Temporal Reachability Graphs
Abstract
While a natural fit for modeling and understanding mobile networks, time-varying graphs remain poorly understood. Indeed, many of the usual concepts of static graphs have no obvious counterpart in time-varying ones. In this paper, we introduce the notion of temporal reachability graphs. A ()-reachability graph is a time-varying directed graph derived from an existing connectivity graph. An edge exists from one node to another in the reachability graph at time if there exists a journey (i.e., a spatiotemporal path) in the connectivity graph from the first node to the second, leaving after , with a positive edge traversal time , and arriving within a maximum delay . We make three contributions. First, we develop the theoretical framework around temporal reachability graphs. Second, we harness our theoretical findings to propose an algorithm for their efficient computation. Finally, we demonstrate the analytic power of the temporal reachability graph concept by applying it to synthetic and real-life datasets. On top of defining clear upper bounds on communication capabilities, reachability graphs highlight asymmetric communication opportunities and offloading potential.
category:
C.2.1 Computer-Communication Networks Network Design and Architecturekeywords:
Store and forward networkscategory:
F.2.2 Analysis of Algorithms and Problem Complexity Nonnumerical Algorithms and Problemscategory:
G.2.2 Discrete Mathematics Graph Theorykeywords:
Time-varying graphs, Reachability, Opportunistic networks, Communication performance bounds1 Introduction
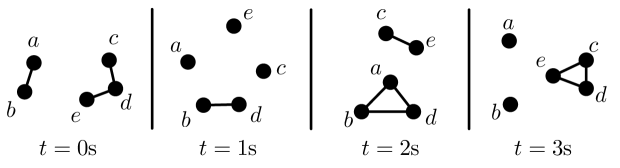
In time-varying graphs (TVG), vertices and edges appear and disappear as a function of time. Alternatively called temporal networks [15] or evolving graphs [29], time-varying graphs have emerged over the past few years as a key model for a variety of complex systems [10, 13, 16, 26, 27]. Time-varying graphs can also serve as a solid theoretical framework for investigating fundamental properties of mobile networks [3, 9]. In Fig. 1, we show an example of a time-varying graph representing a five-node mobile network.
Many of the typical concepts of static graphs such as paths, distance, diameter, or node degree have no obvious counterpart in time-varying graphs. Theorems that are true on static graphs may not hold in time-varying ones [15] and dynamic equivalents of well-known problems on static graphs, such as finding strongly connected components, turn out to be intractable [2]. Naturally, it is always possible to track the evolution of static metrics such as node degree or clustering on snapshots of the time-varying graph at certain time intervals [6] but, while instructive, this approach often fails to capture the correlations between successive snapshots [14]. Recently a number of concepts specific to time-varying graphs have been studied such as journeys [29], temporal diameter [5], or reachability time [14].
In the context of opportunistic mobile networking, much attention has been focused on aggregate inter-contact time distributions. These have been found to fit a power-law (with an parameter smaller than 1) followed by an exponential cutoff in a number of real-life datasets [4]. Should this power-law also hold for pairwise inter-contact times, then the expected values of these would be infinite, a pessimistic result indeed. However, further work has shown that aggregate power-law distributions can emerge from a diversity of pairwise inter-contact laws (including exponential) [7, 22]. Moreover, all information on multi-hop connectivity is ignored. Inter-contact time measurements do not therefore suffice to characterize connectivity in mobile networks.
Temporal reachability graphs (TRG), our contribution, on the other hand, offer an immediate view of communication possibilities in a dynamic network. Given a time-varying graph , an arc exists from vertex to vertex at time in its derived ()-reachability graph if a journey exists in from to leaving after time and arriving at before , given that each single-hop communication takes time . Here, is the edge traversal time and is the upper bound on journey times in . By definition, temporal reachability are directed time-varying graphs. For example, in the context of studying information dissemination in delay-tolerant networks (DTN) [11], would be the one-hop transmission delay and is the maximum tolerated delay.
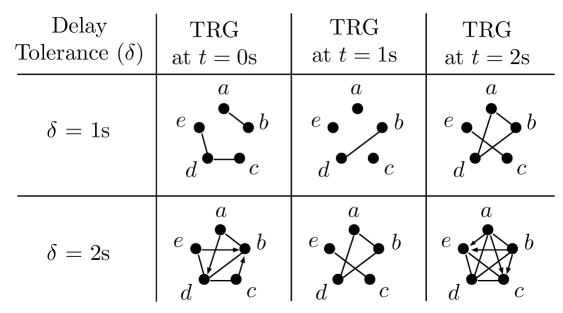
In Fig. 2, we show the instances of the temporal-reachability graph extracted from the opportunistic mobile networks of Fig. 1 at different times (assuming that the graph does not change between the snapshots shown in Fig. 1). We consider in this example that the link traversal time is =1s. When s, the only possible journeys in at are the direct links between nodes – communications tolerate a delay of 1s, which is the time to traverse one single link. When s, several more journeys appear. Consider for instance the reachability graph at s. There is a directed link between and as can wait one time unit for the link to appear ( and ); thus, a two-hop journey through becomes possible.
We make three main contributions:
Temporal reachability graphs. We formalize the concept of reachability graphs. In particular, under conditions that hold for all empirical datasets, we prove an additive property on the delay of reachability graphs. Roughly speaking, knowledge of the reachability graphs for delays and is enough to derive the reachability graph for delay .
Algorithm for efficient computation of TRG. We translate this additive property into an efficient single-pass streaming algorithm [1] to calculate entire families of reachability graphs.
Insights into real-world mobility traces. Once calculated, reachability graphs yield many original insights on the temporal structure of the time-varying graphs they derive from. In this paper, we calculate the reachability graphs of several synthetic and real-life high-resolution connectivity traces [18, 20, 23, 25]. These highlight the concepts of temporal connectivity, temporal asymmetry, and temporal dominating set. From the point of view of opportunistic communications, reachability graphs immediately provide, at all times, the maximum delivery ratio and the minimum set of users required to broadcast a message to the entire network, thereby offering a complete view of opportunistic communication capabilities and offloading potential.
The rest of the paper is structured as follows. Sections 2 and 3 introduce the concepts of time-varying and reachability graphs. Their theoretical properties justify their computation by a streaming algorithm detailed in Section 4. Section 5 then analyzes the reachability graphs of synthetic and real-life connectivity graphs. Related work is presented in Section 6. Finally, Section 7 concludes.
2 Time-varying graphs
Time-varying graphs are a very useful high-level abstraction for studying connectivity over time in mobile network. Terms, notations, and definitions around time-varying graphs vary considerably, but recently, Casteigts et al. have proposed a unified framework for TVGs and, wherever applicable, we will use their definitions and notations [3].
| Notation | Meaning |
|---|---|
| Number of vertices | |
| A time-varying graph (TVG) | |
| Edge traversal time of a TVG | |
| Time step of an -regular TVG | |
| Reachability graph with maximum | |
| delay derived from a TVG | |
| Number of arcs in at time | |
| , | Upper and lower bounds of a reachability |
| graph . . | |
| A time-varying out-dominating set of a | |
| reachability graph | |
| Symmetric subset of : | |
| Asymmetric subset of : | |
Definition 1.
(Time-varying graph) Let be a set of vertices, and the set of possible edges between vertices in . Events occur over a time span , where is the temporal domain ( for discrete-time systems or for continuous-time ones). In the general case, a TVG is a tuple where , called presence function, indicates whether a given edge exists at a given time and , called latency function, indicates the time it takes to cross a given edge if starting at a given date (the latency of an edge could vary in time).
In this paper, we will mostly consider continuous-time TVGs (i.e., ). Furthermore, we will always assume a constant function such that where is our uniform edge traversal time. We also note the set of edges in the snapshot of at time . Hence . Finally, given an edge , we define and .
Definition 2.
(Inclusion) Let and be two TVGs that differ only by their presence functions and . We write if and only if , or equivalently if and only if .
Definition 3.
(Union) Let , , and be three TVGs that differ only by their presence functions. We write if and only if .
Definition 4.
(Journey) A journey in is a sequence of couples such that : (i) ; (ii) ; and (iii) . Here, is this journey’s topological length (i.e., the number of hops). Furthermore, and denote the starting date and the last date , respectively. Finally is the journey’s temporal length. A journey may represent, for example, the sequence of hops that a message follows through an opportunistic network.
3 Temporal Reachability Graphs
Now that we have the necessary background, let us formally define the notion of temporal reachability graphs (or simply reachability graphs in the remainder of this paper, for the sake of readability). Furthermore, we write for . To the best of our knowledge, the definitions and results presented in this section are completely novel.
3.1 Reachability Graphs
Definition 5.
(Reachability graph) For , let be the reachability graph with maximum delay derived from (with edge traversal time ). Formally, , if and only if and there exists at time in a journey from to such that and .
Note that if then is empty, as even one-hop journeys do not have enough time to arrive before the maximum delay.
Proposition 1 (Growth)
Let and be two reachability graphs of . Then .
This follows naturally from the definition of a reachability graph. Note that the reverse is not true. For example let be a TVG with edge traversal time . Its derived reachability graphs and are both empty as their maximum delays are smaller than the time it takes to cross one edge. Therefore, as per definition 2, even though .
Definition 6.
(Composition) Let and be two reachability graphs of . We define their composition as the TVG such that, at all times ,
Theorem 1 (Decomposition)
Let be a TVG with edge traversal time and the set of all its reachability graphs. Let and . Then:
While not yet in a calculable form, this theorem is at the heart of our approach. Intuitively, it states that if all the reachability graphs with delays close to and are known, then one can calculate the reachability graph with delay . A full formal proof is provided in the appendix (Section A.1), but intuitively, it relies on the following simple idea. Any arc in corresponds to a journey in starting after time and arriving before . Either it can be neatly divided into a (possibly empty) journey in starting after and arriving before and another (possibly empty) journey in starting after and arriving before , or it starts crossing an edge before but after that straddles both time intervals. In the latter case, since the edge traversal time is , one can incorporate the straddling edge into a journey arriving before and the rest into another journey leaving after of temporal length less than .
3.2 Regular reachability graphs
Real-life datasets all have a maximum resolution (e.g., a second or a millisecond) that corresponds to the precision with which they were measured. While it is tempting to map their time domain to , in reality one must account for -second edge durations. For example, if the edge traversal time is null, then even ephemeral edges that last seconds may be part of a journey. In the more common situation where is strictly positive, one may still encounter -duration arcs in a reachability graph. For example, consider an edge that is present for only one second. If and are both also equal to one second, then a one-hop journey from to using that edge only exists at precisely the instant that the edge appears. This, in turn, corresponds to two -second arcs in : and . Note that both of these arcs will become one-second-long arcs in the reachability graph when . These observations lead to the definition of regular time-varying graphs.
Definition 7.
(Regular TVG) A TVG is an -regular TVG if there exists such that . Here, is called ’s resolution. The time interval is the epoch of with starting time and ending time .
Without loss of generality, this definition assumes that the first epoch starts at . Intuitively, an -regular TVG is one whose instantaneous graph topology cannot change arbitrarily quickly, as, during each epoch, the graph topology remains constant. Ephemeral -second edges or arcs may exist at the start of an epoch, but the TVG then remains constant until the start of the next epoch. Not only are regular TVGs a natural fit for real-life traces, but, as we will see, they also represent a class of TVGs whose reachability graphs are calculable.
Theorem 2 (Regular reachability graphs)
Let be an -regular TVG whose edge traversal time is . For , let be a reachability graph of . Then is an -regular TVG and .
This theorem ensures that, as long as is a “multiple” of the resolution , carries on the -regularity of . The full formal proof is a little technical (Section A.2 in the appendix), but it relies on the following idea. Let us consider a one-hop journey in an -regular TVG leaving in the middle of an epoch at time . Let be the integer such that . It arrives in the next epoch at time (the theorem assumes that ). Because is -regular, the departure time of this one-journey can be nudged forwards or backwards as long as it remains with the same epoch. Hence all one-hop journeys with a departure time such that are also valid journeys in . This “nudging” can be extended, though not trivially, to multi-hop journeys which proves the theorem.
Furthermore, the hypothesis guarantees that an arc present in a reachability graph during an epoch is present not only at the start of the epoch like in any regular graphs both also at the start of the next epoch. This property will be leveraged later in this section. However . An example of such a situation is discussed in Section 3.3.
Theorem 3 (Sampling)
Let be an -regular TVG whose edge traversal time is with . Let be the set of all its derived -regular reachability graphs. For such that , we have, :
This theorem is the adaptation of Theorem 1 to regular TVGs. The formal proof is in the appendix (Section A.3) but, as previously, it relies on the idea that within an epoch, there exists a little freedom to “nudge” journey departure and arrival times backwards or forwards. In a sense, if both the minimum departure time and maximal arrival time of a journey fall exactly at the start of a time epoch, then this journey can be divided into two sub-journeys whose departure and arrival times also map exactly to the start of epochs. Under this form, the value of a reachability graph at the start of each epoch can be exactly calculated from the values, at the start of each epoch, of the proper set of pairs of reachability graphs.
Unfortunately, this exact formula does not extend to the time spent strictly within an epoch. In a way, the state of the reachability graph during epochs is more important than its state at their starting times. Indeed, the time spent at exactly the start of epochs is infinitesimally small. Therefore any metric averaged over time (e.g. average density) will depend only on the states strictly within epochs. In the next section, we propose an upper and a lower bound on the reachability graph during epochs. As we will later see in Section 5, these upper and lower bounds are in fact nearly always equal and therefore achieve an excellent approximation of the real reachability graph.
3.3 Upper and lower bounds
We define for every regular reachability graph an upper and lower bound, i.e., two TVGs and such that . Both of these bounds are equal to the reachability graph at the start of each epoch but only differ slightly during the epoch. The upper bound is a straightforward application of Theorem 2.
Proposition 2 (Upper Epoch approximation)
Let be an -regular TVG whose edge traversal time is . For , let be a reachability graph of . We define ’s upper approximation, the TVG , as follows ( with ):
-
•
if , then ;
-
•
if , then .
As defined, .
The lower bound is a little more complicated and involves a modified version of the composition operator (Definition 6).
Definition 8.
(Approximate composition) Let and be two reachability graphs of an -regular TVG with and in . Let and be two TVGs such that and . For all times with , we define their approximate composition as follows:
-
•
if , then ;
-
•
if , then
By definition, at the start of each epoch the approximate composition is equal to the regular composition of the reachability graphs. During an epoch, the condition is easier to meet than the more intuitive . Indeed, with Theorem 2, , and this composition operator will catch the arcs (including the -second ones) occurring at the start of the next epoch. The same is true for the condition for arcs ending at the start of the current (-shifted) epoch. Combined, these more inclusive conditions make for a tighter lower bound.
Proposition 3 (Lower Epoch approximation)
Let be an -regular TVG whose edge traversal time is with . Let be the set of all its derived reachability graphs. We recursively define ’s lower approximation (i.e., the TVG ) as follows. For , and for all in such that and ,
As defined, .
The proof, detailed in Section A.4 of the appendix, is fairly straightforward and involves setting the value of in Theorem 1 as a function of , , , and .
This recursive definition means that the exact value of during a time epoch depends on the sequence of compositions that was used to calculate it. For example, in the simple situation where , the lower bounds and may be different. Proposition 3 only guarantees that they are both included in the real reachability graph . However, as we will see, this is not a concern because this lower bound is tight regardless of how it is calculated.
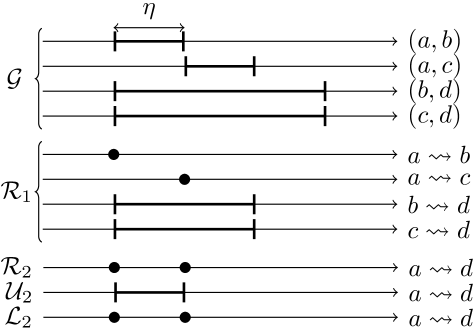
Fig. 3 is an example of a situation with four vertices where the upper bound has an arc during an epoch that is not in the reachability graph. Here s. is exactly derived from by shortening the end time of each edge by . For example, this leads to an ephemeral arc from to and a two-second-long arc from to (down from a three-second-long edge in ). Obviously, not all arcs are represented on Fig. 3. In , there are two ephemeral arcs from to , corresponding to the journey, and the journey an epoch later. In between those instants, it is both too late to use the first journey and too early to use the second. Since this arc exists at the start of two successive epochs, errs in considering that it exists during the entire epoch. In this example, the lower bound matches the reachability graph.
Conversely, Fig. 4 is an example of a situation with three vertices where the lower bound misses an arc during an epoch that is present in the reachability graph. Here again . The one-second-long edges in all become ephemeral -second arcs in (not shown on the figure), that in turn become one-second-long arcs in . Furthermore, also contains two ephemeral arcs and that correspond to the and journeys respectively. Here . Finally, contains an arc that corresponds to the existence of the three-hop journey . correctly identifies this journey at two instants and . At time , it composes arc from with the ephemeral arc in . At time it composes the ephemeral arc in with the arc in . However, for , has no way of finding the journey from to . Note that in this case, is equal to .
The example of Fig. 4 also helps us understand the absence of error propagation when calculating successive lower approximations from previous lower approximations. In this example, thanks to the conditions in Definition 8 that refer to the starting times of epochs, will “bridge” over the missing arc in . However it may miss composed arcs that use the arc in . These missed arcs will be, in-turn, “bridged” in, for instance, a approximation. Roughly speaking, errors during epochs do not propagate beyond two compositions. Combined with the fact that the lower approximation matches the reachability graph at the start of each epoch, this leads, as we will verify empirically, to a tight lower approximation or the reachability graph.
3.4 A few case studies
In this section, we examine how the theoretical results above apply to some simple situations.
Zero edge traversal time. The reachability graphs of -regular TVGs with zero edge traversal time () are very easy to calculate. In particular if and only if and are in the same connected component at time . Similarly, can be calculated from the connected components at time and . Furthermore, Theorem 1 becomes: . This relation can then be applied repeatedly (e.g., in a binary-exponentiation) to obtain any with . Furthermore, the reachability graphs thus calculated are exact. However, in this specific case where the edge traversal time is null, more efficient algorithms for calculating reachability graphs exist. For example the algorithm proposed by Chaintreau et al. for computing delay-optimal paths could be easily adapted to this purpose [5].
Several hops per epoch. While all of the results on regular reachability graphs in Sections 3.2 and 3.3 assume that the edge traversal time is in , they can be simply adapted to the case where with , i.e., when up to edges may be crossed during a single epoch. Indeed, in this case, any -regular graph would also be -regular, and we can apply all of our results as if . For example, Proposition 3 is reduced to .
Unit delay. For , the reachability graph is trivially calculable from . Indeed, for any edge in that appears at time and disappears at time , the arcs and appear in at time and disappear at time . This derivation is simple but essential for bootstrapping iterations of lower bound compositions (e.g., repeated applications of Proposition 3).
4 Efficient computation of reachability graphs
4.1 Families of reachability graphs
Another interesting property of lower approximations of reachability graphs is that an upper approximation may be derived from it. Indeed, since it contains the exact values of the reachability graph at the start of each epoch, it is trivial to calculate their intersection during each epoch. While the method described in this section focuses on the efficient computation of the lower approximations of reachability graphs, it simultaneously computes the upper approximations.
At a high level, the algorithm presented in this section is a binary exponentiation on families of lower bounds of reachability graphs using a special additive operator. To simplify notations, we will consider in this section that and .
Definition 9.
(Lower bound family) Let be a 1-regular TVG whose edge traversal time is . For , let be the lower approximation of a reachability graph of . For , we define , the family of such that .
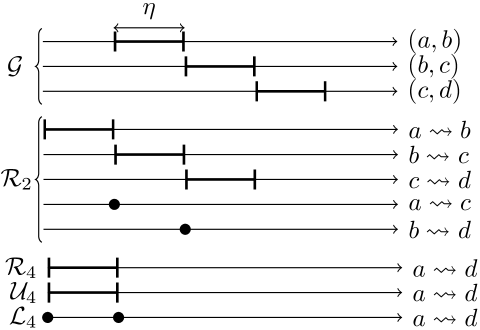
Proposition 4 (Family additivity)
Let be a 1-regular TVG whose edge traversal time is . Let and be two reachability graphs of such that and , and and the respective families of their lower approximations. We define the set of TVGs such that
Then (i) any element with is a lower approximation of , and (ii) any TVG in can be calculated from compositions of pairs of TVGs in .

We now have our self-sufficient elements, the lower bound families, and an additive operation between them. For illustration, Fig. 5 details the process of adding and families to obtain an family. The , , , , , and lower bounds are combined as inputs for three applications of Proposition 3 that yield , , and . Viewed as a black box, this operation combines the and families into an family.
The inner workings of the operator are embarrassingly parallel. Indeed, each application of Proposition 3 can be run completely independently of the others. This opens the way for highly distributed implementations, whose speed will be determined by that of the composition of pairs of lower bounds of reachability graphs. Accordingly, the next section proposes an efficient algorithm for this composition operation.
4.2 Composing reachability graphs
A time-varying graph may be stored as a time-indexed sequence of edge UP and DOWN events. For example, if at time an event occurs, then the edge disappears at time in . Such a representation is well suited for algorithms that sequentially examine all states of the TVG.
We present a streaming algorithm for composing reachability graph lower bounds as in Proposition 3. Streaming algorithms are well suited to TVGs as their memory requirements do not depend on the duration of the trace but only on the number of vertices [1]. Memory is indeed a limited resource, as reachability graphs can become fully connected cliques and data structures such as adjacency matrices cannot therefore be considered sparse. Furthermore, in our case, a streaming algorithm facilitates a parallel implementation of the operator as one process can read the input families, duplicate their events, and dispatch these to various workers, each calculating one composition operation.
Algorithm 1 reads its input from pairs of event streams and writes to its output stream. It makes use of an arc counter that tracks how many of the conditions in the definitions of (see Definition 8) are verified by each arc. When a previously down link fulfills one of these conditions, its counter is initialized to and an UP event is written to the output stream (Line 1). When this counter goes to the arc is removed from and a DOWN event is written to the output stream (Line 1). Note that an arc may be brought up and down at the same time if its counter goes to right after it appears (i.e., an ephemeral arc). In this case, the arc triggers both lines 1 and 1.
In more detail, this algorithm directly maps to the three conditions in the definition of the approximate composition (Definition 8):
Condition 1. . This condition is handled on line 1, before making a decision on bringing arcs up or down at the previous epoch. Indeed, the output stream at time can only be written to after reading the input streams up to time .
Condition 2. . This condition means that down events in must be delayed for one epoch before lowering an arc’s counter. This accounts for the local lists that are processed on lines 1 to 1.
Condition 3. , and . This condition is checked by maintaining for each two adjacency lists and and checking upon UP/DOWN events whether the end of an arc in corresponds to the origin of an arc in (lines 1-1, 1-1, 1-1, and 1-1).
Algorithm 1 is then used as a building block to implement the addition of lower bound families. Starting from ’s family, for any , is obtained in applications of the operation using a binary exponentiation process.
An implementation of Algorithm 1, fully integrated into a binary exponentiation algorithm over lower bound families, is available as a part of our dynamic trace library (DiTL [28]). This package also contains the code for transforming a lower bound TVG into an upper bound TVG, as well as the time-varying dominating set computation used in Section 5.
4.3 Complexity analysis
The worst-case memory requirements for this one-pass streaming algorithm are straightforward. Its local memory contains a non-sparse arc counter that requires up to space. Furthermore, for each , it maintains two non-sparse adjacency matrices and an arc event list thereby requiring space. Adding everything together yields a worst-case space complexity of that is independent of the duration of the trace.
Before examining the worst-case time complexity, a word must be said about the implementation of the adjacency matrices (the arc counter is backed by an adjacency matrix). In our implementation, these are backed by per-vertex hash tables. Insertion and removal are therefore constant time operations but this approach may not scale to TVGs with much greater number of vertices than those considered in this paper. In this analysis we will consider that insertion and removal cost (e.g., by using binary trees).
At each epoch, arcs are brought up and/or down. For each , we note and the number of UP and DOWN events in the entire TVGs and , respectively. Let be the maximum number of events in all the involved TVGs. In the worst case scenario where all possible arcs are updated at each epoch, we have events, where is the number of epochs. Each processed event costs a modification of the arc counter (), an adjacency matrix (), and up to counters for the composed paths (). All of these must be performed for the pairs of input TRGs. Adding everything together yields a worst-case time complexity of , or in terms of exclusively. In practice however , so the first formulation is more accurate.
5 Applications
Having formalized reachability graphs and detailed a method for efficiently computing upper and lower approximations of them in the previous sections, we now study the reachability graphs of several synthetic and real-life traces for a variety of edge traversal times and maximum delays . In particular, we show how the properties of these reachability graphs place bounds on communication capabilities and highlight the asymmetric nature of dynamic networks.
5.1 Datasets and metrics
| Name | |||||
|---|---|---|---|---|---|
| Rollernet | |||||
| Stanford | |||||
| Random Waypoint | |||||
| Community |
While we have calculated reachability graphs on many publicly available datasets, in this paper we present results based on two real-life contact traces selected for their short beaconing periods:
Stanford [23]. As part of an epidemiology study, this trace captures face-to-face contacts among all students, teachers, and staff in a US high school between 7 a.m. and 4 p.m. The 782 ZigBee motes (TelosB Crossbow) sent beacons every 20 seconds (sending times are synchronized in the published trace).
Rollernet [25]. Opportunistic sighting of Bluetooth devices by groups of rollerbladers carrying Intel iMotes during a roller tour. The 62 iMotes performed neighborhood scans every 15 seconds.
For comparison purposes, we also provide results based on two well understood synthetic mobility models:
Random-Waypoint [18]. We simulated nodes with speeds between 3 and 7 m/s from the stationary state in a m2 rectangle sending beacons every second with a 20 m transmission range.
Community Model [19]. We simulated nodes using the same parameters as above with 8 communities. In the community model, nodes with stronger social ties are more likely to be in geographic proximity.
The characteristics of these four -regular traces are summarized in Table 2.
For each reachability graph, we compute its time-varying dominating set (TVDS), i.e., a mutable set such that, at all times, there exists an incoming arc to any vertex in the TVG from a member of the TVDS. Thus, at any given time , the TVDS is a traditional dominating set on the directed graph at time . We note this TVDS if it is derived from a reachability graph .
Even on static graphs, calculating a minimal dominating set is a classic NP-complete problem. Here we adapt the well-known greedy algorithm for choosing multipoint relays for broadcasting in a wireless network to the time-varying context [17]. The size of the dominating set calculated by this algorithm is within a factor of the optimal, where is the number of nodes. Our TVDS calculation algorithm reacts to arc UP/DOWN events as follows.
-
1.
If, after the arc event is processed, the previous dominating set is no longer a dominating set, then proceed to step 2. Otherwise do nothing.
-
2.
Iteratively build the new dominating set, starting from an empty set, by greedily adding the node with the greatest outgoing degree to nodes not yet covered by the new dominating set. If two nodes have equal outgoing degrees, pick the one that is in the previous dominating set.
The time-varying dominating set thus calculated attempts to be both reasonably stable over time and close the optimal.
| Metric name | Definition |
|---|---|
| Avg. dominating set size | |
| Avg. density | |
| Avg. asymmetry |
The rest of this section focuses on the following metrics. Their formulas and average values are found in Table 3.
-
•
Density. The ratio of the number of arcs in a reachability graph at time over the total number of possible arcs.
-
•
Dominating set size. The normalized number of vertices in the dominating set at time .
-
•
Asymmetry. Here we no longer consider directed arcs but undirected pairs of vertices. At time , the asymmetry is the ratio of asymmetric pairs among pairs that have at least one edge between them.
5.2 Algorithm accuracy
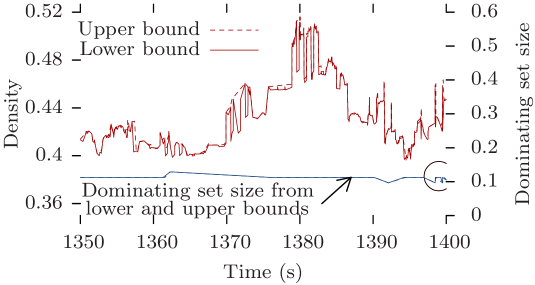
The approximation algorithm detailed in Section 4 is extremely accurate. Indeed, thanks to Theorem 3 and Definition 8, the approximation calculates the exact value for all times . Furthermore, the upper and lower bounds are nearly identical during epochs (). Fig. 6 plots the density over time for both the upper and lower bounds of the Rollernet reachability graph for s and min. The plot has been zoomed in to show only a small span of the -axis for 30 seconds. The upper and lower bounds on density are nearly equal at all times. So are the values of the dominating set size computed from the upper and lower approximations that only disagree in the circled area on Fig. 6. These observations hold for all the reachability graphs computed in this paper. Indeed, looking at the values of average density and average dominating set of the over 5,000 pairs of upper/lower bound TVGs calculated in this paper, the maximum disagreement is for the former and for the latter. In practice, the difference is smaller than the width of the line in plots. Therefore, in the rest of this paper, we only plot the values based on the lower approximation.
5.3 Revealing temporal structural properties
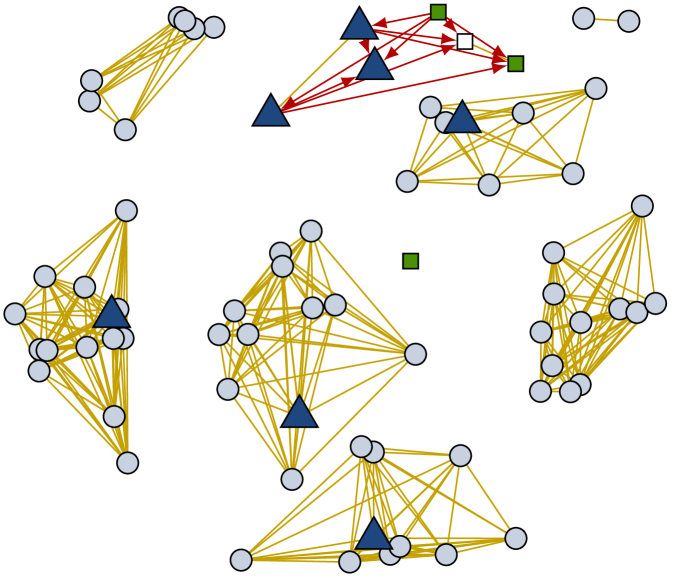
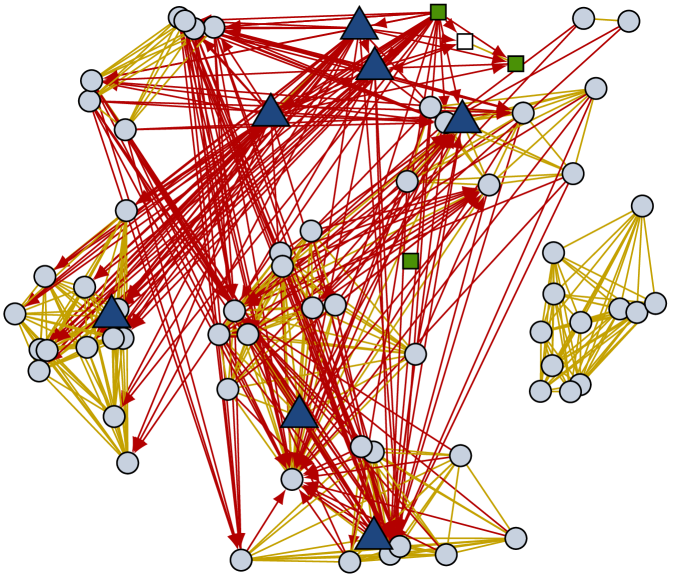
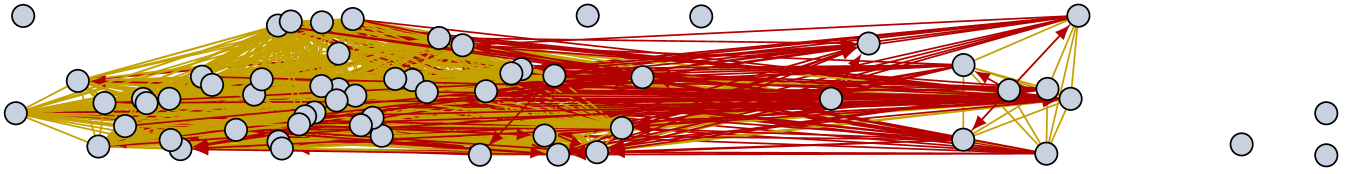
The dynamics of reachability graphs highlight temporal structural properties of the original connectivity trace that are not otherwise accessible. Fig. 7 shows snapshots of a subset of the reachability graph in the high school network captured in the Stanford dataset. When the delay is 20 minutes, the classroom structure of the trace is clearly visible. In the original contact trace, edges within a classroom are unstable and lead to merges and splits of small connected components. In the reachability graph, a classroom is a stable complete subgraph with one teacher. A group of interacting teachers are also visible at the top of Fig. 7a. When some teachers and students later change classrooms, they create strong asymmetries in higher-delay reachability graphs such as the 40-minute one depicted in Fig. 7b.
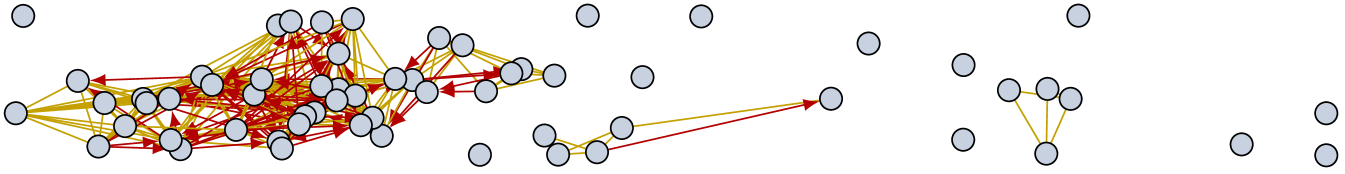
Fig. 8 shows snapshots of the reachability graph captured in the Rollernet dataset. These correspond to an acceleration phase, where the head of the tour (right on Fig. 8) pulls ahead of the rest of the rollerbladers. Due to the accordion phenomenon, the tail of the tour does not react immediately [25]. This completely prevents short delay communications between these two groups (s on Fig. 8a). With a longer delay (e.g., s on Fig. 8b), backward communications towards the rear of the tour become possible (in particular through organizers who stop on the side of the road and let the tour pass them), thereby creating strong asymmetry in the reachability graph.
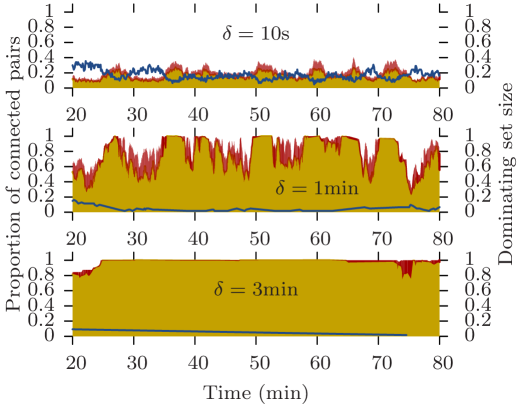
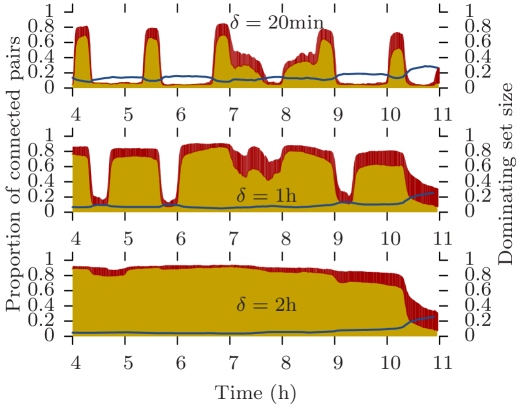
A more systematic study of dynamic properties over time is shown on Fig. 9. It plots both the proportion of connected pairs of vertices (left axis) and the size of the dominating set (right axis). The pairs of vertices are further divided into symmetric pairs (yellow) and asymmetric pairs (red). At a given time, if the red histogram reaches 1 then a journey exists in at least one direction between all pairs of nodes. If the yellow histogram reaches 1, then a journey exist in both direction between all pairs of nodes.
For a 1-minute delay, the Rollernet reachability graph alternates, sometimes very rapidly, between fully connected states and highly asymmetric partially connected states (Fig. 9a). Therefore, any opportunistic communication system aiming for latencies under a minute will be strongly impacted by the accordion phenomenon. However, if a communication system can tolerate up to three minute delays, then it should be possible to smooth out the dynamic mobility. Indeed, the 3-minute reachability graph is fully connected for the entire duration of the trace, and the size of its dominating set is almost always equal to one.
The Stanford trace alternates static phases in classroom (the valleys on Fig. 9b) and dynamic phases moving between classrooms or around the food court (the peaks on Fig 9b). The progressive “shrinking” of the valleys illustrates how reachability graphs “grow backwards” with increasing delays. Indeed, if there exist a journey from to within 20 minutes at time , then there exists a journey from to within 40 minutes at time minus minutes. Of course, after the increase in delays exceeds the width of the valleys, the reachability graph eventually reaches it maximum density. Note that in this case, an incompressible amount of asymmetry subsists throughout the trace.
Due to space constraints, we have only shown, in this section, results for specific values of but, as a general rule, the smaller the value of , the faster the TRG becomes a clique. When analysing a network with a specific application in mind, the value of can be set to a realistic value (e.g. message size over bit-rate), and the plots in this section give an immediate visual understanding of the communication possibilites. The next section examines quantitatively the importance the delay () and the edge traversal time () parameters.
5.4 Bounds on communication capabilities
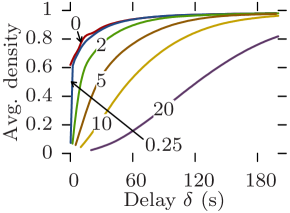
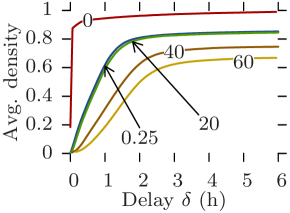
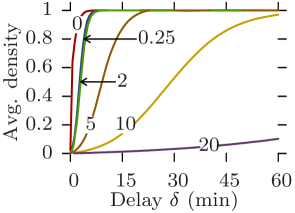
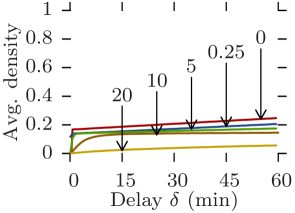
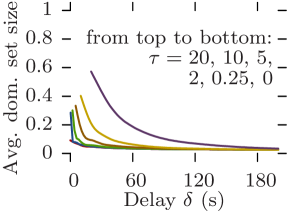
Reachability graphs give straightforward bounds on communication capabilities. Indeed, the density at a given moment is exactly equal to the maximum delivery ratio expectancy of a perfect opportunistic routing protocol whose delay-tolerance is equal to and whose message size over bit-rate ratio is equal to . Furthermore, the size of the dominating set indicates the achievable offload ratio in a scenario where the opportunistic network is assisting an infrastructure (e.g., 3G) for disseminating content to all nodes in the network [12].
Given real-world system requirements, i.e., wireless bit-rate estimates, messages sizes, target delivery ratio, and delay-tolerance, reachability graphs provide an immediate answer to the following question: can an opportunistic network support this service? If not, can it effectively supplement an infrastructure in an offloading scheme?
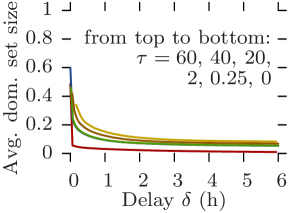
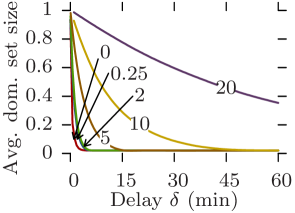
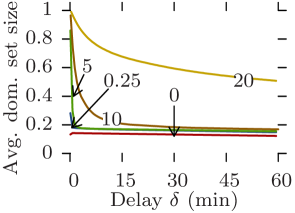
Fig. 10 plots the average density against the delay tolerance for all datasets and for increasing edge traversal times, while Fig. 11 plots the average dominating set size. Rollernet and Random Waypoint share similar characteristics. Both are very sensitive to increasing edge traversal times. When these are close to one second, near 100% density is achievable with a couple of minutes of delay tolerance (Figs. 10a, 10c, 11a, and 11c). In this case, they can support pure opportunistic communications. However, when edge traversal times are longer, tight delay constraints are impossible unless as part of an offloading scenario (e.g., s and s for Rollernet, Fig 10a). For s, Random Waypoint cannot even provide offloading for reasonable delays (Fig. 11c).
Similarly, Stanford and Community share similar features. Regardless of the delay-tolerance and message size, no pure opportunistic routing protocol can provide anything near 100% delivery ratio 111The results for Stanford are an artifact of the 20-second resolution. (Figs. 10b and 10d). Despite this, they are both good offloading scenarios as the size of their dominating sets is consistently below 20% of the total number of nodes, thereby offering potential offload ratios of around 80%. Indeed, in order to disseminate content to the entire network, pushing one copy per classroom in the Stanford case, or one copy per community in the Community case, plus copies to single nodes is an obvious strategy. However, for larger values of (e.g., 20), Community is no longer able to offload content with reasonable delays (Fig. 11d).
5.5 Asymmetry
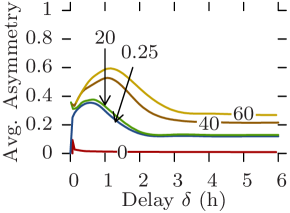
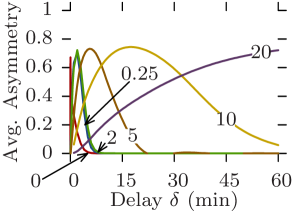
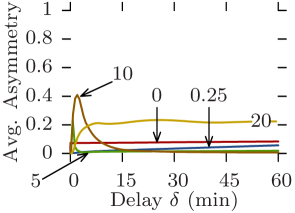
Asymmetric communications are a fundamental aspect of opportunistic networks. Too strong focus on inter-contact times may lead to overlook asymmetry, but reachability graphs provide a natural way of studying and quantifying it.
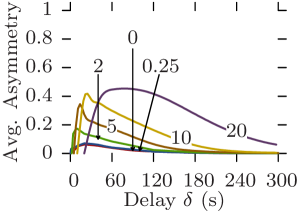
Fig. 12 plots for all datasets the average asymmetry against the maximum delay for increasing values of the edge traversal time. The asymmetry for the graph directly derived from the original contact trace is always 0 as it only contains symmetric arcs (see Section 3.4). Asymmetry in Random Waypoint follows a regular pattern: a bell-shaped curve of constant max value, whose width and center increase with (Fig. 12c). In this scenario, depending on the delay constraint, up to 80% on average of connected pairs of vertices can only communicate in one direction. This is due to nodes traveling long straight distances creating asymmetric reachability to nodes they meet from nodes they had met earlier. As the maximum delay increases, return journeys using different intermediate nodes appear, the reachability becomes complete, and the asymmetry returns to 0.
As previously, Rollernet and Random Waypoint show similar behavior. However, for Rollernet the maximum asymmetry also increases with (Fig. 12a). Indeed, as fewer edges are traversable, journeys become less likely between the front and the rear of the rollerblading tour. When such a journey is possible, it creates a longer-lasting asymmetry. In the Stanford trace, asymmetry follows the same increasing bell shape as in Rollernet, but never returns to 0 (Fig. 12b). In fact, this incompressible minimum asymmetry also increases with .
6 Related Work
Adaptations of traditional static graph distance metrics and algorithms to time-varying graphs have yielded many different concepts. For example, Orda et al. propose a shortest path algorithm for TVGs based on different waiting policies (unrestricted, forbidden, and source waiting) [21]. Our work corresponds to the unrestricted policy, in which a message may wait for an unlimited amount of time anywhere along its path through the TVG. Bui Xuan et al. have proposed efficient algorithms for calculating shortest (in number of hops), fastest (in path traversal time), and foremost (i.e., earliest arrival) paths in TVGs [29]. All these algorithms are designed to compute the shortest paths to all destination from a source and a fixed starting time. Our algorithms, in contrast, computes the reachibility graph by estimating the shortest paths for all possible starting times.
Several approaches to reachability in time-varying graphs exists. For strictly positive edge traversal times, a simple heuristic consists in dividing time into successive slots of length and keeping only edges that are persistently present during each slot [8]. This provides a good lower-bound approximation for small values of (i.e., less than ) whereas our approach can handle arbitrary edge traversal times. From a given starting time , reachability among all pairs of nodes can be calculated by iterating over all edge UP/DOWN events [24]. This calculation can then be repeated for a sample of starting times [14]. This approach yields static reachability graphs for a discrete sequence of starting times, whereas the temporal reachability graphs defined in this paper calculate reachability in continuous time.
Chaintreau et al., in their work on the diameter of opportunistic networks, calculate a Last Departure / Earliest Arrival structure for each pair of nodes [5]. This structure can tell for any pair of nodes , at any time , when is the earliest arrival for a message leaving for at time . A reachability graph could be easily derived from these structures, but would unfortunately only cover the case. Our approach is more general since it can also handle non-zero edge traversal times.
7 Conclusion and further work
In this paper, we introduced the notion of temporal reachability graphs. Given an edge traversal time and a maximum journey delay, temporal reachability graphs capture the temporal connectivity of the time-varying graphs they derive from. After formalizing the concept, we proved that regular reachability graphs, which encompass all experimental datasets, can be composed to compute reachability graphs of higher maximum delay with very high accuracy. Furthermore, we proposed a scalable highly-parallel streaming algorithm for their efficient computation. By applying this algorithm to synthetic and real-life contact traces, we showed how reachability graphs provide fresh new insights on temporal connectivity in time-varying graphs. In particular, they yield an immediate and intuitive picture of the communication capabilities and offloading potential of opportunistic networks.
This work on reachability graphs will be pursued in several directions. Firstly, our results could be extended to the more general case where the edge traversal time is not constant but may take values among multiples of a TVG’s resolution . Secondly, as seen in this paper, reachability graphs seem to reveal community structures that are not immediately apparent in the contact traces. They could therefore lead to new approaches for the difficult problem of community detection in time-varying graphs. Finally, much work remains to be done on the statistical analysis and modeling of reachability graphs. For example, what are the correlations between symmetric and asymmetric arcs from a given node? How do degree and inter-arc time distributions evolve with edge traversal time and delay? If reachability graphs turn out to be easier to model than their underlying time-varying graphs, could they be used as a first step for realistic synthetic connectivity models?
References
- [1] N. Alon, Y. Matias, and M. Szegedy. The space complexity of approximating the frequency moments. In Proc. ACM STOC, 1996.
- [2] S. Bhadra and A. Ferreira. Computing multicast trees in dynamic networks using evolving graphs. Technical Report RR-4531, INRIA, 2002.
- [3] A. Casteigts, P. Flocchini, W. Quattrociocchi, and N. Santoro. Time-varying graphs and dynamic networks. In Ad-hoc, Mobile, and Wireless Networks, volume 6811 of Lecture Notes in Computer Science, pages 346–359. Springer Berlin / Heidelberg, 2011.
- [4] A. Chaintreau, P. Hui, J. Crowcroft, C. Diot, R. Gass, and J. Scott. Impact of human mobility on opportunistic forwarding algorithms. IEEE Transactions on Mobile Computing, 6(6):606 –620, 2007.
- [5] A. Chaintreau, A. Mtibaa, L. Massoulie, and C. Diot. The diameter of opportunistic mobile networks. In Proc. ACM CoNEXT, 2007.
- [6] A. Clauset and N. Eagle. Persistence and Periodicity in a Dynamic Proximity Network. In Proc. DIMACS Workshop on Computational Methods for Dynamic Interaction Network, 2007.
- [7] V. Conan, J. Leguay, and T. Friedman. Characterizing pairwise inter-contact patterns in delay tolerant networks. In Proc. ACM Autonomics, 2007.
- [8] E. M. Daly and M. Haahr. Social network analysis for information flow in disconnected delay-tolerant manets. IEEE Transactions on Mobile Computing, 8(5):606–621, May 2009.
- [9] F. De Pellegrini, D. Miorandi, I. Carreras, and I. Chlamtac. A graph-based model for disconnected ad hoc networks. In Proc. IEEE INFOCOM, 2007.
- [10] S. N. Dorogovtsev and J. F. F. Mendes. Evolution of networks. Advances In Physics, 51(1079-1187):4, 2002.
- [11] K. Fall. A delay-tolerant network architecture for challenged internets. In Proc. ACM SIGCOMM, 2003.
- [12] B. Han, P. Hui, V. Kumar, M. Marathe, J. Shao, and A. Srinivasan. Mobile data offloading through opportunistic communications and social participation. IEEE Transactions on Mobile Computing, 11(5):821 – 834, 2011.
- [13] F. Harary and G. Gupta. Dynamic graph models. Mathematical and Computer Modelling, 25(7):79–88, 2005.
- [14] P. Holme. Network reachability of real-world contact sequences. Phys. Rev. E, 71:046119, Apr 2005.
- [15] D. Kempe, J. Kleinberg, and A. Kumar. Connectivity and inference problems for temporal networks. In Proc. ACM STOC, 2000.
- [16] V. Kostakos. Temporal graphs. Physica A Statistical Mechanics and its Applications, 388:1007–1023, 2009.
- [17] A. Laouiti, A. Qayyum, and L. Viennot. Multipoint relaying: An efficient technique for flooding in mobile wireless networks. In Proc. IEEE HICCS, 2001.
- [18] J.-Y. Le Boudec and M. Vojnovic. Perfect simulation and stationarity of a class of mobility models. In Proc. IEEE Infocom, 2005.
- [19] M. Musolesi, S. Hailes, and C. Mascolo. Adaptive routing for intermittently connected mobile ad hoc networks. In Proc. IEEE WoWMoM, 2005.
- [20] M. Musolesi and C. Mascolo. A community based mobility model for ad hoc network research. In Proc. ACM REALMAN, 2006.
- [21] A. Orda and R. Rom. Shortest-path and minimum-delay algorithms in networks with time-dependent edge-length. J. ACM, 37:607–625, 1990.
- [22] A. Passarella and M. Conti. Characterising aggregate inter-contact times in heterogeneous opportunistic networks. In Proc. IFIP NETWORKING, 2011.
- [23] M. Salathé, M. Kazandjieva, J. W. Lee, P. Levis, M. W. Feldman, and J. H. Jones. A high-resolution human contact network for infectious disease transmission. PNAS, 107(51):22020–22025, 2010.
- [24] J. Tang, M. Musolesi, C. Mascolo, and V. Latora. Characterising temporal distance and reachability in mobile and online social networks. SIGCOMM Computer Communications Review, 40(1):118–124, Jan. 2010.
- [25] P.-U. Tournoux, J. Leguay, F. Benbadis, V. Conan, M. Amorim, and J. Whitbeck. Density aware routing in highly dynamic dtns: the rollernet case. IEEE Transactions on Mobile Computing, 10(12):1755–1768, 2011.
- [26] A. Wagner. The yeast protein interaction network evolves rapidly and contains few redundant duplicate genes. Molecular Biology and Evolution, 18(7):1283–1292, 2001.
- [27] D. J. Watts and S. H. Strogatz. Collective dynamics of small-world networks. Nature, 393(6684):440–442, 1998.
- [28] J. Whitbeck. DynamIc Trace Library. http://github.com/neush/ditl.
- [29] B. B. Xuan, A. Ferreira, and A. Jarry. Computing shortest, fastest, and foremost journeys in dynamic networks. International Journal of Foundations of Computer Science, 14(2):267–285, 2003.
Appendix A Proofs
A.1 Proof of Theorem 1
Lemma 1
Let be a reachability graph of a TVG with edge traversal time . Let be a journey from to such that and . Then such that .
Proof.
If , then we set and we have .
If , let such that . In this case, . ∎
Lemma 2
Let be a reachability graph of a TVG with edge traversal time . Let be a journey from to such that and . Then and such that .
Proof.
The temporal length of journey is . Since it is a valid journey from to , , hence .
If , then , and , .
If , then we set such that . Then, since , and . ∎
We can now prove Theorem 1.
Proof.
(Theorem 1) First, let us show that if an arc fits one of the decompositions then it belongs to . For all times , let be an arc in (). By definition, one of the following conditions holds.
-
1.
. Therefore (Proposition 1).
-
2.
. In this case, there exists a journey in such that and . Therefore, by definition, .
-
3.
. Let and be the respective journeys from to and from to . is a journey from to such that and , i.e. . Therefore .
Conversely, let us show that for any time and any arc , there exists , such that . Let be the journey from to such that and .
Let . There are three possible situations.
-
1.
is not defined, i.e., . Since , , such that (Lemma 2).
-
2.
. Then is a path from to such that and . Therefore , such that (Lemma 1).
-
3.
. In this case, we can divide the journey from to at time into the sub-journeys and . We set . We have . Therefore, such that (Lemma 1). Since is a valid journey in , . Therefore , and .
In all three cases, . ∎
A.2 Proof of Theorem 2
Lemma 3 (One-hop journeys)
Let be an -regular TVG whose edge traversal time is . For , if a one-hop journey exists in such that , then all one-hop journeys with also exist in .
Proof.
Let with . If is a valid journey in , then by definition for all , . Since and is -regular, then for all (Definition 7). Furthermore, since , there exists such that . In this case, . Therefore, since is -regular, for all , (Definition 7). Finally let be a one-hop journey in with . We have and . Since for all , , is a valid journey in . ∎
Lemma 4 (Epoch inclusion)
Let be an -regular TVG whose edge traversal time is . For , let be a reachability graph of . For , let times and be such that and . Then .
Proof.
For , is always empty and the lemma is trivially true. Hereafter we write , with . If an arc is in , then there exists a journey from to such that and .
First we assume that .
Let .
If is not defined then . We consider the journey , such that . By construction, the departure times of all of its one-hop journeys verify . Furthermore, since , all one-hop journeys are valid (Lemma 3). Therefore is a valid journey from to such that and , i.e., .
If is defined then there are two possibilities. If then and is trivially in . If , then we can divide journey into two subjourneys and . As above, we can transform into a valid journey with such that and . Since , is a valid journey from to that leaves after and arrives before . Therefore .
Conversely, let us assume that . Let .
If is not defined, then . We consider the journey , such that . By construction, the departure times of all of its one-hop journeys verify . Furthermore, since , all one-hop journeys are valid (Lemma 3). Therefore is a valid journey from to such that and , i.e., .
If is defined then there are two possibilities. If then and is trivially in . If , then we can divide journey into two subjourneys and . As above, we can transform into a valid journey with such that and . Since , is a valid journey from to that leaves after and arrives before . Therefore . ∎
We can now prove Theorem 2.
A.3 Proof of Theorem 3
Lemma 5 (Journeys in regular graphs)
Let be an -regular TVG whose edge traversal time is . Let be a journey in from to such that , and . Then there exists another journey from to that verifies and .
Proof.
We write with . If , then which is impossible. Therefore .
is a journey from to . For all , we note the integer such that . Here and . Indeed, we have . Then we define .
Firstly, since is a valid journey, for all . Because is -regular, this implies that for all , and therefore all one-hop journeys in are valid.
Secondly, for all , leads to , i.e., . Since these are all integers, we get and all the one-hop journeys in may be taken successively and is therefore a valid journey from to such that and . ∎
We can now prove Theorem 3.
Proof.
We write with . At time , let be an arc in with . By setting , with (Theorem 1).
Conversely, let us consider an . Since ,according to Theorem 1, there exists such that one of the following holds (we note the integer such that ).
-
•
. Therefore (Lemma 5).
- •
-
•
and
. Following the same reasoning as for the first two conditions, we show that and .
In all three cases, there exists such that . ∎
A.4 Proof of Proposition 3
Proof.
For , by definition . By induction, lets us suppose the proposition true until a certain , and show that it also holds for . Let be an arc in . We write the integer such that . If , then (Definition 8 and Theorem 3) and . Hereafter we assume that . Since , there exists such that , , and . In this case, by definition, there exists such that one of the following holds.
-
•
. By setting , one can verify that , such that .
-
•
. By setting , one can verify that , such that .
-
•
and . By induction, and .
With Theorem 1, in all three cases, . By induction, this shows that . ∎