Precoding and Transmit Antenna Subarray Selection for Secure Hybrid Spatial Modulation
Abstract
Spatial modulation (SM) is a particularly important form of multiple-input-multiple-output (MIMO). Unlike traditional MIMO, it uses both modulation symbols and antenna indices to carry information. In this paper, to avoid the high cost and circuit complexity of fully-digital SM, we mainly consider the hybrid SM system with a hybrid precoding transmitter architecture, combining a digital precoder and an analog precoder. Here, the partially-connected structure is adopted with each radio frequency chain (RF) being connected to a transmit antenna subarray (TAS). In such a system, we made an investigation of secure hybrid precoding and transmit antenna subarray selection (TASS) methods. Two hybrid precoding methods, called maximizing the approximate secrecy rate (SR) via gradient ascent (Max-ASR-GA) and maximizing the approximate SR via alternating direction method of multipliers (Max-ASR-ADMM), are proposed to improve the SR performance. As for TASS, a high-performance method of maximizing the approximate SR (Max-ASR) TASS method is first presented. To reduce its high complexity, two low-complexity TASS methods, namely maximizing the eigenvalue (Max-EV) and maximizing the product of signal-to-interference-plus-noise ratio and artificial noise-to-signal-plus-noise ratio (Max-P-SINR-ANSNR), are proposed. Simulation results will demonstrate that the proposed Max-ASR-GA and Max-ASR-ADMM hybrid precoders harvest substantial SR performance gains over existing method. For TASS, the proposed three methods Max-ASR, Max-EV, and Max-P-SINR-ANSNR perform better than existing leakage method. Particularly, the proposed Max-EV and Max-P-SINR-ANSNR is low-complexity at the expense of a little performance loss compared with Max-ASR.
Index Terms:
Spatial modulation, hybrid precoding, physical layer security, secrecy rate, transmit antenna subarray selectionI Introduction
As an essential key technique for future generation wireless communications like 6G and WiFi 7, multiple-input-multiple-output (MIMO) has obtained a continuous extensive and intensive huge amount of research activities from the end of the last century, which can greatly improve the system performance in wireless communications. Two typical forms of MIMO are bell laboratories layer space-time (BLAST) in[1] and space time coding (STC) in [2]. They make their effort to strike a good balance between spatial multiplexing and diversities in MIMO systems. However, as the third form of MIMO, spatial modulation (SM) is attracting more and more research attention from industry and academia due to its advantages of no inter-channel interference (ICI) and inter-antenna synchronization (IAS) [3]. It works by mapping a block of information bits into two information-carrying units. The first information carrying unit is a amplitude/phase modulation (APM) symbol chosen from the signal-constellation diagram. The second information-carrying unit is a transmit antenna index chosen, while other transmit antennas are not activated[4, 3, 5].
There are several ways to improve the performance of SM including transmit antenna selection[6, 7, 8], linear precoding [9, 10], power allocation[11, 12] and so on. The physical layer security of conventional SM is an urgent problem. The authors in [13] focused their attention on the secrecy behavior of SSK and SM, and derived the expression for secrecy rate (SR). In [14], the secrecy performance of SM was improved by making a combination of useful signal and jamming against unknown eavesdropping, and the corresponding SR performance is analyzed. The authors in [15] redefined the transmit antenna indices from the viewpoint of channel state information (CSI) to prevent eavesdropping by assuming that the imperfect legal CSI is available for the eavesdropper. Then, a full-duplex receiver assisted secure spatial modulation scheme was proposed in [16]. Here, jamming signals are designed to protect legitimate receivers from self-interference (SI) and to interfere eavesdroppers. Besides, in [17], the authors proposed two secure transmit antenna selection procedures, which can achieve a better secrecy performance. The problem of power allocation (PA) between confidential message and artificial noise (AN)[18, 19] was addressed in [11]. And the authors in[11, 12] have proposed two PA strategies with performance approaching that of the optimal PA factor.
It is very important to study the security of multiple-antenna communication systems[20, 21, 22, 23, 24]. Furthermore, the security of SM systems is also very important. The precoding schemes of traditional SM can also be generalized to secure SM. For most conventional PSM schemes, the antenna indices at receiver is utilized to carry bits rather than the antenna indices of the transmitter as spatial bits. The optimization of the precoding matrix at transmitter is to address the issues of preprocessing and detection of PSM signals at receiver in order to improve bit-error-rate (BER) performance [10]. However, the authors in [25] have proposed a time-varying precoder for the secret PSM (SPSM), which generated a time-varying interference to the eavesdropper and retains all advantages of PSM at the legal receiver. Then they also derived the upper bounds for BERs at legal receiver and eavesdropper in the massive MIMO systems in [26], and designed a precoder by jointly minimizing the receive power at eavesdropper and maximizing the receive power at legal receiver in [27]. The kind of PSM is also extended to secure multiuser MIMO downlink scenario by introducing a scrambling matrix to disturb the eavesdropper[28].
Until now, we make a literature review about fully-digital (FD) SM. However, as the number of transmit antennas tends to medium-scale or large-scale, the circuit cost and complexity will become a burden on SM. To deal with this problem, hybrid SM, combining hybrid MIMO structure in [29, 30] and SM, emerges as the times require[31, 32, 33, 34, 35, 36, 37]. It could make a good balance among cost, complexity and performance.
In the case of hybrid partially-connected architecture, the total antenna array is divided into multiple transmit antenna subarrays (TASs) with each being connected to single RF chain. Thus, the spatial bits can be carried by selecting the indices of TASs rather than those of transmit antennas. However, there were several papers focusing on hybrid SM. The hybrid SM was first proposed in [31]. But in [31], it actually used analog precoding, and its digital precoder was replaced by the process of TAS selection (TASS) in SM. Besides, hybrid SM was also extended to the multi-user scenario in [32], which showed that the hybrid SM system with hybrid beamforming at transmitter and digital combining at the receiver can achieve an excellent BER performance.
The authors in [33] made an investigation of the macro SM, in which the indexes of the small base stations were used to carry information bits and they also proposed a low-complexity detection method. A multimode hybrid precoder is designed for proposed analog precoding-aided virtual SM and obtain BER performance gain compared with the conventional precoding-aided MIMO systems[34].
For hybrid generalized SM (GSM), in [35], an analog precoder of maximizing spectrum efficiency (SE) was designed with the verified superiority in SE performance. In [36], the digital and analog precoders by turbo optimization was proposed for hybrid GSM systems to improve its SE performance. Furthermore, in [37], the closed-form expression of the achievable SE lower bound of was derived firstly. Then, via exploiting the concavity of the SE expression in digital precoding vectors, the digital precoding vectors were computed, the convex relaxation was invoked to handle the non-convex constraints of analog precoding, and the corresponding problem of analog precoding was converted into a convex optimization problem. Finally, the designed digital and analog precoding schemes harvested higher SE gains over existing methods.
In this paper, several techniques in this paper will be developed to improve the secrecy performance of hybrid SM as follows: TASS, digital precoding for confidential message (CM), AN projection, and analog precoding. Our main contributions are summarized as follows:
-
1.
A hybrid secure SM system model is established, where the transmitter is equipped with the partially-connected architecture, and the desired receiver and eavesdropping receiver are equipped with fully digital architecture. Since each RF chain is connected to a TAS in the partially-connected architecture, the spatial bits are carried by activating the TAS rather than a single transmit antenna, while the APM symbols are transmitted by the active TAS. Each TAS carries single bit stream by using multiple antennas. This will create spatial diversity and will be exploited to improve the secure performance of SM. In addition, with the help of AN interfering with the eavesdropper, the useful signal is sent along the desired subspace to further improve the security of this system.
-
2.
To improve the secrecy performance, two hybrid precoding methods, maximizing the approximate SR (ASR) based on the gradient ascent (Max-ASR-GA) and maximizing the approximate SR (Max-ASR) based on alternating direction method of multipliers (Max-ASR-ADMM), are proposed. Due to the fact that there is no closed-form expression of SR, an ASR expression is presented for hybrid precoding design. The proposed Max-ASR-ADMM method can be expressed as a general form consensus problem, which can be addressed by exiting ADMM. Simulation results show that the SR performance of the proposed Max-ASR-GA is better than conventional hybrid precoding method: SDR-AltMin and the proposed Max-ASR-ADMM. In particular, the proposed Max-ASR-ADMM has a better SR performance than SDR-AltMin in the medium and high regions.
-
3.
Generally, the number of TASs is not a power of two, so TASS is required. In order to improve the secrecy performance, three secure TASS schemes are proposed. Maximizing approximate SR (Max-ASR) TASS method is proposed to consider the effect of the above two factors on secrecy performance. To reduce the complexity of Max-ASR, the maximizing the eigenvalue (Max-EV) TASS method and the maximizing the product of signal-to-interference-plus-noise ratio and artificial noise-to-signal-plus-noise ratio (Max-P-SINR-ANSNR) are proposed as two low complexity methods. Since each TAS corresponds to a sub-channel, it can achieve a good rate performance by choosing the TASs corresponding to the sub-channels with large channel gains. The eigenvalues of each sub-channel are sorted in order and the corresponding TASs of the sub-channels with large eigenvalues are used. The proposed Max-EV performs slightly better than the proposed Max-P-SINR-ANSNR in the medium and high SNR regions with the same complexity as the latter in terms of SR. The proposed Max-ASR harvests a substantial SR performance gain over Max-EV and Max-P-SINR-ANSNR.
II System Model
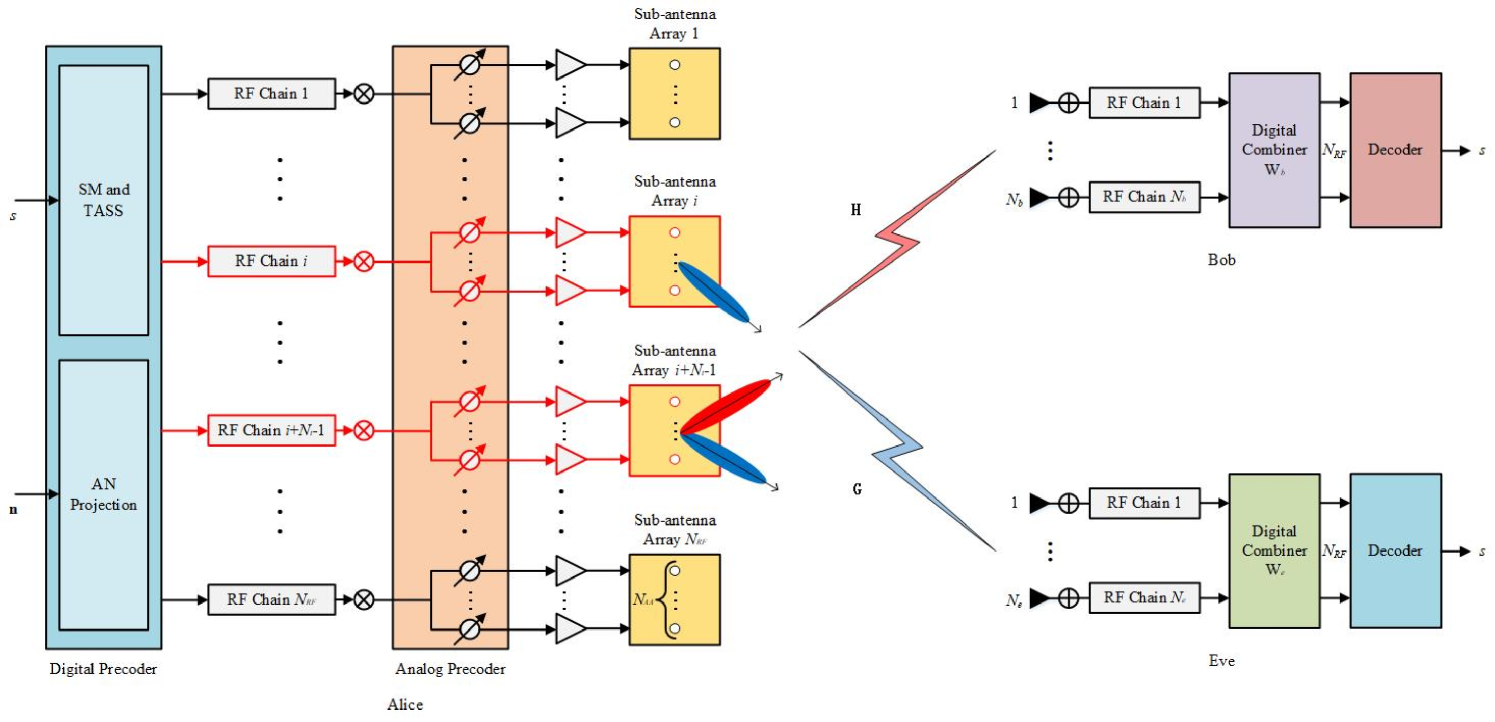
Consider a system of hybrid SM as shown in Fig. 1, where the transmitter (Alice) is equipped with RF chains with each having antennas to transmit one data stream to the legitimate receiver (Bob) equipped with antennas and RF chains. There is an eavesdropper (Eve) with antennas and RF chains trying to eavesdrop on the data stream from Alice to Bob. Alice uses the hybrid sub-connected structure, while Bob and Eve use fully digital structure, namely and .
Now, we extend conventional SM to hybrid structure transmitters in MIMO systems. Therefore, in Fig. 1 system, the first part information bits are used to choose one of TASs and the second part information bits are mapped to the modulation symbol. In what follows, it is assumed that due to the reason that the number of TASs is confined to a power of two. Let be the legitimate TAS subset, where the element is selected from set . A proper TASS strategy can clearly improve system performance. is the set of enumerations of all possible combinations of TAS subsets . The modulation symbol first experiences the digital precoder and then passes through the RF chain connected by the active TAS. Considering the security of communication, AN is needed to disturb the eavesdropper as an efficient secure tool. AN is also projected in digital precoding stage. After the precoded CM plus the projected AN passing the corresponding RF chains,and the phase shifters (PSs) of analog precoding and AN. Finally, the transmit signal is in the following form
| s | ||||
| (1) |
where is the digital symbol chosen from the -ary constellation for , and satisfies . is a block diagonal matrix, and its -th sub-block is the identity matrix, that is, , which means that the -th TAS is activated with . is a block diagonal TASS matrix similar to , where for all , and the other sub-blocks are all-zero matrix, which means that TASs are selected. Since there are Q combinations for , i.e., there are Q possibilities of T, which can be expressed as . is the AN vector, and is the power allocation factor between CM and AN. is the transmit power. And the digital precoding matrix of CM is given by
| (2) |
and is the digital projection matrix of AN, also called the AN precoding matrix. Since only TASs are selected from TASs to work, and the AN n is only projected to the selected TASs, so only has the corresponding rows with non-zero vectors and the remaining rows are all 0. After passing through the corresponding RF chain, the precoded CM plus AN from each RF chain is delivered to the corresponding PSs to perform the corresponding analog precoding. This process can be denoted by the analog precoding matrix as follows
| (3) |
where is the th analog weighting vector for , and all its elements have the same amplitude but distinct phases. Therefore, can be expressed as
| (4) |
where , and . The associated transmit vector after precoding and TASS can be expressed as
| (5) |
where is the modulation symbol after hybrid precoding, and denotes the index of the activated TAS. The received signals at Bob and Eve can be represented as
| (6) |
| (7) |
where is the channel matrix of Alice-to-Bob which can be thought as and is the channel matrix from TAS to Bob. is the channel matrix from Alice to Eve and G can be given by and is the channel matrix from the th TAS to Eve. and denote the complex additive white Gaussian noise (AWGN) vectors at Bob and Eve, respectively. Thus, the received signals observed at Bob and Eve after decoding processing can be respectively formulated as follows
| (8) |
| (9) |
where is the combiner of Bob. It can be expanded as , and . is the combiner of Eve, and , where .
The maximum-likelihood (ML) detector at Bob is given by
| (10) |
The average SR is given as
| (11) |
where
| (12) |
| (13) |
where , , , and ,
| (14) |
| (15) |
and , where , , , and are the possible transmit vectors. and are the covariance matrices of interference plus noise of Bob and Eve respectively, where
| (16) |
| (17) |
with
| (18) |
| (19) |
respectively. Since and are adopted to whiten colored noise into an white noise, they don’t change the mutual information, that is, and .
In addition, to facilitate the hybrid precoding design, is chosen to be the projection matrix in the null space of channel H, satisfying . Therefore,
| (20) |
where is the channel matrix corresponding to the selected subchannels . Due to the relation , once is determined, so can be obtained readily.
The analog precoding corresponding to the selected channel is expressed as
| (21) |
And the digital precoding matrix corresponding to the selected channel is and satisfies , where S is the selection matrix, and the -th column of S is the -th column of .
Therefore, . Let us define , can be given by
| (22) |
where is the normalized factor. According to the power constraint at transmit side, and considering , then we have and . Therefore, we obtain the digital precoder of AN. is the Moore-Penrose pseudo inverse of A.
III Proposed Hybrid Precoding methods
For hybrid SM systems, the design of hybrid precoder at Alice and combiner at Bob is very important to improve the system performance. In this section, the approximate expression of SR is derived by using the definition of cut-off rate in [38]. Then, two hybrid precoders, called Max-ASR-ADMM and Max-ASR-GA, are proposed to enhance the security of SM systems. Additionally, the SDR-AltMin Algorithm in [39] is also extended to be suitable for hybrid SM and used as a performance reference.
III-A Approximate expression of SR
In accordance with the definition of the cut-off rate for traditional MIMO systems in [38], we have the cut-off rate for Bob
| (23) |
For a given channel H, assuming the receive signal is a complex Gaussian distribution, and the corresponding conditional probability is
| (24) |
where and . Making use of (24), we have
| (25) |
which can be derived similar to Appendix A in [38] with a slight modification. Similarly, the cut-off rate for Eve is given by
| (26) |
Since the ASR can be expressed as , the optimization problem of maximizing ASR can be casted as
| (27) | ||||
where is the total precoding matrix, and
| (28) |
where
| (29) | ||||
| (30) |
where , where and are randomly chosen from the set of all possible combinations of x shown in (5).
III-B Proposed Max-ASR-ADMM
Observing the expression of P in (4), we find only one precoding corresponding to the active TAS of the hybrid precoding matrix P is non-zero in the actual communication process, so is at most two subarrays with non-zero values, which means that P is sparse in the actual process of maximizing the SR. For such a high-dimensional but sparse optimization problem, the data of the optimization problem can be segmented and then transformed into a general form consensus problem, which can be solved by using ADMM. With that in mind, the expression in (29) can be further simplified as follows
| (31) | ||||
| (32) | ||||
| (33) |
where
| (36) |
is the precoders corresponding to those activated TASs.
| (39) |
where
| (40) |
is the channel matrix corresponding to those activated TASs.
| (43) |
is the sending symbol, where
| (46) |
is the Kronecker product of two matrices. The above simplification addresses the problem that it is hard to solve the precoding matrix P due to its high-dimensional and sparse characteristic. The derivation from (31) to (33) is achieved by utilizing the trace property, i.e., for matrices A and B.
Similarly, for Eve, can be simplified to
| (47) |
where
| (50) |
| (51) |
is the channel matrix corresponding to those activated TASs.
By using the Jensen’s inequality, the lower bound of is
| (52) | |||
| (53) |
which yields the following optimization problem
| (54) | ||||
Let us define the following function
| (55) |
then, the optimization problem in (54) reduces to a general form consensus problem
| subjectto | ||||
| (56) |
where are functions of P, , and assign the precoding of each TAS to the corresponding position in the precoding matrix P. , , , , and the rest of is zero.
The above general form consensus problem can be solved by ADMM [40]. Let us introduce a new matrix variable , then we obtain the equivalence of (III-B) as follows
| (57) |
Taking the above expression to replace the loss function in (III-B) and introduce dual variables , we have the alternating iterative process of ADMM including three main expressions
| subjectto | (60) | |||
| (61) |
and
| (62) |
where . The third term of (III-B) is the penalty term. Variable P in (61) deals with the global variable P and is also called the central collector or the fusion center. By introducing matrix , the optimization problem in (III-B) is converted into a convex semidefinite programming (SDP) problem, which can be solved conveniently by using convex optimization toolbox CVX. Then, let as the analog precoder of the -th TAS and as the digital precoder of the -th TAS. Now, we complete the design of hybrid precoding. Therefore, a step-by-step summary is provided as follows: Algorithm 1.
III-C Proposed Max-ASR-GA
In the previous section, the Max-ASR-ADMM algorithm is presented to optimize the secure hybrid precoding matrices. For the comparison of the secrecy performance and to offer a new solution to this non-convex optimization problem, we propose another secure hybrid precoding scheme, namely Max-ASR-GA, in what follows. To maximize , the Max-ASR-GA method can be employed to directly optimize the precoding matrix P. The gradient vector of with respect to P can be derived as
| (63) | ||||
where
| (64) |
and
| (65) |
Let , then is the derivatives of with respect to P, which hold due to the fact that
| (66) |
| (67) |
and
| (68) |
In order to find a locally optimal P, we first initialize P and , solve the gradient , and adjust P according to . The value of P is updated according to the following iterative formula
| (69) |
Then, obtain , update P or step size according to the difference between before and after , and repeat the above steps until the termination condition is reached. The steps of this algorithm are summarized as shown in Algorithm 2.
III-D Extended SDR-AltMin
The SDR-AltMin algorithm in [39] is specially constructed for traditional hybrid MIMO systems with partially connected structure. Below, we extend it to the hybrid SM systems. In terms of [39], the optimization problem of digital and analog hybrid precoder matrices can be casted as
| (72) |
where is the optimal FD precoder in terms of singular value decomposition (SVD) criterion, that is, the first right singular vector of H, so . is the feasible set of the analog precoder , which is a block diagonal matrix satisfying (3). Therefore, the power constraint in (III-D) can be rewritten as . Here, the power constraint of can ensure that the expected power constraint of each TAS is 1.
Once is known, can be obtained by
| (73) |
Once is known, the digital precoder design problem can be converted into a SDP problem as follows
| (77) |
where is the set of -dimensional complex hermitian matrices, with an auxiliary variable and ,
| (78) |
| (79) |
and
| (80) |
The optimization problem in (III-D) can be solved by standard convex optimization techniques. Via alternate iteration between (III-D) and (III-D), the corresponding digital precoding and analog precoding matrices can be obtained.
At Bob, as shown in Fig. 1, the multiple-antenna receiver of Bob is fully digital structure. To fully exploit the receive spatial diversity gain, the receive beamforming or combiner is required. Similar to the SVD precoder at transmitter, here the receive combiner is designed as , where . is the first left singular vector of for . To harvest a high channel gain, can be set to be Bob’s combiners for the th TAS, so . Therefore, the receive beamforming vector at Bob is
| (81) |
Until now, we complete the design of all precoder schemes and receive beamformer. In particular, the receive beamforming vector in (81) will be adopted at legitimate receiver in this paper regardless of the kind of precoders and TASSs.
IV Proposed Transmit Antenna Subarray Selection Methods
In traditional SM systems, transmit antenna selection is an important technique to improve the system performance. For hybrid SM, TAS evolves towards TASS. In this section, three TASS methods are proposed for secure hybrid SM systems: Max-EV, Max-ASR, and Max-P-SINR-ANSNR TASS methods. At the same time, the leakage-based TASS method for traditional SM systems in [17] can also be extended to hybrid SM systems.
IV-A Proposed Max-P-SINR-ANSNR
Considering AN is viewed as the useful signal of Eve, the SINR at Eve is defined as ANSNR. If the product of SINR at Bob and ANSNR at Eve is maximized, it is guaranteed that at least one of SINR at Bob and ANSNR at Eve or both is high. This will accordingly improve the SR performance. Since SINR and ANSNR is related to the TASS matrix T, the AN is only projected onto the TAS selected by TASS. In order to facilitate the design, we still assume that each TAS only send AN at the beginning, and then the SINR at Bob and ANSNR at Eve with activated TAS at can be expressed as
| (82) |
and
| (83) |
respectively, where . Both and need to increase. Thus, if we multiply and , their product will form a maximum value at some TASS. Taking the logarithm of their product yields
| (84) | ||||
Observing (IV-A), we can find that maximizing their product is approximately equivalent to maximizing the SR. Therefore, the product of SINR and ANSNR corresponding to each TAS can be obtained independently, and the first largest products are selected as candidates. It can be expressed as
| (85) |
Then, we sorts in a descending order
| (86) |
where is a permutation of . The TASs corresponding to the former are selected as TASs to transmit SM information.
IV-B Proposed Max-EV
In general, a high channel gain corresponds to a good quality of channel, and to achieve a high transmission rate. Therefore, selecting transmit antennas with high channel gains chosen from Alice to Bob can substantially enhance the performance of the system. Before selecting the activated TAS by spatial bits, Alice performs SVD on the channel matrix firstly, as , and is the maximum singular value of . is the first column of , i.e., the associated right singular vector of for . And is the first column of , i.e., the corresponding left singular vector of for .
The maximum singular value means the largest channel gain, i.e., the best quality of channel. Therefore, Alice sorts in a descending order and renames them as: , ,, ,, . Therefore, can be represented as follows
| (87) |
where
| (88) |
and
| (89) |
The former subchannels in (87) are selected to transmit information. We map the spatial position of into the spatial bits. For example, if and , we select and to transmit information, the spatial bits denote that the th TAS is activated to send modulation symbol.
Using the above SVD-based TASS method, in the TASS matrix , only , are equal to the identity matrix , and the remainders are all-zero matrices 0.
IV-C Proposed Max-ASR
The two previous proposed TASS methods, Max-EV and Max-P-SINR-ANSNR, are extremely low-complexity. However, this low-complexity is achievable at the expense of some SR performance loss, which will be verified in the next simulation section. Thus, there is still a substantial enhancement room for secrecy performance. In order to further improve the SR performance, in what follows, by selecting TASs, the problem of directly maximizing SR (Max-SR) be expressed as follows
| (90) |
Considering the complicated expression of SR yield a dramatically high computational complexity, the ASR in (28) will be used to replace the SR in order to reduce the computational complexity. The Max-SR in (IV-C) is simplified as
| (91) |
where and are shown in (29) and (30). and are related to TASS matrix. And since , is used to activate one of the selected transmit TASs, and are also related to TASS matrix. Therefore, (29) and (30) can be rewritten as
| (92) |
| (93) |
Since the TASS in (IV-C) is related to both channel and transmitted modulation symbols, and it is selected for secrecy performance, its performance is better than that of TASS method considering only channel. The Max-SR method in [17] is also select the transmit antenna for ASR. However, the ASR in [17] is not affected by the modulation symbol, so when this method is extended to the hybrid SM system, its performance is inferior to the method in this paper.
IV-D Extended leakage
The leakage method for traditional SM systems in [17] can also be extended to hybrid spatial modulation systems. The signal-to-leakage-and-noise ratio (SLNR) for the -th channel is defined as
| (94) |
Then, the SLNR values per TAS are firstly computed and simply arranged in a descending order. The former TASs can be selected as TASs. Although this method has low-complexity, it considers the leakage from the channel from Alice to Bob into the channel from Alice to Eve. Actually, a small leakage implies a low information leakage. In other words, a good SR performance can be available.
IV-E Computational Complexity Analysis
In this subsection, the approximate computational complexities of the three proposed TASS methods and the extended leakage method in [17] are analyzed.
According to [41, 42], what we know are:
(1) A complex multiplication or division requires 6 floating-point operations (FLOPs), and a complex addition or subtraction requires two FLOPs;
(2) For a complex matrix , SVD costs FLOPs;
(3) Multiplying the complex matrices A and , costs FLOPs.
The unit of computational complexity is FLOPs, which is ignored for convenience in what follows.
For the SINR and ANSNR of TASs of the proposed Max-P-SINR-ANSNR, the computational complexities of those fixed terms in the denominators are omitted. The terms and in the numerators are calculated for each TAS. Therefore, the computational complexity of Max-P-SINR-ANSNR can be approximated as follows
| (95) |
For the proposed Max-EV, according to the computational complexity of SVD [42], its complexity has the following approximate form
| (96) |
For the proposed Max-ASR, ignoring the computational complexity of those fixed terms, the computational complexity is partitioned into three parts: (a) all possible combinations of x, (b) the computation of and , and (c) the computation of and . We can easily get the computational complexity of part (a)
| (97) |
The computational complexity of part (b) can be approximated as
| (98) |
For part (c), we have
| (99) |
To make an exhaustive search of possible TASSs, the above three parts need to be repeated times. Therefore,
| (100) |
Since their complexities depend mainly on and with , according to and in (IV-E) and (IV-E), we find that the computational complexity of Max-EV is far less than that of Max-P-SINR-ANSNR. For the Max-ASR method, the complexity order of each search is according to . When , we get , therefore the Max-ASR and Max-P-SINR-ANSNR have the same magnitude of complexity. However, the and of Max-ASR are also large. Therefore, the complexity of Max-ASR is higher than that of Max-P-SINR-ANSNR. In the same manner, in the case of , we can obtain the same trend, that is, the computational complexities of the three proposed TASS methods are listed in ascending order: Max-EV, Max-P-SINR-ANSNR, and Max-ASR. As the value of increases, the complexity of Max-ASR grows far faster than those of Max-EV and Max-P-SINR-ANSNR.
V Simulation Results and Analysis
In this section, we evaluate the performance of these TASS methods and two hybrid precoding methods proposed by us, with the SDR-AltMin method in [39] as a performance reference. The system parameters are set as follows: , , and quadrature phase shift keying (QPSK) modulation. For the convenience of simulation, it is assumed that the total transmit power W. For the sake of fairness of Bob and Eve, it is assumed that all noise variances in channels are identical, i.e., and .
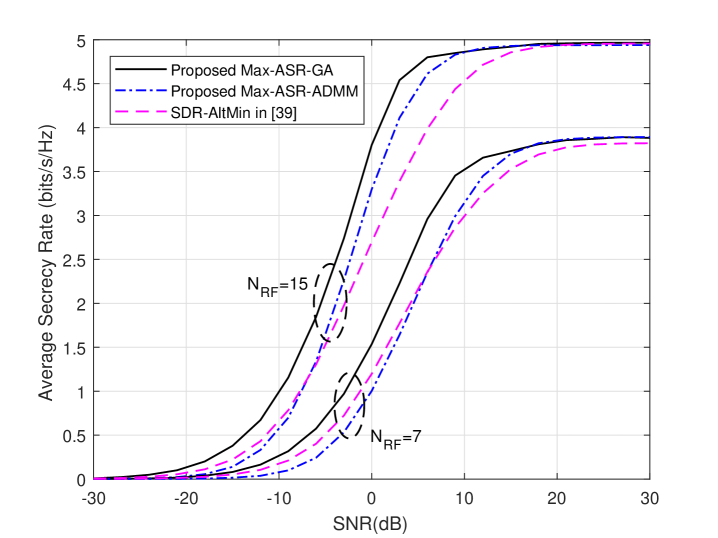
When the Max-EV TASS strategy is adopted in hybrid SM, Fig. 2 demonstrates the average SR performance of the proposed Max-ASR-GA, and proposed Max-ASR-ADMM for and with the SDR-AltMin algorithm extended from [39] as a performance benchmark. Therefore, and . Considering QPSK modulation is used, when , the upper bound of the achievable secrecy capacity is 4bits/s/Hz, and when , the upper bound of the achievable secrecy capacity is 5bits/s/Hz. From Fig. 2, it is seen that the SR of the proposed Max-ASR-GA algorithm is much larger than that of extended SDR-AltMin in the low and medium SNR regions. As the SNR increases, the Max-ASR-GA algorithm can reach the upper bound of the achievable SR with a more rapid rate than SDR-AltMin regardless of or . This tendency implies that the SR performance of the proposed Max-ASR-GA precoding algorithm is better than that of SDR-AltMin. The SR performance of the proposed Max-ASR-ADMM method is in between the proposed Max-ASR-GA and SDR-AltMin in the medium and high SNR regions, and only slightly lower than SDR-AltMin algorithm in the low SNR region.
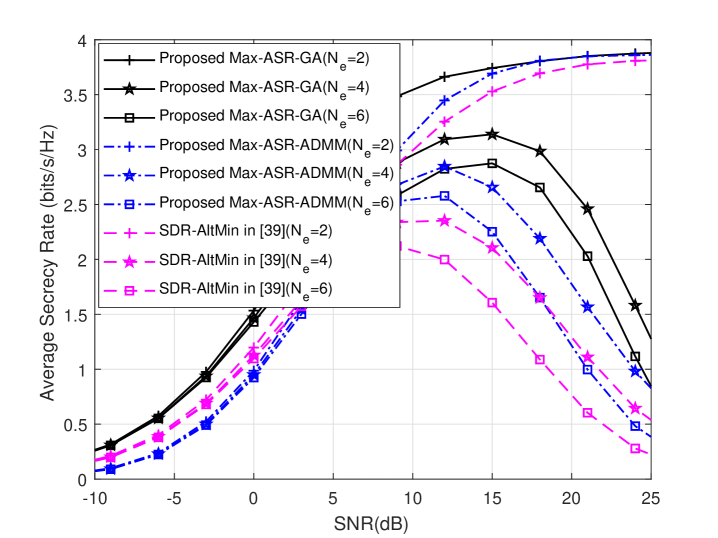
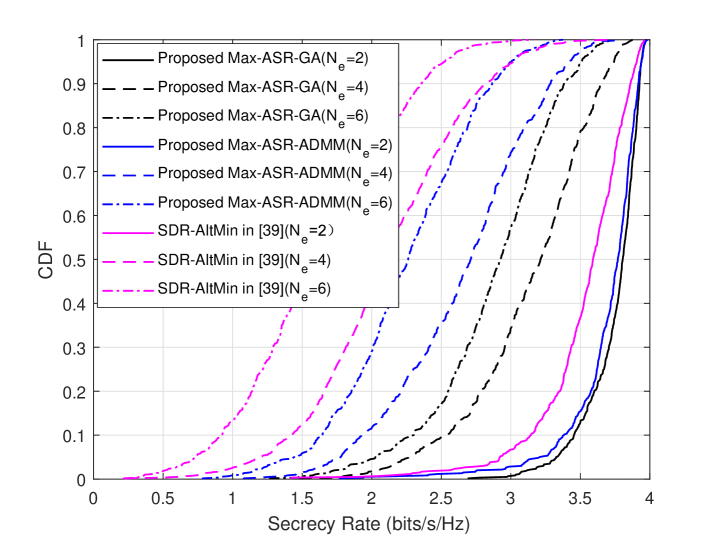
Fig. 3 plots the average SR performance achieved by the above the above three hybrid precoding algorithms by fixing and , and only changing . When , as SNR increases, the SR curves increase until it reaches a certain SNR, and the corresponding SR performance is close to the upper bound. However, when is larger than , the SR will descend when the SNR is beyond some thresholds. As increases, the SR curves can achieve the corresponding maximum SRs, and then decreases. As increases from 4 to 6, the corresponding SNR values of the maximum SRs reached by the three algorithms decreases by about 2.5dB. This is because when SNR is very high, both Bob and Eve have very good quality of channels, while Eve has a larger number of receive antennas than Bob, which is the worst situation, so the SR performance begins to decline. In addition, it can be seen that in the case of , the SR peak of Max-ASR-GA algorithm reaches around 15dB, while the SR peaks of Max-ASR-ADMM and SDR-AltMin algorithms reaches around 12dB and 10dB, respectively. This also shows how well the three algorithms perform.
Fig. 4 shows the CDF curves of the tree precoding algorithms for the different numbers of eavesdropper’s antennas when the SNR = 15dB. In this situation, from Fig. 4, we have the same descending trend in SR performance as Fig. 3: Max-ASR-GA, Max-ASR-ADMM and SDR-AltMin.
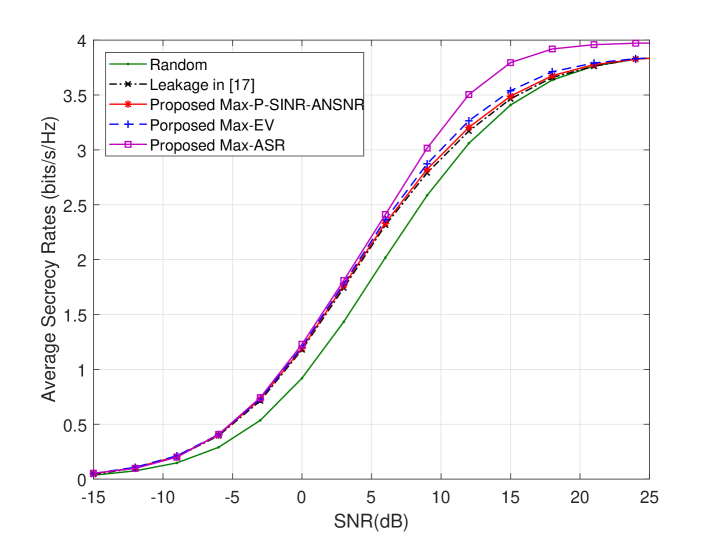
Now, we will fix the hybrid precoding method, and make a performance comparison of five TASS strategies. Fig. 5 demonstrates the curves of average SR versus SNR of five TASS methods when and . From Fig. 5 it can be clearly seen that the proposed Max-ASR TASS strategy is the best one, whereas the random method is the lowest one, and the remaining methods, such as the proposed Max-EV TASS method and the leakage method in [17], are close to the SR of the Max-ASR method in the low SNR region. In summary, their SR performance has a descending tendency as follows: Max-ASR, Max-P-SINR-ANSNR, Max-EV, leakage and random.
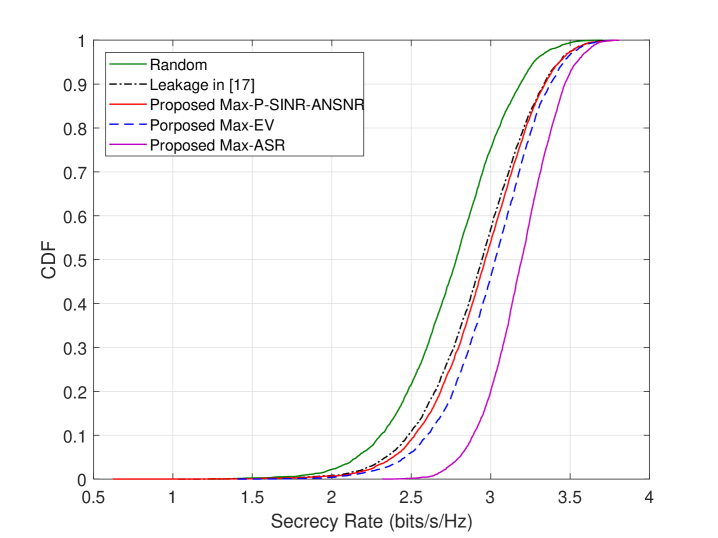
Fig. 6 illustrates the cumulative distribution function (CDF) curves of SRs of these five TASS methods when and SNR=10dB. From Fig. 6, it can be clearly seen that at SNR=10dB, the CDF of proposed Max-ASR method locates to the most right and that of random is shifted to the most left. In other words, in terms of SR, the former is the best one, the latter is the worse one, and the proposed Max-EV and Max-P-SINR-ANSNR method are in between Max-ASR and random.
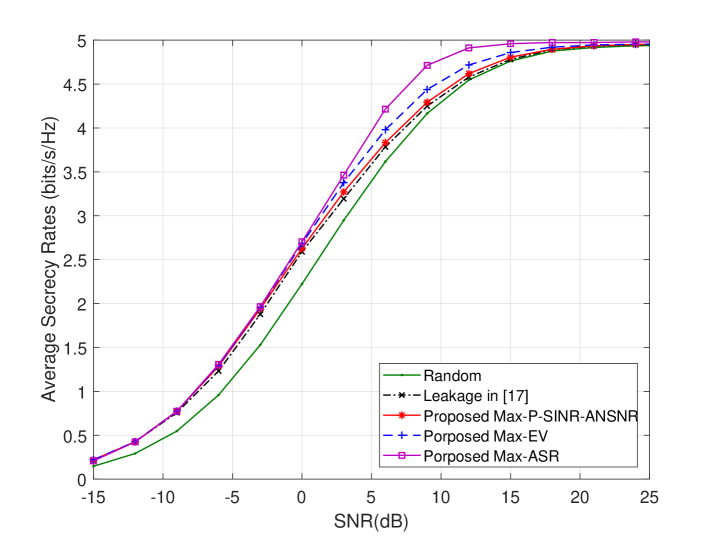
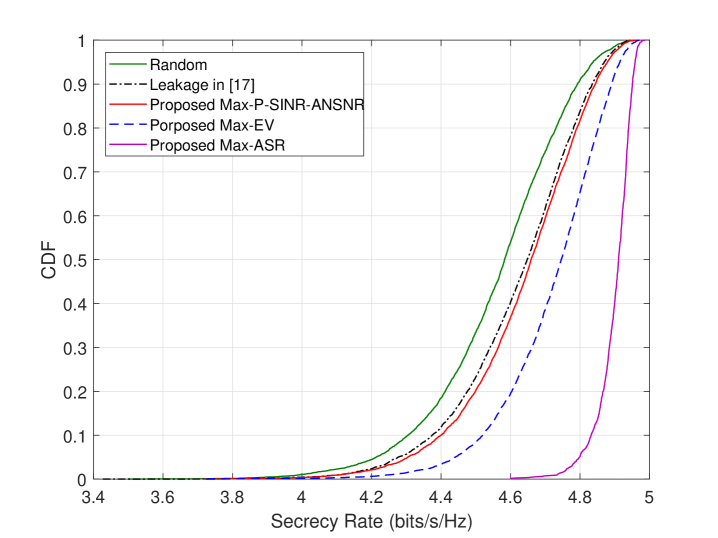
VI Conclusion
In this paper, we have made a comprehensive investigation of precoding and TASS methods concerning hybrid SM. In such a architecture, the first part of bitstream is transmitted by APM symbol, and the second part of bitstream is carried by selecting a TAS in the partially-connected structure rather than a single transmit antenna. Considering the physical-layer security, three TASS methods, Max-P-SINR-ANSNR, Max-ASR, and Max-EV, were proposed, and at the same time the leakage-based TASS is extended from FD SM to hybrid SM. Particularly, two hybrid precoding algorithms were also proposed: Max-ASR-GA and Max-ASR-ADM. Simulation results show that the proposed TASS strategies has an ascending order in SR: random, leakage, Max-P-SINR-ANSNR, Max-EV, and Max-ASR. Compared with Max-ASR, with dramatically low-complexity, Max-P-SINR-ANSNR and Max-EV make a good balance between SR performance and computational complexity. For the hybrid precoding, the proposed Max-ASR-GA and Max-ASR-ADMM hybrid precoding algorithm performs better than existing SDR-AltMin in terms of SR performance.
References
- [1] G. J. Foschini, “Layered space-time architecture for wireless communication in a fading environment when using multi-element antennas,” Bell Labs Tech. J., vol. 1, no. 2, pp. 41–59, Aug. 1996.
- [2] X. Yu, S. H. Leung, B. Wu, and Y. Rui, “Power control for space-time-coded MIMO systems with imperfect feedback over joint transmit-receive-correlated channel,” IEEE Trans. Veh. Technol., vol. 64, no. 6, pp. 2489–2501, Jun. 2015.
- [3] M. D. Renzo, H. Haas, and P. M. Grant, “Spatial modulation for multiple-antenna wireless systems: A survey,” IEEE Commun. Mag., vol. 49, no. 12, pp. 182–191, Dec. 2011.
- [4] R. Y. Mesleh, H. Haas, S. Sinanovic, W. A. Chang, and S. Yun, “Spatial modulation,” IEEE Trans. Veh. Technol., vol. 57, no. 4, pp. 2228–2241, Jul. 2008.
- [5] J. Jeganathan, A. Ghrayeb, and L. Szczecinski, “Spatial modulation: Optimal detection and performance analysis,” IEEE Commun. Lett., vol. 12, no. 8, pp. 545–547, Aug. 2012.
- [6] R. Rajashekar, K. V. S. Hari, and L. Hanzo, “Antenna selection in spatial modulation systems,” IEEE Commun. Lett., vol. 17, no. 3, pp. 521–524, Mar. 2013.
- [7] G. Xia, F. Shu, Y. Zhang, J. Wang, S. ten Brink, and J. Speidel, “Antenna selection method of maximizing secrecy rate for green secure spatial modulation,” IEEE Trans. Green Commun. Netw., vol. 3, no. 2, pp. 288–301, Jun. 2019.
- [8] G. Xia, Y. Lin, T. Liu, F. Shu, and L. Hanzo, “Transmit antenna selection and beamformer design for secure spatial modulation with rough CSI of Eve,” 2019. [Online]. Available: https://arxiv.org/abs/1905.10088.
- [9] S. R. Jin, W. C. Choi, J. H. Park, and D. J. Park, “Linear precoding design for mutual information maximization in generalized spatial modulation with finite alphabet inputs,” IEEE Commun. Lett., vol. 19, no. 8, pp. 1323–1326, Aug. 2015.
- [10] L. L. Yang, “Transmitter preprocessing aided spatial modulation for multiple-input multiple-output systems,” in Proc. IEEE Veh. Technol. Conf., Yokohama, Japan, May 2011, pp. 1–5.
- [11] F. Shu, X. Liu, G. Xia, T. Xu, J. Li, and J. Wang, “High-performance power allocation strategies for secure spatial modulation,” IEEE Trans. Veh. Technol., vol. 68, no. 5, pp. 5164–5168, May. 2019.
- [12] G. Xia, L. Jia, Y. Qian, F. Shu, Z. Zhuang, and J. Wang, “Power allocation strategies for secure spatial modulation,” IEEE Syst. J., vol. 13, no. 4, pp. 3869–3872, Dec. 2019.
- [13] S. R. Aghdam, T. M. Duman, and M. D. Renzo, “On secrecy rate analysis of spatial modulation and space shift keying,” in Proc. IEEE Int. Black Sea Conf. Commun. Netw., Constanta, Romania, May. 2015, pp. 63–67.
- [14] L. Wang, S. Bashar, Y. Wei, and R. Li, “Secrecy enhancement analysis against unknown eavesdropping in spatial modulation,” IEEE Commun. Lett., vol. 19, no. 8, pp. 1351–1354, Aug. 2015.
- [15] X. Wang, X. Wang, and L. Sun, “Spatial modulation aided physical layer security enhancement for fading wiretap channels,” in Proc. IEEE Int. Conf. Wirel. Commun. Signal Process., Yangzhou, China, Oct. 2016, pp. 1–5.
- [16] C. Liu, L. L. Yang, and W. Wang, “Secure spatial modulation with a full-duplex receiver,” IEEE Wireless Commun. Lett., vol. 6, no. 6, pp. 838–841, Dec. 2017.
- [17] F. Shu, Z. Wang, R. Chen, Y. Wu, and J. Wang, “Two high-performance schemes of transmit antenna selection for secure spatial modulation,” IEEE Trans. Veh. Technol., vol. 67, no. 9, pp. 8969–8973, Sept. 2018.
- [18] N. Zhao, Y. Cao, F. R. Yu, Y. Chen, M. Jin, and V. C. Leung, “Artificial noise assisted secure interference networks with wireless power transfer,” IEEE Trans. Veh. Technol., vol. 67, no. 2, pp. 1087–1098, Feb. 2017.
- [19] T.-X. Zheng, H.-M. Wang, J. Yuan, D. Towsley, and M. H. Lee, “Multi-antenna transmission with artificial noise against randomly distributed eavesdroppers,” IEEE Trans. Commun., vol. 63, no. 11, pp. 4347–4362, Nov. 2015.
- [20] X. Chen, D. W. K. Ng, W. H. Gerstacker, and H.-H. Chen, “A survey on multiple-antenna techniques for physical layer security,” IEEE Commun. Surv. Tutor., vol. 19, no. 2, pp. 1027–1053, Jun. 2017.
- [21] J. Hu, F. Shu, and J. Li, “Robust synthesis method for secure directional modulation with imperfect direction angle,” IEEE Commun. Lett., vol. 20, no. 6, pp. 1084–1087, Jun. 2016.
- [22] F. Shu, X. Wu, J. Li, R. Chen, and B. Vucetic, “Robust synthesis scheme for secure multi-beam directional modulation in broadcasting systems,” IEEE Access, vol. 4, pp. 6614–6623, Oct. 2016.
- [23] X. Zhou, Q. Wu, S. Yan, F. Shu, and J. Li, “UAV-enabled secure communications: Joint trajectory and transmit power optimization,” IEEE Trans. Veh. Technol., vol. 68, no. 4, pp. 4069–4073, Apr. 2019.
- [24] Y. Zou, “Physical-layer security for spectrum sharing systems,” IEEE Trans. Wireless Commun., vol. 16, no. 2, pp. 1319–1329, Feb. 2017.
- [25] F. Wu, L. L. Yang, W. Wang, and Z. Kong, “Secret precoding-aided spatial modulation,” IEEE Commun. Lett., vol. 19, no. 9, pp. 1544–1547, Sept. 2015.
- [26] F. Wu, D. Chen, L. L. Yang, and W. Wang, “Secure wireless transmission based on precoding-aided spatial modulation,” in Proc. IEEE Global Commun. Conf., San Diego, CA, USA, Dec. 2015, pp. 1–6.
- [27] F. Wu, R. Zhang, L. L. Yang, and W. Wang, “Transmitter precoding aided spatial modulation for secrecy communications,” IEEE Trans. Veh. Technol., vol. 65, no. 1, pp. 467–471, Jan. 2016.
- [28] Y. Chen, W. Li, Z. Zhao, M. Meng, and B. Jiao, “Secure multiuser MIMO downlink transmission via precoding-aided spatial modulation,” IEEE Commun. Lett., vol. 20, no. 6, pp. 1116–1119, Jun. 2016.
- [29] X. Gao, L. Dai, S. Han, I. Chih-Lin, and R. W. H. Jr, “Energy-efficient hybrid analog and digital precoding for mmWave MIMO systems with large antenna arrays,” IEEE J. Select. Areas Commun., vol. 34, no. 4, pp. 998–1009, Apr. 2016.
- [30] F. Shu, Y. Qin, T. Liu, L. Gui, Y. Zhang, J. Li, and Z. Han, “Low-complexity and high-resolution doa estimation for hybrid analog and digital massive MIMO receive array,” IEEE Trans. Commun., vol. 66, no. 6, pp. 2487–2501, Jun. 2018.
- [31] Y. Cui, X. Fang, and Y. Li, “Hybrid spatial modulation beamforming for mmWave railway communication systems,” IEEE Trans. Veh. Technol., vol. 65, no. 12, pp. 9597–9606, Dec. 2016.
- [32] M. Yüzgeçcioğlu and E. Jorswieck, “Hybrid beamforming with spatial modulation in multi-user massive MIMO mmWave networks,” in Proc. IEEE Int. Symp. Person. Indoor Mobile Radio Commun. Montreal, QC, Canada: IEEE, Oct. 2017, pp. 1–6.
- [33] S. Luo, X. T. Tran, W. Wang, K. C. Teh, and K. H. Li, “Macro spatial modulation for uplink mmWave communication systems,” in Proc. IEEE Globecom Workshops. Singapore: IEEE, Dec. 2017, pp. 1–5.
- [34] M. C. Lee and W. H. Chung, “Adaptive multimode hybrid precoding for single-RF virtual space modulation with analog phase shift network in MIMO systems,” IEEE Trans. Wireless Commun., vol. 16, no. 4, pp. 2139–2152, Apr. 2017.
- [35] L. He, J. Wang, and J. Song, “Spectral-efficient analog precoding for generalized spatial modulation aided mmWave MIMO,” IEEE Trans. Veh. Technol., vol. 66, no. 10, pp. 9598–9602, Oct. 2017.
- [36] Z. Lu, L. He, J. Wang, and J. Song, “Low complexity hybrid precoding algorithm for gensm aided mmWave MIMO systems,” in Proc. IEEE Int. Wirel. Commun. Mob. Comput. Conf. Limassol, Cyprus: IEEE, Jun. 2018, pp. 412–417.
- [37] L. He, J. Wang, and J. Song, “Spatial modulation for more spatial multiplexing: RF-chain-limited generalized spatial modulation aided MM-Wave MIMO with hybrid precoding,” IEEE Trans. Commun., vol. 66, no. 3, pp. 986–998, Mar. 2018.
- [38] S. R. Aghdam and T. M. Duman, “Joint precoder and artificial noise design for MIMO wiretap channels with finite-alphabet inputs based on the Cut-Off rate,” IEEE Trans. Wireless Commun., vol. 16, no. 6, pp. 3913–3923, Jun. 2017.
- [39] X. Yu, J. C. Shen, J. Zhang, and K. Letaief, “Alternating minimization algorithms for hybrid precoding in millimeter wave MIMO systems,” IEEE J. Sel. Top. Sign. Proces., vol. 10, no. 3, pp. 485–500, Apr. 2016.
- [40] S. Boyd, N. Parikh, E. Chu, B. Peleato, J. Eckstein et al., “Distributed optimization and statistical learning via the alternating direction method of multipliers,” Found. Trends Mach. Learn., vol. 3, no. 1, pp. 1–122, 2011.
- [41] S. Boyd and L. Vandenberghe, Convex optimization. Cambridge university press, 2004.
- [42] G. Golub and C. F. Van Loan, Matrix computations. 3rd ed. The Johns Hopkins University Press, 1996.