Satisfiability for two-variable logic
with two successor relations on finite linear orders111Work supported by the FET-Open grant agreement FOX, number FP7-ICT-233599.
Abstract
We study the finite satisfiability problem for first order logic with two variables and two binary relations, corresponding to the induced successor relations of two finite linear orders. We show that the problem is decidable in NExpTime.
1 Introduction
First-order logic with two variables (henceforth denoted by ) is of importance in computer science due to its decidable satisfiability problem (contrary to fragments of FO with 3 or more variables), and since it has connections with many formalisms, such as modal, temporal or description logics. Many fragments of have been studied because of this, especially in the presence of linear orders or equivalence relations. There are, still, a few relevant basic problems that remain open, and our work aims at expanding the classification of in the presence of linear orders. In this setting, linear orders are related with temporal logics, but it is also applicable in other scenarios, like in databases or description logics.
We study the two variable fragment of first-order logic with two variables and two successor relations on two finite linear orders. We show that the problem is decidable in NExpTime. This bound is optimal, since the problem is NExpTime-hard [4]. This logic has been previously claimed to be decidable in 2NExpTime in [12], but the proof was flawed.222In fact, according to its author, the proof of Lemma 4 in [12] is wrong [13], and there does not appear to be an easy way of fixing it. This is a key lemma employed to obtain the decidability results contained in [12]. (Of course, this does not affect the undecidability results contained in [12].) Here we adopt a different strategy to prove decidability. As a corollary of the results from the report [14], this logic is shown to be decidable with a non-primitive-recursive algorithm.333By this we mean an algorithm whose time or space is not bounded by any primitive-recursive function. Our result also trivially extends to the satisfiability of existential monadic second order logic with two variables () and two successor relations on finite linear orders.
This work focuses on the finite satisfiability problem and hence all the results discussed next are relative to finite structures. is a well-known decidable fragment of first-order logic. Over arbitrary relations, it is known to be decidable [15], NExpTime-complete [5]. over words (i.e., with two relations: a successor relation over a finite linear order, and its transitive closure) is NExpTime-complete [4]. The satisfiability problem was shown to be undecidable: in the presence of two transitive relations (even without equality) the satisfiability problem is undecidable [8]; in the presence of one transitive relation and one equivalence relation [11]; in the presence of three linear orders [9]; or in the presence of three equivalence relations [10]. However, if it has only two equivalence relations it is decidable [11]. Over words with one equivalence relation it is decidable [1]. If it only has a transitive closure over a finite linear order and an equivalence relation, then it is NExpTime-complete [1]. If it only has a successor relation over a finite linear order and an equivalence relation, it is in 2NExpTime [1]. On trees, with only successor relations (i.e., the child and next sibling relations) and an equivalence relation it is decidable in 3NExpTime [2].
There have also been works in the presence of a linear order and a linear preorder [17, 14]. In the presence of two finite linear orders, if there is a successor and its transitive closure over one linear order, and a successor over another linear order, it is decidable, and as hard as reachability of VAS according to the report [14]. If there are only two successors, it is known to be NExpTime-hard. Indeed, it is already NExpTime-hard even when no binary relations are present [4]. Here, we show that it is indeed NExpTime-complete. In fact, it sits in the same complexity class as with just one successor relation on a linear order.
2 Preliminaries
Let , , and for every , , . Given a function and a set , by we denote restricted to the elements of , and by we denote the function where and for all . We write to denote , where is the identity function, and to denote . For any number , we denote by its absolute value. We write to denote the number of elements of a set . Given a string , we write to denote the length of , to denote the subword of restricted to positions , and to denote , for any .
2.1 Permutations
First-order structures with elements and two linear orders can be naturally represented as a permutation on with valuations.444We do not claim that we are the first to use this encoding, it may have been used before. This representation will prove useful in the proofs that follow. A permutation of is represented as a set so that for every , has exactly one pair with in the first component, and exactly one pair with in the second component. We will normally use the symbols to denote elements of a permutation.
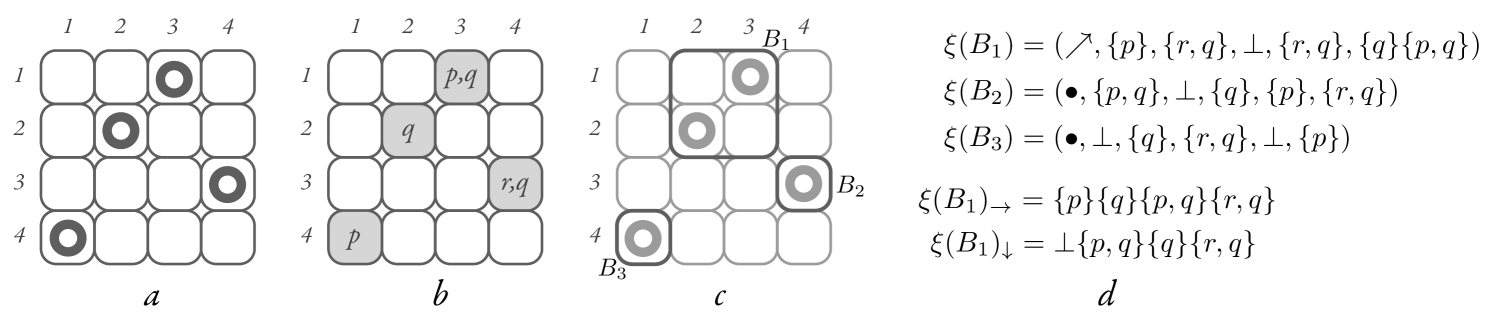
Formally, given , we say that is an n-permutation if for every we have . We say that is a permutation if it is an -permutation for some . Given a permutation and we say that the neighborhood type of in is an element so that: iff , iff , iff , iff , and iff . We denote it with . Figure 1- contains a graphical representation of a -permutation, where , , .
Let us fix to be an enumerable set of propositional letters. A valued permutation is a pair consisting of a permutation and a function that assigns a set of propositional letters to each element of . We say that is the valuation of in . Since for every [resp. for every ] there is only one [resp. only one ] such that we use the notation [resp. ] to denote for the only [resp. only ] such that . For example, the valued permutation of Figure 1- is such that . A valued permutation can be seen as a finite first-order structure with two linear orders, where the permutation element represents the -th element in the first linear order, and the -th element in the second linear order, and its valuation is . Likewise, any finite first-order structure with two linear orders can be represented by a valued permutation.
For convenience in our proofs, we also represent an -permutations with any set with , such that for every , . In this case we say that is a permutation over . Note that for every -permutation over there is an -permutation and a bijection that preserves the order of the elements: for all , , we have that iff and iff . For any we define .
Valued permutations represent, precisely, first-order finite structures with two linear orders. We define then the semantics of over valued permutations.
2.2 with two linear orders
We define on finite structures with the induced successor relations of two finite linear orders, that we denote by . The atoms of are: , , and , for every and every propositional letter . If are formulas of , so are , , , , , where . For any , let be the set of all propositional variables occurring in .
Semantics
We define on valued permutations. The semantics are as expected, we give only some cases to fix notation. Here, is a valued permutation and is a partial function .
| if for some we have | ||||
| if for some we | ||||
| have , | ||||
| if for some we | ||||
| have , | ||||
For any closed formula , we define if , where . In this case we say that satisfies . For example, the valued permutation of Figure 1- satisfies the formula . The satisfiability problem for is then, given a closed formula , whether for some .
Scott normal form
Any formula can be converted into a satisfiability equivalent formula in Scott normal form, which is of the form
where and all the ’s are quantifier-free formulas of . The resulting formula is linear in terms of the size of the original formula. Further, this reduction is polynomial-time (see, e.g., [6]). Henceforward we assume that all the formulas we work with are in Scott normal form, unless otherwise stated.
3 Results
Theorem 1.
The satisfiability problem for is NExpTime-complete.
As an immediate corollary we have that the same bound holds for , where stands for formulas of prefixed by existential quantification over sets of permutation elements.
Corollary 1.
The satisfiability problem for is NExpTime-complete.
Proof sketch
First, in Section 4 we show a property of the blocks of a valued permutation. A block of a permutation can be seen as a set of positions (or ) of the permutation.555A similar notion of block is also used in [14]. We prove that if a formula is satisfiable, then it is satisfiable in a valued model where every block is of size bounded exponentially in the size of . Moreover, the number of different types of blocks that can appear in the valued permutation is also bounded exponentially in the size of .
Second, in Section 5 we show a combinatorial proposition. This involves what we call -permutation constraints, which are sets of positions of where a permutation satisfying this constraint is not allowed to have an element. We give a sufficient condition on how large must be to ensure that there exists a permutation satisfying any constraint with a certain property—namely that it has at most 4 elements in any row or column.
Finally, in Section 6 we introduce a problem called the Restricted Labeled Permutation problem (RLP), which we show to be decidable in NP using the result of Section 5. We then show that satisfiability for can be reduced in NExpTime to the RLP problem, by using the results on the size of the blocks of Section 4. Thus, decidability of the satisfiability problem for follows, with a tight upper bound of NExpTime.
4 Few and small blocks properties
Definition 1 (Block).
Given an -permutation we say that is a block of if for some so that , and either
-
•
, and in this case we say that has type ‘’, or, otherwise,
-
•
for every , we have , and in this case we say that has type ‘’, or
-
•
for every , we have , and in this case we say that has type ‘’.
We say that is the size of the block . A block is maximal if there is no block of with . Figure 1- shows the three maximal blocks of a permutation, one with type and two with type .
Proposition 1.
Any minimal valued permutation satisfying is such that every block is of size at most exponential in .
In fact, note that on blocks is basically like (first order logic with a successor relation on a linear order), where we have the exponential length model property [4]. However, note that a block is within a context of other blocks, and special care must be taken in order to preserve all the elements that may be needed outside the block.
Definition 2 (Fingerprint).
Given a maximal block of a valued permutation , we define , where
-
•
is the type of ,
-
•
if it exists, or otherwise; if it exists, or otherwise,
-
•
if it exists, or otherwise; if it exists, or otherwise,
-
•
for all .
is the fingerprint of , and is the type of (notation: , where ). For , we also define ; and if , or otherwise. The set of fingerprints of a valued permutation is the set of the fingerprints of all its maximal blocks. Figure 1- contains an example of the fingerprints of a valued permutation.
Proposition 2.
If is satisfiable, then it is satisfiable in a minimal model with at most an exponential number of fingerprints.
By Propositions 1 and 2, we can restrict our attention to permutations with labels, over the exponential alphabet of fingerprints of maximal blocks. However, to do this we need restrict the possible permutations. For example, there cannot be two elements in the permutation where both its labels contain fingeprints with type . Indeed, this would imply that the blocks to which these fingerprint correspond were not actually maximal. This suggests that we need to deal with some sort of constraints defining valid permutations. This is the theme of the following section.
5 Permutations under constraints
We define constraints that restrict where permutations may or may not contain elements. A constraint specify some positions in which a permutation satisfying it is not allowed to have an element. More precisely, a constraint contains not more than forbidden positions in an -permutation.
Definition 3 (-constraint).
Given , and with , we say that is a -constraint over if for every we have and . An -permutation over satisfies a -constraint over if . If we say that is just a -constraint.
Remark 1.
As with the permutations, any -permutation over satisfying a -constraint can be equivalently seen as a -permutation satisfying a -constraint and vice-versa.
Proposition 3.
For every -constraint with , there is an -permutation satisfying .
Proof.
This can be shown by a simple application of Hall’s Marriage Theorem [7] (see also [3, p.36]). Remember that Hall’s theorem—in its finite, graph theoretic formulation—states that for any bipartite graph with bipartite sets and of equal size, has a perfect matching if, and only if, every subset verifies . In the formulation, is the neighbourhood of in (i.e., the set of vertices adjacent to some vertex of ).
Let be a constraint where . Consider a bipartite graph , where , . Vertices from represent rows and vertices from represent a columns. The set of edges is defined as all pairs so that (i.e., they represent permutation positions that do not interefere any constraint). Hence, there is a perfect matching between and if, and only if, there is an -permutation satisfying . To prove that there is such a matching, by Halls’ theorem it suffices to verify for every . We show this by case distinction.
-
•
Suppose first . Note that every vertex of has at least edges because there are only constraints in . Then, has vertices because every single vertex in has already edges.
-
•
Suppose now . Since , we have . Then, every vertex from already has one neighbor in , as every vertex from has at least neighbors.
Hence, there is a perfect matching, and thus there exists a permutation satisfying . ∎
We then have the following corollary.
Corollary 2.
For every -constraint with , there is an -permutation that satisfies .
6 Labeled permutations
In this section we prove the NExpTime upper bound of the satisfiability problem for , using the developments of the two previous sections. The idea is to guess the (exponentially many) blocks (of exponential size) of a minimal model that satisfies , and use them as letters of our alphabet. Using this guessing, we reduce the satisfiability problem into a problem we introduce next, the Restricted Labeled Permutation problem (RLP).
6.1 Restricted labeled permutation problem
Definition 4.
A labeled permutation over a (finite) alphabet is a pair where is a permutation and . Note that is nothing else than a valued permutation where exactly one propositional variable holds at any position.
Definition 5 (, ).
Given a labeled -permutation we define and as follows: and , where .
Definition 6.
A label restriction over an alphabet is a triple , where and . We say that a labeled permutation satisfies if for every such that , we have . We say that satisfies a set of label restrictions if it satisfies all of its members.
We define the main problem of this section. Using the result of Section 5 on permutations under constraints, we show that this problem is in NP.
| Problem: | The Restricted Labeled Permutation |
|---|---|
| problem (RLP) | |
| Input: | A finite alphabet , |
| a set of label restrictions , and | |
| two regular languages | |
| (given as NFA). | |
| Question: | Is there a labeled permutation |
| satisfying such that | |
| and ? |
Proposition 4.
The RLP problem is in NP.
Proof.
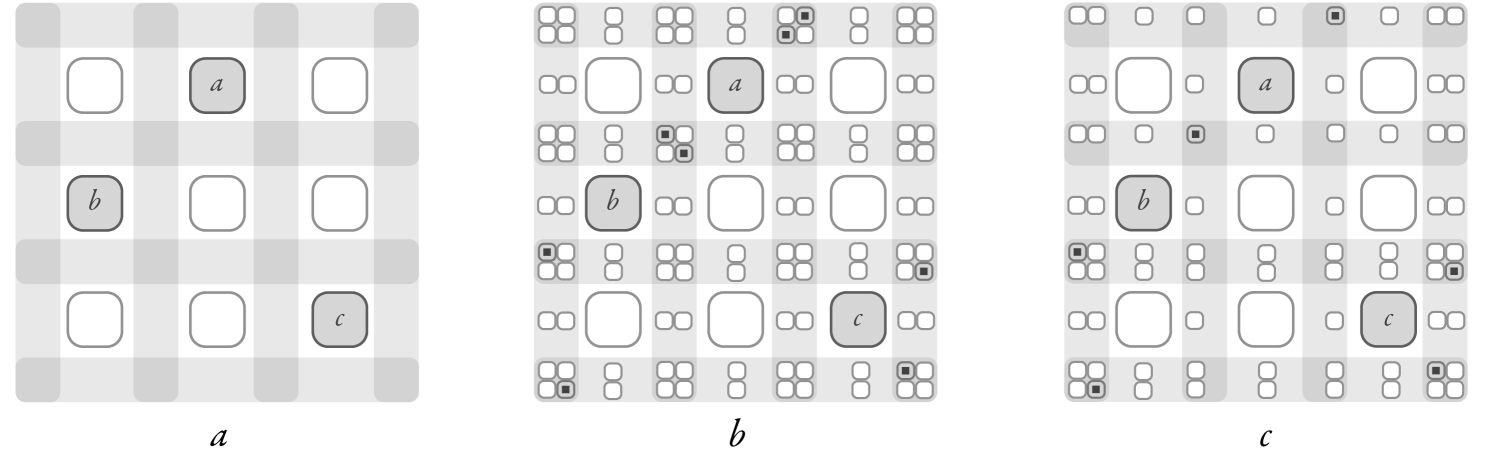
 ) where the label (depicted as
) where the label (depicted as  ) can appear. Here, .
) can appear. Here, .Let be two NFA over the alphabet corresponding to the regular languages respectively. Let be a set of restrictions.
The algorithm first guesses some properties of the labeled permutation that satisfies and is such that and . (We cannot simply guess because it may be too big.) For each letter we guess if it appears exactly times in for some , or if it appears more than times. Let be this guessing; and let us define and .
Let us call zone to any set for . Next, we guess a small labeled permutation over the alphabet . This labeled permutation is such that:
-
1.
All the letters in appear exactly times.
-
2.
There is no zone so that
-
•
has at least two elements, and
-
•
for all .
-
•
-
3.
satisfies the restrictions .
Claim 1.
All possible satisfying the conditions above are labeled permutations of size polynomially bounded by .
Proof.
Note that, once we fix , there are not more than different zones containing only labels, that cover all positions where the label can occur in . These are the zones defined in between the elements of . Then, there cannot be more than elements with label , since otherwise there would be at least one zone with more than one element, contradicting condition (2). Since , the claim follows. For example, Figure 2- depicts the possible zones where the label can appear as the dark gray areas. In Figure 2- we see that there is one zone (in fact, two) that contains more than one element , and therefore condition (2) is falsified (for instance, when ). Finally, Figure 2- shows a labeled permutation satisfying condition (2). ∎
Let be an NFA over that accepts all words such that every appears more than 17 times in . Let [resp. ] be the regular expression resulting from replacing every appearance of in [resp. in ] with the expression . Notice that, for every , any word of is such that the number of appearances of in is exactly , and every other letter appears more than 17 times. Let denote the NFA corresponding to , for every . Observe that , and can be built in polynomial time. Given a language , let denote the Parikh image of . We finally check whether
This can be verified in NP by computing the existential Presburger formulas for both automata in polynomial time [18] and checking for emptiness of its intersection in NP [16].
Claim 2.
if, and only if, there is a labeled permutation that satisfies , such that and .
The rest of the proof is dedicated to prove the statement above.
If , we show that there is a labeled permutation that satisfies and such that and .
Let , such that , and let . For every , let be defined as all such that or (i.e., is the set of possible permutation elements labeled with ). For any , let .
We define the labeled permutation as all the elements such that
-
•
, , and
-
•
[resp. ] is , where
-
–
is the number of occurrences of letters from in [resp. in ] before the -th [resp. -th] appearance of a letter from , and
-
–
is the number of letters in [resp. in ].
Note that .
-
–
We define . We have that is a labeled permutation over satisfying , as satisfies by (3). In fact, it is equivalent to when restricted to elements with labels in (cf. Figures 3-, 3-).
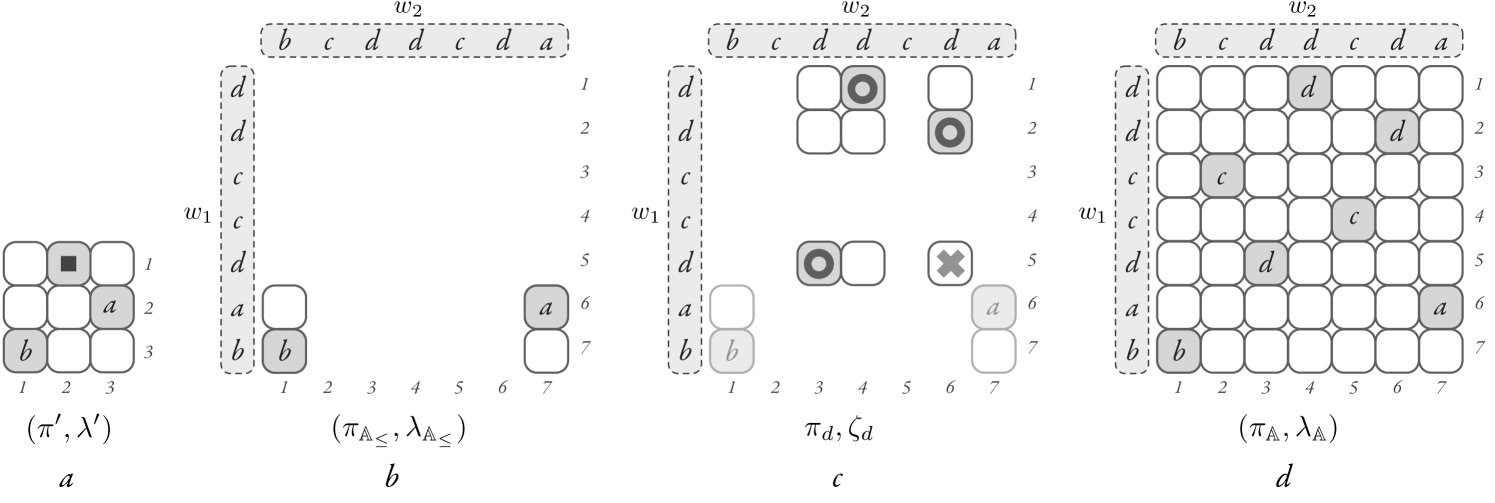
We build, for every , a labeled permutation over satisfying , so that [resp. ] is [resp. ] projected onto . Note that when , is the labeled permutation over we are looking for. We build these inductively.
The base case is when and we then have , which clearly satisfies . Suppose now we have constructed for some , and let be such that . Let be the set of all such that there is some with . Using Corollary 2 one can show that there is always a permutation over satisfying , so that it does not have any two elements one next to the other. In the example of Figure 3, we see in item an illustration of a possible such permutation over , and the constraints originating in this case from .)
Claim 3.
There is a permutation over satisfying the constraints such that there are no two with .
Proof.
We first partition into two sets , so that there are no two elements in (resp. ) with neighboring rows or columns. Let be the set of all such that and are odd; and let be the set of all such that and are even. Since , we have that and . Note that does not have more than restrictions on each row and on each column. Then, is an -constraint with . Hence, by Corollary 2, there exists a permutation over that satisfies . Now let be the set of all such that there is some where . Notice that . Remember that and note that does not have more than restrictions on each row and on each column. Then, applying again Corollary 2, there is a permutation over that satisfies . By definition of and we have that is a permutation over that satisfies both and . Further, since , we have that satisfies . Also, by definition of , we further have that there are no two with . ∎
We therefore define the new permutation ; and for all , and otherwise. Note that it satisfies since for all new positions added there is no other position such that .
Finally, the desired labeled permutation is .
Suppose that ; we show that there is no labeled permutation verifying the restrictions imposed by the problem.
First, we show that there cannot be a solution whose every label appears at most times. By means of contradiction, suppose is such a solution. Then, the algorithm can guess , and we would then have that, by construction, , which is in contradiction of our hypothesis.
Now suppose that is a solution, where is the set of letters that appear more than times in . Let be the replacement in of every label from with . We can now build from , by replacing each block containing only elements (and is maximal in size with respect to this property) with only one element . For example, if is as depicted in Figure 2-, we produce by removing two rows and two columns, ending up with the labeled permutation of Figure 2-.
Let be defined as before from . It is clear that is in and in . It is therefore true that and . Since is a labeled permutation we have that . Then, , which is in contradiction with our hypothesis. Therefore, if , there cannot be a solution to the RLP instance. ∎
6.2 Satisfiability for
We now show that there is a NExpTime reduction from the satisfiability problem for into the RLP problem. This, combined with the fact that RLP is in NP (Proposition 4), concludes the proof of Theorem 1, showing that the satisfiability problem for is in NExpTime; hence it is NExpTime-complete [4].
Before going into the reduction, we show that the satisfaction of a formula in a valued permutation depends solely on its sets of fingerprints, plus some summary information. This summary information says, for every possible valuation , how many times appears in (counting up to a threshold of 3). In the reduction from into RLP we guess the summary information and set of fingerprints of a minimal model (bounded by Propositions 1 and 2), translating the formula into a RLP instance.
Definition 7.
Given a set of fingerprints , let be the set of all the valuations in , that is . Given a set of fingerprints and disjoint sets of valuations , a valued permutation over is any valued permutation such that is the set of fingerprints of , and for every , is the set of valuations that appear exactly times in . We also say that is the summary of .
Given a formula where is a quantifier-free formula, and a valued permutation with a block , whether all the elements from verify or not, depends only on: the summary of , and the fingerprint of . Similarly for formulas . Moreover, we can test this in polynomial time.
We introduce the concept of a fingerprint being consistent with a formula [resp. ] and a summary.666In fact, we do not need the set of fingerprints to define this notion but just the set of valuations , and it is therefore defined over . These are the necessary and sufficient conditions to ensure that every element of a block with such fingerprint in a valued permutation over such summary satisfies [resp. ].
First, note that for any quantifier-free formula of , the validity of only depends on: , and , where: , , and . We will then write , to denote that holds in any model that assigns to , to and so that the neighborhood type between and is . Notice that we can decide in polynomial time. For example, if , we have but .
The formal definition of consistency is given next.
Definition 8.
r Let be a fingerprint, and . Given a set of valuations and three disjoint sets , we say that is consistent with a universal formula and if all of the following conditions hold:
-
1.
For every , we have .
-
2.
If , .
-
3.
If , .
-
4.
For every , if , , , otherwise, if , , .
-
5.
For every ,
-
•
for every then ,
-
•
for every , if for then .
-
•
-
6.
Idem to items 2 and 3, but replacing with , with , and with .
We say that is consistent with an existential formula if for every either
-
1.
-
(a)
,
-
(b)
and and , or
-
(c)
, and ,
-
(a)
-
2.
, and either
-
(a)
and ,
-
(b)
and ,
-
(c)
and there is some , such that , or
-
(d)
and there is with for such that ,
-
(a)
-
3.
, and some condition as the ones in item 2 holds, where and are replaced with and , or
-
4.
Idem as condition , replacing with , with , and with .
Finally, we say that a fingerprint is consistent with a formula in Scott normal form and sets if it is consistent with and with for all .
The following Lemmas follow straightforward from the previous definitions.
Lemma 1.
For every valued permutation over , with a maximal block , and for every formula where is quantifier-free, we have that all the elements from verify if and only if is consistent with and .
Lemma 2.
For every valued permutation over , with a maximal block , for every formula where is quantifier-free, we have that all the elements from verify if and only if is consistent with and .
Remark 2.
Note that the property of consistency of Definition 8 can be checked in polynomial time.
Lemma 3.
There is a NExpTime reduction from the satisfiability problem for into the RLP problem.
Proof.
Let be in Scott normal form, . By Proposition 2, there are at most an exponential number of different fingerprints, and by Proposition 1 each one of them is at most of exponential size. The algorithm guesses the set of all fingerprints needed in a minimal valued permutation that satisfies , and summary sets . The algorithm checks that for every , is consistent with and .
We define the language [resp. ] of all words such that
-
•
the first element of [resp. of ] is , and the last element of [resp. of ] is ,
-
•
for every such that [resp. ] and [resp. ] we have ,
-
•
all the elements of appear in ,
-
•
for every , is the set of valuations that appear exactly times in , where and for .
It is immediate that and are regular languages, and that they can be defined by two NFA that can be built in polynomial time in the size of .
Finally, we define the label restrictions, avoiding having two blocks that actually define a bigger block (because these blocks are supposed to be maximal). Let be the set of all triples such that and either
-
•
, , , or
-
•
, , .
We reduced the satisfiability problem into the RLP problem for , concluding the proof.
Claim 4.
The RLP instance has a positive solution iff the formula is satisfiable.∎
7 Conclusion
Our work shows that the following combinatorial problem is at the core of the satisfiability for and of the RLP problem, and is decidable in NP. Given two regular languages , is there a word and a permutation so that and for all ?
A natural question left open is whether this decidability result can be extended to with successor relations over finite linear orders is decidable, for arbitrary (or at least for ).
References
- [1] Mikołaj Bojańczyk, Claire David, Anca Muscholl, Thomas Schwentick, and Luc Segoufin. Two-variable logic on data words. ACM Trans. Comput. Log., 2010.
- [2] Mikołaj Bojańczyk, Anca Muscholl, Thomas Schwentick, and Luc Segoufin. Two-variable logic on data trees and XML reasoning. Journal of the ACM, 56(3):1–48, 2009.
- [3] Reinhard Diestel. Graph Theory, volume 173 of Graduate Texts in Mathematics. Springer-Verlag, Heidelberg, third edition, 2005.
- [4] Kousha Etessami, Moshe Y. Vardi, and Thomas Wilke. First-order logic with two variables and unary temporal logic. Inf. Comput., 179(2):279–295, 2002.
- [5] Erich Grädel, Phokion G. Kolaitis, and Moshe Y. Vardi. On the decision problem for two-variable first-order logic. Bulletin of Symbolic Logic, 3(1):53–69, 1997.
- [6] Erich Grädel and Martin Otto. On logics with two variables. Theoretical Computer Science, 224(1-2):73–113, 1999.
- [7] Philip Hall. On representatives of subsets. Journal of the London Mathematical Society, 10:26–30, 1935.
- [8] Emanuel Kieroński. Results on the guarded fragment with equivalence or transitive relations. In CSL, volume 3634 of Lecture Notes in Computer Science, pages 309–324. Springer, 2005.
- [9] Emanuel Kieroński. Decidability issues for two-variable logics with several linear orders. In EACSL Annual Conference on Computer Science Logic (CSL’11), volume 12 of Leibniz International Proceedings in Informatics (LIPIcs), pages 337–351. Schloss Dagstuhl, 2011.
- [10] Emanuel Kieroński and Martin Otto. Small substructures and decidability issues for first-order logic with two variables. In LICS, pages 448–457. IEEE Computer Society, 2005.
- [11] Emanuel Kieroński and Lidia Tendera. On finite satisfiability of two-variable first-order logic with equivalence relations. In LICS, pages 123–132. IEEE Computer Society, 2009.
- [12] Amaldev Manuel. Two orders and two variables. In Int. Symp. on Mathematical Foundations of Comp. Sci. (MFCS’10), Lecture Notes in Computer Science. Springer, 2010.
- [13] Amaldev Manuel. Personal communication, 2012.
- [14] Amaldev Manuel and Thomas Zeume. Two-variable logic with a linear successor and a preorder. Unpublished manuscript available at http://www.imsc.res.in/~amal/manuelzeume.pdf, 2011.
- [15] Michael Mortimer. On languages with two variables. Mathematical Logic Quarterly, 21:135–140, 1975.
- [16] Christos H. Papadimitriou. On the complexity of integer programming. Journal of the ACM, 28(4):765–768, 1981.
- [17] Thomas Schwentick and Thomas Zeume. Two-variable logic with two order relations. Logical Methods in Computer Science, 8(1:15):1–27, 2012.
- [18] Kumar Neeraj Verma, Helmut Seidl, and Thomas Schwentick. On the complexity of equational horn clauses. In International Conference on Automated Deduction (CADE’05), volume 3632 of Lecture Notes in Computer Science, pages 337–352. Springer, 2005.
Appendix A Missing proofs
Proof of Lemma 1.
[] Suppose that every element verifies . We show that is consistent with and .
If is the smallest column element of and , it means that , in fact . Since for some , , and since is maximal, we have that and hence that . As and , condition 2 is met. Condition 3 is similar.
Suppose and . This means that there are with , . Since and we have that and . Hence, and and thus condition 4 holds. The proof for is similar.
Suppose now that . Let . This means that there is some with and some with , . Since , we have that and hence the first part of condition 5 is met. On the other hand, if and for , this means that there must be necessarily some other position with valuation . That is, there is some with , . Then, the same reasoning as before applies to show that the second part of condition 5 is met.
[] Suppose that is consistent with and . Let us show that every element verifies .
Proof of Lemma 2.
[] Suppose that every element verifies . We show that is consistent with and .
Let , then there must be such that . If then condition 1a is met. If , then condition 1b is met. If , then condition 1c is met. If , then condition 2a is met. If , then condition 2b is met. If , then either condition 2c or 2d is met. If , then condition 3 is met. If , then condition 4 is met. Thus, is consistent with and .
[] Suppose that is consistent with and . Let us show that every element verifies .
Let . There must be some such that . If condition 1a holds, then . If condition 1b holds, then for some with . If condition 1c holds, then for some with . If condition 2a holds, then for . If condition 2b holds, then for . If condition 2c or 2d holds, then for some with . A similar reasoning applies if 3 or 4 hold. ∎
Proof of Proposition 1.
We show the following statement: Any minimal valued permutation satisfying is such that every block is of size less or equal to
Let be a minimal valued permutation such that . Without loss of generality assume .
Suppose, by means of contradiction, that is a block of of size . Let us assume that is of type (if it has type a symmetrical reasoning applies). For every , choose any three elements from , or, if there are less than three, all the elements; let be the set of these three (or less) elements. Now consider all the sub-blocks defined strictly between elements of , that is, such that , consider the ones that are maximal with respect to inclusion. Since , there are at most such sub-blocks having a total of at least elements. By the Pigeonhole Principle, since , this means that there must be a sub-block with at least elements; suppose it is
where and . There must be two distinct elements with
| () | ||||
Without any loss of generality, suppose that and (the same argument works if and ). Let . It is easy to verify that , where .
Claim 5.
Proof.
Let . For any such that and , we can find such that and such that . This is because, if the neighborhood type is not then it is taken care of by ( ‣ A). Otherwise, it is witnessed by one of the elements from , for . Therefore, verifies for every .
On the other hand, if where , we have that, if , then . Otherwise, we necessarily have that , (or vice-versa). But since and , then , because . ∎
Since is smaller than , and verifies , it cannot be that is minimal in size, which is in contradiction with our hypothesis. Therefore, does not have blocks of size bigger than . ∎
Proof of Proposition 2.
Let be such that is minimal in size. Without any loss of generality we assume that . We show how to build another minimal valued permutation from with a number block fingerprints that is bounded by an exponential function on .
Let , where each is a maximal block. We are going to mark some blocks (only exponentially many), and use only these to build a new valued permutation satisfying . For each , let be a set of 4 elements of —if the set has less than 4 elements, then let be all of them. For every and every , mark the block such that with a color red. It follows that we end up with at most blocks marked with red. On the other hand, for every , let us define , where . For each let us mark with color green one block such that and such that is not marked red. Since there are no more than different ’s, there are only an exponential number of blocks marked with colors red or green.
Now, let be a block with a fingerprint different from all the fingerprints of the marked blocks. There must be a block marked with green, so that . Let be the result of replacing of with in , in the expected way. We then have that .
Claim 6.
.
Proof.
Let .
We first show that holds in . Let .
-
•
If is in the edited block of the permutation (i.e., in the new copy of the fingerprint of ).
-
–
If , then both elements are described inside the fingerprint . Hence, there are two elements in the block of with the same neighborhood type and with the same valuations. Since for those two we have that holds, then it holds for as well. Hence, .
-
–
Otherwise, suppose . Note that in the red colored blocks of there must be at least 4 elements with value . By the same reason there must be 4 elements with value . Since marked blocks are preserved, there must be such that , and , . Since , we have .
-
–
-
•
If both and are in the part that was not modified, then there must clearly be with , so that , . Hence, .
We now show that for every and , holds.
-
•
If is in the edited block of the permutation (i.e., in the new copy of the fingerprint of ), then there must be some in such that . Since , there must be some such that .
-
–
If , then it is described in the fingerprint of and therefore there must be some such that , and , . Then, since .
-
–
Otherwise, suppose that . There must be 4 elements of with the same value inside blocks marked red. Then, there must be a block marked red in containing some with and such that . Then, since .
-
–
-
•
If is in the part that was not modified, then there is some with and . Since , there must be some such that .
-
–
If , then is described in the fingerprint of the block where belongs. Since this fingerprint is preserved (because it is not ), there must be some with and such that . Then, .
-
–
Otherwise, if , there must be 4 other positions with the same value as in , in blocks marked red. Then, there must necessarily be some such that and such that . Then, .
-
–
Therefore, . ∎
Note that since and have the same type, then the number of maximal blocks in is the same as in , and moreover the number of maximal blocks with fingerprints different from the marked fingerprints is decremented by one. Note that in particular this means that . Otherwise, if , we would have that is smaller than which cannot be since is minimal in size. Conversely, if , we could have marked with green instead of and we arrive to the same contradiction.
We can repeat this operation with all the unmarked blocks ending up with a valued permutation whose every block has the fingerprint of a marked block. Since there are only exponentially many marked blocks, there are exponentially many fingerprints. ∎