Quantum algorithms for abelian difference sets
and applications to dihedral hidden subgroups
Abstract
Difference sets are basic combinatorial structures that have applications in signal processing, coding theory, and cryptography. We consider the problem of identifying a shifted version of the characteristic function of a (known) difference set. We present a generic quantum algorithm that can be used to tackle any hidden shift problem for any difference set in any abelian group. We discuss special cases of this framework where the resulting quantum algorithm is efficient. This includes: a) Paley difference sets based on quadratic residues in finite fields, which allows to recover the shifted Legendre function quantum algorithm, b) Hadamard difference sets, which allows to recover the shifted bent function quantum algorithm, and c) Singer difference sets based on finite geometries. The latter class allows us to define instances of the dihedral hidden subgroup problem that can be efficiently solved on a quantum computer.
1 Introduction
Many exponential speedups in quantum computing are the result of solving problems that belong to either the class of hidden subgroup problems (HSPs) or the class of hidden shift problems. For instance, the problems of factoring integers and of computing discrete logarithms in abelian groups [44] can be reformulated as solving instances of hidden subgroup problems in abelian groups [34, 26, 27, 6, 22, 23]: given a function from an abelian group to a set, so that is constant on the cosets of some subgroup and takes distinct values on different cosets, the task is to find generators of .
Successes of the hidden subgroup framework include period finding over the reals which was used by Hallgren to construct an efficient quantum algorithm for solving Pell’s equation [18, 24] and more recently to the discovery of a quantum algorithm for computing unit groups of number fields of arbitrary degree [12]. Moreover, the hidden subgroup problem over symmetric and dihedral groups are related to the graph isomorphism problem [5, 2, 13, 19] and some computational lattice problems [40]. Constructing efficient algorithms for these problems are two major open questions in quantum algorithms.
As far as hidden shift problems are concerned, the shifted Legendre function problem [47], shifted sphere problems and shifts of other non-linear structures [8], problems of finding shifts of non-linear Boolean functions [43, 7] can be reformulated as solving instances of hidden shift problems in abelian groups: given a pair of functions from an abelian group to a set so that is obtained from by shifting the argument by an unknown shift , the task is to find this shift. For further background on hidden subgroup and hidden shift problems see [35, 27, 25, 9, 31].
An intriguing connection exists between injective instances of the hidden shift problem over abelian groups and the hidden subgroup problem for semidirect products of the form where the action of is given by inversion. This connection includes the special case of the hidden shift problem over the cyclic groups , where is a large integer which are related to the dihedral groups . Despite much effort, a fully polynomial-time quantum algorithm for the hidden subgroup problem over the dihedral groups has remained elusive. In this paper we make a step toward solving the hidden subgroup problem over the dihedral groups by exhibiting some instances that can be solved efficiently on a quantum computer. By efficient we mean that the run-time of the quantum part of the computation is bounded polynomially in the input size, which is generally assumed to be , and the run-time of the classical post-processing part of the computation is also bounded polynomially in the input size.


 a)
b)
c)
d)
a)
b)
c)
d)
1.1 Our results
Based on the combinatorial structure of difference sets we derive a class of functions that have a two-level Fourier power spectrum. We then consider the hidden shift problem for these functions, following a general algorithm principle that was used earlier to solve the hidden Legendre symbol [47] and the hidden bent function problem [43].
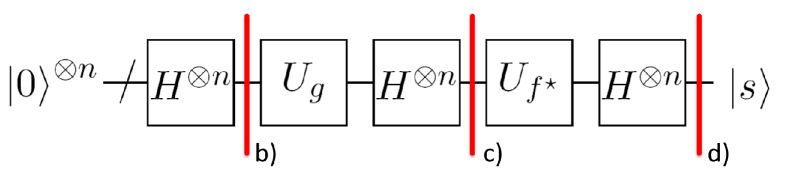
The basic idea underlying all these algorithms is to use the fact that the quantum computer can perform quantum Fourier transforms efficiently. This is used in correlation-based techniques which try to identify a shift by first transforming the function into frequency (Fourier) domain, then performing a point-wise multiplication with the desired target correlator, followed by an inverse Fourier transform and a measurement in the computational basis. After these steps the shift might be obtained, even without further post-processing. An example for this approach is shown in Figure 1 where the underlying group is the Boolean hypercube and the shifted function is a so-called bent function.
A rich theory of difference sets exists and many explicit constructions are known. Furthermore, several applications of difference sets exist in signal processing [38], coding theory [32], cryptography [37], see also [4] for further examples. In this paper we focus on the case of difference sets in abelian groups and show that a correlation-based approach can be successfully applied to several families of difference sets. In one application we consider so-called Singer difference sets, which are difference sets in cyclic groups. These difference sets have parameters
where is a constant and is a parameter that defines the input size of the problem, and , , and are characteristic parameters of the difference set. We construct instances of dihedral hidden subgroup problems that can be (query) efficiently solved on a quantum computer. There is one step in our algorithm that requires the implementation of a diagonal operator whose diagonal elements are certain generalized Gauss sums whose flatness follows from a classic result due to Turyn [46]. In general, we do not known how to implement these diagonal operators efficiently and it seems that the actual computational cost has to be determined on a case-by-case basis. However, for the case of , which leads to difference sets in a cyclic group of order , we can leverage a result by van Dam and Seroussi [48] to implement a quantum algorithm that is fully efficient in terms of its quantum complexity as well as classical complexity. Classically, the underlying problem of this white-box problem is at least as hard as the discrete logarithm problem over a finite field.
1.2 Related work
Several papers study the dihedral hidden subgroup, however, it is an open whether quantum computers can solve this problem efficiently. There is a quantum algorithm which is fully efficient in its quantum part, which however requires an exponential-time classical post-processing [14]. Furthermore, a subexponential-time quantum algorithm for the dihedral subgroup problem is known [28, 41, 29] based on a sieving idea. The dihedral hidden subgroup problem for adversarially chosen hiding functions is believed to be intractable on a quantum computer, even we are not aware of any evidence stronger for this intuition than reductions from lattice problems [40] and subset sum type problems [40, 1]. The connection between hidden shift problems over abelian groups and hidden subgroup problems over semidirect groups of the mentioned special form is well-known and was one of the reasons why the hidden shift problem has been studied for various groups [14, 47, 15, 33, 10, 21, 9].
The study of hidden shift problems has resulted in quantum algorithms that are of independent interest and have even inspired cryptographic schemes that might be candidates for post-quantum cryptography [39]. Besides the mentioned works, problems of hidden shift type were also studied in [42, 16, 17], in the rejection sampling [36] framework, and in the context of multiregister PGM algorithms for Boolean hidden shift problems [7]. The main result of this paper is Theorem 4 which asserts that there exist instances of the hidden subgroup problem over the dihedral groups that can be solved in queries to the hiding function, quantum time, quantum space, and trivial classical post-processing. Moreover, for , where , there exist instances of the hidden subgroup problem over the dihedral group for which the hiding function is white-box and for which the entire quantum computation can be performed in quantum time, quantum space, and trivial classical post-processing. Moreover, the classical complexity of solving these instances is at least as hard as solving the discrete logarithm problem over finite fields. To the best of our knowledge this is the first exponential size family of instances of the dihedral hidden subgroup problem that can be solved efficiently on a quantum computer, whereas for the same class of instances no efficient classical algorithm is known111It is easy to see that it is possible to find instances of the dihedral hidden subgroup problem that can be solved efficiently on a classical computer, e.g., functions that identify the points of a regular -gon that are opposites along a symmetry axis in a linear increasing fashion. On these “taco”-like instances the hidden symmetry axis, and thereby the hidden subgroup, can be found simply by a binary search..
In Corollary 1 we show that for where this theorem implies that there are an expected number of instances of the dihedral HSP (where the hidden subgroup is a reflection) that can be solved efficiently on a quantum computer. This is a small fraction of the set of all instances of such hidden subgroup problems as the number of all instances scales doubly exponential as . In particular, it seems unlikely that the set of such constructed instances has a non-trivial intersection with the set of instances that can be obtain via Regev’s reduction from gapped unique-SVP lattice problems.
The rest of this paper is organized as follows. First, in Section 2 we introduce some notation and basic definitions such as Fourier transform, convolution, and the basic combinatorial object of study in this paper, namely difference sets in finite abelian groups. Next, in Section 3 we present a quantum algorithm that can be applied to any shifted difference set problem, albeit sometimes with low probability of success. We exhibit some instances of shifted difference set problems that can be solved efficiently. These special cases include the so-called class of Singer difference sets which are then used in Section 4 to construct instances of the dihedral hidden subgroup problem that can be solved efficiently on a quantum computer. Finally, in Section 5 we offer conclusions and end with some open problems.
2 Background
2.1 Quantum Fourier transforms over abelian groups
The main tool we will use are Fourier transforms over abelian groups. In the following we state some basic definitions and properties. Recall that for any abelian group the character group is isomorphic to . We denote the irreducible characters of by .
Definition 1.
The quantum Fourier transform on is a unitary transformation defined as .
Example 1.
For the is given by the Hadamard transform .
Definition 2.
The Fourier transform of a (complex-valued) function is a function defined as where . Here is called the Fourier coefficient of at . We can write it explicitly as . The set is called the Fourier spectrum of .
Definition 3.
The convolution of functions is a function defined as .
Fact 1.
Let denote arbitrary functions. The Fourier transform and convolution have the following basic properties:
-
1.
The Fourier transform is linear: .
-
2.
When applied twice, the Fourier transform satisfies . In particular, for the Fourier transform is self-inverse: . From this property also follows that when the Fourier transform is applied four times then the result is the identity.
-
3.
is unitary, so the Plancherel identity holds.
-
4.
The convolution is commutative: , and associative: .
-
5.
The Fourier transform and convolution are related through the following identities: and , where is the entry-wise product of functions and : .
-
6.
A shift of a function in time domain leads to a point-wise multiplication with a “linear phase” in Fourier domain: If there exists such that for all it holds , then for all we have that . This latter property will be crucial for the hidden shift algorithm presented later in this paper.
2.2 Difference sets
We recall the definition of difference sets in finite groups. We focus on the case of abelian groups in this paper. See also [3, 45, 30] for further information, in particular about the treatment for general, non-abelian groups.
Let be a finite abelian group whose group operation we write additively and whose neutral element we denote with . Denote the pairwise inequivalent irreducible characters of by . For a subset of we introduce the notation for the set of all inverses and for the set of all differences of pairs of elements of .
Definition 4 (Difference set).
Let be a finite abelian group of size . A subset of size is called a -difference set, where , if the following equality holds in the group algebra of :
| (1) |
This means that the set of all differences covers each element the same number of times, except for the neutral element, which is covered precisely times. A nice feature of difference sets in abelian group is that they allow to construction functions with almost flat spectrum: the following theorem [46] asserts that all Fourier coefficients of the characteristic function of a difference set in an abelian group have the same absolute value, with a possible exception of a peak at the zero frequency:
Theorem 1 (Turyn, 1965).
Let be an abelian group of order and be an -difference set in . Let be a non-trivial character. Then
| (2) |
holds. For the trivial character we have that .
Proof.
We include a proof as it is instructive to see how the difference set condition can be used when interpreted as the identity (1) in the group ring . Indeed, when identifying with , we obtain from eq. (1) that
| (3) |
Let be non-trivial. Then clearly holds which implies—by applying to both sides of eq. (3)—that . From this we obtain that as claimed. ∎
With each difference set we can canonically associate an incidence structure called the development of , and denoted by .
Definition 5.
Let be a -difference set in an abelian group . Then the points of are given by the elements of and the blocks of are given by , where .
It is well-known that is a symmetric design. More precisely, we have the following result (for a proof see, e.g., [3], [45] or [30]):
Theorem 2.
Let be a -difference set in an abelian group . Then is a symmetric balanced-incomplete block design with parameters .
Theorem 2 implies that there are blocks, that each block has elements, that any two elements have precisely blocks in common and that in addition any two blocks intersect in precisely points. Also, it holds that , see e.g. [30, Prop. 1.1], implying that is determined by the group order of and the size of . This equality allows us also to do a consistency check that the normalized state vector is indeed mapped to a normalized vector under the Fourier transform for the group : using Theorem 1 we find that the length of the transformed vector is given by
as desired.
3 Quantum algorithm for shifted difference sets
Problem 1 (Shifted difference set problem).
Let be an abelian group and let . Let be a (known) difference set and let be given by a membership oracle. The problem is to find .
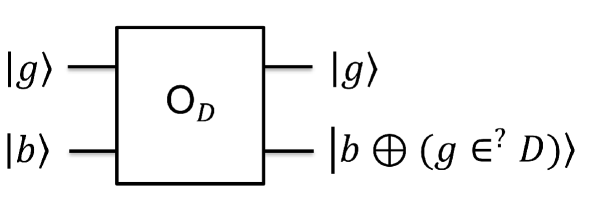
Similar to [43] we can modify Problem 1 by hiding not only the characteristic function of via a membership oracle but also the characteristic function of itself. In this case we assume that we have access to membership oracles for both and . The following quantum algorithm is a general recipe to tackle instances of the shifted difference set problem specified in Problem 1. As we will show in the following, Algorithm 1 can be used to find the hidden shift efficiently in several cases of difference sets for various abelian groups . It should be noted, however, that the probability of success crucially depends on the instance of the problem and there are instances for which the algorithm recovers successfully is only exponentially small. The algorithm can be seen as a generalization of correlation-based algorithms for solving hidden shift problems, e.g., [47], [43], and [7].
Algorithm 1.
The input to the algorithm is a membership oracle as in Problem 1.
Step 1: Prepare the input superposition:
Step 2: Query the shifted difference set. This maps the state to:
Step 3: Apply the quantum Fourier transform for . This maps the state to:
Step 4: Compute into the phase. This maps the state to:
Step 5: Apply the inverse quantum Fourier transform for . This maps the state to:
Step 5: Measure in the standard basis. Obtain with probability and all other group elements uniformly with probability .
3.1 Examples
3.1.1 Paley difference sets and shifted Legendre functions
Let be the additive group of the finite field , where is a prime power such that . Define . It is well-known [3, 45] that is then a difference set in . These difference sets are also known as Paley difference sets. The parameters of are as follows:
Example 2.
Let and consider the irreducible polynomial , defining the finite field . Denote by an -basis of where , the image of under the canonical projection. Then given by the following elements
defines a -difference set in .
Remark 1.
Applying Algorithm 1 finds the hidden shift with probability of success
This means that for large , we can efficiently recover the hidden shift. In this case, the Algorithm 1 specializes to the algorithm given in [47]. We recover the result that an unknown shift of the Legendre symbol can be reconstructed with high probability using query.
3.1.2 Hadamard difference sets and shifted bent functions
Let be the elementary abelian -group , where . Let be a bent function. Define . It is well-known [3, 45] that is a difference set in . These difference sets are also known as Hadamard difference sets. The parameters of are as follows:
Example 3.
Let and let be a bent function from the Maiorana-McFarland family [11]. Then given by the following elements
defines a -difference set in . The blocks of the development of are obtained by taking the characteristic function of and shifting it under all elements of . Hence, the incidence matrix of the -design is given by
Applying Algorithm 1 to the shifted difference problem for a Hadamard difference set finds the hidden shift with probability of success
This means that we always recover the hidden shift with probability . In this case, the Algorithm 1 specializes to the algorithm given in [43]. We recover the result that an unknown shift of a bent function can be reconstructed using query.
3.1.3 Singer difference sets and shifted hyperplanes
Let be a prime power, let and let be the finite field with elements. The Singer difference sets are constructed from -dimensional projective spaces over as follows: consider the trace map from to . Let be a transversal of in that is chosen in such a way that maps onto the values and in only. We can then define a group which turns out to be cyclic. Furthermore, we can define a subset . It turns out [3] that is then a difference set in , where . This difference set has parameters
| (4) |
Example 4.
Let be the two-dimensional projective space over . Then . By choosing an -basis of we obtain an embedding of into . If is a primitive element for , then the corresponding matrix has order and therefore generates a cyclic subgroup of order . Under the canonical projection , the subgroup is mapped to a subgroup of of order (see also [20, Kapitel II, Satz 7.3]). This subgroup is sometimes also called the “Singler cycle.” The Singer cycle operates transitively on the points of the projective space . By picking the particular order , where is the point , we obtain points that we can identify with . The image of the hyperplane given by all points with is given by the set . Then is a -difference set in the cyclic group . The development is given by:
If in eq. (4) we consider to be constant and be a parameter that corresponds to the input size of a hidden shift problem over , we can use Algorithm 1 to solve the hidden shift problem over with probability of success
This means that for constant , we can efficiently recover the hidden shift from a constant number of trials. In Section 4 we show how we can use the instances of hidden difference problems of Singer type to construct efficiently solvable instances of the dihedral hidden subgroup problem.
Remark 2.
We note that not all shifted difference set problems can be solved efficiently by using Algorithm 1. An example is given by the projective planes of order . In this case the input size is given by and the probability of success can be computed to be , i.e., the probability of success is exponentially small in this case. It is an open problem if cases like this can be tackled, e.g., by considering multi-register algorithms.
3.2 Injectivization
As mentioned in the introduction, it is well known that the hidden subgroup problem over semidirect products of the form , where the action of is given by inversion, and the hidden shift problem over are closely related. More precisely, there is a one-to-one correspondence between instances of the hidden subgroup problem in which the subgroup is a conjugate of the order subgroup and instances of injective hidden shift problems over .
This leads to the question whether it is possible to relate instances of hidden shift problems where the hiding function is not injective to the injective case. Thankfully, as shown in [17] such a connection indeed exists. We briefly review this construction.
For given , and a set of elements of we define a new function . Gharibi showed in [17] that if the set is chosen uniformly at random, then the probability that the function is not injective can be upper bounded as
| (5) |
where and for all the so-called influences of at are defined as , i.e., the probability that changes its value when the input is toggled by .
We now show that for instances of shifted difference set problems these influences can be bounded by the parameters of the difference set alone. This in turn allows to establish a bound on the overall number of copies that are needed to make the hiding function injective, namely a bound that grows proportional to .
Lemma 1.
Let be a hiding function corresponding to the characteristic function a -difference set in an abelian group . Then for all we have that .
Proof.
Note that
| (6) | |||||
| (7) | |||||
| (8) |
where in the second equation we used the fact that only elements in the intersection contribute to and in the third equation we used Theorem 2 which implies that for all . ∎
We can now establish the claimed result that the number of copies only grows with the log of the group size.
Theorem 3.
Let be a -difference set in an abelian group and an instance of a hidden difference set problem for . Then copies are enough to obtain an injective instance with probability greater than .
Proof.
From the cited bound (5) we obtain that
It is easy to see that lower bounding the right hand side in this expression by is equivalent to choosing . Now, from Lemma 1 we have that from which we can conclude that in particular holds. Using the fact that holds for , this implies that
| (9) | |||||
| (10) |
Hence copies are enough to guarantee that for chosen uniformly at random, the probability of being injective is at least . ∎
4 Efficiently solvable dihedral hidden subgroup problems
Theorem 4.
There exist instances of the hidden subgroup problem over the dihedral groups that can be solved in queries to the hiding function, quantum time, quantum space, and trivial classical post-processing. Moreover, for , where , there exist instances of the hidden subgroup problem over the dihedral group for which the hiding function is white-box and for which the entire quantum computation can be performed in quantum time, quantum space, and trivial classical post-processing. Moreover, the classical complexity of solving these instances is at least as hard as solving the discrete logarithm problem over finite fields.
Proof.
To construct the instances that can be solved efficiently we proceed in three steps: (i) first, we show that a particular set of hidden shift problems over can be obtained from hiding functions that are indicator functions of hyperplanes and that these indicator functions can be implemented efficiently, (ii) next we show that Algorithm 1 is query, time, and space efficient for these instances; (iii) finally, we show that it is possible to construct instances of the hidden subgroup problem in from the hidden shift instances constructed in (i) and that these instances are unlikely to be solvable on a classical computer, unless computing finite field discrete logarithms is possible in polynomial-time.
Step (i): We instantiate the abelian difference set quantum algorithm for the case of the cyclic group , where . Here is constant and is a parameter that corresponds to the input size of the problem. We use the explicitly (white-box) description of the function , where denotes the trace map from to and where is a primitive element in . Now, the instance of the shifted difference set problem is defined by the hiding function , where . This function can be given as a white-box function by providing the element so that can then be evaluated as . Note that the set defines a hyperplane and therefore a difference set of Singer type.
Step (ii): We now go through each step of Algorithm 1 and check that the steps are time- and space-efficient. In the first step, a Fourier transform is applied to create the equal superposition of all elements of . As is abelian, this can clearly be done efficiently. In the second step, we have to evaluate the function in superposition. Again, as there is an explicit description of the trace which can be computed as sum of powers of the relative Frobenius from to as follows we can evaluate by first constructing a circuit for exponentiation followed by scalar multiplication with , followed by the application of the trace map. Clearly, all these operations can be efficiently implemented by means of a classical Boolean circuit whose size and depth are polynomial in . Hence, by applying standard techniques from reversible computing, we can derive quantum circuits for the evaluation of and . Therefore we can compute Step 2 efficiently on a quantum computer.
Step 3 is another application of a quantum Fourier transform over the abelian group which as in Step 1 can be done efficiently. Step 4 is the most challenging step in the entire algorithm. If we were just interested in the query complexity of the problem we would be done as we could simply apply the diagonal unitary operator , where runs through all non-trivial characters of . This argument is sufficient to establish the first claimed statement in the theorem, i.e., the query complexity result.
For the white-box statement, we are interested in the time- and space-efficiency of the algorithm, i.e., we have to show that can be implemented efficiently. For this we have to assume as required by one of the subsequent steps (and we highlight where). First we use a result due to van Dam and Seroussi [48] establishing that finite field Gauss sums can be approximated efficiently on a quantum computer. The connection to our situation is that the elements of are Gauss sums. We briefly review the van Dam/Seroussi algorithm and then argue that we can apply it in superposition in order to compute .
Let be a finite field where and prime. Let be a non-trivial additive character and let be a non-trivial multiplicative character. Then the Gauss sum is defined as
The additive and multiplicative characters of have a simple description: For denote a primitive -th root of unity in with . Then the additive characters take the form , where runs through all elements of . The multiplicative characters can be described using a primitive elements as follows: , where runs through all non-zero elements of . This means that evaluation requires the computation of a discrete log over the multiplicative group of the field.
It is known that for non-trivial and , the absolute value of the Gauss sum evaluates to , i.e., , where . The paper [48] established that can be approximated with precision by a quantum algorithm in time . As we are overall only looking for a quantum algorithm that can solve the hidden shift problem over with bounded probability of success, it will be enough to approximate the diagonal elements of with constant precision, i.e., we can use the van Dam/Seroussi algorithm to estimate . A minor complication is the fact that in [48] only the case of known character is considered, however, by making all steps of the algorithm conditioned on the character it can be easily seen that the transformation can also be implemented coherently, i.e., on superposition of inputs . The final step is to show how to relate and . For this we make the restriction that so that our parameters always take the form . We then obtain that
where denotes the additive character of and denotes a multiplicative character of . This argument establishes that we can approximate the operator efficiently on a quantum computer with constant precision .
The final two steps of the algorithm are easy to do: Step 5 is just another Fourier transform and Step 6 a measurement in the computational basis, both of which can be done efficiently.
Step (iii): To construct the desired instances of the hidden subgroup problem from the hidden shift problem, we apply the results from Subsection 3.2 and specialize them to the case of the Singer difference sets. We pick random elements and construct the hiding function which according to Theorem 3 is injective with probability greater than . We then apply another standard construction [15, 28] which allows to turn an instance of an injective hidden shift problem into a hidden subgroup problem. Indeed, if is an injective instance of a hidden shift problem with shift , then the corresponding hidden subgroup problem over is given by the hiding function and , where is an encoding of the elements, i.e., and . Conversely, if is a defining function of a hidden subgroup problem with hidden subgroup of order , then and defines a hidden shift problem over .
Overall, we established the claimed result of the existence of an efficient quantum algorithm to solve the hidden subgroup problem. The classical complexity of finding the shift from clearly is as least as hard as solving the discrete logarithm over a finite field. ∎
Corollary 1.
Let , where , there there exist an expected number of instances of hidden subgroup problems over that can be solved efficiently on a quantum computer.
Proof.
From the proof of Theorem 4 we see that in step (iii) for each random choice of elements, where , we obtain a valid injectivization of the hidden shift function. There are an expected number of such functions. ∎
5 Conclusions
We showed that the property of difference sets to give rise to functions with two level Fourier (power) spectrum which makes them useful for classical applications also allows to define hidden shift problems which can then be tackled on a quantum computer. While a solution to general hidden shift problems for arbitrary difference sets remains elusive, we showed that several interesting special cases can indeed be solved efficiently on a quantum computer. This includes the known cases of the Legendre symbol which we show to be an instantiation of our framework for the case of a Paley difference set. Furthermore, it includes the case of hidden bent functions which we show to be special cases of Hadamard difference sets. The case of Singer difference sets appears to be new and allows us to construct white-box instances of dihedral hidden subgroup problems that can be solved fully efficiently on a quantum computer, both in the quantum and in the classical parts of the algorithm.
Open problems include whether these findings have any consequence for more general classes of instances of the dihedral hidden subgroup problem and the hidden subgroup problem in other semidirect products of a similar form. Other open problems include whether it is possible to solve the shifted difference set problem for projective planes which we mentioned cannot be solved by our main algorithm with better than exponentially small probability of success. One possible avenue for future research is to consider multi-register algorithms to tackle this problem. Another open problem is the case of hidden shift problems over abelian groups for functions that have approximately constant spectra, possibly with the exception of the zero frequency as in case of the functions arising from difference sets considered in this paper.
Acknowledgments
The author would like to thank Schloss Dagstuhl for hosting Seminar 15371, during which part of this research was carried out.
References
- [1] Dave Bacon, Andrew M. Childs, and Wim van Dam. Optimal measurements for the dihedral hidden subgroup problem. Chicago Journal of Theoretical Computer Science, 2006(2), Oct 2006. quant-ph/0501044.
- [2] Robert Beals. Quantum computation of Fourier transforms over symmetric groups. In Proceedings of the twenty-ninth annual ACM symposium on Theory of computing, STOC ’97, pages 48–53, New York, NY, USA, 1997. ACM.
- [3] Thomas Beth, Dieter Jungnickel, and Hanfried Lenz. Design Theory, volume I. Cambridge University Press, 2nd edition, 1999.
- [4] Thomas Beth, Dieter Jungnickel, and Hanfried Lenz. Design Theory, volume II. Cambridge University Press, 2nd edition, 1999.
- [5] Dan Boneh and Richard Lipton. Quantum cryptanalysis of hidden linear functions. In Advances in Cryptology — CRYPT0’ 95, volume 963 of Lecture Notes in Computer Science, pages 424–437. Springer, 1995.
- [6] Gilles Brassard and Peter Høyer. An exact polynomial–time algorithm for Simon’s problem. In Proceedings of Fifth Israeli Symposium on Theory of Computing and Systems, pages 12–33. ISTCS, IEEE Computer Society Press, 1997. Also: ArXiv prnote quant–ph/9704027.
- [7] Andrew M. Childs, Robin Kothari, Maris Ozols, and Martin Roetteler. Easy and hard functions for the Boolean hidden shift problem. In 8th Conference on the Theory of Quantum Computation, Communication and Cryptography, TQC 2013, May 21-23, 2013, Guelph, Canada, pages 50–79, 2013.
- [8] Andrew M. Childs, Leonard J. Schulman, and Umesh V. Vazirani. Quantum algorithms for hidden nonlinear structures. In 48th Annual IEEE Symposium on Foundations of Computer Science (FOCS 2007), October 20-23, 2007, Providence, RI, USA, Proceedings, pages 395–404, 2007.
- [9] Andrew M. Childs and Wim van Dam. Quantum algorithms for algebraic problems. Rev. Mod. Phys., 82:1–52, Jan 2010. 0812.0380.
- [10] Andrew M. Childs and Pawel Wocjan. On the quantum hardness of solving isomorphism problems as nonabelian hidden shift problems. Quantum Information and Computation, 7(5):504–521, Jul 2007. quant-ph/0510185.
- [11] John F. Dillon. A survey of bent functions. The NSA technical journal, pages 191–215, 1972.
- [12] Kirsten Eisenträger, Sean Hallgren, Alexei Kitaev, and Fang Song. A quantum algorithm for computing the unit group of an arbitrary degree number field. In Symposium on Theory of Computing, STOC 2014, New York, NY, USA, May 31 - June 03, 2014, pages 293–302, 2014.
- [13] Mark Ettinger and Peter Høyer. A quantum observable for the graph isomorphism problem. quant-ph/9901029, 1999.
- [14] Mark Ettinger and Peter Høyer. On quantum algorithms for noncommutative hidden subgroups. Advances in Applied Mathematics, 25(3):239–251, 2000. quant-ph/9807029.
- [15] Katalin Friedl, Gábor Ivanyos, Frédéric Magniez, Miklos Santha, and Pranab Sen. Hidden translation and orbit coset in quantum computing. In Proceedings of the 35fth Annual ACM Symposium on Theory of Computing (STOC’03), pages 1–9. ACM, 2002. quant-ph/0211091.
- [16] Dmitry Gavinsky, Martin Roetteler, and Jérémie Roland. Quantum algorithm for the boolean hidden shift problem. In Computing and Combinatorics, volume 6842 of Lecture Notes in Computer Science, pages 158–167. Springer Berlin / Heidelberg, 2011. 1103.3017.
- [17] Mirmojtaba Gharibi. Reduction from non-injective hidden shift problem to injective hidden shift problem. Quantum Information and Computation, 13(3&4):212–230, 2013.
- [18] Sean Hallgren. Polynomial-time quantum algorithms for Pell’s equation and the principal ideal problem. J. ACM, 54(1):4:1–4:19, Mar 2007.
- [19] Sean Hallgren, Cris Moore, Martin Roetteler, Alex Russell, and Pranab Sen. Limitations of quantum coset states for graph isomorphism. Journal of the ACM, 57(6):34:1–34:33, 2010.
- [20] Bertram Huppert. Endliche Gruppen I. Springer, 1967.
- [21] Gábor Ivanyos. On solving systems of random linear disequations. Quantum Information and Computation, 8(6&7):579–594, 2008. 0704.2988.
- [22] Richard Jozsa. Quantum algorithms and the Fourier transform. Proceedings of the Royal Society of London. Series A: Mathematical, Physical and Engineering Sciences, 454(1969):323–337, 1998. quant-ph/9707033.
- [23] Richard Jozsa. Quantum factoring, discrete logarithms, and the hidden subgroup problem. Computing in Science Engineering, 3(2):34–43, Mar/Apr 2001. quant-ph/0012084.
- [24] Richard Jozsa. Quantum computation in algebraic number theory: Hallgren’s efficient quantum algorithm for solving Pell’s equation. Annals of Physics, 306(2):241–279, 2003. quant-ph/0302134.
- [25] Phillip Kaye, Raymond Laflamme, and Michele Mosca. An Introduction to Quantum Computing. Oxford University Press, 2007.
- [26] Alexei Yu. Kitaev. Quantum measurements and the abelian stabilizer problem. 1995. quant-ph/9511026.
- [27] Alexei Yu. Kitaev, Alexander Shen, and Mikhail N. Vyalyi. Classical and Quantum Computation, volume 47 of Graduate Studies in Mathematics. American Mathematical Society, 2002.
- [28] Greg Kuperberg. A subexponential-time quantum algorithm for the dihedral hidden subgroup problem. SIAM Journal on Computing, 35(1):170–188, 2005. quant-ph/0302112.
- [29] Greg Kuperberg. Another subexponential-time quantum algorithm for the dihedral hidden subgroup problem. 1112.3333, 2011.
- [30] Eric S. Ladner. Symmetric Designs: An Algebraic Approach, volume 74 of London Mathematical Society Lecture Note Series. Cambridge University Press, 1983.
- [31] Chris Lomont. The hidden subgroup problem - review and open problems. quant-ph/0411037, 2004.
- [32] F. J. MacWilliams and N. J. A. Sloane. The theory of error–correcting codes. North–Holland, Amsterdam, 1977.
- [33] Cristopher Moore, Daniel Rockmore, Alexander Russell, and Leonard J. Schulman. The power of strong Fourier sampling: Quantum algorithms for affine groups and hidden shifts. SIAM J. Comput., 37(3):938–958, Jun 2007. quant-ph/0503095.
- [34] Michele Mosca and Artur Ekert. The hidden subgroup problem and eigenvalue estimation on a quantum computer. In Quantum Computing and Quantum Communications, volume 1509 of Lecture Notes in Computer Science, pages 174–188. Springer, 1999. quant-ph/9903071.
- [35] Michael A. Nielsen and Isaac L. Chuang. Quantum Computation and Quantum Information. Cambridge University Press, 2010.
- [36] Maris Ozols, Martin Roetteler, and Jérémie Roland. Quantum rejection sampling. In Proceedings of the 3rd Innovations in Theoretical Computer Science Conference, ITCS ’12, pages 290–308, New York, NY, USA, 2012. ACM. 1103.2774.
- [37] Josef Pieprzyk, Thomas Hardjono, and Jennifer Seberry. Fundamentals of computer security. Springer, 2003.
- [38] Alexander Pott, Vijay Kumar, Tor Helleseth, and Dieter Jungnickel, editors. Difference sets, sequences, and their correlations, volume 542 of NATO Science Series. Kluwer, 1998.
- [39] Oded Regev. New lattice-based cryptographic constructions. J. ACM, 51(6):899–942, 2004.
- [40] Oded Regev. Quantum computation and lattice problems. SIAM Journal on Computing, 33(3):738–760, 2004.
- [41] Oded Regev. A subexponential time algorithm for the dihedral hidden subgroup problem with polynomial space. quant-ph/0406151, 2004.
- [42] Martin Roetteler. Quantum algorithms to solve the hidden shift problem for quadratics and for functions of large Gowers norm. In Proceedings of the 34st International Symposium on Mathematical Foundations of Computer Science (MFCS’09), volume 5734 of Lecture Notes in Computer Science, pages 663–674. Springer, 2009. 0911.4724.
- [43] Martin Roetteler. Quantum algorithms for highly non-linear Boolean functions. In Proceedings of the 21st Annual ACM-SIAM Symposium on Discrete Algorithms (SODA’10), pages 448–457, 2010. 0811.3208.
- [44] Peter W. Shor. Polynomial-time algorithms for prime factorization and discrete logarithms on a quantum computer. SIAM Journal on Computing, 26(5):1484–1509, 1997. Preliminary version in FOCS 1994.
- [45] Douglas R. Stinson. Combinatorial Designs: Constructions and Analysis. Springer, 2003.
- [46] Richard J. Turyn. Character sums and difference sets. Pacific Journal of Mathematics, 15(1):319–346, 1965.
- [47] Wim van Dam, Sean Hallgren, and Lawrence Ip. Quantum algorithms for some hidden shift problems. SIAM Journal on Computing, 36(3):763–778, 2006. quant-ph/0211140.
- [48] Wim van Dam and Gadiel Seroussi. Quantum algorithms for estimating Gauss sums. quant-ph/0207131, 2002.