Secure Transmission by Leveraging Multiple Intelligent Reflecting Surfaces in MISO Systems
Abstract
Due to the broadcast nature of wireless communications, physical layer security has always been a fundamental but challenging problem. Recent advance of Intelligent Reflecting Surface (IRS) introduces a new dimension for secure communications by reconfiguring the transmission environments. In this paper, we devise a secure transmission scheme for multi-user MISO systems by leveraging multiple collaborative IRSs. Specifically, to guarantee the worst-case achievable secrecy rate among multiple legitimate users, we formulate a max-min problem that can be solved by an alternative optimization method to decouple it into multiple sub-problems. Based on semidefinite relaxation and successive convex approximation, each sub-problem can be further converted into convex problem and easily solved. Extensive experimental results demonstrate that our proposed scheme can adapt to complex scenarios for multiple users and achieve significant gain in terms of achievable secrecy rate. The gap between the secrecy rate from our proposed scheme and that from the traditional sum-rate maximization and our results show that the secrecy rate obtained from our scheme converges to that achieved from the traditional sum-rate maximization when increasing the number of elements on IRSs.
Index Terms:
Physical layer security, intelligent reflecting surface, secrecy rate.I Introduction
Due to the broadcast nature of wireless signals, it is vulnerable for user’s confidential messages in wireless communications. To safeguard communication security, physical layer security, which can be traced back to 1970’s Wyner’s seminal work [1, 2, 3], has been regarded as a key complement to higher-layer encryption techniques [4, 5]. In traditional communication systems, beamforming and Artificial Noise (AN) are considered as two effective approaches to defending against wiretapping channel and achieving secure communication [6, 7, 8, 9]. By exploiting multiple antennas and shaped beams, beamforming technology can be implemented to direct the signal towards the legitimate user and thus reduce the signal leakage. In addition to beamforming, AN technology can create significant interference and lower the SINR at eavesdroppers by properly designing AN signals. Thus, the achievable secrecy rate, which is a widely used criterion to capture the difference between mutual information of “Alice-Bob” intended channel and “Alice-Eve” eavesdropping channel and measure the security level, can be effectively improved especially when the channel state of transmitter-user and transmitter-eavesdropper are highly correlative during the transmission. Nevertheless, due to the complex environment of wireless communications, the proposed approaches do not always work as expected.
As a promising technology to achieve smart radio environment/intelligent radio environment in next generation cellular systems [10, 11], Intelligent Reflecting Surfaces (IRSs) can provide reconfigurable signal propagation environments to support cost-effective and power-efficient wireless communication services. Specifically, IRS is a metasurface composed of a large number of passive reflecting elements, which consumes much lower energy compared with traditional active relays/transceivers [12, 13]. By adaptively adjusting the reflection amplitude and/or phase shift of each element, the strength and direction of the incident electromagnetic wave becomes highly controllable. Thus, IRS is regarded as a novel solution to achieving configurable wireless transmission environment/intelligent radio environment/wireless 2.0 with low hardware/energy cost, and has been applied in various wireless applications such as coverage extension, interference cancellation, and energy efficiency enhancement [12, 10, 14]. Particularly, Zhang et al. [15, 14] articulate how to augment transmission environments with cheap reflectors without damaging aesthetic nature of users’ surrounding to boost transmission performance and present high layer implementation consideration. Due to the aforementioned advantages, the IRS-assisted communication systems have great potential to enhance physical layer security. By jointly optimizing operations on transmitter and passive reflecting elements of IRS, the transmitter-user channel state can be reconfigured to lower the signal leakage to eavesdroppers. Intuitively, users geographically close to the IRS are more likely beneficial from IRS by receiving the tuned signal, whose achievable secrecy rate can be significantly improved.
Recently, some efforts have been made to study IRS-assisted systems for physical layer security. Cui et al. [16] investigated an IRS-aided secure wireless communication systems where a simple scenario with one eavesdropper is investigated to show the effectiveness of IRS. To explore the effectiveness of traditional approach in IRS-assisted scenarios, Guan et al. [5] further considered AN in an IRS-assisted system, whose performance was verified with the significant gain on secrecy rate. To improve the algorithm efficiency, Yu et al. [17] proposed an efficient algorithm adopting block coordinate descent and minorization maximization method for faster convergence especially for large-scale IRS. Dong et al. [18] also adopted a similar efficient design for Mutiple-Input Mutiple-Output (MIMO) systems. Lyu et al. [19] considered a potential IRS threat called IRS jamming attack, which can leverage signals from a transmitter by controlling reflected signals to diminish the signal-to-interference-plus-noise ratio at the user. Since the IRS jammer operates in a passive way, it can be even harder to defend. Xu et al. [20] studied resource allocation design in multi-user scenarios and also considered AN at transmitter. However, the aforementioned efforts only focus on the proof-of-concept study by implementing a single IRS. Thus, the security gain from leveraging multiple collabortive IRSs has not been explored yet, and it is also paramount to jointly optimize wireless transmission environments and allocate resources for legitimate users in multiple IRSs-assisted systems.
To enhance transmission the security from users, in this paper, we study secure transmission schemes for multi-user Mutiple-Input Singe-Output (MISO) systems assisted by multiple collaborative IRSs. The main contributions of this paper are summarized as follows.
-
•
To deal with the threat from potential eavesdroppers, we propose a secure communication scheme in multiple IRSs-assisted systems. Considering the security requirement for each legitimate user, we formulate a max-min problem to maximize the lower bound of the secrecy rate to optimize the worst performance of multiple users in case eavesdroppers “steal” useful information from a certain user.
-
•
To solve the formulated max-min problem, we adopt an alternating algorithm to decouple it into multiple sub-problems. In each iteration, we apply Semi-Definite Relaxation (SDR) and Successive Convex Approximation (SCA) method to solve a convex optimization problem.
-
•
To verify the effectiveness of the proposed scheme, extensive numerical evaluations are conducted. Compared with the traditional IRS scheme with beamforming, the results show that the proposed scheme can achieve significant improvement, and the additional AN can improve achievable secrecy rate especially in multi-user scenarios. Moreover, we compare our scheme with the traditional sum-rate problem to show the gap of security performance. With the increase in the number of elements on IRSs, we show that the performance from our scheme converges to that from the sum-rate maximization in terms of sum of secrecy rate.
Symbol Notation: Boldface lowercase and uppercase letters denote vectors and matrices, respectively. For a vector , denotes the Euclidean norm. For matrix , the conjugate transpose, rank and trace of are denoted as , and , respectively. For a complex number , denotes the modulus. denotes the phase of the complex value . The set of -by- real matrices, complex matrices and complex Hermitian matrices are denoted as , and , respectively. means is a positive semidefinite matrix, and denotes the Gaussian distribution with mean and covariance matrix .
II System Model
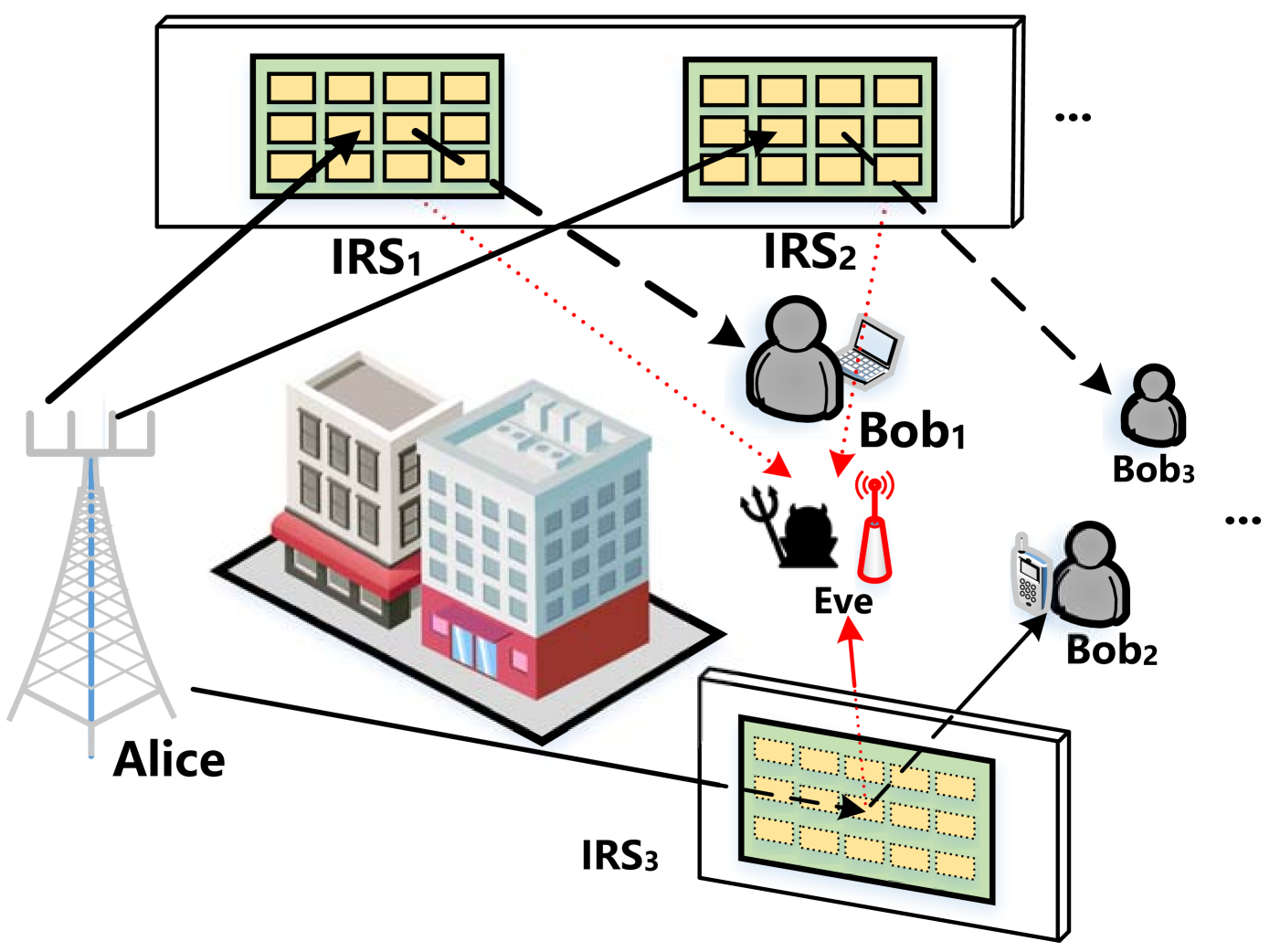
We consider a wireless communication system as shown in Fig. 1, a base station equipped with antennas intends to transmit secure messages to legitimate users equipped with single antenna. Moreover, IRSs have been deployed in advance to assist wireless communications, and each IRS has reflecting elements.
Adversary Model: With respect to the transmitted secure messages, one eavesdropper (Eve) wants to wiretap/intercept transmitted signals, and further crack the secure messages to steal users’ private information or hack users’ equipments. To eliminate the potential threat from the eavesdropper and protect the security of legitimate users, the base station and IRSs need to cooperatively transmit signals to increase received signal power at legitimate users while mitigating the signal leakage at the eavesdropper. In this paper, we attempt to adjust the transmission strategy both at base station and on IRSs to enhance the security level.
Channel Model: There are two parts of a channel experienced from base station to user/Eve, i.e., direct (transmitter-user/Eve) channel and reflecting (transmitter-IRS-user/Eve) channel. The composite reflecting channel is modeled as a combination of three components, i.e., the base station to IRS link, IRS’s reflection with phase shift and IRS to user/Eve link. The equivalent channels from the base station to the -th IRS, the -th user and Eve are denoted by , , , respectively. The equivalent channels from the -th IRS to the -th user and Eve are denoted by , , respectively. Since IRS is a passive reflecting device, we consider a Time Division Duplexing (TDD) protocol for uplink and downlink transmissions and quasi-static flat-fading model (constant within the transmission frame) is adopted for all channels. As discussed in [12, 5, 21], by applying various channel acquisition methods, we can acquire all channel information, and hence here for the current study, we also assume that the Channel State Information (CSI) of all channels are perfectly known. Linear transmit precoding is considered at the base station similar to [13], and each user served by the base station is assigned with one dedicated beamforming vector. To further enhance the physical layer security, additional AN is also adopted. Thus, the signal transmitted from the base station to the -th user can be described as:
| (1) |
where is the beamforming vector for the -th user, is the corresponding transmitted data, and is an AN vector.
Since multiple IRSs have been deployed in the system, each legitimate user can be served by a selected IRS to receive tuned signal, which is effective especially when there exists an obstacle and no Light-of-Sight (LoS) channel between the base station and a user. Let denote the IRS selection for the -th user, i.e., the -th user can receive reflecting signal through the -th IRS if . Meanwhile, let denote the diagonal phase-shifting matrix of the -th IRS, while and denote the amplitude reflection coefficient and the phase shift of the -th element on the -th IRS. In practice, each element of an IRS is usually designed to maximize the signal reflection [13]. Thus, we set in this paper. In this case, for the -th user, the received signal from base station and IRSs can be represented by:
| (2) |
where is the complex Additive White Gaussian Noise (AWGN). For an eavesdropper, the received signal can be represented by:
| (3) |
For notational simplicity, let , . Accordingly, the Signal-to-Noise Ratio (SINR) of received signal at the -th user can be calculated by:
| (4) |
where is the power of AWGN. Similarly, the SINR of the -th user’s signal at the eavesdropper can be calculated by:
| (5) |
III Problem Formulation and Solution
Considering the security requirement for each legitimate user in the system, we want to guarantee the worst performance of all legitimate users in case an eavesdropper might wiretap/intercept too much useful information from a certain user. Thus, in this paper, we aim to maximize the minimum achievable secrecy rate of legitimate users in the system. By jointly configuring the beamforming matrix and AN matrix at the base station, phase shift matrix at IRSs and surface selection matrix between users and IRSs, the optimization problem can be formulated as:
| (6) |
| (C1) | ||||
| (C2) | ||||
| (C3) |
where (C1) represents the transmission power constraint, (C2) implies the unit modulus for each element, i.e., , and (C3) indicates that each user should be served by one IRS in the system. Considering the SINR expression in (4), (5) and applying the Shannon capacity theorem, the achievable secrecy rate (bits/s/Hz) in (6) can be calculated by:
| (7) |
It is intuitive that variables , , and in Problem 1 are coupled, which makes Problem 1 hard to solve. However, if only one variable is considered, the original problem becomes solvable. Inspired by the alternating optimization approaches in [5, 17, 18, 19, 20, 13, 22], we adopt Block Coordinate Descent (BCD) method to decouple variables and obtain the sub-optimal solution efficiently. To optimize a multi-variable objective in BCD method, we optimize the objective in terms of one of the coordinate blocks while the other blocks are fixed at each iteration. Thus, Problem 1 is divided into three sub-problems and each sub-problem is solved iteratively as descried in Algorithm 1. For each sub-problem, we utilize SDR and SCA to convert the original problem into a convex problem. The detailed solving process of each sub-problem is descried in the following sub-sections.
-
•
Initialize , , and ;
-
•
, ;
| (8) | |||
| (9) | |||
| (10) |
III-A Sub-Problem for Beamforming and AN
At first, beamforming and AN matrices are considered to be solved. For given phase shift operation and surface matching , with , we can rewrite Problem 1 as:
| (11) |
| (C1) |
Due to the max function in (11), we can rewrite the objective as
| (12) |
where and denote the solution space for non-positive and positive values, respectively. Once is non-empty, the optimal solution must satisfy . In this case, we can rewrite (11) as when .
To solve this sub-problem for beamforming and AN, we plan to apply SDR in the next. So we start to reformulate the objective with some mathematical transformations. Let , , , , . Then, the achievable secrecy rate can be reformulated as:
| (13) |
where , , and are represented by:
| (14) | |||
| (15) | |||
| (16) | |||
| (17) |
However, the secrecy rate in (13) is still in the form of Difference of Convex (DC) functions. To solve the DC problem in (13), we adopt SCA method [23, 24, 20, 25] to obtain a convex upper bound for the DC objective in an iterative manner. At first, we construct global upper bound of and , respectively. For any feasible solution , the differentiable convex functions and satisfy the following inequalities111Since and are concave functions, according to the definition of concave function, we have . In this case, we can construct global upper bound as [26, Proposition 1.8].:
| (18) | ||||
| (19) |
where the right hand side terms in (18) and (19) are global upper bound of and by using first-order Taylor approximation, respectively. The gradients of functions and with respect to and are given in (8)-(10). Hence, a convex lower bound of objective function in (13) can be obtained as . Let and . Since according to (18) and (19), as long as we guarantee , must be satisfied.
After deploying SCA, the objective function becomes convex. In order to further solve the max-min problem, we also introduce an auxiliary variable into the formulation. By doing so, the original Problem 2a can be transformed to:
| (20) |
| (C1) | ||||
| (C4) | ||||
| (C5) | ||||
| (C6) |
where . Since constraint (C5) is non-convex, we drop this rank-1 constraint by applying SDR. If the obtained solution are of rank-1, they can be written as and , then the optimal beamforming vector and AN can be obtained by applying eigenvalue decomposition. Otherwise, we can adopt Gaussian Randomization to recover and approximately from higher rank solution [27, 28, 29]. In this case, Problem 2b becomes a convex optimization problem. In Algorithm 2, Problem 2b can be efficiently solved at each iteration by using convex optimization solvers, e.g., SeduMi and CVX [30, 31]. In the following, we prove that SCA-based approach in Algorithm 2 can reach the optimal solution at each iteration.
Proposition 1.
Proof.
For notational convenience let and . The constraint (C4) can be rewritten as .
According to (18) and (19), we can obtain . Since constraints (C1), (C4) and (C6) are always satisfied, the optimal solution of the approximated problem (20) at the -th iteration always belongs to the feasible set of the original problem (11) At each iteration, it follows that [32, 33]:
where the second inequality holds because is the global optimum of (20) at the -th iteration, and the last equality holds because . This means that is a monotonically increasing sequence. As the actual objective value in (20) is nondecreasing after every iteration, Algorithm 2 will eventually converge to a point as increases.
Next, we prove that satisfies the KKT conditions of the original problem. From (20), the optimal solution can be found when , thus, Problem 2b can be rewritten as:
| (21) |
Then, the Lagrangian for (21) is:
where is the Lagrangian multiplier for each constraint. Similar to (20), by adopting mathematical transformations and introducing auxiliary variable , the Lagrangian for the original problem (11) can be written as:
For a feasible point obtained from Algorithm 2 at the -th iteration, it is the global optimum for (21), the KKT conditions of (21) must be satisfied, i.e., is feasible for (21) and there exist nonnegative real values satisfying:
Since the gradient of the first-order Taylor approximations and are the same as and , we can also verify that:
which implies that satisfies the KKT conditions for (11). The results imply that the KKT conditions of the original problem will be satisfied after the series of approximations converges to the point . This completes the proof.
∎
-
•
Initialize , , , ;
III-B Subproblem for Phase Shift
For given beamforming matrix , AN matrix and surface selection matrix , we can rewrite Problem 1 as:
| (22) |
| (C2) |
Next, similar to the procedures in the previous section III-A, we also transform the objective function to a solvable convex function by applying SDR and SCA. Let 222This is due to when matrix and . Thus, transmitter-IRS-user channel gives ., . Let , , and . Then, the power of received signal at the -th user in (4) becomes:
Accordingly, the power of the received signal of the -th user at the eavesdropper in (5) becomes:
Furthermore, let , and , . Thus, we have . Let , , , . Also, let , , . Then, the achievable secrecy rate in (III) can be reformulated as:
| (23) |
Note that , and . Define , which needs to satisfy and . Note that , , , . Then (III-B) can be further reformulated as:
| (24) |
where , , and are:
| (25) | |||
| (26) | |||
| (27) | |||
| (28) |
Similarly, we apply the SDR method to remove rank-one constraint and SCA method to construct global upper bounds of and and make (24) become convex function:
| (29) | ||||
| (30) |
Thus, Problem 3a is transformed into a convex problem by introducing auxiliary variable :
| (31) |
| (C2) | ||||
| (C7) | ||||
| (C8) |
To restore the desired solution from the convex Semi-Definite Programming (SDP) solution , eigenvalue decomposition with Gaussian randomization can be used to obtain a feasible solution based on the higher-rank solution obtained by solving Problem 3b. Since unit modulus constraint (C2) for each element on IRS should be satisfied, the reflection coefficients can be obtained by [13, 5]:
| (32) |
where denotes the phase of and the obtained solution can satisfy .
III-C Subproblem for Surface Selection
For given beamforming vector , AN vector and phase shift of IRS , the original problem becomes a 0-1 integer programming problem, and we can rewrite Problem 1 as:
| (33) |
| (C3) |
At first, according to the constraint described in (C3), each user is served by one specific IRS, and thus, we have when and . Then, we can simplify the expression in (4) and the power of the received signal at the -th user becomes:
| (34) |
where , , , . Similarly, the power of the received signal for the -th user at eavesdropper in (5) can be expressed as:
| (35) |
Furthermore, let , . In this case, the achievable secrecy rate in (III) can be reformulated as:
where , , and are represented by:
| (36) | |||
| (37) | |||
| (38) | |||
| (39) |
In order to solve this subproblem, we first relax integer variable , then we solve the problem by using convex optimization. After rounding the relaxed solution, we can get feasible for Problem 4a. Similarly, we adopt the SCA method to construct global upper bounds of and :
| (40) | ||||
| (41) |
where . Thus, Problem 4a can be transformed into a convex problem by introducing auxiliary variable :
| (42) |
| (C9) | ||||
| (C10) |
In this case, Problem 4b becomes a general convex problem.
IV Numerical Evaluation
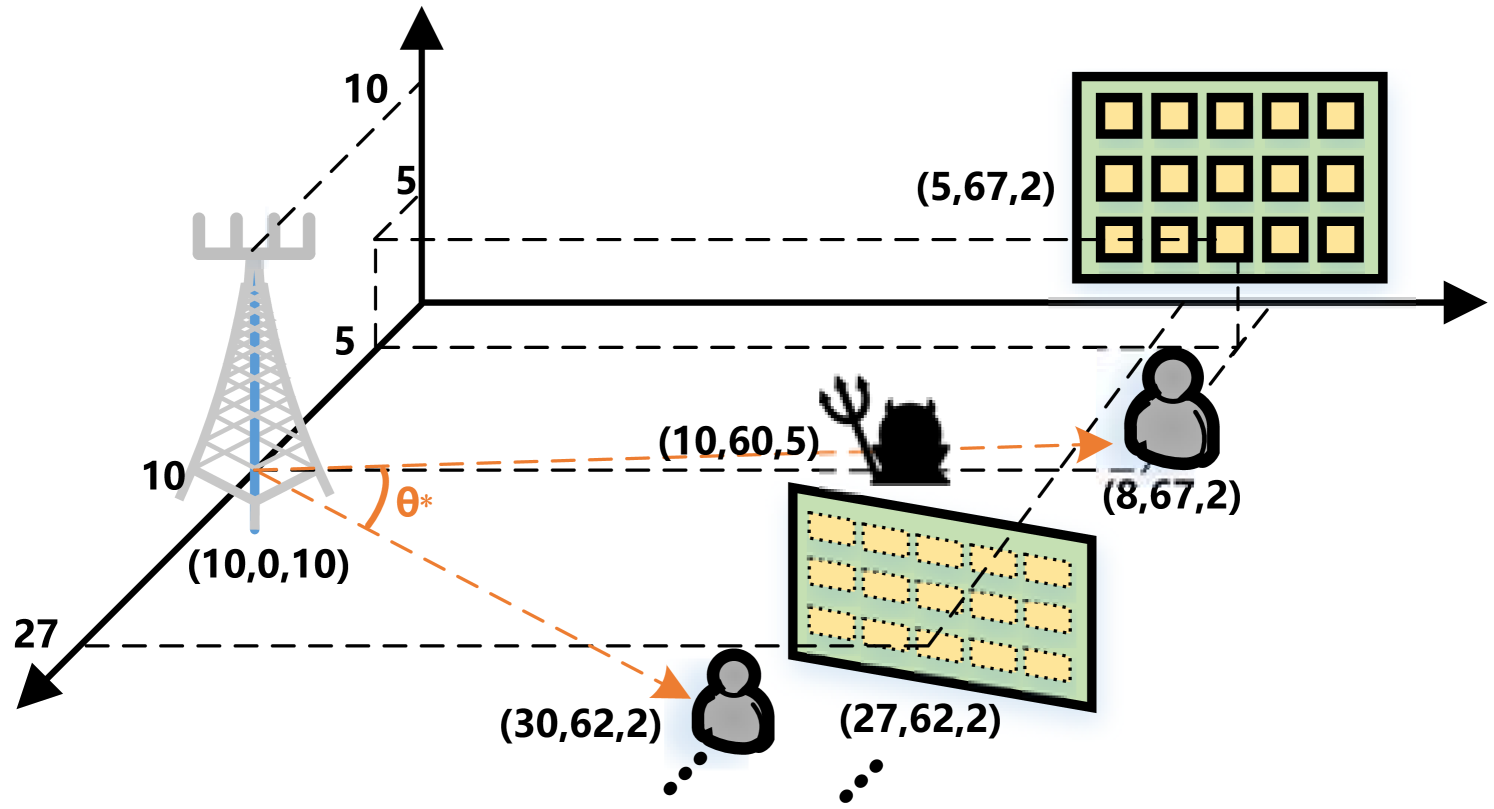
To evaluate the performance of the proposed scheme, we conduct a number of numerical evaluations in this section. The overall setup is shown in Fig. 2, we consider the base station is located at (10, 0, 10), IRSs and legitimate users are uniformly distributed around base station with a constant angle . The first user and IRS are located at (5, 67, 5) and (8, 67, 2), respectively. Eve is located at (10, 60, 5) where in the middle between the base station and the first user. We also assume that the direct channel between the base station and users are blocked by obstacles, which implies the channel state of the base station and a user is much worse than the channel state between the IRS and the user. Specifically, the channels from base station to IRS/users/Eve are assumed to follow the distance-dependent path loss model, which can be generated by , where denotes the distance from location to location , and is the small-scale fading component with Rician fading [34, 35]:
| (43) |
where and represent the deterministic Line-of-Sight (LoS) and Rayleigh fading/Non-LoS (NLoS) components, respectively. The LoS components are expressed as the responses of the -elements uniform linear array . The array response of an N-element IRS can be calculated by:
where and are the inter-antenna separation distance at the transmitter and receiver, and are the LoS azimuth at the base station and the IRS, and and are the angle of departure at the base station and the angle of arrival at the IRS, respectively. The rest of parameter settings are listed in Table I. Two baselines below are considered:
-
•
Baseline 1: Only beamforming is considered at the base station, and the IRS is not deployed in the system.
-
•
Baseline 2: Beamforming is considered at the base station, and only one IRS is deployed in the system.
| Parameter | Value |
| Carrier frequency | 2 GHz |
| IRS configuration | Uniform rectangular array with 5 elements in a row and N/5 columns with spacing |
| Path loss exponent | , , respectively |
| Rician channel factor | , , respectively |
| Path loss at 1 meter | |
| Other parameters | dBm, Tx = 4, , |
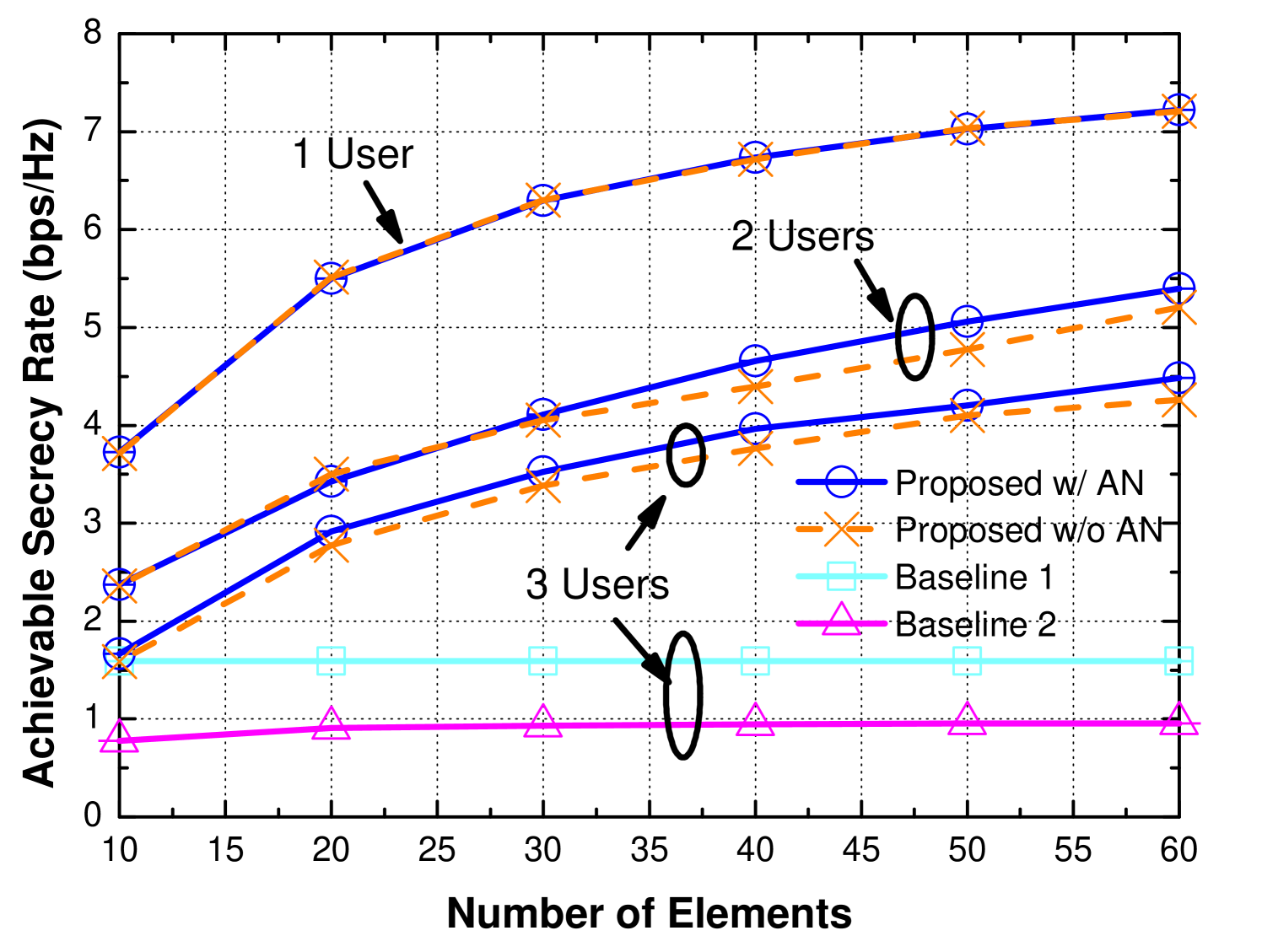
Fig. 3 shows the influence of different number of reflecting elements on each IRS. Due to the existence of obstacles, the LoS component is relatively poor for wireless transmissions between the base station and the user. When only one user is considered, the proposed scheme with AN has almost the same performance as the one without AN, which is is also verified in [13]. When there are 2 or more users, additional AN can help improve secrecy rate about 4-6% especially with the increase in . Without the assistance of IRS and AN, baseline 1 has the worst performance compared with other schemes since the direct channel between the base station and the user is blocked. For fair comparison, we change for the beamforming scheme. The result also shows that the performance of beamforming scheme is relatively poor when there are multiple users. For baseline 2, since users are distributed further apart from each other, only one IRS cannot satisfy the requirement for secure communications.
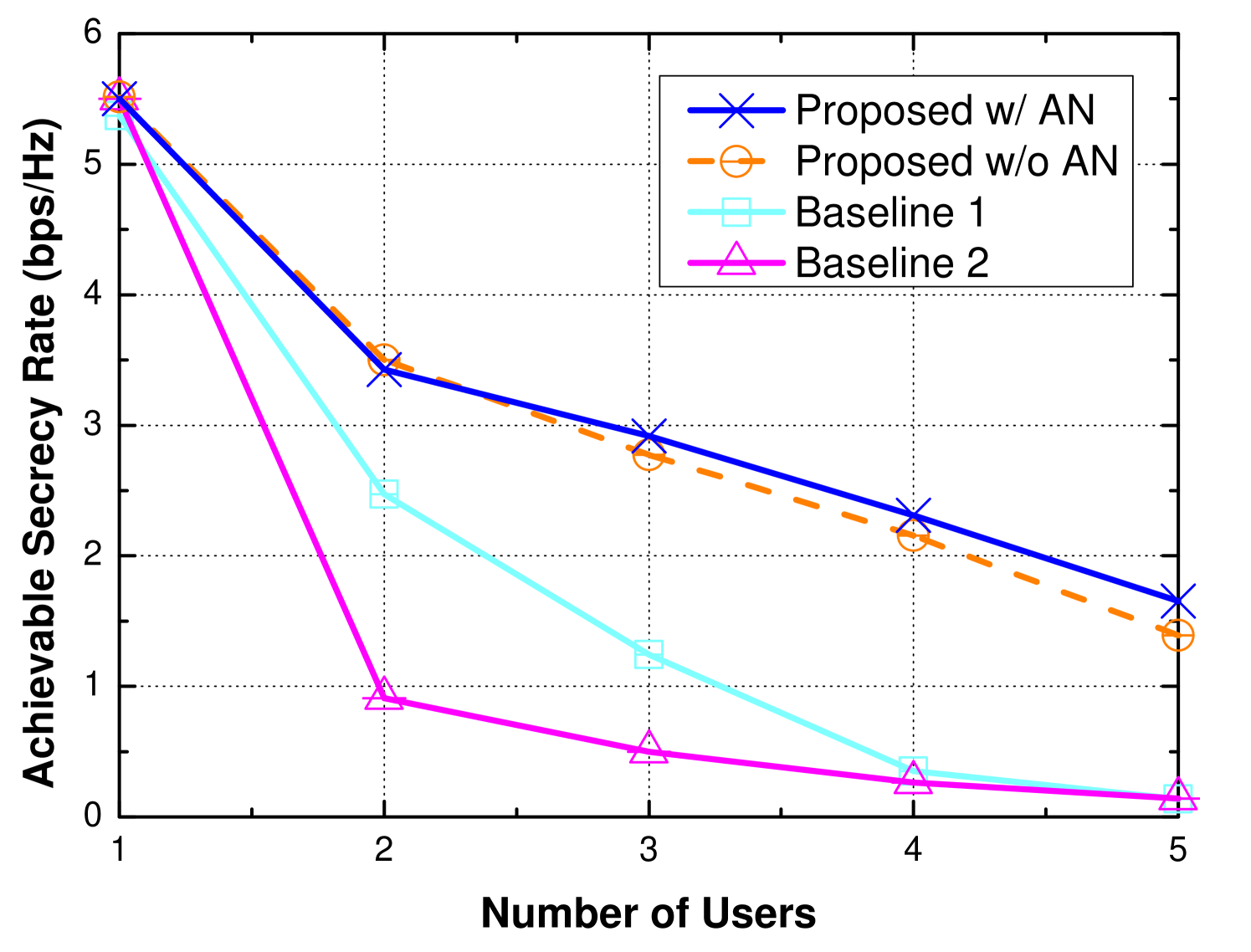
The achievable secrecy rate versus the number of users is shown in Fig. 4. As we observe, the performance of all schemes in terms of achievable secrecy rate are degrading rapidly with the increase in the number of users. When there are more than 2 users, the proposed scheme perform better than AN-disabled scheme by up to 18.9%. Here, for a fair comparison, we also set in baseline 1. The result also shows that the beamforming scheme in baseline 1 cannot deal with multiple users scenarios. Moreover, since the distance between the IRS and users significantly influences the performance of IRS-assisted schemes, we also set up a friendly scenario for baseline 2, i.e., all users are uniformly placed on the line from (8, 67, 2) to (8, 75, 2). When only a single IRS is deployed, the performance becomes even worse than that for baseline 1. The reason is that the environmental diversity provided by the IRS is very limited. If the overall performance is considered, e.g., the sum of secrecy rate, the system still can sacrifice a part of users’ performance to achieve a better overall performance. If the worst performance in the system is considered as the objective, it becomes hard to optimize since each user matters. In this case, the algorithm tends to sacrifice the users who have the highest secrecy rate and make up for the users who have the worst secrecy rate, but the compensation is not significant enough due to the lack of environmental diversity. In this case, a poor performance is observed.
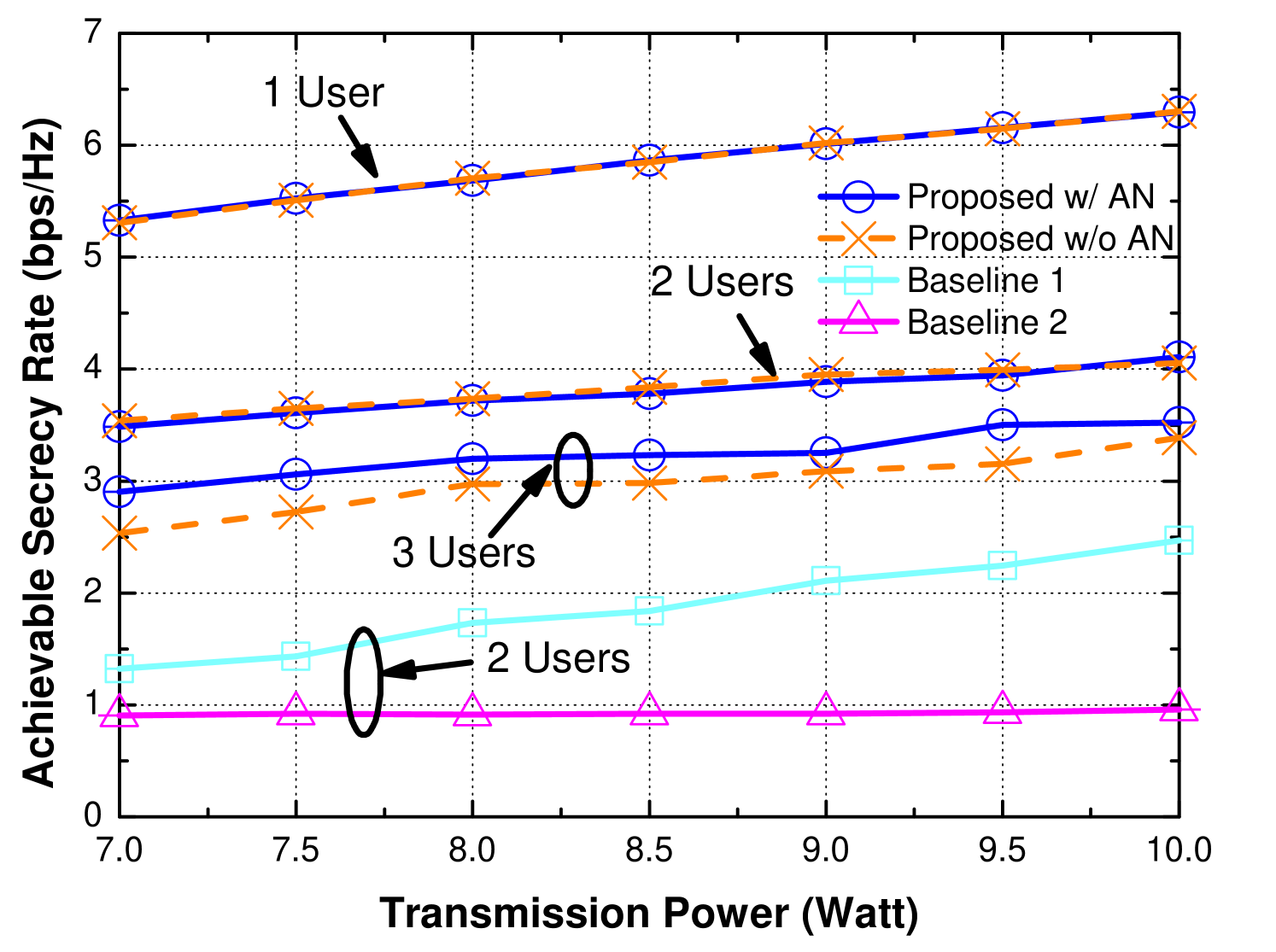
The performance of achievable secrecy rate versus transmission power is shown in Fig. 5. The maximum transmission power ranges from 7W (38.45dBm) to 10W (40dBm). With the increase in transmission power, the performance of all schemes increase linearly. Similar to the results in Fig. 4, the proposed scheme outperforms the AN-disabled scheme when there are more than 2 users in the system. To have a fair comparison, we also consider LoS channel is not blocked by obstacle and set for baseline 1 with 2 users. However, the result shows that the performance of baseline 1 is much lower than IRS-assisted schemes. For baseline 2, since the performance is mainly limited by environmental diversity, it remains relatively steady and increases linearly from 0.9bps/Hz to 0.96bps/Hz with the increase in transmission power.
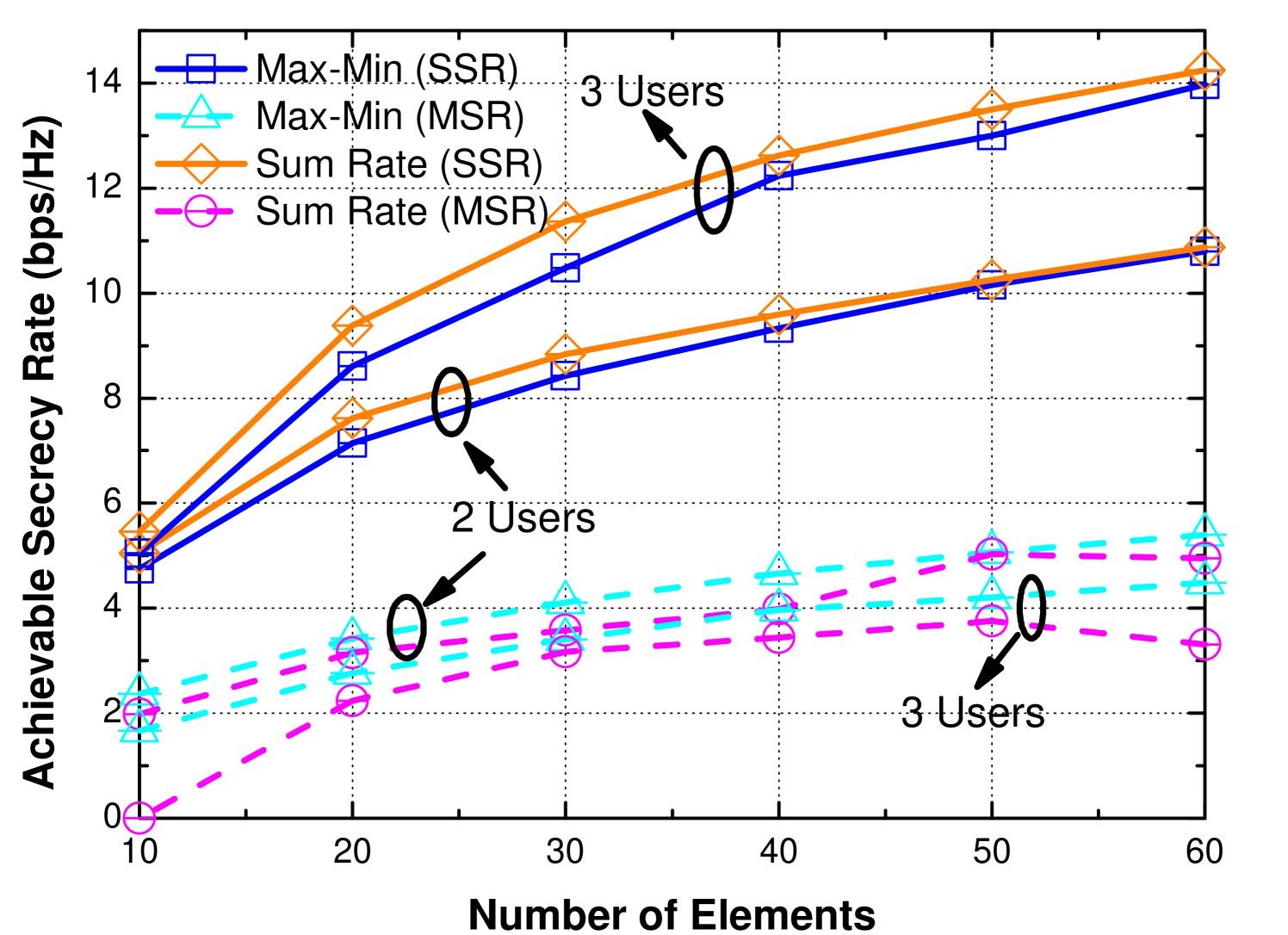
In general, overall security performance is a common objective considered in related works. To compare the performance of the max-min problem proposed in this paper with the commonly studied sum-rate maximization, we plot Fig. 6-7 to show the difference in terms of the minimum secrecy rate and the sum of secrecy rate, where the problem in (6) with constraints (C1)-(C3) can be reformulated as:
| (44) |
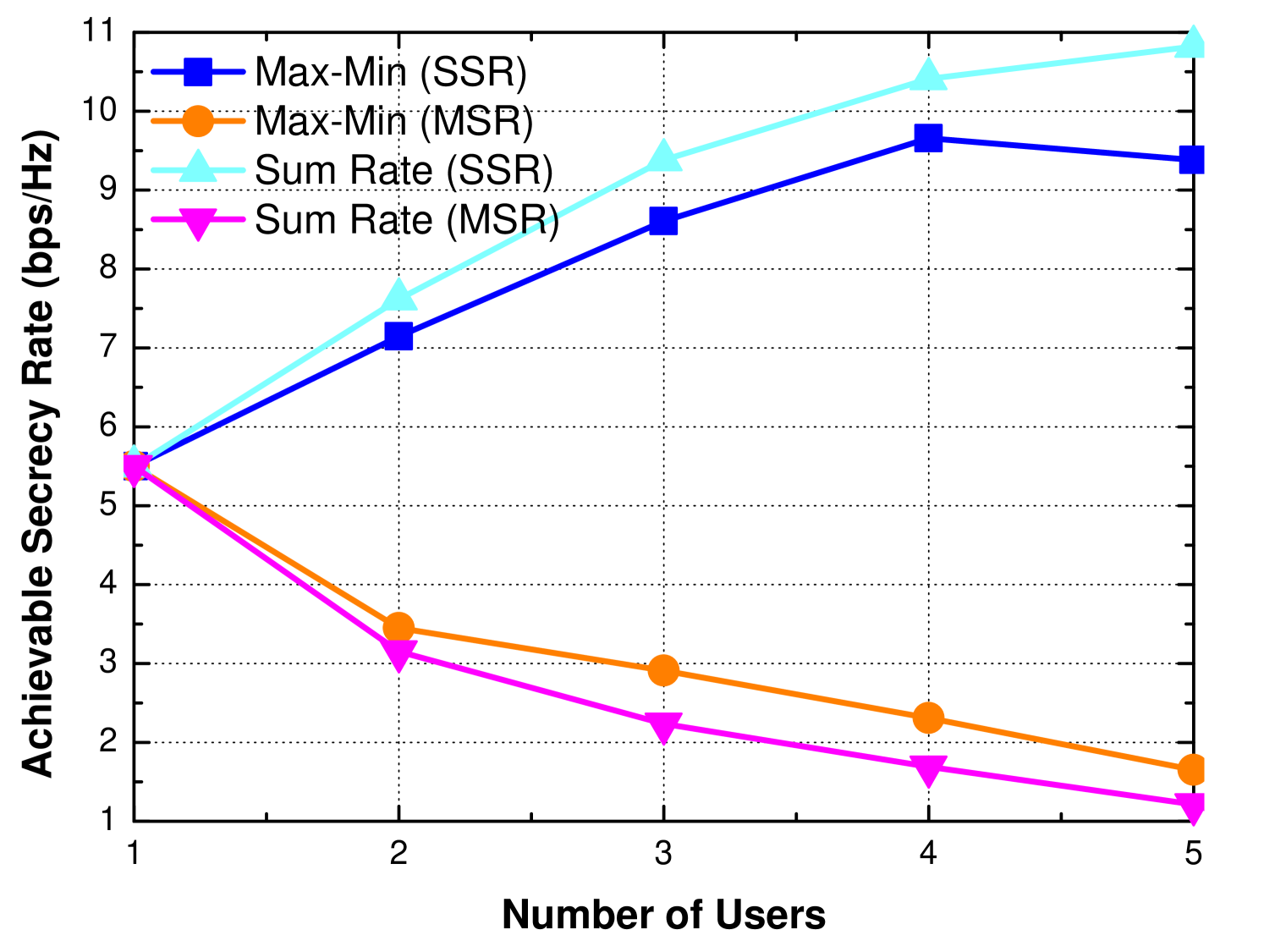
Note that “MSR” and “SSR” in the legend represent the minimum secrecy rate and the sum of secrecy rate, respectively. As shown in Fig. 6, for the performance in terms of the minimum secrecy rate, the gap between two objectives can vary rapidly with different number of elements, especially for the scenarios with more users, which implies that sum-rate objective can hardly guarantee the worst secrecy rates for different users. For the performance in terms of the sum of secrecy rate, with the increase in the number of elements, the overall sum of secrecy rates of these two objective tends to converge and have similar performance. This phenomenon indicates that a max-min problem can achieve better minimum secrecy rate and also reach similar performance in overall secrecy rate for a large-scale IRS-assisted system. Meanwhile, in Fig. 7, the sum of secrecy rate increases with the number of users. Even though it can sacrifice some users’ performance to improve overall performance, the curve shows that the gain becomes less and the sum secrecy rate reaches a threshold with the increase in the number of users, which represents the maximum secrecy capacity in the system. For the gap between two different objectives, it also becomes larger with the increase in the number of users, which is reasonable since the solution space becomes larger with more users in the system, and different solutions obtained from the aforementioned objectives do impact more users.
V Conclusion
In this paper, we have focused on physical layer security in wireless systems with IRSs, and investigated a max-min problem regarding secrecy rate under one typical eavesdropper scenario. By placing multiple collaborative IRSs in complex environment, the base station could leverage the environmental diversity to achieve significant improvement in terms of secrecy rate through joint optimization of beamforming and phase shift on the IRS. Based on our numerical evaluation, when multiple users are considered, the additional AN has been proven to effectively create interference at the eavesdropper and further improve the performance in terms of secrecy rate. Compared with sum-rate maximization studied in related works, we have found out that the performance of the proposed max-min problem converges to that of sum-rate problem in terms of the sum of secrecy rate when increasing the number of elements on IRSs. In the future, we plan to extend our study by considering a general adversary model and explore the specific collaborative protocols/mechanism among multiple IRSs.
References
- [1] M. Chraiti, A. Ghrayeb, and C. Assi, “Achieving full secure degrees-of-freedom for the MISO wiretap channel with an unknown eavesdropper,” IEEE Transactions on Wireless Communications, vol. 16, no. 11, pp. 7066–7079, 2017.
- [2] Q. Li, M. Hong, H.-T. Wai, Y.-F. Liu, W.-K. Ma, and Z.-Q. Luo, “Transmit solutions for MIMO wiretap channels using alternating optimization,” IEEE Journal on Selected Areas in Communications, vol. 31, no. 9, pp. 1714–1727, 2013.
- [3] X. He and A. Yener, “MIMO wiretap channels with unknown and varying eavesdropper channel states,” IEEE Transactions on Information Theory, vol. 60, no. 11, pp. 6844–6869, 2014.
- [4] H.-M. Wang, X. Zhang, Q. Yang, and T. A. Tsiftsis, “Secure users oriented downlink MISO NOMA,” IEEE Journal of Selected Topics in Signal Processing, vol. 13, no. 3, pp. 671–684, 2019.
- [5] X. Guan, Q. Wu, and R. Zhang, “Intelligent reflecting surface assisted secrecy communication: Is artificial noise helpful or not?” IEEE Wireless Communications Letters, 2020.
- [6] Y. Zou, J. Zhu, X. Wang, and V. C. Leung, “Improving physical-layer security in wireless communications using diversity techniques,” IEEE Network, vol. 29, no. 1, pp. 42–48, 2015.
- [7] Y.-S. Shiu, S. Y. Chang, H.-C. Wu, S. C.-H. Huang, and H.-H. Chen, “Physical layer security in wireless networks: A tutorial,” IEEE wireless Communications, vol. 18, no. 2, pp. 66–74, 2011.
- [8] F. Zhu, F. Gao, M. Yao, and H. Zou, “Joint information-and jamming-beamforming for physical layer security with full duplex base station,” IEEE Transactions on Signal Processing, vol. 62, no. 24, pp. 6391–6401, 2014.
- [9] F. Zhu and M. Yao, “Improving physical-layer security for CRNs using SINR-based cooperative beamforming,” IEEE Transactions on Vehicular Technology, vol. 65, no. 3, pp. 1835–1841, 2015.
- [10] M. Di Renzo, A. Zappone, M. Debbah, M.-S. Alouini, C. Yuen, J. de Rosny, and S. Tretyakov, “Smart radio environments empowered by reconfigurable intelligent surfaces: How it works, state of research, and road ahead,” arXiv preprint arXiv:2004.09352, 2020.
- [11] M. Di Renzo, M. Debbah, D.-T. Phan-Huy, A. Zappone, M.-S. Alouini, C. Yuen, V. Sciancalepore, G. C. Alexandropoulos, J. Hoydis, H. Gacanin et al., “Smart radio environments empowered by reconfigurable ai meta-surfaces: An idea whose time has come,” EURASIP Journal on Wireless Communications and Networking, vol. 2019, no. 1, pp. 1–20, 2019.
- [12] Q. Wu and R. Zhang, “Towards smart and reconfigurable environment: Intelligent reflecting surface aided wireless network,” IEEE Communications Magazine, 2019.
- [13] ——, “Intelligent reflecting surface enhanced wireless network via joint active and passive beamforming,” IEEE Transactions on Wireless Communications, vol. 18, no. 11, pp. 5394–5409, 2019.
- [14] L. Zhang, L. Yan, B. Lin, H. Ding, Y. Fang, and X. Fang, “Augmenting transmission environments for better communications: tunable reflector assisted mmwave wlans,” IEEE Transactions on Vehicular Technology, vol. 69, no. 7, pp. 7416–7428, 2020.
- [15] L. Zhang, L. Yan, B. Lin, Y. Fang, and X. Fang, “Tunable reflectors enabled environment augmentation for better mmwave wlans,” in 2019 IEEE/CIC International Conference on Communications in China (ICCC). IEEE, 2019, pp. 7–12.
- [16] M. Cui, G. Zhang, and R. Zhang, “Secure wireless communication via intelligent reflecting surface,” IEEE Wireless Communications Letters, vol. 8, no. 5, pp. 1410–1414, 2019.
- [17] X. Yu, D. Xu, and R. Schober, “Enabling secure wireless communications via intelligent reflecting surfaces,” arXiv preprint arXiv:1904.09573, 2019.
- [18] L. Dong and H.-M. Wang, “Secure MIMO transmission via intelligent reflecting surface,” IEEE Wireless Communications Letters, 2020.
- [19] B. Lyu, D. T. Hoang, S. Gong, D. Niyato, and D. I. Kim, “IRS-based wireless jamming attacks: When jammers can attack without power,” arXiv preprint arXiv:2001.01887, 2020.
- [20] D. Xu, X. Yu, Y. Sun, D. W. K. Ng, and R. Schober, “Resource allocation for secure irs-assisted multiuser MISO systems,” in 2019 IEEE Globecom Workshops (GC Wkshps). IEEE, 2019, pp. 1–6.
- [21] B. Zheng and R. Zhang, “Intelligent reflecting surface-enhanced ofdm: Channel estimation and reflection optimization,” IEEE Wireless Communications Letters, vol. 9, no. 4, pp. 518–522, 2019.
- [22] J. Li, K. Xue, D. S. Wei, J. Liu, and Y. Zhang, “Energy efficiency and traffic offloading optimization in integrated satellite/terrestrial radio access networks,” IEEE Transactions on Wireless Communications, vol. 19, no. 4, pp. 2367–2381, 2020.
- [23] M. Razaviyayn, “Successive convex approximation: Analysis and applications,” 2014.
- [24] Y. Sun, D. W. K. Ng, Z. Ding, and R. Schober, “Optimal joint power and subcarrier allocation for full-duplex multicarrier non-orthogonal multiple access systems,” IEEE Transactions on Communications, vol. 65, no. 3, pp. 1077–1091, 2017.
- [25] A. Alvarado, G. Scutari, and J.-S. Pang, “A new decomposition method for multiuser DC-programming and its applications,” IEEE Transactions on Signal Processing, vol. 62, no. 11, pp. 2984–2998, 2014.
- [26] M. Simchowitz, “Course notes for ee227c (spring 2018): Convex optimization and approximation,” 2018.
- [27] Z.-Q. Luo, W.-K. Ma, A. M.-C. So, Y. Ye, and S. Zhang, “Semidefinite relaxation of quadratic optimization problems,” IEEE Signal Processing Magazine, vol. 27, no. 3, pp. 20–34, 2010.
- [28] W.-K. K. Ma, “Semidefinite relaxation and its applications in signal processing and communications,” IEEE SIGNAL PROCESSING MAGAZINE, vol. 1053, no. 5888/10, 2010.
- [29] W.-K. Ma, “Semidefinite relaxation and its applications in signal processing and communications,” MIIS Tutorial, July 2012.
- [30] “SeDuMi Software,” http://sedumi.ie.lehigh.edu/, accessed September 1, 2020.
- [31] M. Grant and S. Boyd, “CVX: Matlab software for disciplined convex programming, version 2.1,” 2014.
- [32] A. A. Nasir, D. T. Ngo, X. Zhou, R. A. Kennedy, and S. Durrani, “Joint resource optimization for multicell networks with wireless energy harvesting relays,” IEEE Transactions on Vehicular Technology, vol. 65, no. 8, pp. 6168–6183, 2015.
- [33] T. Wang and L. Vandendorpe, “Successive convex approximation based methods for dynamic spectrum management,” in 2012 IEEE International Conference on Communications (ICC). IEEE, 2012, pp. 4061–4065.
- [34] H. Han, J. Zhao, D. Niyato, M. Di Renzo, and Q.-V. Pham, “Intelligent reflecting surface aided network: Power control for physical-layer broadcasting,” arXiv preprint arXiv:1910.14383, 2019.
- [35] Y. Han, W. Tang, S. Jin, C.-K. Wen, and X. Ma, “Large intelligent surface-assisted wireless communication exploiting statistical CSI,” IEEE Transactions on Vehicular Technology, vol. 68, no. 8, pp. 8238–8242, 2019.