Quantum Sampling for Optimistic Finite Key Rates in High Dimensional Quantum Cryptography
Abstract
It has been shown recently that the framework of quantum sampling, as introduced by Bouman and Fehr, can lead to new entropic uncertainty relations highly applicable to finite-key cryptographic analyses. Here we revisit these so-called sampling-based entropic uncertainty relations, deriving newer, more powerful, relations and applying them to source-independent quantum random number generators and high-dimensional quantum key distribution protocols. Along the way, we prove several interesting results in the asymptotic case for our entropic uncertainty relations. These sampling-based approaches to entropic uncertainty, and their application to quantum cryptography, hold great potential for deriving proofs of security for quantum cryptographic systems, and the approaches we use here may be applicable to an even wider range of scenarios.
1 Introduction
Quantum sampling, as introduced by Bouman and Fehr in [1], is a framework allowing for the analysis of quantum systems through classical statistical sampling methods. Informally, it was shown that when sampling a quantum state (via measuring some subset of it in a particular basis), the remaining, unmeasured, portion of the state behaves like a superposition of states that are “close” (with respect to some target value such as Hamming weight) to the observed sample. How close they are depends, in fact, on the error probability of the classical sampling protocol used (where the classical sampling strategy would observe a portion of a classical word in some alphabet and argue about how the remaining, unobserved, portion of the word looks). At a high level, suppose one measures a random portion of some quantum state in the basis and always observes . Then, one would expect that the remainder of the state (the unmeasured portion) should be a superposition of states that are relatively close to the all state. Bouman and Fehr’s framework formalizes this notion, even when the state is entangled with an environment system (e.g., an adversary).
Besides being fascinating on its own, there are now several interesting applications of this work. In their original paper [1], the authors showed some applications to quantum cryptography, namely a security proof of the entanglement-based BB84 QKD protocol for qubits (dimension two systems). Recently in [2, 3], we showed how the quantum sampling framework may be used to derive novel quantum entropic uncertainty relations which are highly applicable to finite-key quantum cryptographic security analyses. Informally, quantum entropic uncertainty relations bound the amount of uncertainty in two different measurement outcomes performed on some quantum system. For instance, the famous Maassen and Uffink relation [4] (which, itself, followed from a conjecture by Kraus in [5] and was an improvement over an uncertainty relation proposed first by Deutsch [6]) states that, given a quantum state acting on a -dimensional Hilbert space , then if two measurements are performed on the system resulting in random variables and respectively, it holds that , where is a function of the two measurements performed (namely their overlap, though we will formally define this later for our applications). In particular, one cannot in general be certain of the outcome of both measurements of the system. By now there are numerous quantum entropic uncertainty relations with various fascinating properties and applications; for a general survey, the reader is referred to [7, 8, 9].
The so-called sampling-based entropic uncertainty relations we introduced in our earlier work [2, 3] turn out to be highly useful in finding optimistic secure bit generation rates for quantum random number generation (QRNG) protocols in the source-independent security model [10]. Our relations bounded the quantum min-entropy as a function of the Shannon entropy of a particular measurement outcome and the measurement overlap. Since min entropy is a highly valuable resource in quantum cryptography (in particular, it can be used to determine how many uniform random bits one may extract from a source, independent of any adversary [11]), finding tight bounds on this quantity is highly desirable when analyzing quantum cryptographic protocols. As we’ve shown in our earlier work, our relations often out-perform prior work in cryptographic settings, producing more optimistic bit generation rates for QRNG protocols leading, potentially, to more rapid implementations of such systems (though here, and in our prior work, we focus only on theoretical analyses - practical settings, though interesting, are outside the scope of this current work). Furthermore, our sampling-based relations incorporate all needed finite sampling effects thus making them easy to use “out of the box.”
Here, we revisit sampling-based entropic uncertainty relations. These relations involve a quantum state , possibly entangled with an adversary, whereby a random sample is chosen and a test is performed by measuring a portion of resulting in some outcome . In this work, we show a highly general, two-party entropic uncertainty relation (Theorem 3.1) which, informally, states that with high probability (based on the failure probability of a classical sampling strategy):
| (1) |
where is the set of all words in some alphabet that are “close” to the observed string ; is the number of qudits that were not measured in the test state; and is a function of the overlap between the two measurements. One of the strong advantages to our new sampling-based relation is that one may design classical sampling strategies suitable to a quantum cryptographic purpose and simply insert it directly into the above; all one needs to do is analyze the classical error probability and bound or evaluate the size of the set (which is typically a combinatorial proof). Though this result is more general than our original, it turns out the proof of this is nearly identical to our prior work in [2, 3]. However the novelty is, first, in the generality of the result that it works for any classical sampling strategy (whereas in [3] only a particular sampling strategy was proven); second in its applications, we show that this new bound is powerful enough to analyze a particular source-independent (a form of partial device independence introduced first in [10]) QRNG protocol producing more optimistic bit-generation rates than prior work using alternative entropic uncertainty relations and, furthermore, unlike our previous work, can provide an alternative proof of the previously mentioned Maassen-Uffink relation for dimensions strictly greater than (in [2] we showed this for dimension systems only).
Our second main contribution is to show a novel three-party sampling-based entropic uncertainty relation involving Alice, Bob, and Eve. Here, Alice and Bob perform a test measurement on some portion of their shared quantum state, resulting in outcome and respectively (these are words in some -character alphabet). Then, informally, our new entropic uncertainty relation (Theorem 4.1) states that, with high probability:
| (2) |
where , the number of systems not measured initially; is a constant depending on the dimension () of the individual systems measured; takes into account imperfect, finite samples; is the -ary Shannon entropy; and is the Hamming distance of words and . Our entropic uncertainty relation can actually incorporate the maximal measurement overlap and the second-maximal overlap , making it useful if the two measurement bases have a similar basis element (e.g., a “vacuum” element, useful in QKD when considering channel loss). This ability shows the great promise in using the Quantum Sampling framework of Bouman and Fehr, augmented with our proof techniques developed here and in our prior work [2, 3] to prove interesting, and useful, entropic uncertainty relations. Indeed, our proof method can even be extended to support additional measurement overlap quantities.
Note that, if , then our result shows that the min-entropy conditioned on the adversary’s system must be high. We use our entropic uncertainty relation to provide a proof of security, in the finite key setting, of the High-Dimensional BB84 protocol [12, 13, 14, 15]. Our security proof is valid against arbitrary attacks by an adversary and applies easily to any dimension of the signal states and can even take into account lossy channels. Since high-dimensional QKD protocols exhibit many fascinating and useful properties (such as increased noise tolerance [13, 16]), and are experimentally feasible today [17, 18, 19, 20], our new analysis may provide even further benefits to these systems. We note that in [1], the sampling framework was used to provide a proof of security for the standard (qubit-based) BB84 using alternative methods which were specific to the qubit-BB84 protocol. Our method provides, first, a novel entropic uncertainty relation which may have numerous other applications to quantum cryptographic protocols outside of HD-BB84; and, secondly, provides as an application a simple proof of security for the high-dimensional variant of BB84 for any dimension of the system.
This work makes several contributions, not the least of which is showing yet further fascinating, and highly applicable, connections between the quantum sampling framework of Bouman and Fehr [1] and quantum information theory, in particular entropic uncertainty. Furthermore, our relations are immediately applicable to quantum cryptography in the finite key setting, leading to composable security [11] and, as we show, in most typical scenarios also highly optimistic secure bit-generation rates for source-independent QRNG protocols and QKD protocols. In practice, such sampling-based approaches show that quantum communication systems may run at higher bit-generation rates than previously thought. Thus, not only does this work provide interesting theoretical contributions, but also potential practical ones (though, as stated, we are not considering practical experimental imperfections here, leaving this as interesting future work). We suspect that there are even more connections and applications of the quantum sampling framework which may shed further light on problems in general information theory and applied quantum cryptography. This paper attempts to take a step forward in that direction.
1.1 Notation
We start with some notation and definitions that we will use throughout this work. An alphabet is a set of characters which we typically label . Given a word , the substring indexed by is the string . The substring denotes the substring indexed by the complement of .
Much of our work involves arguing about the properties of a given word. In particular, given a string , the relative Hamming weight is defined as and the relative character count with respect to is defined as . Note that . We will use to denote the -tuple of all relative counts, namely . The Hamming distance between two strings is .
A density operator is a positive semi-definite Hermitian operator with trace equal to one, acting on some Hilbert space . If acts on some Hilbert space , we write to mean the partial trace of over (similarly for other systems).
We use to denote a -dimensional Hilbert space. Given a basis of , and given a word , we write to mean . If the basis under consideration is clear, we will sometimes write to mean .
The Shannon entropy of a random variable is denoted by . The -ary entropy function is defined as . Note that when this is simply the binary Shannon entropy. Finally, we define the extended -ary entropy to be if ; otherwise if or if .
Given acting on , then the conditional quantum min entropy [11] is defined to be:
| (3) |
When the system is trivial, we have , where the maximum is taken over all eigenvalues of . In particular, if is a classical system (that is, ), then . Note that, for any quantum-quantum-classical state , then it is easy to prove from the definition of min entropy that the following holds:
| (4) |
Though we will not need it here, a useful interpretation of for classical-quantum states (cq-states) (that is, states of the form ) was given in [21] as:
where is the maximal guessing probability that Eve can guess the value of Alice’s register, namely:
where the maximum is over all POVM operators on .
Finally, the conditional smooth min entropy is defined to be [11]
| (5) |
where and here is the trace distance of operator .
For additional notation, given a quantum state and an orthonormal basis of the register, we write to mean the conditional min entropy of after measuring the system using the basis. If the state is pure, namely , we write . This notation is similar for smooth min entropy.
The following Lemma relating the min entropies of mixed and pure states will be useful to our work later as it will allow us to bound the min entropy of a superposition of states by, instead, computing the min entropy of a corresponding mixture of states:
Lemma 1.1.
Quantum min entropy is of vital importance to quantum cryptography as it allows one to determine how many uniform random bits one may extract from a -state that are also independent of Eve. In particular, given a -state (which, itself, is typically the result of running some quantum cryptographic protocol where the register may not be uniform random or completely independent of the register), one may apply the process of privacy amplification (typically running the register through a randomly chosen two-universal hash function) to establish the required uniform and independent random string. If is the result of applying privacy amplification to the initial system, where the register is of size bits, it was shown in [11] that:
| (6) |
Thus, by deriving a lower-bound on the min entropy of the initial state before privacy amplification, one may establish how many uniform and independent bits may be extracted (namely, ) from the state to satisfy the above trace distance inequality up to a desired level of security; e.g., so that the difference between the real state and the “ideal” state (which represents a uniform random string, independent of any other system) is no more than some .
2 Quantum Sampling
In [1], Bouman and Fehr discovered a fascinating connection between classical sampling strategies and quantum sampling. Since our work utilizes this as a foundation to prove our entropic uncertainty relations (later used to prove security of QRNG and QKD protocols), we take the time in this section to provide a review of their main results. Everything in this section, definitions, concepts, and theorems, come from [1] except when explicitly mentioned. Occasionally, we will make some generalizations and simplifications, however wherever we do so, it will be made clear in the narrative.
Let be an alphabet with characters and be fixed. A classical sampling strategy is a triple , where is a probability distribution over subsets of , is a probability distribution over some set called seed values, and is a function:
| (7) |
Given a string , the strategy consists of, first, sampling a subset according to ; sampling a seed value according to , observing the value of and evaluating . This evaluation should lead to a “guess” of the value of some target function evaluated on the unobserved portion of , namely . Informally, a good sampling strategy will ensure that, with high probability, (i.e., the difference in all coordinates of the output function evaluated on the sampled portion of , compared to the target function evaluated on the unobserved portion, are no greater than ). Note that above, we are generalizing the sampling result of [1] to include more general target and guess functions; in [1], and , the Hamming weight of . However, the proof of their main result is easily seen to hold in this more general case, so long as suitable classical strategies are analyzed appropriately (as we do later in this section). Finally, note that in our work, we do not make use of this additional random seed value (which is useful when implementing randomized guess functions ); thus, we disregard writing it from here on out and, instead, our function simply maps strings from to values in .
Now, fix a subset and and consider the set:
| (8) |
This set consists of all “good” words in where, for the given choice of , the estimate produced by is close to the desired target function on the unobserved portion. Note that, when the context is clear, we will forgo writing the and superscripts. From this, the error probability of the given classical sampling strategy is defined to be:
| (9) |
where the probability is over the choice of subsets drawn according to (the notation is used to denote the set defined above for a fixed whereas denotes a random variable over the choice of subset ). Note that the randomness here is only over the choice of subset; if the function need also make random choices, this could be incorporated through the use of the additional seed value. Since our strategies we use here do not need this, we forgo considering it.
From the above definition, it is clear that for any , the probability that the sampling strategy fails to produce an accurate estimate of the target function is at most . The “cl” superscript is used to denote that this is the failure probability of the classical sampling strategy.
These notions may be adapted to quantum states. Let be the -dimensional Hilbert space spanned by some orthonormal basis . The choice of basis may be arbitrary, however all following definitions are taken with respect to the chosen basis.
Given a classical sampling strategy (again, disregarding the seed which we do not use) and a quantum input state , a quantum sampling strategy may be constructed as follows: first, sample according to ; second, measure those qudits in indexed by using basis to produce measurement result ; finally, evaluate the function . The main result from [1], informally, is that the remaining unmeasured portion of the input state should behave like a superposition of states that are close in the target function to the estimated value .
More formally, consider:
where, by , we mean (again, with respect to the given basis). Note that, if , and if subset is actually the one chosen by the sampling strategy, then it is guaranteed that, after measuring those qudits indexed by in the given basis resulting in outcome , the remaining unmeasured portion will be in a superposition of states of the form:
where:
Formally, the main result from [1] is stated below, which argues that the input state will be close in trace distance to an ideal state where this sampling process always yields the correct guess and this collapse always happens. Furthermore, the depends on the error probability of the underlying classical sampling strategy.
Theorem 2.1.
(From [1], though reworded for our application): Let be a classical sampling strategy with classical failure probability for given . Then, for every state with , there exists a collection of states indexed by subsets of with each such that
| (10) |
where represents a sampled subset of .
Proof.
In Bouman and Fehr’s work [1], it was shown that for a fixed it holds that
| (11) |
where the minimum is over all , for a sampling strategy where the target function was . However, in their proof, the above is shown directly by projecting the input into the space , thus directly constructing the ideal states. Namely, the ideal states were defined by the decomposition where the lives in a space orthogonal to the ideal. This minimum is therefore attained by these ideal states. Furthermore, there is no specific reason in this construction to restrict to target functions that are the Hamming weight, nor to target functions that are one-dimensional. Indeed, by considering any definition of , their construction and the subsequent analysis follows identically assuming the error probability is defined as in Equation 9 based on the set . The important difference comes in the analysis of the classical sampling strategy in order to compute . ∎
The fascinating thing about Theorem 2.1 is that, by choosing suitable classical sampling strategies, one may analyze the behavior of ideal states which always behave appropriately for the given strategy. From this, and the fact that the real state is close, in trace distance, to these ideal states (on average over the randomness in the sampling strategy), one may then promote the analysis from the ideal state to the actual input. Already in [2, 3], we used this to prove novel, and useful, quantum entropic uncertainty relations which were then used to analyze particular QRNG protocols. We now generalize these results, analyze a more powerful QRNG protocol, and also show how this can be used to develop three-party entropic uncertainty relations (involving , , and ) with applications to high-dimensional QKD protocols. We show that, furthermore, this provides highly optimistic secure bit generation rates for both the QRNG and QKD protocols in a variety of scenarios. However, to analyze these protocols, we first require some important classical sampling strategies.
2.1 Classical Sampling Strategies
As discussed, Theorem 2.1 allows us to consider classical sampling strategies and use these to analyze quantum protocols. Here we discuss four classical sampling strategies which we denote and . Strategy was analyzed in [1] and we use this to bound the error of the other strategies. The other strategies involve one party () or two parties ( and ) and will be used later when deriving our entropic uncertainty relations.
One-Party HD-Restricted-Sampling : In [1], the following natural sampling strategy was analyzed which we denote here as . We use this result to bound the error in our other sampling strategies to be discussed next. Let be a string and the target function . The strategy, first, chooses a subset of of size , uniformly at random and observes string . Next, it outputs , an estimate of the Hamming weight of the unobserved portion, namely . We call this the HD-Restricted-Sampling strategy as it is high-dimensional, however it only looks at the Hamming weight, ignoring the counts of other characters. The following Lemma was proven in [1]:
Lemma 2.1.
(From [1]): Let and . Then the failure probability of the above described sampling strategy for is:
We comment that there is nothing special in the above sampling strategy, or their proof, about the use of the Hamming weight in the above Lemma; instead one could replace the target function with any single or (to count the number of letters equal to, or not equal to, respectively) and the same bound will follow (for a single, fixed but arbitrary, ). See [1].
One-Party HD-Full-Sampling : In our work, here, we will need three additional sampling strategies. The first sampling strategy, which we denote , is a one-party strategy involving Alice only and will be used for our QRNG analysis later. The strategy works for strings in , where and the target function is where is the relative number of times symbol appears in the word (as defined in Section 1.1). First, the strategy chooses a subset of size from uniformly at random and observes the string . Finally, outputs as an estimate of the relative counts of the unobserved . The proceeding Lemma determines an upper bound on the error probability of the sampling strategy .
Lemma 2.2.
Let and . Then the failure probability of the above described sampling strategy when is:
Proof.
Note that, for any , is exactly the strategy (though, instead of looking at the number of strings with a certain Hamming weight, we are looking at the number of strings with a certain character count). Thus, using the bound provided by Lemma 2.1 we find
∎
Two-Party HD-Sampling : The second strategy we require will be used for our two-party applications later and we denote by . Here, we have an input string , where . The strategy will first choose a subset of size uniformly at random. The strategy will then sample and ; that is, it will observe the portion and portion individually, using the same subset (this may be written strictly using our earlier definitions, however such strict formality is not enlightening). The target function is (where is the relative Hamming distance of words and as defined in Section 1.1) and the output will be . Again, we may bound the error probability of this strategy using Lemma 2.1.
Lemma 2.3.
Let be the strategy defined above; and . Then .
Proof.
Let and and Pick and let , where the subtraction here is character-wise, modulo , in the given alphabet. Clearly , and similarly for . Thus, if and only if . Hence, for every , it holds that:
Since this holds for any , we’re done. ∎
Finally, we define a second two-party sampling strategy which combines with ; we denote this strategy by . For this strategy, the target function is now for some given, fixed, distinguished index (we later call this the “count index”). This sampling strategy chooses a subset according to and outputs a guess It is not difficult to show from Lemmas 2.1 and 2.3 that the error probability of this strategy is:
| (12) |
3 Quantum Sampling Based Entropic Uncertainty
In [2, 3], we showed how the technique of quantum sampling, introduced in [1] and discussed in the previous section, can be used to prove entropic uncertainty relations bounding the smooth quantum min entropy and the Shannon entropy, as a function of the overlap of two projective measurements. Our first work [2] introduced a novel entropic uncertainty relation applicable to qubits (i.e., ) only and with a fixed sampling strategy; in [3], we expanded the result to work for qudits (), however only with a partial basis measurement and a particular, fixed, sampling strategy. Here, we discuss and generalize this result to work with more general sampling strategies allowing a “plug-and-play” entropic uncertainty relation for various classical sampling strategies. Indeed, as shown in this section, one may introduce an arbitrary classical sampling strategy (perhaps one that is useful for a particular cryptographic application); one need only compute the error probability of the given classical strategy, along with the size of a set similar to (generally a classical combinatorial proof) to derive a result applicable to a quantum system. The proof of this follows the same two-step approach we introduced in [2, 3] only with suitable generalizations at certain points.
To describe our sampling based entropic uncertainty relations, we require an experiment which takes as input a quantum state acting on where the portion is an -fold tensor of some smaller -dimensional Hilbert space and the register is a Hilbert space spanned by orthonormal basis where . The experiment also requires an orthonormal basis .
The experiment will first choose a random subset by measuring the register. It will then measure the portion of , indexed by , using the given basis. This measurement results in outcome and a post-measurement state , acting on the unmeasured portion of and . We denote this experiment by . Note that the experiment also returns the subset chosen. Sampling based entropic uncertainty relations allow one to bound the min entropy in the remaining post-measured state, assuming an alternative measurement were to be made on the portion of it. This bound is a function of the measurement overlap and the classical measurement outcome .
The main result from [2, 3] was to relate the min entropy in the remaining portion of the system as a function of the measurement overlap and the binary Shannon entropy (or, in the case of [3], the -ary Shannon entropy) of the relative Hamming weight of the observed outcome after running the experiment. However, the proof technique used there can be applied to a more general setting allowing for arbitrary sampling strategies and, in particular, to bound the min-entropy as a function of the measurement overlap and the size of a particular set of classical strings that are -close to the observed .
Theorem 3.1.
Let and be a classical sampling strategy with error probability for given . Let , and let be an arbitrary quantum state acting on space , where for . Let and be two orthonormal bases of . Furthermore, let , where the sum is over all possible subsets of that could be chosen by and is the probability of subset being chosen as determined by the given classical sampling strategy. Finally, let . Then, it holds that:
| (13) |
where
| (14) |
Above the probability is over the randomness in the experiment (namely the subset chosen and the resulting measurement outcome ).
Proof.
The proof follows the same two-step argument we developed in [2, 3]. In fact, most of the proof is identical with the exception of a few generalizations; we provide the proof here at a high-level only for completeness, referring the reader to [2, 3] for complete technical details when needed.
First Step - Ideal Analysis: We begin by considering the case when the input state is pure; the mixed case then follows through standard purification techniques.
By applying Theorem 2.1 with respect to the given basis and sampling strategy , there exist ideal states such that for every , the state . Note that the target function also depends on the sampling strategy. Furthermore, from this application of Theorem 2.1, if we define then it holds that:
| (15) |
Consider the output of running . Here . It is not difficult to see that the resulting state, after tracing out the measured portion, is of the form:
| (16) |
where (note that some of the ’s may be zero).
Let . From Lemma 1.1, we have , where is the mixed state:
It is straight-forward to show that . This is done by conditioning on an additional classical system, writing out the probability distribution of the basis measurement given and taking advantage of Equation 4 (see [3] for explicit details on how this computation is done given a mixed state of this form). Thus, with certainty, the ideal case, after choosing subset and observing , will have min entropy no less than .
Second Step - Real Case Analysis: The second step involves arguing that the real state cannot behave too differently from the ideal state we just analyzed. We make use of Chebyshev’s inequality while also switching to smooth min entropy to complete the analysis.
Consider the real state where is given as input to the theorem (note that, here, the input state is independent of the subset chosen unlike in the ideal case). The process of choosing a subset , measuring, and observing (resulting in post-measurement state ) may be described, entirely, by the mixed state:
where is the probability of observing outcome given that the subset was sampled; here we use the “R” register to denote the remaining, unmeasured, portion of the state. Likewise, the ideal state, after performing this experiment, may be written as the mixed state: . We define , which may be treated as a random variable over the choice of and observed . We want to show that, with high probability, is “small.”
It is not difficult to show that the expected value of is . Furthermore, the variance of this random variable has the property that (see our proof in [2] for both these computations, though they follow immediately from properties of trace distance and the fact that ).
Now, by Chebyshev’s inequality, we have:
| (17) |
(the last inequality follows since ); note that this probability is over all subsets and measurement outcomes . Thus, except with probability at most , after choosing and observing , it holds that which implies:
Thus, we may conclude that , completing the second step of the proof.
Of course, the above analysis assumed the input state was pure. However, if the state is not pure, it may be purified and, incorporating this extra system to , the result above follows. ∎
Notice that one may choose sampling strategies suitable to a particular application and, then, need only to analyze the classical strategy to attain a result in the quantum setting. Furthermore, arbitrary sampling strategies may be employed with arbitrary target functions, leading to a potential wide-range of applications. One simply needs to analyze the failure probabilities of the resulting classical sampling strategy (Equation 9). We demonstrate this by analyzing a QRNG protocol in the next section.
3.1 Application to Quantum Random Number Generators
Quantum Random Number Generators (QRNG) are protocols which, by utilizing a physical source of randomness in particular quantum sources, attempt to distill a uniform random string. For a cryptographic QRNG, the string should be uniform random and also independent of any adversary. At the most basic level, a QRNG protocol could consist of a source emitting a photon passing through a beam splitter connected to two photon counters. Such a system will lead to a random measurement on one detector or the other, producing a random stream of ’s and ’s. Such a setup assumes fully trusted devices (both the source and measurement apparatus are fully trusted and characterized and outside the control or influence of any adversary).
On the opposite extreme is the fully device independent model [22, 23] whereby the source and measurement apparatus are not trusted (perhaps manufactured by the adversary - though one must still assume, of course, that the actual measurement outcome reported by the untrusted device cannot be sent to the adversary). Fully device independent protocols are obviously highly desirable from a cryptographic standpoint; however in practice, they are slow to implement [24, 25]. This leads to a middle-ground between these two extremes known as the source-independent (SI) model introduced originally in [10] and studied further in several works including [26, 27]. Here, the quantum source is not trusted, however the measurement devices used are trusted and characterized. Such protocols are a step up from the fully trusted scenario (as they can take into account physical imperfections, but also the fact that an adversary may be entangled with the source and, thus, attempt to gain information on the resulting random string). Furthermore, they are highly practical, leading to Gbps implementations [28]. Finally, by not trusting the source, several fascinating possibilities are open, including the use of sunlight as the source [29]. For a general survey of QRNG protocols and their security models, the reader is referred to [30].
In previous work, we showed that sampling-based entropic uncertainty relations provide optimistic results for QRNG protocols. In [2], we analyzed a qubit-based protocol but without an adversary. In [3], we analyzed a SI-QRNG protocol with an adversarial source and qudits (-level systems), however where Alice was restricted to performing only a partial basis measurement (our previous relation could not take into account a full basis measurement for the sampling stage of the protocol). Here, we show how our entropic uncertainty relation can be used to provide highly optimistic bit generation rates for the full high-dimensional SI-QRNG protocol introduced in [10] (where a full basis measurement is required for the test stage). The protocol we analyze requires Alice to be able to measure in two bases and . We assume the measurement devices are fully characterized and so is known. In the following we will assume that for all however our analysis works identically for other scenarios. The protocol, then, operates as follows:
-
1.
Preparation: An adversary prepares a quantum state , where the portion is an -fold tensor of (i.e., the register consists of qudits of dimension for a known ). The portion is sent to Alice while the portion remains with the adversary. An ideal source should prepare the state - that is, a state independent of Eve and with perfect copies of the qudit state . As the source is adversarial, we do not assume anything about the structure of other than it lives in .
-
2.
Sampling and Measurements: Alice chooses a random subset of size and measures those qudits indexed by in the basis, recording the outcome as . The character counts of this will be used to determine how much information an adversary has (it should be that is high). The remaining qudits she measures in the basis, saving the resulting string as . Note we are not considering experimental imperfections on the devices such as dark counts or low-efficiency detectors - we are only interested in the theoretical bound of ideal measurements, leaving these interesting practical measurement concerns as potential future work.
-
3.
Post-Processing: Alice runs a privacy amplification protocol, applying a two-universal hash function to the string , resulting in her final random string . As proven in [31], for a QRNG protocol of this nature, the hash function need only be chosen randomly once and then reused, so no additional randomness is needed here.
The sampling portion of this protocol is easily seen to be introduced in Section 2.1 with target function . In this case, the size of the chosen subset is always leaving qudits unmeasured. So we write in place of from Theorem 3.1 and its definition is:
| (18) |
To apply the sampling based entropic uncertainty relation of Theorem 3.1, we first bound the size of this set. Of course where is the relative Hamming weight of . Then, using the well-known volume of a Hamming ball, we may bound . This is the bound we used in our entropic uncertainty relation in [3] (which was based on the set not the full since full measurements were not supported in our earlier work). However, when we have full information on the string , we may attempt to derive a tighter bound on itself for use in analyzing this QRNG protocol. Theorem 3.2 provides an alternative bound on which is tighter in some scenarios as we discuss later.
Theorem 3.2.
Let and be given. Define the functions for each , dependent on the choice of , to be
then, for defined in Equation 18, we have:
| (19) |
Proof.
To prove this, we count the total number of ways one may construct a string with the required counts. Let and observe that
Let . Of course . This immediately implies
Now let be the values in increasing order which satisfy for all . We can enumerate the set as
Then
The benefit of isolating these partial sums of is that we can take advantage of the Taylor series for to bound this partial sum. We can expand on this to get the following:
Since each , we replace the value of with the value for each , where is defined in the Theorem statement. Furthermore, below, since , we only need to multiply by those . Then,
Now we use Theorems 3.1 and 3.2 to analyze the protocol described above. Let be arbitrarily chosen by the user (this will determine the user’s desired failure probability and security properties). We use
| (23) |
which, by Lemma 2.2 implies that the failure probability will be (and so the in Theorem 3.1 will match the chosen value of here). Finally, let be the distance from an ideal uniform random string of size independent of ’s system.
Using Theorem 3.1 along with privacy amplification (Equation 6), we have that, except with probability at most , the number of uniform random bits extracted from the protocol leading to an secure string is:
| (24) |
where
| (25) |
| (26) | ||||
| (27) |
by Theorem 3.2 and the standard bound on the volume of a Hamming ball as discussed earlier. In our evaluations, we set and which balances the failure probability of Theorem 3.1 (namely, the probability of failure is ) and the smoothing parameter used in the min entropy. With these settings, the failure probability and the value of are on the order of .
We compare our new lower bound for this protocol against the lower bound provided in [10] using alternative methods and an alternative entropic uncertainty relation. We also compare with another high-dimensional SI-QRNG from [32]. Note that, due to our bound on in Equation 25, our new result here will never be worse then the SI-QRNG protocol analyzed in our prior work [3] (which used Equation 27 only) and so we do not compare with that here.
A lower bound for the SI-QRNG protocol of [10], which we denote here as , was given in that reference by:
where is the test size and represents the number of measurement outcomes that result in outcome .
The protocol of [32] is slightly different from the one we analyze. Here, an adversarial source prepares an entangled high-dimensional state (if the source were honest, it would prepare copies of the state ) sending the and registers to Alice. Alice chooses a random subset and measures the and qudit systems each in a -dimensional basis resulting in classical characters and corresponding to the th iteration of registers and . For the remaining unmeasured systems, she discards the system and measures only the system in the basis resulting in her secret string. If the source were honest, it should be that the basis measurement outcomes of the and register are fully correlated. She then applies privacy amplification to the result of the basis measurement. A lower bound for the number of random bits that may be extracted from this protocol, which we denote here as , was computed in [32]:
where
| (28) |
and
| (29) |
The term is computed as the average difference between the measurements values of the pairs, and for from 1 to . That is,
For all protocols, we assume a failure probability on the order of . The difference from the ideal random string (Equation 6) is also set to be . As we are only interested in comparing the relative performance, we do not consider the additional randomness used to choose a random subset of size . Since all protocols in our evaluation are using the same process for this and same sampling sizes (in particular we use of all signals for sampling), they will each lose the same amount from their respective values and so the comparison remains unchanged.
Note that for each of the three bounds, no assumption is needed on the noise in the channel - Alice simply uses the direct measurement result from the test case (in the basis) and evaluates . To compare, however, we will simulate certain noise scenarios. We first compare these protocols assuming a depolarization channel acting on each qudit state independently and identically. Such a channel will cause the qudit to become the completely mixed state with some probability ; otherwise it remains in its original state. In this setting, we see the protocol of [10], but augmented using our new entropic uncertainty relation here outperforms both and . Since is the same protocol we are analyzing with this shows the great benefit of sampling-based entropic uncertainty relations. This evaluation is shown in Figures 1, 2. Next, we evaluate on asymmetric channels which are more likely to add noise towards one basis vector over another (i.e., it is more likely to change a to a as opposed to changing a to a ). Depending on the state favored by the channel, our bound generally outperforms prior work as shown in Figures 3 (right), 4 and 5 (right), though there are scenarios where the protocol of [32] can outperform our analysis as shown in Figures 3 (left) and 5 (left). Note, however, that the protocol of [32] is a different protocol; our methods applied to that protocol may provide a boost in performance in this scenario also, a question we leave as future work. Comparing with , which is the generation rate for the same protocol of [10], shows that our new entropic uncertainty relation always leads to more optimistic bit generation rates in every scenario we simulated. Also, note that in all cases (including in the case highlighted in Figures 3 and 5), if we take the number of signals to be high enough, our bound outperforms.
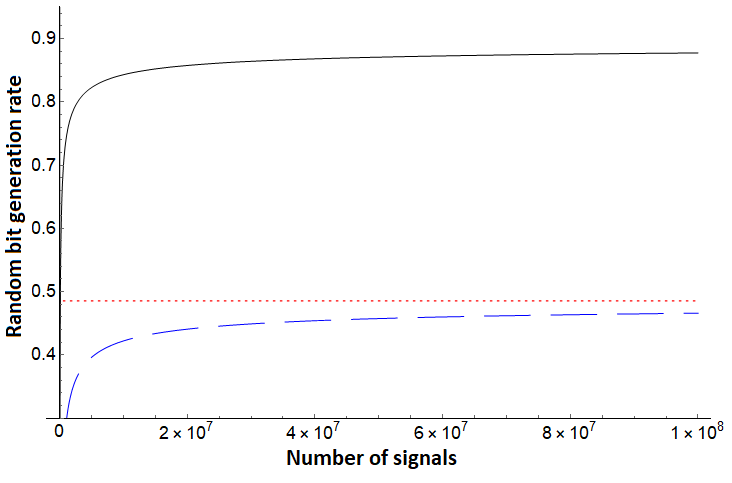
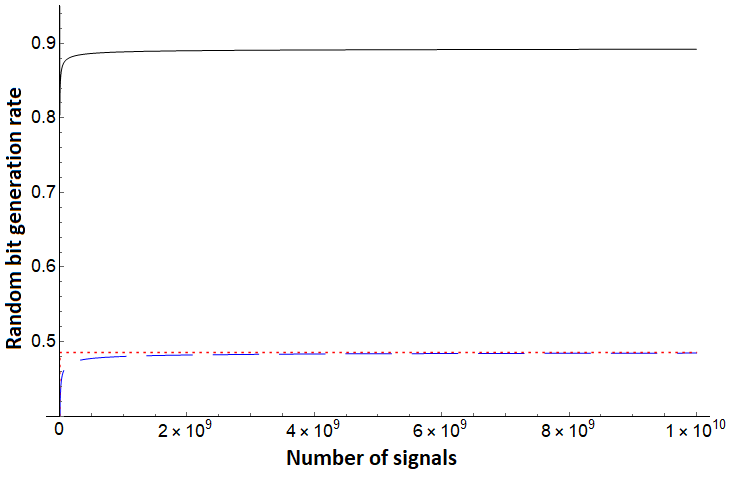
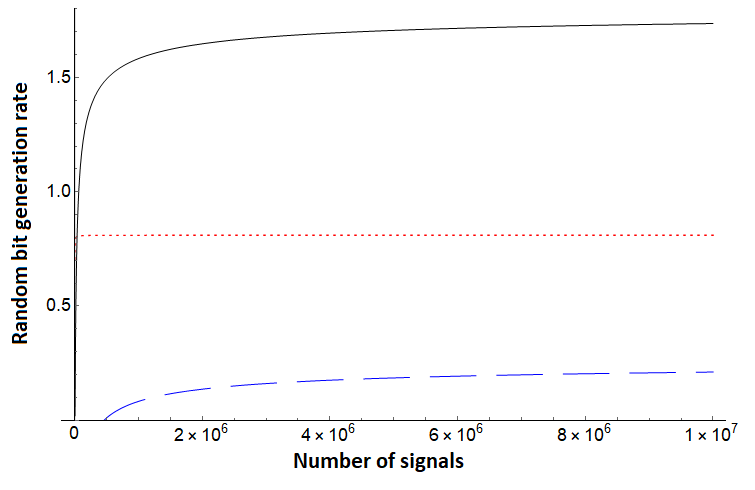
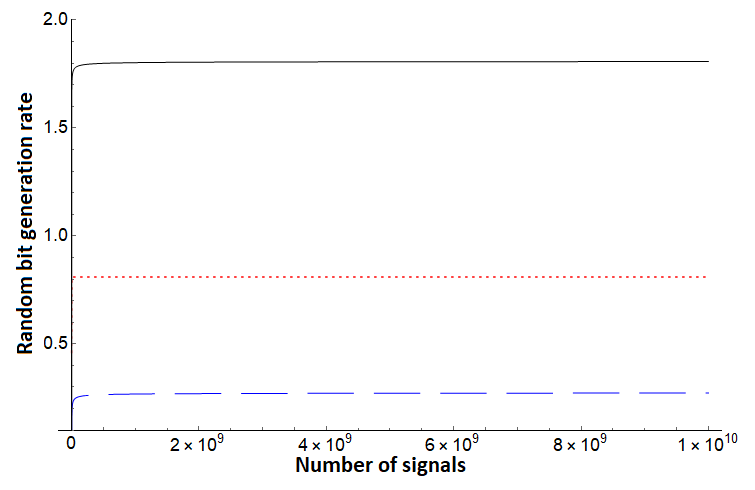
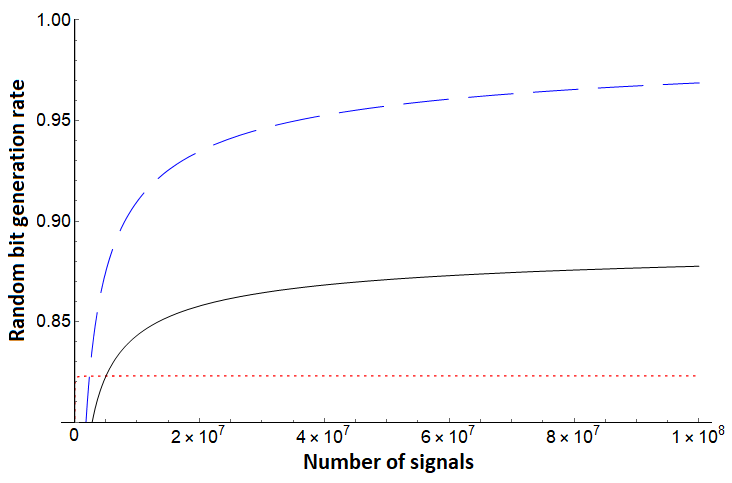
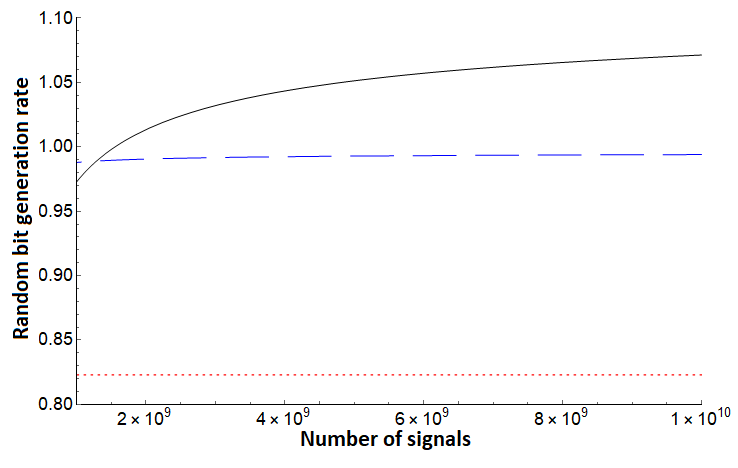
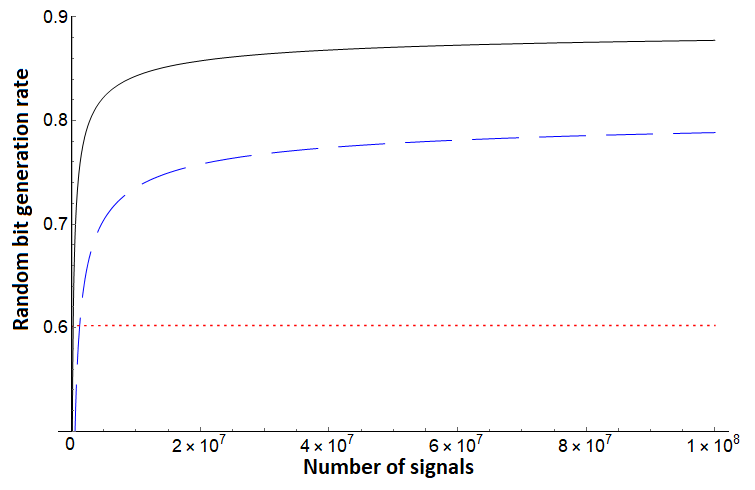
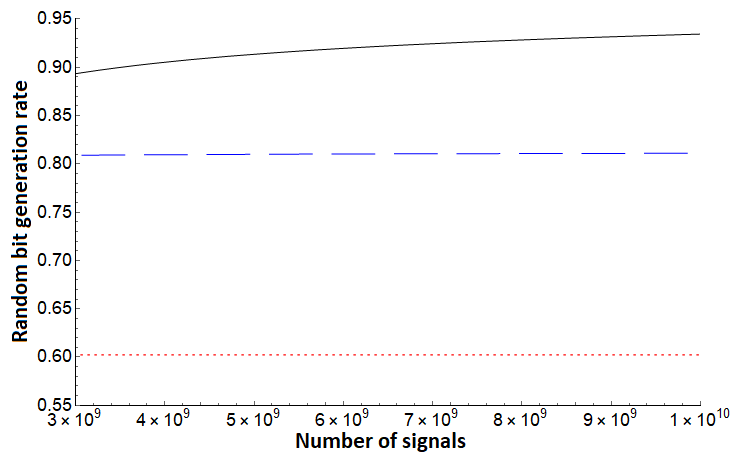
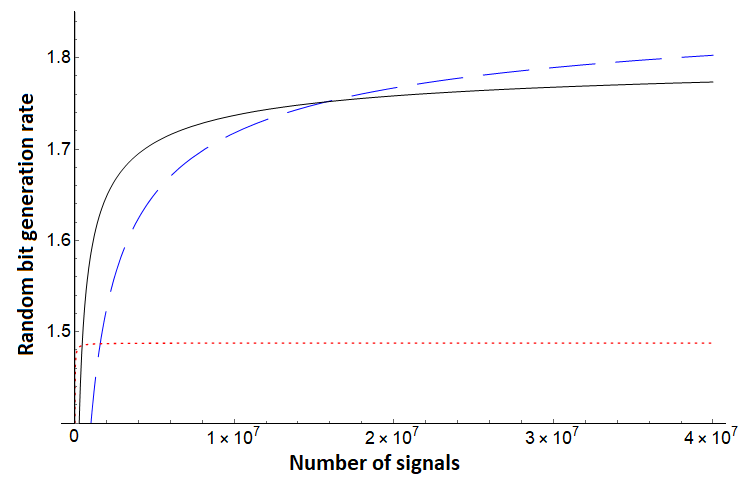
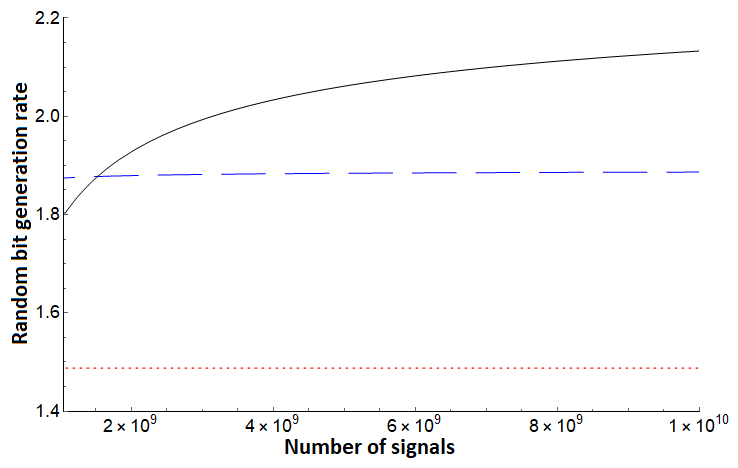
In summary, Figures 1 and 2 highlight how consistently outperforms [10] and [32] on a depolarization channel for different dimensions . Our bound for still performs very well on systems far from depolarization, as shown in Figure 4. However, there can exist quantum channels which lead to producing a lower random bit generation rate than for certain . Even in these cases, Figures 3 and 5 highlight that, assuming sufficient computational power to process larger blocks in the post-processing stage of the protocol, can produce a much higher random bit generation rate than and on a large block of signals.
3.2 Asymptotic Behavior and Analysis
In Equation 25, we take the bound for to be the minimum of Theorem 3.2 and the size of a Hamming ball. The reason for doing so is that while the bound on the size of a Hamming ball is tighter for some scenarios, the bound from Theorem 3.2 is significantly better in others, especially, as our numerical simulations show, for large numbers of signals. In this section, we analyze and compare the asymptotic behavior of both bounds. We will also use this work to show an alternative proof of the famous Maassen-Uffink relation [4] for high dimensional systems.
First, we prove a technical lemma about the relation between the -ary entropy function and the Shannon entropy, which will be needed to analyze the asymptotic behavior.
Lemma 3.1.
Let be a discrete random variable with possible outcomes such that the probability of observing outcome is for each . Then for any , it holds that
where equality holds if and only if for all (i.e., if the distribution is uniform on the other outcomes not equal to ).
Proof.
Fix and let be the random variable where the probability of observing is and the probability of observing for any is . Then
Moreover, observe that
Note the inequality is shown by recalling that Shannon entropy is maximal if and only if given a uniform distribution (which also proves equality if the distribution is uniform on outcomes other than ). ∎
We now show that our bound for converges to the Shannon entropy of the random variable induced by a measurement on some i.i.d. system. This will then lead us to an alternative proof of the Maassen-Uffink relation from [4].
Lemma 3.2.
Let be a quantum state acting on and consider the -fold tensor state . Furthermore, let . Consider measuring all qudits of the state in some -dimensional orthonormal basis resulting in some and from this define the set as before. Then it follows that
Proof.
Define and let
Observe that where we used the fact that . Since we have
Then, as by the law of large numbers and the assumption on , where we use to denote the probability of observing , the ’th basis vector in the measurement basis . Hence,
Finally, by Theorem 3.2, we have , and so we conclude
∎
Now we are ready to show that our bound for grows at most as quickly as the volume of a Hamming ball (used in our earlier work in [3]). How much slower our bound grows asymptotically depends on the observed relative counts from the sampled .
Theorem 3.3.
Let for any . Let , where is the element of such that , and
Let depend on and asymptotically. Then for arbitrary quantum state acting on , we have that
where equality holds if and only if for all given is the probability of observing outcome in basis (measuring ).
Proof.
3.2.1 Alternative Proof of Maassen-Uffink Relation
With the above analysis, our Theorems 3.1 and 3.2 can be used to provide an alternative proof of the Maassen and Uffink entropic uncertainty relation for projective basis measurements of -dimensional states. Note that in [2] we showed quantum sampling can be used to provide an alternative proof of this relation but only for the qubit case. Furthermore, our earlier work in [3] also cannot lead to an alternative proof of this relation in the high dimensional () case as Theorem 3.3 shows.
Corollary 3.1.
Let and be two orthonormal bases and let be a density operator acting on . Then, except with arbitrarily small probability, it holds that
where .
Proof.
Consider the state . We apply Theorem 3.1 to using sampling strategy with . Since is i.i.d., for any subset of size and any measurement outcome on that subset, the post-measurement state is simply .
Fix and . Then, for any and , setting , Theorem 3.1 implies that, except with probability at most , the inequality
holds, where is the observed value after measuring using . Then, by the asymptotic equipartition property, it follows that
This, combined with Lemma 3.2 and the fact that , completes the proof.
∎
4 A Three-Party Sampling-Based Entropic Uncertainty Relation
We now turn our attention to deriving a new three-party sampling-based entropic uncertainty relation involving Alice, Bob, and Eve. Later we show an application to a finite key analysis of the high-dimensional BB84 [13]. To begin, consider the following experiment, extending an earlier version to this three party case: on an input state of the form , choose a random subset by measuring the register, causing the state to collapse to (though, as before, this portion may be independent of the chosen subset in which case a random subset is chosen which does not affect the rest of the input state). We assume . Next, a portion of the and registers, indexed by the chosen subsets, are measured in basis resulting in outcome . This measurement causes the remaining state to collapse to . The experiment outputs .
Note that technically, by considering Alice and Bob as one party for the sampling portion, one could potentially use Theorem 3.1 with a suitable sampling strategy similar to or . However, this would bound the resulting min entropy as a function of the set . It is not difficult to see that (since for any fixed and , and for every , one may find a satisfying ). Recalling from our Theorem that the min entropy is higher when the size of this set is smaller. This would always produce the trivial bound of and so Theorem 3.1 cannot be used for the three-party case. We prove that sampling can provide an entropic uncertainty relation in this scenario for high-dimensional states by suitably modifying the first step of our proof method. Furthermore, we show how our proof method can lead to relations incorporating more than one overlap, useful in case the two bases have a shared vector in common (e.g., a “vaccuum” state vector for QKD).
Theorem 4.1.
Let , , and be an arbitrary quantum state acting on , where with and . Let and be two orthonormal bases of and define the maximal overlap as . Let and be a pair that attains this maximum, then we define the second-greatest overlap as:
(It is possible that for some bases.) Let
Finally, let , where the sum is over all subsets of the form with (over their respective subspaces) and . Then, except with probability at most , after running , it holds that:
where above, denotes the random variable resulting from measuring the remainder of the system of in the basis and the probability is over all choices of subsets and measurement outcomes within the experiment. If , then the above simplifies to:
Proof.
As with our other proofs of sampling based entropic uncertainty relations, this one follows the same two-step structure where, first, we analyze the ideal case, proving the result there; then, finally, we argue that the real case must follow the ideal except with small probability of failure. For this three party version, only the first step changes from our proof of Theorem 3.1, the second step is identical.
Consider sampling strategy defined in Section 2.1 with the count index set to which is the classical strategy we will employ in this scenario. By Theorem 2.1, there exist ideal states , indexed over all subsets , such that and, in this case as we are using , the set
Furthermore, by our choice of , and the failure probability of (from Equation 12), we have: where is the ideal state defined over all subsets and individual ideal states above (as in Theorem 2.1). If we consider performing the given experiment on this ideal state, afterwards, we will receive as output the chosen subset , the measurement results , and the post-measurement state which is guaranteed to be of the form:
where the above and are basis vectors (i.e., and ), and:
Rearranging terms and permuting the and subspaces, we may write the above state as:
where and . Note that some of the and ’s may be zero. Tracing out leaves us with:
where . At this point, measures the remaining portion of her register in the basis, resulting in . By appending a suitable classical system and conditioning on it, we may use Equation 4, to show that
Consider a particular and define . From Lemma 1.1, we have:
We first bound . Taking and measuring in the basis yields:
where
We wish to find an upper bound on for any and (within our constraints on ) which will be used shortly to bound the min entropy of the system. Recall, we have two particular overlaps we are considering: one for and one for the remaining possible pairs. It is not difficult to see that is maximized if, whenever that we have . This can happen at most times due to our constraint on and so the remaining counts (namely ) will be bounded using . Thus, we conclude:
| (30) |
Finally, we append a classical system spanned by orthonormal basis for all producing state:
Then, using Equation 4 and the definition of min entropy, we conclude:
Finally, it is clear that:
where the last inequality follows from the well-known bound on the volume of a Hamming sphere. Since the above analysis holds for any , we have therefore computed the resulting min entropy of the ideal case, namely for any chosen and observed , it holds that:
| (31) |
The second step of the proof involves arguing that the smooth min entropy , for the given input state , is bounded by the same quantity with high probability. This can be done in the same way as the second step in Theorem 3.1. Since the trace distance between the real and ideal states, for our chosen , is no greater than , the same error and smoothing bounds apply as in the second step in Theorem 3.1. thus completing the proof.
∎
4.1 Application to QKD Security
Entropic uncertainty relations involving three parties, , , and have numerous applications, especially in quantum cryptography. Here we demonstrate how our bound produces improved finite-key rate bounds for the High-Dimensional BB84 protocol (HD-BB84) introduced in [13]. High-dimensional QKD protocols have been shown to exhibit several advantages over qubit based protocols in some scenarios, including in noise tolerance. For a general survey of QKD protocols, the reader is referred to [33, 34] while for a survey specific to high-dimensional QKD, the reader is referred to [16].
HD-BB84 involves two orthonormal bases, which we denote and , each of dimension ; we will assume the bases are mutually unbiased and so for all . If we are considering lossy channels, then we will also add a vector to both these bases. Alice chooses a random basis and a random state within that basis (though not the state if it is there), sending it to . , on receipt of a quantum state will measure it in the or basis, choosing randomly. Afterwards, a classical authenticated communication channel is used allowing and to inform each other of their basis choices. If they are incompatible, the round is discarded; otherwise, assuming did not observe , they add bits to their raw key. Repeating times, each and has a raw key of size bits. However, this key is only partially correlated (there may be errors due to natural noise or adversarial interference) and only partially secret. Thus, an Error Correction protocol is run (leaking additional information to the adversary) and, finally, Privacy Amplification (as discussed in Section 1.1), resulting in a secret key of size bits. Maximizing is vital to efficient performance of QKD systems and, from Equation 6, this involves maximizing our estimate of the min entropy .
To analyze this protocol, we consider an equivalent entanglement based version, parameterized by , , and . We also consider an asymmetric version whereby only basis measurements contribute to the raw key, while basis measurements are used only for estimating the error in the channel. The entanglement based HD-BB84 runs as follows:
-
1.
An adversary prepares a quantum state , where . The portion is sent to Alice; the portion is sent to Bob; while Eve keeps the portion to herself.
-
2.
chooses a random subset of size and sends it to ; both parties measure their systems indexed by in the basis resulting in outcomes and respectively (these are strings in ). These values are disclosed to one another using the authenticated channel.
-
3.
and measure the remaining portion of their systems in the basis resulting in their raw-keys and of size at most bits each (if there are observations, those will not contribute to the raw key and so it may be smaller than in a lossy channel).
-
4.
and run an error correction protocol capable of correcting up to errors in their raw keys, leaking bits to Eve.
-
5.
Finally, privacy amplification is run on the error corrected raw key resulting in their secret key.
Note that when this is exactly the BB84 protocol. Note also that, by increasing the basis dimension to , we can add an additional “vacuum” state to both the and basis, such that . In this case the maximal overlap function is and the second maximal overlap function is . (Note that this shows the importance of our relation in being able to handle both cases individually.) Without this vacuum basis state, the dimension will be , and .
Using Equation 6 and results in [11, 35], if and wish to have an -secure key, we have:
Given and using our Theorem 4.1, setting , we have:
| (32) |
where is the number of counts in the observed of the distinguished vacuum basis state (which is shared between both the and basis making ). In particular, if the privacy amplification function is chosen to produce an output of size , it is guaranteed, except with probability at most , that the secret key will be secure according to Equation 6. Note that if we are not considering lossy channels, then the key-rate equation becomes simply:
| (33) |
To compare our new key-rate bound with prior work, we compare with results in [36] which is, to our knowledge, the current best bound for the HD-BB84 protocol in the finite key setting (with composable security, as is ours). Note that they used an entropic uncertainty relation from [37], resulting in a key-rate bound of:
| (34) |
where:
Where, for our evaluations, is the error parameter of a depolarization channel. Note that this prior work could not handle an additional vacuum basis state in each of the and basis (if it were added, the bound from [37] would become the trivial one as the overlap function would be ). So, when we evaluate, we will compare our bounds both without the vacuum basis then later by considering this basis state and loss in the channel.
In practice, the value of or is known and observed based on the actual channel used. However, to evaluate and compare our new key-rate bound we will evaluate assuming a depolarization channel with parameter acting on each qudit independently and identically. Such a channel maps a quantum state to:
Of course, our security proof does not require this depolarization assumption - instead, it is simply a channel we use to evaluate our bound and compare with prior work. It is also one of the most common noise models considered in theoretical QKD security proofs. For both protocols, we use which, for this depolarization channel, is easily found to be .
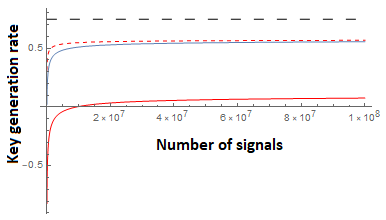
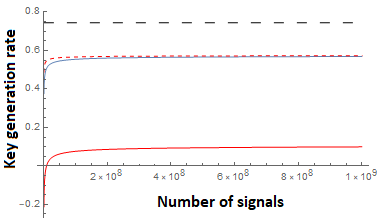
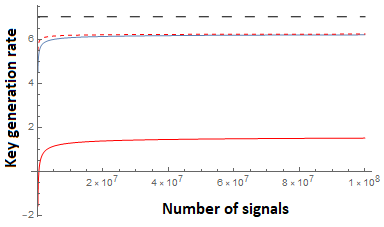
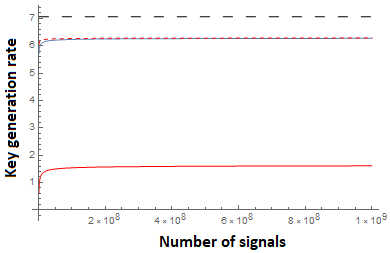
Finally, we compare to the theoretical, asymptotic upper-bound using the entropic uncertainty relation of [38]. This disregards all finite-key effects (such as failure probabilities and sampling imprecision), and takes the number of signals . This bound works out easily to be:
| (35) |
where again we used the easily verified fact that, for a depolarization channel with parameter , and, furthermore, we assume perfect error correction whereby .
Comparisons of both our new bound and prior work are shown in Figure 6 (for dimensions) and Figure 7 (for dimension ). We note that when , our bound is only slightly lower than Equation 34 and this difference decreases as the number of signals increases. Indeed, the difference turns out to be only that our confidence interval, determined by is slightly larger for any particular making our results asymptotically the same, though slightly lower than prior work for this case. However, one of the powers of our new relation is its ability to also handle two overlap functions allowing us to incorporate loss in both and bases. Of course, as the loss increases, the key-rate decreases as expected; our new entropic uncertainty relation can, however, easily handle this scenario. Further refinements to the classical sampling strategy used, may further improve our bound (in both the lossy and loss-less case). Indeed our analysis of Lemma 2.3 is not necessarily tight. Alternative sampling strategies or improved analyses, may be easily incorporated through our methods.
5 Closing Remarks
The quantum sampling framework of Bouman and Fehr, introduced in [1], provides a promising new tool to develop results in general quantum information theory and quantum cryptography. In our prior work [2, 3], we used this framework to introduce so-called sampling-based entropic uncertainty relations. In this paper, we showed how quantum sampling can be used to develop very general quantum entropic uncertainty relations allowing one to insert arbitrary classical sampling strategies, perhaps defined for a specific cryptographic task, which may then be “promoted” to analyze results for quantum systems. Furthermore, we developed an entirely new three-party entropic uncertainty relation using the sampling framework as a foundation, which has applications to high-dimensional QKD as we demonstrated here. Our new relation can also handle two different measurement overlaps, allowing one to work with bases that share common vectors (such as a “vacuum” measurement outcome). Since our relation handles all finite sampling precision, they provide an easy and general purpose framework for other researchers to develop finite-key cryptographic security proofs.
Several interesting future problems remain open. So far we only considered projective basis measurements. Generalizing these results to arbitrary POVM’s would be greatly interesting. However, this would require extending the quantum sampling technique to support such measurements. Furthermore, improving the three-party relation with a tighter sampling strategy would produce even more beneficial results. Finding other interesting theoretical and cryptographic applications of quantum sampling and our sampling-based entropic uncertainty relations would also be highly interesting. We feel that the framework of quantum sampling is powerful and can be employed successfully in other areas of quantum information science, and further exploration of quantum sampling in the domain of quantum information theory can yield even more exciting results in quantum cryptography.
References
- [1] Niek J Bouman and Serge Fehr. Sampling in a quantum population, and applications. In Annual Cryptology Conference, pages 724–741. Springer, 2010.
- [2] Walter O Krawec. Quantum sampling and entropic uncertainty. Quantum Information Processing, 18(12):368, 2019.
- [3] Walter O Krawec. A new high-dimensional quantum entropic uncertainty relation with applications. In IEEE International Symposium on Information Theory, ISIT 2020, pages 1978–1983. IEEE, 2020.
- [4] Hans Maassen and Jos BM Uffink. Generalized entropic uncertainty relations. Physical Review Letters, 60(12):1103, 1988.
- [5] K. Kraus. Complementary observables and uncertainty relations. Phys. Rev. D, 35:3070–3075, May 1987.
- [6] David Deutsch. Uncertainty in quantum measurements. Phys. Rev. Lett., 50:631–633, Feb 1983.
- [7] Iwo Bialynicki-Birula and Łukasz Rudnicki. Entropic uncertainty relations in quantum physics. In Statistical Complexity, pages 1–34. Springer, 2011.
- [8] Patrick J. Coles, Mario Berta, Marco Tomamichel, and Stephanie Wehner. Entropic uncertainty relations and their applications. Rev. Mod. Phys., 89:015002, Feb 2017.
- [9] Stephanie Wehner and Andreas Winter. Entropic uncertainty relations—a survey. New Journal of Physics, 12(2):025009, 2010.
- [10] Giuseppe Vallone, Davide G Marangon, Marco Tomasin, and Paolo Villoresi. Quantum randomness certified by the uncertainty principle. Physical Review A, 90(5):052327, 2014.
- [11] Renato Renner. Security of quantum key distribution. International Journal of Quantum Information, 6(01):1–127, 2008.
- [12] Antonio Acin, Nicolas Gisin, and Valerio Scarani. Security bounds in quantum cryptography using d-level systems. arXiv preprint quant-ph/0303009, 2003.
- [13] Nicolas J Cerf, Mohamed Bourennane, Anders Karlsson, and Nicolas Gisin. Security of quantum key distribution using d-level systems. Physical review letters, 88(12):127902, 2002.
- [14] Georgios M Nikolopoulos and Gernot Alber. Security bound of two-basis quantum-key-distribution protocols using qudits. Physical Review A, 72(3):032320, 2005.
- [15] Georgios M Nikolopoulos, Kedar S Ranade, and Gernot Alber. Error tolerance of two-basis quantum-key-distribution protocols using qudits and two-way classical communication. Physical Review A, 73(3):032325, 2006.
- [16] Daniele Cozzolino, Beatrice Da Lio, Davide Bacco, and Leif Katsuo Oxenløwe. High-dimensional quantum communication: Benefits, progress, and future challenges. Advanced Quantum Technologies, 2(12):1900038, 2019.
- [17] Jian-Yu Guan, Zhu Cao, Yang Liu, Guo-Liang Shen-Tu, Jason S Pelc, MM Fejer, Cheng-Zhi Peng, Xiongfeng Ma, Qiang Zhang, and Jian-Wei Pan. Experimental passive round-robin differential phase-shift quantum key distribution. Physical review letters, 114(18):180502, 2015.
- [18] Hiroki Takesue, Toshihiko Sasaki, Kiyoshi Tamaki, and Masato Koashi. Experimental quantum key distribution without monitoring signal disturbance. Nature Photonics, 9(12):827, 2015.
- [19] Shuang Wang, Zhen-Qiang Yin, HF Chau, Wei Chen, Chao Wang, Guang-Can Guo, and Zheng-Fu Han. Proof-of-principle experimental realization of a qubit-like qudit-based quantum key distribution scheme. Quantum Science and Technology, 3(2):025006, 2018.
- [20] Nurul T Islam, Clinton Cahall, Andrés Aragoneses, A Lezama, Jungsang Kim, and Daniel J Gauthier. Robust and stable delay interferometers with application to d-dimensional time-frequency quantum key distribution. Physical Review Applied, 7(4):044010, 2017.
- [21] Robert Konig, Renato Renner, and Christian Schaffner. The operational meaning of min-and max-entropy. IEEE Transactions on Information theory, 55(9):4337–4347, 2009.
- [22] Roger Colbeck and Adrian Kent. Private randomness expansion with untrusted devices. Journal of Physics A: Mathematical and Theoretical, 44(9):095305, 2011.
- [23] Stefano Pironio and Serge Massar. Security of practical private randomness generation. Physical Review A, 87(1):012336, 2013.
- [24] Peter Bierhorst, Emanuel Knill, Scott Glancy, Yanbao Zhang, Alan Mink, Stephen Jordan, Andrea Rommal, Yi-Kai Liu, Bradley Christensen, Sae Woo Nam, et al. Experimentally generated randomness certified by the impossibility of superluminal signals. Nature, 556(7700):223–226, 2018.
- [25] Yang Liu, Xiao Yuan, Ming-Han Li, Weijun Zhang, Qi Zhao, Jiaqiang Zhong, Yuan Cao, Yu-Huai Li, Luo-Kan Chen, Hao Li, et al. High-speed device-independent quantum random number generation without a detection loophole. Physical review letters, 120(1):010503, 2018.
- [26] Jing-Yan Haw, SM Assad, AM Lance, NHY Ng, V Sharma, Ping Koy Lam, and Thomas Symul. Maximization of extractable randomness in a quantum random-number generator. Physical Review Applied, 3(5):054004, 2015.
- [27] Bingjie Xu, Ziyang Chen, Zhengyu Li, Jie Yang, Qi Su, Wei Huang, Yichen Zhang, and Hong Guo. High speed continuous variable source-independent quantum random number generation. Quantum Science and Technology, 4(2):025013, 2019.
- [28] Marco Avesani, Davide G Marangon, Giuseppe Vallone, and Paolo Villoresi. Secure heterodyne-based quantum random number generator at 17 gbps. arXiv preprint arXiv:1801.04139, 2018.
- [29] Yu-Huai Li, Xuan Han, Yuan Cao, Xiao Yuan, Zheng-Ping Li, Jian-Yu Guan, Juan Yin, Qiang Zhang, Xiongfeng Ma, Cheng-Zhi Peng, et al. Quantum random number generation with uncharacterized laser and sunlight. npj Quantum Information, 5(1):1–5, 2019.
- [30] Miguel Herrero-Collantes and Juan Carlos Garcia-Escartin. Quantum random number generators. Reviews of Modern Physics, 89(1):015004, 2017.
- [31] Daniela Frauchiger, Renato Renner, and Matthias Troyer. True randomness from realistic quantum devices. arXiv preprint arXiv:1311.4547, 2013.
- [32] Feihu Xu, Jeffrey H Shapiro, and Franco NC Wong. Experimental fast quantum random number generation using high-dimensional entanglement with entropy monitoring. Optica, 3(11):1266–1269, 2016.
- [33] Stefano Pirandola, Ulrik L Andersen, Leonardo Banchi, Mario Berta, Darius Bunandar, Roger Colbeck, Dirk Englund, Tobias Gehring, Cosmo Lupo, Carlo Ottaviani, et al. Advances in quantum cryptography. arXiv preprint arXiv:1906.01645, 2019.
- [34] Valerio Scarani, Helle Bechmann-Pasquinucci, Nicolas J. Cerf, Miloslav Dušek, Norbert Lütkenhaus, and Momtchil Peev. The security of practical quantum key distribution. Rev. Mod. Phys., 81:1301–1350, Sep 2009.
- [35] Marco Tomamichel, Charles Ci Wen Lim, Nicolas Gisin, and Renato Renner. Tight finite-key analysis for quantum cryptography. Nature communications, 3(1):1–6, 2012.
- [36] Kamil Brádler, Mohammad Mirhosseini, Robert Fickler, Anne Broadbent, and Robert Boyd. Finite-key security analysis for multilevel quantum key distribution. New Journal of Physics, 18(7):073030, 2016.
- [37] Marco Tomamichel and Renato Renner. Uncertainty relation for smooth entropies. Physical review letters, 106(11):110506, 2011.
- [38] Mario Berta, Matthias Christandl, Roger Colbeck, Joseph M Renes, and Renato Renner. The uncertainty principle in the presence of quantum memory. Nature Physics, 6(9):659–662, 2010.