Novel Outage-Aware NOMA Protocol for Secrecy Fairness Maximization Among Untrusted Users
Abstract
Observing the significance of spectrally-efficient secure non-orthogonal multiple access (NOMA), this paper proposes a novel quality of service (QoS) aware secure NOMA protocol that maximizes secrecy fairness among untrusted users. Considering a base station (BS) and two users, a novel decoding order is designed that provides security to both users. With the objective of ensuring secrecy fairness between users, while satisfying their QoS requirements under BS transmit power budget constraint, we explore the problem of minimizing the maximum secrecy outage probability (SOP). Closed-form expression of pair outage probability (POP) and optimal power allocation (PA) minimizing POP are obtained. To analyze secrecy performance, analytical expressions of SOP for both users are derived, and individual SOP minimization problems are solved using concept of generalized-convexity. High signal-to-noise ratio approximation of SOP and asymptotically optimized solution minimizing this approximation is also found. Furthermore, global-optimal solution from secrecy fairness standpoint is obtained at low computational complexity, and tight approximation is derived to get analytical insights. Numerical results present useful insights on globally optimized PA which ensure secrecy fairness and provide performance gain of about , , and , respectively, compared to fixed PA and individual users’ optimal PAs. Finally, a tradeoff between secrecy fairness performance and QoS demands is presented.
Index Terms 5G communications, non-orthogonal multiple access, physical layer security, power allocation, optimization.
I Introduction
Exponentially increasing network traffic, imposed by internet-enabled applications, poses severe challenges of supporting massive connections loaded with high data rate demands for upcoming fifth generation (5G) communication networks. Non-orthogonal multiple access (NOMA) has been recognized as a potential breakthrough because of the possibility of accommodating a number of users within the same subcarrier allocation [2]. This exhibits a significant spectral efficiency enhancement compared to traditional orthogonal multiple access techniques. But, the broadcast nature of communication at the transmitter makes NOMA vulnerable to the eavesdropping. Therefore, research on security issues in NOMA networks is of great significance. The amalgamation of NOMA and physical layer security (PLS) has been observed as a promising solution to provide spectrally-efficient secure wireless communication [3]. Despite merits, the design process has secrecy challenge of wiretapping in the presence of untrusted NOMA users.
I-A Related Art
To address the demand for massive connections, modern wireless networks strive for better spectral efficiency. Motivated by the potential of NOMA in providing spectrally-efficient networks, survey papers [2], [4] have summarized recent research contributions in power-domain NOMA. Besides, the broadcast nature of wireless transmission leads to security issues on the information-carrying signal. Triggered by these security concerns, researchers have considered the PLS technique which was first recommended by Wyner [5] as a complement to cryptographic approaches. To highlight the capabilities of PLS, [6] has provided the latest survey of PLS research on diverse 5G technologies, such as multiple input multiple output, full-duplex, and millimeter wave.
Even though a great amount of research has been done in NOMA and PLS independently, researchers have recently focused attention on using PLS as a security measure in NOMA. An investigation of PLS in large-scale networks by invoking stochastic geometry has been done in [3], where a base station (BS) communicates with randomly distributed NOMA users and eavesdroppers. The authors have proposed a protected zone around BS to maintain an eavesdropper free zone. Secure NOMA transmission for multiple users against eavesdropper in single-input single-output network has been studied in [7], where the authors have derived a closed-form expression of optimal power allocation (PA) that maximizes sum secure rate of NOMA users. In [8], the authors have investigated the optimal decoding order, individual transmission rates, and PA to each user to design secure NOMA system against external eavesdropper under secrecy outage constraint. The authors have proved that optimal decoding order for secure NOMA scheme against external eavesdropper is same as that for conventional NOMA. Secrecy of a cooperative NOMA system with a decode-and-forward and an amplify-and-forward relay against external eavesdropper has been analyzed in [9]. The authors in [10] have proposed a NOMA-inspired jamming and relaying scheme for enhancing the PLS of untrusted relay networks. In [11], the authors considered a multiple-input single-output NOMA cognitive relay radio network in the presence of multiple eavesdroppers and proposed an artificial noise (AN) aided cooperative jamming scheme for secure transmission in considered network.
It is noteworthy that the aforementioned works have focused on securing NOMA against external eavesdropper only. Besides external eavesdroppers, secure data transmission among NOMA users is much more challenging due to the underlying SIC based decoding at receivers. Actually, due to the sharing of same resource blocks among users in NOMA systems, users may not trust each other in real scenario, and hence at least some level of secrecy must be provided against internal eavesdropping. Based on the idea, assuming far users as untrusted, sum secrecy rate of trusted near users is investigated in [12] for a multiple-input single-output NOMA system. In [13] also, a NOMA system is considered where near user is assumed to be trusted, whereas far user as untrusted, and SOP of trusted user against untrusted user has been investigated. Note that in [12] and [13], it is assumed that the untrusted far user first decodes its own data and then can access the message of the trusted near user with the aid of the SIC technique.
I-B Research Gap and Motivation
Note that existing works [3], [7][11] have considered potential PLS techniques such as AN aided strategy [3], [11], optimal PA [7], [8], and cooperative relaying [9], [10] to enhance secrecy of NOMA transmission against external eavesdroppers assuming all NOMA users as trusted. Since NOMA users share same resource block and have access to decode the message of other paired user to perform SIC, there exists an inherent security issue in NOMA in the case of untrusted users. Therefore, at least some level of secrecy must be provided against internal eavesdropping. Note that the untrusted scenario is a hostile situation, where users have no mutual trust, and each user focuses on achieving secure communication from BS in the presence of other untrusted users, which leads to more complex and constrained resource allocations [14], [15]. It is noteworthy that the existing works [12] and [13] only considered the security problem of trusted near user in a NOMA system against untrusted far untrusted user. However, near user also decodes the data of far user, which causes a serious security risk for far user in the case of untrusted near user. Therefore, from security point of view, it is more desirable to design a secure NOMA system for worst-case scenario, where both near and far users are assumed to be untrusted. Thus, with the objective of designing a smart secure communication network, our work focuses on investigating whether secure communication is possible in NOMA in the presence of untrusted users.
In this direction, [16] considered symbol-level SIC (SLSIC) receiver where other user’s signal is demodulated but not decoded to perform SIC. In contrast, codeword-level SIC (CLSIC) receiver exists in literature [17], where other user’s signal is demodulated and decoded. Since channel decoding is conducted during signal detection in CLSIC receiver, the probability of successful recovery of other user’s signal increases in comparison to SLSIC, and hence, the impact of error propagation can be reduced drastically [17]. Nevertheless, securing all users’ data in an untrusted scenario from a decoding perspective, which is a better system design aspect, has not been considered yet in literature.
It also needs to noted that when both users are assumed to be untrusted in NOMA, one might think that if any of these users is capable of decoding other user’s signal then security and privacy of decoded users are compromised. But, decoding of users’ signals can even happen in orthogonal multiple access because of the broadcast nature of wireless channels [18]. Actually, we focus on achieving secure communication by utilizing the concept of PLS. According to the definition of PLS, information leakage of the legitimate user may occur only when data rate over the desired link is lesser than that of the potential eavesdropper’s link because the secrecy rate for a legitimate user is defined as the difference of the rates when a legitimate user decodes itself, and the rate that another user achieves while decoding data of legitimate user [5], [6]. Therefore, considering the definition of PLS into account for an untrusted NOMA system, our work is focused on designing such a secure NOMA transmission protocol that can be feasible in providing positive secrecy rate for all NOMA users.
Taking this challenge into account, a decoding order has been proposed for a two-user untrusted NOMA scenario in the preliminary version [1] of this work that is feasible in providing positive secrecy rate for both near and far NOMA users. As an extension of [1], in this work, we study all possible decoding orders for a two user NOMA system including conventional one and investigate the best decoding order under secrecy constraint for both users. Besides, in [1], we have considered ideal SIC receivers in which interference from the decoded user is completely removed while decoding the later user. Though better spectral efficiency can be achieved through perfect SIC, but it is not realistic due to various implementation issues such as decoding error and complexity scaling [4], [19]. Therefore, a practical scenario would be, when residual interference from the inaccurately decoded user is considered while decoding later user. To this end, we study secure NOMA to provide positive secrecy rates at all untrusted users with consideration of imperfect SIC based decoding which, to the best of our knowledge, is an open problem.
It should be emphasized that, with the vision of ensuring secure communication to all users, secrecy performance of the far user against the untrusted near user, and rather secrecy fairness between these users cannot be ignored. Fulfilling users’ quality of service (QoS) requirement is also an essential parameter for spectrally-efficient communication. Also, PA to users may play deciding role in obtaining optimal pair outage and secrecy outage performance of a system. Inspired by these solid observations, this paper focuses on investigating numerical and analytical global-optimal PA solutions for a secure NOMA system with untrusted users from a secrecy fairness maximization point of view while satisfying users’ QoS requirements.
I-C Key Contributions
The contributions of this work are summarized as follows:
-
•
Considering a NOMA system with one BS, two untrusted users and imperfect SIC model, a novel optimal decoding order is proposed that provides security to both users.
-
•
Pair outage probability (POP), as a QoS measure, has been derived analytically. Optimal PA minimizing POP has been obtained using generalized-convexity of POP.
-
•
Analytical expressions of SOPs have been derived for both users. SOP minimization problems have been solved using pseudoconvexity of SOP at both users and optimal PAs are obtained numerically. Asymptotic approximations of SOP, and optimal PA for both users are also derived to get analytical insights.
-
•
To maximize the secrecy fairness between users while satisfying users’ QoS demands, we formulate the problem of minimizing the maximum SOP between users under the POP and PA constraints. Global-optimal PA solution is obtained using a low complexity algorithm. Tight analytical approximation for optimal PA is also derived.
-
•
Extensive simulations are conducted that validate the accuracy of analysis, present insights on optimal performance, and evaluate performance gains by the proposed solution. Tradeoff between secrecy fairness performance of system and users’ QoS demands is also investigated.
I-D Organization
The system model, proposed NOMA protocol and investigation on optimal decoding order have been presented in Section II. In Section III, we provide analysis of pair outage performance of the proposed system and derive an optimal PA policy to minimize POP. In section IV, we present SOP analysis for both users, along with their closed-form asymptotic expressions, and also investigate their optimality. Analysis of optimal PA for secrecy fairness maximization between untrusted users under POP constraint is described in Section V. Performance evaluation of proposed analytical model via simulation results is discussed in Section VI, and Section VII presents concluding remarks and future directions.
II Secure NOMA Protocol for Untrusted Users
In this section, we first present the system model, which is followed by the NOMA transmission protocol. Then, an optimal decoding order to secure untrusted NOMA is investigated.
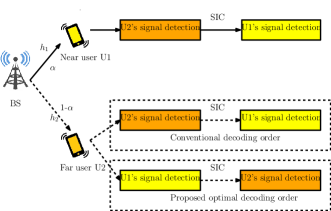
II-A System Model
We consider the downlink NOMA system with one BS and two untrusted users (Fig. 1). The near and far users are denoted as U and U, respectively. Our consideration for two-user model is motivated by two reasons: firstly, NOMA system is an interference limited system because co-channel interference is strong in NOMA due to sharing of same resource by multiple users [20], [21]; and secondly, the implementation complexity at transmitter and receiver sides increases with an increase in number of users because the users perform SIC to remove messages of other users before decoding their own messages [22]. Note that due to these reasons, asking all the users in the system to perform NOMA jointly is not preferable in practice [21] and therefore, the users can be divided into multiple groups, where NOMA is implemented within each group. The users are ordered according to their distance to BS. As a result, U and U are considered as strong and weak users, respectively [23], [24]. The Rayleigh fading channel gain coefficients from BS to U is denoted by for . Channels between BS and users are assumed to be independent and suffer both small scale fading and path loss effects, such that channel power gains follows exponential distribution with mean parameter . Here is path loss constant, is path loss exponent, and is the distance from BS to U. The channel power gains have been sorted such that [23], [24]. All three nodes are assumed to be equipped with a single antenna [13]. denotes total power transmitted by BS to users, and represents the PA coefficient denoting the fraction of allocated to U. Remaining is allocated to U.
II-B Proposed Secure NOMA Protocol
In NOMA, the message signals dedicated to the users are superimposed at the BS and then transmitted to the users. The signal transmitted by BS is [13] where and are unit power signals which contains the message required by U and U, respectively. The signals received by U and U, respectively, from BS are given as
| (1) |
| (2) |
where and denote zero mean additive white Gaussian noise with variance at U and U, respectively. / denotes BS transmit signal-to-noise ratio (SNR).
After obtaining received signals, two steps are followed at receivers in conventional decoding order: (1) far user decodes its own information signal first and after obtaining its own signal it may decode the information signal of the near user using SIC in case of the far user is an untrusted user [12], [13]; (2) near user first decodes the signal intended for far user to perform SIC, and then decodes its own message. As a result, near and far users both have access to the signals of far and near user, respectively, which is a critical issue in secure communication with untrusted users. Note that the SIC can be performed by all users in a system because SIC on the receivers’ side is actually a physical layer capability enabling the receiver to decode packets that arrive collectively. Thus, far user may also decode the information signal of near user using SIC which has been extensively studied in literature also [12], [13], [25], [26]. In this work, we consider imperfect SIC model, where decoding error may occur at both users, resulting in residual interference from the incompletely decoded user after SIC.
Since all users focus to safe their own data from others in untrusted scenario, next we investigate a decoding order that can provide security at both users. Even the conventional decoding order has also not yet been investigated in the literature to ensure positive secrecy for both users in an untrusted NOMA system. Hence, we discuss all possible decoding orders including conventional one to investigate the best decoding order under secrecy constraint.
II-C Optimal Decoding Order from Secrecy Perspective
In secure NOMA, U needs to be protected from U and, vice-versa. Decoding order identifies whether any user decodes its own data first or other user’s data. Note that both U and U are the multiplexed NOMA users which themselves are the part of the system. Now since BS decides the decoding order for both the users of the system, decoding order can also be changed [25]. Thus, for two users’ case, four decoding orders are possible. Let us denote the decoding order as , where and , respectively, denotes users, i.e., U and U (for ) whose data will be decoded first by U and U. For example, means U and U will decode other user’s data first, and then decode its own data. Specifically, the four possible cases are: (a) , (b) , (c) and (d) . Under secrecy considerations, the idea is to study whether it is possible to achieve positive secrecy rate at both users. In this regard, investigation of feasible decoding orders out of total possible decoding orders is presented by Theorem .
Theorem 1
Positive secrecy rate for both near and far users in untrusted NOMA can be obtained in decoding orders , , and .
Proof:
We consider each case of decoding orders one by one and investigate the feasibility under positive secrecy constraint. We first consider the conventional decoding order , where each user first decodes U’s data. Then, the proof continues with a consideration of remaining cases, i.e., , and . Adopting the imperfect SIC model, we use to denote the residual interference from the imperfectly decoded U when data of U is decoded by U.
Case 1: Considering conventional decoding order [13], U first decodes its own signal by considering other signal as noise. After decoding its own signal, it may decode the signal of near user using SIC. Then, U decodes signal associated to U, applies SIC, and then decode its own signal from the remaining signal. Let denote the received signal-to-interference-plus-noise-ratio at U when data of U is decoded by U. Various can be given as [13]
| (3) |
| (4) |
The achievable secrecy rate of U can be given as
| (5) |
where and are given by Shannon’s Theorem [27] as
| (6) |
Positive secrecy rate condition (5), simplified as (6) for U gives a condition , which shows that based on the values of , , , and , a feasible condition can be obtained. This proves that positive secrecy rate can be achievable at U. Similarly, the achievable secrecy rate of U is
| (7) |
where
| (8) |
Here the condition (7), simplified as (8) gives which is an infeasible condition because channel power gains are sorted as . Thus, positive secrecy rate cannot be achieved at U.
Since our goal is to provide positive secrecy rate to both users, the conventional decoding order cannot be considered for untrusted NOMA because it cannot provide positive secrecy rate for the far user against the untrusted near user. Therefore, next we study other possible decoding orders one by one and investigate the optimal decoding order.
Case 2: Next, we consider decoding order where both users first decode signals associated to other user, and then decode their own signal after performing SIC. In decoding order (2,1), the order of decoding is different only for the far user in comparison to conventional decoding order. Note that the far user can even first decode the signal of near user, and then decodes its own signal after applying SIC [25], [26]. As a result, we obtain
| (9) |
| (10) |
Positive secrecy rate condition , at U gives
| (11) |
Similarly, the feasibility condition for positive secrecy rate at U, gives
| (12) |
Observing (11) and (12), we note that decoding order can provide positive secrecy rate to both the users in untrusted NOMA, provided is constrained as .
Case 3: In decoding order , U and U first detect their own signals, apply SIC, and then decode signal of other user. Similar to the aforementioned analysis, we obtain . In this case, leads to , and provides which are feasible. Thus, is concluded as feasible decoding order in providing positive secrecy rate to both users under constraint .
Case 4: In decoding order, U first decodes its own signal, applies SIC and then decodes signal of other user, whereas U first decodes signal of other user, subtracts it via SIC and then decodes its own signal. As a result, . Here gives , and required for positive secrecy rate at U gives which is also feasible. Thus, also can also provide security to both the users, when obtained feasibility conditions are satisfied. ∎
Thus, it can be concluded from the aforementioned analysis that utilizing the concept of PLS, three decoding orders, i.e., , , , are feasible in providing positive secrecy rate for both near and far users, but with a suitable constraint on PA. Next, the investigation of optimal decoding order among these three feasible decoding orders is presented through Theorem .
Theorem 2
For untrusted NOMA scenario, the optimal decoding order among the feasible decoding orders is that gives the best secrecy rate in the system.
Proof:
See Appendix A. ∎
Remark 1
Note that the number of total possible decoding orders is enormous with more users due to which excessive computational complexity occurs in finding an optimal secure decoding order. Therefore, we have studied the system with two users, however, the investigation can be extended for more users easily.
III Pair Outage Performance of untrusted NOMA
In order to ensure users’ QoS demands for reliable communication over all the links, we first derive expression of POP for the optimal decoding order . Next, we obtain optimal PA to minimize POP by utilizing the concept of generalized-convexity.
III-A Pair Outage Probability Analysis
Each user in a network has a predefined QoS demand, i.e., each user desires the transmitter to send data with a minimum information rate guarantees. POP, denoted as , ensures minimum rate guarantee to each user. In other words, is defined as the probability that a pair outage happens, i.e., the achievable rate at each user falls below a pre-determined threshold rate. Assuming as the threshold rate for U and defining , can be given as
| (13) |
where denotes the probability measure. follows from the property of independent events [28]. Here , and . Note that and . and are cumulative distribution function (CDF) and complementary cumulative distribution function (CCDF), respectively, of channel power gain . Similarly, and are CDF and CCDF, respectively, of channel power gain .
Note that in (III-A) can be rewritten for two cases and . The first case , results in a constraint on as . Similarly, the constraint results in the second case . In addition, from the definition of CDF of exponential distribution, we observe that and which leads to and , respectively. Considering and , is given as
| (14) |
Similarly, can be obtained as follows
| (15) |
where , and . Using (III-A), (14), (15), the piecewise definition of as a function of is given at the top of next page in (16)
| (16) |
where
| (17) |
| (18) |
| (19) |
| (20) |
Remark 2
From the closed-form expression of in (16), it can be observed that depends on key system parameters such as threshold rates of users and SNR. It is noted that POP increases with an increase in threshold rates of users and decreases with an increase in the SNR.
III-B Pair Outage Probability Minimization
Observing as a function of , the pair outage optimization problem can be formulated as
| s.t. | (21) |
where indicates PA coefficient bounds.
Note that the closed-form piecewise expression of in (16) is a function of . Therefore, in order to obtain optimal PA solution, next we need to study each case of piecewise expression one by one and find candidate optimal points to obtain the global-optimal solution. The global-optimal solution is given by Lemma .
Lemma 1
The unique global-optimal PA solution is the feasible optimal point from the set of obtained optimal points that minimizes , which is given as
| (22) |
where , , , and are the candidate optimal points.
Proof:
In order to solve the optimization problem, closed-form piecewise expression of in (16) is considered. Each case is taken one by one to find the global-optimal solution.
Case 1 : In the first case, where and , first-order derivative obtained by differentiating with respect to is given as
| (23) |
where . Since , is a monotonically decreasing function of in this range. The optimal point is taken as the corner, given as .
Case 2 : For second case, where , the derivative is given as
| (24) |
where . Note that (III-B) does not indicate any monotonic behavior. However, we observe that is monotonically increasing function of if , and monotonically decreasing function otherwise. The point of inflection can be obtained by solving which can be simplified as a quadratic equation where and . Optimal solutions are the roots of the quadratic equation, given as
| (25) |
Case 3 : In the third case, where , the derivative is given as
| (26) |
which is always greater than zero. Thus, is a monotonically increasing function of . The optimal point, in this case, is given by the corner point of considered range as .
Case 4 : In fourth case, is a constant, i.e., , and it is the maximum feasible value.
From above analysis, we observe that and are two corner points due to monotonically decreasing and increasing property, respectively. and are roots as explained in Case . As a result, POP minimization problem has global-optimal solution , which is feasible optimal point from set {, , , } at which is minimum. ∎
IV Secrecy Outage Performance
To analyze secrecy performance, we derive expressions of SOP for both users and investigate optimal PAs for optimizing SOPs. Next, we provide closed-form asymptotic expressions of SOPs, and optimal PAs to gain analytical insights.
IV-A Secrecy Outage Probability Analysis
For each user, an outage event happens when the received secrecy rate is below a pre-determined threshold. Particularly, SOP is defined as the probability that the maximum achievable secrecy rate is less than a target secrecy rate. Next, we derive analytical expressions of SOPs for both near and far users which have been denoted by for U.
IV-A1 Near user
With and as achievable and target secrecy rate for U, is stated as
| (27) |
where , , and is probability density function (PDF) of channel power gain .
IV-A2 Far user
With and as achievable and target secrecy rate for U, is given as
| (28) |
where , , and denotes PDF of channel power gain .
IV-B Individual Secrecy Outage Probability Minimization
Next, we investigate optimality of SOPs of both the users.
IV-B1 Near User
Considering derived in (IV-A1) as a function of , SOP minimization problem for U can be formulated as
| s.t. | (29) |
Noting the complexity of derived expression of , next we solve SOP minimization problems using pseudoconvexity of SOP. The feasibility of unique solution is asserted by Lemma .
Lemma 2
is a pseudoconvex function of .
Proof:
in (IV-A1) can be rewritten as
| (30) |
Denoting the integrand of as , it can be defined as
| (31) |
Second-order derivative of the logarithm of the integrand function , with respect to is
| (32) |
which is non-increasing. This indicates that the integrand of the objective function is a logarithmically concave (log-concave) function. Since log-concavity is preserved under integration [29], we note that integral function in (30) is also log-concave function. Observing pseudoconcave property [30, Lemma 5] of log-concave function, we can state that integral function of (30) is pseudoconcave, and negative of a pseudoconcave function is a pseudoconvex function [31]. Hence, is a pseudoconvex function of . ∎
Due to pseudoconvexity of of U, there exists unique PA that minimizes [31, Chap. 3.5.9]. We apply a computationally efficient golden section search algorithm [32] to find (optimal value of ). The algorithm considers pseudoconvex function , and as input, where and , respectively, are the lower and upper bounds of at initial stage. It gives optimal solution and corresponding minimum SOP as the output. Since , we first consider and and then the algorithm searches along with acceptable tolerance level of . The algorithm works by reducing the search space with a fixed ratio of at the end of every iteration. Finally, the algorithm terminates after iterations if search length is less than the given tolerance [32].
IV-B2 Far User
SOP minimization problem for U, considering expression of (IV-A2) is stated as
| s.t. | (33) |
In Lemma , we prove the feasibility of unique solution.
Lemma 3
is a pseudoconvex function of .
Proof:
Similar to the proof of minimization problem, the pseudoconvexity of SOP for U can be proved. ∎
Here also, optimal PA solution of minimization problem can be evaluated numerically using golden section search algorithm. Now, the algorithm takes pseudoconvex function , , as input. It provides , and corresponding minimum SOP as optimal output.
IV-C Asymptotic SOP: Analysis and Optimization
Observing the complexity of derived expressions, and involved computations in optimizing SOPs, optimal PAs have been obtained numerically. In order to gain analytical insights, next we derive tight asymptotic expressions of SOPs and optimal PAs under high SNR scenario.
IV-C1 Near User
Asymptotic approximation of SOP for U, , can be obtained by setting in (30), which leads to . Thus, is given as
| (34) |
Considering (IV-C1), minimization problem is given as
| s.t. | (35) |
Asymptotic optimal PA for is given by Lemma .
Lemma 4
The optimal PA minimizing , is given as
| (36) |
Proof:
See Appendix B. ∎
IV-C2 Far User
Similarly, the asymptotic expression for U, using in (IV-A2), can be given as
| (37) |
The (IV-C2) minimization problem for U can be stated as
| s.t. | (38) |
Lemma 5
The unique PA minimizing is given as
| (39) |
Proof:
See Appendix C. ∎
Remark 3
It can be observed from the asymptotic approximations of SOPs, i.e., and , respectively, for U and U, that the SOPs for near user and far user depend on target secrecy rates and SNR. Note that SOP increases with an increase in target secrecy rate of the user and decreases with an increase in the SNR.
V Secrecy Fairness Maximization
In order to ensure secrecy rate guarantee to both the users while satisfying users’ QoS requirements, next we formulate secrecy fairness optimization problem and investigate optimal PA. Also, we present asymptotic approximation of optimal PA to get deeper insights.
V-A Problem Formulation
QoS demands of users, in the form of maximum allowable POP forces an upper bound on , i.e., . Hence, QoS constrained secrecy fairness maximization problem using (16), (IV-A1) and (IV-A2) that minimizes the maximum SOP between users under power budget and POP constraints can be formulated as
| (40) |
Using , an equivalent formulation of can be obtained as follows
| (41) |
where and appears from the definition of max.
Due to the presence of nonconvex constraints and , is a nonconvex problem. We solve it by analyzing candidate optimal points that are characterized by Karush-Kuhn-Tucker (KKT) conditions [33].
V-B Power Control for optimizing Min-Max Secrecy Outage
First, we solve min-max SOP optimization problem without consideration of users’ rate demands. Next, QoS demand is taken into account and optimal NOMA protocol is analyzed.
V-B1 Without Pair Outage Constraint
The secrecy fairness maximization problem without can be formulated as
| s.t. | (42) |
The global-optimal solution is given by Lemma .
Lemma 6
The global-optimal solution of the nonconvex problem , at which maximum SOP between users is minimized, is given as
| (43) |
where are, respectively, obtained by golden section search algorithm by minimizing (cf. Section IV-B), and solving .
Proof:
Keeping the boundary constraint implicit, and associating Lagrange multipliers with and with , the Lagrangian function can be stated as
| (44) |
The corresponding primal feasibility KKT conditions are given by the constraints and . Following (42) and (44), the dual feasibility conditions are given as and . The subgradient conditions are obtained as
| (45) |
The two complementary slackness conditions are given as
| (46) |
Note that there exists three cases. Case 1: and , implies which results in the same solution as SOP minimization problem (29) of U, i.e., . Case 2: and , implies , which results in the solution of SOP minimization (33) of U, i.e., . Case 3: and , implies using (46), which indicates equal SOP for both the users, and this case gives . Hence, has three optimal points, i.e., and for minimizing and , respectively, and is obtained from the condition of . Finally, the global-optimal solution to this problem is obtained at the optimal point for which maximum SOP between users is minimum. ∎
Thus, we conclude that since the secrecy fairness maximization problem is nonconvex due to the presence of nonconvex constraints, we have successfully obtained all possible optimal points of this problem by KKT conditions which are the candidates for the global-optimal solution [33]. Lastly, the optimal point for which maximum SOP between users is minimum is considered as the global-optimal solution.
V-B2 With Pair Outage Constraint
Now we solve problem by taking QoS requirements into account. In this case, the global-optimal solution from secrecy perspective must satisfy the constraint . Theoretically , but due to , acceptable range of gets limited, as obtained in Lemma .
Lemma 7
The lower and upper bound on , required to achieve maximum allowable POP, are given as
| (47) |
respectively, where are the roots of quadratic equations obtained by making an active constraint, i.e., .
Proof:
Due to POP constraint, tight analytical bounds on are obtained by using the expression of given in (16). Since is a piecewise function of , we first consider each case of (16) one by one, substitute , and find bounds in accordance with the respective range. In first case of , where and , the lower and upper bound can be obtained by solving which results in a quadratic equation given as , where and . The roots of the quadratic equation, denoted as and , are given in (48) at next page.
| (48) |
The lower bound of PA in this case can be obtained as iff exists as a feasible point in the range else . Similarly, the upper bound of PA in this case can be given as iff otherwise . Similar to the above analysis, lower and upper bounds can be obtained for other cases also. Let us denote lower and upper bounds, respectively, for the second case as and , and for third case as and . After identifying lower and upper bounds of PA in each case, the in the whole range can be obtained as and similarly, the upper bound can be obtained as . ∎
Global-optimal solution of is given by Lemma .
Lemma 8
The global-optimal power control solution at which maximum SOP between users is minimized, is given as
| (49) |
subject to the feasibility of candidate optimal points as .
Proof:
Since is a nonconvex optimization problem due to the presence of nonconvex constraints and , the candidate optimal points are obtained similar to the proof of Lemma . In order to ensure users’ rates necessity, we check if the obtained candidate optimal points satisfy POP constraint . Knowing and as obtained in the proof of Lemma , feasibility of optimal points can be ensured. After investigating feasible optimal points, the global-optimal solution is obtained at that feasible optimal point for which maximum SOP between users is minimum. ∎
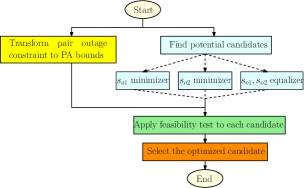
Fig. presents the methodology to find optimal PA for pair outage constrained secrecy fairness maximization problem.
V-C Proposed Algorithm and Complexity Analysis
(A) Finding potential candidates
(B) Check Feasibility
(C) Global-optimal Solution
Next, we present an algorithm that finds global-optimal PA which maximizes secrecy fairness between users while fulfilling their rate demands. For a given set of simulation parameters, and need to be calculated just once. Also, golden section search is applied to find three candidate optimal points of nonconvex optimization problem . Once they are calculated, is obtained by following the steps detailed in Algorithm 1. In order to investigate the complexity of proposed algorithm solving the optimization problem, we calculate total number of computations. The proposed algorithm is based on golden section search which terminates after iterations if . Hence, the total number of iterations in the proposed algorithm are , where .
V-D Asymptotic Power Control for min-max Secrecy Outage
In above analysis, we solved the min-max SOP optimization problem numerically. In order to gain analytical insights, now we derive the asymptotic closed-form expression of global-optimal PA under high SNR region. Considering the users’ rate requirements, problem can be stated as
| s.t. | (50) |
Following , an equivalent formulation of can be given as
| (51) |
where and appears from the definition of max.
We first solve optimization problem without considering QoS constraint, which can be given as
| s.t. | (52) |
Global-optimal solution of is provided by Lemma .
Lemma 9
The global-optimal solution of the optimization problem for maximizing the secrecy fairness is given by
| (53) |
where , respectively, have been obtained by minimizing (cf. IV-C), and is obtained by solving .
Proof:
We associate Lagrange multipliers with , with , and keep the boundary constraint implicit. Then, Lagrangian function can be written as
| (54) |
The corresponding KKT conditions are given by constraints and . Dual feasibility conditions are obtained as and using (52) and (54). The subgradient conditions are given as and . The complementary slackness conditions are obtained as and . Here also, three cases exist. Case 1: and , implies and results from minimization for U (36). Case 2: and , implies and provides the same solution as the optimal solution of minimization, i.e., from (39). Case 3: and , implies and it gives which is given as
| (55) |
Observing that the minimization problem has three optimal points, i.e., , , and , the global optimal solution is obtained as the point where maximum SOP is minimum. ∎
Next, while taking the QoS constraint into account, the global-optimal solution of is given by Lemma .
Lemma 10
Global-optimal solution of optimization problem for minimizing the maximum SOP is given by
| (56) |
subject to the feasibility of candidate optimal points as .
Proof:
Similar to proof of Lemma , we first find the candidate optimal points and . Next, the feasibility of these points is investigated between and . Finally, the global optimal point is obtained as the feasible optimal point where maximum SOP is minimized. ∎
VI Numerical Investigations
Next, numerical results are presented to assess the performance of proposed protocol. We present simulation setup, and discuss the system performance under various system settings. Specifically, we validate accuracy of analytical results, provide insights on effect of users’ distance and optimal PAs, and identify the performance gains achieved by global-optimal PA. Finally, tradeoff between QoS parameter POP and secrecy performance SOP is presented.
VI-A Simulation Setup
Downlink of a NOMA system is considered, where BS communicates with two untrusted users. For the sake of simulation study, near user distance and far user distance from BS are taken as meter and meter, respectively. and are taken as and , respectively. Noise signal at both users follow Gaussian distribution with a noise power of dBm. Small scale fading affecting both links is assumed to have exponential distribution with mean value [13]. Residual interference terms and are assumed to be equal and dBm [19]. Simulation results are averaged over randomly generated channel realizations for both U and U. The correctness of results is observed using the fact that root mean square error (RMSE) in approximating the derived results should be less than [34]. For golden section search, . is considered as the received SNR. POP and SOP are considered as performance metrics to evaluate the performance of system.
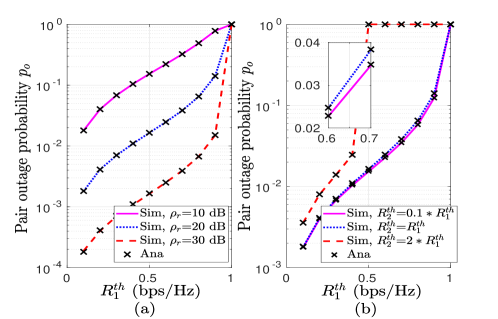
VI-B Validation of Analysis
We first validate analytical expressions of in Fig. 4, and and in Fig. 4. For these results, is considered as . A close match between the simulation and analytical results validates the analysis of , , and with a RMSE of the order of . Accuracy of asymptotic results, marked as ‘Asy’, is also verified with simulation results in Fig. 4(b). We observe that increases with increase in the threshold rates or . Similarly, increasing target secrecy rates and increase and , respectively. Following the fact that the outage occurs when the users’ maximum achievable rate is below a threshold rate, it is natural that increasing threshold rates and target secrecy rates at users, respectively, increases POP and SOP.
From the results it is also observed that threshold rate pair () with lesser value of compared to results a performance improvement in POP. The reason is that the achievable information rate at U is always less in comparison to U due to the poorer channel condition of U. On the other side, outage happens when the rate falls below a threshold rate. Therefore, in such a case, if more value of is considered, outage probability at U will be increased, which will further increase POP. Therefore, it can be concluded that the threshold rate pair () with has more practical significance to obtain better pair outage performance.
Further, we observe that increasing decreases , and . With increasing SNR, achievable data rates and secrecy rates at users increase, hence, for a given threshold rate and target secrecy rate, POP and SOP decreases, respectively. Noting the above observations, we can conclude that the performance of a system is highly dependent on system parameters.
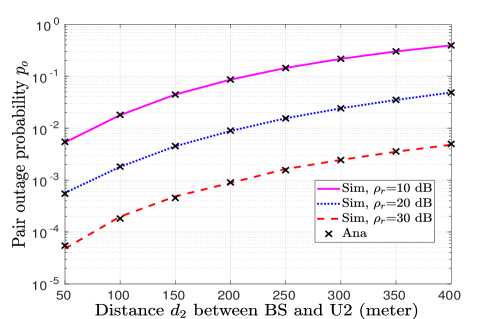
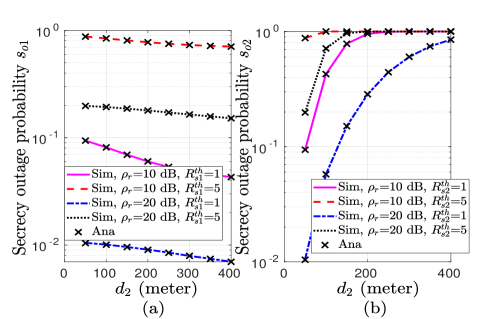
VI-C Impact of Relative Distance between Users
Fixing as meter, now we observe the effect of variation of from BS on achievable POP and SOP. In Fig. 6, increasing implies decrease in achievable data rate and hence, increasing the outage probability of U which results in an increase in POP. On the contrary, the results presented in Fig. 6(a), show that monotonically decreases with the increase in . The reason is, with increasing distance , a decrease in achievable information rate at U improves secrecy rate at U, and hence, SOP at U decreases. Also, decrease in information rate at U implies decrease in secrecy rate at U which increases SOP for U as shown in Fig. 6(b). Note that increasing the distance between BS to U has an opposite effect on and . Similarly, Fig. 6(a) and Fig. 6(b) also show a contradicting effect of on and . Hence, it can be summarized that since POP and SOPs for both the users are important system parameters for reliable and secure NOMA communication and fulfilling them together is highly dependent on the relative distance between BS and users.
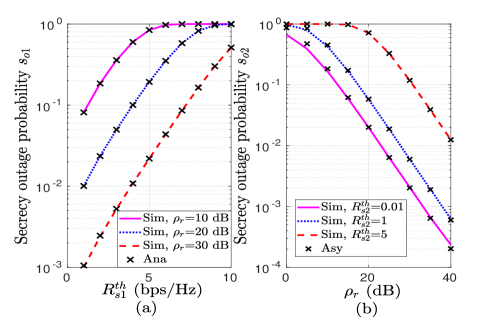
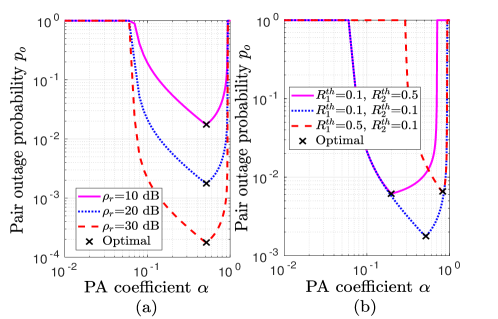
VI-D Insights on optimality
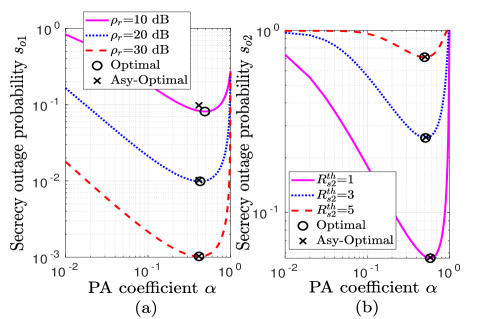
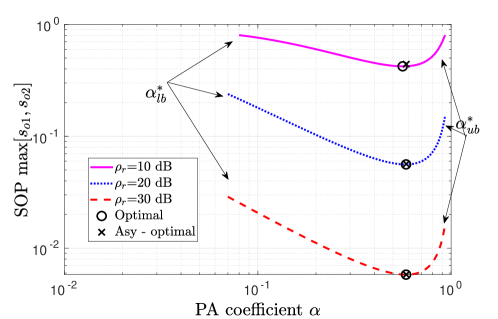
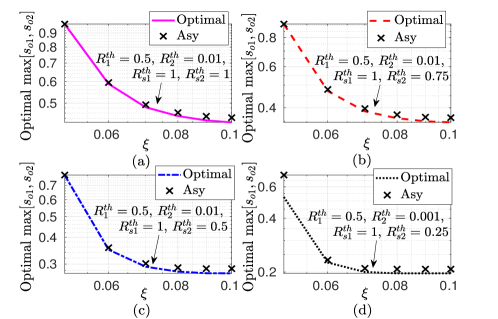
Now we investigate optimal pair outage and secrecy outage performance by presenting the numerical proof of the generalized-convexity of POP and SOP with respect to . Fig. 8(a) and Fig. 8(b) depict POP performance with for different values of SNRs and threshold rates, respectively. The pseudoconvex nature of POP can be easily observed. It confirms the unique solution of PA that provides minimum POP. Analytical results have also been plotted as a validation to the analysis. Similarly, Fig. 8(a) and Fig. 8(b), respectively, validate pseudoconvex nature of and with for different SNRs and threshold rates. The numerical optimal solution obtained using golden section algorithm has also been indicated. We observe that numerical results match with asymptotic results, which confirms the validity of asymptotic analysis. Further, to demonstrate secrecy fairness maximization under QoS constraint, Fig. 10 presents , with . and are shown as lower and upper bounds on , respectively, for an example case of . A close match between numerical and asymptotically optimal results can be observed at dB, which validates high SNR analysis. From the observations, it is worth noting that PA decides allocated powers to users, which effects POP and SOPs. Hence, an appropriate PA for given system parameters can help to obtain an optimal secure and reliable communication system.
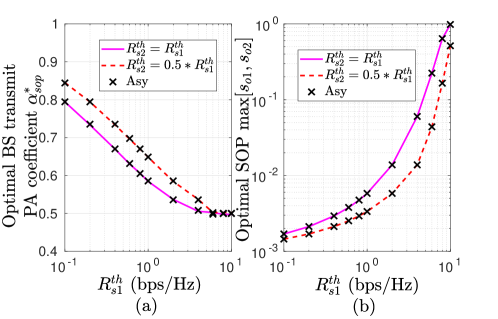
Next, Fig. 10(a) shows global-optimal that minimizes the maximum SOP between users as a function of target secrecy rates for various values of . Results show that for each target secrecy rate pair (, ), there is one and only one such that and are the optimal powers for U and U, respectively. On increasing , the optimal value of decreases, whereas the optimal SOP obtained from min-max optimization problem, presented in Fig. 10(b) increases. Further, lower value of in comparison to provides improvement in SOP which results in a higher value of . This is because the achievable data rate at U is less compared to the achievable data rate at U because of the weaker channel condition of U, due to which the achievable secrecy rate at U decreases. Note that according to the definition of secrecy outage, outage happens when the rate falls below a threshold rate. Therefore, it is natural if more value of is considered, SOP for U will be increased. Therefore, we can conclude that the threshold secrecy rate pair () with is a better choice to improve system performance.
VI-E Performance Comparison
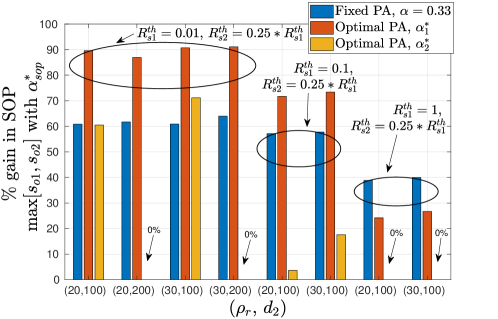
To demonstrate the performance gain achieved by the proposed algorithm for secrecy fairness maximization, Fig. 12 presents the performance comparison of global-optimal PA with fixed PA , and individual optimal PAs and obtained by minimizing and , respectively. Percentage gain depicts that achieves best SOP performance, because it ensures secrecy fairness between U and U. The average percentage improvement by over fixed PA, individual optimal PAs and are respectively around , and . Thus, it can be concluded that the global optimal PA allocated to users plays an important role in providing the best system performance.
VI-F Tradeoff
Secrecy performance and users’ data rates demands both are important system performance parameters for secure and reliable communication. However, fulfilling them together is a challenge because when QoS is considered, system sacrifices secrecy rate to improve QoS demands. This interesting tradeoff between minimized SOP and POP, as shown in Fig. 12, emphasizes the effect of QoS demands on optimal SOP performance. Decrease in SOP with an increase in POP highlights that higher rate demands lead to poor secrecy performance.
VII Concluding Remarks
This paper has proposed a novel decoding order that is capable of providing positive secrecy rate for both near and far users in a two-user untrusted NOMA system. To analyze secrecy performance, SOP for both users are derived, and closed-form expressions are given for the high SNR regime. Individual PA optimization to minimize SOPs and asymptotic optimal solutions have also been presented. In order to ensure users’ QoS demands for reliable communication over all the links, POP has been derived as a QoS measure, and optimal PA minimizing POP has also been obtained. Further, with an intention to provide secrecy fairness between users while satisfying their predefined QoS demands, optimization of PA to minimize the maximum SOP between users is also investigated. Numerical results are provided to verify the correctness of analytical expressions, provide insights on generalized-convexity of POP and SOP, highlight significant performance gains achieved by global-optimal PA, and describe the tradeoff between different system performance requirements. While this work has considered a two user NOMA system, the work can be extended to the study of secrecy in a multi-user scenario and considering other variants like code-domain NOMA. Furthermore, for an untrusted users’ scenario, it would be interesting to compare the performance of a NOMA enabled system with jammer assisted orthogonal multiple access.
Appendix A Proof of Theorem 2
Having obtained feasible decoding orders for NOMA system with the positive secrecy rate consideration at all users, we compare these orders in terms of users’ secrecy rates to investigate the optimal decoding order. The key idea here is, to find out that one decoding order which gives best secrecy rates at users. In this context, we have observed that, for each decoding order, secrecy rates and at U and U, respectively, are in the form of . Therefore, on comparing two decoding orders, we can easily show that a given secrecy rate is higher than its counterpart if either of or is higher, or either of or is lower, with other respective parameters being same. Thus, we can find out the optimal decoding order having maximum secrecy rate.
Considering Theorem , there exists three feasible decoding orders: , , and . We first compare and . In , and for , and, and for . Whereas, in , and for , and, and for . The remaining parameters, i.e., and are the same for the two considered orders for . The same holds true for . Observing in and , we note that in is lower in comparison to in , i.e., . Also, in is higher compared to in , i.e., . This is because is the residual interefence from imperfectly decoded U by U. Similarly, for also, is lower and is higher for in comparison to and , respectively, of . Therefore, it can be concluded that secrecy rate in is higher than for both U and U. In the similar manner, we compare and . In , for and for . Here also, for in and , is lower in compared to the in , and, for , is higher in in comparison to the in . Thus, will provide better secrecy rate than also, at both users.
Thus, we conclude that out of the three feasible decoding orders that can provide positive secrecy rate at both users, is a decoding order that ensures maximum secrecy rate at both the users as compared to other two decoding orders. Therefore, is considered as an optimal decoding order regardless of any PA, which is followed in analysis further.
Appendix B Proof of Lemma 4
Appendix C Proof of Lemma 5
Here also by setting, we obtain . We note is infeasible, because it forces which is not possible. Hence, asymptotic optimal PA for U is given as (39).
References
- [1] S. Thapar, D. Mishra, and R. Saini, “Secrecy fairness aware NOMA for untrusted users,” in Proc. IEEE GLOBECOM, Hawaii, USA, Dec. 2019, pp. 1–6.
- [2] Z. Ding, X. Lei, G. K. Karagiannidis, R. Schober, J. Yuan, and V. K. Bhargava, “A survey on non-orthogonal multiple access for 5G networks: Research challenges and future trends,” IEEE J. Sel. Areas Commun., vol. 35, no. 10, pp. 2181–2195, Oct. 2017.
- [3] Y. Liu, Z. Qin, M. Elkashlan, Y. Gao, and L. Hanzo, “Enhancing the physical layer security of non-orthogonal multiple access in large-scale networks,” IEEE Trans. Wireless Commun., vol. 16, no. 3, pp. 1656–1672, Mar. 2017.
- [4] Y. Liu, Z. Qin, M. Elkashlan, Z. Ding, A. Nallanathan, and L. Hanzo, “Nonorthogonal multiple access for 5G and beyond,” Proceedings of the IEEE, vol. 105, no. 12, pp. 2347–2381, Dec. 2017.
- [5] A. D. Wyner, “The wire-tap channel,” Bell system technical journal, vol. 54, no. 8, pp. 1355–1387, 1975.
- [6] Y. Wu, A. Khisti, C. Xiao, G. Caire, K. Wong, and X. Gao, “A survey of physical layer security techniques for 5G wireless networks and challenges ahead,” IEEE J. Sel. Areas Commun., vol. 36, no. 4, pp. 679–695, Apr. 2018.
- [7] Y. Zhang, H.-M. Wang, Q. Yang, and Z. Ding, “Secrecy sum rate maximization in non-orthogonal multiple access,” IEEE Commun. Lett., vol. 20, no. 5, pp. 930–933, May 2016.
- [8] B. He, A. Liu, N. Yang, and V. K. Lau, “On the design of secure non-orthogonal multiple access systems,” IEEE J. Sel. Areas Commun., vol. 35, no. 10, pp. 2196–2206, Oct. 2017.
- [9] J. Chen, L. Yang, and M. Alouini, “Physical layer security for cooperative NOMA systems,” IEEE Trans. Veh. Technol., vol. 67, no. 5, pp. 4645–4649, May 2018.
- [10] L. Lv, F. Zhou, J. Chen, and N. Al-Dhahir, “Secure cooperative communications with an untrusted relay: A NOMA-inspired jamming and relaying approach,” IEEE Trans. Inf. Forensics Security, vol. 14, no. 12, pp. 3191–3205, 2019.
- [11] F. Zhou, Z. Chu, H. Sun, R. Q. Hu, and L. Hanzo, “Artificial noise aided secure cognitive beamforming for cooperative MISO-NOMA using SWIPT,” IEEE J. Sel. Areas Commun., vol. 36, no. 4, pp. 918–931, 2018.
- [12] Y. Li, M. Jiang, Q. Zhang, Q. Li, and J. Qin, “Secure beamforming in downlink MISO nonorthogonal multiple access systems,” IEEE Trans. Veh. Technol., vol. 66, no. 8, pp. 7563–7567, Aug. 2017.
- [13] B. M. ElHalawany and K. Wu, “Physical-layer security of NOMA systems under untrusted users,” in Proc. IEEE GLOBECOM, United Arab Emirates, Dec. 2018, pp. 1–6.
- [14] R. Saini, D. Mishra, and S. De, “Subcarrier pairing as channel gain tailoring: Joint resource allocation for relay-assisted secure OFDMA with untrusted users,” Physical Communication, vol. 32, pp. 217–230, 2019.
- [15] R. Saini, D. Mishra, and S. De, “Utility regions for DF relay in OFDMA-based secure communication with untrusted users,” IEEE Commun. Lett., vol. 21, no. 11, pp. 2512–2515, Nov. 2017.
- [16] D. Xu, P. Ren, Q. Du, L. Sun, and Y. Wang, “Combat eavesdropping by full-duplex technology and signal transformation in non-orthogonal multiple access transmission,” in Proc. IEEE ICC, Paris, France, May 2017, pp. 1–6.
- [17] C. Yan, A. Harada, A. Benjebbour, Y. Lan, A. Li, and H. Jiang, “Receiver design for downlink non-orthogonal multiple access (NOMA),” in Proc. IEEE VTC Spring, Glasgow, United Kingdom, May 2015, pp. 1–6.
- [18] M. Vaezi, R. Schober, Z. Ding, and H. V. Poor, “Non-orthogonal multiple access: Common myths and critical questions,” IEEE Wireless Commun., vol. 26, no. 5, pp. 174–180, 2019.
- [19] X. Yue, Z. Qin, Y. Liu, S. Kang, and Y. Chen, “A unified framework for non-orthogonal multiple access,” IEEE Trans. Commun., vol. 66, no. 11, pp. 5346–5359, Nov. 2018.
- [20] Z. Ding, M. Peng, and H. V. Poor, “Cooperative non-orthogonal multiple access in 5G systems,” IEEE Commun. Lett., vol. 19, no. 8, pp. 1462–1465, Aug. 2015.
- [21] Z. Ding, P. Fan, and H. V. Poor, “Impact of user pairing on 5G nonorthogonal multiple-access downlink transmissions,” IEEE Trans. Veh. Technol., vol. 65, no. 8, pp. 6010–6023, Aug. 2016.
- [22] T. M. Cover and J. A. Thomas, Elements of information theory. John Wiley & Sons, 2012.
- [23] Y. Liu, Z. Ding, M. Elkashlan, and H. V. Poor, “Cooperative non-orthogonal multiple access with simultaneous wireless information and power transfer,” IEEE J. Sel. Areas Commun., vol. 34, no. 4, pp. 938–953, Apr. 2016.
- [24] N. T. Do, D. B. Da Costa, T. Q. Duong, and B. An, “A BNBF user selection scheme for NOMA-based cooperative relaying systems with SWIPT,” IEEE Commun. Lett., vol. 21, no. 3, pp. 664–667, Mar. 2017.
- [25] X. Chen, A. Beiijebbour, A. Li, H. Jiang, and H. Kayama, “Consideration on successive interference canceller (SIC) receiver at cell-edge users for non-orthogonal multiple access (NOMA) with SU-MIMO,” in Proc. PIMRC, Hong Kong, China, Aug. 2015, pp. 522–526.
- [26] S. Thapar, D. Mishra, and R. Saini, “Decoding orders and power allocation for untrusted NOMA: A secrecy perspective,” in Proc. IEEE WCNC, Seoul, South Korea, May 2020, pp. 1–6.
- [27] D. Tse and P. Viswanath, Fundamentals of wireless communication. Cambridge university press, 2005.
- [28] A. Papoulis and S. U. Pillai, Probability, random variables, and stochastic processes. Tata McGraw-Hill Education, 2002.
- [29] S. Boyd and L. Vandenberghe, Convex optimization. Cambridge university press, 2004.
- [30] D. Mishra, S. De, and C.-F. Chiasserini, “Joint optimization schemes for cooperative wireless information and power transfer over rician channels,” IEEE Trans. Commun., vol. 64, no. 2, pp. 554–571, Feb. 2016.
- [31] M. S. Bazaraa, H. D. Sherali, and C. M. Shetty, Nonlinear programming: theory and applications. New York: John Wiley and Sons, 2006.
- [32] Y.-C. Chang, “N-dimension golden section search: Its variants and limitations,” in Proc. 2nd Int. Conf. on Biomedical Engineering and Informatics (BMEI), Tianjin, China, Oct. 2009, pp. 1–6.
- [33] A. Ravindran, G. V. Reklaitis, and K. M. Ragsdell, Engineering optimization: methods and applications. John Wiley & Sons, 2006.
- [34] D. Mishra and S. De, “Optimal relay placement in two-hop RF energy transfer,” IEEE Trans. Commun., vol. 63, no. 5, pp. 1635–1647, May 2015.