Minimizing Instability in Strategy-Proof Matching Mechanism Using A Linear Programming Approach
Abstract
In this paper we address the design of matching mechanisms that are strategy-proof and simultaneously as stable as possible. Building on the impossibility result by Roth [1982] for one-to-one matching problems, we formulate an optimization problem that maximizes stability under the constraint of strategy-proofness. In our model the objective is to minimize the degree of instability measured as the sum (or worst-case maximum) of stability violations over all preference profiles. We further introduce the socially important properties of anonymity and symmetry into the formulation.
Our computational results show that, for small markets, our optimization approach leads to mechanisms with substantially lower stability violations than RSD. In particular, the optimal mechanism under our formulation exhibits roughly one-third the stability violation of RSD.
For deterministic mechanisms in the three-agent case, we also find that any strategy-proof mechanism hvae at least two blocking pairs at the worst case, and we propose an algorithm that attains this lower bound. Finally, we discuss extensions to larger markets and present simulation evidence that our mechanism yields a reduction of approximately blocking pairs on average compared to SD mechanism.
1 Introduction
Matching theory is a central research area in economics, computer science, and mathematics with numerous real-world applications, such as kidney exchange and residency matching. In particular, the one-to-one matching problem (exemplified by the marriage problem) has received extensive attention. Gale and Shapley [1962] demonstrated that a stable matching always exists in one-to-one matching markets and that the deferred acceptance (DA) algorithm (which is strategy-proof for one side) produces a stable matching. On the other hand, Roth [1982] established an impossibility result showing that no mechanism can simultaneously guarantee stability and strategy-proofness for both sides.
While there is a growing literature on strategy-proof mechanisms, the design of matching mechanisms that achieve the highest possible stability subject to strategy-proofness has not been thoroughly explored. Moreover, aside from SD, little is known about the design of two-sided strategy-proof matching mechanisms.
In this study, we search for the most stable matching mechanism among those that are strategy-proof by formulating an optimization problem that is solved computationally. Strategy-proofness is a critical property: mechanisms that are not strategy-proof may incentivize agents to misreport their preferences, thereby generating inefficient matchings and perceptions of unfairness. Our main contributions are twofold. First, we propose a mechanism for small matching markets that, while satisfying strategy-proofness, substantially reduces instability. Second, we provide a deterministic mechanism for the general case that always yields no more blocking pairs than SD.
Our optimization approach can be applied to many small-market problems, offering a novel perspective on impossibility theorems.
2 Related Work
The one-to-one matching problem was first formalized by Gale and Shapley [1962], who showed the existence of a stable matching. Roth [1982] later demonstrated the impossibility of achieving both stability and two-sided strategy-proofness.
Among prominent matching algorithms, the deferred acceptance algorithm is known to produce stable matchings but is not strategy-proof for both sides. AbdulkadiroÄlu and Sönmez [2003] introduced the top trading cycle (TTC) algorithm for school choice, which is Pareto efficient but not strategy-proof for both-sides. The Boston mechanism, discussed by Kumano [2013], is neither stable nor fully strategy-proof, although it may be strategy-proof and stable under strong non-cyclic preferences—a condition often deemed unrealistic.
Other studies have modeled stable matchings as solutions to linear programming formulations [Roth et al. [1993]] and characterized them as vertices of a polytope. Recent work by Ravindranath et al. [2021] considered the trade-off between stability violations and deviations from strategy-proofness using a neural network approach. However, minimizing a loss function by neural network methods does not yield mechanisms that are exactly strategy-proof or optimally stable. In contrast, our work formulates the design problem as a linear program that explicitly minimizes stability violations under strategy-proofness constraints.
3 Preliminaries
Let denote the set of students and the set of schools. Let be the set of all linear orders on , and let be the set of all linear orders on . Each student has a strict preference over and each school has a strict preference over . We denote the profile of student preferences by , the profile of school preferences by , and the entire preference profile by . The set of all possible preference profiles is denoted by . For any agent , we denote by the preferences of all agents except .
A randomized matching is given by a matrix
satisfying:
-
(i)
for all and ;
-
(ii)
for all ;
-
(iii)
for all .
We denote the set of all randomized matchings by . When for every the entry is either 0 or 1, we say that is deterministic.
By the Birkhoff-von Neumann theorem [Birkhoff, 1946, Von Neumann, 1953], every randomized matching can be represented as a convex combination of deterministic matchings.
A function
is called a randomized matching mechanism. If always returns a deterministic matching, we call it a deterministic matching mechanism.
3.1 Stability
A randomized matching is said to be ex-ante stable if there does not exist a pair such that student prefers school to some school that he is matched with positive probability and school prefers student to some student who is matched with positive probability. In other words, no pair exists such that
We refer to such a pair as a blocking pair.
A randomized matching is said to be ex-post stable if it can be decomposed into stable deterministic matchings. Moreover, is fractionally stable if for every it holds that
| (1) |
For deterministic matchings, ex-ante stability and ex-post stability coincide, and we simply say that is stable. In fact, it is known that ex-post stability and fractional stability are equivalent for randomized matchings (see, e.g., Aziz and Klaus [2019]).
A deterministic matching mechanism is called stable if for every , the matching is stable. Similarly, a randomized matching mechanism is said to be fractionally stable if satisfies (1) for every .
For a given randomized matching , we define the stability violation for a pair as
| (2) |
and the stability violation for a matching as
| (3) |
In the deterministic case, this coincide with the number of blocking pairs.
3.2 Strategy-Proofness
A randomized matching mechanism is said to be strategy-proof if for every student , for every preference profile , for every alternative preference , and for every school with , it holds that
| (4) |
An analogous condition is imposed when the roles of students and schools are interchanged.
3.3 Anonymity
Let and be a permutation of students and permutation of schools respectively. Denote by and the sets of all permutations. Given a school preference and a permutation , define as the preference order obtained by renaming according to ; similarly, define for student preferences.
For example, if , and , then writing yields . (Here, the permutation indicates that the name of student is replaced by , student by , and student by .)
We denote by the profile obtained by applying to each school’s preference.
A randomized matching mechanism is said to be anonymous if for every , for every , , and for every , , letting
we have
| (5) |
That is, permuting the names of agents does not affect the outcome.
3.4 Symmetry
When the number of students equals the number of schools (i.e., ), we say that a randomized matching mechanism is symmetric if for every the following holds. For each student , let be the profile obtained from by interchanging the roles of students and schools: whenever, in , student prefers school to school , in school prefers student to student (and similarly when swapping the roles). Then for every , we require that
| (6) |
This property ensures that the mechanism treats both sides of the market equally.
3.5 Nonwastefullness
A randomized matching mechanism is said to be nonwasteful if for every and for every pair satisfying and , it holds that either
3.6 Individual Rationality
A randomized matching mechanism is called individually rational if for every and every , whenever , it follows that and .
4 The Optimization Problem for Matching Problems
In the following, we assume that every agent strictly prefers being matched with someone rather than remaining unmatched; that is, we assume
Our objective is to design a strategy-proof matching mechanism that maximizes stability. We define the ”most stable” mechanism as the one that minimizes the average (or worst-case) stability violation as measured by (3). Hence, we consider the following optimization problem:
{equationarray}llr
gminimize & ∑≻∈P ∑(s,c)∈S×C
max{ 1 - g(≻)(s, c) - ∑c’ ∈C : c’ ≻sc g(≻)(s, c’)
- ∑s’ ∈S : s’ ≻cs g(≻)(s’, c), 0 }
subject to
0 ≤g(≻)(s, c) ≤1
∀≻∈P, ∀s ∈S, ∀c ∈C
∑s ∈S g(≻)(s, c) ≤1
∀≻∈P, ∀c ∈C
∑c ∈C g(≻)(s, c) ≤1
∀≻∈P, ∀s ∈S
∑c’ ∈C : c’ ⪰sc g(≻)(s, c’) ≥∑c’ ∈C : c’ ⪰sc
g(≻’s, ≻-s)(s, c’)
∀≻∈P, ∀≻’s ∈PS, ∀c ∈C
∑s’ ∈S : s’ ⪰cs g(≻)(s’, c) ≥∑s’ ∈S : s’ ⪰cs g(≻’c, ≻-c)(s’, c) ∀≻∈P, ∀≻’c ∈PC, ∀s ∈S Constraints (4)(4) ensure that is a valid matching mechanism, while (4) and (4) impose strategy-proofness. (If one replaces (4) by , the mechanism is forced to be deterministic.) Since the feasible region is compact and the objective is linear (after suitable linearization of the maximum function), an optimal solution exists.
In this formulation the objective function represents the average stability violation (denoted by objective function ). Alternatively, one may change the objective to minimize
| (7) |
which corresponds to minimizing the worst-case stability violation (denoted by objective function ). In the latter case the mechanism is evaluated independently of the distribution over preference profiles.
Directly solving this optimization problem is extremely time-consuming and leads to results that are complex and difficult to interpret, since the number of variables is as large as even in the case where . Therefore, to both accelerate the computation and facilitate interpretation, we now present two theorems.
The following two theorems show that, without loss of optimality, one may restrict attention to mechanisms that are anonymous and (when ) symmetric.
Theorem 1.
Any value of the objective function that is achievable by a strategy-proof randomized matching mechanism is also achievable by a strategy-proof and anonymous randomized matching mechanism. This holds for both objective functions and .
Proof.
Let be given. Define to be the set of all outcomes resulting from every possible permutation, that is,
Then, for any , we have that if and only if . Moreover, if does not belong to then
Thus, there exist profiles such that for any with , we have
and
Let be a strategy-proof probabilistic matching mechanism. We now define a mechanism as follows: For every , every , and every , let
| (8) |
In other words, returns the average matching probability over all permutations of the agents. We now show that is a strategy-proof and anonymous probabilistic matching mechanism that achieves the same objective value as .
(Anonymity) Let be given. Then there exists a unique such that
Similarly, for any , there exists a unique satisfying
For such and , we have
An analogous property holds when the roles of and are interchanged. Therefore, for any and , there exists a unique pair such that
Thus, for any , we have
(Strategy-Proofness) Let be an alternative preference for student , and denote by . Since is strategy-proof, for every and every we have
Since this inequality remains valid under any permutation of the agents, it follows that for any ,
Since , it follows that for every , every , and every , we have
A similar argument holds when interchanging the roles of and .
(Achievablity) We now show that the objective function value achievable by (with respect to objective function ) is also achievable by . First, observe that
Thus,
Moreover, for every , there is exactly one pair such that
Therefore,
Hence,
Next, we show that the worst-case value of the objective function achievable by is also achievable by . That is,
∎
Theorem 2.
Suppose that . Then any objective value achievable by a strategy-proof randomized matching mechanism is also achievable by a strategy-proof and symmetric randomized matching mechanism. This holds for both objective functions and .
Proof.
Let be given. Define a new preference profile as follows. For each student and for any two schools , if in student prefers school to school , then in we define that school prefers student to student . (A similar definition is applied when interchanging the roles of students and schools.)
Let be a strategy-proof probabilistic matching mechanism. For any and for any , define the mechanism by
| (9) |
That is, outputs the average matching probability over the two assignments given by and by , where in the latter the roles of students and schools are interchanged. We now show that is both strategy-proof and symmetric, and that it attains the same objective function value as .
(Symmetry)
We verify that satisfies symmetry. Observe that
Thus, is symmetric.
(Strategy-Proofness)
Suppose that under the true preference profile student submits a false preference , and let denote the resulting profile. Next, define in an analogous manner as follows: in , for each student , if student prefers school to school , then in we define that school prefers student to student (and the same rule applies when interchanging the roles of students and schools). Then, under if school receives the false preference , the resulting profile coincides with . Consequently, we have
Thus, is strategy-proof.
(Achievablity)
We now show that the objective function value (with respect to both objective functions and ) achieved by is also achievable by .
First, consider objective function . We have
The last equality follows from the fact that corresponds one-to-one with . Hence, the objective function value of is achievable by .
Next, we show that the worst-case objective function value corresponding to objective function that is achievable by is also achievable by . In particular, we have
Thus, the worst-case objective function value (i.e., the value of objective function ) achieved by is also achievable by . ∎
After taking a strategy-proof probabilistic matching mechanism and rendering it anonymous using the method described in the proof of Theorem 1, and subsequently making it symmetric according to the procedure in the proof of Theorem 2, the resulting mechanism is a convex combination of anonymous mechanisms. Hence, its anonymity is easily shown. Thus, by6 Theorems 1 and 2 we can restrict our search to anonymous and symmetric mechanisms (when ) without loss of optimality. This not only reduces computational time and memory requirements but also improves interpretability. In the subsequent optimization we include anonymity and symmetry as constraints.
5 Results
In the following we report computational results for the cases and .
5.1 The Case
When there are two students and two schools, we find that there exists a deterministic matching mechanism that is both strategy-proof and stable.
That is, Algorithm 1 matches mutually top-preferred pairs if they exist; otherwise, it assigns the best available school to student 1 and matches the remaining pair. In fact, for , Algorithm 1 produces the same outcome as the student-proposing DA algorithm.
Lemma 1.
Algorithm 1 is strategy-proof and stable.
Proof.
First, note that if an agent is matched to his second-choice partner, misreporting his preferences cannot yield a match with his top choice. In Algorithm 1, if agent is matched with his second-choice, then either the top-choice pair exists (in which case misreporting is futile) or the top-choice is already assigned to another agent. Hence, truthful reporting is a dominant strategy.
Stability follows directly from the fact that mutually top-preferred pairs are always matched. ∎
5.2 The Case
5.2.1 Deterministic Matching Mechanisms
When restricting attention to deterministic mechanisms, our computational search shows that a strategy-proof, non-wasteful, and anonymous deterministic matching mechanism does not exist when .
Result 1.
For , there is no deterministic matching mechanism that is simultaneously strategy-proof, non-wasteful, and anonymous.
Results 1 shows that if one demands strategy-proofness for deterministic mechanisms, then one must sacrifice anonymity, which is socially undesirable.
Result 2.
For , no deterministic matching mechanism that is strategy-proof can achieve a worst-case stability violation (objective function ) of at most .
In other words, every strategy-proof deterministic mechanism must have at least two blocking pairs in the worst case. The following Algorithm 2 is strategy-proof and achieves a worst-case violation of , thereby being optimal among deterministic mechanisms.
Lemma 2.
Algorithm 2 is strategy-proof, non-wasteful, and the number of blocking pairs at the worst-case is .
Proof.
The strategy-proofness is verified by noting that student 1 is always assigned his top choice, and for the remaining two students, the procedure reduces to Algorithm 1, which is strategy-proof. Non-wastefulness is immediate by construction.
Regarding stability, observe that student 1, being matched with his top choice, cannot form any blocking pair. Moreover, in the remaining assignment, only the pair involving the school chosen by student 1 may possibly form a blocking pair, and at most two such blocking pairs can occur. ∎
It is worth noting that while Algorithm 2 limits the number of blocking pairs to two, SD may yield up to four blocking pairs in the worst case. Moreover, Algorithm 2 extends naturally to cases where (see Section 5.3). In our numerical comparison (see Table 1), Algorithm 2 consistently outperforms SD.
5.2.2 Randomized Matching Mechanisms
We also solve the optimization problem for randomized matching mechanisms under four settings: using objective function or , and with or without the non-wastefulness constraint. We compare the results with RSDs (RSD) as well as a symmetrized version of Algorithm 2 (denoted by Algorithm 2’). Here RSD is implemented in two variants: (1) by assigning random orderings to both students and schools (denoted RSD1) and (2) by assigning an ordering to one side only (denoted RSD2). Both RSD1 and RSD2 satisfy strategy-proofness, non-wastefulness, anonymity, and symmetry. Table 2 reports the average stability violation, worst-case stability violation, and average waste (computed as ) for the various mechanisms.
| Mechanism | Average STV | Worst-case STV | Average Waste |
|---|---|---|---|
| RSD1 (full ordering) | 0.6478 | 1.3333 | 0.0000 |
| RSD2 (one-side ordering) | 0.6229 | 1.3333 | 0.0000 |
| Obj. , no waste constraint | 0.2286 | 0.6224 | 0.0249 |
| Obj. , with waste constraint | 0.2348 | 0.6455 | 0.0000 |
| Obj. , no waste constraint | 0.4218 | 0.5000 | 0.0505 |
| Obj. , with waste constraint | 0.3730 | 0.5000 | 0.0000 |
| Algorithm 2’ | 0.4063 | 1.6666 | 0.0000 |
5.3 Generalization to
Algorithm 2 may be extended to the general case by employing the following procedure.
When the same ordering is used, the number of blocking pairs in the matching produced by Algorithm 3 is no larger than that in SD. This is because in Algorithm 3 the final four agents and those previously matched do not form blocking pairs, whereas under sequential dictatorship blocking pairs may arise. However, when one symmetrizes the mechanism (to enforce anonymity and symmetry) SD may sometimes yield lower stability violations, as evidenced by Table 2.
5.4 Simulation
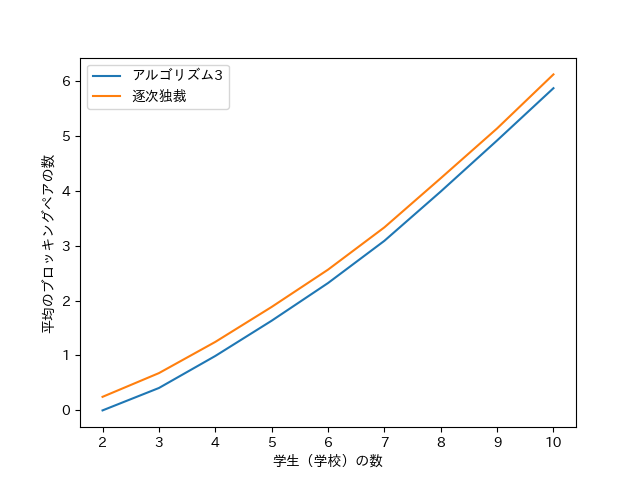
We conducted simulations to evaluate the performance of Algorithm 3 and SD as the number of agents increases. For each between 2 and 10, 1000 random preference profiles were generated and the average stability violation (computed as in (3)) was recorded.
In our implementation both Algorithm 3 and SD used the natural ordering of students 1, 2, , . Figure 2 shows that for all values of , Algorithm 3 produces approximately fewer blocking pairs on average than SD. (In each instance the difference is either or , with a probability of for a difference of .)
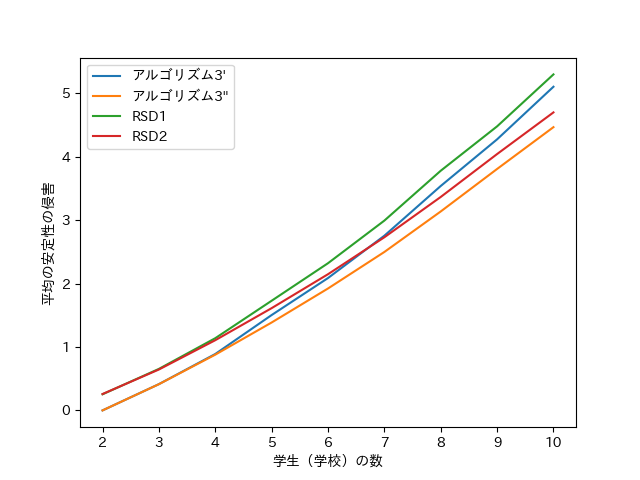
We further compared anonymized and symmetric randomized matching mechanisms. Two methods of symmetrization were considered: (1) assigning a random ordering independently to students and schools, and (2) assigning a random ordering to the union . Denote by Algorithm 3’ the version of Algorithm 3 symmetrized by (1) and by Algorithm 3” the version symmetrized by (2). Similarly, denote by RSD1 and RSD2 the corresponding variants of RSD. Figure 2 displays the simulation results. In both cases the (2) method produces lower average stability violation, and for every Algorithm 3 yields approximately less stability violation on average compared to SD.
6 Conclusion
In this paper we formulated the problem of designing a strategy-proof matching mechanism as an optimization problem, where the goal is to maximize stability (minimize the degree of stability violation) subject to strategy-proofness constraints. By incorporating anonymity and symmetry into our formulation, we are able to reduce the computational complexity and improve interpretability without loss of optimality.
For the case , we presented a deterministic algorithm that is both strategy-proof and stable. In the case , we demonstrated by computational means that no deterministic mechanism can guarantee fewer than two blocking pairs under strategy-proofness, and we proposed an optimal deterministic mechanism accordingly. For randomized matching mechanisms we provided computational evidence that mechanisms exist which reduce both the average and worst-case stability violations by roughly one-third compared to RSD. We also extended our approach to larger markets via a generalization of our algorithm and confirmed by simulation that our method consistently yields fewer blocking pairs.
The optimization techniques developed in this work are applicable to a wide range of small-scale matching problems (for instance, many-to-one matchings with capacity constraints or the roommates problem) and offer a new perspective on circumventing impossibility results by focusing on optimality in small markets.
Acknowledgements
I would like to express my sincere gratitude to Professor Michihiro Kandori for his continuous guidance and advice throughout this research. I am also very grateful to Professor Fuhito Kojima for his thoughtful suggestions that greatly contributed to the progress of this work. My thanks also go to Professors Hitoshi Matsushima and Satoru Takahashi for the many academic insights they shared during seminars and small-group discussions. Finally, I wish to thank all my colleagues and friends for their warm support and invaluable feedback, with special thanks to Keita Kuwahara and Kento Hashimoto.
References
- AbdulkadiroÄlu and Sönmez [2003] Atila AbdulkadiroÄlu and Tayfun Sönmez. School choice: A mechanism design approach. Am. Econ. Rev., 93(3):729–747, May 2003.
- Abdulkadiroglu and Sonmez [1998] Atila Abdulkadiroglu and Tayfun Sonmez. Random serial dictatorship and the core from random endowments in house allocation problems. Econometrica, 66(3):689, May 1998.
- Ashlagi and Gonczarowski [2018] Itai Ashlagi and Yannai A Gonczarowski. Stable matching mechanisms are not obviously strategy-proof. J. Econ. Theory, 177:405–425, September 2018.
- Aziz and Klaus [2019] Haris Aziz and Bettina Klaus. Random matching under priorities: stability and no envy concepts. Social Choice and Welfare, 53(2):213–259, 2019.
- Bade and Root [2023] Sophie Bade and Joseph Root. Royal processions: Incentives, efficiency and fairness in two-sided matching. arXiv [econ.TH], January 2023.
- Birkhoff [1946] Garrett Birkhoff. Three observations on linear algebra. Univ. Nac. Tacuman, Rev. Ser. A, 5:147–151, 1946.
- Gale and Shapley [1962] D Gale and L S Shapley. College admissions and the stability of marriage. Am. Math. Mon., 69(1):9, January 1962.
- Gale and Shapley [2014] David Gale and Lloyd S Shapley. College admissions and the stability of marriage. In Mircea Pitici, editor, The Best Writing on Mathematics 2014, pages 299–307. Princeton University Press, Princeton, December 2014.
- Kumano [2013] Taro Kumano. Strategy-proofness and stability of the boston mechanism: An almost impossibility result. J. Public Econ., 105:23–29, September 2013.
- Li [2019] S Li. Deep learning for two-sided matching markets. 2019.
- Ravindranath et al. [2021] Sai Srivatsa Ravindranath, Zhe Feng, Shira Li, Jonathan Ma, Scott D Kominers, and David C Parkes. Deep learning for two-sided matching. arXiv [cs.GT], July 2021.
- Roth [1982] Alvin E Roth. The economics of matching: Stability and incentives. Math. Oper. Res., 7(4):617–628, November 1982.
- Roth et al. [1993] Alvin E Roth, Uriel G Rothblum, and John H Vande Vate. Stable matchings, optimal assignments, and linear programming. Math. Oper. Res., 18(4):803–828, November 1993.
- Von Neumann [1953] John Von Neumann. A certain zero-sum two-person game equivalent to the optimal assignment problem. Contributions to the Theory of Games, 2(0):5–12, 1953.