Quantum Key Distribution for Critical Infrastructures: Towards Cyber Physical Security for Hydropower and Dams
Abstract
Hydropower facilities are often remotely monitored or controlled from a centralized remote-control room. Additionally, major component manufacturers monitor the performance of installed components. While these communications enable efficiencies and increased reliability, they also expand the cyber-attack surface. Communications may use the internet to remote control a facility’s control systems, or it may involve sending control commands over a network from a control room to a machine. The content could be encrypted and decrypted using a public key to protect the communicated information. These cryptographic encoding and decoding schemes have been shown to be vulnerable, a situation which is being exacerbated as more advances are made in computer technologies such as quantum computing. In contrast, Quantum key distribution (QKD) is not based upon a computational problem, and offers an alternative to conventional public-key cryptography. Although the underlying mechanism of QKD ensures that any attempt by an adversary to observe the quantum part of the protocol will result in a detectable signature as an increased error rate, potentially even preventing key generation, it serves as a warning for further investigation. When the error rate is low enough and enough photons have been detected, a shared private key can be generated known only to the sender and receiver. We describe how this novel technology and its several modalities could benefit the critical infrastructures of dams or hydropower facilities. The presented discussions may be viewed as a precursor to a quantum cybersecurity roadmap for the identification of relevant threats and mitigation.
I Introduction
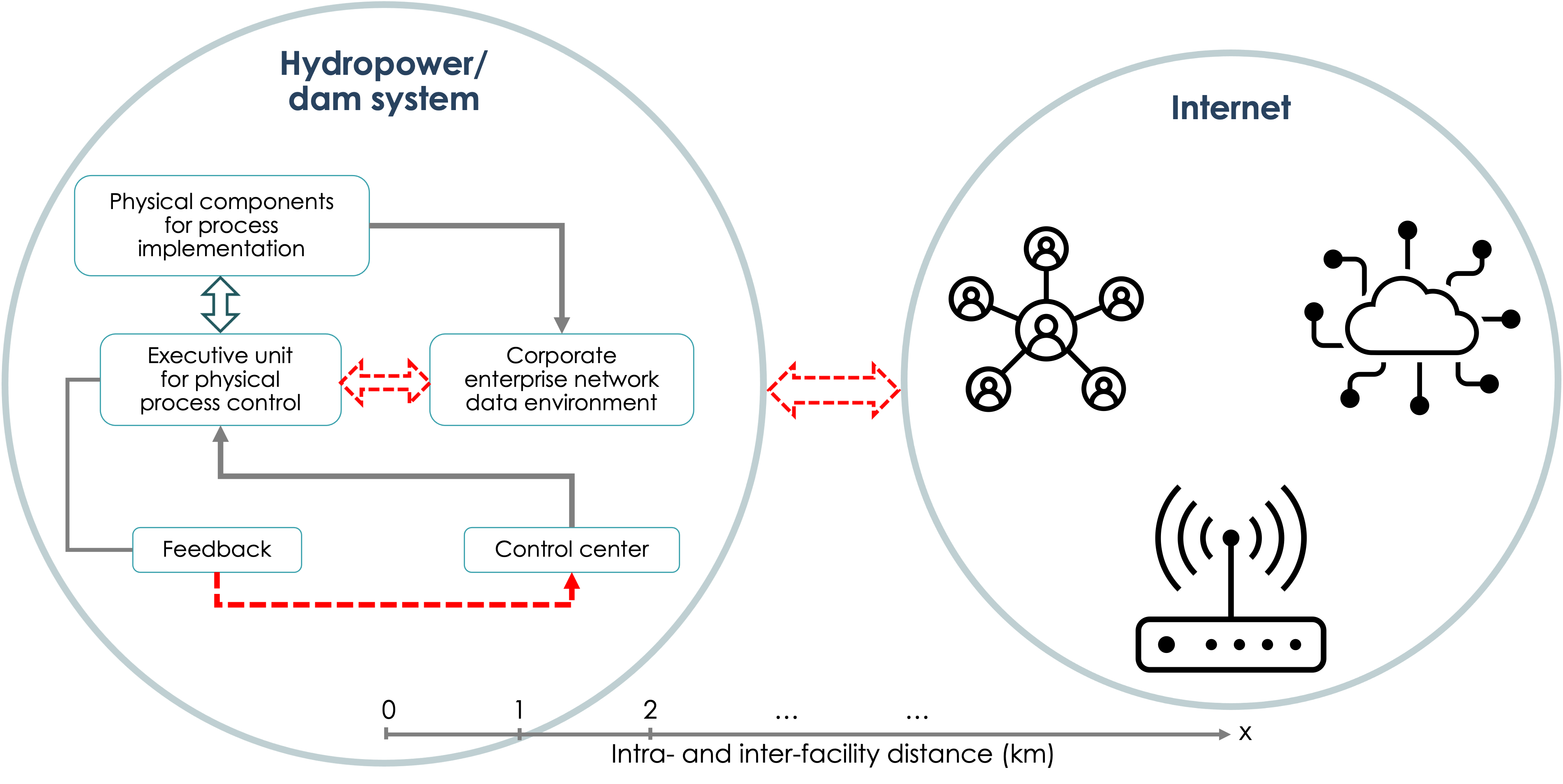
Security of critical infrastructures poses a complex and dynamic problem teeming with loopholes, weak links, and outdated measures that create an array of cyber vulnerabilities and safety concerns Rass et al. (2020); Whyatt et al. (2021); cis (2019). Innovative solutions are needed to protect existing and developing infrastructure (see Rass et al. Rass et al. (2020) for what constitutes a “critical infrastructure” and related discussions). Currently, in the US alone, less than 3 % of the 80,000 dams produce power. Efforts to generate more clean power from these existing dams mean the utilization of advanced technologies and modernization. Therefore, digital technologies are expected to continue to be integrated with hydroelectric projects (including fleet modernization). The gain (e.g., in the efficiency from turbines and generators) that comes with digitalization and the use of advanced information and communication technologies benefit the missions and objectives of an increasing number of stakeholders in hydro energy. These efforts mean increased connectivity (e.g., enhanced remote control and monitoring of the operational conditions of the assets). Higher connectivity is also expected from optimization efforts to operate neighboring hydropower facilities across whole river systems. Predictive and intelligent maintenance Singh et al. (2020), higher efficiency operation, development of digital twins, etc., all require communication of measurement results and associated data analysis from many components and equipment, often in real-time. Higher connectivity, that is, a larger number of communications channels, means a larger cyber-attack surface, and consequently, more risks, as depicted in Fig. 1. A brief summary of some of the basic security issues is provided in Table 1, see also relevant discussions by Ratnam et al. Ratnam et al. (2020). In what follows, for convenience, some relevant terms invoked are defined in Table C.
Clearly, the noted risks associated with exploiting the weaknesses of communications channels need to be addressed. However, known classical (non-quantum) encryption techniques cannot eliminate such risks (for a simple classical encryption example, see Appendix A). This is because, to protect the confidentiality of the communicated messages, classical security utilizes the mathematical complexity of classical cryptography techniques (which ultimately can be figured out with sufficient computer power), as opposed to quantum approaches which capitalize on fundamental physical laws. These laws mean that any attempts to intercept or read off the information will disturb the fragile quantum states carrying the information. The imposed fundamental limits here mean that there is no amount of care one can exercise that would enable this process without creating a detectable quantum disturbance. Thus, without embracing quantum solutions, the long-term security of hydropower and dam infrastructure, remains uncertain.
Traditional encryption is currently used to validate the legitimacy and authenticity of the sender and receiver, while also obfuscating the information from an attacker. This means that even if communication is intercepted Chen and Abu-Nimeh (2011), it cannot be read or understood unless the attacker has the decryption key. Traditional methods rely on secure creation and exchanges of keys to ensure end-to-end protection. Current attacks against encryption include incorrect implementation of encryption in software (vulnerabilities), attacks against the users, supply chain attacks, compromise of the keys, brute forcing the message, or analyzing the encrypted communication to derive the key. With the future advancement of quantum computing, the speed at which brute force attacks can successfully decrypt communications (using many current algorithms) could render them insufficient. The problem of infrastructure vulnerability means that attempts to evade security measures including cyber, malware, and side-channel attacks may generate results Rass et al. (2020). Reported attacks on dams and other critical infrastructure have revealed significant cyber-security gaps and problems in existing infrastructure, which is ultimately due to a lack of secure communications channels. Physically, the two primary channels over which information, commands, and instructions are conveyed/exchanged are either optical fiber or free space with no other comparable alternatives. Both these channels can be exploited by attackers to threaten the assets. This article proposes a solution and how it may be applied to this problem. Clearly, any solution necessarily should be commensurate with the rapidly growing and diversifying information and communications technologies encompassing edge computing and sensing Passian and Imam (2019); Farahi et al. (2012), IIoT (the Industrial Internet of Things), IoE (the Internet of Energy), etc. Such a solution must position the hydro security infrastructure for resiliency against increasingly advanced and sophisticated attacks.
Emerging quantum technologies promise to solve the security problem of communications channels. The most well-established quantum communication technology is currently quantum key distribution (QKD), which has been shown to achieve information-theoretic security (ITS), meaning it does not rely on any technology assumptions, such as what problems are difficult to compute. Such a solution has already been demonstrated in the form of the deployment of state-of-the-art QKD-based communications technologies across the electric grid Alshowkan et al. (2022); Evans et al. (2021); Grice et al. (2013); Kuruganti et al. (2014). To date, as technology transitions from research labs to the commercial sector, only a few commercial QKD systems have made their way to the market. These commercial systems are of basic design and not yet fully adaptable to the hydro environment. An evaluation and comparison of all QKD modalities against hydropower system’s requirements is needed (see Table 1). Logically, one may categorize noise sources in QKD operating in a hydropower environment into two main categories: those induced by the environment, as listed in Table 1, and those independent of it, as listed in Table 1, with related discussions elsewhere Scarani et al. (2009a); Gobby et al. (2004); Yuan et al. (2007); Rosenberg et al. (2005); Hiskett et al. (2007). While noise sources independent of the environment may be addressed with advances in technology and improved equipment, those induced by the dam environment may require specialized solutions tailored to the unique challenges posed by such a setting. Separating these categories could help in better understanding and mitigating the noise sources.
II Objective
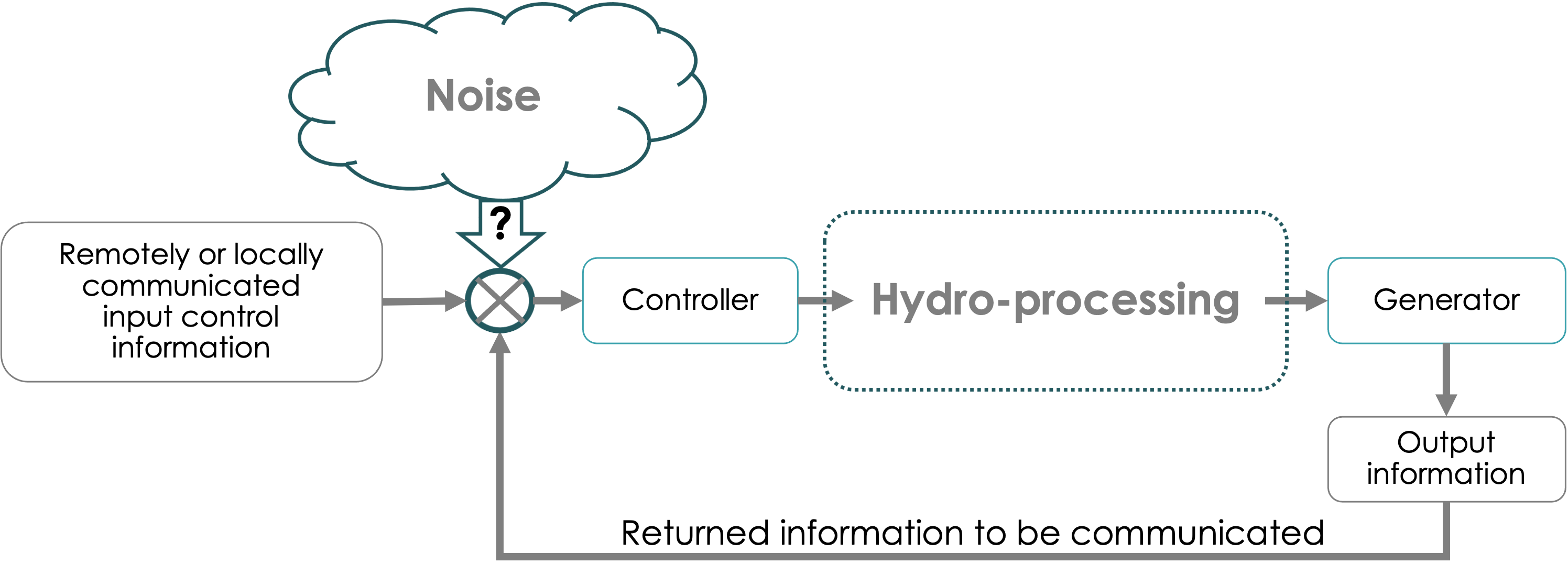
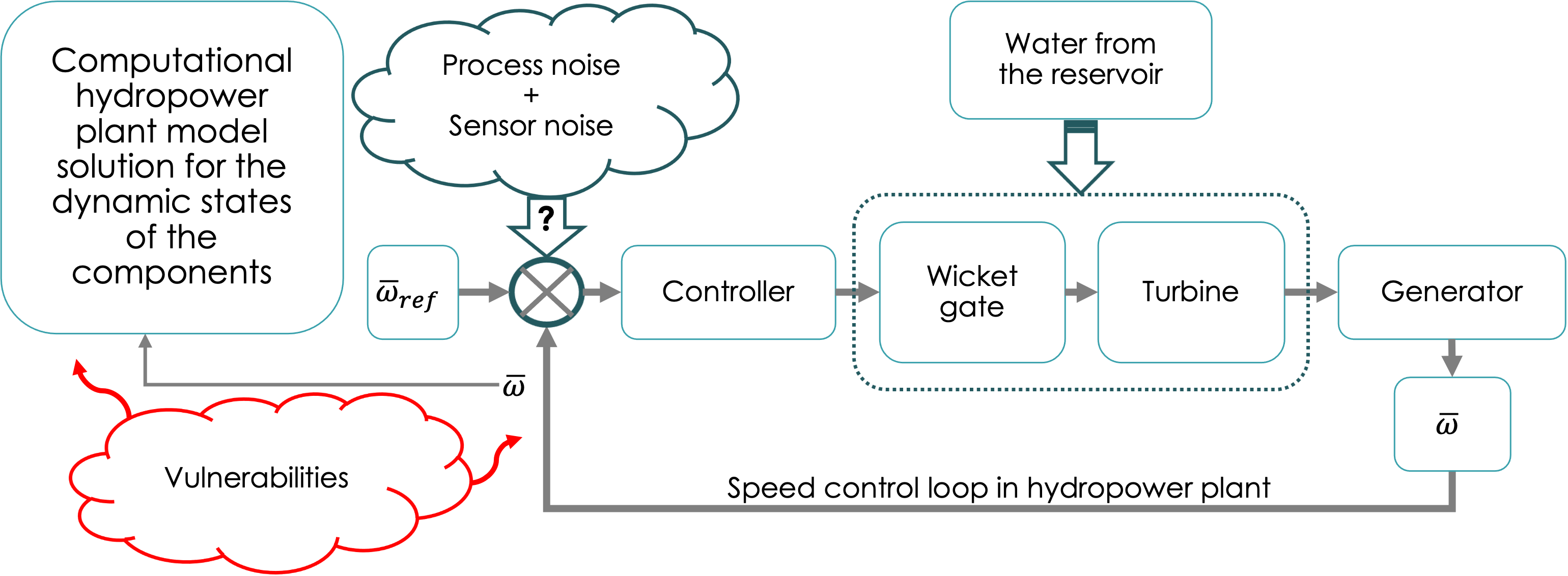
Our objective is to elucidate the utility of QKD for protecting hydropower assets and articulate what quantum security technologies can bring into the critical hydro infrastructure security domain. As simplistically depicted in Fig. 2, a hydropower system is composed of many networked sensors, control systems, and operators which need to communicate with each other over geographically diverse locations. A relevant use case of secure communications may therefore be the implementation of a communications channel between the control room and an equipment controller. This would not only prevent cyber-attacks but also any side-channel attacks. The communications link corresponding to this connectivity can be made secure with long-term security provided by QKD. Any information to be exchanged between a party on the internet and a party on the dam network requires encryption or authentication. QKD can share unique private keys that can be used for this purpose (for a simple quantum encryption example, see Appendix A). Therefore, the generation of secure keys over the communications link is the first step (see Fig. 3). Reaching a working understanding of the technical layout specific to a hydro facility could begin by building on previous work in carrying out cyber technical risk assessments including that of hydropower systems and dams Evans et al. (2021); Lawrence et al. (2020), and development of holistic cybersecurity risk reduction framework for fossil generation facilities Lawrence et al. (2020), as well as deployment of quantum communication for grid security Kuruganti et al. (2014) and Evans et al. (2021); Grice et al. (2013). Given that there are many such plant and systems-level examples of a cyber threat to physical devices of the power plant, during any pilot project, identifying a reasonable location in a dam or an equivalent testbed to implement the QKD is prudent. This important step lays the foundation for developing a similar use-case development methodology that can be applied across various hydro facilities. One may envision research and development of a security use-case taxonomy that can serve the broader energy infrastructure landscape. Such a taxonomy should be of direct benefit to the stakeholders since planning, marketing, energy distribution, customer privacy, service quality, and many other aspects of energy economics can be impacted by a better understanding of the security risks involved.
QKD is currently at the forefront of innovative communications technologies and is typically advertised as the next-generation security technology that, unlike conventional techniques, does not expire when bigger computers are built. QKD has been demonstrated for securing communications between parties on Earth Wang et al. (2022) as well as between Earth and satellites Liao et al. (2017); Yin et al. (2020). To implement QKD, we first note that there are different modalities of QKD. Despite, some modalities still being subject to intense research, new results are leaving research labs, and commercial systems are entering the market. For a brief description of the QKD modalities versus the specific requirements of the present use case see Table 1 (see also the recent survey by Sharma et al. Sharma et al. (2021)
III Quantum key distribution and its implementation
In 1984 the BB84 protocol was introduced by Bennett and Brassard Scarani et al. (2009b). Today, BB84 is just one instance of many possible QKD implementations that rely on the laws of quantum mechanics to share secret keys. As an example of a standard implementation, the polarization of individual photons can be used to encode information. In BB84, the simplest, oldest, and most developed protocol, Alice sends a signal of single photons with random polarizations to Bob, and since quantum states are disturbed when measured, any noise is attributed to an eavesdropper resulting in quantum bit error ratio (QBER), defined as:
| (1) |
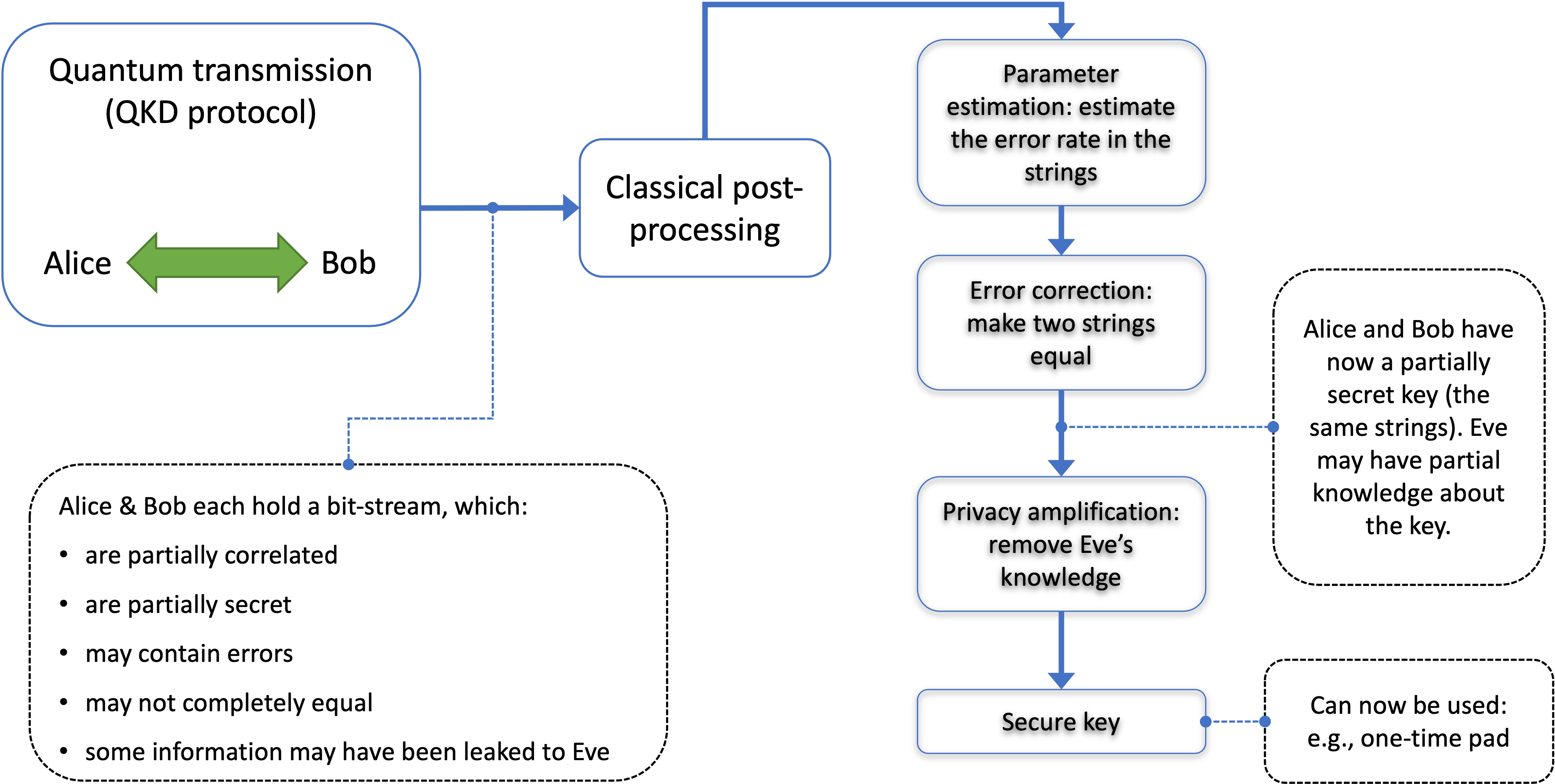
If the QBER is low enough, the two parties can distill a secret key. For many QKD protocols, the process to distill a secure key involves four main steps: raw key exchange, sifting, error correction, and privacy amplification, as shown in Fig. 3. Specifically, in the BB84 protocol, after the raw key is shared through the quantum channel, the sifted key is generated by Bob announcing, over a public classical channel, the basis he used to measure each photon. Alice then compares this with her basis choices. The bits corresponding to mismatched bases are discarded, resulting in the sifted key. Any QKD protocol will have errors in the sifted key due to the experimental imperfections and potential eavesdropping, which are corrected using an algorithm over the authenticated public channel. Finally, privacy amplification is also performed over the public channel to minimize the potential information about the key that Eve may have gathered in the previous three steps. Generally, QKD can be divided into discrete variable (DV) and continuous variable (CV) implementations. DV encoding, such as the polarization example above, involves detecting single quantum states with direct detection single-photon detectors, and results in discrete measurement data. In continuous variable encoding, homodyne detection is used to measure continuous variables of quantum light, namely phase, and amplitude, which carry information between Alice and Bob. CV QKD protocols generally have the potential for higher key generation rates than DV protocols, especially in the presence of lossy channels. This is due to the encoding and detection methods employed by CV systems. However, CV protocols, especially in high-loss scenarios, face challenges related to error reconciliation, given the Gaussian noise characteristics of their keys Scarani et al. (2009b). A benefit of CV protocols is that they can be implemented in shared fiber with classical communication systems without the destruction of the quantum signal Qi et al. (2010). QKD can also be divided into entanglement-based and prepare-and-measure implementations. In many entanglement-based QKD protocols, entangled states of light are generated and shared between Alice and Bob. This can be done by a third party or by one of the participants, such as Alice, who then sends one of the entangled particles to Bob. On the other hand, prepare-and-measure protocols, like BB84, involve Alice preparing a quantum state and sending it directly to Bob. For distances relevant to hydropower dams, prepare-and-measure protocols are the most practical and achieve the highest speeds Scherer et al. (2011). In practical QKD implementations, information is often encoded into weak coherent pulses, such as those from faint lasers. While single-photon or entangled photon sources are ideal for QKD, their practical implementation can be challenging. The decoy state protocol allows weak coherent sources to be used effectively by mitigating certain eavesdropping threats, making it possible to utilize cheaper and faster equipment for quantum light sources without compromising security Lo et al. (2005). This encoding method has evolved to what is called decoy state QKD because certain laser pulses will act as decoys to an eavesdropper for security purposes. Given that decoy-state BB84 is among the most developed protocols and gives the highest data rates for the relevant distances, it makes for a suitable field trial.

Studies of scientific and technical issues surrounding the security of practical implementation of QKD have illuminated the possibility of various conceivable side-channel attacks. Realistic expectations from the performance of QKD subsystems mean that QKD must be carefully implemented Lütkenhaus (2000); Makarov and Khan (2006) to avoid for example Trojan horse and photon-splitting attacks. These attack scenarios are difficult to mount on practical QKD systems which are evolving to safeguard against these and future loopholes in QKD implementation. The implementation of QKD begins by building its physical arrangement, which is composed of light sources, optical components to manipulate light, detectors, and measurement and processing electronics. Alternatively, one may explore the use of commercial QKD systems to generate the needed keys for information encoding. The information encoded by doing a bit-by-bit exclusive “OR” with these keys will be secure if the key is kept private, and the key is larger than the message size. Successful implementation of QKD is measured by generating keys using the physical realization of the diagram shown in Fig. 4.
The key questions to be answered are where QKD can be deployed in a hydropower communications network, and how it can be integrated with existing command and control interfaces. Of importance is the frequency of communications and the requirements of QKD-based one-time-pad (OTP) approaches to meet this need, in addition to communications latency requirements. A summary that systematically and collectively presents the application of QKD to the hydroelectric domain will help to lead the wider utilization of quantum security in hydro infrastructures. Our goal is stimulate the production of this document, which would also complement those focused on classical cybersecurity.
IV Approach
An approach to the security of hydropower assets based on quantum technologies should naturally be relevant to other energy infrastructure security science and technology. Therefore, a high degree of connectivity is expected amongst several works in the energy research portfolio. For example, in fossil power plant cyber security, some previous investigations focused on: 1) assessing how cyber risk changes across a facility’s life cycles, 2) performing consequence analysis to prioritize high-consequence events, 3) identifying the digital asset attack surface in sensors, instrumentation, and control equipment, and 4) mitigating cybersecurity control- or countermeasures Lawrence et al. (2020). Such reports Lawrence et al. (2020), describe the current industry cybersecurity best practices in fossil generation that are based on the first principles for cybersecurity engineering. Another specific example is related to grid security, where previous work focused on:
- •
-
•
Conducting an analysis of smart grid security needs Moreno Escobar et al. (2021).
-
•
Identifying the highest value security needs that can be met by QKD Kong (2020).
The performed analysis was based on the NIST Framework and Roadmap for Smart Grid Interoperability Standards Kuruganti et al. (2014), as described in the related report Gopstein et al. (2021). To achieve the technical objectives above, we may consider the following discussions. It is important to note that operational technology (OT) architectures used in hydropower control and safety systems present unique challenges and considerations from standard information technology (IT) deployment of QKD. OT systems rely on legacy equipment, proprietary, and unique operating systems, specialized protocols, and unique architecture requirements. In addition to the end-use case identification for QKD in hydropower, it is important to consider the impact of these architectures and infrastructure on QKD.
IV.1 Use-case definition for quantum security in hydro
In creating an optimum use case, previous experience, e.g., in performing a cyber security risk assessment of other architectures, may be leveraged to show the holistic security benefit of the QKD solution. Use cases anticipated to be identified include remote monitoring and control, remote sensor, and IIOT deployment. Critical communications which rely on strong authentication in hydropower include:
-
•
Securing remote interactive access (control, maintenance, and repairs)
-
•
Remote monitoring (remote sensors for control/safety/monitoring, remote monitoring only centers with unidirectional traffic)
-
•
Vendor monitoring
-
•
Supply chain security (validation of the authenticity of software and supply chain communications)
Control systems and operational technology (OT) rely on specific protocols for communications between field devices, programmable logic controllers, management servers and workstations, and other control system components. Many hydropower facilities that were designed with SCADAs (supervisory control and data acquisition systems) ces (2011); Alrefaei (2022) are being upgraded to distributed control systems (DCS) as hydropower facilities are undergoing component and digital modernization. The control systems must be carefully architected to provide reliability and safety. Latency and reliability of the communications are crucial in these applications and should be considered. A priority use case should:
-
•
document how it capitalizes on the specific environment of the dam/hydro facility or hydro testbed from a security point of view,
-
•
Identify security benefits/disadvantages of the QKD relative to traditional methods, in the identified use cases,
-
•
document how it highlights the practical (logistical) suitability/applicability of the QKD for implementation within the dam/hydro environment/testbed,
-
•
document a reference architecture for deployment in the selected use case,
-
•
identify operational impacts on QKD deployment,
-
•
highlight how the use case contributes to the missions of hydropower research facilities.
IV.2 Integration of the QKD system with the hydro communications system.
QKD is a novel quantum-based cybersecurity tool that allows for the generation AND secure distribution of truly random number streams. Field demonstration of QKD has been reported in the case of a real-world electric utility optical fiber network Evans et al. (2021). A “key” is simply a string of bits, that is, a sequence of 0s and 1s, and a “message” is in the form of a bit string. The end goal here is the successful use of keys generated using QKD by the communicating parties. For example, when the two communicating parties, share a private key, they can use that key to encrypt any messages they intend to send and decrypt any messages they receive. This encryption prevents eavesdropping from accessing any information in the messages. This could for example take the form of the complete set of communications needed for remote control of a dam, or communication for a SCADA system ces (2011). This would ultimately entail generating random bits, that are supplied to a computer hard drive or memory, at two (or more locations). These bits are then to be used for the encryption of the messages between the two locations. The fiber-based QKD is highly versatile as fibers are immune to electromagnetic interference, and mechanically flexible so that they can penetrate confined areas, elaborate machines, and devices. The QKD process begins with a quantum transmitter (typically referred to as Alice, as indicated in Fig. 5). The sender will have to generate light and prepare it in a specific quantum state. These light pulses, representing bit-strings, are then sent into an optical fiber to travel to another location, where they can be detected by a quantum receiver (typically referred to as Bob, as indicated in Fig. 5), at the other end of the fiber. After concluding the quantum operations between the two communicating parties, to generate the final keys, the bit-streams must be processed using post-algorithms. After processing the keys, as shown in Fig. 5, they can be used to protect the information between communicating entities (users, control systems, sensors, actuators, SCADAs, etc.).
QKD operation means that new keys are attempted to be generated. The conditions of the link and specifics of the QKD system determine the key rate. The key bit strings will be written to a file located on both Alice and Bob’s portions of the node. The keys and hydro communications are then collected on a local computer where the encryption and authentication are implemented Alshowkan et al. (2022). The most computationally efficient (and therefore lowest latency) method remains the one-time pad (OTP) method, where a message is combined with the exclusive OR operation (XOR) and the key. OTP exhibits ITS (information theoretical security), i.e., it is secure regardless of an adversary’s computational power, with the following requirements: (1) the keys must be truly random, be kept secret, and are used once only, and (2) the message length is less than or equal to the length of the key. The resulting communications are then sent out through a classical transceiver. An experimental demonstration of relaying keys between relevant hydro infrastructure locations could conclude after a QKD operation over a given period (e.g., hours). Such an experiment could implement QKD over a metro-area distance (typical of hydro facilities) using a commercial QKD system. The key metric governing QKD system performance is the secret key rate (SKR) – the (average) number of secret bits generated and distributed securely between parties per second. SKR, while largely dependent on the type of system and QKD protocol employed, is ultimately determined by the optical loss on a given fiber link. This loss , expressed in units of dB, is largely due to the fiber’s attenuation dB/km, which typically arises due to absorption and scattering mechanisms and can be written for a fiber of length km as: . It is crucial to minimize the losses, which also can be exacerbated by fiber-to-fiber connectors, sharp fiber bending, and splicing. High losses can compromise the effectiveness and security of the QKD process. The greater the optical loss, the lower the SKR, and vice versa. In situations where the optical link loss is significant, the SKR can be zero, indicating that no secret keys can be generated. From a practical standpoint, as noted above optical losses receive contributions from two main factors: the physical distance along the fiber between two points (length attenuation); and splice, or connection loss. The former is indicative of intrinsic material losses in the optical fiber itself. Modern optical fibers exhibit dB/km depending on fiber type, manufacturer, and wavelength of light. The latter is indicative of fiber-to-fiber connections, including in-field splices during deployment or following line breakage, and patch cable connections within a communications facility or substation. For this attenuation range, if, as simulated in Fig. 6, the fiber is 175 km long, the total loss in the fiber will be in the range: dB. Consequently, a viable QKD deployment must evaluate the optical fiber conditions from points A to B, and link-specific SKR must be measured.
In QKD, the eventual length of the secure key is determined by several factors including channel noise, error rates, and the specifics of the chosen protocol. While longer data collection times can yield larger secret keys, this could introduce delays before the key becomes available for encryption purposes. This is due to the need for post-processing steps like error correction, privacy amplification, and particularly the estimation of parameters such as the quantum bit error rate (QBER) using a substantial portion of the raw key. For real-world applications in hydropower plants, system optimization becomes vital. For instance, when several single-photon detectors in a command center are shared between remote links, the time each remote device utilizes a given detector should be optimized to reduce the total number of necessary detectors. This not only aids in efficient key generation but also in minimizing costs associated with hardware. The key rate or efficiency is not determined by a pre-selected length but rather emerges from the conditions of the quantum channel and post-processing. Practical QKD systems also need to address finite-size effects, where the security of the generated key can be influenced by statistical fluctuations, especially in systems with limited exchanged qubits. These effects become crucial in real-world applications such as hydropower plants, where reliable and timely key generation might be essential. An understanding of the communication frequency and topology between devices in such environments will be pivotal in tailoring QKD systems for optimal performance and cost-efficiency.
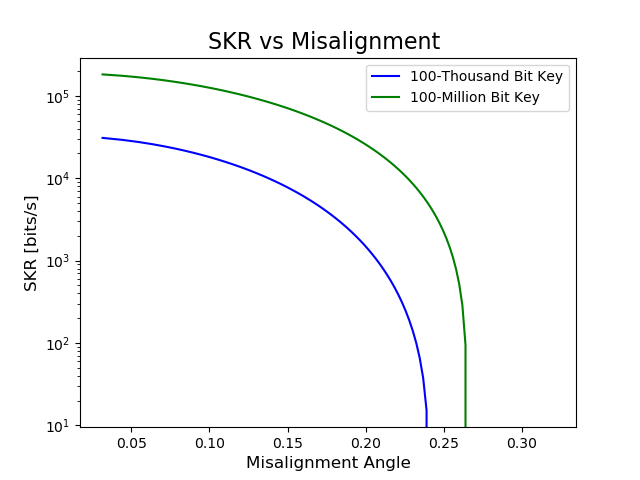
Figure 6 depicts how the SKR varies with distance for different key lengths, highlighting the impact of channel loss on the key rate. Similarly, Figure 6 illustrates the SKR’s sensitivity to misalignment angles in the system. The secure key rate (SKR), as derived from the theoretical framework introduced by Lim et al. Lim et al. (2014), illustrates this dependency. In the protocol proposed by Lim et al., Alice sends Bob randomly polarized coherent states in two orthogonal bases: X and Z. While the X basis contributes to the secure key, the Z basis states are publicly disclosed to estimate the error rate in the X basis. The effective secure key length is then described by:
| (2) |
where and represent the number of dark counts and single-photon counts at Bob’s detector, respectively. The term denotes the error rate in the x basis. The binary entropy function Wilde (2017) is given by:
| (3) |
which captures the maximum information Eve can deduce about the total key given the shared bits used to determine the error rate. As such, the term must be subtracted from the total to yield a portion of the key that remains concealed from Eve. encapsulates the information exposed during error correction, while the concluding terms address finite size effects. A deeper analysis, especially of terms rooted in the X basis signals and shaped by the sacrificed Z basis signals, is detailed in Lim et al. (2014).
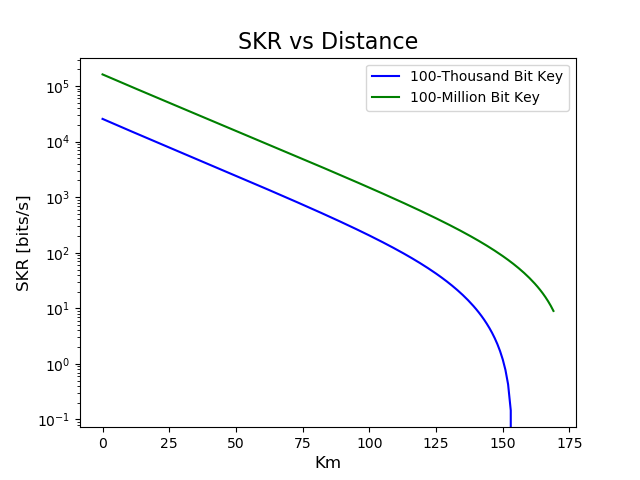
Figure 6 illustrates how the choice of key length, influenced by finite size statistics, affects the secure key rate and associated generation time. Specifically, at a distance of 1 km, starting with the aim to distill a 100-million-bit secure key yields a sifted key rate of approximately 98 kbps. In contrast, aiming for a 100-thousand-bit secure key results in a sifted key rate of about 25 kbps. Nevertheless, the larger initial key length necessitates a longer data collection duration: 17 minutes compared to the mere 4 seconds required for the shorter initial key length. In a continually operating secure communication system, these trade-offs highlight the importance of preemptive considerations. Factors such as communication frequency, average message size, and required security levels play a pivotal role in optimizing system performance and cost. Such metrics also influence choices regarding the QKD protocol, quantum encoding strategy, and equipment selection, ensuring that the system meets or exceeds the desired performance benchmarks.
The unique environment of a hydropower plant (see Table 1) introduces specific imperfections crucial in the context of a QKD system. Predominantly, additional loss and noise from such a setting can elevate the QBER rates for the QKD system. Given the finite size effect in the context of secure encryption, variations in QBER invariably gravitate towards the maximum bound of error. Hence, fluctuations introduced by the dam environment can be quite influential. The channel error model used for QKD simulations is described by Eq. 4 Lim et al. (2014):
| (4) |
where is the error rate for a coherent pulse with intensity , is the background noise rate of the detector (dark count rate), is the after-pulse probability, and is the detection rate. represents the loss due to the fiber optic cables and is given by , with being the fiber length in km. The term stands for the probability of error due to polarization changes in the channel and can be influenced by environmental factors.
Given that turbine operations, with their frequencies typically around 1 Hz and 30 Hz (Table 1), can introduce vibrations of typically less than 1 mm in amplitude and that generators, operating at either 50 Hz or 60 Hz, induce similar amplitudes of vibrations, the environment’s vibrational noise becomes crucial. Environmental factors, from seismic activities to localized events like machinery operations, can further introduce vibrational noise that influences the polarization states in fiber optics, which are sensitive to such changes Ding et al. (2017). Understanding and mitigating these effects is pivotal for QKD. For instance, correlating the vibrational frequency and amplitude data with phase changes in the QKD system could enable real-time counteraction of potential misalignments. As observed in Fig. 6, longer raw key lengths facilitate secure key generation even at higher misalignments, an important consideration in a noise-prone dam environment. To ensure high secure key rates, hydro QKD systems should adopt polarization stabilization techniques Mekhtiev et al. (2021); Wu et al. (2006). Typically, stabilization is achieved through feedback loops that monitor changes in the final state, enabling the sender to effectuate corrections. Given that numerous dams employ fiber-based sensors Inaudi and Blin ; de la Torre et al. (2021), integrating such vibrational and noise data into the stabilization algorithm offers a promising avenue to maintain optical alignment, optimizing the QKD system’s performance.
With measured SKR metrics in hand, the most appropriate cybersecurity strategy for QKD-secured hydro communications should be evaluated. This can be guided by the following principle: if the classical communication bandwidth needs for hydro is less than the SKR, then OTP may be employed (i.e., number of QKD bits ¿ number of classical bits requiring encryption). However, if the classical communication bandwidth needs exceed the link-specific SKR, then an ITS alternative method must be employed where the same QKD key can be used to authenticate multiple messages which can be done as long as a QRNG supplies a new nonce Alshowkan et al. (2022). Finally, regardless of the cryptography option above (OTP or authentication), the interface required to supply QKD keys to the user/application must be developed. This is dependent on the type, vendor, model of the user/application, and methods by which the device allows ingestion of external (i.e., QKD) key material. This final experiment will demonstrate the encryption/decryption of realistic hydropower command/control communications using QKD-supplied keys. Performance challenges include SKR changes with variations in the environment in which the subsystems of QKD are to operate. Dealing with various sources of noise (including those in Table 1) is of great importance in the successful generation of keys. For example, when both quantum and classical light are considered over the channel, a concern arises from “Raman noise”, which is unwanted light generated in the fiber material due to the use of stronger classical light. This effect is particularly pronounced when the wavelengths of the quantum and classical signals are closely multiplexed. However, when they are in separate bands, such as the quantum signal in the O band and the classical signal in the C band, the impact of Raman scattering is substantially mitigated Peters et al. (2009); Chapuran et al. (2009). Appropriate hardware choices can be made to better address the challenges and noise sources associated with the specific setting of the hydro facility. Although several QKD protocols exist, the well-established Bennet–Brassard protocol (BB84 protocol) makes for a suitable trial. Using the software, the dam communications can be interfaced with QKD keys. Similar experiments have been effectively performed to analyze and address implementation challenges facing the deployment of QKD systems in critical infrastructure, for example as demonstrated in the recent field test of three QKD systems on a real-world electric utility optical fiber network Evans et al. (2021), where one endpoint was a hydro/dam.
V Conclusions and outlook
Witnessing the overall growth trends of quantum technologies in solving energy infrastructure problems, the presented material introduced the specific use case of the hydro energy sector. The preliminary discussions presented may help the creation of a more specialized “Quantum for Hydro” roadmap. Parameters that characterize the hydro/dam environment, as summarized in Table 1, are different from those found in a laboratory setting. Some of the parameters likely also differ from those encountered in the electric power grid substations where QKD has been demonstrated. Typical ambient real-world environmental conditions of importance to the performance of any technical measuring device include temperature, humidity, and various noise levels (electromagnetic, acoustic, wind, corrosion, contamination, etc.). QKD is built from sensitive optical and electronic components and devices, each with a set of specifications. Therefore, these parameters, if for example out of range, could impact the rate of key generation. Consideration for application of quantum sensing for environmental monitoring may also prove useful in conjunction with QKD. In compiling such a roadmap, consideration of important issues such as interoperability between QKD systems that operate with dissimilar implementations must be considered. In doing so, QKD standards by the ETSI Quantum-Safe Cryptography Working Group, and QKD network and QKD systems activities within ITU-T SG13 and SG17, respectively, will be put in perspective Evans et al. (2021).
Acknowledgements.
Funding for this work was provided in part by the U.S. Department of Energy (DOE), Office of Cybersecurity Energy Security and Emergency Response (CESER) through the Risk Management Tools and Technologies (RMT) Program, and in part by the Laboratory Directed Research and Development Program at Oak Ridge National Laboratory (ORNL) under US DOE Grant No. DE-FG2-13ER41967. We also thank P. G. Evans for discussions and feedback. AG and GS acknowledge support from the Army Research Office under award W911NF-19-1-0397, and NSF under grant DGE-2152168. ORNL is managed by UT-Battelle, LLC, for the US DOE under Contract No. DE-AC05-00OR22725. The US Government retains and the publisher, by accepting the article for publication, acknowledges that the US Government retains a nonexclusive, paid-up, irrevocable, worldwide license to publish or reproduce the published form of this manuscript or allow others to do so, for the US Government purposes.References
- Rass et al. (2020) S. Rass, S. Schauer, S. König, and Q. Zhu, Cyber-security in critical infrastructures, Vol. 297 (Springer, 2020).
- Whyatt et al. (2021) M. Whyatt et al., Toward a Resilient Cybersecure Hydropower Fleet: Cybersecurity Landscape and Roadmap 2021, Tech. Rep. PNNL-32053 (PNNL, 2021).
- cis (2019) Dams Sector Landscape, Tech. Rep. (CISA, U.S. Department of Homeland Security, Cybersecurity and Infrastructure Security Agency, 2019).
- Singh et al. (2020) P. Singh et al., Materials Today: Proceedings 28, 1569 (2020).
- Ratnam et al. (2020) E. L. Ratnam, K. G. Baldwin, P. Mancarella, M. Howden, and L. Seebeck, The Electricity Journal 33, 106833 (2020), special Issue: The Future Electricity Market Summit.
- Chen and Abu-Nimeh (2011) T. M. Chen and S. Abu-Nimeh, Computer 44, 91 (2011).
- Passian and Imam (2019) A. Passian and N. Imam, Sensors (Basel, Switzerland) 19, 4048 (2019).
- Farahi et al. (2012) R. Farahi et al., ACS Nano 6, 4548 (2012).
- Alshowkan et al. (2022) M. Alshowkan, P. G. Evans, M. Starke, D. Earl, and N. A. Peters, Scientific Reports 12, 12731 (2022).
- Evans et al. (2021) P. Evans et al., IEEE Access 9, 105220 (2021).
- Grice et al. (2013) W. Grice, P. Evans, and R. Pooser, “Quantum key distribution for the smart grid,” in IEEE Vision for Smart Grid Communications: 2030 and Beyond (2013).
- Kuruganti et al. (2014) T. Kuruganti et al., Quantum Key Distribution Applicability to Smart Grid Cybersecurity Systems, Tech. Rep. (ORNL, 2014) gridSQuARe Project.
- Scarani et al. (2009a) V. Scarani, H. Bechmann-Pasquinucci, N. J. Cerf, M. Dušek, N. Lütkenhaus, and M. Peev, Reviews of Modern Physics 81, 1301 (2009a).
- Gobby et al. (2004) C. Gobby, Z. Yuan, and A. Shields, Applied physics letters 84, 3762 (2004).
- Yuan et al. (2007) Z. Yuan, B. Kardynal, A. Sharpe, and A. Shields, Applied Physics Letters 91, 041114 (2007).
- Rosenberg et al. (2005) D. Rosenberg, C. Peterson, J. Harrington, P. Rice, A. Nakassis, N. Dallmann, et al., New Journal of Physics 7, 71 (2005).
- Hiskett et al. (2007) P. Hiskett, G. Buller, A. Loudon, J. Matthews, G. Pryde, A. Gilchrist, et al., New Journal of Physics 8, 193 (2007).
- Lawrence et al. (2020) J. Lawrence et al., Fossil Power Plant Cyber Security Life-Cycle Risk Reduction, A Practical Framework for Implementation, Tech. Rep. (United States, 2020).
- Pakki Bharani Chandra and Potnuru (2021) K. Pakki Bharani Chandra and D. Potnuru, International Journal of Ambient Energy 42, 203 (2021).
- Wang et al. (2022) S. Wang et al., Nature Photonics 16, 154 (2022).
- Liao et al. (2017) S. Liao et al., Nature 549, 43 (2017).
- Yin et al. (2020) J. Yin et al., Nature 582, 501 (2020).
- Sharma et al. (2021) P. Sharma, A. Agrawal, V. Bhatia, S. Prakash, and A. K. Mishra, IEEE Open Journal of the Communications Society 2, 2049 (2021).
- Scarani et al. (2009b) V. Scarani et al., Reviews of Modern Physics 81 (2009b).
- Qi et al. (2010) B. Qi, W. Zhu, L. Qian, and H.-K. Lo, New Journal of Physics 12, 103042 (2010).
- Scherer et al. (2011) A. Scherer et al., Optics express 19 (2011).
- Lo et al. (2005) H. K. Lo et al., Physical Review Letters 94 (2005).
- Wolf (2021) R. Wolf, Quantum key distribution (Springer, 2021).
- Lütkenhaus (2000) N. Lütkenhaus, Physical Review A 61, 052304 (2000).
- Makarov and Khan (2006) V. Makarov and J. Khan, Optics letters 30, 1043 (2006).
- Pljonkin and Singh (2018) A. Pljonkin and P. K. Singh, in 2018 Fifth International Conference on Parallel, Distributed and Grid Computing (PDGC) (2018) pp. 795–799.
- Moreno Escobar et al. (2021) J. J. Moreno Escobar, O. Morales Matamoros, R. Tejeida Padilla, I. Lina Reyes, and H. Quintana Espinosa, Sensors 21, 6978 (2021).
- Kong (2020) P.-Y. Kong, IEEE Systems Journal 16, 41 (2020).
- Gopstein et al. (2021) A. Gopstein et al., “Nist framework and roadmap for smart grid interoperability standards, release 2 (latest 4),” (2021).
- ces (2011) “21 steps to improve cyber security of scada network,” (2011).
- Alrefaei (2022) A. S. Alrefaei, 2022 Fifth National Conference of Saudi Computers Colleges (NCCC) , 88 (2022).
- Lim et al. (2014) C. Lim et al., Physical Review A 89 (2014).
- Wilde (2017) M. M. Wilde, “Preface to the second edition,” in Quantum Information Theory (Cambridge University Press, 2017) pp. xi–xii, 2nd ed.
- Moschandreou et al. (2021) E. Moschandreou et al., Physical Review A 103 (2021).
- Ding et al. (2017) Y.-Y. Ding, H. Chen, S. Wang, D.-Y. He, Z.-Q. Yin, W. Chen, Z. Zhou, G.-C. Guo, and Z.-F. Han, Optics Express 25, 27923 (2017).
- Mekhtiev et al. (2021) E. Mekhtiev, I. Gerasin, N. Rudavin, A. Duplinsky, and Y. Kurochkin, in Journal of Physics: Conference Series, Vol. 2086 (IOP Publishing, 2021) p. 012092.
- Wu et al. (2006) G. Wu, J. Chen, Y. Li, and H. Zeng, arXiv preprint quant-ph/0606108 (2006).
- (43) D. Inaudi and E. R. Blin, .
- de la Torre et al. (2021) O. de la Torre, I. Floris, S. Sales, and X. Escaler, Sensors 21, 4272 (2021).
- Peters et al. (2009) N. A. Peters, P. Toliver, T. E. Chapuran, R. J. Runser, S. R. McNown, C. G. Peterson, D. Rosenberg, N. Dallmann, R. J. Hughes, K. P. McCabe, J. E. Nordholt, and K. T. Tyagi, New Journal of Physics 11, 045012 (2009).
- Chapuran et al. (2009) T. E. Chapuran, P. Toliver, N. A. Peters, J. Jackel, M. S. Goodman, R. J. Runser, S. R. McNown, N. Dallmann, R. J. Hughes, K. P. McCabe, J. E. Nordholt, C. G. Peterson, K. T. Tyagi, L. Mercer, and H. Dardy, New Journal of Physics 11, 105001 (2009).
- Bloom et al. (2022) Y. Bloom, I. Fields, A. Maslennikov, and G. G. Rozenman, Physics 4, 104 (2022).
- Siehler (2011) J. A. Siehler, “The hamming(7,4) code,” (2011).
- Urbina et al. (2016) D. I. Urbina, J. A. Giraldo, A. A. Cardenas, and N. O. Tippenhauer, in IFIP Annual Conference on Data and Applications Security and Privacy (Springer, Cham, 2016) pp. 65–81.
- Lee et al. (2016) R. M. Lee, M. J. Assante, and T. Conway, Analysis of the Cyber Attack on the Ukrainian Power Grid, Tech. Rep. (Electricity Information Sharing and Analysis Center (E-ISAC), 2016).
- Ouellet et al. (2022) S. M. Ouellet, J. Dettmer, G. Olivier, T. DeWit, and M. Lato, Communications Earth & Environment 3, 301 (2022).
- Antonovskaya et al. (2019) G. Antonovskaya, N. Kapustian, I. Basakina, N. Afonin, and K. Moshkunov, Geosciences 9 (2019), 10.3390/geosciences9040187.
- Baron et al. (2022) P. Baron, M. Kočiško, S. Hlavatá, and E. Franas, Advances in Mechanical Engineering 14, 16878132221101023 (2022), https://doi.org/10.1177/16878132221101023 .
- Mohanta et al. (2017) R. K. Mohanta, T. R. Chelliah, S. Allamsetty, A. Akula, and R. Ghosh, Engineering Science and Technology, an International Journal 20, 637 (2017).
- Quaranta and Müller (2021) E. Quaranta and G. Müller, International Journal of Environmental Research and Public Health 18, 13051 (2021).
- Diamanti et al. (2016) E. Diamanti, H.-K. Lo, B. Qi, and Z. Yuan, npj Quantum Information 2, 1 (2016).
- Nandal et al. (2020) R. Nandal, A. Nandal, K. Joshi, and A. K. Rathee, (2020).
- Loudon (2000) R. Loudon, The quantum theory of light (OUP Oxford, 2000).
Appendix A Simplified Examples of Classical and Quantum Encryption
Given the cross-disciplinary nature of our work, it is prudent to provide a simplified introduction to quantum cryptography. Below, starting with a simple classical encryption using the (Vernam cipher) one-time pad (OTP) and quantum encryption through the BB84 QKD protocol, we discuss how a simple message may be encrypted using QKD keys via post-processing protocol. Other simplified QKD experiments and related theories include the work by Bloom et al. Bloom et al. (2022).
A.1 Classical encryption
As an example of classical encryption, suppose we would like to securely communicate the message “dam” between an infrastructure point and a remote control unit. Let us write it in binary representation based on ASCII values. In the ASCII standard, each character is represented using a unique 7-bit binary code. For instance, the binary representation for the character “d” is obtained by translating its ASCII representation (100) to a 7-bit binary string, yielding 1100100. Therefore,
| (5) |
The one-time pad (OTP) is a symmetric-key encryption technique known to be unbreakable when used correctly. It applies a key (usually a random sequence of bits) to the message via a bitwise operation, typically, XOR to produce the ciphertext. To assure security using the OTP, the key should be as long as the plaintext, used only once, and kept secret. As our key, let us take the word “key”. The binary representation for “key” is:
| (6) |
Let us now perform the XOR operation, which is defined as follows. Given two binary values and , the XOR (exclusive or) operation returns a value of 1 if the bits being compared are different, and 0 if they are the same. Formally:
| (7) |
and, if we XOR the result with , we retrieve the original value :
| (8) |
Thus, for our “” operation, we write:
| 1100100 (d) | (9) | |||
| 1100001 (a) | (10) | |||
| 1101101 (m) | (11) |
Thus, the encrypted message is:
| (12) |
To decipher the ciphertext produced using the OTP, we reapply the same XOR operation with the same key. This returns us to the original plaintext. Using our previously derived ciphertext and the key:
| 0001111 | (13) | |||
| 0000100 | (14) | |||
| 0010100 | (15) |
Thus, when deciphered, the ciphertext using the key gives us back the original message:
| (16) |
This illustrates the reversible nature of the XOR operation: the encryption and decryption processes are effectively the same operation. The generation of classical keys, especially for cryptographic purposes, is more intricate than just using a straightforward binary representation of a word, as we simplistically did above. The strength of cryptographic systems often hinges on the quality of the keys and the randomness or unpredictability of key generation. Classical keys may be generated via true, as well as pseudorandom random number generators. Key management practices, including generation, storage, distribution, rotation, and disposal, are vital.
A.2 Quantum encryption
The above encryption can also be performed using the key generated via QKD. The communicating parties (Alice and Bob) could use a QKD protocol such as BB84 to generate a shared, secret random bit string. This process involves sending quantum states (e.g., photon polarizations) between Alice and Bob and performing post-processing following the steps in Fig. 5 and Table 1 (see R. Wolf Wolf (2021) for further reading). Alice can now use the shared key from the QKD process as the OTP key to XOR with her message, “dam” in binary.
Suppose the QKD-generated key is (where each is 7 bits in our toy example). She then XORs her message with this key to get the ciphertext:
The encrypted message is then . For decryption, Bob uses the same QKD-generated key to XOR with the received ciphertext to retrieve the original message.
Step 1: Preparation & Transmission by Alice
-
•
Alice randomly selects bits and their corresponding bases. The bases can be:
-
–
Rectilinear, represented as Z-basis: and .
-
–
Diagonal, represented as X-basis: and .
-
–
-
•
For demonstration, consider the binary of ”dam”: 1100100 1100001 1101101. Alice selects the first 3 bits: 110.
-
–
For the first bit (1), Alice chooses the rectilinear basis and sends .
-
–
For the second bit (1), Alice chooses the diagonal basis and sends .
-
–
For the third bit (0), Alice chooses the rectilinear basis and sends .
-
–
Step 2: Measurement by Bob
-
•
Bob randomly selects a basis for each received qubit and performs a measurement.
-
–
For the first qubit, he chooses rectilinear and measures 1.
-
–
For the second qubit, he chooses rectilinear (a mismatch with Alice) and gets a random result, say 0.
-
–
For the third qubit, he chooses rectilinear and measures 0.
-
–
Step 3: Basis Discussion
-
•
Alice and Bob publicly disclose the bases they used.
-
•
They compare their choices:
-
–
For the first bit, both chose rectilinear - they retain Bob’s result.
-
–
For the second bit, they used different bases - they discard Bob’s result.
-
–
For the third bit, both chose rectilinear - they retain Bob’s result.
-
–
-
•
Their resulting raw key is now: 10.
Step 4: Error Estimation
-
•
A subset of the raw key is selected for error testing.
-
•
They compare their respective bits in this subset publicly.
-
•
Calculate QBER = (number of errors in subset)/(size of subset).
-
•
If QBER exceeds a threshold, the protocol is aborted due to potential eavesdropping.
Step 5: Privacy Amplification
-
•
Aims to reduce any potential eavesdropper’s information to an insignificant level.
-
•
Two-universal hash functions might be applied to the key to produce a shorter, more secure key. For example, take the raw key to be: . Consider a very basic hash function defined as:
-
–
Break the string into groups of 2.
-
–
For each group:
-
*
If it is , it maps to .
-
*
If it is or , it maps to .
-
*
If it is , it maps to .
Given the original key: applying the hash function produces: which is shorter than the original key as a result of a specific transformation.
-
*
-
–
-
•
Classical error-correcting codes can be used to rectify errors introduced by the quantum channel. For example, consider the Hamming(7,4) code Siehler (2011):
-
–
Designed to encode 4 bits of data into 7 bits by adding 3 parity bits.
-
–
Given a 4-bit data ‘1101‘, encoding adds parity bits to produce: 0 0 1 0 1 1 0.
-
–
If an error flips the 6th bit during transmission, we receive: 0 0 1 0 1 0 0.
-
–
The error is detected and corrected using the parity bits, restoring the original encoded string.
-
–
Our plaintext message “dam” has a length of 21 bits, as noted above. Due to the probabilistic nature of quantum measurements and the random choice of bases, typically only around 50% of the initially sent qubits contribute to the raw key post key sifting. So, if Alice wants to ensure a shared secret key of length 21 bits (to match the plaintext message length), she will need to initiate the process with more than 42 qubits (assuming a 50% retention rate after sifting). Thus, the process requires the transmission of a greater number of qubits than the intended message length due to the key sifting process and potential eavesdropping checks.
Appendix B Tables
| Cybersecurity Issue | Description | Impact | Role of QKD |
|---|---|---|---|
| Remote Control System Attacks | Compromise of SCADA Alrefaei (2022) systems controlling dam operations. | Dam failure, potential loss of life, and environmental damage. | Secure keys via QKD encrypt communication, thwarting unauthorized access to the control system. |
| Sensor Spoofing Urbina et al. (2016) | Interference with sensors, leading to inaccurate readings and unsafe operations. | Dam failure, potential loss of life, and environmental damage. | Secure or authenticated communication between sensors and control system, reveals data tampering. |
| Communication Interception Chen and Abu-Nimeh (2011) | Interception or injection of malicious commands in communication channels. | Dam failure, potential loss of life, and environmental damage. | Secure all communications, hindering interception or data tampering. |
| Denial of Service (DoS) Attacks Lee et al. (2016) | Overloading communication channels or control systems. | Operational disruption leading to flooding or other issues. | Indirectly aids by protecting from vulnerabilities exploited in DoS. |
| Physical Security Breaches | Tampering of equipment or insertion of malicious hardware/software. | Dam failure, potential loss of life, and environmental damage. | Indirectly aids by strengthening overall cybersecurity infrastructure. |
| Supply Chain Attacks | Pre-installation compromise of hardware or software. | Compromised dam components leading to security breaches. | Indirectly aids by protecting from vulnerabilities exploited due to compromised components. |
| Insider Threats | Misuse of sensitive systems by authorized individuals. | Operational disruption or sabotage. | Secure communication between control systems and authorized personnel, preventing unauthorized access. |
| Noise Source | Description | Typical Sensor |
|---|---|---|
| Turbine Operations | Noise from turbine movement both in air and underwater. Frequencies Hz with amplitudes mm. | Hydrophone (underwater), Microphone (airborne) |
| Gates and Valves | Noise due to dam gate or spillway operations. Varies based on size and operation speed. | Vibration sensors, Microphone |
| Pumps and Machinery | Noise from operational machinery. Typically Hz. | Microphone, Vibration sensors |
| Flow Turbulence | Noise from rapid and turbulent water flow. Hz. | Hydrophone |
| Waterfall/Spill | Noise due to water spillage. Frequency depends on water volume and height of fall. | Hydrophone, Microphone |
| Bubble Formation | Noise due to bubble formation and collapse. Hz. | Hydrophone |
| Transformer Operations | Buzzing or humming from transformers. Typically at 50 Hz or 60 Hz. | Magnetic field sensors, Microphone |
| High Voltage Equipment | Noise from insulator discharges. Broadband noise typically spanning 10 Hz to 1 kHz. | Electromagnetic sensors, Microphone |
| Vibration | Vibrations inherent to dam structures. Spanning from very low frequencies (¡1 Hz) due to seismic activities to high frequencies (¿100 Hz) from machinery operations. | Accelerometers, Vibration sensors |
| Thermal Expansion/Contraction | Noise from temperature-induced structural changes. Frequency varies based on structure size and material. | Vibration sensors, Microphone |
| Wildlife Activities | Sounds from local fauna. Frequencies are species-specific, ranging broadly from 1 Hz to 10 kHz. | Microphone, Hydrophone |
| Weather Patterns | Noise from atmospheric disturbances, thunder, tornado. Broad frequency range from ¡1 Hz (thunder rumble) to ¿10 kHz (lightning crack). | Wind sensors, Microphone |
| Vehicle Traffic | Noise from vehicular activities. Frequencies range from 20 Hz (engine hum) to 2 kHz (horn). | Accelerometers, Vibration sensors, Microphone |
| Construction/Maintenance | Noise from maintenance or construction work. Broad frequency range depending on tools and machinery. | Accelerometers, Microphone, Vibration sensors |
| Temperature Fluctuations | Ambient temperature changes affecting equipment. Changes can cause material contractions or expansions leading to noise. | Thermocouples, Infrared sensors |
| Moisture/Condensation | Moisture interference with equipment. Can cause electrical noises or material deformations. | Humidity sensors, Moisture meters |
| Noise Source | Description |
|---|---|
| Quantum Bit Error Ratio (QBER) | Represents the ratio of bits that are received in error. Though not a direct noise source, QBER quantifies the impact of various technical factors and imperfections in QKD systems. |
| Dark Counts | False counts arising in photon detectors due to thermal fluctuations or other non-signal measurement events. |
| Dead Time | Time taken by a detector to recover after detecting a photon. Photons arriving during this interval can lead to loss. |
| Detector Jitter | Uncertainty in a detector’s time response when it receives a signal, arising from electronic and photonic fluctuations. |
| Beam Splitting/Coupling Inefficiencies | Imperfections in beam splitters or inefficient coupling into optical fibers leading to photon loss. |
| Fiber or Channel Attenuation | Losses in the optical channel or the transmission fiber. |
| Multi-Photon Emissions | Occurrences when sources produce multi-photon pulses, introducing vulnerabilities and noise. |
| Phase Fluctuations | In protocols like Differential Phase Shift QKD, phase fluctuations in transmission fiber can cause errors. |
| Timing Jitter/Synchronization | Uncertainty or variations in the timing of a system’s clock or reference signal, affecting synchronization. |
| Quantum State Preparation | Imperfections in preparing quantum states like specific polarization states. |
| Spatial Mode Mismatches | Mismatches when transmitting quantum states over channels, leading to decreased detection probabilities. |
| Back Reflections/Scattering | Reflections from interfaces or scattering within components introducing noise photons. |
| QKD Modality | Hydropower System’s Requirements |
|---|---|
| BB84 Protocol (see e.g. Nadal et al. Nandal et al. (2020) for other protocols) | • Suitable for existing optical fiber networks. • Direct point-to-point setups for small-scale plants. • Economically efficient for short distances. |
| Decoy State QKD | • Robust against photon number splitting attacks. • Beneficial for medium to large-scale plants with potential eavesdropping threats. |
| Continuous-Variable QKD | • Preferred for metropolitan-area networks. • Requires direct trusted relay and quantum repeaters for long distances. • Suitable for high transmission rate requirements. |
| MDI-QKD | • Ideal for infrastructures at risk from sophisticated adversaries. • Eliminates detector side-channel vulnerabilities at center detection node. • May require higher initial investment for equipment. |
| Satellite-based QKD | • Best for remote facilities over vast areas. • Capital-intensive but offers broad coverage. • Enables global scale secure communications but at low rates. • Requires clear sky conditions for optimal operations. |
| Other Considerations | • Maintenance and operational costs. • Scalability to future expansions. • Interoperability with existing communication systems. • Training and expertise requirements. • Key management/revocation/lawful intercept requirements |
| Step | Description/Equation |
|---|---|
| Error Estimation | |
| Information Reconciliation | Uses error-correcting codes to rectify key discrepancies. The Cascade protocol is popular; it entails key division, shuffling, and parity comparison. |
| Privacy Amplification | Aims to eliminate any eavesdropper’s partial information. Typically employs universal hash functions, represented as: . |
| Key Sifting | Particularly relevant in the BB84 protocol. Alice and Bob publicly disclose the bases chosen for each qubit. Qubits with differing bases are discarded. |
| Authentication | Confirms genuine communication between Alice and Bob. Utilizes classical authentication methods in tandem with previously shared secret keys. |
Appendix C Glossary
| Glossary of Terms and Definitions | |
|---|---|
| Term | Definition |
| Fiber’s Attenuation: Represented in units of dB/km, it is the property of the optical fiber that quantifies the loss of signal strength per unit length of fiber. | |
| Alice and Bob | Conventionally used names to denote the sender and receiver in cryptographic communications, including in QKD systems. |
| Attenuation | The reduction of signal strength as it travels through a medium, such as an optical fiber, due to absorption, scattering, and other loss mechanisms. |
| BB84 | A quantum key distribution protocol developed in 1984 by Bennett and Brassard, using two non-orthogonal bases Wilde (2017). |
| Binary Entropy Function | A function quantifying the maximum possible information about the total key based on shared bits between parties. Typically denoted as , it represents the uncertainty of a binary random variable and is defined as Wolf (2021); Wilde (2017): H(p) = -p log_2(p) - (1-p) log_2(1-p), where is the probability of one of the two outcomes (e.g., a bit being 1). Consequently, is the probability of the other outcome (the bit being 0). is defined for with a maximum of 1, which occurs when , indicating maximum uncertainty (i.e., both outcomes are equally probable). When or , , there is no uncertainty. In our work, Eq. 3 yields the error rate in a specific basis ( basis) and represents the maximum possible information rate that can be deduced about the total key based on shared bits for error estimation. |
| Channel Loss Parameter () | A dimensionless parameter derived from the total optical loss () and representing the linear loss due to the fiber optic cables in the QKD system. |
| Coherent States | A coherent quantum state is defined as: — α⟩= e^-—α—22 ∑_n=0^∞ αnn! — n ⟩, where is a complex number and are the photon number (Fock) states Loudon (2000). Such states play a fundamental role in quantum optics due to their semi-classical nature and are crucial in various quantum communication protocols, including QKD Wolf (2021). |
| Continuous Variable-Quantum Key Distribution (CV-QKD) | CV-QKD employs continuous quantum variables such as the quadratures of the electromagnetic field to encode information. The most common CV-QKD protocols are based on coherent states using Gaussian modulation of amplitude and phase, and they use homodyne or heterodyne detection for the decoding process. This approach has the advantage of being compatible with conventional telecom technology, potentially allowing for more straightforward integration into existing networks. However, it typically makes more assumptions that detector noise can be “trusted,” and calibrated away. |
| Dark Count | Counts detected in the absence of light, usually due to noise or unwanted signals. |
| Decoy State QKD | A variation of the BB84 QKD protocol which employs additional signal states to improve security against photon number splitting attacks. |
| Discrete Variable (DV) QKD | Discrete Variable (DV) QKD leverages the quantum properties of individual photons to secure communication. It typically operates using polarization or phase encoding schemes to encode the quantum bits (qubits). Protocols such as BB84, B92, and SARG04 are well-known in the DV-QKD sphere Nandal et al. (2020); Kong (2020). |
| Error Correction | A process to identify and correct errors in the quantum key transmission. |
| Error Rate in the X Basis () | A parameter representing the rate of error in the x basis of the key during QKD operations. |
| Error Reconciliation | A procedure in QKD to correct any discrepancies in the key between the two parties. |
| Eve | Eavesdropper: Conventionally used name to denote a potential attacker trying to gain unauthorized access to the secure communication. All errors are typically attributed to her. |
| Fiber-Based Loss | Refers to the loss of signal in optical fibers, affecting the transmission of quantum signals. |
| Fiber Length () | The physical distance covered by the optical fiber, usually represented in kilometers. |
| Finite Size Effects | Describes the effects or limitations of having a finite number of signals in QKD. |
| Homodyne Detection | A technique used in quantum cryptography for measuring a quantum signal through interference with a local oscillator using balanced difference detection. |
| Hydropower | The generation of power through the use of the gravitational force of falling or fast-running water. |
| Information Theoretical Security (ITS) | A security paradigm that assures confidentiality regardless of the computational resources of an adversary. |
| Leakage During Error Correction () | The segment of key information that might be exposed to an eavesdropper during error correction procedures in the QKD protocol. |
| Misalignment Angle | Refers to the variation in the angle of the initial polarization state, which can be caused by factors such as thermal fluctuations or physical stress on the fiber. |
| One-Time Pad (OTP) | A method of encryption where a message is combined with a key using exclusive OR (XOR) operation. |
| Phase Modulation | The modulation of the phase of a carrier signal to encode information, often used in QKD systems to encode quantum information. |
| Photon Avalanche Detectors | Photodetectors that can detect low-intensity light down to single photons, often used in QKD setups. |
| Polarization | Refers to the orientation of oscillations in electromagnetic waves, used to encode information in quantum states in the context of QKD. |
| Quantum Bit Error Rate (QBER) | The rate of errors that occur during quantum transmission. |
| Quantum Cryptography (QC) | A method of securing communication channels by applying quantum mechanics principles. |
| Quantum Key Distribution (QKD) | A cryptographic protocol based on quantum mechanics to securely distribute random private keys between two parties. |
| Secure Key Length () | The length of the secure key, here denoted , in a QKD system, chosen based on various parameters to maintain a balance between security and system performance. |
| Secure Key Rate (SKR) | The rate at which a QKD system can produce secure shared private keys, influenced by factors like distance and error rate. A metric to evaluate the performance of a QKD system |
| Secure Rate Formula | A mathematical representation of the rate at which a QKD system can generate secure keys. |
| Total Optical Loss () | Represented in units of dB, it measures the total loss in the system, arising due to the fiber’s attenuation () and the length of the fiber (). |