Quantum Merlin-Arthur and proofs without relative phase
Abstract
We study a variant of where quantum proofs have no relative phase (i.e. non-negative amplitudes, up to a global phase). If only completeness is modified, this class is equal to [GKS14]; but if both completeness and soundness are modified, the class (named by Jeronimo and Wu [JW23]) can be much more powerful. We show that with some constant gap is equal to , yet with some other constant gap is equal to . One interpretation is that Merlin’s ability to “deceive” originates from relative phase at least as much as from entanglement, since .
1 Introduction
The strangeness of quantum states has at least two fundamental sources: entanglement, the source of “spooky action at a distance”; and relative phase, which allows for destructive interference. We use complexity theory to probe these sources of strangeness. Extending the main result of [JW23], we find that ( where quantum proofs have no relative phase) is as powerful as .
A protocol is a verification task for a quantum computer (termed “Arthur”) when interacting with a dishonest but all-powerful machine (termed “Merlin”). If the statement is true (“completeness”), Merlin sends a quantum state (“proof”) that truthfully convinces Arthur. If the statement is false (“soundness”), Merlin will send any quantum state possible to deceive Arthur. A valid protocol distinguishes these cases, succeeding with probability at least in completeness and at most in soundness. Canonically, is the class of all valid protocols.
One could potentially reduce the power of by restricting Merlin’s proof in completeness. Surprisingly, many restrictions of this type do not reduce the power of the class. For example, this is true even if the quantum state is a subset state (with no relative phase nor relative non-zero amplitude) [GKS14]. The reason behind this is promise gap amplification: there exist techniques to increase the gap to for any polynomial . As a result, a subset state with polynomially small overlap with the best completeness proof succeeds. This argument generalizes to any set of states that form an -covering of all -qubit quantum states, where is at least inverse polynomial in .
By contrast, restricting Merlin’s proof in soundness seems to increase the power of this complexity class, since this reduces Merlin’s ability to “deceive”. For example, if Merlin must send a quantum proof without relative phase, Arthur can ask about its sparsity ( norm). When a state has no relative phase, a low overlap with actually implies it is sparse, as opposed to a state with destructively interfering phases (i.e. any other Hadamard basis vector).
One popular variant of restricts Merlin’s entanglement over a fixed barrier; it is named (as if there are two unentangled Merlins each sending a quantum proof [KMY03]). This complexity class may seem more powerful than , but despite much study [BT10, ABD+08, CD10, Per12, HM13, GSS+18, SY22], little is known except the trivial bounds .
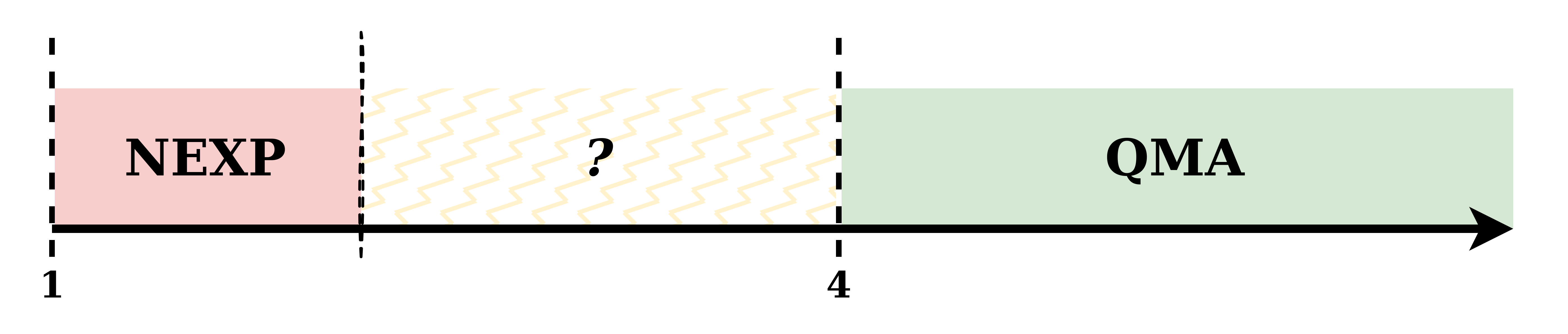
What happens if one restricts both entanglement and relative phase? [JW23] define and , where quantum proofs are required to have no relative phase (non-negative amplitudes, up to a global phase) in both cases.111As noted before, restricting the state in completeness may not change the complexity class, but restricting the state in soundness can make the class more powerful, since the latter limits Merlin’s adversarial strategies. Surprisingly, [JW23] show the existence of constants such that , crucially including a protocol to estimate the sparsity of a quantum proof. This hints perhaps at a route to prove , since there are other constants where .222This is because every state has constant overlap with some state without relative phase. See also Proposition 29.
In this work, we show that restricting relative phase alone gives the power of ; i.e., there exist constants where . Note that assuming , this implies cannot be amplified, since as before, there are other constants where . As a result, techniques to prove must crucially use the unentanglement promise inherent in . See Figure 1 and Figure 2 for a pictorial description.

1.1 Techniques
Our primary technical contribution is to show a protocol for a -complete problem. This directly extends the work of Jeronimo and Wu [JW23], who show a protocol for a -complete problem. As in [JW23], we study constraint satisfaction problems (CSPs) with constant gap. In -GapCSP, either all constraints can be satisfied, or at most a fraction of constraints can be satisfied. These problems are known to be -hard or -hard (depending on the problem size) using the PCP theorem [AS92, ALM+98, Har04].
Before proving with some constant gap equals , we prove (with some other constant gap) equals . This choice (also taken by [JW23]) is pedagogical: it allows us to explain the protocol without worrying about input encoding size, since has a polynomial amount of space and verifier runtime. Here, we consider -GapCSP with polynomially many variables and clauses; the quantum proof must certify that there is a satisfying assignment to all clauses.
The protocol of [JW23] crucially relies on an estimate of sparsity ( norm) of a quantum state without relative phase. The overlap of a -qubit quantum state without relative phase with is exactly the value . With multiple quantum proofs , one can estimate the sparsity by repeating this “sparsity test” on each , and using a swap test to ensure that all are approximately equal. Interestingly, no other part of their protocol requires the no relative phase assumption.333Formally, [JW23] studies states with non-negative amplitudes. Recall that the set of these states, up to global phase, are equivalent to states with no relative phase.
In , we have a single quantum proof, so we cannot use this test to estimate sparsity. Instead, we design a similar test that directly enforces a rigidity property of the proof.444Note that we use the intuition of rigidity in a more general context, where Arthur’s tests, not a non-local game, enforce states of a certain form. The required form is , where the second register is constant-sized. Using a “sparsity test” over the second register, Arthur ensures that the second register has one per ; but using the complement of a “sparsity test” over the whole proof, Arthur ensures the overall state maximizes norm. States of the required form are optimal for this combination of tests. We make use of the no relative phase property in Lemmas 6 and 8.
Now we can describe our protocol. For each constraint , Arthur asks for the values associated with the variables involved in constraint . The protocol either enforces rigidity of the quantum proof, or verifies the constraints of the CSP. Note that we need two kinds of constraint checks: the values must satisfy constraint , and the value of a variable must be consistent across the constraints it participates in. For states with the rigidity property, checking satisfiability is simple: measure in the computational basis and verify the measured constraint . States with the rigidity property will succeed with probability equal to the satisfying fraction of the CSP assignment.
Checking consistency is done using a technique called “regularization” from the PCP literature [Din07]; for each constraint , we verify that each variable participating in has the same value in exactly other constraints for some constant , in a way that the edges form an expander graph. The expansion property guarantees that cheating on this test is as damaging as cheating on the satisfiability test. Jeronimo and Wu [JW23] use a swap test to implement these new checks, but this requires multiple quantum proofs. We show how to use a Hadamard test (which requires only one quantum proof) to achieve the same result, building on ideas from previous work [BFM22]. Since there exists a such that -GapCSP is -hard, this completes the proof of with some constant gap.
When scaling up to , one must be careful of how to succinctly encode the input of a -complete problem. The PCP theorem allows us to choose -GapCSP that is succinct, but we need stronger properties. Following the adjustments taken in [JW23], we choose a PCP system for that is both doubly explicit and strongly uniform. Doubly explicit means that one can efficiently compute the variables participating in a given constraint and the constraints a given variable participates in; using this, we can implement the consistency checks in polynomial time. Strongly uniform means that the number of constraints a variable participates in is efficiently computable, and one of a fixed number of possibilities; using this, we only need to build a fixed number of expander graphs during regularization. Recent work also shows how to construct exponentially-sized expander graphs in polynomial time [Lub09, Alo21]. Once we are through these input encoding difficulties, our protocol is identical to that for .
Fundamentally, the no relative phase property allows Arthur to verify a number of constraints exponential in the number of qubits. Attempts to do this for gave too small a promise gap [BT10, Per12, GNN12], too many provers [ABD+08, CD10, CF11], or too much space or time [HM13, NZ23]. Jeronimo and Wu [JW23] show that circumvents this difficulty: using no relative phase and unentanglement, Arthur enforces the sparsity of a quantum proof to solve a -complete problem. At the center of our work is the insight that no relative phase is enough for Arthur to require constant-sized answers to exponentially many questions, solving a -complete problem with a single polynomial-size quantum proof.
1.2 Related work
The complexity class
The complexity class is known to have promise gap amplification, and to be equal to for any at most polynomial in [HM13]. It is not obvious how to test for entanglement; even determining whether a polynomially-sized vector is entangled is -hard [Gha09]. If there exist efficient approximate “disentanglers” that can create any separable state, then ; see [ABD+08] for some progress. [GSS+18] describe quantum variants of the polynomial hierarchy and connect their properties to bounds on . It is not even known whether there is a quantum oracle separating and [Aar21].
PCPs and expander graphs
Probabilistically checkable proofs (PCPs) show hardness for CSPs with a constant gap [AS92, ALM+98, Har04]. Dinur [Din07] proves the PCP theorem using a regularization step, which adds new constraints associated with the edges of a regular expander graph. Polynomial-time regularization for requires an efficient description of exponentially-sized expander graphs. Recent advances in expander graph constructions [Lub09, Alo21] allow for this type of regularization, first used in [JW23].
Quantum states and relative phase
Up to a global phase, states with non-negative amplitudes are equivalent to states with no relative phase. [JW23] propose the class and , and show . Note that by contrast, restricted to states with real amplitudes is equal to [McK13]. Relative phase was recently proposed as a quantum resource [Xu23]. For both and , restricting Merlin in completeness to send a subset state does not change the power of the complexity class (i.e., and ). [GKS14] also shows why their proof strategy fails if Merlin is restricted in both completeness and soundness.
Rigidity and games
Rigidity was first formally introduced in the context of non-local games [MY04], and have been used to prove several complexity class equalities. For example, the CHSH game [CHSH69] tests for a maximally entangled state on two qubits [Tsi93], and was used to prove [RUV13]. The Mermin-Peres magic square game tests for two copies of a maximally entangled quantum state, and was used to prove [JNV+21]. Rigidity is known to exist in broader contexts, including some (but not all) linear constraint games [CMMN20] and monogamy-of-entanglement games [BC23].
2 Our setup
We restate the definition of from [JW23]. When the proof length is not specified, it is allowed to be at most any polynomial in input size. We follow the conventions , , and with proof length at most .
Definition 1 ().
Let and be polynomial time computable functions. A promise problem is in if there exists a verifier such that for every and every :
-
•
Completeness: if , then there exist unentangled states , each on at most qubits and with real non-negative amplitudes, s.t.
-
•
Soundness: If , then for every set of unentangled states , each on at most qubits and with real non-negative amplitudes, we have
We make a few remarks on this complexity class, with extended discussion in Section 5. First, we stress that the restriction to quantum proofs with non-negative amplitudes is promise-symmetric, i.e. both in completeness and in soundness. This is unlike, for example, the class [GKS14]. Although the restriction to subset states is stronger than non-negative amplitudes,555A subset state is a uniform superposition over a subset of all computational basis states. States with non-negative amplitudes are conical combinations of subset states. its use only in completeness allows for . In fact, our work implies that with a promise-symmetric subset state restriction also interpolates from to , depending on the size of the promise gap.
We also explain why the promise gap of cannot obviously be amplified. The first strategy one might try is parallel repetition: an honest Merlin sends multiple copies of the original proof and Arthur verifies each copy of the original proof. For , entangling the copies in soundness does not help Merlin, since Arthur’s protocol is sound for all quantum states. But perhaps unintuitively, it can help for . (See 28 for a simple example.) This is because partial measurement can destroy the restriction on the quantum proof! For example, Arthur’s first measurement may introduce relative phase in the rest of the proof. This fact also obstructs more clever amplification strategies for such as the proof-length preserving variant [MW05].
Furthermore, it is not clear how to upper-bound beyond the trivial .666 by directly simulating the quantum proof and verifier. One technique to upper-bound is to find the optimal proof using a semidefinite program (or a general convex program). This shows that (or with a convex program). But these arguments do not immediately transfer to . Convex optimization over states with non-negative amplitudes is equivalent to optimizing over the copositive cone [Bur11]. Even the weak membership problem over the copositive cone (deciding if the optimal vector is close to a non-negative vector) is -hard in polynomially-sized vector spaces; recall that quantum states are in exponentially-sized vector spaces. These are the same reasons that prevent straightforward upper bounds for [Gha09].
3 Protocol for
We first define the problem we consider:
Definition 2 (CSP system).
A -CSP system on variables with values in consists of a set (possibly a multi-set) of constraints where the arity of each constraint is exactly .
Definition 3 (Value of CSP).
The value of a -CSP system is the maximum fraction of satisfiable constraints over all possible assignments . The value of is denoted .
Definition 4 (GapCSP).
The -GapCSP problem inputs a CSP system . The task is to distinguish whether is such that (in completeness) or (in soundness) .
Fix the input size , and consider -CSP systems where and are polynomials in . Deciding whether or not these systems are satisfiable is -hard. In fact, there exists such that deciding -GapCSP on these CSP systems is -hard.
Theorem 5 ([Din07]).
There exist constants and such that -GapCSP is -hard.
Our goal in this section is to construct a protocol for -GapCSP given any -CSP system where and . Let . We first outline the protocol. Arthur asks for a quantum state from ; we call the first register the constraint register and the second register the color register. A quantum proof has the following form:
For completeness, consider the satisfying assignment of variables (in ) to values (in ). Merlin sends the quantum proof , where each is the (ordered) list of values associated with the variables participating in .
Arthur then applies one of two kinds of tests:
-
1.
Rigidity tests: These ensure that the quantum proof is of the form .
-
2.
Constraint tests: These verify that values in the quantum proof satisfy constraints of the CSP system.
Below, we separately describe the rigidity tests and constraint tests. In each, we analyze the success probability in completeness and prove lemmas to study soundness. We then combine the technical statements to prove the result.
3.1 Rigidity tests
Arthur enforces rigidity of a quantum proof using two tests. The first test is the Density test, which maximizes norm. Here, we measure the state in the Hadamard basis and accept if the outcome is .777For simplicity, we denote the uniform superposition over all standard basis states by . The dimension is clear from the context. Given , the success probability of this test is
Recall that if is a subset state according to subset , its sparsity is exactly . In completeness, the quantum proof is a subset state with elements, so this test passes with probability .
The second test is the Validity test, which minimizes norm only on the second register. Here, we measure the color register in the Hadamard basis, and reject if the outcome is . Given , the success probability of this test is
where is partial trace over the constraint register. In completeness, recall that the proof has the form , so the success probability is
In fact, no quantum state without relative phase can pass the Validity test with a higher probability:
Lemma 6.
Suppose has no relative phase. Then .
Proof.
The success probability is
where the second equality follows from and the inequality holds since . ∎
It turns out that is impossible to score high on both the Validity test and the Density test. We use this to enforce the rigidity property of .
Lemma 7.
.
Proof.
By Cauchy-Schwarz,
| ∎ |
Why does this help with rigidity? Suppose Arthur inputs a quantum proof (without relative phase) and runs Density test with probability and Validity test with probability . Suppose also that . Then the expected success probability is . Note that this upper bound is achieved in completeness, and for any state of the form . We show that quantum proofs must have this form to reach the upper bound.
One requirement to get close to the upper bound is near-optimal success probability on Validity test. We prove that any quantum proof that has this property must be close to a state that assigns one color to each constraint.
Lemma 8.
Given with no relative phase (i.e. ), let
be associated with maximizing function , and let . Fix any . If , then .
Proof.
Another requirement to get close to the upper bound is near-optimal success probability on Density test, up to Lemma 7. Consider any quantum proof that passes Validity test with probability close to and Density test with probability close to ; we show it must be close to a state of the form . Now we can prove the soundness of the rigidity test by relying on the following fact:
Fact 9.
Let be a positive semi-definite matrix, and let and be quantum states such that . Then .
Proof.
The quantity is upper-bounded by the trace distance of and , which has value . ∎
Lemma 10 (Rigidity lemma).
Let be small constants. Suppose , , and are defined as in Lemma 8, and is defined as
If and , then .
Proof.
Intuitively, Lemma 10 allows us to tune the probability of each test in the protocol. As we explain in the analysis (Section 3.3), if the probabilities of running Validity test and Density test are much higher than that for constraint tests, then if or is large, these two tests catch a “deceptive” quantum proof in soundness. This allows constraint tests to focus on the case of small and ; i.e. nearly rigid quantum proofs.
3.2 Constraint tests
We analyze the constraint tests on rigid quantum proofs, i.e. states of the form . The verifier needs to check two properties:
-
(i)
(satisfiability) For all , the assignment satisfies .
-
(ii)
(consistency) Each variable is assigned the same value when participating in different constraints.
One may ask why we even need to check for consistency. Couldn’t we ask for the assignment of each variable , for example as the quantum proof ? The problem with this is checking satisfiability becomes difficult, since the assigned values are given in superposition.888There is a way around this limitation for CSP systems consisting of unique game constraints, where each (binary) constraint involving variables accepts exactly one for each . See [JW23, Section 6] for more discussion.
Instead, with a state , satisfiability is easy to verify: measure the first register (observing some ), and compute . Let be the number of unsatisfied constraints. The outcome is with probability .
But this form of quantum proof gives Merlin a new way to “deceive”: for a given variable, send different values depending on the constraint! We prevent this by checking for consistency, similarly to the pre-processing step of [Din07] sometimes called regularization. As in [JW23, Section 7], we add “consistency constraints” to the CSP system as follows:999Note that since and are polynomially-sized, this process is efficient.
-
•
For each variable , let represent the constraints that participates in.
-
•
Fix a constant . For each , draw a -regular graph with vertices that is expanding.101010For technical reasons of 11, we require that the Cheeger constant is at least 2.
-
•
Each edge of each expander represents a “consistency constraint”, where we assert that the value of variable sent with constraint equals that sent with constraint .
Using expander graphs allows us to prevent this kind of “deceptive” Merlin: either the proof fails many of the original constraints, or it fails many “consistency constraints”. Let be the number of unsatisfied “consistency constraints” out of :
Claim 11 ([Din07, Lemma 4.1]).
Consider a -CSP system , and apply regularization. If , then all “consistency constraints” can be simultaneously satisfied. If , then the total number of unsatisfied constraints is at least .
How do we check these “consistency constraints”? Over the next few paragraphs, we construct a unitary related to permutations on the constraint graph. In completeness, the quantum proof is an eigenvector of this unitary, but in soundness, all rigid quantum proofs are detectably far (i.e. using a Hadamard test) from an eigenvector. We study the graph with vertices, where each vertex corresponds to a clause and a variable that participates in clause . Let be the union of all consistency edges created during regularization, i.e. for variable becomes the edge . Note that contains a copy of each expander graph, so it is -regular.
We now choose permutations. It is a classical fact that the adjacency matrix of any -regular graph can always be decomposed to permutations. Let be the decomposition of ; recall that these are permutations on where . For each , we identify with a permutation on , where any that is not a vertex of (i.e. variable does not participate in constraint ) is mapped to itself.111111These permutations (and their inverses) are all efficient because and are polynomially-sized. Note that this map always preserves the variable ; without loss of generality, we also identify with its restriction . From here on, we use this last definition of , which maps constraint that variable participates in to another constraint that variable participates in, and identity otherwise.
Now consider a rigid quantum proof, i.e. of the form . Since there are a polynomial number of variables and constraints, we can efficiently transform to , where
Here, are the variables participating in , and is the value of this variable according to .
We now would like to construct a unitary on that maps to for some other constraint that participates in. In completeness, this unitary would leave the state unchanged. Notice that from the perspective of such a unitary, the second register containing is “junk”. Fortunately, we can measure out the second register in the Hadamard basis, and reject if the outcome is not . All rigid states will observe outcome with probability ; one can see this by writing the second register in the Hadamard basis.
Suppose the observed outcome is ; let us call the postselected state , where
For each , we now implement the in-place transformation according to , where
Recall that the map is a permutation. Since we have access both to this permutation and its inverse, we can implement .
Note that in a satisfiable instance, . By contrast, if , is orthogonal to . Hence, is the fraction of satisfied “consistency constraints” observed by . We use the Hadamard test to measure this value, in a similar way to the Spectral test in [BFM22]. Note that unlike the swap test, the Hadamard test only uses one copy of a quantum state.
Definition 12 (Hadamard test).
Let be a quantum state and a unitary operator.
-
1.
Prepend a control qubit to , to create .
-
2.
Apply a Hadamard on the control qubit, to create .
-
3.
Apply , controlled by the control qubit, to create .
-
4.
Apply a Hadamard on the control qubit, to create .
-
5.
Measure the control qubit, and accept if the output is .
The success probability is then
We now can describe the constraint tests together:
-
(i)
With probability , check satisfiability. This succeeds with probability .
-
(ii)
With probability , generate , and measure the second register in the Hadamard basis. If the output state is not , reject. Otherwise, choose a random , and perform a Hadamard test with . This succeeds with probability .121212Note that in our protocol, is always real because and have real values.
The overall success probability of the constraint tests is
We now show a constant gap between completeness and soundness. In completeness, , so passes the constraint tests with probability . In soundness, recall that , so by 11, any rigid quantum proof passes the constraint tests with probability at most . We now apply Lemma 10: any quantum proof that passes Density test and Validity test with probabilities too similar to that in completeness must pass the constraint tests with probability less than .
Corollary 13.
In soundness, if and , then
3.3 Analysis
In the protocol, Arthur applies Density test, Validity test, or constraint tests with probability , respectively, where .
We start by analyzing the success probability of the protocol in completeness. Here, , and the quantum proof is such that is a satisfying assignment to the variables that participate in . The success probability for each test is exactly , , and , respectively. So the success probability of the protocol in completeness is .
We now choose the probabilities . Choose .
-
1.
We first set a distance threshold for a large enough constant satisfying
-
2.
Let . Then let
Now we study soundness, i.e. when . We again denote the quantum proof as . We divide up the analysis into a few parts:
-
1.
A quantum proof that is “too sparse” (i.e. for any ) is detected by Density test.
-
2.
A quantum proof that is “too dense” (i.e. for any ) is detected by Validity test.
where the first inequality follows from Lemma 7.
-
3.
A quantum proof that is “the right density” (i.e. for ) but far from “valid” ( for ) is detected by Validity test when .
-
4.
Lastly, a quantum proof that is nearly rigid (i.e. and for any ) is detected by the constraint tests.
The first inequality follows from Corollary 13, and the second inequality holds by our choice of . Note that by Lemma 6. By Lemma 7, if , then ; otherwise trivially. So then
Combining these cases proves the following result:
Theorem 14.
Given an instance of -GapCSP, the protocol succeeds with probability in completeness and at most in soundness for some constants .
Corollary 15.
There exist constants such that with completeness and soundness .
4 protocol for
Our goal in this section is to modify the previous protocol to solve an -complete problem. Again by the PCP theorem, the succinct -GapCSP problem with exponentially many variables and clauses is -complete. The succinctness allows us to efficiently describe the problem input. What remains is to ensure that the verifier’s protocol is efficient. Previously, the unitary transformations were efficient because the verifier handled -size graphs. Furthermore, the expanders used to check the equality constraints for each variable may have different sizes. Now that there can be exponentially many possibilities for the size of each cluster, naively applying the previous technique is not efficient. These challenges were addressed in [JW23] by considering a PCP construction for with strong properties.
Theorem 16 ([JW23]).
There is a -hard -GapCSP instance for some -CSP system that is both -strongly uniform for some constant and -doubly explicit.
Informally, every constraint in a succinct CSP system must be computable in polynomial time. The doubly explicit property further requires the existence of efficient maps from variables to constraints and from constraints to variables. Intuitively, these maps allow us to efficiently implement the Hadamard test of the consistency checks.
We include the formal definition of these properties. Define to be the list of variables participating in , and be the list of constraints that depend on variable .
Definition 17 (Doubly explicit CSP).
A -CSP system is -doubly explicit if for all and , the following are computable in time :
-
(i)
Cardinality of and for all and .
-
(ii)
; if participates in , then is the index of in .
-
(iii)
; is the -th variable of .
-
(iv)
; if participates in , then is the index of in .
-
(v)
; is the -th variable .
This property alone is not enough for efficient regularization: the verifier must know how to implement an expander of size for all variables . The strongly uniform property resolves this complication.
Definition 18 (Strongly uniform CSP).
Let . A -CSP system is -strongly uniform if the variable set can be partitioned into at most different subsets such that if and belong to the same part . Furthermore, the part can be determined in time .
A -strongly uniform CSP system allows the verifier to use different (possibly exponential size) -regular expanders. These can be constructed in polynomial time:
Theorem 19 (Doubly explicit expander graphs [Lub09, Alo21]).
There is a constant such that the following explicit constructions of expander graphs exist:
-
1.
For every , there is a -regular graph on vertices.
-
2.
For every prime , there is a -regular graph on vertices, and the graph can be decomposed into permutations that can each be evaluated in time .131313In fact, since these graphs are Cayley graphs, both the permutations and their inverses can be evaluated in time . We use both and in the constraint tests to implement the unitary .
Furthermore, the neighbors of each variable can be listed in , and the graphs have Cheeger constant at least 2.
With this theorem, the verifier can choose a large constant , and use Construction 1 if . Otherwise, the verifier can cover almost all vertices with an explicit expander using Construction 2.
Theorem 20 (Primes in short intervals [Che13]).
There is an absolute constant such that for any integer , there is a prime in the interval .
We modify the protocol to expect the quantum proof such that each . The verifier measures the primes, and can always check that every is a prime number in the required range. The rest of the analysis is similar to the protocol, but regularized using these efficient expanders. We first explain how to efficiently implement the constraint tests, and then analyze the protocol.
4.1 Efficient constraint tests
We show how to efficiently implement consistency checks that imply a version of 11. Fix any vertex . Let be the number of constraints that depend on and be the corresponding prime. Let be a large enough constant. If , then use Construction 1 -regular expander to wire new copies of the vertex together, just as for . Otherwise, use Construction 2 to generate a -regular expander graph of size that wires nearly all copies of the vertex together. Then add self-loops for the remaining vertices. The number of vertices with self loops is at most some (for some small constant ) since ; we can make arbitrarily small by choosing a large enough .
Claim 21 ([JW23]).
Consider a -CSP system , and apply efficient regularization. If , then all “consistency constraints” can be simultaneously satisfied. If , then the total number of unsatisfied constraints is at least .
The analysis of 21 is similar to 11. The additional factor of comes from the self-loop constraints; these can be satisfied without violating any “consistency constraint”.
After measuring the primes, let the verifier act on the space . We explicitly define the unitary operators that are used in the protocol. These definitions exactly match [JW23]. First, operator expands the values from the list of values of variables involved in each constraint:
Here, is the list of values of variables involved in constraint , is the -th variable involved in , and is the value of according to . Next, define the permutation operators for each that implement the permutations of each efficiently constructed expander:
The last operation computes the constraints in superposition:
Theorem 22 ([JW23]).
can be implemented by circuits.
4.2 Analysis
The analysis is nearly the same as in the protocol, with the minor difference that the verifier also receives in the quantum proof. The rigidity tests are unchanged. For the constraint tests, the verifier can use the explicit operators :
-
(i)
For satisfiability, the prover computes and measures the second qubit in the standard basis.
-
(ii)
For consistency, the prover computes , selects random , and uses in Hadamard test.
We already know that for a quantum proof of the valid form, we can write the success probability as:
To be able to analyze soundness, all that is left is to reprove Corollary 13 to handle the subtle difference between 21 and 11. Let and , then we can write:
We can choose a small enough (via large enough ) so that .
Corollary 23.
If and , then:
For soundness, the same analysis of Section 3.3 goes through by reducing by a factor of ; this change comes from Corollary 23, which handles the extra self-loop constraints. All together:
Theorem 24.
Consider -GapCSP with a -CSP system that is -doubly explicit and -strongly uniform. The protocol solves this problem with completeness and soundness for some constants .
Corollary 25.
There exist constants such that .
5 Subtle features of
5.1 Promise symmetry matters
One can imagine restricting to proofs with non-negative amplitudes only in completeness. But this class is equal to :
Fact 26.
Consider the class , where the proof must have non-negative amplitudes only in completeness. Since subset states have non-negative amplitudes, . By [GKS14], .
Instead, also restricts the proof in soundness, which reduces the ways Merlin can “deceive” Arthur. This increases the power of the complexity class:
Corollary 27.
Notice that for any choice of , since any protocol is also a protocol. Since , whenever and for any polynomial .
In general, suppose is a set of quantum states that approximate all quantum states (i.e. an -covering) by at least an inverse polynomial in number of qubits. Then is equal to restricted to in completeness, and at most restricted to in both completeness and soundness.
Furthermore, classes that modify only in completeness enjoy promise gap amplification through parallel repetition. This does not hold for promise-symmetric modifications. We provide a simple example of how parallel repetition fails to amplify the promise gap of :
Fact 28.
Consider a Hermitian and positive semidefinite matrix . Let be the maximum value among real non-negative vectors. Then it is possible for .
Proof.
Consider two qubits and the projector , where projects into the Pauli-X basis (i.e. ). Then , maximized at or . But using the state , . ∎
5.2 at some constant gap equals
Perhaps surprisingly, equals for some constants . This is because every quantum state can be approximated (up to a constant) by a quantum state without relative phase:
Proposition 29.
.
Proof.
Consider a problem in , and let be its accepting operator. We will use the same circuit in , and analyze the new completeness and soundness.
-
•
(completeness) The same completeness proof is a valid proof for , accepting with completeness .
-
•
(soundness) Recall that for any with non-negative amplitudes.
Consider any state with real (but possibly negative) amplitudes. Separate and normalize its positive entries and negative entries, i.e. . Notice that , so is of unit norm. Then
where the first inequality holds by Cauchy-Schwarz because is positive semidefinite.
Similarly, consider any state with arbitrary amplitudes. Separate and normalize its real and imaginary entries, i.e. . Notice that is still unit norm. By the same calculation, one finds that .
∎
Corollary 30.
For any , .
Proof.
follows from Proposition 29. The other direction follows from Corollary 27. ∎
This is a strange phenomenon: depending on the choice of constants , could be as small as and as large as !141414 Note that the same phenomenon holds for and with nearly the same proof. This is why [JW23] was perceived as “just a constant gap away” from proving . See Figure 2 for a pictorial description. An implication of our work is that assuming , simply cannot be amplified.
6 Open questions
-
1.
What is the relationship of and ? Our result does not immediately say anything about and . It only suggests that for , the restriction of relative phase is maximally strong. For example, it is possible that ; i.e. the restriction of entanglement across a fixed barrier may be just as powerful. In fact, showing is still an open route to proving , but in light of this work, amplification for must crucially rely on the unentanglement promise.
-
2.
Are other complexity classes sensitive to different constant-sized promise gaps? We show that for , the parameter can be “tuned” to change the power of the class from to (see also Figure 2). Do other complexity classes drastically change power with different promise gaps? One similar class is [Kup15], which equals when (but unlike our work, and are exponentially small). However, when is allowed to be any number above , is equal to [DGF22]. Note that relative to oracles, is not closed under intersection, which was used to separate it from [AKKT20].
-
3.
State complexity vs. decision complexity? Although we prove that there are constants such that , we do not prove the existence of any product test (as in [HM13]). In fact, it is possible that no product test exists! This would show a separation between the complexity of decision problems and state synthesis problems; i.e. but . In fact, it is even possible that but . This inquiry can help us understand whether (or how) the power of unentanglement is useful when solving decision problems.
Acknowledgements
Thanks to Zachary Remscrim for collaborating on early stages of this project. Thanks to Noam Lifshitz, Dor Minzer, and Kevin Pratt for answering questions about algebraic constructions of expanders. Thanks to Srinivasan Arunachalam, Fernando Granha Jeronimo, Supartha Podder, and Pei Wu for comments on a draft of this manuscript.
BF and RB acknowledge support from AFOSR (award number FA9550-21-1-0008). This material is based upon work partially supported by the National Science Foundation under Grant CCF-2044923 (CAREER) and by the U.S. Department of Energy, Office of Science, National Quantum Information Science Research Centers as well as by DOE QuantISED grant DE-SC0020360. KM acknowledges support from the National Science Foundation Graduate Research Fellowship Program under Grant No. DGE-1746045. Any opinions, findings, and conclusions or recommendations expressed in this material are those of the author(s) and do not necessarily reflect the views of the National Science Foundation.
References
- [Aar21] Scott Aaronson. Open Problems Related to Quantum Query Complexity, 2021. arXiv:2109.06917.
- [ABD+08] Scott Aaronson, Salman Beigi, Andrew Drucker, Bill Fefferman, and Peter Shor. The Power of Unentanglement, 2008. arXiv:0804.0802.
- [AKKT20] Scott Aaronson, Robin Kothari, William Kretschmer, and Justin Thaler. Quantum Lower Bounds for Approximate Counting via Laurent Polynomials, 2020. URL https://drops.dagstuhl.de/opus/volltexte/2020/12559/.
- [ALM+98] Sanjeev Arora, Carsten Lund, Rajeev Motwani, Madhu Sudan, and Mario Szegedy. Proof Verification and the Hardness of Approximation Problems. J. ACM, 45(3):501–555, 1998. URL https://doi.org/10.1145/278298.278306.
- [Alo21] Noga Alon. Explicit expanders of every degree and size. Combinatorica, pages 1–17, 2021. arXiv:2003.11673.
- [AS92] Sanjeev Arora and Shmuel Safra. Probabilistic Checking of Proofs; A New Characterization of NP. In 33rd Annual Symposium on Foundations of Computer Science, Pittsburgh, Pennsylvania, USA, 24-27 October 1992, pages 2–13. IEEE Computer Society, 1992. URL https://doi.org/10.1109/SFCS.1992.267824.
- [BC23] Anne Broadbent and Eric Culf. Rigidity for Monogamy-Of-Entanglement Games, 2023. URL https://drops.dagstuhl.de/opus/volltexte/2023/17531/.
- [BFM22] Roozbeh Bassirian, Bill Fefferman, and Kunal Marwaha. On the power of nonstandard quantum oracles. 2022. arXiv:2212.00098.
- [BT10] Hugue Blier and Alain Tapp. A quantum characterization of NP, 2010. arXiv:0709.0738.
- [Bur11] Samuel Burer. Copositive programming. In Handbook on semidefinite, conic and polynomial optimization, pages 201–218. Springer, 2011. URL https://link.springer.com/chapter/10.1007/978-1-4614-0769-0_8.
- [CD10] Jing Chen and Andrew Drucker. Short multi-prover quantum proofs for SAT without entangled measurements. 2010. arXiv:1011.0716.
- [CF11] Alessandro Chiesa and Michael A Forbes. Improved soundness for QMA with multiple provers. 2011. arXiv:1108.2098.
- [Che13] Yuanyou Furui Cheng. Explicit Estimate on Primes between Consecutive Cubes, 2013. arXiv:0810.2113.
- [CHSH69] John F Clauser, Michael A Horne, Abner Shimony, and Richard A Holt. Proposed experiment to test local hidden-variable theories. Physical review letters, 23(15):880, 1969. URL https://doi.org/10.1103/PhysRevLett.23.880.
- [CMMN20] David Cui, Arthur Mehta, Hamoon Mousavi, and Seyed Sajjad Nezhadi. A generalization of CHSH and the algebraic structure of optimal strategies. Quantum, 4:346, oct 2020. arXiv:1911.01593.
- [DGF22] Abhinav Deshpande, Alexey V Gorshkov, and Bill Fefferman. Importance of the Spectral gap in Estimating Ground-State Energies. PRX Quantum, 3(4):040327, 2022. arXiv:2007.11582.
- [Din07] Irit Dinur. The PCP theorem by gap amplification. Journal of the ACM (JACM), 54(3):12–es, 2007. URL https://dl.acm.org/doi/abs/10.1145/1236457.1236459.
- [Gha09] Sevag Gharibian. Strong NP-Hardness of the Quantum Separability Problem, 2009. arXiv:0810.4507.
- [GKS14] Alex B. Grilo, Iordanis Kerenidis, and Jamie Sikora. QMA with subset state witnesses, 2014. arXiv:1410.2882.
- [GNN12] François Le Gall, Shota Nakagawa, and Harumichi Nishimura. On QMA protocols with two short quantum proofs. Quantum Inf. Comput., 12(7-8):589–600, 2012. URL https://doi.org/10.26421/QIC12.7-8-4.
- [GSS+18] Sevag Gharibian, Miklos Santha, Jamie Sikora, Aarthi Sundaram, and Justin Yirka. Quantum Generalizations of the Polynomial Hierarchy with Applications to QMA(2), 2018. URL http://drops.dagstuhl.de/opus/volltexte/2018/9640/.
- [Har04] Prahladh Harsha. Robust PCPs of proximity and shorter PCPs. PhD thesis, Massachusetts Institute of Technology, 2004. URL https://dspace.mit.edu/bitstream/handle/1721.1/26720/59552830-MIT.pdf.
- [HM13] Aram W. Harrow and Ashley Montanaro. Testing product states, quantum Merlin-Arthur games and tensor optimization. Journal of the ACM (JACM), 60(1):1–43, 2013. arXiv:1001.0017.
- [JNV+21] Zhengfeng Ji, Anand Natarajan, Thomas Vidick, John Wright, and Henry Yuen. Mip*= re. Communications of the ACM, 64(11):131–138, 2021. arXiv:2001.04383.
- [JW23] Fernando Granha Jeronimo and Pei Wu. The Power of Unentangled Quantum Proofs with Non-negative Amplitudes. 55th Annual ACM Symposium on Theory of Computing, 2023. URL https://doi.org/10.1145/3564246.3585248.
- [KMY03] Hirotada Kobayashi, Keiji Matsumoto, and Tomoyuki Yamakami. Quantum Merlin-Arthur Proof Systems: Are Multiple Merlins More Helpful to Arthur?, 2003. arXiv:quant-ph/0306051.
- [Kup15] Greg Kuperberg. How hard is it to approximate the Jones polynomial? Theory of Computing, 11(1):183–219, 2015. URL https://doi.org/10.4086/toc.2015.v011a006.
- [Lub09] Alexander Lubotzky. Finite simple groups of Lie type as expanders, 2009. arXiv:0904.3411.
- [McK13] Matthew McKague. On the power quantum computation over real Hilbert spaces. International Journal of Quantum Information, 11(01):1350001, feb 2013. arXiv:1109.0795.
- [MW05] Chris Marriott and John Watrous. Quantum Arthur-Merlin Games, 2005. arXiv:cs/0506068.
- [MY04] Dominic Mayers and Andrew Yao. Self testing quantum apparatus, 2004. arXiv:quant-ph/0307205.
- [NZ23] Anand Natarajan and Tina Zhang. Quantum free games. 2023. arXiv:2302.04322.
- [Per12] Attila Pereszlényi. Multi-Prover Quantum Merlin-Arthur Proof Systems with Small Gap, 2012. arXiv:1205.2761.
- [RUV13] Ben W Reichardt, Falk Unger, and Umesh Vazirani. Classical command of quantum systems. Nature, 496(7446):456–460, 2013. URL https://doi.org/10.1038/nature12035.
- [SY22] Adrian She and Henry Yuen. Unitary property testing lower bounds by polynomials, 2022. arXiv:2210.05885.
- [Tsi93] Boris S Tsirelson. Some results and problems on quantum Bell-type inequalities. Hadronic Journal Supplement, 8(4):329–345, 1993. URL http://www.math.tau.ac.il/~tsirel/download/hadron.pdf.
- [Xu23] Jianwei Xu. Quantifying the phase of quantum states, 2023. arXiv:2304.09028.