SVD-Aided Multi-Beam Directional Modulation Scheme Based on Frequency Diverse Array
Abstract
With the assistance of singular value decomposition (SVD), a multi-beam directional modulation (DM) scheme based on symmetrical multi-carrier frequency diverse array (FDA) is proposed. The proposed DM scheme is capable of achieving range-angle dependent physical layer secure (PLS) transmissions in free space with much lower complexity than the conventional zero-forcing (ZF) method. Theoretical and simulated results about secrecy rate and complexity verify the improved computational efficiency and considerable memory savings despite a very small penalty of secrecy rate.
Index Terms:
Directional modulation; frequency diverse array; physical layer security; singular value decomposition.I Introduction
Directional modulation (DM) has increasingly become a promising technique capable of achieving physical layer secure (PLS) communications.
The work in [1] proposed an angle-dependent DM scheme based on phased arrays (PA) by optimizing the phase shifters at the radio frequency (RF) frontend. A low-complexity DM synthesis method was proposed in [2], which transferred the DM synthesis from RF frontend to baseband. Afterwards, multi-beam angle-dependent DM synthesis methods were researched in [3]-[6]. Specifically, the orthogonal vector synthesis approach was implemented in [3], while [4] proposed a robust synthesis method for multi-beam DM scheme with imperfect direction knowledge. The multipath nature of the channel was exploited in [5] to create a multi-user DM transmissions. Artificial noise (AN) aided multi-beam DM system was studied in [6] using zero-forcing (ZF) criterion.
The above-mentioned single- or multi-beam DM schemes can only achieve angle-dependent secure transmissions, the security of which will fail when the eavesdropper is located along the same direction as the desired receiver. To address this problem, the frequency diverse array (FDA) with non-linear frequency increments was introduced to synthesize both range-angle dependent DM in [7]. The work in [8] proposed a random FDA-based range-angle dependent DM synthesis method, while the AN-aided FDA-DM communication over Nakagami-m fading channels was studied in [9].
These FDA-DM schemes [7]-[9] only considered single-beam DM transmissions for a single desired receiver. To achieve range-angle dependent multi-beam FDA-based DM transmissions, one possible approach [10] is to jointly optimizing the frequency increments, the beamforming vector, and the AN orthogonal matrix, which is too complicated to realize practically. The other approach is to extend the ZF-aided multi-beam PA-DM synthesis [6] to multi-beam FDA-DM synthesis [11]. The ZF method, however, consumes a large amount of memory for the orthogonal matrix and the AN vector.
This paper aims to reduce the complexity of the range-angle dependent multi-beam DM system in free space by re-designing the AN vector and orthogonal matrix with the aid of singular value decomposition (SVD). Compared with the conventional ZF method, the proposed SVD method can improve computational efficiency and save much memory with a small loss of secrecy rate. This makes it possible to achieve secure range-angle dependent multi-beam DM transmissions with lower complexity and lower DC power consumption.
Notations: The operators , , , and represent the transpose, Hermitian transpose, inverse, and Moore-Penrose inverse operations of a matrix, respectively.
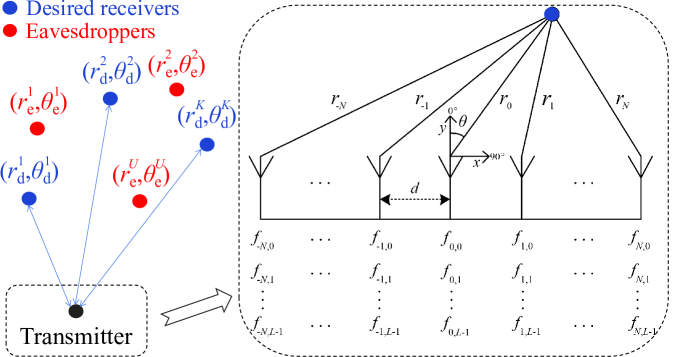
II System Model
As shown in Fig. 1, we consider a ()-element symmetrical linear FDA with multiple carriers [12]. The spacing between adjacent elements is designed as half central wavelength, and carriers are transmitted via each element. The frequency of the -th () carrier for the -th () element of FDA is designed as
| (1) |
where denotes the central carrier frequency, and is a fixed frequency offset satisfying .
Let and represent the range between an arbitrary spatial position and the central FDA element, and the azimuth angle, respectively. The normalized steering vector radiated from the transmit antenna array at is a vector for such a system, which can be expressed as
| (2) | ||||
where is an sub-steering vector caused by the carriers of the -th antenna element [12]. The phase of the -th entry of is
| (3) |
where is light speed, denotes the spacing between adjacent elements, refers to the time variable, and represents the wavelength of the central carrier.
The multi-beam DM model consists of a transmitter with a -element FDA, stationary desired receivers, and passive eavesdroppers in different locations. The spatial coordinate of the -th () desired receiver is assumed to be and the combined set of the desired receivers’ spatial coordinates is expressed as
| (4) |
A steering matrix with size can be obtained by combining the steering vectors of the desired spatial positions , i.e.,
| (5) |
Let denote the confidential baseband symbol vector for the desired receivers. The weighted -tuple transmitted signal vector of the FDA is designed as
| (6) |
where is the total transmit power constraint, and are the power splitting factors satisfying , denotes the normalization factor for the inserted AN, and is the inserted complex AN vector with each entry having zero mean and variance . In order to obtain a desired standard modulation constellation at the desired receivers while distorting the received signals at other undesired receivers, the normalization matrix and the orthogonal matrix should satisfy the following criteria:
| (7) |
In this paper, the normalization matrix is directly designed as the Moore-Penrose inverse matrix of the steering matrix , i.e.,
| (8) |
which satisfies , and the size of which is .
It is known that the null space of a matrix can be derived from its SVD. Therefore, in order to design the orthogonal matrix , we perform the SVD operation on the steering matrix , which is now expressed as
| (9) |
Next, we can obtain a null space, that is, for from (9), which means . Therefore, the orthogonal matrix of the SVD method can be designed as
| (10) |
| Items | ZF method | SVD method |
|---|---|---|
| Orthogonal matrix | , | |
| Size of | ||
| Artificial noise | ||
| Time complexity of calculating | ||
| Space complexity of storing and |
The normalized line-of-sight (LoS) channel is considered in this paper. In fact, the proposed method can also hold over fading channels like Nakagami-m fading [9], as long as the channel state information (CSI) is perfectly estimated. After passing through an LoS channel, the combined vector of the received signals at the desired receivers can be expressed as
| (11) | ||||
where is the circularly symmetric complex additive white Gaussian noise (AWGN) vector with each entry having zero mean and variance .
Similarly, the received signal of an arbitrary eavesdropper at , , can be expressed as
| (12) | ||||
where is the AWGN with zero mean and variance . It is worth emphasizing that the first term of (12) denotes distortion signal for the undesired receiver, and the second term is the inserted AN which cannot be eliminated at the undesired receiver due to the fact that the designed is non-orthogonal to its steering vector .
III Performance Analysis
III-A Secrecy Rate
We assume the eavesdroppers are located at , , respectively, which satisfy for and .
The achievable rate of the link from the transmitter to the -th desired receiver can be calculated by [9]
| (13) |
where is the ratio of signal to interference plus noise (SINR) at the -th desired receiver with the expression of
| (14) |
Similarly, the achievable rate of the link from the transmitter to the -th eavesdropper is expressed as
| (15) |
where
| (16) |
Therefore, the secrecy rate of the proposed multi-beam DM system can be defined as
| (17) |
where .
III-B Time Complexity
Both the normalization matrices of the ZF method in [6][11] and the proposed SVD method are designed as , so the complexity depends on the orthogonal matrix and the inserted AN , as shown in Table I.
Here, we consider the time complexity of calculating the orthogonal matrix . For the ZF method, the orthogonal matrix is designed as , the time complexity of which is [6][13]. For the SVD method, the orthogonal matrix can be directly obtained from the SVD of , which means the time complexity of calculating lies in the time complexity of calculating the SVD of . Since the size of is , (), the time complexity of calculating can be obtained by [13].
Additionally, the Moore-Penrose inverse operation of a matrix can be acquired using SVD algorithm [13], which means the normalization matrix can be directly calculated using the output of SVD. But for the ZF method, the normalization matrix has to be calculated independently.
III-C Space Complexity
The sizes of the orthogonal matrix and the AN can impact the the memory consumption significantly. As shown in Table I, the size of the orthogonal matrix of the ZF method is , and the size of the inserted AN is . By contrast, the size of the orthogonal matrix of the proposed SVD method is , and the size of the inserted AN is .
We define a metric as the ratio of the total memory consumed by and to that of the ZF method, i.e.,
| (18) | ||||
It is worth noting that when is determined and , which means the proposed SVD method can consume at most of the memory required by the ZF method, thereby reducing the amount of memory and lowering DC power consumption requirements.
IV Simulation Results
In our simulations, the parameters are set as GHz, kHz, , , , , , and Gray-coded -QPSK, respectively. The signal-to-noise ratio (SNR) is set as dB. Without loss of generality, we further assume , and the locations of the desired receivers are , , and , respectively.
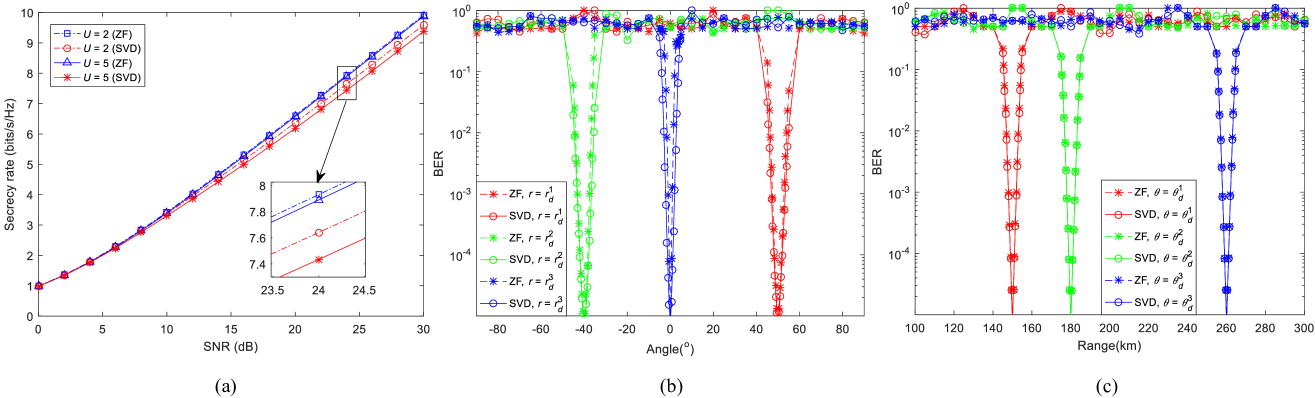
Fig. 2(a) shows the secrecy rate versus SNR (dB) for ZF- and SVD-aided multi-beam DM systems, where the eavesdroppers’ locations are randomly selected in the simulations. It is observed that the SVD method requires slightly higher SNR (dB) than the ZF method in order to achieve the same secrecy rate. For example, only 0.5 dB of additional SNR is required for the SVD method to match the ZF method when bits/s/Hz and . The secrecy loss is due to that the size of the inserted AN of the SVD method is smaller than that of the ZF method, which makes the SINRs of eavesdroppers a little higher than that of the ZF method.
Fig. 2(b) and (c) illustrate the simulated BER performances for ZF and SVD methods versus angle and range, respectively. In the angle dimension, the BER lobes of the ZF method are slightly narrower than the proposed SVD method around the desired receivers. In the range dimension, both ZF and SVD methods can achieve almost the same BER performances.
In order to illustrate the time complexity, we conducted Monte Carlo experiments to record the average time consumption of calculating using MATLAB111Computer configurations: Intel(R) Xeon(R) CPU E5-1620 v2 @ 3.7 GHz; 8.0 GB RAM; 64-bit operating system. MATLAB version: R2016a.. The result shows that the average time consumptions of ZF and SVD methods are and ms, respectively, which verifies that the computational efficiency of the proposed SVD method is better than that of the ZF method.
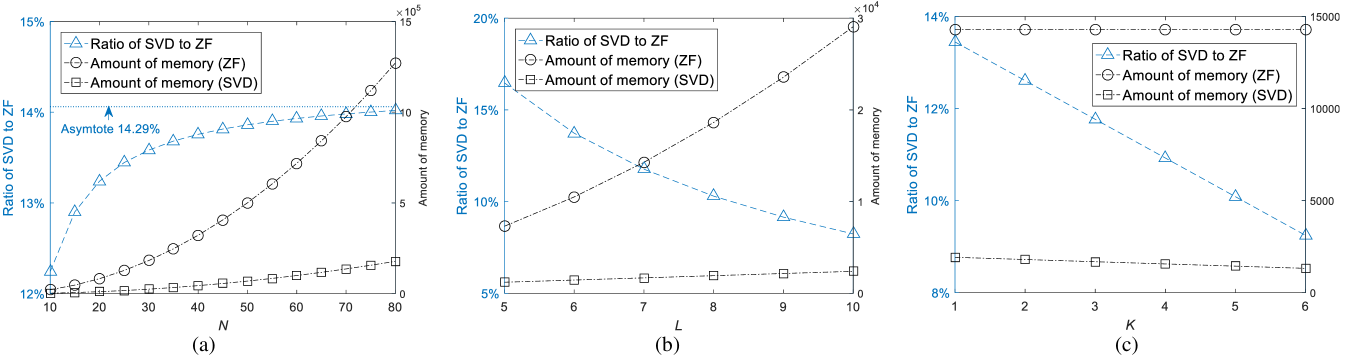
Moreover, Fig. 3 shows the total amount of memory required by the orthogonal matrix and the AN , and the ratio of SVD to ZF versus , and , respectively. From Fig. 3(a), the SVD method only consumes up to of the memory required by the ZF method with and , which is due to when as shown in (18). From Fig. 3(b) and Fig. 2(c), the ratio of SVD to ZF decreases as and increases. Therefore, the SVD method is more efficient than the ZF method with respect to memory required.
V Conclusion
A new SVD-aided low-complexity range-angle dependent multi-beam DM scheme based on symmetrical multi-carrier FDA was proposed. The proposed SVD method outperforms the ZF method in regard to the computational complexity and the amount of memory required for processing, while introducing only a small performance loss of secrecy rate. The SVD method opens a way to reduce the implementing complexity and lower DC power consumption requirements for range-angle dependent multi-beam DM systems.
References
- [1] M. P. Daly and J. T. Bernhard, “Directional modulation technique for phased arrays,” IEEE Trans. Ante. Propag., vol. 57, no. 9, pp. 2633-2640, Sept. 2009.
- [2] Y. Ding and V. Fusco, “A vector approach for the analysis and synthesis of directional modulation transmitters,” IEEE Trans. Ante. Propag., vol. 62, no. 1, pp. 361-370, Jan. 2014.
- [3] Y. Ding and V. Fusco, “Orthogonal vector approach for synthesis of multi-beam directional modulation transmitters,” IEEE Ante. Wirel. Propag. Lett., vol. 14, pp. 1330-1333, Feb. 2015.
- [4] F. Shu, X. Wu, J. Li, R. Chen, and B. Vucetic, “Robust synthesis scheme for secure multi-beam directional modulation in broadcasting systems,” IEEE Access, vol. 4, pp. 6614-6623, Oct. 2016.
- [5] M. Hafez, M. Yusuf, T. Khattab, T. Elfouly, and H. Arslan, “Secure spatial multiple access using directional modulation,” IEEE Trans. Wirel. Commun., vol. 17, no. 1, pp. 563-573, Jan. 2018.
- [6] T. Xie, J. Zhu, and Y. Li, “Artificial-noise-aided zero-forcing synthesis approach for secure multi-beam directional modulation,” IEEE Communications Letters, vol. 22, no. 2, pp. 276-279, Feb. 2018.
- [7] W.-Q. Wang, “DM using FDA antenna for secure transmission,” IET Microw. Ante. Propag., vol. 11, no. 3, pp. 336-345, Mar. 2017.
- [8] J. Hu, S. Yan, F. Shu, J. Wang, J. Li, and Y. Zhang, “Artificial-noise-aided secure transmission with directional modulation based on random frequency diverse arrays,” IEEE Access, vol. 5, pp. 1658-1667, 2017.
- [9] S. Ji, W. Wang, H. Chen, and Z. Zheng, “Secrecy capacity analysis of AN-aided FDA communication over Nakagami-m fading,” IEEE Wirel. Commun. Lett., vol. 7, no. 6, pp. 1034-1037, Dec. 2018.
- [10] B. Qiu, M. Tao, L. Wang, J. Xie, and Y. Wang, “Multi-beam directional modulation synthesis scheme based on frequency diverse array,” IEEE Trans. Info. Foren. & Sec., vol. 14, no. 10, pp.2593-2606, Oct. 2019.
- [11] T. Xie, J. Zhu, Q. Cheng, and J. Luo, “Secure directional modulation using the symmetrical multi-carrier frequency diverse array with logarithmical frequency increment,” IEICE Trans. Funda. Electro., Commun. & Computer Sci., vol. E102-A, no. 4, pp. 633-640, Apr. 2019.
- [12] H. Shao, J. Dai, J. Xiong, H. Chen, and W.-Q. Wang, “Dot-shaped range-angle beampattern synthesis for frequency diverse array,” IEEE Ante. Wirel. Propag. Lett., vol. 15, pp. 1703-1706, Feb. 2016.
- [13] Handbook of Linear Algebra - Discrete Mathematics and Its Applications, 2nd ed., Chapman & Hall/CRC Press, Boca Raton, FL, USA, 2017.