Study of Design of Rate-Compatible Polar Codes Based on Non-Uniform Channel Polarization
Abstract
We propose a novel scheme for rate-compatible arbitrary-length polar code construction for the additive white Gaussian noise (AWGN) channel. The proposed scheme is based on the concept of non-uniform channel polarization. The original polar codes can only be designed with code lengths that are powers of two. Puncturing, shortening and extension are three strategies to obtain arbitrary code lengths and code rates for polar codes. There are other ways to design codes with arbitrary length but which have encoding and decoding with higher complexity such as multi-kernel, concatenated codes and specific constructions for Belief propagation (BP) or Successive Cancellation (SC) decoding. In general, the quality of the projected bit channels by these arbitrary-length techniques differs from that of the original bit channels, which can greatly affect the performance of the constructed polar codes. The proposed Non-Uniform Polarization based on Gaussian Approximation (NUPGA) is an efficient construction technique for rate-compatible arbitrary-length polar codes, which chooses the best channels (i.e., selects the positions of the information bits) by re-polarization of the codeword with desired length. A generalization of the Gaussian Approximation is devised for both polarization and re-polarization processes. We also present shortening and extension techniques for design polar codes. Simulations verify the effectiveness of the proposed NUPGA designs against existing rate-compatible techniques.
Index Terms:
Channel Polarization, Non-uniform Polarization, Re-polarization, Arbitrary-length, Rate-Compatible, Polar Codes.I Introdution
Polar codes, introduced by Arikan [1], were proved to achieve the symmetric capacity of binary input symmetric discrete memoryless channels (B-DMCs) under a Successive Cancellation (SC) decoder as the codelength goes to infinity. The block error rate converges to zero as the code length goes to infinity. Polar codes are based on the phenomenon of channel polarization. The channel polarization theorem states that, as the codelength goes to infinity, the polarized bit-channels become either a noiseless channels or pure noise channels. The information bits are transmitted over the noiseless bit-channels and the pure noise bit-channels are set to zero (frozen bits). The construction of a polar code involves the identification of channel reliability values associated to each bit to be encoded. This identification can be performed for a code length and a specific signal-to-noise ratio. Therefore, polar code construction refers to selecting an appropriate frozen bit position pattern and several polar code construction algorithms have been proposed. Polar codes were recently selected by the 3GPP group as the channel codes for the upcoming 5th generation mobile communication standard (5G) uplink/downlink control channel [2].
In the construction of polar codes, we recall that the code length of standard polar codes is limited to powers of two, i.e., , however, the code length flexibility is required for practical applications. There are several construction techniques applied in the standard polar code model proposed by Arikan [1] considering the SC decoder. Among the most well-known polar codes construction techniques are the Bhattacharyya-based approach, proposed by Arikan [1], the Density Evolution (DE) schemes of Mori [3][4] and Tal [5], the Gaussian Approximation (GA) technique of [6] and the Polarization Weight (PW) algorithm [7]. The Bhattacharyya parameter-based approach was proposed along with Monte-Carlo (MC) simulations to estimate bit channel reliabilities [1]. The MC method needs to estimate the average error probability of each bit-channel via simulations. Therefore, encoding and SC decoding are required in each simulation. In the DE method, we need to compute the probability density function (PDF) of the log-likelihood-ratio (LLR) of each channel first and then choose the channels that are most likely to be correct. Since DE includes function convolutions, its precision is limited by the complexity. Similar to the MC method, the DE method has high computational cost. Extending the ideas of [3] and [4], Tal [5] devised two approximation methods by which one can get upper and lower bounds on the error probability of each bit-channel using efficient schemes of degrading and upgrading quantization. A bit-channel reliability estimation method for AWGN channels based on DEGA has been proposed in [6], giving accurate results with a significant reduction in complexity if compared with DE. The PW algorithm [7] is a recent attempt to study the partial order (PO) [8] for designing universal polar codes, which performs as well as GA but with much lower complexity. An important characteristic of polar codes is that the channel orderings are channel-dependent. PO is based on the observation that the channel orderings are degraded according to the binary expansion of their indexes. Therefore, in this method the channel orderings are not channel-dependent. PO provides us with quality information for all channels. This can be used to simplify code construction of polar codes. In [9] and [10] a comparative study of the performance of polar codes constructed by various techniques using the AWGN channel and SC decoder has been carried out. Construction of polar codes based on the AWGN channel and GA have been reported in [11] and [12]. In [9] the design of good polar codes with any construction method has been verified with the SC decoding error rate for various scenarios and polar code construction algorithms. Polar codes can also be constructed and adapted to a specific decoder, for example, construction of polar code for SCL decoding [13] and BP decoding [14][15]. In [16] the authors propose a genetic algorithm framework that jointly optimizes the code construction and rate with a specific decoder.
To obtain code length flexibility, arbitrary kernels and multi-kernel (MK), puncturing, shortening and extension are typically performed. Polarization matrices of various sizes, for example 3x3, 5x5 and 7x7, were used to build a polar code of any length. BCH kernel matrices proposed in [17] and the code decompositions proposed in [18] both have restrictions on the size of the kernel matrices. Square polarizing kernels larger than two have been proposed in [19], [20] and [21], while a polar code construction with mixed kernel sizes has been proposed in [22][23]. By considering different polarizing kernels of alternate dimensions, MK improves block length flexibility. Although the general coding and decoding structure follows the same structure of Arikan’s standard polar codes, there is an increased complexity with the generalization. Polar codes construction using the Reed-Muller (RM) rule [24][25][26] can improve the performance of the error rate.
Various shortening and puncturing methods for polar codes have been reported in [27]-[41]. Generally, puncturing or shortening causes a loss of performance because when the number of bits punctured or shortened increases the code length decreases, degrading the performance. A review on puncturing and shortening techniques can be found in [27], which includes designs based on the column weights (CW) of the generator matrix and the reversal quasi-uniform puncturing scheme (RQUP) based on bit reversed permutation. In practice, the design of the code is made for and rate-compatible code design techniques use a specifically chosen criterion for shortening or puncturing and generate a codeword with length that is . In [28]-[30] puncturing methods have been reported using belief propagation (BP) decoding based on optimization techniques employing retransmission schemes such as Hybrid Automatic Repeat reQuest (HARQ). Different properties of punctured codes have been explored: minimum distance, exponent binding, stop tree drilling, and the reduced generating matrix method [31]-[34]. Schemes that depend on the analysis of density evolution were proposed in [35] and [36]. On the other hand, shortening methods have been studied with SC decoding. In shortening techniques, we freeze a bit channel that receives a fixed zero value. The decoder, however, uses a plus infinity log-likelihood ratio (LLR) for that code bit as it is often assumed that this value is known. The study in [37] proposed a search algorithm to jointly optimize the shortening patterns and set of frozen bits. The work in [38] devised a simple shortening method, reducing the generator matrix based on the weight of the columns (CW). In [39] the reversal quasi-uniform puncturing scheme (RQUP) for reducing the generator matrix has been proposed. The authors in [40] presented a polarization-driven (PD) shortening technique for the design of rate-compatible polar codes, which consists of reducing the generator matrix by relating its row index with the channel polarization. Recently, the PW algorithm has been used in a puncturing and shortening technique reported in [41].
Extension of polar codes have been studied in [42], [43] and [44]. For HARQ schemes it was proposed that an arbitrary number of incremental coded bits can be generated by extending the polarization matrix such that multiple retransmissions are aggregated to produce a longer polar code with extra coding gain. The complexity of the encoder and decoder are similar to that of standard polar codes. Nevertheless, there is a significant increase in complexity when designing flexible-length polar codes by concatenated codes [45], [49] and by asymmetric kernel construction [47]. In both cases the code construction is specific to each kernel dimension without generalization gains. Chained polar subcodes [48] were shown to be an effective method for achieving length compatible polar codes.
In this paper, we present the concept of non-uniform polarization, which allows the construction of rate-compatible polar codes considering the polarization of channels with an arbitrary distribution of the Bhattacharyya parameter. Generalized channel polarization schemes have been proposed in [49] and [50]. In [49] the authors present a rate-matching scheme for multi-channel polar codes, which can be directly applied to bit-interleaved coded modulation schemes. Moreover, in [50] polar coding schemes are introduced for independent parallel channels in which the channel parameters are no longer fixed but exhibit some random behaviors.
The original construction of Arikan [1] considers a single Bhattacharyya parameter to all channels, which we call uniform polarization. We develop a Non-Uniform Polarization technique based on the Gaussian Approximation (NUPGA) for designing rate-compatible polar codes of arbitrary length [54]. We then develop NUPGA-based shortening and extension algorithms for rate-compatible polar code designs. In the proposed techniques the shortened or extended channels are re-polarized for a more efficient choice of noiseless channels. We also present a generalization of the GA algorithm, which is used for both polarization of the initial channel and re-polarization of the shortened channel, and we present a simplified construct technique for extended polar codes. Simulations compare the proposed NUPGA techniques with existing approaches. A key feature of the proposed designs in that, the encoder and decoder structures are the same as that of the original polar codes [1] and require the same complexity.
In summary, the main contributions of this work are:
-
•
a novel NUPGA approach for designing rate-compatible polar codes along with a proof that it achieves capacity;
-
•
NUPGA-based shortening and extension techniques for designing rate-compatible polar codes;
-
•
an extensive simulation study that compares the NUPGA and existing design techniques.
The rest of the paper is organized as follows. In Section II, we present a brief review of the fundamentals of polar codes required for our exposition, outline their notation, and describe their encoding and SC/SCL decoding. In Section III, we review the principles of polarization theory of polar codes. In Section IV, we discuss the non-uniform polarization of polar codes and show that similarly to uniform polarization, it achieves channel capacity. In Section V, we give a detailed description of the proposed NUPGA-based shortening and extension techniques along with the pseudo-codes for their implementation. We present our simulation results in Section VI and the conclusions in Section VII.
II Polar codes
In this section we review some fundamental aspects of polar codes that will help in the exposition of the proposed techniques. Using the notation proposed by Arikan [1], we describe key principles of the encoder and the decoder of polar codes.
Given a B-DMC , where and denote the input and output alphabets, respectively, we define the channel transition probabilities as , , . As demonstrated in [1], after channel combining and splitting operations on independent uses of , we get successive uses of synthesized binary input channels with . represents the most reliable sub-channels. The indices of form the set of information . They are the ones that carry the information bits. The indices of the remaining sub-channels are included in the complementary set , and can be set to fixed bit values, all zeros.
A polar codes scheme is uniquely defined by three parameters: code-length , code-rate and an information set with cardinality . For encode we have , where is the transform matrix, is the source block and is the codeword. The source block is comprised of information bits and frozen bits . The -dimensional matrix can be recursively defined as , where denotes the Kronecker product, and is the bit-reversal permutation matrix, which can be omitted without loss of generality. Then, the codeword is transmitted to the receiver through AWGN channel.
We may adopt the SC decoder so that the information bits are estimated as [1]:
| (1) |
Having known the decoded bits and received sequence , the likelihood ratio (LR) message of , , can be recursively calculated using the SC decoding algorithm [1]. Then, , an estimated value of , can be computed by:
| (2) |
where , , are decision functions defined as:
| (3) |
for , i-1.
The LR output from the node at row and stage is denoted as , according to the decoding tree in [1]. In order to calculate , as proposed in [1], we compute the following equation recursively:
| (4) |
where and functions were defined in [1] as:
| (5) |
| (6) |
Notice that in (6), is the modulo-2 sum of partial previous decoded bits. The term depicts the successive operation in the SC algorithm. The decision on the current bit strongly depends on the estimate of previously decoded bits. A log-likelihood ratio (LLR)-based SC algorithm has been developed in [51] to simplify the design. Accordingly, (5)-(6) in the natural domain are transformed to the following equations in the logarithm domain:
| (7) |
| (8) |
Similar to LDPC decoding, a min-sum approximation [51] can be further employed to reduce the complexity of (7):
| (9) |
where (8)-(9) describe the LLR version of the SC algorithm.
For the sucessive cancelation list (SCL) decoder [52], let denote the set of candidate sequences in the th step of the decoding process, and is the size of . Let be the maximum allowed size of the list and be a threshold for pruning with . The SCL algorithm can be described as follows:
-
•
bits are estimated successively with index ; for each candidate in the list,
-
•
generate two -length sequences for decoding as bit 0 and bit 1 by SC decoding;
-
•
if the number of candidates is not larger than , there is nothing to do;
-
•
otherwise, reserve candidates with the largest probabilities and drop the others from ;
-
•
check each candidate , if , eliminate from .
For sequence estimation, after all the bits are examined, re-encode every candidate in the list and calculate the corresponding likelihood probabilities. Select the one with the maximal probability as the sequence estimate:
| (10) |
III Theoretical aspects of polar codes construction
In this section, we recall the theoretical aspects of the construction of polar codes and show that the channel polarization theory can be generalized to non-uniform channels. In this scenario, the main aspects of the channel polarization theory are maintained, namely, the conservation of the associated channel capacity and the induction to the polarized channel [1].
III-A PC construction
To construct polar codes, it is necessary to find the set of indices for the information bits, . Standard polar codes can have length distinct bit-channels . If , these bit-channels are divided into either noise free or completely noisy channels. To measure the quality of a binary input channel , the Bhattacharyya parameter of , which is indicated by [1] and defined as
| (11) |
where is the channel transitional probability of input alphabet and output alphabet , , . For any binary discrete memoryless channel (BDMC), the reliability of bit-channels can be recursively determined [1], and with the exception of the BEC channel, for all other channels its method of determination is approximate [1], and as seen earlier, several algorithms have been proposed [9]. For example, BEC channels with close to zero are almost noiseless, whereas channels with close to one are almost pure-noise channels. The essential idea is to choose the most reliable bit-channels (noise free channels) to transmit information bits (), while noisy bit channels known to both encoder and decoder are frozen ().
For the construction of arbitrary-length polar codes, a generalization of channel polarization is necessary for the definition of non-uniform polarization, maintaining the primary results of the channel polarization theory. First, we will generalize channel types to see if full capacity is maintained. Then, we will verify if the channel polarization theory is valid for non-uniform channels.
III-B Channel capacity
Consider the discrete memoryless channel (DMC) shown in Fig. 1, where it is seen that the symbol is passed through the DMC designated by the symbol .

The symbol at the input of the DMC can be considered as generated by a discrete random variable . Similarly, the symbol at the output of the channel is modeled by another discrete random variable . Then, a set of DMC channels from Fig. 1 can be shown as in Fig. 2a. The Bhattacharyya parameter is for all DMC channels. Consider the transmission of different symbols through the channel in a serial manner. Consider that these symbols are generated by independent and identically distributed (i.i.d.) random variables. Without loss of generality, we consider that the transmission of each symbol is through each channel separately, as in Fig. 2a. Therefore, the deduction of the system’s capacity will be the same as if we use other channels, that is, non-uniform channels, as suggested in Fig. 2b.
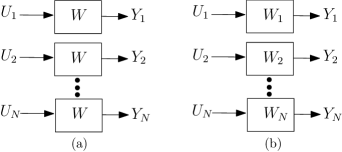
Now, the Bhattacharyya parameter is different for all DMC channels. The mutual information for Fig. 2a and Fig. 2b are shown below.
Let and then the mutual information between U and Y can be written as
| (12) |
If is independent of , , , , then we can write that
Then, (12) can be written as
| (13) |
and let the capacity be , then we have
| (14) |
However, a key concept of channel polarization is that it consists of a method where the channel outputs depend on the other inputs as well. This implies the following inequalities:
That is, (12) cannot be simplified as in (13). In addition, it is necessary to ensure that
| (15) |
which means the individual capacities increase in an orderly manner but the total capacity remains constant, i.e., the total capacity of the channels is maintained, regardless of whether the channels are equal or not, that is, uniform or non-uniform, with different Bhattacharyya parameters. Then, for uniform channels, according to (14), and for non-uniform channels, with the inequality of (15), the capacity of the channels is conserved, and we show that non-uniform polarization schemes achieve symmetric capacity:
| (16) |
Therefore, we can devise methods to construct polar codes that take into account different Bhattacharyya parameters. It is necessary to verify whether the theory of channel polarization [1] converges also for non-uniform channels. In the next sections, we show the main results for channel capacity, channel polarization and polarization convergence. Then, we show that all results remain valid for the case of generalized channels.
III-C Uniform construction
In the classic construction of Arikan [1] the channel polarization considers identical for all channels. Let denote a general symmetric binary input discrete memoryless channel (B-DMC), with input alphabet , output alphabet and the channel transition probability , , . We write to denote the channel corresponding to uses of : thus N N with
| (17) |
The mutual information with equiprobable inputs, or symmetric capacity, is defined by [1]
| (18) |
where the base-2 logarithm is employed, and the corresponding reliability metric, the Bhattacharyya parameter is given by [1]
| (19) |
where . For any B-DMC , we have
| (20) |
Applying the channel polarization transform for independent uses of , after channel combining and splitting operation we obtain the group of polarized channels , , defined by the transition probabilities
| (21) |
where is the code length.
Channel polarization is defined as an operation by which one generates independent copies of a given B-DMC and a second set of channels that show a polarization effect in the sense that, as becomes large, the symmetric capacity terms tend towards or for all but a vanishing fraction of indices .
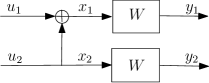
The recursion combines two independent copies of , as shown in Fig. 3, and obtains the channel with the transition probabilities
| (22) |
| (23) |
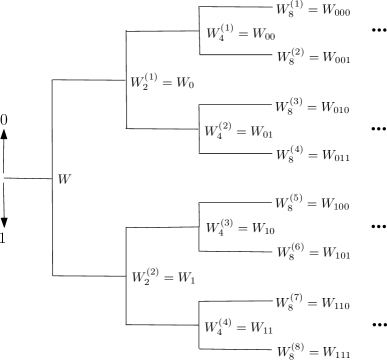
The construction tree used in channel polarization is shown in Fig. 4 [1]. Note that it considers a uniform value of the Bhattacharyya parameter that is represented in the tree by .
For example, we show a set of results for BEC channels. Consider the transformation is rate-preserving and realiability-improving in the sense that [1], and produces as output the following two binary-input DMCs (with larger output alphabets):
| (24) |
and that by definition in (18), we have
| (25) |
where and are iid. From the chain rule, it follows that
| (26) |
and
| (27) |
which results in
| (28) |
For the case of the parameter in the BEC channel we have that the reliability terms further satisfy [1]
| (29) |
| (30) |
The cumulative rate and reliability satisfy [1]
| (31) |
| (32) |
The uniform channel polarization for any set of B-DMCs , , ensures that for arbitrary small there exist polar codes that achieve the sum capacity , in the sense that as , which is a power of 2, the fraction of indices satisfies
| (33) |
where the values of converge to .
IV Proposed Non-uniform Construction
In this section, we show a generalization of the equations presented in Section III.B, and we verify that for non-identical channels, that is, with different Bhattacharyya parameters, they also converge for channel polarization.
If the channels are independent but not uniform, then , as shown in Fig. 5, where we rewrite (17) as
| (34) |
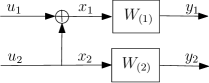
We consider and with the same cardinality and in such a way that their transition probabilities and may differ if . A non-identical channel corresponds to a channel with different Bhattacharyya parameters. As in [1], given any B-DMC the same definitions of the symmetric capacity (18) and the Bhattacharyya parameter (19) are adopted as performance measures, and rewritten as
| (35) |
| (36) |
We notice that the relation in (20) is equivalent and can be rewritten as
| (37) |
where (21) remains valid.
Using the BEC channel again as an example, for a comparison with Section III.B, for the case of the parameter we have:
| (40) |
The reliability terms in (29) and in (30) are rewritten as
| (41) |
| (42) |
| (43) |
The cumulative rate in (31) and the reliability in (32) are then given by
| (44) |
| (45) |

We can show that (26) can be obtained by performing the following operations:
The non-uniform polarization channel for any set of B-DMCs , , for arbitrary small there exist polar codes that achieve the sum capacity , in the sense that as , which is a power of 2, the fraction of indices satisfies
| (46) |
where the values of converge to , which is a novel result related to the established result for uniform channel polarization in (33).
V Proposed NUPGA Design Algorithms
In this section, we describe the proposed NUPGA design algorithms which employ the non-uniform construction. In the proposed NUPGA design algorithms, the tree process for the recursive channel polarization can be redesigned according to Fig.6 without loss of generalization, with the nodes being calculated using the functions described in (29) and (30).
V-A Proposed NUPGA-based shortening
We use the PD shortening technique [40] as a starting point to define the channels that will initially be shortened. We recall that, the purpose of a shortening technique is to reduce the codeword length to , that is . Let denote the number of information bits. Let denote the code length of the basic polar codes, and let denote the code length of the shortened polar codes, where . Let denote the shortening pattern, which is the index set of the shortened bits, and denote the cardinality of shortened bits. The code rate of the shortened codes is . In shortening, the shortened bits of are known at the decoder, such that the LLRs of them can be set to infinity for decoding. Consider that the vector contains the channels obtained by the PD shortening technique [40]. We first generate the codeword by defining the channel in as zero valued (frozen bits). We then reduce the length of the codeword message based on the . Polar codes are characterized by non-universality [1]. In this work, it is adopted the design-SNR equal to zero. As the code has been shortened, the reliability of the bit channels changes and the information set should change accordingly. In this regard, the study in [40] indicates that the order of channel polarization does not change after shortening. For the shortened channels, we consider the parameter penalized a frozen bit, and will be used as input in the NUPGA method.
Under AWGN channels, the LLRs of each subchannel, namely , the estimation of the channel polarization are calculated using the GA [6] algorithm with the following recursions:
| (47) |
where represents the mean of random variable, and
| (48) |
With the generalization we have modified (47) in order to make it applicable to arbitrary code lengths, with and according to Fig.6. This results in the following proposed recursions:
| (49) |
The proposed NUPGA shortening algorithm is described in Algorithm 1. As an example, consider and and initially the scheme without shortening. Then we have that the non-shortened vector is , which is the expected result for . Now consider the shortened vector , which is applied in the operation indicated in step 5 of Algorithm 1. Then, the evolved bit channel capabilities are and the new information set .
V-B Proposed NUPGA-based extension
A simple polar codes extension scheme can be implemented as suggested in Fig.7 [44]. An additional level of polarization is performed in and the information bits . The connection between the additional channels and channels is carried out by the linear polarization sequence of . In the extension scheme the complexity is , less than the puncturing/shortening scheme which is . This scheme is efficient for kernels with low dimension () and for extension of of . Using the proposed NUPGA technique, we can consider all additional bit channels as and as bits output from polarized channels , uniform and limited to the length of the extension. For the encoder we have the same definition, that is, . In the decoder, we have
| (50) |
in the same order.
Note that according to (44), we have
this only happens in the following two cases: either and are noise channel and both of the are equal to 1, or and are both perfect channel such that the two are equal to 0. Using NUPGA, when is perfect and is useless, the two are 1 and 0, respectively. In other words, if the extended bit channel is noise channel and excluding the case that both and are perfect channel, the re-polarization improves the reliability of the shortened channels. With regards to (45), we have
and with the use of NUPGA, we have
and then
which ensures that the extended channels will all be noisy.
This method is similar to the extension of the polarization matrix proposed in [43] and [44]. Note that the construction method for polar codes extension allows us to maintain the same encoder and decoder for codeword N. In the proposed NUPGA Extension algorithm, the original codeword of the channels initially designed is first extended by adding new bits. Thus, it is possible to increase the code length by gradually adding new bits, making it possible to build codewords of any length. The information bit channels are polarized according to the reliability of the bit channel calculated from the new extended channels. The main idea of the proposed NUPGA extension algorithm is to generate the new bit channels as frozen bits and make the associated information bits more reliable than before. The extension length is and the new rate is which can still be decoded efficiently. Therefore, the proposed NUPGA extension algorithm is employed for the design of extension channels. The details of the proposed NUPGA extension algorithm are shown in Algorithm 2.
VI Simulation Results
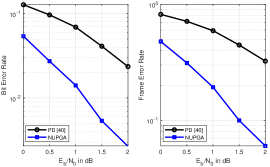
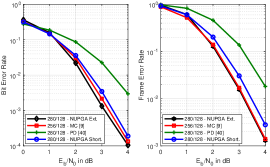
In this section, we evaluate the performance of the proposed NUPGA algorithms described in Section V and compare them with the shortened polar code techniques CW [38], RQUP [39] and PD [40]. We assess the Bit Error Rate (BER) and Frame Error Rate (FER) performances of the polar codes using BPSK for data transmission over an AWGN channel. We consider different shortened codewords, rates and variations of the SC decoder and the SC list (SCL) decoder. In Fig.8 we show the performance of the proposed NUPGA shortening and existing algorithms under the SC decoder as described in [9], whereas Fig.9 shows their performance under SCL [52] with list size . Fig.10 shows the performance of the proposed NUPGA shortening and existing techniques using a Cyclic Redundancy Check (CRC)-aided list decoding (CA-SLC) [52] with list size and CRC with size 24. In Fig.11 we compare the performance of the proposed NUPGA extension algorithm with the PD and NUPGA shortening algorithms with the list decoder.
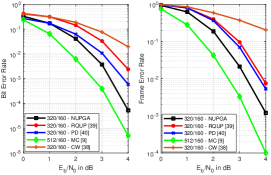
In the first example, in Fig.8, we show the performance of Arikan’s standard polar codes [9] with length , denoted as mother code (MC), and their rate-compatible versions operating at rate with and using the CW [38], RQUP [39], PD [40] and the proposed NUPGA shortening techniques. In Fig.9 we show the performance of codes of length , for the rate-compatible designs and CA-SCL with . In Fig.10 we show the performance of codes of length , , CA-SCL with and CRC with length 24 in a system operating with rate . In Fig.11, we compare the performance of the shortened polar codes and , the proposed NUPGA extension technique with three other curves: with MC [9] of length , the PD [40] algorithm and the proposed NUPGA shortening algorithm under list decoding (CA-SCL) with and CRC with length 24. The results show that the NUPAG extension technique outperforms the NUPGA shortening and the PD algorithms using list decoding with CRC.
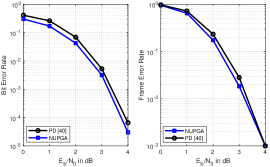
We can observe a performance gain of the NUPGA shortening algorithm in all simulations, and the gain is greater in the case of low rates under list decoding, as shown in Fig.10. In Fig.8 we observe that the performance gain of NUPGA is of the order of 0.5 dB as compared to the approach of CW [38]. In Fig.9, we observe that the gain obtained by NUPGA is less than 0.1dB. In Fig.10 we notice that the gain is up to 1.2dB, which indicates that the NUPGA is advantageous for low rates. In the comparison shown in Fig.11, we observe that the NUPGA extension algorithm achieves a performance improvement over that obtained by the NUPGA shortening algorithm, which is around 0.1 dB. We can see that according to the curves a little incremental extension has good BER performance, maintaining the same FER performance as the original code [9]. Future work will consider the application of NUPGA to detection problems [56, 55, 67, 58, 59, 60, 61, 62, 63, 64, 65, 66, 75, 76, 77, 80, 78, 79, 81].
VII Conclusions
In this work, we have proposed a rate-compatible scheme for constructing arbitrary-length polar codes using a non-uniform channel polarization technique. We have then developed NUPGA-based code design algorithms that exploit the non-uniform channel polarization and the GA technique along with a proof that it achieves capacity. With the proposed NUPGA-based shortening and extension algorithms we can design polar codes for any code length by re-polarizing the length of a conventional polar code. This is in contrast to common schemes like punctured or shortened polar codes. Since the performance of these length-compatible polar codes (including extended, punctured or shortened) deteriorates with the distance to code length of the mother code, our scheme considerably outperforms existing schemes. Simulations illustrate the excellent performance of NUPGA-based designs for short codes.
References
- [1] E. Arikan, “Channel Polarization: A Method for Constructing Capacity-Achieving Codes for Symmetric Binary-Input Memoryless Channels”, IEEE Transactions on Information Theory, vol. 55 no. 7, pp. 3051-3073, July 2009.
- [2] (2018). “Technical Specification Group Radio Access Network” [Online]. Available: http://www.3gpp.org/ftp/Specs/archive/38series/38.212/
- [3] R. Mori and T. Tanaka, “Performance of polar codes with the construction using density evolution”, IEEE Communications Letters, vol. 13, no. 7, pp. 519–521, July 2009.
- [4] R. Mori and T. Tanaka, “Performance and construction of polar codes on symmetric binary-input memoryless channels”, International Symposium on Information Theory (ISIT), 2009, pp. 1496–1500.
- [5] I. Tal and A. Vardy, “How to Construct polar codes”, IEEE Transactions on Information Theory, vol. 59, no. 10, pp. 6562-6582, 2013.
- [6] P. Trifonov, “Efficient design and decoding of polar codes,” IEEE Transactions on Communications, vol. 60, no. 11, pp. 1–7, 2012.
- [7] Y. Ge, R. Zhang, W. Tong, “B-expansion: A Theoretical Framework for Fast and Recursive Construction of Polar Codes”, IEEE Global Communication Conference, 2017.
- [8] C. Schurch, “A partial Order for the Synthesized Channels of a Polar Code”, IEEE International Symposium on Information Theory (ISIT), pp. 220–224, 2016.
- [9] H. Vangala, E. Viterbo and Y. Hong, “A Comparative Study of Polar Code Constructions for the AWGN Channel”, https://arxiv.org/pdf/1501.02473.pdf, Jan 2015.
- [10] J. Li, M. Hu and Z. Cheng, “Research on Polar Code Construction Algorithms under Gaussian Channel”, 2018 Tenth International Conference on Ubiquitous and Future Networks (ICUFN), July 2018.
- [11] D. Wu, Y. Li and Y. Sun, “Construction and Block Error Rate Analysis of Polar Codes Over AWGN Channel Based on Gaussian Approximation”, IEEE Communication Letters, vol. 18, no. 7, Jul 2014.
- [12] H. Li and J. Yuan, “A pratical construction method for Polar Codes in AWGN channels”, IEEE 2013 Tencon - Spring, April 2013.
- [13] P. Yuan, T. Prinz, and G. Bocherer, “Polar Code Construction for List Decoding”, ArXiv e-prints, July 2017.
- [14] M. Qin, J. Guo, A. Bhatia, A. G. i Fabregas, and P. Siegel, “Polar Code Constructions Based on LLR Evolution”, IEEE Commun. Lett., vol. 21, no. 6, pp. 1221–1224, June 2017.
- [15] S. Sun and Z. Zhang, “Designing Practical Polar Codes Using Simulation-Based Bit Selection”, IEEE J. Emerging and Sel. Topics Circuits Syst., vol. 7, no. 4, pp. 594–603, Dec. 2017.
- [16] A. Elkelesh, M. Ebada, S. Cammerer and S. ten Brink, “Genetic Algorithm-based Polar Code Construction for the AWGN Channel”, SCC 2019; 12th International ITG Conference on Systems, Communications and Coding, March 2019.
- [17] S.B. Korada, E. Sasoglu, and R. Urbanke, “Polar codes: Characterization of exponent, bounds, and constructions”, IEEE Trans. Inf. Theory, vol.56, no.12, pp.6253–6264, 2010.
- [18] N. Presman, O. Shapira, and S. Litsyn, “Binary polar code kernels from code decompositions”, Proc. IEEE Int. Symp. Inform. Theory (ISIT), pp.179–183, July 2011.
- [19] L. Zhang, Z. Zhang, and X. Wang, “Polar code with block-length ”, Wireless Communications and Signal Processing (WCSP), International Conference, pp. 1–6, October 2012.
- [20] B. Serbetci and A. E. Pusane, “Practical polar code construction using generalised generator matrices”, IET Communications, vol. 8, no. 4, pp.419–426, March 2014.
- [21] Zhiliang Huang at all, “On the Successive Cancellation Decoding of Polar Codes with Arbitrary Linear Binary Kernel”, https://arxiv.org/pdf/1701.03264v2.pdf, Jan 2017.
- [22] F. Gabry, V. Bioglio, I. Land, and J.-C. Belfiore, “Multi-Kernel Construction of Polar Codes”, IEEE Int. Conf. Commun. (ICC), 2017.
- [23] M. Benammar, V. Bioglio, F. Gabry, and I. Land, “Multi-Kernel Polar Codes: Proof of Polarization and Error Exponents”, IEEE Info. Theory Workshop, 2017.
- [24] N. Hussami, S. B. Korada, and R. Urbanke, “Performance of Polar Codes for Channel and Source Coding”, IEEE Inter. Symp. Inf. Theory (ISIT), June 2009, pp. 1488–1492.
- [25] B. Li, H. Shen, and D. Tse, “A RM-Polar Codes”, ArXiv e-prints, July 2014.
- [26] M. Mondelli, S. H. Hassani, and R. L. Urbanke, “From Polar to ReedMuller Codes: A Technique to Improve the Finite-Length Performance”, IEEE Trans. Commun., vol. 62, no. 9, pp. 3084–3091, Sep. 2014.
- [27] V. Bioglio, F. Gabry and I. Land, “Low-Complexity Puncturing and Shortening of Polar Codes”, 2017 IEEE Wireless Communications and Networking Conference Workshops (WCNCW), San Francisco, CA, pp. 1-6, 2017.
- [28] S. N. Hong et al., “Capacity-achieving rate-compatible polar codes”, arXiv preprint arXiv:1510.01776, 2015.
- [29] H. Saber and I. Marsland, “An incremental redundancy Hybrid ARQ scheme via puncturing and extending of polar codes”, IEEE Transactions on Communications, vol. 63, no. 11, pp. 39643973, 2015.
- [30] K. Chen, K. Niu and J. Lin, “A hybrid ARQ scheme based on polar codes”, IEEE Communications Letters, vol. 17, no. 10, pp. 19961999, 2013.
- [31] K. Niu, K. Chen and J.-R. Lin, “Beyond turbo codes: rate-compatible punctured polar codes”, in IEEE International Conference on Communications (ICC), 2013, pp. 3423-3427.
- [32] D. Shin et al., “Design of Length-Compatible Polar Codes Based on the Reduction of Polarizing Matrices”, IEEE Transactions on Communications, vol. 61, no. 7, July 2013.
- [33] A. Eslami and H. Pishro-Nik, “A practical approach to polar codes”, in IEEE International Symposium on Information Theory Proceedings(ISIT), 2011, pp. 16-20.
- [34] A. Eslami and H. Pishro-Nik, “On finite-length performance of polar codes: stopping sets, error floor, and concatenated design”, IEEE Transactions on Communications, vol. 61, no. 3, March 2013.
- [35] J. Kim et al., “An Efficient Search on Puncturing Patterns for Short Polar Codes”, International Conference on Information and Communication Technology Convergence (ICTC), 2015.
- [36] L. Zhang et al., “On the Puncturing Patterns for Punctured Polar Codes”, IEEE International Symposium on Information Theory, 2014.
- [37] V. Miloslavskaya, “Shortened polar codes”, IEEE Transactions on Information Theory, vol. 61, no. 9, pp. 4852-4865, 2015.
- [38] R. Wang and R. Liu, “A novel puncturing scheme for polar codes”, IEEE Communications Letters, vol. 18, no. 12, pp. 2081-2084, 2014.
- [39] K. Niu et al., “Rate-Compatible Punctured Polar Codes: Optimal Construction Based on Polar Spectra”, https://arxiv.org/pdf/1612.01352, 2016.
- [40] R. M. Oliveira and R. C. de Lamare, “Rate-Compatible Polar Codes Based on Polarization-Driven Shortening”, IEEE Communications Letters, vol. 22, no. 10, pp. 1984-1987, 2018.
- [41] M. Jang et al., “Rate matching for polar codes based on binary domination”, IEEE Transactions on Communications, vol. 67, no. 10, pp. 6668-6681, 2019.
- [42] H. Saber and I. Marsland, “An Incremental Redundancy Hybrid ARQ Scheme via Puncturing and Extending of Polar Codes”, IEEE Transactions on Communications, vol. 63, no. 11, pp. 3964-3973, 2015.
- [43] M. Zhao at all, “An Adaptive IR-HARQ Scheme for Polar Codes by Polarizing Matrix Extension”, IEEE Communications Letters, vol. 22, no. 7, pp. 1306-1309, 2018.
- [44] Yu-Ming Huang at all, “Re-Polarization Processing in Extended Polar Codes”, IEICE Transactions on Communications , vol. E100-B, no. 10, pp. 1765-1777, 2017.
- [45] P. Trifonov and P. Semenov, “Generalized concatenated codes based on polar codes”, 8th International Symposium on Wireless Communication Systems, 2011.
- [46] H. Mahdavifar at all, “On the construction and decoding of concatenated polar codes”, International Symposium on Information Theory (ISIT), pp. 952-956, July 2013.
- [47] A. Cavatassi at all, “Asymmetric Construction of Low-Latency and Length-Flexible Polar Codes”, IEEE International Conference on Communications (ICC), July 2019.
- [48] P. Trifonov, “Chained Polar Subcodes”, 11th International ITG Conference on Systems, Communications and Coding (SCC), June 2017.
- [49] H. Mahdavifar, M. El-Khamy, J. Lee and I. Kang, “Compound polar codes”, 2013 Information Theory and Applications Workshop (ITA), pp. 1-6, 2013.
- [50] J. Kim, J. Lee, “Polar codes for non-identically distributed channels”, EURASIP Journal on Wireless Communications and Networking, 2016:287, 2016.
- [51] C.Leroux, I.Tal, A.Vardy,and W.J. Gross, “Hardware architectures for successive cancellation decoding of polar codes”, IEEE ICASSP, pp. 1665-1668, 2011.
- [52] I. Tal and A. Vardy, “List Decoding of Polar Codes”, IEEE Transactions on Information Theory, vol. 61, no. 5, pp. 2213-2226, May 2015.
- [53] R. M. Oliveira and R. C. de Lamare, “Non-Uniform Channel Polarization and Design of Rate-Compatible Polar Codes”, 16th International Symposium on Wireless Communication Systems (ISWCS), Oulu, Finland, pp. 537-541, 2019.
- [54] R. M. Oliveira and R. C. de Lamare, “Design of Rate-Compatible Polar Codes Based on Non-Uniform Channel Polarization”, IEEE Access, 2021.
- [55] R. C. de Lamare, ”Massive MIMO systems: Signal processing challenges and future trends,” URSI Radio Science Bulletin, vol. 2013, no. 347, pp. 8-20, Dec. 2013.
- [56] W. Zhang et al., ”Large-Scale Antenna Systems With UL/DL Hardware Mismatch: Achievable Rates Analysis and Calibration,” IEEE Transactions on Communications, vol. 63, no. 4, pp. 1216-1229, April 2015.
- [57] P. Li, R. C. de Lamare and R. Fa, “Multiple Feedback Successive Interference Cancellation Detection for Multiuser MIMO Systems”, IEEE Trans. on Wireless Comm., vol. 10, no. 8, pp. 2434-2439, Aug. 2011.
- [58] R. C. de Lamare and R. Sampaio-Neto, ”Adaptive MBER decision feedback multiuser receivers in frequency selective fading channels,” IEEE Communications Letters, vol. 7, no. 2, pp. 73-75, Feb. 2003.
- [59] R. C. De Lamare, R. Sampaio-Neto and A. Hjorungnes, ”Joint iterative interference cancellation and parameter estimation for cdma systems,” IEEE Communications Letters, vol. 11, no. 12, pp. 916-918, December 2007.
- [60] R. C. De Lamare and R. Sampaio-Neto, “Minimum Mean-Squared Error Iterative Successive Parallel Arbitrated Decision Feedback Detectors for DS-CDMA Systems,” IEEE Transactions on Communications, vol. 56, no. 5, pp. 778-789, May 2008.
- [61] Y. Cai and R. C. de Lamare, ”Space-Time Adaptive MMSE Multiuser Decision Feedback Detectors With Multiple-Feedback Interference Cancellation for CDMA Systems,” IEEE Transactions on Vehicular Technology, vol. 58, no. 8, pp. 4129-4140, Oct. 2009.
- [62] R. C. de Lamare and R. Sampaio-Neto, ”Adaptive Reduced-Rank Equalization Algorithms Based on Alternating Optimization Design Techniques for MIMO Systems,” IEEE Transactions on Vehicular Technology, vol. 60, no. 6, pp. 2482-2494, July 2011.
- [63] P. Li and R. C. De Lamare, ”Adaptive Decision-Feedback Detection With Constellation Constraints for MIMO Systems,” IEEE Transactions on Vehicular Technology, vol. 61, no. 2, pp. 853-859, Feb. 2012.
- [64] R. C. de Lamare, “Adaptive and Iterative Multi-Branch MMSE Decision Feedback Detection Algorithms for Multi-Antenna Systems,” IEEE Transactions on Wireless Communications, vol. 12, no. 10, pp. 5294-5308, October 2013.
- [65] P. Li and R. C. de Lamare, ”Distributed Iterative Detection With Reduced Message Passing for Networked MIMO Cellular Systems,” IEEE Transactions on Vehicular Technology, vol. 63, no. 6, pp. 2947-2954, July 2014.
- [66] Y. Cai, R. C. de Lamare, B. Champagne, B. Qin and M. Zhao, ”Adaptive Reduced-Rank Receive Processing Based on Minimum Symbol-Error-Rate Criterion for Large-Scale Multiple-Antenna Systems,” IEEE Transactions on Communications, vol. 63, no. 11, pp. 4185-4201, Nov. 2015.
- [67] R. C. de Lamare and R. Sampaio-Neto, ”Adaptive Reduced-Rank Processing Based on Joint and Iterative Interpolation, Decimation, and Filtering,” in IEEE Transactions on Signal Processing, vol. 57, no. 7, pp. 2503-2514, July 2009.
- [68] D. Angelosante, J. A. Bazerque and G. B. Giannakis, “Online adaptive estimation of sparse signals: where RLS meets the -norm,” IEEE Trans. Sig. Proc., vol. 58, no. 7, pp. 3436-3446, 2010.
- [69] Z. Yang, R. C. de Lamare and X. Li, ” -Regularized STAP Algorithms With a Generalized Sidelobe Canceler Architecture for Airborne Radar,” in IEEE Transactions on Signal Processing, vol. 60, no. 2, pp. 674-686, Feb. 2012.
- [70] R. C. de Lamare and R. Sampaio-Neto, ”Sparsity-Aware Adaptive Algorithms Based on Alternating Optimization and Shrinkage,” in IEEE Signal Processing Letters, vol. 21, no. 2, pp. 225-229, Feb. 2014.
- [71] Jihoon Choi et. al, “Adaptive MIMO decision feedback equalization for receivers with time-varying channels,” in IEEE Trans. on Sig. Proc., vol. 53, no. 11, pp. 4295-4303, Nov. 2005.
- [72] P. S. Bradley et. al, “Feature selection via concave minimization and support vector machines,” in Proc. 13th ICML, 1998, pp. 82–90.
- [73] Xiaodong Wang and H. V. Poor, “Iterative (turbo) soft interference cancellation and decoding for coded CDMA,” in IEEE Trans. on Comm., vol. 47, no. 7, pp. 1046-1061, July 1999.
- [74] A. G. D. Uchoa, C. T. Healy and R. C. de Lamare, ”Iterative Detection and Decoding Algorithms for MIMO Systems in Block-Fading Channels Using LDPC Codes,” IEEE Transactions on Vehicular Technology, vol. 65, no. 4, pp. 2735-2741, April 2016.
- [75] Z. Shao, R. C. de Lamare and L. T. N. Landau, ”Iterative Detection and Decoding for Large-Scale Multiple-Antenna Systems With 1-Bit ADCs,” IEEE Wireless Communications Letters, vol. 7, no. 3, pp. 476-479, June 2018.
- [76] R. B. di Renna and R. C. de Lamare, “Adaptive Activity-Aware Iterative Detection for Massive Machine-Type Communications”, IEEE Wireless Communications Letters, 2019.
- [77] Z. Shao, L. T. N. Landau and R. C. de Lamare, “Dynamic Oversampling for 1-Bit ADCs in Large-Scale Multiple-Antenna Systems,” in IEEE Transactions on Communications
- [78] A. G. D. Uchoa, C. Healy, R. C. de Lamare and R. D. Souza, “Design of LDPC Codes Based on Progressive Edge Growth Techniques for Block Fading Channels,” in IEEE Communications Letters, vol. 15, no. 11, pp. 1221-1223, November 2011
- [79] C. T. Healy and R. C. de Lamare, ”Decoder-Optimised Progressive Edge Growth Algorithms for the Design of LDPC Codes with Low Error Floors,” in IEEE Communications Letters, vol. 16, no. 6, pp. 889-892, June 2012.
- [80] C. T. Healy and R. C. de Lamare, ”Design of LDPC Codes Based on Multipath EMD Strategies for Progressive Edge Growth,” in IEEE Transactions on Communications, vol. 64, no. 8, pp. 3208-3219, Aug. 2016.
- [81] J. Liu and R. C. de Lamare, ”Low-Latency Reweighted Belief Propagation Decoding for LDPC Codes,” IEEE Communications Letters, vol. 16, no. 10, pp. 1660-1663, October 2012.
- [82] L. Liu et. al, “Sparse Signal Processing for Grant-Free Massive Connectivity: A Future Paradigm for Random Access Protocols in the Internet of Things,” in IEEE Sig. Proc. Mag., vol. 35, no. 5, pp. 88-99, Sept. 2018.