On the Secrecy Design of STAR-RIS assisted Uplink NOMA Networks
Abstract
This paper investigates the secure transmission in a simultaneously transmitting and reflecting reconfigurable intelligent surface (STAR-RIS) assisted uplink non-orthogonal multiple access system, where the legitimate users send confidential signals to the base station by exploiting STAR-RIS to reconfigure the electromagnetic propagation environment proactively. Depending on the availability of the eavesdropping channel state information (CSI), both the full CSI and statistical CSI of the eavesdropper are considered. For the full eavesdropping CSI scenario, we adopt the adaptive-rate wiretap code scheme with the aim of maximizing minimum secrecy capacity subject to the successive interference cancellation decoding order constraints. To proceed, we propose an alternating hybrid beamforming (AHB) algorithm to jointly optimize the receive beamforming, transmit power, and reflection/transmission coefficients. While for the statistical eavesdropping CSI scenario, the constant-rate wiretap code scheme is employed to minimize the maximum secrecy outage probability (SOP) subject to the quality-of-service requirements of legitimate users. Then, we derive the exact SOP expression under the constant-rate coding strategy and develop an extended AHB algorithm for the joint secrecy beamforming design. Simulation results demonstrate the effectiveness of the proposed scheme. Moreover, some useful guidance about the quantification of phase shift/amplitude and the deployment of STAR-RIS is provided.
Index Terms:
Non-orthogonal multiple access, physical layer security, STAR-RIS, secrecy beamforming design.I Introduction
Driven by the growing demands for high-data-rate required applications and ubiquitous wireless connectivity, reconfigurable intelligent surface (RIS) is emerged as a promising technique for next-generation wireless communications [1, 2]. Generally, RIS is a type of metamaterial-based planar array, consisting of plenty of passive scattering elements. Each reconfigurable element is able to adjust the phase shift and amplitude independently via a smart controller, thus controlling the radio propagation environment proactively. However, due to the hardware implementation, conventional RISs can only reflect the incident signals and serve wireless devices located on the same side of it, which immensely limits their deployment flexibility and coverage ranges [3, 4, 5]. To address this, a novel type of metamaterial, namely simultaneous transmitting and reflecting RIS (STAR-RIS) [6, 7, 8], is proposed, which supports both electric-polarization and magnetization currents [9, 10], so as to reflect and/or transmit the incident signals upon it. Compared with the conventional RIS, STAR-RIS is able to provide a full-space (i.e., 360∘) service coverage and enjoys a more flexible deployment.
As another enabling technique, non-orthogonal multiple access (NOMA) can serve multiple users within one spectrum resource by leveraging the successive interference cancellation (SIC), to achieve massive connectivity and spectral efficiency enhancement [11]. Compared with orthogonal multiple access (OMA) transmission, NOMA is more sensitive to the wireless channels as it introduces additional co-channel interference. The integration of NOMA and STAR-RIS can naturally overcome the randomness of wireless channels, thus further boosting the spectral performance [12, 13, 14, 15, 16]. The authors of [12] investigated the fundamental coverage characterization of the STAR-RIS assisted NOMA networks, which demonstrated the superior coverage performance of STAR-RIS than conventional RIS. The work of [13] proposed a novel NOMA integrated over-the-air federated learning (AirFL) framework, where STAR-RIS was deployed to enhance spectral efficiency and mitigate interference. In [14], the authors studied the resource allocation problem of the STAR-RIS assisted NOMA network, where a two-layer iterative algorithm was developed to jointly optimize transmit beamforming and reflection/transmission beamforming. Furthermore, the STAR-RIS assisted NOMA enhanced coordinated multi-point transmission (CoMP) transmission was investigated in [15]. In [16], the authors further proposed a general analytical framework for STAR-RIS assisted NOMA networks.
Nevertheless, due to the broadcast characteristic of wireless transmissions, confidential or sensitive data is exposed to vulnerable communication environments. For the provision of the secure and private information transmission, the concept of physical layer security (PLS) is proposed from the perspective of information theory, which exploits the inherent characteristics of wireless channels (e.g., noise, fading, and interference) to degrade the legitimate information leakage [17, 18]. Benefiting from the RIS’s ability to adjust wireless channels, the integration of RIS into the PLS has received much attention [19, 20, 21, 22, 23]. Specifically, The authors of [19] studied the secrecy capacity maximization problem of the RIS assisted multiple-input-single-output (MISO) network, which validated the potential of integrating RIS into PLS. A novel artificial noise (AN) based jamming protocol via RIS was proposed in [20], which shows that AN was conducive to the secrecy enhancement of the RIS assisted networks. The work of [21] further proposed a robust AN aided transmission scheme, which guarantees the secrecy performance without requiring eavesdropping channel state information (CSI). While for NOMA networks, the authors of [22] and [23] studied the secure transmission problems of the RIS assisted NOMA networks under the imperfect and statistical eavesdropping CSI, respectively. More recently, an initial exploration on STAR-RIS assisted PLS was studied in [24], which showed that compared with conventional RIS, STAR-RIS is capable of providing higher secrecy performance.
I-A Motivations and Contributions
From the aforementioned efforts [12, 13, 14, 15, 16, 19, 20, 21, 22, 23, 24], two significant observations are obtained as follows.
-
•
Although many efforts [12, 13, 14, 15, 16] are devoted to the STAR-RIS assisted NOMA communications, the critical issue of securing privacy has not been addressed yet, to the best of our knowledge. In fact, since STAR-RIS is capable of providing a 360∘ service, it inevitably leads to a 360∘ eavesdropping, which brings more serious security hazards to the private information transmission than that with conventional reflecting-only RIS.
-
•
Meanwhile, the existing schemes devoted to the RIS/STAR-RIS enhanced PLS [19, 20, 21, 22, 23, 24] are not applicable to the STAR-RIS assisted uplink transmission due to its unique energy splitting (ES) protocol. Specifically, since both the incident signals from the different sides of STAR-RIS suffer reflection and transmission propagations, a new type of energy/signal leakage, namely opposite-side leakage, appears, i.e., the reflecting/transmitting signals upon the opposite side of STAR-RIS from the base station (BS) are fully leaked, which requires the novel secrecy beamforming framework.
Motivated by the above, we focus on a STAR-RIS assisted uplink NOMA secrecy communication, where both full eavesdropping CSI and statistical eavesdropping CSI are considered. Our goal is to achieve the active control of the wireless propagation environment via the STAR-RIS, thus protecting the NOMA communication from malicious eavesdropping. The main contributions of this paper are summarized as follows.
-
•
We propose a STAR-RIS assisted uplink NOMA communication framework in the presence of an eavesdropper, where the indoor user (IU) and outdoor user (OU) send their signals to the BS through the reflection/transmission links provided by STAR-RIS. Depending on the availability of instantaneous eavesdropping CSI, two types of eavesdropping CSI are considered, i.e., full eavesdropping CSI and statistical eavesdropping CSI. Accordingly, we respectively formulate the joint beamforming and power optimization problems for minimum secrecy capacity maximization and maximum SOP minimization, subject to the SIC decoding constraints and reflection/transmission coefficient constraints.
-
•
To tackle the non-convex optimization problem under the full eavesdropping CSI, we decompose the original problem into two subproblems and develop an alternating hybrid beamforming (AHB) algorithm for secrecy beamforming design. For the joint beamforming optimization subproblem, a polarization identity based two-layer iterative algorithm is designed to obtain the stationary point solution of the receive/passive beamforming. While for the transmit power optimization subproblem, the optimal transmit power policy is derived in the closed-form expression. Moreover, the convergence of the proposed AHB algorithm is theoretically proved.
-
•
To handle the more challenging problem for the case of statistical eavesdropping CSI, we first derive the exact SOP expression, which converts the non-convex objective function to a tractable form. Then, an extended AHB algorithm is proposed to convexify the non-convex constraints, thus minimizing the maximum SOP among legitimate users, where we modify the two-layer iterative algorithm to optimize the hybrid beamforming, and derive the closed-form optimal transmit power strategy based on the monotonicity analysis.
-
•
Simulation results demonstrate the convergence of the proposed algorithms and draw three interesting insights. 1) Secrecy superiority: STAR-RIS assisted NOMA communication achieves the best secrecy performance over other baseline schemes. 2) Secrecy quantization loss: when neglecting the existence of eavesdropper, the transmission rate only requires the -bit quantization to achieve performance of the continuous phase shifts/amplitudes, which is consistent with the conventional reflecting-only RIS. However, when considering the secrecy transmission against the eavesdropper, the secrecy rate needs or more bits for achieving around performance of the continuous case. 3) Secrecy deployment guidance: deploying STAR-RIS near the users or the BS under the adaptive-rate wiretap code setting is preferred, whereas it is preferable to deploy STAR-RIS far away from both of them under the constant-rate wiretap code setting.
The remainder of this paper is as follows. In Section II, we present the system model and formulate the optimization problems. Section III develops an AHB algorithm for the challenging optimization problem with the full eavesdropping CSI case. Section IV extends the AHB algorithm proposed in the previous section to the case of statistical eavesdropping CSI. Our numerical results and discussions are shown in Section V. Finally, the conclusions are presented in Section VI.
Notations: boldface capital and lower-case letter represent matrix and vector respectively. denotes the complex-valued matrix lying in the -dimensional space, while and are the transpose and Hermitian conjugate operations. The rank value, trace operation and spectral norm of X are respectively denoted by , and . The positive semidefinite matrix is denoted by , while the circularly symmetric complex Gaussian (CSCG) vector with zero mean and covariance matrix is . The diagonal matrix whose main diagonal elements equal to the elements of vector x is denoted by , while denotes the ith largest singular value of corresponding matrix. and respectively denote the modulus of complex variable and the Euclidean norm of the vector . · and · are the probability operation and statistical expectation. is the identity matrix, denotes the real component of the complex value, while denotes the Hadamard product.
II System Model and Problem Formulation
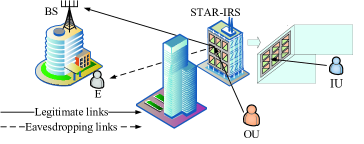
We consider a STAR-RIS assisted uplink NOMA network as shown in Fig. 1, which consists of an IU, an OU, a BS, an eavesdropper (E), and a STAR-RIS. E is located at the BS end and tries to wiretap both signals from IU and OU. There is no direct link between the BS/E and IU/OU due to the obstacles. To resist eavesdropping while relaying the superimposed signals from IU/OU to the BS, we deploy a STAR-RIS on the building facades, with being operating in the ES mode [6]. All the nodes are assumed to operate in a half-duplex mode. The BS is equipped with antennas, while the remaining nodes are equipped with a single antenna. The STAR-RIS has elements, each of which can independently change the amplitudes and phase shifts of reflected/transmitted signals upon it, thus reconfiguring the signal propagation proactively. Let and denote the transmission and reflection coefficients of th element of STAR-RIS, where 111The transmission and reflection amplitude coefficients should obey the law of energy conservation [6]., and [7, 8]. Additionally, there is a smart controller, connected to the STAR-RIS, communicates with the BS via a separate wireless link for pilot acquisition and instant control instruction interaction [2, 3].
The quasi-static block fading channels are considered in this paper, which means that all the channels remain constant in one fading block but vary over the different fading blocks. The baseband equivalent channels from STAR-RIS to BS, IU, OU, and E are denoted as , , and . Since the positions of STAR-RIS and BS can be properly selected to favor line-of-sight (LoS) transmission, the Rician fading model is assumed for , i.e., , where denotes the LoS component, denotes the non-line-of-sight (NLoS) component, and denotes the corresponding Rician factor. While for the remaining links, we consider the Rayleigh fading model for them as the mobile users are usually situated in rich-scattering environments.
Moreover, we assume that the instantaneous CSI of legitimate channels is perfectly available, where the reflecting and transmitting channels can be separately estimated by the anchor-assisted channel estimation approach in [27]. While for E, two types of eavesdropping CSI assumptions are considered in this paper. To elaborate, 1) If E is an internal wiretap node (i.e., another active user of the network), the full eavesdropping CSI is assumed to be available at the legitimate nodes; 2) while if E is an external wiretap node, such as the purely passive eavesdropping device of the third-party network without any pilot information interaction with legitimate nodes, it is assumed that only the statistical eavesdropping CSI is available for legitimate nodes, which can be estimated via the long-term monitoring [28].
Following the uplink NOMA principle, IU and OU transmit and to the BS via the STAR-RIS, where and are corresponding signals with . Accordingly, the received signals at the BS is given by
| (1) |
where and denote the transmit power at the IU and OU, , denote the transmission and reflection coefficient matrices respectively, and represents the additive white Gaussian noise (AWGN) at the BS. On receiving superimposed signals, the multi-antenna BS exploits a receive beamforming vector to combine the linearly by adjusting the phases/amplitudes of the signals [25, 26]. Thus, the extracted signal through the receive beamforming is expressed as
| (2) |
As for E, as it is located near the BS and can intercept the superimposed signals, the received signals are given by
| (3) |
where represents the AWGN at the E.
In uplink NOMA transmission, we assume that the BS adopts the SIC technique to decode the superimposed signals with the optimal decoding order, which starts from the stronger signals to the weaker signals [11]. To facilitate the SIC decoding order optimization, we use and to represent the decoding order of IU and OU respectively, which satisfies . For instance, if the BS first decodes by treating as interference, we have . The received signal-to-interference-plus-noise ratio (SINR) at the BS to decode is given by
| (4) |
Then, the BS can eliminate from its observations and decode without interference. As such, we have , and the received signal-to-noise ratio (SNR) to decode is given by
| (5) |
While for the other case that the BS first decodes , we have and .
As for E, it has different channel conditions from the BS, which may lead to the different SIC decoding orders at E from BS. In other words, both and might be decoded at the second SIC stage, which enjoys an interference-free decoding. To avoid the secrecy performance loss caused by the uncertain decoding order at E, we consider the worst-case assumption from the perspective of PLS in this paper, i.e., E decodes both two signals without suffering from co-channel interference. Thus, the received SNRs at E to decode and are given by
| (6) |
II-A Problem Formulation for Full Eavesdropping CSI
In the full eavesdropping CSI case, as the legitimate nodes possess the instantaneous channel gains of all the transmission links, we can evaluate the channel capacities of the legitimate and wiretap channels. Therefore, we consider the adaptive-rate wiretap code scheme [17], that elaborately design the codeword rate and redundant rate () to minimize the mutual information between the IU/OU and E, thus securing legitimate transmissions perfectly. Accordingly, the secrecy capacity is given by
| (7) |
where . In this case, we aim to maximize the minimum secrecy capacity among IU and OU by jointly optimizing transmit power at the IU/OU, receive beamforming at the BS, and passive beamforming at the STAR-RIS, subject to the total power consumption at the IU/OU, SIC decoding order constraint at the BS, and the phase shifts/amplitudes constraints at the STAR-RIS. The optimization problem is formulated as follows.
| (8a) | ||||
| (8b) | ||||
| (8c) | ||||
| (8d) | ||||
| (8e) | ||||
| (8f) | ||||
where and represent the maximal transmit power at the IU and OU. In problem (8), (8b) denotes the total power consumption limit at IU/OU; (8c) denotes the SIC decoding order constraint at the BS; (8d) denotes the normalization constraint of the receive beamforming ; (8e) and (8f) denote the amplitudes and phase shifts constraints at the STAR-RIS, respectively. Furthermore, to avoid the secrecy performance loss caused by the SIC decoding order, we solve the problem (8) for the cases of and and select the maximal secrecy capacity as the final solution.
II-B Problem Formulation for Statistical Eavesdropping CSI
In statistical eavesdropping CSI case, since there is no available instantaneous channel information of the wiretap links, it is impossible to exactly evaluate the channel capacity of E, which invalidates the adaptive-rate wiretap code scheme above. To guarantee the perfect secure transmission of the legitimate users, the constant-rate wiretap code scheme is considered under this circumstance, where IU and OU transmit signals with the constant codeword rate and the constant secrecy rate () [29]. Ulteriorly, we introduce the SOP as the security metric for network secrecy performance assessment, which is defined as the probability that the positive difference between the presupposed codeword rate and eavesdropping channel capacity is less than the target secrecy rate . It is given by
| (9) |
We aim to minimize the maximum SOP of legitimate users subject to the total power consumption and codeword rate constraint at the IU/OU, SIC decoding order constraint at the BS, and the phase shift/amplitude constraints at the STAR-RIS, by jointly optimizing transmit power at the IU/OU, receive beamforming at the BS and passive beamforming at the STAR-RIS. The problem is formulated as follows.
| (10a) | ||||
| (10b) | ||||
| (10c) | ||||
where (10c) denotes the constant codeword rate.
Remark 1
Due to the two-layer coupling, the formulated problems (8) and (10) are more challenging to tackle than the conventional beamforming optimization problem of the reflecting-only RIS assisted downlink transmission. Specifically, 1) in the outer layer, A three-variable coupling exists in the objective function (8a) and constraints (8c), which cannot be coped with traditional methods applied in joint active and passive beamforming design [3, 19, 40]; 2) in the inner layer, the amplitudes of transmission and reflection beamforming are restricted by each other because of the law of energy conservation, which further exacerbates the optimization difficulty. In the next two sections, we first propose an AHB algorithm to handle the problem (8) and then extend it to the problem (10).
III Proposed Solution for Full Eavesdropping CSI
In this section, we develop an efficient AHB algorithm to maximize the minimum secrecy capacity of IU and OU, where a two-layer iterative algorithm is proposed to optimize reflection/transmission coefficients and receive beamforming jointly, while the optimal transmit power policy is derived in the closed-form expression.
III-A Joint Beamforming Optimization
Define , , and , . With the fixed and , we rewrite the problem (8) as
| (11a) | ||||
| (11b) | ||||
| (11c) | ||||
| (11d) | ||||
| (11e) | ||||
| (11f) | ||||
where and . To tackle the problem (11) with non-convex terms (11a), (11b) and (11f), we adopt the polarization identity [31] to decouple the reflection/transmission coefficients of STAR-RIS and the receive beamforming at the BS. Specifically, according to [31, eq.(1.4.50)], we can equivalently rewrite as
| (12) |
where in the case of while in the case of . By leveraging the first-order Taylor expansion of and , the convex upper bound and the concave lower bound expressions of are respectively given by
| (13) |
| (14) |
where and denote the local points generated in the previous iteration, while and are slack variables introduced to represent the lower bound and upper bound of , respectively.
With the results above, the SIC decoding order constraints (11b) can be conservatively transformed into the following linear form
| (15) |
Similarly, the lower bound of the secrecy capacity of IU/OU can be expressed as , where
| (16) |
Therefore, the optimization problem (11) can be reformulated as
| (17a) | ||||
| (17b) | ||||
| (17c) | ||||
The problem (17) remains non-convex and challenging to deal with due to the non-convexity in (16), (17a) and (17c). To overcome this issue, we introduce slack variable to denote the lower bound SINR of the strong signal, i.e.,
| (18) |
Then, we resort to Lemma 1 to construct the convex upper approximation function of right-hand side of (18) as follows
| (19) |
where .
Lemma 1
According to [32], the convex upper approximation function of the function for is supposed to meet: 1) for arbitrary given parameter , holds; 2) for arbitrary positive and , there always exists a parameter , which satisfies
| (20a) | ||||
| (20b) | ||||
| (20c) | ||||
As a result, we are capable of rewriting (17a) as
| (21) |
where satisfies
| (22) |
Moreover, to guarantee rank-one property of , we adopt the difference-of-convex (DC) relaxation method [33] to extract the rank-one solution from high-rank matrix. To elaborate, is equivalent to , where and . With [33, Prop. 2], it can be further relaxed into the DC constraint below
| (23) |
where denotes the leading eigenvector of obtained in the previous iteration, and is the penalty factor. Up to this point, the problem (19) can be reformulated as a standard fractional programming with non-convex constraint , which, however, can be efficiently handled by the Dinkelbach approach [34] and following lemma. The transformed rank-relaxed problem is given by
| (24a) | ||||
| (24b) | ||||
| (24c) | ||||
| (24d) | ||||
where is the scaling factor of the penalty terms and . Note that denotes the update coefficient, which starts from , and is updated by in each iteration, while is an auxiliary variable, which is introduced to measure the approximation gap between and .
Lemma 2
The obtained solution for the rank-relaxed problem (24) can always guarantee that .
Proof:
See Appendix A. ∎
Remark 2
For any given , the rank-relaxed problem (24) is jointly convex with respect to the optimization variables and can be directly solved by the convex solver (e.g., CVX) in each iteration. Nevertheless, it is supposed to be much careful about the initialization of the value of due to the following reasons. 1) If we initialize scaling factor to be a large value (i.e., ), any tiny decrease in the penalty term (i.e., ) will lead to a significant increase in the objective function. Thus, the objective function (24a) will be dominated by the penalty terms, which efficiently guarantees the rank-one property of but neglects our goal of secrecy capacity maximization. 2) In contrast, if we initialize scaling factor to be a small value (i.e., ), the secrecy rate penalty caused by the high-rank beamforming matrices becomes trivial, which is conducive to obtain a good starting point for secrecy capacity maximization, but cannot ensure the rank-one property of . To overcome this issue, we initialize to be a small value and adopt the two-layer algorithm framework, where remains constant in the inner layer iteration while increasing over the outer layer iterations to converge the stationary point solution of the original problem [36]. The details of the two-layer iterative algorithm is summarized in Algorithm-1, where and denote the convergence accuracy of inner and outer layer loops.
| Algorithm-1: Two-layer Iterative Algorithm |
|---|
| 1: Initialization: Initialize the iteration parameters as , , , , and with ; |
| 2: Outer layer: repeat |
| 3: Inner layer: repeat |
| 4: For given , and , solve problem (24); |
| 5: Set ; |
| 6: Update the iteration parameters , , , |
| . Then, is replaced by the leading |
| eigenvector of ; |
| 7: Until ; |
| 8: Set , ; |
| 9:Until . |
III-B Optimal Transmit Power Policy
With the fixed , problem (8) is equivalent to
| (25a) | ||||
| (25b) | ||||
| (25c) | ||||
For the case of , the objective function (25a) can be rewritten as , where and satisfy
| (26) | |||
| (27) |
As a result, the partial derivatives of are derived as
| (28) | |||
| (29) |
It is clear that is a monotonic decreasing function of because always holds. However, we can not directly judge the monotonicity of with respect to from (28). To further illustrate monotonicity of , we introduce following implicit conditions that if problem (24) is feasible, the optimized variables in Algorithm-1 will satisfy and . This is because that if these two conditions do not hold, the minimum secrecy capacity returned by Algorithm-1 is always less than , which contradicts the constraint . Therefore, by substituting into (28), we can derive , which implies that is a monotonic increasing function with respect to . In the same way, we can also prove that function is a monotonic increasing function with respect to .
Proposition 1
The optimal transmit power policy under the case of is given by
| (30) |
where , and for .
Proof:
With the monotonic property analyzed above, it is clear that the minimum secrecy rate reaches maximal value when . However, since and are the monotonic decreasing and increasing functions of , respectively, two possible situations probably occur when we increase from to : 1) there exists a value of between and , which satisfies ; 2) there is no satisfying , i.e., always holds. In the former case, the minimum secrecy rate reaches maximum when holds, which can be simplified as 222Note that although we can obtain two candidate solutions via solving quadratic equation , there only exists a unique positive solution due to the monotonicity of and with respect to .. In the latter case, the minimum secrecy rate equals to , so the optimal is given by . Furthermore, considering the SIC decoding order constraint (25c), is also limited by . Accordingly, the closed-form optimal can be derived. This completes proof. ∎
By adopting Proposition 1, we can further derive the optimal under the arbitrary SIC decoding order as follows.
| (31) |
where .
III-C Overall Algorithm
The overall algorithm is summarized in Algorithm-2, where is introduced to record the minimum security capacity of each alternate iteration, while is the pre-defined convergence accuracy of AHB algorithm.
| Algorithm-2: Proposed AHB Algorithm for Minimum Secrecy Capacity Maximization |
|---|
| 1: Initialization: Initialize the , and with ; |
| 2: Repeat |
| 3: Perform Algorithm-1 to obtain the stationary point solutions with the fixed |
| ; |
| 4: Calculate the optimal solutions according to (31) with the fixed |
| ; |
| 5: Update and set ; |
| 6: Until . |
Proposition 2
The proposed AHB algorithm is guaranteed to converge to the suboptimal solution over the non-decreasing iterations.
Proof:
See Appendix B. ∎
Since the optimal transmit power are updated by the closed-form expression, the main computational complexity of Algorithm-2 relies on the complexity of Algorithm-1. The complexity to solve (24) via the standard interior-point method is given by [37], where denotes the number of variables, denotes the dimension of the second-order cone (SOC) constraint [38], while , and denote the numbers of the alternating iteration, the outer layer iteration, and the inner layer iteration.
IV Proposed Solution for Statistical Eavesdropping CSI
In this section, we extend the AHB algorithm proposed in the previous section to solve problem (10). Specifically, we first derive the exact SOP expression of IU/OU, and decompose the problem (10) into two subproblems. For the joint beamforming optimization subproblem, the modified two-layer iterative algorithm is developed to optimize reflection/transmission coefficients and receiving beamforming jointly. While for the power optimization subproblem, we derive the optimal transmit power policy in the closed-form expression.
IV-A Exact SOP Expression of IU and OU
Let and , where denote the small fading coefficients, while , and denote the large scale path loss factors. To reveal the distribution of random variables and , we first derive the exact probability density function (PDF) of (), which is defined as . Let , and , where the real random variables , , and follow the independent and identically distributed (i.i.d.) Gaussian distribution with zero mean and variance. Thus, we can rewrite as
| (32) |
where and . By treating , and as the constant coefficients, and can be regarded as the sums of the i.i.d. Gaussian variables and . Thus, and follow the Gaussian distribution, i.e., [30].
While for any linear combination of and , we can rewrite it as
| (33) |
Note and are also Gaussian variables as they are the sums of i.i.d. Gaussian variables and . Obviously, and consist of two i.i.d. Gaussian variables and with orthogonal weight coefficient vectors and , so they follows i.i.d. Gaussian distribution. Since the sum of i.i.d. Gaussian variables is also Gaussian distributed, follows Gaussian distribution, which indicates that and follow two-dimensional Gaussian distribution. Moreover, with the independence of , , and , the correlation between and can be expressed as
| (34) |
which proves the independence of and . Up to now, we have proved that and are the i.i.d. Gaussian variables, which also follow joint Gaussian distribution and independent (also uncorrelated), so the complex variable follows complex Gaussian distribution, i.e., , where . To proceed, by summing the real parts and imaginary parts of and () separately, we have that . Note that this result is also applicable to , i.e., . Then, the PDF of is an exponential distribution function with parameter , .
Accordingly, we can derive the exact SOP as
| (35) |
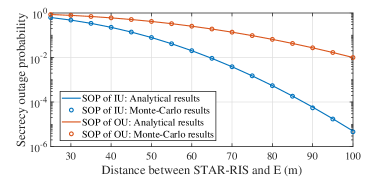
Tightness of the analytical SOP expression: The analytical/numerical SOP of IU and OU versus the distance between the STAR-RIS and E is illustrated in Fig. 2, where the random phase shifts and amplitudes are considered, and the other simulation parameters are the same as Table I. As can be observed, 1) the analytical expression of SOP in (IV-A) for both two users are accurate; and 2) the secrecy performance of IU behaves worse than that of OU, which is because IU is closer to E and suffers stronger eavesdropping links.
IV-B Joint Beamforming and Power Optimization
(1) Optimizing beamforming with fixed : Based on the derivations above, problem (10) is reduced to
| (36a) | ||||
| (36b) | ||||
| (36c) | ||||
where is a weighted linear combination of , i.e., . Similarly, we introduce the slack variables and satisfying (13) and (14), and thus the constraint (11b) can be transformed into (15), while (36c) can be rewritten as the following linear form
| (37) |
To convexify the rank-one constraints (11f), we can rewrite as (23). As for , we can observe that Lagrangian functions with respect to of problems (24) and (36) possess the same form, which implies that the results in Lemma 2 is also applicable to problem (36). Therefore, problem (36) is reformulated as
| (38a) | ||||
| (38b) | ||||
Note that problem (38) is a convex optimization problem with rank-one penalty terms and can be solved similarly as Algorithm-1, so we omit its algorithm for brevity.
(2) Optimizing transmit power with fixed : With given , problem (10) is reduced into
| (39a) | ||||
| (39b) | ||||
By leveraging Proposition 2, we can derive the optimal transmit power policy in the closed-form expression.
Proposition 3
If problem (39) is feasible, the optimal transmit power under the arbitrary decoding order is given by
| (40) |
Proof:
The objective function of problem (39) is , which is a monotonic increasing function with respect to and . Thus, the minimum objective value is obtained only when constraints (10c) is active while the SIC decoding order constraint (11b) is also satisfied. Accordingly, the optimal transmit power policy can be derived as the results in (40). This completes the proof. ∎
IV-C Overall Algorithm
The overall algorithm is summarized in Algorithm-3, where is introduced to record the maximum SOP of each alternate iteration, while is the pre-defined accuracy of the extended AHB algorithm.
| Algorithm-3: Extended AHB Algorithm for Maximum SOP Minimization |
|---|
| 1: Initialization: Initialize the , and with ; |
| 2: Repeat |
| 3: Solve problem (38) to obtain stationary point solutions with the fixed ; |
| 4: Calculate the optimal solutions according to (40) with the fixed ; |
| 5: Update and set ; |
| 6: Until ; |
By exploiting Proposition 2, it is easy to prove that the proposed extended AHB algorithm in Algorithm-3 is guaranteed to converge to the suboptimal solution over the non-increasing iterations. Moreover, the computational complexity of the overall algorithm is given by , where , and respectively denote the numbers of the alternating iteration, the outer layer iteration, and the inner layer iteration, denotes the number of the optimization variables and denotes the size of the SOC constraint.
| The path loss at the reference distance of 1 meter | ||
|---|---|---|
| The path-loss exponent of the STAR-RIS-BS channel | ||
| The path-loss exponents of the STAR-RIS-users channels | ||
| The noise power at receivers | dBm | |
|
, and |
V Simulation Results
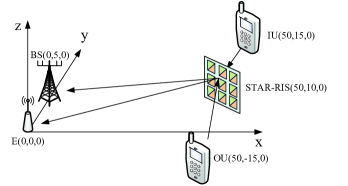
In this section, we provide the numerical results to demonstrate the effectiveness of the proposed algorithms. As shown in Fig. 3, a three-dimensional coordinate network setup is considered, where the BS is located at meter (m), the STAR-RIS is located at m, the E is located at m, while the IU and OU are located at m and m, respectively. The large-scale path loss model is given by , in which denote the path loss at the reference distance m, while and denotes the distance and the path loss exponent between the corresponding transceiver. The main simulation parameters are listed in Table I, and the other parameters are listed in the caption of each simulation figure. Furthermore, each result is the average over independent Monte-Carlo experiments.
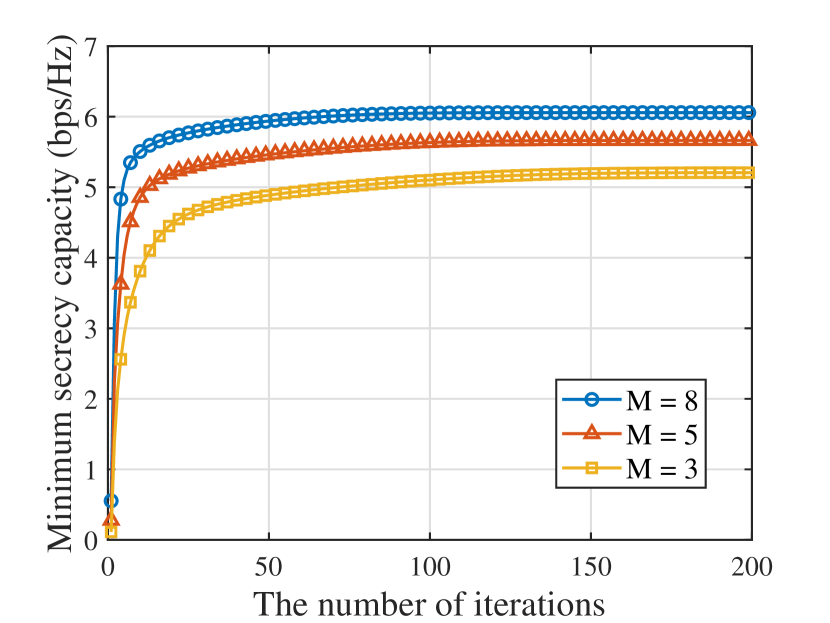
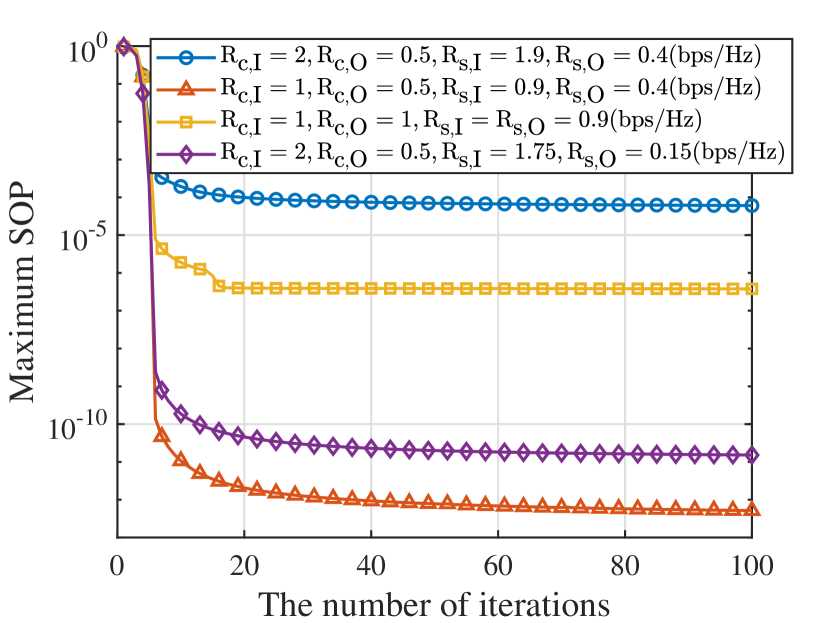
The convergence performances of Algorithm-2 and Algorithm-3 are illustrated in Fig. 5 and Fig. 5, where both two algorithms are guaranteed to converge to the stable solutions over the iterations. In Fig. 5, it can be observed that a larger can achieve a larger minimum secrecy capacity and converge faster. An intuitive explanation to this interesting phenomenon is that: 1) increasing increases the spatial degree-of-freedom (DoF), which provides a more flexible receive beamforming design and achieves better secrecy performance; and 2) although a larger increases the computational complexity of the problem, it improves the optimization degree of each iteration, which helps reduce the number of iterations. It is also observed from Fig. 5 that decreasing the codeword rate and the secrecy rate is conducive to reduce the SOP of the considered network. It is since that decreasing decreases the QoS requirements of IU and OU, which limits the transmit power at the IU/OU, so as to degrade the reception ability of E. Also, a smaller implies that more redundant rate is utilized to confuse E, which thus enhances the secrecy performance of the network.
Fig. 7 and Fig. 7 plot the minimum secrecy capacity and maximum SOP versus the maximal transmit power of IU and OU. To demonstrate the performance of the proposed scheme, we consider the following transmission schemes as the baseline schemes for comparison.
-
•
STAR-RIS-OMA: For the STAR-RIS-OMA scheme, the BS serves IU and OU through the time division multiple access (TDMA) with the assistance of the STAR-RIS.
-
•
C-RIS-NOMA: For the conventional RIS assisted NOMA (C-RIS-NOMA) scheme, we deploy a reflecting-only RIS and a transmitting-only RIS at the same location of the STAR-RIS to serve the IU and OU via the uplink NOMA principle, where each reflecting/transmitting-only RIS is equipped with elements for fairness comparison.
-
•
C-RIS-OMA: For the conventional RIS assisted OMA (C-RIS-OMA) scheme, the BS serves IU and OU via the TDMA with the assistance of a reflecting-only RIS and a transmitting-only RIS.
-
•
Random phase/amplitude: For the random phase/amplitude scheme, we consider to randomly generate the reflection/transmission phase shifts and amplitudes with satisfying and .
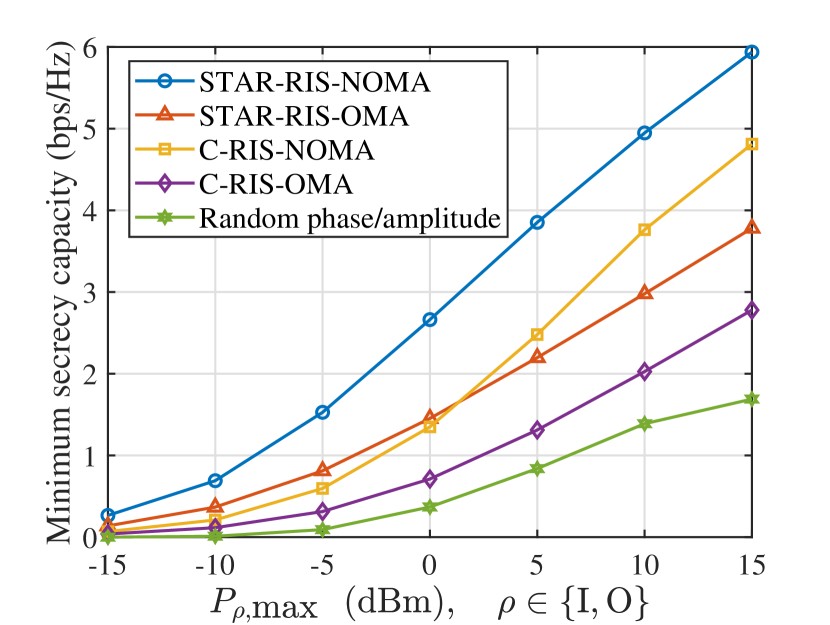
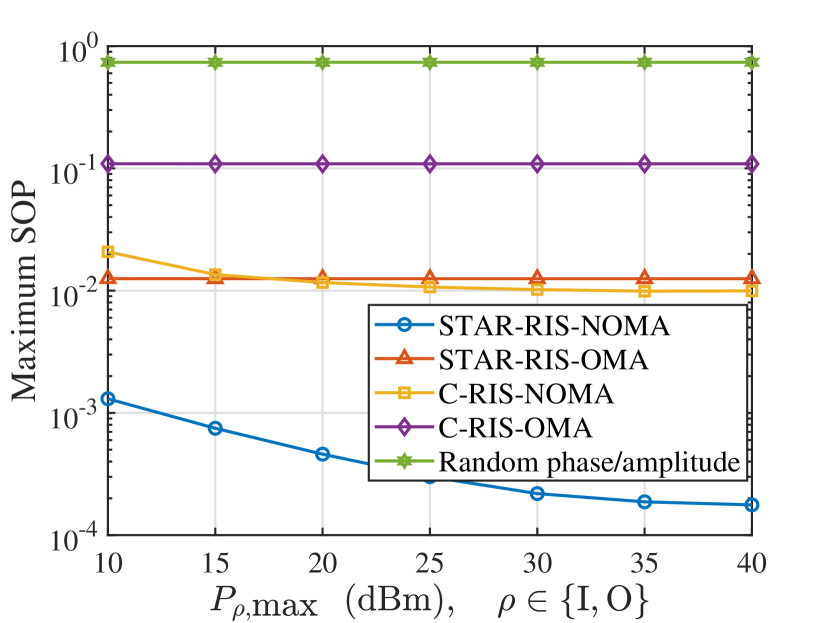
From Fig. 7 and Fig. 7, we can observe that: 1) the STAR-RIS always provides a higher secrecy performance over the conventional RIS; 2) under the same RIS setting, the NOMA transmission outperforms the OMA transmission; and 3) the random phase/amplitude protocol suffers the worst performance in all transmission protocols. The reasons can be explained as follows. Since STAR-RIS can reflect and transmit the signals simultaneously, it is capable of adjusting the legitimate/eavesdropping channels more flexibly via the extra DoF. Also, unlike the conventional RIS employing half number of elements for wireless channel control, STAR-RIS employs all the elements to adaptively balance the legitimate communications and eavesdropping, which further enhances the secrecy performance of the network. On the other hand, NOMA protocol allows IU and OU to transmit their signals with the same time-frequency resource block, thus achieving better performance than OMA. Finally, as the random phase/amplitude protocol cannot unleash the passive gain brought by STAR-RIS, it behaves worst among all the schemes.
Fig. 9 and Fig. 9 illustrate the minimum secrecy capacity and maximum SOP versus the number of the reflection/transmission elements of the STAR-RIS. It can be observed that the secrecy performance achieved by the proposed scheme increases with the increase of , which is because more reflection/transmission elements can provide larger passive beamforming design space for secrecy enhancement. Also can be observed, compared with C-RIS-NOMA, STAR-RIS-OMA achieves the higher secrecy performance in the case of full eavesdropping CSI, but behaves worse in the case of statistical eavesdropping CSI. This is due to the fact that in the case of full eavesdropping CSI, STAR-RIS/C-RIS is able to accurately adjust the eavesdropping channels, and thus, the power-domain multiplexing gains of NOMA take a leading role in the network secrecy enhancement. While in the case of statistical eavesdropping CSI, the transmit power needs to resist the eavesdropping channel uncertainty, so the secrecy performance of the network is dominated by the spatial gains brought by RIS, while STAR-RIS can provide more gains than conventional RIS.
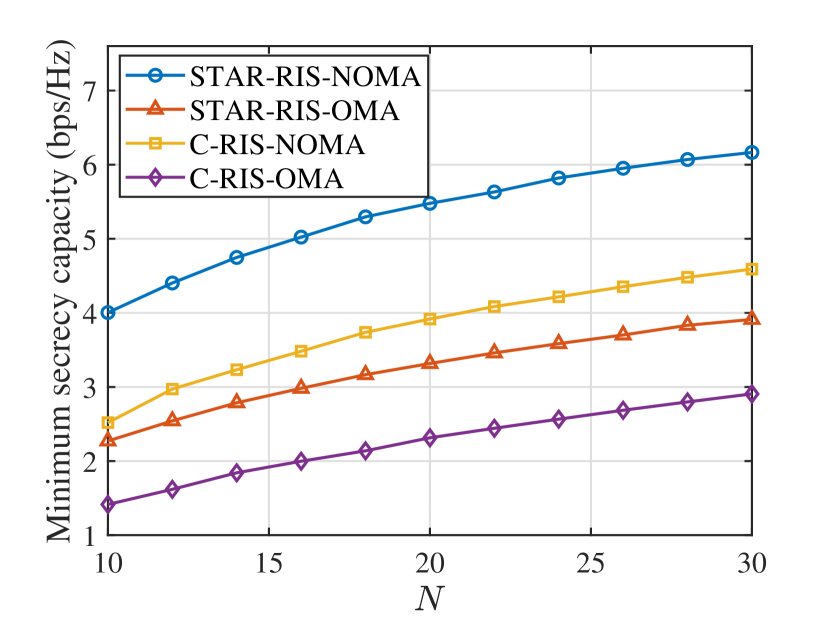
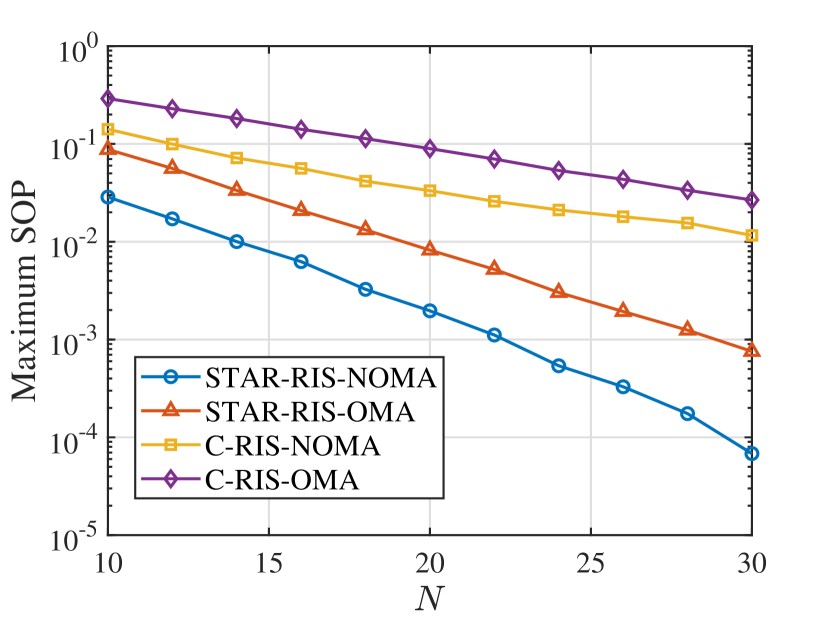
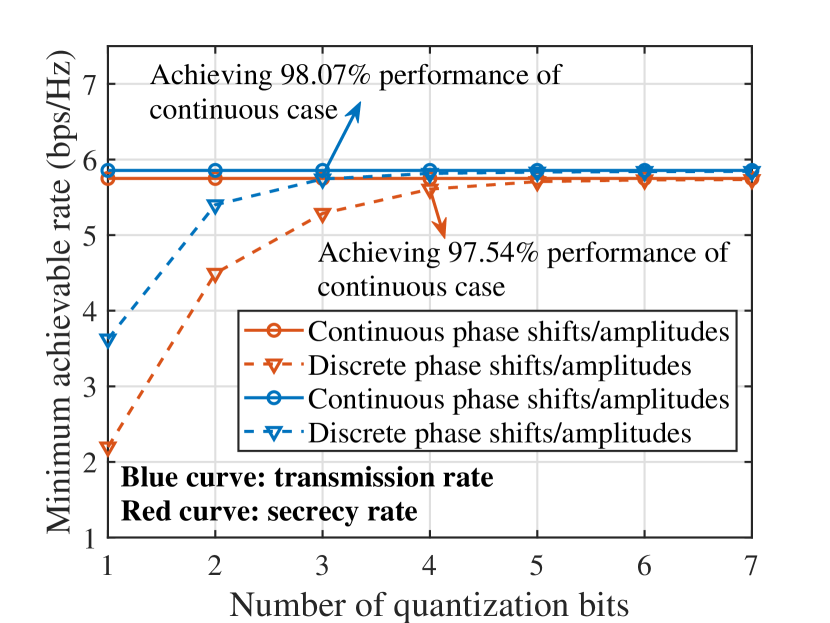
Fig. 11 plots the minimum transmission rate and secrecy rate among IU and OU versus the number of the phase shift/amplitude quantization bits, where the transmission rate denotes the achievable rate without considering eavesdropper, while the quantized phase shift and amplitude are respectively determined as the values in the -bit quantization sets and , with being closest to the corresponding continuous values. It can be observed that even if two dimensions of quantization (i.e., phase shift and amplitude quantization) are considered in the STAR-RIS assisted transmissions, the transmission rate just requires -bit quantization to achieve performance of the continuous phase shifts/amplitudes, while the bits quantized secrecy rate can only achieve performance of the continuous phase shifts/amplitudes. It is explained as 1) for the transmission rate, both phase shifts and amplitudes affect the analog beamforming design at the STAR-RIS, whereas the phase shifts adjustment plays a leading role; while 2) for secrecy rate, STAR-RIS needs to balance the legitimate signal strengthening and wiretap links suppressing, and thus, more accurate phase shifts/amplitudes control is required for secrecy guarantee.
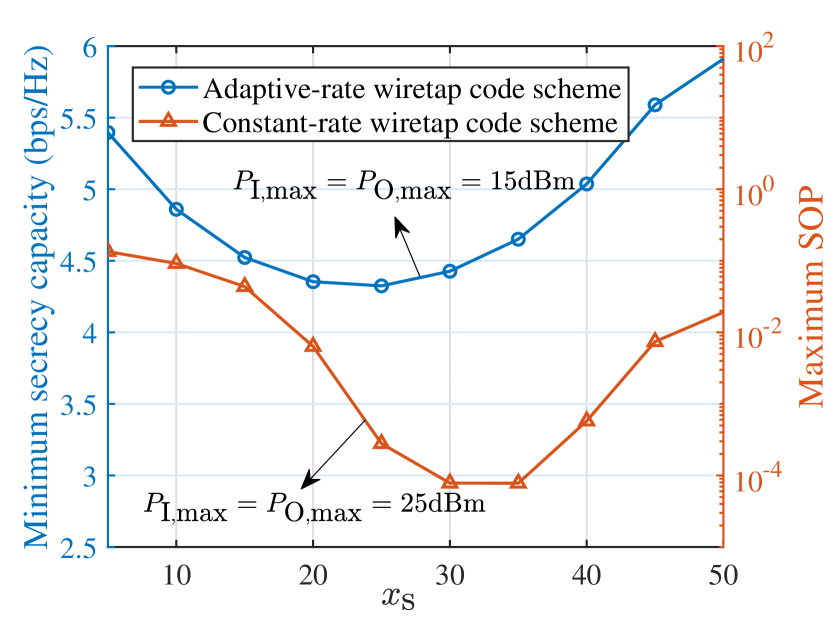
In Fig. 11, we show the minimum secrecy capacity and maximum SOP among IU and OU versus the location of the STAR-RIS, where denotes the abscissa of the STAR-RIS. As can be observed, under the adaptive-rate wiretap code setting, it is better to deploy STAR-RIS near the users or BS for channel strengthening, while under the constant-rate wiretap code setting, it is preferable to deploy STAR-RIS far away from both of them for channel suppressing. It is since that: 1) for the adaptive-rate wiretap code scheme with full eavesdropping CSI, STAR-RIS is able to adjust the legitimate/eavesdropping channels exactly for controlling the codeword rate and redundant rate, which encourages the creation of strong cascaded links for unleashing the space potential of STAR-RIS; while 2) for the constant-rate wiretap code scheme with statistical eavesdropping CSI, STAR-RIS cannot effectively suppress eavesdropping and tends to focus on enhancing legitimate communications, which makes E more sensitive to the STAR-RIS location than BS. Meanwhile, due to the constant codeword rate setting, deploying STAR-RIS near the BS or users for channel strengthening brings no transmission rate increase to legitimate users. Hence, we should artificially deteriorate the cascaded links for the secrecy enhancement.
VI Conclusion
In this paper, a novel uplink transmission framework was proposed, in which STAR-RIS was employed to relay the superimposed signals from IU and OU to the BS while suppressing the malicious eavesdropping. Considering the different eavesdropping CSI assumptions, two joint beamforming optimization problems were respectively formulated for minimum secrecy capacity maximization and maximum SOP minimization. For the full eavesdropping CSI case, an AHB algorithm was proposed, where a polarization identity based two-layer iterative algorithm was developed to optimize the receive and passive beamforming, and the optimal transmit power policy was derived in the closed-form expression. As for the statistical eavesdropping CSI case, the exact SOP expression was derived and a modified AHB algorithm was further designed to minimize the maximum SOP among legitimate users. Numerical results demonstrated the secrecy superiority of the proposed scheme. It was also found that: 1) amplitude quantization had little impact on quantization performance, but the secrecy transmission significantly increased the required quantization resolution; and 2) it was better to deploy STAR-RIS around the users or the BS under the adaptive-rate wiretap code setting for cascaded channel enhancement, while it was preferable to deploy STAR-RIS far away from them for cascaded channel degradation under the constant-rate wiretap code setting.
Appendix A: Proof of Lemma 2
The problem (24) is jointly convex for and meets Slater’s constraint qualification [35]. Therefore, the strong duality holds and the Lagrangian function with respect to can be expressed as
| (A-1) |
where denotes the collection of the terms with no dependence of , while , , and represent the Lagrange multipliers correspondingly. Checking the Karush-Kuhn-Tucker (KKT) conditions of , we list the structure of the optimal as follows
| (A-2a) | |||
| (A-2b) | |||
| (A-2c) | |||
where , , and are the optimal Lagrange multipliers. The KKT condition K3 can be rewritten as
| (A-3) |
where . Here, we show that holds. First, to avoid an unbounded feasible solution space of the dual problem, should be positive. With the KKT condition of , cannot be larger than , i.e., . However, if , we have , i.e., will be a full rank positive definite matrix. In this case, as KKT condition K2 insures that , which however is not the optimal solution. Thus, we know that holds, which implies that is a positive semidefinite matrix with [39]. In this case, we are able to span the null space of by an unit-norm vector , i.e., . Reviewing the KKT condition K2, also lies in the null space of . Thus, the optimal receiving beamforming matrix can be expressed as
| (A-4) |
which completes the proof.
Appendix B: Proof of Proposition 2
In step of Algorithm-2 at the nth iteration, the stationary point solutions are obtained via solving problem (24), which satisfy
| (B-1) |
While in step of Algorithm-2 at the nth iteration, the optimal solutions are obtained according to (31), which meet
| (B-2) |
Combining the above inequalities, it can be readily obtained that
| (B-3) |
Meanwhile, is continuous over the compact feasible set of problem (8) [35], so the upper bound of the objective value is limited by a finite positive number, which proves the convergence of AHB algorithm. Moreover, since the optimization variables and restrict and influence each other in the alternating iterations, the converged solutions are usually some suboptimal solutions [41].
References
- [1] M. Di Renzo, A. Zappone, M. Debbah, M.-S. Alouini, C. Yuen, J. de Rosny, and S. Tretyakov, “Smart radio environments empowered by reconfigurable intelligent surfaces: How it works, state of research, and road ahead,” IEEE J. Sel. Areas Commun., vol. 38, no. 11, pp. 2450–2525, Nov. 2020.
- [2] Q. Wu and R. Zhang,“Towards smart and reconfigurable environment: Intelligent reflecting surface aided wireless network,” IEEE Commun. Mag., vol. 58, no. 1, pp. 106–112, Jan. 2020.
- [3] Q. Wu and R. Zhang, “Intelligent reflecting surface enhanced wireless network via joint active and passive beamforming,” IEEE Trans. Wireless Commun., vol. 18, no. 11, pp. 5394–5409, Nov. 2019.
- [4] Q. Wu and R. Zhang, “Beamforming optimization for wireless network aided by intelligent reflecting surface with discrete phase shifts,” IEEE Trans. Commun., vol. 68, no. 3, pp. 1838–1851, Mar. 2020.
- [5] Q. Wu, S. Zhang, B. Zheng, C. You, and R. Zhang, “Intelligent reflecting surface aided wireless communications: A tutorial,” IEEE Trans. Commun., vol. 69, no. 5, pp. 3313–3351, May. 2021.
- [6] Y. Liu, X. Mu, J. Xu, R. Schober, Y. Hao, H. V. Poor, and L. Hanzo, “STAR: Simultaneous transmission and reflection for 360∘ coverage by intelligent surfaces,” IEEE Wireless Commun., (Accept to appear), 2021, [Online]. Available: http://arxiv.org/abs/2103.09104
- [7] X. Mu, Y. Liu, L. Guo, J. Lin, and R. Schober, “Simultaneously transmitting and reflecting (STAR) RIS aided wireless communications,” IEEE Trans. Wireless Commun., doi: 10.1109/TWC.2021.3118225.
- [8] J. Xu, Y. Liu, X. Mu, and O. A. Dobre, “STAR-RISs: Simultaneous transmitting and reflecting reconfigurable intelligent surfaces,” IEEE Commun. Lett., vol. 25, no. 9, pp. 3134–3138, Sep. 2021.
- [9] NTT DOCOMO, “DOCOMO conducts world’s first successful trial of transparent dynamic metasurface,” Jan. 2020. [Online]. Available: https://www.nttdocomo.co.jp/english/info/media_center/pr/2020/0117_00.html.
- [10] C. Pfeiffer and A. Grbic, “Metamaterial Huygens’ surfaces: Tailoring wave fronts with reflectionless sheets,” Phys. Rev. Lett., vol. 110, no. 19, pp. 197401, 2013.
- [11] L. Lv, J. Chen, Q. Ni, Z. Ding, and H. Jiang, “Cognitive non-orthogonal multiple access with cooperative relaying: A new wireless frontier for 5G spectrum sharing,” IEEE Commun. Mag., vol. 56, no. 4, pp. 188–195, Apr. 2018.
- [12] C. Wu, Y. Liu, X. Mu, X. Gu, and O. A. Dobre, “Coverage characterization of STAR-RIS networks: NOMA and OMA,” IEEE Commun. Lett., vol. 25, no. 9, pp. 3036–3040, Sep. 2021.
- [13] W. Ni, Y. Liu, Y. C. Eldar, Z. Yang, and H. Tian, “STAR-RIS enabled heterogeneous networks: Ubiquitous NOMA communication and pervasive federated learning,” [Online]. Available: https://arxiv.org/abs/2106.08592
- [14] J. Zuo, Y. Liu, Z. Ding, L. Song, and H. V. Poor, “Joint design for simultaneously transmitting and reflecting (STAR) RIS assisted NOMA systems,” [Online]. Available: https://arxiv.org/abs/2106.03001
- [15] T. Hou, J. Wang, Y. Liu, and X. Sun, “A jointly design for STAR-RIS enhanced NOMA-CoMP networks: A simultaneously-signal-enhancement-and-cancellation-based (SSECB) design,” [Online]. Available: https://arxiv.org/abs/2105.00404
- [16] Z. Xie, W. Yi, X. Wu, Y. Liu, and A. Nallanathan, “STAR-RIS aided NOMA in multi-cell networks: A general analytical framework with gamma distributed channel modeling,” [Online]. Available: https://arxiv.org/abs/2108.06704
- [17] A. D. Wyner, “The wire-tap channel,” Bell Syst. Tech. J., vol. 54, no. 8, pp. 1355–1387, Oct. 1975.
- [18] Y. Liu, Z. Qin, M. Elkashlan, Y. Gao, and L. Hanzo, “Enhancing the Physical Layer Security of Non-orthogonal Multiple Access in Large-scale Networks,” IEEE Trans. Wireless Commun., vol. 16, no. 3, pp. 1656–1672, Mar. 2017.
- [19] M. Cui, G. Zhang, and R. Zhang, “Secure wireless communication via intelligent reflecting surface,” IEEE Wireless Commun. Lett., vol. 8, no. 5, pp. 1410–1414, Oct. 2019.
- [20] X. Guan, Q. Wu, and R. Zhang, “Intelligent reflecting surface assisted secrecy communication: Is artificial noise helpful or not?,” IEEE Wireless Commun. Lett., vol. 9, no. 6, pp. 778–782, Jun. 2020.
- [21] L. Dong and H. -M. Wang, “Enhancing secure MIMO transmission via intelligent reflecting surface,” IEEE Trans. Wireless Commun., vol. 19, no. 11, pp. 7543–7556, Nov. 2020.
- [22] Z. Zhang, L. Lv, Q. Wu, H. Deng, and J. Chen, “Robust and secure communications in intelligent reflecting surface assisted NOMA networks,” IEEE Commun. Lett., vol. 25, no. 3, pp. 739–743, Mar. 2021.
- [23] Z. Zhang, J. Chen, Q. Wu, Y. Liu, L. Lv, and X. Su, “Securing NOMA networks by exploiting intelligent reflecting surface,” [Online]. Available: https://arxiv.org/abs/2104.03460
- [24] H. Niu, Z. Chu, F. Zhou, and Z. Zhu, “Simultaneous transmission and reflection reconfigurable intelligent surface assisted secrecy MISO networks,” IEEE Commun. Lett., doi: 10.1109/LCOMM.2021.3109164.
- [25] V. Havary-Nassab, S. Shahbazpanahi, and A. Grami, “Joint receive-transmit beamforming for multi-antenna relaying schemes,” IEEE Trans. Signal Process., vol. 58, no. 9, pp. 4966–4972, Sep. 2010.
- [26] R. Long, Y. -C. Liang, Y. Pei, and E. G. Larsson, “Active reconfigurable intelligent surface aided wireless communications,” IEEE Trans. Wireless Commun., doi: 10.1109/TWC.2021.3064024.
- [27] X. Guan, Q. Wu, and R. Zhang, “Anchor-assisted channel estimation for intelligent reflecting surface aided multiuser communication,” [Online]. Available: http://arxiv.org/abs/2102.10886
- [28] L. Yang, J. Chen, H. Jiang, S. A. Vorobyov, and H. Zhang, “Optimal relay selection for secure cooperative communications with an adaptive eavesdropper,” IEEE Trans. Wireless Commun., vol. 16, no. 1, pp. 26–42, Jan. 2017.
- [29] M. Bloch, J. Barros, M. R. D. Rodrigues, and S. W. McLaughlin, “Wireless information-theoretic security,” IEEE Trans. Inf. Theory., vol. 54, no. 6, pp. 2515–2534, Jun. 2008.
- [30] Z. Ding, R. Schober, and H. V. Poor, “On the impact of phase shifting designs on IRS-NOMA,” IEEE Wireless Commun. Lett., vol. 9, no. 10, pp. 1596–1600, Oct. 2020.
- [31] X.-D. Zhang, Matrix Analysis and Applications. Cambridge, U.K.: Cambridge Univ. Press, 2017.
- [32] A. Beck, A. Ben-Tal, and L. Tetruashvili, “A sequential parametric convex approximation method with applications to nonconvex truss topology design problems,” J. Global Optim., vol. 47, no. 1, pp. 29–51, May. 2010.
- [33] T. Jiang and Y. Shi, “Over-the-air computation via intelligent reflecting surfaces,” in Proc. IEEE Global Commun. Conf. (GLOBECOM), Waikoloa, HI, USA, Dec. 2019, pp. 1–6.
- [34] W. Dinkelbach, “On nonlinear fractional programming,” Manage. Sci., vol. 13, no. 7, pp. 492–498, Mar. 1967. [Online]. Available: http://www. jstor.org/stable/2627691
- [35] S. Boyd and L. Vandenberghe, Convex Optimization. Cambridge, UK: Cambridge Univ., 2004.
- [36] Q. T. Dinh and M. Diehl, “Local convergence of sequential convex programming for nonconvex optimization,” Recent Advances in Optimization and its Applications in Engineering, Springer, 2010.
- [37] A. Ben-Tal and A. Nemirovski, Lectures on Modern Convex Optimization: Analysis, Algorithms, and Engineering Applications. Philadelphia, PA, USA: SIAM, 2001.
- [38] M. Lobo, L. Vandenberghe, S. Boyd, and H. Lebret, “Applications of second-order cone programming,” Linear Algebra and its Applications, vol. 284, pp. 193–228, 1998.
- [39] D. Xu, X. Yu, Y. Sun, D. W. K. Ng, and R. Schober, “Resource allocation for IRS-assisted full-duplex cognitive radio systems,” IEEE Trans. Commun., vol. 68, no. 12, pp. 7376–7394, Dec. 2020.
- [40] B. Ning, Z. Chen, W. Chen, and J. Fang, “Beamforming optimization for intelligent reflecting surface assisted MIMO: A sum-path-gain maximization approach,” IEEE Wireless Commun. Lett., vol. 9, no. 7, pp. 1105–1109, Jul. 2020.
- [41] J. C. Bezdek and R. J. Hathaway, “Convergence of alternating optimization,” Neural, Parallel & Scientific Computations, vol. 11, no. 4, pp. 351–368, 2003