Secrecy Analysis for MISO Broadcast Systems with Regularized Zero-Forcing Precoding
Abstract
As an effective way to enhance the physical layer security (PLS) for the broadcast channel (BC), regularized zero-forcing (RZF) precoding has attracted much attention. However, the reliability performance, i.e., secrecy outage probability (SOP), of RZF is not well investigated in the literature. In this paper, we characterize the secrecy performance of RZF precoding in the large multiple-input single-output (MISO) broadcast system. For this purpose, we first consider a central limit theorem (CLT) for the joint distribution of the users’ signal-to-interference-plus-noise ratio (SINR) and the eavesdropper’s (Eve’s) signal-to-noise ratio (ESNR) by leveraging random matrix theory (RMT). The result is then utilized to obtain a closed-form approximation for the ergodic secrecy rate (ESR) and SOP of three typical scenarios: the case with only external Eves, the case with only internal Eves, and that with both. The derived results are then used to evaluate the percentage of users in secrecy outage and the required number of transmit antennas to achieve a positive secrecy rate. It is shown that, with equally-capable Eves, the secrecy loss caused by external Eves is higher than that caused by internal Eves. Numerical simulations validate the accuracy of the theoretical results.
Index Terms:
Physical layer security (PLS), regularized zero-forcing (RZF) precoding, multiple-input single-output (MISO), central limit theorem (CLT), random matrix theory (RMT).I Introduction
A pivotal problem for wireless communications is eavesdropping due to the broadcast nature of wireless channels [1, 2]. To ensure security, traditional network-layer key-based cryptography has been widely used. However, the dynamics of wireless environments, e.g., fading, lead to issues in key distribution and management, and cause high computational complexity [3]. To provide additional security enhancements, physical layer security (PLS) [4], which utilizes the randomness of the noise and dynamics of the fading channel to limit information leakage to potential eavesdroppers, has been considered as an appealing low-complexity alternative [5].
PLS has become an active area of research, especially in the broadcast channel (BC), where the transmitter tries to broadcast messages to users, with minimum leakage to the eavesdroppers. To this end, linear precoding schemes have been used in confidential transmission of multiple antenna systems due to its simple implementation and effectiveness in interference controlling [6, 7, 8]. In [9, 3], the authors utilized regularized zero-forcing (RZF) precoding, also referred to as regularized channel inversion (RCI), to mitigate the signal leaked to the undesired users and maximize the secrecy sum rate. Despite the wide usage of RZF, its performance analysis is still in the infant stage. Existing works on RZF in MISO BC can be categorized into two types according to the nature of the eavesdroppers, referred to as Eves.
1. Internal Eve: In a MISO BC, users can act maliciously as Eves for other users [10, 11]. Given the Eves are within the BC system, we refer to this scenario as the internal Eve case. Under such circumstances, for a given user, other users are regarded as single-antenna Eves. In [9, 3], the secrecy sum rate of the MISO BC system with internal Eves over independent and identically distributed (i.i.d.) channels was given in closed form by large random matrix theory (RMT). Considering the unequal path loss and correlations of the transmit antennas, the authors of [12] evaluated the secrecy sum rate of RZF using RMT.
2. External Eve: In a practical scenario, external devices can also act as Eves, which are referred to as external Eves. The major difference between internal and external Eves is that the channels of internal Eves are typically correlated with those of the users while the channels of external Eves are typically independent of the users. The impact of external Eves on the secure connectivity was investigated by stochastic geometry (SG) [13, 14, 15]. In [16], assuming that the locations of the Eves are distributed as a Poisson point process (PPP), the authors derived the sum rate and the secrecy outage probability (SOP) with RZF over uncorrelated MISO channels by utilizing RMT and SG. In [17], assuming both users’ and Eves’ locations are distributed as a PPP, the authors derived approximate closed-form results for the SOP and ergodic secrecy rate (ESR) with RZF precoding over uncorrelated MISO channels.
Most existing works focus on the secrecy sum rate of the system [16, 3, 12]. However, the secure reliability performance, i.e., SOP, is not well studied. In [17], the SOP of RZF precoding was derived by SG, considering only large-scale fading, where the impact of small-scale fading on the SOP is ignored. Although the SG based approach is powerful in modeling the dynamics of the network and performing coverage analysis [18], it may not be able to capture long-term behavior of the system where one BS serves a fixed group of users. In this case, the large-scale fading is deterministic and thus the PPP model is not suitable. In particular, the PPP model will dominate the performance analysis such that the impact of small-scale fading can not be fully understood. In this paper, we focus on the impact of small-scale fading on the secrecy performance of MISO BC with RZF precoding and derive the SOP, which is not available in the literature.
A closed-form expression for the SOP is essential for the performance evaluation and will be very beneficial for system design. However, characterization of the secrecy performance, especially the SOP, turns out to be a difficult problem due to the fractional structure of the signal-to-interference-plus-noise ratio (SINR) and the power normalization factor of RZF. In particular, these challenges make it extremely difficult to obtain the closed-form results for the joint distribution of the users’ SINR and Eve’s signal-to-noise ratio (ESNR) in finite dimensions. To overcome this difficulty, asymptotic RMT will be adopted to derive the asymptotic distribution of the SINRs and ESNRs by assuming that the number of transmit antennas, the number of users, and the number of Eves go to infinity with the same pace. In fact, asymptotic RMT has been widely used in large-system analysis of multiple-antenna systems to obtain strikingly simple results [19, 20, 21], which are shown to be effective even for small dimensions.
The contributions of this paper are summarized as follows:
1. We consider a CLT for the joint distribution of the SINRs and ESNRs of a finite number of users and derive explicit expressions for the asymptotic mean and variance. Specifically, we utilize the CLT for the quadratic form and compute the asymptotic second-order attributes by Gaussian tools [20, 22]. The derived results can be extended to the case with imperfect CSI and the analysis of the channel-inversion based precoding method, e.g., secure RZF [23].
2. Based on the CLT, we derive closed-form approximations for the SOP of RZF precoding including three scenarios, namely the External-Eve-Only, Internal-Eve-Only, and External+Internal-Eve cases.
3. The derived results are then used to evaluate how many transmit antennas are needed to guarantee a positive secrecy rate and to estimate the percentage of users in outage. We further compare the performance of RZF for the Internal-Eve-Only and External-Eve-Only cases and derive the theoretical gap between the two secrecy rates, which indicates that the external Eves incur more information leakage than internal ones. Numerical results validate the accuracy of the theoretical results.
The rest of this paper is organized as follows. In Section II, the system model is introduced and the problem is formulated. In Section III, some preliminary results on RMT, which are critical for the derivations in this paper, are given. In Section IV, a CLT for the joint distribution of SINRs and ESNRs and the approximation for the SOP are derived. The derived results are used in Section V to evaluate the percentage of users in outage and the required number of antennas for a positive secrecy rate. Simulation results are provided in Section VI. Section VII concludes the paper.
Notations: Bold, upper case letters and bold, lower case letters represent matrices and vectors, respectively. The probability operator and expectation operator are denoted by and , respectively. The circularly complex Gaussian distribution and real Gaussian distribution are denoted by and , respectively. The -dimensional complex vector space and real vector space are represented and , respectively. The -by- complex and real matrix space, are represented by and , respectively. The centered version of the random variable is denoted by . denotes the Hermitian transpose of and or denotes the -th entry. The conjugate of a complex number is represented by . The spectral norm of is given by . is the trace of , is the by identity matrix, and represents the cumulative distribution function (CDF) of the standard Gaussian distribution. Almost sure convergence, convergence in probability, and convergence in distribution, are represented by , , and , respectively. The set is denoted by and represents the indicator function.
II System Model and Problem Formulation
II-A System Model
We consider the downlink MISO system, where single-antenna users are served by a base station (BS) with transmit antennas. We assume that perfect channel state information (CSI) of users is available at the BS and RZF is adopted to suppress information leakage.
RZF is a linear precoding scheme proposed to serve multiple users in the MISO downlink channel, which often demonstrates better performance than ZF, especially with low SNR [6]. With RZF, the received signal at the -th user is given by
| (1) |
where and denote the transmitted signal for the -th user and the additive white Gaussian noise (AWGN) at the -th user, respectively. Here and represent the channel vector of the -th user and the precoding vector for the -th user, respectively, denotes the power of the -th message and represents the power normalization factor. The precoding matrix of the RZF precoder is given by [6]
| (2) |
where and is the regularization parameter of the RZF precoder. The power normalization factor satisfies , where . The -th user’s SINR is given by
| (3) |
Here we consider single antenna Eves. The channel vector between the BS and the -th Eve is denoted by , . The received signal of the -th Eve, , is given by
| (4) |
where represents the AWGN at the -th Eve with denoting the power of the noise.
It is not straightforward to directly characterize the information leakage, i.e., the information received by the undesired users. Here we consider the worst-case scenario, where all Eves are assumed to work together and be able to cancel out the multiuser interference. This model is widely used in secrecy analysis [3, 12, 24]. Under such circumstances, the ESNR for all Eves to collaboratively overhear the message is given by
| (5) |
where . The corresponding information leakage rate is given by . As a result, the secrecy rate of the -th user is
| (6) |
The SOP of the -th user for a given rate requirement is given by
| (7) |
Note that the Eves can be both internal and external. For the cases with only internal Eves, the channel matrix for the Eves with respect to the -th user can be given by , where is obtained by removing from . In this paper, we will evaluate the ESR in (6) and SOP in (7) in a large system setting where the number of transmit antennas and numbers of users and Eves go to infinity with the same space.
II-B Channel Model
We consider a correlated Rayleigh fading channel for users. Accordingly, the channel vector for the -th user can be represented by , where is the large-scale fading (pathloss) from the BS to the -th user, , and denotes the correlation matrix of the BS towards the users. In this paper, we assume a common transmit correlation matrix for different users, which is widely used in [12, 25, 26, 27] for tractability of the problem. With the common correlation matrix, the channel matrix is given by
| (8) |
where and .
Assume that there are external single-antenna Eves and denote the channel vector for the -th Eve as , . Similar to the channel matrix for the users, the channel matrix of the external Eves, , is given by
| (9) |
where and represent the correlation matrix and the large-scale fading for the Eves, respectively. Here is a random matrix with i.i.d. circularly Gaussian entries, i.e., . Notice that the external Eves overhear the message passively. Thus, we can assume that , and , are independent, i.e., and are independent. Due to the same reason, the CSI of the Eves is not available at the BS. If there are only external Eves, we have .
In this paper, we consider three typical scenarios.
The External-Eve-Only case. According to (5), we can obtain the ESNR for overhearing message as
| (10) |
The achievable secrecy rate for the -th user is given by
| (11) |
The Internal-Eve-Only case. In this case, the unintended users within the MISO BC behave maliciously so that the crosstalk among users causes information leakage [12]. For each user, the other users behave as single-antenna Eves. Specifically, users in can cooperate to jointly eavesdrop the message . In the worst case scenario, they can be regarded as a single Eve with antennas. The ESNR for overhearing message is then given by [9, 3]
| (12) |
The achievable secrecy rate for the -th user is given by
| (13) |
In fact, (11) and (13) can be obtained by taking and in (6), respectively.
The External+Internal-Eve case. In this case, both the internal and external Eves exist and they work in a non-colluding mode. The secrecy rate of the -th user is given by [28, 29]
| (14) |
Note that the first two cases are differentiated by whether the channels of the Eves are independent with those of the intended users. The secrecy sum rate of the Intern-Eve-Only case has been investigated in [9, 3, 12] but the SOP is not available in the literature. In the following, we investigate the ESR and SOP for the three cases.
III Preliminaries
In this section, we provide some preliminary results for the evaluation of SINR and ESNR, and introduce the RMT results and notations which will be frequently used in the following derivations. Necessarily, we first introduce the resolvent matrix , which will be extensively used in the following analysis. Further define , where is obtained by removing the -th column from . By utilizing the identity , the SINR for -th user can be rewritten as
| (15) |
where , , and . Here is obtained by removing the -th row and column of . Similarly, and can be rewritten as
| (16) |
and
| (17) |
respectively, where and . The formulation above resorts the investigation of and to that of the , , , and , which can be regarded as the quadratic forms of when is given. We next introduce three assumptions based on which the analysis in this paper is performed.
Assumption A.1. The dimensions , , and go to infinity at the same pace, i.e., when ,
| (18) | ||||
Assumption A.1 indicates the asymptotic regime where the number of transmit antennas, the number of users, and the number of external Eves are in the same order. Assumption A.2 and A.3 eliminate the extremely low-rank case of and , i.e., the ranks of and do not increase with the number of antennas. The bound guarantees the power for each message is finite. We further define two ratios and .
Lemma 1.
Lemma 1 indicates that the normalized trace of the resolvent converges almost surely to its deterministic equivalent, which is a good approximation for the expectation of the trace of the resolvent. The computation of the variances for the SINR and ESNR is highly related to the trace of the resolvent.
We summarize some frequently used notations in Table I, which are all derived from and . In the following analysis, some of the symbols have the subscript . They are derived similarly as those in Table I, but are parameterized by and with
| (22) |
where is obtained by removing the -th row and -th column in , and . These -related quantities are used to approximate the related statistics.
| Symbols | Expression | Symbols | Expression |
|---|---|---|---|
IV Main Results
In this section, we develop theoretical results on the asymptotic distribution of SINR, , and , and then derive the ESR and SOP of the MISO BC.
IV-A First-order Analysis of the SINR, ESNR, and Secrecy Rate
In this part, we derive approximations for the mean of SINR and ESNR, which will be used to obtain the ESR.
IV-A1 SINR and ESNR
According to (15)-(17), an approximation for SINR, , and can be obtained by the continuous mapping theorem [33], where we need to obtain the deterministic equivalents of , , , , and .
By Lemma 1 and [34, Lemma 14.2], we have
| (23) |
and
| (24) | ||||
where and are given in Table I. Here ,
| (25) |
| (26) | ||||
and
| (27) | ||||
We define and its deterministic equivalent is . In fact, we have
| (28) | ||||
which indicates that can be replaced by in the asymptotic regime A.1. To keep a concise expression for the deterministic equivalent, we will use instead of .
IV-A2 Ergodic Secrecy Rate (ESR)
We approximate the ESR (expectation of the secrecy rate) by replacing the instantaneous SINR and ESNR with their deterministic equivalents in (29) [35]. Specifically, we plug (29) into (11) and (13), respectively, to obtain
| (30) | ||||
Note that, the results in this paper are more general than the existing ones, because the spatial correlation at the transmitter and the power allocation scheme are considered. In particular, the above results include the first-order results of previous works [12, Eq. (48)-(50)()], [9, Eq. (31)], and [3, Theorem 1] as special cases, i.e., by taking , , and .
IV-B Second-order Analysis of the SINR, ESNR, and Secrecy Rate
In this part, we investigate the fluctuations of SINR and ESNR to further investigate the distribution of the secrecy rate. The concerned random quantities, i.e., the SINRs and ESNRs, converge almost surely to a constant as shown in Section IV-A1, which means that their variances vanish when grows to infinity. In order to investigate the second-order performance, in this section, we show that and converge to a Gaussian distribution when goes to infinity.
For a finite number , define SINR, , and for users as the vector , given by
In the following, we first derive the joint distribution for the SINRs and ESNRs and then utilize the result to evaluate the SOP.
IV-B1 Joint distribution for SINRs and ESNRs
The following theorem presents the asymptotic joint distribution of .
Theorem 1.
(CLT for the joint distribution of SINRs and ESNRs) For a finite number , the distribution of the vector converges to a Gaussian distribution
| (31) |
where
| (32) | ||||
Here, , , and are given in (29). The covariance matrix is given by
| (33) |
with , , , , , and . The parameters , , , , and are given by
| (34) |
| (35) | ||||
| (36) |
| (37) | ||||
| (38) | ||||
| (39) | ||||
where , , , , and are given by (90) to (94) in Appendix B. Here, , are given in (40) at the top of the next page.
| (40) | ||||
The terms , , , and are the deterministic approximations for , , , and , respectively, which are proved by Lemma 3 in Appendix B.
Theorem 1 indicates that for a finite number of users, i.e., , the joint distribution of the SINRs and ESNRs converges to a joint Gaussian distribution when , , and go to infinity with the same pace. From the structure of the covariance matrix , we observe that the SINRs of different users are asymptotically independent. Similar results can also be obtained for the ESNR. However, and are not independent, and their covariances are characterized by the diagonal entries of . Similarly, the covariance of the pairs and is characterized by the diagonal entries of and , respectively. It follows from Theorem 1 that for a large system, the SINR and ESNR can be approximated by a Gaussian distribution, which will be utilized to evaluate the SOP in the following.
Theorem 1 is obtained by assuming a common correlation matrix as mentioned in Section II-B. When different correlation matrices are assumed, the system of equations in (19) will become a system of equations parameterized by different correlation matrices, i.e., , ,…,[35, Eq. (11)] and there will be different s instead of only one in (19). In this case, the characterization of the higher order trace of resolvents is more complex. For example, will become , where and are determined by , ,…,. The inverse matrix will appear frequently and its order will increase in the computation of high-order resolvents like in (90) to (94). Although the simplified common correlation matrix is considered, Theorem 1 sets up a framework for the second-order analysis of SINRs and ESNRs in the MISO system with RZF, which can also be used to analyze the scenario with imperfect CSI and other channel-inversion based precoding schemes like the secure RZF proposed recently in [23].
IV-B2 SOP Evaluation
Based on Theorem 1, the SOP of the three cases can be obtained by Propositions 1 to 3 as follows, which are not yet available in the literature.
Proposition 1.
(External-Eve-Only) Given a rate threshold , the SOP of user with only external Eves can be approximated by
| (41) |
where .
Proposition 2.
(Internal-Eve-Only) Given a rate threshold , the SOP of user with only internal Eves can be approximated by
| (42) |
where .
Proposition 3.
(External+Internal-Eve) Given a rate threshold , the SOP of user with both external and internal Eves can be approximated by
| (43) | ||||
where , , and , .
V Large System Analysis
In this section, we utilize the derived results in Section IV to analyze the impact of the system dimensions. To achieve this goal, we ignore the correlation, pathloss, and power allocation and consider the i.i.d. channel, i.e., , , , , and . In this case, the subscript used to differentiate users can be removed and the system of equations in (22) degenerate to the quadratic equation , whose positive solution is given by
| (44) |
In addition, , , and represent the first to third derivatives of with respect to . With the setting above, we only need to consider the joint distribution of , and Theorem 1 can be simplified as follows.
Theorem 2.
Given assumption A.1, we have
| (45) |
where is given by
| (46) |
The covariance matrix is given by
| (47) |
| (48) | ||||
The parameters , , are given as
The SINR distribution of the MISO BC with RZF was investigated in [37], where the i.i.d channel and equal power allocation are assumed. If we discard and , the results in Theorem 2 degenerate to [37, Theorem 3]. The outage probability for the i.i.d. case can be obtained by a similar approach as Propositions 1 to 3. In this paper, the joint distribution of SINR and ESNR is investigated with correlated transmit antennas and unequal power allocation.
V-A How many users are in secrecy outage?
Theorem 2 can be utilized to evaluate how many users are in outage. For that purpose, we define the empirical distribution
| (49) |
where can be either External-Eve-Only or Internal-Eve-Only. Here we consider the External-Eve-Only case and the results for the Internal-Eve-Only case can be obtained similarly. The following proposition is an application of Theorem 2 to compute the quantiles of the users in outage.
Proposition 4.
Given assumptions A.1 to A.3, define and as
| (50) | ||||
Then, we have
| (51) | |||
Proof.
The result follow from the law of large numbers and Theorem 2. ∎
Proposition 4 indicates that for large and , given a target secrecy rate and the noise level , , the proportion of the users in outage is approximated by , where is obtained by solving equation (50). This means that almost users are in outage. Given and , is an increasing function of , which indicates that a larger threshold causes more users in outage.
V-B The Secrecy Loss of the External-Eve-Only and Internal-Eve-Only Cases
Next, we investigate the secrecy loss induced by external and internal Eves. To make a fair comparison, we consider the case where the internal and external Eves are equally powerful, i.e., and , and the precoders have the same . Under such circumstances, , which indicates that the information leakage due to external Eves is larger than that due to internal Eves. This is because, with only internal Eves, the information received by other users is mitigated by RZF due to its ability to cancel interference. With external Eves, RZF precoder will not be able to cancel the interference since the channels of Eves are independent of those of the users.
It can also be observed from (46) that is constant when the ratio is a constant. Moreover, does not depend on the regularization parameter , indicating that the optimal regularization parameter for maximizing the secrecy sum rate is equivalent to that without considering the Eves, i.e., . The optimal value of the regularization parameter is [38].
V-C How many transmit antennas do we need to achieve a positive secrecy rate?
For the External-Eve-Only case with the optimal regularization parameter , the inequality must hold true, i.e.,
| (52) |
in order to obtain a positive secrecy rate. From (52), the minimum required for a positive secrecy rate is
| (53) |
This indicates that if , a positive secrecy rate will be guaranteed. The estimation of is accurate in the high SNR regime because only the term is omitted in the relaxation. When , , we can obtain that grows with the order and a larger requires a higher increasing rate of .
VI Numerical Results
In this section, the theoretical results derived in Sections IV and V are validated by numerical results. Specifically, the accuracy of the SOP approximation and the evaluation of the percentage of users in secure outage are validated by Monte-Carlo simulations. The impact of the regularization factor and number of transmit antennas required for a positive secrecy rate are also investigated.
A. Simulation Settings: In the simulation, we consider a uniform linear array of antennas at the BS. According to the model for conventional linear antenna arrays [39], the correlation matrix at the BS can be obtained by
| (54) | ||||
where and represent the indices of antennas. Here, and denote the relative antenna spacing (in wavelengths) and the dimension of the matrix, respectively, and and represent the mean angle and the mean-square angle spreads, whose units are degree. We adopt the setting . In the following simulations, the correlation matrices are generated according to (54), i.e., , with and . Without loss of generality, we consider the first user, i.e., .
Following [12], a simple model for the large-scale fading of different users , is used, with , where represents the distance between the BS and -th user. The path loss exponent is used to model a shadowed urban area [40]. Here we divide the users into groups and users in the same group have a common distance. We choose so that . Similarly, is generated by . The power of each message is given by and the total power is normalized to be . In the following, we use the setting , , , and . In the figures, we use the notations “Ana.” and “Sim.” to represent the theoretical and the simulation results, respectively.
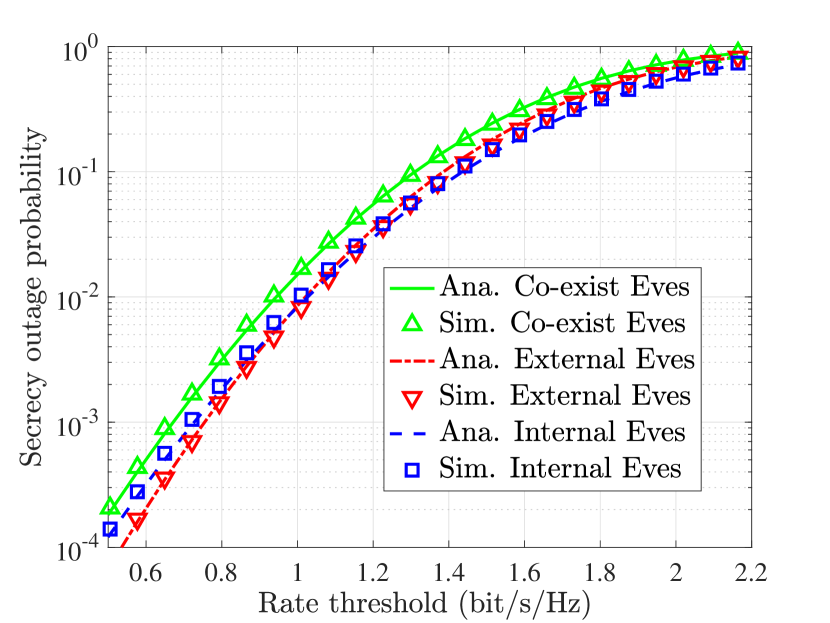
B. The Approximation Accuracy for SOP: In Fig. 1(a), the SOP for three cases are given. The dimensions of the system are set as , , and . The SNRs at the user and external Eves, i.e., and , are dB and dB, respectively. The regularization parameter is set as . The number of the Monte-Carlo realizations is . It can be observed that the approximations for the SOP in Proposition 1 to 3 are accurate. The External+Internal-Eve case has the highest SOP and the gap between the External+Internal-Eve case and the other two represents the performance loss induced by different types of Eves.
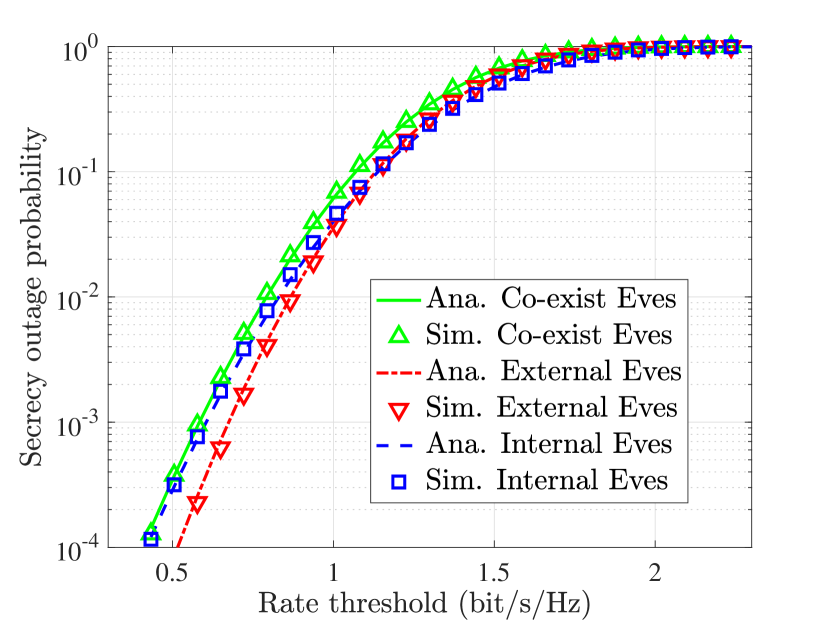
In Fig. 1(b), the SOP of the i.i.d. system is given with the setting , , , dB, and dB. This result validates the accuracy of Theorem 2.
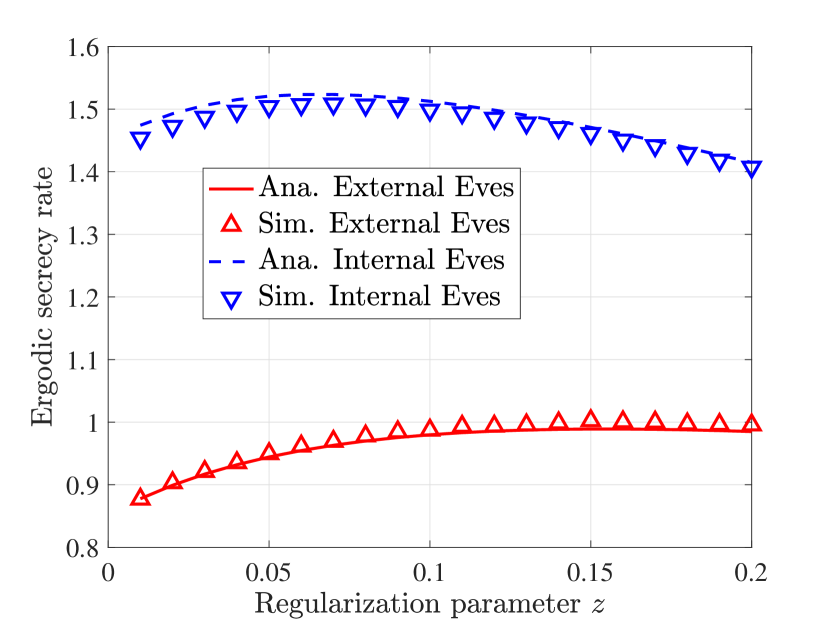
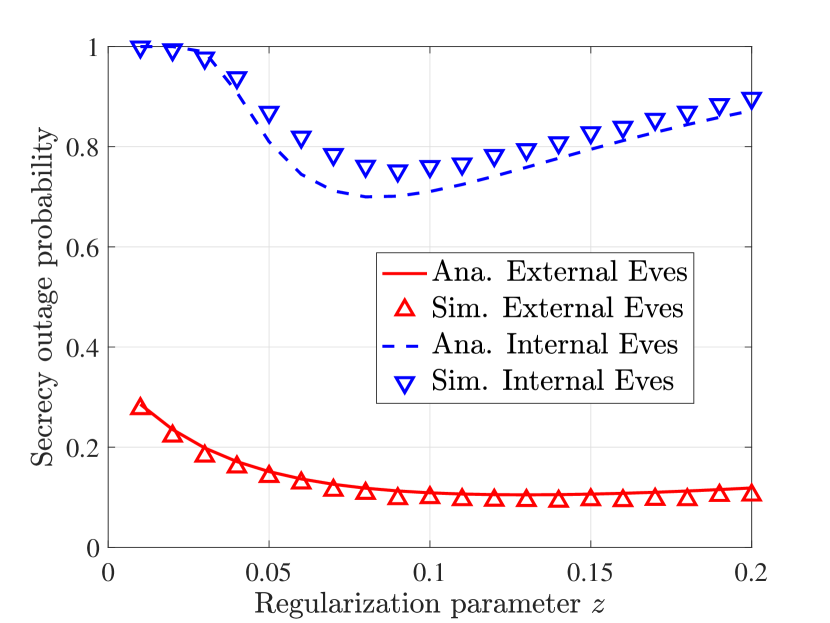
C. Optimal Control: The theoretical results of this paper can be used to investigate the optimal for enhancing secure reliability. Figs. 2(a) and 2(b) investigate the impact of on ESR and SOP for the External-Eve-Only and Internal-Eve-Only case, respectively. Here the i.i.d channel is considered with equal power allocation. The SNR for internal Eves and external Eves are dB and dB, respectively. The rate thresholds for the two cases are set as and , respectively. The optimal that maximizes the ESR can be obtained by (External-Eve-Only) and [3, Eq. (12)] (Internal-Eve-Only). The optimal values are determined as and , respectively, which agree with the simulation results shown in Fig. 2(a). It can be observed from Fig. 2 that the optimal that minimizes the SOP is different from the one that maximizes the ESR.
D. Percentage of Users in Outage: Fig. 3(a) and Fig. 3(b) depict percentages of users in outage for the External-Eve-Only and Internal-Eve-Only case, respectively. The parameters are set as , , , , and dB. It can be observed that the evaluation in (50) matches the empirical result well, which validates the accuracy of Propostion 4 .
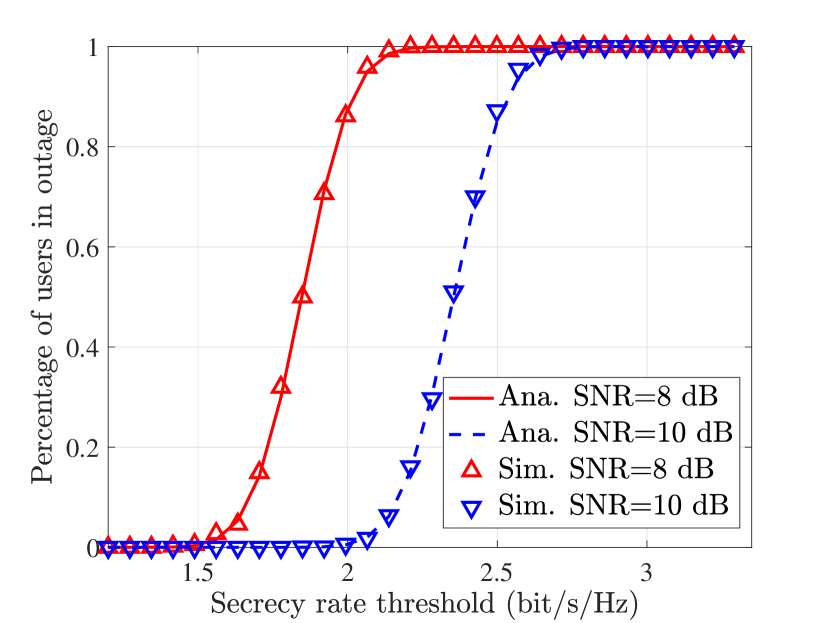
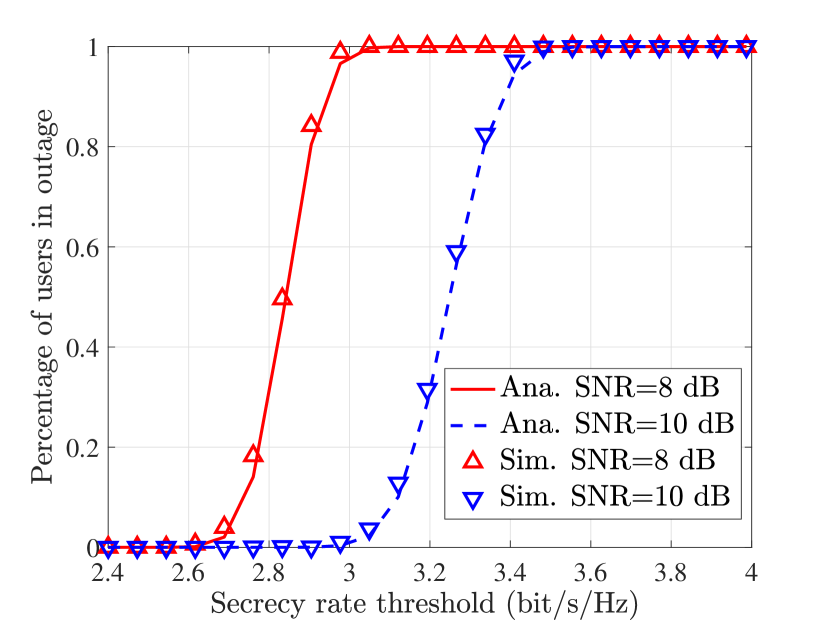
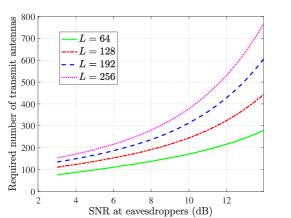
E. The Number of Transmit Antennas Required for a Positive Secrecy: With only the external Eves, Fig. 4 shows the number antennas required to achieve a positive secrecy rate for a given SNR at the Eves. The transmit SNR is set to be dB and . It can be observed that as the ability of Eves increases, the required number of antennas for a positive secrecy rate increases. The increasing rate grows larger as increases, which agrees with the analysis in Section V-C.
VII Conclusion
In this paper, the secrecy performance of RZF in the MISO broadcasting system was investigated. In the asymptotic regime that the numbers of transmit antennas, users, and Eves go to infinity with the same pace, a CLT for the joint distribution of SINRs and ESNRs was derived. The CLT was then used to obtain a closed-form approximation for the SOP of three cases, i.e., External-Eve-Only, Internal-Eve-Only, and External+Internal-Eve. Based on the derived results, the required number of transmit antennas for a positive secrecy rate and the percentage of user in secrecy outage were evaluated in a closed form. The secrecy loss caused by the external Eves and internal Eves were compared, showing that the loss caused by the internal Eves is less than that caused by the external Eves. The derived results were validated by numerical simulations. The methods used in this paper can be applied to analyze the performance of RZF with imperfect CSI and investigate the channel-inversion based precoding scheme like the recently proposed secure RZF [23].
Appendix A Proof of Theorem 1
Proof.
The proof can be summarized by three steps including: 1. Show the Gaussianity of the ; 2. Show the Gaussianity of the ; and 3. Derive the covariances. In the first two steps, without loss of generosity, we consider user , i.e., , and the derivation for other users are the same. The proof of the Gaussianity relies on the CLT for the quadratic forms shown in Lemma 2 of Appendix B. Specifically, we will first show that the SINRs and ESNRs can be approximated by a linear combination of the quadratic forms , , , and , and the approximation is tight in probability. The asymptotic variances obtained in this step are related to the high order resolvents, so we need to determine the variance by their deterministic equivalent. This process involves computations for the high-order resolvents, which are summarized by Lemma 3 in Appendix B. The results will also be utilized to evaluate the covariances. Now we turn to the first step.
A-A The Asymptotic Gaussianity of the
In this step, the fluctuation of will be investigated. To achieve this goal, we first rewrite as
| (55) | ||||
where . For any given , by the Markov inequality, we have
| (56) | ||||
Since is bounded away from zero almost surely, , , and , we have . Therefore, can be approximated by the first two terms at the right hand side of (LABEL:first_app) and the approximation is tight in probability. can be written as
| (57) |
where . By the variance control in [20, 41], we can show that and so that we can prove for a positive by the same approach in (LABEL:eps_s). Then, by substituting (57) into (LABEL:first_app), we have the following linear approximation
| (58) | ||||
where and are given in (40).
Now we turn to determine the asymptotic distribution of the random process at the right hand side of (LABEL:SINR_linear). Given , and are both in quadratic forms. According to Lemma2, we can show that and both converge to a Gaussian distribution when is given so that the linear combination of them also converges to a Gaussian distribution. Thus, we only need to determine the asymptotic variances for , and their covariance, which can be obtained by Lemma 3 in Appendix B as
| (59) |
| (60) |
The covariance of and can be evaluated by
| (61) |
Therefore, we can obtain the asymptotic variance of as
| (62) |
A-B The Asymptotic Gaussianity of
In this part, we will show the Gaussianity of by the same approach as Appendix A-A. We first replace by in (16) to obtain
| (63) |
where . By the variance control in [22, Lemma 3], we have to show so that we only need to consider the asymptotic distribution of . To achieve this goal, we first perform the following decomposition
| (64) | ||||
where , , and . We can then show that , , and vanish in probability and here we take as an example. can be upper bounded by
| (65) | ||||
The term can be upper bounded by
| (66) | ||||
The first term of the RHS in (66) is bounded by
| (67) | ||||
where the inequality holds true due to the boundness of , which was shown in [22, Lemma 2]. We also have the bound for the second term in the RHS of (66) as
| (68) | ||||
and
| (69) |
where , , and are constants which are independent of , , and . By substituting (67)-(68) into (66) and then (65), we can obtain that so that
| (70) |
Similarly, we can show that and . Therefore, we have
| (71) | ||||
| (72) |
where the last step follows from , which can be obtained by the Nash-Poincaré Inequality in [20, 42]. can be evaluated by the integration by parts formula [20, 42],
| (73) | ||||
By the evaluations in Lemma 3, we have
| (74) |
| (75) |
Therefore, we can obtain the asymptotic variance of as
| (76) |
A-C The Asymptotic Gaussianity of
Similar to the manipulation of and , can be approximated by
| (77) | ||||
The asymptotic variance of and the covariance between and can be obtained by
Therefore, we can obtain the asymptotic variance of as
A-D The Evaluation of Covariances
We will first give the closed-form expression for the asymptotic covariances between , , and . By (LABEL:SINR_linear), (LABEL:ex_linear) and (88) in Lemma (3), we can obtain
| (78) | |||
| (79) | ||||
The evaluations of , , and can be found in (59), (61), and (75), respectively. The covariances of the pairs and can be given by
where
| (80) | ||||
and
| (81) | ||||
By far, we have shown that , , and converge to a Gaussian distribution when , , go to infinity with the same pace. Next, we need to investigate the covariance between SINR and ESNR and the covariance between different users. It has been proved in [43, Eq.(2.9)-(2.11)] that and are asymptotically independent. By a similar approach, we can also prove the asymptotic independence between , , , , and , when so that the asymptotic covariances are all zero. ∎
Appendix B Useful Results
Lemma 2.
(CLT for quadratic forms) Given assumptions A.1, , , and , there holds true that
| (82) |
where . Similarly, we also have
| (83) | |||
where and .
Proof.
The first CLT is the separable case in [21] when the resolvent matrix is given. The other two CLTs can be proved by the same approach and the proof is omitted here. ∎
Lemma 3.
(Computation results about the high order resolvents) Given assumptions A.1-A.3 and any deterministic matrices , with bounded norm, the following evaluations hold true
| (84) |
| (85) |
| (86) |
| (87) |
| (88) |
| (89) |
| (90) | ||||
| (91) | ||||
| (92) | ||||
Proof.
The proof of Lemma 3 is given in Appendix C. ∎
The evaluation of the high order resolvent is considered in [22], which is used to set up a CLT for the signal-to-noise ratio (SNR) of minimum variance distortionless response (MVDR) filter. (85) is equivalent to [22, Proposition 3]. However, more complex forms for the fourth order resolvents related to multiple system parameters, e.g. , , need to be evaluated while in [22], only one undetermined parameter is considered. Lemma (3) is more general than those in [22]. If we take the first to be , (87) is equivalent to the result in [22, Proposition 4] .
Appendix C Proof of Lemma 3
Proof.
The main idea is to evaluate the high-order resolvents based on the lower-order results. As a result, we will perform the computation from low order to high order iteratively. We first turn to the evaluation of the second-order resolvent in (84). For any deterministic matrices , , , and with bounded norm, we have
| (95) | ||||
by integration by parts formula. Then we turn to evaluate the third-order resolvent. By the resolvent identity and the integration by parts formula, we have
| (96) | ||||
By solving in (96), taking the trace operation, and using variance control in [20, 22], we can obtain
| (97) | ||||
By letting in (97), we can obtain (85). Then, by the integration by parts formula [20], we can obtain the evaluation for by plugging (95) into (98) below
| (98) | ||||
By replacing the trace of the third-order resolvents by (97) and letting , , in (98), we can obtain (86). The fourth-order resolvent in (87) can be evaluated by the similar approach, which is given in (99) at the top of the next page,
| (99) | ||||
where step in (99) is obtained by plugging (97) and (98) into (99) to replace and , respectively. To obtain (88), we first follow similar steps as in (96) to obtain the evaluation for . Then by replacing the third-order terms in
| (100) | ||||
by (97) and (98), we can conclude (88). The tedious computation is omitted here. Then we turn to evaluate (89). By the integration by parts formula, we can obtain
| (101) | ||||
The third-order term in (101) can be obtained by
| (102) | ||||
The evaluation of (102) can be obtained by plugging the evaluations in (95) and (98) to replace the expectations for the trace of the lower order resolvents. With these evaluations, all the terms in (101) can be obtained so that (89) is concluded.
∎
References
- [1] N. Yang, L. Wang, G. Geraci, M. Elkashlan, J. Yuan, and M. Di Renzo, “Safeguarding 5G wireless communication networks using physical layer security,” IEEE Commun. Mag., vol. 53, no. 4, pp. 20–27, April. 2015.
- [2] Y.-S. Shiu, S. Y. Chang, H.-C. Wu, S. C.-H. Huang, and H.-H. Chen, “Physical layer security in wireless networks: A tutorial,” IEEE Wireless Commun. Mag., vol. 18, no. 2, pp. 66–74, April. 2011.
- [3] G. Geraci, R. Couillet, J. Yuan, M. Debbah, and I. B. Collings, “Large system analysis of linear precoding in MISO broadcast channels with confidential messages,” IEEE J. Sel. Areas Commun., vol. 31, no. 9, pp. 1660–1671, Sep. 2013.
- [4] I. Csiszár and J. Korner, “Broadcast channels with confidential messages,” IEEE Trans. Inf. Theory, vol. 24, no. 3, pp. 339–348, May 1978.
- [5] Y. Deng, L. Wang, M. Elkashlan, A. Nallanathan, and R. K. Mallik, “Physical layer security in three-tier wireless sensor networks: A stochastic geometry approach,” IEEE Trans. Inf. Forensics Security, vol. 11, no. 6, pp. 1128–1138, Jan. 2016.
- [6] C. B. Peel, B. M. Hochwald, and A. L. Swindlehurst, “A vector-perturbation technique for near-capacity multiantenna multiuser communication-part i: channel inversion and regularization,” IEEE Trans. Commun., vol. 53, no. 1, pp. 195–202, Jan. 2005.
- [7] T. Yoo and A. Goldsmith, “On the optimality of multiantenna broadcast scheduling using zero-forcing beamforming,” IEEE J. Sel. Areas Commun., vol. 24, no. 3, pp. 528–541, Mar. 2006.
- [8] A. Wiesel, Y. C. Eldar, and S. Shamai, “Zero-forcing precoding and generalized inverses,” IEEE Trans. Signal Process., vol. 56, no. 9, pp. 4409–4418, Aug. 2008.
- [9] G. Geraci, M. Egan, J. Yuan, A. Razi, and I. B. Collings, “Secrecy sum-rates for multi-user MIMO regularized channel inversion precoding,” IEEE Trans. Commun., vol. 60, no. 11, pp. 3472–3482, Sep. 2012.
- [10] S. A. A. Fakoorian and A. L. Swindlehurst, “On the optimality of linear precoding for secrecy in the MIMO broadcast channel,” IEEE J. Sel. Areas Commun., vol. 31, no. 9, pp. 1701–1713, Aug. 2013.
- [11] S. Yang, M. Kobayashi, P. Piantanida, and S. Shamai, “Secrecy degrees of freedom of MIMO broadcast channels with delayed CSIT,” IEEE Trans. Inf. Theory, vol. 59, no. 9, pp. 5244–5256, Jun. 2013.
- [12] N. Yang, G. Geraci, J. Yuan, and R. Malaney, “Confidential broadcasting via linear precoding in non-homogeneous MIMO multiuser networks,” IEEE Trans. Commun., vol. 62, no. 7, pp. 2515–2530, Jul. 2014.
- [13] X. Zhou, R. K. Ganti, and J. G. Andrews, “Secure wireless network connectivity with multi-antenna transmission,” IEEE Trans. Wireless Commun., vol. 10, no. 2, pp. 425–430, Dec. 2010.
- [14] P. C. Pinto, J. Barros, and M. Z. Win, “Secure communication in stochastic wireless networks—part i: Connectivity,” IEEE Trans. Inf. Forensics Security, vol. 7, no. 1, pp. 125–138, Feb. 2011.
- [15] P. C. Pinto, J. Barros, and M. Z. Win, “Secure communication in stochastic wireless networks—part ii: Maximum rate and collusion,” IEEE Trans. Inf. Forensics Security, vol. 7, no. 1, pp. 139–147, Aug. 2011.
- [16] G. Geraci, S. Singh, J. G. Andrews, J. Yuan, and I. B. Collings, “Secrecy rates in broadcast channels with confidential messages and external eavesdroppers,” IEEE Trans. Wireless Commun., vol. 13, no. 5, pp. 2931–2943, May. 2014.
- [17] H. Chen, X. Tao, N. Li, Y. Hou, J. Xu, and Z. Han, “Secrecy performance analysis for hybrid wiretapping systems using random matrix theory,” IEEE Trans. Wireless Commun., vol. 18, no. 2, pp. 1101–1114, Feb. 2019.
- [18] X. Yu, J. Zhang, M. Haenggi, and K. B. Letaief, “Coverage analysis for millimeter wave networks: The impact of directional antenna arrays,” IEEE J. Sel. Areas Commun., vol. 35, no. 7, pp. 1498–1512, Jul. 2017.
- [19] J. Hoydis, S. Ten Brink, and M. Debbah, “Massive MIMO in the UL/DL of cellular networks: How many antennas do we need?” IEEE J. Sel. Areas Commun., vol. 31, no. 2, pp. 160–171, Feb. 2013.
- [20] W. Hachem, O. Khorunzhiy, P. Loubaton, J. Najim, and L. Pastur, “A new approach for mutual information analysis of large dimensional multi-antenna channels,” IEEE Trans. Inf. Theory, vol. 54, no. 9, pp. 3987–4004, Sep. 2008.
- [21] A. Kammoun, M. Kharouf, W. Hachem, and J. Najim, “A central limit theorem for the SINR at the LMMSE estimator output for large-dimensional signals,” IEEE Trans. Inf. Theory, vol. 55, no. 11, pp. 5048–5063, Nov. 2009.
- [22] F. Rubio, X. Mestre, and W. Hachem, “A CLT on the SNR of diagonally loaded MVDR filters,” IEEE Trans. Signal Process., vol. 60, no. 8, pp. 4178–4195, Aug. 2012.
- [23] S. Asaad, A. Bereyhi, R. R. Müller, and R. F. Schaefer, “Secure regularized zero forcing for multiuser MIMOME channels,” in Proc. Asilomar Conf. Signals, Syst. Comput. (ASILOMAR). Pacific Grove, CA, USA: IEEE, Nov. 2019, pp. 1108–1113.
- [24] A. Bereyhi, S. Asaad, R. R. Müller, R. F. Schaefer, G. Fischer, and H. V. Poor, “Securing massive mimo systems: Secrecy for free with low-complexity architectures,” IEEE Trans. Wireless Commun., vol. 20, no. 9, pp. 5831–5845, Sep. 2021.
- [25] A. Kammoun, M. Kharouf, W. Hachem, and J. Najim, “BER and outage probability approximations for LMMSE detectors on correlated MIMO channels,” IEEE Trans. Inf. Theory, vol. 55, no. 10, pp. 4386–4397, Oct. 2009.
- [26] A. Kammoun, L. Sanguinetti, M. Debbah, and M.-S. Alouini, “Asymptotic analysis of RZF in large-scale MU-MIMO systems over Rician channels,” IEEE Trans. Inf. Theory, vol. 65, no. 11, pp. 7268–7286, Nov. 2019.
- [27] A. Kammoun, A. Chaaban, M. Debbah, M.-S. Alouini et al., “Asymptotic max-min SINR analysis of reconfigurable intelligent surface assisted MISO systems,” IEEE Trans. Wireless Commun., vol. 19, no. 12, pp. 7748–7764, Apr. 2020.
- [28] M. Z. I. Sarkar, T. Ratnarajah, and M. Sellathurai, “Secrecy capacity of nakagami-m fading wireless channels in the presence of multiple eavesdroppers,” in Proc. Asilomar Conf. Signals, Syst. Comput. (ASILOMAR). Pacific Grove, CA, USA: IEEE, Nov 2009, pp. 829–833.
- [29] X. Zhang and S. Song, “Secrecy analysis for IRS-aided wiretap MIMO communications: Fundamental limits and system design,” arXiv preprint arXiv:2209.00392, Sep. 2022.
- [30] R. Couillet, M. Debbah, and J. W. Silverstein, “A deterministic equivalent for the analysis of correlated MIMO multiple access channels,” IEEE Trans. Inf. Theory, vol. 57, no. 6, pp. 3493–3514, Jun. 2011.
- [31] X. Zhang and S. Song, “Bias for the trace of the resolvent and its application on non-Gaussian and non-centered MIMO channels,” IEEE Trans. Inf. Theory, vol. 68, no. 5, pp. 2857–2876, May. 2021.
- [32] X. Zhang, X. Yu, and S. Song, “Outage probability and finite-SNR DMT analysis for IRS-aided MIMO systems: How large IRSs need to be?” IEEE J. Sel. Topics Signal Process., vol. 16, no. 5, pp. 1070–1085, Aug. 2022.
- [33] P. Billingsley, Convergence of probability measures. John Wiley & Sons, 2013.
- [34] R. Couillet and M. Debbah, Random matrix methods for wireless communications. Cambridge University Press, 2011.
- [35] S. Wagner, R. Couillet, M. Debbah, and D. T. Slock, “Large system analysis of linear precoding in correlated MISO broadcast channels under limited feedback,” IEEE Trans. Inf. Theory, vol. 58, no. 7, pp. 4509–4537, Jul. 2012.
- [36] A. W. Van der Vaart, Asymptotic statistics. Cambridge university press, 2000, vol. 3.
- [37] A. Pelletier, R. Couillet, and J. Najim, “Second-order analysis of the joint SINR distribution in Rayleigh multiple access and broadcast channels,” in Proc. Asilomar Conf. Signals, Syst. Comput. (ASILOMAR). Pacific Grove, CA, USA: IEEE, Nov 2013, pp. 1223–1227.
- [38] V. K. Nguyen and J. S. Evans, “Multiuser transmit beamforming via regularized channel inversion: A large system analysis,” in Proc. IEEE Global Commun. Conf. (GLOBECOM). New Orleans, LA, USA: IEEE, Nov. 2008, pp. 1–4.
- [39] S. K. Yong and J. S. Thompson, “Three-dimensional spatial fading correlation models for compact MIMO receivers,” IEEE Trans. Wireless Commun., vol. 4, no. 6, pp. 2856–2869, Nov. 2005.
- [40] J. Miranda, R. Abrishambaf, T. Gomes, P. Gonçalves, J. Cabral, A. Tavares, and J. Monteiro, “Path loss exponent analysis in wireless sensor networks: Experimental evaluation,” in 2013 11th IEEE international conference on industrial informatics (INDIN). IEEE, 2013, pp. 54–58.
- [41] X. Zhang and S. Song, “Asymptotic mutual information analysis for double-scattering MIMO channels: A new approach by Gaussian tools,” arXiv preprint arXiv:2207.12709, Jul. 2022.
- [42] X. Zhang and S. Song, “Second-order coding rate of quasi-static Rayleigh-Product MIMO channels,” arXiv preprint arXiv:2210.08832, 2022.
- [43] G.-M. Pan, M.-H. Guo, and W. Zhou, “Asymptotic distributions of the signal-to-interference ratios of lmmse detection in multiuser communications,” The Annals of Applied Probability, vol. 17, no. 1, pp. 181–206, Feb. 2007.