defined by (93). Moreover, (93) also shows that due to (90), the region is included in the capacity region of a conventional MAC channel with no wiretapping and its achievability proof is well known and is thus omitted here.
In the second case, i.e., when (91) holds, due to (89), there must exist at least one subset such that
| (94) |
and
| (95) |
The inequalities (94) and (95) indicate that is the largest set in which includes all users in and ensures (94). Adding any other users in to results in (95). Note that if there are multiple subsets in making (94) and (95) hold, we let be any of them. Let
| (96) |
Then, we give the following lemma.
Lemma 6.
Proof: See Appendix F.
Based on Lemma 6 it is known that if a rate tuple is inside region and has (94) and (95) met, it is also inside region and thus satisfies
| (99) |
Moreover, thanks to (97), for any rate tuple inside , Theorem 1 and Dantzig’s simplex algorithm can be applied to get such that
| (100) |
The techniques provided in the previous Subsection C-A can then be applied to prove the achievability of the rate tuple. The proof in this and the previous subsections, together with the standard time-sharing over coding strategies, suffices to prove Theorem 2.
Appendix D Proof of Lemma 5
For given -th order product distribution on , recall the definition of conditional -typical sets
| (101) |
Before proving Lemma 5, we first define some auxiliary functions. For given codeword set and received signal at the eavesdropper, assume that they are jointly typical, i.e., , and define functions
| (102) |
and
| (103) |
Obviously, records all possible index sets with each one ensuring that and are jointly typical, and denotes the number of these index sets. By introducing an indicator variable
| (104) |
where , can also be represented as
| (105) |
Using the above definitions, we give in the following theorem upper bounds to the expectation and variance of .
Theorem 4.
For any , the expectation and variance of can be bounded as
| (106) | ||||
| (107) |
where
| (108) |
Proof: See Appendix E.
Define event
| (109) |
We have
| (110) |
where step follows by applying the Chebyshev inequality, and follows by (107). Due to (81), we have . Then, it is obvious that as . For any , define indicator variable
| (111) |
Then, as .
Since there are codewords in each subcodebook , we have
| (112) |
and
| (113) |
Moreover, based on the definitions of and in (103) and (111),
| (114) |
where the last step holds since when , . Then, a tighter upper bound on (in contrast to (D)) can be obtained as
| (115) |
where (a) follows from using (D), (b) holds due to the fact that conditioning reduces entropy and , (c) follows from using (D) and (D), and
| (116) |
Note that by the LLN, as . Hence, as . In addition, since as , as . in (c) of (D) can thus be arbitrarily small as , making the last step of (D) hold. Hence,
| (117) |
Lemma 5 is thus proven.
Appendix E Proof of Theorem 4
Using the conditional typicality lemma, for sufficiently large , we have
| (118) |
Denote
| (119) |
Since are independent, can be upper bounded by
| (120) |
For the special case, if , (E) becomes
| (121) |
Then, using defined in (104), we have
| (122) |
and
| (123) |
where the last step follows from (E) and using (E) as well as (121) to get
| (124) |
| (125) |
Theorem 4 is thus proven.
Appendix F Proof of Lemma 6
We first prove (97). Using the definitions of and given in (C-B) and the chain rule of mutual information, the inequality (95) can be rewritten as
| (126) |
Due to (94), it is clear from (F) that
| (127) |
based on which we get
| (128) |
(F) shows that (97) is true when . If , (97) becomes
| (129) |
which is also true due to assumption (76). Combining (F) and (129), we get (97).
Next, we show that for any rate tuple in region defined by Theorem 2, if (94) and (95) can be satisfied, it is also in region .
If is in region and satisfies (94), we have
| (130) |
To prove that this rate tuple is also in region , we need to further verify the upper bounds on for all possible set choices given in (98). To that end, we separately prove
| (131) |
and
| (132) |
Note that in (F) and (F) belongs to different sets. To avoid ambiguity, instead of using , we use its definition directly in (F) and (F).
We first prove (F). Using (130), the left-hand side term of (F) can be rewritten as
| (133) |
where holds since is in region and thus satisfies (14), follows from using (94), is true since and , and holds due to the fact that are independent of each other. (F) is thus proven.
Next we prove (F). If and , can be divided into two disjoint subsets, and , with and . As defined in (94), . Hence, . Since the rate tuple is in region and thus satisfies (14). By setting , , and in (14), and using (130), we have
| (134) |
Then,
| (135) |
where the first inequality follows from using (F) and (134). Note that here we use in (F) instead of . (F) is thus proven. Combining (130), (F), and (F), it is known that satisfies (98) and is thus also in . Lemma 6 is then proven.
Appendix G
In this appendix, we consider a specific user in and show that if , there is a trade-off in terms of the resulted achievable regions between cases and . For convenience, assume that all the other users are in .
In the first case with , and . For convenience, assume
| (136) |
which guarantees
| (137) |
Then, it is known from Lemma 1 that for any rate tuple satisfying
| (138) |
there exist such that
| (139) |
As shown in Theorem 2, (138) actually constructs the achievable region (with ). Note that due to , which considers the combination of all users, including user , Eve cannot decode the open message . Hence, in the achievability proof of (138), we use metric and hope it vanishes as .
In (138), there are three cases on whether belongs to and or not, i.e., 1) , 2) and , 3) and . Note that here we mean and in (138), which may be different from those in somewhere else, e.g., those in (140). By considering these cases separately, the inequalities in (138) can be divided into three parts as follows
| (140a) | |||
| (140b) | |||
| (140c) | |||
(140a) and (140c) show that for each choice of and , there are two bounds on . We show in the following that compared with the case, sets looser but more upper bounds to the rates.
Now we consider the second case with . In this case, and . Again for convenience, assume
| (141) |
which guarantees
| (142) |
It is known from Theorem 1 that for any rate tuple satisfying
| (143) |
there exist such that
| (144) |
It is obvious from Theorem 2 that (143) constructs the achievable region . Different from the first case, (144) ensures , which does not take user into account. It is thus possible for Eve to decode . Hence, is treated as a known information in (143) and (144), and the worse metric ( in contrast to ) has to be used for the achievability proof of (143).
In (143), there are two cases on whether is in or not, i.e., 1) , 2) . Considering these cases separately, the inequalities in (143) can be divided into two classes as follows
| (145a) | |||
| (145b) | |||
By comparing (145a) with (140a) it can be found that they set upper bounds to the same rate sums, but due to the known information , (145a) gives tighter bounds in contrast to (140a). Similar observations can also be made by comparing (145b) with (140b). In this sense, adding to shrinks the achievable region. However, as we can also see, by including user in , (140) gives many more upper bounds on the rate sums than (145), i.e., (140c), which is obviously a disadvantage in determining the achievable region.
In conclusion, when , there is a trade-off between and in determining the achievable regions. To get a better region, all possible cases have to be taken into account.
Appendix H
In this appendix, we consider a special case with and , and show that the achievable secrecy rate region provided in Lemma 3 is part of that provided in Lemma 4.
For a given joint distribution , assume that , for convenience. When , the inequation systems (11) and (21) can be written in detail as
| (149) |
which constructs regions and . When is or , (21) can be rewritten as
| (152) |
and
| (155) |
which respectively construct regions and . The region over all is then .
If
| (156) |
it is obvious that the regions and are included in . Hence, as shown by Fig. 7,
| (157) |
If
| (158) |
it can be seen from Fig. 7 that there exit points in and which are not included in . Hence,
| (159) |
It can be similarly proven that (159) still holds, if the value of is between those of and . Note that the achievable regions provided by Lemma 3 and Lemma 4 are respectively the unions of and over all . Hence, the achievable region provided by Lemma 3 is contained in that provided by Lemma 4. In this sense, Lemma 4 not only improves the result of Lemma 3, but also that of [13, Theorem ] and [8, Theorem ].
Appendix I Proof of Theorem 3
If , for a given , (14) becomes (21), which can be divided into
| (160) |
and
| (161) |
As stated in Lemma 4, (160) and (161) jointly define an achievable secrecy rate region , and (161) shows that for any secrecy rate tuple in this region, the sum rate is no larger than . We now show that this upper bound is achievable. To that end, we only need to prove that the inequality (161) is not redundant, i.e., any linear combination of inequalities in (160) does not generate (161) or a tighter upper bound to . In [1, Appendix E], we have provided the proof for the case with . When , we could complete the proof by following similar steps. We omit the details here for brevity. Note that for a given , we have . Hence, the achievable upper bound on given by (160) and (161) is . Then, considering all possible , the maximum achievable sum secrecy rate is
| (162) |
Let denote the subset in which achieves (162) and assume
| (163) |
since otherwise we have , i.e., the system reduces to a conventional MAC channel with only open messages. Before proving the second part of Theorem 3, i.e., (26), we first show that with defined above, we have
| (164) |
(164) can be proven by reductio ad absurdum. If (164) is not true, then there exist subsets in such that the corresponding inequalities in (164) do not hold. W.l.o.g., we assume that there exists only one subset in such that
| (165) |
Using the chain rule of mutual information and the fact that are independent of each other, the left-hand side term of (163) is upper bounded by
| (166) |
where the last step holds due to (165). Then, and result in a larger value in (162) than , i.e., can be increased. This is contradicted to the assumption that achieves (162). When there are more subsets in such that the inequalities in (164) do not hold, we may prove by following similar steps that can be further increased. As a result, if achieves (162) and (163) is true, we have (164).
Now we show that if users in transmit their confidential messages at sum rate , the maximum achievable sum rate at which users in could send their open messages is given by (26). We divide the users in into two classes, i.e., and , and consider their maximum sum open message rate separately below.
First, if is a rate tuple in region defined by Theorem 2 and , which is assumed to be positive, by setting , , and in (14), we get
| (167) |
indicating that the sum rate at which users in can encode their open messages is no larger than . Then, we prove that this rate is achievable. Since the rate tuple is in region , with inequalities (163) and (164), we could use Theorem 1 and find such that
| (168) |
It is obvious from (168) that if , we can always split partial rate in to , and get as well as , such that
| (169) |
and
| (170) |
With (I), it can be easily verified that rate tuple is in the region defined by (168). Since the region can be obtained by projecting (168) onto hyperplane , then, according to the characteristics of Fourier-Motzkin elimination [37, Appendix D], we know that rate tuple is in region . Due to (170), with this rate tuple, users in could send their open messages at sum rate .
On the other hand, from the perspective of Bob, we are considering a MAC channel with users. Then, it is known from [37] that with a particular input distribution , an achievable sum rate users in could send their open messages is , which could be achieved by letting Bob jointly decode these users’ messages first (before decoding the messages of users in ). Hence, the maximum achievable sum rate at which users in could send their open messages is no less than . In addition, if , no matter users in transmit open messages or not, the coding scheme provided in Appendix C shows that a ‘garbage’ message at rate has to be introduced to each user , and
| (171) |
has to be guaranteed. Considering that the maximum achievable sum rate of the MAC link (between all users and Bob) is , we have
| (172) |
Therefore, the maximum sum open message rate of users in is .
References
- [1] H. Xu, T. Yang, K.-K. Wong, and G. Caire, “Achievable regions and precoder designs for the multiple access wiretap channels with confidential and open messages,” IEEE J. Sel. Areas Commun., vol. 40, no. 5, pp. 1407–1427, May 2022.
- [2] N. Yang, L. Wang, G. Geraci, M. Elkashlan, J. Yuan, and M. Di Renzo, “Safeguarding 5G wireless communication networks using physical layer security,” IEEE Commun. Mag., vol. 53, no. 4, pp. 20–27, Apr. 2015.
- [3] X. Chen, D. W. K. Ng, W. H. Gerstacker, and H.-H. Chen, “A survey on multiple-antenna techniques for physical layer security,” IEEE Commun. Surveys Tuts., vol. 19, no. 2, pp. 1027–1053, 2nd Quart., 2017.
- [4] C. E. Shannon, “Communication theory of secrecy systems,” Bell Sys. Tech. J., vol. 28, no. 4, pp. 656–715, Oct. 1949.
- [5] A. D. Wyner, “The wire-tap channel,” Bell Sys. Tech. J., vol. 54, no. 8, pp. 1355–1387, Oct. 1975.
- [6] S. Leung-Yan-Cheong and M. Hellman, “The gaussian wire-tap channel,” IEEE Trans. Inf. Theory, vol. 24, no. 4, pp. 451–456, July 1978.
- [7] I. Csiszár and J. Körner, “Broadcast channels with confidential messages,” IEEE Trans. Inf. Theory, vol. 24, no. 3, pp. 339–348, May 1978.
- [8] E. Ekrem and S. Ulukus, “On the secrecy of multiple access wiretap channel,” in Proc. 46th Allerton Conf. Commun., Contr., Comput., Illinois, USA, Sep. 2008, pp. 1014–1021.
- [9] R. Liu, I. Maric, R. D. Yates, and P. Spasojevic, “The discrete memoryless multiple access channel with confidential messages,” in Proc. IEEE Int. Symp. Inf. Theory (ISIT), Seattle, WA, USA, July 2006, pp. 957–961.
- [10] Y. Liang and H. V. Poor, “Multiple-access channels with confidential messages,” IEEE Trans. Inf. Theory, vol. 54, no. 3, pp. 976–1002, Mar. 2008.
- [11] R. Liu, Y. Liang, and H. V. Poor, “Fading cognitive multiple-access channels with confidential messages,” IEEE Trans. Inf. Theory, vol. 57, no. 8, pp. 4992–5005, Aug. 2011.
- [12] M. Nafea and A. Yener, “Generalizing multiple access wiretap and wiretap II channel models: Achievable rates and cost of strong secrecy,” IEEE Trans. Inf. Theory, vol. 65, no. 8, pp. 5125–5143, Aug. 2019.
- [13] E. Tekin and A. Yener, “The gaussian multiple access wire-tap channel,” IEEE Trans. Inf. Theory, vol. 54, no. 12, pp. 5747–5755, Dec. 2008.
- [14] ——, “The general gaussian multiple-access and two-way wiretap channels: Achievable rates and cooperative jamming,” IEEE Trans. Inf. Theory, vol. 54, no. 6, pp. 2735–2751, June 2008.
- [15] H. Xu, G. Caire, and C. Pan, “An achievable region for the multiple access wiretap channels with confidential and open messages,” in Proc. IEEE Int. Symp. Inf. Theory (ISIT), Los Angeles, CA, USA, Jun. 2020, pp. 949–954.
- [16] E. Ekrem and S. Ulukus, “The secrecy capacity region of the gaussian MIMO multi-receiver wiretap channel,” IEEE Trans. Inf. Theory, vol. 57, no. 4, pp. 2083–2114, Apr. 2011.
- [17] R. Liu, T. Liu, H. V. Poor, and S. Shamai, “Multiple-input multiple-output gaussian broadcast channels with confidential messages,” IEEE Trans. Inf. Theory, vol. 56, no. 9, pp. 4215–4227, Sep. 2010.
- [18] H. D. Ly, T. Liu, and Y. Liang, “Multiple-input multiple-output gaussian broadcast channels with common and confidential messages,” IEEE Trans. Inf. Theory, vol. 56, no. 11, pp. 5477–5487, Nov. 2010.
- [19] S. A. A. Fakoorian and A. L. Swindlehurst, “On the optimality of linear precoding for secrecy in the MIMO broadcast channel,” IEEE J. Sel. Areas Commun., vol. 31, no. 9, pp. 1701–1713, Sep. 2013.
- [20] X. Yu, D. Xu, Y. Sun, D. W. K. Ng, and R. Schober, “Robust and secure wireless communications via intelligent reflecting surfaces,” IEEE J. Sel. Areas Commun., vol. 38, no. 11, pp. 2637–2652, Nov. 2020.
- [21] R. Liu, I. Maric, P. Spasojevic, and R. D. Yates, “Discrete memoryless interference and broadcast channels with confidential messages: Secrecy rate regions,” IEEE Trans. Inf. Theory, vol. 54, no. 6, pp. 2493–2507, May 2008.
- [22] O. O. Koyluoglu, H. El Gamal, L. Lai, and H. V. Poor, “On the secure degrees of freedom in the -user gaussian interference channel,” in Proc. IEEE Int. Symp. Inf. Theory (ISIT), Toronto, ON, Canada, July 2008, pp. 384–388.
- [23] X. Tang, R. Liu, P. Spasojević, and H. V. Poor, “Interference assisted secret communication,” IEEE Trans. Inf. Theory, vol. 57, no. 5, pp. 3153–3167, May 2011.
- [24] O. O. Koyluoglu and H. El Gamal, “Cooperative encoding for secrecy in interference channels,” IEEE Trans. Inf. Theory, vol. 57, no. 9, pp. 5682–5694, Sep. 2011.
- [25] A. Kalantari, S. Maleki, G. Zheng, S. Chatzinotas, and B. Ottersten, “Joint power control in wiretap interference channels,” IEEE Trans. Wireless Commun., vol. 14, no. 7, pp. 3810–3823, July 2015.
- [26] D. Park, “Weighted sum rate maximization of MIMO broadcast and interference channels with confidential messages,” IEEE Trans. Wireless Commun., vol. 15, no. 3, pp. 1742–1753, Mar. 2016.
- [27] Y. Oohama, “Coding for relay channels with confidential messages,” in Proc. IEEE Inf. Theory Workshop (ITW), Cairns, QLD, Australia, Sep. 2001, pp. 87–89.
- [28] L. Lai and H. El Gamal, “The relay-eavesdropper channel: Cooperation for secrecy,” IEEE Trans. Inf. Theory, vol. 54, no. 9, pp. 4005–4019, Sep. 2008.
- [29] L. Dong, Z. Han, A. P. Petropulu, and H. V. Poor, “Improving wireless physical layer security via cooperating relays,” IEEE Trans. Sig. Process., vol. 58, no. 3, pp. 1875–1888, Mar. 2010.
- [30] Y. Zou, X. Wang, and W. Shen, “Optimal relay selection for physical-layer security in cooperative wireless networks,” IEEE J. Sel. Areas Commun., vol. 31, no. 10, pp. 2099–2111, Oct. 2013.
- [31] B. Dai and Z. Ma, “Multiple-access relay wiretap channel,” IEEE Trans. Inf. Forensics Security, vol. 10, no. 9, pp. 1835–1849, May 2015.
- [32] X. Chen, C. Zhong, C. Yuen, and H.-H. Chen, “Multi-antenna relay aided wireless physical layer security,” IEEE Commun. Mag., vol. 53, no. 12, pp. 40–46, Dec. 2015.
- [33] C. Liu, N. Yang, R. Malaney, and J. Yuan, “Artificial-noise-aided transmission in multi-antenna relay wiretap channels with spatially random eavesdroppers,” IEEE Trans. Wireless Commun., vol. 15, no. 11, pp. 7444–7456, Nov. 2016.
- [34] H. Xu, C. Pan, W. Xu, M. Chen, and W. Heng, “Improving wireless physical layer security via D2D communication,” in Proc. IEEE GLOBECOM, Abu Dhabi, UAE, Dec. 2018, pp. 1–7.
- [35] H. Xu, G. Caire, W. Xu, and M. Chen, “Weighted sum secrecy rate maximization for D2D underlaid cellular networks,” IEEE Trans. Commun., vol. 68, no. 1, pp. 349–362, Jan. 2020.
- [36] H. Lee, C. Song, J. Moon, and I. Lee, “Precoder designs for MIMO gaussian multiple access wiretap channels,” IEEE Trans. Veh. Tech., vol. 66, no. 9, pp. 8563–8568, Sep. 2017.
- [37] A. El Gamal and Y.-H. Kim, Network information theory. Cambridge University Press, 2011.
- [38] H. Xu, K.-K. Wong, and G. Caire, “A note on fourier-motzkin elimination with three eliminating variables,” ReaearchGate, DOI: 10.13140/RG.2.2.11816.65288, pp. 1–26, Jul. 2022.
- [39] S. I. Gass, Linear programming: methods and applications. Courier Corporation, 2003.
- [40] Y. Sun, P. Babu, and D. P. Palomar, “Majorization-minimization algorithms in signal processing, communications, and machine learning,” IEEE Trans. Sig. Process., vol. 65, no. 3, pp. 794–816, Feb. 2017.
- [41] Y. Jeon, S.-H. Park, C. Song, J. Moon, S. Maeng, and I. Lee, “Joint designs of fronthaul compression and precoding for full-duplex cloud radio access networks,” IEEE Wireless Commun. Lett., vol. 5, no. 6, pp. 632–635, Dec. 2016.
- [42] P. Parada and R. Blahut, “Secrecy capacity of SIMO and slow fading channels,” in Proc. IEEE Int. Symp. Inf. Theory (ISIT), Adelaide, SA, Australia, Sep. 2005, pp. 2152–2155.
- [43] A. Khisti and G. W. Wornell, “Secure transmission with multiple antennas I: the MISOME wiretap channel,” IEEE Trans. Inf. Theory, vol. 56, no. 7, pp. 3088–3104, July 2010.
- [44] S. Shafiee, N. Liu, and S. Ulukus, “Towards the secrecy capacity of the gaussian MIMO wiretap channel: The 2-2-1 channel,” IEEE Trans. Inf. Theory, vol. 55, no. 9, pp. 4033–4039, Sep. 2009.
- [45] M. Vaezi, W. Shin, and H. V. Poor, “Optimal beamforming for Gaussian MIMO wiretap channels with two transmit antennas,” IEEE Trans. Wireless Commun., vol. 16, no. 10, pp. 6726–6735, Oct. 2017.
- [46] M. Vaezi, W. Shin, H. V. Poor, and J. Lee, “MIMO Gaussian wiretap channels with two transmit antennas: Optimal precoding and power allocation,” in Proc. IEEE Int. Symp. Inf. Theory (ISIT), Aachen, Germany, June 2017, pp. 1708–1712.
- [47] A. Khisti and G. W. Wornell, “Secure transmission with multiple antennas-Part II: The MIMOME wiretap channel,” IEEE Trans. Inf. Theory, vol. 56, no. 11, pp. 5515–5532, Nov. 2010.
- [48] S. A. A. Fakoorian and A. L. Swindlehurst, “Optimal power allocation for gsvd-based beamforming in the mimo gaussian wiretap channel,” in Proc. IEEE Int. Symp. Inf. Theory (ISIT), Cambridge, MA, USA, July, 2012, pp. 2321–2325.
- [49] X. Zhang, Y. Qi, and M. Vaezi, “A rotation-based method for precoding in Gaussian MIMOME channels,” IEEE Trans. Commun., vol. 69, no. 2, pp. 1189–1200, Feb. 2021.
- [50] Y.-H. Au-Yeung, “A note on some theorems on simultaneous diagonalization of two hermitian matrices,” in Mathematical Proceedings of the Cambridge Philosophical Society, vol. 70, no. 3. Cambridge University Press, 1971, pp. 383–386.
- [51] S. Boyd and L. Vandenberghe, Convex Optimization. Cambridge University Press, 2004.
- [52] R. Hunger, Floating Point Operations in Matrix-vector Calculus. Munich University of Technology, Inst. for Circuit Theory and Signal Processing, 2005.
- [53] E. U. T. R. Access, “Further advancements for E-UTRA physical layer aspects,” 3GPP TR 36.814, Tech. Rep., 2010.