Upper Bounds on Overshoot in SIR Models with Nonlinear Incidence
Abstract
We expand the calculation of the upper bound on epidemic overshoot in SIR models to account for nonlinear incidence. We lay out the general procedure and restrictions to perform the calculation analytically for nonlinear functions in the number of susceptibles. We demonstrate the procedure by working through several examples and also numerically study what happens to the upper bound on overshoot when nonlinear incidence manifests in the form of epidemic dynamics over a contact network. We find that both steeper incidence terms and larger contact heterogeneity can increase the range of communicable diseases at which the overshoot remains a relatively large public health hazard.
Introduction
Compartmental models have been an invaluable tool for analyzing the dynamics of epidemics for the last century. In particular, the susceptible-infected-recovered (SIR) model has long been a workhorse compartmental model for describing transient epidemics due to its relative simplicity and has received a lot of attention in both the academic literature and the public health arena [1, 2]. The mechanism of transmission of a communicable disease underlying this model and a variety of other contagion models is contact between healthy and infectious individuals, which results in conversion of the healthy individuals into an infected state. Choosing how to precisely define the transmission interaction between healthy and infectious individuals leads to a variety of models depending on the assumptions made. For instance, in a spatially-explicit model, one might represent the contact between individual members of the population as a network. Alternatively, if one is willing to assume all individuals within a compartment are identical, one can formulate a model using ordinary differential equations (ODEs) by assuming an incidence term for how the susceptible and infected compartments mix and generate new infected individuals.
The quintessential SIR ODE model, known as the Kermack-McKendrick model, is shown in (1-3). The model assumes a bilinear incidence rate for the growth term of the infected compartment, with transmissibility parameter and first-order (i.e. linear) with respect to the fraction of population that is susceptible () and infected ().
| (1) | ||||
| (2) | ||||
| (3) |
While a bilinear incidence rate between healthy and infected individuals can be a reasonable first assumption, depending on the real-world situation being modeled and the level of precision required, the assumption can be insufficient or inaccurate. A significant body of work in the literature has been done to generalize this incidence term into more detailed forms [3, 4, 5, 6, 7, 8]. Moving beyond bilinear forms towards nonlinear incidence allows for the consideration of models with more biological complexity and realism. Factors such as network effects, seasonality, and non-pharmaceutical interventions are known to give rise to more complex dynamics [9, 10, 11, 12]. The studying of nonlinear transmission in the context of epidemiology here is a specific case of a larger growing interest across a range of fields in studying the effects of transmission dynamics in complex systems. The exploration of interactions beyond the bilinear form has taken place in contexts ranging from social dynamics [13, 14, 15, 16, 17], ecology [18, 19, 20, 21], economics [22, 23], to molecular biology [24]. Significant effort has also been expended on synthesizing these ideas into a more general model of contagion that can be used in different domains [25, 26, 27].
As the representation of transmission is arguably the most important aspect in setting up a model of communicable disease, the choice for the incidence rate has downstream consequences on many epidemiological quantities of interest. These include, but are not limited too, the epidemic size, the herd immunity threshold, epidemic duration, and the epidemic overshoot. While features such as the epidemic size and the herd immunity threshold have been studied rather extensively in the literature, the behavior of overshoot remains relatively under explored, in particular for more general incidence rates.
Overshoot is a concept from mathematics and control theory that quantifies the amount of excess from when a function exceeds its target value [28, 29]. This concept has been applied to a variety of contexts ranging from ecological and environmental problems that pertain to overconsumption and sustainability [30, 31, 32, 33] to biotechnology that controls blood flow [34]. In the epidemiological context, the overshoot quantifies the number of individuals that become infected after the prevalence peak of infections occurs (Figure 1a). In simple epidemics, as the peak of the epidemic coincides with the threshold at which transmission is sufficiently reduced so that the epidemic is no longer growing, the overshoot reflects the excess in cases beyond this minimal threshold of protection.
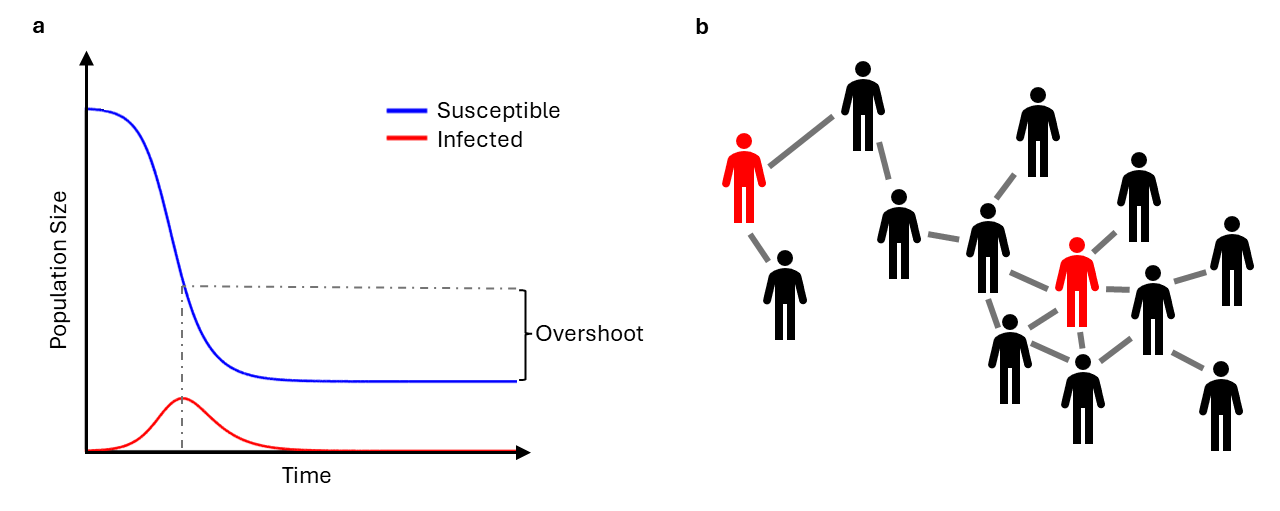
While the terminology excess may give the connotation of a relatively small effect, in the the Kermack-McKendrick SIR model it can be shown that up to nearly of the population can become infected in the overshoot phase of the epidemic [35]. This is also not a rare case, as large values of overshoot occur at rather common values for the basic reproduction () of , which includes communicable diseases such as COVID-19 [36, 37, 38], HIV [39], and influenza [40]. An analysis of data from the the first wave of the COVID-19 pandemic in the urban city of Manaus, Brazil [41, 35], where disease spread went largely unmitigated, suggested that the dynamics could be reasonably approximated by the Kermack-McKendrick SIR model and that nearly of the population became infected in the overshoot phase.
The overshoot highlights the potentially large public-health risk that can be posed by allowing for unmitigated spread or reducing intervention measures prematurely. However, the transmission rates at which the overshoot poses the greatest risk depends on the form of the incidence rate, which drives the need to understand the behavior for incidence beyond the simple bilinear case. As the overshoot quantifies the excess number of cases that occur after the herd immunity threshold has been reached, it is also intimately connected with any potential interventions or mitigation strategies. A question of great concern to epidemiologists and public health officials is figuring out the optimal control strategies for reducing excess cases and mortality [42, 43, 44, 45]. Any optimal strategy by design generally seeks to eliminate the overshoot. Thus, a better understanding the behavior of overshoot under different model assumptions might allow for better control measures to be designed and developed.
While the overshoot within the SIR model has received some attention [42, 46, 47, 48], a detailed understanding of its full mathematical behavior within compartmental models remains incomplete. An observation that the overshoot is largest for intermediate basic reproduction numbers was first numerically observed by Zarnitsyna et al. [49]. An explanation for that phenomena in the context of the Kermack-McKendrick model was recently discovered, showing that the overshoot is derived from a trade-off from the basic reproduction number in driving both the final epidemic size and how quickly the disease burns through the population [35]. Here we lay the foundation to calculate the upper bound for overshoot when considering incidence terms beyond the simple bilinear case. We will first derive the behavior of the overshoot for more general incidence rates within the context of ODE models, where the results and understanding can be analytical and precise. As nonlinear incidence can also arise through the connectivity structure of networks (Figure 1b), we will then numerical explore the effect of network structure and changing network topologies on overshoot.
Results
Effect of Nonlinear Incidence on Overshoot in SIR ODE Models
We first examine the effect of nonlinear incidence on overshoot for ODE models, where the computations can be made analytical. The equations of the Kermack-McKendrick SIR ODE model are given as follows with generic incidence term , where and are functions of and respectively to be specified.
| (4) | ||||
| (5) | ||||
| (6) |
where , , are the fractions of the population that are susceptible, infected, and recovered respectively, are positive-definite parameters for transmission and recovery rate respectively.
For the SIR model, the overshoot is given by the following equation:
| (7) |
where is the fraction of susceptibles at the time of the prevalence peak (i.e. when is maximal in value), , and is the fraction of susceptibles at the end of the epidemic. To solve this equation, the easiest approach is to derive an equation for in terms of only and parameters. We do this by first setting (5) equal to 0 and solving for the critical susceptible fraction .
By using the usual definition for the basic reproduction number, , we obtain the following equation for .
We can see from this equation that will have dependence unless . Thus to make what follows analytically tractable, let us assume . We will provide even stronger justification why must take this form later in the results. This assumption of reduces the above equation to the following.
| (10) |
Thus the main challenge now becomes a problem of finding an equation for and the inverse function . Based on previous results [35], the following outlines the general steps for calculating the maximal overshoot for a SIR model:
-
A.
Take the ratio of and . Integrate the resulting ratio. The indefinite integral requires a constant of integration, which is a conserved quantity that applies at every time point along the system’s trajectory in time.
-
B.
Evaluate the equation for the conserved quantity at the beginning of the epidemic () and the end of the epidemic () using initial conditions and asymptotic values. Then, rearrange the resulting equation for .
-
C.
Find the form for the inverse function, .
-
D.
Combine the equations for and with the overshoot equation.
-
E.
Maximize the resulting overshoot equation by taking the derivative of the equation with respect to and setting the equation to 0 to find the extremal point . This step usually leads to a transcendental equation for , which can be solved numerically.
-
F.
Use the maximizing value in the overshoot equation to calculate the corresponding maximal overshoot.
-
G.
Calculate the corresponding using and the equation.
Thus, the analytical exploration of nonlinear incidence terms of the type is reduced to exploring different forms of .
Restrictions on
The first step is to rule out what forms for the incidence term will not work with the procedure outlined above.
We now show the principle reason why we require . We can see from calculating Step A. in (11) that any incidence term that does not take the form , where is a real scalar, retains dependence upon simplification.
| (11) |
Any deviation from the form results in in the numerator and the denominator not completely cancelling out which will result in having to integrate with respect to , which we will not be able to do analytically. Therefore, must enter linearly into the incidence term. Since can be absorbed into the parameter, all possible incidence terms for the purpose of calculating overshoot analytically will take the form .
Restrictions on
We now turn to what restrictions there are on the form of . We start first with two conditions. First, we must enforce that when there are no susceptibles (), then the incidence rate must go to zero (). Otherwise, since does not have such a restriction, violating this condition would leave open the unrealistic possibility that the model can generate infected people when there are no susceptibles available. To ensure this condition is met, we need the function on S to output zero if the input is zero.
| (12) |
For the second condition, for an outbreak to occur in an SIR model, we must have a minimum value for the basic reproduction number, . Another way to view this condition is by inspecting (2) and recognizing that that the incidence term () needs to be greater than the recovery term (). Otherwise the epidemic cannot grow in size. Comparing the two terms leaves an inequality () which can be rewritten as:
| (13) |
Beyond these conditions, an obvious requirement is that should be a continuous function. In order to be able to calculate the maximal overshoot analytically, the function should be integratable with respect to and should also have a closed-form inverse . As we will demonstrate, non-monotonic functions for are possible.
For , the following examples are constructed using basic functions that satisfy the above criteria:
-
1.
-
2.
Invertible polynomials of
-
3.
Conversely, there are many examples of functions that would not work. An example that satisfies the boundary conditions but that does not have a closed form inverse is . While similar to examples listed, the following violate the boundary conditions: , . Examples that violate conditions of continuity include step functions of or with cusps.
Deriving Maximal Overshoot for Various
As an example, we will now look at a model with nonlinear incidence and apply the whole procedure previously outlined for finding the maximal overshoot.
Example:
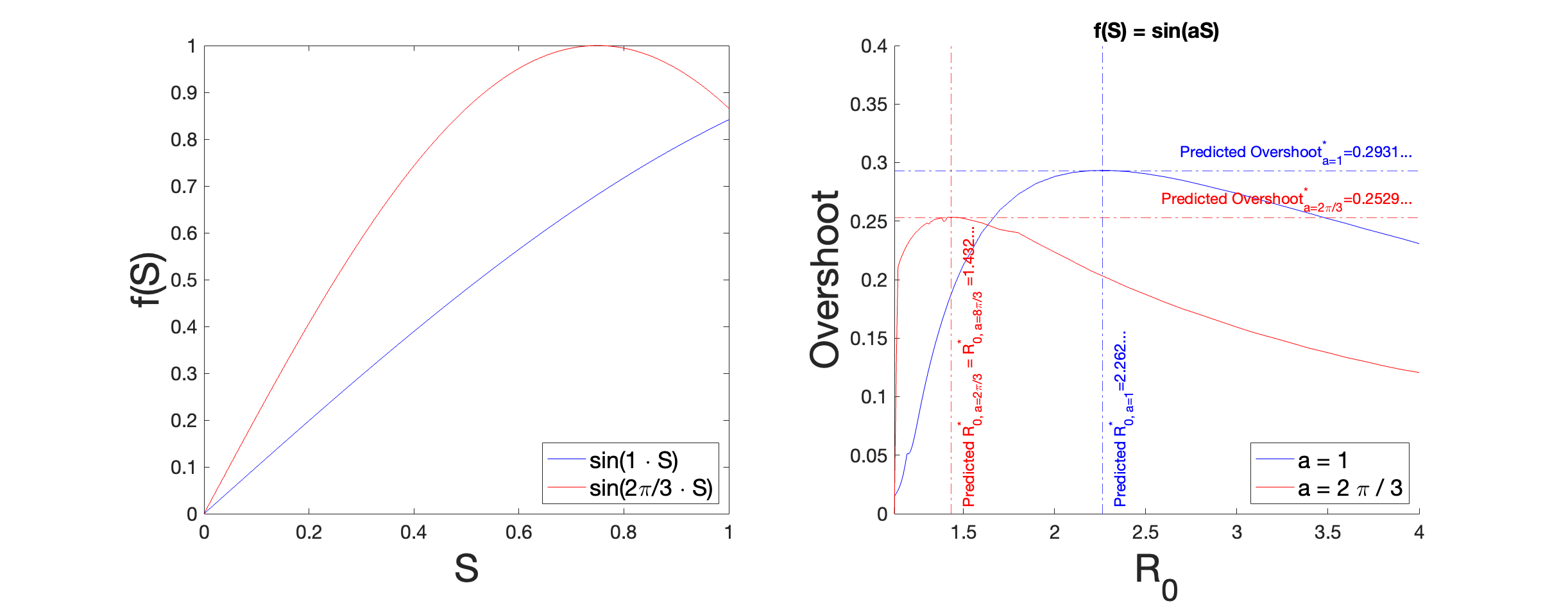
Let us consider an incidence rate that takes on an exponential form. This produces an incidence term that grows slightly faster than the original bilinear incidence term, and so might be relevant in situations where there are network effects.The phenomenon of superspreading occurs when some individuals infect many more people than the typical infected person would normally do [50]. Superspreading allows for explosive outbreaks that exceed the growth rate of infections allowed by simple bilinear incidence and is enabled by inherent heterogeneity in contacts amongst the population, which makes it natural to occur in situations that are approximated by a network. Different models can be formulated to account for superspreading [51, 52]. Here we have chosen the exponential as a qualitative simple example that more closely resembles the growth rate on a heterogeneous network than standard bilinear incidence.
We start at Step A. by solving for the rate of change of as a function of by taking the ratio of and .
| (14) |
from which it follows on integration using the substitution and partial fractions and that is constant along all trajectories.
For Step B., consider the conserved quantity at both the beginning () and end () of the epidemic.
hence
| (15) |
We use the initial conditions: and , where is the (infinitesimally small) fraction of initially infected individuals. We use the standard asymptotic of the SIR model that there are no infected individuals at the end of an SIR epidemic: . This yields:
| (16) |
For Step C., we find the inverse of .
| (17) |
| (18) |
For Step E., differentiation of both sides with respect to and setting the equation to zero to solve for the critical yields:
Since is positive semi-definite over the unit interval for , dropping the absolute value symbols and simplifying yields:
which admits both a trivial solution () and the solution .
For Step F., using the non-trivial solution for in the overshoot equation (18) to obtain the value of the maximal overshoot for this model, yields:
| (19) |
Thus, the maximal overshoot for incidence functions of the form is .
| (20) |
This result is verified numerically in Figure 2. Compared to the overshoot in the Kermack-McKendrick model [49, 35], we see that the maximal overshoot is also near . However, we see that overshoot has a much broader distribution over the domain of , suggesting that exponential incidence rates pose a public health hazard for a greater range of communicable diseases over their bilinear counterparts.
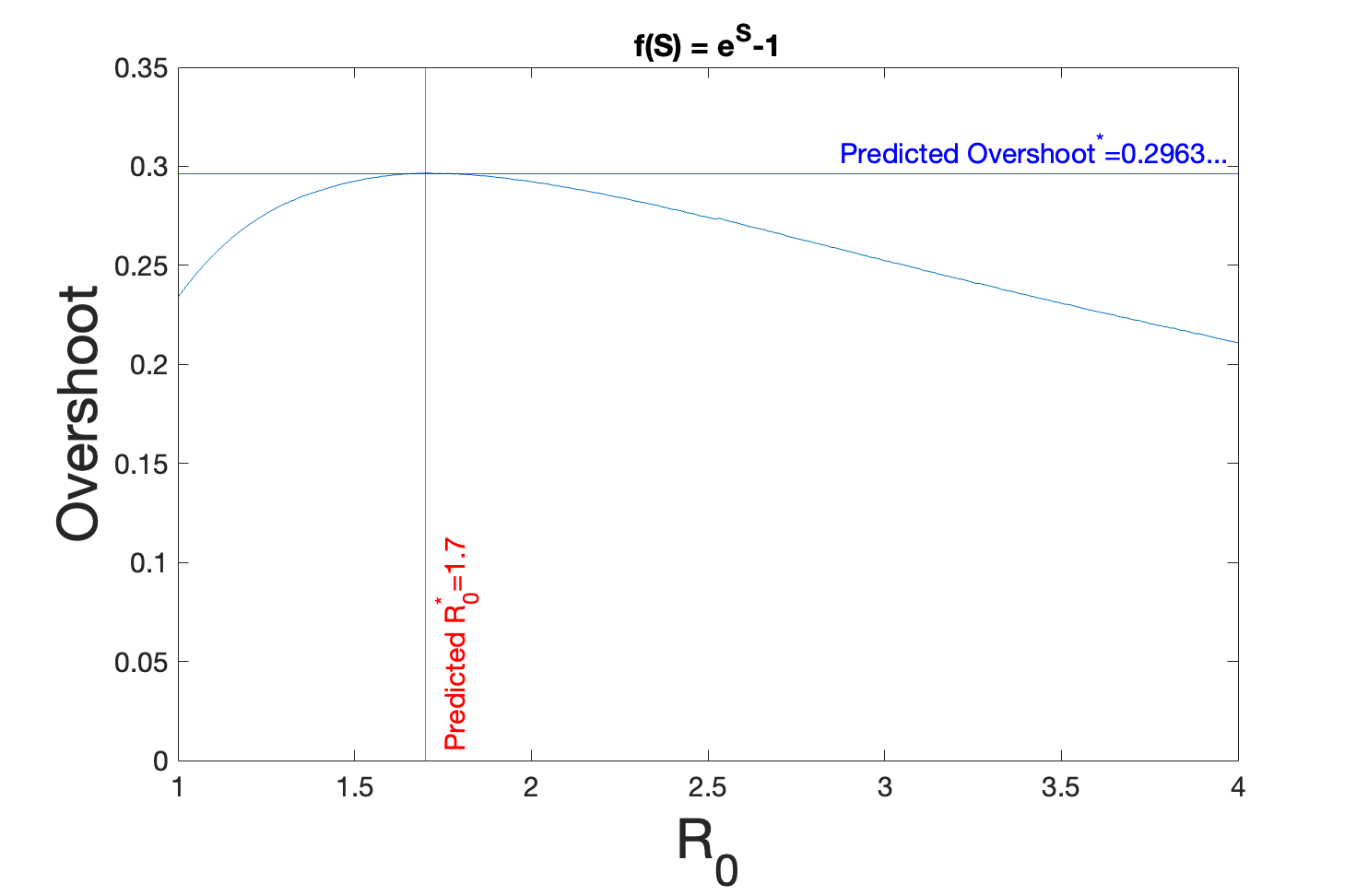
Additional examples for incidence rates of a different mathematical form can be found in the Supplemental Information. One example considers when the form of is given by a polynomial, which can be used to model higher-order effects beyond a simple two-person interaction. Another example considers the consequence of having that is non-monotonic over the domain of , which might reflect real scenarios where there are tipping points in behavior.
Nonlinear Incidence Generated from Dynamics on Networks
In the previous sections, we focused on nonlinear incidence that was generated from the introduction of a nonlinearity in an ordinary differential equation model. Importantly, this fundamentally assumes homogeneity in the transmission, in that all infected individuals are identical in their ability to spread the disease further. In contrast, network models allow for heterogeneous spreading which depends on the local connectivity of each infected individual. This provides an entirely different mechanism through which nonlinear incidence can be generated compared to the ordinary differential equation models. As many real-world complexities and details can be more easily captured and explored in a network model, the consequences of those heterogeneities on the overshoot becomes more transparent through the targeted and fully-fleshed out explorations that can be done through numerical experimentation in network simulations [53, 54, 55, 9, 56]. However, a trade-off for the increased realism is that it becomes more difficult to perform analytical calculations for a general network model, so here we conduct a numerical exploration of the behavior of the overshoot in network models across a range of network structure.
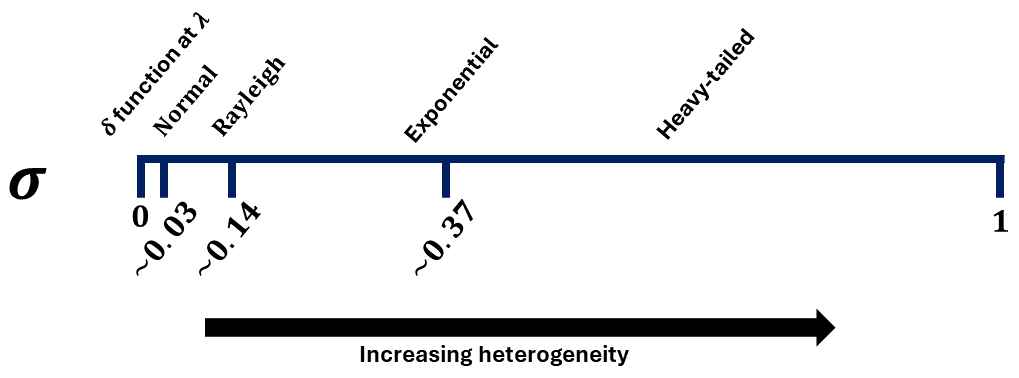
The space of all possible network configurations is immense, so we must restrict ourselves to analyzing a particular subset of possible networks. Here we explore what happens to the overshoot when the contact structure of the population is given by a network graph that is roughly one giant component. While it is possible to construct pathological graphs that produce very complex dynamics, we consider more classical graphs here. Using a parameterization of heterogeneity () given by Ozbay et al. [57] and the configuration model of Newman [58] to randomly construct networks (see Methods for details), we simulated epidemics on a spectrum of networks with structure ranging from the homogeneous limit (well-mixed, complete graph) to a heterogeneous limit (heavy-tailed degree distributions). The spectrum of distributions shapes across the space of used to generate the degree distributions can be seen in the supplement. As the dynamics of the epidemic on a network are stochastic and occur in discrete-time here, they are not parameterized by as in the ODE models. Instead, we use an analogous parameter that we will denote as a basic reproduction number for networks () and is defined as follows:
| (21) |
The transmission probability () and recovery probability () are directly analogous to their counterparts ( and respectively) in in that that correspond to transmission and recovery parameters, albeit for a stochastic model. The inclusion of the mean network degree () as a scalar makes intuitive sense as that represents the average number of potential neighbors an infected node could potentially infect at the beginning of the epidemic, which is analogous to the interpretation of as the number of secondary infections. We observed what happens to the overshoot on these different graphs as we changed .
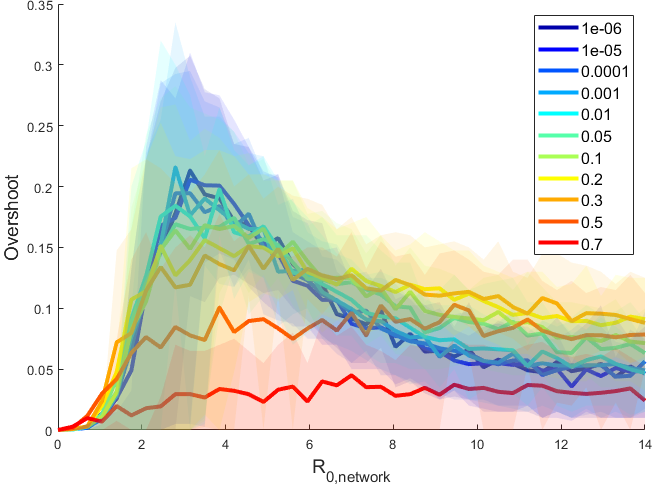
On a network model, where contact structure is made explicit, the homogeneous limit is a complete graph, which recapitulates the well-mixed assumption of the Kermack-McKendrick model. It is not surprising then that the overshoot in the homogeneous graphs ( peaks also around 0.3 (Figure 3, and ), which coincides with the analytical upper bound previously found in the ordinary differential equation Kermack-McKendrick model [35]. However, while the homogeneous graphs shown here are highly regular (i.e. symmetric in the average number of contacts each node has), the network’s connectivity is not close to complete as the mean degree is significantly less than the network size. Thus, the average overshoot is lower than would be the case for a complete graph.
We also see that increasing contact heterogeneity (i.e. ) qualitatively suppresses the overshoot peak both in terms of the overshoot value and the corresponding . Furthermore, increased heterogeneity also flattens out the overshoot curve as a function of . We see that for more heterogeneous graphs, the overshoot is larger at very low . For some intermediate values of contact heterogeneity (Figure 3, and ), the overshoot shows larger overshoot than the homogeneous case for large . This would suggest a larger public health hazard for a larger range of communicable diseases for networks with structure in this regime. The intuition for the larger overshoot at high in more heterogeneous networks is that both the peak occurs earlier and that a significant number of cases can occur in the periphery of a network (Supplemental Materials). The probability of being connected to a high-degree node increases as the heterogeneity of the network increases, which drives the peak of infections to occur sooner. In the second phase of the epidemic as the epidemic expands out to the periphery the epidemic burns more slowly as individuals in the periphery have fewer neighbors.
However, this trend of a overshoot distribution with a big right tail does not monotonically increase with the contact heterogeneity. We see that at very high amounts of contact heterogeneity, the overall area under this overshoot curve decreases. This can be partially explained by the fact that for very heterogeneous networks, a significant fraction of the population have no neighbors at all. This limits the amount of people that can potentially be infected and caps the outbreak size and subsequently overshoot size.
Discussion
While the overshoot has received less attention and exploration than its epidemiological counterpart (the herd immunity threshold), the overshoot poses a significant potential public health hazard for a large range of communicable diseases when there is no mitigation. Generalizing models to include nonlinear incidence terms allows for the consideration of more real-world effects such as higher-order transmission effects and network effects. Thus, to expand the scope of previous work, we have illustrated a general method to analytically find the maximal overshoot for generic nonlinear incidence terms.
Starting with the general incidence term , we have deduced what restrictions must be placed on the form of and to make an analytical calculation possible. As long as the conditions for a suitable are satisfied, in principle the maximal overshoot can be derived. However, in the examples shown in both the main text and supplemental information, we have seen that even relatively simple forms for can quickly lead to complicated integrals and derivatives. For these examples, we have shown the predictions given by the theoretical calculations generally match the empirical results derived from numerical simulation. From a public-health perspective, we find that incidence rates that are steeper over the domain of , such as the examples with the exponential or polynomial functions, show a smaller maximal overshoot, but importantly, a much broader range of ’s at which the the overshoot remains large. As interventions that seek optimal control try to minimize the overshoot, this highlights the need for even stronger interventions when the interactions and subsequent incidence between individuals is higher than a simple bilinear interaction. The example of in the supplemental information is interesting because it can be used to probe the restrictions on the shape of . The case demonstrated that no longer has to be monotonic over the domain of , allowing for tipping point-like behavior.
Nonlinear incidence introduced through having a network structure showed that having network connectivity that was more heterogeneous resulted in a reduction in the upper bound on overshoot and a reduction of the dependence of overshoot on transmission overall. Numerically, the overshoot for a homogeneously connected network (i.e. a complete graph) well-approximates a Kermack-McKendrick ODE model. The ODE model makes a fundamental assumption of a well-mixed population, and similarly, a network with the highest mixing rate would be a complete graph, which a graph approaches as it becomes more homogeneous and the connectivity increases. Thus, an upper bound on the overshoot of approximately in both models [35] is perhaps unsurprising. It is interesting to note though, that due to the stochastic nature of the network simulations, occasionally an epidemic on a very homogeneous contact network will exceed the analytical bound in the ODE framework (see Figure 3, the upper quartiles for and regions exceed ). While more heterogeneous networks did not have an overshoot larger than , the overshoot was greater at larger than the homogeneous case. Future studies that incorporate more nuanced aspects of behavior, interventions, and time dynamics in the network model can further elucidate the complexities of epidemics on networks.
It will also be interesting to see if more complicated nonlinear interaction terms than the ones presented here can be derived. In addition, it will also be interesting to see how these nonlinear incidence terms interact when additional complexity is added to the SIR model, such as the addition of vaccinations or multiple subpopulations.
Methods
Generating Graphs of Differing Heterogeneity
In Figure 3, we presented the results of SIR simulations of epidemics run on graphs of size N = 200 and the mean degree is 7, where the parameter of interest is . Each curve represents a different value of the graph heterogeneity. We implemented the following procedure from [57] for generating graphs as a function of a continuous parameter ():
The following simple procedure generates a graph that has the desired heterogeneity:
-
1.
Choose values of (heterogeneity), the mean node degree (which can be set through the relationship via and an appropriate scale parameter (), and (number of nodes).
-
2.
Draw N random samples from the following distribution using and , rounding these samples to the nearest integer, since the degree of a node can only take on integer values.
-
3.
With the sampled degree distribution from the previous step, now use the configuration model method [58] (which samples over the space of all possible graphs corresponding to a particular degree distribution) to generate a corresponding graph.
This yields a valid graph with the desired amount of heterogeneity as specified by .
Simulating Epidemics on Graphs of Differing Heterogeneity
We implemented the following simulation procedure from [57] for implementing an SIR epidemic on a graph:
Given a graph of heterogeneity , fix a transmission probability and recovery probability :
-
1.
At time , fix a small fraction of nodes to be chosen uniformly on the graph and assign them to the Infected state. The remaining fraction of nodes start as Susceptible.
-
2.
For each , for each pair of adjacent S and I nodes, the susceptible node becomes infected with probability .
-
3.
For each , each infected node recovers with probability .
-
4.
For each simulation, record the overshoot as the difference between the number of susceptibles at the peak of infection prevalence and the end of the time dynamics.
-
5.
Repeat steps (1-4) times for each value of .
-
6.
Repeat steps (1-5) for each value of .
Code for the network simulations is provided in the Supplemental Information.
Numerical Solutions and Code
Where needed, equations were solved numerically using the numerical solver in . Code for the network simulations is provided in the Supplemental Information.
Acknowledgements
The author would like to acknowledge generous funding support provided by the National Science Foundation (DMS-2327711) and a gift from the William H. Miller III.
Author Contributions
M.M.N. designed research, performed research, and wrote and reviewed the manuscript.
Competing Interests
The author declares no competing financial or non-financial interests.
Data Availability Statement
Data sharing is not applicable to this article as no new data were created or analyzed in this study.
References
- [1] Roy M. Anderson and Robert M. May “Infectious Diseases of Humans: Dynamics and Control” OUP Oxford, 1992
- [2] Odo Diekmann, Hans Heesterbeek and Tom Britton “Mathematical Tools for Understanding Infectious Disease Dynamics” Princeton University Press, 2013
- [3] Wei-min Liu, Simon A. Levin and Yoh Iwasa “Influence of nonlinear incidence rates upon the behavior of SIRS epidemiological models” In J. Math. Biology 23.2, 1986, pp. 187–204 DOI: 10.1007/BF00276956
- [4] Wei-min Liu, Herbert W. Hethcote and Simon A. Levin “Dynamical behavior of epidemiological models with nonlinear incidence rates” In J. Math. Biology 25.4, 1987, pp. 359–380 DOI: 10.1007/BF00277162
- [5] H.. Hethcote and P. Driessche “Some epidemiological models with nonlinear incidence” In J. Math. Biol. 29.3, 1991, pp. 271–287 DOI: 10.1007/BF00160539
- [6] Shigui Ruan and Wendi Wang “Dynamical behavior of an epidemic model with a nonlinear incidence rate” In J. Differ. Equ. 188.1, 2003, pp. 135–163 DOI: 10.1016/S0022-0396(02)00089-X
- [7] Yu Jin, Wendi Wang and Shiwu Xiao “An SIRS model with a nonlinear incidence rate” In Chaos Solit. Fractals 34.5, 2007, pp. 1482–1497 DOI: 10.1016/j.chaos.2006.04.022
- [8] Andrei Korobeinikov “Global Properties of Infectious Disease Models with Nonlinear Incidence” In Bull. Math. Biol. 69.6, 2007, pp. 1871–1886 DOI: 10.1007/s11538-007-9196-y
- [9] Romualdo Pastor-Satorras, Claudio Castellano, Piet Van Mieghem and Alessandro Vespignani “Epidemic processes in complex networks” Publisher: American Physical Society In Rev. Mod. Phys. 87.3, 2015, pp. 925–979 DOI: 10.1103/RevModPhys.87.925
- [10] Alexei V. Tkachenko et al. “Time-dependent heterogeneity leads to transient suppression of the COVID-19 epidemic, not herd immunity” Publisher: Proceedings of the National Academy of Sciences In PNAS 118.17, 2021, pp. e2015972118 DOI: 10.1073/pnas.2015972118
- [11] M. M. Gomes et al. “Individual variation in susceptibility or exposure to SARS-CoV-2 lowers the herd immunity threshold” In JTB 540, 2022, pp. 111063 DOI: 10.1016/j.jtbi.2022.111063
- [12] Antonio Montalbán, Rodrigo M. Corder and M. M. Gomes “Herd immunity under individual variation and reinfection” In J. Math. Biol. 85.1, 2022, pp. 2 DOI: 10.1007/s00285-022-01771-x
- [13] Robert Axelrod “The Complexity of Cooperation: Agent-Based Models of Competition and Collaboration” In The Complexity of Cooperation Princeton University Press, 1997 DOI: 10.1515/9781400822300
- [14] Damon Centola “The Spread of Behavior in an Online Social Network Experiment” Publisher: American Association for the Advancement of Science In Science 329.5996, 2010, pp. 1194–1197 DOI: 10.1126/science.1185231
- [15] Alessandro Vespignani “Modelling dynamical processes in complex socio-technical systems” Number: 1 Publisher: Nature Publishing Group In Nat Phys 8.1, 2012, pp. 32–39 DOI: 10.1038/nphys2160
- [16] Sune Lehmann and Yong-Yeol Ahn “Complex Spreading Phenomena in Social Systems: Influence and Contagion in Real-World Social Networks” Google-Books-ID: 53hhDwAAQBAJ Springer, 2018
- [17] Laurent Hébert-Dufresne, Samuel V. Scarpino and Jean-Gabriel Young “Macroscopic patterns of interacting contagions are indistinguishable from social reinforcement” Number: 4 Publisher: Nature Publishing Group In Nat Phys 16.4, 2020, pp. 426–431 DOI: 10.1038/s41567-020-0791-2
- [18] Jordl Bascompte and Ricard V. Solé “Rethinking complexity: modelling spatiotemporal dynamics in ecology” Publisher: Elsevier In TREE 10.9, 1995, pp. 361–366 DOI: 10.1016/S0169-5347(00)89134-X
- [19] Josef Hofbauer and Karl Sigmund “Evolutionary Games and Population Dynamics” Cambridge University Press, 1998
- [20] Jacopo Grilli, György Barabás, Matthew J. Michalska-Smith and Stefano Allesina “Higher-order interactions stabilize dynamics in competitive network models” Number: 7666 Publisher: Nature Publishing Group In Nature 548.7666, 2017, pp. 210–213 DOI: 10.1038/nature23273
- [21] Austin Taylor and Amy Crizer “A Modified Lotka-Volterra Competition Model with a Non-Linear Relationship Between Species” In Rose-Hulman Undergrad. Math J. 6.2, 2017 URL: https://scholar.rose-hulman.edu/rhumj/vol6/iss2/8
- [22] Robert M. May, Simon A. Levin and George Sugihara “Ecology for bankers” Number: 7181 Publisher: Nature Publishing Group In Nature 451.7181, 2008, pp. 893–894 DOI: 10.1038/451893a
- [23] W. Arthur “Foundations of complexity economics” Number: 2 Publisher: Nature Publishing Group In Nat Rev Phys 3.2, 2021, pp. 136–145 DOI: 10.1038/s42254-020-00273-3
- [24] Melanie I. Stefan and Nicolas Le Novère “Cooperative Binding” Publisher: Public Library of Science In PLOS Comput. Biology 9.6, 2013, pp. e1003106 DOI: 10.1371/journal.pcbi.1003106
- [25] William Goffman and Vaun A. Newill “Generalization of Epidemic Theory: An Application to the Transmission of Ideas” Number: 4955 Publisher: Nature Publishing Group In Nature 204.4955, 1964, pp. 225–228 DOI: 10.1038/204225a0
- [26] Alain Barrat, Marc Barthélemy and Alessandro Vespignani “Dynamical Processes on Complex Networks” Google-Books-ID: fUAhAwAAQBAJ Cambridge University Press, 2008
- [27] Damon Centola “How Behavior Spreads: The Science of Complex Contagions” Google-Books-ID: V3GYDwAAQBAJ Princeton University Press, 2018
- [28] John C. Doyle, Bruce A. Francis and Allen R. Tannenbaum “Feedback Control Theory” Google-Books-ID: zrPDAgAAQBAJ Courier Corporation, 2013
- [29] Suresh P. Sethi “What Is Optimal Control Theory?” In Optimal Control Theory: Applications to Management Science and Economics Cham: Springer International Publishing, 2019, pp. 1–26 DOI: 10.1007/978-3-319-98237-3_1
- [30] William R. Catton “Overshoot: The Ecological Basis of Revolutionary Change” University of Illinois Press, 1982
- [31] Mathis Wackernagel et al. “Tracking the ecological overshoot of the human economy” Publisher: Proceedings of the National Academy of Sciences In PNAS 99.14, 2002, pp. 9266–9271 DOI: 10.1073/pnas.142033699
- [32] Corey J.. Bradshaw et al. “Underestimating the Challenges of Avoiding a Ghastly Future” In Front. Conserv. Sci. 1, 2021 URL: https://www.frontiersin.org/articles/10.3389/fcosc.2020.615419
- [33] Andrew L. Fanning, Daniel W. O’Neill, Jason Hickel and Nicolas Roux “The social shortfall and ecological overshoot of nations” Number: 1 Publisher: Nature Publishing Group In Nat Sustain 5.1, 2022, pp. 26–36 DOI: 10.1038/s41893-021-00799-z
- [34] B. Rosengarten, S. Osthaus and M. Kaps “Overshoot and Undershoot: Control System Analysis of Haemodynamics in a Functional Transcranial Doppler Test” In Cerebrovas. Dis. 14.3, 2002, pp. 148–152 DOI: 10.1159/000065672
- [35] Maximilian M. Nguyen, Ari S. Freedman, Sinan A. Ozbay and Simon A. Levin “Fundamental bound on epidemic overshoot in the SIR model” Publisher: Royal Society In J. R. Soc. Interface 20.209, 2023, pp. 20230322 DOI: 10.1098/rsif.2023.0322
- [36] Qun Li et al. “Early Transmission Dynamics in Wuhan, China, of Novel Coronavirus–Infected Pneumonia” Publisher: Massachusetts Medical Society _eprint: https://doi.org/10.1056/NEJMoa2001316 In NEJM 382.13, 2020, pp. 1199–1207 DOI: 10.1056/NEJMoa2001316
- [37] Marco D’Arienzo and Angela Coniglio “Assessment of the SARS-CoV-2 basic reproduction number, R0, based on the early phase of COVID-19 outbreak in Italy” In Biosaf. and Health 2.2, 2020, pp. 57–59 DOI: 10.1016/j.bsheal.2020.03.004
- [38] Maimuna S. Majumder and Kenneth D. Mandl “Early transmissibility assessment of a novel coronavirus in Wuhan, China” In SSRN, 2020, pp. 3524675 DOI: 10.2139/ssrn.3524675
- [39] T. Hollingsworth, Roy M. Anderson and Christophe Fraser “HIV-1 Transmission, by Stage of Infection” In J. Infect. Dis. 198.5, 2008, pp. 687–693 DOI: 10.1086/590501
- [40] Matthew Biggerstaff et al. “Estimates of the reproduction number for seasonal, pandemic, and zoonotic influenza: a systematic review of the literature” In BMC Infect. Dis. 14.1, 2014, pp. 480 DOI: 10.1186/1471-2334-14-480
- [41] Lewis F. Buss et al. “Three-quarters attack rate of SARS-CoV-2 in the Brazilian Amazon during a largely unmitigated epidemic” Publisher: American Association for the Advancement of Science In Science 371.6526, 2021, pp. 288–292 DOI: 10.1126/science.abe9728
- [42] Andreas Handel, Ira M Longini and Rustom Antia “What is the best control strategy for multiple infectious disease outbreaks?” Publisher: Royal Society In Proc. R. Soc. Lond. B 274.1611, 2006, pp. 833–837 DOI: 10.1098/rspb.2006.0015
- [43] Francesco Di Lauro, István Z. Kiss and Joel C. Miller “Optimal timing of one-shot interventions for epidemic control” Publisher: Public Library of Science In PLOS Comput. Biology 17.3, 2021, pp. e1008763 DOI: 10.1371/journal.pcbi.1008763
- [44] Dylan H. Morris, Fernando W. Rossine, Joshua B. Plotkin and Simon A. Levin “Optimal, near-optimal, and robust epidemic control” Publisher: Nature Publishing Group In Commun Phys 4.1, 2021, pp. 1–8 DOI: 10.1038/s42005-021-00570-y
- [45] Pratyush K. Kollepara, Rebecca H. Chisholm, István Z. Kiss and Joel C. Miller “Ethical dilemma arises from optimizing interventions for epidemics in heterogeneous populations” Publisher: Royal Society In J. R. Soc. Interface 21.211, 2024, pp. 20230612 DOI: 10.1098/rsif.2023.0612
- [46] Glenn Ellison “Implications of Heterogeneous SIR Models for Analyses of COVID-19”, Working Paper Series 27373 National Bureau of Economic Research, 2020 DOI: 10.3386/w27373
- [47] Łukasz Rachel “An Analytical Model of Covid-19 Lockdowns” In Center for Macroeconomics, 2020
- [48] David I. Ketcheson “Optimal control of an SIR epidemic through finite-time non-pharmaceutical intervention” In J. Math. Biol. 83.1, 2021, pp. 7 DOI: 10.1007/s00285-021-01628-9
- [49] Veronika I. Zarnitsyna et al. “Intermediate levels of vaccination coverage may minimize seasonal influenza outbreaks” Publisher: Public Library of Science In PLoS One 13.6, 2018, pp. e0199674 DOI: 10.1371/journal.pone.0199674
- [50] Dasha Majra, Jayme Benson, Jennifer Pitts and Justin Stebbing “SARS-CoV-2 (COVID-19) superspreader events” In J. Infection 82.1, 2021, pp. 36–40 DOI: 10.1016/j.jinf.2020.11.021
- [51] Ryo Fujie and Takashi Odagaki “Effects of superspreaders in spread of epidemic” In Physica A 374.2, 2007, pp. 843–852 DOI: 10.1016/j.physa.2006.08.050
- [52] Bjarke Frost Nielsen, Lone Simonsen and Kim Sneppen “COVID-19 Superspreading Suggests Mitigation by Social Network Modulation” Publisher: American Physical Society In Phys. Rev. Lett. 126.11, 2021, pp. 118301 DOI: 10.1103/PhysRevLett.126.118301
- [53] M… Newman “Spread of epidemic disease on networks” Publisher: American Physical Society In Phys. Rev. E 66.1, 2002, pp. 016128 DOI: 10.1103/PhysRevE.66.016128
- [54] Yang Wang, D. Chakrabarti, Chenxi Wang and C. Faloutsos “Epidemic spreading in real networks: an eigenvalue viewpoint” ISSN: 1060-9857 In 22nd International Symposium on Reliable Distributed Systems, 2003. Proceedings., 2003, pp. 25–34 DOI: 10.1109/RELDIS.2003.1238052
- [55] Matt J Keeling and Ken T.D Eames “Networks and epidemic models” Publisher: Royal Society In J. R. Soc. Interface 2.4, 2005, pp. 295–307 DOI: 10.1098/rsif.2005.0051
- [56] István Z. Kiss, Joel C. Miller and Péter L. Simon “Mathematics of Epidemics on Networks: From Exact to Approximate Models” Google-Books-ID: DlEnDwAAQBAJ Springer, 2017
- [57] Sinan A. Ozbay and Maximilian M. Nguyen “Parameterizing network graph heterogeneity using a modified Weibull distribution” Number: 1 Publisher: SpringerOpen In Appl Netw Sci 8.1, 2023, pp. 1–12 DOI: 10.1007/s41109-023-00544-9
- [58] Mark Newman “Networks” Google-Books-ID: YdZjDwAAQBAJ Oxford University Press, 2018
- [59] Nicholas C Grassly and Christophe Fraser “Seasonal infectious disease epidemiology” Publisher: Royal Society In Proc. R. Soc. Lond. B 273.1600, 2006, pp. 2541–2550 DOI: 10.1098/rspb.2006.3604
- [60] Sonia Altizer et al. “Seasonality and the dynamics of infectious diseases” _eprint: https://onlinelibrary.wiley.com/doi/pdf/10.1111/j.1461-0248.2005.00879.x In Ecol. Lett. 9.4, 2006, pp. 467–484 DOI: 10.1111/j.1461-0248.2005.00879.x
- [61] Joan L. Aron and Ira B. Schwartz “Seasonality and period-doubling bifurcations in an epidemic model” In JTB 110.4, 1984, pp. 665–679 DOI: 10.1016/S0022-5193(84)80150-2
Supplemental Materials: Upper Bounds on Overshoot in SIR Models with Nonlinear Incidence
Example 2: = Invertible Polynomials of
Next, let us consider invertible polynomials. Having access to large degree polynomials will allow us to make arbitrarily sharp incidence terms. This allows one to make the growth rate of the epidemic even sharper than the exponential case if needed. Or in general, having access to the toolbox of all polynomials will allow one to pick an appropriately steep incidence term that best matches the data of the particular outbreak being analyzed. While the set of invertible polynomials is a relatively small subset of all polynomials, it still contains an infinitely large number of possible functions. Because the procedure will require integration of while it is in the denominator, the algebraic details of doing this for higher-order polynomials with lower-order terms can quickly become cumbersome. So let us illustrate a test case using just the leading term of a generic cubic function. Let , where .
We start at Step A. by solving for the rate of change of as a function of by taking the ratio of and .
| (1) |
from which it follows on integration that is constant along any trajectory.
For Step B., consider the conserved quantity at both the beginning () and end () of the epidemic.
hence
| (2) |
Using the initial conditions ( and , where ) and asymptotic condition () yields:
| (3) |
For Step C., we find the inverse of .
| (4) |
| (5) |
For Step E., differentiation with respect to and setting the equation to zero to solve for the critical yields:
| (6) |
whose solution is .
For Step F., using in the overshoot equation (5) to obtain the value of the maximal overshoot for this model, yields:
| (7) |
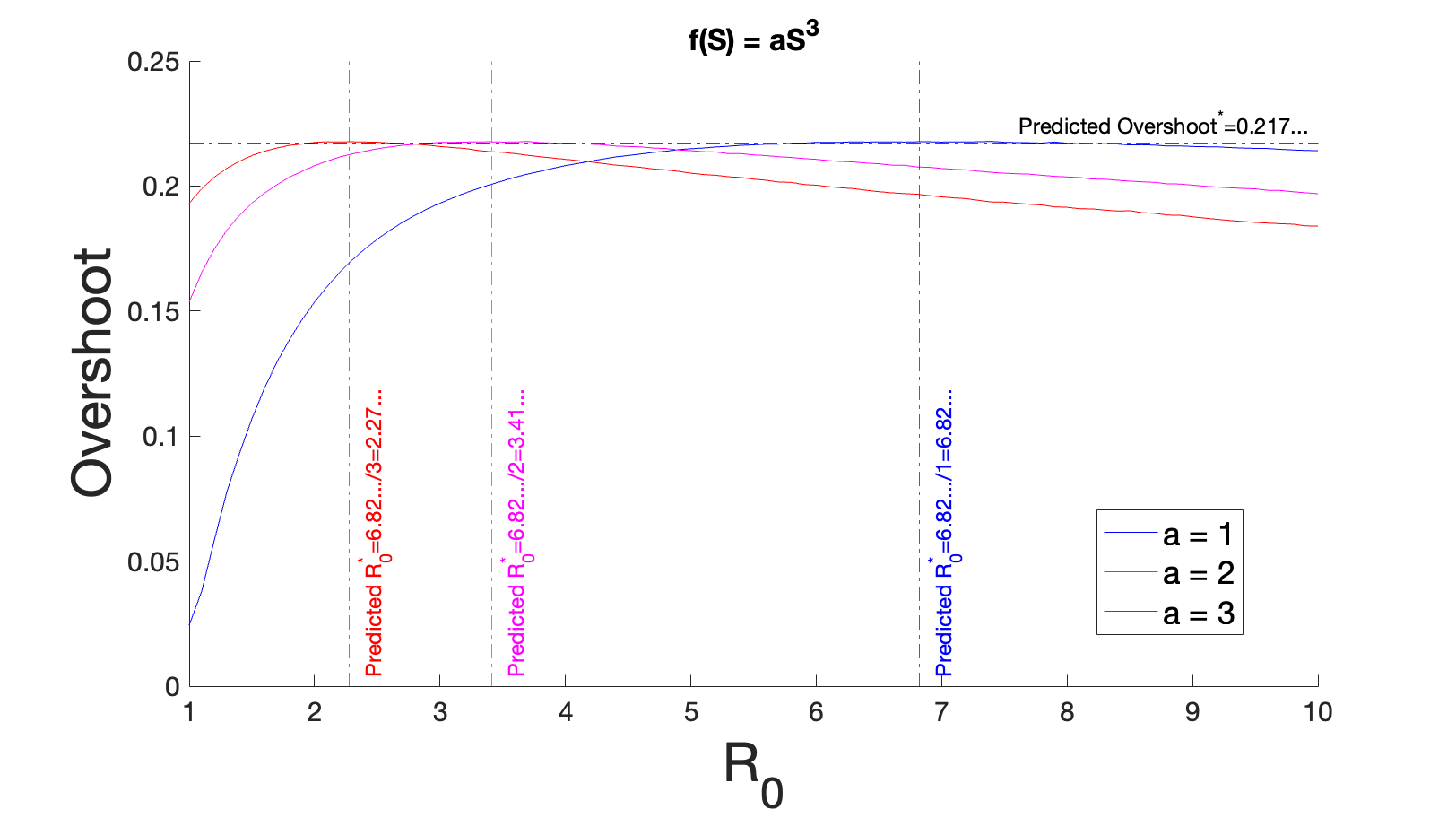
Thus, the maximal overshoot for incidence functions of the form is 0.217… .
| (8) |
This prediction of the maximal overshoot being independent of , whereas the corresponding critical is inversely proportional to is verified numerical in Supplemental Figure 1. Furthermore, it can be shown that the independence of the maximal overshoot of carries holds for any . Since can be absorbed into , the maximal overshoot is consequently independent of and instead only depends on the power of .
Example 3:
The last example considered here is a periodic function of , namely . This might be helpful in a scenario where one gets periodic fluctuations in the incidence rate. This might be relevant for scenarios that try to capture cyclical effects such as seasonality [59]. Some models have accounted for seasonality in the incidence through incorporating a periodic function into the transmission parameter [60, 61]. Here we make the assumption the periodicity in the incidence enters through the susceptibles.
We start at Step A. by solving for the rate of change of as a function of by taking the ratio of and .
from which it follows on integration using the substitution that is constant along all trajectories.
For Step B., consider the conserved quantity at both the beginning () and end () of the epidemic.
hence
| (9) |
Using the initial conditions ( and , where ) and asymptotic condition () yields:
| (10) |
For Step C., we find the inverse of .
| (11) |
| (12) |
For Step E., differentiation of both sides with respect to and setting the equation to zero to solve for the critical yields:
| (13) |
Solving this transcendental equation (13) requires first specifying the value of parameter . For instance, specifying and solving the equation numerically yields .
For Step F., we use in the overshoot equation (12) to obtain the value of the maximal overshoot for this model, . For , we obtain:
| (14) |
Thus, the maximal overshoot for incidence functions of the form is 0.293… .
| (15) |
Now consider , which produces a non-monotonic over the unit interval (Supplemental Figure 2a). Solving (13) for yields . Repeating Steps F. and G. when yields:
| (16) | ||||
| (17) |
This leads to the question of what the applicable domain of is. The larger the value of , the stronger the non-monotonicity of is (Supplemental Figure 2a). We can first eliminate values based on the condition . Clearly that condition is violated if is not positive, since is always positive because and are both positive-definite. Since , then is negative when . Furthermore, since we have a formula for using (10), we can set up the inequality explicitly.
These result for the different cases of are shown in Supplemental Figure 2b.
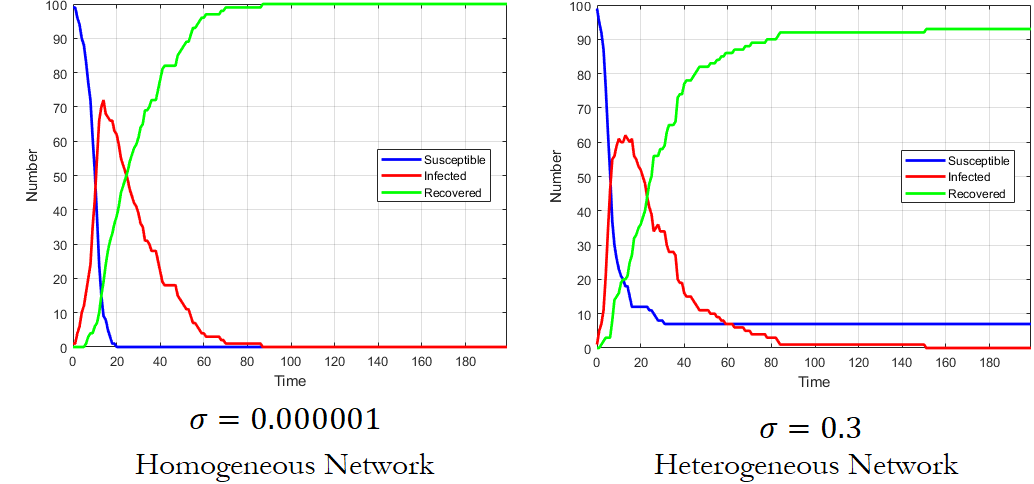
Time Series for Comparing Overshoot in Homogeneous and Heterogeneous Networks
To provide intuition on why heterogeneous networks can have higher overshoot at larger transmission compared to their more homogeneous counterparts, we look in the time-series data of the epidemic.
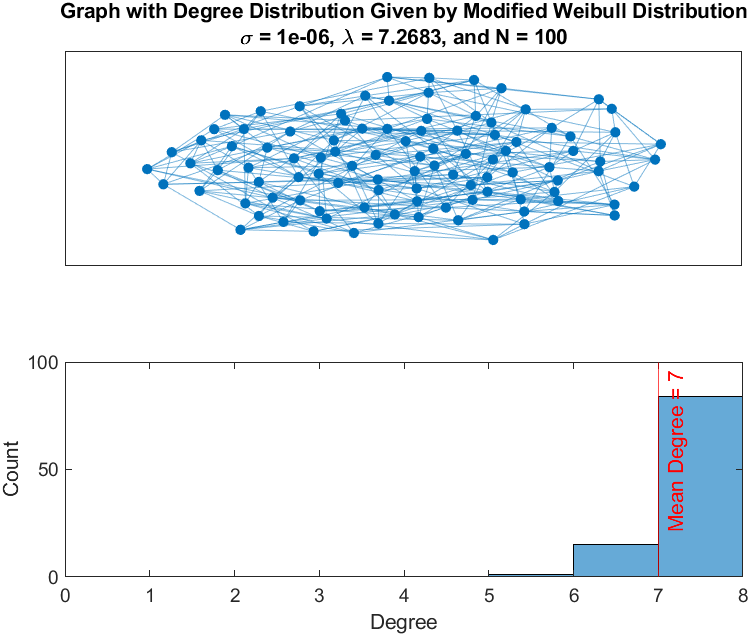
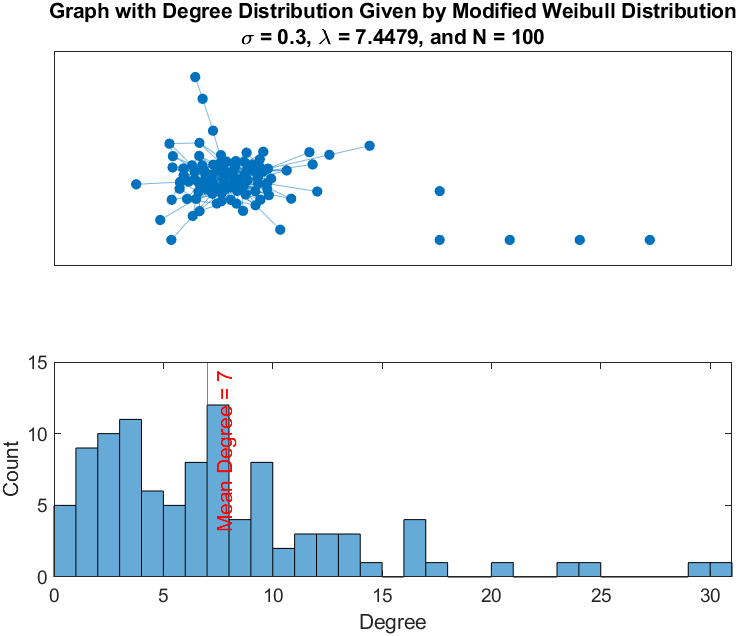
Shown is an example from a network with a very homogeneous network distribution (, Supplemental Figure 4) and a moderately heterogeneous network (, Supplemental Figure 5). The time series for a simulation on both networks in shown in Supplemental Figure 3. Aside from , the other simulation parameters are held constant (i.e. number of nodes (N=100), transmission probability (), recovery probability (), number of initially infected individuals = 1, and = 7).
Supplemental Materials: Upper Bounds on Overshoot in the SIR Models with Nonlinear Incidence
Code to Generate Figures
Code executed in MATLAB R2023a. \UseRawInputEncoding