Towards Data Auctions with Externalities
Abstract
The design of data markets has gained importance as firms increasingly use machine learning models fueled by externally acquired training data. A key consideration is the externalities firms face when data, though inherently freely replicable, is allocated to competing firms. In this setting, we demonstrate that a data seller’s optimal revenue increases as firms can pay to prevent allocations to others. To do so, we first reduce the combinatorial problem of allocating and pricing multiple datasets to the auction of a single digital good by modeling utility for data through the increase in prediction accuracy it provides. We then derive welfare and revenue maximizing mechanisms, highlighting how the form of firms’ private information – whether the externalities one exerts on others is known, or vice-versa – affects the resulting structures. In all cases, under appropriate assumptions, the optimal allocation rule is a single threshold per firm, where either all data is allocated or none is.
Keywords:
Data Markets, Mechanism Design, Externalities
Declaration of interests:
None 00footnotetext: © 2024. This manuscript version is made available under the CC-BY-NC-ND 4.0 license: https://creativecommons.org/licenses/by-nc-nd/4.0/
1 Introduction
There are two key trends in the current era of statistical analysis: (i) an increase in the ease and scale of data collection and exchange due to the growing digitization of modern life; (ii) an increase in the richness of what one can learn from data via large scale statistical analysis due to improved computing capabilities. This is why more and more firms are deploying statistical models to improve their operations and make better decisions regarding, for example, what, when and how much to produce and at what price.
The key differentiating factor that determines the accuracy of these statistical models is access to high-quality data used to train these models, which we henceforth call training data. However, obtaining relevant training data can be challenging for firms, especially if firms do not have the requisite data infrastructure setup to collect data. Addressing this need, many data services now specialize in collecting, aggregating and cleaning data from a wide variety of external sources, and sell it to firms as a product.
In light of the increased usefulness of training data and the growth of data services, firms are increasingly becoming sensitive to the externalities they could face when data is allocated to competing firms. In this paper, we focus our attention on the setting of negative externalities, though under certain conditions, firms may also experience positive externalities from the sharing of data (Raith, 1996). Negative externalities may arise because firms that buy similar data often interact in a downstream market, and the use of data confers on a given firm a competitive advantage which hinders its competitors’ performance. For example, the data being sold could provide information about consumer preferences in the downstream market, which can help a firm capture a larger share of the market via product differentiation. Thus, although data is a freely replicable digital good and in principle can be sold to all firms interested in buying it, a data seller aiming to maximize revenue or welfare must consider the competition structure between buyers in deciding which firms to sell data to, how much to sell, and at what price. Notably, the formal literature which analyzes mechanisms to exchange training data between a collection of buyers and sellers is sparse. Thus, in this paper, we seek to provide a formal answer to the question:
How does the presence of externalities affect the optimal design of data markets?
This question can be approached by solving two coupled problems: First, can we define a tractable yet expressive model for how a buying firm values a collection of datasets and for the externality such a firm experiences when a competing firm is allocated data? Second, given such a model, can we derive efficient or optimal mechanisms to sell data, and how is such a mechanism affected by the presence of externalities?111We note that many data marketplaces do already exist (e.g., Xignite for financial data, Terbine for IoT sensor data (Azcoitia and Laoutaris, 2022)). To the best of our knowledge, these real-world marketplaces tend to offer menu or subscription-based pricing options, but we suspect their pricing strategies are not optimized for welfare or revenue generation given the private valuations of data buyers and possible externalities between them due to downstream competition. Thus one driver of our approach is to explore contexts in which auction-based mechanisms for selling datasets can be optimal. Below, we give an overview of how we tackle these two closely related problems and the answers they provide to the key question posed above.
How to Model a Buyer’s Valuation for Data?
The challenge of modeling a buyer’s utility for data stems from certain characteristics that are intrinsic to virtually all training data used to fit a statistical model: (i) datasets are freely replicable and so have no inherent scarcity; (ii) data is not fungible, and in fact its value is intrinsically combinatorial, i.e., different datasets (or different training features for a statistical model) are bound to have correlations in signal leading to sub-additive or super-additive valuations. In addition, in the presence of externalities, the value a buyer gets from a collection of datasets depends on the data allocated to other competing buyers. Thus a naive parameterization of a buyer’s valuation for a collection of datasets will be exponential in the number of datasets available and in the number of competing firms, rendering such a model intractable.
To circumvent these difficulties, we recall that a major motivation for firms to buy data is to make better predictions. Given this lens and building on the model in Agarwal et al. (2019), a key assumption we make in our formulation is that a buyer’s value for a collection of datasets comes directly from the increase in prediction accuracy it brings to a statistical model. Specifically, we assume that, for each buyer with a given prediction task, there is a commonly known function which maps each collection of datasets to a real number between and . This number is a scalar summary of the increase in prediction accuracy of the statistical model – for example, this could be based on the (normalized) mean-squared error of a regression model trained using these datasets. A buyer’s value for a collection of datasets is then a non-decreasing function of this scalar summary of prediction accuracy. This formulation is not only crucial for a tractable model of a buyer’s valuation over datasets, but also, we believe, a better abstraction for reasoning about the value of data. The inferences drawn from a dataset, rather than the raw data itself, are what is of interest to the buyer of a dataset. Indeed, one would typically be willing to trade one dataset for another as long as the same inferences can be drawn from either of the two datasets.
Further, given that our aim is to understand the effect of externalities in a data market, our model needs to incorporate that a data buyer not only has a positive marginal value for acquiring data, but also has a negative marginal value for its competitors acquiring data. Thus a crucial extension to the model in Agarwal et al. (2019) is that we also assume that the prediction accuracy achieved by a given buyer induces a linear externality on each of the other buyers. This shift in perspective, from raw data to prediction accuracy, along with assuming a linear externality model reduces the combinatorial valuation of each buyer of data to parameters (where is the number of buyers): the positive marginal value for the buyer’s own prediction accuracy and the negative marginal values for the prediction accuracy of the remaining buyers.
The Design and Properties of a Data Market with Externalities.
Given the data valuation and externality model we introduce, we design a data auction for the setting of a monopolistic data seller and potential buyers (or bidders). Since we assume a buyer’s valuation for data is captured by the prediction accuracy, we show that the auction design problem reduces to one of selling a single divisible and freely replicable good. That is, instead of considering the seller as directly allocating data to buyers, we can equivalently consider the seller as allocating prediction accuracies resulting from the same data allocation. Still, a buyer’s bid is multidimensional since it includes private externality parameters in addition to a buyer’s marginal value for their prediction accuracy, and this multidimensionality makes characterizing the welfare-maximizing (i.e., efficient) and revenue-maximizing (i.e., optimal) mechanisms particularly challenging. Further, in such a market, two natural information structures are possible. In the first one, each buyer knows the externalities exerted on them by other buyers, i.e., the buyer’s marginal values for other buyers’ increases in prediction accuracy. In the latter the buyer knows the externalities that they exert on other buyers. We are thus tasked with describing different mechanisms corresponding to the specific information structure and objective being maximized (social welfare or revenue).
Optimal mechanism design with multidimensional bids is notoriously hard and our setting is no exception. When buyers privately know the externalities exerted on them by other buyers, we prove a reduction between the problem of auctioning multiple items to a single additive buyer and our setting. Understanding the structure of optimal mechanisms for the former problem is a major open question in auction theory (even for just two items and i.i.d. valuations). We thus make the problem tractable in this case by restricting either the mechanism structure, or the type distribution. In contrast, when buyers privately know the externalities they exert on other buyers, the problem simplifies and no such restriction is required: we show that the seller ignores the reported externalities and replaces them with their expected values under the common prior.
In all cases, the efficient and optimal mechanisms have a pleasantly simple structure: the allocation rules can be described by thresholds, resulting in allocations, to each given bidder, of either the entirety of the good (equivalently, all the data) or none of it. These thresholds balance a buyer’s marginal value for their own accuracy with others’ (negative) marginal values for the buyer’s accuracy. We also show that under appropriate assumptions, revenue maximization reduces to virtual surplus maximization: the optimal allocation is obtained by replacing the buyers’ marginal values with the corresponding virtual marginal values in the efficient allocation. This property was already observed in the context of single-item auctions (Myerson, 1981), hence our results extend it to the setting with externalities.
The thresholding structure of the optimal allocation has two important robustness implications: (i) the data seller does not require knowledge of the specific statistical models used by the buyers, nor of each buyer’s mapping from data to prediction accuracy, as long as the map is monotonic in the data allocated; (ii) if the prior distribution of private types is unknown, the optimal thresholds can be learned via an online optimization framework. We present such a framework in Appendix A for the case where the buyers’ bids are of the externalities they exert on others.
We now highlight some key properties of the optimal mechanisms that we derive, and how they are affected by externalities. First, we establish that in the presence of externalities, the maximum revenue a data seller can collect increases, even if the overall allocation decreases. This increase in revenue occurs as the data seller collects payments from firms to prevent allocations to other competing firms. Second, a perhaps counter-intuitive property of the optimal mechanisms is that the seller will in some cases collect a payment, which can also be viewed as an entry fee, even from buyers to whom nothing is allocated. This stems from the implicit threat induced by the allocation to other buyers resulting in a negative utility even when a buyer does not participate in the auction. Finally, the payment rules in the presence of externalities extend the intuition of standard second-price auctions. Here, bidders will be charged the minimum externality bid they would have needed to report in order to prevent another bidder from receiving an allocation, in addition to the minimum threshold they needed to bid in order to receive their own allocation. These key properties laid out above provide a meaningful answer to the main question of this paper posed earlier, of how externalities affect the optimal design of data markets.
As our key technical contribution, we extend the Myersonian auction format to the setting of a non-rival, excludable good with multidimensional bids that capture negative externalities. This provides novel results on the design and properties of the optimal mechanism for such settings.
Outline of the Paper.
We conclude the introduction with a discussion of the related work. In Section 2, we formulate the utility model of the firms, discuss our modeling assumptions and present the auction design problem. In Section 3 and Section 4 we describe the welfare- and revenue- maximizing mechanisms respectively. We conclude with a discussion of our main results in Section 5. In Appendix A, we extend our mechanism to when the prior distribution of types is unknown. The remaining appendices contain proofs of our results.
1.1 Related Work
Economics of Information Goods.
The question of information sale has been the subject of a long line of work going back at least to the papers of Admati and Pfleiderer (1986, 1988, 1990) and more recently Kastl et al. (2018); Babaioff et al. (2012); Bergemann et al. (2018); Bimpikis et al. (2019). In this line of work, a (most often) monopolist information seller chooses an information structure—that is, sets of signals and distributions over signals—to offer to one or more agents engaged in a downstream game of incomplete information. The information received by the agents allow them to take better actions in the downstream game, thus increasing their utility. Similar to our results, some of these works find that under certain regimes of competition between firms, it is indeed optimal to sell to a strict subset of firms, balancing gains from information and negative externalities from competition. Importantly, in this line of work, the agents have no private information, hence the information seller does not face a screening problem and can extract the entirety of the surplus generated by their chosen information structure. Consequently, the seller’s problem becomes the one of finding an information structure that maximizes this surplus.
Raith (1996); Ziv (1993) considered the related problem of sharing market-relevant information among competing oligopolists, and showed that the effect of such information sharing on the overall welfare of the firms depends on the type of competition in which they are engaged (e.g. Bertrand or Cournot competition), and the type of market-relevant parameters they are sharing (e.g. firms’ individual production cost estimates or a common market demand parameter). In some cases it is not optimal for any firm to share information with the others, due to the overwhelming negative effects of increased competition on their downstream profit. These findings motivate the study of how different forms of interdependent valuation functions may affect the welfare-maximizing or revenue-maximizing allocation of data. Hellwig and Veldkamp (2009); Myatt and Wallace (2012); Amir and Lazzati (2016) study the closely related problem of information acquisition: there, the information structure is not designed to optimize a specific objective, but rather the goal is to understand which signal(s), among a pre-existing collection, the agents will choose to acquire and analyze the impact of these signals on the downstream equilibrium.
A related but more recent line of work is the one of information design (Elliott et al., 2021; Armstrong and Zhou, 2022) and the closely related problem of Bayesian persuasion. There again, an information designer chooses an information structure to offer to one or more agents engaged in a downstream game of incomplete information. The main difference with information sale is one of perspective: the goal is not as much to find the information structure that maximizes the information provider’s profit, but rather to characterize the set of equilibria that can be induced by the information structure. Typically, the agents are modeled as firms engaged in a downstream market, and one wishes to characterize the range of possible market outcomes (firm-favored vs. consumer-favored). As in the case of information sale, the agents have no private information (prior to receiving a signal from the information provider) and the problem is purely one of designing the information structure, without screening.
In reality, data buyers may have private informational priors and valuations on dataset allocations, which calls for the integration of an auction framework that incentivizes participation and truthful bidding by the buyers. A growing collection of recent papers (Bonatti et al., 2023; Candogan and Strack, 2023; Bonatti et al., 2024; Rodríguez Olivera, 2024; Segura-Rodriguez, 2022)222This line of work postdates the first online appearance of the present paper which directly influenced (Bonatti et al., 2024, 2023). extends standard information design to situations in which the agents have private information (for example, their cost of taking an action in the downstream game). The problem becomes one of jointly designing the information structure (often to maximize a specific objective such as welfare or revenue) while at the same type eliciting the agents’ private information via a truthful direct revelation mechanism. This is a challenging problem that has so far only been considered for single-dimensional types, with the exception of Segura-Rodriguez (2022) (but where there is only a single buyer).
In summary, compared to these papers, our model and assumptions are less sophisticated from an information design perspective but richer from a mechanism design perspective. Indeed, we abstract away the details of downstream game and hence do not have to reason about the impact of the allocated information on the downstream equilibrium.333At a formal level, this means that we do not have to consider the obedience constraint from information design. On the other hand, we explicitly model allocative externalities and allow agents to express preferences about those. As we will show, these reduces our problem to the one of allocating a digital (freely replicable) good to multiple agents in the presence of allocative externalities. We thus face a multidimensional screening problem which is absent from the literature on information design with elicitation. This makes our work closer at a technical level to the literature on auctions with externalities which we discuss below.
Sale of Data.
Still within the mechanism design literature, but moving away from information design, another line of work studies mechanism design for the sale of data, in which the value of data is derived from its informativeness in a learning task. For procurement auctions, Ghosh and Roth (2011) consider a setting in which the buyer wishes to estimate a population statistic while the sellers experience a cost due to privacy loss. In Roth and Schoenebeck (2012), the authors consider a similar problem but assume a known prior on the sellers’ costs. A budget-feasible regression problem is considered in Horel et al. (2014) and Abernethy et al. (2015) consider an online learning setting. Agarwal et al. (2019) develops a two-sided market for selling and buying data, capturing the value of data through increases in prediction accuracy for buyer-specific machine learning models. In our work, we build on this model of valuation and study auctions of data in the presence of externalities.
Other recent works look specifically at the sale of consumer data to firms. Bergemann and Bonatti (2019) provide an excellent survey by considering a general data market framework featuring data buyers, data sellers, and data intermediaries. Key questions at hand include how data should be priced and possibly versioned, either directly by the data sellers or by the data intermediaries. Taylor and Wagman (2014) study specific settings in which firms in an oligopoly may use consumer data to set personalized prices, and find that the outcomes of data policies strongly depend on the oligopoly structure. Acemoglu et al. (2019) study a form of externalities between data sellers who value their privacy. In their model, correlations between consumer signals yield equilibria where consumers sell their data for very cheap prices despite having high values for privacy. Bergemann et al. (2020) similarly consider correlations between consumers’ data in the context of personalized pricing. The authors find that in order to maximize profits, a data intermediary should only sell an aggregate statistic, rather than individual values, of consumer demand to price-setting firms. Like Taylor and Wagman (2014), we consider externalities among data buyers, but assume a general model of additive negative externalities among the buyers that doesn’t necessarily have to arise from competition in oligopoly. Finally, Acquisti et al. (2016) provide a comprehensive review on the economic and privacy implications of collecting, using, and selling consumer data from both theoretical and empirical perspectives.
Auctions with Externalities.
Both efficient and optimal auctions of a single nondivisible good to multiple buyers are well understood in the absence of externalities among the buyers. A welfare-maximizing auction is given by the celebrated Vickrey auction (Vickrey, 1961) which is a second-price sealed bid auction, and a Bayesian-optimal auction for buyers with identical type distributions is given by a second-price auction with a reservation price (Myerson, 1981).
The most relevant line of work in the auction literature studies the question of designing auctions in the presence of externalities. The survey Jehiel and Moldovanu (2006) provides a useful reference. Optimal single-item auctions with additive allocative externalities among bidders were studied in Jehiel et al. (1996, 1999). They consider the same multidimensional, interdependent valuation setting as the one presented here, and provide characterizations of truthful and individually rational mechanisms. However, in order to solve revenue maximization under the information structure setting of known incoming externalities (defined in Section 2.3), Jehiel et al. (1999) impose restrictive symmetry assumptions which effectively reduce the problem to one with a single-dimensional bidding structure. In this paper, we provide a hardness result for the general revenue maximization problem and provide two additional conditions which each yield sensible, yet tractable solutions.
Many papers consider a similar additive model, but often assume that externality parameters are public (Aseff and Chade, 2008; Brocas, 2013) or do not depend on the identity of the competitor (Belloni et al., 2017), effectively reducing the auction to the single dimensional setting. Closest to our work is Deng and Pekec (2011) which extended the setting of Jehiel et al. (1996) to the situation where copies of the same indivisible item are being sold. However, their focus was on quantifying the effect of changing the parameter . Finally, Haghpanah et al. (2013); Zhang et al. (2018) consider single-dimensional non-additive models of externalities yielding tractable auctions.
2 Model
2.1 Data Valuation Model
We consider firms, in the set , acquiring data from a monopolistic data seller with the goal of increasing the prediction accuracy of a statistical model. The data owned by the seller is a finite data set , any subset of which could be sold to any of the buyers. For example, could be a collection of training features or database records. Importantly, data is freely replicable and the seller can for example decide to sell the same subset to two different buyers.
Formally, each firm is parameterized by a “Gain Function”, , which is a set function mapping a subset , to a measure of the prediction accuracy (e.g., (normalized) mean squared error, -accuracy) resulting from the acquisition of . Implicit in are the particulars of the ML model that is trained and used to make predictions through the acquired information. A different for each buyer indicates that we allow each buyer to have a different prediction task or a different prediction procedure. We impose two natural properties on the gain function for each firm .
Property 1 (Monotonicity).
For any two subsets , .
Property 2 (Normalization).
We assume that is normalized such that and . Here denotes the empty set, i.e., no information is allocated to firm i.
Property 1 makes the natural assumption that the gain function is monotone in the amount of information allocated. Property 2 is simply to normalize the various gain functions, and is without loss of generality.
Given a subset of data allocated to firm , define the allocation variable to be the resulting gain in prediction accuracy. Because of Property 2, we have where denotes firm getting allocated the entire set , and denotes firm getting allocated no information.
For each , we assume that firm ’s valuation for a given vector of allocations is given by
| (1) |
where is firm ’s marginal value for an increase in its own prediction accuracy and the externality parameters are the marginal values for a decrease in the prediction accuracies of firms .444We could also allow to capture positive externalities. Characterizations of incentive compatible and individually rational (IR) mechanisms presented in this paper would still hold, but with a different “critical type” defined for IR payments. We focus on negative externalities in this paper, which already yields a rich set of phenomena. Thus, a firm’s valuation for data is linear in the gain in prediction accuracy obtained, and linear in the increases in prediction accuracies of competing firms, in the form of additive negative externalities. As we show in Section 2.2. Equation (1) arises from two natural models of the downstream competition between firms.
Discussion of modeling assumptions.
Inherent in the design of data auctions is the combinatorial nature of data. Since any subset can be selected as a product to be sold, the number of parameters required to capture the valuation function of each firm (including the externalities due to other firms) is in general going to be exponential in the size of the data set and in the number of firms, likely rendering this auction intractable.
Following Agarwal et al. (2019), we circumvent this difficulty by noting that in the setting where firms aim to increase prediction accuracy, it is natural to make the modeling assumption that their valuation is not tied to the specific data that was acquired, but rather from an increase in prediction accuracy of a quantity of interest. Indeed, in some settings, firms may have internal knowledge of how to map an increase in their models’ accuracy to an increase in revenue. For example, streaming platforms may know that an increase in their ability to predict how likely it is for a given user to watch a given video, translates into a increase in advertising revenue. While this assumption abstracts away the details of the competition that the firms engage in and bypasses the need to explicitly model the actions taken by the firms as a result of acquiring information, it is not mutually exclusive with an explicit model of the downstream competition (c.f. examples in Sections 2.2.1 and 2.2.2 below).
Further, the assumption of Property 1 excludes situations in which more information hurts—such as when a more informative experiment (in the sense of mutual information) is worse in the Blackwell order. However, this is a natural assumption in the setting of firms acquiring data for the purpose of increasing the accuracy of a statistical model. Indeed, virtually all estimators studied in statistics come with the guarantee that their statistical error decreases with the number of samples (e.g., the standard least squares estimator for linear regression).
Additionally, in the present model, the externality that each firm exerts on another firm depends only on a parameter and the allocation , which is in direct correspondence with the value that firm receives from its allocation. This allows us to capture how a firm’s increase in performance after acquiring data decreases the utility of competing firms, though it precludes settings where a firm’s utility may depend on additional factors or nonlinear effects such as the correlation between firms’ predictions.
Finally, note that interactions among data buyers do not always feature negative externalities. For instance sharing fraud data between banks or patient data between hospitals may benefit all parties involved (e.g., Rasouli and Jordan (2021)), and the trade-off is in the cost of acquiring and sharing data rather than in the negative externalities between buyers.
2.2 Examples of Downstream Competition
2.2.1 Quality-Based Competition
Consider a setting where two firms, indexed by , such as two smart phone companies, sell similar goods to a population of consumers. Each consumer has a type representing their sensitivity to a good’s quality and they derive a utility for buying firm ’s good. Here, is the product quality, is the price, and is a parameter representing the public perception (e.g., due to advertising effort) of each firm . Thus, those consumers with higher type have a higher willingness to pay for an increase in quality. This parameterization of consumer utility has been widely studied in the economic literature (Leland, 1977; Wauthy, 1996; Chambers et al., 2006). Note that quality can also be interpreted as the alignment of the design parameters of a firm’s good with consumer preferences; it essentially measures how much utility a consumer derives from buying the good.
Suppose the market is fully covered and each consumer only wishes to purchase one good and selects the firm that maximizes its utility . Then each firm ’s net utility, given the price , unit production cost , and quantity of goods sold is , where the last term represents the fraction of the consumer population that purchases from firm .
Suppose now each firm may buy data to improve the quality of its good, or equivalently, improve the alignment of design parameters with consumer preferences, e.g., with new smart phone features, thus increasing to . The following result (proved in Section˜B.1) shows that, under the consumer type distribution studied in Chambers et al. (2006), the resultant increase in firms’ utilities follows the linear model (1).
Fact 2.1.
Given the quality-based consumer model above where consumer types are distributed according to the density function for for some . Assume that the prices are fixed and that . Then, firm ’s valuations of an allocation of data is given by (1) with
for with .
2.2.2 Cournot Competition
In the previous section, we have seen that quality-based competition can be captured exactly by the linear externality model (1). However, note that such a linear model could also be taken as a first-order approximation of a general valuation function with respect to , the allocation vector. We now illustrate this in a case of Cournot competition where externalities turn out to be negative (see also (Jehiel et al., 1996, Section I)).
Consider two firms, indexed by , producing perfect substitute goods. Each firm decides on a production input quantity , and has a unit production cost is , such that the production cost incurred by firm is . Meanwhile, firm ’s production output, or yield, is given by , where captures the production efficiency of firm . Let be the market demand parameter, such that the market clearing price is . A standard computation gives the equilibrium profits of each firm for a given set of parameters .
Let us further assume that firms can purchase data from a third party, and that using such data results in an increase of production efficiency. For , let denote firm ’s production efficiency after acquiring the data, the allocation of which is represented by .555Note, can easily be normalized to lie in so that Property 2 holds. Further, such an falls within the framework of data markets; our formulation does not actually require that the gain function is a prediction task, rather a function that maps allocations of data to utility. Each firm’s valuation for an allocation of data is the difference in its equilibrium profit before and after the changes in production efficiency. The next result shows that to first order, each firm’s valuation for follows the linear externalities model (1). In particular, the signs of the coefficients of properly capture the positive value of one’s own data and the negative effects of competition with other firms.
Fact 2.2.
In the above Cournot model of competition, with an allocation of data represented by its resultant increase in production efficiency , for , to the first order in , the change in equilibrium profit of firm 1 satisfies (1) with nonnegative coefficients
| (2) |
where is the original equilibrium production quantity of firm 1. The result holds similarly for firm 2, with the indices 1 and 2 swapped.
The proof of this fact is provided in Section˜B.2. Although any (differentiable) valuation function admits a linear first-order approximation, Eq. (2) allows us to verify that externalities are indeed negative, i.e., that . Furthermore, knowing the explicit dependency of on the problem’s parameters will be useful when discussing the information structure below (cf. Section˜2.3, and Example 2.3 in particular).
2.3 Firm Private Type
Note from (1) that firm ’s valuation is a function of . The private information a firm has, though, may differ from this set of parameters, depending on the details of the downstream interaction of the firms. We call a firm’s private information its “type”. We consider two natural scenarios of private types:
Scenario 1: Knowledge of Incoming Externalities. Firm ’s private type is , with . In this case, firm knows the externalities that other firms exert on firm , which we refer to as firm ’s “incoming externalities”.
Scenario 2: Knowledge of Outgoing Externalities. Firm ’s private type is , with . In this case, firm knows the externalities it exerts on other firms, which we refer to as the firm ’s “outgoing externalities”.
We find that this difference in what defines the private type of a firm, though subtle, crucially affects the form of the optimal allocation and payment functions.
Example 2.3.
Recall the example of quality-based competition in Section˜2.2.1. In the case where relative firm reputations are negligible (), but production costs are private knowledge to firm , then firms privately know the incoming externalities caused by allocations to other firms, and we are in the setting of Scenario 1. On the other hand, if production costs are common knowledge but advertising efforts are private information to firm , then we are in the realm of Scenario 2.
Next, recall the example of two firms in Cournot competition as in Section˜2.2.2. Using the same notations, suppose each firm privately knows its production cost , while it shares a common prior (known to all firms and the data seller) on the distribution of all other firms’ production costs. Further, suppose all initial production efficiencies are common knowledge, as well as the initial equilibrium production decisions —for example, if they were observed in a previous season. Then the parameters and , in (2) are privately known to firm . In other words, this example is exactly captured by Scenario 2 above.
Bidder Type Spaces and Bid Spaces.
Going forward, we use standard auction terminology and refer to firms as bidders. We denote bidder ’s private type as the vector , where denotes the type space of bidder . In Scenario 1, we have , while in Scenario 2, we have , where is the standard basis of . We abuse notation and let refer to both kinds of private types as it will be clear from context for the remainder of the paper. We further assume the type values lie in bounded ranges: and for , and let , and . Let . A vector of types from all the bidders is denoted as . We denote as the vector of all types other than bidder .
We assume bidders are rational, utility-maximizing agents. It is possible that participating in the auction, i.e. submitting a valid bid, receiving an allocation, and making a payment, may leave bidders worse off than simply not participating. To give bidders the option of non-participation, we define the bid spaces and . Then a bidder can report any type in or choose to not participate in the auction by reporting .
Throughout, we use the convention that a “hat” letter denotes a quantity reported by the bidders, as opposed to the “true” realization of the same quantity. For example, denotes the (true) type of bidder while denotes their bid (i.e. reported type). Similarly, and denote respectively the true types and reported types of all bidders but .
Prior Distribution of Bidder Types.
We make the standard assumption that bidders’ private types are drawn independently from commonly known distributions on , for . Let be the joint distribution function of on . For the individual parameters and , we denote the corresponding marginal density and distribution functions by , , and , respectively.
2.4 Auction Design Setup
By the revelation principle (Myerson, 1981), it suffices to consider incentive compatible mechanisms where bidders directly bid their type. The auction design problem consists of designing the following two functions to maximize social welfare or the seller’s revenue: an allocation function and a payment function . In short, given a vector of bids from the bidders, is the resulting vector of allocations and is the vector of payments required of the bidders. Abusing notation, we let denote both the vector of allocations and the function, which maps bids to this allocation vector, and similarly for .
We assume bidders have quasilinear net utility from participating in the auction. That is, given allocation and payment vectors and , respectively, and true types , bidder ’s utility is
Remark 2.4 (Mapping allocations to data subsets.).
Since we modeled as a set function, it can only take a discrete set of values in the range , leading to possible discontinuities in the allocation. In our auction setup, we relax the problem and consider allocations in the continuous domain , i.e. we will treat in the analysis the allocation as being able to take any value in this domain. Given an allocation , the reverse problem of determining a subset corresponding to can be addressed in several ways. Since only takes finitely many values in , there may not always exist a subset such that . However, one can construct probabilistic allocations or add noise to the data to interpolate between values.
As we will prove (c.f. Table 1 in Section 5 for a summary of results), it turns out that even though we relax the problem to the continuous allocation setting, the optimal allocations (for both welfare and revenue maximization), under appropriate assumptions, are single price thresholds (one per firm), above which the seller allocates all information and below which, allocates no information to a firm. Thus, the mechanism remains realizable for the original problem with discrete allocations and we conveniently avoid the issue of these discontinuities by having to only implement the extremal allocations, (i.e., ) and (i.e., ). Our results of all-or-nothing allocations have the additional benefit that the data seller does not need to know the form of , just that Property 1 holds.
Remark 2.5.
The key difference from standard single-item auction setups is that for digital goods, such as data, there is no feasibility constraint on the allocation function . In particular, we do not require that the sum of the allocations (), is less than or equal to one. The absence of this feasibility constraint is key in obtaining a simple structure for the optimal auctions despite it being a multi-dimensional mechanism design problem (i.e., each bidder is parameterized by a -dimensional vector).
Outside Option.
When a bidder chooses not to participate in the auction, the auctioneer cannot charge the bidder any price nor ‘dump’ any goods on the bidder. That is, we have the restriction that and whenever . Note that even if a given bidder chooses not to participate in the auction, allocations to the other, participating bidders can still affect bidder ’s utility through negative externalities. Thus, it will be necessary to specify what the auction does when subsets of bidders don’t participate.
Since we are interested in finding a Nash equilibrium in which all bidders participate (and bid truthfully), it suffices for us to explicitly define the mechanism under single-bidder deviations from equilibrium and the equilibrium itself. Note we do not consider coalition-proof or strong Nash equilibria, which may not exist. Thus, we seek allocation and payment rules and when at most one component of is . Bidder ’s “outside option” denotes the setting where bidder do not participate and all remaining bidders do participate. Bidder ’s outside option utility, or reservation utility, depends only on others’ bids and the true underlying types. Specifically, given a type vector and a vector of bids from other bidders, the outside option utility of bidder is given by
2.4.1 Definitions of IC and IR Mechanisms
We now define the incentive compatibility (IC) and individual rationality (IR) constraints that the mechanisms must satisfy.
Ex-Post Constraints.
We first consider ex-post truthfulness and participation constraints.
Definition 2.6 (Dominant Strategy Incentive Compatibility).
A mechanism is Dominant Strategy Incentive Compatible (DSIC) if for all type vectors and bidder
Definition 2.7 (Ex-Post Individual Rationality).
A mechanism is ex-post Individually Rational (ex-post IR) if for every type vector and bidder
Dominant strategy incentive compatibility expresses that no matter what the true types are and what other players bid, a bidder cannot strictly increase her net utility by bidding untruthfully. Ex-post individual rationality expresses that no matter what the true types are, in a situation where all other bidders participate and bid truthfully, it is better for each bidder to report truthfully than to not participate. These two properties combined imply that participating and reporting truthfully is a dominant strategy equilibrium of the game induced by the mechanism.
Interim Constraints.
In situations where types are drawn from a known prior distribution and bidders reason in expectation over other bidder’s private types conditioned on their own observed types, we consider interim relaxations of the IC and IR definitions. To this end, define to be the interim expected utility of bidder if they bid with a true type of , and all other bidders bid their type truthfully. Note that the expectation is taken over a random realization conditioned on the event that bidder’s type is .
Definition 2.8 (Bayes–Nash Incentive Compatibility).
A mechanism is Bayes–Nash Incentive Compatible (BNIC) if for all types and bidder , .
Definition 2.9 (Interim Individual Rationality).
A mechanism satisfies interim Individual Rationality (interim IR) if for every type and bidder , .
Appendix D provides relevant characterizations of the payment and allocations functions induced by the interim IC and IR constraints, which depend on the form of bidders’ private types.
3 Social Welfare Maximization
In this section, the seller’s problem is to design allocation and payment functions, and in order to maximize the welfare, i.e. the sum of bidder valuations:
| (3) |
such that the auction: (i) is incentive compatible; (ii) satisfies individual rationality; (iii) has no positive transfers, i.e. the seller never pays a bidder to participate in the auction. We organize this section by the private types of the bidders according to the two scenarios described in Section˜2.3.
3.1 Welfare Maximization in Scenario 1: Known Incoming Externalities
We first consider the setting where the private type of bidder takes the form , i.e., each bidder knows the incoming allocative externalities that others exert on bidder . We instantiate the Vickrey–Clarke–Groves (VCG) mechanism and discuss the resulting allocation and payment functions.
We wish to maximize (3) subject to DSIC (Definition˜2.6), ex-post IR (Definition˜2.7), and the feasibility constraint that for all . To define ex-post IR, recall that we need to instantiate the outside option, i.e. what occurs if bidder chooses not to participate in the auction. Here, we choose the natural outside option, that is to run the welfare-maximizing auction with the remaining set of bidders.
Theorem 3.1 (Efficient Mechanism, Scenario 1).
The mechanism with allocation function
| (4) |
outside option and payment function
| (5) |
where is defined as the welfare contribution of bidder when (only) bidder chooses to not participate in the auction to be, for :
maximizes the welfare among all DSIC and ex-post IR auctions, and has no positive transfer.
A full proof of this theorem is given in Section˜E.1. The result is quite intuitive: if a bidder ’s contribution to the overall welfare, , is positive, then bidder receives the good. Each bidder’s payment can be interpreted as the sum of the change in welfare if they leaves the auction and the sum of externalities they induces in the current allocation.
A feature of the welfare-maximizing VCG mechanism in our setting is that it does not guarantee that each bidder’s net utility will be nonnegative, but rather no less than the bidder’s reservation utility, which could be negative due to externalities. Further, while we choose the outside option to be the welfare-maximizing auction with the remaining bidders, as is natural, we could instead have declared the ensuing auction to have any feasible allocation rule for the bidders that does not depend on bidder ’s bid. For instance, a feasible outside option is to allocate all data to every if bidder does not participate, resulting in utility . This is in fact the worst possible outside option for bidder , which thereby increases the set of IR-satisfying mechanisms. Indeed, as discussed in Section˜4, this worst-case outside option is the revenue-optimal one.
3.2 Welfare Maximization in Scenario 2: Known Outgoing Externalities
We now consider the case where each bidder knows the externalities that they would exert on other bidders if allocated the good, i.e., where the private type of bidder , is .
Note that in this scenario, bidder cannot fully evaluate their valuation of a given allocation , as it depends on the parameters , which are part of the private types of bidders . Each bidder can only reason with their own realized type and the commonly known priors on other bidders’ types. It is more sensible, therefore, to impose interim versions of truthfulness (BNIC) and participation (interim IR) conditions (see Definitions˜2.8 and 2.9 respectively).
Ex-Ante Welfare Optimality.
A first attempt toward a welfare-maximizing mechanism here may try to use the VCG allocation rule (4) that maximizes welfare pointwise. Due to Proposition˜D.3, however, this allocation violates BNIC when the private types are of the form , since the corresponding interim allocation is not in general constant with respect to . In fact, any attempt to find such welfare-maximizing BNIC mechanisms will fail. In general, no mechanism satisfying BNIC can be ex-post (pointwise) welfare-maximal over all types , as stated next.
Proposition 3.2 (Impossibility of Ex-Post Optimality).
Suppose private types are of the form for each bidder . For any joint distribution of types , let be the set of allocation functions implementable in Bayes-Nash equilibrium. Then there exists a distribution of types on such that
| (6) |
A proof of this proposition is provided in Section˜E.2. In particular, it makes use of the characterization of BNIC mechanisms given in Proposition˜D.3 of Section˜D.2. The core of this incompatibility result relies on the multi-dimensionality of signals capturing the allocative externalities. Intuitively, because the parameter in bidder ’s report does not directly appear in bidder ’s valuation function, the BNIC constraint prevents mechanisms from eliciting the true value of , thus precluding ex-post efficiency. Such an incompatibility between efficiency and BNIC for multi-dimensional types has been more generally studied in Jehiel and Moldovanu (2001). Note that in the simpler case of selling a single good with interdependent valuations captured by one-dimensional signals, the generalized VCG mechanism Krishna (2009) provides an ex-post IC and efficient allocation.
Since Proposition 3.2 implies that there are distributions in which no mechanism satisfying BNIC can also be welfare-maximizing over all type realizations, we relax the objective of finding a pointwise optimum to one of maximizing the expected welfare, that is,
| (7) |
Under this relaxed optimality condition, the following theorem describes the mechanism that maximizes welfare in expectation rather than pointwise.
Suppose bidders have private types of the form for . Define the virtual valuation functions for . Suppose the functions are non-decreasing, and define the thresholds .
Theorem 3.3 (Efficient Mechanism, Scenario 2).
Suppose that the functions are non-decreasing, for , and define thresholds . Then, the allocation rule maximizing the expected welfare (7) under the BNIC constraint is
| (8) |
where the outside option is set to run the welfare-maximizing allocation on the remaining set of bidders whenever some subset of bidders chooses not to participate in the auction.
A class of BNIC and IR payment rules associated with this allocation is given by
| (9) |
where is a constant satisfying , for some of the form . In particular, if is non-decreasing for , then
| (10) |
The proof of Theorem˜3.3 is provided in Section˜E.3. Similar to the result of Theorem 3.1, the allocation rule can be interpreted as allocating the good (i.e., the entire data set) to bidders who, conditioned on their , have an expected positive contribution to the social welfare. As discussed regarding Proposition 3.2, a BNIC mechanism must ignore the reported bids of outgoing externalities, so they appear in expectations. Furthermore, the payment rule can be interpreted as each bidder paying the minimum threshold they needed to bid (in ) to receive the good, less the expected externalities they suffer from other bidders who are allocated the good, plus a constant that is set by the outside option.
Remark 3.4.
Note that if we were instead selling a non-replicable good, the feasibility constraint would couple the allocations and would be a function of other bids for .
4 Revenue Maximization
In this section, we focus on the problem of designing auctions that achieve optimal revenue. Specifically, the goal is to design allocation and payment functions and to maximize the seller’s expected revenue subject to BNIC and interim IR constraints.
4.1 Revenue Maximization in Scenario 1: Known Incoming Externalities
To begin, we study the revenue maximization problem in the setting where each bidder knows the externalities they incur from other bidders. Throughout this section, we write the type of bidder as .
4.1.1 Hardness result
Our first result shows that finding the revenue-optimal mechanism in this setting is generically as hard as finding the optimal mechanism for the auction of multiple items to a single buyer with an additive utility function. This is a negative result in that the latter problem is notoriously hard, both from a mathematical and computational perspective, even in the simple setting of i.i.d. item valuations. Daskalakis (2015, Sec. 3) gives a good exposition of the main obstacles:
-
•
Even though the items’ valuations are independent, pricing each item separately is not always optimal and it can be necessary for the optimal mechanism to bundle a subset of the items together.
-
•
The optimal mechanism is not always deterministic and sometimes requires offering lotteries over several bundles.
-
•
Even when the item distributions are described by a finite number of parameters, the optimal mechanisms can require offering uncountably many lotteries.
In light of these obstacles, it is perhaps not a surprise that the optimal mechanism is known in just a handful of special cases. This hardness also manifests itself in the algorithmic realm where computing the optimal mechanism is known to be -hard (Daskalakis et al., 2014). The next proposition shows that all these hardness results extend to the auction of a digital good with additively separable externalities by establishing a reduction from the multi-item auction.666We are deeply indebted to Haifeng Xu and an anonymous referee for this argument. A previous version of this paper contained a derivation of the revenue-optimal mechanism that was in contradiction with Proposition 4.1 and therefore incorrect. In Theorem 4.2 below, we show that this former mechanism is optimal among a restricted class of mechanisms.
Proposition 4.1.
The problem of finding a revenue-optimal mechanism for the auction of items to a single additive buyer reduces to optimally selling a (freely replicable) digital good to bidders with additively separable externalities.
The proof of Proposition˜4.1 is provided in Section˜F.1. The main idea is to construct an instance of the -bidder digital good auction from an instance of the -item auction as follows: bidder ’s type distribution is identical to the buyer in the -item auction, and the type distribution of the remaining bidders is supported on the zero vector. In this case, the valuation over allocations of each of the “dummy” bidders is a constant equal to zero, so no payment is collected from them, and the only thing that matters is the effect of their allocations on bidder ’s utility. The allocation of item to the buyer in the -item auction, becomes equivalent, through the reduction, to the allocation to bidder in the -bidder auction.777Some adjustments are necessary due to the sign discrepancy between externalities and item valuations, and the negative reservation utility in the -item auction. The proof is complete after checking that the reduction preserves revenue as well as the IC and IR constraints.
Given this hardness result, we will not attempt to solve our mechanism problem in the most general case. Instead, we consider two structural assumptions under which we can solve for the optimal mechanism:
-
1.
Restricted-dependency mechanisms. In Section˜4.1.2, we limit our search to direct-revelation mechanisms whose allocation to bidder only depends on the parameters capturing the direct effect of bidder ’s allocation on welfare. Formally, we assume that for some function and each .
This assumption, though strictly suboptimal in general, circumvents computational difficulties that arise from the option of bundling allocations (as in optimal multi-item auctions), and is still meaningful in that it allows the mechanism to incorporate the preferences on the allocation to a given bidder from all affected parties.
-
2.
Single-dimensional types. In Section˜4.1.3, we assume each bidder s type vector is maximally correlated in the sense that for every , where is a publicly known scalar multiplier common to all bidders. In this case, bidder ’s type can be parameterized by the single-dimensional value .
4.1.2 Restricted-dependency mechanisms
We first consider revenue maximization over a simpler class of mechanisms for which the allocation to each bidder is only a function of the parameters that directly capture the effect of bidder ’s allocation on welfare. Formally, we assume that for some function and each .
Theorem 4.2.
Suppose bidders have private types of the form for , and consider the class of restricted-dependency mechanisms, where allocation functions are restricted to the form , for some functions , .
When the virtual valuation functions and are nondecreasing, an allocation rule that maximizes the expected revenue among restricted-dependency BNIC and interim IR mechanisms is given by
| (11) | ||||
The proof of Theorem˜4.2 can be found in Section˜F.2.1 and relies on a characterization of BNIC mechanisms tailored to restricted-dependency mechanisms (Lemma˜F.1). Specifically, under the restricted-dependency assumption and due to the mutual independence of bidders’ types, the structure of the interim allocation vector field disentangles in such a way that its th component only depends on the th component of the input vector , for . As a result, the characterization of BNIC simplifies to (i) requiring monotonicity of each of the component interim functions for , and (ii) pinning down the derivative of the interim payment. The latter lets us express, up to an additive constant, the expected revenue solely in terms of the allocation:
From this expression, the form of the optimal allocation follows in a straightforward manner.
Observe that the allocation rule given in Theorem˜4.2 is similar in form to the threshold functions derived in the two social-welfare maximization cases 4 and 8 but with the virtual values now playing the role of the relevant coordinates of the bidders’ private types. In other words, the revenue-maximizing allocation is the one that maximizes virtual welfare. As is typical in revenue maximization settings, the optimal allocation is not efficient in general, that is, allocates the digital good to bidders less often than the welfare-maximizing allocation. An illustrative example is discussed in Section˜5.
Next, we present an optimal threshold-based payment function that implements the allocation of Theorem˜4.2.
Corollary 4.3.
Under the assumptions of Theorem˜4.2, an optimal payment rule that implements the allocation (11) is given by
| (12) |
where we define the following thresholds
The proof of Corollary˜4.3 is given in Section˜F.2.2. We start from the formula for the interim payment in our BNIC characterization (Lemma˜F.1), where it is determined, up to an additive constant, in terms of the interim allocation. As prescribed by Proposition˜D.2, we optimally set the additive constant by making the participation constraint of bidder bind at their “critical type” . A valid choice for the payment function is to simply equate it with the interim payment pointwise: . We choose instead the more interpretable form (12), in which the payment is expressed in terms of the ex-post allocation, and show in the proof that it still integrates to the same interim payment. As a result, the mechanism remains BNIC and results in the same optimal revenue.
The latter form of payments (12) has the following simple interpretation: once we fix the types of all the bidders but , the thresholds and determine, respectively, the minimum bid of that guarantees allocation of the good to bidder , and the minimum bid of that prevents bidder from being allocated the good. Whenever a coordinate of is high enough to make one these “favorable” events occur, the corresponding threshold bid is added to bidder ’s payment. This extends the intuition of second price auctions, wherein bidders pay the minimum bid needed to receive the good, to the current setting with externalities.
4.1.3 Single-dimensional types
Next, we consider the case where the externality parameters in each bidder’s type vector are proportional to the bidder’s value for being allocated the good. That is, we assume that for each bidder and each , , where is a publicly known constant, common to all bidders. The sensitivity of bidder ’s utility to allocations to other bidders is directly correlated with how much bidder values the good for themselves. Under this assumption, each bidder ’s type, , is effectively one-dimensional. We reject any bids for which , so that valid bids are essentially reports of , and let denote the vector of bids from all bidders.
Proposition 4.4.
Assume that for each , with for . For bidder , define their virtual value function and assume it is non-decreasing.
Then, the allocation that maximizes revenue among BNIC and IR mechanisms is
An optimal payment implementing this allocation rule is given by
where and are the threshold types defined by
The proof of Proposition˜4.4 is given in Section˜F.3. Under the assumption that , the interim allocations and interim payment can be written as a function of only. Furthermore, bidder ’s interim utility becomes linear in the single term , which represents the interim aggregated effect of allocations on bidder :
Hence, the situation becomes equivalent, from the perspective of bidder , to the auction of single item with linear utility. The characterization of BNIC therefore simplifies (see Lemma˜F.2) and becomes essentially equivalent to the one of Myerson (1981), only requiring that be non-decreasing and allowing us to write the expected revenue, up to an additive constant as
From here, the optimal allocation is easily obtained and the derivation of the payment is analogous to the one in Corollary˜4.3.
4.2 Revenue Maximization in Scenario 2: Known Outgoing Externalities
Recall that in Scenario 2, the private type of each bidder is . Using the BNIC characterization of Proposition˜D.3, Theorem˜4.5 below shows that the problem of finding the revenue-optimal mechanism reduces to solving distinct optimizations over univariate functions. Throughout this section, we denote by (resp. ) the cumulative (resp. probability) distribution function of the marginal distribution of , for .
Theorem 4.5.
Suppose bidders have private types of the form for . Define the virtual valuation functions for . Suppose the functions are non-decreasing, and define the thresholds . Then the mechanism with allocation functions
and payments
is revenue-optimal among all BNIC and interim IR mechanisms.
The proof of Theorem˜4.5 can be found in Section˜F.4. Similar to the single parameter setting (Myerson, 1981), we obtain that under the stated regularity assumption, the optimal allocation rule takes a simple form: set a threshold value for each bidder above which all data is allocated and below which no data is allocated. In other words, the optimization problem reduces to finding parameters: the optimal threshold value of each bidder. Again, observe that is similar in form to the threshold functions derived for the two social-welfare maximization cases 4 and 8. In contrast to Theorem˜4.2, the virtual function is only applied to the value parameter .
An interpretation of the payment rule is that each bidder pays their threshold value whenever they receive the good. Additionally, they pay an amount equal to the expected sum of externalities averted, which occurs when any bidder is not allocated the good.
Remark 4.6.
Note that in the present case of known outgoing externalities, the optimal allocation rule only depends on the conditional expectations of the externality parameters. Intuitively, since each buyer reports parameters which do not enter into their own utility but do affect the allocations to others, the BNIC condition (see Proposition D.3) can only be enforced if these reports are ignored. This condition was also relevant for the impossibility result for ex-post efficiency in Proposition 3.2.
In contrast, in the case of known incoming externalities studied in Section 4.1, all parameters reported by a buyer enter their own utility and the seller is thus faced with a full-blown multidimensional screening problem, which is significantly more difficult.
Example 4.7.
In the special case where is independent of , then and the last term in the definition of does not depend on . In this case our assumption on is equivalent to the standard regularity assumption of the marginal distribution of (see Myerson (1981)). The payments also take the simpler form:
4.2.1 Single-dimensional types
In analogy to Section˜4.1.3, we now consider the setting of perfectly correlated type parameters, so that for each bidder with value for the good, the externality bidder causes on every other bidder is , where is a common and publicly known constant. The impact of a bidder’s allocation is proportional to that bidder’s own gains from their allocation.
Under this assumption, each bidder ’s type, , is effectively one-dimensional. We reject any bids for which , so that valid bids are essentially reports of , and once again let denote the vector of bids from all bidders. In this setting, have that for , and a direct application of Theorem˜4.5 yields the following corollary describing the optimal mechanism in this case.
Corollary 4.8.
Under Scenario 2, suppose bidders have one-dimensional types with for each and , and that types are independent across bidders. Define the virtual value functions and suppose the the functions are non-decreasing. Then the allocation the optimal mechanism is given by
Defining the thresholds , a corresponding optimal payment function is given by
Observe that for any distribution of bidder types, when there are at least two bidders and is large enough, the functions will no longer be non-decreasing. For example, consider the case when values are distributed uniformly in , so that . The mechanism provided in Corollary˜4.8 requires that , and works when the tradeoff between the value provided and the externalities caused by allocating to bidder is manageable. Once is no longer non-decreasing, however, the mechanism is no longer BNIC and bidders may be incentivized to misrepresent their types if a large reveals a large negative impact on other firms.
5 Discussion of Results
Summary of Results.
In this paper, we introduced a model for data auctions with firms in the presence of externalities. Our main modeling assumptions reduce the (a priori) combinatorial complex problem associated with allocating data to one of designing auctions for a single, freely-replicable good, with linear utilities parameterized by -dimensional types. Depending on the form of the private types of the firms, we described revenue-maximizing and welfare-maximizing mechanisms and found that in all cases, under appropriate assumptions, the optimal allocations is to either allocate all the data to a firm if its value for data sufficiently outweighs the externalities it causes on other firms, or otherwise allocate none of the data. The specific form of this comparison depends on the situation considered and is summarized in Table˜1.
| Scenario 1 () | Scenario 2 () | |
|---|---|---|
| Welfare max. | ||
| Revenue max.† | ||
| Revenue max. with single dim. types |
We now provide some interpretation for Table˜1. In Scenario 1, we go from welfare maximization to revenue maximization with restricted-dependency mechanisms by simply replacing the types (value for data and externalities) with virtual types. This exactly mimics what happens in the standard result Myerson (1981), where virtual values reduce the problem of maximizing revenue to that of maximizing welfare. In Scenario 2, a similar reduction holds, but only the value for data needs to be transformed via the virtual function. Intuitively, since the externalities reported by a firm do not appear in the firm’s own utility but rather only affect other firms’ utilities in this scenario, the optimal allocations must ignore these reports and instead rely on the prior distribution of externalities. An analogous pattern holds for revenue maximization in the case of single-dimensional types, where the externality parameters are perfectly correlated with the value parameters.
The form of the revenue-maximizing payment rules are summarized in Table˜2. Because the payment rules are determined up to a constant by the thresholding allocation rules, the welfare- and revenue-maximizing payments for each bidder take similar forms. As discussed below Corollary˜4.3, in conjunction with the threshold allocation rules, we see that the payment rules in Scenario 1 extend the intuition of second price auctions: bidders pay the minimum bid of needed in order to receive the good, plus the minimum report of externalities needed to prevent other bidders from receiving an allocation. Both the welfare-maximizing VCG payments and the revenue-maximizing payment rules take this form. A similar interpretation holds in Scenario 2, where each bidder pays the minimum bid of needed to receive the good plus the expected externality that was averted from each bidder who did not end up getting the good. Since each bidder pays an amount equal to the potential externalities that were averted, even buyers that receive no data may have a positive payment.
| Scenario 1 () | Scenario 2 () | |
|---|---|---|
| General types† | ||
| Single-dim. types |
Knowledge of the Type Distribution.
Note that the optimal mechanisms are parameterized by thresholds, determining the allocation and payment of each bidder. In Scenario 2, these optimal thresholds depend only on the type distribution, the knowledge of which is thus required to run the optimal auctions. When this distribution is unknown, a natural setting to consider is where the auctioneer learns the optimal thresholds over time by using a sequence of posted price mechanisms, adjusting the value of the thresholds at each time step based on the observed buyer’s decisions. We explore such a setting in Appendix˜A.
Mixed Information Structures.
While we focus on two information scenarios, one in which all incoming externalities are privately known, and the other in which all outgoing externalities are privately known, there may be situations in which a mixture of incoming and outgoing externalities are known. In general, extending our results to mixed types requires motivating a specific mixed type knowledge structure, a separate specification of what to do when type vectors overlap, and possibly adding assumptions for tractable BNIC characterizations and tractable revenue maximization.
First, if the type vectors of two bidders include the same type (e.g., both bidder 1 and bidder 2 know the externality caused by bidder 2 onto bidder 1) and assuming the type structure is known to the auctioneer, the auctioneer can take advantage of this perfect correlation of types and impose an arbitrarily large penalty if the two bidders report different values of that common type. Thus there will be a Bayes–Nash equilibrium in which the bidders report common types truthfully.
Next, if bidders’ type vectors are disjoint in the sense that no bidder parameter is observed by more than one bidder, we can derive characterizations of Bayes Nash incentive compatibility similar to Proposition D.1 and Proposition D.3, with the additional standard assumption that bidder types vectors are independent across bidders. This assumption may not make much practical sense for arbitrary knowledge structures (e.g., if bidder 1 knows , and while bidder 2 knows ). Further, any parameter which is not reported will be considered in expectation conditional on the reported type vectors.
Additionally, as long as one bidder has a private type that includes incoming externalities (and these parameters are not also present in another bidders’ type to land in the first case), then the reduction for the impossibility result of Proposition 4.1 still holds, showing that solving for the optimal mechanism is at least as hard as solving a multi-item, single-bidder auction. Additional assumptions for tractability may be imposed, as was done with the “restricted dependency” assumption in Section 4.1.2, but again, whether these assumptions are sensible or natural depends on the specific mixed-type information structure.
Welfare vs. Revenue Maximization.
To provide intuition on the differences between efficient and optimal mechanisms, consider the special case of two bidders with uniformly distributed type parameters in Scenario 1. The revenue-maximizing restricted dependency allocation function allocates to bidders less often than does the welfare-maximizing allocation function and is in general not efficient. This is illustrated in Fig.˜1, where the welfare-maximizing and revenue-maximizing allocations are shown to partition the type space of into the regions based on bidder 1’s allocation. For details, see Appendix˜C. Keep in mind that these results are obtained under different assumptions. The social welfare case in Scenario 1 is an instantiation of the VCG mechanism and requires no assumption beyond our externality model. In Scenario 2, since firms do not know the externality other firms cause on them, they have to reason in expectation about their utility and hence this scenario requires a common known prior on the type distribution.
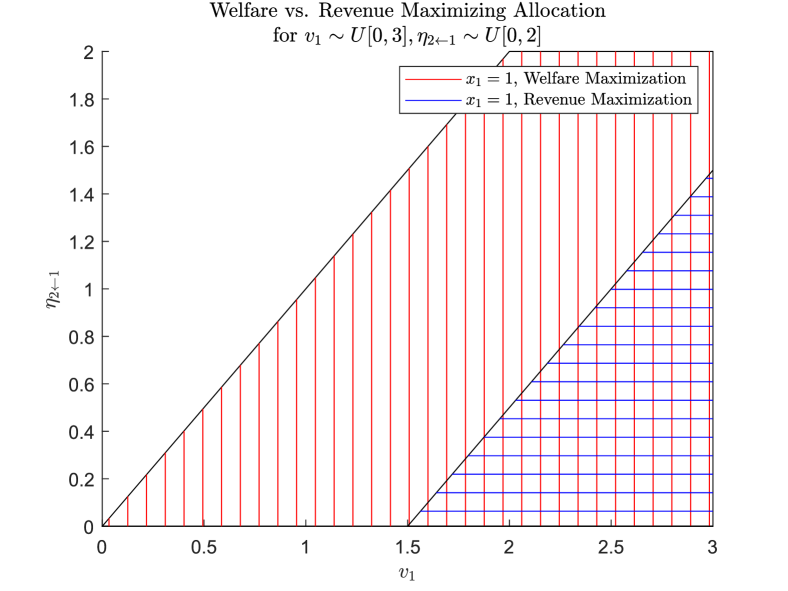
Impact of Externalities.
To further elucidate the effect of the presence and magnitude of negative externalities on the optimal revenue, we consider the simple setting where each bidder has value distributed uniformly in , while externality parameters are deterministic, for . Since the externalities are now common knowledge, Scenario 1 and Scenario 2 are identical. In particular, the optimal mechanism described in Theorem˜4.5 and takes a simple form that we now describe.
For uniform type distributions, the virtual valuation functions are non-decreasing in . A simple computation shows the expected optimal revenue can thus be expressed as , where denotes the share of each bidder’s payment induced by the presence of bidder , and is given by
| (13) |
Some of comments about this expression are in order:
-
1.
When there are no externalities ( for ), we recover the revenue of the optimal posted price mechanism . Otherwise, we see that —and thus the overall revenue—is increasing in the externality parameters for all with .
-
2.
Without externalities, the optimal posted price mechanism allocates with probability . In contrast, in the presence of externalities, there are two regimes: if , the optimal mechanism allocates to with probability , otherwise it never allocates.
-
3.
In both regimes—in particular, even when bidder is not allocated—the optimal mechanism is able to collect at least , corresponding to the “threat” of allocating to bidder in the outside option where bidders do not participate.
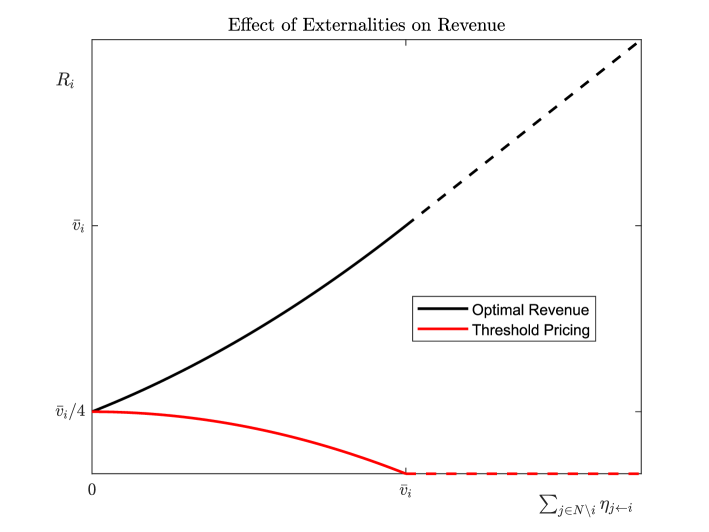
In summary, the presence of externalities implies that the auctioneer can still extract payments from bidders, even when they do not receive an allocation, while still maintaining IR. It turns out that an auctioneer benefits from greater externalities among bidders: even though increased externalities may lead to fewer allocations and therefore less payments directly driven by these allocations (based on ), the entry fee that the auctioneer charges can make up for and actually exceed this loss in profit. However, if the auctioneer were to only charge the optimal threshold upon allocating, without leveraging the outside option, the revenue would in fact be decreasing in the externality parameters. These phenomena are illustrated in Fig.˜2.
Acknowledgments
The authors are grateful to Dirk Bergemann, Alessandro Bonatti, Tan Gan, Andreas Haupt, Ali Jadbabaie and Haifeng Xu for fruitful discussions and comments about this work.
References
- Abernethy et al. [2015] Jacob Abernethy, Yiling Chen, Chien-Ju Ho, and Bo Waggoner. Low-cost learning via active data procurement. In Proceedings of the Sixteenth ACM Conference on Economics and Computation, EC ’15, page 619–636, New York, NY, USA, 2015. Association for Computing Machinery. ISBN 9781450334105. doi: 10.1145/2764468.2764519.
- Acemoglu et al. [2019] Daron Acemoglu, Ali Makhdoumi, Azarakhsh Malekian, and Asuman Ozdaglar. Too much data: Prices and inefficiencies in data markets. Working Paper 26296, National Bureau of Economic Research, September 2019. URL http://www.nber.org/papers/w26296.
- Acquisti et al. [2016] Alessandro Acquisti, Curtis Taylor, and Liad Wagman. The economics of privacy. Journal of economic Literature, 54(2):442–92, 2016.
- Admati and Pfleiderer [1986] Anat R Admati and Paul Pfleiderer. A monopolistic market for information. Journal of Economic Theory, 39(2):400–438, August 1986. ISSN 0022-0531. doi: 10.1016/0022-0531(86)90052-9.
- Admati and Pfleiderer [1988] Anat R Admati and Paul Pfleiderer. Selling and trading on information in financial markets. The American Economic Review, 78(2):96–103, 1988.
- Admati and Pfleiderer [1990] Anat R. Admati and Paul Pfleiderer. Direct and indirect sale of information. Econometrica, 58(4):901–928, 1990. ISSN 0012-9682. doi: 10.2307/2938355.
- Agarwal et al. [2019] Anish Agarwal, Munther Dahleh, and Tuhin Sarkar. A marketplace for data: An algorithmic solution. In Proceedings of the 2019 ACM Conference on Economics and Computation, EC ’19, page 701–726, New York, NY, USA, 2019. Association for Computing Machinery. ISBN 9781450367929. doi: 10.1145/3328526.3329589.
- Amir and Lazzati [2016] Rabah Amir and Natalia Lazzati. Endogenous information acquisition in Bayesian games with strategic complementarities. Journal of Economic Theory, 163:684–698, May 2016. ISSN 0022-0531. doi: 10.1016/j.jet.2016.03.005.
- Armstrong and Zhou [2022] Mark Armstrong and Jidong Zhou. Consumer information and the limits to competition. American Economic Review, 112(2):534–577, February 2022. ISSN 0002-8282. doi: 10.1257/aer.20210083.
- Aseff and Chade [2008] Jorge Aseff and Hector Chade. An optimal auction with identity-dependent externalities. The RAND Journal of Economics, 39(3):731–746, 2008. doi: 10.1111/j.1756-2171.2008.00036.x.
- Azcoitia and Laoutaris [2022] Santiago Andrés Azcoitia and Nikolaos Laoutaris. A survey of data marketplaces and their business models. arXiv preprint arXiv:2201.04561, 2022.
- Babaioff et al. [2012] Moshe Babaioff, Robert Kleinberg, and Renato Paes Leme. Optimal mechanisms for selling information. In Proceedings of the 13th ACM Conference on Electronic Commerce, pages 92–109, 2012.
- Belloni et al. [2017] Alexandre Belloni, Changrong Deng, and Sasa Pekec. Mechanism and network design with private negative externalities. Operations Research, 65(3):577–594, 2017. doi: 10.1287/opre.2016.1585.
- Bergemann and Bonatti [2019] Dirk Bergemann and Alessandro Bonatti. Markets for information: An introduction. Annual Review of Economics, 11:85–107, 2019.
- Bergemann et al. [2018] Dirk Bergemann, Alessandro Bonatti, and Alex Smolin. The design and price of information. American economic review, 108(1):1–48, 2018.
- Bergemann et al. [2020] Dirk Bergemann, Alessandro Bonatti, and Tan Gan. The economics of social data. Cowles Foundation Discussion Paper, 2020.
- Bimpikis et al. [2019] Kostas Bimpikis, Davide Crapis, and Alireza Tahbaz-Salehi. Information sale and competition. Management Science, 65(6):2646–2664, 2019. doi: 10.1287/mnsc.2018.3068.
- Bonatti et al. [2022] Alessandro Bonatti, Munther Dahleh, Thibaut Horel, and Amir Nouripour. Selling information in competitive environments, 2022.
- Bonatti et al. [2023] Alessandro Bonatti, Munther Dahleh, Thibaut Horel, and Amir Nouripour. Coordination via selling information, February 2023.
- Bonatti et al. [2024] Alessandro Bonatti, Munther Dahleh, Thibaut Horel, and Amir Nouripour. Selling information in competitive environments. Journal of Economic Theory, 216:105779, March 2024. ISSN 0022-0531. doi: 10.1016/j.jet.2023.105779.
- Brocas [2013] Isabelle Brocas. Optimal allocation mechanisms with type-dependent negative externalities. Theory and Decision, 75(3):359–387, September 2013. doi: 10.1007/s11238-012-9345-0.
- Candogan and Strack [2023] Ozan Candogan and Philipp Strack. Optimal disclosure of information to privately informed agents. Theoretical Economics, 18(3):1225–1269, 2023. ISSN 1555-7561. doi: 10.3982/TE5173.
- Chambers et al. [2006] Chester Chambers, Panos Kouvelis, and John Semple. Quality-based competition, profitability, and variable costs. Management Science, 52(12):1884–1895, 2006.
- Daskalakis [2015] Constantinos Daskalakis. Multi-item auctions defying intuition? SIGecom Exch., 14(1):41–75, nov 2015. doi: 10.1145/2845926.2845928. URL https://doi.org/10.1145/2845926.2845928.
- Daskalakis et al. [2014] Constantinos Daskalakis, Alan Deckelbaum, and Christos Tzamos. The complexity of optimal mechanism design. In Proceedings of the twenty-fifth annual ACM-SIAM symposium on Discrete algorithms, pages 1302–1318. SIAM, 2014.
- Deng and Pekec [2011] Changrong Deng and Sasa Pekec. Money for nothing: Exploiting negative externalities. In Proceedings of the 12th ACM Conference on Electronic Commerce, EC ’11, page 361–370, New York, NY, USA, 2011. Association for Computing Machinery. ISBN 9781450302616. doi: 10.1145/1993574.1993634.
- Elliott et al. [2021] Matthew Elliott, Andrea Galeotti, Andrew Koh, and Wenhao Li. Market segmentation through information, December 2021.
- Flaxman et al. [2005] Abraham D. Flaxman, Adam Tauman Kalai, and H. Brendan McMahan. Online convex optimization in the bandit setting: Gradient descent without a gradient. In Proceedings of the Sixteenth Annual ACM-SIAM Symposium on Discrete Algorithms, SODA ’05, page 385–394, USA, 2005. Society for Industrial and Applied Mathematics. ISBN 0898715857.
- Ghosh and Roth [2011] Arpita Ghosh and Aaron Roth. Selling privacy at auction. In Proceedings of the 12th ACM Conference on Electronic Commerce, EC ’11, page 199–208, New York, NY, USA, 2011. Association for Computing Machinery. ISBN 9781450302616. doi: 10.1145/1993574.1993605.
- Goldberg et al. [2006] Andrew V. Goldberg, Jason D. Hartline, Anna R. Karlin, Michael Saks, and Andrew Wright. Competitive auctions. Games and Economic Behavior, 55(2):242 – 269, 2006. ISSN 0899-8256. doi: 10.1016/j.geb.2006.02.003. Mini Special Issue: Electronic Market Design.
- Haghpanah et al. [2013] Nima Haghpanah, Nicole Immorlica, Vahab Mirrokni, and Kamesh Munagala. Optimal auctions with positive network externalities. ACM Trans. Econ. Comput., 1(2), May 2013. ISSN 2167-8375. doi: 10.1145/2465769.2465778.
- Hellwig and Veldkamp [2009] Christian Hellwig and Laura Veldkamp. Knowing what others know: Coordination motives in information acquisition. The Review of Economic Studies, 76(1):223–251, January 2009. ISSN 0034-6527. doi: 10.1111/j.1467-937X.2008.00515.x.
- Horel et al. [2014] Thibaut Horel, Stratis Ioannidis, and S. Muthukrishnan. Budget feasible mechanisms for experimental design. In Alberto Pardo and Alfredo Viola, editors, LATIN 2014: Theoretical Informatics, pages 719–730, Berlin, Heidelberg, 2014. Springer Berlin Heidelberg. ISBN 978-3-642-54423-1.
- Jehiel and Moldovanu [2001] Philippe Jehiel and Benny Moldovanu. Efficient design with interdependent valuations. Econometrica, 69(5):1237–1259, 2001. ISSN 00129682, 14680262.
- Jehiel and Moldovanu [2006] Philippe Jehiel and Benny Moldovanu. Allocative and Informational Externalities in Auctions and Related Mechanisms, volume 1 of Econometric Society Monographs, page 102–135. Cambridge University Press, 2006. doi: 10.1017/CBO9781139052269.005.
- Jehiel et al. [1996] Philippe Jehiel, Benny Moldovanu, and Ennio Stacchetti. How (not) to sell nuclear weapons. The American Economic Review, 86(4):814–829, 1996. ISSN 00028282. doi: 10.2307/2118306.
- Jehiel et al. [1999] Philippe Jehiel, Benny Moldovanu, and Ennio Stacchetti. Multidimensional mechanism design for auctions with externalities. Journal of Economic Theory, 85(2):258 – 293, 1999. ISSN 0022-0531. doi: 10.1006/jeth.1998.2501.
- Kastl et al. [2018] Jakub Kastl, Marco Pagnozzi, and Salvatore Piccolo. Selling information to competitive firms. The RAND Journal of Economics, 49(1):254–282, 2018. ISSN 1756-2171. doi: 10.1111/1756-2171.12226.
- Krishna [2009] Vijay Krishna. Auction theory. Academic press, 2009.
- Leland [1977] Hayne E Leland. Quality choice and competition. The American Economic Review, 67(2):127–137, 1977.
- Myatt and Wallace [2012] David P. Myatt and Chris Wallace. Endogenous information acquisition in coordination games. The Review of Economic Studies, 79(1):340–374, January 2012. ISSN 0034-6527. doi: 10.1093/restud/rdr018.
- Myerson [1981] Roger B. Myerson. Optimal auction design. Mathematics of Operations Research, 6(1):58–73, 1981. ISSN 0364765X, 15265471.
- Raith [1996] Michael Raith. A general model of information sharing in oligopoly. Journal of Economic Theory, 71(1):260–288, 1996.
- Rasouli and Jordan [2021] Mohammad Rasouli and Michael Jordan. Data sharing markets. arXiv preprint arXiv:2107.08630, 2021.
- Rodríguez Olivera [2024] Rosina Rodríguez Olivera. Strategic incentives and the optimal sale of information. American Economic Journal: Microeconomics, 16(2):296–353, May 2024. ISSN 1945-7669. doi: 10.1257/mic.20210372.
- Roth and Schoenebeck [2012] Aaron Roth and Grant Schoenebeck. Conducting truthful surveys, cheaply. In Proceedings of the 13th ACM Conference on Electronic Commerce, EC ’12, page 826–843, New York, NY, USA, 2012. Association for Computing Machinery. ISBN 9781450314152. doi: 10.1145/2229012.2229076.
- Segura-Rodriguez [2022] Carlos Segura-Rodriguez. Selling data, August 2022.
- Taylor and Wagman [2014] Curtis Taylor and Liad Wagman. Consumer privacy in oligopolistic markets: Winners, losers, and welfare. International Journal of Industrial Organization, 34:80–84, 2014.
- Vickrey [1961] William Vickrey. Counterspeculation, auctions, and competitive sealed tenders. The Journal of finance, 16(1):8–37, 1961.
- Wauthy [1996] Xavier Wauthy. Quality choice in models of vertical differentiation. The Journal of Industrial Economics, pages 345–353, 1996.
- Zhang et al. [2018] Chaoli Zhang, Xiang Wang, Fan Wu, and Xiaohui Bei. Efficient auctions with identity-dependent negative externalities. In Proceedings of the 17th International Conference on Autonomous Agents and MultiAgent Systems, AAMAS ’18, page 2156–2158, Richland, SC, 2018. International Foundation for Autonomous Agents and Multiagent Systems.
- Ziv [1993] Amir Ziv. Information sharing in oligopoly: The truth-telling problem. The RAND Journal of Economics, pages 455–465, 1993.
Appendix A Prior-independent mechanism
A natural concern with the optimal mechanisms described in Section 4 is that they rely on the knowledge of the type distribution. For example, even in the regular case of Theorem 4.5, the threshold value of bidder is described as the zero of the virtual value function which itself depends heavily on the distribution of the type of bidder . In this section, we explore a situation where the type distribution is initially unknown by the mechanism designer and learned over time.
This problem falls within the realm of online stochastic optimization, and more specifically stochastic derivative-free optimization: indeed, the binary decisions of the bidders at each time step let us compute an unbiased estimator of the the expected revenue, which is the only prerequisite of derivative-free optimization procedures. Standard procedures to do so, such as the one described in Flaxman et al. [2005], can then be applied to algorithmically update the thresholds at each time step and provide an upper bound on the rate of convergence to the optimal revenue.
A.1 Problem description
We consider a sequential learning setting in which at each time step, the seller attempts to sell a digital good in an auction with buyers whose types are drawn from an unknown distribution. The task of the seller is to design an auction mechanism to both satisfy the BNIC and IR constraints at each time step, and also learn the unknown distribution over time and converge to the optimal auction. Specifically, at time step :
-
1.
the data seller announces the BNIC and IR mechanism which will be used for this time step;
-
2.
a vector of types is drawn from the distribution independently of previous time steps;
-
3.
the good is allocated according to and the seller collects the payments .
We emphasize that the underlying distribution from which the types are drawn is unknown to the seller and so cannot depend directly on it. However, the seller observes the types reported in previous time steps and can use these observations to inform the design of and . A natural benchmark to evaluate the performance of the chosen sequence of mechanisms is to compare its cumulative revenue to the one which would have been obtained using the optimal auction. Formally, let and denote the revenue-optimal BNIC and IR auction—which depends on the distribution —and define the regret up to time step by
The goal of the data seller is thus to design a sequence of mechanisms which incurs as small a regret as possible.
Remark A.1.
An important assumption in this sequential learning setting is that the buyers’ types are redrawn at each time step from the same distribution and that buyers only strategize within each time step (hence the BNIC and IR constraints) but not across times steps. As such, we ignore intertemporal incentive issues, which could for example lead buyers to misreport their types in order to bias the learning of the distribution that the seller performs over time. We note that an alternative learning model would consider a single-shot auction in which buyers’ types are drawn from identical distributions. In this case, one can still hope to learn the type distribution in a single time step as the number of buyers goes to infinity. The problem of buyers misreporting their types can be addressed by learning the unknown distribution from a subsample of the buyers and then using the learned mechanism only on the remaining buyers. This approach was for example adopted in Goldberg et al. [2006].
A.2 A stochastic optimization solution
We now provide a solution to the sequential learning problem of Section A.1 which leverages the specific structure of the optimal mechanism described in Section 4.2. We will make the following two simplifying assumptions:
-
•
for each buyer , the distribution of her value is independent from the distribution of externalities she causes on others. Furthermore, for all and , the expectation is known to the seller;
-
•
for each buyer , the function is non-decreasing.
Under these assumptions, Theorem 4.5 combined with Example 4.7 imply that the revenue-optimal BNIC and IR mechanism is given by
where for described in Theorem 4.5. A simple computation further implies that
| (14) |
This formula has a number of important consequences. First, observe that the mechanism obtained by replacing by any other vector of thresholds is also BNIC and IR. Since the optimal mechanism is given by the choice of , optimizing the function over the choice of is sufficient to obtain the optimal mechanism. In other words, the problem of finding the optimal mechanism reduces to the optimization of the function . Furthermore, note that this maximization problem is separable: denoting by the summand in (14) we have that and hence, the problem reduces to separately maximizing each function over the choice of a single-dimension parameter . Finally, observe that the derivative of is which is non-increasing by assumption. Hence, the function is concave.
Learning as stochastic optimization.
The previous observations suggest a natural strategy to learn the optimal auction in the observational model described in Section A.1: using a sequence of posted price mechanisms and iteratively updating the thresholds based on the buyers’ decisions.
Note that when using a posted price mechanism with threshold at time step , the only thing we observe from buyer is her decision to accept or reject the offer, which is the binary random variable . Hence, the suggested strategy does not even require the buyers to report their entire type but simply relies on the binary observations from each time step. From these observations, one can form for each , the quantity
which is an unbiased estimate of , that is, .
This observation conveniently reduces the problem of learning the optimal mechanism to the one of maximizing for each the concave function assuming access to unbiased estimates of for a sequence of our choice. This problem is exactly what is known in the online learning literature as a stochastic derivative-free optimization problem where the quantity plays the role of a zeroth order stochastic oracle. (The stochastic optimization literature distinguishes between first-order stochastic oracles giving unbiased estimates of the gradient of the objective function and zeroth-order oracles given unbiased estimates of the objective function itself.)
Algorithms for stochastic derivative-free optimizations usually take the form of iterative algorithms in which at each time step, the current estimate of the optimal solution is updated based on the previous estimate and the current observation. In our notations, we write:
where is the update rule given by a stochastic optimization algorithm. We instantiate the stochastic optimization framework in our setting and describe in Algorithm 1 a meta algorithm parametrized by a generic function.
All that remains to do to obtain a concrete bound on the regret of our learning procedure is to choose an function from the stochastic optimization literature. Here, we will not aim for optimal bounds but rather give a simple example of how to instantiate Algorithm 1. A common idea is to estimate the derivative of the objective at by where is uniformly random over . Using this estimate of the derivative in projected gradient-ascent suggests the following simple update rule:
| (15) |
where is uniformly random over and is the step size parameter. By applying a standard result (see e.g. Flaxman et al. [2005]) we obtain the following proposition.
Proposition A.2.
Furthermore, since the revenue is a concave function of the chosen threshold, we recover the standard fact that a bound on the regret implies a bound on the objective function.
Corollary A.3.
Proof.
. This follows immediately from Proposition A.2 by application of Jensen’s inequality. ∎
Appendix B Linear Externality Models
B.1 Proof of Fact 2.1
Proof.
By assumption , which implies in particular that and have the same sign. Without loss of generality, assume that and , otherwise the following proof applies after swapping the role of 1 and 2.
Given the distribution of consumer types,
Then taking and noting the linearity of in its arguments, we obtain the result for firm 1. The result for firm 2 follows in a similar manner after observing that . ∎
B.2 Proof of Fact 2.2
Let be the original set of market-relevant parameters before data is purchased and production efficiencies are improved, and let be the market parameters after an allocation of data, such that . For , firm ’s profit is given by
For market parameters , a standard computation gives the equilibrium production quantity and profits of firm 1:
with analogous expressions for those of firm 2 obtained by swapping indices 1 and 2.
We obtain by Taylor expansion the change in equilibrium profits
| (16) |
Furthermore, a simple computation gives and Assuming second order terms in (16) are sufficiently small to be ignored, we obtain
| (17) |
and similarly for firm 2. This has the exact same form as (1). In other words, our externality model captures the first order approximation of the change of profit that results from firms acquiring data. This immediately extends to the general case of firms engaging in Cournot competition.
Appendix C Welfare versus Revenue Maximization in Scenario 1
As stated in Section˜4.1, given a distribution function and corresponding density function for the random variable supported on , for , we define the distribution of on by the distribution and density functions
Further, define for the virtual value function . Then for each and , we can express the virtual functions as
Suppose all for are uniformly distributed on their respective domains. The virtual value functions take the forms
Meanwhile, the welfare-maximizing allocation rule for bidder 1 is
Thus, the revenue-maximizing allocation allocates to bidders less often than does the welfare-maximizing allocation. The optimal mechanism is therefore not efficient in general. This is illustrated in Fig.˜1 in Section˜5, where the type space for is partitioned in terms of the welfare-maximizing and revenue-maximizing allocation to bidder 1.
Appendix D Characterizations of IC and IR Mechanisms
An important step towards elucidating the solution structure of the welfare and revenue maximizing mechanisms is to obtain a characterization of the IC and IR constraints. Since our valuation model has the same form as the one in Jehiel et al. [1996, 1999], we rely on the characterizations found in these papers, and state them below for completeness.
D.1 Characterizations in Scenario 1: Incoming Externalities
Recall that each bidder ’s type is the vector of the form where denotes the th vector of the standard basis.
For each bidder , with true type and bid , the overall interim expected allocation is defined as and the interim expected payment as . Under the given assumption of independent bidder types, the interim expected allocation and payment functions do not depend on bidder ’s true type , so we write to indicate the interim expected allocation function and likewise, for the interim expected payment.
Note that is a vector field mapping to . Finally, for every bidder , we define the critical type , which will feature in the following IC and IR characterizations. Note consists of the type parameter values that are of the smallest magnitude.
Proposition D.1 ([Jehiel et al., 1999, Proposition 1]).
Suppose bidders’ private types are of the form for each bidder . Then the mechanism is BNIC if and only if for each bidder :
-
(i)
is a conservative vector field101010A vector field is conservative if it can be expressed as the gradient of some scalar potential function . Equivalently, line integrals of are independent of path taken between the endpoints.
-
(ii)
is a monotone vector field, that is for all .
-
(iii)
for each type , the interim payment is given by
(18) where is an arbitrary integration constant whose value sets , the interim utility of bidder when its type is .
We provide the following characterization of interim IR for BNIC mechanisms that maximize revenue.
Proposition D.2.
Suppose private types are of the form for each bidder . Then a revenue-maximizing BNIC mechanism satisfies the interim IR constraint if and only if this condition is satisfied for the critical type . Further, the optimal mechanism sets .
Proof.
We first show that the optimal outside option when bidder does not participate allocates the digital good to all remaining participants . We then show that it suffices to check that interim IR is satisfied for the type , and finally find the optimal value of the integration constant .
Optimal outside option.
The interim IR constraint is essentially a constraint on the values that the constant can take. That is, after plugging in the form of the payment rule (18), interim IR can be expressed as:
Maximizing revenue corresponds to maximizing the expected sum of the interim payments and thus of minimizing . Since , we can maximize the feasible region for IR payments by setting with an outside option that allocates to all when does not participate. That is, we set for all and .
Sufficiency of checking interim IR for type .
If the interim IR constraint holds for all types , then it clearly holds for the type . Now suppose that . Note that given the optimal outside option of allocating to all remaining bidders, we have that for every ,
| (19) |
Then for every
where the first inequality uses that , and as an allocation vector, the second equality follows from (19), and the last inequality follows from our assumption that .
Optimal IR Constant.
Since it suffices to satisfy interim IR for the critical type , for each , in order to maximize revenue we make the IR constraint bind at
| (20) |
where we plugged in the utility of non-participation of bidder under the optimal outside option allocation. ∎
D.2 Characterizations in Scenario 2: Outgoing Externalities
Recall that each bidder ’s type is the vector of the form where denotes the th vector of the standard basis. Note that in this scenario, bidder ’s expected outside option utility does not depend on .
For each bidder with true type and bid the interim expected allocation to bidder is given by and the interim expected payment for bidder is . Again, under the given assumption of independent bidder types, the interim functions do not depend on bidder ’s true type , so we define to be the interim expected allocation function for bidder and likewise, to be the interim expected payment function. The following two propositions then characterize BNIC mechanisms, and interim IR for BNIC mechanisms.
Proposition D.3.
Assume that private types are of the form for each bidder . The mechanism is BNIC if and only if for each bidder :
-
(i)
there exists a non-decreasing function such that the interim allocation satisfies for all but countably many and all .
-
(ii)
the interim payment function is given by
(21) where is an arbitrary integration constant.
Furthermore, if these conditions are satisfied, then is constant with respect to for almost every , and for all .
Proof.
We first show the necessary implications of IC. Writing Definition 2.8 for as the true type and as the reported type, and then vise versa, i.e.,
| (22) | |||
Combining the two inequalities yields
By Lemma D.4 below, this implies condition (i), so we let for any .
Note also that the inequality (22), by adding and subtracting the term to the right hand side and regrouping terms, can be written equivalently as
| (23) |
Then plugging in and into the preceding inequality yields , where we recall that . Swapping the roles of and yields the inequality in the opposite direction, and we have that is independent of :
We henceforth define for any .
To prove (ii), we first note that is convex in . (22) implies that
Thus, is the maximum of a family of linear functions of and is thus convex in . (D.2) implies that is a subderivative of . In fact, since is convex in , it is differentiable almost everywhere and
Further, this implies that
| (24) |
Now plugging in the following expression for ,
and solving for , we get
| (25) |
We next show the sufficiency of the conditions for IC, by proving the equivalent condition for IC, (D.2). We have that
where the first equality follows from (24) and the inequality follows from condition (i) that is increasing in .
Lemma D.4.
For , let be a bounded function such that
Then, there exists a non-decreasing function such that for all and for all but at most countably many values of .
By a rescaling and shifting of we assume without loss of generality that the range of is contained in . Let us now define and for , and observe that .
We now prove that . Indeed, consider , distinct points in , and for each , such that . Then
where the first inequality uses the definition of , the equality is summation by parts, the second inequality uses our assumption on and the last inequality uses that the range of is contained in . It then follows that , i.e. that , which in turn implies that is countable.
Define by for (this definition does not depend on the choice of by definition of ). Then our assumption on immediately implies that is non-decreasing on . We can thus extend to a non-decreasing function defined over all of (for example by right continuity). The resulting satisfies the stated requirements. ∎
Proposition D.5.
Suppose private types are of the form for each bidder . Then a BNIC mechanism satisfies the interim IR constraint for all , if and only if this condition is satisfied for some type of the form , where for .
Proof.
Note that BNIC implies (24), and since , we have that for all . Since is independent with respect to , it is both necessary and sufficient for IR to hold that the IR condition holds for some type of the form , for each bidder . ∎
Appendix E Welfare Maximization
E.1 Proof of Theorem 3.1
We show that the specified VCG mechanism (1) satisfies DSIC, (2) ex-post IR, and (3) uses nonnegative payments. Recall that in this setting, private types are of the form , for .
-
1.
For all and all , let us temporarily define the following quantities for ease of notation. Note the only quantity varying in the following terms is bidder ’s bid, while all other parameters are fixed.
We show that the following expression is nonnegative, which is precisely the statement of DSIC:
For the first equality we used the second expression of the payment rule in (5), we regrouped terms and used the definitions of for the second and third equalities. The final inequality holds because
and likewise for , implying that each term in the summation is nonnegative.
-
2.
Let be an arbitrary type realization. Showing ex-post IR is equivalent to showing
Plugging in the payment rule, we get the equivalent inequality
Rearranging and regrouping terms, we get that this is equivalent to
Since , the first term is always nonnegative. The terms in the summation are likewise nonnegative since
Thus, the IR constraint is satisfied for all types .
-
3.
Let be an arbitrary type realization. Note that since , we can lower bound the payments in (5) by
We have that
Matching up the cases, we get that , so payments are nonnegative.
E.2 Proof of Proposition 3.2
Consider a uniform type distribution over two points: and , where and are arbitrary, fixed values. We choose and satisfying
| (26) |
For instance, we can take and .
Let us consider an allocation . By Proposition˜D.3 there exists a non-decreasing function such that , . However, under the distribution , only takes the single value , so the function must be constant-valued. We now consider two cases depending on the sign of this constant value.
If for all , then define by and for all . We have that
where the strict inequality follows from (26) and that .
Likewise, if for all , define by and for all . Then
where the strict inequality follows from (26) and that .
Thus, we have shown that for any BNIC allocation, there exists some type realization for which a different BNIC allocation rule yields strictly greater social welfare. This is precisely the statement in (6).
E.3 Proof of Theorem 3.3
Allocations.
To solve for the form of the expected welfare maximizing allocation function satisfying the IC constraints, we first express the objective in terms of the interim allocations . Defining as in Section 3.1, we have
Now, the BNIC characterization from Proposition D.3 implies that there must exist functions such that for almost all . Plugging in this representation above, we get
Noting the linearity of the objective in , we find that the optimal allocation rule is
Under the given assumptions, is non-decreasing in , so BNIC is satisfied. Finally, note that since we can express the objective function and constraints only in terms of the interim allocations for , we can without loss of generality for all , set the allocation rule .
Payments.
The induced interim payment rule associated with as derived in Proposition D.3, condition (ii) is
| (27) |
Recall that the constant term is set such that the payment function satisfies IR. By Proposition D.5, it suffices to check IR for any type of the form , for each . Here, bidder ’s expected utility if she doesn’t participate is the sum of the externalities effects from the allocations in the welfare-maximizing auction run with the remaining set of bidders, and given the assumption of non-decreasing, we have
| (28) |
Then any payment rule of the form (27) with the constant set greater than or equal to in (E.3) will give us an IR mechanism.
Finally, since the objective function and constraints can be expressed solely in terms of the interim payments , we can set . Under the given assumption that is non-decreasing, we can re-express the allocation rule as
| (29) |
The integral term in (27) then becomes
Plugging in the above expression, along with the form of the allocation (29), into (27) completes the proof.
Appendix F Revenue Maximization
F.1 Proof of Proposition 4.1
An instance of the -item auction is a distribution over -tuples of item valuations. We make the standard assumption that item valuations are non-negative (i.e. the marginals of are supported on ), and denote by the support of . Let be the involution that flips the signs of all but the first of its input’s coordinates: . We define the distribution over type profiles in the digital good auction, where is the pushforward of through and denotes the Dirac measure at . In other words, the support of is , and is distributed according to iff is distributed according to and are constant equal to .
Let be a mechanism for the -item auction, with describing the allocation probabilities of each of the items, and being the corresponding payment function. For each , we define a corresponding mechanism for the -player digital good auction as follows: for each ,
| (30) |
Then,
| (31) |
We used that induces a bijection from to in the first equivalence, and the definitions of , and in the second. Adding to both sides of the inequality yields the third equivalence. Recall that under , each of the type vectors is supported on a.s., hence truthful reporting of players to is trivially guaranteed. Finally, (31) shows that is IC iff satisfies the IC constraint of player .
We now look at the participation constraints. In the -item auction, non-participation implies that the buyer is allocated no item (and no payment is collected), resulting in a vanishing reservation utility. In the -player digital good auction, we set the allocation of player in case of non-participation to be , which results in the worst possible reservation utility for type . Then, following the same steps as in (31):
This shows that guarantees participation of player 1 iff is IR. Furthermore, the participation constraints of player to are trivially satisfied under . Note also that these constraints require the payment functions to be identically zero for .
The previous two paragraphs show that there exists a mapping between mechanisms, namely the one given by (30), that establishes a one-to-one correspondence between (i) IC and IR mechanisms for the -item auction under distribution , and (ii) IC and IR mechanisms for the -player digital good auction under distribution (with outside option defined as above). Furthermore, the expected revenue of each mechanism is equal to the expected revenue of the corresponding mechanism . Since the outside option we considered makes the IR constraint of player the slackest, this implies that the range of contains an optimal mechanism for the digital good auction. The preimage of such a mechanism under is therefore optimal for the -item auction under .
F.2 Proofs of Theorem 4.2 and Corollary 4.3
Recall that for either scenario of private types, for each bidder , with true type and bid , the overall interim expected allocation is defined as and the interim expected payment as . Note that, under the given assumption of independent bidder types, the interim expected allocation and payment functions do not depend on bidder ’s true type , so we write to indicate the interim expected allocation function and likewise, for the interim expected payment.
We begin with the following lemma which provides a characterization of BNIC tailored to restricted-dependency mechanisms.
Lemma F.1.
For restricted-dependency mechanisms, the th coordinate of the interim allocation vector only depends on , and we write . A restricted-dependency mechanism is BNIC iff
-
(i)
for each , the function is non-decreasing.
-
(ii)
the interim payment of bidder is given by
(32) for some constant whose value sets the interim utility of bidder at .
Proof.
The mechanism is BNIC iff for each . We re-express this condition in terms of interim allocations and payments:
By a well-known characterization of convexity, this is equivalent to requiring that the interim utility be convex and admits as a subgradient for each . This is in turn equivalent to being a cyclically monotone vector field. Due to the restricted-dependency assumption, it is easy to see that is cyclically monotone iff is non-decreasing for all . But then, is integrable, hence is conservative with (convex) potential , and we can write
Thus the interim payments take the form
F.2.1 Proof of Theorem 4.2
Deriving the Optimal Allocation.
We first use the form of the interim payment functions from the BNIC characterization of restricted-dependency mechanisms under Scenario 1 given in Lemma˜F.1 to express our objective solely in terms of interim allocation functions . The expected revenue then becomes
The first line follows by the law of total expectation, which allows us to express the expected revenue as the sum of interim expected payments. In the last equality, we shifted the lower bounds of integration from components of to components of along with the corresponding constant of integration to . The type vector can be considered the “lowest” type of bidder , as it yields the lowest valuation on any given allocation over all feasible types, while the critical type is the type vector closest to the origin and is the binding type for IR constraints. Originally , and now the new constant of integration sets the value of . The constant term can be set independently of the allocation functions, and we defer finding the optimal such (and thus ) satisfying IR to the last part of this proof, after we have solved for the optimal allocation rules.
Recall that , and for streamlined notation, let and denote the pdf and cdf of , respectively, for . Note that for , and .
The expectation of each of the integral summands becomes
where in the second line, we swapped the order of integration, in the third line, we evaluated the inner integral and renamed the dummy variable to , and in the last line, multiplied by to retrieve the expectation.
The expected revenue, up to the constant , can be written as
where in the last line we used the tower law of expectation.
The expected revenue is linear in the allocations . Subject to the constraint that for all , the restricted-dependency revenue maximizing allocation can be read off as
Since and , it follows that and and we obtain the expression (11) for the allocation.
Verifying BNIC.
Note that for , the allocation functions are only dependent on , for all . Further, is increasing in since the relevant term is increasing in . This can be derived from our assumption that is increasing in , which implies that is decreasing in and increasing in .
Then by Lemma˜F.1, and the payment function derived from the corresponding interim payment functions in (32) yield a restricted-dependency BNIC mechanism. The constant can be optimized to maximize revenue, as is done in Corollary˜4.3, whose proof is given in the following subsection.
F.2.2 Proof of Corollary 4.3
Recall that by Proposition˜D.2, the optimal outside option is to allocate to all bidders when bidder does not participate, and the optimal constant in the interim payment (32) is determined by setting the utility of critical type equal to its reservation utility:
Although taking the payment functions to be equal to the interim payments given in (32) of the BNIC characterization of Lemma˜F.1 is suitable for maximizing revenue, we can alternatively define the following payment functions in terms of the non-interim allocation functions :
| (33) |
where is the vector collecting all entries of except for . Note that taking the conditional expectation of this payment respect to yields the correct interim payment form, (32), of the BNIC characterization of Lemma˜F.1:
where in the second line we swapped the order of conditional expectation with integration by Fubini’s theorem and nonnegativity of the argument, and in the last line recovered the interim allocations.
Given the assumptions that the virtual valuation functions and are non-decreasing, we can equivalently express the optimal allocations (11) in a threshold form:
where we define the thresholds
Plugging these expressions into (33), we have
Evaluating the integrals, plugging in the optimal constant and simplifying, we get
F.3 Proof of Proposition 4.4
Under the assumptions of Proposition˜4.4, given allocation vector and payment , the net utility of bidder with type simplifies to
| (34) |
Furthermore, we see that the interim allocation of bidder , is a function of only. Similarly, we write for the interim payment. Using (34), bidder ’s interim utility becomes
where we defined the interim aggregated allocation effect
In other words, from the perspective of bidder , the situation is exactly equivalent to the one of a single-dimensional allocation with linear utility. The IC characterization of Proposition˜D.1 thus simplifies significantly and becomes essentially equivalent to the one of Myerson [1981] (see also [Bonatti et al., 2022, Prop. 3.6]).
Lemma F.2.
Assume that, for each , with for . Then, the mechanism is BNIC iff for each bidder :
-
(i)
the interim aggregated allocation effect is non-decreasing.
-
(ii)
the interim payment is given by
(35) for some constant .
Proof of Proposition˜4.4.
Using (35), we first compute the expected payment of firm in terms of the virtual value function associated with ’s distribution (cf. [Bonatti et al., 2022, Lemma 4.4]):
where we swapped the order of integration in the third line. We recognize the virtual value function in the last line, hence
Note that using the law of total expectation
which implies the following expression for the expected revenue
where we swapped the order of summation on the right-hand side. This immediately implies that the optimal allocation is given by
We conclude by verifying that the resulting mechanism is BNIC. For this, it suffices to check that the aggregated allocation effect is non-decreasing. Denoting by the c.d.f. of and by the c.d.f of , we compute (cf. [Bonatti et al., 2022, Prop 4.6])
Since cumulative distribution functions are non-decreasing and by regularity of the distribution of , the function is non-decreasing and is non-increasing (for each ), which concludes the proof. ∎
F.4 Proof of Theorem 4.5
We consider a mechanism , and use the BNIC characterization of Proposition D.3. In particular, recall that there exists a non-decreasing function such that , where is the interim allocation. Plugging in the form of interim payments given by (21) we get
| (36) |
Observe that the last term on the right-hand side is independent of the choice of and can thus be ignored when searching for the revenue optimal auction.
For the second term, swapping the order of integration gives
For the third term, we write
where the first, third and last equality use the law of total expectation, the second equality is just a change of index and the penultimate is by definition of .
Combining the previous derivations, we get that the revenue maximizing problem is equivalent to maximizing
| (37) |
where is the interim allocation computed from and must be non-decreasing by Proposition D.3. Hence, we see that the objective function as well as the BNIC and IR constraints can be written solely in terms of the functions . It is thus sufficient to optimize over each summand separately, under the constraint that be non-decreasing and -valued.
Under the regularity condition that is non-decreasing, observe that each summand in (37) can be written concisely in terms of as . The choice maximizes the integrand pointwise and is non-decreasing in since is also non-decreasing. Hence it also maximizes the expectation subject to the monotonicity constraint, yielding the optimal BNIC allocation rule.