The two-edge connectivity survivable-network design problem in planar graphs
Abstract
Consider the following problem: given a graph with edge costs and a subset of vertices, find a minimum-cost subgraph in which there are two edge-disjoint paths connecting every pair of vertices in . The problem is a failure-resilient analog of the Steiner tree problem arising, for example, in telecommunications applications. We study a more general mixed-connectivity formulation, also employed in telecommunications optimization. Given a number (or requirement) for each vertex in the graph, find a minimum-cost subgraph in which there are edge-disjoint -to- paths for every pair of vertices.
We address the problem in planar graphs, considering a popular relaxation in which the solution is allowed to use multiple copies of the input-graph edges (paying separately for each copy). The problem is max SNP-hard in general graphs and strongly NP-hard in planar graphs. We give the first polynomial-time approximation scheme in planar graphs. The running time is .
Under the additional restriction that the requirements are only non-zero for vertices on the boundary of a single face of a planar graph, we give a polynomial-time algorithm to find the optimal solution.
1 Introduction
In the field of telecommunications network design, an important requirement of networks is resilience to link failures [24]. The goal of the survivable network problem is to find a graph that provides multiple routes between pairs of terminals. In this work we address a problem concerning edge-disjoint paths. For a set of non-negative integers, an instance of the -edge connectivity design problem is a pair where is a undirected graph with edge costs and connectivity requirements . The goal is to find a minimum-cost subgraph of that, for each pair of vertices, contains at least edge-disjoint -to- paths.
In telecommunication-network design, failures are rare; for this reason, there has been much research on low-connectivity network design problems, in which the maximum connectivity requirement is two. Resende and Pardalos [24] survey the literature, which includes heuristics, structural results, polyhedral results, computational results using cutting planes, and approximation algorithms. This work focuses on -edge connectivity problems in planar graphs.
We consider the previously studied variant wherein the solution subgraph is allowed to contain multiple copies of each edge of the input graph (a multi-subgraph); the costs of the edges in the solution are counted according to multiplicity. For -connectivity, at most two copies of an edge are needed. We call this the relaxed version of the problem and use the term strict to refer to the version of the problem in which multiple copies of edges of the input graph are disallowed.
A polynomial-time approximation scheme (PTAS) for an optimization problem is an algorithm that, given a fixed constant , runs in polynomial time and returns a solution within of optimal. The algorithm’s running time need not be polynomial in . The PTAS is efficient if the running time is bounded by a polynomial whose degree is independent of . In this paper, we focus on designing a PTAS for -edge connectivity.
Two edge-connected spanning subgraphs
A special case that has received much attention is the problem of finding a minimum-cost subgraph of in which every pair of vertices is two edge-connected. Formally this is the strict -edge connectivity design problem. This problem is NP-hard [12] (even in planar graphs, by a reduction from Hamiltonian cycle) and max-SNP hard [10] in general graphs. In general graphs, Frederickson and JáJá [13] gave an approximation ratio of 3 which was later improved to 2 (and 1.5 for unit-cost graphs) by Khuller and Vishkin [17]. In planar graphs, Berger et al. [4] gave a polynomial-time approximation scheme (PTAS) for the relaxed -edge connectivity design problem and Berger and Grigni [5] gave a PTAS for the strict -edge connectivity design problem. Neither of these algorithms is efficient; the degree of the polynomial bounding the running time grows with . For the relaxed version of spanning planar 2-edge connectivity, the techniques of Klein [19] can be used to obtain a linear-time approximation scheme.
Beyond spanning
When a vertex can be assigned a requirement of zero, edge-connectivity design problems include the Steiner tree problem: given a graph with edge costs and given a subset of vertices (called the terminals), find a minimum-cost connected subgraph that includes all vertices in the subset. More generally, we refer to any vertex with a non-zero connectivity requirement as a terminal. For -edge connectivity design problem, in general graphs, Ravi [23] showed that Frederickson and JáJá’s approach could be generalized to give a 3-approximation algorithm (in general graphs). Klein and Ravi [20] gave a 2-approximation for the -edge connectivity design problem. (In fact, they solve the even more general version in which requirements are specified for pairs of vertices.) This result was generalized to connectivity requirements higher than two by Williamson et al. [27], Goemans et al. [14], and Jain [16]. These algorithms each handle the strict version of the problem.
In their recent paper on the spanning case [5], Berger and Grigni raise the question of whether there is a PTAS for the -edge connectivity design problem in planar graphs. In this paper, we answer that question in the affirmative for the relaxed version. The question in the case of the strict version is still open.
1.1 Summary of new results
Our main result is a PTAS for the relaxed -edge connectivity problem in planar graphs:
Theorem 1.1.
For any , there is an algorithm that, given a planar instance of relaxed -edge connectivity, finds a solution whose cost is at most times optimal.
This result builds on the work of Borradaile, Klein and Mathieu [7, 8, 9] which gives a PTAS for the Steiner tree (i.e. -edge connectivity) problem. This is the first PTAS for a non-spanning two-edge connectivity problem in planar graphs.
Additionally, we give an exact, polynomial-time algorithm for the special case where are the vertices with non-zero requirement are on the boundary of a common face:
Theorem 1.2.
There is an -time algorithm that finds an optimal solution to any planar instance of relaxed -edge-connectivity in which only vertices are assigned nonzero requirements and all of them are on the boundary of a single face. For instances of relaxed -edge connectivity (i.e. all requirements are 0 or 2), the algorithm runs in linear time.
1.2 Organization
We start by proving Theorem 1.2 in Section 3. The proof of this result is less involved and provides a good warm-up for the proof of Theorem 1.1. The algorithm uses the linear-time shortest-path algorithm for planar graphs [15] and a polynomial-time algorithm for the equivalent boundary Steiner-tree problem [11] as black boxes.
In order to prove Theorem 1.1, we need to review the framework developed for the Steiner tree problem in planar graphs. We give an overview of this framework in Section 4 and show how to use it to solve the relaxed -edge connectivity problem. The correctness of the PTAS relies on a Structure Theorem (Theorem 4.6) which bounds the number of interactions of a solution between different regions of the graph while paying only a small relative penalty in cost. We prove this Structure Theorem in Section 5. The algorithm itself requires a dynamic program; we give the details for this in Section 6.
2 Basics
We consider graphs and multi-subgraphs. A multi-subgraph is a subgraph where edges may be included with multiplicity. In proving the Structure Theorem we will replace subgraphs of a solution with other subgraphs. In doing so, two of the newly introduced subgraphs may share an edge.
For a subgraph of a graph , we use to denote the set of vertices in . For a graph and set of edges , denotes the graph obtained by contracting the edges .
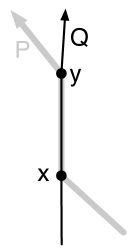
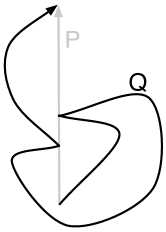
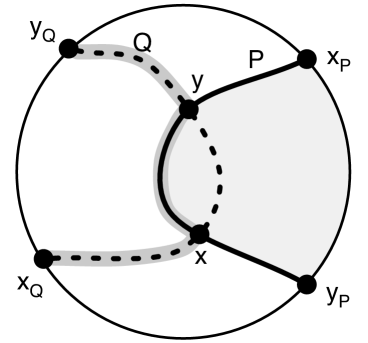
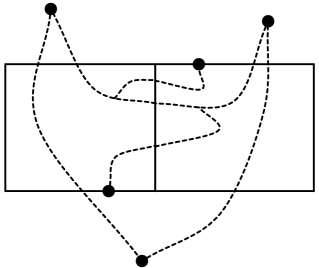
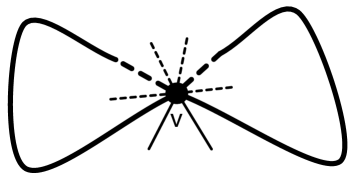
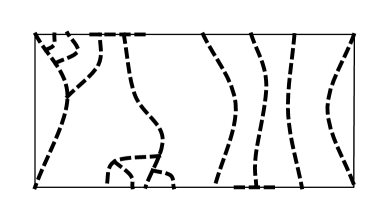
For a path , denotes the -to- subpath of for vertices and of ; and denote the first and last vertices of ; denotes the reverse of path . For paths and , denotes the concatenation of and . See Figure 1 for an illustration of the notion of paths crossing. A cycle is non-self-crossing if every pair of subpaths of the cycle do not cross.
We employ the usual definitions of planar embedded graphs. For a face , the cycle of edges making up the boundary of is denoted . We assume the planar graph is connected and is embedded in the plane, so there is a single infinite face, and we denote its boundary by .
For a cycle in a planar embedded graph, denotes an -to- path in for vertices and of . There are two such paths and the choice between the two possibilities will be disambiguated by always choosing the subpath in the clockwise direction. A cycle is said to enclose the faces that are embedded inside it. encloses an edge/vertex if the edge/vertex is embedded inside it or on it. In the former case, strictly encloses the edge/vertex. For non-crossing -to- paths and , is said to be left of if is a clockwise cycle.

We will use the following as a subroutine:
Theorem 2.1.
2.1 Edge-connectivity basics
Since we are only interested in connectivity up to and including two-edge connectivity, we define the following: For a graph and vertices , let
For two multi-subgraphs and of a common graph and for a subset of the vertices of , we say achieves the two-connectivity of for if for every . We say achieves the boundary two-connectivity of if it achieves the two-connectivity of for .
Several of the results in the paper build on observations of the structural property of two-edge connected graphs. The first is a well-known property:
Lemma 2.2 (Transitivity).
For any graph , for vertices ,
Note that in the following, we can replace “strictly encloses no/strictly enclosed” with “strictly encloses all/strictly not enclosed” without loss of generality (by viewing a face enclosed by as the infinite face).
Lemma 2.3 (Empty Cycle).
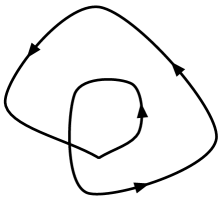
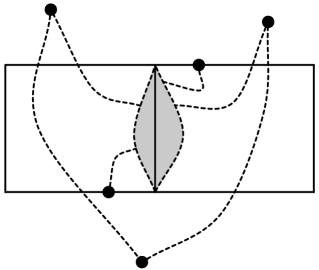
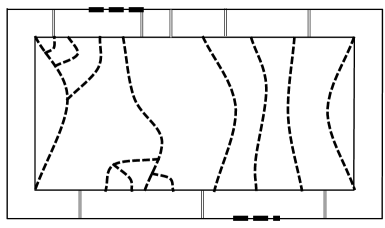
Let be a (multi-)subgraph of and let be a non-self-crossing cycle of that strictly encloses no terminals. Let be the subgraph of obtained by removing the edges of that are strictly enclosed by . Then achieves the two-connectivity of .
Proof.
See Figure 2(b). Without loss of generality, view as a clockwise cycle. Consider two terminals and . We show that there are edge-disjoint -to- paths in that do not use edges strictly enclosed by . There are two nontrivial cases:
-
Let be an -to- path in . If intersects , let be the first vertex of that is in and let be the last vertex of that is in . Let . If does not intersect , let . is an -to- path in that has no edge strictly enclosed by .
-
Let and be edge-disjoint -to- paths in . If does not intersect , then and are edge-disjoint paths, neither of which has an edge strictly enclosed by (where is as defined above). Suppose that both and intersect . Define and as for . Suppose these vertices are ordered , , , around . Then and are edge disjoint -to- paths that do not use any edges enclosed by . This case is illustrated in Figure 2; other cases (for other orderings of along ) follow similarly.
We have shown that we can achieve the boundary two-connectivity of without using any edges strictly enclosed by a cycle of . The lemma follows. ∎
2.2 Vertex-connectivity basics
The observations in this section do not involve planarity. Although our results are for edge connectivity, we use vertex connectivity in Section 5 to simplify our proofs.
Vertices and are biconnected (a.k.a. two-vertex-connected) in a graph if contains two -to- paths that do not share any internal vertices, or, equivalently, if there is a simple cycle in that contains both and . For a subset of vertices of , we say is -biconnected if for every pair of vertices of , contains a simple cycle through and . We refer to the vertices of as terminals.
Lemma 2.4.
A minimal -biconnected graph is biconnected.
Proof.
Suppose has a cut-vertex : where and for . If and both have terminals then does not biconnect every pair of terminals. If, say, does not have a terminal then is a smaller subgraph that biconnects the terminals. ∎
For the next two proofs, we use the notion of an (open) ear decomposition. An ear decomposition of a graph is a partition of the edges into a cycle and a sequence of paths such that the endpoints of are in . The ear decomposition is open if the endpoints of are distinct. A graph is biconnected iff it has an open ear decomposition [25]. Ear decompositions can be built greedily starting with any cycle.
Theorem 2.5.
Let be a minimal -biconnected graph. Every cycle in contains a vertex of .
Proof.
Assume for a contradiction that contains a cycle that does not contain any terminals. By Lemma 2.4, is biconnected and so has an open ear decomposition starting with ; let be an open ear decomposition of . Define to be the subgraph composed of and the first ears: . We construct another open ear decomposition with one fewer ear of as follows (note there is no ear ) and use to denote .
Let and be the endpoints of . Let . Let be the portion of that is not used in . We will maintain the invariant:
Clearly this invariant holds for . For , we define using and . Note that one or more of the endpoints of may be in and so is not necessarily a valid ear decomposition. However, by the invariant, ’s endpoints are in , allowing us to define a new valid ear by extending along to reach as follows: is the minimal path of whose endpoints are in such that is a subpath of . Define . Since has distinct endpoints, does not contain all the edges of , thus maintaining the invariant.
By construction, is an open ear decomposition of and so is biconnected. Since and does not contain any terminals, is -biconnected and since contains at least one edge, contradicts the minimality of . ∎
Theorem 2.6.
Let be a minimal -biconnected graph. For any cycle in , every -to- path contains a vertex of .
Proof.
Let be any cycle. By Theorem 2.5, contains a terminal. We consider an ear decomposition of built as follows. Consider not spanned by . Then there are vertex-disjoint paths from to since and the terminal on, for example, are biconnected. Let be the ear formed by these vertex-disjoint paths. Observe that by this construction each ear contains a terminal for every .
Suppose every path in with two endpoints in strictly contains a vertex of . We prove that this is then the case for . Since is an ear, its endpoints are in and so any -to- path that uses an edge of would have to contain the entirety of ; therefore cannot introduce a terminal-free path. ∎
3 An exact algorithm for boundary -edge connectivity
Our algorithm for the boundary case of -edge connectivity, as formalized in Theorem 1.2 is based on the observation that there is an optimal solution to the problem that is the union of Steiner trees whose terminals are boundary vertices, allowing us to employ the boundary-Steiner-tree algorithm of Theorem 2.1.
When terminals are restricted to the boundary of the graph, no cycle can strictly enclose a terminal. By Lemma 2.3, we get:
Corollary 3.1.
Let be a subgraph of and let be a minimal subgraph of that achieves the boundary two-connectivity of . Then in every cycle strictly encloses no edges.
In the following we will assume that the boundary of the graph is a simple cycle; that is, a vertex appears at most once along . Let us see why this is a safe assumption. Suppose the boundary of is not simple: there is a vertex that appears at least twice along . Partition into two graphs and such that , appears exactly once along and . Let be a vertex of and let be a vertex of . Then , allowing us to define new connectivity requirements and solve the problem separately for and .
Lemma 3.2.
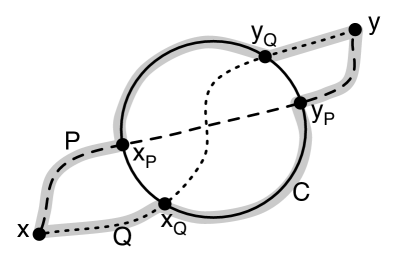
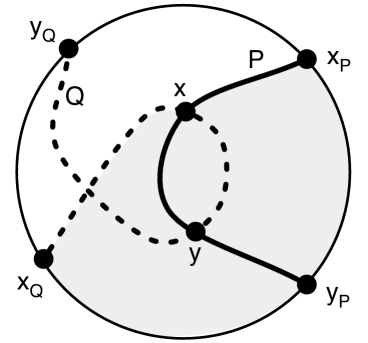
Let and be leftmost non-self-crossing -to- and -to- paths, respectively, where , , , and are vertices in clockwise order on . Then does not cross .
Proof.
For a contradiction, assume that crosses . Refer to Figure 3(a). Let (interior shaded) be the cycle . strictly encloses neither nor . If crosses , there must be a subpath of enclosed by . Let be the first vertex of in and let be the last. There are two cases:
Lemma 3.3.
Let be a subgraph of . Let be a subset of such that, for every , . Then there is a non-self-crossing cycle in such that and the order that visits the vertices in is the same as their order along .
Proof.
Assume that the vertices of are in the clockwise order along .
Let be the leftmost non-self-crossing -to- path in , taking the indices modulo . Let . Certainly visits each of the vertices in order. By Lemma 3.2, does not cross for all . Therefore, is non-self-crossing, proving the lemma. ∎
We now give an algorithm for the following problem: given a planar graph with edge costs and an assignment of requirements such that only for vertices of , find a minimum-cost multi-subgraph of that satisfies the requirements (i.e. such that there are at least edge-disjoint -to- paths in ).
Boundary2EC 1. Let be the cyclic ordering of vertices . 2. For , let . 3. For , let be the minimum-cost Steiner tree spanning . 4. Return the disjoint union .
We show that Boundary2EC correctly finds the minimum-cost multi-subgraph of satisfying the requirements. Let denote an optimal solution. By Lemma 3.3, contains a non-self-crossing cycle that visits (as defined in Boundary2EC). By Corollary 3.1, strictly encloses no edges of . Let be the leftmost -to- path in . The vertices in are connected in , by the input requirements. Let be the subgraph of that connects . This subgraph is enclosed by . Replacing by achieves the same connectivity among vertices with without increasing the cost.
We will use the following lemma to give an efficient implementation of Boundary2EC.
Lemma 3.4.
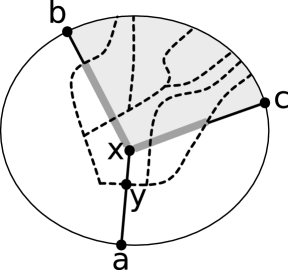
Let , and be vertices ordered along the clockwise boundary of a planar graph . Let be the shortest-path tree rooted at (using edge costs for lengths). Then for any set of terminals in , there is a minimum-cost Steiner tree connecting them that enclosed by the cycle .
Proof.
Refer to Figure 4. Let . Let be a minimum-cost Steiner tree in connecting . Suppose some part of is not enclosed by . Let be a maximal subtree of not enclosed by . The leaves of are on . Let be the minimum subpath of that spans these leaves. Let be the -to- path in . See Figure 4.
We consider the case when is a vertex of and is a vertex of (the other cases, when and are either both vertices of or both vertices of , are simpler). Then must cross where is the last vertex common to and (i.e. the lowest common ancestor in of and ). Let be a vertex of . Since is a shortest-path tree in an undirected path, every subpath of and , for any vertex , is a shortest path. We have that:
Let . By construction, spans . Using that , we have that since is a subpath of .
Repeating this process for every subtree of not enclosed by results in a tree enclosed by spanning that is no longer than . ∎
We describe an -time implementation of Boundary2EC (where is the number of terminals). Compute a shortest-path tree rooted at terminal in linear time. For each , consider the graph enclosed by . Compute the minimum Steiner tree spanning in . By Lemma 3.4, has the same cost as the minimum spanning tree spanning in . Since each edge of appears in at most two subgraphs and , the trees can be computed in time (by Theorem 2.1).
Note: if the requirements are such that for every vertex on the boundary of , then the sets have cardinality 2. Instead of computing Steiner trees in Step 3, we need only compute shortest paths. The running time for this special case is therefore linear.
This completes the proof of Theorem 1.2.
4 A PTAS framework for connectivity problems in planar graphs
In this section, we review the approach used in [9] to give a PTAS framework for the Steiner tree problem in planar graphs. While the contents of this section are largely a summary of the framework, we generalize where necessary for the survivable network design problem, but refer the reader to the original paper [9] for proofs and construction details that are not unique to the focus of this article.
Herein, denote the set of terminals by . denotes an optimal solution to the survivable network design problem. We overload this notation to also represent the cost of the optimal solution.
4.1 Mortar graph and bricks
The framework relies on an algorithm for finding a subgraph MG of , called the mortar graph [9]. The mortar graph spans and has total cost no more than times the cost of a minimum Steiner tree in spanning (Lemma 6.9 of [9]). Since a solution to the survivable network problem necessarily spans , the mortar graph has cost at most
| (1) |
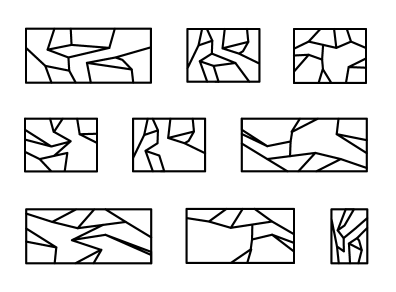
The algorithm for computing MG first computes a 2-approximate Steiner tree [21, 26, 28] and then augments this subgraph with short paths. The resulting graph is a grid-like subgraph (the bold edges in Figure 5(a)) many of whose subpaths are -short:
Definition 4.1.
A path in a graph is -short if for every pair of vertices and on ,
That is, the distance from to along is at most times the distance from to in .
For each face of the mortar graph, the subgraph of enclosed by that face (including the edges and vertices of the face boundary) is called a brick (Figure 5(b)), and the brick’s boundary is defined to be . The boundary of a brick is written . The interior of is defined to be the subgraph of edges of not belonging to . The interior of is written .
Bricks satisfy the following:
Lemma 4.2 (Lemma 6.10 [9]).
The boundary of a brick , in counterclockwise order, is the concatenation of four paths (west, south, east, north) such that:
-
1.
The set of edges is nonempty.
-
2.
Every vertex of is in or in .
-
3.
is 0-short in , and every proper subpath of is -short in .
-
4.
There exists a number and vertices ordered from west to east along such that, for any vertex of , the distance from to along is less than times the distance from to in : .
The number is given by:
| (2) |
The mortar graph has some additional properties. Let be a brick, and suppose ’s eastern boundary contains at least one edge. Then there is another brick whose western boundary exactly coincides with . Similarly, if is a brick whose western boundary contains at least one edge then there is a brick whose eastern boundary coincides with ’s western boundary.
The paths forming eastern and western boundaries of bricks are called supercolumns.
Lemma 4.3 (Lemma 6.6 [9]).
The sum of the costs of the edges in supercolumns is at most .
The mortar graph and the bricks are building blocks of the structural properties required for designing an approximation scheme. Borradaile, Klein and Mathieu demonstrated that there is a near-optimal Steiner tree whose interaction with the mortar graph is “simple” [9]. We prove a similar theorem in Section 5. In order to formalize the notion of “simple”, we select a subset of vertices on the boundary of each brick, called portals, and define a portal-connected graph.
4.2 Portals and simple connections
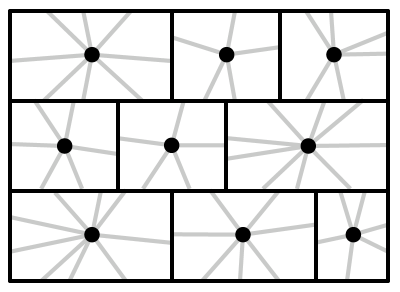
We define a subset of evenly spaced vertices along the boundary of every brick. The value of depends polynomially on the precision and on , a parameter that represents how complex the solution can be within a single brick ( will be defined precisely in Equation (6))
| (3) |
The portals are selected to satisfy the following:
Lemma 4.4 (Lemma 7.1 [9]).
For any vertex on , there is a portal such that the cost of the -to- subpath of is at most times the cost of .
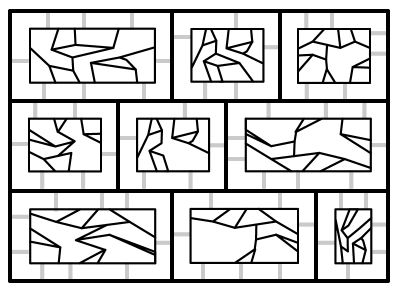
Recall that, for each face of the mortar graph , there is a corresponding brick , and that includes the vertices and edges comprising the boundary of . The next graph construction starts with the disjoint union of the mortar graph with all the bricks. Each edge of the mortar graph is represented by three edges in the disjoint union: one in (the mortar-graph copy of ) and one on each of two brick boundaries (the brick copies of ). Similarly, each vertex on the boundary of a brick occurs several times in the disjoint union.
The portal-connected graph, denoted , is obtained from the disjoint union as follows: a copy of each brick of is embedded in the interior of the corresponding face of , and each portal of is connected by an artificial edge to the corresponding vertex of . The construction is illustrated in Figure 5(c). The artificial edges are called portal edges, and are assigned zero cost.
Noting that each vertex on the boundary of a brick occurs several times in , we identify the original vertex of with that duplicate in that belongs to . In particular, each terminal (vertex in ) is considered to appear exactly once in , namely in . Thus the original instance gives rise to an instance in : the goal is to compute the optimal solution w.r.t. the terminals on in and then map the edges of this solution to . Since can be obtained from by contracting portal edges and identifying all duplicates of each edge and all duplicates of each vertex, we infer:
Lemma 4.5.
Let be a subgraph of that, for each pair of terminals , contains at least edge-disjoint -to- paths. Then the subgraph of consisting of edges of that are in has the same property.
The graph , which we call the brick-contracted graph, is obtained by contracting each brick in to a single vertex, called a brick vertex, as illustrated in Figure 5(d). This graph will be used in designing the dynamic program in Section 6.
4.3 Structure Theorem
Lemma 4.5 implies that, to find an approximately optimal solution in , it suffices to find a solution in whose cost is not much more than the cost of the optimal solution in . The following theorem, which we prove in Section 5, suggests that this goal is achievable. An equivalent theorem was proven for the Steiner tree problem [9].
Theorem 4.6 (Structure Theorem).
For any and any planar instance of the -edge connectivity problem, there exists a feasible solution to the corresponding instance such that
-
•
the cost of is at most where is an absolute constant, and
-
•
the intersection of with any brick is the union of a set of non-crossing trees whose leaves are portals.
4.4 Approximation scheme
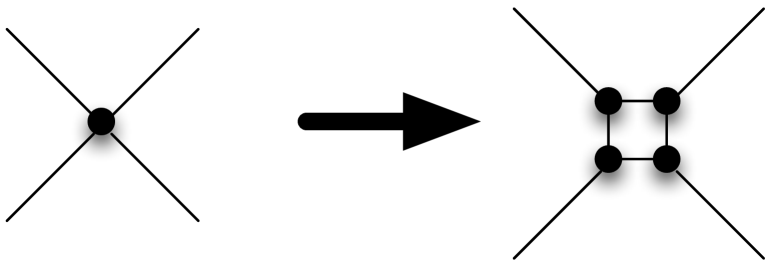
We assume that the input graph has degree at most three. This can be achieved using a well-known embedding-preserving transformation in which each vertex of degree is replaced with a cycle of degree-three vertices, as shown in Figure 6. Making this assumption simplifies the dynamic program using for Step 5 below.
The approximation scheme consists of the following steps.
-
Step 1:
Find the mortar graph MG.
-
Step 2:
Decompose MG into “parcels”, subgraphs with the following properties:
-
(a)
The parcels partition the faces of MG. Since each edge of MG belongs to the boundaries of exactly two faces, it follows that each edge belongs to at most two parcels.
-
(b)
The cost of all boundary edges (those edges belonging to two parcels) is at most . We choose so that this bound is :
(4) -
(c)
The planar dual of each parcel has a spanning tree of depth at most .
Each parcel corresponds to a subgraph of , namely the subgraph consisting of the bricks corresponding to the faces making up . Let us refer to this subgraph as the filled-in version of .
-
(a)
-
Step 3:
Select a set of “artificial” terminals on the boundaries of parcels to achieve the following:
-
•
for each filled-in parcel, there is a solution that is feasible with respect to original and artificial terminals whose cost is at most that of the parcel’s boundary plus the cost of the intersection of OPT with the filled-in parcel, and
-
•
the union over all parcels of such feasible solutions is a feasible solution for the original graph.
-
•
-
Step 4:
Designate portals on the boundary of each brick.
-
Step 5:
For each filled-in parcel , find a optimal solution in the portal-connected graph, . Output the union of these solutions.
Step 1 can be carried out in time [9]. Step 2 can be done in linear time via breadth-first search in the planar dual of MG, and then applying a “shifting” technique in the tradition of Baker [1]. Step 3 uses the fact that each parcel’s boundary consists of edge-disjoint, noncrossing cycles. If such a cycle separates terminals, a vertex on the cycle is designated an artificial terminal. We set if the cycle separates terminals with requirement 2 and otherwise. Under this condition, any feasible solution for the original graph must cross the cycle; by adding the edges of the cycle, we get a feasible solution that also spans the artificial terminal. Step 3 can be trivially implemented in linear time. Step 5 is achieved in linear time using dynamic programming (Section 6).
5 Proof of the Structure Theorem
We are now ready to prove the Structure Theorem for -edge connectivity, Theorem 4.6. In order to formalize the notion of connectivity across the boundary of a brick, we use the following definition:
Definition 5.1 (Joining vertex).
Let be a subgraph of and be a subpath of . A joining vertex of with is a vertex of that is the endpoint of an edge of .
We will use the following structural lemmas in simplifying . The first two were used in proving a Structure Theorem for the Steiner tree PTAS [9]; in these, is a tree and is an -short path on the boundary of the graph in which and are embedded. The third is in fact a generalization of the second lemma that we require for maintaining two connectivity.
Lemma 5.2 (Simplifying a tree with one root, Lemma 10.4 [9]).
Let be a vertex of . There is another tree that spans and the vertices of such that and has at most joining vertices with .
Lemma 5.3 (Simplifying a tree with two roots, Lemma 10.6 [9]).
Let and be two vertices of . There is another tree that spans and and the vertices of such that and has at most joining vertices with , where and are constants.
Lemma 5.4.
Let be a set of non-crossing trees whose leaves are vertices of -short boundary paths and and such that each tree in the forest has leaves on both these paths. There is a cycle or empty set , a set of trees, and a mapping with the following properties
-
•
For every tree in , spans ’s leaves.
-
•
For two trees and in , if for at least one of then and are edge-disjoint (taking into account edge multiplicities).
-
•
The subgraph has joining vertices with .
-
•
where is an absolute constant.
Proof.
View the embedding of the boundary such that is on top and is at the bottom. Let be the trees of ordered according the order of their leaves from left to right.
There are two cases.
Case 1) . In this case, we reduce the number of trees by incorporating a cycle . Let be the smallest index such that and let be the largest index such that . We will replace trees with a cycle. Let be the minimal subpath of that spans the leaves of on . We likewise define . Let be the leftmost -to- path in and let be the rightmost -to- path in . Since is -short,
| (5) |
To obtain from , we replace the trees with the cycle and set to . By construction spans the leaves of .
Case 2) . In this case, the number of trees is already bounded. We set so as to not eliminate any trees, and we set to be the empty set.
In both cases, for each remaining tree () we do the following. Let be a minimal subtree of that spans all the leaves of on and exactly one vertex of . Let be the minimal subpath of that spans the leaves of on . We replace with the tree that is the union of and the tree guaranteed by Lemma 5.2 for tree with root and -short path . By construction spans the leaves of . We set for .
has at most four joining vertices with . Each tree has one joining vertex with and, by Lemma 5.2, joining vertices with . By the choice of and , there are at most of the trees in the second part of the construction. This yields the bound on joining vertices.
The total cost of the replacement cycle is:
The total cost of the replacement trees is:
By the ordering of the trees and the fact that they are non-crossing, and the ’s are disjoint. Combining the above gives the bound on cost. ∎
5.1 Construction of a new solution
We start with a brief overview of the steps used to prove the structure theorem. We start with an edge multiset forming an optimal solution, . Each step modifies either the input graph or a subgraph thereof while simultaneously modifies the solution. The graphs and edge multisets resulting from these steps are denoted by subscripts. Details are given in subsequent sections.
- Augment
-
We add two copies of each supercolumn, obtaining and . We consider the two copies to be interior to the two adjacent bricks. This step allows us, in the restructure step, to concern ourselves only with connectivity between the north and south boundaries of a brick.
- Cleave
-
Cleaving a vertex refers to splitting it into two vertices and adding an artificial edge between the two vertices. In the cleave step, we modify (and so in turn modify and ) to create (and and ) by cleaving certain vertices while maintaining a planar embedding. Let be the set of artificial edges introduced. Note that . The artificial edges are assigned zero cost so the metric between vertices is preserved. The artificial edges are added to the solution, possibly in multiplicity, so connectivity is preserved.
- Flatten
-
In this step, for each brick , we consider the intersection of the solution with ; we replace some of the connected components of the intersection with subpaths of the boundary of . We denote the resulting solution by .
- Map
-
We map the edges of to creating . This step temporarily disconnects the solution.
- Restructure
-
In this step, we modify the solution . For each brick in , the part of strictly interior to is replaced with another subgraph that has few joining vertices with . We denote the resulting solution by .
- Rejoin
-
In order to re-establish connections broken in the Map step, we add edges to . Next, we contract the artificial edges added in the cleave step. We denote the resulting solution by .
Note that the solutions , , and so on are multisets; an edge can occur more than once. We now describe these steps in greater detail.
5.1.1 Augment
Recall that a supercolumn is the eastern boundary of one brick and the western boundary of another, and that the sum of costs of all supercolumns is small. In the Augment step, for each supercolumn , we modify the graph as shown in Figure 7:
-
•
Add to the graph two copies of , called and , creating two new faces, one bounded by and and the other bounded by and .
-
•
Add and to .
The resulting graph is denoted , and the resulting solution is denoted . We consider and to be internal to the two bricks. Thus remains part of the boundary of each of the bricks, and contains but not or . Since and share no internal vertices with , the joining vertices of with belong to and .
We perform one more step, a minimality-achieving step:
-
•
We remove edges from until it is a minimal set of edges achieving the desired connectivity between terminals.
Let be the resulting set. We get:
Lemma 5.5.
For every brick , the joining vertices of with belong to and .
5.1.2 Cleave
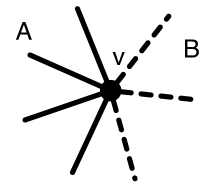
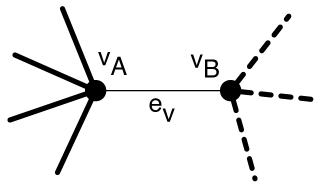
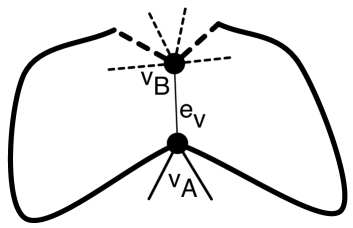
We define a graph operation, cleave. Given a vertex and a bipartition of the edges incident to , is cleaved by
-
•
splitting into two vertices, and ,
-
•
mapping the endpoint of edges in to ,
-
•
mapping the endpoint of edges in to , and
-
•
introducing a zero-cost edge .
This operation is illustrated in Figure 8(a) and (b). If the bipartition is non-interleaving with respect to the embedding’s cycle of edges around then the construction maintains a planar embedding.
We use two types of cleavings:
- Simplifying cleavings
-
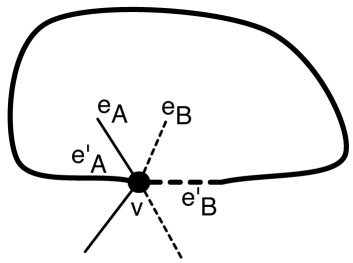
Refer to Figures 8(c) and (d). Let be a clockwise non-self-crossing, non-simple cycle that visits vertex twice. Define a bipartition of the edges incident to as follows: given the clockwise embedding of the edges incident to , let start and end with consecutive edges of and contain only two edges of . Such a bipartition exists because is non-self-crossing.
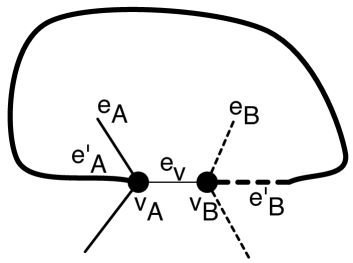
- Lengthening cleavings
-
Refer to Figures 8(e) and (f). Let be a cycle, let be a vertex on with two edges and adjacent to embedded strictly inside , and let and be consecutive edges of adjacent to such that the following bipartition is non-crossing with respect to the embedding: is a bipartition of the edges adjacent to such that and .
We perform simplifying cleavings for non-simple cycles of until every cycle is simple; the artificial edges introduced are not included in . The following lemma does not use planarity and shows that (since cycles get mapped to cycles in this type of cleaving) simplifying cleavings preserve two-edge connectivity.
Lemma 5.6.
Let be an edge in a graph . Let be the graph obtained from by a simplifying cleaving. Then is a cut-edge in iff it is a cut-edge in .
Proof.
Let be the endpoints of and let be the cycle w.r.t. which a simplifying cleaving was performed. If contains an -avoiding -to- path for then is not a cut-edge in , and similarly for . Suppose therefore that removing separates from in . Then the same is true in , and conversely. ∎
Corollary 5.7.
For , if two vertices are -edge connected in then any of their copies are -edge connected in .
Moreover, after all the simplifying cleavings, every cycle is simple, so:
Lemma 5.8.
Vertices that are two-edge-connected in are biconnected.
Next we perform lengthening cleavings w.r.t. the boundary of a brick and edges and of ; we include in all the artificial zero-cost edges introduced. Lengthening cleavings clearly maintain connectivity. Suppose that vertices and are biconnected in , and consider performing a lengthening cleaving on a vertex . Since there are two internally vertex-disjoint -to- paths in , cannot appear on both of them. It follows that there remain two internally vertex-disjoint -to- paths after the cleaving. We obtain the following lemma.
Lemma 5.9.
Lengthening cleavings maintain biconnectivity.
Lengthening cleavings are performed while there are still multiple edges of the solution embedded in a brick that are incident to a common boundary vertex. Let be the set of artificial edges that are introduced by simplifying and lengthening cleavings. We denote the resulting graph by , we denote the resulting mortar graph by , and we denote the resulting solution by .
As a result of the cleavings, we get the following:
Lemma 5.10.
Let be a brick in with respect to . The intersection is a forest whose joining vertices with are the leaves of the forest.
Proof.
Let be a connected component of . As a result of the lengthening cleavings, the joining vertices of with have degree 1 in . Suppose otherwise; then there is a vertex of that has degree in . Hence is a candidate for a lengthening cleaving, a contradiction.
By Theorem 2.5 and the minimality-achieving step of the Augment step, any cycle in must include a terminal with by Theorem 2.5. Since there are no terminals strictly enclosed by bricks, must be a vertex of . However, that would make a joining vertex of with . As argued above, such vertices are leaves of , a contradiction to the fact that is a vertex of a cycle in . Therefore is acyclic.
Furthermore, leaves of are vertices of since is minimal with respect to edge inclusion and terminals are not strictly internal to bricks. ∎
Lemma 5.11.
Let be a cycle in . Let be a brick. Distinct connected components of belong to distinct components of .
Proof.
Assume the lemma does not hold. Then there is a -to- path in . Each vertex of that is strictly interior to is not a terminal. A vertex of that was on would be a candidate for a lengthening cleaving, a contradiction. Therefore includes no terminals. This contradicts Theorem 2.6. ∎
5.1.3 Flatten
For each brick , consider the edges of that are strictly interior to . By Lemma 5.10, the connected components are trees. By Lemma 5.5, for each such tree , every leaf is either on ’s northern boundary or on ’s southern boundary . For each such tree whose leaves are purely in , replace with the minimal subpath of that contains all the leaves of . Similarly, for each such tree whose leaves are purely in , replace with the minimal subpath of that contains all the leaves of .
Let be the resulting solution. Note that is a multiset. An edge of the mortar graph can appear with multiplicity greater than one.
5.1.4 Map
This step is illustrated in Figures 9(a) and (b). In this step, the multiset of edges resulting from the flatten step is used to select a set of edges of . Recall that every edge of corresponds in to three edges: two brick copies (one in each of two bricks) and one mortar-graph copy. In this step, for every edge of , we include the mortar-graph copy of in with multiplicity equal to the multiplicity of in . At this point, none of the brick copies are represented in .
Next, recall that in the augment step, for each supercolumn , we created two new paths, and , and added them to . The edges of these two paths were not considered part of the mortar graph, so mortar-graph copies were not included in for these edges. Instead, for each such edge , we include the brick-copy of in with multiplicity equal to the multiplicity of in .
Finally, for each edge interior to a brick, we include in with the same multiplicity as it has in .
5.1.5 Restructure
Let be a brick. For simplicity, we write the boundary paths of as . Let be the multiset of edges of that are in the interior of . is a forest (Lemma 5.10). As a result of the flatten step, each component of connects to . We will replace with another subgraph and map each component of to a subgraph of where spans the leaves of and is a tree or a cycle. Distinct components of are mapped by to edge-disjoint subgraphs (taking into account multiplicities).
Refer to Figure 10. We inductively define -to- paths and corresponding integers . Let be the vertices of guaranteed by Lemma 4.2 (where is the vertex common to and and is the vertex common to and ). Let be the easternmost path in from to . Let be the integer such that is in . Inductively, for , let be the easternmost path in from to that is vertex-disjoint from . Let be the integer such that . This completes the inductive definition of . Note that the number of paths is at most , which in turn is at most as defined in Equation 2.
We use these paths to decompose , as illustrated in Figure 10. Let be the set of edges of enclosed by the cycle formed by , , and . Clearly . If is connected to , they share at most one vertex, . If they are not connected, we say is undefined.
There are two cases: either is connected or not.
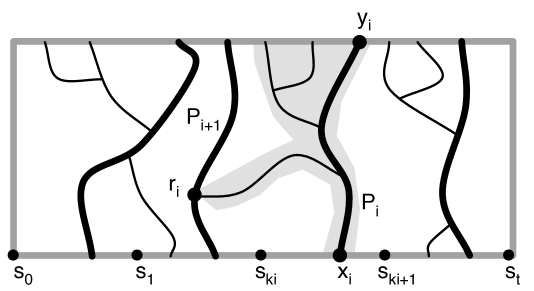
Connected case:
There are two subcases. Either spans vertices of or not.
Suppose spans vertices of . Let be a minimal subtree of that spans and let be a minimal subtree of that spans . Let be the first vertex of in and let be the last vertex of in . A path in from to that does not go through contradicts the choice of as there would be a path in from to that is disjoint from . It follows that and are edge disjoint: if they intersect they may only do so at . If is defined, then there is a path from to ; intersects between and , for otherwise there would be a superpath of that contradicts the choice of .
If is defined and , then we replace with the tree guaranteed by Lemma 5.3 with roots and . Otherwise, we replace with the tree guaranteed by Lemma 5.2 with root . We do the same for .
Suppose does not span vertices of . Let be a minimal connected subgraph of that spans . Let be the first vertex of in . If is defined, then there is a path from to and ’s intersection with belongs to , for otherwise there would be a superpath of that contradicts the choice of . If is defined and , then we replace with the tree guaranteed by Lemma 5.3 with roots and along with , , and . Otherwise we replace with the tree guaranteed by Lemma 5.2 with root along with , , and .
In both cases, we define to be the resulting tree that replaces . By construction, spans the leaves of and and (if defined).
Disconnected case:
In this case, by the definition of , is a subset of the vertices of , for otherwise there would be a path to the right of that connects to and is disjoint from .
If is connected to , then the western-most tree is a tree with root and leaves on and does not connect to as that would contradict the choice of ; if this is the case, let be the tree guaranteed by Lemma 5.2 and define .
If is connected to , let be the subpath of that spans the eastern-most tree ’s leaves on . Let be the tree guaranteed by Lemma 5.3 that spans the eastern-most tree’s leaves on and roots and and define .
Let be the set of remaining trees, let , and let in Lemma 5.4. Let , , and be the cycle (or empty set), set of trees, and mapping that satisfy the properties stated in the lemma.
We define to consist of the trees of and the cycle (and , and if defined).
We replace every with , as described above, for every brick, creating . This is illustrated in Figure 11(a). Now we define in terms of . A component of is partitioned into adjacent trees in this restructuring: namely , . and may be restructured via the disconnected case and all others are restructured via the connected case. Define . If , then consecutive trees and share a vertex and by construction and also share this vertex. Since spans the leaves of , we get that spans the leaves of , as desired. Also by construction, the submapping of of trees to trees (and not cycles) is bijective; the same holds for .
Number of joining vertices
In both the connected and disconnected case, the number of leaves is the result of a constant number of trees resulting from Lemmas 5.2, 5.3 and 5.4. Therefore, has joining vertices with and . Since , has joining vertices with the boundary of each brick. This is the number of connections required to allow a solution to be nearly optimal and affects the number of portals required in Equation (3):
| (6) |
This will allow us to prove the second part of the Structure Theorem.
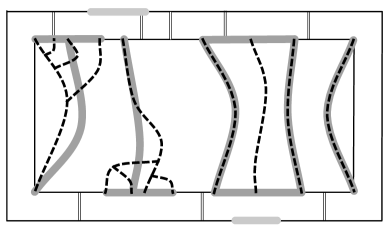
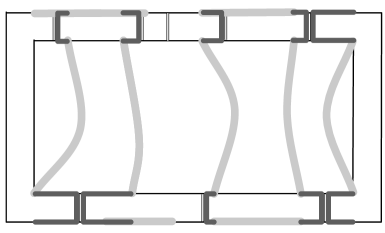
5.1.6 Rejoin
In this step, we make inter-brick connections for parts that were disconnected in the mapping step. Since joining vertices represent the ends of all disconnected parts, it suffices to connect joining vertices of with to their mortar-graph counterparts via portal edges.
This is illustrated in Figure 11 (d): We first move the edges of to for every brick . Such edges may have been introduced in the restructure step: for every brick , we connect to the mortar graph. For every joining vertex of , we find the nearest portal , add the subpath of and connecting and and add the portal edge corresponding to . (We need at most two copies of each portal edge.) Finally we contract the edges introduced in the cleaving step. This produces a solution of .
5.2 Analysis of connectivity
In the augment step, because the added paths and form a cycle, this transformation preserves two-connectivity and connectivity between terminals. Cleaving clearly preserves connectivity and, by Lemmas 5.8 and 5.9, terminals that require two-connectivity are biconnected in . Therefore, for terminals and requiring connectivity, there is a path in connecting them. If and require two-connectivity, there is a simple cycle in connecting them. We follow and through the remaining steps.
- Flatten
-
Consider a tree that is replaced by a subpath of a northern or southern boundary of a brick that spans ’s leaves. spans any terminals that spanned, since there are no terminals internal to bricks.
is therefore a (set of) leaf-to-leaf paths and so contains an -to- path. It follows that there is an -to- path in .
By Lemma 5.11, is a single path and, by the above reasoning, is a leaf-to-leaf path. Therefore contains a cycle through and . It follows that there is a cycle through and in
- Map
-
() gets mapped to a sequence , (a cyclic sequence ) of paths of in such that each path either consists completely of mortar-graph edges or consists completely of brick-copy edges. The last vertex of one path and the first vertex of the next path are copies of the same vertex of , and that vertex belongs to a north or south boundary of . By Lemma 5.10, each path in or that consists of brick-copy edges starts and ends at the northern or southern boundary of a brick.
- Restructure
-
We define a mapping , based in part on the map defined in Section 5.1.5. For a path in or that uses mortar-copy edges, define . For a path in or that uses brick-copy edges, let be the tree in that contains and define .
Let be the cyclic sequence of trees and cycles to which maps by . Since spans the leaves (joining vertices) of , consecutive trees/cycles in contain copies of the same vertex. By Lemma 5.11 and that, within a brick, the preimage of the set of trees mapped to by , the trees of are edge disjoint. (The cycles may be repeated.)
Likewise we define having the same properties except for the fact that the sequence is not cyclic.
- Rejoin
-
This step reconnects and .
Consider a tree in either of these sequences that contains brick-copy edges. The rejoin step first moves any edge of that is in a brick boundary to the mortar copy. It then connects joining vertices to the mortar by way of detours to portals and portal edges. Therefore, is mapped to a tree that connects the mortar copies of ’s leaves.
Consider a cycle in either or . contains a subpath of and whose edges are moved to their mortar copy and two -to- paths whose joining vertices are connected to their mortar copies. Therefore is mapped to a cycle through the mortar copies of the boundary vertices of .
Let the resulting sequence and cyclic sequence of trees and cycles be and . Since consecutive trees/cycles in contain copies of the same vertex, in consecutive trees/cycles contain common mortar vertices. We have that is a cyclic sequence of trees and cycles, through and , the trees of which are edge-disjoint. Therefore the union of these contains a cycle through and .
Similarly, we argue that the union of the trees and cycles in contains and -to- path.
5.3 Analysis of cost increase
By Lemma 4.3, the total costs of all the east and west boundaries of the bricks is an fraction of , so we have
| (7) |
The cleaving step only introduces edges of zero cost, so
| (8) |
The flatten step replaces trees by -short paths, and so can only increase the cost by an fraction, giving:
| (9) |
The mapping step does not introduce any new edges, so
| (10) |
The restructure step involves replacing disjoint parts of for each brick by applying Lemmas 5.2, 5.3, and 5.4. This increases the cost of the solution by at most an fraction. Further we add subpaths of where contains disjoint subpaths from to and by the brick properties, . This increases the the cost of the solution by at most another fraction. We get, for some constant :
| (11) |
In the rejoin step, we add two paths connecting a joining vertex to its nearest portal: along the mortar graph and along the boundary of the brick. The cost added per joining vertex is at most twice the interportal cost: at most for a joining vertex with the boundary of brick , by Lemma 4.4. Since each mortar graph edge appears as a brick-boundary edge at most twice, the sum of the costs of the boundaries of the bricks is at most (Equation (1)). Since there are joining vertices of with each brick, the total cost added due to portal connections is at most . Replacing and via Equations (6) and (3) gives us that the total cost added due to portal connections is
| (12) |
Combining equations (7) through (12), for some constant , proving Theorem 4.6.
6 Dynamic Program
In this section we show that there is a dynamic program that finds an approximately optimal solution in the portal-connected graph .
6.1 Structure of solution
We start by showing that we can restrict our attention to solutions whose intersection with each brick is a small collection of trees whose leaves are portals.
Lemma 6.1.
Let be a minimal solution to the instance of the -edge connectivity problem. Let be a brick, and suppose that the intersection of with is the union of a set of non-crossing trees whose leaves are portals. Then the number of such trees is at most three times the number of portals.
Proof.
Let the portals be in counterclockwise order. Each tree induces a subpartition on the set of pairs as follows: if the leaves of the tree are where , then the parts are
Because the trees are non-crossing, the corresponding subpartitions are non-crossing as well: for each pair of trees, either each part of is a subset of some part of , or vice versa.
Therefore the trees themselves form a rooted tree according to the nesting relation of the corresponding subpartitions. Furthermore, by minimality of , no three trees have the same sets of leaves. This shows that a node of with only one child has a parent with at least two children. The number of leaves of is at most the number of pairs , which is at most . This shows that the number of trees is at most . ∎
Corollary 6.2.
There exists a function
that maps each brick to a cardinality-at-most- subpartition
of the portals of with the following property:
for each brick , for each part of , let be any
minimum-cost tree in whose leaves are , and let be the
union . Then there is a feasible solution
to the instance such that
-
•
the cost of is at most where is an absolute constant, and
-
•
the intersection of with any brick is .
Proof.
Theorem 4.6 states that there is a feasible solution of cost at most such that the intersection of with any brick is the multi-set union of a family of non-crossing trees whose leaves are portals. We assume that is a minimal feasible solution. Lemma 6.1 shows that .
Now we construct the multi-subgraph from . For each brick , replace each tree in with a minimum-cost tree having the same leaves. Clearly the cost of is at most that of . It remains to show that is a feasible solution.
Let and be two terminals. Let or be a minimal -to- path or minimal cycle containing and in using edges of . We obtain a -to- path in or a cycle in containing and as follows. For each brick , the intersection of or with is a set of paths through the trees in such that each path starts and ends on a portal. For each path , the tree in connecting the endpoints of is replaced in by another tree that includes the same endpoints, so that tree contains a path with the same endpoints. We replace each path with the path . Let and be the subgraphs obtained by performing these transformations for each brick . The transformations ensure that and are in . The path shows that and are connected in .
For a cycle in , we still need to show that is a cycle. In particular, we need to show that, for each brick , the paths forming the intersection of with all belong to different trees in . Assume for a contradiction that and belong to a single tree . By the assumption that the degree is at most three, and cannot share a vertex. Therefore there is a -to- path in containing at least one edge. However, since is a cycle containing and , an edge of the -to- path can be removed while preserving feasibility, a contradiction. ∎
6.2 The tree used to guide the dynamic program
Recall that is the brick-contracted graph, in which each brick of is contracted to a vertex. Recall that a parcel is a subgraph of and defines a set of bricks contained by the faces of . The planar dual of the parcel has a spanning tree of depth . The algorithm transforms into a spanning tree of the planar dual of as follows. Each brick is a vertex of ; replace that vertex with a cycle minus one edge consisting of the duals of the portal edges, as shown in Figure 12.
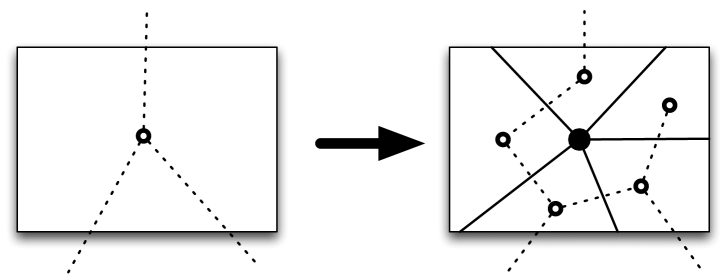
Since each brick has at most portal edges, it follows that the spanning tree of the dual of has depth at most . Next, the algorithm defines to be the set of edges of whose duals are not in . A classical result on planar graphs implies that is a spanning tree of . The construction ensures that each vertex of that corresponds to a brick has only one incident edge in . By our assumption that each vertex in the input graph has degree at most three, every vertex of that appears in has degree at most three in . Thus has degree at most three. The bound on the depth of ensures that, for each vertex of , the graph contains at most edges between descendents of and non-descendents.
6.3 The dynamic programming table
The algorithm considers the spanning tree of as rooted at an arbitrary leaf. By our assumption that the input graph has degree three, each vertex of has at most two children. Let denote the subtree of rooted at . For each vertex of , define
and define to be the subgraph of induced by . Let be the subset of edges with exactly one endpoint in the subgraph (i.e. a cut). It follows that the cut in is equal to the cut in and so has edges. The dynamic programming table will be indexed over configurations, defined below.
6.3.1 Configurations
Let for a connected, vertex-induced subgraph of . We define a configuration corresponding to , illustrated in Figure 13. First, for each edge , we defined two edges and to reflect the fact that an edge can be used twice. Let be the resulting set of edges, . A configuration is a forest with no degree-2 vertices whose leaf edges are a subset of , and such that, for each edge , if the forest contains both and then these two edges are incident to the same vertex in the forest, together with a labeling of the internal vertices. We denote the set of all configurations on edge set by .
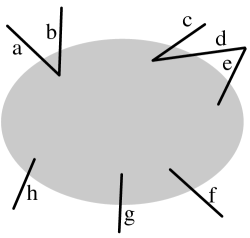
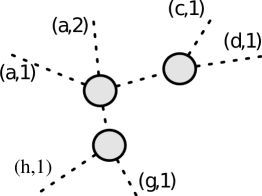
Lemma 6.3.
The number of configurations for where is at most and these trees can be computed in time.
Proof.
A configuration can be selected as follows. First, for each of the edges, decide whether edge is to be included and whether is to be included. (There are choices.) Let be the number of edges for which either or is to be included. Next, select a tree with the selected edges as leaf edges. It follows from Cayley’s formula that the number of such trees is , which is at most . Next, delete some subset of non-leaf edges of the tree. There are at most ways of selecting such a subset. Finally, select a labeling of the internal vertices. There are at most such labelings.
The set of trees can be computed in amortized time per tree [22]. ∎
Connecting
A configuration is connecting if, for each internal vertex of , if has label then contains paths from to leaves.
Compatibility
Configurations and are compatible if for every edge either or .
Compressed bridge-block forest
For a graph , a block is a maximal subgraph such that, for every two vertices and in the subgraph, there are two edge-disjoint -to- paths. Contracting each block of to a single vertex yields the bridge-block forest of . It is easy to see that it is indeed a forest. An edge of is an edge of this forest if is a bridge of , i.e. if the endpoints of are in different connected components of .
We define the compressed bridge-block forest to be the forest obtained from the bridge-block forest by substituting an edge for each maximal path of internal degree two. We denote the compressed bridge-block forest of by .
Consistency
We say a configuration is consistent with a set of mutually compatible configurations if
-
•
there is an isomorphism between and that preserves the identity of leaf edges of , and
-
•
for each vertex of that is labeled 2, is in a block of that corresponds to a vertex in that is labeled 2.
Meeting
Let be a connected, vertex-induced subgraph of . Let be a minimal solution to an instance . Let be the graph obtained from as follows. Remove edges not in . Next, for each vertex outside of , if has incident edges, replace with copies of , one incident to each of these edges.
We say meets a configuration if and if, for each terminal in , either contains edge-disjoint paths to vertices outside of or contains edge-disjoint paths to every other terminal .
DP table entry
The dynamic program constructs a table for each vertex of . The table is indexed by the configurations of . We showed in Section 6.1 that we can restrict our attention to solutions with the following property:
the intersection with each brick is a cardinality-at-most- collection of minimum-cost trees whose leaves are portals.
For each configuration of , the entry is the minimum cost of a subgraph of that meets configuration and has the above property. We do not count the cost of edges of .
6.3.2 The filling procedure
If is not a leaf of , then we populate the entries of with the procedure fill. We use the shorthand for and for . The cuts are with respect to the graph .
| fill | |||
| Initialize each entry of to . | |||
| Let be the children of . | |||
| For every set of connecting, mutually compatible configurations , | |||
| For every connecting configuration that is consistent with , | |||
| . | |||
Since has degree at most three, the number of children of each vertex in is at most two.
If is a leaf of and does not correspond to a brick (i.e. ), the problem is trivial. Each configuration is a star: is the center vertex, and the edges of are the edges of . Since the cost of any subgraph that is induced by is zero, the value of is zero for every .
Suppose is a leaf of and is a brick . Recall that we restrict our attention to solutions whose intersection with is a collection of at most minimum-cost trees whose leaves are portals. The algorithm populates the table as follows. Initialize each entry of to . Next, iterate over cardinality-at-most- families of subsets of the portals. For each family ,
-
•
define a subgraph to be the multi-set union over subsets in of a minimum-cost tree spanning ,
-
•
find the configuration corresponding to , and
-
•
set .
The minimum-cost tree spanning a subset of portals can be computed in time using the algorithm of Theorem 2.1.
6.3.3 Running time
Consider the time required to populate the for all the leaves of . We need only consider non-crossing partitions of subsets of since is the union of non-crossing trees. The number of non-crossing partitions of an element ordered set is the Catalan number, which is at most . Therefore, the number of non-crossing sub-partitions is at most . It follows that the time to populate for a brick vertex is which is since depends polynomially on . Since a vertex appears at most twice in the set of bricks, the time needed to solve all the base cases in where is the number of vertices in the parcel.
Consider the time required to populate the for all the internal vertices of . The number of edges in in is . By Lemma 6.3, it follows that the corresponding number of configurations is since and each depend polynomially on . There are vertices of the recursion tree and so the time required for the dynamic program, not including the base cases is .
The total running time of the dynamic program is where is the number of vertices in the parcel.
6.4 Correctness
The connecting property guarantees that the final solution is feasible (satisfying the conectivity requirements). The definitions of compatible and consistent guarantee the inductive hypothesis.
We show that the procedure fill correctly computes the cost of a minimum-cost subgraph of that meets the configuration . We have shown that this is true for the leaves of the recursion tree. Since is the configuration corresponding to the cut , is a star. Therefore is the cost of the edges of : is both the configuration and a minimum-cost subgraph that meets that configuration. Further, is the cost of the edges of that are in (for ). is equal to the cost of the edges common to and if and zero otherwise. By the inductive hypothesis the cost computed is that of a : the subgraph of of a minimum-cost graph that meets this configuration.
Consider the entries of where is the root of . Since is empty, there is only one configuration corresponding to this subproblem: the trivial configuration. Therefore, the dynamic program finds the optimal solution in .
As argued in Section 4.4, combining parcel solutions forms a valid solution in our input graph. We need to compare the cost of the output to the cost of an optimal solution.
Recall that new terminals are added at the parcel boundaries to guarantee connectivity between the parcels; let denote the requirements including these new terminals. Let denote the optimal solution in graph with requirements .
For each parcel , there is a (possibly empty) solution in for the original and new terminals in consisting of edges of (where is the set of parcels and is the set of boundary edges of all parcels). We have:
Every edge of not in appears in for exactly one parcel , and so
Every edge of appears in at most two parcels, and so
Since a feasible solution for the original and new terminals in can be obtained by adding a subset of the edges of to , the cost of the output of our algorithms is at most
Combining the cost of the parcel boundaries, the definition of , and the cost of the mortar graph, we obtain . Finally, by Theorem 4.6, the cost of the output is at most . This gives:
Theorem 6.4.
There is an approximation scheme for solving the -edge connectivity problem (allowing duplication of edges) in planar graphs. The running time is .
Comments
The PTAS framework used is potentially applicable to problems where (i) the input consists of a planar graph with edge-costs and a subset of the vertices of (we call the set of terminals), and where (ii) the output spans the terminals. Steiner tree and two-edge-connectivity have been solved using this framework. The PTAS for the subset tour problem [18] (which was the inspiration for this framework) can be reframed using this technique. Since the extended abstract of this work first appeared, Borradaile, Demaine and Tazari have also this framework to give PTASes for the same set of problems in graphs of bounded genus [6], Bateni, Hajiaghayi and Marx [3] have extended the framework to the Steiner forest problem and Bateni et al. [2] have extended the framework to prize collecting problems.
Acknowledgements
The authors thank David Pritchard for comments on early versions of this work and discussions with Baigong Zheng regarding Theorems 2.5 and 2.6. This material is based upon work supported by the National Science Foundation under Grant Nos. CCF-0964037, CCF-0963921, CCF-14-09520 and by a Natural Science and Research Council of Canada Postdoctoral Fellowship.
References
- [1] B. Baker. Approximation algorithms for NP-complete problems on planar graphs. Journal of the ACM, 41(1):153–180, 1994.
- [2] M. Bateni, C. Chekuri, A. Ene, M. Hajiaghayi, N. Korula, and D. Marx. Prize-collecting Steiner problems on planar graphs. In Proceedings of the 22nd Annual ACM-SIAM Symposium on Discrete Algorithms, pages 1028–1049, 2011.
- [3] M. Bateni, M. Hajiaghayi, and D. Marx. Approximation schemes for Steiner forest on planar graphs and graphs of bounded treewidth. J. ACM, 58(5):21, 2011.
- [4] A. Berger, A. Czumaj, M. Grigni, and H. Zhao. Approximation schemes for minimum 2-connected spanning subgraphs in weighted planar graphs. In Proceedings of the 13th European Symposium on Algorithms, volume 3669 of Lecture Notes in Computer Science, pages 472–483, 2005.
- [5] A. Berger and M. Grigni. Minimum weight 2-edge-connected spanning subgraphs in planar graphs. In Proceedings of the 34th International Colloquium on Automata, Languages and Programming, volume 4596 of Lecture Notes in Computer Science, pages 90–101, 2007.
- [6] G. Borradaile, E. Demaine, and S. Tazari. Polynomial-time approximation schemes for subset-connectivity problems in bounded-genus graphs. Algorithmica, 2012. Online.
- [7] G. Borradaile, C. Kenyon-Mathieu, and P. Klein. A polynomial-time approximation scheme for Steiner tree in planar graphs. In Proceedings of the 18th Annual ACM-SIAM Symposium on Discrete Algorithms, pages 1285–1294, 2007.
- [8] G. Borradaile, P. Klein, and C. Mathieu. Steiner tree in planar graphs: An approximation scheme with singly exponential dependence on epsilon. In Proceedings of the 10th International Workshop on Algorithms and Data Structures, volume 4619 of Lecture Notes in Computer Science, pages 275–286, 2007.
- [9] G. Borradaile, P. Klein, and C. Mathieu. An approximation scheme for Steiner tree in planar graphs. ACM Transactions on Algorithms, 5(3):1–31, 2009.
- [10] A. Czumaj and A. Lingas. On approximability of the minimum cost k-connected spanning subgraph problem. In Proceedings of the 10th Annual ACM-SIAM Symposium on Discrete Algorithms, pages 281–290, 1999.
- [11] R. Erickson, C. Monma, and A. Veinott. Send-and-split method for minimum-concave-cost network flows. Mathematics of Operations Research, 12:634–664, 1987.
- [12] K. Eswaran and R. Tarjan. Augmentation problems. SIAM Journal on Computing, 5(4):653–665, 1976.
- [13] G. Frederickson and J. Jájá. Approximation algorithms for several graph augmentation problems. SIAM Journal on Computing, 10(2):270–283, 1981.
- [14] M. Goemans, A. Goldberg, S. Plotkin, D. Shmoys, É. Tardos, and D. Williamson. Improved approximation algorithms for network design problems. In Proceedings of the 5th Annual ACM-SIAM Symposium on Discrete Algorithms, pages 223–232, 1994.
- [15] M. Henzinger, P. Klein, S. Rao, and S. Subramanian. Faster shortest-path algorithms for planar graphs. Journal of Computer and System Sciences, 55(1):3–23, 1997.
- [16] K. Jain. A factor 2 approximation algorithm for the generalized Steiner network problem. Combinatorica, 2001(1):39–60, 21.
- [17] S. Khuller and U. Vishkin. Biconnectivity approximations and graph carvings. Journal of the ACM, 41(2):214–235, 1994.
- [18] P. Klein. A subset spanner for planar graphs, with application to subset TSP. In Proceedings of the 38th Annual ACM Symposium on Theory of Computing, pages 749–756, 2006.
- [19] P. Klein. A linear-time approximation scheme for TSP in undirected planar graphs with edge-weights. SIAM Journal on Computing, 37(6):1926–1952, 2008.
- [20] P. Klein and R. Ravi. When cycles collapse: A general approximation technique for constraind two-connectivity problems. In Proceedings of the 3rd International Conference on Integer Programming and Combinatorial Optimization, pages 39–55, 1993.
- [21] K. Mehlhorn. A faster approximation algorithm for the Steiner problem in graphs. Information Processing Letters, 27(3):125–128, 1988.
- [22] S. Nakano and T. Uno. Efficient generation of rooted trees. Technical Report NII-2003-005E, National Institute of Informatics, 2003.
- [23] R. Ravi. Approximation algorithms for Steiner augmentations for two-connectivity. Technical Report TR-CS-92-21, Brown University, 1992.
- [24] M. Resende and P. Pardalos, editors. Handbook of Optimization in Telecommunications. Springer, 2006.
- [25] H. Whitney. Non-separable and planar graphs. Trans. Amer. Math. Soc., 34:339–362, 1932.
- [26] P. Widmayer. A fast approximation algorithm for Steiner’s problem in graphs. In Graph-Theoretic Concepts in Computer Science, volume 246 of Lecture Notes in Computer Science, pages 17–28. Springer Verlag, 1986.
- [27] D. Williamson, M. Goemans, M. Mihail, and V. Vazirani. A primal-dual approximation algorithm for generalized Steiner network problems. In Proceedings of the 25th Annual ACM Symposium on Theory of Computing, pages 708–717, 1993.
- [28] Y. Wu, P. Widmayer, and C. Wong. A faster approximation algorithm for the Steiner problem in graphs. Acta informatica, 23(2):223–229, 1986.