This work has been submitted to Advanced Robotics for possible publication.
Secure Motion-Copying via Homomorphic Encryption
Abstract
This study aims to develop an encrypted motion-copying system using homomorphic encryption for secure motion preservation and reproduction. A novel concept of encrypted motion-copying systems is introduced, realizing the preservation, edition, and reproduction of the motion over encrypted data. The developed motion-copying system uses the conventional encrypted four-channel bilateral control system with robotic arms to save the leader’s motion by a human operator in the ciphertext in a memory. The follower’s control system reproduces the motion using the encrypted data loaded from the secure memory. Additionally, the developed system enables us to directly edit the motion data preserved in the memory without decryption using homomorphic operation. Finally, this study demonstrates the effectiveness of the developed encrypted motion-copying system in free motion, object contact, and spatial scaling scenarios.
keywords:
Motion-copying; encrypted control; experimental validation; four-channel bilateral control; teleoperation1 Introduction
Motion-copying systems record and reproduce human operations, leveraging bilateral control to extract motion data [1, 2]. The motion-copying systems find applications in fields such as tasks by skilled workers (e.g., spinning), calligraphy, and education [1, 3, 4, 5, 6]. Unlike motion capture and robot teaching, which rely solely on position data, the motion-copying system stores both position and force data. This duality facilitates the replication of intricate movements, notably in skilled labor and surgical procedures.
Numerous studies have been dedicated to enhancing the motion-copying system. For example, spatial scaling (resizing motion trajectories) and time scaling (variable playback speeds) have been studied extensively in [2, 7, 8, 9, 10, 11]. In [12, 13], the authors have explored the methods of reducing the size of stored motion data and have developed efficient data compression techniques. Furthermore, there have been studies on modeling the environment via the motion data when the follower robot contacts with the environment [14, 15]. In [16, 17], the authors have investigated methods for efficiently searching for motions that match the current environment and configuration within an accumulated database. In [5, 18], the motion-copying system between robots with different structures has been developed. Additionally, the stability of motion-copying systems is analyzed in [19].
However, the network involved in the bilateral control system is needed for operating a motion-copying system effectively. Concerns regarding the security of such networked systems arise when there are malicious attackers on the network. There have been instances of industrial control systems being targeted in cyberattacks, such as Stuxnet and Industroyer [20, 21]. As a countermeasure to cyberattacks on control systems, an encrypted control method that operates on encrypted data using homomorphic encryption [22, 23, 24] has been proposed in [25, 26]. Encrypted control involves encrypting input and output signals and parameters using a specific homomorphic encryption scheme, providing effective protection against eavesdropping and tampering attacks. There have been several application studies on encrypted control, such as PID control systems [27, 28] and encrypted bilateral control systems [29, 30], to enhance cybersecurity for remote control and operation. Enhancing the cybersecurity of motion-copying systems by applying homomorphic encryption is crucial, especially when dealing with sensitive and confidential data such as the movements of skilled workers.
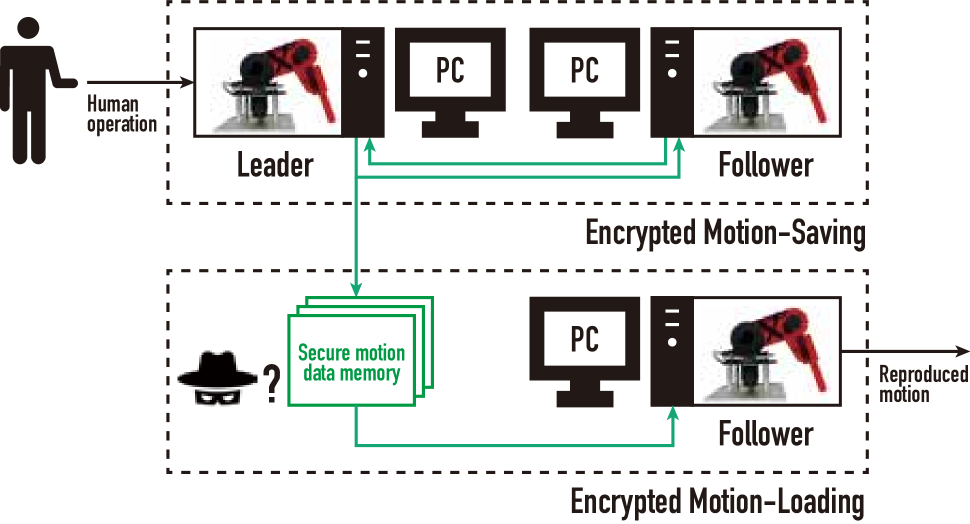
The objective of this study is to develop an encrypted motion-copying system using homomorphic encryption for secure motion preservation and reproduction. We introduce a novel concept of encrypted motion-copying systems, presented in Fig. 1, where encrypted signals and control parameters are highlighted in green. The concept is an extension of the conventional methods [1, 31] that realizes storing, editing, and reproducing the motion while encrypted. Based on this framework, this study develops the encrypted motion-copying system using the encrypted four-channel bilateral control system with the leader and follower robotic arms from [32]. The encrypted motion-copying system comprises the motion-saving and motion-loading phases. In saving motion, the system uses the encrypted bilateral control system to save the leader’s motion by a human operator in the secure memory in the ciphertext. In loading motion, the follower’s control system reproduces the saved motion. Additionally, the proposed system allows for editing the encrypted stored motion data directly without decryption, facilitating the generation of appropriate motions. By maintaining motion in ciphertext, eavesdropping attempts by malicious entities are thwarted. Finally, this study demonstrates the effectiveness of the developed encrypted motion-copying system in free motion, object contact, and spatial scaling scenarios.
The contributions of this paper are as follows. i) This study presents the new concept of an encrypted motion-copying system, which can be realized using the conventional encrypted four-channel bilateral control system. The developed system is the first application of the encrypted control fashion to motion-copying. ii) This study reveals that homomorphic encryption helps establish a secure framework of motion-copying, bolstering cybersecurity for motion preservation and reproduction.
The reminder structure of this paper is as follows. Section 2 provides preliminary information about the encrypted bilateral control system. Section 3 proposes the encrypted motion-copying system involving the saving and loading phases and how to scale the motion data. Section 4 demonstrates the developed encrypted motion-copying system to confirm the motion reproduction. Finally, Section 5 concludes this paper.
2 Preliminaries
This section provides preliminary information about the homomorphic encryption scheme proposed in [22], the maps between real and integer numbers to encode and decode used in [25], and the encrypted bilateral control system developed in [29].
2.1 Multiplicatively homomorphic encryption
The ElGamal encryption scheme, denoted as , consists of three fundamental algorithms: key generation , encryption , and decryption . With a key length of bits, the key generation algorithm, , produces a public key and a private key , which can be expressed as . The encryption algorithm, , is responsible for encrypting a plaintext using the public key , resulting in ciphertext , i.e., . The decryption algorithm, , is employed to decrypt the ciphertext using both the public key and the private key , and it yields the plaintext , i.e., . It’s important to note that the equation holds true.
ElGamal encryption possesses a multiplicative homomorphic property, allowing for ciphertext multiplication. Given two plaintexts, and , and their respective ciphertexts, and , the resulting ciphertext of their product is expressed as , where represents element-wise multiplication. This property is known as a multiplicative homomorphism.
2.2 Encoding and decoding
To utilize ElGamal encryption, real numbers must be encoded to the plaintext space using an appropriate quantization gain and , as defined by the following function:
| (1) |
where if and otherwise, and signifies rounding to the nearest element in the plaintext space . If and are prime, and are called a Sophie Germain prime and a safe prime number, respectively. Such primes play a crucial role in enhancing the security of ElGamal encryption. Furthermore, the decrypted plaintext is decoded as follows:
| (2) |
where if and otherwise and denotes rational numbers. Hereafter, we redefine to perform encoding and encryption and to perform decryption and decoding.
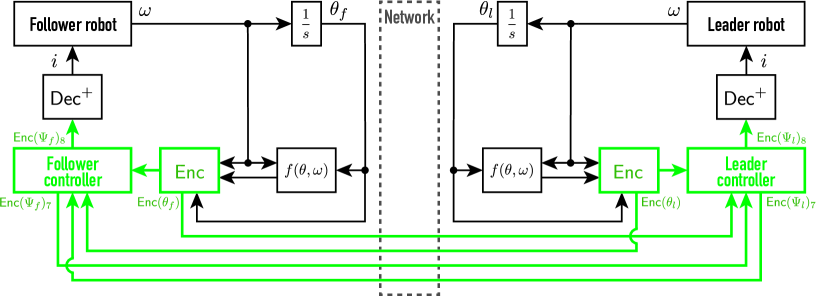
2.3 Encrypted bilateral control system
The encrypted four-channel bilateral control system with robotic arms, as illustrated in Fig. 2, is used to construct the proposed secure motion-copying system. The control objective is to achieve ideal kinesthetic coupling:
| (3) |
between the yaw-axis motors of the leader and follower robotic arms:
| (4) |
where is a continuous time, is the angle measured by the encoder; represents the unknown disturbance torque; represents the current input to the motor; and represent the nominal moment of inertia and torque coefficient of the motor, which are described in its specifications; subscripts and denote the leader and follower, respectively. The torque is expressed in the following equation consisting of modeling error, cable tension, friction, and an external force :
| (5) | ||||
| (6) |
where and represent the moment of inertia and the torque coefficient of the motor, which are not measurable, respectively, and a nonlinear function of the angle and velocity , encompasses cable tension and friction forces:
| (7) | ||||
| (8) |
To achieve the control objective for the robotic arm (4), we designed model-based linear controllers consisting of Proportional-Derivative (PD) and Proportional (P) controllers for position and force control, Disturbance Observer (DOB), and Reaction Force Observer (RFOB). Discretizing the controllers by a bilinear transformation with a sampling period results in the following discrete-time state-space representation:
| (9) |
with
| (10) |
| (11) |
where subscript represents a step (discrete time), and are controller outputs for the leader and follower, respectively; and are the controller inputs for the leader and follower, respectively; is identical controller parameters (system matrix) for the leader and follower. Moreover, and indicate the leader and follower controllers, respectively.
Let , where and denote addition and multiplication on the leader, respectively, and similarly, is defined on the follower. If the quantization error is negligibly small, the leader and follower encrypted controllers and are represented as follows:
| (12) |
where and , which are computed using the multiplicative homomorphism. Define . Then, and are obtained as follows:
| (13) |
where is a modified ElGamal encryption scheme. In addition, the quantization error, denoted as , is assumed to be negligible in this study, and the definition and derivation of the matrices and vectors are detailed in [29]. Consequently, the encrypted four-channel bilateral control system with the robotic arms, encrypted controller (12), and modified decryption (13), can be constructed as illustrated in Fig. 2, where it features encrypted communications and blocks, highlighted in green.
3 Encrypted Motion-Copying System
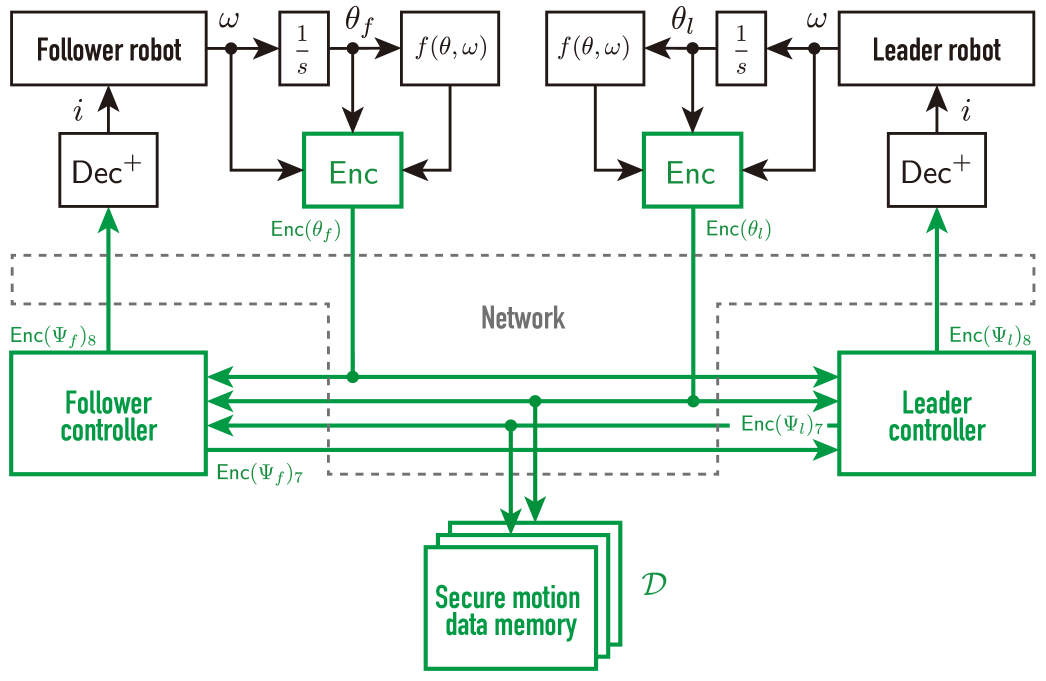
This section proposes a concept of encrypted motion-copying systems capable of storing motion data in a ciphertext and editing the stored data without decryption to reproduce the motion. The proposed motion-copying system consists of three phases: saving, spatial scaling, and loading the motion. The saving and loading phases consider the motion-saving and motion-loading systems illustrated in Fig. 3. To realize the proposed concept, this study uses the encrypted four-channel bilateral control system described in Section 2.3.
3.1 Secure motion data memory
Firstly, the secure motion data memory is introduced to store and edit the motion data. The memory is supposed to be located on a specific networked server that the motion-saving and motion-loading systems can communicate with, and the secure motion data on the memory is denoted as a finite set of data sequences:
| (14) |
where and are a ciphertext at step and means a sequence of encrypted signal with data length . The multiplicative homomorphism of the ElGamal encryption scheme allows us to scale the data set by scaling parameter with the corresponding quantization gain . This operation is referred to as spatial scaling [8]. When the motion data are scaled, the updated data set is denoted as
| (15) |
It should be noted that the motion data, and , and scaling parameter, , are all encrypted and stored in the memory. In addition, although the proposed concept enables us to store multiple motion-data sequences with different data lengths in the memory, this paper considers two sequences with identical lengths for simplicity.
Remark 1.
Spatial scaling is required when the size of the follower robot differs between motion-saving and motion-loading phases. This study achieves spatial scaling using multiplicative homomorphic encryption. Meanwhile, the temporal scaling that adjusts timestamps regarding the motion data, proposed [9], involves addition and multiplication, so a fully homomorphic encryption scheme is required to realize our proposed concept. This extension will be future work to address editing the motion data for several conditions.
3.2 Encrypted motion-saving system
We present the encrypted motion-saving system, illustrated in Fig. 3(a), consisting of the encrypted four-channel bilateral control system and the secure motion data memory to save the leader’s motion data. This study considers that the motion data measured during the operation are the encrypted rotation angle and estimated torque regarding the yaw-axis motor, which appears in the argument and output of the leader’s encrypted controller in (12). They are encapsulated within the set denoted as :
| (16) |
Fig. 3(a) confirms that the presented motion-saving system is a secure networked system configuration. The green lines and blocks indicate the encrypted communications and data processing, so the controllers and memory outside the plant sides operate with encrypted signals and parameters. Hence, even if malicious attackers eavesdrop on the control system or steal data from the secure motion data memory, it is challenging to ascertain the stored motions.
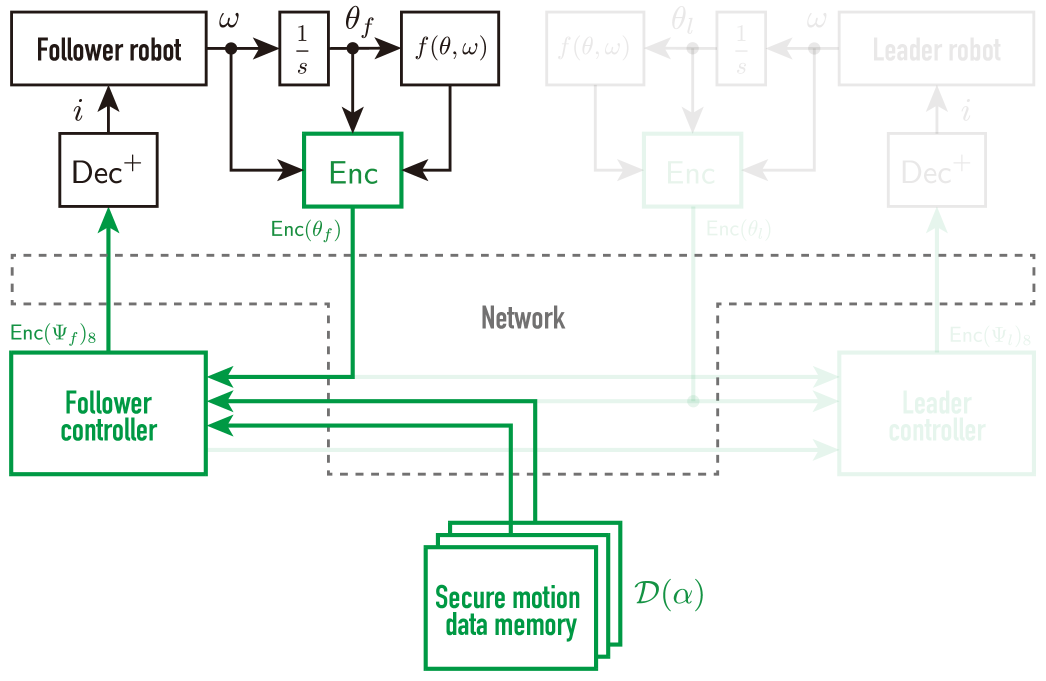
3.3 Encrypted motion-loading system
We present the encrypted motion-loading system, illustrated in Fig. 3(b), consisting of the follower-side control system with the robotic arm and the secure motion data memory to reproduce the motion. This study considers that the motion data in (16) are computed using an appropriate scaling parameter to be updated, as follows:
| (17) |
When the follower wants to reproduce the motion, the motion-loading system transmits the secure motion data of from the memory to the follower’s controller. Noted that the decoder installed on the follower side must have quantization gain set to , where and are quantization gains corresponding to encoding signals and parameters , respectively. Then, the follower robotic arm is controlled by the decrypted control command regarding an input current, which reproduces the desired motion.
Fig. 3(b) confirms that the presented motion-loading system is also a secure networked system configuration because the follower controller and memory outside the plant side are operated with the signals and parameters encrypted. Hence, it is challenging for malicious attackers to ascertain the stored motions.
Remark 2.
The introduced concept in this study can be applied to a different motion-loading situation where the follower’s controller is unencrypted and located on the plant side. In this setup, the decryption and encryption blocks on the plant side are not needed; The signal is input directly to the follower controller; The secure motion data loaded from the memory are decrypted in receiving on the follower controller, and the decrypted data are used to control processing. This implementation implies that the follower control system is not necessarily encrypted from the viewpoint of secure motion-copying.
Consequently, the concept of the proposed motion-copying system allows for the secure preservation and reproduction of motion. In the following section, we will delve into the practical setup used to investigate the effectiveness of the proposed system.
4 Experimental validation
This section demonstrates the effectiveness of the proposed encrypted motion-copying system through three scenarios: free motion, object contact, and spatial scaling. This study conducted experimental validation because it is challenging to model human-robot and robot-environment interactions, such as human movements and the response of the contact environment. The experiments set the sampling period , data length , and key length to , 750, and , taking computer resources and real-time computation into account. The quantization gains , , and were all set to , in trial and error. The controller parameters in were as follows,
| (18) |
| (19) | ||||
| (20) | ||||
| (21) |
For PC controller specifications and other parameters, please refer to [29].
4.1 Free motion
The free motion scenario represents saving and loading motion data without physical interaction with objects. In saving motion, a human operator controls the leader robot, and the follower robot replicates its movements, resulting in a 15-second motion sequence regarding the leader that is stored in the secure motion data memory. In loading motion, the developed system reproduces the stored motion such that the follower emulates the leader’s actions, where the scaling parameter was set to (1,1). The obtained results for saving and loading the motion are shown in Fig. 4.
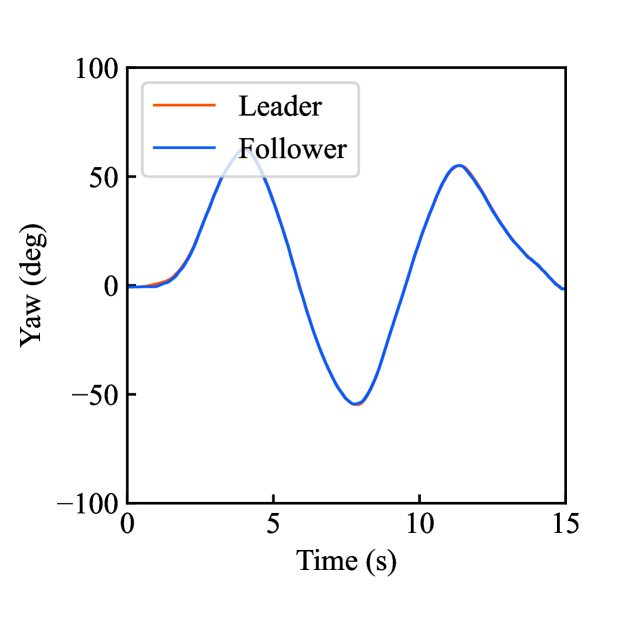
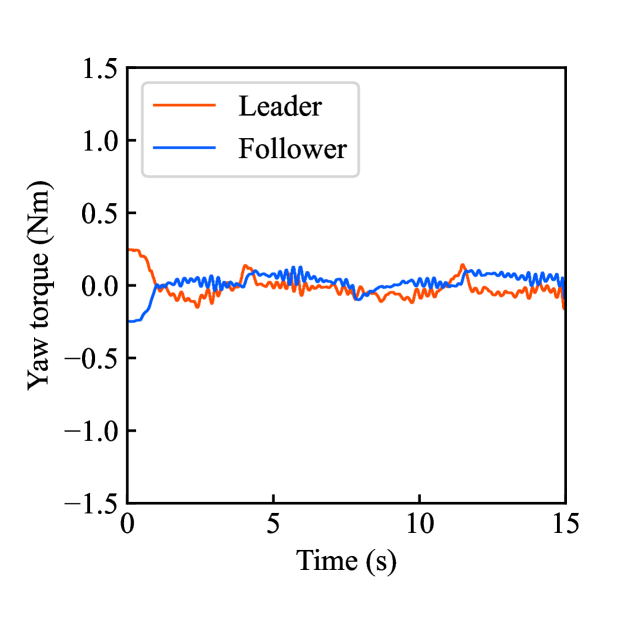
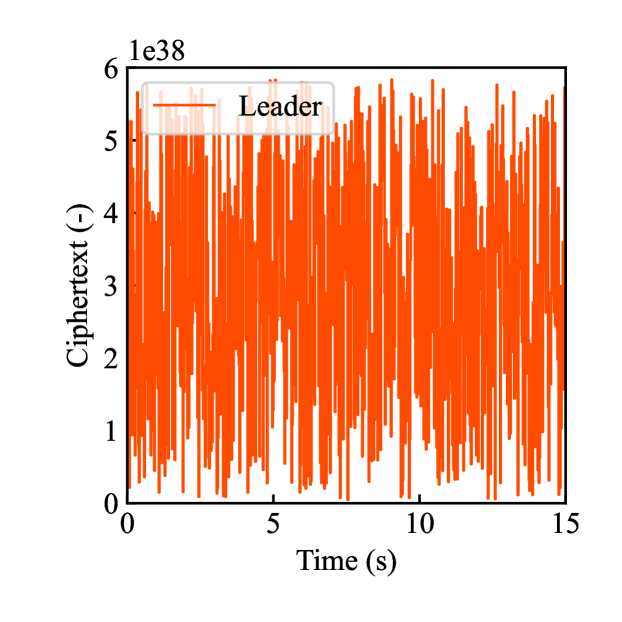
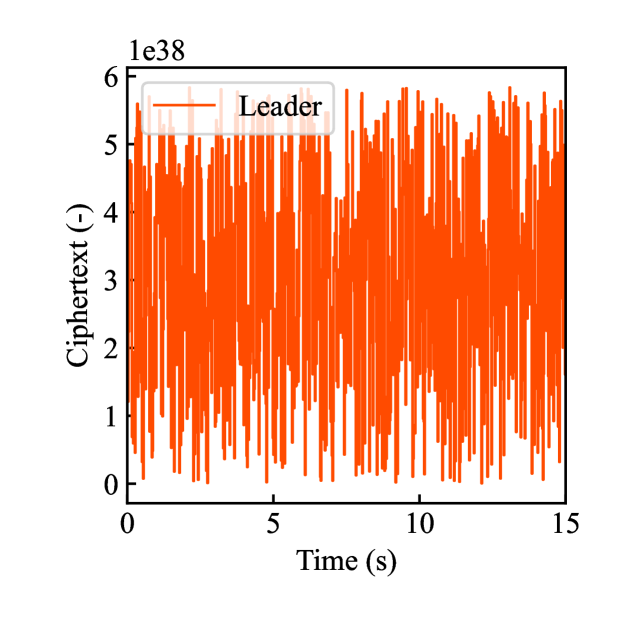
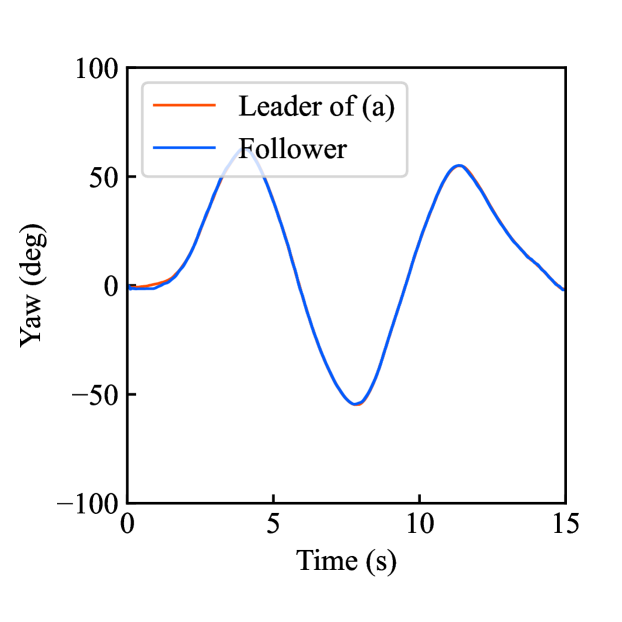
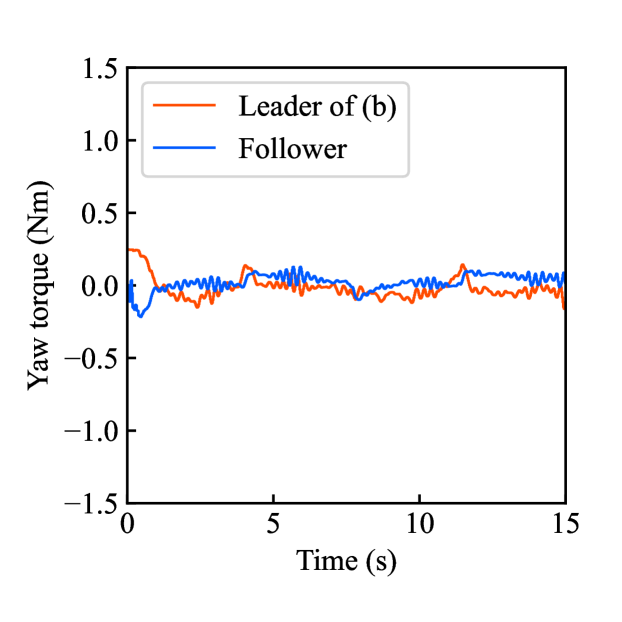
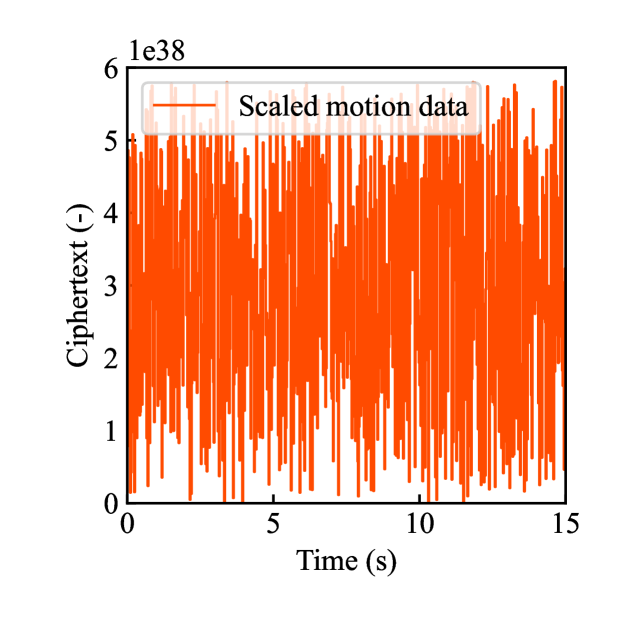
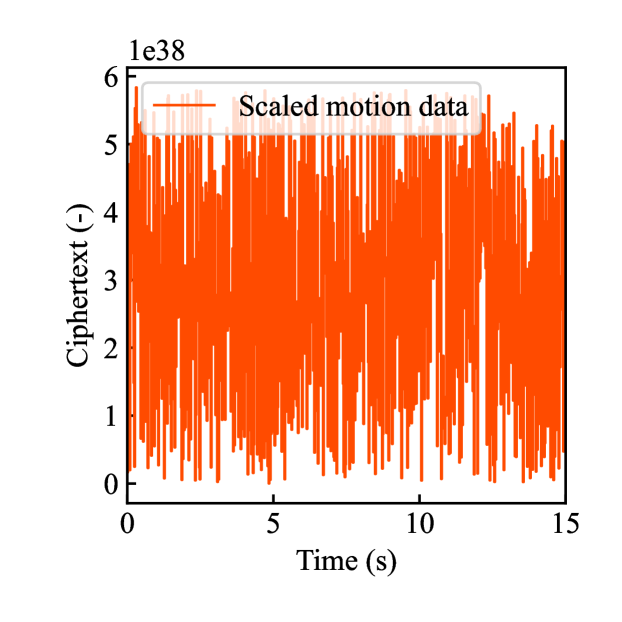
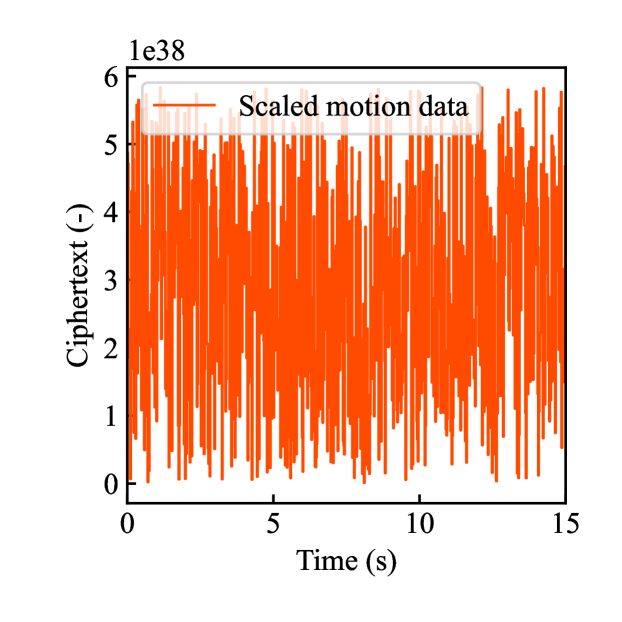
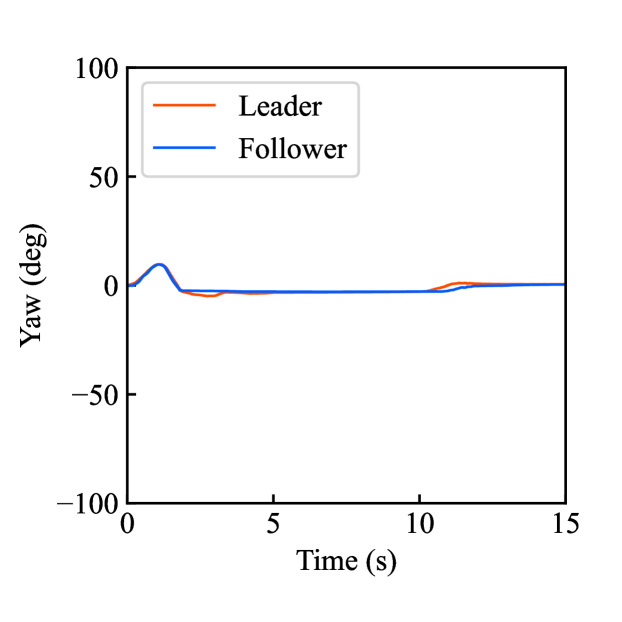
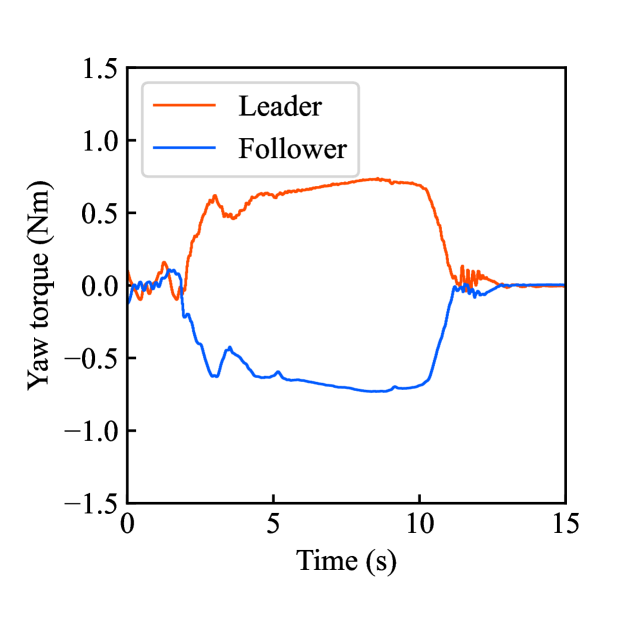
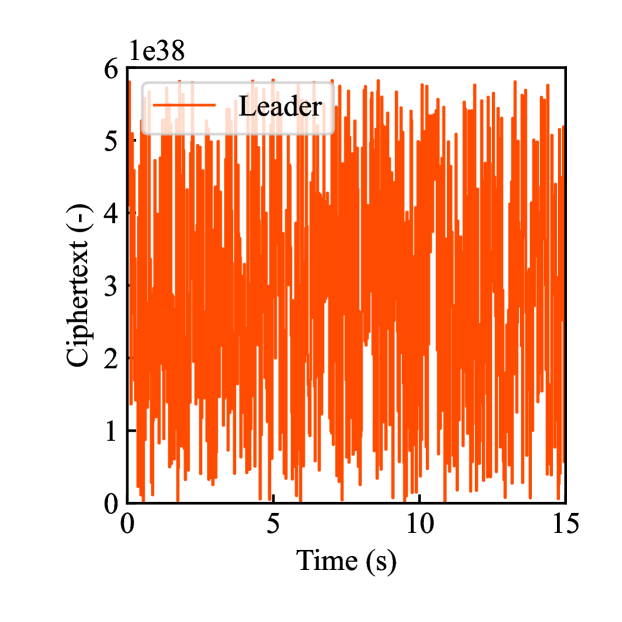
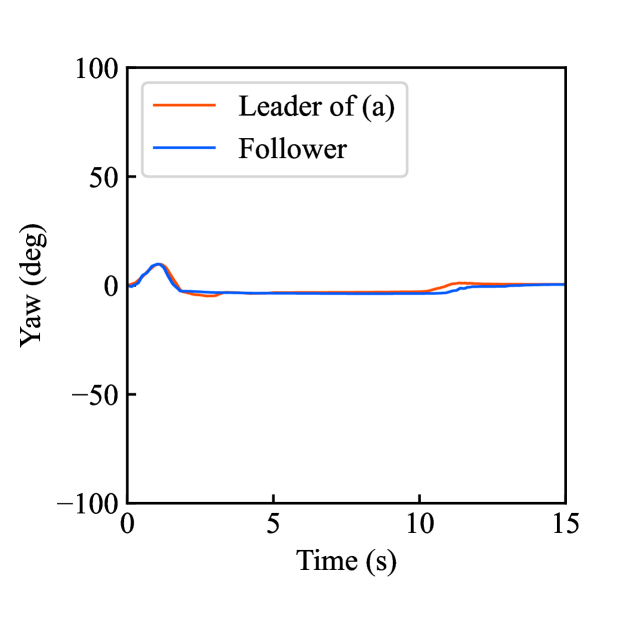
Figs. 4(a)-(d) show the time responses of the leader and follower robotic arms during saving motion, where the red and blue lines indicate the leader and follower, respectively. Figs. 4(a) and (b) illustrate the yaw-axis rotation angles and the estimated torque on the leader and follower sides, respectively. Figs. 4(c) and (d) show the encrypted rotation angle and estimated torque of the leader, respectively. The figures confirm that the follower’s behavior almost matches the leader’s and that the torques are approximately zeros due to no contact. The encrypted motions regarding and shown in Figs. 4(c) and (d) were stored in the secure motion data memory , where the encrypted data exhibit random fluctuations at the order of .
Figs. 4(e)-(h) show the time responses of the follower during loading motion from . Figs. 4(e) and (f) illustrate the yaw-axis rotation angles and the estimated torques, respectively, where the blue line indicates the resulting follower’s behavior and the red line being the same as one of Figs. 4(a) and (b) was added for comparison. Figs. 4(g) and (h) show the encrypted rotation angles and estimated torques that were loaded from , respectively. Consequently, the figures confirm that the reproduced behavior of the follower has a good tracking performance to the original behavior and that the estimated torque of the follower is almost the same as that of the follower in saving motion.
4.2 Object contact
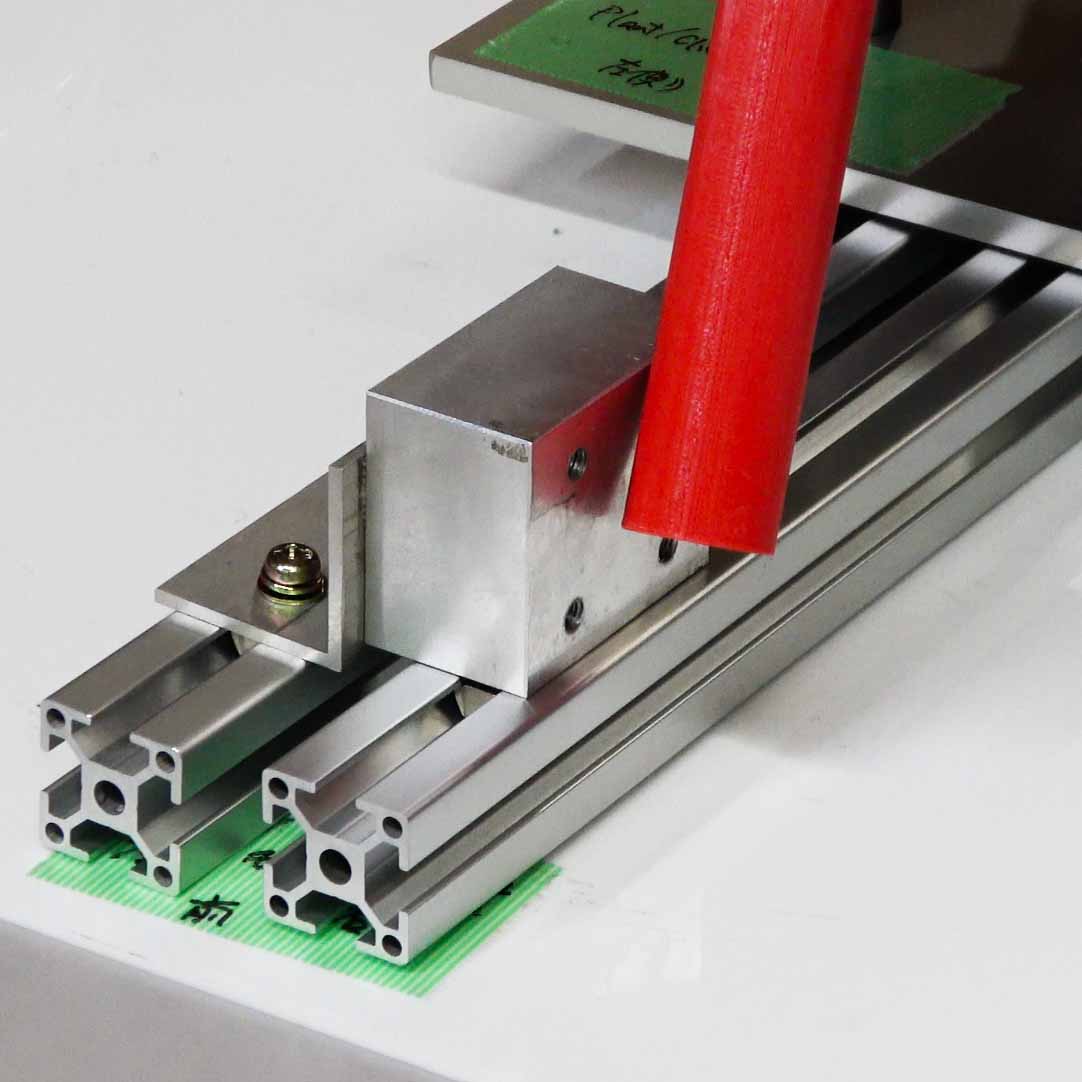
The object contact scenario represents saving and loading motion data involving physical object interaction, highlighting the capability of reproducing the contact force. This experiment considers an aluminum block fixed on the basement as an obstacle within the movable range of the follower’s robotic arm, as shown in Fig. 5. In saving motion, the follower robotic arm physically contacts the aluminum block in the telemanipulation by the operator, resulting in a 15-second motion sequence. In loading motion, the developed system reproduces the stored motion such that the follower emulates the leader’s movements during and after contact with the object, where the scaling parameter was set to (1,1). The obtained results are shown in Fig. 6.
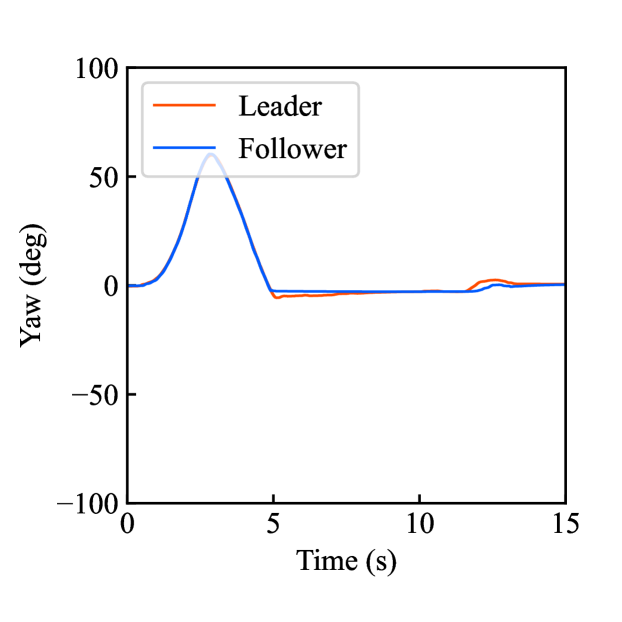
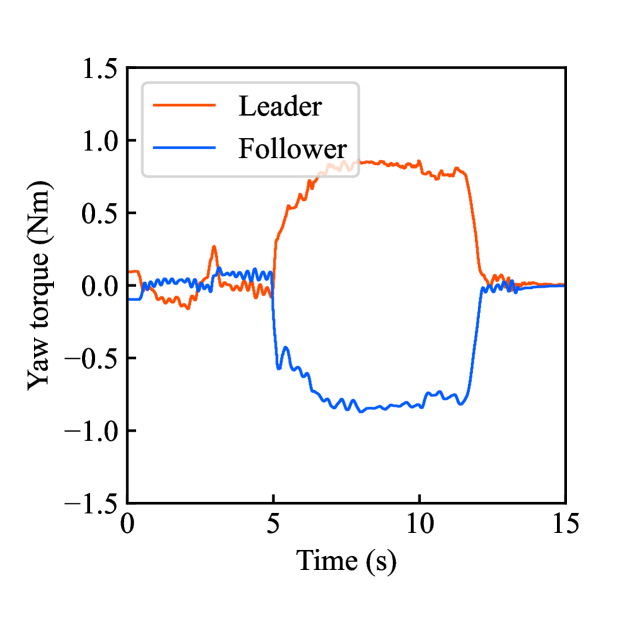
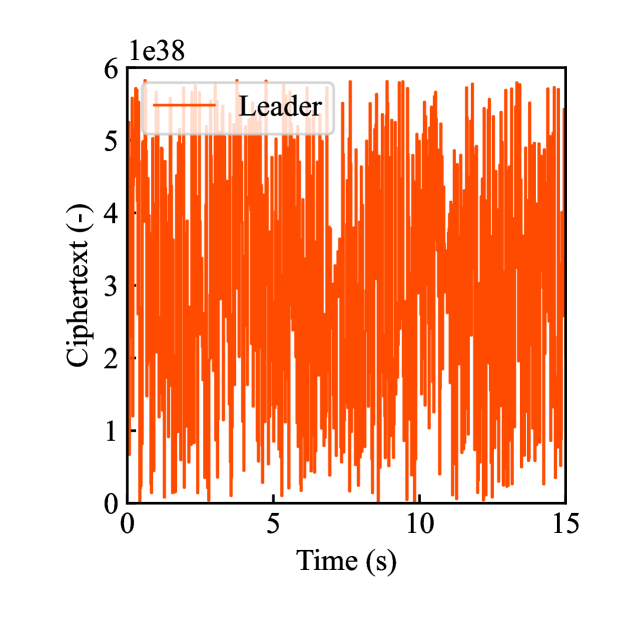
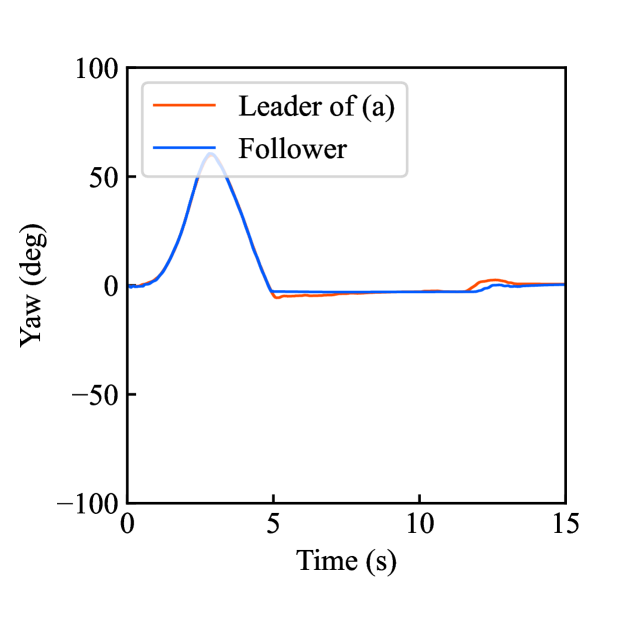
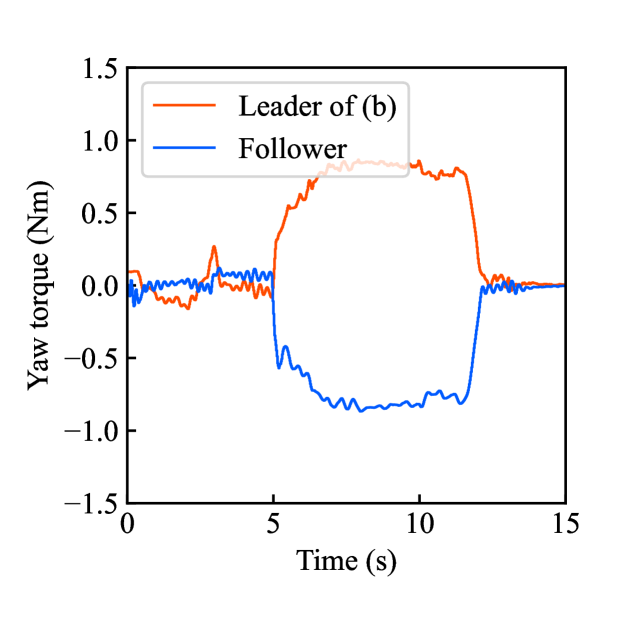
Figs. 6(a)-(d) show the time responses of the leader and follower robotic arms during saving motion, where the red and blue lines indicate the leader and follower, respectively. Figs. 6(a) and (b) illustrate the yaw-axis rotation angles and the estimated torque of the leader and follower, respectively. Figs. 6(c) and (d) shows the encrypted motions regarding and . These figures confirm that the follower comes into contact with the aluminum object at while maintaining nearly identical rotation angles to the leader and that estimated torques for the leader and follower are equal magnitudes and opposite signs, affirming adherence to Newton’s third law. The encrypted rotation angles and estimated torques exhibiting random fluctuations at were stored in .
Figs. 6(e)-(h) show the time responses of the follower during loading motion, where the object is fixed on the same location as saving motion. Figs. 6(e) and (f) illustrate the yaw-axis rotation angles and the estimated torques, respectively, where the meanings of the blue and red lines are the same as those in Fig. 4. Figs. 6(g) and (h) illustrate the leader’s encrypted motion loaded from . Consequently, these figures confirm that even in the aluminum-block environment, the proposed system securely reproduces the follower’s behavior which was almost the same as the leader’s behavior.
4.3 Spatial scaling
The spatial scaling scenario represents saving and loading the scaled motion with and without object contact. This experiment investigates the system’s capability of reproducing the scaled motion in each scenario of free motion with and object contact with . Similarly, in saving motion, 15-second motion sequences were stored in the secure memory , and in loading motion, the follower’s behavior was reproduced using the scaled motion loaded from . The obtained results for the free motion and object contact scenarios are shown in Figs. 7 and 8, respectively.
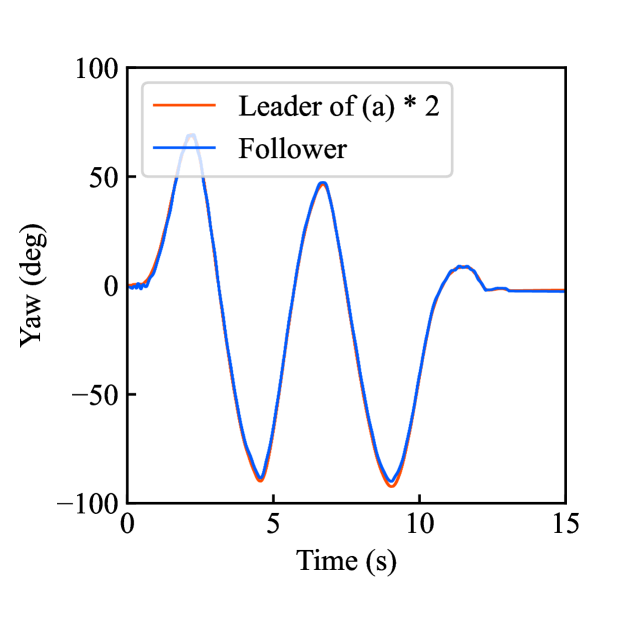
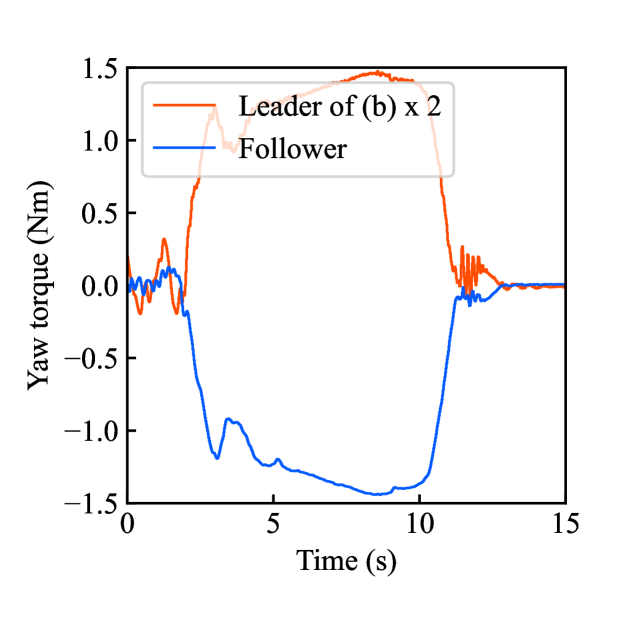
Figs. 7(a)-(d) show the time responses of both the robotic arms during saving motion, which confirms that the follower’s behavior matches the leader’s behavior. Meanwhile, Figs. 7(e)-(h) show the time responses of the follower’s behavior during loading motion. Fig. 7(e) confirms that the yaw-axis rotation angle of the follower was successfully doubled to the original leader’s behavior, while the estimated torque in Fig. 7(f) has no significant impact. Figs. 7(g) and (h) illustrate the encrypted rotation angle and estimated torque that were loaded from .
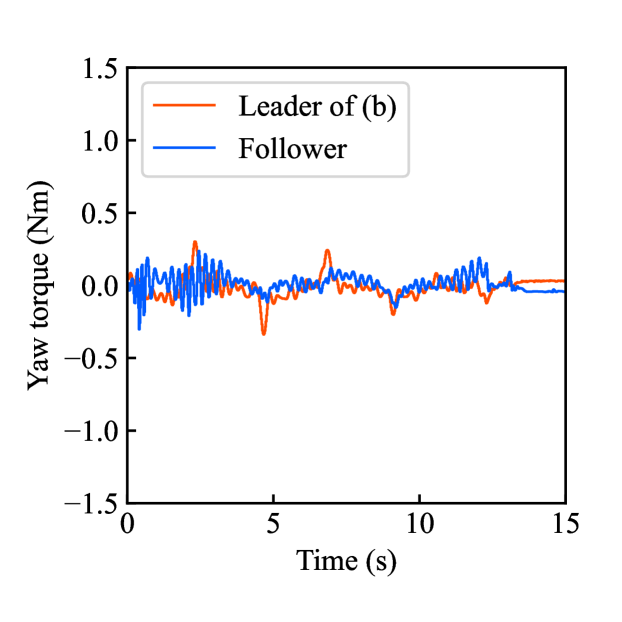
Furthermore, Figs. 8(a)-(d) show the time responses of both the robotic arms during saving motion. In this case, the follower comes into contact with the aluminum object at 2 s. During contact, the leader maintains a rotation angle nearly identical to the follower’s, exhibiting an estimated torque of the opposite sign. Meanwhile, Figs. 8(e)-(h) show the time responses of both the robotics arms during loading motion. Fig. 8(f) confirms that the estimated torque of the follower was successfully doubled to the original leader’s behavior, while the rotation angle in Fig. 8(e) has no significant impact. Fig. 8(g) and (h) illustrate the scaled encrypted behavior that was loaded from .
5 Conclusion
This study developed the encrypted motion-copying system with the robotic arms in the encrypted control fashion to ensure secure motion preservation and reproduction. The experimental validation across the three scenarios confirmed that the developed system could operate using the encrypted motions and scale the preserved motions for reproduction without decryption.
In future work, a fully homomorphic and keyed-homomorphic encryption scheme will be applied to construct motion-copying systems, bolstering the security level in managing preserved motions. Moreover, we will perform the stability analysis of the developed control system, which overcomes the difficulty of addressing both nonlinearity and quantization errors.
Funding
This work was supported by JSPS KAKENHI Grant Number 22H01509.
References
- [1] Yokokura Y, Katsura S, Ohishi K. Motion copying system based on real-world haptics. In: IEEE International Workshop on Advanced Motion Control; 2008. p. 613–618.
- [2] Yuki Yokokura, Seiichiro Katsura, Kiyoshi Ohishi. Motion copying system based on real-world haptics in variable speed. In: International Power Electronics and Motion Control Conference; 2008. p. 1604–1609.
- [3] Yokokura Y, Ohishi K. Reproducibility analysis and experimental validation of motion-copying system. In: Annual Conference on IEEE Industrial Electronics Society; 2012. p. 4430–4435.
- [4] Matsui A, Miura K, Katsura S. Robust motion-copying system using motion-data memory. In: IEEE International Symposium on Industrial Electronics; 2013. p. 1–6.
- [5] Matsui A, Katsura S. A method of motion reproduction for calligraphy education. In: IEEE International Conference on Mechatronics; 2013. p. 452–457.
- [6] Onoyama H, Katsura S. Reproducibility and operationability of motion-copying system for education. In: IEEE International Workshop on Advanced Motion Control; 2014. p. 627–632.
- [7] Kuwahara H, Ohnishi K, Tsunashima N, et al. Design method for motion reproduction system including time scaling based on robot dynamics. In: IEEE International Conference on Industrial Technology; 2010. p. 483–488.
- [8] Miura K, Katsura S. Spatially scaled motion-reproduction control using modified motion data. In: IEEE International Workshop on Advanced Motion Control; 2014. p. 248–253.
- [9] Igarashi K, Katsura S. Spatial shaping of motion-data based on motion-copying system using variable temporal scaling. In: Annual Conference of the IEEE Industrial Electronics Society; 2014. p. 2866–2871.
- [10] Igarashi K, Katsura S. Motion-data processing and reproduction based on motion-copying system. IEEJ Journal of Industry Applications. 2015;4(5):543–549.
- [11] Okano T, Oboe R, Ohnishi K, et al. Comparative study of soft motion for motion copying system with environmental variations. In: IEEE/ASME International Conference on Advanced Intelligent Mechatronics; 2018. p. 646–651.
- [12] Hiroyuki Tanaka, Kouhei Ohnishi. Haptic data compression/decompression using DCT for motion copy system. In: IEEE International Conference on Mechatronics; 2009. p. 1–6.
- [13] Nakano T, Yu K, Ohnishi K. Human task reproduction with Gaussian mixture models. In: IEEE International Conference on Industrial Technology; 2015. p. 283–288.
- [14] Yokokura Y, Katsura S. Environment copying system based on real-world haptics. In: Annual Conference of IEEE Industrial Electronics; 2009. p. 1865–1870.
- [15] Kobayashi R, Katsura S. Environmental modeling for motion-copying system using element description method. In: Annual Conference of the IEEE Industrial Electronics Society; 2022. p. 1–6.
- [16] Yokokura Y, Katsura S. Searching system of haptic environment. In: International Power Electronics and Motion Control Conference; 2010. p. T1–6.
- [17] Ohnishi Y, Katsura S. Motion modeling and search method based on hidden Markov model for motion database. In: Annual Conference of the IEEE Industrial Electronics Society; 2011. p. 4232–4237.
- [18] Phuong TT, Ohishi K, Yokokura Y. Motion-copying system of a different master-slave mechanism with variable reproduction speed. In: IEEE International Symposium on Industrial Electronics; 2014. p. 2244–2249.
- [19] Yokokura Y, Katsura S, Ohishi K. Stability analysis and experimental validation of a motion-copying system. IEEE Transactions on Industrial Electronics. 2009;56(10):3906–3913.
- [20] Chen TM, Abu-Nimeh S. Lessons from stuxnet. Computer. 2011;44(4):91–93.
- [21] Robert ML, Michael JA, Tim C. Analysis of the cyber attack on the ukrainian power grid. Electricity Information Sharing and Analysis Center. 2016;.
- [22] Elgamal T. A public key cryptosystem and a signature scheme based on discrete logarithms. 1985;31(4):469–472.
- [23] Paillier P. Public-Key Cryptosystems Based on Composite Degree Residuosity Classes. In: Stern J, editor. Proc. Advances in Cryptology — EUROCRYPT ’99; Berlin, Heidelberg. Springer Berlin Heidelberg; 1999. p. 223–238.
- [24] Emura K, Hanaoka G, Nuida K, et al. Chosen ciphertext secure keyed-homomorphic public-key cryptosystems. Designs, Codes, and Cryptography. 2018 8;86(8):1623–1683.
- [25] Kogiso K, Fujita T. Cyber-security enhancement of networked control systems using homomorphic encryption. In: Proc. IEEE Conf. Decis. Control.; 2015. p. 6836–6843.
- [26] Darup MS, Alexandru AB, Quevedo DE, et al. Encrypted control for networked systems: An illustrative introduction and current challenges. 2021;41(3):58–78.
- [27] Cheon JH, Han K, Hong SM, et al. Toward a secure drone system: Flying with real-time homomorphic authenticated encryption. IEEE Access. 2018;6:24325–24339.
- [28] Miyamoto M, Teranishi K, Emura K, et al. Cybersecurity-enhanced encrypted control system using keyed-homomorphic public key encryption. IEEE Access. 2023;11:45749–45760.
- [29] Takanashi H, Kosugi A, Teranishi K, et al. Cyber-secure teleoperation with encrypted four-channel bilateral control [Submitted to IEEE Transactions on Control Systems Technology, https://arxiv.org/abs/2302.13709]; 2023.
- [30] Naoto S, Tetsuro M, Kaoru T, et al. Implementation of encrypted control of pneumatic bilateral control system using wave variables. In: Proc. 27th Int. Symp. Artif. Life Robot.; 2022.
- [31] Matsui A, Katsura S. Motion-copying system using modal information for motion reproduction. In: Annual Conference of the IEEE Industrial Electronics Society; 2013. p. 6132–6137.
- [32] Tanaka Y, Katsura S. A voice-controlled motion reproduction using large language models for polishing robots. In: IEEE International Conference on Mechatronics; 2023. p. 1–6.